
Want to create or adapt books like this? Learn more about how Pressbooks supports open publishing practices.

Chapter 3: Cyberbullying Within the Context of Peers and School
Krista Mehari and Natasha Basu
Effective cyberbullying prevention is based on an accurate understanding of risk and protective factors of cyberbullying across systems. Cyberbullying prevention should include individual, relationship, community, and societal factors. Cyberbullying is closely related to in-person bullying and aggression, but it has some unique risk and protective factors also. This chapter conceptualizes cyberbullying as broadly within the umbrella of peer interactions. In this chapter, we describe how other peer interactions and peer relationships can predict the occurrence of cyberbullying and cybervictimization. Similarly, given that youth spend the majority of their time at school, school plays a fundamental role in adolescents’ lives. In this chapter, we also discuss school-level factors that predict or reduce cyberbullying. These factors can be leveraged for school-based prevention. The chapter concludes with the current understanding of effective school-based prevention and school practices in responding to cyberbullying.
As discussed in previous chapters, cyberbullying is perpetrated through electronic communication technologies. Individual, peer, and school factors play an important role in the development of cyberbullying behaviors. Cyberbullying involvement has significant implications for adolescents’ peer and school interactions. Within the context of the socio-ecological model introduced in Chapter 1, peer interactions fall within “relationship” factors, and school factors fall within the “community” level. Cyberbullying happens among peers, so it is important to understand how other peer interactions and peer relationships can predict the occurrence of cyberbullying and cybervictimization. Similarly, understanding school-level factors that predict or reduce cyberbullying is vital for effective intervention.
ASSOCIATIONS BETWEEN CYBERBULLYING INVOLVEMENT AND BULLYING INVOLVEMENT
Cyberbullying and cybervictimization are closely related to in-person bullying and in-person victimization. Many studies have demonstrated strong concurrent relations between cyberbullying and in-person bullying. According to a meta-analysis, in-person bullying is one of the best predictors of cyberbullying. The only stronger correlate of cyberbullying identified in the meta-analysis was cybervictimization. [1] Most of the research on what predicts cyberbullying has been conducted in Western countries. [2]
Research across Asian countries is limited. The available research demonstrates a positive association between in-person bullying and cyberbullying. In a study conducted among adolescents in New Delhi, India, cyberbullying was correlated with indirect or relational bullying but not with physical bullying. [3] In a study conducted with Chinese high school students, in-person bullying was found to be a significant and strong predictor of cyberbullying. [4] Research conducted among South Korean adolescents found a significant positive association between in-person bullying and cyberbullying. [5] Additionally, Kwan and Skoric [6] found strong associations between school bullying and cyberbullying ( r = .56) in adolescents from Singapore. In Hong Kong, a study conducted with 1917 adolescents found a positive correlation between in-person bullying and cyberbullying ( r = .51). [7] Further, in-person bullying was positively associated with cyberbullying in Cyprus ( r = .61). [8]
Based on the existing research in both Western and Asian countries, it is likely that both cyberbullying and in person bullying are types of bullying that manifest through different media. Almost all youth who perpetrate cyberbullying also perpetrate in-person bullying. It is highly uncommon for youth to perpetrate cyberbullying without also having perpetrated in-person bullying. However, it is likely that a smaller percentage of youth who perpetrate in-person bullying also perpetrate cyberbullying. [9] , [10] , [11] These findings suggest that interventions to reduce in-person bullying may be effective in reducing cyberbullying. However, given that cyberbullying is different from bullying, those interventions may need to be adapted slightly to address the unique aspects of cyberbullying.
Similarly, cybervictimization and in-person victimization are also closely correlated. In the meta-analysis conducted by Kowalski and colleagues, [12] cybervictimization and in-person victimization were correlated at r = .4 indicating a small-to-medium relationship. Again, the only stronger correlate of cybervictimization was cyberbullying. [13] More recent research using behavior-based measures has identified correlations between cybervictimization and in-person victimization as large as .85, indicating a large relationship. Again, most research has been conducted in Western countries.
Emerging research in Asia provides emerging support for the relation between cybervictimization and in-person victimization. For example, a study conducted in Hong Kong found in-person victimization was positively associated with cyberbullying victimization. [14] This relationship was also significant in South Korean adolescents. [15] A positive relationship was demonstrated between in-person victimization and cybervictimization in China ( r = .18), [16] Cyprus ( r = .48), [17] Japan ( r = .32), [18] India ( r = .13), [19] Indonesia ( r = .73), [20] and Singapore ( r = .48). [21] However, one study conducted among middle school students in New Delhi, India did not find a relation between cybervictimization and in-person victimization. [22] However, the majority of the research suggests that cybervictimization and in-person victimization are correlated in Asia. Together, there appears to be a significant association between in-person bullying and cyberbullying across different cultures and countries in Asia.
Based on emerging longitudinal research, it appears that youth are first victimized in person. Youth who are victimized in-person are more likely to experience increases in cybervictimization. For example, it is possible that rumors that are started about an adolescent in person are then spread via text messages or social media. It is also possible that adolescents who victimize a particular adolescent in person begin victimizing that adolescent online in other ways (e.g., making fun of photos, posting rude comments, sending threats). In contrast, youth who are cyber-victimized are not more likely to experience increases in in-person victimization. [23] , [24] That is, there is no evidence that victimization that starts online causes an increase in in-person victimization.

