
- Calculators
- Swot Analysis
- Pestle Analysis
- Five Forces Analysis
- Organizational Structure
- Copywriting
- Research Topics
- Student Resources

Services We Provide

Resources We Provide

Login / Register

- 15 Latest Networking Research Topics for Students
Comparative analysis between snort and suricata IDS software(s)
Description of the topic
The main focus of this research is to conduct a comparative analysis between Snort and Suricata software to determine which IDS software can provide better performance. There are various IDS software(s) available that can be used by organizations but it is difficult to identify which one is best (Aldarwbi et al., 2022). Different organizational structures are often facing problems while setting up an IDS system which results in false positives and intrusions. Through this research, it can be identified which IDS software is better and what secure configuration is required to detect intrusions (Waleed et al., 2022).
Research objectives
- To evaluate Snort and Suricata IDS software(s) to determine the most optimal one.
- To identify the false positive rate of Snort and Suricata on the networked environment.
Research questions
RQ1: Which IDS software can perform better on the production network in terms of performance, security, scalability and reliability?
RQ2: What different ways can be followed to deal with false positive problems in IDS technology?
Research methodology
The given research objectives and research questions can be addressed using quantitative research methodology where an experimental approach can be followed. For the given topic, both Snort and Suricata IDS systems should be configured and tested against different attacks. Depending on the findings, it can be analyzed which IDS software can perform better in terms of performance and security (Shuai & Li, 2021).
- Aldarwbi, M.Y., Lashkari, A.H. and Ghorbani, A.A. (2022) “The sound of intrusion: A novel network intrusion detection system,” Computers and Electrical Engineering , 104, p. 108455.
- Shuai, L. and Li, S. (2021) “Performance optimization of Snort based on DPDK and Hyperscan,” Procedia Computer Science , 183, pp. 837-843.
- Waleed, A., Jamali, A.F. and Masood, A. (2022) “Which open-source ids? Snort, Suricata or Zeek,” Computer Networks , 213, p. 109116.
Role of honeypots and honey nets in network security
Network Security has become essential nowadays and there is a need for setting up robust mechanisms to maintain confidentiality and integrity (Feng et al., 2023). Due to the number of security mechanisms available, organizations found it hard to finalize and implement them on their network. For example, honey pots and honeynet approaches look almost the same and have the same purpose but work differently. Under this research topic, the configuration of honeynets and honeypots can be done to check which one can perform better security in terms of trapping cyber attackers. The entire implementation can be carried out in the cloud-based instance for improved security and it can be identified which type of honey pot technology must be preferred (Maesschalck et al., 2022).
- To set up a honey pot system using Open Canary on the virtual instance to protect against cyber attackers.
- To set up a honeynet system on the virtual instance to assure protection is provided against malicious attackers.
- To test honeypots and honeynets by executing DDoS attacks to check which can provide better security.
RQ1: Why is there a need for using honeypots over honey pots in a production networked environment?
RQ2: What are the differences between cloud-based and local honey pot systems for endpoint protection?
This research can be carried out using the quantitative method of research. At the initial stage, the implementation of honeypots and honeypots can be done on the virtual instance following different security rules. Once the rules are applied, the testing can be performed using a Kali Linux machine to check whether honey pots were effective or honeynets (Gill et al., 2020).
- Feng, H. et al. (2023) “Game theory in network security for Digital Twins in industry,” Digital Communications and Networks [Preprint].
- Gill, K.S., Saxena, S. and Sharma, A. (2020) “GTM-CSEC: A game theoretic model for cloud security based on ids and Honeypot,” Computers & Security , 92, p. 101732
- Maesschalck, S. et al. (2022) “Don’t get stung, cover your ICS in honey: How do honeypots fit within industrial control system security,” Computers & Security , 114, p. 102598.
How do malware variants are progressively improving?
This research can be based on evaluating how malware variants are progressively improving and what should be its state in the coming future. Malware is able to compromise confidential user’s information assets which is why this research can be based on identifying current and future consequences owing to its improvements (Deng et al., 2023). In this field, there is no research work that has been carried out to identify how malware variants are improving their working and what is expected to see in future. Once the evaluation is done, a clear analysis can also be done on some intelligent preventive measures to deal with dangerous malware variants and prevent any kind of technological exploitation (Tang et al., 2023).
- To investigate types of malware variants available to learn more about malware's hidden features.
- To focus on future implications of malware executable programs and how they can be avoided.
- To discuss intelligent solutions to deal with all malware variants.
RQ1: How do improvements in malware variants impact enterprises?
RQ2: What additional solutions are required to deal with malware variants?
In this research, qualitative analysis can be conducted on malware variants and the main reason behind their increasing severity. The entire research can be completed based on qualitative research methodology to answer defined research questions and objectives. Some real-life case studies should also be integrated into the research which can be supported by the selected topic (Saidia Fasci et al., 2023).
- Deng, H. et al. (2023) “MCTVD: A malware classification method based on three-channel visualization and deep learning,” Computers & Security , 126, p. 103084.
- Saidia Fasci, L. et al. (2023) “Disarming visualization-based approaches in malware detection systems,” Computers & Security , 126, p. 103062.
- Tang, Y. et al. (2023) “BHMDC: A byte and hex n-gram based malware detection and classification method,” Computers & Security , p. 103118.
Implementation of IoT - enabled smart office/home using cisco packet tracer
The Internet of Things has gained much more attention over the past few years which is why each enterprise and individual aims at setting up an IoT network to automate their processes (Barriga et al., 2023). This research can be based on designing and implementing an IoT-enabled smart home/office network using Cisco Packet Tracer software. Logical workspace, all network devices, including IoT devices can be used for preparing a logical network star topology (Elias & Ali, 2014). To achieve automation, the use of different IoT rules can be done to allow devices to work based on defined rules.
- To set up an IoT network on a logical workspace using Cisco Packet Tracer simulation software.
- To set up IoT-enabled rules on an IoT registration server to achieve automation (Hou et al., 2023).
