- USC Libraries
- Research Guides

Organizing Your Social Sciences Research Paper
- Theoretical Framework
- Purpose of Guide
- Design Flaws to Avoid
- Independent and Dependent Variables
- Glossary of Research Terms
- Reading Research Effectively
- Narrowing a Topic Idea
- Broadening a Topic Idea
- Extending the Timeliness of a Topic Idea
- Academic Writing Style
- Applying Critical Thinking
- Choosing a Title
- Making an Outline
- Paragraph Development
- Research Process Video Series
- Executive Summary
- The C.A.R.S. Model
- Background Information
- The Research Problem/Question
- Citation Tracking
- Content Alert Services
- Evaluating Sources
- Primary Sources
- Secondary Sources
- Tiertiary Sources
- Scholarly vs. Popular Publications
- Qualitative Methods
- Quantitative Methods
- Insiderness
- Using Non-Textual Elements
- Limitations of the Study
- Common Grammar Mistakes
- Writing Concisely
- Avoiding Plagiarism
- Footnotes or Endnotes?
- Further Readings
- Generative AI and Writing
- USC Libraries Tutorials and Other Guides
- Bibliography
Theories are formulated to explain, predict, and understand phenomena and, in many cases, to challenge and extend existing knowledge within the limits of critical bounded assumptions or predictions of behavior. The theoretical framework is the structure that can hold or support a theory of a research study. The theoretical framework encompasses not just the theory, but the narrative explanation about how the researcher engages in using the theory and its underlying assumptions to investigate the research problem. It is the structure of your paper that summarizes concepts, ideas, and theories derived from prior research studies and which was synthesized in order to form a conceptual basis for your analysis and interpretation of meaning found within your research.
Abend, Gabriel. "The Meaning of Theory." Sociological Theory 26 (June 2008): 173–199; Kivunja, Charles. "Distinguishing between Theory, Theoretical Framework, and Conceptual Framework: A Systematic Review of Lessons from the Field." International Journal of Higher Education 7 (December 2018): 44-53; Swanson, Richard A. Theory Building in Applied Disciplines . San Francisco, CA: Berrett-Koehler Publishers 2013; Varpio, Lara, Elise Paradis, Sebastian Uijtdehaage, and Meredith Young. "The Distinctions between Theory, Theoretical Framework, and Conceptual Framework." Academic Medicine 95 (July 2020): 989-994.
Importance of Theory and a Theoretical Framework
Theories can be unfamiliar to the beginning researcher because they are rarely applied in high school social studies curriculum and, as a result, can come across as unfamiliar and imprecise when first introduced as part of a writing assignment. However, in their most simplified form, a theory is simply a set of assumptions or predictions about something you think will happen based on existing evidence and that can be tested to see if those outcomes turn out to be true. Of course, it is slightly more deliberate than that, therefore, summarized from Kivunja (2018, p. 46), here are the essential characteristics of a theory.
- It is logical and coherent
- It has clear definitions of terms or variables, and has boundary conditions [i.e., it is not an open-ended statement]
- It has a domain where it applies
- It has clearly described relationships among variables
- It describes, explains, and makes specific predictions
- It comprises of concepts, themes, principles, and constructs
- It must have been based on empirical data [i.e., it is not a guess]
- It must have made claims that are subject to testing, been tested and verified
- It must be clear and concise
- Its assertions or predictions must be different and better than those in existing theories
- Its predictions must be general enough to be applicable to and understood within multiple contexts
- Its assertions or predictions are relevant, and if applied as predicted, will result in the predicted outcome
- The assertions and predictions are not immutable, but subject to revision and improvement as researchers use the theory to make sense of phenomena
- Its concepts and principles explain what is going on and why
- Its concepts and principles are substantive enough to enable us to predict a future
Given these characteristics, a theory can best be understood as the foundation from which you investigate assumptions or predictions derived from previous studies about the research problem, but in a way that leads to new knowledge and understanding as well as, in some cases, discovering how to improve the relevance of the theory itself or to argue that the theory is outdated and a new theory needs to be formulated based on new evidence.
A theoretical framework consists of concepts and, together with their definitions and reference to relevant scholarly literature, existing theory that is used for your particular study. The theoretical framework must demonstrate an understanding of theories and concepts that are relevant to the topic of your research paper and that relate to the broader areas of knowledge being considered.
The theoretical framework is most often not something readily found within the literature . You must review course readings and pertinent research studies for theories and analytic models that are relevant to the research problem you are investigating. The selection of a theory should depend on its appropriateness, ease of application, and explanatory power.
The theoretical framework strengthens the study in the following ways :
- An explicit statement of theoretical assumptions permits the reader to evaluate them critically.
- The theoretical framework connects the researcher to existing knowledge. Guided by a relevant theory, you are given a basis for your hypotheses and choice of research methods.
- Articulating the theoretical assumptions of a research study forces you to address questions of why and how. It permits you to intellectually transition from simply describing a phenomenon you have observed to generalizing about various aspects of that phenomenon.
- Having a theory helps you identify the limits to those generalizations. A theoretical framework specifies which key variables influence a phenomenon of interest and highlights the need to examine how those key variables might differ and under what circumstances.
- The theoretical framework adds context around the theory itself based on how scholars had previously tested the theory in relation their overall research design [i.e., purpose of the study, methods of collecting data or information, methods of analysis, the time frame in which information is collected, study setting, and the methodological strategy used to conduct the research].
By virtue of its applicative nature, good theory in the social sciences is of value precisely because it fulfills one primary purpose: to explain the meaning, nature, and challenges associated with a phenomenon, often experienced but unexplained in the world in which we live, so that we may use that knowledge and understanding to act in more informed and effective ways.
The Conceptual Framework. College of Education. Alabama State University; Corvellec, Hervé, ed. What is Theory?: Answers from the Social and Cultural Sciences . Stockholm: Copenhagen Business School Press, 2013; Asher, Herbert B. Theory-Building and Data Analysis in the Social Sciences . Knoxville, TN: University of Tennessee Press, 1984; Drafting an Argument. Writing@CSU. Colorado State University; Kivunja, Charles. "Distinguishing between Theory, Theoretical Framework, and Conceptual Framework: A Systematic Review of Lessons from the Field." International Journal of Higher Education 7 (2018): 44-53; Omodan, Bunmi Isaiah. "A Model for Selecting Theoretical Framework through Epistemology of Research Paradigms." African Journal of Inter/Multidisciplinary Studies 4 (2022): 275-285; Ravitch, Sharon M. and Matthew Riggan. Reason and Rigor: How Conceptual Frameworks Guide Research . Second edition. Los Angeles, CA: SAGE, 2017; Trochim, William M.K. Philosophy of Research. Research Methods Knowledge Base. 2006; Jarvis, Peter. The Practitioner-Researcher. Developing Theory from Practice . San Francisco, CA: Jossey-Bass, 1999.
Strategies for Developing the Theoretical Framework
I. Developing the Framework
Here are some strategies to develop of an effective theoretical framework:
- Examine your thesis title and research problem . The research problem anchors your entire study and forms the basis from which you construct your theoretical framework.
- Brainstorm about what you consider to be the key variables in your research . Answer the question, "What factors contribute to the presumed effect?"
- Review related literature to find how scholars have addressed your research problem. Identify the assumptions from which the author(s) addressed the problem.
- List the constructs and variables that might be relevant to your study. Group these variables into independent and dependent categories.
- Review key social science theories that are introduced to you in your course readings and choose the theory that can best explain the relationships between the key variables in your study [note the Writing Tip on this page].
- Discuss the assumptions or propositions of this theory and point out their relevance to your research.
A theoretical framework is used to limit the scope of the relevant data by focusing on specific variables and defining the specific viewpoint [framework] that the researcher will take in analyzing and interpreting the data to be gathered. It also facilitates the understanding of concepts and variables according to given definitions and builds new knowledge by validating or challenging theoretical assumptions.
II. Purpose
Think of theories as the conceptual basis for understanding, analyzing, and designing ways to investigate relationships within social systems. To that end, the following roles served by a theory can help guide the development of your framework.
- Means by which new research data can be interpreted and coded for future use,
- Response to new problems that have no previously identified solutions strategy,
- Means for identifying and defining research problems,
- Means for prescribing or evaluating solutions to research problems,
- Ways of discerning certain facts among the accumulated knowledge that are important and which facts are not,
- Means of giving old data new interpretations and new meaning,
- Means by which to identify important new issues and prescribe the most critical research questions that need to be answered to maximize understanding of the issue,
- Means of providing members of a professional discipline with a common language and a frame of reference for defining the boundaries of their profession, and
- Means to guide and inform research so that it can, in turn, guide research efforts and improve professional practice.
Adapted from: Torraco, R. J. “Theory-Building Research Methods.” In Swanson R. A. and E. F. Holton III , editors. Human Resource Development Handbook: Linking Research and Practice . (San Francisco, CA: Berrett-Koehler, 1997): pp. 114-137; Jacard, James and Jacob Jacoby. Theory Construction and Model-Building Skills: A Practical Guide for Social Scientists . New York: Guilford, 2010; Ravitch, Sharon M. and Matthew Riggan. Reason and Rigor: How Conceptual Frameworks Guide Research . Second edition. Los Angeles, CA: SAGE, 2017; Sutton, Robert I. and Barry M. Staw. “What Theory is Not.” Administrative Science Quarterly 40 (September 1995): 371-384.
Structure and Writing Style
The theoretical framework may be rooted in a specific theory , in which case, your work is expected to test the validity of that existing theory in relation to specific events, issues, or phenomena. Many social science research papers fit into this rubric. For example, Peripheral Realism Theory, which categorizes perceived differences among nation-states as those that give orders, those that obey, and those that rebel, could be used as a means for understanding conflicted relationships among countries in Africa. A test of this theory could be the following: Does Peripheral Realism Theory help explain intra-state actions, such as, the disputed split between southern and northern Sudan that led to the creation of two nations?
However, you may not always be asked by your professor to test a specific theory in your paper, but to develop your own framework from which your analysis of the research problem is derived . Based upon the above example, it is perhaps easiest to understand the nature and function of a theoretical framework if it is viewed as an answer to two basic questions:
- What is the research problem/question? [e.g., "How should the individual and the state relate during periods of conflict?"]
- Why is your approach a feasible solution? [i.e., justify the application of your choice of a particular theory and explain why alternative constructs were rejected. I could choose instead to test Instrumentalist or Circumstantialists models developed among ethnic conflict theorists that rely upon socio-economic-political factors to explain individual-state relations and to apply this theoretical model to periods of war between nations].
The answers to these questions come from a thorough review of the literature and your course readings [summarized and analyzed in the next section of your paper] and the gaps in the research that emerge from the review process. With this in mind, a complete theoretical framework will likely not emerge until after you have completed a thorough review of the literature .
Just as a research problem in your paper requires contextualization and background information, a theory requires a framework for understanding its application to the topic being investigated. When writing and revising this part of your research paper, keep in mind the following:
- Clearly describe the framework, concepts, models, or specific theories that underpin your study . This includes noting who the key theorists are in the field who have conducted research on the problem you are investigating and, when necessary, the historical context that supports the formulation of that theory. This latter element is particularly important if the theory is relatively unknown or it is borrowed from another discipline.
- Position your theoretical framework within a broader context of related frameworks, concepts, models, or theories . As noted in the example above, there will likely be several concepts, theories, or models that can be used to help develop a framework for understanding the research problem. Therefore, note why the theory you've chosen is the appropriate one.
- The present tense is used when writing about theory. Although the past tense can be used to describe the history of a theory or the role of key theorists, the construction of your theoretical framework is happening now.
- You should make your theoretical assumptions as explicit as possible . Later, your discussion of methodology should be linked back to this theoretical framework.
- Don’t just take what the theory says as a given! Reality is never accurately represented in such a simplistic way; if you imply that it can be, you fundamentally distort a reader's ability to understand the findings that emerge. Given this, always note the limitations of the theoretical framework you've chosen [i.e., what parts of the research problem require further investigation because the theory inadequately explains a certain phenomena].
The Conceptual Framework. College of Education. Alabama State University; Conceptual Framework: What Do You Think is Going On? College of Engineering. University of Michigan; Drafting an Argument. Writing@CSU. Colorado State University; Lynham, Susan A. “The General Method of Theory-Building Research in Applied Disciplines.” Advances in Developing Human Resources 4 (August 2002): 221-241; Tavallaei, Mehdi and Mansor Abu Talib. "A General Perspective on the Role of Theory in Qualitative Research." Journal of International Social Research 3 (Spring 2010); Ravitch, Sharon M. and Matthew Riggan. Reason and Rigor: How Conceptual Frameworks Guide Research . Second edition. Los Angeles, CA: SAGE, 2017; Reyes, Victoria. Demystifying the Journal Article. Inside Higher Education; Trochim, William M.K. Philosophy of Research. Research Methods Knowledge Base. 2006; Weick, Karl E. “The Work of Theorizing.” In Theorizing in Social Science: The Context of Discovery . Richard Swedberg, editor. (Stanford, CA: Stanford University Press, 2014), pp. 177-194.
Writing Tip
Borrowing Theoretical Constructs from Other Disciplines
An increasingly important trend in the social and behavioral sciences is to think about and attempt to understand research problems from an interdisciplinary perspective. One way to do this is to not rely exclusively on the theories developed within your particular discipline, but to think about how an issue might be informed by theories developed in other disciplines. For example, if you are a political science student studying the rhetorical strategies used by female incumbents in state legislature campaigns, theories about the use of language could be derived, not only from political science, but linguistics, communication studies, philosophy, psychology, and, in this particular case, feminist studies. Building theoretical frameworks based on the postulates and hypotheses developed in other disciplinary contexts can be both enlightening and an effective way to be more engaged in the research topic.
CohenMiller, A. S. and P. Elizabeth Pate. "A Model for Developing Interdisciplinary Research Theoretical Frameworks." The Qualitative Researcher 24 (2019): 1211-1226; Frodeman, Robert. The Oxford Handbook of Interdisciplinarity . New York: Oxford University Press, 2010.
Another Writing Tip
Don't Undertheorize!
Do not leave the theory hanging out there in the introduction never to be mentioned again. Undertheorizing weakens your paper. The theoretical framework you describe should guide your study throughout the paper. Be sure to always connect theory to the review of pertinent literature and to explain in the discussion part of your paper how the theoretical framework you chose supports analysis of the research problem or, if appropriate, how the theoretical framework was found to be inadequate in explaining the phenomenon you were investigating. In that case, don't be afraid to propose your own theory based on your findings.
Yet Another Writing Tip
What's a Theory? What's a Hypothesis?
The terms theory and hypothesis are often used interchangeably in newspapers and popular magazines and in non-academic settings. However, the difference between theory and hypothesis in scholarly research is important, particularly when using an experimental design. A theory is a well-established principle that has been developed to explain some aspect of the natural world. Theories arise from repeated observation and testing and incorporates facts, laws, predictions, and tested assumptions that are widely accepted [e.g., rational choice theory; grounded theory; critical race theory].
A hypothesis is a specific, testable prediction about what you expect to happen in your study. For example, an experiment designed to look at the relationship between study habits and test anxiety might have a hypothesis that states, "We predict that students with better study habits will suffer less test anxiety." Unless your study is exploratory in nature, your hypothesis should always explain what you expect to happen during the course of your research.
The key distinctions are:
- A theory predicts events in a broad, general context; a hypothesis makes a specific prediction about a specified set of circumstances.
- A theory has been extensively tested and is generally accepted among a set of scholars; a hypothesis is a speculative guess that has yet to be tested.
Cherry, Kendra. Introduction to Research Methods: Theory and Hypothesis. About.com Psychology; Gezae, Michael et al. Welcome Presentation on Hypothesis. Slideshare presentation.
Still Yet Another Writing Tip
Be Prepared to Challenge the Validity of an Existing Theory
Theories are meant to be tested and their underlying assumptions challenged; they are not rigid or intransigent, but are meant to set forth general principles for explaining phenomena or predicting outcomes. Given this, testing theoretical assumptions is an important way that knowledge in any discipline develops and grows. If you're asked to apply an existing theory to a research problem, the analysis will likely include the expectation by your professor that you should offer modifications to the theory based on your research findings.
Indications that theoretical assumptions may need to be modified can include the following:
- Your findings suggest that the theory does not explain or account for current conditions or circumstances or the passage of time,
- The study reveals a finding that is incompatible with what the theory attempts to explain or predict, or
- Your analysis reveals that the theory overly generalizes behaviors or actions without taking into consideration specific factors revealed from your analysis [e.g., factors related to culture, nationality, history, gender, ethnicity, age, geographic location, legal norms or customs , religion, social class, socioeconomic status, etc.].
Philipsen, Kristian. "Theory Building: Using Abductive Search Strategies." In Collaborative Research Design: Working with Business for Meaningful Findings . Per Vagn Freytag and Louise Young, editors. (Singapore: Springer Nature, 2018), pp. 45-71; Shepherd, Dean A. and Roy Suddaby. "Theory Building: A Review and Integration." Journal of Management 43 (2017): 59-86.
- << Previous: The Research Problem/Question
- Next: 5. The Literature Review >>
- Last Updated: May 15, 2024 9:53 AM
- URL: https://libguides.usc.edu/writingguide

Organizing Academic Research Papers: Theoretical Framework
- Purpose of Guide
- Design Flaws to Avoid
- Glossary of Research Terms
- Narrowing a Topic Idea
- Broadening a Topic Idea
- Extending the Timeliness of a Topic Idea
- Academic Writing Style
- Choosing a Title
- Making an Outline
- Paragraph Development
- Executive Summary
- Background Information
- The Research Problem/Question
- Theoretical Framework
- Citation Tracking
- Content Alert Services
- Evaluating Sources
- Primary Sources
- Secondary Sources
- Tertiary Sources
- What Is Scholarly vs. Popular?
- Qualitative Methods
- Quantitative Methods
- Using Non-Textual Elements
- Limitations of the Study
- Common Grammar Mistakes
- Avoiding Plagiarism
- Footnotes or Endnotes?
- Further Readings
- Annotated Bibliography
- Dealing with Nervousness
- Using Visual Aids
- Grading Someone Else's Paper
- How to Manage Group Projects
- Multiple Book Review Essay
- Reviewing Collected Essays
- About Informed Consent
- Writing Field Notes
- Writing a Policy Memo
- Writing a Research Proposal
- Acknowledgements
Theories are formulated to explain, predict, and understand phenomena and, in many cases, to challenge and extend existing knowledge, within the limits of the critical bounding assumptions. The theoretical framework is the structure that can hold or support a theory of a research study. The theoretical framework introduces and describes the theory which explains why the research problem under study exists.
Importance of Theory
A theoretical framework consists of concepts, together with their definitions, and existing theory/theories that are used for your particular study. The theoretical framework must demonstrate an understanding of theories and concepts that are relevant to the topic of your research paper and that will relate it to the broader fields of knowledge in the class you are taking.
The theoretical framework is not something that is found readily available in the literature . You must review course readings and pertinent research literature for theories and analytic models that are relevant to the research problem you are investigating. The selection of a theory should depend on its appropriateness, ease of application, and explanatory power.
The theoretical framework strengthens the study in the following ways .
- An explicit statement of theoretical assumptions permits the reader to evaluate them critically.
- The theoretical framework connects the researcher to existing knowledge. Guided by a relevant theory, you are given a basis for your hypotheses and choice of research methods.
- Articulating the theoretical assumptions of a research study forces you to address questions of why and how. It permits you to move from simply describing a phenomenon observed to generalizing about various aspects of that phenomenon.
- Having a theory helps you to identify the limits to those generalizations. A theoretical framework specifies which key variables influence a phenomenon of interest. It alerts you to examine how those key variables might differ and under what circumstances.
By virtue of its application nature, good theory in the social sciences is of value precisely because it fulfills one primary purpose: to explain the meaning, nature, and challenges of a phenomenon, often experienced but unexplained in the world in which we live, so that we may use that knowledge and understanding to act in more informed and effective ways.
The Conceptual Framework. College of Education. Alabama State University; Drafting an Argument . Writing@CSU. Colorado State University; Trochim, William M.K. Philosophy of Research. Research Methods Knowledge Base. 2006.
Strategies for Developing the Theoretical Framework
I. Developing the Framework
Here are some strategies to develop of an effective theoretical framework:
- Examine your thesis title and research problem . The research problem anchors your entire study and forms the basis from which you construct your theoretical framework.
- Brainstorm on what you consider to be the key variables in your research . Answer the question, what factors contribute to the presumed effect?
- Review related literature to find answers to your research question.
- List the constructs and variables that might be relevant to your study. Group these variables into independent and dependent categories.
- Review the key social science theories that are introduced to you in your course readings and choose the theory or theories that can best explain the relationships between the key variables in your study [note the Writing Tip on this page].
- Discuss the assumptions or propositions of this theory and point out their relevance to your research.
A theoretical framework is used to limit the scope of the relevant data by focusing on specific variables and defining the specific viewpoint (framework) that the researcher will take in analyzing and interpreting the data to be gathered, understanding concepts and variables according to the given definitions, and building knowledge by validating or challenging theoretical assumptions.
II. Purpose
Think of theories as the conceptual basis for understanding, analyzing, and designing ways to investigate relationships within social systems. To the end, the following roles served by a theory can help guide the development of your framework.*
- Means by which new research data can be interpreted and coded for future use,
- Response to new problems that have no previously identified solutions strategy,
- Means for identifying and defining research problems,
- Means for prescribing or evaluating solutions to research problems,
- Way of telling us that certain facts among the accumulated knowledge are important and which facts are not,
- Means of giving old data new interpretations and new meaning,
- Means by which to identify important new issues and prescribe the most critical research questions that need to be answered to maximize understanding of the issue,
- Means of providing members of a professional discipline with a common language and a frame of reference for defining boundaries of their profession, and
- Means to guide and inform research so that it can, in turn, guide research efforts and improve professional practice.
*Adapted from: Torraco, R. J. “Theory-Building Research Methods.” In Swanson R. A. and E. F. Holton III , editors. Human Resource Development Handbook: Linking Research and Practice . (San Francisco, CA: Berrett-Koehler, 1997): pp. 114-137; Sutton, Robert I. and Barry M. Staw. “What Theory is Not.” Administrative Science Quarterly 40 (September 1995): 371-384.
Structure and Writing Style
The theoretical framework may be rooted in a specific theory , in which case, you are expected to test the validity of an existing theory in relation to specific events, issues, or phenomena. Many social science research papers fit into this rubric. For example, Peripheral Realism theory, which categorizes perceived differences between nation-states as those that give orders, those that obey, and those that rebel, could be used as a means for understanding conflicted relationships among countries in Africa. A test of this theory could be the following: Does Peripheral Realism theory help explain intra-state actions, such as, the growing split between southern and northern Sudan that may likely lead to the creation of two nations?
However, you may not always be asked by your professor to test a specific theory in your paper, but to develop your own framework from which your analysis of the research problem is derived . Given this, it is perhaps easiest to understand the nature and function of a theoretical framework if it is viewed as the answer to two basic questions:
- What is the research problem/question? [e.g., "How should the individual and the state relate during periods of conflict?"]
- Why is your approach a feasible solution? [I could choose to test Instrumentalist or Circumstantialists models developed among Ethnic Conflict Theorists that rely upon socio-economic-political factors to explain individual-state relations and to apply this theoretical model to periods of war between nations].
The answers to these questions come from a thorough review of the literature and your course readings [summarized and analyzed in the next section of your paper] and the gaps in the research that emerge from the review process. With this in mind, a complete theoretical framework will likely not emerge until after you have completed a thorough review of the literature .
In writing this part of your research paper, keep in mind the following:
- Clearly describe the framework, concepts, models, or specific theories that underpin your study . This includes noting who the key theorists are in the field who have conducted research on the problem you are investigating and, when necessary, the historical context that supports the formulation of that theory. This latter element is particularly important if the theory is relatively unknown or it is borrowed from another discipline.
- Position your theoretical framework within a broader context of related frameworks , concepts, models, or theories . There will likely be several concepts, theories, or models that can be used to help develop a framework for understanding the research problem. Therefore, note why the framework you've chosen is the appropriate one.
- The present tense is used when writing about theory.
- You should make your theoretical assumptions as explicit as possible . Later, your discussion of methodology should be linked back to this theoretical framework.
- Don’t just take what the theory says as a given! Reality is never accurately represented in such a simplistic way; if you imply that it can be, you fundamentally distort a reader's ability to understand the findings that emerge. Given this, always note the limitiations of the theoretical framework you've chosen [i.e., what parts of the research problem require further investigation because the theory does not explain a certain phenomena].
The Conceptual Framework. College of Education. Alabama State University; Conceptual Framework: What Do You Think is Going On? College of Engineering. University of Michigan; Drafting an Argument . Writing@CSU. Colorado State University; Lynham, Susan A. “The General Method of Theory-Building Research in Applied Disciplines.” Advances in Developing Human Resources 4 (August 2002): 221-241; Tavallaei, Mehdi and Mansor Abu Talib. A General Perspective on the Role of Theory in Qualitative Research. Journal of International Social Research 3 (Spring 2010); Trochim, William M.K. Philosophy of Research. Research Methods Knowledge Base. 2006.
Writing Tip
Borrowing Theoretical Constructs from Elsewhere
A growing and increasingly important trend in the social sciences is to think about and attempt to understand specific research problems from an interdisciplinary perspective. One way to do this is to not rely exclusively on the theories you've read about in a particular class, but to think about how an issue might be informed by theories developed in other disciplines. For example, if you are a political science student studying the rhetorical strategies used by female incumbants in state legislature campaigns, theories about the use of language could be derived, not only from political science, but linguistics, communication studies, philosophy, psychology, and, in this particular case, feminist studies. Building theoretical frameworks based on the postulates and hypotheses developed in other disciplinary contexts can be both enlightening and an effective way to be fully engaged in the research topic.
Another Writing Tip
Don't Undertheorize!
Never leave the theory hanging out there in the Introduction never to be mentioned again. Undertheorizing weakens your paper. The theoretical framework you introduce should guide your study throughout the paper. Be sure to always connect theory to the analysis and to explain in the discussion part of your paper how the theoretical framework you chose fit the research problem, or if appropriate, was inadequate in explaining the phenomenon you were investigating. In that case, don't be afraid to propose your own theory based on your findings.
Still Another Writing Tip
What's a Theory? What's a Hypothesis?
The terms theory and hypothesis are often used interchangeably in everyday use. However, the difference between them in scholarly research is important, particularly when using an experimental design. A theory is a well-established principle that has been developed to explain some aspect of the natural world. Theories arise from repeated observation and testing and incorporates facts, laws, predictions, and tested hypotheses that are widely accepted [e.g., rational choice theory; grounded theory].
A hypothesis is a specific, testable prediction about what you expect to happen in your study. For example, an experiment designed to look at the relationship between study habits and test anxiety might have a hypothesis that states, "We predict that students with better study habits will suffer less test anxiety." Unless your study is exploratory in nature, your hypothesis should always explain what you expect to happen during the course of your research.
The key distinctions are:
- A theory predicts events in a broad, general context; a hypothesis makes a specific prediction about a specified set of circumstances.
- A theory has been extensively tested and is generally accepted among scholars; a hypothesis is a speculative guess that has yet to be tested.
Cherry, Kendra. Introduction to Research Methods: Theory and Hypothesis . About.com Psychology; Gezae, Michael et al. Welcome Presentation on Hypothesis . Slideshare presentation.
- << Previous: The Research Problem/Question
- Next: 5. The Literature Review >>
- Last Updated: Jul 18, 2023 11:58 AM
- URL: https://library.sacredheart.edu/c.php?g=29803
- QuickSearch
- Library Catalog
- Databases A-Z
- Publication Finder
- Course Reserves
- Citation Linker
- Digital Commons
- Our Website
Research Support
- Ask a Librarian
- Appointments
- Interlibrary Loan (ILL)
- Research Guides
- Databases by Subject
- Citation Help
Using the Library
- Reserve a Group Study Room
- Renew Books
- Honors Study Rooms
- Off-Campus Access
- Library Policies
- Library Technology
User Information
- Grad Students
- Online Students
- COVID-19 Updates
- Staff Directory
- News & Announcements
- Library Newsletter
My Accounts
- Interlibrary Loan
- Staff Site Login
FIND US ON

