Public repository of content for classes I teach at PSU
Cs 493/593: digital forensics.
Location : FAB 46 (MW 16:40-18:30)
Instructor : D. Kevin McGrath
- PDX username: dmcgrath
- Location: FAB 120-15 and Zoom (PW: PSUSecure)
- Monday: 10:00 - 11:30 (FAB 120-15 only)
- Tuesday: 11:00 - 12:00 (Zoom only)
- Tuesday: Code Party! 18:30 - 22:00 (FAB 86-01/88-03)
- Wednesday: 10:00 - 11:30 (FAB 120-15 only) – except first and third Wednesdays of the month due to faculty meetings.
- Thursday: 09:30 - 11:30 (Zoom only)
Recorded Lectures : These will be made available via MediaSpace . Login required.
- Mobile forensics – a brief introduction to mobile forensics
- tmux config
- Technical Writing
- VM Setup on Windows
- VM Setup on macOS
- Ubuntu configuration
- Powershell profile
- Networking Fundamentals
- SSH Tunnel for Windows RDP
- Introduction
- Case Studies
Each homework will build on the previous assignment. These aren’t your typical “write answers to questions” type assignments, but rather are intended to be more hands-on. We will be adding to, modifying, or otherwise doing something to the VM environment to enable us to do something else. The first assignment will be to get the VM environment set up and configured. Subsequent assignments will build on this.
All work will be submitted via MarkDown documents within an internal gitlab repo. You will be using this repo for the rest of the term. This repo exists on the CECS intranet. You will need to add myself and the TA to this repo as Developers. Grades and feedback will be done via a merge request from the TA.
The grader for this class is Teo Coffman. His PDX username is theodos .

Assignments
- Final Project
Useful links for learning
- tmux cheatsheet
- Linux Handbook on tmux
- The GNU make manual
- Managing projects with make
- The chmod calculator
- The Python tutor
- The Linux Command Line (Direct PDF link )
- Adventures with the Linux Command Line
- The Linux Development Platform
- gdb tutorial
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
Digital.Forensics.Final.Report.pdf
Latest commit, file metadata and controls.