RQ: Why is the Cisco packet tracer preferred for network simulation over other network simulators?
At the beginning of this research, a quantitative research methodology can be followed where proper experimental set-up can be done. As a packet tracer is to be used, the star topology can be used to interconnect IoT devices, sensors and other network devices at the home/office. Once a placement is done, the configuration should be done using optimal settings and all IoT devices can be connected to the registration server. This server will have IoT rules which can help in achieving automation by automatically turning off lights and fans when no motion is detected (Baggan et al., 2022).
- Baggan, V. et al. (2022) “A comprehensive analysis and experimental evaluation of Routing Information Protocol: An Elucidation,” Materials Today: Proceedings , 49, pp. 3040–3045.
- Barriga, J.A. et al. (2023) “Design, code generation and simulation of IOT environments with mobility devices by using model-driven development: Simulateiot-Mobile,” Pervasive and Mobile Computing , 89, p. 101751.
- Elias, M.S. and Ali, A.Z. (2014) “Survey on the challenges faced by the lecturers in using packet tracer simulation in computer networking course,” Procedia - Social and Behavioral Sciences , 131, pp. 11–15.
- Hou, L. et al. (2023) “Block-HRG: Block-based differentially private IOT networks release,” Ad Hoc Networks , 140, p. 103059.
Comparative analysis between AODV, DSDV and DSR routing protocols in WSN networks
For wireless sensor networks (WSN), there is a major need for using WSN routing rather than performing normal routines. As WSN networks are self-configured, there is a need for an optimal routing protocol that can improve network performance in terms of latency, jitter, and packet loss (Luo et al., 2023). There are often various problems faced when WSN networks are set up due to a lack of proper routing protocol selection. As a result of this, severe downtime is faced and all links are not able to communicate with each other easily (Hemanand et al., 2023). In this research topic, the three most widely used WSN routing protocols AODV, DSDV and DSR can be compared based on network performance. To perform analysis, three different scenarios can be created in network simulator 2 (Ns2).
- To create three different scenarios on ns2 software to simulate a network for 1 to 100 seconds.
- To analyze which WSN routing is optimal in terms of network performance metrics, including latency, jitter and packet loss.
- To use CBR and NULL agents for all wireless scenarios to start with simulation purposes.
RQ: How do AODV, DSR and DSDV routing protocols differ from each other in terms of network performance?
This research can be carried out using a quantitative research method. The implementation for the provided research topic can be based on Ns2 simulation software where three different scenarios can be created (AODV, DSDV and DSR). For each scenario, NULL, CSR and UDP agents can be done to start with simulation for almost 1 to 100 seconds. For all transmissions made during the given time, network performance can be checked to determine which routing is best (Mohapatra & Kanungo, 2012).
- Human and, D. et al. (2023) “Analysis of power optimization and enhanced routing protocols for Wireless Sensor Networks,” Measurement: Sensors , 25, p. 100610. Available at: https://doi.org/10.1016/j.measen.2022.100610.
- Luo, S., Lai, Y. and Liu, J. (2023) “Selective forwarding attack detection and network recovery mechanism based on cloud-edge cooperation in software-defined wireless sensor network,” Computers & Security , 126, p. 103083. Available at: https://doi.org/10.1016/j.cose.2022.103083.
- Mohapatra, S. and Kanungo, P. (2012) “Performance analysis of AODV, DSR, OLSR and DSDV routing protocols using NS2 Simulator,” Procedia Engineering , 30, pp. 69–76. Available at: https://doi.org/10.1016/j.proeng.2012.01.835.
Securing wireless network using AAA authentication and WLAN controller
Wireless networks often face intrusion attempts due to insecure protocols and sometimes open SSIDs. As a result of this, man-in-the-middle and eavesdropping attacks become easier which results in the loss of confidential information assets (Sivasankari & Kamalakkannan, 2022). When it comes to managing networks in a large area, there are higher chances for attacks that enable cyber attackers in intercepting ongoing communication sessions. However, there is currently no research conducted where the use of AAA authentication has been done with WLAN controllers to make sure a higher level of protection is provided (Nashwan, 2021). The proposed research topic can be based on securing wireless networks with the help of AAA authentication and WLAN controllers. The use of AAA authentication can be done to set up a login portal for users whilst the WLAN controller can be used for managing all wireless access points connected to the network (Nashwan, 2021).
- To set up AAA authentication service on the wireless network simulated on Cisco Packet Tracer for proper access control.
- To set up a WLAN controller on the network to manage all wireless access points effortlessly.
- To use WPA2-PSK protocol on the network to assure guest users are only able to access wireless networks over a secure protocol.
RQ1: What additional benefits are offered by AAA authentication on the WLAN networks?
RQ2: Why are wireless networks more likely to face network intrusions than wired networks?
This research topic is based on the secure implementation of a wireless LAN network using a Cisco packet tracer. Hence, this research can be carried out using a quantitative research method. The implementation can be carried out using AAA authentication which can assure that access control is applied for wireless logins. On the other hand, a WLAN controller can also be configured which can ensure that all WAPs are managed (ZHANG et al., 2012).
- Nashwan, S. (2021) “AAA-WSN: Anonymous Access Authentication Scheme for wireless sensor networks in Big Data Environment,” Egyptian Informatics Journal , 22(1), pp. 15–26.
- Sivasankari, N. and Kamalakkannan, S. (2022) “Detection and prevention of man-in-the-middle attack in IOT network using regression modeling,” Advances in Engineering Software , 169, p. 103126.
- ZHANG, J. et al. (2012) “AAA authentication for Network mobility,” The Journal of China Universities of Posts and Telecommunications , 19(2), pp. 81-86.
OWASP's approach to secure web applications from web application exploits
The research can revolve around the development of web applications by considering OWASP's top 10 rules. Usually, web applications are deployed by organizations depending on their requirements and these applications are vulnerable to various exploits, including injection, broken authentication and other forgery attacks (Poston, 2020). Identifying every single vulnerability is difficult when reference is not taken and often organizations end up hosting a vulnerable server that leads to privacy issues and compromises confidential information easily. In this research, OWASP's top 10 approaches can be followed to develop a secure web application that can be able to protect against top web application exploits. This approach is based on emphasizing severe and minor vulnerabilities which must be patched for protecting against web application attacks (Deepa & Thilagam, 2016).
