
An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
https://www.nist.gov/news-events/news/2022/07/nist-announces-first-four-quantum-resistant-cryptographic-algorithms

NIST Announces First Four Quantum-Resistant Cryptographic Algorithms
Federal agency reveals the first group of winners from its six-year competition..

GAITHERSBURG, Md. — The U.S. Department of Commerce’s National Institute of Standards and Technology (NIST) has chosen the first group of encryption tools that are designed to withstand the assault of a future quantum computer, which could potentially crack the security used to protect privacy in the digital systems we rely on every day — such as online banking and email software. The four selected encryption algorithms will become part of NIST’s post-quantum cryptographic standard, expected to be finalized in about two years.
“Today’s announcement is an important milestone in securing our sensitive data against the possibility of future cyberattacks from quantum computers,” said Secretary of Commerce Gina M. Raimondo. “Thanks to NIST’s expertise and commitment to cutting-edge technology, we are able to take the necessary steps to secure electronic information so U.S. businesses can continue innovating while maintaining the trust and confidence of their customers.”
The announcement follows a six-year effort managed by NIST, which in 2016 called upon the world’s cryptographers to devise and then vet encryption methods that could resist an attack from a future quantum computer that is more powerful than the comparatively limited machines available today. The selection constitutes the beginning of the finale of the agency’s post-quantum cryptography standardization project .
“NIST constantly looks to the future to anticipate the needs of U.S. industry and society as a whole, and when they are built, quantum computers powerful enough to break present-day encryption will pose a serious threat to our information systems,” said Under Secretary of Commerce for Standards and Technology and NIST Director Laurie E. Locascio. “Our post-quantum cryptography program has leveraged the top minds in cryptography — worldwide — to produce this first group of quantum-resistant algorithms that will lead to a standard and significantly increase the security of our digital information.”
Four additional algorithms are under consideration for inclusion in the standard, and NIST plans to announce the finalists from that round at a future date. NIST is announcing its choices in two stages because of the need for a robust variety of defense tools. As cryptographers have recognized from the beginning of NIST’s effort , there are different systems and tasks that use encryption, and a useful standard would offer solutions designed for different situations, use varied approaches for encryption, and offer more than one algorithm for each use case in the event one proves vulnerable.
“Our post-quantum cryptography program has leveraged the top minds in cryptography — worldwide — to produce this first group of quantum-resistant algorithms that will lead to a standard and significantly increase the security of our digital information.” —NIST Director Laurie E. Locascio
Encryption uses math to protect sensitive electronic information, including the secure websites we surf and the emails we send. Widely used public-key encryption systems , which rely on math problems that even the fastest conventional computers find intractable, ensure these websites and messages are inaccessible to unwelcome third parties.
However, a sufficiently capable quantum computer, which would be based on different technology than the conventional computers we have today, could solve these math problems quickly, defeating encryption systems. To counter this threat, the four quantum-resistant algorithms rely on math problems that both conventional and quantum computers should have difficulty solving, thereby defending privacy both now and down the road.
The algorithms are designed for two main tasks for which encryption is typically used: general encryption, used to protect information exchanged across a public network; and digital signatures, used for identity authentication. All four of the algorithms were created by experts collaborating from multiple countries and institutions.
For general encryption, used when we access secure websites, NIST has selected the CRYSTALS-Kyber algorithm. Among its advantages are comparatively small encryption keys that two parties can exchange easily, as well as its speed of operation.
For digital signatures, often used when we need to verify identities during a digital transaction or to sign a document remotely, NIST has selected the three algorithms CRYSTALS-Dilithium , FALCON and SPHINCS+ (read as “Sphincs plus”). Reviewers noted the high efficiency of the first two, and NIST recommends CRYSTALS-Dilithium as the primary algorithm, with FALCON for applications that need smaller signatures than Dilithium can provide. The third, SPHINCS+, is somewhat larger and slower than the other two, but it is valuable as a backup for one chief reason: It is based on a different math approach than all three of NIST’s other selections.
Three of the selected algorithms are based on a family of math problems called structured lattices, while SPHINCS+ uses hash functions. The additional four algorithms still under consideration are designed for general encryption and do not use structured lattices or hash functions in their approaches.
While the standard is in development, NIST encourages security experts to explore the new algorithms and consider how their applications will use them, but not to bake them into their systems yet, as the algorithms could change slightly before the standard is finalized.
To prepare, users can inventory their systems for applications that use public-key cryptography, which will need to be replaced before cryptographically relevant quantum computers appear. They can also alert their IT departments and vendors about the upcoming change. To get involved in developing guidance for migrating to post-quantum cryptography, see NIST’s National Cybersecurity Center of Excellence project page .
All of the algorithms are available on the NIST website .
Cryptography Research Group
Paul G. Allen School of Computer Science & Engineering University of Washington
The Cryptography Group in the Paul G. Allen School of Computer Science & Engineering carries out research on a wide range of topics in the foundations and applications of cryptography. These include public-key and symmetric cryptography, obfuscation, attribute-based and functional encryption, secure multi-party computation, zero-knowledge proofs, anonymous credentials, post-quantum and quantum cryptography, information-theoretic cryptography, and more.
We meet weekly for a reading group/seminar . Also subscribe to seattle-crypto for annoucements of cryptography-related events in the Seattle area.
Check out our cryptography classes .
Our research has been supported by NSF, DARPA, the Simons Foundation, the Sloan Foundation, CISCO, JP Morgan, and Microsoft.
Related groups: [UW Theory] [UW Security & Privacy] [MSR Cryptography, Security, and Privacy] [UW Blockchain Lab]

Graduate Students

Former Members
John Retterer Moore MS 2015
Wei Dai MS 2016 → UCSD (PhD) → Bain Capital Crypto (Research Partner)
Binyi Chen PhD 2019 → Google → Espresso Systems (Chief Cryptographer)
Michael Agun PhD 2019 → Western Digital
Pratik Soni PhD 2020 → CMU (postdoc) → University of Utah (Assistant Professor)
Xihu Zhang MS 2022 → Oracle
Ashrujit Ghoshal PhD 2022 → CMU (postdoc)
Viet Tung Hoang Postdoc 2015-16 → Florida State University ( Assistant Associate Professor)
Christian Matt Postdoc 2017-18 → Concordium (Senior Researcher)
Aishwarya Thiruvengadam Postdoc 2017-18 → TU Darmstadt (Postdoc) → IIT Madras (Assistant Professor)
Marshall Ball Postdoc 2020-21 (CI Fellow) → New York University (Assistant Professor)
Joseph Jaeger Postdoc 2019-21 → Georgia Institute of Technology (Assistant Professor)
Tianren Liu Postdoc 2019-21 → Peking University (Assistant Professor)
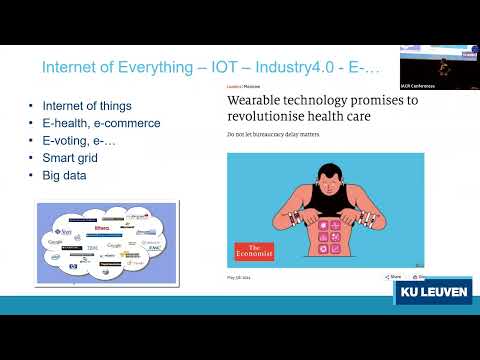
- Cryptography
Cryptography enables the private, authenticated, and confidential communication that allows the internet to thrive. We’re researching quantum-safe cryptography, zero-knowledge proofs, and lattice-based cryptography, to secure everything from mainframes to the hybrid cloud.
Expanding the quantum-safe cryptography toolbox
- Quantum Safe
Federated Learning meets Homomorphic Encryption
- Distributed Systems
- Fully Homomorphic Encryption
IBM’s Cryptography Bill of Materials to speed up quantum-safe assessment
Breaking Rainbow takes a weekend on a laptop
How we quantum-proofed ibm z16.

How IBM is helping make the world’s networks quantum safe
- See more of our work on Cryptography
Is your cybersecurity ready to take the quantum leap?
Our CTO of Security Research, J.R. Rao and Jay Gambetta, VP of Quantum Computing, discuss with the World Economic Forum how enterprises can prepare for the quantum decade ahead.
Crypto Anchors

Privacy-preserving Biometric Authentication

Number Theoretic Cryptography
Zero-knowledge proofs.
Protecting today’s systems from tomorrow’s threats
IBM cryptographer Vadim Lyubashevsky explains how quantum computers coming in the near future could break all modern cryptography — and how they can keep machines safe with post-quantum cryptography.
Publications
- Kenneth G. Paterson
- Frank Libsch
- Steve Bedell
- Nathan Manohar
- Eurocrypt 2024
- Jonathan Bootle
- Elizabeth Crites
- Banashri Karmakar
- Nishat Koti
- S&P 2024
Related topics
Quantum-safe cryptography and migration , data and ai security, threat management, mathematical sciences, quantum information science.
What a lovely hat
Is it made out of tin foil .

International Association for Cryptologic Research
The International Association for Cryptologic Research (IACR) is a non-profit scientific organization whose purpose is to further research in cryptology and related fields. Cryptology is the science and practice of designing computation and communication systems which are secure in the presence of adversaries.

Photo: Pixabay
Eurocrypt 2024
26 - 30 may 2024 zurich, switzerland.

Photo: John Wiley User:Jw4nvc - Santa Barbara, California [ CC BY 3.0 ], via Wikimedia Commons
Crypto 2024
18 - 22 august 2024 santa barbara, usa.

Photo: Mikael Kristenson
Asiacrypt 2024
9 - 13 december 2024 kolkata, india.

Photo: John-Mark Smith
Fast Software Encryption
25 - 29 march 2024 leuven, belgium.

Photo: GraphicCycle [ CC BY-SA 4.0 ], via Wikimedia Commons
Cryptographic Hardware and Embedded Systems
4 - 7 september 2024 halifax, canada.

Photo: pxhere.com , CC0 Public Domain
Theory of Cryptography Conference
2 - 6 december 2024 milan, italy.

Photo: by Kenny Paterson
Real World Crypto Symposium
26 - 28 march 2025 sofia, bulgaria.

The International Conference on Practice and Theory in Public Key Cryptography
12 - 15 may 2025 røros, norway.
Announcement: Announcing the 2024 IACR Test-of-Time Award for Eurocrypt
Announcement: IACR Statement On the War in Gaza
School: Graz Security Week 2024 - Summer School on Security, Privacy and Correctness Graz, Österreich, 23 September - 27 September 2024
ePrint Report: SQIPrime: A dimension 2 variant of SQISignHD with non-smooth challenge isogenies Max Duparc, Tako Boris Fouotsa
ePrint Report: Reducing the Share Size of Weighted Threshold Secret Sharing Schemes via Chow Parameters Approximation Oriol Farràs, Miquel Guiot
ePrint Report: SQIsign2D-East: A New Signature Scheme Using 2-dimensional Isogenies Kohei Nakagawa, Hiroshi Onuki
ePrint Report: Sublinear-Round Broadcast without Trusted Setup Andreea B. Alexandru, Julian Loss, Charalampos Papamanthou, Giorgos Tsimos, Benedikt Wagner
ePrint Report: Time-Based Cryptography From Weaker Assumptions: Randomness Beacons, Delay Functions and More Damiano Abram, Lawrence Roy, Mark Simkin
Publications

Journal of Cryptology
Vincent Rijmen, Editor-in-chief Published by Springer-Verlag since 1988

Conference Proceedings
Regional and Area Conferences Published by Springer-Verlag since 1984
Open Access Journals
Transactions on Symmetric Cryptography
Transactions on Cryptographic Hardware and Embedded Systems

IACR ePrint Archive
Joppe W. Bos & Matthias J. Kannwischer, Co-editors Established 2000
Recent Awards
TCC Test-of-time award, TCC 2007, Multi-authority Attribute Based Encryption
TCC Best Young Researcher Award, TCC 2023, Memory Checking for Parallel RAMs
Best Paper Award, CRYPTO 2023, Fast Practical Lattice Reduction through Iterated Compression
Best Early Career Paper, CRYPTO 2023, Fully Adaptive Schnorr Threshold Signatures
Best paper award, PKC 2023, Post-Quantum Anonymity of Kyber
Featured Video
You are using an outdated browser. Please upgrade your browser to improve your experience.
The Cryptography Group is part of the Theory and Security groups in the EECS Department at the University of California, Berkeley .
Research in the group spans topics in cryptography from theory to applications. We study foundational questions on subjects such as computing on encrypted data, functional encryption, program obfuscation, verifiable computation, zero-knowlege proofs, and others. We also investigate concrete efficiency aspects and implementations of cryptographic protocols, as well as build practical systems that use cryptography to address real-world security problems.
If you would like to join Berkeley's EECS Department as a graduate student, apply to our Ph.D. program .
- Alessandro Chiesa
- Sanjam Garg
- Raluca Ada Popa
- David Wagner
- Nico Döttling (04.2016 to present)
- Divya Gupta (03.2016 to present)
- Pratyay Mukherjee (12.2015 to present)
Graduate students
- Tobias Boelter
- Peihan Miao
- Pratyush Mishra
- Akshayaram Srinivasan
- Nick Spooner (08.2016 to 09.2016)
- Ameer Mohameed (07.2016 to 08.2016)
- Mohammad Mahmoody (07.2016 to 08.2016)
- Claudio Orlandi (07.2016 to 08.2016)
- Daniel Apon (06.2016 to 08.2016)
- Omkant Pandey (06.2016 to 08.2016)
- Ariel Gabizon (03.2016 to 04.2016)
- Susumu Kiyoshima (01.2016 to 07.2016)
- Pratyay Mukherjee (06.2015 to 11.2015)
- Omkant Pandey (06.2015 to 12.2015)
- Antigoni Polychroniadou (03.2015 to 09.2015)
- Madars Virza (10.2015 to 11.2015 & 03.2016)
- Cryptography Reading Group
- Bay Area Crypto Day
- Cryptography Program at the Simons Institute for the Theory of Computing
- Security Reading Group
- Security Seminar
- list of project webpages?
- list of recent papers? (probably too long? so maybe only the ones with prizes?)
Undergraduate
- CS 161 : Computer Security ( s17 , f16 , s16 , s15 , s14 , s13 , s11 , s10 , f08 , f05 )
- CS 261: Computer Security ( f15 , f12 , s11 , f11 , f09 , f08 , f07 , f04 , f02 , f00 , f98 )
- CS 276: Cryptography ( f16 , f15 , f14 , s09 , s06 , s04 , s02 )
- CS 294: Advanced Topics in Computer Security ( s10 )
- CS 294: Analysis and Design of Cryptographic Primitives ( s02 )
- CS 294: Probabilistically Checkable and Interactive Proof Systems ( s17 )
- CS 294: Special Topic in Cryptography: Secure Computation ( s16 )
More courses can be found in the websites of the Theory group and Security group , and also the EECS course directory .
- Cryptography
We work broadly in all areas in Cryptography: applied as well as foundational.
This includes topics such as zero-knowledge proofs, secure multi-party computation, blockchains and cryptocurrencies, game theory, verifiable computation, program obfuscation, computing on encrypted data, differential privacy, non-malleable cryptography, leakage-resilient cryptography, and anonymous communication. Please check the individual webpages for publications and projects
Events in Cryptography
Crypto seminar, april 30, 2024.
Maliciously-secure PIR (almost) for free
CyLab Blockchain Distinguished Seminar
April 29, 2024.
Recent Developments in Succinct Proof Systems and Their Applications
April 18, 2024
Hard Languages in NP ∩ coNP and NIZK Proofs from Unstructured Hardness
- Faculty Research Guide
- Artificial Intelligence
- Programming Languages
- Security and Privacy
Area Website:
Http://crypto.cs.cmu.edu, faculty working in this area.

