
- school Campus Bookshelves
- menu_book Bookshelves
- perm_media Learning Objects
- login Login
- how_to_reg Request Instructor Account
- hub Instructor Commons

Margin Size
- Download Page (PDF)
- Download Full Book (PDF)
- Periodic Table
- Physics Constants
- Scientific Calculator
- Reference & Cite
- Tools expand_more
- Readability
selected template will load here
This action is not available.

1.9: Case Study - Mapping the Internet to the Ethernet
- Last updated
- Save as PDF
- Page ID 58494

- Jerome H. Saltzer & M. Frans Kaashoek
- Massachusetts Institute of Technology via MIT OpenCourseWare
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
This case study begins with a brief description of Ethernet using the terminology and network model of this chapter. It then explores the issues involved in routing that are raised when one maps a packet-forwarding network such as the Internet to an Ethernet.
A Brief Overview of Ethernet
Ethernet is the generic name for a family of local area networks based on broadcast over a shared wire or fiber link on which all participants can hear one another's transmissions. Ethernet uses a listen-before-sending rule (known as "carrier sense") to control access and it uses a listen-while-sending rule to minimize wasted transmission time if two stations happen to start transmitting at the same time, an error known as a collision . This protocol is named Carrier Sense Multiple Access with Collision Detection , and abbreviated CSMA/CD. Ethernet was demonstrated in 1974 and documented in a 1976 paper by Metcalfe and Boggs [ Suggestions for Further Reading 1.1.3 ]. Since that time several successively higher-speed versions have evolved. Originally designed as a half duplex system, a full duplex, point-to-point specification that relaxes length restrictions was a later development. The primary forms of Ethernet that one encounters either in the literature or in the field are the following:
- Experimental Ethernet , a long obsolete 3 megabit per second network that was used only in laboratory settings. The 1976 paper describes this version.
- Standard Ethernet , a 10 megabit per second version.
- Fast Ethernet , a 100 megabit per second version.
- Gigabit Ethernet , which operates at the eponymous speed.
Standard, fast, and gigabit Ethernet all share the same basic protocol design and format. The format of an Ethernet frame (with some subfield details omitted) is:
The leader field contains a standard bit pattern that frames the payload and also provides an opportunity for the receiver’s phase-locked loop to synchronize. The destination and source fields identify specific stations on the Ethernet. The type field is used for protocol multiplexing in some applications and to contain the length of the data field in others. (The format diagram does not show that each frame is followed by 96 bit times of silence, which allows finding the end of the frame when the length field is absent.)
The maximum extent of a half duplex Ethernet is determined by its propagation time; the controlling requirement is that the maximum two-way propagation time between the two most distant stations on the network be less than the 576 bit times required to transmit the shortest allowable packet. This restriction guarantees that if a collision occurs, both colliding parties are certain to detect it. When a sending station does detect a collision, it waits a random time before trying again; when there are repeated collisions it uses exponential backoff to increase the interval from which it randomly chooses the time to wait. In a full duplex, point-to-point Ethernet there are no collisions, and the maximum length of the link is determined by the physical medium.
There are many fascinating aspects of Ethernet design and implementation ranging from debates about its probabilistic character to issues of electrical grounding; we omit all of them here. For more information, a good place to start is with the paper by Metcalfe and Boggs. The Ethernet is completely specified in a series of IEEE standards numbered 802.3, and it is described in great detail in most books devoted to networking.
Broadcast Aspects of Ethernet
Section 1.4.5 of this chapter mentioned Ethernet as an example of a network that uses a broadcast link. As illustrated in Figure \(\PageIndex{1}\), the Ethernet link layer is quite simple: every frame is delivered to every station. At its network layer, each Ethernet station has a 48 bit address, which to avoid confusion with other addresses we will call a station identifier. (To help reduce ambiguity in the examples that follow, station identifiers will be the only two-digit numbers.)
.png?revision=1)
Figure \(\PageIndex{1}\): An Ethernet.
The network layer of Ethernet is quite simple. On the sending side, ETHERNET_SEND does nothing but pass the call along to the link layer. On the receiving side, the network handler procedure of the Ethernet network layer is straightforward:
procedure ETHERNET_HANDLE ( net_packet , length ) destination ← net_packet.target_id if destination = my_station_id then GIVE_TO_END_LAYER ( net_packet.data , net_packet.end_protocol , net_packet.source_id ) else ignore packet
There are two differences between this network layer handler and the network layer handler of a packet-forwarding network:
- Because the underlying physical link is a broadcast link, it is up to the network layer of the station to figure out that it should ignore packets not addressed specifically to it.
- Because every packet is delivered to every Ethernet station, there is no need to do any forwarding.
Most Ethernet implementations actually place ETHERNET_HANDLE completely in hardware. One consequence is that the hardware of each station must know its own station identifier, so it can ignore packets addressed to other stations. This identifier is wired in at manufacturing time, but most implementations also provide a programmable identifier register that overrides the wired-in identifier.
Since the link layer of Ethernet is a broadcast link, it offers a convenient additional opportunity for the network layer to create a broadcast network . For this purpose, Ethernet reserves one station identifier as a broadcast address , and the network handler procedure acquires one additional test:
procedure ETHERNET_HANDLE ( net_packet , length ) destination ← net_packet.target_id if destination = my_station_id or destination = BROADCAST_ID then GIVE_TO_END_LAYER ( net_packet.data , net_packet.end_protocol , net_packet.source_id ) else ignore packet
The Ethernet broadcast feature is seductive. It has led people to propose also adding broadcast features to packet-forwarding networks. It is possible to develop broadcast algorithms for a forwarding network, but it is a much trickier business. Even in Ethernet, broadcast must be used judiciously. Reliable transport protocols that require every receiving station to send back an acknowledgment lead to a problematic flood of acknowledgment packets. In addition, broadcast mechanisms are too easily triggered by mistake. For example, if a request is accidentally sent with its source address set to the broadcast address, the response will be broadcast to all network attachment points. The worst case is a broadcast sent from the broadcast address, which can lead to a flood of broadcasts. Such mechanisms make a good target for malicious attack on a network, so it is usually thought to be preferable not to implement them at all.
Layer Mapping: Attaching Ethernet to a Forwarding Network
Suppose we have several workstations and perhaps a few servers in one building, all connected using an Ethernet, and we would like to attach this Ethernet to the packet-forwarding network illustrated in Figure \(1.5.4\) from Section 1.5.2 , by making the Ethernet a sixth link on router \(K\) in that figure. This connection produces the configuration of Figure \(\PageIndex{2}\).
There are three kinds of network-related labels in the figure. First, each link is numbered with a local single-digit link identifier (in \(italics\)), as viewed from within the station that attaches that link. Second, as in Figure \(\PageIndex{1}\), each Ethernet attachment point has a two-digit Ethernet station identifier. Finally, each station has a one-letter name, just as in the packet-forwarding network in the figure from Section 1.5.2 . With this configuration, workstation \(L\) sends a remote procedure call to server \(N\) by sending one or more packets to station 18 of the Ethernet attached to it as link number \(1\).
.png?revision=1)
Figure \(\PageIndex{2}\): Connecting an Ethernet to a packet forwarding network.
Workstation \(L\) might also want to send a request to the computer connected to the destination \(E\), which requires that \(L\) actually send the request packet to router \(K\) at Ethernet station 19 for forwarding to destination \(E\). The complication is that \(E\) may be at address 15 of the packet-forwarding network, while workstation \(M\) is at station 15 of the Ethernet. Since Ethernet station identifiers may be wired into the hardware interface, we probably can’t set them to suit our needs, and it might be a major hassle to go around changing addresses on the original packet-forwarding network. The bottom line here is that we can’t simply use Ethernet station identifiers as the network addresses in our packet-forwarding network. But this conclusion seems to leave station \(L\) with no way of expressing the idea that it wants to send a packet to address \(E\).