- The first objective can be setting up an insecure web application on the cloud environment which can be exploited with different techniques.
- The second objective can be to consider all techniques and procedures provided by OWASP's top 10 methodologies.
- The last objective can be applying all fixes to insecure web applications to make them resistant to OWASP top 10 attacks (Sonmez, 2019).
RQ1: What are the benefits of using OWASP's top 10 approaches to harden web applications in comparison to other security approaches?
The research methodology considered for this research project can be quantitative using an experimental approach. The practical work can be done for the selected topic using AWS or the Azure cloud platform. Simply, a virtual web server can be configured and set up with a secure and insecure web application. Following OWASP's top 10 techniques and procedures, the web application can be secured from possible attacks. In addition, insecure applications can also be exploited and results can be evaluated (Applebaum et al., 2021).
- Applebaum, S., Gaber, T. and Ahmed, A. (2021) “Signature-based and machine-learning-based web application firewalls: A short survey,” Procedia Computer Science , 189, pp. 359–367. Available at: https://doi.org/10.1016/j.procs.2021.05.105.
- Deepa, G. and Thilagam, P.S. (2016) “Securing web applications from injection and logic vulnerabilities: Approaches and challenges,” Information and Software Technology , 74, pp. 160–180. Available at: https://doi.org/10.1016/j.infsof.2016.02.005.
- Poston, H. (2020) “Mapping the owasp top Ten to the blockchain,” Procedia Computer Science , 177, pp. 613-617. Available at: https://doi.org/10.1016/j.procs.2020.10.087.
- Sonmez, F.Ö. (2019) “Security qualitative metrics for Open Web Application Security Project Compliance,” Procedia Computer Science , 151, pp. 998-1003. Available at: https://doi.org/10.1016/j.procs.2019.04.140.
Importance of configuring RADIUS (AAA) server on the network
User authentication has become significant nowadays as it guarantees that a legitimate user is accessing the network. But a problem is faced when a particular security control is to be identified for authentication and authorization. These controls can be categorized based on mandatory access controls, role-based access control, setting up captive portals and many more. Despite several other security controls, one of the most efficient ones is the RADIUS server (SONG et al., 2008). This server can authenticate users on the network to make sure network resources are accessible to only legal users. This research topic can be based on understanding the importance of RADIUS servers on the network which can also be demonstrated with the help of the Cisco Packet Tracer. A network can be designed and equipped with a RADIUS server to ensure only legal users can access network resources (WANG et al., 2009).
- To configure RADIUS (AAA) server on the network which can be able to authenticate users who try to access network resources.
- To simulate a network on a packet tracer simulation software and verify network connectivity.
RQ1: What are other alternatives to RADIUS (AAA) authentication servers for network security?
RQ2: What are the common and similarities between RADIUS and TACACS+ servers?
As a logical network is to be designed and configured, a quantitative research methodology can be followed. In this research coursework, a secure network design can be done using a packet tracer network simulator, including a RADIUS server along with the DMZ area. The configuration for the RADIUS server can be done to allow users to only access network resources by authenticating and authorizing (Nugroho et al., 2022).
- Nugroho, Y.S. et al. (2022) “Dataset of network simulator related-question posts in stack overflow,” Data in Brief , 41, p. 107942.
- SONG, M., WANG, L. and SONG, J.-de (2008) “A secure fast handover scheme based on AAA protocol in Mobile IPv6 Networks,” The Journal of China Universities of Posts and Telecommunications , 15, pp. 14-18.
- WANG, L. et al. (2009) “A novel congestion control model for interworking AAA in heterogeneous networks,” The Journal of China Universities of Posts and Telecommunications , 16, pp. 97-101.
Comparing mod security and pF sense firewall to block illegitimate traffic
Firewalls are primarily used for endpoint security due to their advanced features ranging from blocking to IDS capabilities and many more. It is sometimes challenging to identify which type of firewall is best and due to this reason, agencies end up setting up misconfigured firewalls (Tiwari et al., 2022). This further results in a cyber breach, destroying all business operations. The research can be emphasizing conducting a comparison between the two most widely used firewalls i.e. Mod Security and pF sense. Using a virtualized environment, both firewalls can be configured and tested concerning possible cyber-attacks (Lu & Yang, 2020).
- To use the local environment to set up Mod security and pF sense firewall with appropriate access control rules.
- To test both firewalls by executing distributed denial of service attacks from a remote location.
- To compare which type of firewall can provide improved performance and robust security.
RQ: How do Mod security and pF sense differ from each other in terms of features and performance?
The practical experimentation for both firewalls can be done using a virtualized environment where two different machines can be created. Hence, this research can be carried out using a quantitative research method . The first machine can have Mod security and the second machine can have pF sense configured. A new subnet can be created which can have these two machines. The third machine can be an attacking machine which can be used for testing firewalls. The results obtained can be then evaluated to identify which firewall is best for providing security (Uçtu et al., 2021).
- Lu, N. and Yang, Y. (2020) “Application of evolutionary algorithm in performance optimization of Embedded Network Firewall,” Microprocessors and Microsystems , 76, p. 103087.
- Tiwari, A., Papini, S. and Hemamalini, V. (2022) “An enhanced optimization of parallel firewalls filtering rules for scalable high-speed networks,” Materials Today: Proceedings , 62, pp. 4800-4805.
- Uçtu, G. et al. (2021) “A suggested testbed to evaluate multicast network and threat prevention performance of Next Generation Firewalls,” Future Generation Computer Systems , 124, pp. 56-67.