Want to create or adapt books like this? Learn more about how Pressbooks supports open publishing practices.
4 Theories in scientific research
As we know from previous chapters, science is knowledge represented as a collection of ‘theories’ derived using the scientific method. In this chapter, we will examine what a theory is, why we need theories in research, the building blocks of a theory, how to evaluate theories, how can we apply theories in research, and also present illustrative examples of five theories frequently used in social science research.
Theories are explanations of a natural or social behaviour, event, or phenomenon. More formally, a scientific theory is a system of constructs (concepts) and propositions (relationships between those constructs) that collectively presents a logical, systematic, and coherent explanation of a phenomenon of interest within some assumptions and boundary conditions (Bacharach 1989). [1]
Theories should explain why things happen, rather than just describe or predict. Note that it is possible to predict events or behaviours using a set of predictors, without necessarily explaining why such events are taking place. For instance, market analysts predict fluctuations in the stock market based on market announcements, earnings reports of major companies, and new data from the Federal Reserve and other agencies, based on previously observed correlations . Prediction requires only correlations. In contrast, explanations require causations , or understanding of cause-effect relationships. Establishing causation requires three conditions: one, correlations between two constructs, two, temporal precedence (the cause must precede the effect in time), and three, rejection of alternative hypotheses (through testing). Scientific theories are different from theological, philosophical, or other explanations in that scientific theories can be empirically tested using scientific methods.
Explanations can be idiographic or nomothetic. Idiographic explanations are those that explain a single situation or event in idiosyncratic detail. For example, you did poorly on an exam because: you forgot that you had an exam on that day, you arrived late to the exam due to a traffic jam, you panicked midway through the exam, you had to work late the previous evening and could not study for the exam, or even your dog ate your textbook. The explanations may be detailed, accurate, and valid, but they may not apply to other similar situations, even involving the same person, and are hence not generalisable. In contrast, nomothetic explanations seek to explain a class of situations or events rather than a specific situation or event. For example, students who do poorly in exams do so because they did not spend adequate time preparing for exams or because they suffer from nervousness, attention-deficit, or some other medical disorder. Because nomothetic explanations are designed to be generalisable across situations, events, or people, they tend to be less precise, less complete, and less detailed. However, they explain economically, using only a few explanatory variables. Because theories are also intended to serve as generalised explanations for patterns of events, behaviours, or phenomena, theoretical explanations are generally nomothetic in nature.
While understanding theories, it is also important to understand what theories are not. A theory is not data, facts, typologies, taxonomies, or empirical findings. A collection of facts is not a theory, just as a pile of stones is not a house. Likewise, a collection of constructs (e.g., a typology of constructs) is not a theory, because theories must go well beyond constructs to include propositions, explanations, and boundary conditions. Data, facts, and findings operate at the empirical or observational level, while theories operate at a conceptual level and are based on logic rather than observations.
There are many benefits to using theories in research. First, theories provide the underlying logic for the occurrence of natural or social phenomena by explaining the key drivers and outcomes of the target phenomenon, and the underlying processes responsible for driving that phenomenon. Second, they aid in sense-making by helping us synthesise prior empirical findings within a theoretical framework and reconcile contradictory findings by discovering contingent factors influencing the relationship between two constructs in different studies. Third, theories provide guidance for future research by helping identify constructs and relationships that are worthy of further research. Fourth, theories can contribute to cumulative knowledge building by bridging gaps between other theories and by causing existing theories to be re-evaluated in a new light.
However, theories can also have their own share of limitations. As simplified explanations of reality, theories may not always provide adequate explanations of the phenomenon of interest based on a limited set of constructs and relationships. Theories are designed to be simple and parsimonious explanations, while reality may be significantly more complex. Furthermore, theories may impose blinders or limit researchers’ ‘range of vision’, causing them to miss out on important concepts that are not defined by the theory.
Building blocks of a theory
David Whetten (1989) [2] suggests that there are four building blocks of a theory: constructs, propositions, logic, and boundary conditions/assumptions. Constructs capture the ‘what’ of theories (i.e., what concepts are important for explaining a phenomenon?), propositions capture the ‘how’ (i.e., how are these concepts related to each other?), logic represents the ‘why’ (i.e., why are these concepts related?), and boundary conditions/assumptions examines the ‘who, when, and where’ (i.e., under what circumstances will these concepts and relationships work?). Though constructs and propositions were previously discussed in Chapter 2, we describe them again here for the sake of completeness.
Constructs are abstract concepts specified at a high level of abstraction that are chosen specifically to explain the phenomenon of interest. Recall from Chapter 2 that constructs may be unidimensional (i.e., embody a single concept), such as weight or age, or multi-dimensional (i.e., embody multiple underlying concepts), such as personality or culture. While some constructs, such as age, education, and firm size, are easy to understand, others, such as creativity, prejudice, and organisational agility, may be more complex and abstruse, and still others such as trust, attitude, and learning may represent temporal tendencies rather than steady states. Nevertheless, all constructs must have clear and unambiguous operational definitions that should specify exactly how the construct will be measured and at what level of analysis (individual, group, organisational, etc.). Measurable representations of abstract constructs are called variables . For instance, IQ score is a variable that is purported to measure an abstract construct called ‘intelligence’. As noted earlier, scientific research proceeds along two planes: a theoretical plane and an empirical plane. Constructs are conceptualised at the theoretical plane, while variables are operationalised and measured at the empirical (observational) plane. Furthermore, variables may be independent, dependent, mediating, or moderating, as discussed in Chapter 2. The distinction between constructs (conceptualised at the theoretical level) and variables (measured at the empirical level) is shown in Figure 4.1.
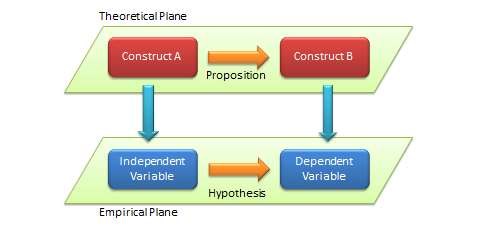
Propositions are associations postulated between constructs based on deductive logic. Propositions are stated in declarative form and should ideally indicate a cause-effect relationship (e.g., if X occurs, then Y will follow). Note that propositions may be conjectural but must be testable, and should be rejected if they are not supported by empirical observations. However, like constructs, propositions are stated at the theoretical level, and they can only be tested by examining the corresponding relationship between measurable variables of those constructs. The empirical formulation of propositions, stated as relationships between variables, are called hypotheses . The distinction between propositions (formulated at the theoretical level) and hypotheses (tested at the empirical level) is depicted in Figure 4.1.
The third building block of a theory is the logic that provides the basis for justifying the propositions as postulated. Logic acts like a ‘glue’ that connects the theoretical constructs and provides meaning and relevance to the relationships between these constructs. Logic also represents the ‘explanation’ that lies at the core of a theory. Without logic, propositions will be ad hoc, arbitrary, and meaningless, and cannot be tied into the cohesive ‘system of propositions’ that is the heart of any theory.
Finally, all theories are constrained by assumptions about values, time, and space, and boundary conditions that govern where the theory can be applied and where it cannot be applied. For example, many economic theories assume that human beings are rational (or boundedly rational) and employ utility maximisation based on cost and benefit expectations as a way of understand human behaviour. In contrast, political science theories assume that people are more political than rational, and try to position themselves in their professional or personal environment in a way that maximises their power and control over others. Given the nature of their underlying assumptions, economic and political theories are not directly comparable, and researchers should not use economic theories if their objective is to understand the power structure or its evolution in an organisation. Likewise, theories may have implicit cultural assumptions (e.g., whether they apply to individualistic or collective cultures), temporal assumptions (e.g., whether they apply to early stages or later stages of human behaviour), and spatial assumptions (e.g., whether they apply to certain localities but not to others). If a theory is to be properly used or tested, all of the implicit assumptions that form the boundaries of that theory must be properly understood. Unfortunately, theorists rarely state their implicit assumptions clearly, which leads to frequent misapplications of theories to problem situations in research.
Attributes of a good theory
Theories are simplified and often partial explanations of complex social reality. As such, there can be good explanations or poor explanations, and consequently, there can be good theories or poor theories. How can we evaluate the ‘goodness’ of a given theory? Different criteria have been proposed by different researchers, the more important of which are listed below:
Logical consistency: Are the theoretical constructs, propositions, boundary conditions, and assumptions logically consistent with each other? If some of these ‘building blocks’ of a theory are inconsistent with each other (e.g., a theory assumes rationality, but some constructs represent non-rational concepts), then the theory is a poor theory.
Explanatory power: How much does a given theory explain (or predict) reality? Good theories obviously explain the target phenomenon better than rival theories, as often measured by variance explained (R-squared) value in regression equations.
Falsifiability: British philosopher Karl Popper stated in the 1940s that for theories to be valid, they must be falsifiable. Falsifiability ensures that the theory is potentially disprovable, if empirical data does not match with theoretical propositions, which allows for their empirical testing by researchers. In other words, theories cannot be theories unless they can be empirically testable. Tautological statements, such as ‘a day with high temperatures is a hot day’ are not empirically testable because a hot day is defined (and measured) as a day with high temperatures, and hence, such statements cannot be viewed as a theoretical proposition. Falsifiability requires the presence of rival explanations, it ensures that the constructs are adequately measurable, and so forth. However, note that saying that a theory is falsifiable is not the same as saying that a theory should be falsified. If a theory is indeed falsified based on empirical evidence, then it was probably a poor theory to begin with.
Parsimony: Parsimony examines how much of a phenomenon is explained with how few variables. The concept is attributed to fourteenth century English logician Father William of Ockham (and hence called ‘Ockham’s razor’ or ‘Occam’s razor’), which states that among competing explanations that sufficiently explain the observed evidence, the simplest theory (i.e., one that uses the smallest number of variables or makes the fewest assumptions) is the best. Explanation of a complex social phenomenon can always be increased by adding more and more constructs. However, such an approach defeats the purpose of having a theory, which is intended to be a ‘simplified’ and generalisable explanation of reality. Parsimony relates to the degrees of freedom in a given theory. Parsimonious theories have higher degrees of freedom, which allow them to be more easily generalised to other contexts, settings, and populations.
Approaches to theorising
How do researchers build theories? Steinfeld and Fulk (1990) [3] recommend four such approaches. The first approach is to build theories inductively based on observed patterns of events or behaviours. Such an approach is often called ‘grounded theory building’, because the theory is grounded in empirical observations. This technique is heavily dependent on the observational and interpretive abilities of the researcher, and the resulting theory may be subjective and non-confirmable. Furthermore, observing certain patterns of events will not necessarily make a theory, unless the researcher is able to provide consistent explanations for the observed patterns. We will discuss the grounded theory approach in a later chapter on qualitative research.
The second approach to theory building is to conduct a bottom-up conceptual analysis to identify different sets of predictors relevant to the phenomenon of interest using a predefined framework. One such framework may be a simple input-process-output framework, where the researcher may look for different categories of inputs, such as individual, organisational, and/or technological factors potentially related to the phenomenon of interest (the output), and describe the underlying processes that link these factors to the target phenomenon. This is also an inductive approach that relies heavily on the inductive abilities of the researcher, and interpretation may be biased by researcher’s prior knowledge of the phenomenon being studied.
The third approach to theorising is to extend or modify existing theories to explain a new context, such as by extending theories of individual learning to explain organisational learning. While making such an extension, certain concepts, propositions, and/or boundary conditions of the old theory may be retained and others modified to fit the new context. This deductive approach leverages the rich inventory of social science theories developed by prior theoreticians, and is an efficient way of building new theories by expanding on existing ones.
The fourth approach is to apply existing theories in entirely new contexts by drawing upon the structural similarities between the two contexts. This approach relies on reasoning by analogy, and is probably the most creative way of theorising using a deductive approach. For instance, Markus (1987) [4] used analogic similarities between a nuclear explosion and uncontrolled growth of networks or network-based businesses to propose a critical mass theory of network growth. Just as a nuclear explosion requires a critical mass of radioactive material to sustain a nuclear explosion, Markus suggested that a network requires a critical mass of users to sustain its growth, and without such critical mass, users may leave the network, causing an eventual demise of the network.
Examples of social science theories
In this section, we present brief overviews of a few illustrative theories from different social science disciplines. These theories explain different types of social behaviors, using a set of constructs, propositions, boundary conditions, assumptions, and underlying logic. Note that the following represents just a simplistic introduction to these theories. Readers are advised to consult the original sources of these theories for more details and insights on each theory.
Agency theory. Agency theory (also called principal-agent theory), a classic theory in the organisational economics literature, was originally proposed by Ross (1973) [5] to explain two-party relationships—such as those between an employer and its employees, between organisational executives and shareholders, and between buyers and sellers—whose goals are not congruent with each other. The goal of agency theory is to specify optimal contracts and the conditions under which such contracts may help minimise the effect of goal incongruence. The core assumptions of this theory are that human beings are self-interested individuals, boundedly rational, and risk-averse, and the theory can be applied at the individual or organisational level.
The two parties in this theory are the principal and the agent—the principal employs the agent to perform certain tasks on its behalf. While the principal’s goal is quick and effective completion of the assigned task, the agent’s goal may be working at its own pace, avoiding risks, and seeking self-interest—such as personal pay—over corporate interests, hence, the goal incongruence. Compounding the nature of the problem may be information asymmetry problems caused by the principal’s inability to adequately observe the agent’s behaviour or accurately evaluate the agent’s skill sets. Such asymmetry may lead to agency problems where the agent may not put forth the effort needed to get the task done (the moral hazard problem) or may misrepresent its expertise or skills to get the job but not perform as expected (the adverse selection problem). Typical contracts that are behaviour-based, such as a monthly salary, cannot overcome these problems. Hence, agency theory recommends using outcome-based contracts, such as commissions or a fee payable upon task completion, or mixed contracts that combine behaviour-based and outcome-based incentives. An employee stock option plan is an example of an outcome-based contract, while employee pay is a behaviour-based contract. Agency theory also recommends tools that principals may employ to improve the efficacy of behaviour-based contracts, such as investing in monitoring mechanisms—e.g. hiring supervisors—to counter the information asymmetry caused by moral hazard, designing renewable contracts contingent on the agent’s performance (performance assessment makes the contract partially outcome-based), or by improving the structure of the assigned task to make it more programmable and therefore more observable.
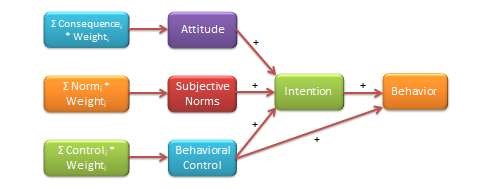
Theory of planned behaviour. Postulated by Azjen (1991), [6] the theory of planned behaviour (TPB) is a generalised theory of human behaviour in social psychology literature that can be used to study a wide range of individual behaviours. It presumes that individual behaviour represents conscious reasoned choice, and is shaped by cognitive thinking and social pressures. The theory postulates that behaviours are based on one’s intention regarding that behaviour, which in turn is a function of the person’s attitude toward the behaviour, subjective norm regarding that behaviour, and perception of control over that behaviour (see Figure 4.2). Attitude is defined as the individual’s overall positive or negative feelings about performing the behaviour in question, which may be assessed as a summation of one’s beliefs regarding the different consequences of that behaviour, weighted by the desirability of those consequences. Subjective norm refers to one’s perception of whether people important to that person expect the person to perform the intended behaviour, and is represented as a weighted combination of the expected norms of different referent groups such as friends, colleagues, or supervisors at work. Behavioural control is one’s perception of internal or external controls constraining the behaviour in question. Internal controls may include the person’s ability to perform the intended behaviour (self-efficacy), while external control refers to the availability of external resources needed to perform that behaviour (facilitating conditions). TPB also suggests that sometimes people may intend to perform a given behaviour but lack the resources needed to do so, and therefore posits that behavioural control can have a direct effect on behaviour, in addition to the indirect effect mediated by intention.
TPB is an extension of an earlier theory called the theory of reasoned action, which included attitude and subjective norm as key drivers of intention, but not behavioural control. The latter construct was added by Ajzen in TPB to account for circumstances when people may have incomplete control over their own behaviours (such as not having high-speed Internet access for web surfing).
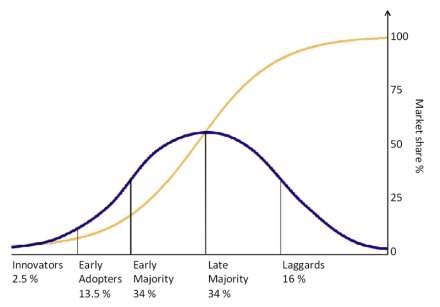
Innovation diffusion theory. Innovation diffusion theory (IDT) is a seminal theory in the communications literature that explains how innovations are adopted within a population of potential adopters. The concept was first studied by French sociologist Gabriel Tarde, but the theory was developed by Everett Rogers in 1962 based on observations of 508 diffusion studies. The four key elements in this theory are: innovation, communication channels, time, and social system. Innovations may include new technologies, new practices, or new ideas, and adopters may be individuals or organisations. At the macro (population) level, IDT views innovation diffusion as a process of communication where people in a social system learn about a new innovation and its potential benefits through communication channels—such as mass media or prior adopters— and are persuaded to adopt it. Diffusion is a temporal process—the diffusion process starts off slow among a few early adopters, then picks up speed as the innovation is adopted by the mainstream population, and finally slows down as the adopter population reaches saturation. The cumulative adoption pattern is therefore an s-shaped curve, as shown in Figure 4.3, and the adopter distribution represents a normal distribution. All adopters are not identical, and adopters can be classified into innovators, early adopters, early majority, late majority, and laggards based on the time of their adoption. The rate of diffusion also depends on characteristics of the social system such as the presence of opinion leaders (experts whose opinions are valued by others) and change agents (people who influence others’ behaviours).
At the micro (adopter) level, Rogers (1995) [7] suggests that innovation adoption is a process consisting of five stages: one, knowledge : when adopters first learn about an innovation from mass-media or interpersonal channels, two, persuasion : when they are persuaded by prior adopters to try the innovation, three, decision : their decision to accept or reject the innovation, four,: their initial utilisation of the innovation, and five, confirmation : their decision to continue using it to its fullest potential (see Figure 4.4). Five innovation characteristics are presumed to shape adopters’ innovation adoption decisions: one, relative advantage : the expected benefits of an innovation relative to prior innovations, two, compatibility : the extent to which the innovation fits with the adopter’s work habits, beliefs, and values, three, complexity : the extent to which the innovation is difficult to learn and use, four, trialability : the extent to which the innovation can be tested on a trial basis, and five, observability : the extent to which the results of using the innovation can be clearly observed. The last two characteristics have since been dropped from many innovation studies. Complexity is negatively correlated to innovation adoption, while the other four factors are positively correlated. Innovation adoption also depends on personal factors such as the adopter’s risk-taking propensity, education level, cosmopolitanism, and communication influence. Early adopters are venturesome, well educated, and rely more on mass media for information about the innovation, while later adopters rely more on interpersonal sources—such as friends and family—as their primary source of information. IDT has been criticised for having a ‘pro-innovation bias’—that is for presuming that all innovations are beneficial and will be eventually diffused across the entire population, and because it does not allow for inefficient innovations such as fads or fashions to die off quickly without being adopted by the entire population or being replaced by better innovations.
Elaboration likelihood model . Developed by Petty and Cacioppo (1986), [8] the elaboration likelihood model (ELM) is a dual-process theory of attitude formation or change in psychology literature. It explains how individuals can be influenced to change their attitude toward a certain object, event, or behaviour and the relative efficacy of such change strategies. The ELM posits that one’s attitude may be shaped by two ‘routes’ of influence: the central route and the peripheral route, which differ in the amount of thoughtful information processing or ‘elaboration required of people (see Figure 4.5). The central route requires a person to think about issue-related arguments in an informational message and carefully scrutinise the merits and relevance of those arguments, before forming an informed judgment about the target object. In the peripheral route, subjects rely on external ‘cues’ such as number of prior users, endorsements from experts, or likeability of the endorser, rather than on the quality of arguments, in framing their attitude towards the target object. The latter route is less cognitively demanding, and the routes of attitude change are typically operationalised in the ELM using the argument quality and peripheral cues constructs respectively.
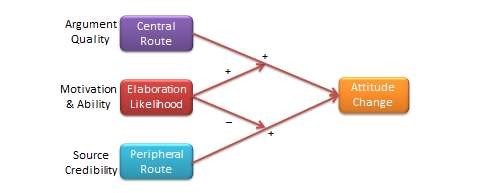
Whether people will be influenced by the central or peripheral routes depends upon their ability and motivation to elaborate the central merits of an argument. This ability and motivation to elaborate is called elaboration likelihood . People in a state of high elaboration likelihood (high ability and high motivation) are more likely to thoughtfully process the information presented and are therefore more influenced by argument quality, while those in the low elaboration likelihood state are more motivated by peripheral cues. Elaboration likelihood is a situational characteristic and not a personal trait. For instance, a doctor may employ the central route for diagnosing and treating a medical ailment (by virtue of his or her expertise of the subject), but may rely on peripheral cues from auto mechanics to understand the problems with his car. As such, the theory has widespread implications about how to enact attitude change toward new products or ideas and even social change.
General deterrence theory. Two utilitarian philosophers of the eighteenth century, Cesare Beccaria and Jeremy Bentham, formulated general deterrence theory (GDT) as both an explanation of crime and a method for reducing it. GDT examines why certain individuals engage in deviant, anti-social, or criminal behaviours. This theory holds that people are fundamentally rational (for both conforming and deviant behaviours), and that they freely choose deviant behaviours based on a rational cost-benefit calculation. Because people naturally choose utility-maximising behaviours, deviant choices that engender personal gain or pleasure can be controlled by increasing the costs of such behaviours in the form of punishments (countermeasures) as well as increasing the probability of apprehension. Swiftness, severity, and certainty of punishments are the key constructs in GDT.
While classical positivist research in criminology seeks generalised causes of criminal behaviours, such as poverty, lack of education, psychological conditions, and recommends strategies to rehabilitate criminals, such as by providing them job training and medical treatment, GDT focuses on the criminal decision-making process and situational factors that influence that process. Hence, a criminal’s personal situation—such as his personal values, his affluence, and his need for money—and the environmental context—such as how protected the target is, how efficient the local police are, how likely criminals are to be apprehended—play key roles in this decision-making process. The focus of GDT is not how to rehabilitate criminals and avert future criminal behaviours, but how to make criminal activities less attractive and therefore prevent crimes. To that end, ‘target hardening’ such as installing deadbolts and building self-defence skills, legal deterrents such as eliminating parole for certain crimes, ‘three strikes law’ (mandatory incarceration for three offences, even if the offences are minor and not worth imprisonment), and the death penalty, increasing the chances of apprehension using means such as neighbourhood watch programs, special task forces on drugs or gang-related crimes, and increased police patrols, and educational programs such as highly visible notices such as ‘Trespassers will be prosecuted’ are effective in preventing crimes. This theory has interesting implications not only for traditional crimes, but also for contemporary white-collar crimes such as insider trading, software piracy, and illegal sharing of music.
- Bacharach, S.B. (1989). Organizational theories: some criteria for evaluation. Academy of Management Review , 14(4), 496-515. ↵
- Whetten, D. (1989). What constitutes a theoretical contribution? Academy of Management Review , 14(4), 490-495. ↵
- Steinfield, C.W. and Fulk, J. (1990). The theory imperative. In J. Fulk & C.W. (Eds.), Organizations and communications technology (pp. 13–26). Newsburt Park, CA: Sage Publications. ↵
- Markus, M.L. (1987). Toward a ‘critical mass’ theory of interactive media: universal access, interdependence and diffusion. Communication Research , 14(5), 491-511. ↵
- Ross, S.A. (1973). The economic theory of agency: The principal’s problem. American Economic , 63(2), 134-139 ↵
- Ajzen, I. (1991). The theory of planned behavior. Organizational Behavior and Human Decision Processes , (50), 179–211. ↵
- Rogers, E. (1995). Diffusion of innovations (4th ed.). New York: Free Press. ↵
- Petty, R.E. and Cacioppo, J.T. (1986). C ommunication and persuasion: Central and peripheral routes to attitude change . New York: Springer-Verlag. ↵
Social Science Research: Principles, Methods and Practices (Revised edition) Copyright © 2019 by Anol Bhattacherjee is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License , except where otherwise noted.
Share This Book
- Library databases
- Library website
Theories and Frameworks: Introduction
Theoretical & conceptual frameworks.
The terms theoretical framework and conceptual framework are often used interchangeably to mean the same thing. Although they are both used to understand a research problem and guide the development, collection, and analysis of research, it's important to understand the difference between the two. When working on coursework or dissertation research, make sure to clarify what is being asked and any specific course or program requirements.
Theoretical framework
A theoretical framework is a single formal theory. When a study is designed around a theoretical framework, the theory is the primary means in which the research problem is understood and investigated. Although theoretical frameworks tend to be used in quantitative studies, you will also see this approach in qualitative research.
Conceptual framework
A conceptual framework includes one or more formal theories (in part or whole) as well as other concepts and empirical findings from the literature. It is used to show relationships among these ideas and how they relate to the research study. Conceptual frameworks are commonly seen in qualitative research in the social and behavioral sciences, for example, because often one theory cannot fully address the phenomena being studied.
Investigate theory
Identifying and learning about theories requires a different search strategy than other types of research. Even though the steps are different, you will still use many of the same skills and tools you’ve used for other library research.
- psychology: human development, cognition, personality, motivation
- sociology: social change, race, class, gender
- business: leadership, management
- health: patient care, well-being, environment
- course textbooks
- encyclopedias and handbooks
- credible websites
Theory in doctoral research
Identifying a theory that aligns with your dissertation or doctoral study takes time. It’s never too early to start exploratory research. The process of identifying an appropriate theory can seem daunting, so try breaking down the process into smaller steps.
- your theory courses
- completed dissertations and doctoral studies
- the scholarly literature on your topic
- Keep a list of theories and take notes on how and why they were used.
- Identify and learn more about relevant theories.
- Locate influential and seminal works related to those theories.
- Next Page: Discover Theories
- Office of Student Disability Services
Walden Resources
Departments.
- Academic Residencies
- Academic Skills
- Career Planning and Development
- Customer Care Team
- Field Experience
- Military Services
- Student Success Advising
- Writing Skills
Centers and Offices
- Center for Social Change
- Office of Academic Support and Instructional Services
- Office of Degree Acceleration
- Office of Research and Doctoral Services
- Office of Student Affairs
Student Resources
- Doctoral Writing Assessment
- Form & Style Review
- Quick Answers
- ScholarWorks
- SKIL Courses and Workshops
- Walden Bookstore
- Walden Catalog & Student Handbook
- Student Safety/Title IX
- Legal & Consumer Information
- Website Terms and Conditions
- Cookie Policy
- Accessibility
- Accreditation
- State Authorization
- Net Price Calculator
- Contact Walden
Walden University is a member of Adtalem Global Education, Inc. www.adtalem.com Walden University is certified to operate by SCHEV © 2024 Walden University LLC. All rights reserved.
- Find My Rep
You are here
Find the Theory in Your Research Little Quick Fix
- Janet E. Salmons - Free-range Scholar, Vision2Lead and Research Community Manager at SAGE MethodSpace
- Description
One of the most crucial foundational steps in any research project surrounds understanding and choosing an appropriate theory to frame the research question. Theoretical frameworks don’t just impact design, they impact how the entire study is interpreted, contextualized, and discussed. There are lots of resources about epistemologies and ontologies, but most focus on the philosophical and historical dimensions that can quickly overwhelm students. They need something quick that helps them understand the practical connection between theory and the purpose/nature of the study and, more importantly, decide which theory is best suited to their particular study. This Little Quick Fix covers questions like: What is theory? How does theory relate to research design? What is a theoretical framework? What is a theoretical contribution? How do I choose which theory (or theories) fits my research? What practical steps should I take to integrate theory into my research?
Little Quick Fix titles provide quick but authoritative answers to the problems, hurdles, and assessment points students face in the research course, project proposal, or design—whatever their methods learning is.
- Lively, ultra-modern design; full-colour, each page a tailored design.
- An hour's read. Easy to dip in and out of with clear navigation enables the reader to find what she needs—quick.
- Direct written style gets to the point with clear language. Nothing needs to be read twice. No fluff.
- Learning is reinforced through a 2-minute overview summary; 3-second summaries with super-quick Q&A
- DIY tasks create a work plan to accomplish a task, do a self-check quiz, solve a problem, get students to what they need to show their supervisor.
- Checkpoints in each section make sure students are nailing it as they go and support self-directed learning.
- How do I know I’m done? Each Little Quick Fix wraps up with a final checklist that allows the reader to self-assess they’ve got what they need to progress, submit, or ace the test or task.
A brief but focused look at a key aspect of any research.
This book is one of this series which are excellent introductions that all students no matter what their prior experience and knowledge will be able to engage, explore and learn from to support their research as education students, highly recommended.
This is a fantastic little book for students
Nice little guide that focuses on specific issues and are explained in an appealing way for undergraduate students struggling with academic writing and research methods.
It is easy to understand for students studying the foundation of research
All titles in this set are excellent and introduced to all students during their intial induction study day
An excellent and digestible small book that will help students to understand the importance and meaning of situating 'theory' in their research.
I was really excited about a quick, little book that my students could use as a quick start in the subject. However, to be honest, I think it is totally useless and provides no additional value. if you switch a little bit back and forth on wikipedia, you get more insights and help. That is not what I expected...
Preview this book
Sample materials & chapters.
Intro & Qu 1: What do researchers mean when they talk about epistemology, ontolo
For instructors
Select a purchasing option, order from:.
- VitalSource
- Amazon Kindle
- Google Play
Related Products

Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

A guide to writing a theoretical research paper

This is a guide to help (my) students to write better papers (as well as better research plans and outlines). If you are a teacher, feel free to use it in any way you like (including "stealing" from it). Feedback would be highly appreciated. If you are a student and you found this guide helpful, feel free to share it with others. This guide is formatted to be printed as an A5 booklet.
Related Papers
Sher Singh Bhakar
Organisation of Book: The book is organized into two parts. Part one starts with thinking critically about research, explains what is (and isn’t) research, explains how to properly use research in your writing to make your points, introduces a series of writing exercises designed to help students to think about and write effective research papers. Instead of explaining how to write a single “research paper,” The Process of Research Writing part of the book breaks down the research process into many smaller and easier-to manage parts like what is a research paper, starting steps for writing research papers, writing conceptual understanding and review of literature, referencing including various styles of referencing, writing research methodology and results including interpretations, writing implications and limitations of research and what goes into conclusions. Part two contains sample research articles to demonstrate the application of techniques and methods of writing good resear...
Marivic Sumagaysay
Stevejobs.education
Dr. David Annan
Very often, little attention is paid to how students have to prepare and understand the processes of conducting research and mostly young scholars struggle in the early stages in the university career about what is required of them and how to present their proposal to their supervisors. Keeping this in mind, the purpose of this guidebook is to offer a critical and practical mind map introduction to research writing to assist researchers in creating an appropriate design for their research studies and to offer the simplest guide of creating a logical orientated research. The book is made using simple graphs to explain what is expected of researchers at each stage of their research writing to enable them to understand if any a missing link when conducting their research. The book is mostly content mind-map and figures to make it easier for the researcher to understand what is expected of them from the stages of their research to completion. It presents the basic tenets of methodological steps so that the researcher can become familiar with how to conduct research and what techniques to use in their choice for research writing.
Dr Dare E Ajayi
The complexities and diversities of human nature and challenges necessitated the need to discover and identify ways to solving and meeting human and academic problem needs. The existence of problems gave rise to the the need for research. The book takes researchers and students through the latest and best research practice through the adoption of simple, adoptable and practicable research models for academic and contemporary research writing.
Journal of Universal College of Medical Sciences
bishal joshi
INTRODUCTION A research paper is a part of academic writing where there is a gathering of information from different sources. It is multistep process. Selection of title is the most important part of research writing. The title which is interesting should be chosen for the research purpose. All the related information is gathered and the title for research is synthesized. After thorough understanding and developing the title, the preliminary outline is made which maintains the logical path for its exploration. After preliminary research, proper research work is started with collection of previous resources which is then organized and important points are noted. Then research paper is written by referring to outlines, notes, articles, journals and books. The research paper should be well structured containing core parts like introduction, material and methods, results and disscussion and important additional parts like title, abstract, references.
Abstract Students sometimes find the general process of writing an empirical research paper to be daunting. Yet, when the process is approached in a systematic way, students can become more comfortable with the writing and standard formatting used in an empirical article. Accordingly, the current paper serves as a template for the budding social scientist.
Kevin O'Donnell
Roohullah Nawandish
Richard Baskas, Ed.D. Candidate
Scientific Research Journal of Clinical and Medical Sciences
Ahmed Alkhaqani
Background: Confusion about elements of a research paper is common among students. The key to writing a good research paper is to know these common elements and their definitions. Maybe find that writing a research paper is not as easy as it seems. There are many parts and steps to the process, and it can be hard to figure out what needs to do and when. Objective: This article aims to teach these common aspects of a research paper to avoid common mistakes while drafting own. Conclusion: Each section of the research paper serves a distinct purpose and highlights a different aspect of the research. However, before starting drafting the manuscript, having a clear understanding of each section's purposes will help avoid mistakes.
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
- Skip to main content
- Skip to primary sidebar
- Skip to footer
- QuestionPro

- Solutions Industries Gaming Automotive Sports and events Education Government Travel & Hospitality Financial Services Healthcare Cannabis Technology Use Case NPS+ Communities Audience Contactless surveys Mobile LivePolls Member Experience GDPR Positive People Science 360 Feedback Surveys
- Resources Blog eBooks Survey Templates Case Studies Training Help center
Home Market Research Research Tools and Apps
Theoretical Research: Definition, Methods + Examples

Research is the careful study of a particular research problem or concern using the scientific method. A theory is essential for any research project because it gives it direction and helps prove or disprove something. Theoretical basis helps us figure out how things work and why we do certain things.
Theoretical research lets you examine and discuss a research object using philosophical ideas and abstract theoretical structures.
In theoretical research, you can’t look at the research object directly. With the help of research literature, your research aims to define and sketch out the chosen topic’s conceptual models, explanations, and structures.
LEARN ABOUT: Research Process Steps
This blog will cover theoretical research and why it is essential. In addition to that, we are going to go over some examples.
What is the theoretical research?
Theoretical research is the systematic examination of a set of beliefs and assumptions.
It aims to learn more about a subject and help us understand it better. The information gathered in this way is not used for anything in particular because this kind of research aims to learn more.
All professionals, like biologists, chemists, engineers, architects, philosophers, writers, sociologists, historians, etc., can do theoretical research. No matter what field you work in, theoretical research is the foundation for new ideas.
It tries to answer basic questions about people, which is why this kind of research is used in every field of knowledge.
For example , a researcher starts with the idea that we need to understand the world around us. To do this, he begins with a hypothesis and tests it through experiments that will help him develop new ideas.
What is the theoretical framework?
A theoretical framework is a critical component in research that provides a structured foundation for investigating a specific topic or problem. It encompasses a set of interconnected theories, existing theories, and concepts that guide the entire research process.
The theoretical framework introduces a comprehensive understanding of the subject matter. Also, the theoretical framework strengthens the research’s validity and specifies the key elements that will be explored. Furthermore, it connects different ideas and theories, forming a cohesive structure that underpins the research endeavor.
A complete theoretical framework consists of a network of theories, existing theories, and concepts that collectively shape the direction of a research study.
The theoretical framework is the fundamental principle that will be explored, strengthens the research’s credibility by aligning it with established knowledge, specifies the variables under investigation, and connects different aspects of the research to create a unified approach.
Theoretical frameworks are the intellectual scaffolding upon which the research is constructed. It is the lens through which researchers view their subject, guiding their choice of methodologies, data collection, analysis, and interpretation. By incorporating existing theory, and established concepts, a theoretical framework not only grounds the research but also provides a coherent roadmap for exploring the intricacies of the chosen topic.
Benefits of theoretical research
Theoretical research yields a wealth of benefits across various fields, from social sciences to human resource development and political science. Here’s a breakdown of these benefits while incorporating the requested topics:
Predictive power
Theoretical models are the cornerstone of theoretical research. They grant us predictive power, enabling us to forecast intricate behaviors within complex systems, like societal interactions. In political science, for instance, a theoretical model helps anticipate potential outcomes of policy changes.
Understanding human behavior
Drawing from key social science theories, it assists us in deciphering human behavior and societal dynamics. For instance, in the context of human resource development, theories related to motivation and psychology provide insights into how to effectively manage a diverse workforce.
Optimizing workforce
In the realm of human resource development, insights gleaned from theoretical research, along with the research methods knowledge base, help create targeted training programs. By understanding various learning methodologies and psychological factors, organizations can optimize workforce training for better results.
Building on foundations
It doesn’t exist in isolation; it builds upon existing theories. For instance, within the human resource development handbook, theoretical research expands established concepts, refining their applicability to contemporary organizational challenges.
Ethical policy formulation
Within political science, theoretical research isn’t confined to governance structures. It extends to ethical considerations, aiding policymakers in creating policies that balance the collective good with individual rights, ensuring just and fair governance.
Rigorous investigations
Theoretical research underscores the importance of research methods knowledge base. This knowledge equips researchers in theory-building research methods and other fields to design robust research methodologies, yielding accurate data and credible insights.
Long-term impact
Theoretical research leaves a lasting impact. The theoretical models and insights from key social science theories provide enduring frameworks for subsequent research, contributing to the cumulative growth of knowledge in these fields.
Innovation and practical applications
It doesn’t merely remain theoretical. It inspires innovation and practical applications. By merging insights from diverse theories and fields, practitioners in human resource development devise innovative strategies to foster employee growth and well-being.
Theoretical research method
Researchers follow so many methods when doing research. There are two types of theoretical research methods.
- Scientific methods
- Social science method
Let’s explore them below:

Scientific method
Scientific methods have some important points that you should know. Let’s figure them out below:
- Observation: Any part you want to explain can be found through observation. It helps define the area of research.
- Hypothesis: The hypothesis is the idea put into words, which helps us figure out what we see.
- Experimentation: Hypotheses are tested through experiments to see if they are true. These experiments are different for each research.
- Theory: When we create a theory, we do it because we believe it will explain hypotheses of higher probability.
- Conclusions: Conclusions are the learnings we derive from our investigation.
Social science methods
There are different methods for social science theoretical research. It consists of polls, documentation, and statistical analysis.
- Polls: It is a process whereby the researcher uses a topic-specific questionnaire to gather data. No changes are made to the environment or the phenomenon where the polls are conducted to get the most accurate results. QuestionPro live polls are a great way to get live audiences involved and engaged.
- Documentation: Documentation is a helpful and valuable technique that helps the researcher learn more about the subject. It means visiting libraries or other specialized places, like documentation centers, to look at the existing bibliography. With the documentation, you can find out what came before the investigated topic and what other investigations have found. This step is important because it shows whether or not similar investigations have been done before and what the results were.
- Statistic analysis : Statistics is a branch of math that looks at random events and differences. It follows the rules that are established by probability. It’s used a lot in sociology and language research.
Examples of theoretical research
We talked about theoretical study methods in the previous part. We’ll give you some examples to help you understand it better.
Example 1: Theoretical research into the health benefits of hemp
The plant’s active principles are extracted and evaluated, and by studying their components, it is possible to determine what they contain and whether they can potentially serve as a medication.
Example 2: Linguistics research
Investigate to determine how many people in the Basque Country speak Basque. Surveys can be used to determine the number of native Basque speakers and those who speak Basque as a second language.
Example 3: Philosophical research
Research politics and ethics as they are presented in the writings of Hanna Arendt from a theoretical perspective.
LEARN ABOUT: 12 Best Tools for Researchers
From our above discussion, we learned about theoretical research and its methods and gave some examples. It explains things and leads to more knowledge for the sake of knowledge. This kind of research tries to find out more about a thing or an idea, but the results may take time to be helpful in the real world.
This research is sometimes called basic research. Theoretical research is an important process that gives researchers valuable data with insight.
QuestionPro is a strong platform for managing your data. You can conduct simple surveys to more complex research using QuestionPro survey software.
At QuestionPro, we give researchers tools for collecting data, such as our survey software and a library of insights for any long-term study. Contact our expert team to find out more about it.
FREE TRIAL LEARN MORE
MORE LIKE THIS
Data Information vs Insight: Essential differences
May 14, 2024

Pricing Analytics Software: Optimize Your Pricing Strategy
May 13, 2024

Relationship Marketing: What It Is, Examples & Top 7 Benefits
May 8, 2024

The Best Email Survey Tool to Boost Your Feedback Game
May 7, 2024
Other categories
- Academic Research
- Artificial Intelligence
- Assessments
- Brand Awareness
- Case Studies
- Communities
- Consumer Insights
- Customer effort score
- Customer Engagement
- Customer Experience
- Customer Loyalty
- Customer Research
- Customer Satisfaction
- Employee Benefits
- Employee Engagement
- Employee Retention
- Friday Five
- General Data Protection Regulation
- Insights Hub
- Life@QuestionPro
- Market Research
- Mobile diaries
- Mobile Surveys
- New Features
- Online Communities
- Question Types
- Questionnaire
- QuestionPro Products
- Release Notes
- Research Tools and Apps
- Revenue at Risk
- Survey Templates
- Training Tips
- Uncategorized
- Video Learning Series
- What’s Coming Up
- Workforce Intelligence
Quick links
- Directories
- Make a Gift
Writing Papers That Apply Sociological Theories or Perspectives
This document is intended as an additional resource for undergraduate students taking sociology courses at UW. It is not intended to replace instructions from your professors and TAs. In all cases follow course-specific assignment instructions, and consult your TA or professor if you have questions.
About These Assignments
Theory application assignments are a common type of analytical writing assigned in sociology classes. Many instructors expect you to apply sociological theories (sometimes called "perspectives" or "arguments") to empirical phenomena. [1] There are different ways to do this, depending upon your objectives, and of course, the specifics of each assignment. You can choose cases that confirm (support), disconfirm (contradict), [2] or partially confirm any theory.
How to Apply Theory to Empirical Phenomena
Theory application assignments generally require you to look at empirical phenomena through the lens of theory. Ask yourself, what would the theory predict ("have to say") about a particular situation. According to the theory, if particular conditions are present or you see a change in a particular variable, what outcome should you expect?
Generally, a first step in a theory application assignment is to make certain you understand the theory! You should be able to state the theory (the author's main argument) in a sentence or two. Usually, this means specifying the causal relationship (X—>Y) or the causal model (which might involve multiple variables and relationships).
For those taking sociological theory classes, in particular, you need to be aware that theories are constituted by more than causal relationships. Depending upon the assignment, you may be asked to specify the following:
- Causal Mechanism: This is a detailed explanation about how X—>Y, often made at a lower level of analysis (i.e., using smaller units) than the causal relationship.
- Level of Analysis: Macro-level theories refer to society- or group-level causes and processes; micro-level theories address individual-level causes and processes.
- Scope Conditions: These are parameters or boundaries specified by the theorist that identify the types of empirical phenomena to which the theory applies.
- Assumptions: Most theories begin by assuming certain "facts." These often concern the bases of human behavior: for example, people are inherently aggressive or inherently kind, people act out of self-interest or based upon values, etc.
Theories vary in terms of whether they specify assumptions, scope conditions and causal mechanisms. Sometimes they can only be inferred: when this is the case, be clear about that in your paper.
Clearly understanding all the parts of a theory helps you ensure that you are applying the theory correctly to your case. For example, you can ask whether your case fits the theory's assumptions and scope conditions. Most importantly, however, you should single out the main argument or point (usually the causal relationship and mechanism) of the theory. Does the theorist's key argument apply to your case? Students often go astray here by latching onto an inconsequential or less important part of the theory reading, showing the relationship to their case, and then assuming they have fully applied the theory.
Using Evidence to Make Your Argument
Theory application papers involve making a claim or argument based on theory, supported by empirical evidence. [3] There are a few common problems that students encounter while writing these types of assignments: unsubstantiated claims/generalizations; "voice" issues or lack of attribution; excessive summarization/insufficient analysis. Each class of problem is addressed below, followed by some pointers for choosing "cases," or deciding upon the empirical phenomenon to which you will apply the theoretical perspective or argument (including where to find data).
A common problem seen in theory application assignments is failing to substantiate claims, or making a statement that is not backed up with evidence or details ("proof"). When you make a statement or a claim, ask yourself, "How do I know this?" What evidence can you marshal to support your claim? Put this evidence in your paper (and remember to cite your sources). Similarly, be careful about making overly strong or broad claims based on insufficient evidence. For example, you probably don't want to make a claim about how Americans feel about having a black president based on a poll of UW undergraduates. You may also want to be careful about making authoritative (conclusive) claims about broad social phenomena based on a single case study.
In addition to un- or under-substantiated claims, another problem that students often encounter when writing these types of papers is lack of clarity regarding "voice," or whose ideas they are presenting. The reader is left wondering whether a given statement represents the view of the theorist, the student, or an author who wrote about the case. Be careful to identify whose views and ideas you are presenting. For example, you could write, "Marx views class conflict as the engine of history;" or, "I argue that American politics can best be understood through the lens of class conflict;" [4] or, "According to Ehrenreich, Walmart employees cannot afford to purchase Walmart goods."
Another common problem that students encounter is the trap of excessive summarization. They spend the majority of their papers simply summarizing (regurgitating the details) of a case—much like a book report. One way to avoid this is to remember that theory indicates which details (or variables) of a case are most relevant, and to focus your discussion on those aspects. A second strategy is to make sure that you relate the details of the case in an analytical fashion. You might do this by stating an assumption of Marxist theory, such as "man's ideas come from his material conditions," and then summarizing evidence from your case on that point. You could organize the details of the case into paragraphs and start each paragraph with an analytical sentence about how the theory relates to different aspects of the case.
Some theory application papers require that you choose your own case (an empirical phenomenon, trend, situation, etc.), whereas others specify the case for you (e.g., ask you to apply conflict theory to explain some aspect of globalization described in an article). Many students find choosing their own case rather challenging. Some questions to guide your choice are:
- Can I obtain sufficient data with relative ease on my case?
- Is my case specific enough? If your subject matter is too broad or abstract, it becomes both difficult to gather data and challenging to apply the theory.
- Is the case an interesting one? Professors often prefer that you avoid examples used by the theorist themselves, those used in lectures and sections, and those that are extremely obvious.
Where You Can Find Data
Data is collected by many organizations (e.g., commercial, governmental, nonprofit, academic) and can frequently be found in books, reports, articles, and online sources. The UW libraries make your job easy: on the front page of the library website ( www.lib.washington.edu ), in the left hand corner you will see a list of options under the heading "Find It" that allows you to go directly to databases, specific online journals, newspapers, etc. For example, if you are choosing a historical case, you might want to access newspaper articles. This has become increasingly easy to do, as many are now online through the UW library. For example, you can search The New York Times and get full-text online for every single issue from 1851 through today! If you are interested in interview or observational data, you might try to find books or articles that are case-studies on your topic of interest by conducting a simple keyword search of the UW library book holdings, or using an electronic database, such as JSTOR or Sociological Abstracts. Scholarly articles are easy to search through, since they contain abstracts, or paragraphs that summarize the topic, relevant literature, data and methods, and major findings. When using JSTOR, you may want to limit your search to sociology (which includes 70 journals) and perhaps political science; this database retrieves full-text articles. Sociological Abstracts will cast a wider net searching many more sociology journals, but the article may or may not be available online (find out by clicking "check for UW holdings"). A final word about using academic articles for data: remember that you need to cite your sources, and follow the instructions of your assignment. This includes making your own argument about your case, not using an argument you find in a scholarly article.
In addition, there are many data sources online. For example, you can get data from the US census, including for particular neighborhoods, from a number of cites. You can get some crime data online: the Seattle Police Department publishes several years' worth of crime rates. There are numerous cites on public opinion, including gallup.com. There is an online encyclopedia on Washington state history, including that of individual Seattle neighborhoods ( www.historylink.org ). These are just a couple options: a simple google search will yield hundreds more. Finally, remember that librarian reference desks are expert on data sources, and that you can call, email, or visit in person to ask about what data is available on your particular topic. You can chat with a librarian 24 hours a day online, as well (see the "Ask Us!" link on the front page of UW libraries website for contact information).
[1] By empirical phenomena, we mean some sort of observed, real-world conditions. These include societal trends, events, or outcomes. They are sometimes referred to as "cases." Return to Reading
[2] A cautionary note about critiquing theories: no social theory explains all cases, so avoid claiming that a single case "disproves" a theory, or that a single case "proves" a theory correct. Moreover, if you choose a case that disconfirms a theory, you should be careful that the case falls within the scope conditions (see above) of the given theory. For example, if a theorist specifies that her argument pertains to economic transactions, it would not be a fair critique to say the theory doesn't explain dynamics within a family. On the other hand, it is useful and interesting to apply theories to cases not foreseen by the original theorist (we see this in sociological theories that incorporate theories from evolutionary biology or economics). Return to Reading
[3] By empirical evidence, we mean data on social phenomena, derived from scientific observation or experiment. Empirical evidence may be quantitative (e.g., statistical data) or qualitative (e.g., descriptions derived from systematic observation or interviewing), or a mixture of both. Empirical evidence must be observable and derived from real-world conditions (present or historical) rather than hypothetical or "imagined". For additional help, see the "Where You Can Find Data" section on the next page. Return to Reading
[4] If your instructor does not want you to use the first-person, you could write, "This paper argues…" Return to Reading
- Newsletter
- Technical Support
- Find My Rep
You are here
Find the Theory in Your Research Little Quick Fix
- Janet E. Salmons - Free-range Scholar, Vision2Lead and Research Community Manager at SAGE MethodSpace
- Description
One of the most crucial foundational steps in any research project surrounds understanding and choosing an appropriate theory to frame the research question. Theoretical frameworks don’t just impact design, they impact how the entire study is interpreted, contextualized, and discussed. There are lots of resources about epistemologies and ontologies, but most focus on the philosophical and historical dimensions that can quickly overwhelm students. They need something quick that helps them understand the practical connection between theory and the purpose/nature of the study and, more importantly, decide which theory is best suited to their particular study. This Little Quick Fix covers questions like: What is theory? How does theory relate to research design? What is a theoretical framework? What is a theoretical contribution? How do I choose which theory (or theories) fits my research? What practical steps should I take to integrate theory into my research?
Little Quick Fix titles provide quick but authoritative answers to the problems, hurdles, and assessment points students face in the research course, project proposal, or design—whatever their methods learning is.
- Lively, ultra-modern design; full-colour, each page a tailored design.
- An hour's read. Easy to dip in and out of with clear navigation enables the reader to find what she needs—quick.
- Direct written style gets to the point with clear language. Nothing needs to be read twice. No fluff.
- Learning is reinforced through a 2-minute overview summary; 3-second summaries with super-quick Q&A
- DIY tasks create a work plan to accomplish a task, do a self-check quiz, solve a problem, get students to what they need to show their supervisor.
- Checkpoints in each section make sure students are nailing it as they go and support self-directed learning.
- How do I know I’m done? Each Little Quick Fix wraps up with a final checklist that allows the reader to self-assess they’ve got what they need to progress, submit, or ace the test or task.
See what’s new to this edition by selecting the Features tab on this page. Should you need additional information or have questions regarding the HEOA information provided for this title, including what is new to this edition, please email [email protected] . Please include your name, contact information, and the name of the title for which you would like more information. For information on the HEOA, please go to http://ed.gov/policy/highered/leg/hea08/index.html .
For assistance with your order: Please email us at [email protected] or connect with your SAGE representative.
SAGE 2455 Teller Road Thousand Oaks, CA 91320 www.sagepub.com
A brief but focused look at a key aspect of any research.
This book is one of this series which are excellent introductions that all students no matter what their prior experience and knowledge will be able to engage, explore and learn from to support their research as education students, highly recommended.
This is a fantastic little book for students
Nice little guide that focuses on specific issues and are explained in an appealing way for undergraduate students struggling with academic writing and research methods.
It is easy to understand for students studying the foundation of research
All titles in this set are excellent and introduced to all students during their intial induction study day
An excellent and digestible small book that will help students to understand the importance and meaning of situating 'theory' in their research.
I was really excited about a quick, little book that my students could use as a quick start in the subject. However, to be honest, I think it is totally useless and provides no additional value. if you switch a little bit back and forth on wikipedia, you get more insights and help. That is not what I expected...
Preview this book
Sample materials & chapters.
Intro & Qu 1: What do researchers mean when they talk about epistemology, ontolo
For instructors
Select a purchasing option.
Shipped Options:
Little Quick Fixes for Research Projects Set 2021
Little Quick Fixes: The Box Set 2021
Related Products

An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- SAGE Open Med
Grounded theory research: A design framework for novice researchers
Ylona chun tie.
1 Nursing and Midwifery, College of Healthcare Sciences, James Cook University, Townsville, QLD, Australia
Melanie Birks
Karen francis.
2 College of Health and Medicine, University of Tasmania, Australia, Hobart, TAS, Australia
Background:
Grounded theory is a well-known methodology employed in many research studies. Qualitative and quantitative data generation techniques can be used in a grounded theory study. Grounded theory sets out to discover or construct theory from data, systematically obtained and analysed using comparative analysis. While grounded theory is inherently flexible, it is a complex methodology. Thus, novice researchers strive to understand the discourse and the practical application of grounded theory concepts and processes.
The aim of this article is to provide a contemporary research framework suitable to inform a grounded theory study.
This article provides an overview of grounded theory illustrated through a graphic representation of the processes and methods employed in conducting research using this methodology. The framework is presented as a diagrammatic representation of a research design and acts as a visual guide for the novice grounded theory researcher.
Discussion:
As grounded theory is not a linear process, the framework illustrates the interplay between the essential grounded theory methods and iterative and comparative actions involved. Each of the essential methods and processes that underpin grounded theory are defined in this article.
Conclusion:
Rather than an engagement in philosophical discussion or a debate of the different genres that can be used in grounded theory, this article illustrates how a framework for a research study design can be used to guide and inform the novice nurse researcher undertaking a study using grounded theory. Research findings and recommendations can contribute to policy or knowledge development, service provision and can reform thinking to initiate change in the substantive area of inquiry.
Introduction
The aim of all research is to advance, refine and expand a body of knowledge, establish facts and/or reach new conclusions using systematic inquiry and disciplined methods. 1 The research design is the plan or strategy researchers use to answer the research question, which is underpinned by philosophy, methodology and methods. 2 Birks 3 defines philosophy as ‘a view of the world encompassing the questions and mechanisms for finding answers that inform that view’ (p. 18). Researchers reflect their philosophical beliefs and interpretations of the world prior to commencing research. Methodology is the research design that shapes the selection of, and use of, particular data generation and analysis methods to answer the research question. 4 While a distinction between positivist research and interpretivist research occurs at the paradigm level, each methodology has explicit criteria for the collection, analysis and interpretation of data. 2 Grounded theory (GT) is a structured, yet flexible methodology. This methodology is appropriate when little is known about a phenomenon; the aim being to produce or construct an explanatory theory that uncovers a process inherent to the substantive area of inquiry. 5 – 7 One of the defining characteristics of GT is that it aims to generate theory that is grounded in the data. The following section provides an overview of GT – the history, main genres and essential methods and processes employed in the conduct of a GT study. This summary provides a foundation for a framework to demonstrate the interplay between the methods and processes inherent in a GT study as presented in the sections that follow.
Glaser and Strauss are recognised as the founders of grounded theory. Strauss was conversant in symbolic interactionism and Glaser in descriptive statistics. 8 – 10 Glaser and Strauss originally worked together in a study examining the experience of terminally ill patients who had differing knowledge of their health status. Some of these suspected they were dying and tried to confirm or disconfirm their suspicions. Others tried to understand by interpreting treatment by care providers and family members. Glaser and Strauss examined how the patients dealt with the knowledge they were dying and the reactions of healthcare staff caring for these patients. Throughout this collaboration, Glaser and Strauss questioned the appropriateness of using a scientific method of verification for this study. During this investigation, they developed the constant comparative method, a key element of grounded theory, while generating a theory of dying first described in Awareness of Dying (1965). The constant comparative method is deemed an original way of organising and analysing qualitative data.
Glaser and Strauss subsequently went on to write The Discovery of Grounded Theory: Strategies for Qualitative Research (1967). This seminal work explained how theory could be generated from data inductively. This process challenged the traditional method of testing or refining theory through deductive testing. Grounded theory provided an outlook that questioned the view of the time that quantitative methodology is the only valid, unbiased way to determine truths about the world. 11 Glaser and Strauss 5 challenged the belief that qualitative research lacked rigour and detailed the method of comparative analysis that enables the generation of theory. After publishing The Discovery of Grounded Theory , Strauss and Glaser went on to write independently, expressing divergent viewpoints in the application of grounded theory methods.
Glaser produced his book Theoretical Sensitivity (1978) and Strauss went on to publish Qualitative Analysis for Social Scientists (1987). Strauss and Corbin’s 12 publication Basics of Qualitative Research: Grounded Theory Procedures and Techniques resulted in a rebuttal by Glaser 13 over their application of grounded theory methods. However, philosophical perspectives have changed since Glaser’s positivist version and Strauss and Corbin’s post-positivism stance. 14 Grounded theory has since seen the emergence of additional philosophical perspectives that have influenced a change in methodological development over time. 15
Subsequent generations of grounded theorists have positioned themselves along a philosophical continuum, from Strauss and Corbin’s 12 theoretical perspective of symbolic interactionism, through to Charmaz’s 16 constructivist perspective. However, understanding how to position oneself philosophically can challenge novice researchers. Birks and Mills 6 provide a contemporary understanding of GT in their book Grounded theory: A Practical Guide. These Australian researchers have written in a way that appeals to the novice researcher. It is the contemporary writing, the way Birks and Mills present a non-partisan approach to GT that support the novice researcher to understand the philosophical and methodological concepts integral in conducting research. The development of GT is important to understand prior to selecting an approach that aligns with the researcher’s philosophical position and the purpose of the research study. As the research progresses, seminal texts are referred back to time and again as understanding of concepts increases, much like the iterative processes inherent in the conduct of a GT study.
Genres: traditional, evolved and constructivist grounded theory
Grounded theory has several distinct methodological genres: traditional GT associated with Glaser; evolved GT associated with Strauss, Corbin and Clarke; and constructivist GT associated with Charmaz. 6 , 17 Each variant is an extension and development of the original GT by Glaser and Strauss. The first of these genres is known as traditional or classic GT. Glaser 18 acknowledged that the goal of traditional GT is to generate a conceptual theory that accounts for a pattern of behaviour that is relevant and problematic for those involved. The second genre, evolved GT, is founded on symbolic interactionism and stems from work associated with Strauss, Corbin and Clarke. Symbolic interactionism is a sociological perspective that relies on the symbolic meaning people ascribe to the processes of social interaction. Symbolic interactionism addresses the subjective meaning people place on objects, behaviours or events based on what they believe is true. 19 , 20 Constructivist GT, the third genre developed and explicated by Charmaz, a symbolic interactionist, has its roots in constructivism. 8 , 16 Constructivist GT’s methodological underpinnings focus on how participants’ construct meaning in relation to the area of inquiry. 16 A constructivist co-constructs experience and meanings with participants. 21 While there are commonalities across all genres of GT, there are factors that distinguish differences between the approaches including the philosophical position of the researcher; the use of literature; and the approach to coding, analysis and theory development. Following on from Glaser and Strauss, several versions of GT have ensued.
Grounded theory represents both a method of inquiry and a resultant product of that inquiry. 7 , 22 Glaser and Holton 23 define GT as ‘a set of integrated conceptual hypotheses systematically generated to produce an inductive theory about a substantive area’ (p. 43). Strauss and Corbin 24 define GT as ‘theory that was derived from data, systematically gathered and analysed through the research process’ (p. 12). The researcher ‘begins with an area of study and allows the theory to emerge from the data’ (p. 12). Charmaz 16 defines GT as ‘a method of conducting qualitative research that focuses on creating conceptual frameworks or theories through building inductive analysis from the data’ (p. 187). However, Birks and Mills 6 refer to GT as a process by which theory is generated from the analysis of data. Theory is not discovered; rather, theory is constructed by the researcher who views the world through their own particular lens.
Research process
Before commencing any research study, the researcher must have a solid understanding of the research process. A well-developed outline of the study and an understanding of the important considerations in designing and undertaking a GT study are essential if the goals of the research are to be achieved. While it is important to have an understanding of how a methodology has developed, in order to move forward with research, a novice can align with a grounded theorist and follow an approach to GT. Using a framework to inform a research design can be a useful modus operandi.
The following section provides insight into the process of undertaking a GT research study. Figure 1 is a framework that summarises the interplay and movement between methods and processes that underpin the generation of a GT. As can be seen from this framework, and as detailed in the discussion that follows, the process of doing a GT research study is not linear, rather it is iterative and recursive.