ASSOCIATIONS BETWEEN CYBERBULLYING INVOLVEMENT AND INDIVIDUAL FACTORS
A range of individual-level characteristics, such as demographics (e.g., gender, age) and psycho-social factors (such as attitudes and impulsivity) have been explored as possible factors of cyberbullying. These factors can predict why some youth are more likely to be involved in cyberbullying than others.
GENDER DIFFERENCES IN CYBERBULLYING
There is varying evidence about the rates of cyberbullying across gender. Multiple studies have identified higher prevalence of self-reported cyberbullying among male adolescents. This includes a sample adolescents in Australia, Canada, Finland, Taiwan, Turkey, Singapore, and Switzerland. [25] , [26] , [27] , [28] , [29] , [30] However, several of these studies used the word “bullied” in their measure, which male adolescents may be more willing to endorse because it is less socially undesirable for a boy to admit to bullying than for a girl. Ybarra and Mitchell (2007), who avoided the word “bullied” in their measure, found no gender differences in prevalence of cyberbullying. Still, male adolescents were more likely to be frequent aggressors. [31] On the other hand, Calvete and colleagues (2010) found that there were no gender differences in frequency of perpetration overall, but that male adolescents were more likely to send sexual messages and to post videos of assaults. [32]
No gender differences in perpetration of cyberbullying were found in a number of studies in Canada. These studies included ethnically diverse samples of adolescents in Europe, the United States, and online. [33] , [34] , [35] , [36] , [37] , [38] , [39] , [40] , [41] , [42] Overall, findings indicate that there are no gender differences. If gender differences exist, male adolescents are slightly more likely to self-report perpetration of cyberbullying. Despite these findings, researchers continue to argue that female adolescents prefer indirect and relational forms of aggression that are easily perpetrated through electronic means. [43] This is not supported, and in fact often contradicted, by research.
Gender differences in cyberbullying in Asian countries and specifically in India have yet to be fully explored. One study of 11-15-year-old students in the Delhi area found that male adolescents reported higher prevalence of cybervictimization. There were no gender differences in cyberbullying perpetration. [44] In general, existing surveillance data suggest that male adolescents have greater access to electronic communication devices than female adolescents in India, especially in rural areas. [45] It is possible that male adolescents may be more likely to have cyberbullying involvement simply due to access. More research is needed to explore whether there are gender differences in cyberbullying involvement in India.
AGE DIFFERENCES IN CYBERBULLYING ACROSS ADOLESCENCE
In addition to gender differences, several studies have explored age differences in cyberbullying across adolescence. There is some evidence that cyberbullying peaks in early adolescence (11-14 years old) and decreases in later adolescence (15 years old and older). This finding is comparable to the trajectory observed in in-person bullying. This broad pattern has been found in the U.S. and Canada. [46] , [47] , [48] It is possible that as adolescents enter secondary schools (e.g., middle school, junior high, high school) where they are first exposed to cyberbullying. Then they begin to perpetrate cyberbullying due to observational learning and perhaps reactive aggression. It is unclear whether this pattern is comparable in other countries, especially in lower or middle-income countries, where private access to electronic communication devices might be less common in early adolescence.
PSYCHO-SOCIAL RISK FACTORS FOR CYBERBULLYING INVOLVEMENT
Most research on individual-level factors associated with cyberbullying involvement has been cross-sectional. That is, the hypothesized “risk” factors are assessed at the same time point as the outcome (cyberbullying involvement). Therefore, it is impossible to determine whether these factors cause cyberbullying, whether cyberbullying causes those other factors, or whether something else (something that was not assessed) causes both cyberbullying involvement and the other factors. Because of this, at most, we can assume that these factors co-occur with cyberbullying involvement.
Psycho-social characteristics that may place adolescents at risk for cyberbullying perpetration include low levels of empathy, moral disengagement, beliefs supporting aggression, impulsivity, other delinquent behavior, and substance use. [49] , [50] , [51] , [52] , [53] , [54] In addition, adolescents who use the Internet more frequently and engage in more risky online behaviors (e.g., sharing personal information, agreeing to meet in person with someone they met online) are more likely to perpetrate cyberbullying. [55] Patterns of Internet usage also predict other digital risks such as online sexual solicitations and sexual risk behaviors, exposure to a variety of explicit content, and information breaches and privacy violations. This is explained in further detail in Chapter 5 of this book.
Similar to cyberbullying perpetration, psycho-social characteristics that place adolescents at risk for cybervictimization include low levels of empathy, beliefs supporting aggression, lower social intelligence and social anxiety, lower academic achievement, substance use, and loneliness. [56] As with cyberbullying perpetration, adolescents who spend more time on the Internet and engage in more risky online behaviors are more likely to be victimized. [57] , [58] It is important to note that most of the research on psycho-social predictors of cyberbullying involvement was conducted in Western and high-income countries. It is unclear whether risks for cyberbullying perpetration would be the same or different in Asian countries and lower- to middle-income countries. Because of this, more research is needed to understand what individual-level factors may explain individual differences in cyberbullying involvement among youth in Asian countries.
ASSOCIATIONS BETWEEN CYBERBULLYING INVOLVEMENT AND PEER FACTORS
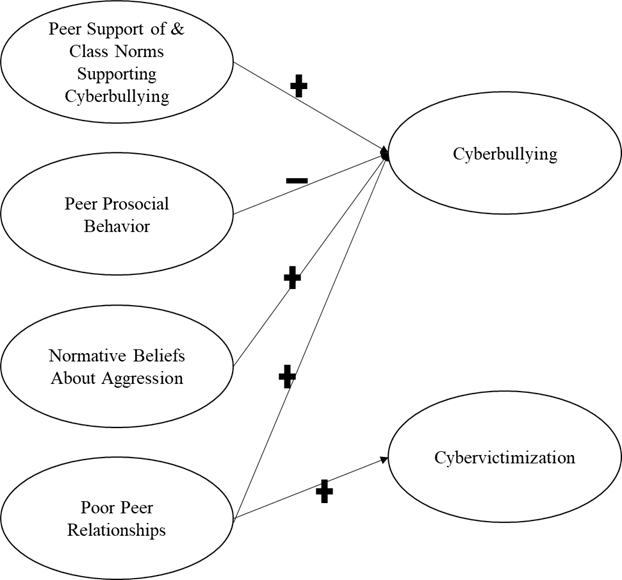
Peer factors fall within the “relationship” domain of the socio-ecological model. Like individual-level factors, they explain a significant percentage of differences in youths’ levels of cyberbullying involvement. Broadly, peer attitudes supporting bullying or cyberbullying predict individual youths’ levels of bullying and cyberbullying perpetration. [59] This may be due to social mimicry. Specifically, peers who support cyberbullying may be more likely to model cyberbullying behaviors. This may cause increased cyberbullying due to increased exposure to aggressive peer models. [60] In addition, when adolescents do try out aggressive behaviors, they are likely to be reinforced by their peers if their peers have attitudes justifying cyberbullying perpetration. For example, when adolescents believe their peers support and approve of cyberbullying, they are more likely to take online risks like cyberbullying. [61] Adolescents who have pro-social peers have lower levels of cyberbullying.
In a peer group that supports aggression, using aggression may provide adolescents with power, status, and privilege among their peers. This finding is consistent with a research study conducted with adolescents from Singapore and Malaysia, whose ethnic identification included Chinese, Malay, and Indian. It found a positive association between cyberbullying and normative beliefs about aggression. [62] Reinforcement by friends was found to be positively associated with cyberbullying in Japan. [63] This finding is supported by a qualitative study in Indonesia which demonstrated that group conformity facilitated an increase in the prevalence of cyberbullying among adolescents. [64] Finally, a study in China found that pro-cyberbullying class norms predicted the occurrence of cyberbullying in high school. [65] Interestingly, this was only true when students perceived their class to be highly cohesive. In contrast, when a high school student perceived their class to have low cohesion, there was not a significant relationship between pro-cyberbullying class norms and incidents of cyberbullying. [66] This study demonstrated one possible mechanism for why these normative beliefs might vary across groups.
Popularity and social acceptance may play an interesting role in cyberbullying. One study of adolescents in the western United States found that both cyberbullying and cybervictimization were positively associated with popularity and social acceptance cross-sectionally. In addition, popularity predicted increases in cyberbullying, whereas cyberbullying predicted increases in popularity for girls but decreases in popularity for boys. Social acceptance predicted increased cyberbullying for boys but not for girls. [67] In a sample of students in secondary schools in Germany, cybervictimization during chat sessions was negatively associated with self-reported perceived popularity with other chatters. [68] In a sample of elementary school children in a predominantly white, upper SES school in the United States, cyberbullying perpetration was concurrently associated with lower popularity and social acceptance. Both popularity and social acceptance were measured by peer report. Similarly, cyberbullying was associated with fewer mutual friendships. [69] Currently, the majority of the research on popularity, social acceptance, and cyberbullying is conducted in Europe and North America. As such, there is no research on the generalizability of these relationships in Asian countries.
The relation between peer rejection and cyberbullying is complex. In a study of middle school students in the midwestern United States, peer rejection was concurrently correlated with relational and verbal cyberbullying. It also predicted increases in cyberbullying. [70] Cyberbullying was also linked to loneliness in a sample of elementary school children in the United States. [71] Research conducted in Asia also suggests that cyberbullying involvement is associated with poor peer relationships. For example, a study of Chinese middle school students found a positive association between cyberbullying and loneliness. [72] Similarly, another cross-sectional study of Chinese middle school students reported better peer relationships were negatively associated with engagement in cyberbullying. [73] Cross-national research conducted with adolescents living in China, India, and Japan found that peer attachment was negatively associated with cyberbullying perpetration in China and India, but not in Japan. Additionally, within China, India, and Japan, adolescents who were not involved in cyberbullying had greater peer attachment compared to youth with any involvement in cyberbullying (victimization, perpetration, or some combination of those). [74]
It is possible that peer rejection and aggression are part of a vicious cycle. In this cycle, children who are aggressive in a non-socially skilled way are more likely to be rejected. Children may react to rejection with increased aggression. It is also possible that adolescents engage in cyberbullying as a way to establish their social position and to attempt to maintain their social status. However, it is possible that the skill level of adolescents varies widely. This means that cyberbullying may promote the social status of socially skilled youth, but that it may harm the social status of socially awkward youth. It is also possible that cyberbullying is less reinforced than in-person bullying. Thus, is less likely to promote social dominance, than in-person bullying [75] because of the asynchronicity of interactions during online communications. That is, an adolescent could post a mocking picture of a peer, but not know or notice when it was shared, laughed at, or commented on. It is also possible that fewer peers in the same social circles would know about the post than if it happened in person at school, where youth spend the majority of their time together.
ASSOCIATIONS BETWEEN CYBERBULLYING INVOLVEMENT AND SCHOOL FACTORS
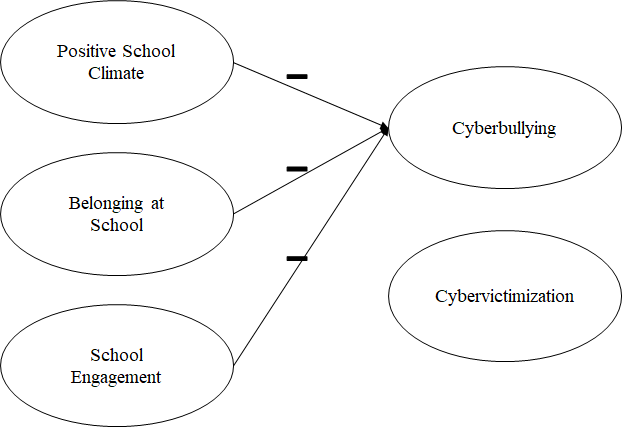
School factors fall within the “community” level of the socio-ecological model. Like individual and relationship level factors, school factors explain a small but significant amount of individual differences in cyberbullying. Although schools are often on the front lines of confronting cyberbullying behaviors (Pelfrey et al., 2015), little is known about the associations between school factors and cyberbullying involvement. It is important to note that cyberbullying appears to have higher rates of perpetration during out-of-school time compared to during school hours (e.g., Smith et al., 2008). Therefore, although supervision and restriction may reduce cyberbullying during the school day, it may not help in prevention of all acts of cyberbullying. Other factors related to school climate, including fostering a positive climate and promoting healthy relationships, may be more important. In a meta-analysis of research mostly conducted in Western countries, school climate and school safety had small but significant correlations with lower rates of cyberbullying perpetration and victimization (Kowalski et al., 2014). That is, adolescents in schools that they perceived to be safe, with positive student-student and student-teacher relationships, were less likely both to perpetrate cyberbullying and experience cybervictimization. In school environments, close relationships with teachers are associated with reduced likelihood of bullying and cyberbullying. [76] Teachers’ awareness of cyberbullying and intervention has also been related to lower rates cyberbullying. [77] At an individual level, youth who are involved in cyberbullying may have more problems at school than youth who are not involved in cyberbullying, such as getting in trouble and not feeling safe at school. [78] , [79]
School risk factors for cyberbullying involvement is an emerging body of research in Asian countries. Wang and colleagues (2019) found in a study conducted in China that adolescents who perceived a more positive school climate were less likely to perpetrate cyberbullying. [80] Further, in a study of Hong Kong youth, a sense of belonging at school was associated with lower levels of cyberbullying perpetration. [81] A more recent study in Hong Kong found different relations between school factors and cyberbullying for male and female students. [82] For male adolescents, positive school experiences and school involvement were negatively associated with cyberbullying perpetration. For female adolescents, a sense of belonging in school was negatively associated with cyberbullying perpetration. [83] Together, these studies underscore the importance of considering school influences to understand developmental processes that lead to cyberbullying.
SCHOOL-BASED PREVENTION PROGRAMS
Schools can be an ideal setting for prevention efforts due to their reach. The heavy majority of youth attend school. Because of this, schools have a golden opportunity to promote the safety, health, well-being, and citizenship of the majority of youth in a country. School-based prevention strategies include primary prevention (strategies to prevent cyberbullying before it begins) and secondary prevention (strategies to reduce the frequency of cyberbullying or mitigate the impact of cyberbullying). A combination of the two strategies is important for a holistic prevention approach. In addition to specific prevention programs, schools can create policies that may serve as primary and secondary prevention strategies. There can be two approaches to these prevention strategies: a punitive, fear-based approach, or a resilience-based approach. A fear-based approach includes heavy restrictions of digital media, zero-tolerance policies, and punishment for undesired behavior without training, modeling, scaffolding of, and reinforcement of desired behavior. In contrast, a resilience-based approach focuses on creating a positive school climate; training, modeling, and reinforcing desired behaviors. It also focuses on building capacity in adult stakeholders to prevent and intervene in cyberbullying. Further it focuses on providing remedial skill-building for youth who engage in cyberbullying.
PRIMARY PREVENTION
Existing reviews of cyberbullying prevention programs suggest that most cyberbullying prevention programs are school-based and show promise of effectiveness. [84] , [85] , [86] However, in general, individual programs have only been supported by a single research study conducted by the program developers. [87] More research is needed to identify the active ingredients for effective school-based cyberbullying prevention programs. Due to the high degree of overlap between cyberbullying and in-person bullying, many of the skills taught in school-based violence or bullying prevention programs are likely to be relevant to the reduction of cyberbullying. Such programs may include anger management, empathy, and problem-solving.
However, because of the differences in circumstances surrounding in-person and electronic communication, those programs may need to be adapted or include cyberbullying-specific modules. For example, teaching adolescents to read facial expressions or other physical cues will not improve empathy in situations where the other person’s facial expressions are not visible. In that case, teaching perspective-taking based on identifying the situation and thinking about how people might feel when they were in that situation may help to improve empathy in electronic communications. Beliefs about aggression are also particularly relevant to aggressive behaviors and may be different for cyberbullying. There is some emerging evidence to support this. [88] Intervention programs may need to target cyberbullying-specific beliefs. It is possible that adolescents perceive the social context for electronic aggression to be less disapproving than for in-person aggression. Initial focus group data also suggests that adults in India may be more tolerant of cyberbullying than of physical bullying. This may cause youth to believe that they may not have effective advocates in the adults close to them. [89] Because of this, school-based efforts may need to include education for parents and guardians on cyberbullying, its impact, and its prevention. In addition, for both youth and adults, digital safety behaviors, including protection of private information, should be taught as part of intervention programs. [90] , [91] A more comprehensive description of digital safety is provided in Chapter 5.
Promoting a positive school climate and positive peer relationships may also help to reduce cyberbullying. Adolescents are unlikely to tell their parents about victimization experiences, and even more unlikely to tell teachers. [92] , [93] , [94] , [95] On the other hand, as much as 75% of victimized adolescents will tell their friends. [96] Friendship is a strong resource for adolescents. It has been shown to mitigate the effects of victimization as well as to reduce the likelihood of victimization occurring in the future. [97] Because of this, interventions could also teach adolescents how they can best help their friends when they know that their friends are perpetrating cyberbullying, being cyber-victimized, or both.
PRIMARY PREVENTION: SCHOOL-LEVEL POLICY
Currently, many schools do not have policies and procedures around appropriate and safe behavior online. There is an urgent need for schools to establish and promulgate expectations for digital behavior and to identify procedures for when those expectations are not met. [98] Clear expectation-setting prior to problematic behavior can often reduce the occurrence of problematic behaviors. These policies should include identification and reinforcement of pro-social behavior both online and in-person. An example of an intervention based on clear expectation-setting and reinforcement of desired behaviors is School-Wide Positive Behavior Support (SWPBS). SWPBS is a widely-used, whole-school behavior support program that focuses on establishing clear behavior expectations for students. It also focuses on consistently reinforcing desired behavior across school settings, and identifying and implementing a range of consequences for problem behaviors. [99] Such school-level strategies can be helpful in preventing cyberbullying before it becomes a problem.
SECONDARY PREVENTION: SCHOOL RESPONSES TO CYBERBULLYING INCIDENTS
Even if the most effective primary prevention strategies are implemented, it is likely that some cyberbullying will occur. This creates a need to establish procedures to respond to cyberbullying. Cyberbullying is unusual in that it does not occur in a physical space. This raises the question of whose responsibility it is to monitor electronic interactions and enforce consequences for adolescents who are perpetrating cyberbullying. Most researchers have pointed to the schools as the primary responsible authority. Despite most cyberbullying occurring outside of school property, schools have an ethical and legal responsibility to intervene when cyberbullying creates an unsafe environment that impedes students’ ability to learn. [100] Schools are placed in a difficult position. On one hand, they may not violate students’ freedom of speech in countries that protect freedom of speech, particularly when that speech is occurring off school grounds. On the other hand, the school is required to provide a safe learning environment with equal access to education. A school is liable in the United States if it has “effectively caused, encouraged, accepted, tolerated, or failed to correct” a hostile environment that impairs a student’s ability to learn (p. S65). [101] Because of schools’ somewhat vague position as monitor and enforcer, it is also important for parents and guardians to be involved. Schools are only responsible to intervene when they are aware of the situation and can demonstrate that the situation is interfering in the learning process in some way. Parents and guardians can advocate for changes in school policy and government regulations, as well as draw media attention to areas of concern. [102] Parents and guardians can also monitor their children’s digital behavior, teach and model respectful interactions, and intervene if their child is aggressive or victimized.
As schools craft policies related to cyberbullying and digital behavior, there are important issues to keep in mind:
- Youth who are victimized should not be responsible for investigating or proving the incident. Before the aggressor is identified and the wrongful nature of the act is established, it is important that the person who reported the aggression (bystander, victim, or parent) does not bear the burden of proving what happened and who did it. It is an unfortunate effect of “innocent until proven guilty” that the victims or reporters are wrong until they prove themselves right. This approach decreases the likelihood that adolescents will put themselves through that painful process. One way to circumvent this unintentional punishment is to establish a school staff member to receive complaints, anonymously if desired, and to investigate the incident. Then, if aggression is established, the steps outlined in school policy must be followed. This will remove the burden of proof from reporters, thus teaching reporters that they will not be punished for seeking help. It will also teach adolescents who are perpetrating aggression that their behavior will be detected and addressed. The process of implementing clear, just school policies and procedures may change the dynamics from a conflict between the aggressor and the reporter (likely the victim) into an established procedure in which school officials take action against a violation of school policy.
- Restriction of victimized youths’ access to electronic media may be punitive and unhelpful. Encouraging adolescents who have been victimized to simply reduce their electronic interactions (e.g., taking down personal pages on social networking sites, or not going online at all) may be the first intervention response that comes to mind for adults. However, fear of online restriction is one of the primary reasons that adolescents do not tell adults about their victimization experiences. It is important to understand that adolescents consider reduced access to communication technologies to be a punishment. [103] , [104] It may be productive to encourage communication between adolescents and their teachers. But before this is done, adolescents must first know that reporting will both resolve the problem and not result in negative outcomes for themselves.