Conducting a comprehensive investigation on the PETYA malware
The main purpose of this research is to conduct a comprehensive investigation of the PETYA malware variant (McIntosh et al., 2021). PETYA often falls under the category of ransomware attacks which not only corrupt and encrypt files but can compromise confidential information easily. Along with PETYA, there are other variants also which lead to a security outage and organizations are not able to detect these variants due to a lack of proper detection capabilities (Singh & Singh, 2021). In this research, a comprehensive analysis has been done on PETYA malware to identify its working and severity level. Depending upon possible causes of infection of PETYA malware, some proactive techniques can also be discussed (Singh & Singh, 2021). A separation discussion can also be made on other malware variants, their features, and many more.
- The main objective of this research is to scrutinize the working of PETYA malware because a ransomware attack can impact the micro and macro environment of the organizations severely.
- The working of PETYA malware along with its source code can be reviewed to identify its structure and encryption type.
- To list all possible CVE IDs which are exploited by the PETYA malware.
RQ1: How dangerous is PETYA malware in comparison to other ransomware malware?
This research can be based on qualitative research methodology to evaluate the working of PETYA malware from various aspects, the methodology followed and what are its implications. The research can be initiated by evaluating the working of PETYA malware, how it is triggered, what encryption is applied and other factors. A sample source code can also be analyzed to learn more about how cryptography is used with ransomware (Abijah Roseline & Geetha, 2021).
- Abijah Roseline, S. and Geetha, S. (2021) “A comprehensive survey of tools and techniques mitigating computer and mobile malware attacks,” Computers & Electrical Engineering , 92, p. 107143.
- McIntosh, T. et al. (2021) “Enforcing situation-aware access control to build malware-resilient file systems,” Future Generation Computer Systems , 115, pp. 568-582.
- Singh, J. and Singh, J. (2021) “A survey on machine learning-based malware detection in executable files,” Journal of Systems Architecture , 112, p. 101861.
Setting up a Live streaming server on the cloud platform
Nowadays, various organizations require a live streaming server to stream content depending upon their business. However, due to a lack of proper hardware, organizations are likely to face high network congestion, slowness and other problems (Ji et al., 2023). Referring to the recent cases, it has been observed that setting up a streaming server on the local environment is not expected to perform better than a cloud-based streaming server configuration (Martins et al., 2019). This particular research topic can be based on setting up a live streaming server on the AWS or Azure cloud platform to make sure high network bandwidth is provided with decreased latency. The research gap analysis would be conducted to analyze the performance of live streaming servers on local and cloud environments in terms of network performance metrics (Bilal et al., 2018).
- To set up a live streaming server on the AWS or Azure cloud platform to provide live streaming services.
- To use load balancers alongside streaming servers to ensure the load is balanced and scalability is achieved.
- To use Wireshark software to test network performance during live streaming.
RQ1: Why are in-house streaming servers not able to provide improved performance in comparison to cloud-based servers?
RQ2: What additional services are provided by cloud service providers which help in maintaining network performance?
The implementation is expected to carry out on the AWS cloud platform with other AWS services i.e. load balancer, private subnet and many more (Efthymiopoulou et al., 2017). Hence, this research can be carried out using a quantitative research method. The configuration of ec2 instances can be done which can act as a streaming server for streaming media and games. For testing this project, the use of OBS studio can be done which can help in checking whether streaming is enabled or not. For network performance, Wireshark can be used for testing network performance (George et al., 2020).
- Bilal, KErbad, A. and Hefeeda, M. (2018) “QoE-aware distributed cloud-based live streaming of multi-sourced Multiview Videos,” Journal of Network and Computer Applications , 120, pp. 130-144.
- Efthymiopoulou, M. et al. (2017) “Robust control in cloud-assisted peer-to-peer live streaming systems,” Pervasive and Mobile Computing , 42, pp. 426-443.
- George, L.C. et al. (2020) “Usage visualization for the AWS services,” Procedia Computer Science , 176, pp. 3710–3717.
- Ji, X. et al. (2023) “Adaptive QoS-aware multipath congestion control for live streaming,” Computer Networks , 220, p. 109470.
- Martins, R. et al. (2019) “Iris: Secure reliable live-streaming with Opportunistic Mobile Edge Cloud offloading,” Future Generation Computer Systems , 101, pp. 272-292.
Significance of using OSINT framework for Network reconnaissance
Network reconnaissance is becoming important day by day when it comes to penetration testing. Almost all white hat hackers are dependent on the OSINT framework to start with network reconnaissance and footprinting when it comes to evaluating organizational infrastructure. On the other hand, cyber attackers are also using this technique to start fetching information about their target. Currently, there is no investigation carried out to identify how effective the OSINT framework is over traditional reconnaissance activities (Liu et al., 2022). This research is focused on using OSINT techniques to analyze victims using different sets of tools like Maltego, email analysis and many other techniques. The analysis can be based on fetching sensitive information about the target which can be used for conducting illegal activities (Abdullah, 2019).
- To use Maltego software to conduct network reconnaissance on the target by fetching sensitive information.
- To compare the OSINT framework with other techniques to analyze why it performs well.
RQ1: What is the significance of using the OSINT framework in conducting network reconnaissance?
RQ2: How can the OSINT framework be used by cyber hackers for conducting illegitimate activities?
The OSINT framework is easily accessible on its official website where different search options are given. Hence, this research can be carried out using a quantitative research method. Depending upon the selected target, each option can be selected and tools can be shortlisted for final implementation. Once the tools are shortlisted, they can be used to conduct network reconnaissance (González-Granadillo et al., 2021). For example, Maltego can be used as it is a powerful software to fetch information about the target.
- Abdullah, S.A. (2019) “Seui-64, bits an IPv6 addressing strategy to mitigate reconnaissance attacks,” Engineering Science and Technology , an International Journal, 22(2), pp. 667–672.
- Gonzalez-Granadillo, G. et al. (2021) “ETIP: An enriched threat intelligence platform for improving OSINT correlation, analysis, visualization and sharing capabilities,” Journal of Information Security and Applications , 58, p. 102715.
- Liu, W. et al. (2022) “A hybrid optimization framework for UAV Reconnaissance Mission Planning,” Computers & Industrial Engineering , 173, p. 108653.
