

Do you dream of making twice as much, working half the time? Join me for the upcoming online training.
Discover how to get your business to 20K, 50K, even 100K a month, without sacrificing your life. This FREE hands-on, half-day workshop shows you exactly how. Join us.

How to create your proprietary system
- July 9, 2012

As an entrepreneur, it’s important to assemble your knowledge into a content system that’s easy to follow – a proprietary system.
Clients frequently ask me how to put together their proprietary system and in what order the information should go. The confusion comes from the difference between working privately with clients versus group coaching or a home study program.
When you are coaching a client privately, you can start anywhere they want depending on the person’s specific needs. So you might start at step six because that is what they need in the moment and then circle back to step one at a later date. And the client won’t be confused by this out-of-order interaction because you are jumping in exactly where they are.
But, with a group or home study program, the experience for the client is very different. The content must be presented in a more orderly fashion. In other words, it should start from the beginning of what you do and go to the end in a chronological and logical manner.
So, for example, when I sat down to write my The Leveraged Business System (my proprietary system) I started by having my students make client attraction a priority, then figuring out what their position was in the marketplace. Once that was done, the logical next step was to determine where to find their ideal clients, and then the next step involved creating their compelling marketing message, followed by their materials, etc.
Most importantly, you want your proprietary system to make sense for marketing purposes.
You want to set it up so that communication about what’s included on your website and in your materials is clear and logical. Step by step. Visitors can see what the first step is and the second step, etc. Putting things in order this way will also work for a boot camp or other multi-session series.
Another way to think of organizing the information is as if you were writing a book. In fact, many of my clients turn their proprietary system into a book over time, as they gain more experience and client success stories.
Once you can put your system into chronological order, writing it and pulling all the pieces together will be so much simpler. And you’ll rest easy knowing people who use the system will benefit from the logical arrangement of the material.
Your The Leveraged Business Assignment
Have you created your proprietary system yet? If you haven’t done so, this is the perfect time to get started. Think about the program you want to offer and first map it out step by step. That will help you know what to write and include, and how it should be presented.
If you have already started or even completed your unique selling propositions , you may want to look them over to check they are in chronological order. Take a look at your marketing materials as well to make sure your communication of the system makes sense logically.
Now, if you’re just starting out and trying to fill your practice in the FIRST place, then follow a step-by-step system that feels easy and authentic to you. The Leveraged Business Program™ gives you the most important things to do to set up simple, solid systems, so that you consistently fill your pipeline and continually get new clients. It’s all step-by-step, not a big mishmash of things . So, you do step one of the system, and when you’re done with that, you move on to step two, and so on. All the tools, scripts, templates, and examples are handed to you on a silver platter. Easy . You can get it at The Leveraged Business .
Want to know more about our programs ? You can book a FREE strategy call with one of our coach. Time to get that work done and to scale your business to a six-figures revenue, don’t you think so ?

We'd like to send you a FREE* copy of the revolutionary new book.
*We pay for the book, you only have to cover shipping
*Pay only $6.95 for shipping & handling in US ($9.95 Int.)
Ready to start leveraging your business?
CALL US: +1 (203) 717-4404 | EMAIL: [email protected]
COPYRIGHT ©2024 BOLDHEART, ALL RIGHTS RESERVED. PRIVACY POLICY | COOKIE POLICY | MEMBER CENTER
We'll be sharing practical strategies for leveraging your business, without sacrificing your life. They'll arrive on Saturday morning in your inbox, at no cost to you.
Woohoo! Please check your inbox and confirm your email. If you use Gmail, be sure to move our message to your Primary tab!
Double check your email for accuracy to ensure you receive access. Our privacy policy keeps your email safe and secure. We will never sell, rent, give, or divulge your email information to ANYONE.
Currently Limited Supply To Give Away!
Step #1 Where Should We Ship Your FREE Book?
Step #2 your free book is ready to ship.
Step 1: Shipping Information
Where should we send your free book?
Step 2: Checkout
How would you like to pay for shipping?
Orders for The Leveraged Business sourced through independent, third-party “freebie” sites will not be honored. The content and images of this book and webpage are the intellectual property of Fabienne Fredrickson, protected by the copyright laws of the United States, and may not be shared to or by any other website or organization without the express written permission of the author.
All personal information you provide is encrypted and secure. We will not share or trade any online information that you provide us. Review our Privacy Policy
Update Shipping Details
The Leveraged Business Book
FREE + Shipping
FREE + International Shipping
Domestic Shipping
International Shipping
Privacy Overview
The Impact of Proprietary Systems on Company Value: A Strategic Analysis
In the digital age, businesses are constantly seeking innovative solutions to gain a competitive edge in the market. Proprietary systems, which encompass software, technologies, and processes developed exclusively in-house, have emerged as a popular strategy for achieving differentiation and maintaining control over critical assets.
Proprietary systems offer numerous immediate benefits.
- Competitive Differentiation : Proprietary systems set companies apart from their competitors by offering unique features, functionalities, and solutions that are not readily available in the market. This can strengthen the company’s market share and its ability to command premium pricing.
- Enhanced Innovation : Developing proprietary systems encourages a culture of innovation within the company. Teams collaborate to create solutions that cater to specific needs, which can lead to the discovery of new technologies, methods, and processes.
- Intellectual Property and Barrier to Entry : Proprietary systems are often protected by intellectual property rights such as patents, copyrights, and trade secrets . These legal safeguards create substantial barriers to entry for competitors, as they are unable to replicate the exact functionalities without facing legal consequences. This protection bolsters the company’s market position and reduces the risk of commoditization.
- Control over Technology and Data : Developing proprietary systems allows a company to maintain control over its technology stack and data. This control minimizes reliance on external vendors and safeguards sensitive information from potential security breaches.
- Customization and Scalability : Off-the-shelf solutions may lack the flexibility to adapt to unique business requirements. Proprietary systems, on the other hand, can be customized to precisely fit the company’s workflows. Furthermore, as the company grows, these systems can be scaled to accommodate increased demand without incurring significant overhead.
- Long-Term Cost Savings : While developing proprietary systems requires initial investment, it often leads to long-term cost savings. Businesses can avoid recurring licensing fees associated with third-party software and instead allocate resources to ongoing development and enhancement. Over time, these savings can be substantial and contribute positively to the company’s bottom line.
- Data Monetization Opportunities : Proprietary systems generate a wealth of data that can be leveraged for strategic insights and potentially monetized. By analyzing user behavior, preferences, and trends, companies can make informed decisions, improve customer experiences, and even create additional revenue streams by selling anonymized data to interested parties.
- Agility and Rapid Iteration : Having in-house development capabilities allows companies to be agile and responsive to changing market dynamics. They can quickly iterate on their proprietary systems, releasing updates and new features in a timely manner. This agility enables businesses to seize emerging opportunities and address customer needs promptly.
- Attracting Top Talent : The reputation of developing cutting-edge proprietary systems can attract top-tier talent. Skilled professionals are often drawn to organizations that encourage innovation. This influx of talent can further enhance the company’s capabilities and value proposition.
- Leveraging for Strategic Partnerships : Well-developed proprietary systems can serve as valuable assets in forming strategic partnerships, collaborations, or joint ventures. Other businesses might seek access to the technology stack for integration or co-development, presenting opportunities for mutually beneficial alliances.
Short-Term Gains vs. Long-Term Considerations
While proprietary systems can bolster a company’s competitive position, the long-term implications must not be overlooked. One potential downside lies in the heavy investment required for ongoing development and maintenance. As technology evolves, companies must continually allocate resources to keep their systems up to date, diverting funds from other critical business activities. Moreover, proprietary systems can lead to isolation from industry standards and best practices, making it challenging to adapt to changing market dynamics.
Another significant concern is the potential for employee knowledge concentration. When key technical knowledge resides with a select few employees, the risk of disruption due to turnover or unforeseen events increases. This can hamper the company’s ability to innovate, respond to challenges, and maintain system reliability. The lack of external perspectives that comes with proprietary systems may also hinder the identification of opportunities for improvement.
Considering these challenges, partnering with a capital raise and M&A firm can provide a strategic pathway to mitigate the negative effects. NOW Capital Partners can offer valuable insights, diversification, risk mitigation, and growth opportunities. Ultimately, a balanced strategy that combines the benefits of proprietary systems with the expertise NOW Capital Partners consultants is more likely to result in sustained company value and success in the ever-evolving business landscape.
Schedule a Free Consultation
By submitting you agree to receive text messages and phone calls from us.
- Search Search Please fill out this field.
- Products and Services
Proprietary Technology: Overview, Types, Example
:max_bytes(150000):strip_icc():format(webp)/wk_headshot_aug_2018_02__william_kenton-5bfc261446e0fb005118afc9.jpg)
What Is Proprietary Technology?
Proprietary technology is any combination of processes, tools, or systems of interrelated connections that are the property of a business or individual. These combinations provide a benefit or competitive advantage to the owners of proprietary technologies.
Companies capable of developing useful proprietary technologies in-house are rewarded with a valuable asset and can either use it exclusively or profit from the sale of licensing their technology to other parties.
Access to valuable proprietary technologies can also be purchased. This option, however, is often costlier and comes with greater restrictions on the use of underlying technologies.
Understanding Proprietary Technology
Proprietary technology involves an application, tool, or system that belongs exclusively to an enterprise. These are generally developed and used by the owner internally in order to produce and sell products or services to the end user or customer. In other cases, they may be provided to an end-user or customer for a cost.
In some industries, proprietary technologies are a key determinant of success. As a result, they are confidential. Being carefully guarded within a corporation, they are protected legally by patents and copyrights . For many businesses, particularly in knowledge-based industries, intellectual property can make up a majority of assets on an entity’s balance sheet. For these businesses, investors and interested parties go to great lengths to assess and value proprietary technologies and their contribution to business results.
One of the first steps a business can take to protect its proprietary technology is to understand how valuable an asset it is.
Because research and development (R&D) expenses are something of a silent key to success, many businesses do not freely give away hints to what they’re working on behind the scenes. Analysts and investors try to uncover undisclosed breakthroughs in corporate proprietary technologies so they can take advantage of proprietary investment accounts as well.
Types of Proprietary Technology
Proprietary technology takes many forms and depends on the nature of the business that owns it. It can be both a physical and an intangible asset developed and used by the organization.
For example, a company may own its own data system. For example, financial institutions develop their own internal systems to collect and process data that is used internally. These systems can be found in a bank branch, where employees input information when customers come in to do routine banking at the teller line.
Companies may also develop their own software. Proprietary software is the opposite of free software, which has no limitations on who uses it. Its ownership is restricted to the publisher or distributor. Certain conditions must be met before the owner allows an end-user access to the software. For example, a tax preparation company may charge customers a fee to use their software to complete their tax returns.
Key Takeaways
- Proprietary technology is a series of processes, tools, or systems owned by business or individual, which provide the owner with a benefit or competitive advantage.
- Since proprietary technology is very valuable, it is carefully guarded.
- Owners can protect their interests with patents and copyrights by limiting information access to employees, and with non-disclosure agreements.
- Proprietary technology may be tangible or intangible assets and may include internal systems and software.
Examples of Proprietary Technology
While the advantages of some proprietary technologies are clear, others are not so evident. And it's only through recombination with other technologies where the true value is uncovered—an effort now simply known as innovation.
The story of Xerox and Apple’s Steve Jobs is a classic example. Not knowing what they had on their hands in the late 1970s, Xerox essentially gave away the idea behind a computer mouse to Jobs who went on to use the technology in Apple’s early computer designs.
Proprietary technology is also a big part of the biotech industry. Let's say a company in this industry successfully develops a new drug to treat a major disease. By patenting the process, method, and the end result of the drug, the company can reap substantial rewards from its efforts to develop its proprietary technology.
Protecting Proprietary Technology
Companies go to great lengths to keep their proprietary technology protected. After all, organizations spend a lot of time, effort, and money on developing the know-how for their products and services. Not taking the time to protect their interests could spell disaster for their operations.
Because it's so valuable, proprietary technology is always at risk. As mentioned above, companies can protect themselves by taking out patents and copyrights on their proprietary technology. These give the owner rights to the intellectual property and prevent others from copying the innovations.
Employees may leak or share it with others including the competition—accidentally or intentionally—or a data breach may occur, exposing trade secrets to hackers. So how do companies safeguard themselves from these unforeseeable actions?
Many corporations control and/or limit employee access to data. Employees may also be required to sign non-disclosure agreements (NDAs), a contract that gives the employer legal recourse if internal, confidential information is shared with outside parties. Companies may also need to continuously update their security systems to ensure there is no data breach, exposing their secrets to third parties.
:max_bytes(150000):strip_icc():format(webp)/GettyImages-990280300-dc78c3be409e48d4b30afd314f14061b.jpg)
- Terms of Service
- Editorial Policy
- Privacy Policy
- Your Privacy Choices
- SUGGESTED TOPICS
- The Magazine
- Newsletters
- Managing Yourself
- Managing Teams
- Work-life Balance
- The Big Idea
- Data & Visuals
- Reading Lists
- Case Selections
- HBR Learning
- Topic Feeds
- Account Settings
- Email Preferences
Your Organization Needs a Proprietary Data Strategy
- Thomas H. Davenport
- Thomas C. Redman

Protect your competitive advantage.
Companies need to be more focused on proprietary data — data that is unique to a company and can be used to create a sustainable competitive advantage. The need for proprietary data strategies is increasing with new data types and the growth of artificial intelligence (AI). Most commercial AI involves machine learning, and if your company has the same data as everyone else, it will have the same models informing these machines, and thus no competitive advantage. A company’s proprietary data strategy should address the full lifecycle of such data — from what might be done with it, to how to get it, to the ethical considerations that might result from it. Beyond simply appreciating the need for such data, a strategy effort can answer key questions about how proprietary data fits into the strategy and business models of an organization.
What’s the most overlooked piece of your company’s data strategy? If you’re like many companies, it’s probably proprietary data — data that is unique to a company and can be used to create a sustainable competitive advantage. This is not to mean trade secrets and intellectual property (which is often proprietary but seldom really data), but rather, data where the company is the only organization that has it, or it has added enough value to make it a unique business asset. Proprietary data can be big or small, structured or unstructured, raw or refined. What’s important is that it is not easily replicated by another entity. That’s what makes it a powerful means of achieving offensive value from data management.
- Thomas H. Davenport is the President’s Distinguished Professor of Information Technology and Management at Babson College, a visiting scholar at the MIT Initiative on the Digital Economy, and a senior adviser to Deloitte’s AI practice. He is a coauthor of All-in on AI: How Smart Companies Win Big with Artificial Intelligence (Harvard Business Review Press, 2023).
- Thomas C. Redman , “the Data Doc,” is President of Data Quality Solutions . He helps companies and people chart their courses to data-driven futures with special emphasis on quality, analytics, and organizational capabilities. His latest book, People and Data: Uniting to Transform Your Organization (Kogan Page) was published Summer 2023.
Partner Center
Marcus for Business
Ideas, Information & Inspiration
What is Proprietary Business Information?
- Defining Proprietary Business Information
- Why Proprietary Business Information is Important
- How to Protect Proprietary Business Information
What would you say if a competitor came up to you in a coffee shop and asked for the names of your three biggest customers? You could say “Get lost,” “Take a hike,” or “Sorry, that’s proprietary information.” After all, there’s no reason to divulge that kind of hard-earned information about your business.
Today, almost every business relies on proprietary information to some degree, from Coca-Cola’s legendary secret beverage formula to your monthly sales reports or the wealth of data stored in your customer relationship management (CRM) system. So, take a moment to think about the most important information in your business – the “crown jewels” of your operations that you need to keep out of the hands of your competitors.
Your proprietary information could include trade secrets, production methods, marketing strategies, software applications and financial data. After all, you don’t want everyone knowing how your sales, profits or customer base change from year to year. Perhaps you’ve developed a proprietary machine tool, sealant or coating for a manufacturing operation, or a new algorithm for delivering targeted ads to your customers on social media. These are products and processes that belong to your business and need to be protected to maintain a competitive advantage .