Cryptography and Communications
Discrete Structures, Boolean Functions and Sequences
- Covers all the fundamental and computational aspects of these fields.
- Offers an outlet for specialized work in information theory.
- Focuses on discrete structures used in stream and block ciphers in symmetric cryptography.
- Emphasizes code division multiple access in communications.
- Explores random number generation for statistics, cryptography, and numerical methods.
- Claude Carlet

Latest issue
Volume 16, Issue 3
Latest articles
On generalized nega-hadamard transform and nega-crosscorrelation.
- Deepmala Sharma
- Mayasar Ahmad Dar
\(\mathcal {S}_0\) -equivalence classes, a new direction to find better weightwise perfectly balanced functions, and more
- Agnese Gini
- Pierrick Méaux

Construction of DNA codes with multiple constrained properties
- Siddhartha Siddhiprada Bhoi
- Udaya Parampalli
- Abhay Kumar Singh

Integer syndrome decoding in the presence of noise
- Vlad-Florin Drăgoi
- Brice Colombier
- Vincent Grosso

Additive codes with few weights
- Daniel Panario
- Murat Sahin
Journal updates
Cfp: quantum cryptanalysis of symmetric ciphers.
Guest Editor: Subhamoy Maitra
Last Date for Submission of Papers: April 30, 2022
CfP: Contemporary Interactions between Codes, Cryptography and or Sequences
Guest Editor: Sihem Mesnager
Last Date for Submission of Papers: October 1, 2022
Special issue guidelines
Journal information.
- ACM Digital Library
- Current Contents/Engineering, Computing and Technology
- EI Compendex
- Google Scholar
- Japanese Science and Technology Agency (JST)
- Mathematical Reviews
- OCLC WorldCat Discovery Service
- Science Citation Index Expanded (SCIE)
- TD Net Discovery Service
- UGC-CARE List (India)
Rights and permissions
Editorial policies
© Springer Science+Business Media, LLC, part of Springer Nature
- Find a journal
- Publish with us
- Track your research
Polynomial and Vector Commitments
Fast amortized KZG proofs .
Dankrad Feist, Dmitry Khovratovich .
.css-hl8k99{display:-webkit-box;display:-webkit-flex;display:-ms-flexbox;display:flex;-webkit-align-items:center;-webkit-box-align:center;-ms-flex-align:center;align-items:center;width:100%;outline:2px solid transparent;outline-offset:2px;transition-property:var(--chakra-transition-property-common);transition-duration:var(--chakra-transition-duration-normal);font-size:1rem;-webkit-padding-start:var(--chakra-space-4);padding-inline-start:var(--chakra-space-4);-webkit-padding-end:var(--chakra-space-4);padding-inline-end:var(--chakra-space-4);padding-top:var(--chakra-space-2);padding-bottom:var(--chakra-space-2);padding-left:0px;}.css-hl8k99:focus,.css-hl8k99[data-focus]{box-shadow:var(--chakra-shadows-outline);}.css-hl8k99:hover,.css-hl8k99[data-hover]{background:var(--chakra-colors-blackAlpha-50);}.css-hl8k99[disabled],.css-hl8k99[aria-disabled=true],.css-hl8k99[data-disabled]{opacity:0.4;cursor:not-allowed;} .css-1evogsj{width:1em;height:1em;display:inline-block;line-height:1em;-webkit-flex-shrink:0;-ms-flex-negative:0;flex-shrink:0;color:var(--chakra-colors-gray-600);opacity:1;-webkit-transition:-webkit-transform 0.2s;transition:transform 0.2s;transform-origin:center;font-size:var(--chakra-fontSizes-sm);vertical-align:middle;} .css-1v235bj{color:var(--chakra-colors-gray-600);font-size:var(--chakra-fontSizes-sm);} Abstract
In this note we explain how to compute n KZG proofs for a polynomial of degree d in time superlinear of (n+d). Our technique is used in lookup arguments and vector commitment schemes.
Halo Infinite: Proof-Carrying Data from Additive Polynomial Commitments .
Dan Boneh, Justin Drake, Ben Fisch, Ariel Gabizon .
Crypto 2021. PDF.
Polynomial commitment schemes (PCS) have recently been in the spotlight for their key role in building SNARKs. A PCS provides the ability to commit to a polynomial over a finite field and prove its evaluation at points. A succinct PCS has commitment and evaluation proof size sublinear in the degree of the polynomial. An efficient PCS has sublinear proof verification. Any efficient and succinct PCS can be used to construct a SNARK with similar security and efficiency characteristics (in the random oracle model).
Proof-carrying data (PCD) enables a set of parties to carry out an indefinitely long distributed computation where every step along the way is accompanied by a proof of correctness. It generalizes incrementally verifiable computation and can even be used to construct SNARKs. Until recently, however, the only known method for constructing PCD required expensive SNARK recursion. A system called Halo first demonstrated a new methodology for building PCD without SNARKs, exploiting an aggregation property of the Bulletproofs innerproduct argument. The construction was heuristic because it makes non-black-box use of a concrete instantiation of the Fiat-Shamir transform. We expand upon this methodology to show that PCD can be (heuristically) built from any homomorphic polynomial commitment scheme (PCS), even if the PCS evaluation proofs are neither succinct nor efficient. In fact, the Halo methodology extends to any PCS that has an even more general property, namely the ability to aggregate linear combinations of commitments into a new succinct commitment that can later be opened to this linear combination. Our results thus imply new constructions of SNARKs and PCD that were not previously described in the literature and serve as a blueprint for future constructions as well.
Aggregatable subvector commitments for stateless cryptocurrencies .
Alin Tomescu, Ittai Abraham, Vitalik Buterin, Justin Drake, Dankrad Feist, Dmitry Khovratovich .
SCN 2020. PDF.
An aggregatable subvector commitment (aSVC) scheme is a vector commitment (VC) scheme that can aggregate multiple proofs into a single, small subvector proof. In this paper, we formalize aSVCs and give a construction from constant-sized polynomial commitments. Our construction is unique in that it has linear-sized public parameters, it can compute all constant-sized proofs in quasilinear time, it updates proofs in constant time and it can aggregate multiple proofs into a constant-sized subvector proof. Furthermore, our concrete proof sizes are small due to our use of pairing-friendly groups. We use our aSVC to obtain a payments-only stateless cryptocurrency with very low communication and computation overheads. Specifically, our constant-sized, aggregatable proofs reduce each block's proof overhead to a single group element, which is optimal. Furthermore, our subvector proofs speed up block verification and our smaller public parameters further reduce block size.
Efficient polynomial commitment schemes for multiple points and polynomials .
We present an enhanced version of the Kate, Zaverucha and Goldberg polynomial commitment scheme [KZG10] where a single group element can be an opening proof for multiple polynomials each evaluated at a different arbitrary subset of points.
As a sample application we “plug in” this scheme into the PLONK proving system[GWC19] to obtain improved proof size and prover run time at the expense of additional verifier G2 operations and pairings, and additional G2 SRS elements.
We also present a second scheme where the proof consists of two group elements and the verifier complexity is better than previously known batched verification methods for [KZG10].
Verifiable Delay Functions and Random Beacons
Origami: Fold a Plonk for Ethereum’s VDF .
Zhenfei Zhang, Ethereum Foundation .
We present Origami verifiable delay function, build from the MinRoot hash and our dedicated plonk proof system that utilizes a tailored custom gate and a folding scheme. MinRoot VDF is the leading candidate for Ethereum adoption. For N iterations of MinRoot hash function, the overall cost of Origami is N +o(N ) group operations; improving the previous best known result of 6N from a Nova based solution. The proof size is 128k + 224 bytes if we fold the proofs for k times; and may be further reduce to around 960 bytes, regardless of k, via a standard recursive prover.
Bingo: Adaptivity and Asynchrony in Verifiable Secret Sharing and Distributed Key Generation .
Ittai Abraham; Philipp Jovanovic; Mary Maller; Sarah Meiklejohn; Gilad Stern .
Crypto 2023. PDF.
We present B i n g o \mathsf{Bingo} B i n g o , an adaptively secure and optimally resilient packed asynchronous verifiable secret sharing (PAVSS) protocol that allows a dealer to share f + 1 f+1 f + 1 secrets with a total communication complexity of O ( λ n 2 ) O(\lambda n^2) O ( λ n 2 ) words, where λ \lambda λ is the security parameter and n n n is the number of parties.
Using B i n g o \mathsf{Bingo} B i n g o , we obtain an adaptively secure validated asynchronous Byzantine agreement (VABA) protocol that uses O ( λ n 3 ) O(\lambda n^3) O ( λ n 3 ) expected words and constant expected time, which we in turn use to construct an adaptively secure high-threshold asynchronous distributed key generation (ADKG) protocol that uses O ( λ n 3 ) O(\lambda n^3) O ( λ n 3 ) expected words and constant expected time.
To the best of our knowledge, our ADKG is the first to allow for an adaptive adversary while matching the asymptotic complexity of the best known static ADKGs.
MinRoot: Candidate Sequential Function for Ethereum VDF .
Dmitry Khovratovich, Mary Maller, Pratyush Ranjan Tiwari .
SBC 2022. PDF.
We present a candidate sequential function for a VDF protocol to be used within the Ethereum ecosystem. The new function, called MinRoot, is an optimized iterative algebraic transformation and is a strict improvement over competitors VeeDo and Sloth++. We analyze various attacks on sequentiality and suggest weakened versions for public scrutiny. We also announce bounties on certain research directions in cryptanalysis.
Reaching Consensus for Asynchronous Distributed Key Generation .
Ittai Abraham, Philipp Jovanovic, Mary Maller, Sarah Meiklejohn, Gilad Stern, Alin Tomescu .
PODC 2021. PDF.
We give a protocol for Asynchronous Distributed Key Generation (A-DKG) that is optimally resilient (can withstand f ≤ n / 3 f \leq n/3 f ≤ n / 3 faulty parties), has a constant expected number of rounds, has O ~ ( n 3 ) \tilde{\mathcal{O}}(n^3) O ~ ( n 3 ) expected communication complexity, and assumes only the existence of a PKI. Prior to our work, the best A-DKG protocols required Ω ( n ) \Omega(n) Ω ( n ) expected number of rounds, and Ω ( n 4 ) \Omega(n^4) Ω ( n 4 ) expected communication.
Our A-DKG protocol relies on several building blocks that are of independent interest. We define and design a Proposal Election (PE) protocol that allows parties to retrospectively agree on a valid proposal after enough proposals have been sent from different parties. With constant probability the elected proposal was proposed by a nonfaulty party. In building our PE protocol, we design a Verifiable Gather protocol which allows parties to communicate which proposals they have and have not seen in a verifiable manner. The final building block to our A-DKG is a Validated Asynchronous Byzantine Agreement (VABA) protocol. We use our PE protocol to construct a VABA protocol that does not require leaders or an asynchronous DKG setup. Our VABA protocol can be used more generally when it is not possible to use threshold signatures.
Aggregatable Distributed Key Generation .
Kobi Gurkan, Philipp Jovanovic, Mary Maller, Sarah Meiklejohn, Gilad Stern, Alin Tomescu .
Eurocrypt 2021. PDF.
In this paper, we introduce a distributed key generation (DKG) protocol with aggregatable and publicly-verifiable transcripts. Compared with prior publicly-verifiable approaches, our DKG reduces the size of the final transcript and the time to verify it from O ( n 2 ) \mathcal{O}(n^2) O ( n 2 ) to O ( n log n ) \mathcal{O}(n \log n) O ( n lo g n ) , where n denotes the number of parties. As compared with prior non-publicly-verifiable approaches, our DKG leverages gossip rather than all-to-all communication to reduce verification and communication complexity. We also revisit existing DKG security definitions, which are quite strong, and propose new and natural relaxations. As a result, we can prove the security of our aggregatable DKG as well as that of several existing DKGs, including the popular Pedersen variant. We show that, under these new definitions, these existing DKGs can be used to yield secure threshold variants of popular cryptosystems such as El-Gamal encryption and BLS signatures. We also prove that our DKG can be securely combined with a new efficient verifiable unpredictable function (VUF), whose security we prove in the random oracle model. Finally, we experimentally evaluate our DKG and show that the perparty overheads scale linearly and are practical. For 64 parties, it takes 71 ms to share and 359 ms to verify the overall transcript, while for 8192 parties, it takes 8 s and 42.2 s respectively.
Verifiable Delay Functions from Supersingular Isogenies and Pairings .
Luca De Feo, Simon Masson, Christophe Petit, Antonio Sanso .
Asiacrypt 2019. PDF.
We present two new Verifiable Delay Functions (VDF) based on assumptions from elliptic curve cryptography. We discuss both the advantages and some drawbacks of our constructions, we study their security and we demonstrate their practicality with a proof-of-concept implementation.
Post-Quantum Verifiable Random Function from Symmetric Primitives in PoS Blockchain .
Maxime Buser, Rafael Dowsley, Muhammed F. Esgin, Shabnam Kasra Kermanshahi, Veronika Kuchta, Joseph K. Liu, Raphael Phan, and Zhenfei Zhang .
ESORICS 2022. PDF.
Verifiable Random Functions (VRFs) play a key role in Proof-of-Stake blockchains such as Algorand to achieve highly scalable consensus, but currently deployed VRFs lack post-quantum security, which is crucial for future-readiness of blockchain systems. This work presents the first quantum-safe VRF scheme based on symmetric primitives. Our main proposal is a practical many-time quantum-safe VRF construction, X-VRF, based on the XMSS signature scheme. An innovation of our work is to use the state of the blockchain to counter the undesired stateful nature of XMSS by constructing a blockchain-empowered VRF. While increasing the usability of XMSS, our technique also enforces honest behavior when creating an X-VRF output so as to satisfy the fundamental uniqueness property of VRFs. We show how X-VRF can be used in the Algorand setting to extend it to a quantum-safe blockchain and provide four instances of X-VRF with different key life-time. Our extensive performance evaluation, analysis and implementation indicate the effectiveness of our proposed constructions in practice. Particularly, we demonstrate that X-VRF is the most efficient quantum-safe VRF with a maximum proof size of 3 KB and a possible TPS of 449 for a network of thousand nodes.