Wired and wireless network hardening in cisco packet tracer
At present, network security has become essential and if enterprises are not paying attention to the security infrastructure, there are several chances for cyber breaches. To overcome all these issues, there is a need for setting up secure wired and wireless networks following different techniques such as filtered ports, firewalls, VLANs and other security mechanisms. For the practical part, the use of packet tracer software can be done to design and implement a highly secure network (Sun, 2022).
- To use packet tracer simulation software to set up secure wired and wireless networks.
- Use different hardening techniques, including access control rules, port filtering, enabling passwords and many more to assure only authorized users can access the network (Zhang et al., 2012).
RQ: Why is there a need for emphasizing wired and wireless network security?
Following the quantitative approach, the proposed research topic implementation can be performed in Cisco Packet Tracer simulation software. Several devices such as routers, switches, firewalls, wireless access points, hosts and workstations can be configured and interconnected using Cat 6 e cabling. For security, every device can be checked and secure design principles can be followed like access control rules, disabled open ports, passwords, encryption and many more (Smith & Hasan, 2020).
- Smith, J.D. and Hasan, M. (2020) “Quantitative approaches for the evaluation of Implementation Research Studies,” Psychiatry Research , 283, p. 112521.
- Sun, J. (2022) “Computer Network Security Technology and prevention strategy analysis,” Procedia Computer Science , 208, pp. 570–576.
- Zhang, YLiang, R. and Ma, H. (2012) “Teaching innovation in computer network course for undergraduate students with a packet tracer,” IERI Procedia , 2, pp. 504–510.
Different Preemptive ways to resist spear phishing attacks
When it comes to social engineering, phishing attacks are rising and are becoming one of the most common ethical issues as it is one of the easiest ways to trick victims into stealing information. This research topic is based on following different proactive techniques which would help in resisting spear phishing attacks (Xu et al., 2023). This can be achieved by using the Go-Phish filter on the machine which can automatically detect and alert users as soon as the phished URL is detected. It can be performed on the cloud platform where the apache2 server can be configured along with an anti-phishing filter to protect against phishing attacks (Yoo & Cho, 2022).
- To set up a virtual instance on the cloud platform with an apache2 server and anti-phishing software to detect possible phishing attacks.
- To research spear phishing and other types of phishing attacks that can be faced by victims (Al-Hamar et al., 2021).
RQ1: Are phishing attacks growing just like other cyber-attacks?
RQ2: How effective are anti-phishing filters in comparison to cyber awareness sessions?
The entire research can be conducted by adhering to quantitative research methodology which helps in justifying all research objectives and questions. The implementation of the anti-phishing filter can be done by creating a virtual instance on the cloud platform which can be configured with an anti-phishing filter. Along with this, some phishing attempts can also be performed to check whether the filter works or not (Siddiqui et al., 2022).
- Al-Hamar, Y. et al. (2021) “Enterprise credential spear-phishing attack detection,” Computers & Electrical Engineering , 94, p. 107363.
- Siddiqui, N. et al. (2022) “A comparative analysis of US and Indian laws against phishing attacks,” Materials Today: Proceedings , 49, pp. 3646–3649.
- Xu, T., Singh, K. and Rajivan, P. (2023) “Personalized persuasion: Quantifying susceptibility to information exploitation in spear-phishing attacks,” Applied Ergonomics , 108, p. 103908.
- Yoo, J. and Cho, Y. (2022) “ICSA: Intelligent chatbot security assistant using text-CNN and multi-phase real-time defense against SNS phishing attacks,” Expert Systems with Applications , 207, p. 117893.
Evaluating the effectiveness of distributed denial of service attacks
The given research topic is based on evaluating the effectiveness of distributed denial of service attacks on cloud and local environments. Hence, this research can be carried out using a quantitative research method. Cyber attackers find DDoS as one of the most dangerous technological exploitation when it comes to impacting network availability (Krishna Kishore et al., 2023). This research can revolve around scrutinizing the impact of DDoS attacks on the local environment and cloud environment. This can be done by executing DDoS attacks on a simulated environment using hoping or other software(s) to check where it has a higher magnitude (de Neira et al., 2023).
- To set up a server on the local and cloud environment to target using DDoS attacks for checking which had experienced slowness.
- To determine types of DDoS attack types, their magnitude and possible mitigation techniques.
RQ: Why do DDoS attacks have dynamic nature and how is it likely to sternly impact victims?
The experimentation for this research can be executed by creating a server on the local and cloud environment. Hence, this research can be carried out using a quantitative research method. These servers can be set up as web servers using apache 2 service. On the other hand, a Kali Linux machine can be configured with DDoS execution software. Each server can be targeted with DDoS attacks to check its effectiveness (Benlloch-Caballero et al., 2023).
- Benlloch-Caballero, P., Wang, Q. and Alcaraz Calero, J.M. (2023) “Distributed dual-layer autonomous closed loops for self-protection of 5G/6G IOT networks from distributed denial of service attacks,” Computer Networks , 222, p. 109526.
- de Neira, A.B., Kantarci, B. and Nogueira, M. (2023) “Distributed denial of service attack prediction: Challenges, open issues and opportunities,” Computer Networks , 222, p. 109553.
- Krishna Kishore, P., Ramamoorthy, S. and Rajavarman, V.N. (2023) “ARTP: Anomaly-based real time prevention of distributed denial of service attacks on the web using machine learning approach,” International Journal of Intelligent Networks , 4, pp. 38–45.
Recommended Readings
Latest Web Development Research Topics
Top Management Research Topics
Newest AI Research Topics

Research in every field is becoming more and more essential because of constant developments around the world. Similar is the case in the field of networking. This is the reason; students who are preparing to master the field of networking need to keep their knowledge of the current state of the art in the field up to date.
However, choosing the right research topic often becomes a tough task for students to carry out their research effectively. That being the case, this list contains 15 latest research topics in the field of networking. Whether you are a seasoned researcher or just starting, this list can provide you with ample inspiration and guidance to drive your research forward in the dynamic and evolving field of Networking.
