- A+ Cert Exam
- Network + Cert Exam
- Server+ Cert Exam
- Security+ Cert Exam
- CCNA Cert Exam
- CCNP Cert Exam
- ITIL Foundation Cert Exam
- PMP Cert Exam
- JNCIA-Junos Cert Exam
- OCPJP Cert Exam
- OCA Cert Exam
- CIW Associate Cert Exam
- SMT Component & Assembly
- Reliability Enhancement
- SMD Components
- Nano Technology Introduction
- Fundamentals of SatCom
- Link Budgeting Explained
- Satellite link budget calculator
- Satellite look-angle calculator
- Satellite Phones
- RF, Microwave, and Optical Comm. - A review
- Satellites and Services
- Motherboard Connectors On a PC
- Motherboard-I
- Motherboard-II
- Flash Memory Tutorial
- Printers and Scanners
- Cellular Phones
- OSI Model: A tutorial
- Introduction to TCP/IP
Computer Networking
- Routers-IOS & JUNOS
- Wimax,LTE, and 3G/3.5G - Intro
- WiMAX: Wireless Broadband
- Broadband Internet Technologies
- RFID: A Beginner's Guide
- Spread Spectrum Comms.
- A tutorial on IPv6
- Cloud Computing
- Introduction to MPLS
- Initial Software Config on SRX100
- comptia aplus core 1 study notes
- comptia aplus core 2 study notes
- comptia Networkplus study notes
- comptia Securityplus study notes
- comptia Serverplus study notes
- comptia IT Fundamentals study notes
- Cisco CCNA study notes
- Cisco CCNP ENCOR study notes
- Cisco CCNP ENARSI study notes
- Cisco CCST Networking study notes
- Cisco CCST Cybersecurity study notes
- Juniper JNCIA study notes
- Co-axial Cable Measurements
- Spectrum Analyzers Intro
- Noise Figure Measurement
- Time/Frequency Standards
- Coax Cables - Intro
- Android App Development
- Essentials of Webpage Development
- Introduction to HTML5
- Introduction to Java
- Introduction to MySQL
- ActiveX EXE:Beginner's Guide
- Working w/ MyODBC & MySQL
- Drag-n-Drop Using Visual Basic
- Drag-n-Drop Using VB.net
- Network Simulator-2 (NS2)
- Computers & Networking
- The OSI (Open Systems Interconnection) model

The OSI (Open Systems Interconnection) Model
1. the osi (open systems interconnection) model.
Definition: The OSI model defines internetworking in terms of a vertical stack of seven layers. The upper layers of the OSI model represent software that implements network services like encryption and connection management. The lower layers of the OSI model implement more primitive, hardware-oriented functions like routing, addressing, and flow control.
The OSI model was introduced in 1984. Although it was designed to be an abstract model, the OSI model remains a practical framework for today's key network technologies like Ethernet and protocols like IP.
The OSI model should be used as a guide for how data is transmitted over the network. It is an abstract representation of the data pathway and should be treated as such.
The OSI model was specifically made for connecting open systems. These systems are designed to be open for communication with almost any other system. The model was made to break down each functional layer so that overall design complexity could be lessened. The model was constructed with seven layers for the flow of information. These are:
- Application Layer
- Presentation layer
- Session layer
- Transport layer
- Network layer
- Data link layer
- Physical layer
1.1 Application layer
Provides a means for the user to access information on the network through an application. This layer is the main interface for the user to interact with the application and therefore the network.
The application layer is the OSI layer closest to the end user, which means that both the OSI application layer and the user interact directly with the software application. This layer interacts with software applications that implement a communicating component. Such application programs fall outside the scope of the OSI model. Application layer functions typically include identifying communication partners, determining resource availability, and synchronizing communication. When identifying communication partners, the application layer determines the identity and availability of communication partners for an application with data to transmit. When determining resource availability, the application layer must decide whether sufficient network resources for the requested communication exist. In synchronizing communication, all communication between applications requires cooperation that is managed by the application layer.
Some examples of application layer implementations include Telnet, File Transfer Protocol (FTP), and Simple Mail Transfer Protocol (SMTP).
1.2 Presentation layer
Manages the presentation of the information in an ordered and meaningful manner. This layer's primary function is the syntax and semantics of the data transmission. It converts local host computer data representations into a standard network format for transmission on the network. On the receiving side, it changes the network format into the appropriate host computer's format so that data can be utilized independent of the host computer. ASCII and EBCDIC conversions, cryptography, and the like are handled here.
The presentation layer provides a variety of coding and conversion functions that are applied to application layer data. These functions ensure that information sent from the application layer of one system would be readable by the application layer of another system. Some examples of presentation layer coding and conversion schemes include common data representation formats, conversion of character representation formats, common data compression schemes, and common data encryption schemes.
Common data representation formats, or the use of standard image, sound, and video formats, enable the interchange of application data between different types of computer systems. Using different text and data representations, such as EBCDIC and ASCII, uses conversion schemes to exchange information with systems. Standard data compression schemes enable data that is compressed. or encrypted at the source device to be properly decompressed, or deciphered at the destination.
Presentation layer implementations are not typically associated with a particular protocol stack. Some well-known standards for video include QuickTime and Motion Picture Experts Group (MPEG). QuickTime is an Apple Computer specification for video and audio, and MPEG is a standard for video compression and coding.
Among the well-known graphic image formats are Graphics Interchange Format (GIF), Joint Photographic Experts Group (JPEG), and Tagged Image File Format (TIFF). GIF is a standard for compressing and coding graphic images. JPEG is another compression and coding standard for graphic images, and TIFF is a standard coding format for graphic images.
1.3 Session layer
Coordinates dialogue/session/connection between devices over the network. This layer manages communications between connected sessions. Examples of this layer are token management (the session layer manages who has the token) and network time synchronization.
The session layer establishes, manages, and terminates communication sessions. Communication sessions consist of service requests and service responses that occur between applications located in different network devices. These requests and responses are coordinated by protocols implemented at the session layer. Some examples of session-layer implementations include Zone Information Protocol (ZIP), the AppleTalk protocol that coordinates the name binding process; and Session Control Protocol (SCP), the Decent Phase IV session layer protocol.
1.4 Transport layer
Responsible for reliable transmission of data and service specification between hosts. The major responsibility of this layer is data integrity--that data transmitted between hosts is reliable and timely. Upper layer data grams are broken down into network-sized data grams if needed and then implemented using appropriate transmission control. The transport layer creates one or more than one network connection, depending on conditions. This layer also handles what type of connection will be created. Two major transport protocols are the TCP (Transmission Control Protocol) and the UDP (User Data gram Protocol).
Important features of Transport layer:
- Transport layer ensures reliable service.
- Breaks the message (from sessions layer) into smaller packets, assigns sequence number and sends them.
- Reliable transport connections are built on top of X.25 or IP.
- In case IP, lost packets arriving out of order must be reordered.
Important features of TCP/UDP:
- TCP/IP Widely used for network/transport layer (UNIX).
- TCP (Transport Control Protocol): This is a connection oriented protocol.
- UDP (Universal Data gram Protocol): This is a connectionless transport layer protocol.
- Application programs that do not need connection-oriented protocol generally use UDP.
1.5 Network layer
Responsible for the routing of data (packets) through the network; handles the addressing and delivery of data. This layer provides for congestion control, accounting information for the network, routing, addressing, and several other functions. IP (Internet Protocol) is a good example of a network layer protocol. Network layer does not deal with lost messages.
Important features of Network layer protocols:
- Concerned with the transmission of packets.
- Choose the best path to send a packet (routing).
- The routing may be complex in a large network (e.g. Internet).
- Routing packets through a network may be accomplished by using simple static routes or by using complex dynamic routing algorithms.
1.6 Data link layer
Provides for the reliable delivery of data across a physical network. This layer deals with issues such as flow regulation, error detection and control, and frames. This layer has the important task of creating and managing what frames are sent out on the network. The network data frame, or packet, is made up of checksum, source address, destination address, and the data itself. The largest packet size that can be sent defines the maximum transmission Unit (MTU).
Important features of Data link layer:
- Handles errors in the physical layer.
- Groups bits into frames and ensures their correct delivery.
- Adds some bits at the beginning and end of each frame plus the checksum.
- Receiver verifies the checksum.
- If the checksum is not correct, it asks for retransmission. (Send a control message).
- Consists of two sub layers:
Logical Link Control (LLC) defines how data is transferred over the cable and provides data link service to the higher layers.
Medium Access Control (MAC) defines who can use the network when multiple computers are trying to access it simultaneously (i.e. Token passing, Ethernet [CSMA/CD]).
The data link layer provides reliable transit of data across a physical network link. Different data link layer specifications define different network and protocol characteristics, including physical addressing, network topology, error notification, sequencing of frames, and flow control. Physical addressing (as opposed to network addressing) defines how devices are addressed at the data link layer. Network topology consists of the data link layer specifications that often define how devices are to be physically connected, such as in a bus or a ring topology. Error notification alerts upper-layer protocols that a transmission error has occurred, and the sequencing of data frames reorders frames that are transmitted out of sequence. Finally, flow control moderates the transmission of data so that the receiving device is not overwhelmed with more traffic than it can handle at one time.
The protocols used in Data link layer are SLIP, PPP, MTU, and CSLP.
1.7 Physical layer
Handles the bit-level electrical/light communication across the network channel. The physical layer defines the electrical, mechanical, procedural, and functional specifications for activating, maintaining, and deactivating the physical link between communicating network systems. Physical layer specifications define characteristics such as media, voltage levels, timing of voltage changes, physical data rates, maximum transmission distances, and physical connectors.
Basically, this layer ensures that a bit sent on one side of the Network is received correctly on the other side.
Data travels from the application layer of the sender, down through the levels, across the nodes of the network service, and up through the levels of the receiver
To keep track of the transmission, each layer "wraps" the preceding layer's data and header with its own header. A small chunk of data will be transmitted with multiple layer headers attached to it. On the receiving end, each layer strips off the header that corresponds to its respective level.
Physical layer is concerned with the following:
- Physical interface characteristics like electrical, and mechanical specifications,
- Number of bits of second to be transmitted,
- Transmission type like duplex or half-duplex etc.
Frequently used Physical layer protocols:
Some of the important standards that deal with physical layer specifications are:
RS-232(for serial communication lines), X.21, EIA 232, and G730.
Physical layer and Data link layer implementations can be categorized as either LAN or WAN specifications.

- Privacy Policy
- Copyright © 2003-2024 TutorialsWeb.com
Presentation layer and Session layer of the OSI model
There are two popular networking models: the OSI layers model and the TCP/IP layers model. The presentation layer and session layer exist only in the OSI layers models. The TCP/IP layers model merges them into the application layer.
The Presentation Layer
The presentation layer is the sixth layer of the OSI Reference model. It defines how data and information is transmitted and presented to the user. It translates data and format code in such a way that it is correctly used by the application layer.
It identifies the syntaxes that different applications use and formats data using those syntaxes. For example, a web browser receives a web page from a web server in the HTML language. HTML language includes many tags and markup that have no meaning for the end user but they have special meaning for the web browser. the web browser uses the presentation layer's logic to read those syntaxes and format data in such a way the web server wants it to be present to the user.

On the sender device, it encapsulates and compresses data before sending it to the network to increase the speed and security of the network. On the receiver device, it de-encapsulates and decompresses data before presenting it to the user.
Examples of the presentation layer
Example standards for representing graphical information: JPEG, GIF, JPEG, and TIFF.
Example standards for representing audio information: WAV, MIDI, MP3.
Example standards for representing video information: WMV, MOV, MP4, MPEG.
Example standards for representing text information: doc, xls, txt, pdf.
Functions of the presentation layer
- It formats and presents data and information.
- It encrypts and compresses data before giving it to the session layer.
- It de-encrypts and decompresses the encrypted and compressed data it receives from the session layer.
Session layer
The session layer is the fifth layer of the OSI layers model. It is responsible for initiating, establishing, managing, and terminating sessions between the local application and the remote applications.
It defines standards for three modes of communication: full duplex, half-duplex, and simplex.

In the full duplex mode, both devices can send and receive data simultaneously. The internet connection is an example of the full duplex mode.
In the half duplex mode, only one device can send data at a time. A telephone conversation is an example of the half-duplex mode.
In the simplex mode, only one device can send data. A radio broadcast is an example of the simplex mode.
Functions of the session layer
- It is responsible for terminating sessions, creating checkpoints, and recovering data when sessions are interrupted.
- It opens and maintains logical communication channels between network applications running on the local host and network applications running on the remote host.
- If a network application uses an authentication mechanism before it opens a logical communication channel (session) with the remote host, it handles the authentication process.
Examples of the session layer
Structure Query Language (SQL), Remote Procedure Call (RPC), and Network File System (NFS) are examples of the session layer.
By ComputerNetworkingNotes Updated on 2024-05-05 05:30:01 IST
ComputerNetworkingNotes CCNA Study Guide Presentation layer and Session layer of the OSI model
We do not accept any kind of Guest Post. Except Guest post submission, for any other query (such as adverting opportunity, product advertisement, feedback, suggestion, error reporting and technical issue) or simply just say to hello mail us [email protected]