We were able to express this idea in words because in the two figures we assigned a unique letter identifier to every station. What our design needs is a more universal concept of network—a cloud that encompasses every station in both the Ethernet and the packet-forwarding network and assigns each station a unique network address. Recall that the letter identifiers originally stood for addresses in the packet-forwarding network; they may even be hierarchical identifiers. We can simply extend that concept and assign identifiers from that same numbering plan to each Ethernet station, in addition to the wired-in Ethernet station identifiers.
What we are doing here is mapping the letter identifiers of the packet-forwarding network to the station identifiers of the Ethernet. Since the Ethernet is itself decomposable into a network layer and a link layer, we can describe this situation, as was suggested in Section 1.3.6 , as a mapping composition—an upper-level network layer is being mapped to lower-level network layer. The upper network layer is a simplified version of the Internet, so we will label it with the name "internet," using a lower case initial letter as a reminder that it is simplified. Our internet provides us with a language in which workstation \(L\) can express the idea that it wants to send an RPC request to server \(E\), which is located somewhere beyond the router:
NETWORK_SEND ( data , length , RPC, INTERNET, E )
where \(E\) is the internet address of the server, and the fourth argument selects our internet forwarding protocol from among the various available network protocols. With this scheme, station \(A\) also uses the same network address \(E\) to send a request to that server. In other words, this internet provides a universal name space.
Our new, expanded, internet network layer must now map its addresses into the Ethernet station identifiers required by the Ethernet network layer. For example, when workstation \(L\) sends a remote procedure call to server \(N\) by
NETWORK_SEND ( data , length , RPC, INTERNET, N )
the internet network layer must turn this into the Ethernet network-layer call
NETWORK_SEND ( data , length , RPC, ENET, 18 )
in which we have named the Ethernet network-layer protocol ENET .
For this purpose, \(L\) must maintain a table like Table \(\PageIndex{2}\), in which each internet address maps to an Ethernet station identifier. This table maps, for example, address \(N\) to ENET , station 18, as required for the NETWORK_SEND call above. Since our internet is a forwarding network, our table also indicates that for address \(E\) the thing to do is send the packet on ENET to station 19, in the hope that it (a router in our diagram) will be sufficiently well connected to pass the packet along to its destination. This table is just another example of a forwarding table like the ones in Section 1.5 of this chapter.
The Address Resolution Protocol
The forwarding table could simply be filled in by hand, by a network administrator who, every time a new station is added to an Ethernet, visits every station already on that Ethernet and adds an entry to its forwarding table. But the charm of manual network management quickly wears thin as the network grows in number of stations, and a more automatic procedure is usually implemented.
An elegant scheme, known as the address resolution protocol (ARP) , takes advantage of the broadcast feature of Ethernet to dynamically fill in the forwarding table as it is needed. Suppose we start with an empty forwarding table and that an application calls the internet NETWORK_SEND interface in \(L\), asking that a packet be sent to internet address \(M\). The internet network layer in \(L\) looks in its local forwarding table, and finding nothing there that helps, it asks the Ethernet network layer to send a query such as the following:
NETWORK_SEND (“where is M ?”, 11, ARP, ENET, BROADCAST)
where 10 is the number of bytes in the query, ARP is the network-layer protocol we are using, rather than INTERNET , and BROADCAST is the station identifier that is reserved for broadcast on this Ethernet.
Since this query uses the broadcast address, it will be received by the Ethernet network layer of every station on the attached Ethernet. Each station notices the ARP protocol type and passes it to its ARP handler in the upper network layer. Each ARP handler checks the query, and if it discovers its own internet address in the inquiry, sends a response:
NETWORK_SEND (“ M is at station 15”, 18, ARP, ENET, BROADCAST)
At most, one station—the one whose internet address is named by the ARP request—will respond. All the others will ignore the ARP request. When the ARP response arrives at station 17, that station's Ethernet network layer will pass it up to the ARP handler in its upper network layer, which will immediately add an entry relating address \(M\) to station 15 to its forwarding table, shown below. The internet network handler of station 17 can now proceed with its originally requested send operation.
Suppose now that station \(L\) tries to send a packet to server \(E\), which is on the internet but not directly attached to the Ethernet. In that case, server \(E\) does not hear the Ethernet broadcast, but the router at station 19 does, and it sends a suitable ARP response instead. The forwarding table then has a second entry as shown below. Station \(L\) can now send the packet to the router, which presumably knows how to forward the packet to its intended destination.
One more step is required—the server at \(E\) will not be able to reply to station \(L\) unless \(L\) is in its own forwarding table. This step is easy to arrange: whenever router \(K\) hears, via ARP , of the existence of a station on its attached Ethernet, it simply adds that internet address to the list of addresses that it advertises, and whatever routing protocol it is using will propagate that information throughout the internet. If hierarchical addresses are in use, the region designer might assign a region number to be used exclusively for all the stations on one Ethernet, to simplify routing.
Mappings from Ethernet station identifiers to the addresses of the higher network level are thus dynamically built up, and eventually station \(L\) will have the full table shown in Table \(\PageIndex{2}\). Typical systems deployed in the field have developed and refined this basic set of dynamic mapping ideas in many directions: The forwarding table is usually managed as a cache, with entries that time out or can be explicitly updated, to allow stations to change their station identifiers; the ARP response may also be noted by stations that didn’t send the original ARP request for their own future reference; a newly-attached station may, without being asked, broadcast what appears to be an ARP response simply to make itself known to existing stations (advertising); and there is even a reverse version of the ARP protocol that can be used by a station to ask if anyone knows its own higher-level network address, or to ask that a higher-level address be assigned to it. These refinements are not important to our case study, but many of them are essential to smooth network management.
Help | Advanced Search
Computer Science > Software Engineering
Title: modeling network architecture: a cloud case study.
Abstract: The Internet s ability to support a wide range of services depends on the network architecture and theoretical and practical innovations necessary for future networks. Network architecture in this context refers to the structure of a computer network system as well as interactions among its physical components, their configuration, and communication protocols. Various descriptions of architecture have been developed over the years with an unusually large number of superficial icons and symbols. This situation has created a need for more coherent systematic representations of network architecture. This paper is intended to refine the design, analysis, and documentation of network architecture by adopting a conceptual model called a thinging (abstract) machine (TM), which views all components of a network in terms of a single notion: the flow of things in a TM. Since cloud computing has become increasingly popular in the last few years as a model for a shared pool of networks, servers, storage, and applications, we apply the TM to model a real case study of cloud networks. The resultant model introduces an integrated representation of computer networks.
Submission history
Access paper:.
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
DBLP - CS Bibliography
Bibtex formatted citation.
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
Case Study in Computer Design
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
- Skip to content
- Skip to search
- Skip to footer