- Abusing youth who perpetrate cyberbullying is not effective in changing behavior. It is important not to place all the blame on adolescents who cyberbully. As shown by the high correlation between cyberbullying and cybervictimization, there are often no purely provocative adolescents or blameless victims. Adolescents learn negative patterns of interactions through modeling and reinforcement. They are often impulsive and misinterpret cues. Sometimes they may simply have difficulty taking the other person’s perspective into account or understanding the damage caused by their actions. In addition, there are currently few clear rules or expectations regarding electronic behavior, which may feed into a perception that aggressive behavior is not a problem and will not be punished. Anticipation of blame also reduces adolescents’ likelihood to report their experiences when victimized, because they believe that the only negative consequences will be for themselves (Mishna et al., 2009). The consequences for aggressive adolescents should be aversive but should also help them to identify pro-social strategies for reaching goals, managing anger, controlling impulsivity, and resolving conflict. Doing this will avoid abusing adolescents who likely have been victimized themselves while promoting a healthy and respectful electronic culture. Specific ways to accomplish these goals may include anger management or perspective-taking training.
- Most policy changes have not been empirically tested. Currently, the best-practice recommendations for school policy are based on descriptive research and anecdotal evidence. To address these issues, creating, implementing, and evaluating policies and procedures for cyberbullying involvement is vital (Hertz & David-Ferdon, 2008).
The following chapters discuss how to avoid cyberbullying and to some extent how to effectively deal with cyberbullying. Chapter four addresses parents’ and caregivers’ needs for guidance and reassurance on how best maintain their children’s safety online and protect against cyberbullying. We emphasize the importance of parent-child communication, warm parent-child relationships, and parental monitoring that supports adolescents’ search for autonomy. In short, this chapter details the role of family, especially parental relationships and media parenting with respect to cyberbullying behavior among youth.
Cyberbullying and cybervictimization are closely related to in-person bullying and victimization. Because we know that a range of individual psychosocial factors, relationship factors, and community factors predict cyberbullying, intervention strategies should not just target individual youth, but should also target peer groups and schools. Schools have the potential to play an important role in cyberbullying prevention. It is important to use the existing research on cyberbullying prevention and bullying prevention so that we can make sure that we are investing our resources in prevention strategies that keep youth safe online.
KEY TAKEAWAYS
- Peer and school factors predict perpetration of cyberbullying.
- Best practice cyberbullying prevention strategies should promote healthy relationship, emotion regulation, and problem-solving skills, as well as digital safety and citizenship.
- Effective prevention and intervention must include school-level policies and procedures that promote a positive school climate, create clear expectations for appropriate behavior, and identify resilience-based strategies to respond to cyberbullying incidents.
- Both school policy and prevention programs must be evaluated and modified to be maximally effective.
- Kowalski RM, Giumetti GW, Schroeder AN, Lattanner MR. Bullying in the digital age: A critical review and meta-analysis of cyberbullying research among youth. Psychological Bulletin 2014;140(4):1073-1073-1137. ↵
- Farrell AD, Thompson EL, Mehari KR, Sullivan TN, Goncy EA. Assessment of in-person and cyber aggression and victimization, substance use, and delinquent behavior during early adolescence. Assessment 2020;27(6):1213-1229. ↵
- Sharma D, Kishore J, Sharma N, Duggal M. Aggression in schools: cyberbullying and gender issues. Asian journal of psychiatry 2017;29:142-145. ↵
- Li Q. Bullying in the new playground: Research into cyberbullying and cyber victimisation. Australasian Journal of Educational Technology 2007;23(4). ↵
- Hong JS, Kim DH, Thornberg R, Kang JH, Morgan JT. Correlates of direct and indirect forms of cyberbullying victimization involving South Korean adolescents: An ecological perspective. Comput Hum Behav 2018;87:327-336. ↵
- Kwan GCE, Skoric MM. Facebook bullying: An extension of battles in school. Comput Hum Behav 2013;29(1):16-25. ↵
- Wong DS, Chan HCO, Cheng CH. Cyberbullying perpetration and victimization among adolescents in Hong Kong. Children and youth services review 2014;36:133-140. ↵
- Solomontos-Kountouri O, Tsagkaridis K, Gradinger P, Strohmeier D. Academic, socio-emotional and demographic characteristics of adolescents involved in traditional bullying, cyberbullying, or both: Looking at variables and persons. International Journal of Developmental Science 2017;11(1-2):19-30. ↵
- Raskauskas J, Stoltz AD. Involvement in traditional and electronic bullying among adolescents. Dev Psychol 2007;43(3):564. ↵
- Kowalski RM, Morgan CA, Limber SP. Traditional bullying as a potential warning sign of cyberbullying. School Psychology International 2012;33(5):505-519. ↵
- Smith PK, Mahdavi J, Carvalho M, Fisher S, Russell S, Tippett N. Cyberbullying: Its nature and impact in secondary school pupils. Journal of child psychology and psychiatry 2008;49(4):376-385. ↵
- Wright MF, Aoyama I, Kamble SV, Li Z, Soudi S, Lei L, et al. Peer attachment and cyber aggression involvement among Chinese, Indian, and Japanese adolescents. Societies 2015;5(2):339-353. ↵
- Safaria T. Prevalence and impact of cyberbullying in a sample of indonesian junior high school students. Turkish Online Journal of Educational Technology-TOJET 2016;15(1):82-91. ↵
- Jose PE, Kljakovic M, Scheib E, Notter O. The joint development of traditional bullying and victimization with cyber bullying and victimization in adolescence. J Res Adolesc 2012;22(2):301-309. ↵
- Mehari KR, Thompson EL, Farrell AD. Differential longitudinal outcomes of in-person and cyber victimization in early adolescence. Psychology of violence 2020;10(4):367. ↵
- i Q. Cyberbullying in schools: A research of gender differences. School psychology international 2006;27(2):157-170. ↵
- Huang Y, Chou C. An analysis of multiple factors of cyberbullying among junior high school students in Taiwan. Comput Hum Behav 2010;26(6):1581-1590. ↵
- Aricak T, Siyahhan S, Uzunhasanoglu A, Saribeyoglu S, Ciplak S, Yilmaz N, et al. Cyberbullying among Turkish adolescents. Cyberpsychology & behavior 2008;11(3):253-261. ↵
- Ang RP, Goh DH. Cyberbullying among adolescents: The role of affective and cognitive empathy, and gender. Child Psychiatry & Human Development 2010;41(4):387-397. ↵
- Sourander A, Brunstein Klomek A, Ikonen M,et al. Psychosocial risk factors associated with cyberbullying among adolescents: A population-based study. Archives of General Psychiatry 2010 July 1;67(7):720-728. ↵
- Perren S, Dooley J, Shaw T, Cross D. Bullying in school and cyberspace: Associations with depressive symptoms in Swiss and Australian adolescents. Child and adolescent psychiatry and mental health 2010;4(1):1-10. ↵
- Ybarra ML, Mitchell KJ. Prevalence and frequency of Internet harassment instigation: Implications for adolescent health. Journal of Adolescent Health 2007;41(2):189-195. ↵
- Calvete E, Orue I, Estévez A, Villardón L, Padilla P. Cyberbullying in adolescents: Modalities and aggressors’ profile. Comput Hum Behav 2010;26(5):1128-1135. ↵
- Slonje R, Smith PK, Frisén A. The nature of cyberbullying, and strategies for prevention. Comput Hum Behav 2013;29(1):26-32. ↵
- Beran T, Li Q. Cyber-harassment: A study of a new method for an old behavior. Journal of educational computing research 2005;32(3):265. ↵
- Kowalski RM, Limber SP. Electronic bullying among middle school students. Journal of adolescent health 2007;41(6):S22-S30. ↵
- Sontag LM, Graber JA, Clemans KH. The role of peer stress and pubertal timing on symptoms of psychopathology during early adolescence. Journal of youth and adolescence 2011;40(10):1371-1382. ↵
- Werner NE. Do Hostile Attribution Biases in Children and Parents Predict Relationally Aggressive Behavior? The Journal of genetic psychology 07/2012;173(3):221; 221-245; 245. ↵
- Wade A, Beran T. Cyberbullying: The new era of bullying. Canadian Journal of School Psychology 2011;26(1):44-61. ↵
- Bauman S. Cyberbullying in a rural intermediate school: An exploratory study. The Journal of Early Adolescence 2010;30(6):803-833. ↵
- Hinduja S, Patchin JW. Cyberbullying: An exploratory analysis of factors related to offending and victimization. Deviant Behav 2008;29(2):129-156. ↵
- UNICEF. Child online protection in India. 2017. ↵
- Navarro R, Serna C, Martínez V, Ruiz-Oliva R. The role of Internet use and parental mediation on cyberbullying victimization among Spanish children from rural public schools. European journal of psychology of education 2013;28(3):725-745. ↵
- Casas JA, Del Rey R, Ortega-Ruiz R. Bullying and cyberbullying: Convergent and divergent predictor variables. Comput Hum Behav 2013;29(3):580-587. ↵
- Elledge LC, Williford A, Boulton AJ, DePaolis KJ, Little TD, Salmivalli C. Individual and contextual predictors of cyberbullying: The influence of children’s provictim attitudes and teachers’ ability to intervene. Journal of youth and adolescence 2013;42(5):698-710. ↵
- Moffitt TE. Adolescence-limited and life-course-persistent antisocial behavior: a developmental taxonomy. Psychol Rev 1993;100(4):674. ↵
- Sasson H, Mesch G. Parental mediation, peer norms and risky online behavior among adolescents. Comput Hum Behav 2014;33:32-38. ↵
- Ang RP, Tan K, Talib Mansor A. Normative beliefs about aggression as a mediator of narcissistic exploitativeness and cyberbullying. J Interpers Violence 2011;26(13):2619-2634. ↵
- Barlett CP, Gentile DA, Anderson CA, Suzuki K, Sakamoto A, Yamaoka A, et al. Cross-cultural differences in cyberbullying behavior: A short-term longitudinal study. Journal of cross-cultural psychology 2014;45(2):300-313. ↵
- Rahmawati R. Cyberbullying Behavior among Teens Moslem in Pekalongan Indonesia. Proceedings of Universiti Sains Malaysia 2015;238. ↵
- Dang J, Liu L. When peer norms work? Coherent groups facilitate normative influences on cyber aggression. Aggressive Behav 2020;46(6):559-569. ↵
- Badaly D, Kelly BM, Schwartz D, Dabney-Lieras K. Longitudinal associations of electronic aggression and victimization with social standing during adolescence. Journal of youth and adolescence 2013;42(6):891-904. ↵
- Katzer C, Fetchenhauer D, Belschak F. Cyberbullying: Who are the victims? A comparison of victimization in Internet chatrooms and victimization in school. Journal of media Psychology 2009;21(1):25-36. ↵
- Schoffstall CL, Cohen R. Cyber aggression: The relation between online offenders and offline social competence. Social Development 2011;20(3):587-604. ↵
- Wright MF, Li Y. The association between cyber victimization and subsequent cyber aggression: The moderating effect of peer rejection. Journal of youth and adolescence 2013;42(5):662-674. ↵
- Jiang Q, Zhao F, Xie X, Wang X, Nie J, Lei L, et al. Difficulties in emotion regulation and cyberbullying among Chinese adolescents: a mediation model of loneliness and depression. J Interpers Violence 2020:0886260520917517. ↵
- Wang P, Wang X, Lei L. Gender differences between student–student relationship and cyberbullying perpetration: An evolutionary perspective. J Interpers Violence 2019:0886260519865970. ↵
- Salmivalli C, Sainio M, Hodges EV. Electronic victimization: Correlates, antecedents, and consequences among elementary and middle school students. Journal of Clinical Child & Adolescent Psychology 2013;42(4):442-453. ↵
- Doty JL, Gower AL, Sieving RE, Plowman SL, McMorris BJ. Cyberbullying victimization and perpetration, connectedness, and monitoring of online activities: Protection from parental figures. Social Sciences 2018;7(12):265. ↵
- Chan HC, Wong DS. Traditional school bullying and cyberbullying perpetration: Examining the psychosocial characteristics of Hong Kong male and female adolescents. Youth & Society 2019;51(1):3-29. ↵
- Gaffney H, Farrington DP, Espelage DL, Ttofi MM. Are cyberbullying intervention and prevention programs effective? A systematic and meta-analytical review. Aggression and violent behavior 2019;45:134-153. ↵
- Doty JL, Giron K, Mehari KR, Sharma D, Smith SJ, Su Y, et al. Interventions to Prevent Cyberbullying Perpetration and Victimization: A Systematic Review. Prevention Science in press. ↵
- Pearce N, Cross D, Monks H, Waters S, Falconer S. Current evidence of best practice in whole-school bullying intervention and its potential to inform cyberbullying interventions. Journal of Psychologists and Counsellors in Schools 2011;21(1):1-21. ↵
- Gonzales J, Mehari KR. Attitudes about Cyber Intimate Partner Violence: Scale Development and Preliminary Psychometrics. 2021. ↵
- Sharma D, Mehari KR, Doty JL. Stakeholder Focus Groups on Cyberbullying in India. 2021. ↵
- Willard NE. The authority and responsibility of school officials in responding to cyberbullying. Journal of Adolescent Health 2007;41(6):S64-S65. ↵
- Agatston PW, Kowalski R, Limber S. Students’ perspectives on cyber bullying. Journal of Adolescent Health 2007;41(6):S59-S60. ↵
- Slonje R, Smith PK. Cyberbullying: Another main type of bullying? Scand J Psychol 2008;49(2):147-154. ↵
- Cassidy W, Brown K, Jackson M. “Making Kind Cool”: Parents’ Suggestions for Preventing Cyber Bullying and Fostering Cyber Kindness. Journal of Educational Computing Research 2012;46(4):415-436. ↵
- Hodges EV, Boivin M, Vitaro F, Bukowski WM. The power of friendship: protection against an escalating cycle of peer victimization. Dev Psychol 1999;35(1):94. ↵
- Hertz MF, David-Ferdon C. Electronic media and youth violence: A CDC issue brief for educators and caregivers. : Centers for Disease Control Atlanta, GA; 2008. ↵
- Horner RH, Sugai G. School-wide PBIS: An example of applied behavior analysis implemented at a scale of social importance. Behavior analysis in practice 2015;8(1):80-85. ↵
- Shariff S. Confronting Cyber-Bullying: What Schools Need to Know to Control Misconduct and Avoid Legal Consequences. : ERIC; 2009. ↵
Cyberbullying and Digital Safety: Applying Global Research to Youth in India Copyright © 2022 by Krista Mehari and Natasha Basu is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License , except where otherwise noted.
Share This Book
Methods: Guiding Principles
- Disability and Psychoeducation Studies
- Family and Consumer Sciences, School of
Research output : Chapter in Book/Report/Conference proceeding › Chapter
In this chapter, we propose five principles to serve as guidelines for cyberbullying research methods: engaging multidisciplinary teams, using a broad selection of quality methods, understanding the importance of formative research, realizing the value of target audience involvement, and promoting ethical practice in online environments. We do not describe these guidelines as “best practice, " as there is insufficient evidence to date that these methods (some of which are unique to measure cyberbullying behavior) produce superior results. Nevertheless, considering what is known about research in general and research on aggression; victimization; and bullying, in particular, we believe these principles are grounded in sound scientific methods and fundamental beliefs about the research enterprise. We are also mindful that scientific inquiry into the use of technology is a relatively new area, and we have taken this into account in our recommendations.
ASJC Scopus subject areas
- General Psychology
Access to Document
- 10.4324/9780203084601-24
Other files and links
- Link to publication in Scopus
- Link to the citations in Scopus
Fingerprint
- Cyberbullying Medicine & Life Sciences 100%
- Bullying Medicine & Life Sciences 39%
- Crime Victims Medicine & Life Sciences 38%
- Guidelines Medicine & Life Sciences 38%
- victimization Social Sciences 32%
- aggression Social Sciences 31%
- Aggression Medicine & Life Sciences 30%
- research method Social Sciences 29%
T1 - Methods
T2 - Guiding Principles
AU - Bauman, Sheri
AU - Cross, Donna
N1 - Publisher Copyright: © 2013 by Taylor & Francis Group, LLC.
PY - 2012/1/1
Y1 - 2012/1/1
N2 - In this chapter, we propose five principles to serve as guidelines for cyberbullying research methods: engaging multidisciplinary teams, using a broad selection of quality methods, understanding the importance of formative research, realizing the value of target audience involvement, and promoting ethical practice in online environments. We do not describe these guidelines as “best practice, " as there is insufficient evidence to date that these methods (some of which are unique to measure cyberbullying behavior) produce superior results. Nevertheless, considering what is known about research in general and research on aggression; victimization; and bullying, in particular, we believe these principles are grounded in sound scientific methods and fundamental beliefs about the research enterprise. We are also mindful that scientific inquiry into the use of technology is a relatively new area, and we have taken this into account in our recommendations.
AB - In this chapter, we propose five principles to serve as guidelines for cyberbullying research methods: engaging multidisciplinary teams, using a broad selection of quality methods, understanding the importance of formative research, realizing the value of target audience involvement, and promoting ethical practice in online environments. We do not describe these guidelines as “best practice, " as there is insufficient evidence to date that these methods (some of which are unique to measure cyberbullying behavior) produce superior results. Nevertheless, considering what is known about research in general and research on aggression; victimization; and bullying, in particular, we believe these principles are grounded in sound scientific methods and fundamental beliefs about the research enterprise. We are also mindful that scientific inquiry into the use of technology is a relatively new area, and we have taken this into account in our recommendations.
UR - http://www.scopus.com/inward/record.url?scp=85121888210&partnerID=8YFLogxK
UR - http://www.scopus.com/inward/citedby.url?scp=85121888210&partnerID=8YFLogxK
U2 - 10.4324/9780203084601-24
DO - 10.4324/9780203084601-24
M3 - Chapter
AN - SCOPUS:85121888210
SN - 9780415897495
BT - Principles of Cyberbullying Research
PB - Taylor and Francis
Numbers, Facts and Trends Shaping Your World
Read our research on:
Full Topic List
Regions & Countries
- Publications
- Our Methods
- Short Reads
- Tools & Resources
Read Our Research On:
Teens and Cyberbullying 2022
- Methodology
Table of Contents
- Age and gender are related to teens’ cyberbullying experiences, with older teen girls being especially likely to face this abuse
- Black teens are about twice as likely as Hispanic or White teens to say they think their race or ethnicity made them a target of online abuse
- Black or Hispanic teens are more likely than White teens to say cyberbullying is a major problem for people their age
- Roughly three-quarters of teens or more think elected officials and social media sites aren’t adequately addressing online abuse
- Large majorities of teens believe permanent bans from social media and criminal charges can help reduce harassment on the platforms
- Acknowledgments
The analysis in this report is based on a self-administered web survey conducted from April 14 to May 4, 2022, among a sample of 1,316 dyads, with each dyad (or pair) comprised of one U.S. teen ages 13 to 17 and one parent per teen. The margin of sampling error for the full sample of 1,316 teens is plus or minus 3.2 percentage points. The survey was conducted by Ipsos Public Affairs in English and Spanish using KnowledgePanel, its nationally representative online research panel.
The research plan for this project was submitted to an external institutional review board (IRB), Advarra, which is an independent committee of experts that specializes in helping to protect the rights of research participants. The IRB thoroughly vetted this research before data collection began. Due the risks associated with surveying minors, this research underwent a full board review and received approval (Pro00060166).
KnowledgePanel members are recruited through probability sampling methods and include both those with internet access and those who did not have internet access at the time of their recruitment. KnowledgePanel provides internet access for those who do not have it and, if needed, a device to access the internet when they join the panel. KnowledgePanel’s recruitment process was originally based exclusively on a national random-digit-dialing (RDD) sampling methodology. In 2009, Ipsos migrated to an address-based sampling (ABS) recruitment methodology via the U.S. Postal Service’s Delivery Sequence File (DSF). The Delivery Sequence File has been estimated to cover as much as 98% of the population, although some studies suggest that the coverage could be in the low 90% range. 3
Panelists were eligible for participation in this survey if they indicated on an earlier profile survey that they were the parent of a teen ages 13 to 17. A random sample of 5,580 eligible panel members were invited to participate in the study. Responding parents were screened and considered qualified for the study if they reconfirmed that they were the parent of at least one child ages 13 to 17 and granted permission for their teen who was chosen to participate in the study. In households with more than one eligible teen, parents were asked to think about one randomly selected teen and that teen was instructed to complete the teen portion of the survey. A survey was considered complete if both the parent and selected teen completed their portions of the questionnaire, or if the parent did not qualify during the initial screening.
Of the sampled panelists, 1,607 (excluding break-offs) responded to the invitation and 1,316 qualified, completed the parent portion of the survey, and had their selected teen complete the teen portion of the survey yielding a final stage completion rate of 29% and a qualification rate of 82%. 4 The cumulative response rate accounting for nonresponse to the recruitment surveys and attrition is 1%. The break-off rate among those who logged on to the survey (regardless of whether they completed any items or qualified for the study) is 37%.
Upon completion, qualified respondents received a cash-equivalent incentive worth $10 for completing the survey.
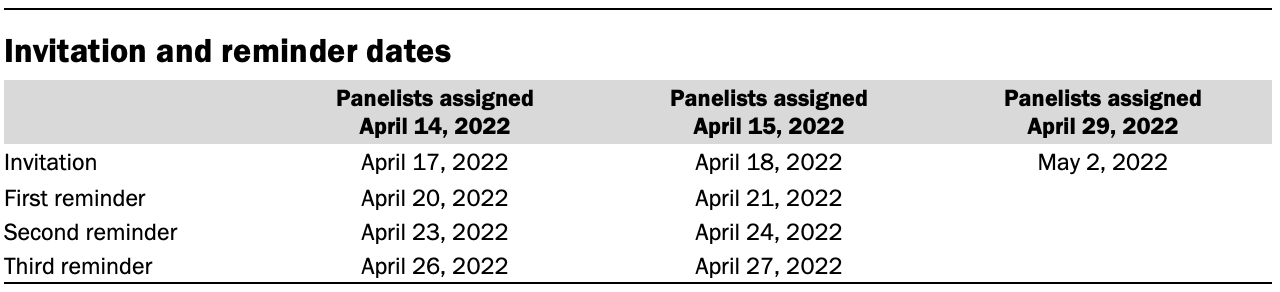
Panelists were assigned to take the survey in batches. Email invitations and reminders were sent to panelists according to a schedule based on when they were assigned this survey in their personalized member portal, shown in the table below. The field period was closed on May 4, 2022, and thus no further email contacts past the invitation were sent for the final set of panelists.
The analysis in this report was performed using a teen weight. A weight for parents was also constructed, forming the basis of the teen weight. The parent weight was created in a multistep process that begins with a base design weight for the parent, which is computed to reflect their probability of selection for recruitment into the KnowledgePanel. These selection probabilities were then adjusted to account for the probability of selection for this survey, which included oversamples of Black and Hispanic parents. Next, an iterative technique was used to align the parent design weights to population benchmarks for parents of teens ages 13 to 17 on the dimensions identified in the accompanying table to account for any differential nonresponse that may have occurred.
To create the teen weight, an adjustment factor was applied to the final parent weight to reflect the selection of one teen per household. Finally, the teen weights were further raked to match the demographic distribution for teens ages 13 to 17 who live with parents. The teen weights were adjusted on the same teen dimensions as parent dimensions with the exception of teen education, which was not used in the teen weighting.
Sampling errors and tests of statistical significance take into account the effect of weighting. Interviews were conducted in both English and Spanish.
In addition to sampling error, one should bear in mind that question wording and practical difficulties in conducting surveys can introduce error or bias into the findings of opinion polls.
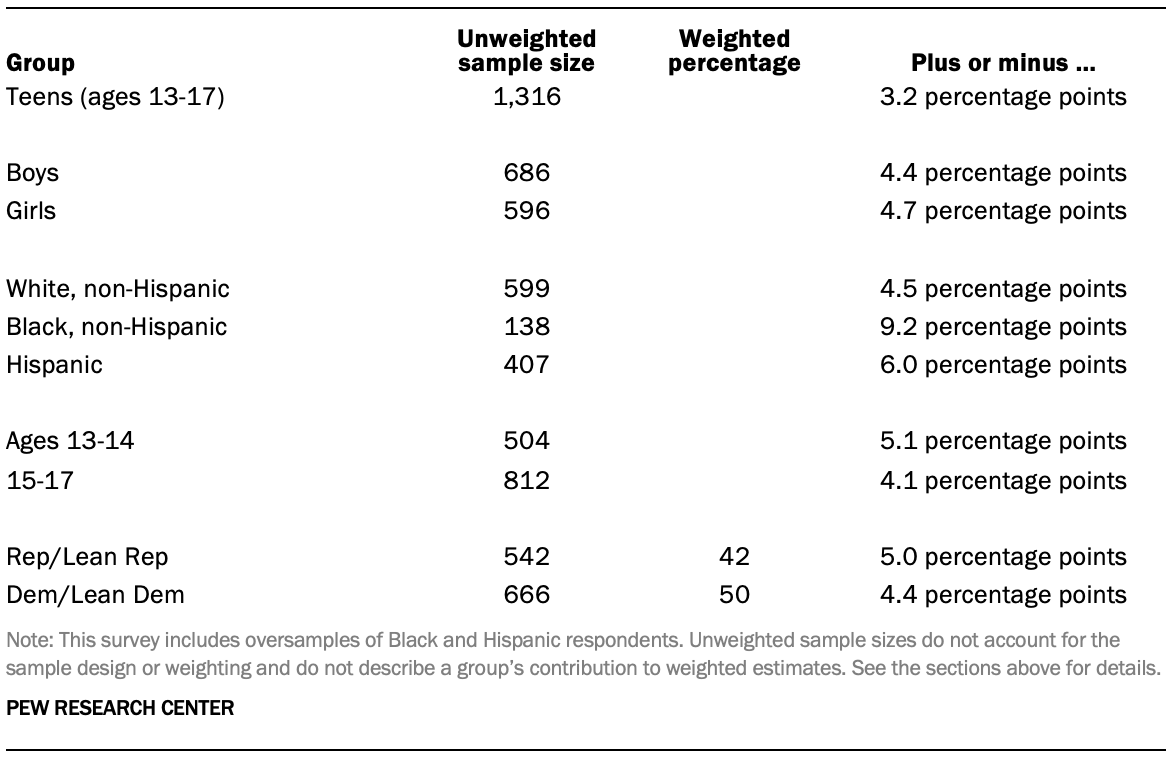
The following tables show the unweighted sample sizes and the error attributable to sampling that would be expected at the 95% level of confidence for different groups in the survey:
Sample sizes and sampling errors for other subgroups are available upon request.
Dispositions and response rates
The tables below display dispositions used in the calculation of completion, qualification and cumulative response rates. 5