Zero-Knowledge Proofs
Baloo: Nearly Optimal Lookup Arguments .
Arantxa Zapico, Ariel Gabizon, Dmitry Khovratovich, Mary Maller, Carla Ràfols .
We present "Baloo", the first protocol for lookup tables where the prover work is linear on the amount of lookups and independent of the size of the table. "Baloo" is built over the lookup arguments of Caulk and Caulk+, and the framework for linear relations of Ràfols and Zapico.
Our protocol supports commit-and-prove expansions : the prover selects the subtable containing the elements used in the lookup, that is unknown to the verifier, commits to it and later prove relation with the committed element. This feature makes "Baloo" especially suitable for prover input-output relations on hash functions, and in particular to instantiate the Ethereum Virtual Machine (EVM).
We provide an implementation of Baloo, as well as benchmarks for comparison with existing protocols.
flookup: Fractional decomposition-based lookups in quasi-linear time independent of table size .
Ariel Gabizon, Dmitry Khovratovich .
We present two protocols for checking the values of a committed polynomial ϕ ( X ) \phi (X) ϕ ( X ) over a mutliplicative subgroup H ⊂ F H \subset \mathbb{F} H ⊂ F of size m m m are contained in a table T ∈ F N T\in \mathbb{F}^N T ∈ F N . After a preprocessing step, the prover algorithm runs in time O ( m log 2 m ) O(m\log ^2 m) O ( m lo g 2 m ) . This improves a recent result of Caulk+[PK22] for the same problem with run time O ( m 2 ) O(m^2) O ( m 2 ) , that in turn improved another recent result with run time O ( m 2 + m log N ) O(m^2+m\log N) O ( m 2 + m lo g N ) Caulk[ZBK+22]. We pose further improving this complexity to O ( m log m ) O(m\log m) O ( m lo g m ) as the next important milestone for efficient zk-SNARK lookups.
Caulk: Lookup Arguments in Sublinear Time .
Arantxa Zapico, Vitalik Buterin, Dmitry Khovratovich, Mary Maller, Anca Nitulescu, Mark Simkin .
CCS 2022. PDF.
We present position-hiding linkability for vector commitment schemes: one can prove in zero knowledge that one or m m m values that comprise commitment cm \textsf{cm} cm all belong to the vector of size N N N committed to in \C \C \C . Our construction Caulk \textsf{Caulk} Caulk can be used for membership proofs and lookup arguments and outperforms all existing alternatives in prover time by orders of magnitude.
For both single- and multi-membership proofs the Caulk \textsf{Caulk} Caulk protocol beats SNARKed Merkle proofs by the factor of 100 even if the latter is instantiated with Poseidon hash. Asymptotically our prover needs O ( m 2 + m log N ) O(m^2 + m\log N) O ( m 2 + m lo g N ) time to prove a batch of m m m openings, whereas proof size is O ( 1 ) O(1) O ( 1 ) and verifier time is O ( log ( log N ) ) O(\log(\log N)) O ( lo g ( lo g N ) ) .
As a lookup argument, Caulk \textsf{Caulk} Caulk is the first scheme with prover time sublinear in the table size, assuming O ( N log N ) O(N\log N) O ( N lo g N ) preprocessing time and O ( N ) O(N) O ( N ) storage. It can be used as a subprimitive in verifiable computation schemes in order to drastically decrease the lookup overhead.
Our scheme comes with a reference implementation and benchmarks.
SNARKBlock: Federated Anonymous Blocklisting from Hidden Common Input Aggregate Proofs .
Michael Rosenberg; Mary Maller; Ian Miers .
S&P 2022. PDF.
Zero-knowledge blocklists allow cross-platform blocking of users but, counter-intuitively, do not link users identities inter- or intra-platform, or to the fact they were blocked. Unfortunately, existing approaches (Tsang et al. '10) require that servers do work linear in the size of the blocklist for each verification of a non-membership proof.
We design and implement S N A R K B l o c k \mathsf{SNARKBlock} S N A R K B l o c k , a new protocol for zero-knowledge blocklisting with server-side verification that is logarithmic in the size of the blocklist. S N A R K B l o c k \mathsf{SNARKBlock} S N A R K B l o c k is also the first approach to support ad-hoc, federated blocklisting: websites can mix and match their own blocklists from other blocklists and dynamically choose which identity providers they trust.
Our core technical advance, of separate interest, is the H I C I A P \mathsf{HICIAP} H I C I A P zero-knowledge proof system, which addresses a common problem in privacy-preserving protocols: using zero-knowledge proofs for repeated but unlinkable interactions. Rerandomzing a Groth16 proof achieves unlinkability without the need to recompute the proof for every interaction. But this technique does not apply to applications where each interaction includes multiple Groth16 proofs over a common hidden input (e.g., the user's identity). Here, the best known approach is to commit to the hidden input and feed it to each proof, but this creates a persistent identifier, forcing recomputation. H I C I A P \mathsf{HICIAP} H I C I A P resolves this problem by aggregating n n n Groth16 proofs into one O ( log n ) O(\log n) O ( lo g n ) -sized, O ( log n ) O(\log n) O ( lo g n ) -verification time proof which also shows that the input proofs share a hidden input. Because H I C I A P \mathsf{HICIAP} H I C I A P is zero-knowledge, repeated shows of the same aggregate or an updated aggregate are unlinkable even though the underlying Groth16 proofs are never recomputed.
SnarkPack: Practical SNARK Aggregation .
Nicolas Gailly, Mary Maller, Anca Nitulescu .
FC 2022. PDF.
Zero-knowledge SNARKs (zk-SNARKs) are non-interactive proof systems with short and efficiently verifiable proofs that do not reveal anything more than the correctness of the statement. zk-SNARKs are widely used in decentralised systems to address privacy and scalability concerns.
A major drawback of such proof systems in practice is the requirement to run a trusted setup for the public parameters. Moreover, these parameters set an upper bound to the size of the computations or statements to be proven, which results in new scalability problems.
We design and implement SnarkPack, a new argument that further reduces the size of SNARK proofs by means of aggregation. Our goal is to provide an off-the-shelf solution that is practical in the following sense: (1) it is compatible with existing deployed SNARK systems, (2) it does not require any extra trusted setup. SnarkPack is designed to work with Groth16 scheme and has logarithmic size proofs and a verifier that runs in logarithmic time in the number of proofs to be aggregated. Most importantly, SnarkPack reuses the public parameters from Groth16 system.
SnarkPack can aggregate 8192 proofs in 8.7s and verify them in 163ms, yielding a verification mechanism that is exponentially faster than other solutions. SnarkPack can be used in blockchain applications that rely on many SNARK proofs such as Proof-of-Space or roll-up solutions.
Proofs for inner pairing products and applications .
Benedikt Bünz, Mary Maller, Pratyush Mishra, Nirvan Tyagi, Psi Vesely .
Asiacrypt 2021. PDF.
We present a generalized inner product argument and demonstrate its applications to pairing-based languages. We apply our generalized argument to proving that an inner pairing product is correctly evaluated with respect to committed vectors of n source group elements. With a structured reference string (SRS), we achieve a logarithmic-time verifier whose work is dominated by 6 log n target group exponentiations. Proofs are of size 6 log n target group elements, computed using 6n pairings and 4n exponentiations in each source group. We apply our inner product arguments to build the first polynomial commitment scheme with succinct (logarithmic) verification, O ( d ) \mathcal{O}(\sqrt{d}) O ( d ) prover complexity for degree d d d polynomials (not including the cost to evaluate the polynomial), and a CRS of size O ( d ) \mathcal{O}(\sqrt{d}) O ( d ) . Concretely, this means that for d = 228, producing an evaluation proof in our protocol is 76 × \times × faster than doing so in the KZG [KZG10] commitment scheme, and the CRS in our protocol is 1,000 × \times × smaller: 13MB vs 13GB for KZG. This gap only grows as the degree increases. Our polynomial commitment scheme is applicable to both univariate and bivariate polynomials.
As a second application, we introduce an argument for aggregating n Groth16 zkSNARKs into an O ( log n ) \mathcal{O}(\log n) O ( lo g n ) sized proof. Our protocol is significantly more efficient than aggregating these SNARKs via recursive composition [BCGMMW20]: we can aggregate about 130,000 proofs in 25min, while in the same time recursive composition aggregates just 90 proofs.
Finally, we show how to apply our aggregation protocol to construct a low-memory SNARK for machine computations. For a computation that requires time T and space S, our SNARK produces proofs in space O ~ ( S + T ) \tilde{\mathcal{O}}(S + T) O ~ ( S + T ) , which is significantly more space efficient than a monolithic SNARK, which requires space O ~ ( S ⋅ T ) \tilde{\mathcal{O}}(S \cdot T) O ~ ( S ⋅ T ) .
Snarky Ceremonies .
Markulf Kohlweiss, Mary Maller, Janno Siim, Mikhail Volkhov .
Succinct non-interactive arguments of knowledge (SNARKs) have found numerous applications in the blockchain setting and elsewhere. The most efficient SNARKs require a distributed ceremony protocol to generate public parameters, also known as a structured reference string (SRS). Our contributions are two-fold:
– We give a security framework for non-interactive zero-knowledge arguments with a ceremony protocol.
– We revisit the ceremony protocol of Groth's SNARK [Bowe et al., 2017]. We show that the original construction can be simplified and optimized, and then prove its security in our new framework. Importantly, our construction avoids the random beacon model used in the original work.
Hash Functions
Hash Functions Monolith for ZK Applications: May the Speed of SHA-3 be With You .
Lorenzo Grassi; Dmitry Khovratovich; Reinhard Lüftenegger; Christian Rechberger; Markus Schofnegger; Roman Walch .
The rising popularity of computational integrity protocols has led to an increased focus on efficient domain-specific hash functions, which are one of the core components in these use cases. For example, they are used for polynomial commitments or membership proofs in the context of Merkle trees. Indeed, in modern proof systems the computation of hash functions is a large part of the entire proof's complexity.
In the recent years, authors of these hash functions have focused on components which are verifiable with low-degree constraints. This led to constructions like Poseidon, Rescue, Griffin, Reinforced Concrete, and Tip5, all of which showed significant improvements compared to classical hash functions such as SHA-3 when used inside the proof systems.
In this paper, we focus on lookup-based computations, a specific component which allows to verify that a particular witness is contained in a lookup table. We work over 31-bit and 64-bit finite fields F p \mathbb{F}_p F p , both of which are used in various modern proof systems today and allow for fast implementations. We propose a new 2-to-1 compression function and a SAFE hash function, instantiated by the Monolith permutation. The permutation is significantly more efficient than its competitors, both in terms of circuit friendliness and plain performance, which has become one of the main bottlenecks in various use cases. This includes Reinforced Concrete and Tip5, the first two hash functions using lookup computations internally. Moreover, in Monolith we instantiate the lookup tables as functions defined over F 2 \mathbb{F}_2 F 2 while ensuring that the outputs are still elements in F p \mathbb{F}_p F p . Contrary to Reinforced Concrete and Tip5, this approach allows efficient constant-time plain implementations which mitigates the risk of side-channel attacks potentially affecting competing lookup-based designs. Concretely, our constant time 2-to-1 compression function is faster than a constant time version of Poseidon2 by a factor of 7. Finally, it is also the first arithmetization-oriented function with a plain performance comparable to SHA3-256, essentially closing the performance gap between circuit-friendly hash functions and traditional ones.
Generic Security of the SAFE API and Its Applications .
Dmitry Khovratovich, Mario Marhuenda Beltrán, Bart Mennink .
We provide security foundations for SAFE, a recently introduced API framework for sponge-based hash functions tailored to prime-field-based protocols. SAFE aims to provide a robust and foolproof interface, has been implemented in the Neptune hash framework and some zero-knowledge proof projects, but currently lacks any security proof.
In this work we identify the SAFECore as versatile variant sponge construction underlying SAFE, we prove indifferentiability of SAFECore for all (binary and prime) fields up to around ∣ F p ∣ c / 2 |\mathbb{F}_p|^{c/2} ∣ F p ∣ c / 2 queries, where F p \mathbb{F}_p F p is the underlying field and c c c the capacity, and we apply this security result to various use cases.
We show that the SAFE-based protocols of plain hashing, authenticated encryption, verifiable computation, non-interactive proofs, and commitment schemes are secure against a wide class of adversaries, including those dealing with multiple invocations of a sponge in a single application. Our results pave the way of using SAFE with the full taxonomy of hash functions, including SNARK-, lattice-, and x86-friendly hashes.
SAFE: Sponge API for Field Elements .
JP Aumasson, Taurus and Inference; Dmitry Khovratovich, Ethereum Foundation and Dusk Network; Bart Mennink, Radboud University Nijmegen; Porçu Quine, Lurk Lab and Protocol Labs .
From hashing and commitment schemes to Fiat-Shamir and encryption, hash functions are everywhere in zero-knowledge proofsystems (ZKPs), and minor performance changes in ``vanilla'' implementations can translate in major discrepancies when the hash is processed as a circuit within the proofsystem.
Protocol designers have resorted to a number of techniques and custom modes to optimize hash functions for ZKPs settings, but so far without a single established, well-studied construction. To address this need, we define the Sponge API for Field Elements (SAFE), a unified framework for permutation-based schemes (including AEAD, Sigma, PRNGs, and so on). SAFE eliminates the performance overhead, is pluggable in any field-oriented protocol, and is suitable for any permutation algorithm.
SAFE is implemented in Filecoin's Neptune hash framework, which is our reference implementation (in Rust). SAFE is also being integrated in other prominent ZKP projects. This report specifies SAFE and describes some use cases.
Among other improvements, our construction is among the first to store the protocol metadata in the sponge inner part in a provably secure way, which may be of independent interest to the sponge use cases outside of ZKP.
Poseidon2: A Faster Version of the Poseidon Hash Function .
Lorenzo Grassi, Ponos Technology; Dmitry Khovratovich, Ethereum Foundation; Markus Schofnegger, Horizen Labs .
AFRICACRYPT 2023. PDF.
Zero-knowledge proof systems for computational integrity have seen a rise in popularity in the last couple of years. One of the results of this development is the ongoing effort in designing so-called arithmetization-friendly hash functions in order to make these proofs more efficient. One of these new hash functions, Poseidon, is extensively used in this context, also thanks to being one of the first constructions tailored towards this use case. Many of the design principles of Poseidon have proven to be efficient and were later used in other primitives, yet parts of the construction have shown to be expensive in real-word scenarios.
In this paper, we propose an optimized version of Poseidon, called Poseidon2. The two versions differ in two crucial points. First, Poseidon is a sponge hash function, while Poseidon2 can be either a sponge or a compression function depending on the use case. Secondly, Poseidon2 is instantiated by new and more efficient linear layers with respect to Poseidon. These changes allow to decrease the number of multiplications in the linear layer by up to 90% and the number of constraints in Plonk circuits by up to 70%. This makes Poseidon2 the currently fastest arithmetization-oriented hash function without lookups.
Besides that, we address a recently proposed algebraic attack and propose a simple modification that makes both Poseidon and Poseidon2 secure against this approach.
Note: Updated cryptanalysis results for the original Poseidon.
Reinforced Concrete: A Fast Hash Function for Verifiable Computation .
Lorenzo Grassi, Dmitry Khovratovich, Reinhard Lüftenegger, Christian Rechberger, Markus Schofnegger, Roman Walch .
We propose a new hash function Reinforced Concrete, which is the first generic purpose hash that is fast both for a zero-knowledge prover and in native x86 computations. It is suitable for a various range of zero-knowledge proofs and protocols, from set membership to generic purpose verifiable computation. Being up to 15x faster than its predecessor Poseidon hash, Reinforced Concrete inherits security from traditional time-tested schemes such as AES, whereas taking the zero-knowledge performance from a novel and efficient decomposition of a prime field into compact buckets.
The new hash function is suitable for a wide range of applications like privacy-preserving cryptocurrencies, verifiable encryption, protocols with state membership proofs, or verifiable computation. It may serve as a drop-in replacement for various prime-field hashes such as variants of MiMC, Poseidon, Pedersen hash, and others.
T5: Hashing Five Inputs with Three Compression Calls .
Yevgeniy Dodis, Dmitry Khovratovich, Nicky Mouha, Mridul Nandi .
ITC 2021. PDF.
We prove that this construction matches Stam’s bound, by providing O ~ ( q 2 / 2 n ) \tilde{\mathcal{O}}(q^2 / 2^n) O ~ ( q 2 / 2 n ) collision security and O ( q 3 / 2 2 n + n q / 2 n ) \mathcal{O}(q^3 / 2^{2n} + nq/2^n) O ( q 3 / 2 2 n + n q / 2 n ) preimage security (the latter term dominates in the region of interest, when q ≤ 2 n / 2 q \leq 2^{n/2} q ≤ 2 n / 2 ). In particular, it provides birthday security for hashing 5 inputs using three 2n-to-n compression calls, instead of only 4 inputs in prior constructions.