The network drives our business
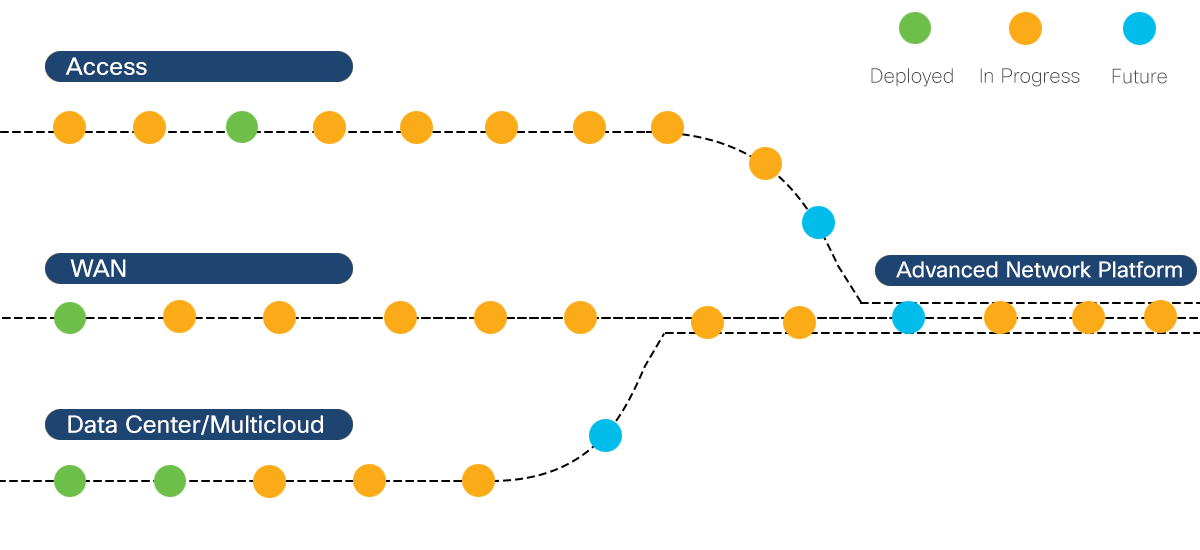
Cisco's network is made up of systems that address the unique needs of each place in the network, connected by a common infrastructure. These systems help us speed new technology, protect network and data integrity, and improve employee productivity.
- See our IBN journey
Cisco IT Road to Intent-Based Networking
Cisco it shares insights and lessons learned from our own ongoing network transformation journey across access, wan, and data center/cloud..
In Progress
Mobile workplace
Flexible collaborative workplace designed to improve productivity and optimize workspace resources.
Telework/BYOD
Telework/ BYOD
AnyDevice program enabling employees to choose and own their own device, and secure it for safe business use.
Scalable access policy.
Cisco Software-Defined Access (SD-Access) for simplified, centralized, and automated policy management across converged LAN and Campus networks.
Work from anywhere.
Secure, seamless roaming across corporate and public Wi-Fi and mobile (LTE/5G) networks.
Coming soon..
Network segmentation
Automated, policy-based segmentation across campus and branch access networks for security, agility, and policy enablement within between and segments.
Ai-enabled analytics.
Artificial Intelligence and Machine Learning to provide accurate insights for reactive and proactive event management and faster remediation.
Iot/human telemetry.
Employing wireless and sensors to collect location and state information from people and devices for better workplace safety and efficiency and resource management.
Itsm integration.
Integration of full IT Service Management (in Cisco, ServiceNow / Cisco ESP) with other automated management systems for end to end infrastructure inventory...
AI-enabled policy automation
AI-enabled automation of intent translation, application classification and application performance policy creation and activation.
Autonomous access
Full cycle automation for onboarding all users and devices on any part of the private or public network, including user and deivce identification, authentication and policy definition and activation.
Combined WAN supporting voice, video and data across hybrid network connections for efficiency and cost.
CoLo enterprise backbone
A new WAN architecture (CloudPort) with Internet access & Security / WAN hub in CoLo Carrier Neutral Facility (CNF).
Cloud backbone.
Dual parallel backbone WAN of Leased and Internet connections enabling QoS route selection and overall lower cost.
Secure automated sd-wan.
Cisco Software-Defined WAN (SD-WAN) for simplified, centralized, and automated policy management of virtual overlay WANs across any WAN circuit(s).
Secure multi-cloud access
Secure multi-cloud access (SIG/SASE)
Multiple security functions integrated in one cloud service; flexibility to deploy security services how and where you choose; ability to secure direct-to-internet access...
View more >
WAN AI analytics
Provide AI-enabled insights across WAN, Internet and Cloud connections for reactive and proactive application service level optimization.
Autonomous WAN
AI / ML guided, fully reactive and proactive WAN as a Service automation.
Autonomous multi-cloud
Fully automated cloud-connected, SaaS/IaaS-connected WAN / Core as a Service.
E2e segmentation, automated policy-based segmentation for any user or device anywhere to any application or workload anywhere., e2e policy automation, automated policy-based application optimization for any user or device anywhere to any application anywhere., e2e assurance.
End to end application service monitoring and assurance with AI-enabled predictive trouble shooting and remediation.
E2e closed loop ibn.
End to end intent-based networking continuously aligns network to meet changing business needs, application requirements and user experience.
Data Center/Multicloud
Private cloud network.
CITEIS first generation private cloud VMWare IaaS / OpenShift PaaS cloud environment.
Elastic xaas.
Full service private cloud - supporting OpenStack, KVM Docker containers & Kubernetes, with full PaaS support for multiple combinations of Dev/Sec/Ops...
Automatation DC Network Operations
Automated DC network operations(ACI/ Segmentation)
A Software-Defined data center infrastructure, policy-based deployment and white-list security.
DC network assurance (NI)
Cisco network assurance engine helps network operations teams meet the agility, uptime, and security policy compliance requirements of modern data center networks., multicloud workload simplification.
Automate and assure consistent network policies for your distributed applications across multicloud environments.
Multicloud Workload Optimisation
Multicloud network workload optimization
Simplify network operations with policy automation and insights for your distributed application, managed centrally across your multicloud environment.