- AAPOR Task force on Address-based Sampling. 2016. “AAPOR Report: Address-based Sampling.” ↩
- The 1,316 qualified and completed interviews exclude seven cases that were dropped because respondents did not answer one-third or more of the survey questions. ↩
- For more information on this method of calculating response rates, see Callegaro, Mario & DiSogra, Charles. 2008. “Computing response metrics for online panels.” Public Opinion Quarterly 72(5). pp. 1008-1032. ↩
Sign up for our weekly newsletter
Fresh data delivery Saturday mornings
Sign up for The Briefing
Weekly updates on the world of news & information
- Online Harassment & Bullying
- Teens & Tech
- Teens & Youth
Teens and Video Games Today
9 facts about bullying in the u.s., life on social media platforms, in users’ own words, after musk’s takeover, big shifts in how republican and democratic twitter users view the platform, the behaviors and attitudes of u.s. adults on twitter, most popular.
1615 L St. NW, Suite 800 Washington, DC 20036 USA (+1) 202-419-4300 | Main (+1) 202-857-8562 | Fax (+1) 202-419-4372 | Media Inquiries
Defining cyberbullying: A qualitative research into the perceptions of youngsters

2008, CyberPsychology & …
Related Papers
New media & society
Heidi Vandebosch
Hapindi Arista
Psychological Bulletin
Amber Schroeder
Zeitschrift Fur Psychologie-journal of Psychology
Jacek Pyzalski
Zeitschrift für Psychologie / Journal of Psychology
Jacek Pyzalski , Julian Dooley
Haley Burgess , Mitchell Hobbs
Cyberbullying is a relatively recent phenomenon that can have significant consequences for young people’s wellbeing due to the specific technological affordances of social media. To date, research into cyberbullying has been largely quantitative; thus, it often elides the complexity of the issue. Moreover, most studies have been “top down,” excluding young people’s views. Our qualitative research findings suggest that young people engage in cyberbullying to accrue social benefits over peers and to manage social pressures and anxiety, while cultural conventions in gender performance see girls engage differently in cyberbullying. We conclude that cyberbullying, like offline bullying, is a socially constructed behavior that provides both pleasure and pain.
International Journal of Consumer Studies
Carrie La Ferle
Cyberbullying in the digital sphere has impacted individuals of all age groups. Recent findings indicate an increase in suicidal tendencies among victims. An opportunity to prevent cyberbullying exists in the actions of bystanders. The current study proposes the possible impact of religion (Christianity) in motivating bystanders to aid victims of abuse. Using an experimental design, the research explored the interplay of individual religiosity and religious symbolism on American bystanders’ ad attitudes and intentions to call a helpline. Findings indicate a congruency effect for low religiosity individuals between the control and religious ads. High religiosity individuals liked both ads equally well, but within the religious ad, again a congruency effect appeared where highly religious individuals found the religious ad significantly more appealing than low religious individuals. Theoretical and practical implications are discussed.
Mitchell Hobbs
Peter Smith , Sonia Livingstone
Journal of Child Psychology and Psychiatry
Sonia Livingstone
RELATED PAPERS
Georges Steffgen , trijntje vollink , francine dehue
Sameer Hinduja , Justin W . Patchin
Jacek Pyzalski , Camilla Hällgren
Aggressive Behavior
Australian Journal of Guidance and Counselling
Anja Schultze-krumbholz
Barbara Spears
Education and Information Technologies
Tali Heiman
Rizalyn Castillo
Gilberto Marzano
Conor Guckin
Behaviour & Information Technology
Computers in Human Behavior
Gayle Brewer
Calvin Dota
wesley bruce
Katie Davis , Carrie James
Triantoro Safaria , Triantoro Safaria
francine dehue
Scandinavian journal of psychology
Rita Zukauskiene
Ray Block , Laurie Cooper Stoll
Sora Park , Jee Young Lee , Soeun Yang
Http Dx Doi Org 10 1080 15388220 2012 762921
Rivka Witenberg
glenda reyes
Pedro Ferraz de Abreu
Giulia Mura
Journal of School Violence
Emma-Kate Corby , phillip slee
Toks Dele Oyedemi
Nicholas Brody
Lilian Lechner
Studies in health technology and informatics
Cigdem Topcu
Michel Walrave
Tiffany Jones
The western journal of emergency medicine
Joel Meyers , Kris Varjas
Łukasz Tomczyk
Emotional and Behavioural Difficulties
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
Q Methodology as an Innovative Addition to Bullying Researchers’ Methodological Repertoire
- Original Article
- Open access
- Published: 11 May 2022
- Volume 4 , pages 209–219, ( 2022 )
Cite this article
You have full access to this open access article

- Adrian Lundberg ORCID: orcid.org/0000-0001-8555-6398 1 &
- Lisa Hellström ORCID: orcid.org/0000-0002-9326-1175 1
6388 Accesses
2 Altmetric
Explore all metrics
A Correction to this article was published on 18 July 2022
This article has been updated
The field of bullying research deals with methodological issues and concerns affecting the comprehension of bullying and how it should be defined. For the purpose of designing relevant and powerful bullying prevention strategies, this article argues that instead of pursuing a universal definition of what constitutes bullying, it may be of greater importance to investigate culturally and contextually bound understandings and definitions of bullying. Inherent to that shift is the transition to a more qualitative research approach in the field and a stronger focus on participants’ subjective views and voices. Challenges in qualitative methods are closely connected to individual barriers of hard-to-reach populations and the lack of a necessary willingness to share on the one hand and the required ability to share subjective viewpoints on the other hand. By reviewing and discussing Q methodology, this paper contributes to bullying researchers’ methodological repertoire of less-intrusive methodologies. Q methodology offers an approach whereby cultural contexts and local definitions of bullying can be put in the front. Furthermore, developmentally appropriate intervention and prevention programs might be created based on exploratory Q research and could later be validated through large-scale investigations. Generally, research results based on Q methodology are expected to be useful for educators and policymakers aiming to create a safe learning environment for all children. With regard to contemporary bullying researchers, Q methodology may open up novel possibilities through its status as an innovative addition to more mainstream approaches.
Similar content being viewed by others

Using Qualitative Methods to Measure and Understand Key Features of Adolescent Bullying: A Call to Action
The importance of being attentive to social processes in school bullying research: adopting a constructivist grounded theory approach.

Problems and Coping Strategies in Conducting Comparative Research in School Bullying Between China and Norway
Avoid common mistakes on your manuscript.
Introduction
Bullying, internationally recognized as a problematic and aggressive form of behavior, has negative effects, not only for those directly involved but for anybody and in particular children in the surrounding environment (Modin, 2012 ). However, one of the major concerns among researchers in the field of bullying is the type of research methods employed in the studies on bullying behavior in schools. The appropriateness of using quantitative or qualitative research methods rests on the assumption of the researcher and the nature of the phenomena under investigation (Hong & Espelage, 2012 ). There is a need for adults to widen their understanding and maintain a focus on children’s behaviors to be able to provide assistance and support in reducing the amount of stress and anxiety resulting from online and offline victimization (Hellström & Lundberg, 2020 ). A crucial step for widening this understanding is an increased visibility of children’s own viewpoints. When the voices of children, particularly those of victims and perpetrators, but also those of bystanders are heard in these matters, effective support can be designed based specifically on what children want and need rather than what adults interpret and understand to be supporting the child (O’Brien, 2019 ). However, bullying victims and their perpetrators are hard-to-reach populations (Shaghaghi et al., 2011 ; Sydor, 2013 ) for a range of reasons. To name but a few, researchers perennially face difficulties regarding potential participants’ self-identification, the sensitivity of bullying topics, or the power imbalance between them and their young respondents. Furthermore, limited verbal literacy and/or a lack of cognitive ability of some respondents due to age or disability contribute to common methodological issues in the field. Nevertheless, and despite ethical restrictions around the immediate questioning of younger children or children with disabilities that prohibit researchers to perform the assessments with them directly, it would be ethically indefensible to not study a sensitive topic like bullying among vulnerable groups of children. Hence, the research community is responsible for developing valid and reliable methods to explore bullying among different groups of children, where the children’s own voices are heard and taken into account (Hellström, 2019 ). Consequently, this paper aims to contribute to bullying researchers’ methodological repertoire with an additional less-intrusive methodology, particularly suitable for research with hard-to-reach populations.
Historically, the field of bullying and cyberbullying has been dominated by quantitative research approaches, most often with the aim to examine prevalence rates. However, recent research has seen an increase in the use of more qualitative and multiple data collection approaches on how children and youth explain actions and reactions in bullying situations (e.g., Acquadro Maran & Begotti, 2021 ; Eriksen & Lyng, 2018 ; Patton et al., 2017 ). This may be translated into a need to more clearly understand the phenomenon in different contexts. As acknowledged by many researchers, bullying is considerably influenced by the context in which it occurs and the field is benefitting from studying the phenomenon in the setting where all the contextual variables are operating (see, e.g., Acquadro Maran & Begotti, 2021 ; Scheithauer et al., 2016 ; Torrance, 2000 ). Cultural differences in attitudes regarding violence as well as perceptions, attitudes, and values regarding bullying are likely to exist and have an impact when bullying is being studied. For this reason, listening to the voices of children and adolescents when investigating the nature of bullying in different cultures is essential (Hellström & Lundberg, 2020 ; Scheithauer et al., 2016 ).
In addition to studying outcomes or products, bullying research has also emphasized the importance of studying processes (Acquadro Maran & Begotti, 2021 ). Here, the use of qualitative methods allows scholars to not only explore perceptions and understandings of bullying and its characteristics, but also interpret bullying in light of a specific social context, presented from a specific internal point of view. In other words, qualitative approaches may offer methods to understand how people make sense of their experiences of the bullying phenomenon. The processes implemented by a qualitative approach allow researchers to build hypotheses and theories in an inductive way (Atieno, 2009 ). Thus, a qualitative approach can enrich quantitative knowledge of the bullying phenomenon, paying attention to the significance that individuals attribute to situations and their own experiences. It can allow the research and clinical community to better project and implement bullying assessment and prevention programs (Hutson, 2018 ).
Instead of placing qualitative and quantitative approaches in opposition, they can both be useful and complementary, depending on the purpose of the research (Acquadro Maran & Begotti, 2021 ). In their review of mixed methods research on bullying and peer victimization in school, Hong and Espelage ( 2012 ) underlined that instead of using single methods, mixed methods have the advantage of generating a deeper and more complex understanding of the phenomenon. By combining objective data with information about the personal context within which the phenomenon occurs, mixed methods can generate new insights and new perspectives to the research field (Hong & Espelage, 2012 ; Kulig et al., 2008 ; Pellegrini & Long, 2002 ). However, Hong and Espelage ( 2012 ) also argued that mixed methods can lead to divergence and contradictions in findings that may serve as a challenge to researchers. For example, Cowie and Olafsson ( 2000 ) examined the impact of a peer support program to reduce bullying using both quantitative and qualitative data collection methods. While a quantitative approach collecting pre-test and post-test data showed no effects in decreasing bullying, interviews with peer supporters, students, and potential users of the intervention revealed the strength of the program and its positive impact, in light of students and peer supporters. Thus, rather than rejecting the program, the divergence in findings leads to a new rationale for modifying the program and addressing its limits.
Understandably, no single data collection approach is complete but deals with methodological issues and concerns affecting the research field and the comprehension of bullying. To provide a robust foundation for the introduction of an additional methodological perspective in bullying research, common data collection methods and methodological issues are outlined below.
Methodological Issues in Bullying Research
Large-scale cohort studies generating statistical findings often use R-statistics, descriptive analyses, averages, and correlations to estimate and compare prevalence rates of bullying, to explore personality traits of bullies and victims, and the main correlates and predictors of the phenomenon. Nevertheless, large-scale surveys have a harder time examining why bullying happens (O’Brian, 2019 ) and usually do not give voice to study objects’ own unique understanding and experiences (Acquadro Maran & Begotti, 2021 ; Bosacki et al., 2006 ; Woodhead & Faulkner, 2008 ). Other concerns using large-scale surveys include whether a definition is used or the term bullying is operationalized, which components are included in the definition, what cut-off points for determining involvement are being used, the lack of reliability information, and the absence of validity studies (Swearer et al., 2010 ).
Other issues include the validity in cross-cultural comparisons using large-scale surveys. For example, prevalence rates across Europe are often established using standard questionnaires that have been translated into appropriate languages. Comparing four large-scale surveys, Smith et al. ( 2016 ) found that when prevalence rates by country are compared across surveys, there are some obvious discrepancies, which suggest a need to examine systematically how these surveys compare in measuring cross-national differences. Low external validity rates between these studies raise concerns about using these cross-national data sets to make judgments about which countries are higher or lower in victim rates. The varying definitions and words used in bullying research may make it difficult to compare findings from studies conducted in different countries and cultures (Griffin & Gross, 2004 ). However, some argue that the problem seems to be more about inconsistency in the type of assessments (e.g., self-report, nominations) used to measure bullying rather than the varying definition of bullying (Jia & Mikami, 2018 ). When using a single-item approach (e.g., “How often have you been bullied?”) it is not possible to investigate the equivalency of the constructs between countries, which is a crucial precondition for any statistically valid comparison between them (Scheithauer et al., 2016 ). Smith et al. ( 2016 ) conclude that revising definitions and how bullying is translated and expressed in different languages and contexts would help examine comparability between countries.
Interviews, focus groups and the use of vignettes (usually with younger children) can all be regarded as suitable when examining youths’ perceptions of the bullying phenomenon (Creswell, 2013 ; Hellström et al., 2015 ; Hutson, 2018 ). They all allow an exploration of the bullying phenomenon within a social context taking into consideration the voices of children and might solve some of the methodological concerns linked to large-scale surveys. However, these data collection methods are also challenged by individual barriers of hard-to-reach populations (Ellard-Gray et al., 2015 ) and may include the lack of a necessary willingness to share on the one hand and the required ability to share subjective viewpoints on the other hand.
Willingness to Share
In contrast to large-scale surveys requiring large samples of respondents with reasonable literacy skills, interviews, which may rely even heavier on students’ verbal skills, are less plentiful in bullying research. This might at least partially be based on a noteworthy expectation of respondents to be willing to share something. It must be remembered that asking students to express their own or others’ experiences of emotionally charged situations, for example concerning bullying, is particularly challenging (Khanolainen & Semenova, 2020 ) and can be perceived as intrusive by respondents who have not had the opportunity to build a rapport with the researchers. This constitutes a reason why research in this important area is difficult and complex to design and perform. Ethnographic studies may be considered less intrusive, as observations offer a data collection technique where respondents are not asked to share any verbal information or personal experiences. However, ethnographical studies are often challenging due to the amount of time, resources, and competence that are required by the researchers involved (Queirós et al., 2017 ). In addition, ethnographical studies are often used for other purposes than asking participants to share their views on certain topics.
Vulnerable populations often try to avoid participating in research about a sensitive topic that is related to their vulnerable status, as recalling and retelling painful experiences might be distressing. The stigma surrounding bullying may affect children’s willingness to share their personal experiences in direct approaches using the word bullying (Greif & Furlong, 2006 ). For this reason, a single-item approach, in which no definition of bullying is provided, allows researchers to ask follow-up questions about perceptions and contexts and enables participants to enrich the discussion by adjusting their answers based on the suggestions and opinions of others (Jacobs et al., 2015 ). Generally, data collection methods with depersonalization and distancing effects have proven effective in research studying sensitive issues such as abuse, trauma, stigma and so on (e.g., Cromer & Freyd, 2009 ; Hughes & Huby, 2002 ). An interesting point raised by Jacobs and colleagues ( 2015 ) is that a direct approach that asks adolescents if they have ever experienced cyberbullying may lead to a poorer discussion and an underestimation of the phenomenon. This is because perceptions and contexts often differ between persons and because adolescents do not perceive all behaviors as cyberbullying. The same can be true for bullying taking place offline (Hellström et al., 2015 ).
When planning research with children, it is important to consider the immediate research context as it might affect what children will talk about (Barker & Weller, 2003 ; Hill, 2006 ; Punch, 2002 ). In addition to more material aspects, such as the room or medium for a dialog, the potential power imbalance created in an interview situation between an adult researcher and the child under study adds to a potentially limited willingness to share. Sitting in front of an adult interviewer may create situations where children may find it difficult to express their feelings and responses may be given based on perceived expectations (Punch, 2002 ). This effect is expected to be even stronger when studying a sensitive topic like bullying. Therefore, respondents may provide more honest responses when they are unaware that the construct of bullying is being assessed (Swearer et al., 2010 ). Moreover, in research about sensitive topics, building a strong connection with participants (Lyon & Carabelli, 2016 ), characterized by mutual trust, is vital and might overcome the initial hesitation to participate and share personal accounts. Graphic vignettes have successfully been used as such unique communication bridges to collect detailed accounts of bullying experiences (Khanolainen & Semenova, 2020 ). However, some reluctance to engage has been reported even in art-based methods, usually known to be effective in research with verbally limited participants (Bagnoli, 2009 ; Vacchelli, 2018 ) or otherwise hard-to-reach populations (Goopy & Kassan, 2019 ). Most commonly, participants might not see themselves as creative or artistic enough (Scherer, 2016 ). In sum, the overarching challenging aspect of art-based methods related to a limited willingness to share personal information is an often-required production of some kind.
Ability to Share
Interviews as a data collection method demand adequate verbal literacy skills for participants to take part and to make their voices heard. This may be challenging especially for younger children or children with different types of disabilities. There is a wide research gap in exploring the voices of younger children (de Leeuw et al., 2020 ) and children with disabilities (Hellström, 2019 ) in bullying research. Students’ conceptualization of bullying behavior changes with age, as there are suggestions that younger students tend to focus more on physical forms of bullying (such as fighting), while older students include a wider variety of behaviors in their view of bullying, such as verbal aggression and social exclusion (Hellström & Lundberg, 2020 ; Monks & Smith, 2006 ; Smith et al., 2002 ; Hellström et al., 2015 ). This suggests that cognitive development may allow older students to conceptualize bullying along a number of dimensions (Monks & Smith, 2006 ). Furthermore, the exclusion of the voices of children with disabilities in bullying research is debated. It is discussed that the symptoms and characteristics of disabilities such as Attention Deficit Hyperactivity Disorder (ADHD) or Autism Spectrum Disorder (ASD), i.e., difficulties understanding the thoughts, emotions, reactions, and behaviors of others, which makes them the ideal target for bullying may also make it hard for them to perceive, verbalize and report bullying and victimization in a reliable and valid manner (Slaughter et al., 2002 ). It may also be difficult for children with ASD to differentiate between playful teasing among friends and hurtful teasing. While many argue that children with ASD are unreliable respondents of victimization, under-reporting using parental and teacher reports has been shown in research on bullying (Waters et al., 2003 ; Bradshaw et al., 2007 ) and child maltreatment (Compier-de Block et al., 2017 ).