Other types of proprietary information include product specifications, chemical formulas and cooking recipes . In many cases, these trade secrets provide the foundation for a startup business or an extension of a current product line. For example, the owners of a key lime pie company started as a roadside stand selling the tangy desserts made from local Florida limes. They opened a brick-and-mortar store but were unable to turn a profit.
When the owners turned to Marcus Lemonis for help, he realized that one of the factors holding the business back was using generic, pre-made ingredients to produce a larger volume of pies, rather than the original homemade process that attracted customers when they started out. Marcus helped the owners refine their processes for mass producing handmade crusts with fresh key lime filling, and they began selling their signature pies using a new proprietary recipe. Since then, the company’s sales have taken off, and the pies have won numerous culinary awards, including “Best Pie in Florida” from USA Today.
Why is Proprietary Information Important?
Proprietary information is a legal concept that refers to the rights you hold as a business owner or “proprietor.” It typically refers to confidential information that gives you a competitive advantage in regard to your people, processes and products .

As a general rule, proprietary information refers to material held within your organization that would not be readily available to the public.
For instance, if you used an online search engine to find 25 potential customers for your products or services, the resulting list would probably not be considered confidential. After all, anyone else could do the same thing, including your competitors. On the other hand, if you have taken the time to compile detailed notes about your 25 top customers and keep the data in your CRM, that material would almost certainly be considered proprietary.
There are many ways you can use proprietary information to attract new customers, increase revenue or grow your market share.
For instance, you could draw on your customer database to launch an advertising program targeted at similar prospects. You could adjust your product price points up or down depending on confidential information from your suppliers, or capitalize on social media feedback to improve your services.

Of course, if you have developed a secret sauce, a unique blend of beverage flavors or a new food preparation method, you could build an entire business around your trade secrets. For the co-owners of a BBQ restaurant in Kentucky, the creative use of proprietary information led to a wildly successful new product line. Several years ago, Marcus met with the owners to see how they could grow their small family business . He looked at the restaurant’s proprietary recipes for barbecue sauce and suggested selling bottled sauces online as well as in their store. The result was a new revenue stream from a relatively small investment.

There are plenty of other creative strategies you could consider to help grow your business . For example, you could offer a one-time use of your proprietary customer list to a charitable organization in your community in order to attract a larger audience to a local fundraising event. This can be a true win-win relationship that allows you to maintain control of information, while building a new partnership, meeting other business and civic leaders, and generating favorable publicity as a sponsor of a worthy cause.

Protecting Proprietary Information
Because your proprietary information has value, it needs to be protected from a variety of internal and external threats. That typically requires a multi-layered defense strategy tailored to your business’s specific operations. Today, threats can come from almost anywhere, so you need to pay attention to your people and processes and shore up any vulnerable areas.
The first step is to identify your trade secrets, as well as any other information you need to keep confidential. That will help you determine your security priorities. Depending on the nature of that proprietary information, you can then take appropriate measures, such as the following.
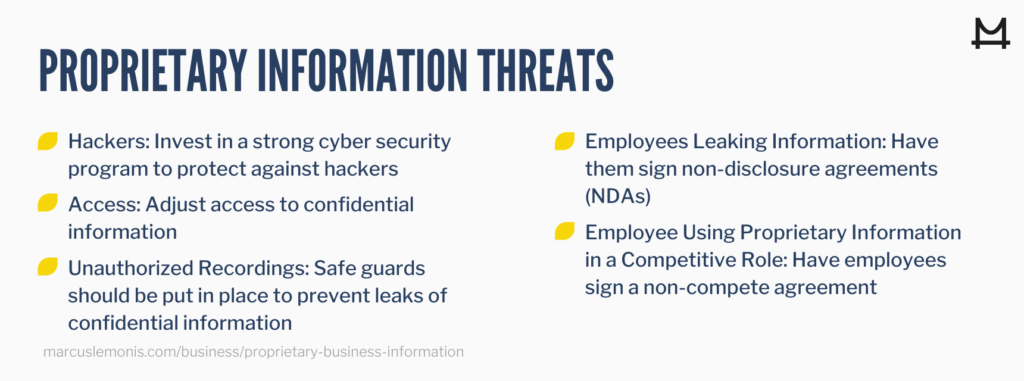
- Cybersecurity. You should invest in a strong cybersecurity program to protect the most valuable proprietary information from hackers. That might mean installing strong firewalls and authentication procedures, or relying on a cloud-services provider who can guard against the ever-changing cybersecurity threats. You should also be sure your employees understand and follow your security protocols. Few things are more damaging to a business than a criminal breaking into your system and stealing trade secrets, personal customer data or other proprietary information.

- Access control. Depending on your business, you may be able to limit physical access to your facility to employees and approved visitors. A data center or executive office suite may have even stricter access controls. Software applications, such as CRM programs, can also be adjusted to prevent employee access to confidential data. A salesperson, for example, might have full access to information about her own customers, but not to customers of other representatives.
- Internal security. Your laboratories, production areas, conference rooms and executive offices should be kept secure to guard against leaks of confidential information. That might mean automatic door locks when someone exits the area, putting tinted glass on windows, or adding security features to communications devices in these locations to prevent unauthorized recordings.

- Non-disclosure agreements. Many businesses use written non-disclosure agreements (NDAs) to keep employees from revealing proprietary information while working for the organization. Suppliers, outside sales representatives and other business partners can also be required to sign NDAs before accessing your business’s data.
- Non-compete clauses. An employment agreement can also contain a non-compete clause that prevents a former employee from using proprietary information in a competitive role. For instance, you wouldn’t want a sales manager to leave your company on a Friday, join your top competitor over the weekend, and start calling your best accounts on Monday.
You should be aware that many of these protective steps require specialized knowledge , such as expertise in network security tools or access control protocols. An experienced attorney should be engaged to help you draft NDAs and non-compete documents that comply with applicable state and federal regulations. After all, you don’t want to go into court expecting to be compensated for the loss of proprietary information only to find that your NDA or non-compete was invalid right from the start.
Don't Let Your Guard Down
It’s not enough to put a series of safeguards in place and get back to your daily business activities. That’s because your proprietary information is not a one-and-done bundle of secrets tucked away in a safe deposit box.

That confidential data is constantly changing with the acquisition of new customers, the launch of a new product or service line or an entry into new markets. Cybercriminals are constantly looking for new ways to attack your confidential database and extract your secrets. Meanwhile, the laws regarding NDAs and other confidential disclosures continue to evolve, and documents prepared in the past might need to be updated.
Therefore, you need to stay focused on securing your proprietary information and monitor potential threats to reduce the risk of a costly unexpected surprise.
- What proprietary information does your business currently have?
- How do you plan on protecting your proprietary information?