Research design framework: summary of the interplay between the essential grounded theory methods and processes.
Grounded theory research involves the meticulous application of specific methods and processes. Methods are ‘systematic modes, procedures or tools used for collection and analysis of data’. 25 While GT studies can commence with a variety of sampling techniques, many commence with purposive sampling, followed by concurrent data generation and/or collection and data analysis, through various stages of coding, undertaken in conjunction with constant comparative analysis, theoretical sampling and memoing. Theoretical sampling is employed until theoretical saturation is reached. These methods and processes create an unfolding, iterative system of actions and interactions inherent in GT. 6 , 16 The methods interconnect and inform the recurrent elements in the research process as shown by the directional flow of the arrows and the encompassing brackets in Figure 1 . The framework denotes the process is both iterative and dynamic and is not one directional. Grounded theory methods are discussed in the following section.
Purposive sampling
As presented in Figure 1 , initial purposive sampling directs the collection and/or generation of data. Researchers purposively select participants and/or data sources that can answer the research question. 5 , 7 , 16 , 21 Concurrent data generation and/or data collection and analysis is fundamental to GT research design. 6 The researcher collects, codes and analyses this initial data before further data collection/generation is undertaken. Purposeful sampling provides the initial data that the researcher analyses. As will be discussed, theoretical sampling then commences from the codes and categories developed from the first data set. Theoretical sampling is used to identify and follow clues from the analysis, fill gaps, clarify uncertainties, check hunches and test interpretations as the study progresses.
Constant comparative analysis
Constant comparative analysis is an analytical process used in GT for coding and category development. This process commences with the first data generated or collected and pervades the research process as presented in Figure 1 . Incidents are identified in the data and coded. 6 The initial stage of analysis compares incident to incident in each code. Initial codes are then compared to other codes. Codes are then collapsed into categories. This process means the researcher will compare incidents in a category with previous incidents, in both the same and different categories. 5 Future codes are compared and categories are compared with other categories. New data is then compared with data obtained earlier during the analysis phases. This iterative process involves inductive and deductive thinking. 16 Inductive, deductive and abductive reasoning can also be used in data analysis. 26
Constant comparative analysis generates increasingly more abstract concepts and theories through inductive processes. 16 In addition, abduction, defined as ‘a form of reasoning that begins with an examination of the data and the formation of a number of hypotheses that are then proved or disproved during the process of analysis … aids inductive conceptualization’. 6 Theoretical sampling coupled with constant comparative analysis raises the conceptual levels of data analysis and directs ongoing data collection or generation. 6
The constant comparative technique is used to find consistencies and differences, with the aim of continually refining concepts and theoretically relevant categories. This continual comparative iterative process that encompasses GT research sets it apart from a purely descriptive analysis. 8
Memo writing is an analytic process considered essential ‘in ensuring quality in grounded theory’. 6 Stern 27 offers the analogy that if data are the building blocks of the developing theory, then memos are the ‘mortar’ (p. 119). Memos are the storehouse of ideas generated and documented through interacting with data. 28 Thus, memos are reflective interpretive pieces that build a historic audit trail to document ideas, events and the thought processes inherent in the research process and developing thinking of the analyst. 6 Memos provide detailed records of the researchers’ thoughts, feelings and intuitive contemplations. 6
Lempert 29 considers memo writing crucial as memos prompt researchers to analyse and code data and develop codes into categories early in the coding process. Memos detail why and how decisions made related to sampling, coding, collapsing of codes, making of new codes, separating codes, producing a category and identifying relationships abstracted to a higher level of analysis. 6 Thus, memos are informal analytic notes about the data and the theoretical connections between categories. 23 Memoing is an ongoing activity that builds intellectual assets, fosters analytic momentum and informs the GT findings. 6 , 10
Generating/collecting data
A hallmark of GT is concurrent data generation/collection and analysis. In GT, researchers may utilise both qualitative and quantitative data as espoused by Glaser’s dictum; ‘all is data’. 30 While interviews are a common method of generating data, data sources can include focus groups, questionnaires, surveys, transcripts, letters, government reports, documents, grey literature, music, artefacts, videos, blogs and memos. 9 Elicited data are produced by participants in response to, or directed by, the researcher whereas extant data includes data that is already available such as documents and published literature. 6 , 31 While this is one interpretation of how elicited data are generated, other approaches to grounded theory recognise the agency of participants in the co-construction of data with the researcher. The relationship the researcher has with the data, how it is generated and collected, will determine the value it contributes to the development of the final GT. 6 The significance of this relationship extends into data analysis conducted by the researcher through the various stages of coding.
Coding is an analytical process used to identify concepts, similarities and conceptual reoccurrences in data. Coding is the pivotal link between collecting or generating data and developing a theory that explains the data. Charmaz 10 posits,
codes rely on interaction between researchers and their data. Codes consist of short labels that we construct as we interact with the data. Something kinaesthetic occurs when we are coding; we are mentally and physically active in the process. (p. 5)
In GT, coding can be categorised into iterative phases. Traditional, evolved and constructivist GT genres use different terminology to explain each coding phase ( Table 1 ).
Comparison of coding terminology in traditional, evolved and constructivist grounded theory.
Adapted from Birks and Mills. 6
Coding terminology in evolved GT refers to open (a procedure for developing categories of information), axial (an advanced procedure for interconnecting the categories) and selective coding (procedure for building a storyline from core codes that connects the categories), producing a discursive set of theoretical propositions. 6 , 12 , 32 Constructivist grounded theorists refer to initial, focused and theoretical coding. 9 Birks and Mills 6 use the terms initial, intermediate and advanced coding that link to low, medium and high-level conceptual analysis and development. The coding terms devised by Birks and Mills 6 were used for Figure 1 ; however, these can be altered to reflect the coding terminology used in the respective GT genres selected by the researcher.
Initial coding
Initial coding of data is the preliminary step in GT data analysis. 6 , 9 The purpose of initial coding is to start the process of fracturing the data to compare incident to incident and to look for similarities and differences in beginning patterns in the data. In initial coding, the researcher inductively generates as many codes as possible from early data. 16 Important words or groups of words are identified and labelled. In GT, codes identify social and psychological processes and actions as opposed to themes. Charmaz 16 emphasises keeping codes as similar to the data as possible and advocates embedding actions in the codes in an iterative coding process. Saldaña 33 agrees that codes that denote action, which he calls process codes, can be used interchangeably with gerunds (verbs ending in ing ). In vivo codes are often verbatim quotes from the participants’ words and are often used as the labels to capture the participant’s words as representative of a broader concept or process in the data. 6 Table 1 reflects variation in the terminology of codes used by grounded theorists.
Initial coding categorises and assigns meaning to the data, comparing incident-to-incident, labelling beginning patterns and beginning to look for comparisons between the codes. During initial coding, it is important to ask ‘what is this data a study of’. 18 What does the data assume, ‘suggest’ or ‘pronounce’ and ‘from whose point of view’ does this data come, whom does it represent or whose thoughts are they?. 16 What collectively might it represent? The process of documenting reactions, emotions and related actions enables researchers to explore, challenge and intensify their sensitivity to the data. 34 Early coding assists the researcher to identify the direction for further data gathering. After initial analysis, theoretical sampling is employed to direct collection of additional data that will inform the ‘developing theory’. 9 Initial coding advances into intermediate coding once categories begin to develop.
Theoretical sampling
The purpose of theoretical sampling is to allow the researcher to follow leads in the data by sampling new participants or material that provides relevant information. As depicted in Figure 1 , theoretical sampling is central to GT design, aids the evolving theory 5 , 7 , 16 and ensures the final developed theory is grounded in the data. 9 Theoretical sampling in GT is for the development of a theoretical category, as opposed to sampling for population representation. 10 Novice researchers need to acknowledge this difference if they are to achieve congruence within the methodology. Birks and Mills 6 define theoretical sampling as ‘the process of identifying and pursuing clues that arise during analysis in a grounded theory study’ (p. 68). During this process, additional information is sought to saturate categories under development. The analysis identifies relationships, highlights gaps in the existing data set and may reveal insight into what is not yet known. The exemplars in Box 1 highlight how theoretical sampling led to the inclusion of further data.
Examples of theoretical sampling.
Thus, theoretical sampling is used to focus and generate data to feed the iterative process of continual comparative analysis of the data. 6
Intermediate coding
Intermediate coding, identifying a core category, theoretical data saturation, constant comparative analysis, theoretical sensitivity and memoing occur in the next phase of the GT process. 6 Intermediate coding builds on the initial coding phase. Where initial coding fractures the data, intermediate coding begins to transform basic data into more abstract concepts allowing the theory to emerge from the data. During this analytic stage, a process of reviewing categories and identifying which ones, if any, can be subsumed beneath other categories occurs and the properties or dimension of the developed categories are refined. Properties refer to the characteristics that are common to all the concepts in the category and dimensions are the variations of a property. 37
At this stage, a core category starts to become evident as developed categories form around a core concept; relationships are identified between categories and the analysis is refined. Birks and Mills 6 affirm that diagramming can aid analysis in the intermediate coding phase. Grounded theorists interact closely with the data during this phase, continually reassessing meaning to ascertain ‘what is really going on’ in the data. 30 Theoretical saturation ensues when new data analysis does not provide additional material to existing theoretical categories, and the categories are sufficiently explained. 6
Advanced coding
Birks and Mills 6 described advanced coding as the ‘techniques used to facilitate integration of the final grounded theory’ (p. 177). These authors promote storyline technique (described in the following section) and theoretical coding as strategies for advancing analysis and theoretical integration. Advanced coding is essential to produce a theory that is grounded in the data and has explanatory power. 6 During the advanced coding phase, concepts that reach the stage of categories will be abstract, representing stories of many, reduced into highly conceptual terms. The findings are presented as a set of interrelated concepts as opposed to presenting themes. 28 Explanatory statements detail the relationships between categories and the central core category. 28
Storyline is a tool that can be used for theoretical integration. Birks and Mills 6 define storyline as ‘a strategy for facilitating integration, construction, formulation, and presentation of research findings through the production of a coherent grounded theory’ (p. 180). Storyline technique is first proposed with limited attention in Basics of Qualitative Research by Strauss and Corbin 12 and further developed by Birks et al. 38 as a tool for theoretical integration. The storyline is the conceptualisation of the core category. 6 This procedure builds a story that connects the categories and produces a discursive set of theoretical propositions. 24 Birks and Mills 6 contend that storyline can be ‘used to produce a comprehensive rendering of your grounded theory’ (p. 118). Birks et al. 38 had earlier concluded, ‘storyline enhances the development, presentation and comprehension of the outcomes of grounded theory research’ (p. 405). Once the storyline is developed, the GT is finalised using theoretical codes that ‘provide a framework for enhancing the explanatory power of the storyline and its potential as theory’. 6 Thus, storyline is the explication of the theory.
Theoretical coding occurs as the final culminating stage towards achieving a GT. 39 , 40 The purpose of theoretical coding is to integrate the substantive theory. 41 Saldaña 40 states, ‘theoretical coding integrates and synthesises the categories derived from coding and analysis to now create a theory’ (p. 224). Initial coding fractures the data while theoretical codes ‘weave the fractured story back together again into an organized whole theory’. 18 Advanced coding that integrates extant theory adds further explanatory power to the findings. 6 The examples in Box 2 describe the use of storyline as a technique.
Writing the storyline.
Theoretical sensitivity
As presented in Figure 1 , theoretical sensitivity encompasses the entire research process. Glaser and Strauss 5 initially described the term theoretical sensitivity in The Discovery of Grounded Theory. Theoretical sensitivity is the ability to know when you identify a data segment that is important to your theory. While Strauss and Corbin 12 describe theoretical sensitivity as the insight into what is meaningful and of significance in the data for theory development, Birks and Mills 6 define theoretical sensitivity as ‘the ability to recognise and extract from the data elements that have relevance for the emerging theory’ (p. 181). Conducting GT research requires a balance between keeping an open mind and the ability to identify elements of theoretical significance during data generation and/or collection and data analysis. 6
Several analytic tools and techniques can be used to enhance theoretical sensitivity and increase the grounded theorist’s sensitivity to theoretical constructs in the data. 28 Birks and Mills 6 state, ‘as a grounded theorist becomes immersed in the data, their level of theoretical sensitivity to analytic possibilities will increase’ (p. 12). Developing sensitivity as a grounded theorist and the application of theoretical sensitivity throughout the research process allows the analytical focus to be directed towards theory development and ultimately result in an integrated and abstract GT. 6 The example in Box 3 highlights how analytic tools are employed to increase theoretical sensitivity.
Theoretical sensitivity.

The grounded theory
The meticulous application of essential GT methods refines the analysis resulting in the generation of an integrated, comprehensive GT that explains a process relating to a particular phenomenon. 6 The results of a GT study are communicated as a set of concepts, related to each other in an interrelated whole, and expressed in the production of a substantive theory. 5 , 7 , 16 A substantive theory is a theoretical interpretation or explanation of a studied phenomenon 6 , 17 Thus, the hallmark of grounded theory is the generation of theory ‘abstracted from, or grounded in, data generated and collected by the researcher’. 6 However, to ensure quality in research requires the application of rigour throughout the research process.
Quality and rigour
The quality of a grounded theory can be related to three distinct areas underpinned by (1) the researcher’s expertise, knowledge and research skills; (2) methodological congruence with the research question; and (3) procedural precision in the use of methods. 6 Methodological congruence is substantiated when the philosophical position of the researcher is congruent with the research question and the methodological approach selected. 6 Data collection or generation and analytical conceptualisation need to be rigorous throughout the research process to secure excellence in the final grounded theory. 44
Procedural precision requires careful attention to maintaining a detailed audit trail, data management strategies and demonstrable procedural logic recorded using memos. 6 Organisation and management of research data, memos and literature can be assisted using software programs such as NVivo. An audit trail of decision-making, changes in the direction of the research and the rationale for decisions made are essential to ensure rigour in the final grounded theory. 6
This article offers a framework to assist novice researchers visualise the iterative processes that underpin a GT study. The fundamental process and methods used to generate an integrated grounded theory have been described. Novice researchers can adapt the framework presented to inform and guide the design of a GT study. This framework provides a useful guide to visualise the interplay between the methods and processes inherent in conducting GT. Research conducted ethically and with meticulous attention to process will ensure quality research outcomes that have relevance at the practice level.
Declaration of conflicting interests: The author(s) declared no potential conflicts of interest with respect to the research, authorship, and/or publication of this article.
Funding: The author(s) received no financial support for the research, authorship, and/or publication of this article.

- Privacy Policy

Home » Theory – Definition, Types and Examples
Theory – Definition, Types and Examples
Table of Contents

Definition:
Theory is a set of ideas or principles used to explain or describe a particular phenomenon or set of phenomena. The term “theory” is commonly used in the scientific context to refer to a well-substantiated explanation of some aspect of the natural world that is based on empirical evidence and rigorous testing.
Types of Theories
Types of Theories are as follows:
Scientific Theories
These are theories that explain natural phenomena and are based on empirical evidence. Examples include the theory of evolution, the germ theory of disease, and the theory of relativity.
Social Theories
These are theories that attempt to explain social phenomena, such as human behavior, culture, and society. Examples include social learning theory, structural functionalism, and feminist theory.
Psychological Theories
These are theories that attempt to explain human behavior and mental processes. Examples include behaviorism, cognitive psychology, and psychoanalysis.
Economic Theories
These are theories that attempt to explain economic phenomena, such as the behavior of markets, businesses, and consumers. Examples include supply and demand theory, Keynesian economics, and game theory.
Political Theories
These are theories that attempt to explain political phenomena, such as the behavior of governments, political systems, and international relations. Examples include liberalism, conservatism, and Marxism.
Philosophical Theories
These are theories that attempt to explain fundamental concepts, such as the nature of reality, knowledge, and morality. Examples include existentialism, utilitarianism, and metaphysics.
Mathematical Theories
These are theories that use mathematical concepts and models to explain phenomena in various fields, such as physics, economics, and computer science. Examples include set theory, probability theory, and game theory.
Communication Theories
These are theories that attempt to explain the processes and effects of communication, such as the transmission of information, the influence of media, and the development of language. Examples include social penetration theory, media effects theory, and speech act theory.
Biological Theories
These are theories that attempt to explain biological phenomena, such as the functioning of the human body, genetics, and evolution. Examples include the theory of natural selection, the germ theory of disease, and the central dogma of molecular biology.
Environmental Theories
These are theories that attempt to explain the interactions between humans and the natural environment, including the effects of human activities on the environment and the impact of environmental changes on human society. Examples include ecological systems theory, environmental determinism, and sustainability theory.
Educational Theories
These are theories that attempt to explain the processes and effects of learning and education. Examples include behaviorism, constructivism, and social learning theory.
Cultural Theories
These are theories that attempt to explain cultural phenomena, such as the formation and transmission of cultural values, norms, and beliefs. Examples include cultural studies, postcolonial theory, and critical race theory.
Examples of Theories
There are many theories in various fields of study. Here are some examples of theories in different areas:
- Evolutionary Theory: The theory of evolution by natural selection, proposed by Charles Darwin, explains how species change over time in response to their environment.
- Quantum Theory : Quantum theory is the branch of physics that describes the behavior of matter and energy on a very small scale.
- Social Learning Theory: Social learning theory suggests that people learn by observing and imitating the behaviors of others.
- Chaos Theory: Chaos theory is a branch of mathematics that studies complex systems and how they can exhibit unpredictable behavior.
- Cognitive Dissonance Theory : This theory explains how people often experience discomfort or tension when their beliefs, attitudes, and behaviors are inconsistent with each other.
- Attachment Theory: Attachment theory explains how early relationships between infants and their caregivers can shape their emotional and social development later in life.
- General Relativity: General relativity is a theory of gravitation that explains how the force of gravity arises from the curvature of spacetime caused by massive objects.
- Game Theory: Game theory is a mathematical approach used to model and analyze the strategic interactions between individuals or groups.
- Self-Determination Theory: This theory suggests that people are motivated by three fundamental needs: autonomy, competence, and relatedness.
- Systems Theory: Systems theory is a framework for understanding complex systems that emphasizes their interdependence, feedback loops, and dynamic behavior.
Applications of Theories
Applications of Theories are as follows:
- Science : Scientific theories are used to develop new technologies, create new medicines, and explore the natural world. For example, the theory of evolution by natural selection is used to understand the diversity of life on Earth, while the theory of relativity is used to develop new technologies such as GPS.
- Psychology : Theories of psychology are used to understand human behavior and to develop effective therapies. For example, the theory of cognitive dissonance helps us to understand why people resist changing their beliefs, while the theory of operant conditioning is used to help people change their behavior.
- Sociology : Sociological theories are used to understand social structures, institutions, and relationships. For example, the theory of social capital helps us to understand the importance of social networks in promoting economic and social development, while the theory of cultural capital explains how cultural knowledge and practices contribute to social inequality.
- Economics : Economic theories are used to understand markets, trade, and economic growth. For example, the theory of comparative advantage helps to explain why countries specialize in certain goods and services, while the theory of supply and demand helps us to understand the behavior of consumers and producers.
- Education : Theories of learning and teaching are used to develop effective educational practices. For example, the theory of constructivism emphasizes the importance of students constructing their own knowledge, while the theory of multiple intelligences suggests that students have different types of intelligence that should be recognized and nurtured.
Purpose of Theory
The purpose of a theory is to provide a framework or explanation for observed phenomena in a particular field of study. Theories are developed through a process of observation, experimentation, and analysis, and they are used to explain how and why things happen the way they do.
In science, theories are used to describe and predict natural phenomena, while in social sciences, theories are used to explain human behavior and social interactions. Theories can be tested through further observation and experimentation, and they can be modified or discarded if new evidence contradicts them.
Characteristics of Theory
- Explanation : Theories provide an explanation of a phenomenon or event. They identify the causes and underlying mechanisms that contribute to the observed outcomes.
- Predictive power: Theories have the ability to predict future outcomes or behaviors based on the identified causes and mechanisms.
- Testable: Theories are testable through empirical research. They can be subjected to observation, experimentation, and analysis to determine their validity and accuracy.
- Falsifiability : Theories can be falsified if they are found to be inconsistent with empirical evidence. This means that they can be proven to be false if the evidence does not support them.
- Generalizability : Theories are generalizable to other contexts and situations beyond the original research setting. They are not specific to a particular time or place.
- Organizing framework : Theories provide an organizing framework for understanding and interpreting information. They help researchers organize their observations and make sense of complex phenomena.
- Parsimony: Theories are typically simple and concise. They strive to explain phenomena using the fewest number of assumptions or variables possible.
Advantages of Theory
- Framework for research: Theories provide a framework for research by guiding the development of hypotheses and research questions.
- Organizing information: Theories help researchers organize their observations and make sense of complex phenomena. They provide a structure for understanding and interpreting information.
- Prediction: Theories can predict future outcomes or behaviors based on the identified causes and mechanisms.
- Understanding causality: Theories help researchers understand the causal relationships between variables and events.
- Integration of knowledge: Theories integrate existing knowledge and provide a foundation for new discoveries.
- Application : Theories can be applied to real-world problems to develop interventions and policies that address social issues.
- Communication: Theories provide a common language and understanding for researchers, which facilitates communication and collaboration.
Disadvantages of Theory
- Limited scope: Theories are limited by the scope of their research and the context in which they were developed. They may not be applicable to other contexts or situations beyond the original research setting.
- Simplification : Theories often simplify complex phenomena and may oversimplify or exclude important aspects of the phenomenon being studied.
- Bias : Theories can be influenced by researcher bias, which can affect the development and interpretation of the theory.
- Difficulty in testing: Some theories may be difficult to test empirically, making it challenging to determine their validity and accuracy.
- Incomplete understanding : Theories may provide an incomplete understanding of a phenomenon, as they are based on limited research and knowledge.
- Resistance to change : Theories can be resistant to change, making it challenging to update or revise them in light of new evidence.
- Inconsistency: Different theories within the same field may conflict with each other or present different explanations for the same phenomenon, leading to inconsistencies and confusion.
About the author
Muhammad Hassan
Researcher, Academic Writer, Web developer
You may also like

What is Art – Definition, Types, Examples

What is Anthropology – Definition and Overview

What is Literature – Definition, Types, Examples

Economist – Definition, Types, Work Area

Anthropologist – Definition, Types, Work Area

What is History – Definitions, Periods, Methods
- ArXiv Papers
Bounds on the Distribution of a Sum of Two Random Variables: Revisiting a problem of Kolmogorov with application to Individual Treatment Effects
Published 5/14/2024
We revisit the following problem, proposed by Kolmogorov: given prescribed marginal distributions $F$ and $G$ for random variables $X,Y$ respectively, characterize the set of compatible distribution functions for the sum $Z=X+Y$. Bounds on the distribution function for $Z$ were given by Markarov (1982), and Frank et al. (1987), the latter using copula theory. However, though they obtain the same bounds, they make different assertions concerning their sharpness. In addition, their solutions leave some open problems in the case when the given marginal distribution functions are discontinuous. These issues have led to some confusion and erroneous statements in subsequent literature, which we correct. Kolmogorov's problem is closely related to inferring possible distributions for individual treatment effects $Y_1 - Y_0$ given the marginal distributions of $Y_1$ and $Y_0$; the latter being identified from a randomized experiment. We use our new insights to sharpen and correct results due to Fan and Park (2010) concerning individual treatment effects, and to fill some other logical gaps.
Prediction of the creeping of AFC based on fuzzy reasoning and Bi-LSTM fusion iteration
- Open access
- Published: 16 May 2024
- Volume 57 , article number 142 , ( 2024 )
Cite this article
You have full access to this open access article