This Paper’s Contribution
The present paper contributes to this special issue about qualitative school bullying and cyberbullying research by reviewing and discussing Q methodology as an innovative addition to more mainstream approaches in the field. Despite the fact that Q methodology had been proclaimed as “especially valuable […] in educational psychology” (Stephenson, 1935 , p. 297) nearly 90 years ago, the approach has only relatively recently been described as an up-and-coming methodological choice of educational researchers interested in participants’ subjective views (Lundberg et al., 2020 ). Even though, Q enables researchers to investigate and uncover first-person accounts, characterized by a high level of qualitative detail in its narrative description, only few educational studies have applied Q methodology to investigate the subject of bullying (see Camodeca & Coppola, 2016 ; Ey & Spears, 2020 ; Hellström & Lundberg, 2020 ; Wester & Trepal, 2004 ). Within the wider field of bullying, Q methodology has also been used to investigate workplace bullying in hospitals (Benmore et al., 2018 ) and nursing units (Choi & Lee, 2019 ). By responding to common methodological issues outlined earlier, the potential Q methodology might have for bullying research is exemplified. A particular focus is thereby put on capturing respondents’ subjective viewpoints through its less-intrusive data collection technique. The present paper closes by discussing implications for practice and suggesting future directions for Q methodological bullying and cyberbullying research, in particular with hard-to-reach populations.
An Introduction to Q Methodology
Q as a methodology represents a larger conceptual and philosophical framework, which is by no means novel. However, the methodology has largely been marginalized since its invention in the 1930s by William Stephenson (Brown, 2006 ). As a research technique, it broadly consists of three stages that each can be split into a set of steps (see Fig. 1 ); (1) carefully constructing a data collection instrument, (2) collecting data, and (3) analyzing and interpreting data. The central, and therefore also best-known feature of Q methodology is Q sorting to collect data in the form of individual Q sorts. Participants thereby rank order a sample of self-referent stimuli along a continuum and in accordance with a central condition of instruction; for example, children might be asked to what extent particular scenarios describe bullying situations (Hellström & Lundberg, 2020 ) or they might be instructed to sort illustrated ways to resolve social exclusion according to the single face-valid dimension of “least preferred to most preferred” (de Leeuw et al., 2019 ). As soon as all items are placed on a most often bell-shaped distribution grid (see Fig. 2 ), participants might be asked to elaborate on their item placement to add a further layer of qualitative data. Such so-called post-sorting activities might include written annotations of items placed at the ends of the continuum or form the structure for interviews (Shemmings & Ellingsen, 2012 ).
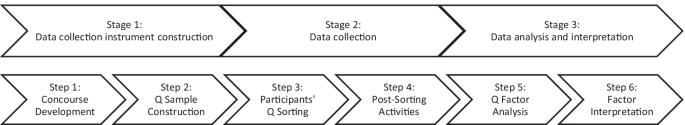
Three stages and six steps of a Q methodological research process (adapted from Lundberg et al., 2020 )
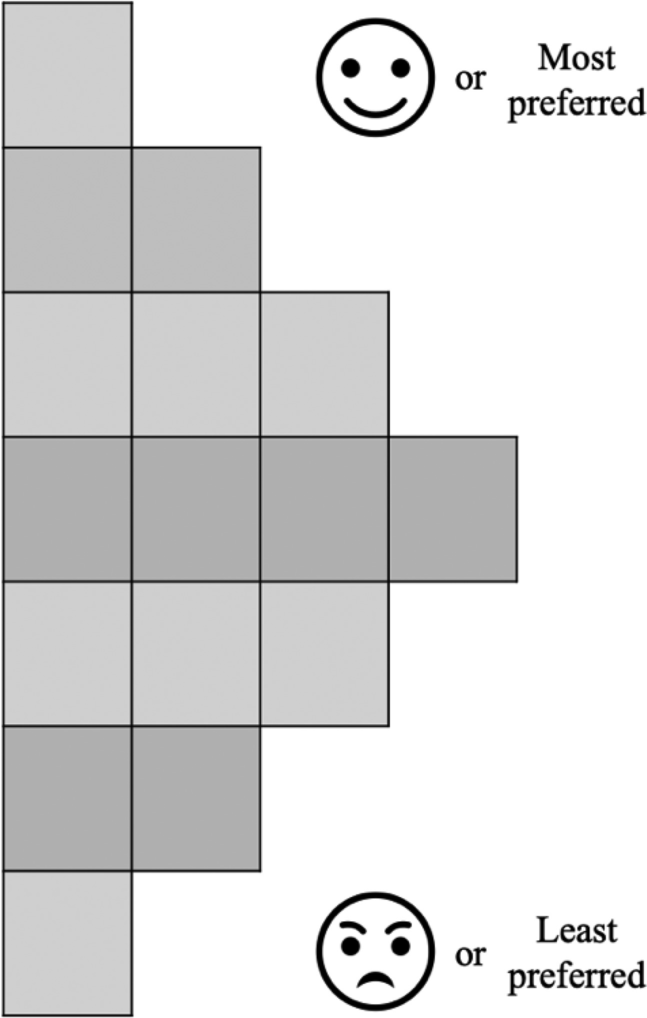
A vertical distribution grid with two examples of face-valid dimensions. This rather small distribution is designed for a 16-item Q sample and therefore contains 16 slots to be filled
For participants to provide their subjective viewpoint toward a specific topic in the form of a Q sort, researchers need to construct the data collection instrument, called Q sample. Such a set of stimulus items is a representative sample from all possible items concerning the topic, which in the technical language in Q methodology is called concourse (Brown, 1980 ). The development of such a concourse about the topic at hand might stem from a wide range of sources, including academic literature, policy documents, informal discussions, or media (Watts & Stenner, 2012 ). Moreover, in a participatory research fashion, participants’ statements can be used verbatim to populate the concourse. This way, children’s own words and voices are part of the data collection instrument. A sophisticated structuring process then guides the researchers in selecting a Q sample from all initial statements in the concourse (Brown et al., 2019 ). In Hellström & Lundberg ( 2020 ), a literature review on findings and definitions of bullying, stemming from qualitative and quantitative research, provided the initial concourse. A matrix consisting of different modes, types, and contexts of bullying supported the construction of the final Q sample.
As a student and assistant of Charles Spearman, Q’s inventor Stephenson was well-informed about R-methodological factor analysis based on correlating traits. The British physicist-psychologist however inverted the procedure and thereby suggested correlating persons to study human behavior (Stephenson, 1935 , 1953 ). A detailed description of the statistical procedure of Q factor analysis is outside the scope of this article, especially as the focus of this special issue is put on qualitative research methods. In addition, with its focus on producing quantifiable data from highly subjective viewpoints (Duncan & Owens, 2011 ), it is safe to say that Q methodology is more often treated as a qualitative methodology with quantitative features than the other way around. Nevertheless, it is important to note that through factor analysis, individual viewpoints are clustered into so-called factors, representing shared viewpoints if they sufficiently correlate (see Fig. 3 ). In that sense, no outside criterion is applied to respondents’ subjective views and groups of similar sorts (factors/viewpoints) are not logically constructed by researchers. Instead, they inductively emerge through quantitative analysis, which helps “in learning how the subject, not the observer, understands and reacts to items” (Brown, 1980 , p. 191). This procedure allowed Hellström & Lundberg ( 2020 ) to describe two age-related definitions of bullying. Older students in particular perceived offline bullying as more severe than online bullying and their younger peers were mostly concerned about bullying situations taking place in a private setting.
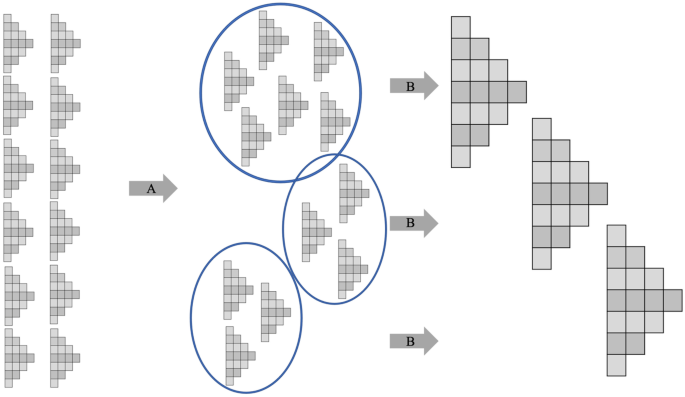
A simplified illustration of Q factor analysis (step 5). Arrow A represents the statistical correlation of all collected individual viewpoints. Arrow B represents inverted factor analysis as the data condensation technique resulting in a manageable number of shared viewpoints
Despite its quantitative analysis, participant selection in Q methodology is largely in line with purposive sampling with small numbers. It, therefore, represents a major difference to R methodological research, where larger opportunity samples are desired. In Q methodology, participants are selected strategically in line with those who might likely “express a particularly interesting or pivotal point of view” (Watts & Stenner, 2012 , p. 71). Investigating a large number of similar respondents might therefore simply lead to more participants correlating with the same shared viewpoint and not necessarily add new viewpoints. In recent educational Q research, the average number of participants is 37 (Lundberg et al., 2020 ). Many studies have however been successfully conducted with considerably fewer, as for example illustrated by Benmore et al. ( 2018 ), who described three distinctive groups within their sample of 12 participants.
To illustrate Q methodology in bullying research, our small scale and exploratory study published in Educational Research (Hellström & Lundberg, 2020 ) serves as a practical example. The purpose of that study was to investigate definitions of bullying from young people’s perspectives and was guided by the following research question: What are students’ subjective viewpoints on bullying behavior? . In Table 1 , we describe the methodological steps introduced in Fig. 1 .
Q Methodology’s Response to the Methodological Issues Outlined Above
Above, methodological issues have been structured according to participants’ willingness and ability to share their subjective viewpoints and lived experiences. In order to respond to those, the present section focuses on Q methodology’s built-in features. A particularly important component is Q sorting as the central data collection technique that facilitates participants’ communicability of their subjectivity.
Engaging participants in a card sorting activity encourages students to express their viewpoints and thereby making their voices heard in a less-intrusive way, despite being cognitively engaging. Because they are asked to rank-order a predetermined sample of items, ideally in accordance with a carefully selected condition of instruction, they do not need to report or disclose their own personal experiences and are not obliged to actively create anything, as criticized in arts-based research. In that sense, Q methodology can be seen as a method to collect sensitive data in a more depersonalized way. This provides the basis to find a vital “balance between protecting the child and at the same time allowing access to important information” (Thorsen & Størksen, 2010 , p. 9), which is of particular importance for research about emotionally charged situations or sensitive topics as it is often the case with bullying (Ellingsen et al., 2014 ). Sharing their view through a fixed collection of items certainly makes participation in research for young children or otherwise hard-to-reach respondents less intimidating and results can be expected to be more truthful.
In comparison to researchers applying ethnographical approaches, who immerse themselves into the studied context to understand and document patterns of social behavior and interaction in a less intrusive way, Q methodologists are not expected to observe their participants. Even though the purpose of these approaches is different, being part of the culture under investigation or at least involving community partners in Q methodological research can still be useful for at least two reasons. As mentioned in Table 1 featuring the study by Hellström & Lundberg ( 2020 ), the pupils’ physical education and health teacher guided an exploratory and informal discussion and thereby provided valuable insights into the participants’ lifeworld that informed the Q sample. In addition to better tailoring the sample to the participants and making them feel seen and heard, the community partner could help build a positive rapport between participants and researchers, which otherwise requires much work. During the actual data collection exercise, participants were already familiar with the topic, well-informed about the research project, and perceived the sorting activity as an integral part of their lesson.
The play-like character of Q sorting has as well been reported as a positive influence on respondents’ motivation to participate (de Leeuw et al., 2019 ) and Wright ( 2013 ) mentions the engaging atmosphere created between the sorter and the researcher. The combination of these features allows assuming that obtaining participants’ viewpoint through Q methodology is less threatening than for example sitting in front of an interviewer and providing on-spot oral responses about a sensitive topic.
Q sorting as a data collection instrument represents a major advantage for Q methodological research with participants that do not (yet) possess sufficient verbal literacy and/or cognitive ability to process receptive or expressive language. To illustrate, two features are outlined here: first the flexibility of the Q sample, say the set of stimuli and second the fact that primary data collection in Q methodology is based on a silent activity.
Written statements are undoubtedly the most common type of items used in Q methodology and the number of such in a Q sample greatly varies. In recent research reporting from compulsory education settings, the average Q sample consists of about 40 items (Lundberg et al., 2020 ). In addition to applying a smaller set of items, their complexity can easily be adapted in line with participants’ receptive literacy skills and their developmental stage to facilitate understanding. Statements can for example be shortened or they can start identically to make the activity less taxing (Watts & Stenner, 2012 ). A different approach to cater to limited verbal literacy is the use of images instead of written statements. Constructing a visual Q sample might be more challenging for the researcher, in particular, if images are carefully selected and culturally tailored, meaning that they are clear, appealing and without too many details (Thorsen & Størksen, 2010 ). It might nevertheless be worth it, as such items provide a powerful tool to elicit viewpoints from otherwise marginalized or hard-to-reach research participants. Combes and colleagues ( 2004 ) for example, created a 37-item-Q sample with intellectually disabled participants’ own pictures to evaluate the planning of activities and de Leeuw et al. ( 2019 ) have used 15 images of hypothetical scenarios of social exclusion in a study with primary school pupils. Furthermore, as illustrated by Allgood and Svennungsen ( 2008 ) who photographed their participant’s own sculptures, Q samples consisting of objects (e.g., toys) or symbols (emojis) might be other options to investigate issues about bullying and cyberbullying without using text.
In addition to adaptations to the data collection instrument, the sorting process is usually carefully introduced and illustrated. Researchers might want to go through the entire Q sample to ensure the participants are able to discriminate each item (Combes et al., 2004 ). Even with adult participants without any cognitive impairments, it is suggested to pre-sort items into three provisional categories (Watts & Stenner, 2012 ). Two categories represent the respective ends of the continuum in the distribution grid and might be labeled and. Any items the sorter feels insecure or neutral about, are moved to the third category, which receives a question mark (?) for the sake of this exercise. During the actual rank-ordering process, the participants start to allocate items to one of the ends of the continuum (the top of the distribution grid in Fig. 2 ) with cards from the ☺ category and work themselves toward the center of the distribution grid. The process continues with items in the ☹ category, which are placed from the opposite end of the continuum toward the center. Any free spots are then filled with the remaining items in the (?) category. The graphic display of their viewpoint has been experienced as enabling for self-reflection (Combes et al., 2004 ) and might be utilized for a further discussion about the topic, for example as part of teacher workshops (Ey & Spears, 2020 ).
Meeting children at an appropriate cognitive level through adaptations of the data collection instrument and procedure, is not only a promising and important ethical decision in order to show young participants the respect they deserve (Thorsen & Størsken, 2010 ), but makes the sorting procedure a pleasant experience for the participants (John et al., 2014 ). Unsurprisingly, Q methodology has been described as a respectful, person-centered, and therefore child-friendly approach (Hughes, 2016 ).
Limitations
Despite its potential for bullying research, Q methodology has its limitations. The approach is still relatively unknown in the field of bullying research and academic editors’ and reviewers’ limited familiarity with it can make publishing Q methodological research challenging. Notwithstanding the limitation of not being based on a worked example, the contribution of the present paper hopefully fulfills some of the needed spadework toward greater acceptability within and beyond a field, which has only seen a limited number of Q methodological research studies. Because the careful construction of a well-balanced Q sample is time-consuming and prevents spontaneous research activities, a core set of items could be created to shorten the research process and support the investigation of what bullying means to particular groups of people. Such a Q sample would then have to be culturally tailored to fit local characteristics. Finally, the present paper is limited in our non-comprehensive selection of data collection methods as points of comparison when arguing for a more intensive focus on Q methodology for bullying research.
Future Research Directions
The results of Q methodological studies based on culturally tailored core Q samples would allow the emergence of local definitions connected to the needs of the immediate society or school context. As illustrated by Hellström & Lundberg ( 2020 ), even within the same school context, and with the same data collection instrument (Q sample), Q methodology yielded different, age-related definitions of bullying. Or in Wester and Trepal ( 2004 ), Q methodological analysis revealed more perceptions and opinions about bullying than researchers usually mention. Hence, Q methodology offers a robust and strategic approach that can foreground cultural contexts and local definitions of bullying. If desired, exploratory small-scale Q research might later be validated through large-scale investigations. A further direction for future research in the field of bullying research is connected to the great potential of visual Q samples to further minimize research participation restrictions for respondents with limited verbal or cognitive abilities.
Implications for Practice
When designing future bullying prevention strategies, Q methodology presents a range of benefits to take into consideration. The approach offers a robust way to collect viewpoints about bullying without asking participants to report their own experiences. The highly flexible sorting activity further represents a method to investigate bullying among groups that are underrepresented in bullying research, such as preschool children (Camodeca & Coppola, 2016 ). This is of great importance, as tackling bullying at an early age can prevent its escalation (Alsaker & Valkanover, 2001 ; Storey & Slaby, 2013 ). Making the voices of the hard-to-reach heard in an unrestricted way and doing research with them instead of about them (de Leeuw et al., 2019 ; Goopy & Kassan, 2019 ) is expected to enable them to be part of discussions about their own well-being. By incorporating social media platforms, computer games, or other contextually important activities when designing a Q sample, the sorting of statements in Hellström & Lundberg, ( 2020 ) turned into a highly relevant activity, clearly connected to the reality of the students. As a consequence, resulting policy creation processes based on such exploratory studies should lead to more effective interventions and bullying prevention programs confirming the conclusion by Ey and Spears ( 2020 ) that Q methodology served as a great model to develop and implement context-specific programs. Due to the enhanced accountability and involvement of children’s own voices, we foresee a considerable increase in implementation and success rates of such programs. Moreover, Q methodology has been suggested as an effective technique to evaluate expensive anti-bullying interventions (Benmore et al., 2018 ). Generally, research results based on exploratory Q methodology that quantitatively condensates rich data and makes commonalities and diversities among participants emerge through inverted factor analysis are expected to be useful for educators and policymakers aiming to create a safe learning environment for all children. At the same time, Q methodology does not only provide an excellent ground for participatory research, but is also highly cost-efficient due to its status as a small-sample approach. This might be particularly attractive, when neither time nor resources for other less-intrusive methodological approaches, such as for example ethnography, are available. Due to its highly engaging aspect and great potential for critical personal reflection, Q sorting might be applied in classes regardless of representing a part of a research study or simply as a learning tool (Duncan & Owens, 2011 ). Emerging discussions are expected to facilitate and mediate crucial dialogs and lead toward collective problem-solving among children.
The use of many different terminologies and different cultural understandings, including meaning, comprehension, and operationalization, indicates that bullying is a concept that is difficult to define and subject to cultural influences. For the purpose of designing relevant and powerful bullying prevention strategies, this paper argues that instead of pursuing a universal definition of what constitutes bullying, it may be of greater importance to investigate culturally and contextually bound understandings and definitions of bullying. Although the quest for cultural and contextual bound definitions is not new in bullying research, this paper offers an additional method, Q methodology, to capture participants’ subjective views and voices. Since particularly the marginalized and vulnerable participants, for example, bullying victims, are usually hard to reach, bullying researchers might benefit from a methodological repertoire enriched with a robust approach that is consistent with changes in methodological and epistemological thinking in the field. In this paper, we have argued that built-in features of Q methodology respond to perennial challenges in bullying research connected to a lack of willingness and limited ability to share among participants as well as studying bullying as a culturally sensitive topic. In summary, we showcased how Q methodology allows a thorough and less-intrusive investigation of what children perceive to be bullying and believe that Q methodology may open up novel possibilities for contemporary bullying researchers through its status as an innovative addition to more mainstream approaches.
Availability of Data and Material
Not applicable.
Code Availability
Change history, 18 july 2022.
A Correction to this paper has been published: https://doi.org/10.1007/s42380-022-00135-9
Acquadro Maran, D., & Begotti, T. (2021). Measurement ideas relevant to qualitative studies. In P. K. Smith & J. O’Higgins Norman (Editors). Handbook of bullying (no pages assigned yet). John Wiley & Sons Limited.
Allgood, E., & Svennungsen, H. O. (2008). Toward an articulation of trauma using the creative arts and Q-methodology: A single-case study. Journal of Human Subjectivity, 6 (1), 5–24.
Google Scholar
Alsaker, F. D., & Valkanover, S. (2001). Early diagnosis and prevention of victimization in kindergarten. In J. Juvonen & S. Graham (Eds.), Peer harassment in school (pp. 175–195). Guilford Press.
Atieno, O. P. (2009). An analysis of the strengths and limitation of qualitative and quantitative research paradigms. Problems of Education in the 21st Century , 13 (1), 13–38.
Bagnoli, A. (2009). Beyond the standard interview: The use of graphic elicitation and arts-based methods. Qualitative Research, 9 (5), 547–570. https://doi.org/10.1177/1468794109343625
Article Google Scholar
Barker, J., & Weller, S. (2003). “Is it fun?” Developing children centred research methods. International Journal of Sociology and Social Policy, 23 (1/2), 33–58. https://doi.org/10.1108/01443330310790435
Benmore, G., Henderson, S., Mountfield, J., & Wink, B. (2018). The Stopit! programme to reduce bullying and undermining behaviour in hospitals: Contexts, mechanisms and outcomes. Journal of Health Organization and Management, 32 (3), 428–443. https://doi.org/10.1108/JHOM-02-2018-0047
Article PubMed Google Scholar
Bosacki, S. L., Marini, Z. A., & Dane, A. V. (2006). Voices from the classroom: Pictorial and narrative representations of children’s bullying experiences. Journal of Moral Education, 35 , 231–245. https://doi.org/10.1080/03057240600681769
Bradshaw, C. P., Sawyer, A. L., & O’Brennan, L. M. (2007). Bullying and peer victimization at school: Perceptual differences between students and school staff. School Psychology Review, 36 , 361–382. https://doi.org/10.1080/02796015.2007.12087929
Brown, S. (1980). Political subjectivity: Applications of Q methodology in political science . Yale University Press.
Brown, S. (2006). A match made in heaven: A marginalized methodology for studying the marginalized. Quality and Quantity, 40 (3), 361–382. https://doi.org/10.1007/s11135-005-8828-2
Brown, S., Baltrinic, E., & Jencius, M. (2019) From concourse to Q sample to testing theory. Operant Subjectivity, 41 , 1–17. https://doi.org/10.15133/j.os.2019.002
Camodeca, M., & Coppola, G. (2016). Bullying, empathic concern, and internalization of rules among preschool children: The role of emotion understanding. International Journal of Behavioral Development, 40 , 459–465.
Choi, J. K., & Lee, B. S. (2019). Response patterns of nursing unit managers regarding workplace bullying: A Q methodology approach. Journal of Korean Academy of Nursing, 49 , 562–574.
Combes, H., Hardy, G., & Buchan, L. (2004). Using Q-methodology to involve people with intellectual disability in evaluating person-centred planning. Journal of Applied Research in Intellectual Disabilities, 17 , 149–159. https://doi.org/10.1111/j.1468-3148.2004.00191.x
Compier-de Block, L. H., Alink, L. R., Linting, M., van den Berg, L. J., Elzinga, B. M., Voorthuis, A., Tollenaar, M. S., & Bakermans-Kranenburg, M. J. (2017). Parent-child agreement on parent-to-child maltreatment. Journal of Family Violence, 32 , 207–217. https://doi.org/10.1007/s10896-016-9902-3
Cowie, H., & Olafsson, R. (2000). The role of peer support in helping the victims of bullying in a school with high levels of aggression. School Psychology International, 21 , 79–95.