Week 21 Homework Digital Forensics
In this week’s assignment, you will continue to work with your group to continue the final report you began in class. The instructions are included here again for reference. There is also a bonus activity aimed to sharpen your skills in locating and identifying data in a forensic image.
Just as in a real-world scenario, you will complete a final report to present your findings. You will work with your team to fill out the report.
- The final report should be submitted as the homework deliverable for this week. Everything your group has completed in class should be included. What you do not finish today can be continued at home.
- Use the Final Case Report Google Doc template to complete your report. Make a copy and be sure that each student has editing access. This will allow everyone in the group to access and work on the document at the same time.
- Each group will turn in one completed report to be graded.
- iPhone Forensics – Important Files and Databases
Lab Environnement
- This homework will use the Digital Forensics – Autopsy lab in Kali Linux.
- You will find the tracy-phone-2012-07-15.final.E01 file located in the /corpus directory in Autopsy.
Instructions
You’ve examined and documented quite a bit of information from the iPhone image file. Now you will use that documentation to build a final report.
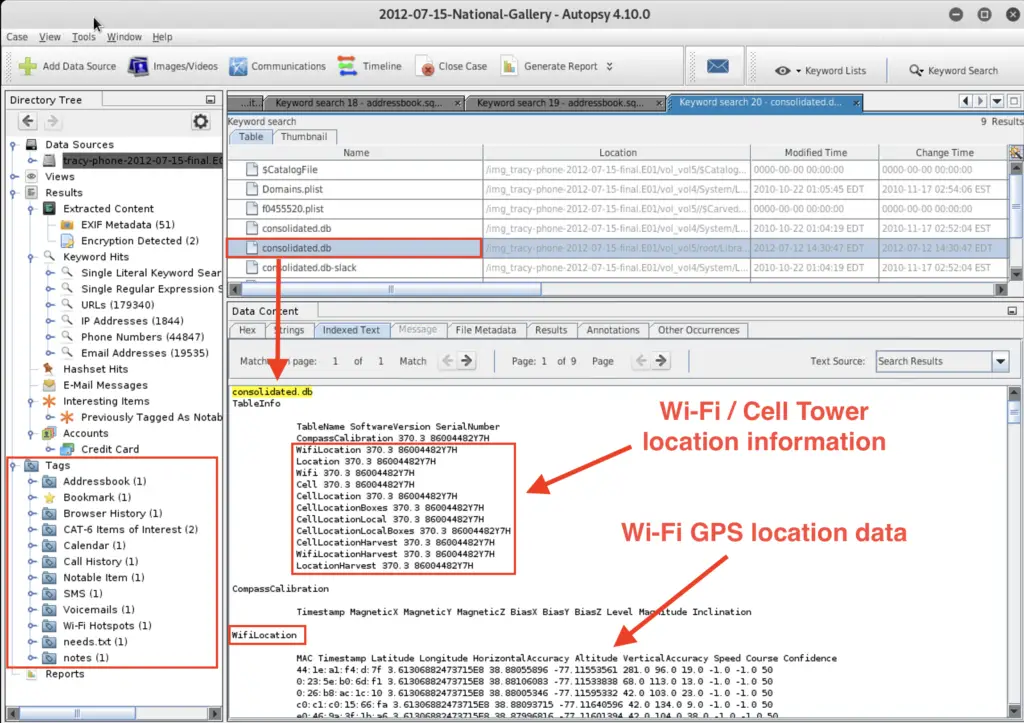
- Location Information Worksheet Your group can look for WiFi and GPS info the following directories:
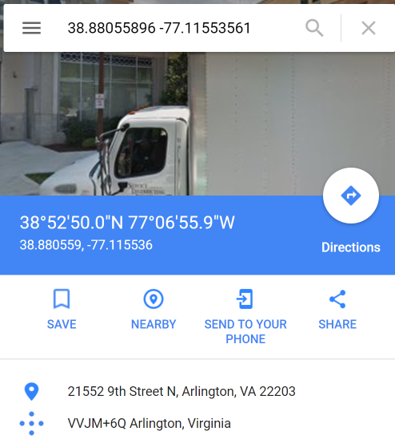
- Note: Input GPS coordinates into Google Maps to see the locations.
- Refer to the image below as an example:
- Find information related to WiFi and cell tower location information in consolidated.db .
- You will rely on the Locations Information and Correspondence Evidence Worksheets you’ve completed so far. Additionally, you can use the iPhone Forensics – Important Files and Databases resource to analyze and find more information to support your case, such as Voicemails and notes from the Notepad iPhone application.
- For example, Autopsy, the operating system (Kali Linux), text editors (Nano), etc.
- When including pictures from the iPhone, please use the time stamp of the Created time from autopsy.
Submission Guidelines
- Each group should submit one version of the completed Final Case Report document.
Bonus Assignment: Russian Tea Room
The goal of this assignment is to sharpen your skills in locating and identifying data in a forensic image.