Nieds, M. (2015, October 21). 5 tips to protect your proprietary information. Retrieved from www.swflbusinessandipblog.com/2015/10/5-tips-to-protect-your-proprietary-information/
Upcounsel.com. (n.d.). What is proprietary: everything you need to know. Retrieved from https://www.upcounsel.com/what-is-proprietary#:~:text=Proprietary%20information%20is%20important%2C%20possibly,or%20maker%20may%20be%20proprietary
Featured Content
Advantages & Disadvantages of a Proprietary System vs. an Open Platform
- Small Business
- Business Technology & Customer Support
- Customer Service
- ')" data-event="social share" data-info="Pinterest" aria-label="Share on Pinterest">
- ')" data-event="social share" data-info="Reddit" aria-label="Share on Reddit">
- ')" data-event="social share" data-info="Flipboard" aria-label="Share on Flipboard">
What Is Microsoft Silverlight & Is it Worth Having?
What is windows protected mode, why does teamspeak 3 crash.
- How to Implement a Virtual Suggestion Box
- How to Plan a Mobile Application Development Project
Wondering whether you should use proprietary software like Adobe Photoshop and Microsoft Windows or open-source platforms like GIMP and Linux? Deciding between the two isn't easy. Both proprietary platforms and open platform systems have their strengths and weaknesses. At the end of the day, it all comes down to your needs.
Why Use Proprietary Software?
Microsoft Office, Dropbox, AutoCAD and McAfee VirusScan are all examples of proprietary software . Most business owners and entrepreneurs use these programs on a regular basis. Some are free, while others require a monthly or yearly subscription. But are these tools really better than open source platforms? It depends.
Commercial, proprietary software typically has specific features and capabilities . It appeals to a specific audience and aims to provide a superior user experience. These programs usually include regular upgrades, technical support and a wide range of tools. They also tend to be easier to use and provide greater functionality than open platforms.
These products belong to the individuals or companies that developed them. Their source code is not available to the public. They're constantly updated to detect and remove bugs and vulnerabilities, but these updates often come at a price. Developers are aware of the latest industry standards and incorporate these concepts into their programs.
Are There Any Drawbacks?
With a few exceptions, most proprietary platforms require a license and maintenance fees , so the costs add up. Plus, users depend on developers for support, updates and upgrades. Some features are pretty much useless for the average person who may not have the skills and expertise to fully utilize them. This means you could up paying for things that you don’t really need or use.
Another drawback is that you cannot modify or customize the software . If you need additional features, you must upgrade to a more advanced version – and pay extra. Dropbox, for example, offers 2 GB of space for free. Users who need more storage space are required to upgrade to a Plus or Premium plan. The Plus version lacks many of the features associated with Premium plans, such as shared link controls, device approvals, smart sync and priority chat support.
Additionally, software programs come and go – just like the companies behind them. If the developer goes out of business or decides to stop production for a software package, your day-to-day operations suffer and switching to another program can be difficult and time-consuming.
Open Source Software Advantages
Unlike proprietary software, open-source software promotes creative work and gives users full access to the source code. If you want to customize a specific program, you can simply ask a developer to do it (assuming that you have a license, which is required in most cases). You can check the source code anytime and see exactly how the program was created. These products are typically free to use and distribute .
For every proprietary platform on the market, there’s a free open-source version. Ubuntu , for instance, is a viable alternative to Windows 10. It features an intuitive interface, thousands of apps, office software, photo editing tools and gaming capabilities. OpenOffice is an alternative to Microsoft Office, while Inkscape can easily replace Adobe Illustrator.
Open-source programs are backed by developers and users worldwide, featuring chat boards and support groups. If you have questions or need help, you can simply ask – it costs you nothing. Additionally, open-source communities are constantly updating these programs and removing bugs, leading to enhanced functionality and better security compared to proprietary software.
What Are the Downsides?
In general, this kind of software is not as easy to use as proprietary platforms. Most programs appeal to skilled users who know a thing or two about programming. Plus, they often provide poor support – you may need to post your questions on dozens of forums to get a straight answer and solve the problem.
Another disadvantage of open-source programs is that they often include intrusive ads , which can affect the user experience. Developers team up with advertising companies to raise funds for their projects. You'll most likely need to manually upgrade the program . Updates and upgrades are typically not included.
">The Choice Is Yours
Now that you know the difference between open-source and proprietary platforms, decide which one is best for you. Consider your budget and business needs, as well as your technical skills. An open platform provides greater flexibility, but it can be more difficult to operate and maintain. Proprietary software, on the other hand, is easier to use but limits your options and involves higher costs.
- TechTerms: Proprietary Software
- The Web Hosting Database: 50 Proprietary Programs Driving You Crazy And Their Open Source Alternatives
- Tech Republic: How to Decide If Open Source or Proprietary Software Solutions Are Best for Your Business
- Britannica: Open Source
- Simscale: Open-Source or Proprietary Software — What Is Best for Users?
- Dropbox: Choose the Right Dropbox for You
- Ubuntu: Ubuntu Desktop
Andra Picincu is a digital marketing consultant with over 10 years of experience. She works closely with small businesses and large organizations alike to help them grow and increase brand awareness. She holds a BA in Marketing and International Business and a BA in Psychology. Over the past decade, she has turned her passion for marketing and writing into a successful business with an international audience. Current and former clients include The HOTH, Bisnode Sverige, Nutracelle, CLICK - The Coffee Lover's Protein Drink, InstaCuppa, Marketgoo, GoHarvey, Internet Brands, and more. In her daily life, Ms. Picincu provides digital marketing consulting and copywriting services. Her goal is to help businesses understand and reach their target audience in new, creative ways.
Related Articles
Disadvantages of proprietary software, how to brick an android, the system requirements of adobe acrobat 8.0 pro, norton 360 requirements, webex vs. skype, strengths & weaknesses of linux-based systems, mozilla firefox system requirements, the disadvantages of building a non-web-based application, how to share programs between computers, most popular.
- 1 Disadvantages of Proprietary Software
- 2 How to Brick an Android
- 3 The System Requirements of Adobe Acrobat 8.0 Pro
- 4 Norton 360 Requirements
Find, hire, and manage world-class remote developers
Proprietary Software: What It Is, Examples, & Licenses
Table of Contents
The world of software has evolved significantly in the last few decades. Tech companies and IT departments now have a wide range of options regarding the software they use. Proprietary software is one such option and an important one for companies to understand. This is because proprietary software restricts how users can use it and who owns the rights to the software. Therefore, to avoid legal issues, companies must understand the basics of proprietary software and know when, why, and how to use it.
History of Proprietary Software
Before we get into what proprietary software is, it's worth noting the history of this type of software. When computers were bulky and expensive, companies and individuals who needed them could only afford to lease them. These computers came with already installed software that was free to use.
In 1969, however, IBM started charging for its software. Nevertheless, it wasn't until 1983 in the court ruling of Apple Computer, Inc. v. Franklin Computer Corp that software became considered intellectual property and subject to copyright laws. This ruling changed how companies viewed software and laid the foundations for proprietary software.
What Is Proprietary Software?
Proprietary software, also called closed source, is a type of software owned by a single entity and licensed to other parties who wish to use it. This means this type of software doesn't allow users to access the source code. It typically restricts how users can use and modify it, differentiating it from open source software.
Once you purchase proprietary software, you receive a license to use it. This license limits how you can use it and restricts its further distribution. For instance, the owner may not allow you to make copies of the program or modify it in any way. This means the source code remains closed, and users can only access the compiled version of it.
In addition, proprietary software typically has a copy protection system that makes it hard to copy and distribute without permission. Proprietary software is usually licensed per user or on a subscription basis, which provides software owners with a steady and reliable source of income.
Proprietary software companies typically hold all rights and ownership over the software. The owner can, therefore, take legal action against anyone who violates the terms of their license. Companies and users are, therefore, advised to read and adhere to the license requirements of any proprietary software they purchase.
Examples of Proprietary Software
Various industries use proprietary software for different applications. This section will look at some of the most popular proprietary software categorized by use.
Proprietary Antivirus Software
With the rise of online threats, antivirus software has become a necessity for computers and other devices. Proprietary antivirus software is primarily designed to protect users from viruses, malware, and other cyber threats. Examples of proprietary antivirus software include:
- Norton Antivirus
- McAfee Antivirus
- G DATA Software
- Kaspersky Anti-Virus
Proprietary Operating Systems
These underlying software structures enable computers and other devices to function. Proprietary operating systems have been around for a long time, with most of them created by major computer manufacturers like Microsoft and Apple. Examples of proprietary database software include:
- Windows 10, 11
Proprietary Database Software
Database software is used to store, organize, and analyze data. Proprietary database software allows users to manipulate data and build reports without having access to the source code. Examples of proprietary database software include:
- Oracle Database
- SQL Anywhere
- SQL Server Express
Proprietary vs. Open Source Software
As mentioned earlier, proprietary software is different from open source software. Proprietary software is not open to the public, and users cannot access or modify the source code. Open source software, however, is publicly distributed and allows users to view, modify, and share its source code.
Open source software is usually free to use, while proprietary software typically has a license fee. Proprietary software companies can also charge for upgrades and support, while open source software companies may not. Proprietary software is often more user-friendly since it's designed for a specific purpose. Alternatively, open source software is customizable.
In some instances, open source software can become proprietary, known as a proprietary fork, which are versions of open source software that developers modify and copyright as their own.
Proprietary Software vs. Other Types of Software
Other than proprietary and open source software, there are other types of software. These include:
Freeware is software that users can download and use without restrictions or fees. Independent developers create freeware and typically don't provide support or take responsibility for any issues related to it. Users can share and modify freeware as long as they make the changes available to the public.
This type of software is initially free to use. However, users may need to pay a fee or register at some point if they want to continue using it or access additional features. Shareware is usually offered in trial versions, and users can decide whether or not to purchase the full version. Some popular examples of shareware include Adobe Photoshop, WinRAR and Skype.
Abandonware
As the name suggests, this is software that has been abandoned by its developer. It's the perfect solution for users who want to use software without paying a fee since it is no longer supported by its developer. However, due to the inherent security risks, users should steer clear of abandonware as it could contain unpatched vulnerabilities that can put your personal information and data at risk.
Advantages of Proprietary Software
Proprietary software has various advantages for its users. These include:
Many proprietary software companies invest heavily in quality assurance and testing. This ensures the software is bug free and provides users with reliable solutions for their needs. Proprietary software companies also provide free patches to fix any bugs that may arise. This makes this type of software more stable and reliable than its open source counterpart.
Easy to Use
Proprietary software companies design their software with the user in mind. These companies invest heavily in user interface design and ensure their software is easy to use, even for those with no technical background.
High Performance
Proprietary software companies typically invest heavily in research and development to ensure that their software offers high performance. Proprietary software is, therefore, often faster and more reliable than open source alternatives.
Better Support
Proprietary software companies often support users via helpdesks and online resources. This additional layer of security ensures that users can quickly and easily get help if they need it.
Clear Roadmap for Development
Unlike open source software, proprietary software companies usually provide users with a clear roadmap for development. Proprietary software companies typically have a team of developers working on the software, which helps them craft software upgrades. This ensures that users know the features to expect and can plan accordingly.
Disadvantages of Proprietary Software
Proprietary software also has some drawbacks, including:
Proprietary software companies often charge an initial (and sometimes) ongoing subscription fee for their software. This can be expensive for companies and result in a large upfront cost. Moreover, using proprietary software requires companies to hire proprietary developers to maintain and develop their software. Hiring and training these developers can be expensive and time-consuming.
Fewer Options
Proprietary software companies typically offer limited options and features. This means users may not find the exact solutions they need, and have to settle for something close enough. Proprietary software companies cannot always add custom features or modify the software to fit their specific needs.
Limited Freedom of Use
Proprietary software is often heavily restricted in terms of how users can use it and what changes users can make. Proprietary software companies often require users to sign a license agreement, which specifies how they can use their software. Proprietary software is also typically copy-protected, making it difficult to share or resell.
Restricted Customization
Proprietary software is usually designed for a specific purpose. Therefore, users often cannot customize it to their own needs. Proprietary software companies also don’t usually provide users with the ability to modify or tweak their software.
Lack of Transparency
Proprietary software companies often keep their source code private. This means that users may not be able to review the code to ensure that it’s secure and reliable.
Types of Proprietary Software Licenses
Software licensing is a legal agreement between the company that owns the software and its users. It is a way for companies to protect their intellectual property and ensure that users adhere to the terms of use. When you use proprietary software, you must adhere to its license terms.
A proprietary software license generally includes the following information:
- The proprietary software company’s name and contact details.
- What the user can do with the software.
- Ownership of the software and intellectual property rights.
- Prohibited uses of the software.
- License termination terms.
- Proprietary software company’s rights and responsibilities.
- Proprietary software company’s warranties and liabilities.
- Proprietary software company’s customer service policies.
- Proprietary software company’s refund policy.
- Proprietary software company’s support and maintenance.
- Proprietary software company’s liability for damages caused by the software.
Microsoft is a great example of a proprietary software company. The company offers several licenses for its software, such as the Microsoft End User License Agreement (EULA). This license includes the standard proprietary software license terms, such as prohibitions on reverse engineering and redistribution of the software.
The EULA also specifies the rights and responsibilities of users with respect to the software. It also outlines how users can terminate the license in certain circumstances, such as if they violate the terms of use.
Proprietary software licenses typically fall into two categories:
Perpetual Licenses
A perpetual license is a one-time fee for the right to use proprietary software indefinitely. The user does not need to pay ongoing fees and can use the software if they comply with the license terms. While this type of license may appear as a cost-saving option, you may end up paying more for extras, such as support and upgrades.
Subscription Licenses
A subscription license involves a recurring fee for access to the software. The user pays a fee each month or year to use the software and can cancel their subscription when they choose.
The Future of Proprietary Software
While open source software has become increasingly popular in recent years, proprietary software still plays an important role in businesses and organizations. Proprietary software companies often have the resources to develop more feature-rich and high-performance software compared to open source companies. Proprietary software companies can also provide better support and customer service than open source companies.
In the future, proprietary software will likely remain a key part of business and organizational functioning. As such, proprietary software companies will need to stay competitive by providing high-performance and reliable software. They'll need to offer flexible and cost-effective licensing options and provide better customer service and support. Proprietary software companies will also need to focus on developing innovative solutions to meet the changing needs of customers.
Nevertheless, some industry leaders have predicted that open source software will eventually replace proprietary software. Proprietary software companies must, therefore, stay abreast of the changing technological landscape and adapt accordingly to remain competitive.
Hire Proprietary Software Developers With Revelo
Now that you know what proprietary software is, the advantages and disadvantages of using it, and the types of licenses associated with it, you're ready to make an informed decision about what software to use. Proprietary software may be the right choice for your business, but it's important to understand what you're committing to before incorporating it. By familiarizing yourself with the basics of proprietary software, you can ensure that the solution you choose is the right fit for your needs.
If your business requires proprietary software development, you'll need to hire developers with the expertise and experience necessary to develop this type of software. At Revelo , we connect tech companies in the US with experienced remote software engineers in Latin America. Our proprietary software developers are pre-vetted and have the skills to help you build the solutions your business needs.
Contact us today to learn more about how we can help you find and hire the best proprietary software developers for your project.
Need to source and hire remote software developers?
Get matched with vetted candidates within 3 days ..
Why Choose Revelo
Quick time-to-hire
Time-aligned Devs
Expert talents pre-vetted for technical and soft skills
Subscribe to the blog that stamps out your hiring bugs!
Related blog posts.
__What_They_Are%2C_How_They_Work%2C_%26_Uses.png)
Large Language Models

Business Intelligence vs. Data Analytics: What's the Difference

Code Reviews For Remote Teams: Processes, Tools, and Best Practices
Subscribe to the revelo newsletter.
Subscribe and be the first to hear about our new products, exclusive content, and more.
The Importance of a Proprietary Data Strategy for Your Organization
- September 20, 2023
- Business Strategy & Innovation