The OSI Model – The 7 Layers of Networking Explained in Plain English

This article explains the Open Systems Interconnection (OSI) model and the 7 layers of networking, in plain English.
The OSI model is a conceptual framework that is used to describe how a network functions. In plain English, the OSI model helped standardize the way computer systems send information to each other.
Learning networking is a bit like learning a language - there are lots of standards and then some exceptions. Therefore, it’s important to really understand that the OSI model is not a set of rules. It is a tool for understanding how networks function.
Once you learn the OSI model, you will be able to further understand and appreciate this glorious entity we call the Internet, as well as be able to troubleshoot networking issues with greater fluency and ease.
All hail the Internet!
Prerequisites
You don’t need any prior programming or networking experience to understand this article. However, you will need:
- Basic familiarity with common networking terms (explained below)
- A curiosity about how things work :)
Learning Objectives
Over the course of this article, you will learn:
- What the OSI model is
- The purpose of each of the 7 layers
- The problems that can happen at each of the 7 layers
- The difference between TCP/IP model and the OSI model
Common Networking Terms
Here are some common networking terms that you should be familiar with to get the most out of this article. I’ll use these terms when I talk about OSI layers next.
A node is a physical electronic device hooked up to a network, for example a computer, printer, router, and so on. If set up properly, a node is capable of sending and/or receiving information over a network.
Nodes may be set up adjacent to one other, wherein Node A can connect directly to Node B, or there may be an intermediate node, like a switch or a router, set up between Node A and Node B.
Typically, routers connect networks to the Internet and switches operate within a network to facilitate intra-network communication. Learn more about hub vs. switch vs. router.
Here's an example:
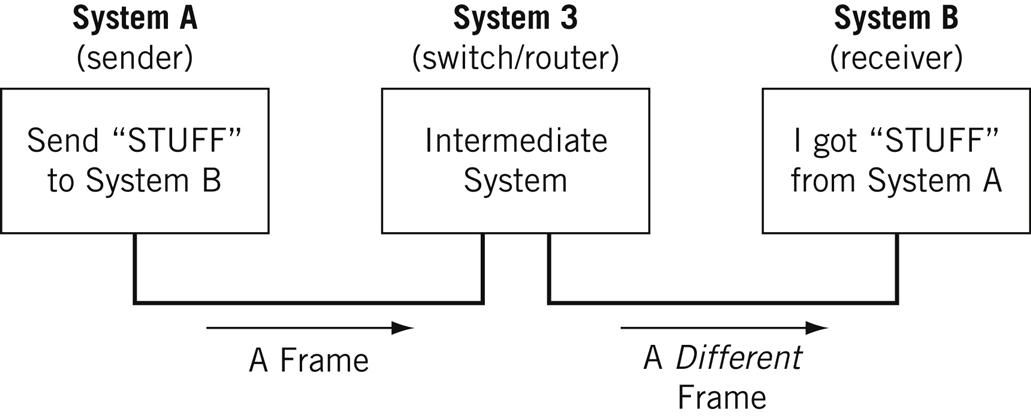
For the nitpicky among us (yep, I see you), host is another term that you will encounter in networking. I will define a host as a type of node that requires an IP address. All hosts are nodes, but not all nodes are hosts. Please Tweet angrily at me if you disagree.
Links connect nodes on a network. Links can be wired, like Ethernet, or cable-free, like WiFi.
Links to can either be point-to-point, where Node A is connected to Node B, or multipoint, where Node A is connected to Node B and Node C.
When we’re talking about information being transmitted, this may also be described as a one-to-one vs. a one-to-many relationship.
A protocol is a mutually agreed upon set of rules that allows two nodes on a network to exchange data.
“A protocol defines the rules governing the syntax (what can be communicated), semantics (how it can be communicated), and synchronization (when and at what speed it can be communicated) of the communications procedure. Protocols can be implemented on hardware, software, or a combination of both. Protocols can be created by anyone, but the most widely adopted protocols are based on standards.” - The Illustrated Network.
Both wired and cable-free links can have protocols.
While anyone can create a protocol, the most widely adopted protocols are often based on standards published by Internet organizations such as the Internet Engineering Task Force (IETF).
A network is a general term for a group of computers, printers, or any other device that wants to share data.
Network types include LAN, HAN, CAN, MAN, WAN, BAN, or VPN. Think I’m just randomly rhyming things with the word can ? I can ’t say I am - these are all real network types. Learn more here .
Topology describes how nodes and links fit together in a network configuration, often depicted in a diagram. Here are some common network topology types:
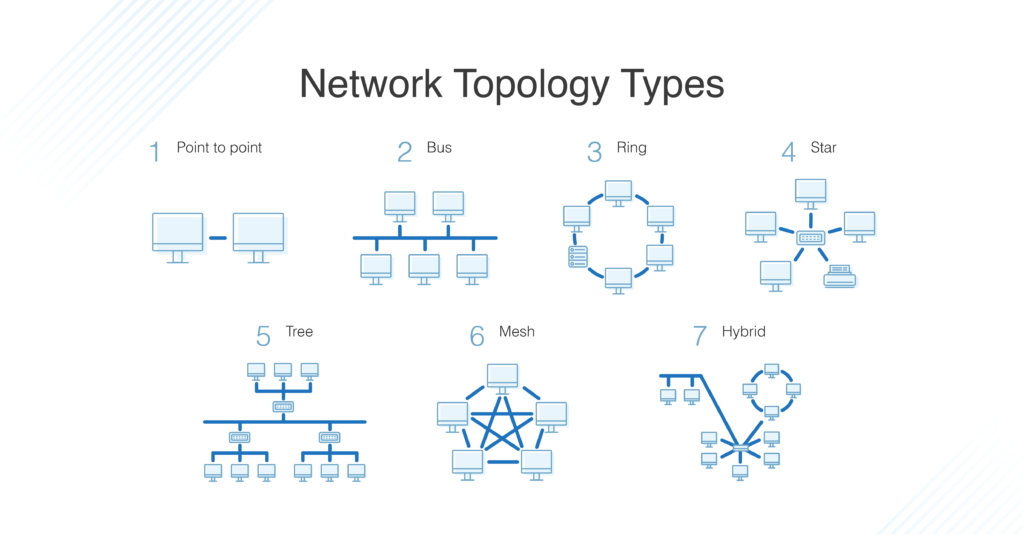
A network consists of nodes, links between nodes, and protocols that govern data transmission between nodes.
At whatever scale and complexity networks get to, you will understand what’s happening in all computer networks by learning the OSI model and 7 layers of networking.
What is the OSI Model?
The OSI model consists of 7 layers of networking.
First, what’s a layer?

No, a layer - not a lair . Here there are no dragons.
A layer is a way of categorizing and grouping functionality and behavior on and of a network.
In the OSI model, layers are organized from the most tangible and most physical, to less tangible and less physical but closer to the end user.
Each layer abstracts lower level functionality away until by the time you get to the highest layer. All the details and inner workings of all the other layers are hidden from the end user.
How to remember all the names of the layers? Easy.
- Please | Physical Layer
- Do | Data Link Layer
- Not | Network Layer
- Tell (the) | Transport Layer
- Secret | Session Layer
- Password (to) | Presentation Layer
- Anyone | Application Layer
Keep in mind that while certain technologies, like protocols, may logically “belong to” one layer more than another, not all technologies fit neatly into a single layer in the OSI model. For example, Ethernet, 802.11 (Wifi) and the Address Resolution Protocol (ARP) procedure operate on >1 layer.
The OSI is a model and a tool, not a set of rules.
OSI Layer 1
Layer 1 is the physical layer . There’s a lot of technology in Layer 1 - everything from physical network devices, cabling, to how the cables hook up to the devices. Plus if we don’t need cables, what the signal type and transmission methods are (for example, wireless broadband).
Instead of listing every type of technology in Layer 1, I’ve created broader categories for these technologies. I encourage readers to learn more about each of these categories:
- Nodes (devices) and networking hardware components. Devices include hubs, repeaters, routers, computers, printers, and so on. Hardware components that live inside of these devices include antennas, amplifiers, Network Interface Cards (NICs), and more.
- Device interface mechanics. How and where does a cable connect to a device (cable connector and device socket)? What is the size and shape of the connector, and how many pins does it have? What dictates when a pin is active or inactive?
- Functional and procedural logic. What is the function of each pin in the connector - send or receive? What procedural logic dictates the sequence of events so a node can start to communicate with another node on Layer 2?
- Cabling protocols and specifications. Ethernet (CAT), USB, Digital Subscriber Line (DSL) , and more. Specifications include maximum cable length, modulation techniques, radio specifications, line coding, and bits synchronization (more on that below).
- Cable types. Options include shielded or unshielded twisted pair, untwisted pair, coaxial and so on. Learn more about cable types here .
- Signal type. Baseband is a single bit stream at a time, like a railway track - one-way only. Broadband consists of multiple bit streams at the same time, like a bi-directional highway.
- Signal transmission method (may be wired or cable-free). Options include electrical (Ethernet), light (optical networks, fiber optics), radio waves (802.11 WiFi, a/b/g/n/ac/ax variants or Bluetooth). If cable-free, then also consider frequency: 2.5 GHz vs. 5 GHz. If it’s cabled, consider voltage. If cabled and Ethernet, also consider networking standards like 100BASE-T and related standards.
The data unit on Layer 1 is the bit.
A bit the smallest unit of transmittable digital information. Bits are binary, so either a 0 or a 1. Bytes, consisting of 8 bits, are used to represent single characters, like a letter, numeral, or symbol.
Bits are sent to and from hardware devices in accordance with the supported data rate (transmission rate, in number of bits per second or millisecond) and are synchronized so the number of bits sent and received per unit of time remains consistent (this is called bit synchronization). The way bits are transmitted depends on the signal transmission method.
Nodes can send, receive, or send and receive bits. If they can only do one, then the node uses a simplex mode. If they can do both, then the node uses a duplex mode. If a node can send and receive at the same time, it’s full-duplex – if not, it’s just half-duplex.
The original Ethernet was half-duplex. Full-duplex Ethernet is an option now, given the right equipment.
How to Troubleshoot OSI Layer 1 Problems
Here are some Layer 1 problems to watch out for:
- Defunct cables, for example damaged wires or broken connectors
- Broken hardware network devices, for example damaged circuits
- Stuff being unplugged (...we’ve all been there)
If there are issues in Layer 1, anything beyond Layer 1 will not function properly.
Layer 1 contains the infrastructure that makes communication on networks possible.
It defines the electrical, mechanical, procedural, and functional specifications for activating, maintaining, and deactivating physical links between network devices. - Source
Fun fact: deep-sea communications cables transmit data around the world. This map will blow your mind: https://www.submarinecablemap.com/
And because you made it this far, here’s a koala:

OSI Layer 2
Layer 2 is the data link layer . Layer 2 defines how data is formatted for transmission, how much data can flow between nodes, for how long, and what to do when errors are detected in this flow.
In more official tech terms:
- Line discipline. Who should talk for how long? How long should nodes be able to transit information for?
- Flow control. How much data should be transmitted?
- Error control - detection and correction . All data transmission methods have potential for errors, from electrical spikes to dirty connectors. Once Layer 2 technologies tell network administrators about an issue on Layer 2 or Layer 1, the system administrator can correct for those errors on subsequent layers. Layer 2 is mostly concerned with error detection, not error correction. ( Source )
There are two distinct sublayers within Layer 2:
- Media Access Control (MAC): the MAC sublayer handles the assignment of a hardware identification number, called a MAC address, that uniquely identifies each device on a network. No two devices should have the same MAC address. The MAC address is assigned at the point of manufacturing. It is automatically recognized by most networks. MAC addresses live on Network Interface Cards (NICs). Switches keep track of all MAC addresses on a network. Learn more about MAC addresses on PC Mag and in this article . Learn more about network switches here .
- Logical Link Control (LLC): the LLC sublayer handles framing addressing and flow control. The speed depends on the link between nodes, for example Ethernet or Wifi.
The data unit on Layer 2 is a frame .
Each frame contains a frame header, body, and a frame trailer:
- Header: typically includes MAC addresses for the source and destination nodes.
- Body: consists of the bits being transmitted.
- Trailer: includes error detection information. When errors are detected, and depending on the implementation or configuration of a network or protocol, frames may be discarded or the error may be reported up to higher layers for further error correction. Examples of error detection mechanisms: Cyclic Redundancy Check (CRC) and Frame Check Sequence (FCS). Learn more about error detection techniques here .
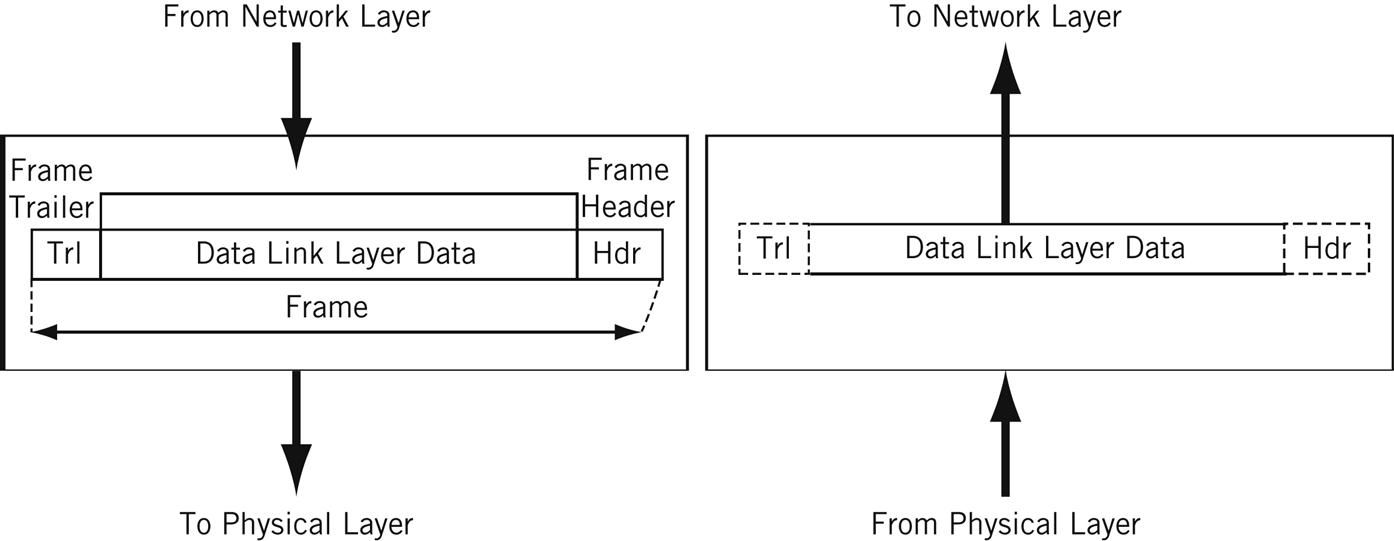
Typically there is a maximum frame size limit, called an Maximum Transmission Unit, MTU. Jumbo frames exceed the standard MTU, learn more about jumbo frames here .
How to Troubleshoot OSI Layer 2 Problems
Here are some Layer 2 problems to watch out for:
- All the problems that can occur on Layer 1
- Unsuccessful connections (sessions) between two nodes
- Sessions that are successfully established but intermittently fail
- Frame collisions
The Data Link Layer allows nodes to communicate with each other within a local area network. The foundations of line discipline, flow control, and error control are established in this layer.
OSI Layer 3
Layer 3 is the network layer . This is where we send information between and across networks through the use of routers. Instead of just node-to-node communication, we can now do network-to-network communication.
Routers are the workhorse of Layer 3 - we couldn’t have Layer 3 without them. They move data packets across multiple networks.
Not only do they connect to Internet Service Providers (ISPs) to provide access to the Internet, they also keep track of what’s on its network (remember that switches keep track of all MAC addresses on a network), what other networks it’s connected to, and the different paths for routing data packets across these networks.
Routers store all of this addressing and routing information in routing tables.
Here’s a simple example of a routing table:
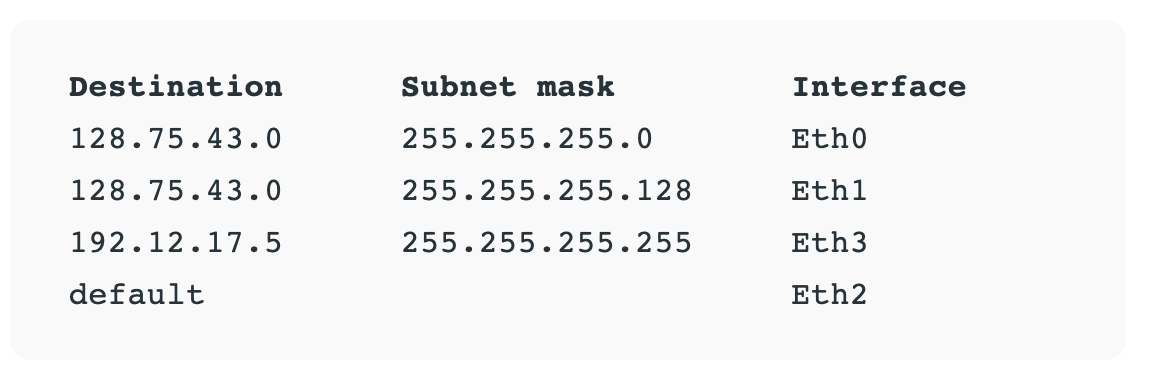
The data unit on Layer 3 is the data packet . Typically, each data packet contains a frame plus an IP address information wrapper. In other words, frames are encapsulated by Layer 3 addressing information.
The data being transmitted in a packet is also sometimes called the payload . While each packet has everything it needs to get to its destination, whether or not it makes it there is another story.
Layer 3 transmissions are connectionless, or best effort - they don't do anything but send the traffic where it’s supposed to go. More on data transport protocols on Layer 4.
Once a node is connected to the Internet, it is assigned an Internet Protocol (IP) address, which looks either like 172.16. 254.1 (IPv4 address convention) or like 2001:0db8:85a3:0000:0000:8a2e:0370:7334 (IPv6 address convention). Routers use IP addresses in their routing tables.
IP addresses are associated with the physical node’s MAC address via the Address Resolution Protocol (ARP), which resolves MAC addresses with the node’s corresponding IP address.
ARP is conventionally considered part of Layer 2, but since IP addresses don’t exist until Layer 3, it’s also part of Layer 3.
How to Troubleshoot OSI Layer 3 Problems
Here are some Layer 3 problems to watch out for:
- All the problems that can crop up on previous layers :)
- Faulty or non-functional router or other node
- IP address is incorrectly configured
Many answers to Layer 3 questions will require the use of command-line tools like ping , trace , show ip route , or show ip protocols . Learn more about troubleshooting on layer 1-3 here .
The Network Layer allows nodes to connect to the Internet and send information across different networks.
OSI Layer 4
Layer 4 is the transport layer . This where we dive into the nitty gritty specifics of the connection between two nodes and how information is transmitted between them. It builds on the functions of Layer 2 - line discipline, flow control, and error control.
This layer is also responsible for data packet segmentation, or how data packets are broken up and sent over the network.
Unlike the previous layer, Layer 4 also has an understanding of the whole message, not just the contents of each individual data packet. With this understanding, Layer 4 is able to manage network congestion by not sending all the packets at once.
The data units of Layer 4 go by a few names. For TCP, the data unit is a packet. For UDP, a packet is referred to as a datagram. I’ll just use the term data packet here for the sake of simplicity.
Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are two of the most well-known protocols in Layer 4.
TCP, a connection-oriented protocol, prioritizes data quality over speed.
TCP explicitly establishes a connection with the destination node and requires a handshake between the source and destination nodes when data is transmitted. The handshake confirms that data was received. If the destination node does not receive all of the data, TCP will ask for a retry.
TCP also ensures that packets are delivered or reassembled in the correct order. Learn more about TCP here .
UDP, a connectionless protocol, prioritizes speed over data quality. UDP does not require a handshake, which is why it’s called connectionless.
Because UDP doesn’t have to wait for this acknowledgement, it can send data at a faster rate, but not all of the data may be successfully transmitted and we’d never know.
If information is split up into multiple datagrams, unless those datagrams contain a sequence number, UDP does not ensure that packets are reassembled in the correct order. Learn more about UDP here .
TCP and UDP both send data to specific ports on a network device, which has an IP address. The combination of the IP address and the port number is called a socket.
Learn more about sockets here .
Learn more about the differences and similarities between these two protocols here .
How to Troubleshoot OSI Layer 4 Problems
Here are some Layer 4 problems to watch out for:
- Blocked ports - check your Access Control Lists (ACL) & firewalls
- Quality of Service (QoS) settings. QoS is a feature of routers/switches that can prioritize traffic, and they can really muck things up. Learn more about QoS here .
The Transport Layer provides end-to-end transmission of a message by segmenting a message into multiple data packets; the layer supports connection-oriented and connectionless communication.
OSI Layer 5
Layer 5 is the session layer . This layer establishes, maintains, and terminates sessions.
A session is a mutually agreed upon connection that is established between two network applications. Not two nodes! Nope, we’ve moved on from nodes. They were so Layer 4.
Just kidding, we still have nodes, but Layer 5 doesn’t need to retain the concept of a node because that’s been abstracted out (taken care of) by previous layers.
So a session is a connection that is established between two specific end-user applications. There are two important concepts to consider here:
- Client and server model: the application requesting the information is called the client, and the application that has the requested information is called the server.
- Request and response model: while a session is being established and during a session, there is a constant back-and-forth of requests for information and responses containing that information or “hey, I don’t have what you’re requesting.”
Sessions may be open for a very short amount of time or a long amount of time. They may fail sometimes, too.
Depending on the protocol in question, various failure resolution processes may kick in. Depending on the applications/protocols/hardware in use, sessions may support simplex, half-duplex, or full-duplex modes.
Examples of protocols on Layer 5 include Network Basic Input Output System (NetBIOS) and Remote Procedure Call Protocol (RPC), and many others.
From here on out (layer 5 and up), networks are focused on ways of making connections to end-user applications and displaying data to the user.
How to Troubleshoot OSI Layer 5 Problems
Here are some Layer 5 problems to watch out for:
- Servers are unavailable
- Servers are incorrectly configured, for example Apache or PHP configs
- Session failure - disconnect, timeout, and so on.
The Session Layer initiates, maintains, and terminates connections between two end-user applications. It responds to requests from the presentation layer and issues requests to the transport layer.
OSI Layer 6
Layer 6 is the presentation layer . This layer is responsible for data formatting, such as character encoding and conversions, and data encryption.
The operating system that hosts the end-user application is typically involved in Layer 6 processes. This functionality is not always implemented in a network protocol.
Layer 6 makes sure that end-user applications operating on Layer 7 can successfully consume data and, of course, eventually display it.
There are three data formatting methods to be aware of:
- American Standard Code for Information Interchange (ASCII): this 7-bit encoding technique is the most widely used standard for character encoding. One superset is ISO-8859-1, which provides most of the characters necessary for languages spoken in Western Europe.
- Extended Binary-Coded Decimal Interchange Code (EBDCIC): designed by IBM for mainframe usage. This encoding is incompatible with other character encoding methods.
- Unicode: character encodings can be done with 32-, 16-, or 8-bit characters and attempts to accommodate every known, written alphabet.
Learn more about character encoding methods in this article , and also here .
Encryption: SSL or TLS encryption protocols live on Layer 6. These encryption protocols help ensure that transmitted data is less vulnerable to malicious actors by providing authentication and data encryption for nodes operating on a network. TLS is the successor to SSL.
How to Troubleshoot OSI Layer 6 Problems
Here are some Layer 6 problems to watch out for:
- Non-existent or corrupted drivers
- Incorrect OS user access level
The Presentation Layer formats and encrypts data.
OSI Layer 7
Layer 7 is the application layer .
True to its name, this is the layer that is ultimately responsible for supporting services used by end-user applications. Applications include software programs that are installed on the operating system, like Internet browsers (for example, Firefox) or word processing programs (for example, Microsoft Word).
Applications can perform specialized network functions under the hood and require specialized services that fall under the umbrella of Layer 7.
Electronic mail programs, for example, are specifically created to run over a network and utilize networking functionality, such as email protocols, which fall under Layer 7.
Applications will also control end-user interaction, such as security checks (for example, MFA), identification of two participants, initiation of an exchange of information, and so on.
Protocols that operate on this level include File Transfer Protocol (FTP), Secure Shell (SSH), Simple Mail Transfer Protocol (SMTP), Internet Message Access Protocol (IMAP), Domain Name Service (DNS), and Hypertext Transfer Protocol (HTTP).
While each of these protocols serve different functions and operate differently, on a high level they all facilitate the communication of information. ( Source )
How to Troubleshoot OSI Layer 7 Problems
Here are some Layer 7 problems to watch out for:
- All issues on previous layers
- Incorrectly configured software applications
- User error (... we’ve all been there)
The Application Layer owns the services and functions that end-user applications need to work. It does not include the applications themselves.
Our Layer 1 koala is all grown up.

Learning check - can you apply makeup to a koala?
Don’t have a koala?
Well - answer these questions instead. It’s the next best thing, I promise.
- What is the OSI model?
- What are each of the layers?
- How could I use this information to troubleshoot networking issues?
Congratulations - you’ve taken one step farther to understanding the glorious entity we call the Internet.
Learning Resources
Many, very smart people have written entire books about the OSI model or entire books about specific layers. I encourage readers to check out any O’Reilly-published books about the subject or about network engineering in general.
Here are some resources I used when writing this article:
- The Illustrated Network, 2nd Edition
- Protocol Data Unit (PDU): https://www.geeksforgeeks.org/difference-between-segments-packets-and-frames/
- Troubleshooting Along the OSI Model: https://www.pearsonitcertification.com/articles/article.aspx?p=1730891
- The OSI Model Demystified: https://www.youtube.com/watch?v=HEEnLZV2wGI
- OSI Model for Dummies: https://www.dummies.com/programming/networking/layers-in-the-osi-model-of-a-computer-network/
Chloe Tucker is an artist and computer science enthusiast based in Portland, Oregon. As a former educator, she's continuously searching for the intersection of learning and teaching, or technology and art. Reach out to her on Twitter @_chloetucker and check out her website at chloe.dev .
Read more posts .
If you read this far, thank the author to show them you care. Say Thanks
Learn to code for free. freeCodeCamp's open source curriculum has helped more than 40,000 people get jobs as developers. Get started
Home > Learning Center > OSI Model
Article's content