- Suhua Li ORCID: orcid.org/0000-0002-8282-1165 1 , 2 ,
- Jiacheng Xie ORCID: orcid.org/0000-0002-7136-1140 1 , 2 ,
- Xuewen Wang ORCID: orcid.org/0000-0001-6028-9430 1 , 2 &
- Fuxiang Ge 1 , 2
Abstract
The creeping of Armoured Face Conveyor (AFC) is an engineering problem that needs to be avoided in coal mining production process. In this paper, a method for predicting the creeping accident of AFC based on fuzzy reasoning and Bi-directional Long Short-Term Memory (Bi-LSTM) fusion iteration is put forward. Firstly, through the force analysis of the AFC and the fuzzy correlation analysis method in the actual operation process, the reasons for the creeping of AFC are analyzed; Secondly, according to the propulsion characteristics of the AFC in the time sequence development, the method of the AFC running track based on Bi-LSTM neural network is proposed; Then, on the basis of the virtual transformation of the prediction results, a judgment mechanism for the extent of the creeping of the AFC based on fuzzy evidence reasoning based on fuzzy comprehensive evaluation method and Dempster-Shafer evidence theory (D-S evidence theory) is established; Finally, the analysis on the creeping of 9711 full-mechanized mining face in Kaiyuan Mine under virtual environment after 6 cycles of continuous advancement shows that the extent of creeping of AFC is relatively high and coal mining accidents are likely to occur.
Avoid common mistakes on your manuscript.
With the rapid development of production and manufacturing towards intelligence (Kang et al. 2016 ), the fast-paced and less humanized production mode brings high efficiency, low cost and high benefit. At the same time, with the potential impact of uncertain factors such as production environment, climate and personnel operation, some accidents will bring irreversible engineering accidents (Qiang 2020 ), which will bring huge losses to human, material and financial resources. The development of digital twin technology, artificial intelligence technology and human–computer interaction technology provides technical support for the analysis of engineering problems such as analyzing the causes of engineering accidents, predicting the development trend of production process and judging the development degree of engineering accidents (Le and Ahn 2011 ). If based on the above technology, a pertinent analysis platform for engineering accidents can be established, a prediction mechanism facing the development trend of production process or accident and an accident decision-making and analysis mechanism can be established, potential problems in current production process or the development degree of engineering accidents can be found, and corresponding countermeasures can be provided,, which can achieve the purpose of providing timely and effective solutions to engineering problems and reduce the impact of accidents.
The coal mining industry usually belongs to the typical deep space operation production, the production environment is bad, the geological environment is complex, and there are many uncertain factors interfering with the production process. With the advancement of intelligent coal mining (Huang et al. 2020 ), the requirements for unmanned mining have become higher, and a safer and more efficient mining mode is being pursued (Wang and Huang 2017 ). However, in the mining process, under the combined action of coal seam fluctuation and equipment interaction, it is easy to cause some accidents that are difficult to avoid. The creeping of Armoured Face Conveyor (AFC) is one of the common and typical engineering problems in the process of coal mining. The small movement of the line pan of the AFC will affect the straightness of the whole fully mechanized mining face. When the movement is serious, it will even cause the equipment to accumulate (Peng et al. 2019 ), resulting in major mining accidents. This paper selects the engineering problem of the creeping of AFC as an example to build the general prediction framework of accident, and provides research framework and key technical support for other engineering problems.
Relevant technical teams and scholars (CSIRO 2021 ; Zhang et al. 2018 ; Michael and Hainsworth 2005 ; Song and Wang 2014 ; Niu 2015 ) have studied the mechanism and control of the up-slip of AFC, but there are still the following deficiencies in the research of creeping on fully-mechanized mining face. Firstly, when analyzing the cause mechanism and establishing the mechanical model, the analysis idea is mostly the single factor analysis method, which ignores the correlation between the factors, i.e., the influence of the chain effect brought by the joint action of the factors on the equipment position state. Therefore, in the process of research, it is more one-sided to analyze only the single factor for the creeping of the AFC. Secondly, the analysis of the mechanism of the creeping of AFC is carried out under ideal coal seam conditions, resulting in a certain gap between the research environment and the actual environment in the whole analysis process. When analyzing the mechanism of equipment creep in the whole mining environment, it only judges whether the equipment moves based on the visual perception of miners, and there is no specific measurement standard for the degree of creeping. Thirdly, it is found that after the adjustment of the conveyor, the creeping of the equipment has been reduced, i.e., the technical control of the scraper has been improved, which has a certain impact on the decline of the mining technology.
With the development of digital twin technology, the establishment of digital twin of physical environment and the simulation and pre-experiment in virtual environment can provide conclusions and scheme support for the research in physical environment (Xie et al. 2022 ; Guo et al. 2019 ). As a virtual simulation engine that supports multi-dimensional and interactive graphical development environment, Unity3D can realize the visualization of complex working environment and establish the digital twin of physical environment (Cai et al. 2023 ). The existing research (Ge et al. 2020 ; Shen et al. 2021 ) shows that the virtual simulation and research of coal mine underground related work in Unity3D has great advantages, and can provide visual ideas and research schemes for solving the problems such as the creeping of fully mechanized mining face. Therefore, in view of the problems and deficiencies existing in the current research, a visual analysis platform for the creeping of the AFC can be created in Unity3D. During the simulation process, the reconstruction and extrapolation of the motion trajectory of the digital twin model is one of the keys to support the subsequent research, which requires further prediction of the periodic properties of the trajectory extracted in space and time to support the relevant analysis of future working conditions. The application of commonly used neural networks in performing trajectory prediction is shown in Table 1 .
From Table 1 , it can be seen that compared to other networks, the Bi-LSTM neural network can better predict the next state by simultaneously predicting the forward and backward directions during time series prediction. Bi-LSTM neural network has a good application in the prediction and diagnosis of power supply and demand prediction (Özer et al. 2021 ), load prediction (Yeming et al. 2022 ) fault diagnosis (Tong et al. 2021 ) and other events related to timing processing (Özer et al. 2021 ). The characteristic of such events is that it is necessary to predict and judge the future data according to the historical data and the characteristics of the data is periodic. In the mining process, when there are no folds, faults and other complex geological structures of the coal seam, the overall fluctuation of the coal seam floor is small, so that the floor changes gently in the continuous space–time advance, (Guo et al. 2019 ), which makes there are small differences between the laying trajectories of the AFC. The fixity of the coal mining process, coupled with the influence of the coal cutting mode of memory cutting, makes the AFC trajectories also have periodic changes in the process of advancing with the reciprocating cutting operation of the shearer (CSIRO 2021 ). Therefore, Bi-LSTM neural network algorithm can also be applied to the prediction process of the position coordinates of the AFC. When the predicted position trajectory of the AFC is obtained, there is a positioning benchmark for the position of relevant equipment in the virtual environment in the future, but whether the position state of the equipment is normal or not is still unknown. Therefore, it is necessary to establish a judgment mechanism for this uncertain event of abnormal position state of the equipment. According to the prediction information, the accidents or accident grades that may be caused in the future mining are evaluated, so as to provide ideas for the subsequent mining process adjustment. Dempster-Shafer evidence theory (D-S evidence theory) is a complete theory for dealing with uncertain events (Dempster 1967 , 1968 ). It shows great flexibility in distinguishing unknown events, uncertain events (Wang et al. 2022 ) and event evaluation (Jie et al. 2021 ). The treatment of fuzzy events based on D-S evidence theory is a relatively reliable decision-making method. Therefore, this paper adopts D-S evidence theory to make a decision on the degree of the creeping of AFC.
Based on the above contents, this paper carries out a visual comprehensive analysis on the creeping mechanism of AFC from the perspective of virtual-real mapping based on the digital twin theory. Bi-LSTM neural network model in virtual running environment was built to forecast position coordinate track of AFC in continuous propulsion. On the premise that the predicted results can be converted into information of virtually drive the AFC, a judgment mechanism of creeping degree of AFC based on fuzzy D-S evidence theory in virtual environment is established to judge the creeping degree of AFC, and finally to provide guidance for the change of mining technology scheme of the next knife. The above contents are integrated and a virtual simulation system for visual analysis of the creeping of AFC is established.
1 Overall framework
Aiming at the problem of the creeping of AFC during coal mining, from the point of view of accident occurrence mechanism and production and operation data, this paper integrates digital twin technology with predictive analysis technology, and establishes a research framework to solve such engineering problems based on multi-disciplinary analysis theory. The overall framework is shown in Fig. 1 .
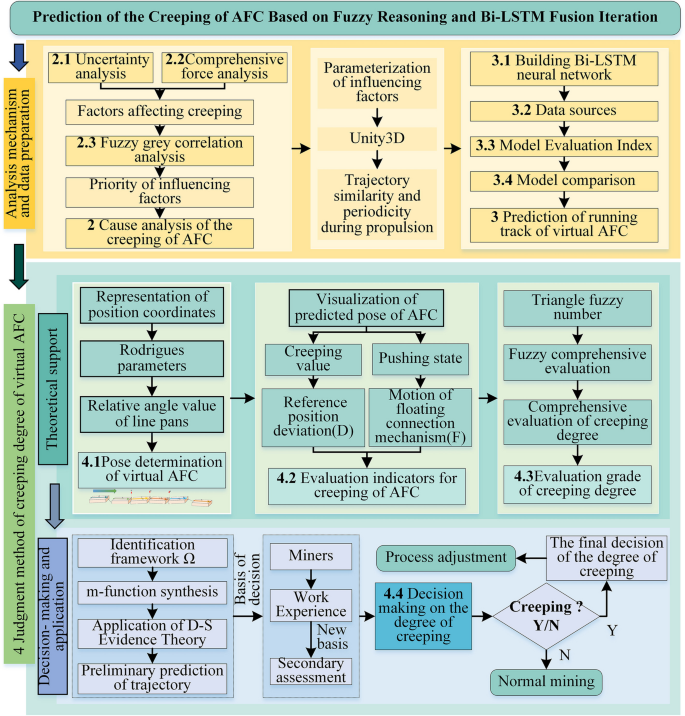
Method flow chart of the paper
Taking Unity3D as the main research and analysis platform, and based on the analysis of the causes and mechanism of the creeping of the AFC, this paper establishes the prediction model of propulsion trajectory and the judgment model of the creeping degree, and realizes the prediction of the occurrence and development degree of the engineering problem. The process is as follows:
Analysis on influencing factors of the creeping of AFC. According to the reasons for the creeping of the AFC in the actual propulsion process, the corresponding influencing factors are determined in the virtual environment based on the digital twin theory, and the influencing factors of the AFC are analyzed based on the fuzzy grey correlation analysis.
Trajectory prediction of AFC based on Bi-LSTM neural network. The configuration parameters of the virtual simulation environment are determined on the basis of content (1). According to the similarity and periodicity of the trajectory during propulsion, Bi-LSTM neural network is selected to predict the trajectory of AFC in this paper. According to the characteristics of coordinate points in the propulsion process of AFC in virtual environment, the prediction model of AFC running trajectory is established. In view of the characteristics of virtual equipment position coordinates, the data set is established. Compared with the traditional LSTM neural network, it further proves the reliability of this model.
The judgment mechanism of creeping degree of AFC based on fuzzy evidence reasoning theory. The prediction results are transformed, and the evaluation degree grade of the creeping of AFC is established based on fuzzy comprehensive evaluation method. Then, the evaluation method of creeping degree of AFC based on D-S evidence theory is proposed to determine the development degree of current accident and provide corresponding countermeasures.
2 Cause analysis of the creeping of AFC based on digital twin and fuzzy grey correlation analysis
When predicting the degree of creeping on the AFC, it is necessary to analyze the root cause of this engineering problem. The shearer, hydraulic support, and AFC are the core equipment of the fully mechanized mining face (Niu 2015 ). During the production process, the operating status of the shearer and hydraulic support will have a certain impact on the operation of the AFC.
2.1 Uncertainty performance in determining the degree of creeping of AFC
The uncertainty of 3D modeling of coal seam. In the process of judging the creeping of the AFC, the fineness of the 3D modeling of the coal seam environment is one of the key factors. In the process of constructing a coal seam 3D model, it is susceptible to various factors such as the complexity of coal seam structure, inaccuracy or inconsistency of modeling data, and subjectivity of modeling personnel, which inevitably leads to a certain degree of uncertainty in the established 3D model of coal seam. These uncertainties often cause a certain degree of deviation in the vertical resolution of the constructed coal seam 3D model, and limiting its further application level.
The uncertainty of the impact of auxiliary mining processes. During the advancement of the fully mechanized mining face, dust reduction will be carried out by sprinkling water as the mining progresses, which reduces the frictional force between the equipment and the coal seam floor during advancement. Coupled with the uncertainty of the coal seam, it may promote the occurrence of creeping phenomenon. In addition, during the comprehensive mining construction, there may be a phenomenon of bulging of the bottom plate, which causes the AFC to curl up and cause the creeping during propulsion.
The uncertainty of straightness of AFC. However, due to the spatial motion characteristics of the hydraulic support during movement, the displacement of the line pan generated during movement is minimal, and gradually accumulates with advancement, resulting in the randomness of the straightness of the AFC (Li et al. 2022 ). The circular motion of the line pan during movement will generate lateral thrust on adjacent equipment, driving the occurrence of creeping.
2.2 Comprehensive analysis of force on AFC
2.2.1 force analysis of the afc.
The force analysis of the AFC when it creeps mainly focuses on the sources of influence from the environment and equipment (Fig. 2 ).
Environmental impact of mining . When the inclination angle of the coal seam is too large, the AFC may creep under the influence of gravity such as the shearer, coal blocks (Holm 2014 ), and its own gravity (refers to G). Due to the frequent watering and dust spraying on the working face, the friction coefficient is further reduced, changing the magnitude of the friction force F f , causing the AFC to creep.
The cutting force of the shearer is affected. The shearer uses a scraper conveyor as a platform and anchor point (Hu 2016 ), which will apply opposite forces ( F 4 , F 6 ) on the AFC; In addition, the resistance ( F 1 , F 2 ) generated by the shearer when cutting the coal wall, as well as the running resistance ( F 3 , F 5 ) generated between the sliding shoe and the AFC, which may cause the scraper conveyor to creep.
The influence of the pushing posture of the AFC. During the propulsion process of the AFC, it will go through two stages: serpentine and straightening, and will be subject to resistance from the straight section during operation and resistance from the curved section during operation. These two resistances constitute the main part of the operating resistance ( F ) of the AFC, which will to some extent affect the creep;
The influence of hydraulic support pushing force. When the hydraulic support group and the AFC are in a misaligned state, the force will be distributed along the coal seam inclination (refers to F T ), which will also have an impact on the creeping of the AFC.
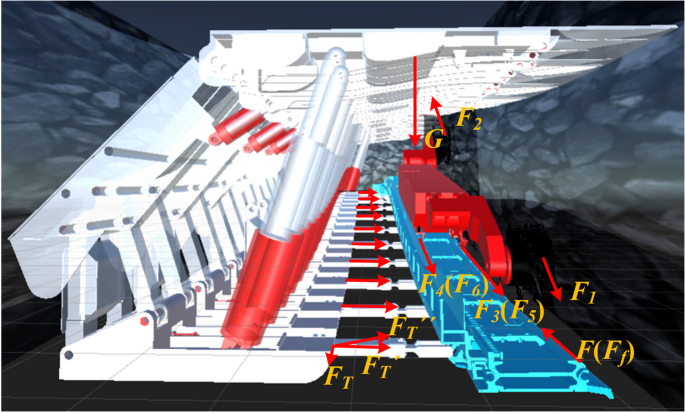
Force analysis of the AFC
2.2.2 Comprehensive analysis of force
According to the above analysis, the creeping force of the AFC can be analyzed from the force promoting or hindering the creeping of the AFC.
In any case, the gravity of the equipment and coal blocks has the force \({{\text{F}}}^{\mathrm{^{\prime}}}\) to promote the downslide of the AFC. The resistance \(F\) of the AFC during propulsion and the friction \({F}_{f}\) of the AFC during propulsion will prevent the downslide of the AFC.
The force generated by the shearer traction on the AFC is opposite to the traction direction. When the shearer is upward cutting, the force F 3 ’ , F 4 ’ , F 5 ’ , F 6 ’ of the shearer on the AFC will promote the AFC to downslide, and vice versa.
The force of the hydraulic support on the AFC is related to the swing direction of the push rod. When pushing the AFC, when the push rod is inclined downward as a whole, it will promote the AFC to downslide.
In conclusion, the comprehensive effects of various forces on the creeping of AFC are shown in Table 2 .
When the shearer goes up to cut coal, the resultant force to promote the AFC to downslide is \({F}_{d}\) , the total force preventing the AFC from downslide is \({F}_{sd}\) .
2.3 Factor analysis of creeping mechanism in virtual environment based on fuzzy grey correlation analysis
Corresponding to Sect. 2.2 , the factors influencing the creeping of AFC in virtual environment mainly include inclination along the direction of coal seam, friction coefficient between the equipment and the floor, and attributes of related forces, the coupling effect between these factors has significant uncertainty, fuzziness, and grayness. In actual production, different degrees of creeping of the AFC correspond to different response measures. However, the degree of creeping is a vague concept, and the analysis of this degree in the mining process is often judged based on the production experience of coal miners. Once a misjudgment occurs, it may lead to irreversible consequences. Therefore, this paper aims at the fuzzy variable of the degree of creeping of the AFC, combines the fuzzy theory with the grey correlation analysis method, and objectively carries out the correlation analysis on the influencing factors of creeping of the AFC. In this paper, the AFC is regarded as a rigid structure (Xu 1999 ; Verma 2013 ; Wang et al. 2020 ), the force of the hydraulic support push rod on the AFC can be regarded as the effect of external force, and the connection between the hydraulic support push rod and the AFC is realized by kinematics method.
On the basis of realizing the virtual connection between the hydraulic support and the AFC (Li et al. 2021 ), the reference position variation of the creeping of the AFC is selected as the reference sequence \(Y\left\{k\right\}\) , which is used as the data sequence to study the characteristics of behavior of the AFC. The data variation law of each group of plans can be regarded as the actual change of creeping, and the relation is shown in Eq. ( 1 ).
The comparison sequence is friction coefficient \({X}_{1}\left\{k\right\}\) , coal seam inclination \({X}_{2}\left\{k\right\}\) , the force of shearer \({X}_{3}\left\{k\right\}\) , Angular Drag value \({X}_{4}\left\{k\right\}\) , Drag value \({X}_{5}\left\{k\right\}\) , which reflects the data sequence of influencing factors on the change of reference position of the creeping of the AFC. It is assumed that there are n experimental plans and the corresponding comparative sequence matrix is shown in Eq. ( 2 ).
Due to the different dimensions of data in each factor, it is impossible to directly compare and analyze the values. Therefore, in order to ensure the reliability of the analysis results, dimensionless processing of variables is required, as shown in Eq. ( 3 ).
To describe the degree of belonging to different evaluation levels, the included cosine method is used to calculate the fuzzy membership, which is not affected by the linear proportional relationship of data. The similarity between reference and comparison series can be determined by the included cosine value between parameters, as shown in Eq. ( 4 ).
Through the design of different experimental schemes, the environment setting of each influencing factor in the simulation system is carried out to promote the virtual AFC, and the position change parameter value \(Y\left\{k\right\}\) of the AFC under different experimental schemes is obtained. Calculating grey correlation coefficient between the comparison sequence and the reference sequence \({\xi }_{i}(k)\) . This coefficient shown in Eq. ( 5 ) reflects the degree of correlation between the reference sequence and the comparison sequence.
where, ρ is the resolution coefficient, \(\rho \in \left[0,1\right]\) . According to the value principle of \(\rho\) (Deng 1988 ), when \(\rho \le 0.5\) , it is easier to observe the changes in resolution of \({\xi }_{i}(k)\) on \({X}_{i}\left\{k\right\}\) and \(Y\left\{k\right\}\) ; However, in order to monitor the amount of creeping, the selected reference sequence \(Y\left\{k\right\}\) has a relatively stable value, and \(\rho\) should be taken as the larger value, so ρ = 0.5 is extracted in this paper.
As the values of multiple correlation coefficients are scattered, it is difficult to make overall comparison. The correlation degree \({\xi }_{i}(k)\) between each comparison sequence and reference sequence is averaged in different dimensions. The obtained \({{r}_{i}}{\prime}\) values are regarded as grey correlation degree, as shown in Eq. ( 6 ).
When comprehensively comparing the influencing factors of the creeping of the AFC, the two evaluation indexes of \({\xi }_{i}(k)\) and \({{r}_{i}}{\prime}\) are oriented to different mining stages, The former focuses on the impact on the creeping of the AFC when various influencing factors change due to process switching during single-cutting propulsion; The latter focuses on the influence of various factors in the overall propulsion, starting from the perspective of the correlation between the cutting floors, and after comprehensively considering the impact of process switching and equipment movement on the degree of creeping. Therefore, both indicators are equally important for evaluating the degree of creeping during propulsion and independent, this paper adopts linear weighted synthesis method to merge, and obtain the comprehensive index value of influencing factors on the AFC propulsion, i.e. the fuzzy grey correlation degree is obtained. The expression is shown in Eq. ( 7 ).
According to the above contents, the priority of each influencing factor in virtual environment to the impact degree of the creeping of AFC can be obtained. The propulsion environment of AFC can be configured according to the optimal scheme, and the obtained track information can be used as the data source for prediction analysis, so as to predicate the current running state of AFC.
3 Prediction of running track of virtual AFC based on Bi-LSTM neural network
Due to the workflow of the coal mining process and the memory of the cutting process of the shearer, the track obtained by the AFC during the driving process has certain similarity in the adjacent two knives, and shows certain periodicity with the fluctuation and cutting of the coal seam. Under the premise of realizing the visualization of virtual simulation environment and the optimization of environmental factors, the trajectory of the current AFC can be predicted according to the change law of the trajectory of the two adjacent AFC in the historical information in the time series.
3.1 Bi-LSTM neural network
LSTM is composed of input gate, forget gate, and output gate (Hochreiter and Schmidhuber 1997 ), which control the state of the cell and the state of the hidden layer, and delete or add information to it. The calculation model is shown in Eqs. ( 8 ) - ( 13 ).
where, \({f}_{t}\) , \({i}_{t}\) , \({o}_{t}\) stands for Forgetting gate, Input gate and Output gate respectively; \({c}_{t-1}\) represents the memory state of the cell at the previous time, \({c}_{t}\) , \({\widehat{c}}_{t}\) represents the memory state of cell unit; \({h}_{t-1}\) represents the output state of the cell unit at the previous time, \({h}_{t}\) represents the output state of the cell unit at the current time; \({x}_{t}\) represents the input state of the current cell unit; \({W}_{f}\) , \({W}_{i}\) , \({W}_{o}\) , \({b}_{f}\) , \({b}_{i}\) , \({b}_{o}\) is an adjustable parameter matrix or vector.
However, the information in LSTM is one-way transmission, which only learns the influence of historical state on current state, without fully utilizing the dependency relationship between time series (Quan et al. 2021 ). Considering that the position of the AFC is more susceptible to the influence of the floor undulation and the equipment forces, as well as the long cutting cycle time sequence of the fully-mechanized mining face, Bi-LSTM is selected to establish the prediction model. As shown in Fig. 3 , the independent Bi-LSTM neural network is used to extract the timing feature information from the historical running track of AFC, and the obtained feature information is spliced by feature fusion technology. The splicing information is input to the second layer Bi-LSTM network. The final output is the splicing of the results with two directions forecast.
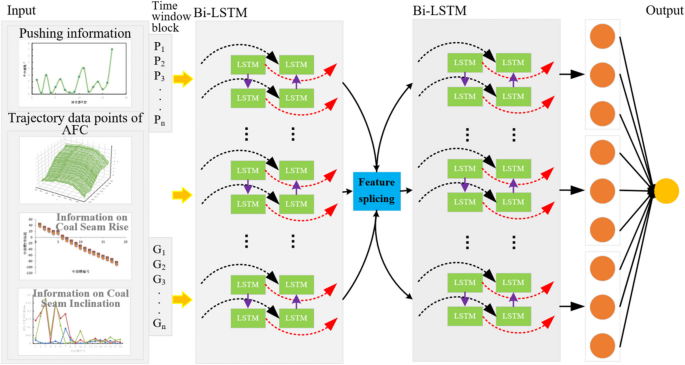
Track prediction model of AFC based on Bi-LSTM neural network
Bi-LSTM processes the timing data independently through the forward layer and the backward layer. The forward layer can obtain the past data information of the input sequence, and the backward layer can obtain the future data information of the input sequence, and transmit the processing results to the output layer at the same time, which can make full use of the characteristics contained in the past and future data. At time t , the forward and backward output results of Bi-LSTM are shown in Eqs. ( 14 )-( 16 ).
where, \({\rm H}_{t}\) is the output value of the hidden layer, \(\overrightarrow{{h}_{t}}\) is the output value of the forward layer and \(\overleftarrow{{h}_{t}}\) is the output value of the backward layer.
The trajectory point characteristics of the AFC with t - th blade are represented as \({x}_{t}=(t,{x}_{l}^{i},{y}_{l}^{i},{z}_{l}^{i},{d}^{i},{\varphi }^{i}),({x}_{l}^{i},{y}_{l}^{i},{z}_{l}^{i})\) contains information on the undulations and dip angles of coal seam; The trajectory point of the AFC with t + 1 blade is \({y}_{t+1}=\left(t,{x}_{l}^{i},{y}_{l}^{i},{z}_{l}^{i}\right)\) ; The mapping function between the output value and the input value is defined as \({y}_{t+1}=f({x}_{t},{x}_{t-1},\dots {x}_{t-T+2},{x}_{t-T+1})\) .
This model learns the correlation and temporal dependencies between data by stacking multiple Bi-LSTM networks, and predicts the trajectory of the AFC through a fully connected layer and a regression layer. The input information in the model is \(X=({x}_{t-1},{x}_{t-2},{x}_{t-3},\cdots {x}_{t-n})\) and the output layer information are the predicted coordinates of the Bi-LSTM model in the line pans of the AFC at the t-th blade. According to the relationship between the cutting depth of the shearer and the structure of the line pan during the advancement of the fully mechanized mining face (the cutting depth of shearer is approximately equal to the width of three line pans), the time step is set to 3.
Based on the prediction task in this article, the number of layers for Bi-LSTM is set to 2, where the number of neurons in the first hidden layer is set to 250, the number of neurons in the second hidden layer is set to 30, the number of training sample sets is 1200, the learning rate is set in the range of [0.005,0.05], the maximum number of iterations is 1000, the gradient threshold is set as 1 to prevent gradient explosion, Dropout is used to reduce over-fitting, RMSE and MAPE are used as the loss function.
In order to achieve long-term prediction, this article adopts a rolling prediction method. After selecting a fixed time window of 3-blade data and training a time series model each time, the trajectory of the future 3-blade scraper conveyor is predicted. After prediction, the data from the same time window in the test set is added to the training set to continue training the model.
3.2 Data sources
In virtual simulation system, virtual positioning of shearer is carried out by means of virtual Strapdown Inertial Navigation System (SINS) and virtual odometer, and AFC trajectory is obtained by trajectory inversion. In this system, the sum of positioning error and inversion error of shearer is simulated by defining an arbitrary number, and the range is set ( error_min , error_max ). Given the absolute coordinate system of the virtual fully-mechanized mining face, the following functions are used to simulate the output of detection results when the position of line pan is detected by SINS.
The hydraulic support number in the virtual scene is yyzz_num(num ∈ (1, n )); The number of the line pan of the AFC is zbc_num(num ∈ (1, m )). Where, n is the number of hydraulic supports and m is the number of line pans. Through the above program, the position coordinates of each line pan are output in the format of xml in Unity3D, the displacement and yaw angle values of the pushing mechanism of the hydraulic support are output in the same way, and imported into Matlab in the form of cell array as the data set of Bi-LSTM neural network prediction.
If the hydraulic support and the AFC advance continuously on the virtual floor, determine the advance times of the AFC according to the visualization of the creeping movement of the AFC in the scene. The track coordinates of the AFC after the completion of the last process in each propulsion process are used as the predicted data set. Due to the similarity between the cutting depth of the shearer and the pushing distance of the AFC, the overall running track of the adjacent two-blade of AFC is less affected by the overall fluctuation of the coal seam and has certain correlation, which will lead to the lag between the predicted value and the true value. In this paper, differential calculation is used to eliminate the autocorrelation.
3.3 Model Evaluation Index
Root Mean Square Error (RMSE) and Mean Absolute Percentage Error (MAPE) are used as the evaluation index of simulation deviation to reflect the degree of difference between measured and simulated values.
where, n is the sample size, \({p}_{i}\) and \({q}_{i}\) are the predicted values and the predicted values of the track coordinates of the AFC respectively ( i =1... n ).
3.4 Model comparison
If the number of line pan and hydraulic support are both 40, the hydraulic support continuously pushes the AFC through 8 cycles with a total of 16 × 40 data. The 15th data set is used to forecast the 16th data set and the number of iterations is 250. Since the x-coordinate of AFC varies greatly with the fluctuation of coal seam, the two-difference method is used to process the most data set. In this paper, Bi-LSTM neural network and LSTM neural network are selected for comparative analysis. The difference between the predicted results and the actual values is shown in Fig. 4 .
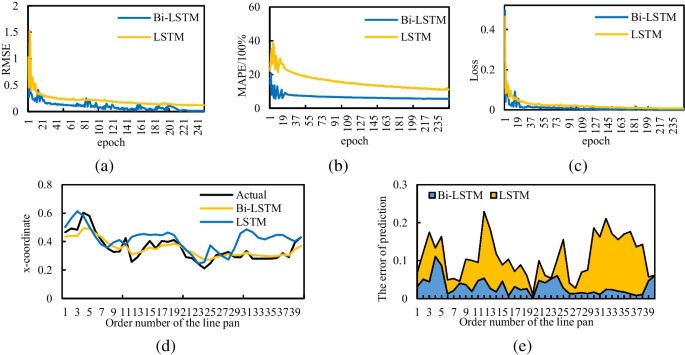
Prediction results
From the changes in the values of the indicators during training in Fig. 4 (a)-(b) that the Bi-LSTM neural network has a better prediction and convergence level than the LSTM neural network in predicting the trajectory of the AFC. It can be seen from Fig. 4 (d) that the prediction results of Bi-LSTM neural network fluctuate around the actual value curve and are relatively close to the fluctuation of the actual value curve; The LSTM neural network also fluctuates around the actual value curve, but the fluctuation is large; It can be seen from Fig. 4 (e) that the area of the error value obtained by using LSTM neural network for prediction will be greater than that by using Bi-LSTM neural network, which shows that the error of LSTM neural network for prediction is large. In conclusion, the prediction accuracy of Bi-LSTM neural network is higher, so the prediction of Bi-LSTM neural network is reliable.
4 Judgment mechanism of the creeping degree of AFC based on fuzzy evidence reasoning theory
4.1 pose determination of virtual afc based on rodrigues parameters.
On the basis of obtaining the position coordinates of the AFC, it needs to be converted into the information that can virtually drive the AFC in Unity3D. The driving factor selected in this article is the relative deflection angle between adjacent line pans. Therefore, it is necessary to establish a conversion mechanism between the position coordinates and the deflection angle.
The Rodrigues parameter is a formula for calculating a new vector obtained by rotating a vector around the axis of rotation by a given angle in three-dimensional space. Therefore, when the two vectors before and after the rotation are known, the angle of rotation can be calculated. The calculation equation of Rodrigues parameter is shown in Eq. ( 19 ):
where \(\mathbf{\varnothing }\) is the Rodrigues parameter, \(\alpha\) is the rotation angle of \({P}_{i}\) around the rotation axis n, and \({\varvec{n}}\) is the rotation axis. It can be seen from the formula that this method is prone to the problem of singular values (the rotation angle is ± 180°). However, due to the limitations of mining conditions and the structure characteristic of the AFC, the deflection angle of the line pan is generally not more than 4°, so this paper selects the Rodrigues parameter to solve the relative deflection angle between the line pans.
The position coordinate of the line pan \({A}_{i}\) is represented by a vector \({P}_{i}({x}_{i},{y}_{i},{z}_{i})\) , and the relative deflection angle between the two adjacent line pans is determined by calculating the angle between the two adjacent vectors. On the premise of obtaining the vector representing the position of each line pan of the AFC, the vertical axis of the Character Joint component is used as the rotating axis \({\varvec{n}}\) . The relative deflection angle between two adjacent line pans is determined by the relative rotation between the two vectors \({P}_{i}\) and \({P}_{i+1}\) and can be expressed by Eq. ( 20 ).
where ∅ is the module of the Rodrigues parameter and R is the rotation matrix expressed by the Rodrigues parameter from \({P}_{i}\) to \({P}_{i+1}\) . The expression of the rotation matrix is shown in Eq. ( 21 ).
Set the difference of Euler angle between the line pan \({A}_{i+1}\) and \({A}_{i}\) to be the yaw angle \(\Delta \varphi\) , pitch angle \(\Delta \theta\) , roll angle \(\Delta \gamma\) , then the relation between euler angle and Rodrigues parameter is shown in Eq. ( 22 ):
The difference of euler angle between line pan \({A}_{i+1}\) and \({A}_{i}\) is obtained as Eq. ( 23 ).
4.2 Evaluating the creep degree based on Fuzzy Comprehensive Evaluation method
4.2.1 triangular fuzzy numbers.
In order to better describe the fuzzy variable of the degree of the creeping of the AFC, this paper uses triangular fuzzy numbers to describe the degree of equipment creeping. Triangular fuzzy numbers have the characteristics of simple construction and easy operation in the process of expressing fuzzy semantics (Bowen et al. 1992 ). Its writing form is ( x , y , z ), where x , y and z represent the left end point, midpoint and right end point of fuzzy number respectively. The operation rules are as follows:
where \(A=\left({x}_{1},{y}_{1},{{\text{z}}}_{1}\right),\) \(B=({x}_{2},{y}_{2},{{\text{z}}}_{2})\) . Take A as an example to describe the membership function:
In order to realize the quantitative comparison between different degrees, it is necessary to defuzzify the evaluation results when determining the degree of creeping of AFC. In this paper, barycenter method is used for defuzzification, as shown in Eq. ( 26 ).
4.2.2 Fuzzy Comprehensive Evaluation
In response to the problem of subjective influence on numerical evaluation when judging the degree of creeping of AFC, the fuzzy comprehensive evaluation method is adopted to make up for it in this paper. The process is as follows: Firstly, based on the evaluation method of fuzzy mathematics, the quantitative evaluation of the degree of creeping is fuzzified to form a fuzzy terminology set; Secondly, conduct fuzzy evaluation and obtain fuzzy conclusions through fuzzy reasoning; Finally, defuzzification is performed to obtain the risk priority number RPN.
The Risk Priority Number (RPN) is used to evaluate the degree of the accident. The higher its value is, the more serious the consequence of the accident is. The calculation equation of RPN is:
where, ESR (Effect Severity Ranking) is the severity level of the accident, OPR (Occurrence Probability Ranking) is the probability of the accident and DDR (Detection Difficulty Ranking) is the difficulty of the accident detection.
According to the research on the creeping of AFC in the existing engineering cases(V Xu 1999 ; Verma 2013 ; Wang et al. 2020 ), the creeping degree of AFC in the virtual environment is quantified as the ratings VL, L, M, H and VH, which indicate Very Low, Low, Medium, High and Very High. The final established fuzzy rating and corresponding fuzzy numbers are shown in Table 3 , where \({P}_{A}\) is the probability of corresponding degree of the creeping of AFC.
4.2.3 Schematic diagram of the degree of creeping of the AFC
Figure 5 shows the corresponding creep degree diagram of AFC in Table 3 , in which Fig. 5 (a) shows the scene when AFC is operating normally. Figure 5 (b) shows that the degree of creeping on AFC is VL, and the creeping on AFC can hardly be judged by naked eyes, requiring special high-precision positioning device to determine; Fig. 5 (c) shows that the degree of creeping on AFC is L. At this time, the creep of AFC is small and the position change is difficult to judge compared with reference datum, so traditional sensor positioning device is needed to detect it. Figure 5 (d) shows that the creeping degree of the AFC is M. at this time, the position of the AFC changes greatly, and the equipment is separated from the roadway, which can be clearly judged by the naked eye; Fig. 5 (e) shows that the creeping degree of the AFC is H, at this time, the head position of the AFC has been completely separated from the roadway, and the tail tends to accumulate in the roadway; Fig. 5 (f) shows that the creeping degree of the AFC is VH. At this time, it is very easy to observe with the naked eye, and the equipment has been stacked.
Degree of the creeping of AFC
4.3 Evaluation indicators for creeping of AFC based on equipment movement
4.3.1 the motion of floating connection mechanism (f).
Because the connection between the hydraulic support and the AFC is a floating connection mechanism, when the AFC is creeping, the mechanism will deflect along with the key points on the line pan, and the moving direction of the AFC is consistent with the deflection direction of the push rod of the floating connection mechanism. Whether the AFC creeps can be judged according to the specific motion parameter values of each structure of the floating connection mechanism. For example, when the direction of the relay bar is deflected downwards, it indicates that the AFC has downslide.
4.3.2 Reference position deviation of AFC (D)