A flexible collaborative workplace designed to improve productivity and optimize workspace resources.
Prior to the 2020 pandemic, more than 70% of employees worked from home at least one day a week. this meant that on any given day, only 50% of our office space was occupied. we redesigned our office space to efficiently accommodate different work styles based on advanced wireless and collaboration technologies..
Icon signifies an area of technology that is continuously refreshed.
- Cisco Wi-Fi
- Cisco Collaboration
Related links:
- Cisco Connected Workplace: More Productivity and Satisfaction, Less Office Space and CO2
- Preparing the Enterprise for Wi-Fi 6
Cisco has gained multiple business benefits from secure mobility, starting with our first implementation of a WLAN in 2000, through VPN connectivity, Mobile Device Management (MDM), and the redesigned office spaces and BYOD policies of recent years. Learn about the benefits and details regarding what we have implemented in our mobility journey.
- Cisco AnyConnect
- Cisco Meraki Systems Manager (MDM)
- Five ways we’re improving telework with SD-WAN and telemetry
- Transforming the enterprise with secure mobility
- Mobile Device Management in the Meraki Cloud
- Scaling VPN when the global workforce moved home

Cisco IT manages thousands of switches and APs in more than 400 global offices. We’re always looking for ways to strengthen compliance with security policy, improve the user experience, and simplify our jobs to make more time for innovation. Enforcing security policies based on identity rather than location saves time for IT and gives people more flexibility to choose where they work.
- Cisco SD-Access
- Cisco DNA-Center Controller
- Catalyst 9K switches
- Cisco Aironet 4800 Wireless AP's
- Catalyst 9000 WLC's and AP's
- Measuring the impact of a software-defined access fabric network
- Journey to a software-defined access fabric network, part 2
- Journey to a software-defined access fabric network, part 1
- Secure flexible access with SD-Access
OpenRoaming will provide our mobile users with frictionless onboarding and secure access to resources across private and public Wi-Fi and 5G networks. Users need to sign on only once with a trusted identity provider. Afterward, they will be automatically connected to OpenRoaming networks whenever and wherever one is available.
- Cisco OpenRoaming
- Coming soon...
Enforcing security policies and automated segmentation based on identity rather than location saves time for IT, protects resources, and gives people more flexibility to choose where they work.
- Cisco Catalyst Center
- Cisco Identity Services Engine (ISE)
5 ways automating software image management is making Cisco IT engineers’ lives better
- Cisco Catalyst Center smooths network operations
By applying advanced analytics and machine learning across our own Data Center, WAN, and Access networks public Internet and Cloud networks we will be able to empower administrators to significantly improve performance and issue resolution.
- Cisco Catalyst Center Assurance
- Cisco vManage/vAnalytics
- Cisco Meraki Dashboard
- Cisco ThousandEyes
- Cisco IT—our future network
Employee safety is top of mind as we gradually welcome employees back to Cisco offices across the globe. Before allowing employees to return, our Workplace Resources team wants to make sure employees are practicing social distancing—not standing or sitting too close or gathering in large groups. Our network is vital in ensuring the resumption of safe, productive, and collaborative work.
- Cisco DNA Spaces
- Cisco Aironet APs
- Cisco Catalyst 9K APs
- Managing a safer return to work with Cisco DNA Spaces — An early report
- Helping to keep employees safe
Integration of full IT Service Management (in Cisco, ServiceNow / Cisco ESP) with other automated management systems for end to end infrastructure inventory and status management.
We are integrating our network controller systems ad itsm system in multiple ways to make it easier to find the right information to solve problems, streamline tasks for network changes, and allow routine operational tasks to run autonomously in an end-to-end automated workflow..
- Cisco DevNet
- 3 ways Cisco Catalyst Center and ServiceNow integration makes IT more efficient
- Using Catalyst Center as a Platform
AI-enabled automation of intent translation, application classification, and application performance policy creation and activation.
With low cost, fixed form factor iot endpoints becoming increasingly prevalent on our networks, there is an urgent need to automate identification and apply access policies. we need an automated method of finding, identifying, segmenting, and monitoring traffic for all types of connected devices..
- Cisco Catalyst Center AI Endpoint Analytics
Full cycle automation for onboarding all users and devices to any part of the private or public network, including user and device identification, authentication, and policy activation.
- Cisco Catalyst Center Policy Automation
To ensure consistently good voice, video and data application experiences for all users has traditionally required the integration of a comprehensive set of WAN traffic control and security features into our branch-office routers. Cisco IT has long used WAAS to optimize WAN bandwidth and improve performance for Cisco users when they access content-rich applications from remote offices.
- Cisco ISR 4000 Series Routers
- Secrets to Ensuring Application Performance at the Branch
- Reducing Cloud Application Bandwidth
IT must change WAN designs from centralized around internal DC to more disperse utilization of the ""Cloud"" and various Cloud Services. To do this Cisco IT has built secure CloudPorts in or near Carrier Neutral facilities which enable optimized connectivity to Cloud resources and allow to quickly & securely interconnect clouds.
- Cisco Catalyst 9K
- Cisco Nexus 7K
- Cisco Firepower
- Cisco IT Multicloud Backbone Securely Inter-connecting Clouds