Need help protecting your applications?
See how imperva can help, what is the osi model.
The Open Systems Interconnection (OSI) model describes seven layers that computer systems use to communicate over a network. It was the first standard model for network communications, adopted by all major computer and telecommunication companies in the early 1980s
The modern Internet is not based on OSI, but on the simpler TCP/IP model. However, the OSI 7-layer model is still widely used, as it helps visualize and communicate how networks operate, and helps isolate and troubleshoot networking problems.
OSI was introduced in 1983 by representatives of the major computer and telecom companies, and was adopted by ISO as an international standard in 1984.
OSI Model Explained: The OSI 7 Layers
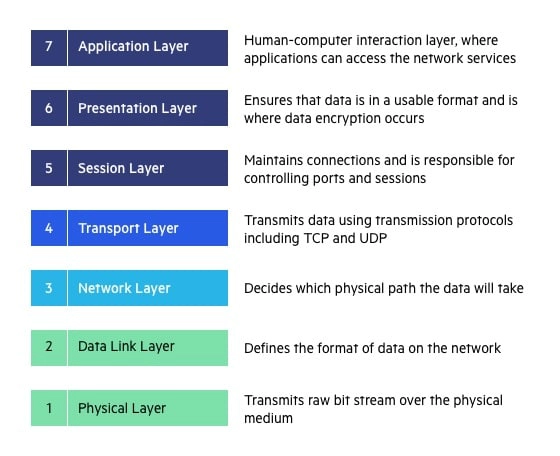
We’ll describe OSI layers “top down” from the application layer that directly serves the end user, down to the physical layer.
7. Application Layer
The application layer is used by end-user software such as web browsers and email clients. It provides protocols that allow software to send and receive information and present meaningful data to users. A few examples of application layer protocols are the Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP), Post Office Protocol (POP), Simple Mail Transfer Protocol (SMTP), and Domain Name System (DNS).
6. Presentation Layer
The presentation layer prepares data for the application layer. It defines how two devices should encode, encrypt, and compress data so it is received correctly on the other end. The presentation layer takes any data transmitted by the application layer and prepares it for transmission over the session layer.
5. Session Layer
The session layer creates communication channels, called sessions, between devices. It is responsible for opening sessions, ensuring they remain open and functional while data is being transferred, and closing them when communication ends. The session layer can also set checkpoints during a data transfer—if the session is interrupted, devices can resume data transfer from the last checkpoint.
4. Transport Layer
The transport layer takes data transferred in the session layer and breaks it into “segments” on the transmitting end. It is responsible for reassembling the segments on the receiving end, turning it back into data that can be used by the session layer. The transport layer carries out flow control, sending data at a rate that matches the connection speed of the receiving device, and error control, checking if data was received incorrectly and if not, requesting it again.
3. Network Layer
The network layer has two main functions. One is breaking up segments into network packets, and reassembling the packets on the receiving end. The other is routing packets by discovering the best path across a physical network. The network layer uses network addresses (typically Internet Protocol addresses) to route packets to a destination node.
2. Data Link Layer
The data link layer establishes and terminates a connection between two physically-connected nodes on a network. It breaks up packets into frames and sends them from source to destination. This layer is composed of two parts—Logical Link Control (LLC), which identifies network protocols, performs error checking and synchronizes frames, and Media Access Control (MAC) which uses MAC addresses to connect devices and define permissions to transmit and receive data.
1. Physical Layer
The physical layer is responsible for the physical cable or wireless connection between network nodes. It defines the connector, the electrical cable or wireless technology connecting the devices, and is responsible for transmission of the raw data, which is simply a series of 0s and 1s, while taking care of bit rate control.
Advantages of OSI Model
The OSI model helps users and operators of computer networks:
- Determine the required hardware and software to build their network.
- Understand and communicate the process followed by components communicating across a network.
- Perform troubleshooting, by identifying which network layer is causing an issue and focusing efforts on that layer.
The OSI model helps network device manufacturers and networking software vendors:
- Create devices and software that can communicate with products from any other vendor, allowing open interoperability
- Define which parts of the network their products should work with.
- Communicate to users at which network layers their product operates – for example, only at the application layer, or across the stack.
Battling Bad Bots: The Latest Trends, Stats & Defense Strategies
Register Now
OSI vs. TCP/IP Model
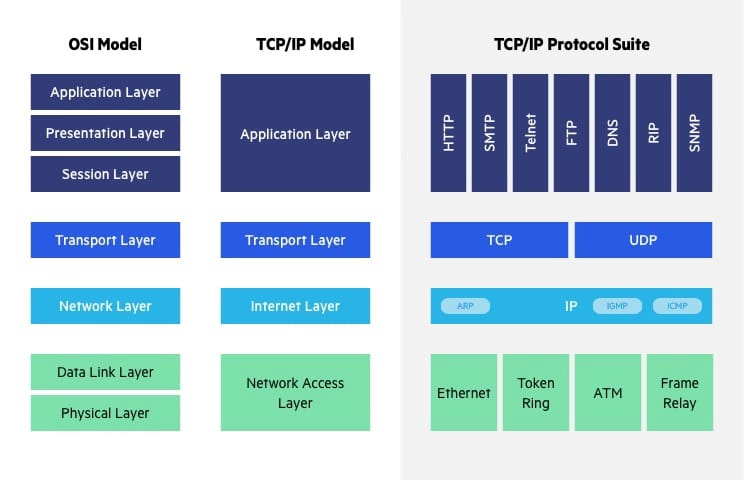
The Transfer Control Protocol/Internet Protocol (TCP/IP) is older than the OSI model and was created by the US Department of Defense (DoD). A key difference between the models is that TCP/IP is simpler, collapsing several OSI layers into one:
- OSI layers 5, 6, 7 are combined into one Application Layer in TCP/IP
- OSI layers 1, 2 are combined into one Network Access Layer in TCP/IP – however TCP/IP does not take responsibility for sequencing and acknowledgement functions, leaving these to the underlying transport layer.
Other important differences:
- TCP/IP is a functional model designed to solve specific communication problems, and which is based on specific, standard protocols. OSI is a generic, protocol-independent model intended to describe all forms of network communication.
- In TCP/IP, most applications use all the layers, while in OSI simple applications do not use all seven layers. Only layers 1, 2 and 3 are mandatory to enable any data communication.
See how Imperva Web Application Firewall can help you with application security.
Imperva Application Security
Imperva security solutions secure your applications across multiple layers of the OSI model, from the network layer, protected by Imperva DDoS mitigation, to Imperva’s web application firewall (WAF), bot management and API security technology that safeguards the application layer.
To secure applications and networks across the OSI stack, Imperva provides multi-layered protection to make sure websites and applications are available, easily accessible and safe. The Imperva applicati on security solution includes:
- DDoS Protection —maintain uptime in all situations. Prevent any type of DDoS attack, of any size, from preventing access to your website and network infrastructure.
- CDN —enhance website performance and reduce bandwidth costs with a CDN designed for developers. Cache static resources at the edge while accelerating APIs and dynamic websites.
- WAF —cloud-based solution permits legitimate traffic and prevents bad traffic, safeguarding applications at the edge. Gateway WAF keeps applications and APIs inside your network safe.
- Bot protection —analyzes your bot traffic to pinpoint anomalies, identifies bad bot behavior and validates it via challenge mechanisms that do not impact user traffic.
- API security —protects APIs by ensuring only desired traffic can access your API endpoint, as well as detecting and blocking exploits of vulnerabilities.
- Account takeover protection —uses an intent-based detection process to identify and defends against attempts to take over users’ accounts for malicious purposes.
- RASP —keep your applications safe from within against known and zero‑day attacks. Fast and accurate protection with no signature or learning mode.
- Attack analytics —mitigate and respond to real cyber security threats efficiently and accurately with actionable intelligence across all your layers of defense.
Latest Blogs

Feb 19, 2024 6 min read

Dec 14, 2023 5 min read

Daniel Johnston
Dec 14, 2023 3 min read
Latest Articles
- Cybersecurity 101
118.8k Views
116.7k Views
113.4k Views
97.4k Views
57.8k Views
56.8k Views
2024 Bad Bot Report
Bad bots now represent almost one-third of all internet traffic
The State of API Security in 2024
Learn about the current API threat landscape and the key security insights for 2024
Protect Against Business Logic Abuse
Identify key capabilities to prevent attacks targeting your business logic
The State of Security Within eCommerce in 2022
Learn how automated threats and API attacks on retailers are increasing
Prevoty is now part of the Imperva Runtime Protection
Protection against zero-day attacks
No tuning, highly-accurate out-of-the-box
Effective against OWASP top 10 vulnerabilities
An Imperva security specialist will contact you shortly.
Top 3 US Retailer
- Artificial Intelligence
- Generative AI
- Cloud Computing
- CPUs and Processors
- Data Center
- Edge Computing
- Enterprise Storage
- Virtualization
- Internet of Things
- Network Management Software
- Network Security
- Enterprise Buyer’s Guides
- United States
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Copyright Notice
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld

The OSI model explained and how to easily remember its 7 layers
A tutorial on the open systems interconnection networking reference model and tips on and how to memorize the seven layers.

The Open Systems Interconnect (OSI) model is a conceptual framework that describes networking or telecommunications systems as seven layers, each with its own function.
The layers help network pros visualize what is going on within their networks and can help network managers narrow down problems (is it a physical issue or something with the application?), as well as computer programmers (when developing an application, which other layers does it need to work with?). Tech vendors selling new products will often refer to the OSI model to help customers understand which layer their products work with or whether it works “across the stack”.
The 7 layers of the OSI model
The layers are: Layer 1—Physical; Layer 2—Data Link; Layer 3—Network; Layer 4—Transport; Layer 5—Session; Layer 6—Presentation; Layer 7—Application.
It wasn’t always this way. Conceived in the 1970s when computer networking was taking off, two separate models were merged in 1983 and published in 1984 to create the OSI model that most people are familiar with today. Most descriptions of the OSI model go from top to bottom, with the numbers going from Layer 7 down to Layer 1. The layers, and what they represent, are as follows:
Layer 7 – Application
The Application Layer in the OSI model is the layer that is the “closest to the end user”. It receives information directly from users and displays incoming data to the user. Oddly enough, applications themselves do not reside at the application layer. Instead the layer facilitates communication through lower layers in order to establish connections with applications at the other end. Web browsers (Google Chrome, Firefox, Safari, etc.) TelNet, and FTP, are examples of communications that rely on Layer 7.
Layer 6 – Presentation
The Presentation Layer represents the area that is independent of data representation at the application layer. In general, it represents the preparation or translation of application format to network format, or from network formatting to application format. In other words, the layer “presents” data for the application or the network. A good example of this is encryption and decryption of data for secure transmission; this happens at Layer 6.
Layer 5 – Session
When two computers or other networked devices need to speak with one another, a session needs to be created, and this is done at the Session Layer . Functions at this layer involve setup, coordination (how long should a system wait for a response, for example) and termination between the applications at each end of the session.
Layer 4 – Transport
The Transport Layer deals with the coordination of the data transfer between end systems and hosts. How much data to send, at what rate, where it goes, etc. The best known example of the Transport Layer is the Transmission Control Protocol (TCP), which is built on top of the Internet Protocol (IP), commonly known as TCP/IP. TCP and UDP port numbers work at Layer 4, while IP addresses work at Layer 3, the Network Layer.
Layer 3 – Network
Here at the Network Layer is where you’ll find most of the router functionality that most networking professionals care about and love. In its most basic sense, this layer is responsible for packet forwarding, including routing through different routers . You might know that your Boston computer wants to connect to a server in California, but there are millions of different paths to take. Routers at this layer help do this efficiently.
Layer 2 – Data Link
The Data Link Layer provides node-to-node data transfer (between two directly connected nodes), and also handles error correction from the physical layer. Two sublayers exist here as well–the Media Access Control (MAC) layer and the Logical Link Control (LLC) layer. In the networking world, most switches operate at Layer 2. But it’s not that simple. Some switches also operate at Layer 3 in order to support virtual LANs that may span more than one switch subnet, which requires routing capabilities.
Layer 1 – Physical
At the bottom of our OSI model we have the Physical Layer, which represents the electrical and physical representation of the system. This can include everything from the cable type, radio frequency link (as in a Wi-Fi network), as well as the layout of pins, voltages, and other physical requirements. When a networking problem occurs, many networking pros go right to the physical layer to check that all of the cables are properly connected and that the power plug hasn’t been pulled from the router, switch or computer, for example.
Why you need to know the 7 OSI layers
Most people in IT will likely need to know about the different layers when they’re going for their certifications, much like a civics student needs to learn about the three branches of the US government. After that, you hear about the OSI model when vendors are making pitches about which layers their products work with.
In a Quora post asking about the purpose of the OSI model, Vikram Kumar answered this way:
“The purpose of the OSI reference model is to guide vendors and developers so the digital communication products and software programs they create will interoperate, and to facilitate clear comparisons among communications tools.”
While some people may argue that the OSI model is obsolete (due to its conceptual nature) and less important than the four layers of the TCP/IP model, Kumar says that “it is difficult to read about networking technology today without seeing references to the OSI model and its layers, because the model’s structure helps to frame discussions of protocols and contrast various technologies.”
If you can understand the OSI model and its layers, you can also then understand which protocols and devices can interoperate with each other when new technologies are developed and explained.
The OSI model remains relevant
In a post on GeeksforGeeks, contributor Vabhav Bilotia argues several reasons why the OSI model remains relevant, especially when it comes to security and determining where technical risks and vulnerabilities may exist.
For example, by understanding the different layers, enterprise security teams can identify and classify physical access, where the data is sitting, and provide an inventory of the applications that employees use to access data and resources.
“Knowing where the majority of your company’s data is held, whether on-premises or in cloud services, will help define your information security policy,” writes Bilotia. “You can invest in the correct solutions that provide you data visibility within the proper OSI layers once you have this knowledge.”
In addition, the OSI model can be used to understand cloud infrastructure migrations, particularly when it comes to securing data within the cloud.
And because the model has been around for so long and understood by so many, the uniform vocabulary and terms helps networking professionals understand quickly about the components of the networking system “While this paradigm is not directly implemented in today’s TCP/IP networks, it is a useful conceptual model for relating multiple technologies to one another and implementing the appropriate technology in the appropriate way,” Bilotia writes. We couldn’t agree more.
How to remember the OSI Model 7 layers – 8 mnemonic tricks
If you need to memorize the layers for a college or certification test, here are a few sentences to help remember them in order. The first letter of each word is the same as the first letter an OSI layer.
From Application to Physical (Layer 7 to Layer 1):
- All People Seem To Need Data Processing
- All Pros Search Top Notch Donut Places
- A Penguin Said That Nobody Drinks Pepsi
- A Priest Saw Two Nuns Doing Pushups
From Physical to Application (Layer 1 to Layer 7):
- Please Do Not Throw Sausage Pizza Away
- Pew! Dead Ninja Turtles Smell Particularly Awful
- People Don’t Need To See Paula Abdul
- Pete Doesn’t Need To Sell Pickles Anymore
Keith Shaw was a Network World editor and the writer of the Cool Tools column. He is now a freelance writer and editor from Worcester, Mass.
Related content
Kyndryl bolsters its bridge infrastructure services, compressing files using the zip command on linux, high-bandwidth memory nearly sold out until 2026, nsa, fbi warn of email spoofing threat, newsletter promo module test.

The first gadget Keith Shaw ever wanted was the Merlin, a red plastic toy that beeped and played Tic-Tac-Toe and various other games. A child of the '70s and teenager of the '80s, Shaw has been a fan of computers, technology and video games right from the start. He won an award in 8th grade for programming a game on the school's only computer, and saved his allowance to buy an Atari 2600.
Shaw has a bachelor's degree in newspaper journalism from Syracuse University and has worked at a variety of newspapers in New York, Florida and Massachusetts, as well as Computerworld and Network World. He won an award from the American Society of Business Publication Editors for a 2003 article on anti-spam testing, and a Gold Award in their 2010 Digital Awards Competition for the "ABCs of IT" video series.
Shaw is also the co-creator of taquitos.net , the crunchiest site on the InterWeb, which has taste-tested and reviewed more than 4,000 varieties of snack foods.
More from this author
What is a virtual machine, and why are they so useful, what is a network switch and how does it work, what is zero trust network access, what is sd-wan, and what does it mean for networking, security, cloud, most popular authors.

- Elizabeth Montalbano
Show me more
Download our sase and sse enterprise buyer’s guide.

Frontier retains top spot among world's fastest supercomputers

Nvidia teases quantum accelerated supercomputers

Has the hype around ‘Internet of Things’ paid off? | Ep. 145

Episode 1: Understanding Cisco’s Converged SDN Transport

Episode 2: Pluggable Optics and the Internet for the Future

Has the hype around ‘Internet of Things’ paid off?

Are unused IPv4 addresses a secret gold mine?