- These skills are important for tasks related to locating and decoding data, such as executable code or malicious documents embedded in images or network logs.
Scenario: The Case of the Little Russian Tea Room
- There was a fire at the Little Russian Tea Room restaurant last week, and the only thing recovered was a hard drive. To start rebuilding the business, the restaurant hired you as a forensics investigator to look at the disk image and reconstruct the menu.
- You’ll be working with an EnCase image of the hard drive.
- Luckily, the English and Russian menu are both in the hard drive image. However, only the English menu and two sections of the Russian menu are readable. Your must decode several sections of the Russian menu.
The strings in the EnCase image are hex and represent the UTF-16 format. You’ll need to be familiar with hex and UTF-16 encoding and decoding for this activity.
- Review this Unicode Tutorial and the practice exercises. This review will help you locate the menus on the hard drive image.
Below are the files required to complete the assignment:
- RussianTeaRoom.zip (560 KB): The Autopsy case file and Encase image file.
- menu.pdf (56.0 KB): The Little Russian Tea Room menu.
- Google Sheets: Russian Team Room
- Unicode-Tutorial.md : Short Unicode tutorial.
The files can also be found in the /root/autopsy-files/homework directory in Autopsy.
Your task is to find, decode, and document six of the menus from the hard drive image using the Unicode Cyrillic and Latin character (cipher) set.
- Open the RussianTeaRoom folder and select RussianTeaRoom.aut .
- Add the Russian-TeamRoom.E01 EnCase image file to the case.
- This is a sample of the hex data in the Autopsy RussianTeaRoom case file:
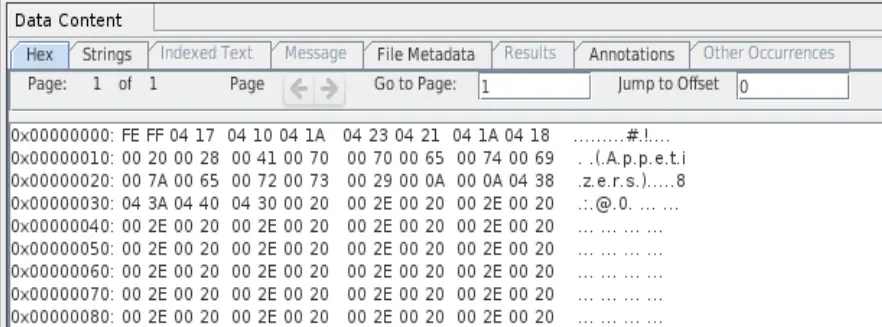
- 2 Use Google Sheets: Russian Team Room to document the remaining information from the EnCase image for the investigation.
- Hint: There may be multiple locations for the same file.
- Pancakes (Menu #3)
- Hint: Use the Hex and String tabs in Data Content window in Autopsy to view the data.
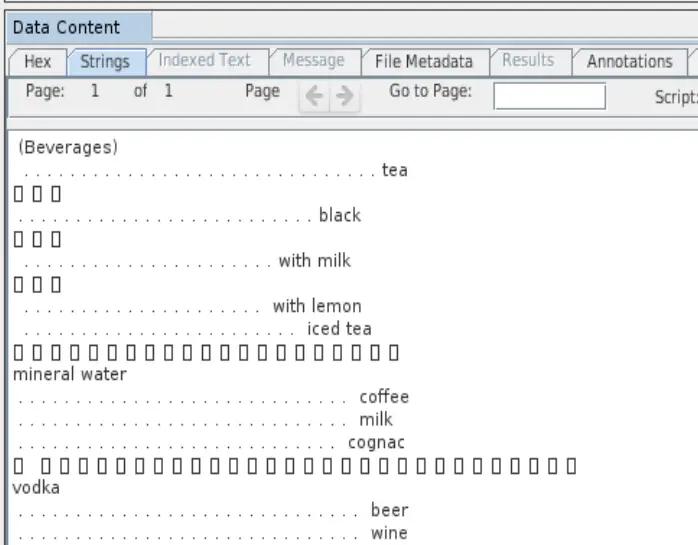
- For example: 0x00000010
- For example: 00 42 00 65 00 76 00 65 00 72 00 61 00 67 00 65 00 73
- For example: \u0042\u0065\u0076\u0065\u0072\u0061\u0067\u0065\u0073
- Submit the completed Google Sheets: Russian Team Room file.
Important Note for Certification Prep Week
- In Certification Prep Week, Day 1 you will be using CertMaster Practice in class.
- Make sure you have access to the tool and should be ready to use it during this unit.