In this age of multicloud, Cisco IT realized we needed a new WAN backbone that will allow us to operate more like a service provider for our internal clients. Built on the Cisco ASR 9000 Series Aggregation Services Routers running Cisco IOS-XR software, this highly scalable and programmable router provides a strong foundation for access to and between increasingly distributed applications and users.
- Cisco ASR 9K
- Cisco FirePower 9300s
- Cisco CSP 21xx & 55xx
- Cisco SD-WAN Cloud OnRamp
- How the network team’s bold steps + agile mindset launched a cloud-ready backbone
- As the Landscape Evolves, so must the Enterprise Backbone
We’re becoming a true multi-cloud company. We use almost 1000 cloud services, including Cisco Webex, Salesforce, Office365, and Box. Currently, more than 25% of traffic from our campuses and branch offices heads to public clouds. So we needed more capacity, operational consistency, and agility to keep delivering a great application experience to employees in our 450 branch offices.
- Cisco vManage
- ASR-1002-HX
- Meraki SD-WAN
- A simpler, more flexible SD-WAN design for branches, from Customer Zero. Top five benefits
- Network of the Future, Today. How We’re Growing WAN Capacity While Optimizing Costs
Multiple security functions integrated into one cloud service; the flexibility to deploy security services how and where you choose; ability to secure direct-to-internet access, cloud app usage, and roaming users; plus, no appliances to deploy.
- The SASE Story III
- The SASE Story II
- The SASE Story I
Provide AI-enabled insights across WAN, Internet, and Cloud connections for reactive and proactive application service-level optimization.
- Cisco AppDynamics
- Employees do their own performance troubleshooting with ThousandEyes
- Zeroing in on network performance issues with ThousandEyes
- Simple way to measure user experience? ThousandEyes on Raspberry Pis
AI / ML guided, fully reactive, and proactive WAN as a Service automation.
Ai-enabled sd-wan uses insights to identify application performance impacting network issues and dynamically takes action to achieve performance enhancements. it uses apm, public network telemetry, and sd-wan analytics to ensure a proactive response to dynamic network, application, and security conditions., a fully automated lifecycle for multicloud networking enabling agile and secure workload management and access. • applications: workloads including modern architectures composed of microservices and containers, supported by an agile, flexible, and elastically scalable network that delivers consistent and simple provisioning, management, and security. • access: highly available and responsive access to applications (including on premises, iaas, and saas) delivered with consistent security, reliability, and performance to users and devices anywhere..
- Cisco Multicloud Networking
- How Cisco IT is solving multi-cloud management: a single pane of glass
Automated policy-based segmentation consistently across all network domains (access, WAN, DC, multicloud). Allows automated zero-trust on-boarding, categorization, and access to only authorized resources.
End-to-end activation of stated business intent and application performance requirements from user or device to and between workloads consistently across all network domains (access, wan, dc, multicloud)..
- Cisco Nexus Dashboard
- Cisco Intersight
True end-to-end application visibility and assurance of stated business intent and policy from user or device to applications or between workload consistently across all network domains (access, WAN, DC, multicloud).
- Cisco ThousandEye
End to end intent-based networking continuously aligns the network to meet changing business needs, application requirements, and user experience demands.
In 2013 the cisco it elastic infrastructure services program, or citeis, was our internal implementation of infrastructure as a service (iaas) and platform as a service (paas) resources in a private cloud. citeis was designed to provide a consumer-type it experience to our developers while cisco it maintains governance and control over the infrastructure..
- Cisco IT Best Practices for Creating a Private Cloud
Full service private cloud - supporting OpenStack, KVM Docker containers & Kubernetes, with full PaaS support for multiple combinations of Dev/Sec/Ops platform tools for app designers.
In 2018 we extended the concepts behind citeis to an expanded internal cisco it cloud’s compute and storage service. this service is built upon a new private-cloud infrastructure utilizing cisco unified computing system™ (cisco ucs®) c-series servers and cisco application-centric infrastructure (aci), as well as openstack and other open-source software..
- Offering an Internal Cloud Service
Automated DC network operations (ACI/Segmentation)
A software-defined data center infrastructure, policy-based deployment, and white-list security., by moving our platform as a service (paas) application development and dev/ops private cloud to our aci fabric we are bringing greater automation, security, ease of use and cost-savings to our it data center infrastructure through open source and open apis..
- Cisco Nexus 9Ks
- Cisco Nexus 1000v
- Cisco UCS Manager
- Cisco UCS Director
- Cisco IT Nearing Final Phase of ACI Journey
Cisco IT uses NAE to transform ACI network operations from a reactive posture to a highly proactive approach. This approach substantially drives down MTTR for incidents, shrinks change windows, and optimizes planning in large scale data centers.
- Cisco Network Assurance Engine
- Cisco IT Advances Proactive, Predictive Operations with Cisco Nexus Dashboard
- Cisco IT Cisco Network Assurance Engine Deployment
Cisco is extending existing policies, governing tenants or workloads, across network fabrics that traverse on-premises and cloud environments, with centralized policy provisioning and management applied consistently across this multicloud network.
- Cisco Cloud ACI
Simplify network operations with policy automation and insights for your distributed applications, managed centrally across your multicloud environment
- Cisco Network Insights
- Explore journey
- Show overview
IT networking stories