Creswell, J. (2013). Qualitative inquiry and research design: Choosing among five approaches (3 rd ed.). Sage.
Cromer, L. D., & Freyd, J. J. (2009). Hear no evil, see no evil? Associations of gender, trauma history, and values with believing trauma vignettes. Analyses of Social Issues and Public Policy, 9 (1), 85–96. https://doi.org/10.1111/j.1530-2415.2009.01185.x
De Leeuw, R. R., de Boer, A. A., Beckmann, E. J., van Exel, J., & Minnaert, A. E. M. G. (2019). Young children’s perspectives on resolving social exclusion within inclusive classrooms. International Journal of Educational Research, 98 , 324–335. https://doi.org/10.1016/j.ijer.2019.09.009
De Leeuw, R. R., Little, C., & Rix, J. (2020). Something needs to be said – Some thoughts on the possibilities and limitations of ‘voice.’ International Journal of Educational Research, 104 , 101694. https://doi.org/10.1016/j.ijer.2020.101694
Duncan, N., & Owens, L. (2011). Bullying, social power and heteronormativity: Girls’ constructions of popularity. Children & Society, 25 , 306–316. https://doi.org/10.1111/j.1099-0860.2011.00378.x
Ellard-Gray, A., Jeffrey, N. K., Choubak, M., Crann, S. E. (2015). Finding the hidden participant: Solutions for recruiting hidden, hard-to-reach, and vulnerable populations. International Journal of Qualitative Methods, 1–10. https://doi.org/10.1177/1609406915621420
Ellingsen, I. T., Thorsen, A. A., Størksen, I. (2014). Revealing children’s experiences and emotions through. Q Methodology Child Development Research, 1–9. https://doi.org/10.1155/2014/910529
Eriksen, M. I., & Lyng, S. T. (2018). Relational aggression among boys: Blind spots and hidden dramas. Gender and Education, 30 (3), 396–409. https://doi.org/10.1080/09540253.2016.1214691
Ey, L., & Spears, B. (2020). Engaging early childhood teachers in participatory co-design workshops to educate young children about bullying. Pastoral Care in Education, 38 , 230–253. https://doi.org/10.1080/02643944.2020.1788129
Greif, J. L., & Furlong, M. J. (2006). The assessment of school bullying. Journal of School Violence, 5 , 33–50. https://doi.org/10.1300/J202v05n03_04
Griffin, R. S., & Gross, A. M. (2004). Childhood bullying: Current empirical findings and future directions for research. Aggression and Violent Behavior, 9 , 379–400. https://doi.org/10.1016/S1359-1789(03)00033-8
Goopy, S., & Kassan, A. (2019). Arts-based engagement ethnography: An approach for making research engaging and knowledge transferable when working with harder-to-reach communities. International Journal of Qualitative Methods, 18 , 1–10. https://doi.org/10.1177/1609406918820424
Hellström, L. (2019). A systematic review of polyvictimization among children with Attention Deficit Hyperactivity or Autism Spectrum Disorder. International Journal of Environmental Research and Public Health, 16 (13), 2280. https://doi.org/10.3390/ijerph16132280
Hellström, L. & Lundberg, A. (2020). Understanding bullying from young people’s perspectives: An exploratory study. Educational Research, 62 (4), 414-433. https://doi.org/10.1080/00131881.2020.1821388
Hellström, L., Persson, L. & Hagquist, C. (2015). Understanding and defining bullying– adolescents’ own views. Archives of Public Health 73 (4), 1-9. https://doi.org/10.1186/2049-3258-73-4
Hill, M. (2006). Children’s voices on ways of having a voice: Children’s and young people’s perspectives on methods used in research and consultation. Childhood, 13 (1), 69–89. https://doi.org/10.1177/0907568206059972
Hong, J. S., & Espelage, D. L. (2012). A review of mixed methods research on bullying and peer victimization in school. Educational Review, 64 (1), 115–126. https://doi.org/10.1080/00131911.2011.598917
Hughes, M. (2016). Critical, respectful, person-centred: Q methodology for educational psychologists. Educational and Child Psychology, 33 (1), 63–75.
Hughes, R., & Huby, M. (2002). The application of vignettes in social and nursing research. Journal of Advanced Nursing, 37 (4), 382–386. https://doi.org/10.1046/j.1365-2648.2002.02100.x
Hutson, E. (2018). Integrative review of qualitative research on the emotional experience of bullying victimization in youth. Journal of School Nursing, 34 (1), 51–59. https://doi.org/10.1177/1059840517740192
Jacobs, N., Goossens, L., Dehue, F., Völlink, T., & Lechner, L. (2015). Dutch cyberbullying victims’ experiences, perceptions, attitudes and motivations related to (coping with) cyberbullying: Focus group interviews. Societies, 5 (1), 43–64. https://doi.org/10.3390/soc5010043
Jia, M., & Mikami, A. (2018). Issues in the assessment of bullying: Implications for conceptualizations and future directions. Aggression and Violent Behavior, 41 , 108–118. https://doi.org/10.1016/j.avb.2018.05.004
John, A., Montgomery, D., & Halliburton Tate, A. (2014). Using Q methodology in conducting research with young children. In O. Saracho (Editor): Handbook of Research Methods in Early Childhood Education , Volume 1, (pp. 147–173), University of Maryland.
Khanolainen, D., & Semenova, E. (2020). School bullying through graphic vignettes: Developing a new arts-based method to study a sensitive topic. International Journal of Qualitative Methods, 19 , 1–15. https://doi.org/10.1177/1609406920922765
Kulig, J. C., Hall, B., & Grant Kalischuk, R. (2008). Bullying perspectives among rural youth: A mixed methods approach. Rural and Remote Health, 8 , 1–11.
Lyon, D., & Carabelli, G. (2016). Researching young people’s orientations to the future: The methodological challenges of using arts practice. Qualitative Research, 16 (4), 430–445. https://doi.org/10.1177/1468794115587393
Lundberg, A., de Leeuw, R., & Aliani R. (2020). Using Q methodology: sorting out subjectivity in educational research. Educational Research Review, 31 , 100361. https://doi.org/10.1016/j.edurev.2020.100361
Modin, B. (2012). Beteendeproblem bidrar till utsatthet för mobbning och psykisk ohälsa. I: Skolans betydelse för barns och ungas psykiska hälsa - en studie baserad på den nationella totalundersökningen i årskurs 6 och 9 hösten 2009 behavior problems contribute to victimization from bullying and poor self-related mental health. in: The role of the school for young people’s mental health. A study based on the national Swedish survey of students in grades 6 and 9 in 2009. ( No. 2012–5–15). National Board of Health and Welfare and Centre for Health Equity Studies.
Monks, C. P., & Smith, P. K. (2006). Definitions of bullying: Age differences in understanding of the term, and the role of experience. British Journal of Developmental Psychology, 24 (4), 801–821. https://doi.org/10.1348/026151005X82352
O’Brien, N. (2019). Understanding alternative bullying perspectives through research engagement with young people. Frontiers in Psychology, 10 , 1984. https://doi.org/10.3389/fpsyg.2019.01984
Article PubMed PubMed Central Google Scholar
Patton, D. U., Hong, J. S., Patel, S., & Kral, M. J. (2017). A systematic review of research strategies used in qualitative studies on school bullying and victimization. Trauma, Violence & Abuse, 18 (1), 3–16. https://doi.org/10.1177/1524838015588502
Pellegrini, A. D., & Long, J. D. (2002). A longitudinal study of bullying, dominance, and victimization during the transition from primary school through secondary school. British Journal of Developmental Psychology, 20 , 259–280. https://doi.org/10.1348/026151002166442
Punch, S. (2002). Research with children: The same or different from research with adults? Childhood, 9 (3), 321–341. https://doi.org/10.1177/0907568202009003005
Queirós, A., Faria, D., & Almeida, R. (2017). Strengths and limitations of qualitative and quantitative research methods. European Journal of Education Studies, 3 (9), 369–387. https://doi.org/10.46827/ejes.v0i0.1017
Scheithauer, H., Smith, P. K., & Samara, M. (2016). Cultural issues in bullying and cyberbullying among children and adolescents: Methodological approaches for comparative research. International Journal of Developmental Science 10 , 3–8. https://doi.org/10.3233/DEV-16000085
Scherer, L. (2016). Children’s engagements with visual methods through qualitative research in the primary school as “Art that didn’t work.” Sociological Research Online, 21 (1), 1–16. https://doi.org/10.5153/sro.3805
Shaghaghi, A., Bhopal, R. S., & Sheikh, A. (2011). Approaches to recruiting ‘hard to reach’ populations into research: A review of the literature. Health Promotion Perspectives, 1 , 86–94. https://doi.org/10.5681/hpp.2011.009
Shemmings, D., & Ellingsen, I. T. (2012). Using Q methodology in qualitative interviews. In J.F. Gubrium, J.A. Holstein, A.B. Marvasti, & K.D. McKinney (Eds.), The SAGE handbook of interview research: The complexity of the craft (2 nd ed), (pp. 415–426). Sage.
Slaughter, V., Dennis, M. J., & Pritchard, M. (2002). Theory of mind and peer acceptance in preschool children. British Journal of Developmental Psychology, 20 , 545–564.
Smith, P. K., Cowie, H., Olafsson, R. F., & Liefooghe, A. P. D. (2002). Definitions of bullying: A comparison of terms used, and age and gender differences, in a fourteen–country international comparison. Child Development 73 (4): 1119–1133. https://doi.org/10.1111/1467-8624.00461
Smith, P. K., Robinson, S., & Marchi, B. (2016). Cross-national data on victims of bullying: What is really being measured? International Journal of Developmental Science, 10 (1–2), 9–19. https://doi.org/10.3233/DEV-150174
Stephenson, W. (1935). Technique of factor analysis. Nature, 136 , 297.
Stephenson, W. (1953). The study of behavior: Q technique and its methodology. Chicago University Press.
Storey, K., & Slaby, R. (2013). Eyes on bullying in early childhood. Education Development Center. Retrieved from www.eyesonbullying.org
Swearer, S. M., Siebecker, A. B., Johnsen-Frerichs, L. A., & Wang, C. (2010). Assessment of bullying/victimization. The problem of comparability across studies and across methodologies. In S.R. Jimerson, S.M. Swearer, & D.L. Espelage (Eds.), Handbook of bullying in schools: An international perspective (pp 305- 328). Routledge
Sydor, A. (2013). Conducting research into hidden or hard-to-reach populations. Nurse Researcher, 20 , 33–37.
Thorsen, A. A., & Størksen, I. (2010). Ethical, methodological, and practical reflections when using Q methodology in research with young children. Operant Subjectivity, 33 (1–2), 3–25.
Torrance, D. A. (2000). Qualitative studies into bullying within special schools. British Journal of Special Education, 27 , 16–21.
Vacchelli, E. (2018). Embodiment in qualitative research: Collage making with migrant, refugee and asylum seeking women. Qualitative Research, 18 (2), 171–190. https://doi.org/10.1332/policypress/9781447339069.003.0004
Waters, E., Stewart-Brown, S., & Fitzpatrick, R. (2003). Agreement between adolescent self-report and parent reports of health and well-being: Results of an epidemiological study. Child Care Health Development, 29 , 501–509. https://doi.org/10.1046/j.1365-2214.2003.00370.x
Watts, S., & Stenner, P. (2012). Doing Q methodological research: Theory, method and interpretation . Sage.
Book Google Scholar
Wester, K. L., & Trepal, H. C. (2004). Youth perceptions of bullying: Thinking outside the box. Operant Subjectivity, 27 , 68–83.
Woodhead, M., & Faulkner, D. (2008). Subjects, objects or participants? Dilemmas of psychological research. In P. Christensen & A. James (Eds.), Research with children (2nd ed., pp. 10–39). Routledge.
Wright, P. N. (2013). Is Q for you?: Using Q methodology within geographical and pedagogical research. Journal of Geography in Higher Education, 37 (2), 152–163. https://doi.org/10.1080/03098265.2012.729814
Download references
Open access funding provided by Malmö University.
Author information
Authors and affiliations.
Malmö University, Malmö, Sweden
Adrian Lundberg & Lisa Hellström
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Adrian Lundberg .
Ethics declarations
Ethics approval, consent to participate, consent for publication, conflict of interest.
The authors declare no competing interests.
Additional information
The original online version of this article was revised: References are not in alphabetical order.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Lundberg, A., Hellström, L. Q Methodology as an Innovative Addition to Bullying Researchers’ Methodological Repertoire. Int Journal of Bullying Prevention 4 , 209–219 (2022). https://doi.org/10.1007/s42380-022-00127-9
Download citation
Accepted : 26 April 2022
Published : 11 May 2022
Issue Date : September 2022
DOI : https://doi.org/10.1007/s42380-022-00127-9
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Bullying prevention
- Children’s voice
- Hard-to-reach
- Methodological issues
- Q methodology
- Find a journal
- Publish with us
- Track your research
Joining forces to Combat Cyberbullying in Schools
Category: Chapter 3: Cyberbullying
3. cyberbullying.
Social media sites have tremendous value and potential for learning, socializing, leisure and development of young people. However, they are not always healthy and problem-free environments. Some potential challenges include interference with cognitive processes such as attention, memory, information processing and emotional processing, “Facebook depression”, sexting, exposure to inappropriate content and cyberbullying.
In this chapter, we will be focusing specifically on cyberbullying as one of the most problematic aspects of social media and communication technology. We will be thinking about how having fun online needs to come with responsibility. Social networking can often be just one click away from cyberbullying. The key to decreasing cyberbullying among young people is to ‘ think before they click 3 , especially as just one click has the power to change someone’s life forever.
The first section of this chapter will define key terminology connected to cyberbullying. An overview of what research tells us about cyberbullying and how it works is followed by information on key risk factors and protective factors. Finally, we will list a few guidelines for addressing cyberbullying and legal considerations that we must keep in mind when working in school contexts.
3.1 What is What in Cyberbullying?
Short definitions below are listed with the purpose of establishing a common language and understanding among stakeholders within our project. They should be considered not final descriptions but working definitions that participants are welcome to discuss, challenge and amend as the project knowledge base evolves.
3.1.1 Bullying and cyberbullying
Bullying is an aggressive behaviour of more powerful individuals against weaker ones, for example hitting, verbally threatening or mocking, spreading rumours, taking the money and other actions. Bullying typically peaks in frequency during adolescence.
Cyberbullying is deliberately using digital media to communicate false, embarrassing, or hostile information about another person. It can happen through cell phones, computers, tablets and other electronic devices and communication tools like websites, text messages, instant messages, e-mail, social networking sites, applications or chat. Cyberbullying is the most common online risk for teens, can occur to any young person online, and can cause psychosocial outcomes 4 such as depression, anxiety, severe isolation, and even suicide.
Cyberbullying can have many forms. It can be a mean, hurtful or threatening message to someone or about someone. It can be an embarrassing post, picture or video. It can be a website or a fake profile. It can be a rumour spread by e-mails, texts or posted on social networking sites and many other things. Cyberbullying is often anonymous (the bully does not use his or her name), public (in open view for other people) and viral (rapidly and widely circulates on the internet or through other media). This video can give you an idea how cyberbullying can spread quickly, much like a virus.
3.1.2 Bullies, targets and bystanders
Cyberbullying usually includes a bully (or bullies), a target and several observers. Cyberbully is someone who engages in cyberbullying. Cyberbullies use the internet and electronic devices to emotionally hurt others by making fun of them or insulting them.
Targets of cyberbullying are individuals who are hurt by such actions. Most often, cyberbullying does not stay limited to the bully and the target. There may be many observers, who can take on many roles: they can be passive bystanders , they can perpetuate the bullying or they can act to stop cyberbullying.
3.1.3 Preventative measures and strategies
Cyberbullying is difficult to stop. However, there are things individuals and communities can do to stop it from happening or limit it from spreading. For example, targets of cyberbullying can temporarily limit their online connection time; avoid opening messages from unknown sources, change passwords or accounts. In extreme cases, authorities may get involved and legal actions may be taken.
Often, cyberbullying becomes a bigger problem than just something between individuals. A community might become aware that cyberbullying has become prevalent and threatens the well-being of its members and develop specific measures to fight it and to relieve negative effects. Such activities can be simple activities or complex strategies .
With the rise of cyberbullying, certain organizations, initiatives, and projects have been developed to deal specifically with this phenomenon. Their activities can be online-based (some examples include informational and promotional videos, infographics, websites, virtual campaigns, online courses for teachers and youth workers) or done in-person or through other media (workshops, counselling, lectures, research, training, skill building activities, TV shows or magazines articles). Preventative measures to fight cyberbullying often include basic online safety training.
3.1.4 Online safety
3.1.5 Digital citizenship
Digital citizenship has nine elements: digital access, digital commerce, digital communication, digital literacy, digital etiquette, digital law, digital rights and responsibilities, digital health and wellness and digital security. Themes like digital security, etiquette, rights and responsibilities, health and wellness are closely connected to the topic of cyberbullying. Many cyberbullying prevention programs focus on teaching these skills.
Digital etiquette or netiquette is a new word that combines the concepts of ‘inter net ’, net working and etiquette . It means online etiquette, the rules of online communication. Netiquette covers common courtesy online as well as the informal do’s and don’ts of cyberspace.
Respect, educate and protect (REPs) is another popular concept closely connected to digital citizenship that is often used in cyberbullying prevention. It is a way to present nine elements of digital citizenship in a way that is appropriate even for very young learners (from kindergarten level onwards).
3.2 How is Cyberbullying Different from ‘Traditional’ Bullying?
Hurting someone’s feelings, causing problems for them and making them feel bad are not new phenomena among young people. We would like to believe that we are teaching young people intra- and interpersonal skills that will help them feel confident in themselves as well as emphatic and respectful towards others, but the reality is that peer bullying has been a big challenge for schools, youth organizations, and local communities for many years. Is cyberbullying just a contemporary expression of this?
Studies are beginning to show 3 that cyberbullying is very different from traditional schoolyard bullying. Some important differences are shown in the picture below.
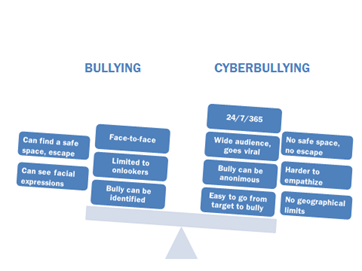
Research indicates that cyberbullying is rarely premeditated like traditional bullying. 3 Cyberbullying is often done impulsively and not planned out like in traditional bullying where the bully plans the attacks.
Traditional bullying is usually limited to certain times and places, for example, the playground or the way to school. This gives the target some (although limited) sense of predictability, and there are times and places where he or she can feel safe. In contrast, technology is everywhere: we have our phones and computers around us all the time. Cyberbullying can happen 24 hours a day, 7 days a week and 356 days a year. It can happen in our close proximity or through great distances. It is difficult for the target to find a safe space.
Furthermore, traditional bullying is characterized by the need for power and control, aggression and proactively targeting the target. These characteristics may not be present in cyberbullying cases.
Cyberbullying is “an easier way to bully because unlike traditional bullying it doesn’t involve face to face interaction.” 3 Hiding behind the computer decreases empathy the bully feels toward the target. When we do not see the person’s reaction to what we post or text them, we might not know that we have gone too far. Desensitized by the computer screen, it becomes easier to say or do things we would not do to a person’s face. Furthermore, while “traditional” bullies can mostly be identified, it can be very difficult to find out who the anonymous cyberbullies are, making it easier for bullies to avoid seeing and facing the consequences of their actions.
In traditional bullying, we are usually working with a bully, target or bystander. Although we often find that bullies have previously experienced violence themselves (perhaps when they were younger or by someone with more power), the roles in each case are pretty clear. This is not necessarily the case in cyberbullying. Young people often play multiple roles at once, such as cyberbully, target, and witness. There is also no clear-cut profile of who can be the cyberbully and who can be the target, it can happen to anyone.
An especially problematic aspect of cyberbullying is that it often has many, many onlookers. Traditional bullying is more often done in private than in public. But in cyberbullying, technology makes it easy to quickly spread content to a large number of people. Online bullying can quickly become very public or even viral. This wide audience makes the experience especially difficult and embarrassing for the target.
Current research in public health indicates that many “social” factors such as education, socioeconomic conditions, access to services and resources, family ties, employment etc. are closely related to the person’s general health and mental health, including the ability to avoid or cope with violence and “traditional” bullying. Such connections with cyberbullying are less clear. It rather seems that there are no ‘typical’ cyberbullies and targets, it can happen to anyone. For example, it is well documented that in traditional bullying males are more likely to become bullies than females; that older adolescents are more likely to bully than preadolescents, and that bullies are more likely to have low than high self-esteem. For cyberbullying, on the other hand, age, gender or self-perception do not seem to be reliable predictors. Interestingly, high-quality relationships with important adults seem to be a strong protective factor in both types of bullying, traditional and cyber.
3.3 Dynamics of cyberbullying
Cyberbullying is often done by young people who have increasingly early access to online media and technologies. In this section, we will review how this dynamic typically plays out.
3.3.1 How does cyberbullying begin?
A big part of cyberbullying does not start out with an intention to deeply hurt someone. Young people post or text something they think is a joke or a random comment, but it may not be all that funny for the receiver. In fact, it could easily cross the line to cyberbullying.
In a recent online pilot study, young people who engage in cyberbullying behaviour reported the following reasons for their actions: posting without thinking they could hurt anyone (72%), to get back at someone (58%), the target deserved it (58%), for fun or entertainment (28%), to embarrass the target (21%), to be mean (14%), to show off to friends (11%) and other reasons (16%).
We will be exploring who is especially at-risk of becoming a cyberbully or a target in one of the following sections. For now, it is important to know that cyberbullying can happen to anyone. Relatively little can be said about a typical cyber target or a typical cyberbully: they can be rich kids or poor kids, left-out kids or popular ones, A-students or struggling students, majority or minority students, someone who has been bullied before or someone who has never experienced violence, someone who is online much too much or someone who rarely uses technology, it can be someone who uses technology to pass their free time by browsing and chatting, but also someone who mostly uses it for online learning, research, time management or school.
Nevertheless, there are some things young people can do to protect themselves online: 3
- Keep privacy settings on. Secure all online information.
- Protect their usernames and passwords. Do not share them with friends.
- Choose friends wisely, including virtual contacts.
- Only accept close friends on social networking sites.
- Do not share personal information online.
- Do not open anything from someone they don’t know.
3.3.2 What happens next?
After the hurtful messages, comments or pictures have been posted recipients are likely to respond inwardly with feelings of fear, sadness, and anxiety. Even if cyberbullying is done jokingly or unintentionally, it does not change the fact that this action can deeply hurt the targeted individual.
Signs that someone is being cyberbullied are similar to signs of being victimized in other ways. Some emotional, academic, social and behavioural indicators to look out for are listed in the chart below 12 .