As shown in Fig. 5 , it is a schematic diagram of the creep of the AFC during operation, in which the yellow line represents the edge line of the roadway, the white line represents the position of the head when the creep movement does not occur, and the red line represents the actual position of the head. When the AFC creeps, select a key part of the AFC as the reference standard to determine whether the AFC creeps according to the position change of the part. As the head and tail of the AFC, the position change of the head and tail is easier to obtain than that of other line pans, so one of them can be selected as the reference position for the creep of the AFC.
4.4 Judgment method of creeping degree of virtual AFC based on D-S evidence theory
4.4.1 evaluation of the degree of creeping based on d-s evidence theory.
According to the evaluation grade of the creeping degree of the AFC, the identification framework Ω of D-S evidence theory (Dempster 1967 , 1968 ; Shafer 1976 ) is established, as shown in the following Eq. ( 28 ):
where, H i ( 1 ≤ i ≤ 5 ) represents the evaluation level of the creeping degree of the AFC of the current blade, which is VL, L, M, H, VH.
Let the evidence set be \({F}_{i}\) (i = 1,2 ), where F 1 represents the displacement d of the AFC and F 2 represents the deflection \(\mathrm{\varphi }\) of the floating connection mechanism. Based on the evaluation indicators (F, D), the range of creeping rate ( \({d}_{0}^{i},{d}_{1}^{i}\) ) and the range of yaw angle ( \({\varphi }_{0}^{i},{\varphi }_{1}^{i}\) ) of the floating connection mechanism corresponding to each level were preliminarily deduced through simulation and rehearsal in a virtual environment. Establish the basic probability allocation function for each evaluation level based on the established identification framework, which is the mapping shown in Eq. ( 29 ), also known as the m function (Shafer 1976 ), where \(m:{2}^{\Omega }\to [\mathrm{0,1}]\) . Establish the m function for two pieces of evidence on the Ω.
The set \({\text{E}}={{\text{H}}}_{1}\cup {{\text{H}}}_{2}\cup {{\text{H}}}_{3}\cup {{\text{H}}}_{4}\cup {{\text{H}}}_{5}\) represents the inability to determine the current level of creeping. Let \({m}_{1}\) is the m function of \({F}_{1}\) on \(\Omega\) ,, where \({k}_{1}\) is the reliability parameter of \({F}_{1}\) , and \({c}_{1i}=\left(d/\left({d}_{0}^{i}+{d}_{1}^{i}\right)\right)/\sum_{i=1}^{5}\left(d/\left({d}_{0}^{i}+{d}_{1}^{i}\right)\right)\) ; \({m}_{2}\) is the m function of \({F}_{2}\) on \(\Omega\) , \({k}_{2}\) is the reliability parameter of \({F}_{2}\) , and \({c}_{2i}=\left(\varphi /\left({\varphi }_{0}^{i}+{\varphi }_{1}^{i}\right)\right)/\sum_{i=1}^{5}\left(\varphi /\left({\varphi }_{0}^{i}+{\varphi }_{1}^{i}\right)\right)\) .
The basic probability distribution function satisfies the following two conditions in Eq. ( 30 ), where \(m\left(a\right)\) represents the degree of support for event a :
This article uses an improved Yager formula (Yager 1987 ) for function synthesis. For specified events and other unknown propositions, function synthesis is performed according to Eq. ( 31 ):
where, \(k=\widetilde{k}=2/n\left(n-1\right)\sum_{i<j\le n}{k}_{ij}\) , \({k}_{ij}={\sum }_{{a}_{i}\cap {a}_{j}=\varnothing ,{a}_{i}\in {F}_{i},{a}_{j}\in {F}_{j}}{m}_{i}({a}_{i}){m}_{j}({a}_{j})\) is the conflict value between the evidence set \({F}_{1}\) and \({F}_{2}\) , \(p\left(a\right)=\sum_{{a}_{i}\in {F}_{i},\bigcap_{i=1}^{n}{a}_{i}=\Omega }{m}_{1}\left({a}_{1}\right)...{m}_{n}({a}_{n})\) , \(q(a)=1/n\sum_{i=1}^{n}{m}_{i}(\Omega )\) , \(\varepsilon ={e}^{-k}\) .
4.4.2 Virtual decision making of creeping degree of AFC
Based on the content of the above chapters, the prediction method in Sect. 3 is used to predict the position track of the AFC, and the evaluation grade, triangular fuzzy number and accident evaluation results are preliminarily determined according to the virtual conversion results of the predicted track. On the basis of the evaluation results obtained and virtual visualization of prediction results achieved, two coal miners are invited to conduct a secondary evaluation according to their work experience, evaluation indicators (F, D) based on the predicted trajectory of the AFC as the evidence set of reasoning. The final decision-making result of the creeping degree of the AFC is obtained is shown in Eq. ( 32 ).
where S is the result of synthesis using Yager formula, and the value range of membership function is between [0, 1]. The closer the result is to 1, the higher the support for the decision; \({S}_{i}\) ( i = 1,…,3) respectively represent the preliminary evaluation results obtained based on the prediction results, the expert's work experience, and the results obtained from the evaluation indicators (F, D); \({s}_{i}\) stands for results in \({S}_{i}\) . Based on the decision results, if there is an creeping trend, on the basis of determining the degree of the accident, timely process adjustments should be made to ensure safe production or minimize losses; If not, coal mining can continue according to the original process.
5 Experimental research
Under the analysis of the single factor influencing the creeping of the AFC in Sect. 2.2 , the single factor influencing the creeping of the AFC is analyzed first. By building a test platform for the creeping of the AFC in the laboratory environment, the impact of each factor on the creeping of the AFC is tested in the virtual environment and the laboratory environment respectively, which proves the reliability of the virtual simulation analysis system. Then the 9711 high mining height fully- mechanized working face of a group KaiYuan mine is selected for research. According to the historical operation information of the AFC, the degree of the creeping of the AFC in the process of propulsion is judged.
5.1 Reliability verification of virtual simulation system for analyzing the creeping of AFC
5.1.1 virtual simulation system for analyzing the creeping of afc.
As shown in Fig. 6 , the virtual monitoring control panel mainly includes Data input area, Action control area, Data storage area, Input preparation area and Scene monitoring area, and uses the predicted trajectory established in Sect. 4 to conduct virtual conversion of the predicted trajectory of the AFC in Unity3D. The data interface is reserved in the C# script, and the established factor allocation scheme is input into the parameter setting area of the system interface, so that the research environment can be configured, including the inclination of the support, the inclination of the AFC, the inclination of the coal seam, the friction factor, the Drag, the Angular Drag, and the acting force of the coal miner, including inclination of hydraulic support, inclination of AFC, inclination of floor, friction factor, Drag, Angular Drag, force of shearer. On the basis of virtual connection between hydraulic support and AFC, virtual infrared ranging sensor is installed at the head of AFC. The position of AFC can be monitored during pushing and the relative position of head and tunnel can be output in real time.
Interface of virtual simulation subsystem for influencing factor analysis of the creeping of AFC
5.1.2 Parameter configuration of virtual simulation system
During the process of sliding from static to dynamic of AFC, combined with the influence of water spraying and dust during running of shearer, there is a conversion of friction coefficient between equipment and floor. In order to accurately describe this friction process, Stribeck friction model is used to determine the friction coefficient between the line pans and the floor.
where \({f}_{D}\) is the dynamic friction factor, \({f}_{S}\) is the static friction factor, \({v}_{s}\) is the running speed of the AFC and \({v}_{St}\) is the critical Stribeck speed. In this paper, the simulation parameters of \({v}_{s}\) and \({v}_{st}\) are set as 1 m/s and 0.001 m/s respectively.
In order to establish the mapping relationship between coal machine equipment in virtual environment and coal machine equipment in physical environment (Guo et al. 2019 ), it is necessary to establish virtual mapping of physical parameters of equipment in Unity3D to get the digital twin of "Three Machines" in comprehensive mining face. Setting the environmental parameters according to Table 4 .
5.1.3 Construction of test platform
As shown in Fig. 7 , this experiment takes the fully-mechanized mining face prototype platform (Fig. 7 (a)) under the laboratory environment as the experimental research platform. The whole platform is composed of hydraulic support prototype model, adjustable floor model (Fig 7( c)), AFC model and fixed floor model (Fig. 7 (d)). Due to the limited number of prototype models of hydraulic support in the laboratory, this experiment cannot be completed, therefore, this experiment adopts a straight wooden stick with flattened and the same four sides. According to the principle of centering with the line pan, a rope is tied at the cable trough between the wooden stick and the prototype of the line pan. As shown in Fig. 7 (b), the prototype of the AFC is pushed by rotating the wooden stick. The fluctuation of adjustable floor model can be changed by adjusting the height of sliding trough and by laying different layers of friction coefficient on the base of prototype. The operating resistance between the two adjacent line pans of the AFC model can be changed by adjusting the tightness of the connections.
Test device
Install the infrared distance sensor module in the No. 1 line pan and simulate the tunnel with the side of the carton. By monitoring the relative distance between the line pan of the sensor and the simulated tunnel during the process of pushing the AFC by the hydraulic support, it can be judged whether the prototype of AFC has creeped.
5.1.4 Reliability analysis of virtual simulation system
Experimental scheme
Input the parameter values in the scheme as shown in the Table 5 at the monitoring panel in the virtual environment for test respectively. The initial scheme value of each affected parameter value is (15°, 0.35, 500N, 1.5, 15) to ensure that the equipment can operate normally without virtual test. When a single factor is tested according to the scheme in the table, other values in the initial scheme value remain unchanged.
Due to the limitation of laboratory conditions, only limited resources can be used for this test. The test scheme is shown in Table 6 .
The experimental design scheme is shown in Fig. 8 , in which Fig. 8 (a) is the undulation setting scheme along the coal seam strike, Fig. 8 (b) is the friction factor setting scheme between equipment and coal seam floor, Fig. 8 (c) is the dip angle setting scheme of coal seam, and Fig. 8 (d) is the angular resistance setting scheme.
Experimental result
Scheme setting
As can be seen from Fig. 9 (a), under the condition of the same average coal seam inclination angle, when there is no fluctuation, the position change is relatively large, indicating that the creeping phenomenon of the AFC is relatively serious; On the contrary, the position of the head hardly changes, which shows that the fluctuation of the coal seam floor along the coal seam strike will weaken the degree of the creep of the AFC. The relative distance at point 7 shows a non-linear relationship with the number of advances, as the mesh stitching is not smooth enough during virtual coal seam modeling, resulting in slight protrusions in the virtual coal seam.
Test results
As can be seen from Fig. 9 (b), through the comparison of the two curves, it is found that with the advancement of the AFC, the data fluctuation increases, it is due to the vibration of the sensor module and the fluctuation of coal seam, but the relative distance of S1 is gradually greater than S2, which is consistent with the conclusion in Fig. 9 (a).
As can be seen from Fig. 10 (a), with the increase of friction coefficient, the position of AFC becomes more stable. When the friction coefficient is within the range of (0.3,0.5), the final relative distance between AFC and roadway benchmark changes very little during the propulsion, and the operation state of AFC is relatively stable; As can be seen from Fig. 10 (b), the coarser the surface material of the coal seam, the smaller the relative distance between the infrared ranging sensor module and the simulated roadway, and the smaller the amount of the creep of the AFC, which shows that when the friction coefficient between the floor and the AFC is greater, the AFC is less likely to creep. In the coal mine, the friction coefficient of the floor to the coal machine equipment is 0.35–0.40, which is basically consistent with the above conclusions, which proves the effectiveness and feasibility of the simulation test in the virtual environment.
It can be seen from Fig. 11 (a) that the final relative distance between AFC and roadway datum increases by an average of 0.3 dm with the increase of coal seam dip, when the inclination angle of coal seam exceeds 15°. In Fig. 11 (b), as the number of nuts increases, the final relative position between the AFC and the simulated tunnel increases by an average of 2.5 cm. It can be seen that whether in the virtual environment or in the laboratory environment, with the increase of coal seam inclination, the amount of the creep of AFC gradually increases. This is consistent with the conclusion that the dip angle is more likely to cause the AFC to creep due to the influence of the coal seam basement in the actual mining process, proving that the analysis of relevant experiments by the virtual simulation system is feasible.
As can be seen from Fig. 12 (a), the relative creeping amount of the AFC is about 0.1 dm for every 1N reduction in Angular Drag; When the Angular Drag value is between (1.5, 2), the position of the AFC tends to be stable when moving. As can be seen from Fig. 12 (b), when the Angular Drag is small, the relative distance between the AFC and the simulated roadway is large. In summary, the greater the Angular Drag, the smaller the impact on the creeping of the AFC, and the straightness of AFC is easier to maintain and less prone to movement. This phenomenon corresponds to actual production conditions, proving the reliability of conducting simulation experiments in a virtual environment.
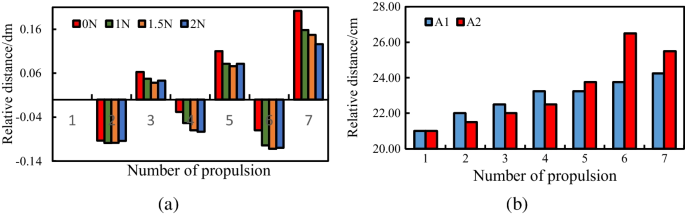
5.2 Determination of creeping of the AFC for virtual fully-mechanized mining face with large mining height
After overcoming the key technologies, based on the Digital Twin theory, a targeted virtual simulation analysis system can be established to analyze the influencing characteristics of each factor and the priority of influencing degree among the factors. And when the parameters of each influencing factor are known, the virtual environment is specially configured to predict the development degree of the engineering problem of the creeping of AFC in actual production process.
9711 fully-mechanized mining face with large mining height in Kaiyuan Mine of a group was selected for study. The depth of the fully-mechanized working face is 364 ~ 417 m, with an average of 390.5 m, the strike length of the working face is 462 m, and the inclined length is 220 m. There are 4 mining roadways in the working face, i.e. air inlet, air return, low and high, and the roof is managed by the full-height mining technology with large mining height and full-collapse method. MG750/1900-GWD shearer and ZY8000/26/56D hydraulic support are used in the working face with a center distance of 1.75 m. During the initial mining of 9711 working face, there is bottom coal left, and the upper bottom coal is thicker, the lower bottom coal is thinner, the height difference between upper and lower lanes is small, the height difference between return lane and inlet lane is 20.7 m, the average angle of working face is 5.4 degrees, and the maximum angle is 10°, as shown in Fig. 13 .
Profile of 9711 fully-mechanized mining face
Due to the long working face strike length, the amount of data is large when analyzing and studying the creeping of AFC. This paper chooses the data of the line pan of the two process sections nearest the tail of the return lane for analysis, i.e. the data of the 16 line pans connected with the tail. Determine whether the AFC has slipped up or down by judging the position of the tail.
5.2.1 Virtual monitoring subsystem for creeping of the AFC in 9711 working face
Fuzzy grey correlation analysis of the influencing factors of creeping of AFC
According to the content of Sect. 2.3 , the friction coefficient \({X}_{1}\left\{k\right\}\) , coal seam inclination \({X}_{2}\left\{k\right\}\) , shearer force \({X}_{3}\left\{k\right\}\) , Angular Drag value \({X}_{4}\left\{k\right\}\) , Drag value \({X}_{5}\left\{k\right\}\) were compared with the creeping limit value \(Y\left\{k\right\}\) of the creeping amount. The results between each comparison sequence and the reference sequence are shown in Table 7 .
From Table 7 , it can be seen that the priority factors affecting the creeping of AFC in the virtual environment are: Shearer force, Angular Drag value, Inclination angle of coal seam, Friction coefficient, and Drag value. In order to make decisions on the degree of creeping of AFC in a virtual environment, it is necessary to configure the propulsion environment of the AFC based on the priority of the influencing factors obtained.
Parameter settings for virtual monitoring subsystem
As shown in Fig. 14 , the interface of the virtual monitoring subsystem for the creeping of the AFC in the 9711 working face is shown. The virtual monitoring subsystem has the same function as the virtual simulation subsystem for the analysis of the factors affecting the creeping of the AFC. In the subsystem, there are 120 hydraulic supports, 120 line pans (including head and tail). In the virtual environment, the horizontal bending resistance and transverse bending resistance are 1.460 N and 2.480 N respectively. In Unity3D, the Angular Drag value is 3.940 N. Under the virtual environment, the drag value of the AFC is 19.334 N, the friction factor is 0.35, the single motor cutting power of the shearer is 750 KW, and the total power is 1900 KW.
Interface of virtual monitoring subsystem for the creeping of AFC in 9711 working face
5.2.2 Prediction of the propulsion trajectory of the virtual AFC
The mining height of 9711 fully mechanized working face is relatively high and the coal seam strength is low. According to the environmental parameters determined in Sect. 5.2.1 , without any interference with the advance state of the AFC, the AFC can be continuously advanced for 6 cycles, and the position of the head will be output in the form of an xml file in real time during the advance process. In the process of propulsion, the position of the head is output in the form of an xml file in real time. After the number of cutters is filtered by propulsion, the filtered data is processed again using the difference method, and the built Bi-LSTM network is used for prediction. The prediction results are shown in Fig. 15 .
Trajectory of AFC
It can be seen from Fig. 15 (a) that the prediction accuracy of the AFC trajectory by using this prediction algorithm is high, the maximum error is 0.2, the RMSE value is 0.085783, and the MAPE value is 0.242512. It can be seen from Fig. 15 (b) that the predicted three-dimensional trajectory of the AFC almost coincides with the converted observation trajectory, indicating that the reliability of Bi-LSTM in predicting the AFC trajectory is high.
5.2.3 Determination of the creep degree of the AFC
Convert the predicted track into the rotation angle of the line pans according to Sect. 4.1 , and control the rotation of each line pan through C# script. The obtained track curve is shown in Fig. 16 (b). According to the x-coordinate value of the AFC, the creep degree can be determined. In this paper, only the x-coordinate part is intercepted for research.
Virtual transformation results
The calculated deflection angle (T-Angle) and the deflection angle (V-Angle) of the virtual transformation of the predicted trajectory are shown in Fig. 16 (a). The difference between the theoretical calculation angle and the angle after virtual application is within 0.9°, and the accuracy is 87.1%; The x-coordinate value of the predicted trajectory after virtual application and the x-coordinate value of the predicted trajectory are differentially processed with the x-coordinate of the previous trajectory, and the obtained trajectory curves are recorded as (P–T) and (V-T) respectively. The difference between the predicted trajectory and the virtual trajectory is within 0.2 dm. This shows that the application accuracy of the virtual transformation model in Sect. 4.1 is high.
According to the predicted AFC trajectory, the comparison with the initial trajectory is obtained as shown in Fig. 17 (a) shows the comparison between the predicted trajectory (P–T) and the virtual converted trajectory (V-T) of the predicted result and the initial trajectory (I-T) of the AFC. Figure 17 (b) shows the comparison between the implied channeling momentum (D-C-P) in the virtual track and the implied channeling momentum (D-C-V) in the virtual transition track. It can be seen that the difference between the two tracks is within 0.2 dm, which indicates that it is feasible to determine the creeping degree of AFC using the virtual transition track. The channeling momentum can be described by using the fuzzy number (5, 7, 9) and the preliminary judgment grade is H.
According to the results of virtual conversion, the specific movement parameters of each degree of freedom of the floating connection mechanism are obtained as shown in Fig. 18 , where A1 and A2 respectively represent the yaw angle and pitch angle of the relay bar, A3 represents the yaw angle of the connection head, D1 represents the amount of displacement, Si (i = 1…16) represents the serial number of the hydraulic support, and its own experience determines the extent of creeping. From Fig. 18 , it can be seen that the deflection angles A1 and A2 of the relay bar are both positive, which indicates that the relay bar is swaying downwards along the inclination direction of the seam floor, and the value A3 is positive, indicating that the deflection direction of the connection head is the same as that of the relay bar. The piston rod extension indicates that the hydraulic support is on the push AFC without the shift frame. These four factors comprehensively explain that during the process of pushing the AFC by the hydraulic support, the AFC is creeping and needs to stop for inspection according to experience.
Variation of motion parameters of the floating connection mechanism
According to the content of Sect. 4 , referring to the predicted momentum of the AFC track and the movement results of the floating connection mechanism, the extent of the creep of the AFC is judged and the result shown in Table 8 is obtained.
From Table 8 , the following synthesis results are obtained: \(S\left(VL\right)={10}^{-4}, S\left(L\right)=2\times {10}^{-4}, S\left(M\right)=0.007801, S\left(H\right)=0.9024, S(VH)=6\times {10}^{-4}\) . It can be seen that the degree of support for rating H is relatively high. Therefore, it can be considered that the extent of creeping on the AFC is H. There is a high probability of coal mining accidents. Emergency shutdown is required and measures are taken to prevent the AFC from continuing to creep and to avoid property damage caused by equipment accumulation.
5.3 Discussion
From the experimental results, it can be seen that the trend of the virtual simulation experiment is basically consistent with that of the laboratory experiment, which shows that it is feasible to analyze the creeping of the AFC through the virtual simulation system created in this paper to a certain extent. However, due to the limitation of experimental conditions, there is a certain gap between the test bench and the actual mining environment in the laboratory environment, and only qualitative analysis can be made on the creeping of the AFC.
The trajectory of AFC in virtual environment is predicted with high precision; When the prediction results are converted into parameters that can drive the creeping of the AFC under the virtual environment, the virtual conversion results are also of high accuracy, so the conversion results can be used as one of the criteria for determining the extent of creeping of the AFC under the virtual environment. However, there is a certain difference between the prediction results and the conversion results, which may be due to the impact of the collision of the physical engine installed on the equipment during the propulsion process, and the impact of the change of y coordinate value has not been taken into account in the established virtual conversion model.
According to the judgment of the degree of creeping of the AFC, it is found that the degree of creeping is relatively high, so it is necessary to take timely control measures. Starting from the machine head, the short knife is used to cut the coal downward, and finally the knife is used to cut through. The method of one-way frame shifting and sliding is adopted from the machine head to the tail. Feed every 20 hydraulic supports, and finally cut through the cutter from the tail to the head, so as to realize the rotary inclination adjustment of the fully mechanized working face and gradually reverse the creeping of the AFC.
6 Conclusion
Based on the Digital Twin theory and starting from the mechanism of problem occurrence, this paper takes the discrimination method of engineering problem of creeping of AFC as an example, integrates virtual reality technology with Bi-LSTM prediction algorithm, combines relevant decision-making reasoning algorithm and establishes the engineering problem prediction based on the fusion iteration of Digital Twin and prediction algorithm based on Fuzzy reasoning. The conclusions are as follows:
In this paper, a mechanism for analyzing the reasons of the creeping of AFC based on Digital Twin and grey correlation analysis is proposed. According to the reasons for the creeping of the AFC in the physical environment and mapped to the specific virtual factors in the virtual environment, a multi-factor analysis mechanism based on fuzzy grey correlation analysis method is established, which can determine the priority among the influencing factors. This is very important to the parameter configuration of the virtual environment and indirectly ensure the reliability of the final decision-making result.
The prediction method of AFC running track based on Bi-LSTM network in virtual environment is proposed. In the created virtual environment, the key operation information of equipment is extracted, and the established prediction model is used to predict the future operation information of equipment. On the premise of ensuring high prediction accuracy, the prediction results are used to provide data support for the determination of equipment operation health status.
The decision-making mechanism of the creeping of AFC based on fuzzy evidence reasoning is established. According to the prediction trajectory conversion model established in this paper, the future operation information of equipment in virtual environment is obtained. After fuzzifying the judgment degree of engineering problems with the fuzzy comprehensive evaluation method, and integrating the movement of the equipment with the D-S evidence theory, the judgment mechanism of the creeping of AFC is finally established. The judgment results can provide a reference for the operation state judgment of equipment and process adjustment in the physical environment.
The research framework proposed in this paper can provide research ideas for engineering problems in the production process of other industries. If the virtual interface is reserved in the established virtual scene, the virtual real two-way control technology is used to monitor the production scene driven by real-time data, and the deep learning prediction algorithm such as Bi-LSTM is used to predict the operation state of the equipment. The corresponding treatment measures are formulated in advance according to the established accident judgment mechanism, rehearsed in the virtual scene, and the treatment scheme is dynamically modified according to the virtual operation results. Such iterative operation until the optimal scheme is determined, and finally the health state prediction and response measures of the whole scene driven by real-time mining data are formulated in advance.
Bowen J, Lai R, Bahler D (1992) Fuzzy semantics and fuzzy constraint networks. In: IEEE International Conference on Fuzzy Systems. San Diego, CA, USA, pp 1009–1016. https://doi.org/10.1109/FUZZY.1992.258793
Cai N, Xie J, Wang X et al (2023) Method for the relative pose reconstruction of hydraulic supports driven by digital twins. IEEE Sens J 23(5):P4707–4719. https://doi.org/10.1109/JSEN.2023.3236971
Article Google Scholar
CSIRO (2021) Creep Control. Retrieved from http://www.lascautomation.com/dev/index.php/newoptimi-se/newcontrol/newcreepcontrol . Accessed December 5, 2021.
Dempster AP (1967) Upper and lower probabilities induced by a multivalued mapping. Ann Math Stat 38(2):325–339
Article MathSciNet Google Scholar
Dempster AP (1968) Generalization of Bayesian Inference. Journal of the RoyalStatistical Society. Series B 30:205–247
Google Scholar
Deng J (1988) Properties of relational space for grey systems. Grey System. China Ocean Press, Beijing
Feng YY, Ming SL, Bo ML (2023) Dynamic prediction of moving trajectory in pipe jacking: GRU-based deep learning framework. Front Sturct Civ Eng 17(7):994–1010. https://doi.org/10.1007/s11709-023-0942-5
Ge X, Xie J, Wang X et al (2020) A virtual adjustment method and experimental study of the support attitude of hydraulic support groups in propulsion state. Measurement 158:107743. https://doi.org/10.1016/j.measurement.2020.107743
Guo J, Zhao N, Sun L et al (2019) Modular based flexible digital twin for factory design. J Amb Intel Hum Comp 10:1189–1200. https://doi.org/10.1007/s12652-018-0953-6
Hochreiter S, Schmidhuber J (1997) Long short-term memory. Neural Comput 9(8):1735–1780. https://doi.org/10.1162/neco.1997.9.8.1735
Holm M (2014) The effect of longitudinal inclination in automatic controlled shearer workfaces. In:14th SGEM GeoConference on Science and technologies in geology, exploration and mining, Albena, Bulgaria, pp 653-663. https://doi.org/10.5593/SGEM2014/B13/S3.085
Hu D (2016) Mechnical system analysis and experimental research of scraper conveyor. Dissertation, China University of Mining & Technology
Huang Z, Wang F, Zhang S (2020) Research on the architecture and key technologies of intelligent coal mining system. J China Coal Soc 45:1959–1972. https://doi.org/10.13225/j.cnki.jccs.zn20.0348
Jie W, Zhijie Z, Hu C et al (2021) Performance evaluation of aerospace relay based on evidential reasoning rule with distributed referential points. Measurement 182:109667. https://doi.org/10.1016/j.measurement.2021.109667
Kang HS, Lee JY, Choi S et al (2016) Smart manufacturing: Past research, present findings, and future directions. Int J Pr Eng Man-Gt 3:111–128. https://doi.org/10.1007/s40684-016-0015-5
Le TD, Ahn KK (2011) A vibration isolation system in low frequency excitation region using negative stiffness structure for vehicle seat. J Sound Vib 330:6311–6335. https://doi.org/10.1016/j.jsv.2011.07.039
Li S, Xie J, Wang X et al (2022) A method of straightening armoured face conveyor based on space kinematics of reserve pushing mechanism. Proc Inst Mech Eng C J Mech Eng Sci 236(6):3073–3092. https://doi.org/10.1177/09544062211036103
Li S, Xie J, Ren F, et al (2021) Virtual straightening of scraper conveyor based on the position and attitude solution of industrial robot model. Int J Coal Sci Techn 8:1149–1170. https://doi.org/10.1007/s40789-020-00389-y
Michael S, Hainsworth D (2005) Outcomes of the landmark long-wall automation project with reference to ground control issues. In: The 24th International Conference on Ground Control in Mining. Lakeview Scanticon Resort&Conference Center, Morgantown, WV, USA, pp 1–8. http://hdl.handle.net/102.100.100/183258
Min K, Kim D, Park J et al (2019) RNN-Based Path Prediction of Obstacle Vehicles With Deep Ensemble. IEEE T Veh Technol 68(10):0252–10256. https://doi.org/10.1109/TVT.2019.2933232
Niu JF (2015) Automatic incline adjustment and anti-skid control system development for full-mechanized mining face. Coal Min Techno 20(2):32–34. https://doi.org/10.13532/j.cnki.cn11-3677/td.2015.02.010
Özer İ, Efe SB, Özbay H (2021) CNN/Bi-LSTM-based deep learning algorithm for classification of power quality disturbances by using spectrogram images. Int Trans Electr Energ Syst 31(12):13204. https://doi.org/10.1002/2050-7038.13204
Peng SS, Du F, Cheng J et al (2019) Automation in U.S. longwall coal mining: A state-of-the-art review. Int J Min Sci Technol 29:151–159. https://doi.org/10.1016/j.ijmst.2019.01.005
Qiang L (2020) Study on Architecture of Intelligent Manufacturing Theory. Chin J Mech Eng-En 31:24–36. https://doi.org/10.3969/j.issn.1004-132X.2020.01.004
Quan R, Zhu L, Wu Y (2021) Holistic LSTM for Pedestrian Trajectory Prediction. IEEE T Image Process 30:3229–3239. https://doi.org/10.1109/TIP.2021.3058599
Shafer G (1976) A Mathematical Theory of Evidence. Princeton University Press, Princeton
Book Google Scholar
Shen H, Xie J, Li J et al (2021) Collision Detection of Virtual Powered Support Groups Under Complex Floors. IEEE T Instrum Meas 70:1–13. https://doi.org/10.1109/TIM.2021.3104412
Shenguang H, Xing X, Ju X et al (2023) Adaptive control of dual-motor autonomous steering system for intelligent vehicles via Bi-LSTM and fuzzy methods. Control Eng Pract 130:105362. https://doi.org/10.1016/j.conengprac.2022.105362
Simone Z, Kefato ZT, Sarunas G et al (2022) Pedestrian trajectory prediction with convolutional neural networks. Pattern Recogn 121:108252. https://doi.org/10.1016/j.patcog.2021.108252
Song X, Wang L (2014) Research on Mining Engineering with Dual Gradient High Inclination-Angle Fully Mechanized Mining Technology. Adv Mat Res 977:231–234. https://doi.org/10.4028/www.scientific.net/AMR.977.231
Tong Y, Wu P, He J et al (2021) Bearing Fault Diagnosis Via Combining Deep Residual Shrinkage Network and Bidirectional LSTM. Meas Sci Technol 33(3):034001. https://doi.org/10.1088/1361-6501/ac37eb
Verma P (2013) An experimental investigation of the creep behavior of an underground coalmine roof with shaEle formation. West Virginia University. Department of Mining Engineering, Morgantown
Wang J, Huang Z (2017) The Recent Technological Development of Intelligent Mining in China. Eng 3(4):439–444. https://doi.org/10.1016/J.ENG.2017.04.003
Wang S, Wang S, Liu W (2020) Longwall Retreat and Creep Measurement Based on UWB Radar Imaging Method. Math Probl Eng 2(2020):1–13. https://doi.org/10.1155/2020/4056246
Wang Q, Cai M, Wei G (2022) A scenario analysis under epistemic uncertainty in Natech accidents: imprecise probability reasoning in Bayesian Network. Environ Res Commun 4(1):015008. https://doi.org/10.1088/2515-7620/ac47d4
Xie J, Li S, Wang X (2022) A digital smart product service system and a case study of the mining industry: MSPSS. Adv Eng Inform 53:101694. https://doi.org/10.1016/j.cie.2022.108050
Xiping W, Hongyu Y, Hu C et al (2022) Long-term 4D trajectory prediction using generative adversarial networks. Transport Res C-Emer 136:103554. https://doi.org/10.1016/j.trc.2022.103554
Xu YQ (1999) Coal Ming. China University of Mining and Technology Press, BeiJing
Yager RR (1987) On the dempster-shafer framework and new combination rules. Inform Sci 41(2):93–137. https://doi.org/10.1016/0020-0255(87)90007-7
Yeming D, Qiong Z, Mingming L et al (2022) Improving the Bi-LSTM model with XGBoost and attention mechanism: A combined approach for short-term power load prediction. Appl Soft Comput 130:109632. https://doi.org/10.1016/j.asoc.2022.109632
Zhang KX, Li SB, He MC et al (2018) Study on key technologies of intelligent unmanned coal mining series: study on diagonal adjustment control technology of intelligent fully-mechanized coal mining face. Coal Sci Techno 46:139–149. https://doi.org/10.13199/j.cnki.cst.2018.01.020
Download references
Acknowledgements
This research was supported by the Central Guidance on Local Science and Technology Development Fund of Shanxi Province (YDZISX2022A014);Shanxi 1331 Project(1331); Fund Program for the Scientific Activities of Selected Returned Overseas Professionals in Shanxi Province(20230008), Research Project Supported by Shanxi Scholarship Council of China (2023-071), and the National Natural Science Foundation of China (52004174) .
Author information
Authors and affiliations.
College of Mechanical and Vehicle Engineering, Key Laboratory of Fully Mechanized Coal Mining Equipment, Taiyuan University of Technology, Shanxi, 030024, China
Suhua Li, Jiacheng Xie, Xuewen Wang & Fuxiang Ge
Taiyuan University of Technology, No.216 Mailbox HuYu Campus, No.18, XinKuangYuan Road, TaiYuan, ShanXi Province, People’s Republic of China
You can also search for this author in PubMed Google Scholar
Contributions
S.L. and J.X. carried out conceptual analysis; X.W. and J.X. determined the structure of the paper; X.W. and J.X. applied for fundings; S.L. wrote the main manuscript text; S.L. and J.X. conducted literature review and investigation; S.L. and X.W. determined the specific formula; X.W. managed the whole thesis; S.L. and F.G. completed the construction of simulation environment and test platform; S.L., J.X. and F.G. conducted data processing; S.L., X.Wn. revised the article format.
Corresponding author
Correspondence to Xuewen Wang .
Ethics declarations
Competing interests.
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Li, S., Xie, J., Wang, X. et al. Prediction of the creeping of AFC based on fuzzy reasoning and Bi-LSTM fusion iteration. Artif Intell Rev 57 , 142 (2024). https://doi.org/10.1007/s10462-024-10773-8
Download citation
Accepted : 18 April 2024
Published : 16 May 2024
DOI : https://doi.org/10.1007/s10462-024-10773-8
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Digital Twin
- Fuzzy Comprehensive Evaluation
- D-S evidence theory
- Find a journal
- Publish with us
- Track your research
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 14 May 2024
Nonlinear evolution characteristics and seepage mechanical model of fluids in broken rock mass based on the bifurcation theory
- Jia Yunlong 1 ,
- Cao Zhengzheng 1 , 2 , 3 ,
- Li Zhenhua 2 , 3 ,
- Du Feng 2 , 3 ,
- Huang Cunhan 2 , 3 ,
- Lin Haixiao 1 ,
- Wang Wenqiang 2 , 3 &
- Zhai Minglei 2 , 3
Scientific Reports volume 14 , Article number: 10982 ( 2024 ) Cite this article
69 Accesses
Metrics details
- Civil engineering
With the deep extension of coal mining in China, fault water inrush has become one of the major disasters threatening the safety production of coal mine. Based on the control equations of steady state and non-Darcy seepage in fractured rock mass, the multi-parameter nonlinear dynamic seepage equations of fractured rock mass are established in this paper. Based on the nonlinear dynamics theory, the function of the state variable in the system is derived, and the influence of the gradual change of non-Darcy flow factors on the structural stability of seepage system is studied. The research achievements show that there are three branches in the equilibrium state of the seepage system. Specifically, the stability of the equilibrium state changes abruptly near the limit parameter. The seepage dynamic system of fractured rock mass has the delayed bifurcation, and the coal mine disaster such as fault water inrush occurs easily at the bifurcation point. The research results are of great significance to enrich the theory of fault water inrush in coal mine, and to reveal the disastrous mechanism of fault water inrush and guide its prevention and control technology in coal mine, which can provide the theoretical reference for predicting the water seepage stability in fractured rock mass.
Similar content being viewed by others