Copyright © 2023 CrowJack. All Rights Reserved

Engineer's Planet
Mtech, Btech Projects, PhD Thesis and Research Paper Writing Services in Delhi
Computer Network Project Topics With Abstracts and Base Papers 2024
Embark on a transformative journey into the world of computer networks with our carefully curated selection of M.Tech project topics for 2024, seamlessly paired with trending IEEE base papers. These projects encapsulate the cutting-edge developments and challenges in networking, providing an invaluable resource for M.Tech students eager to delve into the dynamic landscape of connectivity and communication. Our comprehensive compilation spans an array of Computer Network project topics, each thoughtfully accompanied by an associated base paper and a succinct abstract. From advanced routing algorithms and network security to emerging technologies like 5G and IoT, these projects represent the latest trends in the ever-evolving field of networking. Stay abreast of industry demands by exploring projects that align with the forefront of technological innovation. Whether you’re a student, researcher, or industry professional, our collection serves as a gateway to the forefront of networking advancements. The project titles are strategically chosen to incorporate keywords that resonate with the current trends in networking, ensuring alignment with the latest IEEE standards and technological breakthroughs. Delve into the abstracts to quickly grasp the scope, methodologies, and potential impacts of each project.
M.Tech Projects Topics List In Computer Network
Leave a Reply Cancel reply
This site uses Akismet to reduce spam. Learn how your comment data is processed .
- Council Members
- Council Meetings
- CCC Council Nominations
- Governing Documents
- 2011 and Prior Years
- CS for Social Good White Paper Competition
- Workshop Reports
- RFP – Creating Visions for Computing Research
- Robotics Roadmap
- Call for Council Nominations
- Big Data Regional Hubs
- Leadership in Science Policy Institute
- Postdoc Best Practice Final Reports
- Postdoc Best Practice Resources
- CIFellows 2020
- CIiFellows 2021
- CIFellows 2020: For the Record
- CI Fellows 2014 Workshop
- Success Stories
- ADDRESSING THE UNFORESEEN DELETERIOUS IMPACTS OF TECHNOLOGY (AUDIT)
- COMPUTATIONAL FOUNDATIONS FOR SUSTAINABILITY AND CLIMATE RESILIENCE
- GRAND CHALLENGES IN COMPUTING
- SOCIOTECHNICAL COLLABORATIONS OF AI+X
- FULL STACK: FROM HARDWARE TO PEOPLE
- PAST TASK FORCES
- CCC Call for Content
- CCC Led Whitepapers
- Presentations
- CCC Responds to the Community
- Recent CCC Activities
- Ongoing CCC Activities
- Computing Research in Action
- Computing Research Highlights
- Great Innovative Ideas
- Event Videos
- Catalyzing Computing Podcast
- Upcoming Events
- Special Events
- Past Events
- CCC at AAAS 2020
- CCC at AAAS 2019
- CCC at AAAS 2018
- CCC at AAAS 2017
- CCC at AAAS 2016
- CCC at AAAS 2013
- AI /ML / ROBOTICS
- ARCHITECTURE / SYSTEMS / NETWORKING
- DATABASES / INFORMATICS / DATA SCIENCE / HPC
- HUMAN-COMPUTER INTERACTION / GRAPHICS / VISUALIZATION
- IOT / UBIQUITOUS
- PROGRAMMING LANGUAGES / COMPILERS / SOFTWARE ENGINEERING
- SECURITY / PRIVACY / FAIRNESS
- THEORY / ALGORITHMS
- MISCELLANEOUS

Computing Community Consortium Blog
The goal of the Computing Community Consortium (CCC) is to catalyze the computing research community to debate longer range, more audacious research challenges; to build consensus around research visions; to evolve the most promising visions toward clearly defined initiatives; and to work with the funding organizations to move challenges and visions toward funding initiatives. The purpose of this blog is to provide a more immediate, online mechanism for dissemination of visioning concepts and community discussion/debate about them.
The 25 “Coolest” Computer Networking Research Projects
Network World is out with a list of the 25 “coolest” computer networking research projects :
University labs, fueled with millions of dollars in funding and some of the biggest brains around, are bursting with new research into computer and networking technologies. Wireless networks, computer security and a general focus on shrinking things and making them faster are among the hottest areas, with some advances already making their way into the market.
Among the projects highlighted (following the link):
Duolingo This free website, Duolingo , from a pair of Carnegie Mellon University computer scientists serves double duty: It helps people learn new languages while also translating the text on Web pages into different languages. CMU’s Luis von Ahn and Severin Hacker have attracted more than 100,000 people in a beta test of the system, which initially offered free language lessons in English, Spanish, French and German, with the computer offering advice and guidance on unknown words. Using the system could go a long way toward translating the Web, many of whose pages are unreadable by those whose language skills are narrow. Von Ahn is a veteran of such crowdsourcing technologies, having created online reCAPTCHA puzzles to cut down on spam while simultaneously digitizing old books and periodicals. Von Ahn’s spinoff company, reCAPTCHA, was acquired by Google in 2009. Duolingo, spun off in November to offer commercial and free translation services, received $3.3 million in funding from Union Square Ventures, actor Ashton Kutcher and others. Serval Princeton University computer science researchers envision an Internet that is more flexible for data center operators and more useful to mobile users. Princeton’s open source Serval system is what Assistant Professor of Computer Science Michael Freedman calls a Service Access Layer that sits between the IP Network Layer (Layer 3) and Transport Layer (Layer 4), where it can work with unmodified network devices. Serval’s purpose is to make Web services such as Gmail and Facebook more easily accessible, regardless of where an end user is, via a services naming scheme that augments what the researchers call an IP address set-up “designed for communication between fixed hosts with topology-dependent addresses.” Data center operators could benefit by running Web servers in virtual machines across the cloud and rely less on traditional load balancers. Serval, which Freedman describes as a “replacement” technology, will likely have its first production applications in service-provider networks. “Its largest benefits come from more dynamic settings, so its features most clearly benefit the cloud and mobile spaces,” he says. If any of this sounds similar to software-defined networking (SDN), there are in fact connections. Freedman worked on an SDN/OpenFlow project at Stanford University called Ethane that was spun out into a startup called Nicira for which VMware recently plunked down $1.26 billion. Hyperspeed signaling University of Tulsa engineers want to slow everything down, for just a few milliseconds, to help network administrations avoid cyberattacks. By slowing traffic, the researchers figure more malware can be detected and then headed off via an algorithm that signals at hyperspeed to set up defenses — though researcher Sujeet Shenoi told the publication New Scientist [subscription required] that it might not be cheap to set up such a defense system, between the caching system and reserved data pipes needed to support the signals. Control-Alt-Hack University of Washington researchers have created a card game called Control-Alt-Hack that’s designed to introduce computer science students to security topics. The game, funded in part by Intel Labs and the National Science Foundation , made its debut at the Black Hat security conference in Las Vegas over the summer. The tabletop game involves three to six players working for an outfit dubbed Hackers, Inc., that conducts security audits and consulting, and players are issued challenges, such as hacking a hotel mini bar payment system or wireless medical implant, or converting a robotic vacuum cleaner into a toy. The game features cards (including descriptions of well-rounded hackers who rock climb, ride motorcycles and do more than sit at their computers), dice, mission cards, “hacker cred tokens” and other pieces, and is designed for players ages 14 and up. It takes about an hour to play a game. No computer security degree needed. “We went out of our way to incorporate humor,” said co-creator Tamara Denning , a UW doctoral student in computer science and engineering, referring to the hacker descriptions and challenges on the cards. “We wanted it to be based in reality, but more importantly we want it to be fun for the players.”