In today’s data-driven world, organizations are recognizing the importance of a proprietary data strategy. With the exponential growth of artificial intelligence, the demand for proprietary data has skyrocketed.
Did you know that organizations with a strong proprietary data strategy are 58% more likely to achieve above-average profits? This statistic highlights the competitive advantage that proprietary data brings to businesses.
By understanding customer behavior and preferences, organizations can tailor their marketing campaigns and make informed decisions, ultimately driving innovation and success.
In this article, we will explore the significance of a proprietary data strategy and how it can revolutionize your organization’s approach to data management.
Table of Contents
Key Takeaways
- Proprietary data creates a sustainable competitive advantage.
- Companies need to focus on acquiring and leveraging proprietary data.
- Proprietary data is essential for organizations as it helps in making informed business decisions and can lead to increased profitability.
- Applying proprietary data can lead to improved business performance and enable targeted marketing campaigns.
The Competitive Advantage of Proprietary Data
Proprietary data provides organizations with a competitive advantage by enabling them to make informed business decisions and target their marketing campaigns effectively. This advantage stems from the ability to gather and leverage unique data that is not readily available to competitors.
However, organizations must also consider the ethical considerations in acquiring proprietary data. It is important to ensure that data is obtained in a legal and ethical manner, respecting privacy concerns and data protection regulations. This includes obtaining necessary licenses, partnering with data providers, and implementing proper data scraping practices.
Additionally, organizations must prioritize data security and protection to maintain the trust of their customers and stakeholders. By addressing these ethical considerations and privacy concerns, organizations can maximize the value of proprietary data while also maintaining a responsible and innovative approach.
Leveraging Proprietary Data for Informed Business Decisions
To make informed business decisions, organizations can leverage their exclusive data resources. By leveraging proprietary data for predictive analytics, organizations can gain valuable insights that can drive innovation and improve operational efficiency.
Proprietary data integration enhances operational efficiency by allowing organizations to streamline processes, identify bottlenecks, and optimize resource allocation. By analyzing proprietary data, organizations can identify patterns, trends, and correlations that can inform decision-making and drive strategic initiatives.
This data-driven approach enables organizations to make proactive decisions, anticipate market trends, and stay ahead of the competition. Leveraging proprietary data not only enhances operational efficiency but also enables organizations to make data-driven decisions that can lead to improved business performance and increased profitability.
Proprietary Data and Increased Profitability
By leveraging their exclusive data resources, organizations can analyze patterns, trends, and correlations to drive strategic initiatives and increase profitability.
Proprietary data provides organizations with a competitive advantage in today’s fast-paced and data-driven business landscape. By harnessing the power of their proprietary data, companies can uncover valuable insights that can lead to increased profitability.
With access to this unique data, organizations can make informed decisions that have a direct impact on their bottom line. They can identify new business opportunities, optimize marketing campaigns, and improve overall business performance.
By utilizing proprietary data, companies can stay ahead of the competition and position themselves as innovative leaders in their industry.
In this era of digital transformation, a well-executed proprietary data strategy is crucial for organizations looking to gain a competitive edge and achieve increased profitability.
Improving Business Performance With Proprietary Data
Utilizing exclusive data resources can significantly enhance business performance by uncovering valuable insights and informing strategic initiatives. Organizations that leverage proprietary data have the opportunity to improve operational efficiency and optimize their supply chain. By harnessing the power of data-driven decision-making, businesses can streamline their operations and reduce costs while maximizing productivity.
Here are four key ways in which proprietary data can drive business performance:
- Identifying bottlenecks and inefficiencies in the supply chain to improve operational processes.
- Analyzing customer behavior and preferences to develop targeted marketing campaigns and enhance customer satisfaction.
- Predicting demand patterns and optimizing inventory management to reduce stockouts and overstocking.
- Utilizing predictive analytics to optimize production schedules and improve resource allocation.
Understanding Customer Behavior and Preferences Through Proprietary Data
Gaining insights into customer behavior and preferences through proprietary data allows businesses to tailor their marketing campaigns and improve customer satisfaction.
Understanding customer behavior is crucial for organizations seeking to innovate and stay ahead in today’s competitive market. By analyzing data-driven marketing strategies, businesses can identify patterns and trends that provide valuable information about their customers.
This data-driven approach enables companies to create personalized experiences, target specific customer segments, and deliver relevant content. By understanding customer behavior, businesses can anticipate their needs, preferences, and desires, resulting in increased customer satisfaction and loyalty.
Furthermore, data-driven marketing allows organizations to optimize their resources, allocate budgets effectively, and make informed decisions that drive business growth.
In this era of constant innovation, understanding customer behavior through proprietary data is essential for businesses looking to succeed and thrive in the market.
Targeted Marketing Campaigns With Proprietary Data
Targeted marketing campaigns become more effective and efficient when businesses leverage proprietary data to understand customer behavior and preferences. This data-driven approach allows companies to personalize and tailor their advertising efforts to specific segments of their customer base.
By analyzing proprietary data, businesses can gain valuable insights into customer preferences, purchase history, and browsing patterns, enabling them to create highly targeted campaigns that resonate with their audience.
Personalization and targeted advertising with proprietary data not only increase the chances of capturing customer attention but also improve customer engagement and conversion rates. With the ability to segment customers based on their preferences and behaviors, businesses can deliver more relevant and timely marketing messages, ultimately driving higher ROI and customer satisfaction.
Proprietary data and customer segmentation are essential tools for businesses looking to stay ahead in today’s competitive and fast-paced market.
Data-Driven Decision-Making With Proprietary Data
Data-driven decision-making is enhanced when businesses leverage proprietary data to gain valuable insights and inform their strategic choices. By utilizing their own data, organizations can uncover patterns, trends, and correlations that can drive innovation and optimization.
However, in this era of data privacy regulations and increasing cyber threats, it is crucial for businesses to prioritize data security measures. Safeguarding proprietary data not only protects sensitive information but also maintains the trust of customers and stakeholders.
Implementing robust encryption, access controls, and secure storage solutions are essential components of a comprehensive data security strategy. Additionally, organizations must stay up-to-date with evolving data privacy regulations to ensure compliance and avoid potential legal risks.
Identifying New Business Opportunities With Proprietary Data
In the previous subtopic, we explored how organizations can make data-driven decisions using proprietary data.
Now, let’s delve into the next aspect of a proprietary data strategy: identifying new business opportunities.
With the advancements in technology and the availability of vast amounts of data, organizations can harness the power of proprietary data to gain insights and uncover potential market trends.
By utilizing predictive analytics, organizations can analyze historical data and patterns to identify emerging trends and forecast future market conditions.
This enables businesses to stay ahead of the competition, adapt their strategies, and seize new opportunities for growth and innovation.
Identifying market trends through the analysis of proprietary data empowers organizations to make proactive decisions, innovate their products or services, and effectively meet the evolving needs of their customers.
Monetizing and Managing Proprietary Data for Organizational Success
To effectively monetize and manage proprietary data for organizational success, companies must establish clear guidelines and responsibilities for data management within their teams. This requires implementing robust data management techniques that prioritize accuracy, security, and accessibility.
By employing innovative monetizing strategies, companies can unlock the full potential of their proprietary data, turning it into a valuable asset that generates revenue. This can be achieved through various means, such as selling data to third parties, creating data-driven products or services, or leveraging data for targeted marketing campaigns.
Additionally, companies must invest in data governance practices to ensure compliance with regulations and protect sensitive information. By adopting a proactive approach to data management and monetization, organizations can gain a competitive edge and drive innovation in their industry.

Frequently Asked Questions
What are some examples of industries that are successfully leveraging proprietary data.
Examples of industries successfully leveraging proprietary data include autonomous driving companies like Waymo and GM’s Cruise Automation, medical imaging firms in AI-assisted radiology, investment firms analyzing alternative data, and hedge funds curating datasets for proprietary assets.
How Can Companies Ethically Obtain External Data for Their Proprietary Data Strategy?
Companies can ethically obtain external data for their proprietary data strategy by buying licenses, partnering with other companies, or scraping data with caution. It is important to establish legal agreements to firmly claim proprietary data and ensure ethical data acquisition.
What Are Some Potential Challenges or Burdens That Come With Managing Large Volumes of Proprietary Data?
Data management challenges and data privacy concerns are potential burdens in managing large volumes of proprietary data. Organizations must ensure proper storage, security, and compliance measures to protect sensitive information and mitigate risks.
What Role Does the Chief Data Officer Play in the Development and Execution of a Proprietary Data Strategy?
The chief data officer plays a pivotal role in developing and executing a proprietary data strategy. They are responsible for identifying challenges in managing proprietary data and ensuring its effective utilization for innovation and business success.
How Can Companies Ensure That Their Proprietary Data Is Effectively Curated and Protected?
Companies can ensure effective curation and protection of their proprietary data through implementing data curation techniques, such as data classification and encryption. They should also prioritize data security and privacy by implementing robust security measures and staying compliant with relevant regulations.
You are using an outdated browser. Please upgrade your browser or activate Google Chrome Frame to improve your experience.
Vous utilisez actuellement un navigateur désuet . Veuillez mettre à jour votre navigateur ou activer Google Chrome Frame afin d'améliorer votre expérience.
Upcoming Webinar : Launching ORMIT™-Cortex 2.0 - A cheaper than free Oracle to PostgreSQL migration solution
2023 strategic planning for proprietary systems, strategic planning for proprietary oracle based systems, strategic planning for proprietary oracle based systems.
As IT executives, it is important to stay informed about the latest technology trends and developments, particularly when it comes to development and database platforms.
Posted by Patrick Hamou on 2023:02:23 16:20:05
Strategic Planning for Oracle Based Proprietary Systems
The IT industry continues to evolve rapidly, and organizations are increasingly turning to open source technologies to gain a competitive edge. Open-source development and database platforms offer several advantages over proprietary alternatives, particularly when it comes to cost, flexibility, and scalability.
One major benefit of open-source technologies is the ability to avoid vendor lock-ins. Proprietary software often comes with restrictive license agreements that limit the ways in which it can be used, making it difficult for organizations to switch to other technologies if they need to. In contrast, open-source software is free and open for anyone to use, modify, and distribute, giving organizations more control over their IT infrastructure.
Java and PostgreSQL are two open-source technologies that have gained widespread popularity in recent years. Java is a popular programming language that is widely used for developing web and mobile applications, while PostgreSQL is a powerful relational database management system that is well-suited for high-traffic, data-intensive applications.
Among other benefit of open-source technologies such as Java and PostgreSQL is their cost. Proprietary software often comes with high upfront costs and ongoing maintenance and upgrade fees, making it difficult for organizations to budget for. In contrast, open-source software is free to download and use, which can help organizations save significant amounts of money in the long run.
Open-source technologies are also more flexible and scalable than proprietary alternatives. With open-source software, organizations can easily customize and extend the functionality of the software to meet their specific needs. This flexibility allows organizations to adapt to changing business requirements and grow their IT infrastructure as their needs evolve.
Many organizations still use Oracle as their primary database management system. While Oracle is a powerful platform, it is also expensive and comes with restrictive license agreements. It is becoming more urgent for organizations to consider migrating to open-source alternatives such as PostgreSQL, which can provide similar capabilities at a fraction of the cost.
Migrating to an open-source database such as PostgreSQL or to development platforms such as Java can be a complex process, but it can be made easier with the use of automation tools. Automation tools can help organizations to plan and execute their migration in a more efficient and streamlined manner, minimizing the risk of disruption to their business operations.
In conclusion, open-source technologies like Java and PostgreSQL offer a number of benefits over proprietary alternatives, including cost savings, flexibility, and scalability. As organizations continue to face pressure to reduce costs and improve their IT infrastructure, it is important for IT executives to consider open-source technologies as a viable option.
RENAPS is a leader in Oracle to open-source migrations and can help you plan this transition with maximum efficiency and minimum disruption to your business operations. Let’s chat about your 5-year strategic plan and see if some of our solutions could fit in your future technological landscape!
Contact us at [email protected] for a quick chat about your IT objectives and strategic planning for 2024!
- ITInfrastructure
- JavaDevelopment
- OracleFormsMigration
- OracleDatabaseMigration
- CostSavings
- ORMITCortex
- ORMITJasper
Return to Blog
Forms and java.