Providing secure, easy access to the corporate network from anywhere, at any time, on any device.
Preparing the enterprise for Wi-Fi 6
Migrating to a new Cisco wireless infrastructure
Automating Cisco home and remote access router updates
Cost-effective connectivity for small offices

Connecting branches to data centers and multi-cloud environments through a single fabric.
Bringing SD-WAN to Our Branch Offices: Our Journey and Lessons Learned
Go anywhere with Catalyst 9000s

Software-defined network
Delivering a centralized, programmable network, making it more flexible and easier to manage
Cisco Catalyst Center: early results from intent-based networking
Using Cisco Catalyst Center for network as a platform
SDN and its role in automating and scaling in the data center
- Read all networking stories
Meet the IT bloggers
Read the latest news on what's happening in Cisco IT from those on the front lines. Read more

Zeroing in on network performance issues, with ThousandEyes
Network performance metrics for every hop from the branch to the cloud? They're at our fingertips, with ThousandEyes Enterprise Agent on Catalyst 9000 switches.

Journey Map – all paths lead to an intent-based network
Check out Cisco IT's interactive journey map to Intent-Based Networking. We share insights and lessons learned from our own ongoing network transformation journey.

Cisco IT is automating many steps in the device software upgrade process by leveraging the SWIM capability in Cisco Catalyst Center.
- Visit other IT blogs

Cisco retail store of the future
Cisco is updating an outdated retail space on its main campus with technologies that make the space easier to shop, easier to run, and capable of learning from customers.
- Cisco store and smart cameras (6:44)
Catalyst 9K in North Sydney
By deploying Catalyst 9000 on a parallel network, IT can learn about real-world challenges within the company and get a firsthand perspective of what Cisco customers experience.
- Catalyst 9K in North Sydney (7:57)

4800 access points | customer zero
We go behind the scenes to track a real-life product deployment of Cisco Aironet 4800 access points in Charlotte, North Carolina, with a few members of our IT staff.
- 4800 access points (8:03)

- Computers & Technology
- Networking & Cloud Computing

Download the free Kindle app and start reading Kindle books instantly on your smartphone, tablet, or computer - no Kindle device required .
Read instantly on your browser with Kindle for Web.
Using your mobile phone camera - scan the code below and download the Kindle app.

Image Unavailable

- To view this video download Flash Player
Network Design and Case Studies (CCIE Fundamentals) (2nd Edition) Subsequent Edition
Authorized preparation materials for CCIE candidates.
- Prepare for the CCIE lab exam while mastering essential protocols and technologies
- Learn new design and configuration strategies for ATM, IP multicasting, network management, switching architectures, CIP, and network security
- Implement practical networking techniques to build scalable, reliable, and secure networks
- Learn to identify key technologies and appropriate implementations for your internetwork design
Cisco CCIE Fundamentals: Network Design and Case Studies, Second Edition offers a comprehensive collection of updated configuration scenarios and design recommendations. By reading this book, you will gain insight into the implementation of practical internetworking strategies, identify features and capabilities of routers and switches, and begin the process of mastering the technologies and protocols necessary to become an effective Cisco Certified Internetwork Expert (CCIE).
This two-part book is the compilation of design and configuration examples authored and previously released by Cisco Systems. Numerous subject matter experts have revised and restructured each chapter and added coverage of several new topics.
The design guide portion of this book is intended to support the network engineer who designs and implements router-based or switched internetworks. Practical design recommendations include coverage of large-scale networks with IGPs and BGP, ATM, APPN, DLSw+, DDR, ISDN, LAN switching, multicast networks, and more. The case study portion of this book presents real-world configurations that complement the design material. Implementation and troubleshooting advice is offered for EIGRP and OSPF redistribution, ATM, DDR, ISDN, network security, and HSRP.
- ISBN-10 1578701678
- ISBN-13 978-1578701674
- Edition Subsequent
- Publisher Cisco Systems
- Publication date October 19, 1999
- Language English
- Dimensions 7.5 x 2.5 x 9 inches
- Print length 1000 pages
- See all details