Thus, we get a sequential variant of the Merkle-Damgard (MD) hashing, where t message blocks are hashed using only 3 t / 4 3t/4 3 t / 4 calls to the 2n-to-n compression functions; a 25% saving over traditional hash function constructions. This time reduces to t / 4 t/4 t / 4 (resp. t / 2 t/2 t / 2 ) sequential calls using 3 (resp. 2) parallel execution units; saving a factor of 4 (resp. 2) over the traditional MD-hashing, where parallelism does not help to process one message.
We also get a novel variant of a Merkle tree, where t message blocks can be processed using 0.75( t t t − 1) compression function calls and depth 0 . 8 6 log 2 t 0.86 \log_2 t 0 . 8 6 lo g 2 t , thereby saving 25% in the number of calls and 14% in the update time over Merkle trees. We provide two modes for a local opening of a particular message block: conservative and aggressive. The former retains the birthday security, but provides longer proofs and local verification time than the traditional Merkle tree.
For the aggressive variant, we reduce the proof length to a 29% overhead compared to Merkle trees ( 1 . 2 9 log 2 t 1.29 \log_2 t 1 . 2 9 lo g 2 t vs log 2 t \log_2 t lo g 2 t ), but the verification time is now 14% faster ( 0 . 8 6 log 2 t 0.86 \log_2 t 0 . 8 6 lo g 2 t vs log 2 t \log_2 t lo g 2 t ). However, birthday security is only shown under a plausible conjecture related to the 3-XOR problem, and only for the (common, but not universal) setting where the root of the Merkle tree is known to correspond to a valid t-block message.
Threshold Cryptography
Fully Adaptive Schnorr Threshold Signatures .
Elizabeth Crites, Chelsea Komlo, Mary Maller .
We prove adaptive security of a simple three-round threshold Schnorr signature scheme, which we call Sparkle. The standard notion of security for threshold signatures considers a static adversary – one who must declare which parties are corrupt at the beginning of the protocol. The stronger adaptive adversary can at any time corrupt parties and learn their state. This notion is natural and practical, yet not proven to be met by most schemes in the literature.
In this paper, we demonstrate that Sparkle achieves several levels of security based on different corruption models and assumptions. To begin with, Sparkle is statically secure under minimal assumptions: the discrete logarithm assumption (DL) and the random oracle model (ROM). If an adaptive adversary corrupts fewer than t/2 out of a threshold of t + 1 signers, then Sparkle is adaptively secure under a weaker variant of the one-more discrete logarithm assumption (AOMDL) in the ROM. Finally, we prove that Sparkle achieves full adaptive security, with a corruption threshold of t, under AOMDL in the algebraic group model (AGM) with random oracles. Importantly, we show adaptive security without requiring secure erasures. Ours is the first proof achieving full adaptive security without exponential tightness loss for any threshold Schnorr signature scheme; moreover, the reduction is tight.
Snowblind: A Threshold Blind Signature in Pairing-Free Groups .
Elizabeth Crites, Chelsea Komlo, Mary Maller, Stefano Tessaro, Chenzhi Zhu .
Both threshold and blind signatures have, individually, received a considerable amount of attention. However, little is known about their combination, i.e., a threshold signature which is also blind, in that no coalition of signers learns anything about the message being signed or the signature being produced. Several applications of blind signatures (e.g., anonymous tokens) would benefit from distributed signing as a means to increase trust in the service and hence reduce the risks of key compromise. This paper builds the first blind threshold signatures in pairing-free groups. Our main contribution is a construction that transforms an underlying blind non-threshold signature scheme with a suitable structure into a threshold scheme, preserving its blindness.
The resulting signing protocol proceeds in three rounds, and produces signatures consisting of one group element and two scalars. The underlying non-threshold blind signature schemes are of independent interest, and improve upon the current state of the art (Tessaro and Zhu, EUROCRYPT ’22) with shorter signatures (three elements, instead of four) and simpler proofs of security. All of our schemes are proved secure in the Random Oracle and Algebraic Group Models, assuming the hardness of the discrete logarithm problem.
Threshold Private Set Intersection with Better Communication Complexity .
Satrajit Ghosh, Mark Simkin .
PKC 2023. PDF.
Given ℓ \ell ℓ parties with sets X 1 , … , X ℓ X_1, \ldots, X_{\ell} X 1 , … , X ℓ of size n n n , we would like to securely compute the intersection ∩ i = 1 ℓ X i \cap_{i=1}^{\ell} X_i ∩ i = 1 ℓ X i , if it is larger than n − t n-t n − t for some threshold t t t , without revealing any other additional information. It has previously been shown (Ghosh and Simkin, Crypto 2019) that this function can be securely computed with a communication complexity that only depends on t t t and in particular does not depend on n n n . For small values of t t t , this results in protocols that have a communication complexity that is sublinear in the size of the inputs. Current protocols either rely on fully homomorphic encryption or have an at least quadratic dependency on the parameter t t t .
In this work, we construct protocols with a quasilinear dependency on t t t from simple assumptions like additively homomorphic encryption and oblivious transfer. All existing approaches, including ours, rely on protocols for computing a single bit, which indicates whether the intersection is larger than n − t n-t n − t without actually computing it. Our key technical contribution, which may be of independent interest, takes any such protocol with secret shared outputs and communication complexity O ( λ ℓ ⋅ p o l y ( t ) ) \mathcal{O}(\lambda \ell \cdot \mathsf{poly}(t)) O ( λ ℓ ⋅ p o l y ( t ) ) , where λ \lambda λ is the security parameter, and transforms it into a protocol with communication complexity O ( λ 2 ℓ t ⋅ p o l y l o g ( t ) ) \mathcal{O}(\lambda^2 \ell t \cdot \mathsf{polylog}(t)) O ( λ 2 ℓ t ⋅ p o l y l o g ( t ) ) .
Stronger Lower Bounds for Leakage-Resilient Secret Sharing .
Charlotte Hoffmann, Mark Simkin .
Latincrypt 2023. PDF.
Threshold secret sharing allows a dealer to split a secret s s s into n n n shares, such that any t t t shares allow for reconstructing s s s , but no t − 1 t-1 t − 1 shares reveal any information about s s s . Leakage-resilient secret sharing requires that the secret remains hidden, even when an adversary additionally obtains a limited amount of leakage from every share.
Benhamouda et al. (CRYPTO'18) proved that Shamir's secret sharing scheme is one bit leakage-resilient for reconstruction threshold r ≥ 0 . 8 5 n r \geq 0.85n r ≥ 0 . 8 5 n and conjectured that the same holds for t = c n t = cn t = c n for any constant 0 ≤ c ≤ 1 0 \leq c \leq 1 0 ≤ c ≤ 1 . Nielsen and Simkin (EUROCRYPT'20) showed that this is the best one can hope for by proving that Shamir's scheme is not secure against one-bit leakage when t = c n / log n t = c n / \log n t = c n / lo g n .
In this work, we strengthen the lower bound of Nielsen and Simkin. We consider noisy leakage-resilience, where a random subset of leakages is replaced by uniformly random noise. We prove a lower bound for Shamir's secret sharing, similar to that of Nielsen and Simkin, which holds even when a constant fraction of leakages is replaced by random noise. To this end, we first prove a lower bound on the share size of any noisy-leakage-resilient sharing scheme. We then use this lower bound to show that there exist universal constants c 1 c_1 c 1 , c 2 c_2 c 2 , such that for infinitely many n, it holds that Shamir's secret sharing scheme is not noisy-leakage-resilient for t ≤ c 1 n / log n t \leq c_1 n / \log n t ≤ c 1 n / lo g n , even when a c 2 c_2 c 2 fraction of leakages are replaced by random noise.
Better than Advertised Security for Non-interactive Threshold Signatures .
Mihir Bellare; Elizabeth Crites; Chelsea Komlo; Mary Maller; Stefano Tessaro; Chenzhi Zhu .
Crypto 2022. PDF.
We give a unified syntax, and a hierarchy of definitions of security of increasing strength, for non-interactive threshold signature schemes. These are schemes having a single-round signing protocol, possibly with one prior round of message-independent pre-processing.
We fit FROST1 and BLS, which are leading practical schemes, into our hierarchy, in particular showing they meet stronger security definitions than they have been shown to meet so far. We also fit in our hierarchy a more efficient version FROST2 of FROST1 that we give.
These definitions and results, for simplicity, all assume trusted key generation. Finally, we prove the security of FROST2 with key generation performed by an efficient distributed key generation protocol.
How to Prove Schnorr Assuming Schnorr: Security of Multi-and Threshold Signatures .
In this paper, we present new techniques for proving the security of multi- and threshold signature schemes under discrete logarithm assumptions in the random oracle model. The purpose is to provide a simple framework for analyzing the relatively complex interactions of these schemes in a concurrent model, thereby reducing the risk of attacks. We make use of proofs of possession and prove that a Schnorr signature suffices as a proof of possession in the algebraic group model without any tightness loss. We introduce and prove the security of a simple, three-round multisignature SimpleMuSig.
Using our new techniques, we prove the concurrent security of a variant of the MuSig2 multisignature scheme that includes proofs of possession as well as the FROST threshold signature scheme. These are currently the most efficient schemes in the literature for generating Schnorr signatures in a multiparty setting. Our variant of MuSig2, which we call SpeedyMuSig, has faster key aggregation due to the proofs of possession.
Lattice Cryptography
Squirrel: Efficient Synchronized Multi-Signatures from Lattices .
Nils Fleischhacker, Mark Simkin, Zhenfei Zhang .
The focus of this work are multi-signatures schemes in the synchronized setting. A multi-signature scheme allows multiple signatures for the same message but from independent signers to be compressed into one short aggregated signature, which allows verifying all of the signatures simultaneously. In the synchronized setting, the signing algorithm takes the current time step as an additional input. It is assumed that no signer signs more than one message per time step and we aim to aggregate signatures for the same message and same time step. This setting is particularly useful in the context of blockchains, where validators are naturally synchronized by the blocks they sign. We present Squirrel, a concretely efficient lattice-based multi-signature scheme in the synchronized setting that works for a bounded number of 2 τ 2^{\tau} 2 τ time steps and allows for aggregating up to ρ \rho ρ signatures at each step, where both τ \tau τ and ρ \rho ρ are public parameters upon which the efficiency of our scheme depends. Squirrel allows for non-interactive aggregation of independent signatures and is proven secure in the random oracle model in the presence of rogue-key attacks assuming the hardness of the short integer solution problem in a polynomial ring. We provide a careful analysis of all parameters and show that Squirrel can be instantiated with good concrete efficiency. For τ = 2 4 \tau = 24 τ = 2 4 and ρ = 4 0 9 6 \rho = 4096 ρ = 4 0 9 6 , a signer could sign a new message every 10 seconds for 5 years non-stop. Assuming the signer has a cache of 112 MB, signing takes 68 ms and verification of an aggregated signature takes 36 ms. The size of the public key is 1 KB, the size of an individual signature is 52 KB, and the size of an aggregated signature is 771 KB.
Property-Preserving Hash Functions for Hamming Distance from Standard Assumptions. .
Nils Fleischhacker, Kasper Green Larsen, Mark Simkin .
Eurocrypt 2022. PDF.
Property-preserving hash functions allow for compressing long inputs x 0 x_0 x 0 and x 1 x_1 x 1 into short hashes h ( x 0 ) h(x_0) h ( x 0 ) and h ( x 1 ) h(x_1) h ( x 1 ) in a manner that allows for computing a predicate P ( x 0 , x 1 ) P(x_0, x_1) P ( x 0 , x 1 ) given only the two hash values without having access to the original data. Such hash functions are said to be adversarially robust if an adversary that gets to pick x 0 x_0 x 0 and x 1 x_1 x 1 after the hash function has been sampled, cannot find inputs for which the predicate evaluated on the hash values outputs the incorrect result.
In this work, we construct robust property-preserving hash functions for the hamming-distance predicate which distinguishes inputs with a hamming distance at least some threshold t t t . The security of the construction is based on standard lattice hardness assumptions. Our construction has several advantages over the best known previous construction by Fleischhacker and Simkin (Eurocrypt 2021). Our construction relies on a single well-studied hardness assumption from lattice cryptography whereas the previous work relied on a newly introduced family of computational hardness assumptions.
In terms of computational effort, our construction only requires a small number of modular additions per input bit, whereas the work of Fleischhacker and Simkin required several exponentiations per bit as well as the interpolation and evaluation of high-degree polynomials over large fields. An additional benefit of our construction is that the description of the hash function can be compressed to λ \lambda λ . Previous work has descriptions of length O ( ℓ λ ) \mathcal{O}(\ell \lambda) O ( ℓ λ ) bits for input bit-length ℓ \ell ℓ .
We prove a lower bound on the output size of any property-preserving hash function for the hamming distance predicate. The bound shows that the size of our hash value is not far from optimal.
Hybrid Dual Attack on LWE with Arbitrary Secrets .
Lei Bi, Xianhui Lu, Junjie Luo, Kunpeng Wang, and Zhenfei Zhang .
Cybersecur. 5(1) 2022. PDF.
In this paper, we study the hybrid dual attack over Learning with Errors (LWE) problems for any secret distribution. Prior to our work, hybrid attacks are only considered for sparse and/or small secrets. A new and interesting result from our analysis shows that for most cryptographic use cases a hybrid dual attack outperforms a standalone dual attack, regardless of the secret distribution. We formulate our results into a framework of predicting the performance of the hybrid dual attacks. We also present a few tricks that further improve our attack. To illustrate the effectiveness of our result, we re-evaluate the security of all LWE related proposals in round 3 of NIST's post-quantum cryptography process, and improve the state-of-the-art cryptanalysis results by 2-14 bits, under the BKZ-core-SVP model.
An SVP attack on Vortex .
Zhenfei Zhang .
In [BS22], the authors proposed a lattice based hash function that is useful for building zero-knowledge proofs with superior performance. In this short note we analysis the underlying lattice problem with the classic shortest vector problem, and show that 2 out of 15 proposed parameter sets for this hash function do not achieve the claimed security.
TensorCrypto: High Throughput Acceleration of Lattice-based Cryptography Using Tensor Core on GPU .
Wai-Kong Lee, Hwajeong Seo, Zhenfei Zhang, and Seongoun Hwang .
IEEE Access 2021. PDF.
Tensor core is a specially designed hardware included in new NVIDIA GPU chips, aimed at accelerating deep learning applications. With the introduction of tensor core, the matrix multiplication at low precision can be computed much faster than using conventional integer and floating point units in NVIDIA GPU. In the past, applications of tensor core were mainly restricted to machine learning and mixed precision scientific computing. In this paper, we show that for the first time, tensor core can be used to accelerate state-of-the-art lattice-based cryptosystems. In particular, we employed tensor core to accelerate NTRU, one of the finalists in NIST post-quantum standardization. Towards our aim, several parallel algorithms are proposed to allow the tensor core to handle flexible matrix sizes and ephemeral key pair. Experimental results show that the polynomial convolution using tensor core is 2.79× (ntruhps2048509) and 2.72× (ntruhps2048677) faster than the version implemented with conventional integer units of NVIDIA GPU. The proposed tensor core based polynomial convolution technique was applied to NTRU public key scheme (TensorTRU). It achieved 1.94×/1.95× (encryption) and 1.97×/2.02× (decryption) better performance for the two parameter sets, compared to the conventional integer based implementations in GPU. TensorTRU is also more than 20× faster than the reference implementation in CPU and 2× faster than the AVX2 implementation, for both encryption and decryption. To demonstrate the flexibility of the proposed technique, we have extended the implementation to other lattice-based cryptosystems that have a small modulus (LAC and two variant parameter sets in FrodoKEM). Experimental results show that the tensor core based polynomial convolution is flexible and useful in accelerating lattice-based cryptosystems that cannot utilize number theoretic transform in performing polynomial multiplication.
Data Structures
Invertible Bloom Lookup Tables with Less Memory and Randomness .
Nils Fleischhacker, Kasper Green Larsen, Maciej Obremski, Mark Simkin .
In this work we study Invertible Bloom Lookup Tables (IBLTs) with small failure probabilities. IBLTs are highly versatile data structures that have found applications in set reconciliation protocols, error-correcting codes, and even the design of advanced cryptographic primitives. For storing n n n elements and ensuring correctness with probability at least 1 − δ 1 - \delta 1 − δ , existing IBLT constructions require Ω ( n ( log 1 / δ log n + 1 ) ) \Omega( n( \frac{ \log 1/\delta}{\log n} + 1) ) Ω ( n ( lo g n lo g 1 / δ + 1 ) ) space and they crucially rely on fully random hash functions.