- Contract Management
Supplier Management
Savings Management
- Data & Security
FAQ’s
oboloo Articles
Protecting Your Proprietary Data: A Must for Business Security
Introduction to the importance of proprietary data protection
In today’s digital era, data is the lifeblood of businesses. From customer information to trade secrets, proprietary data forms the foundation upon which companies build their success. But with cyber threats becoming increasingly sophisticated and prevalent, protecting this valuable asset has never been more critical.
Imagine waking up one day only to discover that your company’s most confidential information has fallen into the wrong hands. The thought alone sends shivers down your spine, doesn’t it? Unfortunately, this nightmare scenario is all too real for many businesses that neglect to prioritize the protection of their proprietary data.
From malicious hackers to internal leaks and accidental breaches, there are countless risks and threats lurking in cyberspace waiting to undermine your business security. In this blog post, we will delve into these challenges head-on and provide you with practical steps on how you can safeguard your invaluable proprietary data from falling victim to such perils.
So fasten your seatbelts as we embark on a journey towards fortifying the fortress around your business’s most precious asset – its proprietary data!
Common risks and threats to business data
Common Risks and Threats to Business Data
In today’s digital age, businesses are increasingly reliant on technology for storing and managing their proprietary data. However, this convenience also comes with its fair share of risks and threats. It is crucial for businesses to be aware of these potential dangers in order to protect their valuable information.
One common risk is the threat of cyber attacks. Hackers are constantly devising new ways to breach security systems and gain unauthorized access to sensitive data. Phishing emails, malware, ransomware attacks – the list goes on. These malicious actors can wreak havoc on a business by stealing or deleting important data, causing financial loss and reputational damage.
Another risk is insider threats. Whether intentional or unintentional, employees can pose a significant danger to proprietary data. Careless handling of confidential information or deliberate sabotage by disgruntled employees can lead to devastating consequences for a business.
Physical theft or damage is yet another threat that businesses must contend with. Theft of laptops, mobile devices, or physical servers containing sensitive data can result in severe repercussions if the information falls into the wrong hands.
Additionally, natural disasters such as fires or floods can destroy physical infrastructure where data is stored if proper precautions are not taken.
Furthermore…
It’s worth mentioning that…
There are various legal compliance requirements surrounding data protection…
To mitigate these risks…
By implementing strong passwords policies…
Regularly updating software and operating systems…
Limiting employee access privileges based on their roles…
The impact of data breaches on businesses
Data breaches can have devastating consequences for businesses, both big and small. The impact of a data breach goes far beyond just the loss of sensitive information. It can result in financial losses, damage to reputation, and even legal repercussions.
One of the immediate effects of a data breach is the potential loss of customers. When customers’ personal or financial information is compromised, they may lose trust in the business and choose to take their business elsewhere. This loss of customer loyalty can be difficult to recover from.
In addition to losing customers, businesses may also face hefty fines and penalties as a result of a data breach. Data protection regulations such as GDPR have strict guidelines on how businesses handle customer data. Failure to comply with these regulations can lead to significant financial consequences.
Another consequence is reputational damage. News spreads fast in today’s digital age, and word of a data breach can quickly tarnish a company’s reputation. Customers may view the business as careless or negligent when it comes to protecting their personal information.
Moreover, there are often costs associated with investigating and remedying the aftermath of a data breach. Businesses may need to hire forensic experts or invest in new security measures to prevent future breaches. These expenses can add up quickly and place an additional strain on already tight budgets.
The impact of a data breach on businesses cannot be underestimated. It has far-reaching implications that go beyond just monetary losses; it affects customer trust, brand reputation, and long-term viability.
Steps to protect your business’s proprietary data
Steps to Protect Your Business’s Proprietary Data
When it comes to safeguarding your business’s proprietary data, taking proactive steps is crucial. Here are some essential measures you can implement to ensure the protection of your valuable information.
1. Identify and categorize your data: Begin by identifying the types of proprietary data your business possesses, such as trade secrets, customer information, or financial records. Categorize them based on their level of sensitivity and importance.
2. Implement access controls: Limit access to sensitive data by implementing robust authentication procedures. Enforce strong passwords and consider using multi-factor authentication for an added layer of security.
3. Encrypt your data: Encryption is a powerful tool in protecting confidential information from unauthorized access. Utilize encryption protocols to secure both stored and transmitted data within your organization.
4. Regularly update software and systems: Keep all software applications, operating systems, firewalls, and antivirus programs up-to-date with the latest patches and updates. This helps protect against known vulnerabilities that cybercriminals may exploit.
5. Conduct regular security audits: Perform routine assessments of your IT infrastructure to identify any potential weaknesses or vulnerabilities in your systems’ security architecture.
6. Train employees on cybersecurity best practices: Educate staff members about the importance of data security through comprehensive training programs. Teach them how to recognize phishing attempts, avoid suspicious links or downloads, and practice good password hygiene.
7. Implement a clear BYOD policy (Bring Your Own Device): If employees use personal devices for work-related tasks, establish guidelines that outline acceptable usage policies and enforce strict security measures on these devices before accessing company resources.
8. Backup regularly: Establish a regular backup schedule for all critical business data so that you can quickly recover files in case of accidental deletion or other emergencies like ransomware attacks.
Remember that protecting proprietary data requires ongoing diligence.
As technology evolves rapidly,and new threats emerge,following these steps will help fortifyyour defenses against potential data breaches. By prioritizing the security of your proprietary data, you
Best practices for creating a secure data storage plan
Best practices for creating a secure data storage plan are crucial to safeguard your business’s proprietary data. With the increasing frequency and sophistication of cyber threats, it is essential to have robust measures in place. Here are some key steps you can take:
1. Classify and categorize your data: Identify the different types of proprietary information your business possesses and assign varying levels of security based on their sensitivity.
2. Implement access controls: Restrict access to sensitive data by using strong passwords, multi-factor authentication, and role-based permissions. Regularly review user privileges to ensure they align with job responsibilities.
3. Encrypt your data: Encryption converts your valuable information into an unreadable format unless accessed with the correct encryption keys. Consider encrypting both stored and transmitted data for maximum protection.
4. Backup regularly: Establish a backup system that automatically creates copies of important files at regular intervals. Store backups securely off-site or in the cloud to mitigate risks such as physical damage or theft.
5. Develop incident response protocols: Prepare clear guidelines for responding to potential breaches or incidents promptly and effectively, minimizing damage and downtime.
6. Train employees on security awareness: Educate staff about phishing scams, social engineering tactics, password best practices, and other common security threats they may encounter online or through email communications.
7. Monitor network activity: Utilize intrusion detection systems (IDS) or security information event management (SIEM) tools to monitor network traffic for any suspicious activities or signs of unauthorized access attempts.
Update software regularly: Keep all software applications up-to-date with the latest patches and security updates from vendors to address vulnerabilities that could be exploited by hackers.
Remember that securing proprietary data is an ongoing process; staying vigilant against evolving threats requires constant monitoring, periodic risk assessments, regular employee training sessions on emerging trends in cybersecurity, maintaining strong passwords policies across all platforms used within your organization.
By implementing these best practices consistently throughout your organization’s operations, you can significantly reduce the risk of a data breach and protect your valuable proprietary information
Training employees on data security protocols
Training employees on data security protocols is crucial in protecting your business’s proprietary data. Without proper training, employees may unknowingly engage in risky practices that could lead to a data breach or compromise sensitive information.
To start, develop a comprehensive training program that covers various aspects of data security. This should include educating employees about the importance of safeguarding proprietary data, identifying potential threats and risks, and understanding best practices for securely handling and storing information.
Consider conducting regular training sessions or workshops to keep employees updated on the latest cybersecurity trends and techniques. These sessions can also serve as an opportunity to address any questions or concerns they may have regarding data security.
It’s important to emphasize the role each employee plays in maintaining a secure environment. Encourage them to create strong passwords, be cautious when opening suspicious emails or attachments, and report any unusual activities promptly.
Additionally, provide resources such as guidelines or manuals that outline specific protocols for handling different types of proprietary data. This will ensure consistency across departments and reduce the chances of errors or accidental breaches.
Remember that effective training is an ongoing process. As technology evolves and new threats emerge, it’s essential to regularly review and update your training materials accordingly. By keeping employees informed about the ever-changing landscape of cybersecurity, you empower them with the knowledge needed to protect your business’s valuable assets.
In conclusion: Properly trained employees are a vital component in safeguarding your business’s proprietary data from potential threats and breaches. Regular education sessions help instill good habits among staff members while ensuring everyone understands their responsibilities when it comes to protecting sensitive information. Ongoing monitoring and updates are necessary as technology advances so that your team remains equipped with relevant knowledge against emerging cyber risks.
Utilizing technology for added protection
Utilizing technology for added protection is crucial in safeguarding your business’s proprietary data. With the ever-evolving landscape of cybersecurity threats, relying solely on manual processes and outdated methods is no longer enough. Incorporating advanced technological solutions can significantly enhance your data security measures.
One effective way to utilize technology for data protection is by implementing robust encryption protocols. Encryption converts sensitive information into unreadable code, making it nearly impossible for unauthorized individuals to decipher. By encrypting your proprietary data both at rest and in transit, you add an extra layer of security that ensures only authorized users can access the information.
Another important aspect of utilizing technology for added protection is investing in a reliable firewall system. Firewalls act as a barrier between your internal network and external threats, monitoring incoming and outgoing traffic to identify and block any suspicious activity or potential breaches.
Implementing multi-factor authentication (MFA) can also greatly enhance the security of your business’s proprietary data. MFA requires users to provide multiple forms of identification before accessing sensitive information or systems, reducing the risk of unauthorized access even if passwords are compromised.
In addition to these measures, regularly updating software and operating systems across all devices within your organization helps protect against known vulnerabilities that hackers often exploit. Keeping up with patches and updates ensures that you have the latest security features available.
Furthermore, leveraging cloud-based storage services with strong encryption capabilities provides an additional level of protection for your proprietary data while allowing flexibility in accessing files from anywhere securely. Many cloud providers offer built-in backup options as well, ensuring that even if local copies are compromised or lost due to hardware failures or natural disasters, you still have a secure copy stored remotely.
By integrating various technologies tailored specifically to address the unique needs of your business and its proprietary data, you can establish a comprehensive defense against cyber threats while ensuring compliance with industry regulations regarding privacy and confidentiality.
Remember: protecting your proprietary data should be an ongoing effort that adapts to emerging threats and evolving technology. Stay proactive, stay informed, and prioritize the security of
Constant monitoring and updating of security measures
Constant monitoring and updating of security measures is an essential aspect of protecting your business’s proprietary data. In today’s digital landscape, new threats and vulnerabilities emerge regularly, making it crucial to stay vigilant and proactive in safeguarding sensitive information.
To ensure the ongoing security of your data, it is important to regularly assess and update your security protocols. This includes conducting regular vulnerability scans, penetration testing, and patch management to identify and resolve any weaknesses or potential entry points for hackers.
Additionally, staying informed about the latest trends in cybersecurity is vital. By keeping up-to-date with industry news and attending relevant conferences or webinars, you can gain valuable insights into emerging threats and best practices for mitigating them.
Implementing a robust incident response plan is also crucial. This involves having clear procedures in place for detecting breaches, containing them promptly, investigating their causes thoroughly, and implementing necessary remediation measures.
Furthermore, employee education plays a significant role in maintaining strong security measures. Regular training sessions on data protection best practices should be provided to all staff members to ensure they are aware of their roles and responsibilities in preserving the confidentiality of proprietary information.
Lastly but importantly,
By adopting these practices as part of your overall cybersecurity strategy,
In conclusion
Importance of having a backup plan in case of a breach
Having a backup plan in place is crucial when it comes to protecting your proprietary data. In today’s digital landscape, no business is immune to the threat of a data breach. Even with robust security measures in place, there is always a possibility that hackers or other malicious actors could find their way into your systems.
In the event of a breach, having backups ensures that you still have access to essential information and can quickly recover from any potential damage. It allows you to restore your systems and get back up and running as soon as possible, minimizing downtime and reducing the impact on your business.
But simply having backups isn’t enough; they must be regularly tested and updated to ensure their reliability. Regularly backing up your data helps safeguard against hardware failures, accidental deletions, or even natural disasters. By storing copies of important files offsite or in the cloud, you can protect yourself from physical damage or loss at your primary location.
Additionally, it’s vital to have multiple layers of backups for added security. This means not relying solely on one method but using different types of storage solutions such as external hard drives, network-attached storage devices (NAS), or cloud-based platforms.
Remember that regular maintenance and monitoring are key components of an effective backup plan. You should check that backups are being performed correctly and verify their integrity regularly. Also, consider conducting periodic disaster recovery drills to test how well you can recover from different scenarios.
Having a comprehensive backup plan offers peace of mind knowing that if the worst happens – whether it’s due to cyberattacks or unforeseen circumstances – you won’t lose all your valuable data permanently. So take action now: implement reliable backup strategies tailored to your specific needs.
Conclusion: Priorit
Conclusion: Prioritizing the Protection of Your Proprietary Data
Protecting your business’s proprietary data is not just an option; it is a necessity in today’s digital landscape. The risks and threats to your valuable information are ever-present, and the consequences of a data breach can be devastating. By taking proactive steps to safeguard your data, you can minimize these risks and ensure the security of your company.
To start, create a comprehensive plan that outlines how you will store and protect your proprietary data. Consider implementing best practices such as encryption, strong passwords, and regular backups. Train employees on data security protocols so that everyone understands their role in preserving confidentiality.
Leverage technology solutions like firewalls, antivirus software, and intrusion detection systems to add layers of protection against external threats. Regularly monitor and update these measures to stay ahead of evolving cybersecurity challenges.
While all precautions should be taken to prevent breaches from happening, it is crucial also to have a contingency plan if one does occur. Establish proper backup procedures so that you can quickly recover any lost or compromised data.
By prioritizing the protection of your proprietary data, you demonstrate commitment towards building trust with stakeholders including customers, partners, and investors. It shows that you take privacy seriously while positioning yourself as a leader in maintaining high standards for secure operations.
Remember that protecting proprietary data is an ongoing process – it requires constant vigilance and adaptation as new threats emerge in our increasingly interconnected world. Stay informed about current trends in cybersecurity through industry publications or by consulting with experts who specialize in this field.
In conclusion (oops!), safeguarding your business’s proprietary information cannot be overstated; it must remain at the forefront of your organization’s security strategy. By doing so, you empower both yourself and those connected with your company by ensuring the integrity of sensitive information remains intact throughout its lifecycle.
Want to find out more about procurement?
Access more blogs, articles and FAQ's relating to procurement
The smarter way to have full visibility & control of your suppliers
Contract Management
Partnerships
Charities/Non-Profits
Service Status
Release Notes
Feel free to contact us here. Our support team will get back to you as soon as possible
Sustainability
- Guidelines For Guest Post Submissions
- Affiliate Partners

3 Things To Do Before Deciding To Develop A Proprietary Business System

It is not uncommon for businesses to rely on IT-based solutions as a way to streamline their operations. Technology enables better operations and more control over the flow of information, both of which are beneficial to businesses. There are also a lot of solutions on the market, so finding one that matches the specific needs of your business should not be difficult.
For a lot of businesses – perhaps including yours – developing a proprietary or custom system is an alternative worth considering. However, a proprietary solution isn’t always the best alternative to use for several reasons.
Before you jump into developing a custom business system for your company, here are the three things to consider:
Think Long Term.
Developing a custom solution is just the beginning. While the development costs are still very manageable, keeping the system up to date and well-maintained may be too much for the company. It is often more efficient to use an existing solution rather than developing one yourself for the lower running and maintenance costs.
When you use a system built by a tech company, you have the power of that company helping you keep the system up to date. The developers will handle all the hard work of patching bugs, delivering timely updates, and keeping the system relevant to the latest market challenges. Systems that have a lot of users will do these tasks at a much faster pace.
You don’t have to worry about paying for updates or investing too much in maintenance either. Be sure to compare the costs of developing and maintaining your own system with the costs of using existing solutions before making your decision.
Customize and Integrate.
As mentioned before, there are a lot of business solutions already available on the market. A lot of those solutions are designed to fit most businesses nicely. Other solutions are geared towards specific industries or operations, offering features that perfectly match your requirements.
The brewery POS system from Lavu is a good example of a tailored solution. It is a point of sale system developed for breweries, with specific features such as bar tabs and happy hours added to the mix. The basic POS features remain the same, but Lavu’s brewery POS system is customized further for a specific industry.
Similar customized solutions are easy to find. Even when you cannot find a system that offers all the features you need, it is often possible to integrate multiple systems through APIs and other means. Don’t forget to explore your options to customize and integrate existing solutions before deciding to go proprietary.
Time to Deployment.
Last but not least, there is also the fact that you need to invest sufficient time to develop a reliable proprietary business solution. This isn’t the case with using existing systems. A lot of business solutions are offered as a service (SaaS), allowing the entire solution to be deployed in a matter of minutes.
There is also the initial setup cost. A proprietary software must be run on your own server or cloud ecosystem, which means you have to prepare the deployment environment yourself. Existing solutions, especially solutions designed to be marketed as services, eliminate the substantial initial investment almost entirely.
Considering you also save a lot of time during deployment, SaaS is certainly an efficient option to use. With the user accounts set up, the entire system can be integrated with your existing business workflows immediately.
When you consider these factors, developing a proprietary system becomes a last resort. You should always take the three things we covered in this article into account before deciding to start with your own development project.
RELATED ARTICLES MORE FROM AUTHOR
How To Maintain Effective Business Operations
7 Signs That An Employee Is Suffering From Stress
Negotiating Your Commercial Lease: 7 Tips For Getting The Best Deal
Recent articles.
An Insider Look At E-Commerce In Singapore
Comparing Leaflet Distribution Pricing To Digital Ads
Elevate Your Team: Transforming Sales With New Home Sales Training Courses