Editorial Reviews
From the back cover, about the author, product details.
- Publisher : Cisco Systems; Subsequent edition (October 19, 1999)
- Language : English
- Hardcover : 1000 pages
- ISBN-10 : 1578701678
- ISBN-13 : 978-1578701674
- Item Weight : 4.27 pounds
- Dimensions : 7.5 x 2.5 x 9 inches
- #201 in ISDN Networking
- #987 in LANs (Books)
- #3,957 in Computer Networking (Books)
Customer reviews
Customer Reviews, including Product Star Ratings help customers to learn more about the product and decide whether it is the right product for them.
To calculate the overall star rating and percentage breakdown by star, we don’t use a simple average. Instead, our system considers things like how recent a review is and if the reviewer bought the item on Amazon. It also analyzed reviews to verify trustworthiness.
- Sort reviews by Top reviews Most recent Top reviews
Top reviews from the United States
There was a problem filtering reviews right now. please try again later..
- Amazon Newsletter
- About Amazon
- Accessibility
- Sustainability
- Press Center
- Investor Relations
- Amazon Devices
- Amazon Science
- Sell on Amazon
- Sell apps on Amazon
- Supply to Amazon
- Protect & Build Your Brand
- Become an Affiliate
- Become a Delivery Driver
- Start a Package Delivery Business
- Advertise Your Products
- Self-Publish with Us
- Become an Amazon Hub Partner
- › See More Ways to Make Money
- Amazon Visa
- Amazon Store Card
- Amazon Secured Card
- Amazon Business Card
- Shop with Points
- Credit Card Marketplace
- Reload Your Balance
- Amazon Currency Converter
- Your Account
- Your Orders
- Shipping Rates & Policies
- Amazon Prime
- Returns & Replacements
- Manage Your Content and Devices
- Recalls and Product Safety Alerts
- Conditions of Use
- Privacy Notice
- Consumer Health Data Privacy Disclosure
- Your Ads Privacy Choices
- Generative AI
- Office Suites
- Collaboration Software
- Productivity Software
- Augmented Reality
- Emerging Technology
- Remote Work
- Artificial Intelligence
- Operating Systems
- IT Leadership
- IT Management
- IT Operations
- Cloud Computing
- Computers and Peripherals
- Data Center
- Enterprise Applications
- Vendors and Providers
- Enterprise Buyer’s Guides
- United States
- Netherlands
- United Kingdom
- New Zealand
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Copyright Notice
- Member Preferences
- About AdChoices
- E-commerce Affiliate Relationships
- Your California Privacy Rights
Our Network
- Network World
- Case studies in network and systems management
These case studies exemplify how corporate IT departments are using new tools and approaches to managing their networks and servers.
Mandarin Oriental Hotel Group , a unit of Mandarin Oriental International Ltd., Hong Kong
Mission: Owner and operator of 18 luxury hotels on three continents, in locations such as Hong Kong, London, Geneva, Bermuda, Bangkok and Singapore.
Challenge: As the hotel chain grew from its Asian base to other continents, it needed a way to manage its growing network, build its infrastructure quickly and remain agile — with little capital investment, says Nick Price, director of technology (the equivalent of a CIO) at Mandarin Oriental Hotel Group in Hong Kong.
Technology: To meet those goals, the hotel group decided to outsource network management to InteQ Corp. , a managed services provider in Bedford, Mass. The vendor’s InfraService offering monitors the hotel group’s servers, applications and network devices and remotely resolves problems. (The hotel group uses an Internet-based virtual private network because of the geographic dispersion.) The Web-based interface provides a window to how the network is doing, offers real-time alerts and demonstrates the value of the service to upper management.
Payoff: “InteQ did what would have taken us two years to do,” says Geoff McClelland, vice president of technology for hotel development, based in Sydney, Australia. And it would be hard for the hotel group to maintain the high-caliber staff expertise that InteQ has, McClelland adds.
Intellinex LLC , an independent business unit launched by Ernst & Young International, Cleveland
Mission: Intellinex provides sophisticated online and multimedia educational programs for major corporate clients.
Challenge: An e-learning division that catered to 30,000 people within Ernst & Young was spun off into a company serving 175,000 people — but its IT infrastructure couldn’t handle that scale, says Mark Bockeloh, Intellinex’s chief technology officer, who is based in Las Calinas, Texas. The training programs are full of multimedia content such as streaming video, and have complex, dynamic features like bookmarking the student’s place in an online course and providing different paths through the course depending on how the student answers the questions. In addition, there are registration and scheduling chores.
Technology: Intellinex obtained San Mateo, Calif.-based MetiLinx Inc. ‘s iSystem Enterprise server optimization and management software. The suite determines the transaction mix on the servers and optimizes the traffic in real time, finding the best route and the best server to handle it, Bockeloh says. “It routes the work to the server with the greatest health, which might be Machine 10 in Miami, and then routes it to Miami,” he says.
Payoff: The result of the optimization is “46% more throughput, and no downtime,” Bockeloh says, “and that means I don’t need 46% more hardware.”
Sony Online Entertainment Inc. , San Diego
Mission: This online gaming division of Sony Corp. runs “massively multiplayer” online games — including the blockbuster EverQuest — with more than 13 million registered users.
Challenge: Sony Online has more than 1,500 servers and 100,000 simultaneous players across three continents. The company needed a network monitoring tool that was inexpensive, easy to configure, easy to manage and easy to blend with custom applications that the gaming network uses, says Adam Joffe, vice president of IT. “Our custom applications wouldn’t fit real well with any of the standard network-monitoring packages that are out there,” he explains.
Technology: Sony Online selected NetVigil from Fidelia Inc. in Princeton, N.J. NetVigil is flexible and has open application programming interfaces “so we could plug in our own custom monitoring tools,” Joffe says.
Payoff: NetVigil was a better choice than larger network management packages, Joffe says. “They would have been overkill, and we’d have paid an awful lot of money for only certain features. NetVigil gives us a broad view of all of our devices — host and network devices. Other packages do either the network well or the host well, but not necessarily both,” he says.
- Taking Control
Stories in this report:
- The Story So Far: Network and Systems Management
- Coping with bandwidth hogs
- Field Report: Network and Systems Management Tools
- Simple Network Management Protocol
- Expediting Content Delivery
- How to Thrive in the Networking Market
- Partitioning: Your Mainframe becomes a Hotel for OS ‘Guests’
- Success With Content Delivery Networks Lies in the Planning
Related content
The mobile, distributed, future of work, the brilliant android breakthrough you didn’t hear about at google i/o, visa leverages ai to help retailers access more customer data, windows 11 insider previews: what’s in the latest build, from our editors straight to your inbox.
Mitch Betts is an executive editor at IDG Enterprise. He was previously executive editor of CIO and Computerworld magazines.
More from this author
Buyers’ guide: prices dropping for data visualization software, it service providers get low marks for innovation, two big mistakes cios make with digital strategy, how crm buyers can negotiate the best deal, most popular authors.