Check out the full list here .
And click here to learn about a couple quick and easy ways you can work with us to publicize your own research!
(Contributed by Erwin Gianchandani , CCC Director)
Disclaimer: Posts on this blog report on happenings, opportunities, and issues that arise in the broad computing research community, and do not necessarily reflect the opinion of the CCC or the National Science Foundation.
Related posts:
- “Computer Scientist Banks on Human Superiority Over Machines”
- Future Internet Architecture: Content-Centric Networking
- First Person: “The Man Who Wants to Translate the Web”
- Open Networking Foundation Announced
- OSTP Studying Benefits of Video Games

great information and i like the way you write – thumbs up!
You are absolutely right I have heard about Duolingo. I have read about it in some article.
Very well and informative post you have shared. Your style is just awesome, I like the content as well. Thanks.
Trackbacks / Pingbacks
- The 25 ?Coolest? Computer Networking Research Projects – CCC Blog | ysycyvetuk

The CCC’s official podcast, “Catalyzing Computing,” features interviews with researchers and policy makers about their background and experiences in the computing community.

- CCC @ AAAS: How Big Trends in Computing are Shaping Science – Part Five
- CCC @ AAAS: How Big Trends in Computing are Shaping Science – Part Four
- CCC @ AAAS: How Big Trends in Computing are Shaping Science – Part Three
- CCC @ AAAS: How Big Trends in Computing are Shaping Science – Part Two
- CCC @ AAAS: How Big Trends in Computing are Shaping Science – Part One

Back to Top
© 2024 CCC Blog · CCC · Unsubscribe/Removal of Information · CRA · Home
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
computer-networks-project
Here are 13 public repositories matching this topic..., rajvi-patel-22 / internet-radio-multicasting-multimedia-over-ip.
This project will work as mentioned below.First, Client will send a join request to the server to join the multicast group.After that Server will provide station list, site info to the client through TCP. Then whichever station it selects from the station list, it is connected to that station.All the stations are sending data, irrespective of cl…
- Updated Dec 5, 2023
ashwinn-v / Traffic-classifier-SDN
A system that could classify DNS, Telnet, Ping, Voice, Game, and Video traffic flows based on packet and byte information simulated by the Distributed Internet Traffic Generator (D-ITG) tool in an Software Defined Network (SDN) based network topology with Open vSwitch (OVS) using machine learning algorithms such as Logistic regression,K-Means cl…
- Updated Dec 22, 2021
DenizKrdy98 / Distance-Vector-Routing-and-Flow-Control-Simulator
The project simulates a network traffic in a given topology where the distance vector algorithm is used for path computations, routing and forwarding.
- Updated Oct 18, 2020
BhishmaGohel / Routing_demo_in_C
This repository is having one main.c code which basically giving the demo of static routing using C language.
- Updated May 5, 2020
Ut03 / Wireless-Network-Proposal
The main aim of this project is to design a network setup which meets the requirements of a university allowing effective exchange of information between the various departments. We implemented this using cisco packet tracer ad kali linux.
- Updated Nov 24, 2022
guilherme-marcello / cnet-java-traffic-analyser
Tool for analyzing network traffic written in Java
- Updated Dec 11, 2022
siddhesh-desai / Vishwakarma-Labs-Terminal-Based
Vishwakarma Labs is an attendance management system designed for labs. With features like real-time chat, attendance tracking, and support for multiple participants, it makes managing lab sessions easy and efficient. The attendance is only marked if a student attends for a certain period of time.
- Updated May 25, 2023
Tiberiu-Cocei / ProiectRC
Proiect RC - Top muzical
- Updated Sep 3, 2019
Koralovy / PUT-INF5-SK2
Computer Networks 2 repository for the 5th semester of full-time Computing studies at the Poznań University of Technology. Server in C and client in C++ Qt5.
- Updated Mar 26, 2022
AitzazTahirCh / OSPF-Simulation
This repository contains the project implementing OSPF protocol (widely used protocol in Computer networking) and simulating it using Python, Pygame, Multiprocessing etc. For more information refer to " OSPF report.docx " and " CN Project Proposal.docx " in this same repository.