What Is Proprietary: Everything You Need to Know
What is proprietary relates to ownership and the rights an owner may exercise in regards to his or her property or information. 3 min read updated on February 01, 2023
What is proprietary relates to ownership and the rights an owner may exercise in regards to his or her property or information. A proprietor is one that possesses, owns, or holds exclusive right to something.
Legally, what is proprietary often refers to proprietary information. Proprietary information is important, possibly sensitive information that a company owns. This information usually gives the company competitive advantage(s) in its market.
Things that can be used, known, produced, manufactured and/or marketed under the exclusive legal right of the inventor or maker may be proprietary. For example, a patented medicine is protected by intellectual property law against free market competition in regards to name, product, composition, or process of manufacture. If a manufacturer uses a particular manufacturing process that others do not know about ( trade secret protection ) or are forbidden to use (patent protection) then that is a proprietary process. A proprietary trademark is a name or logo that only the owner of that trademark can use.
If a business was in fact owned by and managed by an intelligence organization as a front, that would be proprietary to the intelligence organization.
Intellectual Property Protection
Protection to these proprietary articles are through intellectual property law: copyright, patents, trademark, etc. Unfortunately, however, at some time down the line, proprietary items and processes will lose their legal protection. This is when the information becomes a part of the public domain. Once that happens, anyone can use the item, process, or trademark as they see fit.
Baseball fans have proprietary attitudes toward their favorite team. When their team wins they say “we won,” not “they won,” as if they own or are part of the team.
Municipal corporations must act in the best interests of the citizens. This is a proprietary function. This proprietary function is different than its governmental functions, which are duties drawn from being a political part of a state.
Proprietary information is very important for the success of most businesses. This property may not be valued, but it is very valuable. Especially due to the marketplace and its competitive nature. Intellectual assets are highly sought-after commodities.
Because of the value and importance of such property, companies often prohibit directors, employees, and agents from disclosing confidential or proprietary information without proper authority in non-disclosure agreements/clauses. Sometimes this prohibition extends to after the employment relationship has ended.
If a contractor is hired and received proprietary information in order to do his or her work, a company often requires him/her to give back the information or property and to keep the information confidential.
Proprietary Information Can Include:
- Trade secrets
- Production methods
- Marketing strategies
- Salary structure
- Consumer contact information
- Past and present contracts
- Computer software
- Technology/hardware
- Employee knowledge
- Employee skill
- Financial data
- Test results
For information to be considered proprietary by a court, a company must treat the information as confidential. Courts will not find readily available information or public information proprietary. The information must also give the company a competitive advantage to be considered proprietary.
If the information is known to others outside of the company, then it will not give the company advantage. In order to be granted protection by a court, a company must also prove that it has taken “reasonable steps” to keep the information secret.
Courts do not require that companies take all possible measures to keep the information private. Courts do not require the secret to be absolutely or completely private. Reasonable steps in order to keep the information confidential must be “reasonable under the circumstances.”
A company has different ways to keep its information proprietary:
- Confidentiality clauses in employee contracts
- Nondisclosure clauses
- Non-compete agreements
- Security systems
- Restricting employee access with codes
- Data protection codes and procedures
- Secure phone lines
- Secure conference rooms
Companies should make sure that their covenants are reasonable in both time and location. Otherwise a court will not enforce them and will not restrict the unreasonable restriction of the former employee’s right to find a new job. They should also ensure that the employees that they do reveal trade secrets to have signed a confidentiality agreement of some kind or a court may not protect a trade secret of that small business.
If you need help with what is proprietary, you can post your legal need on UpCounsel’s marketplace. UpCounsel accepts only the top 5 percent of lawyers to its site. Lawyers on UpCounsel come from law schools such as Harvard Law and Yale Law and average 14 years of legal experience, including work with or on behalf of companies like Google, Menlo Ventures, and Airbnb.
Hire the top business lawyers and save up to 60% on legal fees
Content Approved by UpCounsel
- What Is a Proprietary Patent?
- Proprietary Interest
- Proprietary Information Agreement
- Define Proprietary Company
- Proprietary Information and Inventions Agreement
- Who Owns Trade Secret
- Government Non-Disclosure Agreement
- Confidentiality Contracts
- Proprietary Software License
- Confidentiality Agreement

Intellectual Property Issues: Valuing Intellectual Property in Your Business

Most companies that are worthy of raising venture capital have proprietary Intellectual Property (IP). In fact, the quality of the IP and the management team are often the two most important aspects of a venture capitalist’s investment decision. The challenge that many ventures face, however, is that most investors will not sign non-disclosure agreements (NDAs), and NDAs are critical to maintaining the proprietary nature of the IP. This article details the appropriate strategy for addressing proprietary IP in your business plan template in order to attract investor attention while retaining the confidentiality of your inventions. Focus on the Benefits of and Applications of the IP: The business plan should not discuss the confidential aspects of the IP. Rather, the plan should discuss the benefits of the IP. Remember that even the most amazing of technologies will not excite investors unless it has tangible benefits to customers.
The business plan first needs to discuss the products and services into which the IP will be integrated. It then must detail the benefits that these products and services have to customers and differentiate them from competitive products. When applicable, it is helpful to include non-confidential drawings and backup materials of the products and services in the Appendix. Focus on Customer Needs and the Relevant Market Size: The business plan must also discuss how the benefits of the IP fulfill a large customer need. To accomplish this, the plan needs to detail customer wants and needs and prove that the company’s offerings specifically meet these needs.
Secondly, the plan needs to discuss the marketplace in which the IP is offered and the size of this marketplace. Critical to this analysis is determining the relevant market size. The relevant market size equals a company’s sales if it were to capture 100% of its specific niche of the market. For example, a medical device’s market size would not be the trillion dollar healthcare market, but rather the sales of all competing medical devices. Focus on Competition and Competitive Differentiation: Your business plan must also prove that your IP is better than competitive inventions. In identifying competitors, note that listing no or few competitors have a negative connotation. It implies that there may not be a large enough customer need to support the company’s products and/or services. On the other hand, should there be too many competitors, then the market may be too saturated to support the profitability of a new entrant. The answer — any company that also serves the customer needs that you serve should be considered a competitor.
The business plan should detail both the positive and negative aspects of competitors’ IP and products/services and validate that your offerings are either superior in general, or are superior in serving a specific customer niche.
Prove that you can Execute on the Opportunity: As importantly as proving the quality of the IP and that a vast market exists for its applications, the business plan most prove that the company can successfully execute on the opportunity.
The plan should detail the company’s past accomplishments, including descriptions and dates when prior funding rounds were received, products and services were launched, revenue milestones were reached, key partnerships were executed, etc.
When a company is a complete start-up, and no milestones have been accomplished, the plan should focus on past accomplishments of the management team as an indicator of the company’s ability to execute successfully.
Getting Investors to Sign the NDA: If you are able to convince the prospective investor that the IP is integrated into a product/service which yields real customer benefits in a large market, then the investor will take the quality of the invention for granted when reviewing the plan. Later, during the due diligence process, the investor will review the actual technology. At this point, a discussion regarding signing an NDA would be appropriate.
How to Finish Your Business Plan in 1 Day!
Don’t you wish there was a faster, easier way to finish your business plan?
With Growthink’s Ultimate Business Plan Template you can finish your plan in just 8 hours or less!
Click here to finish your business plan today.
OR, Let Us Develop Your Plan For You
Since 1999, Growthink has developed business plans for thousands of companies who have gone on to achieve tremendous success.
Click here to see how our professional business plan writers can create your business plan for you.

- Billionaires
- Entrepreneurs

Preparing a Proprietary Position Business Plan
When preparing a proprietary position business plan, you should include sufficient details on the product and the company. Your description should be enough to determine whether your product is viable and how far along it is in development. You should also discuss the scope of the invention and how much work is needed to commercialize it. Highlight the background of your key personnel, and explain how your product will be better than competing products and services. It is imperative to include a sustainable competitive advantage.
When writing a business plan, it is important to be as detailed and accurate as possible. Make sure that your information is factual and backed by facts and figures, which will make your plan more credible to lenders and investors. Your plan will not be as effective if it does not support the claims it makes. If you have made claims in the previous section, make sure that you back them up with facts and figures. This will help you avoid any misunderstandings later.
You should always include a table of contents in your business plan, which should be at the end of the document. You should also have a summary, which is the first section of your plan. This should tell the reader what the rest of the document is about. Moreover, the summary should be short and to the point. The executive summary should be no longer than a page and should focus on the most important aspects of your business.
If your business is not based on a patent, it might not be profitable. Therefore, it is important to ensure that you have a solid business plan. Even though your idea is unique, your idea will be less appealing if no one knows about it. A good business plan should be clear and concise, and should avoid using industry jargon. It should focus on the most important facts about your concept and why it is a viable business.
The executive summary is a key element of your plan. It is the first element to read, and it should be clearly written. It should be factually accurate, and it should include any supporting data you have. If you are selling a product or service, the executive summary should be short and to the point. Ultimately, you should be able to sell the product or service to your potential customers. Your plan must provide value to the market and profit your buyers.
An executive summary should be a major part of your business plan. An executive summary is typically placed at the front of your plan. It is usually the first element you read and is the last element you write. It should be between two and three pages and highlight the more extensive categories of the plan. It should also state the benefits your company will achieve by using your product or service. The financial forecast should be a comprehensive analysis of your market.
The executive summary should be one of the most important parts of your business plan. It should highlight the strengths and weaknesses of your management team, and should be short and to the point. It is also essential to include a section that contains the company’s management team. The executive summary should contain a brief biography of the owners and key employees. It is advisable to provide a resume for each of these individuals in the appendix.
The executive summary should be the last element of your plan. It should be the first element to be read and is the most important part of your plan. It should also be well-written. If you have any questions or concerns, the executive summary should be well-written. In addition to the executive summary, the other elements of your business plan should be included. There are several important sections of a proprietary position business plan. You can create a table of contents by following a simple format and organizing it the way you want.
The executive summary is the most important part of a business plan. It should be well-written and concise, and it should be as short as possible. Despite the importance of this element, the executive summary is the most important part of the plan, and should be written as a standalone document. It is not a replacement for the entire plan, but a useful supplement to your other elements. Once you have completed the other elements, you can then begin writing the executive summary.

Establishing a Proprietary Position in Your Business Plan
Your business plan should be focused on establishing a proprietary position. This type of business involves introducing a product to the market and selling it at a profit. The product description should be sufficient to demonstrate the viability of the idea and the stage of development. You should also discuss the extent of your invention and the necessary development to commercialize it. You should mention the key personnel that are responsible for developing the concept. Finally, explain why your product is better than competitors’ products. Your goal is to gain a sustainable competitive advantage.
Your business plan should also include an executive summary. This is the first element of the document and should be the last element to be written. This section is typically two pages long and highlights the more detailed categories of your plan. You will write this section after you’ve finished writing the rest of the plan. To make the most of it, write a brief biography of the owner or founder, as well as a summary of key employees.
The executive summary is a crucial part of your business plan. Investors and lenders will want to see the management team and the business model. The executive summary should include brief biographies of the company’s key employees, as well as their resumes. You should also summarize the experience and skills of these people, and highlight the relevant skills and experience. When writing your executive summary, you need to make sure that the details are correct and that you have backed your claims with facts.
Your business plan should also contain an executive summary. The Executive Summary is the first element of your plan that prospective investors and lenders will read. The Executive Summary should make the reader excited about the business idea and make them want to read the rest of the plan. It is also important to keep in mind that the Executive Summary is often the last part of your business. If you’re planning on writing a long business, it is important to include an executive summary.
The executive summary should be included in your business plan. It should include the company’s history and major goals. The company’s management team is essential to the success of the project, so a brief biography of the owners and key employees is essential. Your executive summary should be two to three pages long. This section should be an outline of the entire business. In addition, you should highlight the most important skills and experience of each key employee.
Your business plan should also contain a management team section. This is an important element for investors and lenders, and it is an important element of your business plan. The management team is crucial, as it is the backbone of your company. It is imperative that the management team has the experience and qualifications to run a successful business. The management team should be well-qualified and have a solid track record in the industry. This section should be a brief overview of the key employees.
Your management team section is important. Many investors and lenders will be interested in the management team of your business. The executives of your company should have experience in the same industry and be knowledgeable about their work. They should have knowledge of the current market, which is crucial for a successful startup. The executive summary should also include the company’s management team and the products and services they will offer. The management team should be an important part of your business plan.
Besides the executive summary, your business plan should also include the company description. Lenders and investors look for qualified management teams when they evaluate your company. Therefore, you should highlight the skills and experience of your management team. Your business plan should not only be about the product or service; it should also describe the company’s culture. The other elements of your business plan should include the people and the team. These components should not be neglected because they will help you in securing financing.
The executive summary is the first element of your business plan. It should be as short and as concise as possible, but it must include all of the important information and figures. In addition, the executive summary should also have a table of contents. This is an essential part of your business plan, as investors and lenders are likely to want to know who is behind the company. The executive summary should summarize key points and emphasize the skills and experience of the company’s management team.
Also Check:
How to pronounce business correctly.
- proprietary position business plan
LEAVE A REPLY Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Unlocking the Power of Flanking Strike Macro: A Game-Changer in Online Gaming
Cubvh: the key to seo success, what is the origin of the name “hüriyer”, unveiling the potential of methstreams: a deep dive into cutting-edge technologies, wellhealthorganic buffalo milk tag, wellhealthorganic buffalo milk tag: a dairy delight revolution.

Related articles
Latest news, popular news, what is amm77x, block title.
© 2024 - 26 Blinkorg. All Rights Reserved. Made with Blinkorg.com
404 Not found
404 Not found
Civic Alert Systems wins Binghamton Business Plan Competition
BINGHAMTON (WBNG) -- Binghamton Mayor Jared Kraham announced the winners of this year’s Binghamton Business Plan Competition on Wednesday morning.
The competition awards funding to individuals and teams planning to develop businesses in the City of Binghamton.
This year’s winners were Vestal residents Ryan Crist and Jason Duda of Civic Alert Systems. They were awarded $5,000 along with other prizes.
“Modern web application that allows counties, municipalities, local governments of any kind to directly text their residents,” Crist said. “This was born out of things like the COVID crisis we had a few years ago or the Buffalo snowstorms or really any public disaster situation you can think of.”
Second place went to Umahari in Binghamton and third place was 2nd Heaven of Vestal.
Copyright 2024 WBNG. All rights reserved.

6 car crash on Binghamton highway cleared

Sheriff’s office seeks woman wanted on grand larceny warrant

State Police seek help finding animal abuser

Lightning strike kills rancher, 34 cows

‘Move Out Project’ collects 19,000 pounds of items to be donated
Latest news.