We present new constructions of IBLTs that are simultaneously more space efficient and require less randomness. For storing n n n elements with a failure probability of at most δ \delta δ , our data structure only requires O ( n + log ( 1 / δ ) log log ( 1 / δ ) ) \mathcal{O}( n + \log(1 / \delta) \log\log(1 / \delta) ) O ( n + lo g ( 1 / δ ) lo g lo g ( 1 / δ ) ) space and O ( log ( log ( n ) / δ ) ) \mathcal{O}( \log( \log( n ) / \delta ) ) O ( lo g ( lo g ( n ) / δ ) ) -wise independent hash functions.
As a key technical ingredient we show that hashing n n n keys with any k k k -wise independent hash function h : U ↦ [ C n ] h: U \mapsto [Cn] h : U ↦ [ C n ] for some sufficiently large constant C C C guarantees with probability 1 − 2 − Ω ( k ) 1 - 2^{-\Omega(k)} 1 − 2 − Ω ( k ) that at least n / 2 n / 2 n / 2 keys will have a unique hash value. Proving this is highly non-trivial as k k k approaches n n n . We believe that the techniques used to prove this statement may be of independent interest.
Compressing Encrypted Data Over Small Fields .
A recent work of Fleischhacker, Larsen, and Simkin (Eurocrypt 2023) shows how to efficiently compress encrypted sparse vectors. Subsequently, Fleischhacker, Larsen, Obremski, and Simkin (Eprint 2023) improve upon their work and provide more efficient constructions solving the same problem. Being able to efficiently compress such vectors is very useful in a variety of applications, such as private information retrieval, searchable encryption, and oblivious message retrieval.
Concretely, assume one is given a vector ( m 1 , … , m n ) (m_1, \ldots, m_n) ( m 1 , … , m n ) with at most t t t distinct indices i ∈ [ n ] i \in [n] i ∈ [ n ] , such that m i ≠ 0 m_i \neq 0 m i ≠ 0 and assume ( G e n , E n c , D e c ) (\mathsf{Gen}, \mathsf{Enc}, \mathsf{Dec}) ( G e n , E n c , D e c ) is an additively homomorphic encryption scheme. The authors show that one can compress ( E n c ( k , m 1 ) , … , E n c ( k , m n ) ) (\mathsf{Enc}(k, m_1), \ldots, \mathsf{Enc}(k, m_n)) ( E n c ( k , m 1 ) , … , E n c ( k , m n ) ) , without knowing the secret key k k k , into a digest with size dependent on the upper bound on the sparsity t t t , but not on the total vector length n n n .
Unfortunately, all existing constructions either only work for encryption schemes that have sufficiently large plaintext spaces or require additional encrypted auxiliary information about the plaintext vector.
In this work, we show how to generalize the results of Fleischhacker, Larsen, and Simkin to encryption schemes with arbitrarily small plaintext spaces. Our construction follows the same general ideas laid out in previous works but modifies them in a way that allows compressing the encrypted vectors correctly with high probability, independently of the size of the plaintext space.
How to Compress Encrypted Data .
Eurocrypt 2023. PDF.
We study the task of obliviously compressing a vector comprised of n n n ciphertexts of size ξ \xi ξ bits each, where at most t t t of the corresponding plaintexts are non-zero. This problem commonly features in applications involving encrypted outsourced storages, such as searchable encryption or oblivious message retrieval. We present two new algorithms with provable worst-case guarantees, solving this problem by using only homomorphic additions and multiplications by constants. Both of our new constructions improve upon the state of the art asymptotically and concretely.
Our first construction, based on sparse polynomials, is perfectly correct and the first to achieve an asymptotically optimal compression rate by compressing the input vector into O ( t ξ ) \mathcal{O}(t \xi) O ( t ξ ) . Compression can be performed homomorphically by performing O ( n log n ) \mathcal{O}( n \log n) O ( n lo g n ) homomorphic additions and multiplications by constants. The main drawback of this construction is a decoding complexity of Ω ( n ) \Omega(\sqrt{n}) Ω ( n ) .
Our second construction is based on a novel variant of invertible bloom lookup tables and is correct with probability 1 − 2 − κ 1 - 2^{-\kappa} 1 − 2 − κ . It has a slightly worse compression rate compared to our first construction as it compresses the input vector into O ( ξ κ t / log t ) \mathcal{O}(\xi\kappa t / \log t) O ( ξ κ t / lo g t ) bits, where κ ≥ log t \kappa \geq \log t κ ≥ lo g t . In exchange, both compression and decompression of this construction are highly efficient. The compression complexity is dominated by O ( n κ / log t ) \mathcal{O}(n \kappa / \log t) O ( n κ / lo g t ) homomorphic additions and multiplications by constants. The decompression complexity is dominated by O ( κ t / log t ) \mathcal{O}(\kappa t / \log t ) O ( κ t / lo g t ) decryption operations and equally many inversions of a pseudorandom permutation.
Elliptic Curves, Class Groups and Isogenies
A note on key control in CSIDH .
Antonio Sanso, Ethereum Foundation, Ruhr Universität Bochum .
In this short note we explore a particular behaviour of the CSIDH key exchange that leads to a very special form of (shared) key control via the use of the quadratic twists. This peculiarity contained in CSIDH with regard to quadratic twists was already noted in the original CSDIH work and used in several subsequent papers but we believe spelling out this in the form of an attack might be useful to the wider community.
Cryptanalysis of an oblivious PRF from supersingular isogenies .
Andrea Basso, Péter Kutas, Simon-Philipp Merz, Christophe Petit, and Antonio Sanso .
We cryptanalyse the SIDH-based oblivious pseudorandom function from supersingular isogenies proposed at Asiacrypt'20 by Boneh, Kogan and Woo. To this end, we give an attack on an assumption, the auxiliary one-more assumption, that was introduced by Boneh et al. and we show that this leads to an attack on the oblivious PRF itself. The attack breaks the pseudorandomness as it allows adversaries to evaluate the OPRF without further interactions with the server after some initial OPRF evaluations and some offline computations. More specifically, we first propose a polynomial-time attack. Then, we argue it is easy to change the OPRF protocol to include some countermeasures, and present a second subexponential attack that succeeds in the presence of said countermeasures. Both attacks break the security parameters suggested by Boneh et al. Furthermore, we provide a proof of concept implementation as well as some timings of our attack. Finally, we examine the generation of one of the OPRF parameters and argue that a trusted third party is needed to guarantee provable security.
Bandersnatch: a fast elliptic curve built over the BLS12-381 scalar field .
Simon Masson, Antonio Sanso, Zhenfei Zhang .
In this short note, we introduce Bandersnatch, a new elliptic curve built over the BLS12-381 scalar field. The curve is equipped with an efficient endomorphism, allowing a fast scalar multiplication algorithm. Our benchmark shows that the multiplication is 42% faster, compared to another curve, called Jubjub, having similar properties. Nonetheless, Bandersnatch does not provide any performance improvement for either rank 1 constraint systems (R1CS) or multi scalar multiplications, compared to the Jubjub curve.
A note on the low order assumption in class group of an imaginary quadratic number fields .
Karim Belabas, Thorsten Kleinjung, Antonio Sanso, Benjamin Wesolowski .
In this short note we analyze the low order assumption in the imaginary quadratic number fields. We show how this assumption is broken for Mersenne primes. We also provide a description on how to possible attack this assumption for other class of prime numbers leveraging some new mathematical tool coming from higher (cubic) number fields.
Miscellaneous
Ramen: Souper Fast Three-Party Computation for RAM Programs .
Lennart Braun, Mahak Pancholi, Rahul Rachuri, Mark Simkin .
Secure RAM computation allows a number of parties to evaluate a function represented as a RAM program in a way that reveals nothing about the private inputs of the parties except from what is already revealed by the function output itself. In this work we present Ramen, which is a new protocol for computing RAM programs securely among three parties, tolerating up to one passive corruption. Ramen provides reasonable asymptotic guarantees and is concretely efficient at the same time. We have implemented our protocol and provide extensive benchmarks for various settings.
Asymptotically, our protocol requires a constant number of rounds and a amortized sublinear amount of communication and computation per memory access. In terms of concrete efficiency, our protocol outperforms previous solutions. For a memory of size 2 2 6 2^{26} 2 2 6 our memory accesses are 3 0 × 30\times 3 0 × faster in the LAN and 8 . 7 × 8.7\times 8 . 7 × faster in the WAN setting, when compared to the previously fastest solution by Vadapalli, Henry, and Goldberg (ePrint 2022). Due to our superior asymptotic guarantees, the efficiency gap is only widening as the memory gets larger and for this reason Ramen provides the currently most scalable concretely efficient solution for securely computing RAM programs.
Foundations of Data Availability Sampling .
Mathias Hall-Andersen, Mark Simkin, Benedikt Wagner .
Towards building more scalable blockchains, an approach known as data availability sampling (DAS) has emerged over the past few years. Even large blockchains like Ethereum are planning to eventually deploy DAS to improve their scalability. In a nutshell, DAS allows the participants of a network to ensure the full availability of some data without any one participant downloading it entirely. Despite the significant practical interest that DAS has received, there are currently no formal definitions for this primitive, no security notions, and no security proofs for any candidate constructions. For a cryptographic primitive that may end up being widely deployed in large real-world systems, this is a rather unsatisfactory state of affairs.
In this work, we initiate a cryptographic study of data availability sampling. To this end, we define data availability sampling precisely as a clean cryptographic primitive. Then, we show how data availability sampling relates to erasure codes. We do so by defining a new type of commitment schemes which naturally generalizes vector commitments and polynomial commitments. Using our framework, we analyze existing constructions and prove them secure. In addition, we give new constructions which are based on weaker assumptions, computationally more efficient, and do not rely on a trusted setup, at the cost of slightly larger communication complexity. Finally, we evaluate the trade-offs of the different constructions.
Laconic Private Set-Intersection From Pairings .
Diego Aranha, Chuanwei Lin, Claudio Orlandi, Mark Simkin .
Private set-intersection (PSI) is one of the most practically relevant special-purpose secure multiparty computation tasks, as it is motivated by many real-world applications. In this paper we present a new private set-intersection protocol which is laconic, meaning that the protocol only has two rounds and that the first message is independent of the set sizes. Laconic PSI can be useful in applications, where servers with large sets would like to learn the intersection of their set with smaller sets owned by resource-constrained clients and where multiple rounds of interactions are not possible.
Previously, practically relevant laconic PSI protocols were only known from factoring-type assumptions. The contributions of this work are twofold: 1) We present the first laconic PSI protocol based on assumptions over pairing-friendly elliptic curves; and 2) For the first time we provide empirical evaluation of any laconic PSI protocol by carefully implementing and optimising both our and previous protocols. Our experimental results show that our protocol outperforms prior laconic PSI protocols.
Distributed Shuffling in Adversarial Environments .
Kasper Green Larsen, Maciej Obremski, Mark Simkin .
ITC 2023. PDF.
We study mix-nets in the context of cryptocurrencies. Here we have many computationally weak shufflers that speak one after another and want to jointly shuffle a list of ciphertexts ( c 1 , … , c n ) (c_1, \ldots, c_n) ( c 1 , … , c n ) . Each shuffler can only permute k ≪ n k \ll n k ≪ n ciphertexts at a time. An adversary A \mathcal{A} A can track some of the ciphertexts and adaptively corrupt some of the shufflers.
We present a simple protocol for shuffling the list of ciphertexts efficiently. The main technical contribution of this work is to prove that our simple shuffling strategy does indeed provide good anonymity guarantees and at the same time terminates quickly.
Our shuffling algorithm provides a strict improvement over the current shuffling strategy in Ethereum's block proposer elections. Our algorithm is secure against a stronger adversary, provides provable security guarantees, and is comparable in efficiency to the current approach.
Interactive Non-Malleable Codes Against Desynchronizing Attacks in the Multi-Party Setting .
Nils Fleischhacker, Suparno Ghoshal, Mark Simkin .
Interactive Non-Malleable Codes were introduced by Fleischhacker et al. (TCC 2019) in the two party setting with synchronous tampering. The idea of this type of non-malleable code is that it "encodes" an interactive protocol in such a way that, even if the messages are tampered with according to some class F \mathcal{F} F , the result of the execution will either be correct, or completely unrelated to the inputs of the participating parties. In the synchronous setting the adversary is able to modify the messages being exchanged but cannot drop messages nor desynchronize the two parties by first running the protocol with the first party and then with the second party. In this work, we define interactive non-malleable codes in the non-synchronous multi-party setting and construct such interactive non-malleable codes for the class F b o u n d e d s \mathcal{F}^s_{\mathsf{bounded}} F b o u n d e d s . The construction is applicable to any multi-party protocol with a fixed message topology.
The Legendre Symbol and the Modulo-2 Operator in Symmetric Schemes over Fpn .
Lorenzo Grassi, Dmitry Khovratovich, Sondre Rønjom, Markus Schofnegger .
ToSC 2022. PDF.
Motivated by modern cryptographic use cases such as multi-party computation (MPC), homomorphic encryption (HE), and zero-knowledge (ZK) protocols, several symmetric schemes that are efficient in these scenarios have recently been proposed in the literature. Some of these schemes are instantiated with low-degree nonlinear functions, for example low-degree power maps (e.g., MiMC, HadesMiMC, Poseidon) or the Toffoli gate (e.g., Ciminion). Others (e.g., Rescue, Vision, Grendel) are instead instantiated via high-degree functions which are easy to evaluate in the target application. A recent example for the latter case is the hash function Grendel, whose nonlinear layer is constructed using the Legendre symbol.
In this paper, we analyze high-degree functions such as the Legendre symbol or the modulo-2 operation as building blocks for the nonlinear layer of a cryptographic scheme over F p n \mathbb{F}_p^n F p n . Our focus regards the security analysis rather than the efficiency in the mentioned use cases. For this purpose, we present several new invertible functions that make use of the Legendre symbol or of the modulo-2 operation.
Even though these functions often provide strong statistical properties and ensure a high degree after a few rounds, the main problem regards their small number of possible outputs, that is, only three for the Legendre symbol and only two for the modulo-2 operation. By fixing them, it is possible to reduce the overall degree of the function significantly. We exploit this behavior by describing the first preimage attack on full Grendel, and we verify it in practice.
Reputable List Curation from Decentralized Voting .
Elizabeth Crites, Mary Maller, Sarah Meiklejohn, Rebekah Mercer .
PETS 2020. PDF.
Token-curated registries (TCRs) are a mechanism by which a set of users are able to jointly curate a reputable list about real-world information. Entries in the registry may have any form, so this primitive has been proposed for use— and deployed— in a variety of decentralized applications, ranging from the simple joint creation of lists to helping to prevent the spread of misinformation online. Despite this interest, the security of this primitive is not well understood, and indeed existing constructions do not achieve strong or provable notions of security or privacy. In this paper, we provide a formal cryptographic treatment of TCRs as well as a construction that provably hides the votes cast by individual curators. Along the way, we provide a model and proof of security for an underlying voting scheme, which may be of independent interest.
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Published: 15 June 2020
Entanglement-based secure quantum cryptography over 1,120 kilometres
- Juan Yin ORCID: orcid.org/0000-0002-9909-6211 1 , 2 , 3 ,
- Yu-Huai Li 1 , 2 , 3 ,
- Sheng-Kai Liao ORCID: orcid.org/0000-0002-4184-9583 1 , 2 , 3 ,
- Meng Yang 1 , 2 , 3 ,
- Yuan Cao ORCID: orcid.org/0000-0002-0354-2855 1 , 2 , 3 ,
- Liang Zhang 2 , 3 , 4 ,
- Ji-Gang Ren 1 , 2 , 3 ,
- Wen-Qi Cai 1 , 2 , 3 ,
- Wei-Yue Liu 1 , 2 , 3 ,
- Shuang-Lin Li 1 , 2 , 3 ,
- Rong Shu 2 , 3 , 4 ,
- Yong-Mei Huang 5 ,
- Lei Deng 6 ,
- Li Li 1 , 2 , 3 ,
- Qiang Zhang ORCID: orcid.org/0000-0003-3482-3091 1 , 2 , 3 ,
- Nai-Le Liu 1 , 2 , 3 ,
- Yu-Ao Chen ORCID: orcid.org/0000-0002-2309-2281 1 , 2 , 3 ,
- Chao-Yang Lu ORCID: orcid.org/0000-0002-8227-9177 1 , 2 , 3 ,
- Xiang-Bin Wang 2 ,
- Feihu Xu ORCID: orcid.org/0000-0002-1643-225X 1 , 2 , 3 ,
- Jian-Yu Wang 2 , 3 , 4 ,
- Cheng-Zhi Peng ORCID: orcid.org/0000-0002-4753-5243 1 , 2 , 3 ,
- Artur K. Ekert ORCID: orcid.org/0000-0002-1504-5039 7 , 8 &
- Jian-Wei Pan ORCID: orcid.org/0000-0002-6100-5142 1 , 2 , 3
Nature volume 582 , pages 501–505 ( 2020 ) Cite this article
33k Accesses
366 Citations
629 Altmetric
Metrics details
- Quantum information
- Single photons and quantum effects