Show me more
Senators propose $32b on ai spending without firm regulatory oversight.

Meta signals the end of the road for Workplace

There aren't nearly enough workers to support new US chip production
Will new AI tools create a better Siri or voice assistant?

Is AI crushing creativity, or creating mediocrity?

Why AI hallucinations are here to stay


IMAGES
VIDEO
COMMENTS
Computer Networking: Case Study Analysis. By: GPDCM Jayasekara. 2. Case Overview. To understand the Local and Wide Area Network technologies, materials and protocols relate. them to develop ...
1.. IntroductionThis paper describes the outcomes of a novel design automation tool for optimizing network topology. Design automation (DA) is a field of study, which is focused on modeling system and developing software programs, known as a computer-aided design (CAD). For many years CAD tools are utilized in guiding and helping in the design of systems, which mainly comprise of integrated ...
Caching—one of our case study applications—had a median power variation of 9.2% over sixty seconds, with a 99th percentile of 26.2%. Other applica-tions, such as a web server, had a median power variation of 37.2% and a 99th percentile of 62.2%. The appropriateness of in-network computing depends on the power variance.
in which we have named the Ethernet network-layer protocol ENET. For this purpose, L L must maintain a table like Table 1.9.2 1.9. 2, in which each internet address maps to an Ethernet station identifier. This table maps, for example, address N N to ENET, station 18, as required for the NETWORK_SEND call above.
The topological studies are carried out by a custom-built evolutionary software tool that automatically selects, integrates and optimizes network devices into a 3-level network topology. The evolutionary tool searches the discrete design space for minimal 3-level hierarchy topology cost while satisfying the protocol translation and network ...
Modeling Network Architecture: A Cloud Case Study. Sabah Al-Fedaghi, Dana Al-Qemlas. The Internet s ability to support a wide range of services depends on the network architecture and theoretical and practical innovations necessary for future networks. Network architecture in this context refers to the structure of a computer network system as ...
This chapter contains sections titled: Design Principles Design Decisions Identification of System Elements Architectural Design Test Strategies Fau Case Study in Computer Design | part of Computer, Network, Software, and Hardware Engineering with Applications | Wiley-IEEE Press books | IEEE Xplore
Case Study in Computer Design. Norman F. Schneidewind, Naval Postgraduate School, USA. Search for more papers by this author. ... Computer, Network, Software, and Hardware Engineering with Applications. Related; Information; Close Figure Viewer. Return to Figure. Previous Figure Next Figure.
Retail company-A Case Study," IJCSNS International Journal of Computer Science and Network Security, vol. 12, no. 8, 2012 [5] X. Zhou, B. Li, Y. Qi, and W. Dong, "Mimic Encryption Box for Network ...
Chapter Description. This chapter from CCDA Exam Certification Guide reviews the topologies used in network design and covers the technologies and design approaches used when designing a local-area network (LAN). The hierarchical, redundant, and secure topology models are covered. Technologies like Ethernet, Fast Ethernet, FDDI, and Token Ring ...
This report will briefly explain the network topology of the "FranPyCisco.pvt ltd" Scenario, where targeting areas such as its relevant features/attributes applied, designed network, topology, main configurations applied, IP addressing, screenshots with related supportive evidence, background information, deep analysis on all aspects along ...
We have been asked to produce the network solutions for 3 different types of schools, with type 1 being a large school, type 2: a medium school and type 3: a small school. Explained below are our team's proposal for the project.
The network drives our business. Cisco's network is made up of systems that address the unique needs of each place in the network, connected by a common infrastructure. These systems help us speed new technology, protect network and data integrity, and improve employee productivity. See our IBN journey.
CCIE Fundamentals: Network Design and Case Studies, Second Edition provides a comprehensive collection of configuration scenarios and design recommendations tailored for CCIE preparation. Each chapter is a self-contained solution that presents insights into the implementation of practical networking strategies flexible enough to fit a variety ...
Isolate and solve problems easier with detailed configuration examples and case studies. Cisco CCIE Fundamentals: Network Design and Case Studies, Second Edition offers a comprehensive collection of updated configuration scenarios and design recommendations. By reading this book, you will gain insight into the implementation of practical ...
Here are the steps for designing a computer network for your business: Gather Requirements. Size Your Network. Study Your Office Floor Plan. Choose An Internet Service Provider (ISP) Create A Network Design. Document The Network Design. Follow Network Design Best Practices.
Analysis of user and network requirement has been done and the result design to implementing is hierarchical network design, high availability backbone, and users segmentation to all user with spreads on some building. Tarumanagara University already has a computer network infrastructure to support various activities both administrative and academic. Infrastructure that was built has been ...
FBLA NETWORK DESIGN CASE STUDY JUDGE'S INSTRUCTIONS JUDGING THE PRESENTATION 1. This is a team presentation event where the students will read a case study and present ... Diagrams and explanations of the physical network and computer design as well as the logical network design (server installation, domain layout, etc.) can also be included ...
A group of luxury hotels outsources network management. An e-learning company gets a 46% boost in server throughput. And an online gaming company finds a low-cost network monitoring tool that ...
SAMPLE CASE STUDY: NETWORK DESIGN CASE STUDY SITUATION You are interested in starting your own Music Store, QualitySounds, in a suburban area of your town. You ... Your plan should include a complete network and computer system that meets these requirements and future expansion plans. The two store locations will (eventually) be within a five ...