Important Note for Career Prep Week
- After Certification Prep Week, we will move on to Career Prep. You will take a closer look at the cyber career landscape and will learn practical tips on how to prepare for the job hunt, hone their resume, craft their LinkedIn profile, and ace the behavioral and technical interviews.
- Please come to class with a digital copy of your resume which you will be working on and sharing with your fellow peers.
- You must also have a LinkedIn profile set up as well. If you did not set up a LinkedIn account during pre-work, please make sure you do so prior to Career Prep week.
© 2020 Trilogy Education Services, a 2U Inc Brand. All Rights Reserved.
Week 21 Homework Solution: Digital Forensics
Refer to the following solution files for the homework worksheets:
- Week 21 Homework Solution: Digital Forensics – Final Report
© 2020 Trilogy Education Services, a 2U, Inc. brand. All Rights Reserved.

WordPress Social Login and Register Authentication Bypass

Wireless Pentesting Cheat Sheet

Kali Linux Cheat Sheet

Awesome Forensics

Awesome Event IDs

Agile Security Operations

11488/11688/11788 — Spring 2022
Concepts in Digital Multimedia and Cyber Forensics

With new AI-based technologies that power almost all activities in the digital world, cybercrime is on an unprecedented increase. Forensics is the science of tracing causes, methods and perpetrators from evidence, once a crime has been committed. This course will teach you some of the key technologies that are being used to track cybercriminals.
Instructor and TAs
Instructor: Rita Singh ([email protected]) Ian Lane ([email protected])
TAs: Hira Dhamyal ([email protected]) Ankit Shah ([email protected])\
IMPORTANT INFORMATION:
This semester’s version of the course has the following desired (but not enforced) prerequisites : 15744 (computer networks) or 11-775 (large scale multimedia analysis) or 18-491/18-691 (digital signal processing) or 18290 (signals and systems). if you have questions about these prerequisites or would like to find out how to navigate this course without them, please email the instructors [email protected] or [email protected]. the homeworks and quizzes may not be administered as planned this semester, due to serious setbacks. they may be replaced entirely by periodic oral exams or projects. if you are planning on taking this course, please be prepared for this change., basic course structure.
There will be 14 weeks of lectures. A different forensic subarea will be covered each week in 2 lectures of 1 hr 20 mins each. There will be one quiz at the end of each week (released Thursday midnight, due Sunday midnight) and 4 homeworks in all. Each homework will be due within 2 weeks from the date of release.
Schedule of lectures (The order of topics, is tentative, and may change later):
Week 1: Introduction Week 2: Network Forensics Week 3: Dark Web Forensics Week 4: Computer Forensics Week 5: Artificial Intelligence, Machine Learning and Deep Learning (+ Exams) Week 6: Digital Fingerprint Analysis Week 7: Text and Social Media Forensics Week 8: Audio Forensics Week 9: Image Forensics Week 10: Video Forensics Week 11: Steganography Week 12: Cryptography Week 13: DeepFakes: generation and tracking Week 14: Class Presentations and Exams
A more comprehensive syllabus can be found here .
The weekly lectures will be slide-based. Research papers, (accessible) textbook chapters and notes will be provided as links where necessary. Slides for each class will be uploaded on Canvas after each class, on the same day as the class. Homeworks will be released in class, and explained in a 30 minute recitation at the end of the corresponding class. Attendance is expected and recommended. Lectures will be recorded.
Enrollment requirements
You must know programming (preferably Python). Basic skills in maths, statistics and probability are expected.