Preparing for a 6G wireless world: Exciting changes coming to the wireless industry

The OSI Model: What It Is and Why It’s Important
01-26-22 Flash Gooden
What are the seven layers of the OSI model? Let’s demystify the application, presentation, session, transport, network, data link, and physical layers to better understand how we digitally communicate with one another.
I spent a great portion of my career in telecommunications. While I was there, I worked on an assortment of jobs that helped me to connect thousands of people to the internet from the physical side: installing modems, running fiber optics to commercial and residential areas, and even placing utility poles into the ground and attaching connections on them to light up the city with the internet. My career also allowed me to work on cloud farms setting up servers, databases, and network racks.
Before I got into web development as a career at Sparkbox, I always wondered how all of the hardware components I worked with properly transferred all that data through so many conduits. I wrote this article to demystify some of the architecture that allows us to communicate with one another using devices, like our phones, computers, smart home devices...or anything that uses the internet.
Transferring data over Wi-Fi or cabling is no easy task…but it’s not magic either. The ability to communicate with one another in a matter of seconds is a luxury that we may sometimes take for granted. During my journey to understand network communication better, I stumbled across different resources about how computer systems communicate, mainly the TCP/IP Model and the Open Systems Interconnection (OSI) Model. Learning about these models helped me to become more knowledgeable in how computer systems transform code to light and vice versa. The model that first caught my interest was the OSI Model, which is the format that I will focus on here.
What Is the OSI Model?
Let me preface this breakdown by saying that the OSI model is not the standard in how our networks communicate today, but it did serve as a framework to get to the more widely adopted TCP/IP model . The OSI model is simply an idea about how our computer network systems can communicate. It has become one of the pioneering concepts for how we communicate through multiple layers of network transmission by using necessary components, from physical computer parts to fully built applications. This network communication process involves seven layers:

By using layers, we can separate the responsibilities of the network communication process, which makes things easier to troubleshoot. Learning each layer’s responsibility helps us understand how our data is managed and transformed.
The Application Layer: What It Is and Why It’s Important
The application layer is where applications can initially make network requests to send down the pipeline. This is usually where users can send messages, request web pages, or download music by interacting with our devices. These interactions become messages that typically travel through the code that we write, destined to become signals that will shoot light beams to any distance.
This layer is important because it focuses on how our network requests choose initial communication protocols. These protocols will give specific information about how we want our network request to be sent. One of the most popular protocols is HTTP, which is used by Google Chrome, Safari, and Firefox to send and receive information displayed on web pages. Communication from this protocol is sent to or received from the presentation layer.
The Presentation Layer: What It Is and Why It’s Important
Because our network requests come from other applications, they need to communicate with your Operating System. Whether you use OSX, Windows, or Linux, this layer helps translate what the browser or other applications data consists of to make it more universally digestible for other computer processes.
This layer is important because it helps translate the application code into code geared to send over a network. When we want to send data, we can’t send it as a regular “string,” a.k.a. text. Even if you are sending a network transmission that consists of just a few letters, such as your name, it must be converted to 1s and 0s (binary) for it to be readable by the other parts of the network transmission process. The presentation layer is also important because it involves encrypting information before it is sent over a network or decrypting a network transmission if we are receiving data.
The Session Layer: What It Is and Why It’s Important
The session layer is responsible for creating, regulating, and destroying connections between systems. Once the operating system knows that it needs to send data, this layer manages how long that connection should remain open and ensures that we receive all of the information we are requesting or sending before terminating itself.
When we send data, it does not reach our devices all at once. Think of the session layer as a traffic light that signals us when we have more information. When that process is completed, it prevents unnecessary data from reaching our system. This layer also handles a bit of authentication so that we can trust that the data reaching us is coming from the place that we requested.
The Transport Layer: What It Is and Why It’s Important
The transport layer controls the limits set on the information that we transport around our application process. This layer determines the size or block of information to transport and how fast that data can be transmitted to or from us.
We can compare the transport layer to a highway. On this road, we are getting information about a truck that has our valuable cargo on it. The truck can go at a certain speed, and we’ve informed the packing company of exactly how many items we need on the back of that truck. In other words, the transport layer is essentially making sure that the cargo (data) is supplied in a way that we anticipate. Most network services usually utilize two transporting protocols: TCP (Transmission Control Protocol) or UDP (User Datagram Protocol). We may use TCP if we want reliable, stellar data that we can’t afford to lose (e.g., FTP & email), or UDP when we need fast data and may be okay with the occasional packet drop (e.g., live streaming, online gaming, etc.).
The Network Layer: What It Is and Why It’s Important
The network layer, also known as “level three,” is responsible for managing the movement of data from one host computer to the next. It allows packet management to find the shortest route to where the data needs to go. This is controlled by packet management devices such as a router.
Routers have long saved us by identifying which computer is sending a message. Being able to give computers logical addresses so that data can be requested or received is beneficial because we don’t want data floating around the internet– it should have a specific destination. Routers examine a frame, which essentially is data that contains a source and destination address. This frame also includes a “Payload”—a.k.a. the piece of data sent down the pipeline. This layer uses IP addresses to ensure that network requests go to the intended computer.
The Data Link Layer: What It Is and Why It’s Important
The data link layer, also known as DLL or “layer two”, is a complex layer that divides itself into two additional layers called the Logical Link Control (LLC), and the Media Access Control (MAC). This layer ensures that the delivery from computer node to computer node is complete. It is usually controlled by the Network Interface Card (NIC).
This part of the network request dictates how two machines talk to one another. The “frames” that the network layer examines are assembled by the data link layer. The MAC portion helps us to avoid collisions of our data if we send multiple requests while also establishing the medium in which our data will be sent (wireless vs. wired). The main job of the LLC is to identify our network protocols and analyze our frames for errors.
The Physical Layer: What It Is and Why It’s Important
The last layer of the network application process is handled on the physical layer. This is where modems, cables, or hubs handle data. It captures the whole frame data and converts the data transmissions to bits.
Light travels through fiber optic cables at 124,188 miles per second—that’s fast! We use satellites, fiber optic cables, routers, modems, and many other physical interfaces to send data from one world location to another. The physical layer is all about doing the heavy lifting by transporting our light waves at “warp” speed.
These layers allow us to conceptualize what a complete network transmission, from top to bottom, would look like. Our data will traverse each layer, and convert the code that we write into data that different protocols can interpret. If we want better insight into how modern networks have used this as a realistic platform, we can also look at the TCP/IP model to see what layers are used in today’s network transmissions.
Additional Reading:
The OSI Model Doesn’t Map Well to TCP/IP
The Actual OSI Model
Internet Protocol Suite
Related Content
User-centered thinking: 7 things to consider and a free guide.
Want the benefits of UX but not sure where to start? Grab our guide to evaluate your needs, earn buy-in, and get hiring tips.
Get Email Updates
See everything in.
- Inspiration
More Like This
Case study: corporate website strategy, ux, and redesign for a fortune 500 company.
Chris Schmelter
Sometimes the biggest challenge in an engagement is deciding which problems to solve. With a recent client, we were able to pivot to design and tell their story in a whole new way.
What Even Are Dragging Movements?
Catherine Meade
Understanding and implementing the Web Accessibility Content Guidelines (WCAG) can be difficult for even trained experts. Catherine helps us with WCAG 2.2′s newest guideline by explaining the requirements and providing examples of how to improve our user interfaces.
Relaunching Sparkbox.com
Learn how Sparkbox avoided the “cobbler’s children have no shoes” problem with updates to its website and the Foundry.
Want to talk about how we can work together?
Katie can help

Katie Jennings
Vice President of Business Development

CCNA 200-301
- CCNA 200-301 Labs
- CCNP 350-401 ENCOR
- CCNP 350-401 ENCOR Labs
- CCNP 300-410 ENARSI
- CCIE Enterprise Infrastructure
- Cisco Packet Tracer Lab Course
- NRS II IRP Course
- NRS II MPLS Course
- NRS II Service Architecture
- Nokia Configuration Course
- Nokia SRC Program
- JNCIA Junos
- HCIA (HCNA)
- HCIA Configuration Course
- What is Huawei R&S Certification?
- Huawei ICT Certifications
- Python Course
- IPv6 Course
- IP Multicast Course
- NRS I Configuration Course
- Cisco Packet Tracer How To Guide
- Online Courses
- Udemy Courses
- CCNA Flashcard Questions
- Protocol Cheat Sheets
- Subnetting Cheat Sheet
- Linux Cheat Sheet
- Python Cheat Sheet
- CLI Commands Cheat Sheets
- Miscellaneous Cheat Sheets
- Cisco Packet Tracer Labs
- Cisco GNS3 Labs
- Huawei eNSP Labs
- Nokia GNS3 Labs
- Short Config Videos
- Network Tools
- IPCisco on Social Media
- Network Engineer Interview Questions
- Personality Interview Training
- Sign In/Up | Members
- Lost password
- Sign In/Sign Up
- ENROLL HERE

- OSI Referance Model
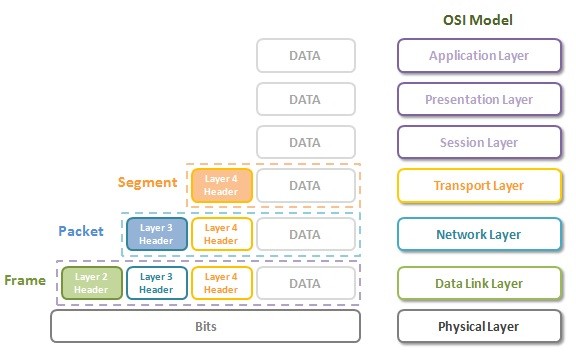
Table of Contents
OSI Model and TCP/IP Model
Computer network communication are a little complex. To understand this communication, experts divides computer network communication into different layers. To do this division, there are two standard models. These models are OSI Model and TCP/IP Model . Both of these models has different layers. OSI Model has 7 layers and TCP/IP model has 4 or 5 layers. Here, we will focus on OSI Reference Model.
As a beginner in networking, OSI Model and TCP/IP Model are very important to understand the network world. These two common standards has also been a classical question of a network engineer technical interviews . These questions are like: What are the layers of OSI Model ? How many Layers does TCP/IP Model has? What is the role of Data Link Layer?, Which devices works on Network Layer? Which protocols are there in Transport layer? etc…
Now, let’s start with the details of OSI Model Layers . In another lesson, we will talk about TCP/IP Model and its layers detailly.

OSI Reference Model is the first term that a network engineer learn in networking. It is generally the first lesson of almost all the certification courses. It is also generally always encountered especially at the technical job interviews of junior network engineers. But OSI Model is only a visionary concept. In real network operations, you will not think about this standard and its layers.
So, what is this Referance Model? What are these OSI Layers ? Below, you can find these layers orderly from starting at the bottom, from Layer 1, to Layer 7, to the top.
Physical Layer (Layer 1)
- Data-link Layer (Layer 2)
Network Layer (Layer 3)
Transport layer (layer 4), session layer (layer 5), presentation layer (layer 6), application layer (layer 7).
As you can see, there are 7 layers in OSI Reference Model. The first four layers are the Lower Layers and the last three layers are Upper Layers . If we compare OSI and TCP/IP Models, Lowers layers of these models has some differences, but the application layer of TCP/IP model is similar to the upper layers od OSI model.
So, whats are the roles of each OSI Model Layer ? Lets talk about them one by one detailly
Physical Layer (Layer 1) is the actual connectivity between the source and the destination. It is the layer in which the physical characteristic of the network is defined and bit flow transfer is done. These bits are determined with signals . These signals can be both analog and digital. Electrical signals are used for fixed connections and radio signals are used for wireless connections.
In other words, bit flow is done in this level, in other words meaningful 0 and 1 bits are transferred here. Basically, it is the layer in which bit streams are transferred over different media types. Network cabling , different types of cables and network connectors are on physical layer of OSI Model .
As a simple and old network equipment, simple hubs works in physical layer (layer 1). Because, there are not smart devices and on layer 1, there is no need for a smart device.
Below, you can find operation examples in Layer 1. The upper two are a little complex but the lower two can be a good examples:)

Data-link Layer (Layer 2)
Data-link Layer (Layer 2) is the medium provision Layer. It defines how data is formatted for the transmission over physical medium. Layer 2 provides, node-to node connectivity. It is also the layer of physical MAC addresses .
The most important devices work on layer 2 of OSI Model is Layer 2 switches . As a network engineer, a network technician or a network admin, you will work on these data-link layer devices too much.
Data Link Layer encapsulates the data by adding a layer 2 header and layer 2 trailer . The data after adding Layer 2 Header and layer 2 trailer is called “ frame ”. Layer 2 header contains source and destination MAC Addresses . So, it is responsible to find the next destination in the network. For decapsulation, it also removes these header and trailer and sends the data to the upper network layer.
Data Link Layer provides Error-free transfer of different categories of data frames. It detects physical layer errors and corrects them.
Different network protocols and standards are used in the different layers of OSI model. You can think them as the groups of rules. According to these protocols and standards, network technologies are used and device configurations are done.
Ethernet is one of the most popular protocol in data link layer. Ethernet is the general name of the standard which is used in our home or office networks. It defines a lot of things like cable types, data speed etc.
There are other protocols and standards in data link layers. Some of them are: PPP, HDLC, FDDI, ATM, Frame Relay.
Data-link Layer has two sub-layers . These layers are:
- Media Access Control (MAC) Layer
- Logical Link Control (LLC) Layer
The MAC Sub Layer controls how a computer on the network gains access to the data and permission to transmit it. And it carries the physical address of each device on the network.
The Logical Link Control (LLC) responsible for managing frames to upper and lower layers, Flow control mechanism and Error checking.

Network Layer is the layer of logical addressing. This layer decides the logical address of the destination with IP addresses. By doing this, it connects different networks that use different medias each other. These addresses can be IPv4 address or IPv6 address .
Network layer is also responsible for routing . With routing, it decides the path of the packets through the network. In other words, it defines the routers that the data will go through. This is one of the popular areas for network engineers :) So, routing protocols works on layer 3 (network layer).
A Layer 3 Header (IP Header for IP) is added to the data in this layer. After this addition, frame is called as “ packet ”. In this header also the next level protocol is mentioned. It can be any transport layer protocol like, TCP , UDP and SCTP .
Frame fragmentation is also done in this Layer. If a frame is longer than MTU (Maximum Transmission Unit) , then it is fragmented (divided to the little packets).
There are different protocols used in network layer of OSI. Some of these protocols are IPv4, IPv6, ICMP, IPSec, OSPF, BGP etc.