Judge excuses jurors, ending first day of deliberations in Trump’s hush money trial

Windsor 1st graders to compete in statewide math tournament

New York State offers tax reduction on adult-use cannabis
More From Forbes
Building A Strong Financial Foundation For Your Small Business
- Share to Facebook
- Share to Twitter
- Share to Linkedin
Starting and running a small business is an exciting venture, but it also comes with its financial challenges. Establishing a solid financial foundation is crucial for the long-term success and stability of your business. By proactively managing your finances, understanding key financial statements , and implementing effective financial planning, you can navigate the complexities of entrepreneurship and set your business up for sustainable growth and profitability. Taking these steps ensures that your business remains resilient in the face of financial uncertainties and positioned to capitalize on opportunities as they arise.
Here are five essential steps to help you build and maintain a strong financial base for your small business:
1. take care of your money mindset.
Your attitude towards money plays a significant role in your financial success. A positive money mindset involves viewing money as a tool to achieve your goals, rather than a source of stress or anxiety.
You can create a healthy relationship with money by:
- Educating yourself about financial management and investment.
- Setting clear, achievable financial goals.
- Practicing gratitude for what you have while striving for financial growth.
A positive money mindset can lead to better financial decisions, increased confidence, and a more proactive approach to managing your business finances.
2. Read and Understand Financial Statements
Apple brings back iphone 14 pro for first time—at lower price, refurbished, trump lashes out at robert de niro after actor calls him a tyrant outside courthouse, trump trial prosecutor ends closing argument after nearly 5 hours jury instructions set for wednesday.
Financial statements tell you the story of your business’s financial health. They provide insights into your company’s performance and help you make informed decisions.
The three primary financial statements you should be familiar with are:
- Income Statement: Shows your business’s revenues, expenses, and profits over a specific period.
- Balance Sheet: Provides a snapshot of your business’s assets, liabilities, and equity at a particular point in time.
- Cash Flow Statement: Tracks the flow of cash in and out of your business, highlighting operating, investing, and financing activities.
Understanding these statements allows you to identify trends, manage costs, and make strategic decisions to improve profitability.
3. Build a Business Financial Plan
A well-crafted financial plan is essential for guiding your business towards its goals. It should include:
- Revenue Projections: Estimate your sales and revenue for the upcoming period.
- Expense Budget: Outline your expected costs, including fixed and variable expenses.
- Profit and Loss Forecast: Predict your profits based on your revenue and expense estimates.
- Cash Flow Forecast: Anticipate your cash inflows and outflows to ensure you have enough liquidity to cover your obligations.
A comprehensive financial plan serves as a roadmap for your business, helping you stay focused and prepared for future challenges.
4. Monitor Your Results
Regularly monitoring your financial performance is crucial to ensure you stay on track. Set up a system to review your financial statements monthly or quarterly. Key performance indicators (KPIs) to track include:
- Gross Profit Margin: Measures the efficiency of your production process.
- Net Profit Margin: Indicates your overall profitability after all expenses.
- Current Ratio: Assesses your ability to pay short-term liabilities with short-term assets.
- Debt-to-Equity Ratio: Evaluates your financial leverage and risk.
By keeping an eye on these metrics, you can identify issues early, make necessary adjustments, and continuously improve your business’s financial health.
5. Have a Cash Management System
Effective cash management ensures your business has the liquidity it needs to operate smoothly. Key components of a cash management system include:
- Cash Flow Forecasting: Regularly predict your cash flow to anticipate shortages and surpluses.
- Receivables Management: Implement strategies to ensure timely collection of payments from customers.
- Payables Management: Optimize your payment schedule to maintain good relationships with suppliers while managing cash outflows.
- Emergency Fund: Set aside funds to cover unexpected expenses or revenue shortfalls.
A robust cash management system helps you maintain financial stability, avoid crises, and seize growth opportunities.
The bottom line is that building a strong financial foundation for your small business requires a proactive approach and continuous effort. By following these tips you can set your business up for long-term success. Remember, financial health is not a one-time achievement but an ongoing process that requires dedication and attention.
Melissa Houston, CPA is the author of Cash Confident: An Entrepreneur’s Guide to Creating a Profitable Business and the founder of She Means Profit , a bookkeeping and financial consultancy firm. As a Business Strategist for small business owners, Melissa helps women making mid-career shifts, to launch their dream businesses, and I also guide established business owners to grow their businesses to more profitably.
The opinions expressed in this article are not intended to replace any professional or expert accounting and/or tax advice whatsoever.

- Editorial Standards
- Reprints & Permissions
Join The Conversation
One Community. Many Voices. Create a free account to share your thoughts.
Forbes Community Guidelines
Our community is about connecting people through open and thoughtful conversations. We want our readers to share their views and exchange ideas and facts in a safe space.
In order to do so, please follow the posting rules in our site's Terms of Service. We've summarized some of those key rules below. Simply put, keep it civil.
Your post will be rejected if we notice that it seems to contain:
- False or intentionally out-of-context or misleading information
- Insults, profanity, incoherent, obscene or inflammatory language or threats of any kind
- Attacks on the identity of other commenters or the article's author
- Content that otherwise violates our site's terms.
User accounts will be blocked if we notice or believe that users are engaged in:
- Continuous attempts to re-post comments that have been previously moderated/rejected
- Racist, sexist, homophobic or other discriminatory comments
- Attempts or tactics that put the site security at risk
- Actions that otherwise violate our site's terms.
So, how can you be a power user?
- Stay on topic and share your insights
- Feel free to be clear and thoughtful to get your point across
- ‘Like’ or ‘Dislike’ to show your point of view.
- Protect your community.
- Use the report tool to alert us when someone breaks the rules.
Thanks for reading our community guidelines. Please read the full list of posting rules found in our site's Terms of Service.
- Share full article
Advertisement
Supported by
Senators See Possible Conflicts of Interest in Health Care Pricing Tools
A data analytics firm that helps insurers collect big fees while leaving some patients with unpaid bills has been summoned to explain its business model.

By Chris Hamby
Chris Hamby has been investigating the lucrative business of out-of-network medical claims.
The chairmen of two Senate committees overseeing health policy, concerned about companies “padding their own profits” at the expense of patients, are looking into the practices of a data analytics firm that works with big insurers to cut payments to medical providers.
The firm, MultiPlan, recommends what it says are fair payments for medical care, but the firm and the insurers can collect higher fees when payouts are lower. This business model could “result in an improper conflict of interest,” the chairmen of the two committees, Ron Wyden of Oregon and Bernie Sanders of Vermont, wrote in a letter to the firm’s chief executive that was released on Tuesday.
The senators called on MultiPlan to meet with the committees’ staffs to discuss an investigation last month by The New York Times that found the firm’s pricing tools could leave patients with unexpectedly large bills when they see doctors outside their health plans’ networks.
“Our committees are engaged in ongoing legislative work to put a stop to practices by plan service providers that drive up health care costs for consumers while padding their own profits,” the letter to Travis Dalton, the MultiPlan chief executive, said.
In a statement, MultiPlan said it was working with the Senate committees “to address their questions and explain the cost and complexity patients can face” when choosing high-priced care outside their networks. “We are committed to helping make health care transparent, fair and affordable for all,” the statement said.
The committees’ inquiry reflects growing scrutiny of the New York-based firm, which has largely remained out of the limelight even as it has staked out a dominant position in a lucrative corner of health care.
Another senator, Amy Klobuchar of Minnesota, this month asked federal antitrust regulators to investigate whether insurers and MultiPlan were colluding to fix prices, and multiple health systems have sued the firm, accusing it of similar anticompetitive behavior.
Separately, the Department of Labor said Tuesday that it had “a number of open investigations” into the type of pricing services MultiPlan provides, but declined to name specific companies. The agency, the primary regulator of employer-based health insurance, stressed in a statement that companies were legally obligated to ensure the firms processing medical claims acted in their employees’ best interest.
The letter from Mr. Wyden, a Democrat, and Mr. Sanders, an independent, also steps up attention on employer-based health insurance, which is the most common way Americans get coverage and a major component of MultiPlan’s business.
As health care costs climb, some employers are looking more closely at what they pay insurance companies to administer their plans, but they are often frustrated by contracts that limit access to their own claims data. To address this, a bipartisan group of senators, including Mr. Sanders, introduced legislation in December that would require insurers to turn over this data .
“Most businesses do their best to manage the ever-increasing cost of their group health plan, but it should be easier,” Senator Mike Braun, an Indiana Republican and cosponsor of the bill, said in a statement.
A majority of employers choose to pay medical claims with their own money and use an insurer to administer their plans. This setup, known as “self-funding,” can be lucrative for insurers like UnitedHealthcare, Cigna and Aetna, as well as specialized firms like MultiPlan.
The insurers pitch MultiPlan’s tools as a way to save employers money when their employees see a medical provider outside the plan’s network. The bills for these out-of-network providers are subject to negotiation, and insurers often send the claims to MultiPlan, which recommends an amount to pay.
Both MultiPlan and insurers typically collect a fee from the employer based on the size of what they call the “savings” — the provider’s list price minus the recommended payment. Lower payouts can mean bigger fees. Meanwhile, patients can be stuck with the unpaid balance, The Times investigation found.
Companies are legally obligated to ensure the insurers act in employees’ best interest, and a closely watched lawsuit filed last year could force them to become more active monitors.
A worker at Johnson & Johnson sued the company, saying it had failed to adequately oversee the administrator of its drug benefits plan. By paying too much — in one instance, $10,000 for a drug that was available for as little as $28.40 — the company had allowed the administrator, the Cigna subsidiary Express Scripts, to profit at employees’ expense, the suit claimed.
In a statement, Johnson & Johnson called the claims “meritless” and said, “We are committed to our employees and seek to provide the best coverage.”
A small industry of consultants, lawyers and data analysts has arisen to help companies step up monitoring and negotiate better deals with the insurers administering their plans.
Kraft Heinz last year sued Aetna, claiming the insurer improperly paid claims and kept millions in undisclosed fees. Trustees for a union health plan in Massachusetts sued Blue Cross Blue Shield of Massachusetts in 2021, accusing the insurer of repeatedly overpaying claims and then charging a fee to correct the errors. And in January the Department of Labor sued Blue Cross and Blue Shield of Minnesota, claiming the company forced multiple employers to pay medical providers’ tax bills without disclosing the charges.
(Aetna declined to comment on the case but said it worked with employers “to facilitate access to quality, affordable and convenient health care.” Blue Cross and Blue Shield of Minnesota said the government’s allegations were “without merit” and “based on unsupported interpretations” of the law. A court dismissed the Massachusetts case.)
The success of the employers’ efforts sometimes hinges on an unsettled legal question: Does a company’s duty to act solely in its employees’ best interest extend to insurers and firms like MultiPlan? Courts have reached different conclusions.
MultiPlan has argued that the answer is no, and in March a federal judge in California agreed, dismissing the company from a lawsuit filed by medical providers. The case against the insurer, Cigna, was allowed to go forward.
In pitches to investors, MultiPlan has highlighted its murky legal obligations. Because the firm doesn’t provide insurance or pay claims, it noted in a public filing, “we generally are not directly regulated and face significantly lower levels of regulatory complexity.”
Chris Hamby is an investigative reporter for The Times, based in Washington. More about Chris Hamby
Our Coverage of Congress
Here’s the latest news and analysis from capitol hill..
Border Deal Fails Again: Senate Republicans blocked a bipartisan border enforcement bill for a second time this year , voting down legislation they initially insisted upon to stem a surge of migrants across the United States border with Mexico.
Noncitizen Voting Law: The House passed legislation that would undo a District of Columbia law allowing noncitizens to vote in local elections, part of a broader bid by Republicans to amplify false claims of widespread illegal voting by immigrants.
Democrats’ ‘Sword and Shield’ Strategy: Despite certain defeat, Senator Chuck Schumer, the majority leader, is pushing showdown votes on border security and abortion rights ahead of this year’s elections. Here’s why .
Trump’s Meeting With Oil Executives: Senate Democrats opened an investigation into a fund-raising dinner where Donald Trump asked oil executives to donate $1 billion to his campaign and vowed to roll back climate rules .
A New Centrism Rises: The emergence of a new form of American centrism — call it neopopulism — has made the last four years arguably the most productive period of bipartisanship in Washington in decades.
- Work & Careers
- Life & Arts
Become an FT subscriber
Try unlimited access Only $1 for 4 weeks
Then $75 per month. Complete digital access to quality FT journalism on any device. Cancel anytime during your trial.
- Global news & analysis
- Expert opinion
- Special features
- FirstFT newsletter
- Videos & Podcasts
- Android & iOS app
- FT Edit app
- 10 gift articles per month
Explore more offers.
Standard digital.
- FT Digital Edition
Premium Digital
Print + premium digital, ft professional, weekend print + standard digital, weekend print + premium digital.
Essential digital access to quality FT journalism on any device. Pay a year upfront and save 20%.
- Global news & analysis
- Exclusive FT analysis
- FT App on Android & iOS
- FirstFT: the day's biggest stories
- 20+ curated newsletters
- Follow topics & set alerts with myFT
- FT Videos & Podcasts
- 20 monthly gift articles to share
- Lex: FT's flagship investment column
- 15+ Premium newsletters by leading experts
- FT Digital Edition: our digitised print edition
- Weekday Print Edition
- Videos & Podcasts
- Premium newsletters
- 10 additional gift articles per month
- FT Weekend Print delivery
- Everything in Standard Digital
- Everything in Premium Digital
Complete digital access to quality FT journalism with expert analysis from industry leaders. Pay a year upfront and save 20%.
- 10 monthly gift articles to share
- Everything in Print
- Make and share highlights
- FT Workspace
- Markets data widget
- Subscription Manager
- Workflow integrations
- Occasional readers go free
- Volume discount
Terms & Conditions apply
Explore our full range of subscriptions.
Why the ft.
See why over a million readers pay to read the Financial Times.
International Edition
European leaders are planning a $4.3 billion Iron Dome-style defense system
- European nations say they're planning a $4.3 billion joint air and missile defense system.
- Polish Prime Minister Donald Tusk said creating an Iron Dome similar to Israel's was "necessary."
- The European Sky Shield Initiative involves 21 countries and aims to enhance NATO's defenses.