Quantum key distribution (QKD) 1 , 2 , 3 is a theoretically secure way of sharing secret keys between remote users. It has been demonstrated in a laboratory over a coiled optical fibre up to 404 kilometres long 4 , 5 , 6 , 7 . In the field, point-to-point QKD has been achieved from a satellite to a ground station up to 1,200 kilometres away 8 , 9 , 10 . However, real-world QKD-based cryptography targets physically separated users on the Earth, for which the maximum distance has been about 100 kilometres 11 , 12 . The use of trusted relays can extend these distances from across a typical metropolitan area 13 , 14 , 15 , 16 to intercity 17 and even intercontinental distances 18 . However, relays pose security risks, which can be avoided by using entanglement-based QKD, which has inherent source-independent security 19 , 20 . Long-distance entanglement distribution can be realized using quantum repeaters 21 , but the related technology is still immature for practical implementations 22 . The obvious alternative for extending the range of quantum communication without compromising its security is satellite-based QKD, but so far satellite-based entanglement distribution has not been efficient 23 enough to support QKD. Here we demonstrate entanglement-based QKD between two ground stations separated by 1,120 kilometres at a finite secret-key rate of 0.12 bits per second, without the need for trusted relays. Entangled photon pairs were distributed via two bidirectional downlinks from the Micius satellite to two ground observatories in Delingha and Nanshan in China. The development of a high-efficiency telescope and follow-up optics crucially improved the link efficiency. The generated keys are secure for realistic devices, because our ground receivers were carefully designed to guarantee fair sampling and immunity to all known side channels 24 , 25 . Our method not only increases the secure distance on the ground tenfold but also increases the practical security of QKD to an unprecedented level.
This is a preview of subscription content, access via your institution
Access options
Access Nature and 54 other Nature Portfolio journals
Get Nature+, our best-value online-access subscription
24,99 € / 30 days
cancel any time
Subscribe to this journal
Receive 51 print issues and online access
185,98 € per year
only 3,65 € per issue
Buy this article
- Purchase on Springer Link
- Instant access to full article PDF
Prices may be subject to local taxes which are calculated during checkout
Similar content being viewed by others
Entanglement of nanophotonic quantum memory nodes in a telecom network
Creation of memory–memory entanglement in a metropolitan quantum network
Cavity-enhanced photon indistinguishability at room temperature and telecom wavelengths
Data availability.
The data that support the findings of this study are available from the corresponding authors on reasonable request.
Bennett, C. H. & Brassard, G. Quantum cryptography: public key distribution and coin tossing. In Proc. Int. Conf. on Computers, Systems and Signal Processing 175–179 (1984).
Ekert, A. K. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett . 67 , 661 (1991).
ADS MathSciNet CAS PubMed MATH Google Scholar
Bennett, C. H., Brassard, G. & Mermin, N. D. Quantum cryptography without Bell’s theorem. Phys. Rev. Lett . 68 , 557 (1992).
Peng, C.-Z. et al. Experimental long-distance decoy-state quantum key distribution based on polarization encoding. Phys. Rev. Lett . 98 , 010505 (2007).
ADS PubMed Google Scholar
Rosenberg, D. et al. Long-distance decoy-state quantum key distribution in optical fiber. Phys. Rev. Lett . 98 , 010503 (2007).
Yin, H.-L. et al. Measurement-device-independent quantum key distribution over a 404 km optical fiber. Phys. Rev. Lett . 117 , 190501 (2016).
Boaron, A. et al. Secure quantum key distribution over 421 km of optical fiber. Phys. Rev. Lett . 121 , 190502 (2018).
ADS CAS PubMed Google Scholar
Liao, S.-K. et al. Satellite-to-ground quantum key distribution. Nature 549 , 43 (2017).
Liao, S.-K. et al. Space-to-ground quantum key distribution using a small-sized payload on Tiangong-2 Space Lab. Chin. Phys. Lett . 34 , 090302 (2017).
ADS Google Scholar
Yin, J. et al. Satellite-to-ground entanglement-based quantum key distribution. Phys. Rev. Lett . 119 , 200501 (2017).
Schmitt-Manderbach, T. et al. Experimental demonstration of free-space decoy-state quantum key distribution over 144 km. Phys. Rev. Lett . 98 , 010504 (2007).
Ursin, R. et al. Entanglement-based quantum communication over 144 km. Nat. Phys . 3 , 481 (2007).
CAS Google Scholar
Elliott, C. et al. Current status of the DARPA quantum network. In Quantum Information and Computation III Vol. 5815, 138–150 (International Society for Optics and Photonics, 2005).
Peev, M. et al. The SECOQC quantum key distribution network in Vienna. New J. Phys . 11 , 075001 (2009).
Chen, T.-Y. et al. Field test of a practical secure communication network with decoy-state quantum cryptography. Opt. Express 17 , 6540 (2009).
Sasaki, M. et al. Field test of quantum key distribution in the Tokyo QKD network. Opt. Express 19 , 10387–10409 (2011).
Qiu, J. et al. Quantum communications leap out of the lab. Nature 508 , 441 (2014).
Liao, S.-K. et al. Satellite-relayed intercontinental quantum network. Phys. Rev. Lett . 120 , 030501 (2018).
Koashi, M. & Preskill, J. Secure quantum key distribution with an uncharacterized source. Phys. Rev. Lett . 90 , 057902 (2003).
Ma, X., Fung, C.-H. F. & Lo, H.-K. Quantum key distribution with entangled photon sources. Phys. Rev. A 76 , 012307 (2007).
Briegel, H.-J., Dur, W., Cirac, J. I. & Zoller, P. Quantum repeaters: the role of imperfect local operations in quantum communication. Phys. Rev. Lett . 81 , 5932–5935 (1998).
ADS CAS Google Scholar
Yang, S.-J., Wang, X.-J., Bao, X.-H. & Pan, J.-W. An efficient quantum light–matter interface with sub-second lifetime. Nat. Photon . 10 , 381 (2016).
Yin, J. et al. Satellite-based entanglement distribution over 1200 kilometers. Science 356 , 1140 (2017).
CAS PubMed Google Scholar
Lo, H.-K., Curty, M. & Tamaki, K. Secure quantum key distribution. Nat. Photon . 8 , 595 (2014).
Xu, F., Ma, X., Zhang, Q., Lo, H.-K. & Pan, J.-W. Secure quantum key distribution with realistic devices. Rev. Mod. Phys . 92 , 025002 (2020).
Lydersen, L. et al. Hacking commercial quantum cryptography systems by tailored bright illumination. Nat. Photon . 4 , 686 (2010).
Zhao, Y., Fung, C.-H., Qi, B., Chen, C. & Lo, H.-K. Quantum hacking: experimental demonstration of time-shift attack against practical quantum-key-distribution systems. Phys. Rev. A 78 , 042333 (2008).
Weier, H. et al. Quantum eavesdropping without interception: an attack exploiting the dead time of single-photon detectors. New J. Phys . 13 , 073024 (2011).
Li, H.-W. et al. Attacking a practical quantum-key-distribution system with wavelength-dependent beam-splitter and multiwavelength sources. Phys. Rev. A 84 , 062308 (2011).
Sajeed, S. et al. Security loophole in free-space quantum key distribution due to spatial-mode detector-efficiency mismatch. Phys. Rev. A 91 , 062301 (2015).
Clauser, J. F., Horne, M. A., Shimony, A. & Holt, R. A. Proposed experiment to test local hidden-variable theories. Phys. Rev. Lett . 23 , 880 (1969).
ADS MATH Google Scholar
Koashi, M. Simple security proof of quantum key distribution based on complementarity. New J. Phys . 11 , 045018 (2009).
ADS MathSciNet Google Scholar
Tomamichel, M., Lim, C. C. W., Gisin, N. & Renner, R. Tight finite-key analysis for quantum cryptography. Nat. Commun . 3 , 634 (2012).
ADS PubMed PubMed Central Google Scholar
Peng, C.-Z. et al. Experimental free-space distribution of entangled photon pairs over 13 km: towards satellite-based global quantum communication. Phys. Rev. Lett . 94 , 150501 (2005).
Cao, Y. et al. Bell test over extremely high-loss channels: towards distributing entangled photon pairs between earth and the moon. Phys. Rev. Lett . 120 , 140405 (2018).
Ladd, T. D. et al. Quantum computers. Nature 464 , 45–53 (2010).
Makarov, V., Anisimov, A. & Skaar, J. Effects of detector efficiency mismatch on security of quantum cryptosystems. Phys. Rev. A 74 , 022313 (2006).
Qi, B., Fung, C.-H.F., Lo, H.-K. & Ma, X. Time-shift attack in practical quantum cryptosystems. Quantum Inf. Comput . 7 , 73 (2007).
MathSciNet MATH Google Scholar
Gerhardt, I. et al. Experimentally faking the violation of Bell’s inequalities. Phys. Rev. Lett . 107 , 170404 (2011).
Bugge, A. N. et al. Laser damage helps the eavesdropper in quantum cryptography. Phys. Rev. Lett . 112 , 070503 (2014).
Lo, H.-K., Curty, M. & Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett . 108 , 130503 (2012).
Scarani, V. et al. The security of practical quantum key distribution. Rev. Mod. Phys . 81 , 1301–1350 (2009).
Shor, P. & Preskill, J. Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett . 85 , 441 (2000).
Gottesman, D., Lo, H.-K., Lütkenhaus, N. & Preskill, J. Security of quantum key distribution with imperfect devices. Quantum Inf. Comput . 4 , 325 (2004).
Mayers, D. J. Unconditional security in quantum cryptography. J. Assoc. Comput. Mach . 48 , 351–406 (2001).
Lo, H. K. & Chau, H. F. Unconditional security of quantum key distribution over arbitrarily long distances. Science 283 , 2050 (1999).
Ben-Or, M., Horodecki, M., Leung, D. W., Mayers, D. & Oppenheim, J. In Proc. 2nd Int. Conf. on Theory of Cryptography (TCC'05) 386–406 (Springer, 2005).
Renner, R. Security of quantum key distribution. PhD thesis , ETH Zurich (2005); preprint at https://arxiv.org/abs/quant-ph/0512258 .
Tsurumaru, T. Leftover hashing from quantum error correction: unifying the two approaches to the security proof of quantum key distribution. Preprint at https://arxiv.org/abs/1809.05479 (2018).
Serfling, R. J. Probability inequalities for the sum in sampling without replacement. Ann. Stat . 2 , 39–48 (1974).
Curty, M. et al. Finite-key analysis for measurement-device-independent quantum key distribution. Nat. Commun . 5 , 3732 (2014).
Fung, C.-H. F., Tamaki, K., Qi, B., Lo, H.-K. & Ma, X. Security proof of quantum key distribution with detection efficiency mismatch. Quantum Inf. Comput . 9 , 131–165 (2009).
Marøy, Ø., Lydersen, L. & Skaar, J. Security of quantum key distribution with arbitrary individual imperfections. Phys. Rev. A 82 , 032337 (2010).
Download references
Acknowledgements
We acknowledge discussions with X. Ma and C. Jiang. We thank colleagues at the National Space Science Center, China Xi’an Satellite Control Center, National Astronomical Observatories, Xinjiang Astronomical Observatory, Purple Mountain Observatory, and Qinghai Station for their management and coordination. We thank G.-B. Li, L.-L. Ma, Z. Wang, Y. Jiang, H.-B. Li, S.-J. Xu, Y.-Y. Yin, W.-C. Sun and Y. Wang for their long-term assistance in observation. This work was supported by the National Key R&D Program of China (grant number 2017YFA0303900), the Shanghai Municipal Science and Technology Major Project (grant number 2019SHZDZX01), the Anhui Initiative in Quantum Information Technologies, Science and Technological Fund of Anhui Province for Outstanding Youth (grant number 1808085J18) and the National Natural Science Foundation of China (grant numbers U1738201, 61625503, 11822409, 11674309, 11654005 and 61771443).
Author information
Authors and affiliations.
Hefei National Laboratory for Physical Sciences at the Microscale and Department of Modern Physics, University of Science and Technology of China, Hefei, China
Juan Yin, Yu-Huai Li, Sheng-Kai Liao, Meng Yang, Yuan Cao, Ji-Gang Ren, Wen-Qi Cai, Wei-Yue Liu, Shuang-Lin Li, Li Li, Qiang Zhang, Nai-Le Liu, Yu-Ao Chen, Chao-Yang Lu, Feihu Xu, Cheng-Zhi Peng & Jian-Wei Pan
Shanghai Branch, CAS Center for Excellence in Quantum Information and Quantum Physics, University of Science and Technology of China, Shanghai, China
Juan Yin, Yu-Huai Li, Sheng-Kai Liao, Meng Yang, Yuan Cao, Liang Zhang, Ji-Gang Ren, Wen-Qi Cai, Wei-Yue Liu, Shuang-Lin Li, Rong Shu, Li Li, Qiang Zhang, Nai-Le Liu, Yu-Ao Chen, Chao-Yang Lu, Xiang-Bin Wang, Feihu Xu, Jian-Yu Wang, Cheng-Zhi Peng & Jian-Wei Pan
Shanghai Research Center for Quantum Science, Shanghai, China
Juan Yin, Yu-Huai Li, Sheng-Kai Liao, Meng Yang, Yuan Cao, Liang Zhang, Ji-Gang Ren, Wen-Qi Cai, Wei-Yue Liu, Shuang-Lin Li, Rong Shu, Li Li, Qiang Zhang, Nai-Le Liu, Yu-Ao Chen, Chao-Yang Lu, Feihu Xu, Jian-Yu Wang, Cheng-Zhi Peng & Jian-Wei Pan
Key Laboratory of Space Active Opto-Electronic Technology, Shanghai Institute of Technical Physics, Chinese Academy of Sciences, Shanghai, China
Liang Zhang, Rong Shu & Jian-Yu Wang
The Institute of Optics and Electronics, Chinese Academy of Sciences, Chengdu, China
Yong-Mei Huang
Shanghai Engineering Center for Microsatellites, Shanghai, China
Mathematical Institute, University of Oxford, Oxford, UK
Artur K. Ekert
Centre for Quantum Technologies, National University of Singapore, Singapore, Singapore
You can also search for this author in PubMed Google Scholar
Contributions
C.-Z.P., A.K.E. and J.-W.P. conceived the research. J.Y., C.-Z.P. and J.-W.P. designed the experiments. J.Y., Y.-H.L., S.-K.L., M.Y., Y.C., J.-G.R., S.-L.L., C.-Z.P. and J.-W.P. developed the follow-up optics and monitoring circuit. J.Y., Y.-M.H., C.-Z.P. and J.-W.P. developed the efficiency telescopes. J.Y., S.-K.L., Y.C., L.Z., W.-Q.C., R.S., L.D., J.-Y.W., C.-Z.P. and J.-W.P. designed and developed the satellite and payloads. J.Y., L.Z., W.-Q.C., W.-Y.L. and C.-Z.P. developed the software. F.X., X.-B.W., A.K.E. and J.-W.P. performed the security proof and analysis. L.L., Q.Z., N.-L.L., Y.-A.C., X.-B.W., F.X., C.-Z.P., A.K.E. and J.-W.P. contributed to the theoretical study and implementation against device imperfections. F.X., C.-Y.L., C.-Z.P. and J.-W.P. analysed the data and wrote the manuscript, with input from J.Y., Y.-H.L., M.Y., Y.C. and A.K.E. All authors contributed to the data collection, discussed the results and reviewed the manuscript. J.-W.P. supervised the whole project.
Corresponding authors
Correspondence to Cheng-Zhi Peng or Jian-Wei Pan .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Extended data figures and tables
Extended data fig. 1 satellite-to-delingha link efficiencies under different weather conditions..
a , The data in previous work 23 was taken in different orbits during the period of 7 December 2016 to 22 December 2016. b , The data in current work was taken in different orbits during the period of 6 September 2018 to 22 October 2018. Here the change of link efficiencies on different days was caused by the weather conditions.
Extended Data Fig. 2 Multiple orbits of satellite-to-Delingha link efficiencies under good weather conditions.
Stable and high collection efficiencies were observed during the period of October 2018 to April 2019.
Extended Data Fig. 3 The comparison of satellite-to-Delingha link efficiency under the best-orbit condition.
a , After improving the link efficiency with high-efficiency telescopes and follow-up optics, on average, the current work shows a 3-dB enhancement in the collection efficiency over that of ref. 23 . The lines are linear fits to the data. b , Some representative values.
Extended Data Fig. 4 The finite-key secret key rate R versus the QBER.
For the 3,100 s of data collected in our experiment, a QBER of below about 6.0% is required to produce a positive key. The previous work 23 demonstrated a QBER of 8.1%, which is not sufficient to generate a secret key. In this work, a QBER of 4.5% and a secret key rate of 0.12 bits per second are demonstrated over 1,120 km. If one ignores the important finite-key effect, the QBER in ref. 23 is slightly lower than the well known asymptotic limit of 11% (ref. 43 ).
Extended Data Fig. 5 Schematics of the detection and blinding-attack monitoring circuit.
The biased voltage (HV) is applied to an avalanche photodiode through a passive quenching resistance ( R q = 500 kΩ) and a sampling resistance ( R s = 10 kΩ). The avalanche signals are read out as click or no-click events through a signal-discrimination circuit. The blinding signal monitor is shown in the dot-dash diagram. A resistor-capacitor filter and a voltage follower are used to smooth and minimize the impact on the signals. The outputs of an analogue to digital converter (ADC), at a sampling rate of 250 kHz, are registered by computer data acquisition (PC-DAQ). R1, resistor; C1, capacitor; OA, operational amplifier.
Extended Data Fig. 6
The transmission of the beam splitter within the selected bandwidth of wavelength.
Rights and permissions
Reprints and permissions
About this article
Cite this article.
Yin, J., Li, YH., Liao, SK. et al. Entanglement-based secure quantum cryptography over 1,120 kilometres. Nature 582 , 501–505 (2020). https://doi.org/10.1038/s41586-020-2401-y
Download citation
Received : 15 July 2019
Accepted : 13 May 2020
Published : 15 June 2020
Issue Date : 25 June 2020
DOI : https://doi.org/10.1038/s41586-020-2401-y
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
This article is cited by
Entanglement in photo-ionization process.
- I. A. Ivanov
- Kyung Taec Kim
Scientific Reports (2024)
Verifying the security of a continuous variable quantum communication protocol via quantum metrology
- Lorcán O. Conlon
- Biveen Shajilal
- Syed M. Assad
npj Quantum Information (2024)
Quantum key distribution over a mimicked dynamic-scattering channel
- Fang-Xiang Wang
- Zheng-Fu Han
Science China Information Sciences (2024)
Quantum-secured time transfer between precise timing facilities: a field trial with simulated satellite links
- Francesco Picciariello
- Francesco Vedovato
- Florian Moll
GPS Solutions (2024)
FSO-QKD protocols under free-space losses and device imperfections: a comparative study
- Mitali Sisodia
- Joyee Ghosh
Quantum Information Processing (2024)
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing newsletter — what matters in science, free to your inbox daily.
A New Approach of Cryptography for Data Encryption and Decryption
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Suggestions or feedback?
MIT News | Massachusetts Institute of Technology
- Machine learning
- Social justice
- Black holes
- Classes and programs
Departments
- Aeronautics and Astronautics
- Brain and Cognitive Sciences
- Architecture
- Political Science
- Mechanical Engineering
Centers, Labs, & Programs
- Abdul Latif Jameel Poverty Action Lab (J-PAL)
- Picower Institute for Learning and Memory
- Lincoln Laboratory
- School of Architecture + Planning
- School of Engineering
- School of Humanities, Arts, and Social Sciences
- Sloan School of Management
- School of Science
- MIT Schwarzman College of Computing
School of Engineering welcomes new faculty
Press contact :.