COMMENTS
Week 21 Homework: Digital Forensics. In this week's assignment, you will continue to work with your group to continue the final report you began in class. The instructions are included here again for reference. There is also a bonus activity aimed to sharpen your skills in locating and identifying data in a forensic image.
This weeks homework we performed a digital forensic analysis of an Iphone's data. This homework was based on the National Gallery Exercise, however rather than looking at the overall scenario, we focused specifically on Tracy's IPhone, and how it related to the stamp theft. Week 21 Homework
Contribute to Lucasdomanski1984/Week-21-Homework-Digital-Forensics development by creating an account on GitHub.
Shell 46.7%. Python 46.0%. PHP 7.3%. University of Richmond Cyber Security Boot Camp. Contribute to Jprosser91/Boot-Camp development by creating an account on GitHub.
Forensic images were collected by me from an image of the iPhone 3G on August 14, 2021, in Markham, Ontario. The forensic image files of the iPhone 3G, tracy-phone-2012-07-15- final.E01 can be viewed as an exact snapshot of the data present on the iPhone 3G during its acquisition. The tools used in our findings consisted of using the following:
Published Oct 29, 2021. + Follow. In this week's assignment, you will continue to work with your group to continue the final report you began in class. The instructions are included here again ...
Week 21 Homework Digital Forensics - Penetration Testing Tools, ML and Linux Tutorials. In this week's assignment, you will continue to work with your group to continue the final report you began in class. The instructions are included here again. 1:08 PM · Oct 29, 2021
Location Information . Artifact # Timestamp. Header Information. Body. Map Screenshot. McMullin real estate. 2012-06-07 03:04:13 AWST. To 2012-07-13 02:30:47 AWST
View Final_Report_week_21.docx from FIT 2093 at Monash University. CASE REPORT NATIONAL GALLERY DC Tracy's iPhone [2012-07-15-National-Gallery] 2012-07-15-National-Gallery Digital Forensic AI Homework Help
CS 493/593: Digital Forensics. Location: FAB 46 (MW 16:40-18:30) Instructor: D. Kevin McGrath. PDX username: dmcgrath; Office hours: Location: FAB 120-15 and Zoom (PW: PSUSecure) Times: Monday: 10:00 - 11:30 (FAB 120-15 only) ... Each homework will build on the previous assignment. These aren't your typical "write answers to questions ...
Contribute to Wba-01/Week-21-Homework-Digital-Forensics development by creating an account on GitHub.
Topic Week Starting 1 Introduction to Digital Forensics 2/1/21 2 Acquiring Evidence 2/8/21 3 Filesystems 2/22/21 4 Open-Source Forensic Tools 3/1/21 ... 7 Programming for Digital Forensics 3/22/21 8 Application & Database Forensics 3/29/21 . IMPORTANT DATES January 28, 2021 - Spring 2021 semester begins February 2, 2021 - First class meeting
This homework will use the Digital Forensics - Autopsy lab in Kali Linux. You will find the tracy-phone-2012-07-15.final.E01 file located in the /corpus directory in Autopsy. Instructions. You've examined and documented quite a bit of information from the iPhone image file. Now you will use that documentation to build a final report.
Week 21 Homework Digital Forensics In this week's assignment, you will continue to work with your group to continue the final report you began in class. The instructions are included here again
Forensics is traditionally a reaction to an event or in response to a request for support or refutation of an interpretation of a situation. Memory-based forensics, or live forensics is a proactive activity designed to audit current activity or events. Helpful to catch bad actors red-handed, and to aid in developing system and network ...
This semesters version of the course has the following prerequisites : 15744 (Computer Networks) OR 11-775 (Large Scale Multimedia Analysis) OR 18-491/18-691 (Digital Signal Processing) OR 18290 (Signals and Systems). If you have questions about these prerequisites please email the instructors [email protected] or [email protected].
This website is the companion to the Digital Forensics Workbook, which contains over 60 hands-on activities using over 40 different tools for digital forensic examiners.From this site readers of the book can download data sets and receive updates to the book. The Digital Forensics Workbook was written for those, who are seeking hands-on practice acquiring and analyzing digital artifacts from ...
Each homework will be due within 2 weeks from the date of release. Schedule of lectures (The order of topics, is tentative, and may change later): Week 1: Introduction Week 2: Network Forensics Week 3: Dark Web Forensics Week 4: Computer Forensics Week 5: Artificial Intelligence, Machine Learning and Deep Learning (+ Exams) Week 6: Digital ...
Cybersecurity Module 21 - iPhone Forensic Image Important Databases and Files GETTING STARTED To view the files in the Encase Image: 1. Locate Results in the left-hand navigation. 2. Double-click Encryption Detected (1). 3. In the Listing pane, click documents.zip. 4. Expand vol5. File Name Description File Location AddressBook.sqlitedb Contact information and personal data like name, email ...
Week 21 Homework Digital Forensics #DigitalForensics #iPhoneForensics #KaliLinux #DFIR #D3pak https://reconshell.com/week-21-homework-digital-forensics/
Comunidad de Programadores y Desarrolladores Web - KolMitE