Semi-analytical solution for bottomhole pressure transient analysis of a hydraulically fractured horizontal well in a fracture-cavity reservoir
Instability motion characteristics of overburden rock and the distribution pattern of fissures in shallow thick seam mining
Re-crushing process and non-Darcian seepage characteristics of broken coal medium in coal mine water inrush
Introduction.
In engineering practice, the fractured rock mass of dam foundation, slope and roadbed is often unstable due to seepage instability 1 . After the dam is loaded with water, the upstream fault is stretched and the downstream fault is compressed, forcing the seepage pressure under the dam foundation to rise 2 , 3 . The seepage pressure water extrudes the fractured rock mass to destroy the dam foundation, and the reservoir water thoroughly erodes the fractured rock mass of the dam foundation, resulting in a series of catastrophic accidents 4 , 5 . The existence of groundwater in fractured rock mass strongly affects the deformation and stability of rock mass structure through various physical and chemical actions such as lubrication, subduction, hydrolysis, bonding, freeze–thaw, and hydraulic fracturing mechanics caused by hydro-static pressure and dynamic water pressure 6 .
Fractured rock mass is a common deformable porous medium in engineering, which can be roughly divided into two categories 7 . Specifically, one is the in-situ fractured rock mass broken by structural and mining stress but still in the original position (such as the loose ring rock mass around the excavation of the roadway), while the other is the accumulated fractured rock mass broken by engineering excavation and can be compacted again under high pressure (such as the overburden accumulation body broken by mining action). Compared with intact and dense rock mass, fractured rock mass has higher compactibility and permeability, and its permeability coefficient is one to several orders higher than that of intact rock mass. Therefore, the research work of fractured rock mass seepage characteristics has a broad engineering application prospect.
The seepage law of liquid in fractured rock mass has been studied by many scholars. Ma et al. 8 studied the influence of stress and grade pair on pore size distribution, pore fractal and nonlinear seepage characteristics behavior of fractured rock mass, and built a permeability prediction model of fractured rock mass based on nuclear magnetic resonance. On the basis of collecting and sorting out relevant data at home and abroad, Yang et al. 9 summarized the research status of nonlinear seepage characteristics water inrush in fractured rock mass from the aspects of nonlinear seepage characteristics theory equation, non-Darcy seepage test and nonlinear seepage characteristics numerical model method. Xu et al. 10 used the constant head steady state permeability method to study the permeability performance of fractured rock mass in the caving zone of goaf and the permeability coefficient of fractured rock mass with different porosity. The results show that the underground water flow in the fractured rock mass in the caving zone of goaf is characterized by high-speed nonlinear seepage characteristics, and the characteristics of underground water flow are obviously affected by the porosity and particle size distribution of the permeating medium. Zhang et al. 11 studied the seepage characteristics of fractured rock mass under the confining conditions, and the results show that the porosity of both the collapse column and limestone samples decrease exponentially with the increase of axial pressure, but the porosity of the collapse column samples decrease slightly more than that of limestone. An et al. 12 analyzed the fault erosion water inrush process under the action of confined water on the floor in detail through numerical simulation. Based on the fractal theory of porous media and the nonlinear seepage characteristics theory, Liu et al. 13 established a nonlinear seepage characteristics mathematical model of fractured rock mass considering the composition of clay and the effect of mud filling. The results show that with the decrease of the permeability of rock mass in the fractured zone, the critical pressure gradient at the beginning of nonlinear occurrence also increases, and the nonlinear critical pressure gradient can be used to quantify the water-blocking ability of fractured rock mass. Based on the theory of two-phase flow, Du et al. 14 analyzed the characteristics of water–sand two-phase seepage in fractured rock mass and the applicable theoretical model, and the results show that as the particle size of fractured rock mass increases, the β factor and acceleration coefficient of water–sand two-phase non-Darcy flow decreases, and the mobility increases. Xu et al. 15 carried out a non-Darcy seepage test of fractured rock mass under the action of high hydraulic gradient, and the results show that there is a negative exponential relationship between the non-Darcy equivalent permeability coefficient and the hydraulic gradient, and its value is affected by the pore structure of the sample. Yao et al. 16 , 17 conducted a variable mass permeability test of fractured rock mass with different proportions. The results show that the filling content has an important effect on the permeability of fractured rock mass. With the increase of the proportion of fill in the sample, the maximum mass loss rate of the sample increases and the porosity increases. Both the initial permeability and the increase of permeability show a change law of first increasing and then decreasing. Chen et al. 18 established a method to extract the permeability parameters of fractured rock mass with variable mass based on the time series of pressure gradient and seepage velocity, and analyzed the feasibility and accuracy of this method for calculating the permeability parameters of fractured rock mass with variable mass through a numerical example. Zhang et al. 19 studied the stress and seepage coupling model of fractured rock mass, and the results show that the increase of pore water pressure reduced the peak strength of rock mass, and the existence of high-pressure water increases the deterioration degree of rock mass and the development degree of cracks, thus increasing the risk of disaster caused by water inrush.
The mechanism of seepage disaster in fractured rock mass has become an important research topic in the mechanism of water inrush 20 . In summary, there are three main hypotheses to explain the mechanism of water inrush in coal mines, which are water inrush hypothesis caused by rock mass structure failure, water inrush hypothesis caused by seepage and loss stability, and water inrush hypothesis caused by rock mass deformation and seepage instability in coupling system. The hypothesis of seepage instability is that the accidents of water inrush, gas outburst and sand collapse in coal mine are the manifestations of seepage instability. Li et al. 21 , 22 established a dynamic model of non-Darcy seepage flow in fractured rock mass, without involving the mass change. For such fractured rock mass that does not consider the mass change in the process of infiltration, the key point to explain the mechanism of water inrush from the perspective of seepage instability is whether the instability condition of the seepage system can be physically achieved. Li et al. 23 studied and discussed whether the instability condition can be physically achieved. Bifurcation theory is widely used. For example, a non-smooth bifurcation exists in a grid-connected inverter controlled by a generator 24 . In terms of turning direction stability of high-speed UAV, saddle knot bifurcation and Hopf bifurcation occurs in the system 25 . In this paper, the structural stability of seepage system in fractured rock mass is studied by numerical response analysis based on bifurcation theory and nonlinear seepage dynamics equation.
Control equation of nonlinear seepage characteristics
One-dimensional nonlinear seepage characteristics dynamics equation.
The governing equation of nonlinear seepage characteristics in fractured rock mass consists of three parts, namely, the mass conservation equation, the seepage motion equation and the state equation 26 .
When fluid flows in porous media, it follows the law of conservation of mass, and the differential equation satisfied by this conservation of mass is the continuity equation:
where v is the seepage velocity, \(\phi\) is the porosity, \(\rho\) is the mass density of the fluid, and q is the source term.
For passive unsteady seepage, the continuity equation can be simplified as follows:
For one-dimensional unsteady flow, \(v_{x} = v\) . Applying the continuity equation, we can get
Darcy’s law is the motion equation of steady state seepage flow. For more general unsteady Darcy seepage flow, the following motion equation is given in the literature 27 :
where \(g_{a}\) is called the acceleration coefficient tensor. Permeability k is a scalar for homogeneous isotropic media and a second-order tensor for anisotropic media.
For unsteady nonlinear seepage characteristics flow of fractured rock mass, its one-dimensional motion equation can be expressed as:
where \(g_{a}\) is the acceleration coefficient, f is the Darcy flow deviation factor, p is the pore fluid pressure, μ is the dynamic viscosity of the fluid, and k is the permeability of the broken rock.
The equation of state is 28 , 29 :
where \(\rho_{0}\) and \(\phi_{0}\) are the porosity and mass density corresponding to the reference pressure \(p_{0}\) , and \(c_{f}\) is the isothermal compression coefficient of the fluid. \(c_{\phi }\) is the pore compression coefficient.
Combine the above two formulas, then
where \(o(c^{2} )\) represents a term with a compression coefficient of 2 or more. Assuming the comprehensive compression coefficient \(c_{t} = c_{f} + c_{\phi }\) , then
By substituting Eq. ( 9 ) into Eq. ( 3 ), then
Therefore, the dynamic equations of one-dimensional non-Darcy seepage in fractured rock mass are obtained from Eqs. ( 5 ) and ( 10 ),
When the compressibility of water is not considered, it is obtained by Eq. ( 12 ):
Perform a dimensionless transformation of the above equation, let.
\(\overline{p} = \frac{p}{{p_{0} }}\) , \(\overline{x} = \frac{x}{H}\) , \(\overline{v} = \frac{v}{\mu /fk}\) , \(\overline{t} = \frac{t}{fkH/\mu }\) .
There into.
\(n_{0} = \frac{1}{{p_{0} \phi_{0} c_{t} }}\) , \(n_{1} = \frac{{p_{0} }}{{g_{a} \rho_{0} }}(\frac{fk}{\mu })^{2}\) , \(n_{2} = \frac{fH}{{g_{a} \rho_{0} }}\) , \(n_{3} = n_{2}\) , \(n_{4} = (\frac{fk}{\mu })^{2} \cdot \frac{H \cdot g}{{g_{a} }}\) ;
Initial and boundary conditions of one-dimensional non-Darcy seepage system of fractured rock mass:
Schematic diagram of seepage from broken rock mass is shown in Fig. 1 . Set the initial conditions of the seepage system: pore pressure \(p_{0} (x) = p_{01} + \frac{{p_{02} - p_{01} }}{H}x\) (Where H is the accumulation height of the broken rock body, and \(p_{01}\) , \(p_{02}\) are the initial pore water pressure at the lower and upper ends of the accumulated rock body, respectively), seepage velocity \({\text{v}}_{0} (x) = v_{0}\) , seepage direction along the x-axis upward.
Schematic diagram of seepage from broken rock mass.
Boundary condition: \(\left. p \right|_{x = 0} = p_{1}\) , \(\left. p \right|_{x = H} = p_{2}\) , where the \(p_{1} > p_{2}\) , the flow direction is upward along the x-axis.
After nondimensionalization, we can get: \(\overline{p}_{0} (\overline{x}) = \frac{{p_{01} }}{{p_{0} }} + \frac{{p_{02} - p_{01} }}{{p_{0} }}\overline{x}\) , \({\overline{\text{v}}}_{0} (\overline{x}) = \frac{fk}{\mu }v_{0}\) , here \(\overline{x} \in \left[ {0,1} \right]\) ; \(\left. p \right|_{x = 0} = \frac{{p_{1} }}{{p_{0} }}\) , \(\left. p \right|_{x = H} = \frac{{p_{2} }}{{p_{0} }}\) .
Equilibrium state of one-dimensional non-Darcy seepage system in fractured rock mass
The equilibrium state of the system \((\overline{p}_{s} ,\overline{v}_{s} )\) is found below, and when the system is in equilibrium, it is obtained by Eq. ( 14 ).
According to the pore pressure boundary condition of the percolation system of accumulative fractured rock mass is \(\left. {\overline{p}_{1} } \right|_{{\overline{x} = 0}} = \frac{{p_{1} }}{{p_{0} }}\) , \(\left. {\overline{p}_{2} } \right|_{{\overline{x} = 1}} = \frac{{p_{2} }}{{p_{0} }}\) , Then, pore water pressure \(\overline{p}_{s}\) and seepage velocity \(\overline{v}_{s}\) at equilibrium can be obtained respectively.
Because \(n_{1} = \frac{{p_{0} }}{{g_{a} \rho_{0} }}(\frac{fk}{\mu })^{2}\) , \(\frac{{p_{1} - p_{2} }}{{p_{0} }} > 0\) , \(n_{3} = n_{2} = \frac{fH}{{g_{a} \rho_{0} }}\left\{ \begin{gathered} > 0,{\text{ f}} > 0 \hfill \\ = 0,{\text{ f}} = 0 \hfill \\ < 0,{\text{ f}} < 0 \hfill \\ \end{gathered} \right.\)
So in Eq. ( 16 ). \(n_{1} \frac{{p_{1} - p_{2} }}{{p_{0} }} - n_{4} = \frac{1}{{g_{a} \rho_{0} }}\left( {\frac{fk}{\mu }} \right)^{2} (p_{1} - p_{2} - \rho_{0} gH) > 0\) .
That is, when \(f > 0\) , \(n_{3} = n_{2} > 0\) the system has only one equilibrium state
When \(f < 0\) , \(n_{3} = n_{2} < 0\) , the equilibrium state of the system can be obtained from Eq. ( 16 ).
If \(f_{s} = - \frac{{\mu^{2} H}}{{4k^{2} (p_{1} - p_{2} - \rho_{0} gH)}}\) , then all equilibrium states of the system are
All the solution results are drawn into the system solution diagram, as shown in Fig. 2 . It can be seen that the equilibrium state of the system has three branches. Namely, branch I ( \(f > 0,\overline{v}_{s} > 0\) ), branch II ( \(f < 0,\overline{v}_{s} > - 0.5\) ), and branch III ( \(f < 0,\overline{v}_{s} < - 0.5\) ).
Solution of non-Darcy water seepage system in fractured rock mass.
Numerical simulation of nonlinear seepage characteristics system in fractured rock
The numerical calculation is carried out by the successive sub-relaxation iterative method 30 . According to Eq. ( 13 ), the forward difference formula is used for the partial derivative of time and the central difference formula is used for the partial derivative in the height direction. Dividing nodes along time and height directions respectively, with i representing time and j representing space, then there is
Then, according to the sub-relaxation iterative formula \(\overline{p}_{i + 1,j} \leftarrow (1 - \omega )\overline{p}_{i,j} + \omega \overline{p}_{i + 1,j}\) , \(\overline{v}_{i + 1,j} \leftarrow (1 - \omega )\overline{v}_{i,j} + \omega \overline{v}_{i + 1,j}\) (where \(\omega\) is the relaxation factor, \(0 < \omega < 1\) ). The time series of pore pressure and seepage velocity of each node can be obtained by iterative calculation of each point.
Set the pressure boundary \(p_{1} = 0.65\) (MPa), \(p_{2} = 0.25\) (MPa), fractured rock mass at reference pressure \(p_{0} = 0.35\) (MPa), the initial porosity of fractured rock mass under reference pressure is \(\phi_{0} = 0.3\) , and the dynamic viscosity \(\mu = 1.0 \times 10^{ - 3}\) (Pa s), and the permeability \(k = 0.5 \times 10^{ - 13}\) (m 2 ), acceleration coefficient \(g_{a} = 9.5 \times 10^{9}\) , liquid compressibility coefficient \(c_{f} = 4.77 \times 10^{ - 10}\) (Pa −1 ), the pore compressibility coefficient \(c_{\phi } = 2.01 \times 10^{ - 9}\) (Pa −1 ), \(\rho_{0} = 1000\) (kg/m 3 ), H = 5m, \(\Delta \overline{x} = 0.1\) (here the height of the accumulated rock mass is divided into 10 equal parts), \(\omega = 0.5\) .
The deviation factor of Darcy flow is taken \(f = 3.5 \times 10^{12}\) (kg/m 4 ), and the equilibrium state of the system \(\overline{v}_{s} = 6.1{62} \times 10^{ - 4}\) can be obtained by calculation. If both pore water pressure and seepage velocity at the initial moment deviate from the equilibrium state relatively close, take \(p_{01} = {0}{\text{.5}}\) (MPa), \(p_{02} = 0\) (MPa), \(\overline{v}_{0} = {6}{\text{.5}} \times 10^{ - 4}\) .
As shown in Fig. 3 , the damping motion of the seepage velocity through oscillation attenuation approaches to the equilibrium state. The phase orbitals of different heights are shown in Fig. 4 . At this time, the attractor is the stable focus in two-dimensional space, and its corresponding equilibrium state is stable.
Seepage velocity change curve.
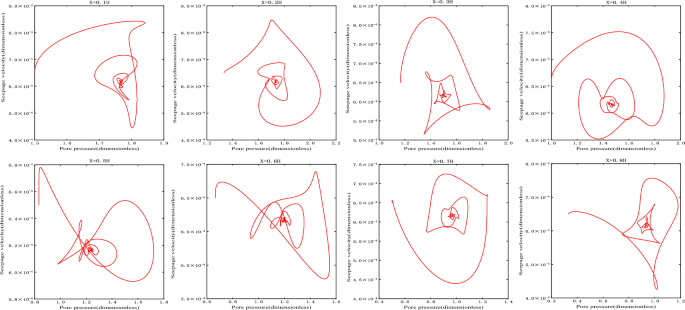
Phase orbit.
With the deviation of Darcy flow from factor f , how will the whole seepage system change. Keeping the boundary conditions and initial velocity constant, take \(p_{01} = {0}{\text{.5}}\) (MPa), \(p_{02} = 0\) (MPa), \(\overline{v}_{0} = {6}{\text{.5}} \times 10^{ - 4}\) ; The values of f are \(3.5 \times 10^{12}\) (kgm −4 ), \(8 \times 10^{12}\) (kgm −4 ), and \(3.5 \times 10^{13}\) (kgm -4 ), respectively. The relationship between seepage velocity and time is shown in Fig. 5 .
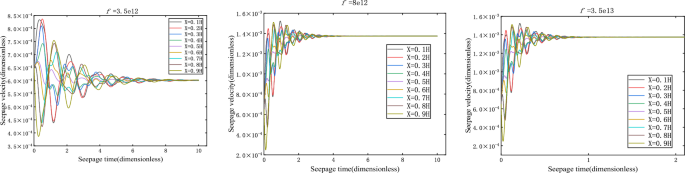
In fact, for f greater than 0, no matter what value v takes, the system is stable and eventually converges to \(v_{s}\) . However, if the Darcy flow deviates from factor f , the system changes significantly. When f is greater than 0, as f decreases, the time required for the system to reach the equilibrium state becomes longer, and the time history curves of seepage velocity and pore pressure converge slowly. With the increase of f , the time required for the system to reach the equilibrium state becomes shorter, and the corresponding time history curves of seepage velocity and pore pressure converge faster. According to the above analysis, the equilibrium state corresponding to branch I is stable.
It can be seen from the bifurcation diagram that when the Darcy flow deviates from factor \(f < 0\) , there are two branches in the equilibrium state bounded by the limit point: branch II and branch III. Then there are two equilibrium velocities for each parameter f , denoted as \(\overline{v}_{s2}\) , \(\overline{v}_{s3}\) , respectively. Obtain a corresponding limiting parameter \(f_{s}\) from the parameters given above, \(f_{s} = - \frac{{\mu^{2} H}}{{4k^{2} (p_{1} - p_{2} - \rho_{0} gH)}}\) . Therefore, when the parameter f changes between \(f_{s} < f < 0\) , the stability of the equilibrium state on each branch can be observed through the numerical calculation results. According to the parameters given above, the limit parameters are calculated \(f_{s} = - 1.453133903133904 \times 10^{15}\) (kg/m 4 ).
As shown in Fig. 6 , choose a f value between: \(f_{s} < f < 0\) , \(f = - 7.265 \times 10^{14}\) (kg/m 4 ). And the corresponding velocity of the two equilibrium states on the solution graph are \(\overline{v}_{s2} = - 0.1464\) , \(\overline{v}_{s3} = - 0.8536\) , respectively.
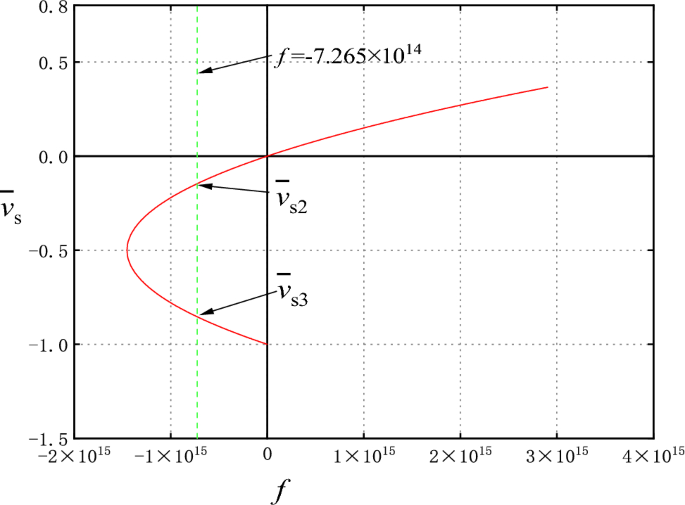
System Diagram.
When \(\overline{v}_{02} > \overline{v}_{s2}\) , take \(\overline{v}_{02} = - 0.1\) , the initial velocity deviates from the equilibrium state and is located on the upper side of the equilibrium state, and finally returns to the equilibrium state \(\overline{v}_{s2}\) stably after the evolution trajectory, as shown in the Fig. 7 , which is the dynamic response when the initial velocity of branch II is greater than the equilibrium state velocity. Its phase trajectory at different heights is shown in Fig. 8 , which converges to one point after a series of changes.
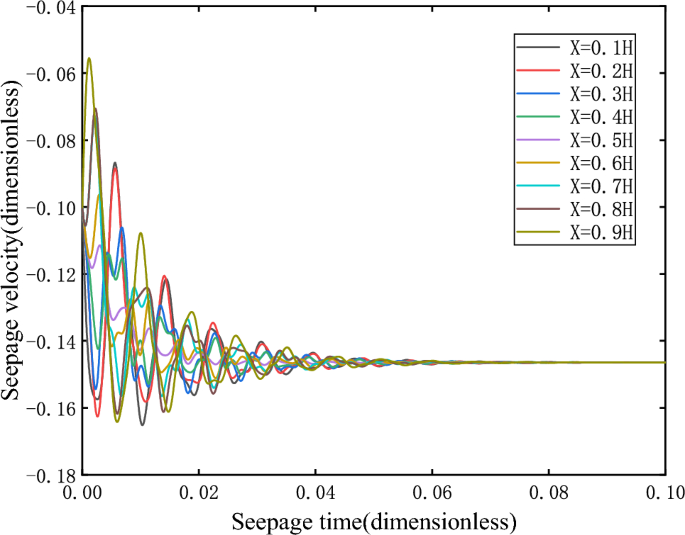
In particular, it should be noted that when \(f < 0\) , the time in the time history curve of all physical quantities such as pore pressure and seepage velocity is the size or absolute value of \(\overline{t}\) (the non-dimensional time).
When \(\overline{v}_{02} < \overline{v}_{s2}\) , take \(\overline{v}_{02} = - 0.2\) , the initial velocity deviates from the equilibrium state and is located on the lower side of the equilibrium state, and finally returns stably to the equilibrium state \(\overline{v}_{s2}\) (− 0.1464) after the evolution trajectory, as shown in the Fig. 9 . As shown in Fig. 10 , the phase trajectory composed of seepage velocity and pore pressure at different heights eventually converges to a point.
It can be seen that the equilibrium point corresponding to branch II is a stable node.
When \(\overline{v}_{03} > \overline{v}_{s3}\) , take \(\overline{v}_{03} = - 0.8\) , the initial velocity deviates from the equilibrium state and is located on the upper side of the equilibrium state. After evolution, it is found that the orbit does not return to its corresponding equilibrium state \(\overline{v}_{s3}\) , but is attracted to the corresponding equilibrium point \(\overline{v}_{s2}\) on branch II, as shown in Fig. 11 .
When \(\overline{v}_{03} < \overline{v}_{s3}\) , \(\overline{v}_{s3} = - 0.8536\) , take \(\overline{v}_{03} = - 0.9\) , the initial velocity deviates from the equilibrium state and is located on the lower side of the equilibrium state. After evolution, it is found that the orbit does not return to its corresponding equilibrium state \(\overline{v}_{s3}\) , but more and more deviates from the equilibrium state and flows to negative infinity, as shown in Fig. 12 .
As can be seen from the changes in speed and pressure, the sudden change of instability when the system is unstable is extremely fast.
It can be seen that the equilibrium state corresponding to branch III is unstable. When the initial velocity is greater than the equilibrium state velocity, the orbit is eventually attracted to the corresponding equilibrium point on branch II. However, when the initial velocity is less than the equilibrium velocity, its orbit moves away from the equilibrium point and tend to negative infinity, that is, branch III is the boundary between the attraction domain of the stable node trajectory on branch II and the attraction domain of infinity. Therefore, the equilibrium point on branch III is the saddle point.
Conclusions
The stability analysis of seepage system is the theoretical basis for correctly predicting and preventing fault water inrush disaster. A dynamic system is inevitably subject to various unpredictable perturbations. These disturbances can be small changes in the surrounding environment, such as fluctuations in air flow, temperature, or electromagnetic fields, or they can be intrinsic fluctuations in the system, such as the thermal motion of molecules and atoms. The stability of the solution (state of motion) means that if the system deviates from the solution (state of motion) under disturbance, it automatically returns to the state of motion represented by the solution. That is, the system can stay in this state of motion stably for a long time or at least not deviate too far from it. Otherwise, the solution of the equation is said to be unstable. Where Lyapunov stability means that the solution does not deviate too much under perturbations or small changes in initial conditions. In the asymptotically stable case, even if the system is disturbed, it eventually returns to the undisturbed solution (state of motion). In the case of instability, any disturbance or small change in the initial conditions is sufficient to cause the subsequent solution (state of motion) to deviate beyond any given range.
According to the non-Darcy characteristics of fractured rock seepage, the motion equation of fractured rock seepage is established in this paper. Combined with continuity equation and state equation, one-dimensional nonlinear dynamic partial differential equations for non-Darcy seepage in fractured rock mass are given. By means of dimensionless transformation, the equilibrium solution diagram of the seepage dynamic system under the given boundary conditions is obtained. With the change of parameter f , the equilibrium solution diagram of the seepage system can be divided into three branches. The numerical analysis shows that the equilibrium state (Branch I) is stable when the parameters \(f > 0\) are used. When \(f < 0\) , the equilibrium state has two branches, the equilibrium point on one branch (Branch II) is a stable node, and the equilibrium point on the other branch (Branch III) is an unstable saddle point. When f gradually decreases and approaches the limit parameter \(f_{s}\) (negative value), the saddle point meets the node and annihilates. When \(f_{s} < f\) the equilibrium point disappears, the small disturbance of the system causes the seepage loss stability. Near the limit parameter, the stability of the equilibrium state of the system changes abruptly, so that the seepage system is prone to collapse mutation at the bifurcation point leading to water inrush and other disasters. The analysis in this paper can provide theoretical reference for the prediction of the water seepage instability in fractured rock mass.
Data availability
Some or all data, models, or codes generated or used during the study are available from the corresponding authors by request.
Cao, Z. Z. et al. Evolution mechanism of water-conducting fractures in overburden under the influence of water-rich fault in underground coal mining. J. Sci. Rep. 14 , 5081. https://doi.org/10.1038/s41598-024-54803-5 (2024).
Article CAS Google Scholar
Wang, W. et al. Study of roof water inrush control technology and water resources utilization during coal mining in a Karst area. J. Mine Water Environ. 42 , 546–559. https://doi.org/10.1007/s10230-023-00953-3 (2023).
Article ADS Google Scholar
Xue, Y. et al. Experimental study on the effect of heating and liquid nitrogen-cooling cyclic treatment on mechanical properties and fracturing characteristics of granite. Int. J. Rock Mech. Min. Sci. 176 , 105691 (2024).
Article Google Scholar
Wang, L. C. et al. Effect of weakening characteristics of mechanical properties of granite under the action of liquid nitrogen. J. Front. Ecol. Evol. https://doi.org/10.3389/fevo.2023.1249617 (2023).
Wu, Y. J. et al. Seepage evolution characteristics and water inrush mechanism in collapse column under mining influence. J. Sci. Rep. 14 , 5862. https://doi.org/10.1038/s41598-024-54180-z (2024).
Wang, L. C. et al. Experimental study on mode I fracture characteristics of granite after low temperature cooling with liquid nitrogen. J. Water https://doi.org/10.3390/w15193442 (2023).
Cao, Z. Z. et al. Research on slurry diffusion and seepage law in mining overburden fractures based on CFD numerical method. J. Sci. Rep. 13 , 21302. https://doi.org/10.1038/s41598-023-48828-5 (2023).
Ma, D. et al. Pore structure characterization and nonlinear seepage characteristics of rock mass in fault fracture zones. J. China Coal Soc. 48 (2), 666–677. https://doi.org/10.13225/j.cnki.jccs.S022.1678 (2023).
Yang, T. H. et al. State of the art and trends of water-inrush mechanism of nonlinear flow in fractured rock mass. J. China Coal Soc. 41 (07), 1598–1609. https://doi.org/10.13225/j.cnki.jccs.2016.0336 (2016).
Xu, S. Y. et al. Flow characteristics and experimental study on the permeability of mining-induced fractured rock mass in caving zones. J. Saf. Environ. Eng. 29 (01), 128–134. https://doi.org/10.13578/j.cnki.issn.1671-1556.20210645 (2022).
Zhang, B., Liu, G., Li, Y. & Lin, Z. Experimental study on the seepage mutation of natural karst collapse pillar (KCP) flings over mass outfow. J. Environ. Sci. Pollut. Res. https://doi.org/10.1007/s11356-023-30230-3 (2023).
An, T. L. et al. Study on the fault erosion-seepage rule under the effect of floor confined water. J. Mining Saf. Eng. 40 (02), 354–360. https://doi.org/10.13545/j.cnki.jmse.2021.0586 (2023).
Liu, W. T., Zhao, J. Y., Huo, Z. C., et al . Study on a mathematical model and experiments for nonlinear seepage characteristics in complex crushed rocks with mud-rock slurry. J/OL. Coal Sci. Technol. 1–15 (2024).
Du, F., Cao, Z. Z. & Li, Z. H. Research progress of two phases water-sand flow characteristics in crushed rock mass. J. Coal Sci. Technol. 46 (07), 48–53. https://doi.org/10.13199/j.cnki.cst.2018.07.007 (2018).
Xu, Z. G. et al. Study on non-Darcy seepage characteristic and model of the broken rock mass of fault zone. Chin. J. Rock Mech. Eng. 42 (S2), 4099–4108. https://doi.org/10.13722/j.cnki.jrme.2022.1165 (2023).
Yao, B. H. et al. Experiment on the variable mass seepage of the broken rock under the different filling mass proportions. J. Saf. Environ. 18 (02), 481–486. https://doi.org/10.13637/j.issn.1009-6094.2018.02.013 (2018).
Yao, B. H. Research on Variable Mass Fluid-Solid Coupling Dynamic Theory of Broken Rock-Mass and Application (China University of Mining and Technology, 2012).
Google Scholar
Chen, Z. Q. et al. A method for calculating permeability parameters of variable mass of broken rock. Chin. J. Appl. Mech. 31 (06), 927–932 (2014).
Zhang, C. et al. Study on stress seepage coupling model and numerical simulation of fractured rock mass. J. Mining Saf. Eng. 38 (06), 1220–1230. https://doi.org/10.13545/j.cnki.jmse.2020.0267 (2021).
Tian, Z. C., Liu, Y. J. & Wang, R. C. Discussion on the application of nonlinear dynamic bifurcation theory in mining. J. Mod. Mining 27 (11), 54–56 (2012).
Zhang, J. Y. Study on Nonlinear Seepage Law of Mining Broken Rock Mass (China University of Mining and Technology, 2019).
Li, S. C., Li, Q., Guo, J. N. System structural stability study of seepage in broken coal (rock) C . in Proceedings of the 25th National Structural Engineering Academic Conference (2016).
Li, T. Z., Ma, L. & Zhang, L. Y. Discussion about positive or negative sign of permeability indexes in non-Darcy flow of mudstone. J. Mining Saf. Eng. 2007 (04), 481–485 (2007).
Cao, Z. Z. et al. Abnormal ore pressure mechanism of working face under the influence of overlying concentrated coal pillar. J. Sci. Rep. 14 , 626. https://doi.org/10.1038/s41598-024-51148-x (2024).
Article ADS CAS Google Scholar
Qi, E. et al. Simulation of gas fracturing in reservoirs based on a coupled thermo-hydro-mechanical-damage model. J. Appl. Sci. 14 (5), 1763. https://doi.org/10.3390/app14051763 (2024).
Wang, P. S. et al. Experimental research on mechanical performance of grouting plugging material with large amount of fly ash. J. Sci. Rep. 14 , 6308. https://doi.org/10.1038/s41598-024-53623-x (2024).
Cai, Y. et al. Risk assessment and analysis of rock burst under high-temperature liquid nitrogen cooling. J. Water 16 (4), 516 (2024).
Cao, Z. Z. et al. Migration mechanism of grouting slurry and permeability reduction in mining fractured rock mass. J. Sci. Rep. 14 , 3446. https://doi.org/10.1038/s41598-024-51557-y (2024).
Xue, Y. et al. An experimental study on mechanical properties and fracturing characteristics of granite under high-temperature heating and liquid nitrogen cooling cyclic treatment. J. Geoenergy Sci. Eng. 237 , 212816. https://doi.org/10.1016/j.geoen.2024.212816 (2024).
Teng, T., Li, Z. L., Wang, Y. M., Liu, K. & Jia, W. J. Experimental and numerical validation of an effective stress-sensitive permeability model under hydromechanical interactions. J. Transp. Porous Media 151 , 449–467. https://doi.org/10.1007/s11242-023-02043-y (2024).
Download references
This research is supported by the Natural Science Foundation of Henan Province (242300421246, 222300420007), the National Natural Science Foundation of China (52004082, 52174073, 52274079, U23A20600), the Science and Technology Project of Henan Province (232102321098), the Program for the Scientific and Technological Innovation Team in Universities of Henan Province (23IRTSTHN005), the Program for Science & Technology Innovation Talents in Universities of Henan Province (24HASTIT021), the Cultivation Project of "Double first-class" Creation of Safety Discipline (AQ20240724, AQ20240738), the Young Teacher Foundation of Henan Polytechnic University(2023XQG-01, 2019XQG-08). The research work in the article is carefully supervised by Chen Zhanqing and Li Shuncai (China University of Mining and Technology).
Author information
Authors and affiliations.
International Joint Research Laboratory of Henan Province for Underground Space Development and Disaster Prevention, School of Civil Engineering, Henan Polytechnic University, Jiaozuo, 454000, Henan, China
Jia Yunlong, Cao Zhengzheng & Lin Haixiao
Henan Mine Water Disaster Prevention and Control and Water Resources Utilization Engineering Technology Research Center, Henan Polytechnic University, Jiaozuo, 454000, Henan, China
Cao Zhengzheng, Li Zhenhua, Du Feng, Huang Cunhan, Wang Wenqiang & Zhai Minglei
Collaborative Innovation Center of Coal Work Safety and Clean High Efficiency Utilization, Jiaozuo, 454000, Henan, China
You can also search for this author in PubMed Google Scholar
Contributions
J.Y.: Supervision, Writing-review and editing. C.Z.: Data curation, methodology, writing-original draft. L.Z.: Conceptualization, project administration, supervision. D.F.: Project administration, resources. H.C.: Conceptualization, writing-original draft, writing-review and editing. L.H.: Project administration, resources. W.W.: Writing-original draft. Z.M.: Conceptualization, project administration. All authors reviewed the manuscript. All authors of this article consent to publish.
Corresponding authors
Correspondence to Cao Zhengzheng , Li Zhenhua or Huang Cunhan .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Yunlong, J., Zhengzheng, C., Zhenhua, L. et al. Nonlinear evolution characteristics and seepage mechanical model of fluids in broken rock mass based on the bifurcation theory. Sci Rep 14 , 10982 (2024). https://doi.org/10.1038/s41598-024-61968-6
Download citation
Received : 14 January 2024
Accepted : 13 May 2024
Published : 14 May 2024
DOI : https://doi.org/10.1038/s41598-024-61968-6
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Fault water inrush
- Nonlinear seepage characteristics
- Bifurcation theory
- Numerical simulation
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing newsletter — what matters in science, free to your inbox daily.