Previous image Next image
The School of Engineering welcomes 15 new faculty members across six of its academic departments. This new cohort of faculty members, who have either recently started their roles at MIT or will start within the next year, conduct research across a diverse range of disciplines.
Many of these new faculty specialize in research that intersects with multiple fields. In addition to positions in the School of Engineering, a number of these faculty have positions at other units across MIT. Faculty with appointments in the Department of Electrical Engineering and Computer Science (EECS) report into both the School of Engineering and the MIT Stephen A. Schwarzman College of Computing. This year, new faculty also have joint appointments between the School of Engineering and the School of Humanities, Arts, and Social Sciences and the School of Science.
“I am delighted to welcome this cohort of talented new faculty to the School of Engineering,” says Anantha Chandrakasan, chief innovation and strategy officer, dean of engineering, and Vannevar Bush Professor of Electrical Engineering and Computer Science. “I am particularly struck by the interdisciplinary approach many of these new faculty take in their research. They are working in areas that are poised to have tremendous impact. I look forward to seeing them grow as researchers and educators.”
The new engineering faculty include:
Stephen Bates joined the Department of Electrical Engineering and Computer Science as an assistant professor in September 2023. He is also a member of the Laboratory for Information and Decision Systems (LIDS). Bates uses data and AI for reliable decision-making in the presence of uncertainty. In particular, he develops tools for statistical inference with AI models, data impacted by strategic behavior, and settings with distribution shift. Bates also works on applications in life sciences and sustainability. He previously worked as a postdoc in the Statistics and EECS departments at the University of California at Berkeley (UC Berkeley). Bates received a BS in statistics and mathematics at Harvard University and a PhD from Stanford University.
Abigail Bodner joined the Department of EECS and Department of Earth, Atmospheric and Planetary Sciences as an assistant professor in January. She is also a member of the LIDS. Bodner’s research interests span climate, physical oceanography, geophysical fluid dynamics, and turbulence. Previously, she worked as a Simons Junior Fellow at the Courant Institute of Mathematical Sciences at New York University. Bodner received her BS in geophysics and mathematics and MS in geophysics from Tel Aviv University, and her SM in applied mathematics and PhD from Brown University.
Andreea Bobu ’17 will join the Department of Aeronautics and Astronautics as an assistant professor in July. Her research sits at the intersection of robotics, mathematical human modeling, and deep learning. Previously, she was a research scientist at the Boston Dynamics AI Institute, focusing on how robots and humans can efficiently arrive at shared representations of their tasks for more seamless and reliable interactions. Bobu earned a BS in computer science and engineering from MIT and a PhD in electrical engineering and computer science from UC Berkeley.
Suraj Cheema will join the Department of Materials Science and Engineering, with a joint appointment in the Department of EECS, as an assistant professor in July. His research explores atomic-scale engineering of electronic materials to tackle challenges related to energy consumption, storage, and generation, aiming for more sustainable microelectronics. This spans computing and energy technologies via integrated ferroelectric devices. He previously worked as a postdoc at UC Berkeley. Cheema earned a BS in applied physics and applied mathematics from Columbia University and a PhD in materials science and engineering from UC Berkeley.
Samantha Coday joins the Department of EECS as an assistant professor in July. She will also be a member of the MIT Research Laboratory of Electronics. Her research interests include ultra-dense power converters enabling renewable energy integration, hybrid electric aircraft and future space exploration. To enable high-performance converters for these critical applications her research focuses on the optimization, design, and control of hybrid switched-capacitor converters. Coday earned a BS in electrical engineering and mathematics from Southern Methodist University and an MS and a PhD in electrical engineering and computer science from UC Berkeley.
Mitchell Gordon will join the Department of EECS as an assistant professor in July. He will also be a member of the MIT Computer Science and Artificial Intelligence Laboratory. In his research, Gordon designs interactive systems and evaluation approaches that bridge principles of human-computer interaction with the realities of machine learning. He currently works as a postdoc at the University of Washington. Gordon received a BS from the University of Rochester, and MS and PhD from Stanford University, all in computer science.
Kaiming He joined the Department of EECS as an associate professor in February. He will also be a member of the MIT Computer Science and Artificial Intelligence Laboratory (CSAIL). His research interests cover a wide range of topics in computer vision and deep learning. He is currently focused on building computer models that can learn representations and develop intelligence from and for the complex world. Long term, he hopes to augment human intelligence with improved artificial intelligence. Before joining MIT, He was a research scientist at Facebook AI. He earned a BS from Tsinghua University and a PhD from the Chinese University of Hong Kong.
Anna Huang SM ’08 will join the departments of EECS and Music and Theater Arts as assistant professor in September. She will help develop graduate programming focused on music technology. Previously, she spent eight years with Magenta at Google Brain and DeepMind, spearheading efforts in generative modeling, reinforcement learning, and human-computer interaction to support human-AI partnerships in music-making. She is the creator of Music Transformer and Coconet (which powered the Bach Google Doodle). She was a judge and organizer for the AI Song Contest. Anna holds a Canada CIFAR AI Chair at Mila, a BM in music composition, and BS in computer science from the University of Southern California, an MS from the MIT Media Lab, and a PhD from Harvard University.
Yael Kalai PhD ’06 will join the Department of EECS as a professor in September. She is also a member of CSAIL. Her research interests include cryptography, the theory of computation, and security and privacy. Kalai currently focuses on both the theoretical and real-world applications of cryptography, including work on succinct and easily verifiable non-interactive proofs. She received her bachelor’s degree from the Hebrew University of Jerusalem, a master’s degree at the Weizmann Institute of Science, and a PhD from MIT.
Sendhil Mullainathan will join the departments of EECS and Economics as a professor in July. His research uses machine learning to understand complex problems in human behavior, social policy, and medicine. Previously, Mullainathan spent five years at MIT before joining the faculty at Harvard in 2004, and then the University of Chicago in 2018. He received his BA in computer science, mathematics, and economics from Cornell University and his PhD from Harvard University.
Alex Rives will join the Department of EECS as an assistant professor in September, with a core membership in the Broad Institute of MIT and Harvard. In his research, Rives is focused on AI for scientific understanding, discovery, and design for biology. Rives worked with Meta as a New York University graduate student, where he founded and led the Evolutionary Scale Modeling team that developed large language models for proteins. Rives received his BS in philosophy and biology from Yale University and is completing his PhD in computer science at NYU.
Sungho Shin will join the Department of Chemical Engineering as an assistant professor in July. His research interests include control theory, optimization algorithms, high-performance computing, and their applications to decision-making in complex systems, such as energy infrastructures. Shin is a postdoc at the Mathematics and Computer Science Division at Argonne National Laboratory. He received a BS in mathematics and chemical engineering from Seoul National University and a PhD in chemical engineering from the University of Wisconsin-Madison.
Jessica Stark joined the Department of Biological Engineering as an assistant professor in January. In her research, Stark is developing technologies to realize the largely untapped potential of cell-surface sugars, called glycans, for immunological discovery and immunotherapy. Previously, Stark was an American Cancer Society postdoc at Stanford University. She earned a BS in chemical and biomolecular engineering from Cornell University and a PhD in chemical and biological engineering at Northwestern University.
Thomas John “T.J.” Wallin joined the Department of Materials Science and Engineering as an assistant professor in January. As a researcher, Wallin’s interests lay in advanced manufacturing of functional soft matter, with an emphasis on soft wearable technologies and their applications in human-computer interfaces. Previously, he was a research scientist at Meta’s Reality Labs Research working in their haptic interaction team. Wallin earned a BS in physics and chemistry from the College of William and Mary, and an MS and PhD in materials science and engineering from Cornell University.
Gioele Zardini joined the Department of Civil and Environmental Engineering as an assistant professor in September. He will also join LIDS and the Institute for Data, Systems, and Society. Driven by societal challenges, Zardini’s research interests include the co-design of sociotechnical systems, compositionality in engineering, applied category theory, decision and control, optimization, and game theory, with society-critical applications to intelligent transportation systems, autonomy, and complex networks and infrastructures. He received his BS, MS, and PhD in mechanical engineering with a focus on robotics, systems, and control from ETH Zurich, and spent time at MIT, Stanford University, and Motional.
Share this news article on:
Related links.
- Department of Aeronautics and Astronautics
- Department of Biological Engineering
- Department of Chemical Engineering
- Department of Civil and Environmental Engineering
- Department of Electrical Engineering and Computer Science
- Department of Materials Science and Engineering
Related Topics
- Aeronautical and astronautical engineering
- Biological engineering
- Chemical engineering
- Civil and environmental engineering
- Electrical Engineering & Computer Science (eecs)
- Music and theater arts
- Broad Institute
- Computer Science and Artificial Intelligence Laboratory (CSAIL)
- Laboratory for Information and Decision Systems (LIDS)
- Research Laboratory of Electronics
- Computer science and technology
- Artificial intelligence
- Computer vision
- Human-computer interaction
- human-robot interaction
- Electronics
- Environment
- Cryptography
- School of Humanities Arts and Social Sciences
Related Articles