Transport Layer (Layer 4) establishes, maintains and manages end to end secure connection. This layer allows multiple transports on same physical connection.
Transport layer is responsible for end-to-end Error Recovery and Flow Control . Transport Layer is also the Layer that QoS facilities also performed.
Different transport layer protocols are used in this layer. According to used Layer 4 protocol, Layer 4 Header is added to the packet in this Layer. After this the packet called “ segment ”.
There are two common Transport Layer Protocols. These Protocols are UDP (User Datagram Protocol) and TCP (Transmission Control Protocol) . There are also other Transport Layer Protocols like SCTP, RSVP etc. But in CCNA, we will focus on TCP and UDP. We will explain the details of these protocols in the following lessons.
Below, you can find some of TCP layer 4 operations and transport layer protocols comparison.
Session Layer (Layer 5) is the OSI layer, that responsible for session jobs between the end points. It provides session establishment, maintenance and termination. Logging is also done in this layer. One of the other main roles of this session layer is multiplexing transport layer services.
Session layer is mainly used by applications themselves. So, network engineers do not work on this layer. This is the job of application developers.
Log in to a computer for file transfer can be an example of session layer job.
Presentation Layer (Layer 6) is the Translator of the network. There are many data formats in any network. This layer provides translation between different formats.
For example, image formats like jpeg, gif, voice formats like mp3 and video format like mp4 are all need different behaviors. Presentation layer converts this different data into a readable format.
Encryption and compression of the data are also done in presentation layer (layer 6) of OSI Model.

Application Layer (Layer 7) is the closest layer to user. It is the interface between applications and the underlying Layers. It provides the provision of the communication between Applications. Application Layer let programs to reach different network resources.
Some of the protocols used in Application Layer are Telnet, FTP , SMTP, HTTPS, SSL etc. Different services work with these protocols. For example, the browser that you use internet, works with HTTP. By the way, the application itself is not belong to this layer.

- Network Devices
As you know in a network there are some common network devices like Hubs, Repeaters, Bridges, Switches and Routers. These devices operates in different Layers of OSI model. Lets check this devices and the Layers they are used.
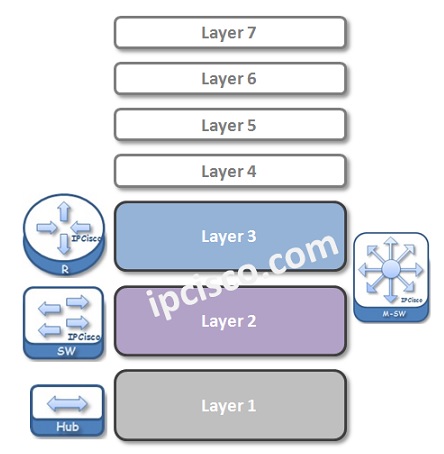
Everything begins with the data at the Application Layer. Then through out the destination, in each Lower Layer, an additional Header is added to these Data. And at the Physical Layer, all these are send via 1s and 0s as voltages over the cables.
What are these Headers of OSI Model Layers and how effects the data?
- At Transport Layer , Layer 4 Header is added. Here the name of “Data and Layer 4 Header” is “ Segment ”.
- At Network Layer , Layer 3 Header is added. Here the name of “Data and Layer 3 Header” is “ Packet ”.
- At Data-Link Layer , Layer 2 Header is added. Here the name of “Data and Layer 2 Header” is “ Frame ”.
- At Physical Layer , all of them is translate to 1s and 0s as voltages.And these values are sent and received over different media types(cables).
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Network Fundamentals
- Collision Domain vs Broadcast Domain
- Coaxial Cable Details
- Types of Networks
- Top Internet Access Technologies
- WAN Topology Types
- Network Topology Architectures
- Power Over Ethernet (PoE)
- Ethernet Collisions and Troubleshooting
- Cisco NGFW and Cisco NGIPS
- Networking Connectors
- Ping Command
- Basic Cisco Router Configuration on Packet Tracer
- ICMP (Internet Control Message Protocol)
- Address Resolution Protocol (ARP)
- Network Cabling
- TCP/IP Model
IPv4 Addressing
- Verify IP Parameters for Client OS
- IPv4 vs IPv6 Comparison
- Cisco IP Address Configuration
- APIPA Address
- Private IP Address Ranges
- Subnetting Examples
- IP Addressing (IPv4)
- IP Subnetting and Subnetting Examples
TCP and UDP
- TCP Header : Sequence & Acknowledgement Number
- TCP Handshake
- TCP versus UDP
- UDP (User Datagram Protocol)
- TCP (Transmission Control Protocol)
- TCP Header : TCP Options
- TCP Header : TCP Window Size, Checksum & Urgent Pointer
- TCP Header : TCP Flags
- Voice VLAN Configuration
- Packet Tracer VLAN Example 2
- How to Configure Cisco VLANs
- VTP Configuration with Packet Tracer
- VTP (VLAN Trunking Protocol)
- DTP and VLAN Frame Tagging protocols ISL, dot1.q
- Cisco Packet Tracer VLAN Configuration Example
- VLAN Port Assignment and VLAN Port Types
- VLANs (Virtual Local Area Networks)
Switching and LANs
- Ethernet Basics
- Cisco Switch Configuration on Cisco Packet Tracer
- MAC Address Lookup
- What is a mac address
- Local Area Networks
- Network Topologies
- Hubs, Switches and Routers
Spanning Tree Protocol
- Loop Guard, Uplink Fast, Backbone Fast and UDLD
- Portfast, Root Guard, BPDU Filter and BPDU Guard
- PVST+ and Rapid PVST+
- STP (Spanning Tree Protocol) Example on Packet Tracer
- RSTP Configuration on Packet Tracer
- STP Portfast Configuration with Packet Tracer
- Spanning Tree Protocol Operation
- Rapid Spanning Tree Protocol (RSTP)
- Spanning Tree Protocol (STP)
Neighbor Discovery
- LLDP Configuration on Cisco IOS
- Neighbour Discovery Protocols
- CDP Configuration with Packet Tracer
EtherChannels
- PAgP Configuration on Cisco Devices
- LACP Configuration on Cisco Devices
- Link Aggregation Control Protocol (LACP)
Routing Fundamentals
- Route Summarization
- Routing Path Determination
- Routing Table
- Static Routes
- IPv4 Floating Static Routes
- Inter VLAN Routing Configuration on Packet Tracer
- Switch Virtual Interface Configuration on Packet Tracer
- Switch Virtual Interfaces
- Inter VLAN Routing with Router on Stick
- IP and Layer 3 Overview
- Static Route Configuration on Cisco Routers
- Dynamic Routing Protocols
- OSPF Cost and SPF Algorithm
- OSPFv3 Configuration Example on Cisco IOS
- OSPFv3 (Open Shortest Path First Version 3)
- Cisco Single Area OSPF Configuration
- Other OSPF Key Points
- OSPF Network Types
- OSPF Area Types
- OSPF LSA Types
- OSPF Packet Types
- OSPF Adjacency
- OSPF(Open Shortest Path First) Overview
WAN (Wide Area Networks)
- MLPPP Configuration on Cisco Packet Tracer
- What is MLPPP?
- Metro Ethernet Technology
- WAN and WAN Technologies
DHCP and DNS
- DNS Configuration on Cisco Routers
- Domain Name System Overview
- Router DHCP Configuration with Packet Tracer
- DHCP IP Allocation Operation
- DHCP (Dynamic Host Configuration Protocol)
- NAT (Network Address Translation)
- PAT Configuration with Packet Tracer
- Dynamic NAT Configuration with Packet Tracer
- Static NAT Configuration with Packet Tracer
First Hop Redundancy
- HSRP Configuration on Cisco IOS
- HSRP (Hot Standby Router Protocol)
- First Hop Redundancy Protocols (FHRPs)
Network Management
- Syslog Overview
- Configuration Register
- TFTP, FTP, SFTP and SCP
- SSH Configuration on Packet Tracer
- Syslog Configuration Cisco
- Cisco NTP Configuration
- NTP (Network Time Protocol)
- SNMP Overview
- SNMP Configuration On Cisco IOS
- Cisco Router Password Recovery
- IPv6 Floating Static Routes
- IPv6 Static and Default Route Configuration
- Stateless Address Auto Configuration
- IPv6 NDP (Neighbour Discovery Protocol)
- IPv6 Configuration on Cisco Packet Tracer
- What does IPv6 bring?
- Subnetting in IPv6
- IPv6 Address Types
- IPv4 and IPv6 Headers
- IPv6 and IPv6 Addresses
Quality of Service
- Network Traffic Types
- Policing and Shaping in QoS
- Classification and Marking in QoS
- Quality of Service Overview
- Radius Configuration for Wireless Users
- Cisco RADIUS Server Configuration on Packet Tracer
- TACACS+ Overview
- RADIUS Overview
- AAA Protocols : RADIUS and TACACS+
- Authentication, Authorization, Accounting (AAA)
- WLAN Frequency Bands
- Other Wireless Network Extention Types
- Wireless Principles
- WLAN Components
- Wireless Network Design Models
- WLC Management Access Connections
- Wireless Access Point Modes
- Wireless Security Protocols
- WLAN Configuration on Packet Tracer
Security Fundamentals
- DHCP Snooping Configuration on Packet Tracer
- Cisco Banner Configuration on Packet Tracer
- What is DHCP Snooping?
- Access Control Lists
- Multifactor Authentication (MFA)
- Dynamic ARP Inspection
- Cyber Attacks, Network Attacks, Threats and Mitigation
- 802.1x (Port Based Network Access Control)
- Switch Port Security Configuration on Cisco Packet Tracer
- Switch Port Security
- Extended Access List Configuration With Packet Tracer
- Standard Access List Configuration With Packet Tracer
- Basic Cisco Router Security Configuration
Automation and Programmability
- Ansible vs Puppet vs Chef
- Chef Overview
- Puppet Overview
- Ansible Overview
- Network Automation Tools
- Interpret JSON Encoded Data
- Cisco DNA Center
- Cisco SD-Access
- Data Serialization Languages: JSON, YAML, XML
- Traditional Network Management versus Cisco DNA Center
- Cisco DNA and Intent-Based Networking (IBN)
- How Network Automation Impacts Network Management
SDN (Software Defined Networking)
- What is SDN ?
- Traditional Network Drawbacks Versus SDN
- What Will SDN Bring?
- SDN Architecture Components
- SDN Terminology
- Virtualization
- Virtual Network Structure
Latest Lessons
- VLSM Part of: CCNA 200-301
- Coaxial Cable Details Part of: CCNA 200-301
- IPv4 vs IPv6 Comparison Part of: CCNA 200-301
- IGMPv3 Overview Part of: IP Multicast Course
- IGMPv3 Overview Part of: CCIE Enterprise Infrastructure
- Subnetting IPv6 Part of: CCIE Enterprise Infrastructure
- IPv6 and Subnetting Part of: CCNP Enterprise 350-401 ENCOR
- IPv6 Link Local Address Type Part of: CCIE Enterprise Infrastructure
- Cisco Switch Configuration on Cisco Packet Tracer Part of: CCNA 200-301
- Switch Configuration on Cisco Packet Tracer Part of: Cisco Packet Tracer Lab Course
- More Lessons
Latest Blog Posts
WHAT YOU WILL FIND?
- 250.000+ Students All Over The World
- 8.000+ Questions & Answers
- 100+ Lab Files & Cheat Sheets
- 30+ IT/Network Courses
- A Real Desire To Help You
- Daily Social Media Shares
- %100 Satisfaction
- CISCO Courses
- NOKIA Courses
- HUAWEI Courses
- JUNIPER Courses
- PYTHON Course
- KEY Courses
- VIDEO Courses
- UDEMY Courses
- Cheat Sheets
- Configuration Files
- Interview Questions
- IPCisco On Social Media
- Pärnu mnt. 139c – 14, 11317, Tallinn, Estonia
- [email protected]
Session and Presentation layers in the OSI model
Alessandro Maggio
- December 29, 2016

Share This Post
Session and presentation layers in the OSI stack can be considered fancy layers , as they are known only by a small part of Network Engineers. This is probably because all their features blend either in transport-layer protocols or in application-layer protocols. However, with this article, you will discover all the beauty of these two layers, learning what they do and how they are implemented.
UDP limitations
Back in the CCNA course, we found out that the only place we can see the session and presentation layers truly implemented is when they are based on UDP transport. UDP leaves some room to these two layers (if compared to TCP) because it is extremely simple and lacking features . These features can be then implemented in upper layers individually, adding modularity. Just to refresh your mind, UDP has the following two limitations.