IMAGES
VIDEO
COMMENTS
"The General Method of Theory-Building Research in Applied Disciplines." Advances in Developing Human Resources 4 (August 2002): 221-241; Tavallaei, Mehdi and Mansor Abu Talib. "A General Perspective on the Role of Theory in Qualitative Research." Journal of International Social Research 3 (Spring 2010); Ravitch, Sharon M. and Matthew Riggan.
A theoretical framework guides the research process like a roadmap for the study, so you need to get this right. Theoretical framework 1,2 is the structure that supports and describes a theory. A theory is a set of interrelated concepts and definitions that present a systematic view of phenomena by describing the relationship among the variables for explaining these phenomena.
A theoretical framework is a foundational review of existing theories that serves as a roadmap for developing the arguments you will use in your own work. Theories are developed by researchers to explain phenomena, draw connections, and make predictions. In a theoretical framework, you explain the existing theories that support your research ...
Theoretical Framework Example for a Thesis or Dissertation. Published on October 14, 2015 by Sarah Vinz . Revised on July 18, 2023 by Tegan George. Your theoretical framework defines the key concepts in your research, suggests relationships between them, and discusses relevant theories based on your literature review.
The theoretical framework may be rooted in a specific theory, in which case, you are expected to test the validity of an existing theory in relation to specific events, issues, or phenomena.Many social science research papers fit into this rubric. For example, Peripheral Realism theory, which categorizes perceived differences between nation-states as those that give orders, those that obey ...
A theoretical framework is an essential part of any research study or paper, as it helps to provide a theoretical basis for the research and guide the analysis and interpretation of the data. ... It demonstrates that the research is based on a solid understanding of the relevant theory and that the research questions are grounded in a clear ...
The use of theory in science is an ongoing debate in the production of knowledge. Related to qualitative research methods, a variety of approaches have been set forth in the literature using the terms conceptual framework, theoretical framework, paradigm, and epistemology.
A central topic in teaching research methods is the role of theory-both in general (Kawulich 2009) and in IS and digitalization (Gregor 2006;Truex, Duane, Jonny Holmström 2006). Theory is a ...
As we know from previous chapters, science is knowledge represented as a collection of 'theories' derived using the scientific method. In this chapter, we will examine what a theory is, why we need theories in research, the building blocks of a theory, how to evaluate theories, how can we apply theories in research, and also present illustrative examples of five theories frequently used in ...
A theoretical framework is a single formal theory. When a study is designed around a theoretical framework, the theory is the primary means in which the research problem is understood and investigated. Although theoretical frameworks tend to be used in quantitative studies, you will also see this approach in qualitative research.
A theory paper is a manuscript that seeks to develop new scientific arguments or extend existing arguments about relationships between units observed or approximated in the ... 1530) emphasized that making a theoretical contribution "usually begins with a research question, which can come from the phenomenon of interest, variations ...
Preview. One of the most crucial foundational steps in any research project surrounds understanding and choosing an appropriate theory to frame the research question. Theoretical frameworks don't just impact design, they impact how the entire study is interpreted, contextualized, and discussed. There are lots of resources about epistemologies ...
The aim of this paper is to describe and discuss how theory (a 'comprehensive explanation of some aspect of nature that is supported by a body of evidence') can inform and improve the quality and relevance of pharmacy-based research. ... Wacker JG. A definition of theory: research guidelines for different theory-building research methods in ...
Lajos Brons. This is a guide to help (my) students to write better papers (as well as better research plans and outlines). If you are a teacher, feel free to use it in any way you like (including "stealing" from it). Feedback would be highly appreciated. If you are a student and you found this guide helpful, feel free to share it with others.
A theory is essential for any research project because it gives it direction and helps prove or disprove something. Theoretical basis helps us figure out how things work and why we do certain things. Theoretical research lets you examine and discuss a research object using philosophical ideas and abstract theoretical structures.
Some theory application papers require that you choose your own case (an empirical phenomenon, trend, situation, etc.), whereas others specify the case for you (e.g., ask you to apply conflict theory to explain some aspect of globalization described in an article).
Preview. One of the most crucial foundational steps in any research project surrounds understanding and choosing an appropriate theory to frame the research question. Theoretical frameworks don't just impact design, they impact how the entire study is interpreted, contextualized, and discussed. There are lots of resources about epistemologies ...
Theory production has been a central focus of management research for decades, mostly because theory legitimizes both management research and, ... Similarly, as part of its stated objectives, the Strategic Management Journal "seeks to publish papers that . . . develop and/or test theory." Another example is the Journal of Management, ...
Preliminary pages: These will normally include the Certificate of Research, an abstract, a title page (according to the format specified in the general section), and a table of contents, which includes the chapters of the paper and also the materials in the Appendices. Abstract: A short summary of the topic and the main findings (max. 100--150 ...
Figure 1. Research design framework: summary of the interplay between the essential grounded theory methods and processes. Grounded theory research involves the meticulous application of specific methods and processes. Methods are 'systematic modes, procedures or tools used for collection and analysis of data'. 25 While GT studies can ...
Definition: Theory is a set of ideas or principles used to explain or describe a particular phenomenon or set of phenomena. The term "theory" is commonly used in the scientific context to refer to a well-substantiated explanation of some aspect of the natural world that is based on empirical evidence and rigorous testing.
This paper explores theories of motivation, including instinct theory, arousal theory, incentive theory, intrinsic theory, extrinsic theory, the ARCS model, self-determination theory, expectancy-value theory, and goal-orientation theory. Each theory is described in detail, along with its key concepts, assumptions, and implications for behavior.
Learn how cognitive theories explain different aspects of learning and inform classroom practices in this PDF article on ResearchGate.
Building upon the Social Fact theory and Social Impact theory, this paper presents an innovative exploration of how collective consciousness and conformity behavior impact ... Gong, Z., & Han, X. (2016). Research on the Public's Intention of Sustainable Use of Government Websites based on Grounded Theory. Journal of Information, 35(05): 180-187
The aim of the current paper is to demonstrate the key aspects of Piaget's cognitive development theory and evaluate Piaget's idea based on later studies. Asian Institute of Research Educati on ...
The Journal of Creative Behavior is the original journal devoted specifically to creativity research, publishing papers on theory & applications of creativity. ABSTRACT This paper expands upon the invitation to rethink how psychology has constructed knowledge, theories, and research while analyzing the epistemological foundations of educational ...
Research; Preprints; ... (1982), and Frank et al. (1987), the latter using copula theory. However, though they obtain the same bounds, they make different assertions concerning their sharpness. In addition, their solutions leave some open problems in the case when the given marginal distribution functions are discontinuous. ... ArXiv Paper 2405 ...
Semantic Scholar extracted view of "Theory and Explanation in GeographyTheory and Explanation in GeographyBy Henry Wai-chung YeungHoboken, NJ: John Wiley and Sons, 2024." ... Semantic Scholar's Logo. Search 218,401,693 papers from all fields of science. Search. Sign In Create Free Account. DOI: 10.1080 ... AI-powered research tool for ...
Therefore, this paper adopts D-S evidence theory to make a decision on the degree of the creeping of AFC. ... The research framework proposed in this paper can provide research ideas for engineering problems in the production process of other industries. If the virtual interface is reserved in the established virtual scene, the virtual real two ...
The research results are of great significance to enrich the theory of fault water inrush in coal mine, and to reveal the disastrous mechanism of fault water inrush and guide its prevention and ...