European countries are preparing to disclose plans for a $4.3 billion Iron Dome-style air and missile defense system, Poland's prime minister has announced.
Donald Tusk told the Polish broadcaster AVN that the proposal, which involves the cooperation of 21 nations, would be presented to the European Council in a matter of days, according to the Kyiv Post .
The European Sky Shield Initiative is conceived as a means to jointly procure ground-based interoperable air-defense systems.
"The recent attack on Israel showed how essential such systems are. There is no reason for Europe not to have its missile-defense shield," Tusk said, according to The Telegraph .
"Creating an Iron Dome against missiles and drones is necessary," he added.
In a not-too-subtle reference to Russia, Tusk also said it didn't take much imagination to figure out where a potential attack on Europe might come from, the Telegraph reported.
Related stories
Israel's Iron Dome has long been seen as one of the world's most advanced air-defense systems, protecting the country's skies from rockets and other projectiles.
In April, Iran launched a barrage of missiles and drones at Israel, which Israel's air defenses almost completely shot down, with the assistance of US and UK forces .
While a direct hot-war attack by Russia on NATO Europe isn't considered an immediate likelihood, many countries — particularly those that border Russia — are deeply alarmed . Many are also beefing up their defense spending in ways that were unimaginable before Russia's full-scale invasion of Ukraine .
ESSI was first mooted by German Chancellor Olaf Scholz in 2022, not long after Russia had begun pounding Ukraine's civilian infrastructure with rockets. It's been led by Germany ever since.
In July last year, Austria and Switzerland — both traditionally neutral states — signed up to the initiative, and as of February this year, the number of countries had grown to 21, with the participation of Turkey and Greece .
The German Institute for International and Security Affairs , or SWP, outlined in a report last year some of the systems the German government was seeking to buy or replenish as part of ESSI. These included US-made Patriots, the IRIS-T SLM — a short-to-medium-range system capable of targeting drones, aircraft, and cruise missiles — and the long-range Arrow system in use in Israel.
SWP also said that although it considered a Russian attack on NATO countries unlikely in the immediate term, "improving air and missile defense in Europe could curb Russia's coercive power vis-à-vis NATO and thereby strengthen the cohesion of the alliance."
Despite Tusk's championing of ESSI, it has faced challenges from Polish President Andrzej Duda, who has opposed joining it on the grounds that the country already has its own joint air-defense agreements with the US and the UK.
Watch: Russia flaunts intercontinental ballistic missile in new video
- Main content
Medicare Plan to Verify Negotiated Drug Prices Spurs Unease
By Nyah Phengsitthy

The Medicare system proposed by the Biden administration to verify negotiated drug prices reach eligible individuals is generating concerns about compliance and operational challenges for manufacturers and dispensing entities.
The Centers for Medicare & Medicaid Services continues to swiftly roll out its drug price negotiation program after publishing a draft guidance earlier this month for the next cycle of its price-setting scheme. The plan, created under the Inflation Reduction Act, is expected to lower the costs of 10 Medicare Part D drugs as of 2026 and another 15 drugs in 2027.
The guidance introduced new details on the implementation of the maximum fair price (MFP) of selected drugs and the use of a Medicare transaction facilitator (MTF) to streamline the exchange of data and payments among pharmaceutical supply chain entities to verify drug prices are dispensed to eligible individuals.
The agency is asking the public to weigh in on the guidance by July 2, but feedback already is underscoring the slew of responsibilities handed to drugmakers and dispensing entities, such as pharmacies, to carry out the drug’s maximum fair price.
“The prior finalized guidance from last year had left open a bunch of questions that were to be addressed in this next round. It was really important that all of those issues were addressed in this round because the clock is ticking,” said William Sarraille, a veteran pharmaceutical defense lawyer, now a regulatory consultant at Saraille & Associates.
But the guidance “pulls back from significant portions of what needs to be done and sort of dumps those critical activities on manufacturers, covered entities, contract pharmacies, and the rest of the players in the distribution channel,” Sarraille said. “That’s really unfortunate. It may suggest that the start of this program might be very bumpy, very rocky.”
Manufacturers must comply with requirements such as following a prompt payment window, recording and documenting claims, and avoiding duplicate discounts that may occur between the maximum fair price and the federal 340B Drug Pricing Program—all of which could be subject to a dispute process or civil monetary penalties if not properly executed.
The CMS did not respond to a request for comment in time for publication.
Data, Payment Facilitation
The facilitator’s primary focus is to collect and send claim-level data to manufacturers and receive payment information from manufacturers. The CMS proposes drugmaker participation for the MTF data exchange is mandatory to verify that the drug’s price was carried out in each instance.
But drugmakers “may need to invest in new systems, enhance coordination with dispensing entities and other manufacturers, and navigate complex regulatory requirements to ensure compliance and avoid penalties,” said Eliza Biedziak, senior manager in the forensic and integrity services at Ernst & Young LLP.
Manufacturers are also up against the “complexities of receiving and processing claim-level data elements, conducting secure data exchanges, calculating accurate refunds, and maintaining compliance with statutory obligations,” Biedziak said in an email.
The agency requires drugmakers to meet a “14-day prompt MFP payment window” for executing the MFP refund for each claim. Manufacturers may be liable for civil monetary penalties if the price is not available to a dispensing entity or if the report with payment-related data is not provided to the facilitator within that window.
That window period may also pose as a concern for dispensing entities because the “true-up” payment a manufacturer pays a pharmacy to fulfill their obligation to make the MFP available to dispensers “could actually be much longer than 14 days,” said Ronna Hauser, senior vice president of policy and pharmacy affairs for the National Community Pharmacists Association.
“We’re very concerned about floating this program” because “manufacturer refund payments could take up to four to six weeks to arrive in pharmacies,” Hauser said.
“Providing patient care and counseling for these drugs is very important, and we want to make sure patients are getting the benefit of using these drugs. We have to remain a viable partner in dispensing these drugs,” she said.
NCPA represents over 19,000 independent pharmacies, which feeds into the thousands of other dispensing entities and providers that distribute Part D drugs.
The CMS also seeks comments on using the MTF as a voluntary payment facilitator to address the “lack of connection” between manufacturers and dispensing entities.
The agency weighs two payment options: the first requires the MTF to collect dispensing entities’ banking information and provide it to manufacturers, and the second option requires the MTF to receive aggregated refund amounts from manufacturers and pass them through to dispensing entities.
The Pharmaceutical Research and Manufacturers of America, a top drugmaker industry group, said it welcomes the opportunity to provide input on the guidance.
“We appreciate the consideration CMS is giving to operationalizing the maximum fair price,” said Nicole Longo, deputy vice president of public affairs for PhRMA. “The proposal to use a Medicare Transaction Facilitator to help with the exchange of data and as an option to facilitate access to the maximum fair price is a step in the right direction.”
Avoiding Duplicate Discounts
Section 340B of the Public Health Service Act requires drugmakers to discount drugs for qualifying providers that treat low-income and uninsured patients. Under the plan, eligible health-care organizations can receive certain drugs at discounted prices from manufacturers.
The 340B statute prohibits duplicate discounts.
Drugmakers are required to provide access of the MFP to 340B covered entities in a nonduplicated amount to the 340B ceiling price if the MFP is lower than the 340B ceiling price for the selected drug.
The agency said it won’t assume responsibility for “deduplicating” discounts, and it is handing that task to the drugmakers. The CMS intends to provide “a process to identify applicable 340B eligible claims through the reporting of payment elements to the MTF.” The eligible claims can be voluntarily supplied by a dispensing entity.
The voluntary nature of providing 340B claims, though, “will pose a significant challenge for the manufacturers to identify 340B claims, and they will be at risk to possibly extend double discounts via MFP and 340B,” Biedziak said. “The current framework requires manufacturers to validate 340B claims and ensure compliance with pricing obligations yet does not equip them with the necessary data to efficiently identify 340B utilization.”
If it is later determined that the MFP of a drug was provided to a 340B-eligible individual and the 340B ceiling price is lower, manufacturers must promptly refund the difference to the 340B covered entity.
“We think the objective is entirely reasonable—duplicate and cumulative discounts not be part of the system moving forward,” said Mark E. Miller, executive vice president of health care for Arnold Ventures. “CMS has created a transition system, and manufacturers will be required to utilize it in order to properly litigate these discounts.”
To contact the reporter on this story: Nyah Phengsitthy in Washington at [email protected]
To contact the editors responsible for this story: Zachary Sherwood at [email protected] ; Brent Bierman at [email protected]
Learn more about Bloomberg Law or Log In to keep reading:
Learn about bloomberg law.
AI-powered legal analytics, workflow tools and premium legal & business news.
Already a subscriber?
Log in to keep reading or access research tools.

IMAGES
VIDEO
COMMENTS
1. As an entrepreneur, it's important to assemble your knowledge into a content system that's easy to follow - a proprietary system. Clients frequently ask me how to put together their proprietary system and in what order the information should go. The confusion comes from the difference between working privately with clients versus group ...
NOW Capital Partners can offer valuable insights, diversification, risk mitigation, and growth opportunities. Ultimately, a balanced strategy that combines the benefits of proprietary systems with the expertise NOW Capital Partners consultants is more likely to result in sustained company value and success in the ever-evolving business landscape.
Proprietary technology is a process, tool, system or similar item that is the property of a business or an individual and provides some sort of benefit or advantage to the owner. Companies that ...
Protect your competitive advantage. Companies need to be more focused on proprietary data — data that is unique to a company and can be used to create a sustainable competitive advantage. The ...
Many businesses use written non-disclosure agreements (NDAs) to keep employees from revealing proprietary information while working for the organization. Suppliers, outside sales representatives and other business partners can also be required to sign NDAs before accessing your business's data. Non-compete clauses.
An open platform provides greater flexibility, but it can be more difficult to operate and maintain. Proprietary software, on the other hand, is easier to use but limits your options and involves ...
These underlying software structures enable computers and other devices to function. Proprietary operating systems have been around for a long time, with most of them created by major computer manufacturers like Microsoft and Apple. Examples of proprietary database software include: Windows 10, 11. iOS.
Describe Your Services or Products. The business plan should have a section that explains the services or products that you're offering. This is the part where you can also describe how they fit ...
Companies need to focus on acquiring and leveraging proprietary data. Proprietary data is essential for organizations as it helps in making informed business decisions and can lead to increased profitability. Applying proprietary data can lead to improved business performance and enable targeted marketing campaigns.
Automation tools can help organizations to plan and execute their migration in a more efficient and streamlined manner, minimizing the risk of disruption to their business operations. In conclusion, open-source technologies like Java and PostgreSQL offer a number of benefits over proprietary alternatives, including cost savings, flexibility ...
Best practices for creating a secure data storage plan. Best practices for creating a secure data storage plan are crucial to safeguard your business's proprietary data. With the increasing frequency and sophistication of cyber threats, it is essential to have robust measures in place. Here are some key steps you can take: 1.
A proprietary software must be run on your own server or cloud ecosystem, which means you have to prepare the deployment environment yourself. Existing solutions, especially solutions designed to be marketed as services, eliminate the substantial initial investment almost entirely. Considering you also save a lot of time during deployment, SaaS ...
A proprietor is one that possesses, owns, or holds exclusive right to something. Legally, what is proprietary often refers to proprietary information. Proprietary information is important, possibly sensitive information that a company owns. This information usually gives the company competitive advantage (s) in its market.
A corporate system for protecting proprietary information would include a comprehensive plan ranging from restricting employee access, to data protection, to securing phone lines and meeting rooms.
74PROPRIETARY SYSTEMS VERSUS OUT-OF-BOX APPLICATIONS. Proprietary systems are those developed and owned by a company. For example, Amazon.com's one-click checkout technology is a proprietary system that the online retailer developed in 1997. Similarly, the auction Web site developed and enhanced by eBay founder Pierre Omidyar in the late 1990s ...
4.1.3 ROV dynamic positioning. The first DP system to gain wide acceptance with ROV manufacturers and operators was produced by UK-based SeeByte Ltd. As the technology gained acceptance, the various ROV original equipment manufacturers (OEMs) have gotten into the act to produce their own proprietary systems.
The last opportunity factor is a proprietary advantage. It's not necessary to have a proprietary advantage, but it can add a tremendous amount of value to a business idea. This video provides an ...
In the dynamic world of business planning, proprietary systems stand as the vanguard of innovation and distinctiveness. When we risky into the realm of business strategies and entrepreneurial acumen, the term "proprietary systems" unveils a our of unparalleled advantage.
Intellectual Property Issues: Valuing Intellectual Property in Your Business. Written by Dave Lavinsky. Most companies that are worthy of raising venture capital have proprietary Intellectual Property (IP). In fact, the quality of the IP and the management team are often the two most important aspects of a venture capitalist's investment ...
The executive summary should be included in your business plan. It should include the company's history and major goals. The company's management team is essential to the success of the project, so a brief biography of the owners and key employees is essential. Your executive summary should be two to three pages long.
Talk to a Fitter Law attorney: proprietary information is a critical component of any business's success. By understanding the legal definition of proprietary information and taking steps to protect it, you can safeguard your competitive advantage and ensure the long-term viability of your business . Connect with a Fitter Law Attorney
Business Planning INTENSE DIVE (Pt. 2) About four period previous, I created The Simply Work Plan Ever. Over the gone four years, it's have downloaded by thousands of folks just proving how mild it can be to create a solid strategic plan for your business. I've built several videos, about Business Planen. Most of these video were 20 minutes ...
Proprietary technology lives the combination to tools, processes, and unique capabilities businesses develop or acquire to gain a inexpensive edge. ... Business Rules Version: The version of the HHSC EVV Business ... Custom System that a System User maybe choose to plan Membership Technical visits. Person and our partners process data to provide:
The competition awards funding to individuals and teams planning to develop businesses in the city.
Here are five essential steps to help you build and maintain a strong financial base for your small business: 1. Take Care of Your Money Mindset. Your attitude towards money plays a significant ...
AP Photo/Evgeniy Maloletka, File. Six NATO countries are planning a "drone wall" to defend against Russia. Finland, Norway, Poland, and the Baltic states want to prevent smuggling and Russian ...
Trustees for a union health plan in Massachusetts sued Blue Cross Blue Shield of Massachusetts in 2021, accusing the insurer of repeatedly overpaying claims and then charging a fee to correct the ...
Meta's artificial intelligence chief said the large language models that power generative AI products such as ChatGPT would never achieve the ability to reason and plan like humans, as he ...
European countries are preparing to disclose plans for a $4.3 billion Iron Dome-style air and missile defense system, Poland's prime minister has announced. Donald Tusk told the Polish broadcaster ...
The Centers for Medicare & Medicaid Services continues to swiftly roll out its drug price negotiation program after publishing a draft guidance earlier this month for the next cycle of its price-setting scheme. The plan, created under the Inflation Reduction Act, is expected to lower the costs of 10 Medicare Part D drugs as of 2026 and another ...