UDP, all by itself, do not order packets, and therefore the receiver cannot guess in which order they were sent originally. Moreover, it is not reliable, what is lost is just lost, no UDP component will trigger a re-transmission. Adding these features, however, would increase the complexity of the algorithm behind UDP running on hosts and will add extra fields in the UDP header sent with every segment. All of that, and specifically the extra bytes added in the segment’s header, is called overhead : the extra amount of information that allows application data to be delivered correctly. Our goal is to obtain the delivery of application data as we want it with the least overhead possible .
In the article about advanced TCP , we already explained the ways we can reduce the TCP overhead using selective ACK and header compression, but all of these complex items cannot reduce the TCP header to the size of a UDP header. Instead, with UDP we follow a different approach: we start from almost no features (only delivery to the correct application using port numbers) and we add the features we need in upper layers.
Session layer
The session layer is the one implementing one-to-one application sessions: it defines the re-transmission of data, the segment ordering method, and control the communication in general. All these features are covered by TCP for applications using that transport protocol, but applications that leverage UDP have to implement these features autonomously (within the application) or rely on an extra protocol specifically sitting at the session layer. Many applications (such as TFTP) rely on the first option, while the second alternative is the privileged one for VoIP. For VoIP traffic, the protocol we rely on for the session is the Real-time Transport Protocol (RTP) . As we are talking about applications using UDP as their underlying transport, spending some time on RTP is certainly well-worth since Voice and Video are the king applications among all UDP-based applications .
The RTP header in the picture is inserted just after the UDP header, and add extra features such as the reordering of segments and their timing, which are extremely important for an application that must run real-time. Here’s the explanation of its fields.
- Version – Version of RTP, the up-to-date one is version 2
- P (Padding) – Flag used to indicate whether padding is present or not in the segment
- X (Extension) – Flag used to indicate whether extension header is present or not
- CC (CSRC count) – Number of CSRC identifiers contained in the header
- M (Marker) – Flag that, if set, indicates that this segment has some special relevance for the application
- PT (Payload Type) – Indicates the type of RTP payload (e.g. for VoIP/Video stream)
- Sequence number – Used from the receiver to reorder packets, incremented by one each segment sent
- Timestamp – Time the segment was created, used to allow the receiver to play the content of the segment (assuming that it is audio or video) at the proper interval
- SSCS – Synchronization Source Identifier, identifies a stream of UDP/RTP segments
- CSRC – Contributing Source IDs, indicates the source of the audio stream, multiple CSRCs can be specified if there are multiple sources (e.g. in a three-party conference)
- Header extension – extra header, optional and profile-specific
These fields are the minimum needed to allow the transmission and are specifically designed for real-time streams, audio, and video mainly. Looking at the header, you can still find the Sequence number as in TCP, but no acknowledgment number . This is because RTP allows the receiver to reorder segments , but not to arrange a re-transmission. This behavior is purposefully designed this way, as a VoIP call or a video stream needs to be delivered now. In case something is lost, there is no time to re-transmit it, the show must go on. If we re-transmit it, it would arrive too late so there is no point in the retransmission at all. Another interesting field adding a feature UDP is lacking is the timestamp, with that field you can know when the content was generated and reproduce the sound and video at the same interval it was generated. Otherwise, you would have audio and video streams increasing and decreasing speed according to the network connection available.
A question I’ve been asked several times when talking about reordering packets is “How they arrive in the wrong order in the first place?” and this is surely a good question. The answer has a lot to do with routing , so it lays at the Network Layer in the OSI Stack. Routers work independently from the upper layer protocols and applications, they run based on IP addressing and routes. It might happen that a node fails over the network and traffic takes a different path to avoid falling on the faulty link, or simply a router discovers a better path to a destination. Since all of this happens dynamically, at a given moment the traffic might go over a link and one second later over another. Not all links have the same speed, so it is possible that a segment sent later but over a fast link will arrive before a segment sent previously but on a slow link. Let’s have a look at the following picture.
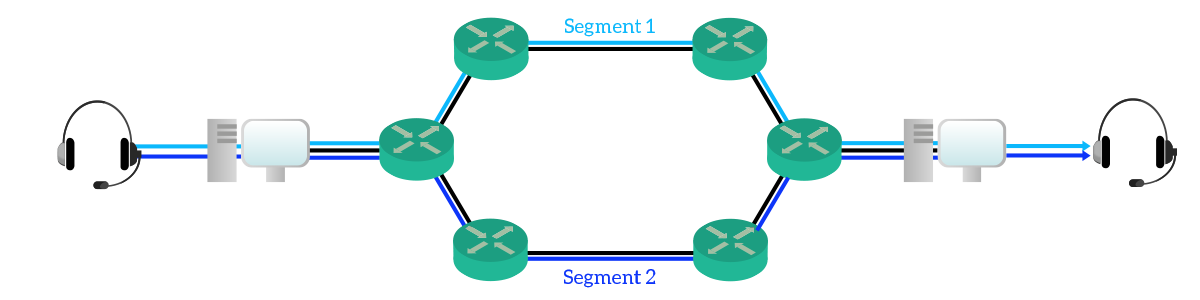
Edge devices (computers, servers) do not know about the network infrastructure, so they just know that there is the possibility that segments are disordered during the transmission by taking different ways. Because of that, they have to implement mechanisms for reordering . Reordering is crucial to almost any application, to transfer a file we need to know the order of its part, and to transfer audio stream we need to know in which order to play the sounds.
Presentation for Real-Time applications
The presentation layer is probably the most mysterious one. This is because almost no application implements it, neither among the UDP applications. What this layer does, is to define how data should be presented to the application. Once again, coming to rescue us we have VoIP and Video stream, the ones leveraging this layer the most. Basically, when you make a VoIP call there are some parameters involved in the audio stream, such as the bitrate or the compression rate just to name a few. To have the smoothest audio stream possible, all the parties involved must agree on how they are going to exchange audio and video. RTP is the common ground that cannot be changed, here we are talking about how to write the payload of the RTP segment. In other words, we are defining the codec.
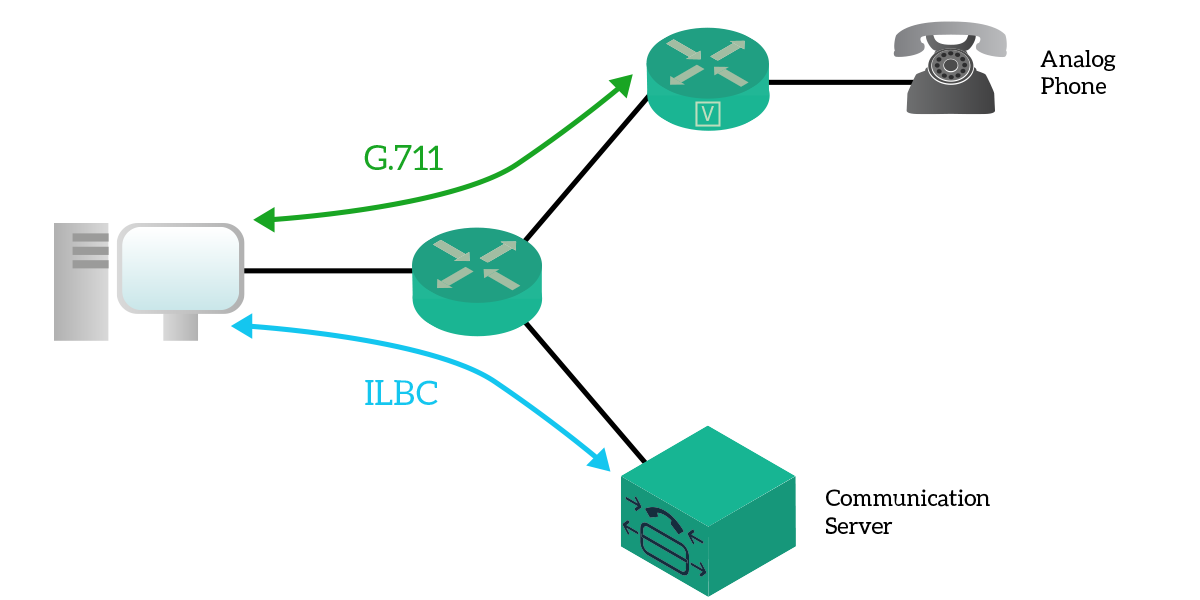
Some codecs may privilege the compression, using less bandwidth but more computational resources, others may use a lot of bandwidth but almost no computational resources or other ones require fewer resources sacrificing audio quality. No choice can be right on all occasions, the best codec for any situation depends on your needs.
Session and presentation layers in the shadow
We now know what these two layers are truly about, but let’s take a moment to check out why they are not famous like the other OSI layers. Even previously we had the chance to understand how there is almost no need to implement them, as their features are covered elsewhere, however it is time to give some examples, as in the following picture.
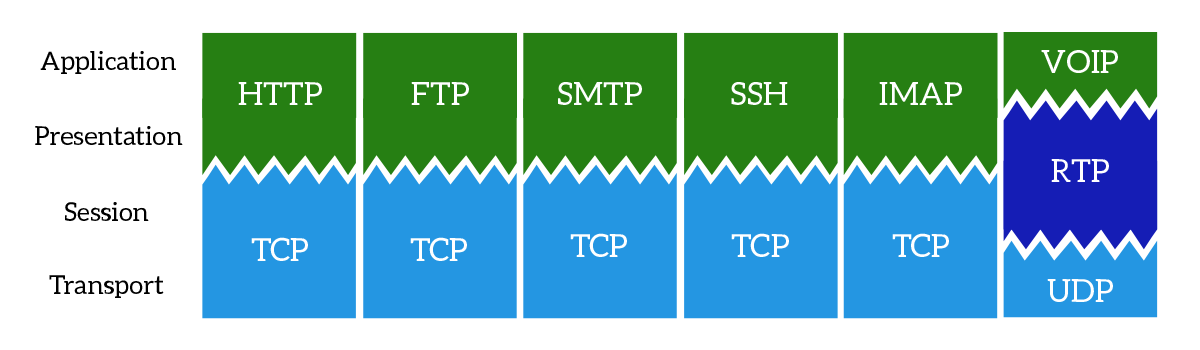
What the picture says is also listed below in a little more detail.
- HTTP (Hyper-Text Transfer Protocol) – Used to transfer web-pages, the session layer is handled by TCP while there is no need for a presentation layer as the information is sent in simple text or raw binary
- FTP (File Transfer Protocol) – Used to transfer files to and from a server, the session layer is handled by TCP while there is no need for a presentation layer as the information is sent in raw binary
- SMTP (Simple Mail Transfer Protocol) – Used to send emails from a server o another, the session layer is handled by TCP while there is no need for a presentation layer as the information is sent in simple text
- SSH (Secure Shell) – Used to connect to a remote device and control it via textual commands using encryption, the session layer is handled by TCP while there is no need for a presentation layer as the information is sent in simple text
- IMAP (Internet Message Access Protocol) – Used to connect to an email server and check emails, the session layer is handled by TCP while there is no need for a presentation layer as the information is sent in simple text
- VoIP (Voice over IP) – This is not a real protocol, but instead a type of application, RTP manages the session layer while the presentation layer exists and is managed at the application layer
This article was really lightweight, as UDP is. With this knowledge, you know all the differences between UDP and TCP and you are ready to discuss the technologies implemented in a network to support modern applications. In the following articles, we will start to see some application layer protocols before we can dive into the configuration items.
Never Stop Learning...
The 7 most effective time management strategies, 6 amazing generative ai use cases for the real world, don't fail the ccna exam, failing the ccna exam equals wasting $300. don't do that, be prepared instead., together with our free course, we offer a companion book with questions and answers. and it's only $27.50 if you are following the course..
Join the Newsletter to Get Ahead
Revolutionary tips to get ahead with technology directly in your inbox..
2016-12-29T16:30:49+00:00
Unspecified
Free CCNA Course
Want Visibility from Tech Professionals?
If you feel like sharing your knowledge, we are open to guest posting - and it's free. find out more now..

Accessibility
Free courses.
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
- Computer Network Tutorial
Basics of Computer Network
- Basics of Computer Networking
- Introduction to basic Networking Terminology
- Goals of Networks
- Basic characteristics of Computer Networks
- Challenges of Computer Network
- Physical Components of Computer Network
Network Hardware and Software
- Types of Computer Networks
- LAN Full Form
- How to Set Up a LAN Network?
- MAN Full Form in Computer Networking
- MAN Full Form
- WAN Full Form
- Introduction of Internetworking
- Difference between Internet, Intranet and Extranet
- Protocol Hierarchies in Computer Network
- Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter)
- Introduction of a Router
- Introduction of Gateways
- What is a network switch, and how does it work?
Network Topology
- Types of Network Topology
- Difference between Physical and Logical Topology
- What is OSI Model? - Layers of OSI Model
- Physical Layer in OSI Model
- Data Link Layer
- Session Layer in OSI model
Presentation Layer in OSI model
- Application Layer in OSI Model
- Protocol and Standard in Computer Networks
- Examples of Data Link Layer Protocols
- TCP/IP Model
- TCP/IP Ports and Its Applications
- What is Transmission Control Protocol (TCP)?
- TCP 3-Way Handshake Process
- Services and Segment structure in TCP
- TCP Connection Establishment
- TCP Connection Termination
- Fast Recovery Technique For Loss Recovery in TCP
- Difference Between OSI Model and TCP/IP Model
Medium Access Control
- MAC Full Form
- Channel Allocation Problem in Computer Network
- Multiple Access Protocols in Computer Network
- Carrier Sense Multiple Access (CSMA)
- Collision Detection in CSMA/CD
- Controlled Access Protocols in Computer Network
SLIDING WINDOW PROTOCOLS
- Stop and Wait ARQ
- Sliding Window Protocol | Set 3 (Selective Repeat)
- Piggybacking in Computer Networks
IP Addressing
- What is IPv4?
- What is IPv6?
- Introduction of Classful IP Addressing
- Classless Addressing in IP Addressing
- Classful Vs Classless Addressing
- Classless Inter Domain Routing (CIDR)
- Supernetting in Network Layer
- Introduction To Subnetting
- Difference between Subnetting and Supernetting
- Types of Routing
- Difference between Static and Dynamic Routing
- Unicast Routing - Link State Routing
- Distance Vector Routing (DVR) Protocol
- Fixed and Flooding Routing algorithms
- Introduction of Firewall in Computer Network
Congestion Control Algorithms
- Congestion Control in Computer Networks
- Congestion Control techniques in Computer Networks
- Computer Network | Leaky bucket algorithm
- TCP Congestion Control
Network Switching
- Circuit Switching in Computer Network
- Message switching techniques
- Packet Switching and Delays in Computer Network
- Differences Between Virtual Circuits and Datagram Networks
Application Layer:DNS
- Domain Name System (DNS) in Application Layer
- Details on DNS
- Introduction to Electronic Mail
- E-Mail Format
- World Wide Web (WWW)
- HTTP Full Form
- Streaming Stored Video
- What is a Content Distribution Network and how does it work?
CN Interview Quetions
- Top 50 Networking Interview Questions (2024)
- Top 50 TCP/IP interview questions and answers
- Top 50 IP addressing interview questions and answers
- Last Minute Notes - Computer Networks
- Computer Network - Cheat Sheet
- Network Layer
- Transport Layer
- Application Layer
Prerequisite : OSI Model
Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extracted and manipulated here as per the required format to transmit over the network. The main responsibility of this layer is to provide or define the data format and encryption. The presentation layer is also called as Syntax layer since it is responsible for maintaining the proper syntax of the data which it either receives or transmits to other layer(s).
Functions of Presentation Layer :
The presentation layer, being the 6th layer in the OSI model, performs several types of functions, which are described below-
- Presentation layer format and encrypts data to be sent across the network.
- This layer takes care that the data is sent in such a way that the receiver will understand the information (data) and will be able to use the data efficiently and effectively.
- This layer manages the abstract data structures and allows high-level data structures (example- banking records), which are to be defined or exchanged.
- This layer carries out the encryption at the transmitter and decryption at the receiver.
- This layer carries out data compression to reduce the bandwidth of the data to be transmitted (the primary goal of data compression is to reduce the number of bits which is to be transmitted).
- This layer is responsible for interoperability (ability of computers to exchange and make use of information) between encoding methods as different computers use different encoding methods.
- This layer basically deals with the presentation part of the data.
- Presentation layer, carries out the data compression (number of bits reduction while transmission), which in return improves the data throughput.
- This layer also deals with the issues of string representation.
- The presentation layer is also responsible for integrating all the formats into a standardized format for efficient and effective communication.
- This layer encodes the message from the user-dependent format to the common format and vice-versa for communication between dissimilar systems.
- This layer deals with the syntax and semantics of the messages.
- This layer also ensures that the messages which are to be presented to the upper as well as the lower layer should be standardized as well as in an accurate format too.
- Presentation layer is also responsible for translation, formatting, and delivery of information for processing or display.
- This layer also performs serialization (process of translating a data structure or an object into a format that can be stored or transmitted easily).
Features of Presentation Layer in the OSI model: Presentation layer, being the 6th layer in the OSI model, plays a vital role while communication is taking place between two devices in a network.
List of features which are provided by the presentation layer are:
- Presentation layer could apply certain sophisticated compression techniques, so fewer bytes of data are required to represent the information when it is sent over the network.
- If two or more devices are communicating over an encrypted connection, then this presentation layer is responsible for adding encryption on the sender’s end as well as the decoding the encryption on the receiver’s end so that it can represent the application layer with unencrypted, readable data.
- This layer formats and encrypts data to be sent over a network, providing freedom from compatibility problems.
- This presentation layer also negotiates the Transfer Syntax.
- This presentation layer is also responsible for compressing data it receives from the application layer before delivering it to the session layer (which is the 5th layer in the OSI model) and thus improves the speed as well as the efficiency of communication by minimizing the amount of the data to be transferred.
Working of Presentation Layer in the OSI model : Presentation layer in the OSI model, as a translator, converts the data sent by the application layer of the transmitting node into an acceptable and compatible data format based on the applicable network protocol and architecture. Upon arrival at the receiving computer, the presentation layer translates data into an acceptable format usable by the application layer. Basically, in other words, this layer takes care of any issues occurring when transmitted data must be viewed in a format different from the original format. Being the functional part of the OSI mode, the presentation layer performs a multitude (large number of) data conversion algorithms and character translation functions. Mainly, this layer is responsible for managing two network characteristics: protocol (set of rules) and architecture.
Presentation Layer Protocols : Presentation layer being the 6th layer, but the most important layer in the OSI model performs several types of functionalities, which makes sure that data which is being transferred or received should be accurate or clear to all the devices which are there in a closed network. Presentation Layer, for performing translations or other specified functions, needs to use certain protocols which are defined below –
- Apple Filing Protocol (AFP): Apple Filing Protocol is the proprietary network protocol (communications protocol) that offers services to macOS or the classic macOS. This is basically the network file control protocol specifically designed for Mac-based platforms.
- Lightweight Presentation Protocol (LPP): Lightweight Presentation Protocol is that protocol which is used to provide ISO presentation services on the top of TCP/IP based protocol stacks.
- NetWare Core Protocol (NCP): NetWare Core Protocol is the network protocol which is used to access file, print, directory, clock synchronization, messaging, remote command execution and other network service functions.
- Network Data Representation (NDR): Network Data Representation is basically the implementation of the presentation layer in the OSI model, which provides or defines various primitive data types, constructed data types and also several types of data representations.
- External Data Representation (XDR): External Data Representation (XDR) is the standard for the description and encoding of data. It is useful for transferring data between computer architectures and has been used to communicate data between very diverse machines. Converting from local representation to XDR is called encoding, whereas converting XDR into local representation is called decoding.
- Secure Socket Layer (SSL): The Secure Socket Layer protocol provides security to the data that is being transferred between the web browser and the server. SSL encrypts the link between a web server and a browser, which ensures that all data passed between them remains private and free from attacks.
Please Login to comment...
Similar reads.