Outward responses of cyberbullying recipients can also vary. Some recipients may just ‘shake it off’ and not let it bother them; others may react aggressively or retaliate. Some might respond, but be assertive but polite and others may stay passive and not do anything about the problem. Some might plan steps and actions to take. Some might respond emotionally. They might tell someone or hide what is happening from others or do a range of other things.
In prevention work with young people, it is important to teach them how different kinds of responses are likely to impact the outcome of cyberbullying. For example, retaliation or aggressive response has been shown to make the situation worse, whereas passive avoidance could lead to serious psychological consequences for the targeted individual.
Some basic tips for young people who encounter cyberbullying are:
- Tell a trusted adult if they are being cyberbullied.
- If they know someone who is being a cyberbully tell them to stop or report it.
- Contact host/site providers if inappropriate material is being posted on their site.
- Save all evidence if they are being bullied online. Do not delete anything without keeping a copy for yourself.
- Do not respond to rude messages. Rude comebacks only make things worse.
- Do not post anything online that they would mind their parents and friends seeing.
- Most importantly, treat others as they want to be treated. Consider what they are posting or uploading and ask themselves: “Would I want someone saying or putting that about me online?”
3.3.3 How does cyberbullying end?
Cyberbullying might die out on its own in time. However, if not stopped, cyberbullying can go on for a long time, and due to its public and viral nature, it can be especially damaging. Prolonged exposure can lead to serious consequences, so it is not advisable to wait. Cyberbullying often stops only through the involvement of outside support, either by contacting the social media used that takes down the offending content and informs the cyberbully of the consequences or through parental and teacher involvement.
Prevention and intervention work for combating cyberbullying should include some simple strategies An example of a useful, simple four-step strategy for dealing with cyberbullying is presented in this video and this worksheet .
After the cyberbullying has stopped, follow-up work needs to be done with targets of cyberbullying as well as the bullies. Targeted young people need support to work through feelings of embarrassment, shame, guilt, fear, isolation, sadness and anxiety. Counselling is often useful.
Cyberbullies, on the other hand, need to be shown the impact of their action and strengthen their social and communication skills, moral reasoning, empathy and conflict resolution skills. Non-judgemental and restorative approaches have been shown effective to stop cyberbullies repeat their behaviour.
3.4 Who is At Risk?
What does it mean to be at-risk of cyberbullying? This means that it is quite likely that someone might become involved in cyberbullying; either as a target, as a bully or as a bystander. In the last subchapter, we already mentioned some things that might put someone at risk of or protect them from bullying or cyberbullying.
3.4.1 What puts someone at risk and what protects them?
When we talk about at-risk groups for any problems that children and youth face, we like to think in terms of risk factors and protective factors : what puts someone at risk of unwanted things happening to them? What protects them from the problem or at least from suffering serious consequences? We understand many risk factors and protective factors that influence the physical and mental wellbeing of children and youth, their educational success, their relationships, their self-esteem, their future happiness, job prospects and their resilience to difficult events or other challenges.
For example, we know that children and young people, who face higher risks of becoming involved in ‘traditional’ bullying, often feel lonely, perceive their parents as distant and have problematic relationships with other adults in their lives like their teachers. They might have personal experience with violence in the family, peer group or other immediate environment. Many also have low self-esteem, poor social skills and communication skills. Traditional bullies are more likely to be male than female and more likely to be older adolescents than preadolescents. Targets of ‘traditional’ bullying, on the other hand, are likely to have low self-esteem, distinct physical features are also very common (for example short and weak, glasses, obesity, disability), they are also often less popular among their peers. A very strong protective factor for someone that is a target of traditional bullying, for example, is having a trusted adult that they can talk to about what is happening, or growing up in an environment where information and support are available.
This short sampling of risk factors and protective factors probably seems so self-evident that we do not even need to mention them! However, it is worth mentioning them because something interesting happens when we take a closer look at cyberbullying.
3.4.2 What are risk factors and protective factors in cyberbullying?
A number of studies and scholarly papers investigate which children and adolescents are most and least at risk of experiencing cyberbullying. Results are interesting and unexpected: when it comes to cyberbullying, there are almost no common risk factors except opportunity. Online access and unsupervised online time and technology use is clearly a ‘prerequisite’ for cyberbullying. However, not all forms of media usages raise the risk of experiencing cyberbullying. Children and adolescents who spend more time using their cell phone are more likely to report receiving aggressive or threatening electronic communication, but no such relationship seems to exist between time spent on the internet and either form of online bullying 6 .
Most studies find that age and gender do not have a very clear predictive role in cyberbullying. Some early research findings suggested that cyberbullies are often kids who were themselves bullied in real life. But later research found that cyberbullies and targets can just as well be popular, well-adjusted kids who have not been exposed to peer-aggression before. Whereas low self-esteem is usually linked to traditional bullying, many cyberbullies demonstrate a high perception of self-esteem in perceiving their relationships with peers as satisfying. However, feelings of loneliness and a perception of unsafety at school were often linked to cyberbullying.
In short, there seem to be very few common risk factors and even fewer protective factors that would prevent children and young people from becoming involved in cyberbullying. It really can happen to anyone. Research findings suggest that the most important protective factors against cyberbullying are strong parent relationships and positive experiences at school. Restrictions on media use enforced by adults were far less effective in fighting cyberbullying. 6
However, although there are few risk factors that can help us predict involvement in cyberbullying and very few protective factors that would prevent children and young people from becoming involved, there are some important protective factors that can help them respond to cyberbullying resiliently. We might not be able to prevent cyberbullying from happening, but we can do things to minimize the damage so that the children and young people do not suffer prolonged or even life-threatening consequences. This can make a key difference in outcomes of cyberbullying both for the bullies and the targets.
Again, strong relationships among children and adults and positive school experiences are the strongest predictors of resilient response for children and adolescents who have faced cyberbullying. More specifically, students tended to behave resiliently if they:
- they could find an environment that felt emotionally and physically safe,
- had a trusted adult to talk to about problems,
- had parents of caretakers with basic digital competencies and awareness of online safety,
- experienced peer support and felt they are not alone in their experience,
- had access to practical information on what they can do to stop cyberbullying,
- had strong self-esteem, empathy, and social skills,
- were able (or given support) to cope with emotions, especially feelings of shame, guilt, sadness and fear.
Children and young people who have been onlookers are often at risk of perpetuating such behaviour. This is why it is so important to build healthy, empowering communities where cyberbullying does not go unrecognized, where such behaviour is talked about and challenged and where solutions for better relationships are found and invested in.
3.5 Types of Cyberbullying
Cyberbullying has many forms and can include a variety of acts. It can be sending a mean text message, making online threats, sending unwanted provocative photos, posting insults or hate speech, attempting to infect the target’s computer with a virus, flooding an e-mail inbox with messages 2 or sending harmful material and any other form of social aggression using the Internet or other digital technologies. Some of the most common cyberbullying tactics are briefly described below.
3.6 Case studies
Educators, youth workers, parents and other adults working with children and young people are likely to come across cyberbullying incidents. To successfully deal with cyberbullying we must first learn to recognize it, analyse it and understand what exactly is going on. Secondly, we need to be aware of effective strategies to support the victim and challenge the bullying behaviour.
Our reactions will often determine the outcomes of cyberbullying incidents: what will be the consequences for the victim, the bully, and the onlookers; how will the community and relationships be shaped by this experience; will children and young people learn from it or be harmed by it? Furthermore, when faced with cyberbullying cases we might want to think about how to prevent similar events in the future and how to help children and young people develop skills for healthy, positive use of online media and communication technology.
In the following section, we have compiled short descriptions of six real-life cyberbullying cases that are also available on the internet in even more detail. We would suggest you take the time to read through them, think about them and try to propose solutions or guidelines for intervention. For the first three cases, we have already outlined some bullet points to help you think through them. However, these are suggestions rather than definite solutions. You might find solutions that are even more appropriate for your school, your community, your group of children or young people.
3.6.1 How to use case studies
What is a case study? It is a form of problem-based learning. A case study describes a situation that needs a solution, an idea, an intervention, a strategy. You may want to do this by yourself or with the discussion in small groups. Case studies are a wonderful tool to help you understand key concepts in much more depth. This is more important than finding perfect solutions. They are also great team-building opportunities. To solve a case, team members will have to work through different opinions, ideas, perspectives, and ways of working. This is why we recommend you use the following case studies in your training sessions for school staff, parents and youth workers. To facilitate a training session using case studies, you might follow these steps:
- Greet the group and introduce yourself.
- Briefly, present the topic of a session (e.g. types of cyberbullying and effective strategies for each type).
- Introduce the situation in a sentence or two.
- Give a print of the case (and perhaps some thought-provoking discussion questions) to each participant.
- Have participants quietly read through the text.
- Have the group summarize the key points; make sure everyone understands the basics of the case.
- Divide participants in pairs or small groups. Have them talk about the case and the discussion questions. Have them brainstorm and discuss possible solutions and strategies.
- Ask each pair or small group to contribute one or two important ideas.
- Address open questions and dilemmas. But remember: you are not expected to have all the answers. Your job is to help participants think deeply about this important topic, not to give answers and recipes.
- Review key concepts of the training session together with participants.
Case studies are also a very helpful tool to work with children and young people. Real cases and specific situations are something they can understand and relate to. Experience helps them learn. You can use case studies during cyberbullying awareness workshops, mediation club meetings and in conflict-resolution training sessions. You might want to have the students read and discuss the cases or even use role-play to act them out. However, a word of caution: students might perceive these cases very differently than adults. Make sure the case descriptions are age-appropriate, understandable, short and concise. A very important point is also NOT to overburden students emotionally: for example, it might be very difficult for them to process stories about cyberbullying resulting in suicides of young people. We also strongly encourage you to use case studies with happy or open endings when working with students.
3.7 Case study 1: Ashley’s new website, unknown to her