Previous item Next item
More MIT News

Understanding why autism symptoms sometimes improve amid fever
Read full story →

Study explains why the brain can robustly recognize images, even without color
Turning up the heat on next-generation semiconductors

Sarah Millholland receives 2024 Vera Rubin Early Career Award

A community collaboration for progress

MIT scholars will take commercial break with entrepreneurial scholarship
- More news on MIT News homepage →
Massachusetts Institute of Technology 77 Massachusetts Avenue, Cambridge, MA, USA
- Map (opens in new window)
- Events (opens in new window)
- People (opens in new window)
- Careers (opens in new window)
- Accessibility
- Social Media Hub
- MIT on Facebook
- MIT on YouTube
- MIT on Instagram
Carbon Insight
A platform to display carbon neutralization information for researchers, decision-makers, and other participants in the community.
Carbon Insight (opens in new tab) is a platform aiming to display the carbon neutralization roadmap for researchers, decision-makers, and other participants in the community. Our mission is to visualize the world’s most cutting-edge research on carbon emission, carbon sink, and carbon flux to generate insights of carbon and society. We strive to accelerate climate studies and global climate actions with computational innovations.
With the global consensus of the 1.5°C goal of the Paris Agreement, the world has a goal to achieve carbon neutralization by 2050. This ambitious goal requires collaboration from all fields. To tackle the climate crisis together, we must first understand where carbon comes from and where it goes.
With Carbon Insight, you can work with the world’s most updated carbon-related data and generate insights as you wish.
- Follow on Twitter
- Like on Facebook
- Follow on LinkedIn
- Subscribe on Youtube
- Follow on Instagram
- Subscribe to our RSS feed
Share this page:
- Share on Twitter
- Share on Facebook
- Share on LinkedIn
- Share on Reddit

IMAGES
VIDEO
COMMENTS
Cryptography Research, Inc. is a San Francisco based cryptography company specializing in applied cryptographic engineering, including technologies for building tamper-resistant semiconductors. It was purchased on June 6, 2011 by Rambus for $342.5M.
NIST is a leading agency in cryptography research and standards development for 50 years. Learn about the types of cryptography NIST works on, such as block ciphers, hash algorithms, post-quantum cryptography, and more.
July 5, 2022. The first four algorithms NIST has announced for post-quantum cryptography are based on structured lattices and hash functions, two families of math problems that could resist a quantum computer's assault. GAITHERSBURG, Md. — The U.S. Department of Commerce's National Institute of Standards and Technology (NIST) has chosen the ...
A group of researchers in the Paul G. Allen School of Computer Science & Engineering who work on various topics in cryptography. Learn about their projects, publications, events, classes, and alumni.
Learn about IBM Research's history and achievements in cryptography, from the first Data Encryption Standard to quantum-safe cryptography and zero-knowledge proofs. Explore the projects and publications related to cryptography and its applications.
The International Association for Cryptologic Research. The International Association for Cryptologic Research (IACR) is a non-profit scientific organization whose purpose is to further research in cryptology and related fields. Cryptology is the science and practice of designing computation and communication systems which are secure in the ...
The group studies privacy problems in real-world systems and creates practical solutions using modern cryptography and privacy technologies. Learn about their objectives, projects, publications, and colloquium events.
Journal of Cryptology publishes original research in cryptography and cryptanalysis, covering theoretical and practical aspects of information security. It is the official journal of the International Association for Cryptologic Research and has an impact factor of 3.0.
Publishes research on a wide range of topics including public-key cryptography, secret-key cryptography, and post-quantum cryptography. Focuses on implementations, attacks, and countermeasures for secure and robust systems. Serves both the academic and corporate R&D community. Recommended by authors for an excellent publishing experience.
The group studies cryptography from theory to applications, including encryption, obfuscation, zero-knowledge proofs, and more. It also offers courses, events, and practical systems for cryptography and security.
Cryptography is the study of assured communication procedure which allows only the sender and the intended person to review the message and the content shared. The simplest method used is the symmetric algorithm in which once the message is encrypted it is sent to the recipient along with its secret key. 2.
Cryptography is an international, scientific, peer-reviewed, open access journal on cryptography published quarterly online by MDPI.. Open Access — free for readers, with article processing charges (APC) paid by authors or their institutions.; High Visibility: indexed within Scopus, ESCI (Web of Science), dblp, and other databases. Journal Rank: CiteScore - Q2 (Applied Mathematics)
Cryptography. We work broadly in all areas in Cryptography: applied as well as foundational. This includes topics such as zero-knowledge proofs, secure multi-party computation, blockchains and cryptocurrencies, game theory, verifiable computation, program obfuscation, computing on encrypted data, differential privacy, non-malleable cryptography ...
Focuses on discrete structures used in stream and block ciphers in symmetric cryptography. Emphasizes code division multiple access in communications. Explores random number generation for statistics, cryptography, and numerical methods.
Welcome to the web page for security and cryptography research in the Department of Computer Science and Engineering at the University of California at San Diego.Our group conducts research in areas spanning from theory to practice: we work on the theoretical foundations of cryptography; the development and analysis of cryptographic protocols and algorithms; and on applied cryptography ...
Danagoulian and his research team developed a system that could greatly improve the process for verifying compliance of nuclear warheads. April 23, 2020. Read full story →. 3 Questions: Ron Rivest on trusting electronic voting systems. MIT cryptography expert and election technology developer explains how to verify an election outcome.
ESORICS 2022. Abstract. Reputable List Curation from Decentralized Voting. Elizabeth Crites, Mary Maller, Sarah Meiklejohn, Rebekah Mercer. PETS 2020. Abstract. Explore the cryptography research and papers published by the Ethereum Foundation.
Quantum key distribution (QKD) 1, 2, 3 is a theoretically secure way of sharing secret keys between remote users. It has been demonstrated in a laboratory over a coiled optical fibre up to 404 ...
Cryptography has been used from time immemorial for preserving the confidentiality of data/information in storage or transit. Thus, cryptography research has also been evolving from the classical Caesar cipher to the modern cryptosystems, based on modular arithmetic to the contemporary cryptosystems based on quantum computing. The emergence of quantum computing poses a major threat to the ...
Welcome to the webpage of the Cryptographic Engineering Research Group at George Mason University. Cryptography, from Greek krpto (hidden) and grapho (write), is the science and practice of hiding information. Most Internet users come in contact with cryptography when they go to a secure website of an Internet retailer.
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications. ... Public-key cryptography ...
Cryptography has the importa nt purpose of providing reliabl e, strong, and robust network and data security. In this paper, we. demonstrated a review of some of the research that has been ...
Cryptography is the solution to secure data from different security risks. To enhance the security of communication systems better cryptosystems technology is obvious in the area of cryptography. Our research focuses on data encryption and decryption technique for a better cryptosystem; where we have proposed a new approach that ensures better ...
Her research interests include cryptography, the theory of computation, and security and privacy. Kalai currently focuses on both the theoretical and real-world applications of cryptography, including work on succinct and easily verifiable non-interactive proofs. She received her bachelor's degree from the Hebrew University of Jerusalem, a ...
Follow. Dublin, May 21, 2024 (GLOBE NEWSWIRE) -- The "Global Post Quantum Cryptography Market: Focus on End Use Industry, Application, Type, and Region" report has been added to ResearchAndMarkets ...
Overview. People. Downloads. Carbon Insight is a platform aiming to display the carbon neutralization roadmap for researchers, decision-makers, and other participants in the community. Our mission is to visualize the world's most cutting-edge research on carbon emission, carbon sink, and carbon flux to generate insights of carbon and society ...
68 Cybersecurity and Infrastructure Security Agency, " Quantum-Readiness: Migration to Post-Quantum Cryptography," August 21, 2023. 69 Sift, " Q2 2023 Digital Trust & Safety Index - Fighting Fraud in the Age of AI and Automation," June 22, 2023. 70 Precedence Research, "Generative AI Market Growth Is Booming With 27.02%," July 11 ...
Lactic acid bacteria (LAB) can produce peptides known as bacteriocins with antagonistic activity against foodborne pathogens. The potential of LAB isolated from the surface of jalapeno peppers to produce bacteriocins with antagonistic activity against Listeria monocytogenes, Staphylococcus aureus, Escherichia coli O157:H7, and Salmonella Typhimurium was evaluated. Previously isolated LAB ...