Improve your Coding Skills with Practice
What kind of Experience do you want to share?

STP Operations

Troubleshooting Scenarios

Troubleshooting Methodologies
Application, Presentation, and Session
This topic explain how the functions of the application layer, presentation layer, and session layer work together to provide network services to end user applications. Start learning CCNA 200-301 for free right now!!
Note : Welcome: This topic is part of Chapter 15 of the Cisco CCNA 1 course, for a better follow up of the course you can go to the CCNA 1 section to guide you through an order.
Table of Contents
Application Layer
In the OSI and the TCP/IP models, the application layer is the closest layer to the end user. As shown in the figure, it is the layer that provides the interface between the applications used to communicate, and the underlying network over which messages are transmitted. Application layer protocols are used to exchange data between programs running on the source and destination hosts.

Based on the TCP/IP model, the upper three layers of the OSI model (application, presentation, and session) define functions of the TCP/IP application layer.
There are many application layer protocols, and new protocols are always being developed. Some of the most widely known application layer protocols include Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP), Trivial File Transfer Protocol (TFTP), Internet Message Access Protocol (IMAP), and Domain Name System (DNS) protocol.
Presentation and Session Layer
Presentation Layer
The presentation layer has three primary functions:
- Formatting, or presenting, data at the source device into a compatible format for receipt by the destination device.
- Compressing data in a way that can be decompressed by the destination device.
- Encrypting data for transmission and decrypting data upon receipt.
As shown in the figure, the presentation layer formats data for the application layer, and it sets standards for file formats. Some well-known standards for video include Matroska Video (MKV), Motion Picture Experts Group (MPG), and QuickTime Video (MOV). Some well-known graphic image formats are Graphics Interchange Format (GIF), Joint Photographic Experts Group (JPG), and Portable Network Graphics (PNG) format.
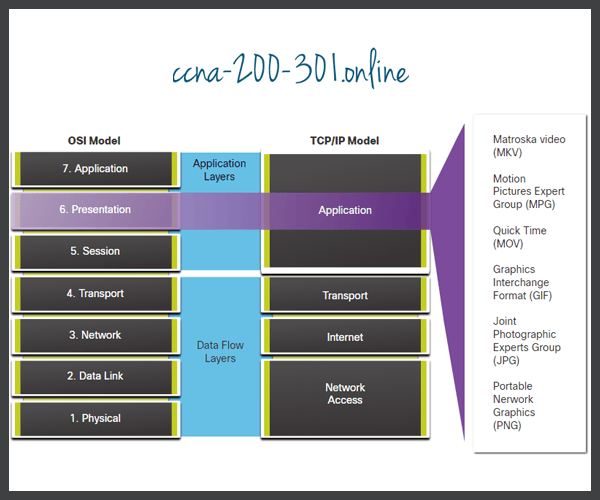
Session Layer
As the name implies, functions at the session layer create and maintain dialogs between source and destination applications. The session layer handles the exchange of information to initiate dialogs, keep them active, and to restart sessions that are disrupted or idle for a long period of time.
TCP/IP Application Layer Protocols
The TCP/IP application protocols specify the format and control information necessary for many common internet communication functions. Application layer protocols are used by both the source and destination devices during a communication session. For the communications to be successful, the application layer protocols that are implemented on the source and destination host must be compatible.
Click each application protocol type to learn more about each protocol.
- Name System
- Host Config
- File Transfer
DNS - Domain Name System (or Service)
- TCP, UDP client 53
- Translates domain names, such as cisco.com, into IP addresses.
BOOTP - Bootstrap Protocol
- UDP client 68, server 67
- Enables a diskless workstation to discover its own IP address, the IP address of a BOOTP server on the network, and a file to be loaded into memory to boot the machine
- BOOTP is being superseded by DHCP
DHCP - Dynamic Host Configuration Protocol
- Dynamically assigns IP addresses to be re-used when no longer needed
SMTP - Simple Mail Transfer Protocol
- Enables clients to send email to a mail server
- Enables servers to send email to other servers
POP3 - Post Office Protocol
- Enables clients to retrieve email from a mail server
- Downloads the email to the local mail application of the client
IMAP - Internet Message Access Protocol
- Enables clients to access email stored on a mail server
- Maintains email on the server
FTP - File Transfer Protocol
- TCP 20 to 21
- Sets rules that enable a user on one host to access and transfer files to and from another host over a network
- FTP is a reliable, connection-oriented, and acknowledged file delivery protocol
TFTP - Trivial File Transfer Protocol
- UDP client 69
- A simple, connectionless file transfer protocol with best-effort, unacknowledged file delivery
- It uses less overhead than FTP
HTTP - Hypertext Transfer Protocol
- TCP 80, 8080
- A set of rules for exchanging text, graphic images, sound, video, and other multimedia files on the World Wide Web
HTTPS - HTTP Secure
- TCP, UDP 443
- The browser uses encryption to secure HTTP communications
- Authenticates the website to which you are connecting your browser
Glossary : If you have doubts about any special term, you can consult this computer network dictionary .
Ready to go! Keep visiting our networking course blog, give Like to our fanpage ; and you will find more tools and concepts that will make you a networking professional.


IMAGES
VIDEO
COMMENTS
The session layer is meant to store states between two connections, like what we use cookies for when working with web programming. The presentation layer is meant to convert between different formats. This was simpler when the only format that was worried about was character encoding, ie ASCII and EBCDIC. When you consider all of the different ...
Application Layer Presentation Layer Present Layer=> Session Layer Transport Layer Network Layer Data Layer Physical Layer. Working of Session Layer : Session Layer, which is the 5th layer in the OSI model, uses the services provided by The transport layer, enables applications to establish and maintain sessions and to synchronize the sessions ...
The model was made to break down each functional layer so that overall design complexity could be lessened. The model was constructed with seven layers for the flow of information. These are: Application Layer. Presentation layer. Session layer. Transport layer. Network layer. Data link layer.
The Internet application layer maps to the OSI application layer, presentation layer, and most of the session layer. The TCP/IP transport layer maps to the graceful close function of the OSI session layer as well as the OSI transport layer. The internet layer performs functions as those in a subset of the OSI network layer.
The session layer is the fifth layer of the OSI layers model. It is responsible for initiating, establishing, managing, and terminating sessions between the local application and the remote applications. It defines standards for three modes of communication: full duplex, half-duplex, and simplex. In the full duplex mode, both devices can send ...
The Session Layer initiates, maintains, and terminates connections between two end-user applications. It responds to requests from the presentation layer and issues requests to the transport layer. OSI Layer 6. Layer 6 is the presentation layer. This layer is responsible for data formatting, such as character encoding and conversions, and data ...
6. Presentation Layer. The presentation layer prepares data for the application layer. It defines how two devices should encode, encrypt, and compress data so it is received correctly on the other end. The presentation layer takes any data transmitted by the application layer and prepares it for transmission over the session layer. 5. Session ...
The 7 layers of the OSI model. The layers are: Layer 1—Physical; Layer 2—Data Link; Layer 3—Network; Layer 4—Transport; Layer 5—Session; Layer 6—Presentation; Layer 7—Application. It ...
L5, therefore, takes on data from the transport layer (L4) and forwards it further to the presentation layer (L6) and vice-versa. A. ll the tasks that relate to establishing and maintaining a two-way link for data transfer fall under the scope of the session layer! Layer 6: Presentation layer
Session, Presentation, and Application Layers. Recall that there are two popular network models in use: the OSI Reference Model and the TCP/IP Reference Model. In this chapter you'll learn about the top three layers of the OSI model. Those three OSI layers correspond to the Application Layer (top layer) in the TCP/IP model.
Session layer. The session layer is responsible for network coordination between two separate applications in a session. A session manages the beginning and ending of a one-to-one application connection and synchronization conflicts. Network File System (NFS) and Server Message Block (SMB) are commonly used protocols at the session layer ...
The different layers of the OSI Model are the application layer, presentation, session, transport, network, data link, and physical. And if you wanted to roll that into a single sentence, you would remember- All People Seem To Need Data Processing, which refers to application, presentation, session, transport, network, data link, and physical ...
Learn ISO OSI 7 layer network model, OSI Stack, Open System Interconnection model or networking model. Application, Presentation, and Session layers are expl...
The presentation layer translates or formats data for the application layer based on the semantics or syntax the application accepts. This layer also handles the encryption and decryption that the application layer requires. Layer 5. The session layer. The session layer sets up, coordinates and terminates conversations between applications. Its ...
The OSI model includes the application, presentation, session, transport, network, data link, and physical layers. By using layers, we can separate the responsibilities of the network communication process, which makes things easier to troubleshoot. Learning each layer's responsibility helps us understand how our data is managed and transformed.
A quick tutorial on the Application, Presentation, and Session Layers of the OSI Model. Good basics for students studying for the CCNA
Data-link Layer (Layer 2) Network Layer (Layer 3) Transport Layer (Layer 4) Session Layer (Layer 5) Presentation Layer (Layer 6) Application Layer (Layer 7) As you can see, there are 7 layers in OSI Reference Model. The first four layers are the Lower Layers and the last three layers are Upper Layers.
The Presentation layer deals with the format of the data, it is there to abstract the meaning of the data as the application sees it into a standardised format that can be used by the underlying network layers. Where an application may be providing freeform text, the network needs a way of encoding it. An example of a protocol working at this ...
Session layer. The session layer is the one implementing one-to-one application sessions: it defines the re-transmission of data, the segment ordering method, and control the communication in general. All these features are covered by TCP for applications using that transport protocol, but applications that leverage UDP have to implement these ...
In going from OSI to TCP/IP, everything above TCP (OSI Layers 5-7) is considered the Application layer (TCP/IP Layer 4). From TCP/IP to OSI there can be a lot of disagreement over what falls into each of layers 5-7. To add to the complication there are protocols which span multiple layers, for example, Ethernet is both layer 1 AND 2 in the OSI ...
The presentation layer is responsible for formatting and converting data and ensuring that the data is presentable for one application through the network to another application. The session layer is responsible for coordinating communication interactions between applications. The reliable transport layer is responsible for segmenting and ...
Prerequisite : OSI Model Introduction : Presentation Layer is the 6th layer in the Open System Interconnection (OSI) model. This layer is also known as Translation layer, as this layer serves as a data translator for the network. The data which this layer receives from the Application Layer is extracted and manipulated here as per the required format to transmit over the network.
Application layer protocols are used to exchange data between programs running on the source and destination hosts. Based on the TCP/IP model, the upper three layers of the OSI model (application, presentation, and session) define functions of the TCP/IP application layer. There are many application layer protocols, and new protocols are always ...