Unknown to Ashley at the time, a classmate when she was 11 began taking photos of her. The images were then made part of a portfolio of information posted on the Internet with a fake social media page. The topic was Ashley and the website page was made to look as if Ashley posted everything herself. It was only through friends and third parties that Ashley became aware of the existence of the online information. The data was detailed as well; it included her school name, her home address, her family information, birthdays and more. Worse, all the data was set to be wide open to the public without any filtering or restriction. The creator of the page was confronted but denied the act. In the meantime, Ashley began to be ostracized by her friends at school. To break the freeze-out cycle Ashley had to enrol in a different middle school to regain a “clean slate.”
In Ashley’s case, the damage was limited and constrained to the loss of a few friends. However, it could have been far worse. Further, the damage was caused by another child who simply had the time and access to post whatever was desired on the Internet for anyone to read.
3.8 Case study 2: Nude photo leaked online

Jessica was feeling miserable and depressed. She was afraid to go to school and started skipping classes. Jessica’s mother only learned of a problem at all when she started getting letters from school reporting that her daughter was skipping school. Jessica’s mother took away her daughter’s car and drove her to school herself, but Jessica still skipped classes. She told her mother there were pictures involved and a group of younger girls had received them and were harassing her and calling her vicious names. Unfortunately, the mother didn’t realize the full extent of her daughter’s despair.
When the school officials became aware of the harassment they offered to go to one of the girls who had the pictures and tell her to delete them from her phone and never speak to Jessica again. Jessica’s mother saw the solution in talking to the parents of the girls who were bullying Jessica, but her daughter said that would only open her to even more ridicule.
2 months later Jessica committed suicide.
3.9 Case study 3: Emails from an unknown sender

One day as Sara arrived at school, other students began to giggle and laugh at her. Some even made strange remarks about her eating lunch in the lunchroom. Sara was embarrassed and confused. She did not mention this to anyone that day and thought that it would just go away.
After returning home from school, Sara decided to check her email. She had one email from a person that she did not recognize. Inside the email, was an embarrassing picture of Sara in the lunchroom eating. Immediately, Sara realized that this picture was the reason that all the students had been laughing at her when she arrived at school that day. Another student must have taken this picture in the lunchroom at school and sent it to everyone in her class. Sara was alarmed and began to cry. She immediately deleted the email and did not tell anyone about the email.
As the weeks passed, the incidents escalated. Sara received more and more embarrassing and sometimes even threatening emails from the person. She deleted each and every one. Sara was too humiliated to tell her parents or her teachers. Her teachers noticed that she had begun to fall behind in school and seemed to be very depressed.
3.10 Case study 4: Hateful texting

Gina’s parents had never talked to her about bullying, or how to handle such behaviour when you become the victim. The 14-year-old was completely unprepared to face such a major assault on her self-esteem. She was devastated, and soon began to withdraw from her friends and active social life. She spent more and more time alone in her room. Her mom grew concerned when Gina would no longer talk about what was going on at school or in her life. So she reached out to one of Gina’s closest friends and learned about the hateful texts her daughter was receiving.
Gina’s mom took action before the emotional toll became worse. She told Gina she knew about the cyberbullying, and together, they discussed the situation with the school counsellor and principal. With support from her family and teachers she trusted, Gina found the strength to talk to the girlfriend she had argued with, apologized for the quarrel and asked her to call off the texting campaign. While their friendship was over, the cyberbullying stopped.
3.11 Case study 5: Rumours and exclusion

3.12 Case study 6: The New Kid at School

The postings became nastier, and soon some students were making loud comments in the lunchroom and on the playground. Henry had to endure many weeks of feeling humiliated and hurt before anyone realized what was going on. His parents didn’t even know because Henry was too embarrassed to tell them. Finally, a teacher overheard some of the names and asked Henry what was going on. He described the social media page and cyberbullying.
The school, which had trained its teachers and had a zero-tolerance policy on bullying, responded quickly. They identified the ringleaders, and with the help of their parents, had the creator of the unauthorized school page take it down from the social media site. School officials hosted sessions for parents and students about cyberbullying and how to prevent it.

IMAGES
VIDEO
COMMENTS
Chapter 3: Research Design and Methodology. Introduction. The purpose of the study is to examine the impact social support (e.g., psych services, peers, family, bullying support groups) has on ...
School bullying research has a long history, stretching all the way back to a questionnaire study undertaken in the USA in the late 1800s (Burk, 1897).However, systematic school bullying research began in earnest in Scandinavia in the early 1970s with the work of Heinemann and Olweus ().Highlighting the extent to which research on bullying has grown exponentially since then, Smith et al. found ...
This chapter provided an overview of the wide range of research methods that have been used in cyberbullying research over the years, including descriptions of our own experiences with these methods. Because cyberbullying is a phenomenon that has mainly been studied among children and adolescents, special attention has been paid to the ...
Cyberbullying prevention should include individual, relationship, community, and societal factors. Cyberbullying is closely related to in-person bullying and aggression, but it has some unique risk and protective factors also. This chapter conceptualizes cyberbullying as broadly within the umbrella of peer interactions.
As a new focus of inquiry, the knowledge base on cyberbullying is limited, and the need for solid information is great. Because cyberbullying is a worldwide problem affecting young people, new knowledge has important applications to the development of prevention and intervention programs that are sorely needed. This volume is the first to provide guidelines for cyberbullying researchers in ...
ABSTRACT. In 2010, the International Cyberbullying Think Tank was held in order to discuss questions of definition, measurement, and methodologies related to cyberbullying research. The attendees' goal was to develop a set of guidelines that current and future researchers could use to improve the quality of their research and advance our ...
Abstract. In this chapter, we propose five principles to serve as guidelines for cyberbullying research methods: engaging multidisciplinary teams, using a broad selection of quality methods, understanding the importance of formative research, realizing the value of target audience involvement, and promoting ethical practice in online environments.
In book: Principles of Cyberbullying Research: Definitions, Measures and Methodology (pp.112-124) Chapter: Methods Used in Cyberbullying Research
entitled 'New bottle but old wine: A research of cyberbullying in schools', shows that 54% of. the 177 seventh grade students in Canada had been bullied offline, and 25% had been bullied ...
Methodology The analysis in this report is based on a self-administered web survey conducted from April 14 to May 4, 2022, among a sample of 1,316 dyads, with each dyad (or pair) comprised of one U.S. teen ages 13 to 17 and one parent per teen.
Despite the mounting volume of research in the area of traditional forms of bullying (i.e., verbal, physical, relational) that are transmitted face to face, cyberbullying research is only recently beginning to burgeon. The goals of this chapter are threefold. First, we review numerous theories that have been empirically supported in the aggression, bullying, and general social development ...
View PDF. Chapter 3: Research Design and Methodology Introduction The purpose of the study is to examine the impact social support (e.g., psych services, peers, family, bullying support groups) has on academic success, self-esteem, and self-efficacy among college students who are cyberbullying victims.
Abstract. Despite cyberbullying being regarded as a new form of bullying, it is also contextualized within the broader bullying literature. This chapter will provide a review of the literature concerning cyberbullying, to offer insight into its conceptualization. The chapter will discuss the development of digital technologies and opportunities ...
A mixed-methods research design first using quantitative then qualitative data was used in order to explore what cyberbullying policies are being employed by principals in the state of Nevada.
researchers such as Law et al. (2012) also suggested that bullying whether it is tra-ditional face-to-face bullying or cyberbullying should include the component of a power differential between bully and victim. Kowalski and Limber (2007) examined cyberbullying among 3,767 mid-dle school students in United States.
Principles of Cyberbullying Research. : Sheri Bauman, Donna Cross, Jenny L. Walker. Routledge, 2013 - Computers - 358 pages. In 2010, the International Cyberbullying Think Tank was held in order to discuss questions of definition, measurement, and methodologies related to cyberbullying research. The attendees' goal was to develop a set of ...
study's scope and methodology and addresses how the research will be conducted and analyzed. Chapter four presents the results of the study as well as a discussion of the three key themes that emerged from the research and how they align with the guiding theory presented in chapter two. Finally, chapter five summarizes the study, discusses
Cyberbullying often occurs within the context of existing social (offline) groups and is mostly aimed at one individual. In this way, cyberbullying also differs from forms of harassment by strangers aimed at one wellchosen target (e.g., pedophilic acts) or at a group of people (e.g., sending viruses or spam). REFERENCES 1.
School bullying and cyberbullying are complex phenomena, and a range of methodological approaches is thus needed to understand their complexity (Pellegrini & Bartini, 2000; Thornberg, 2011). Indeed, over-relying on quantitative meth-ods limits understanding of the contexts and experiences of bullying (Hong & Espelage, 2012; Patton et al., 2017).
Chapter 3 Research Methodology. Research Design The research I was conducting is a qualitative research. The information to be gathered are words and not numbers. My research is about finding ways to prevent bullying in UNCA. This research is finding more about the bullying that's happening in school.
CHAPTER 3 METHODOLOGY Overview This research details the pilot study implementing the Olweus Bully Prevention Program. The study took place in a third - eighth grade school setting during the 2005-2006 school year. The program was based on evidence of bullying behaviors occurring in the school. The goal was to reduce, if not eliminate, the ...
Bullying, internationally recognized as a problematic and aggressive form of behavior, has negative effects, not only for those directly involved but for anybody and in particular children in the surrounding environment (Modin, 2012).However, one of the major concerns among researchers in the field of bullying is the type of research methods employed in the studies on bullying behavior in schools.
Category: Chapter 3: Cyberbullying. 3. Cyberbullying. Social media sites have tremendous value and potential for learning, socializing, leisure and development of young people. However, they are not always healthy and problem-free environments. Some potential challenges include interference with cognitive processes such as attention, memory ...