- Updated Jul 30, 2022
siddhesh-desai / Vishwakarma-Labs
Vishwakarma Labs is an attendance management system designed for labs. With features like real-time chat, attendance tracking, and support for multiple participants, it makes managing lab sessions easy and efficient.
guilherme-marcello / cnet-java-http-server
HTTP-Server implementation written in Java
- Updated Feb 21, 2023
Apekshagaonkar / PYGAMES
- Updated Apr 19, 2020
Improve this page
Add a description, image, and links to the computer-networks-project topic page so that developers can more easily learn about it.
Curate this topic
Add this topic to your repo
To associate your repository with the computer-networks-project topic, visit your repo's landing page and select "manage topics."
Computer Science
Computer networks.
Computer networks allow computers to communicate with one another, and provide the fundamental infrastructures supporting our modern society. Research on computer networks at Yale improves on essential network system properties such as efficiency, robustness, and programmability. The research spans all networking layers, including application-network integration (ANI); highly robust, flexible networking; software-defined networking (SDN) and programmable networking applications; and mobile networking.
Faculty working in this area:
Highlights in this area:.
- Generative AI
- Office Suites
- Collaboration Software
- Productivity Software
- Augmented Reality
- Emerging Technology
- Remote Work
- Artificial Intelligence
- Operating Systems
- IT Leadership
- IT Management
- IT Operations
- Cloud Computing
- Computers and Peripherals
- Data Center
- Enterprise Applications
- Vendors and Providers
- Enterprise Buyer’s Guides
- United States
- Netherlands
- United Kingdom
- New Zealand
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Copyright Notice
- Member Preferences
- About AdChoices
- E-commerce Affiliate Relationships
- Your California Privacy Rights
Our Network
- Network World
20 kick-ass network research projects
While start-up funding and the emergence of exciting new network startups has fizzled over the past year, research projects at university and other labs continue to sizzle. Here’s look at 20 of the coolest:
Plotting a cheap, distributed zero-day worm defense
Shutting down zero-day computer attacks could be carried out inexpensively by peer-to-peer software that shares information about anomalous behavior, say researchers at the University of California at Davis. The software would interact with existing personal firewalls and intrusion detection systems to gather data about anomalous behavior, says Senthil Cheetancheri, the lead researcher on the project he undertook as a grad student at UC Davis from 2004 to 2007. The software would share this data with randomly selected peer machines to determine how prevalent the suspicious activity was, he says. If many machines experience the identical traffic, that increases the likelihood that it represents a new attack for which the machines have no signature. The specific goal would be to detect self-propagating worms that conventional security products have not seen before.
MIT’s sticky notes killer (though they say it isn’t)
MIT computer science professor David Karger’s research team has developed software dubbed List.it that’s designed to computerize many of the things people currently do through sticky notes: organize email addresses, passwords and the like. The software lives in your Firefox browser and can be downloaded here. The software comes out of MIT’s Computer Science and Artificial Intelligence Lab (CSAIL), a perennial hotbed for IT inventions. “I would never make the claim that we’re trying to replace Post-its,” says Michael Bernstein, a graduate student in Karger’s lab. “We want to understand the classes of things people do with Post-its and see if we can help users do more of what they wanted to do in the first place.”
Researchers devise undetectable phishing attack With the help of about 200 Sony Playstations, an international team of security researchers have devised a way to undermine the algorithms used to protect secure Web sites and launch a nearly undetectable phishing attack. To do this, they’ve exploited a bug in the digital certificates used by Web sites to prove that they are who they claim to be. By taking advantage of known flaws in the MD5 hashing algorithm used to create some of these certificates, the researchers were able to hack VeriSign’s RapidSSL.com certificate authority and create fake digital certificates for any Web site on the Internet. Although the researchers believe that a real-world attack using their techniques is unlikely, they say that their work shows that the MD5 hashing algorithm should no longer be used by the certificate authority companies that issue digital certificates. “It’s a wake-up call for anyone still using MD5,” said David Molnar a Berkeley graduate student who worked on the project.
Website Morphing
Web sites that automatically customize themselves for each visitor so they come across as more appealing or simply less annoying can boost sales for online businesses by close to 20%, MIT research says. These sites adapt to display information so everyone who visits sees a version best suited to their preferred style of absorbing information, say the four researchers who wrote about such sites in “Website Morphing”, a paper published in Marketing Science last year. So the site might play an audio file and present graphics to one visitor, but present the same information as text to the next depending on each person’s cognitive style. Morphing sites deduce that style from the decisions visitors make as they click through pages on the site.
Making quantum computers a reality
Researchers in the U.K. and the U.S. published a paper detailing discoveries that might bring a fully functional quantum computer one step closer to reality. Quantum computing, which has been researched for decades, has traditionally had a problem of keeping data in a coherent format, making it difficult to run programs or computing tasks. The researchers have found a way to preserve electrons, which store the data, longer, which allows a system to process data more coherently and run programs more effectively. The group’s research focused on phosphorus atoms in silicon. The best attempts previously have flowed a current past the electrons via small electrical wires, but that has brought in a lot of quantum noise, removing a key advantage of the material.
Separately, researchers from Toshiba and Cambridge University’s Cavendish Laboratory are reporting a breakthrough they say could make quantum cryptography a reality in the near-term. The gist of the research is that they’ve come up with a much less complicated way (a “decoy protocol” generated using a laser and a compact detector) to support quantum cryptography, one that does not rely on cryogenic cooling or complicated optical configurations.Making your PC talk in its sleep
Microsoft and University of California, San Diego researchers have developed a device they say can save on energy costs by enabling end users to put their computers into a “sleep talking” mode that falls somewhere in between awake and sleep modes. They say it could save 60% to 80% on energy usage. The USB device, dubbed Somniloquy, features a low-power processor that works at the PC’s network interface level on wired and wireless networks. It boasts an embedded operating system and flash memory, and disguises itself as a sleeping PC to other systems on a network. But it can also wake up the actual PC in times of need, such as if a large file is coming in.
Separately, University of Liverpool researchers have developed software called PowerDown that they say could save big organizations close to US$17K per month simply by automating the shutoff of computer systems not being used.
Giving the boot to rebooting PCs
NSF-funded researchers are applying ultra-thin ferroelectric materials found on ATM and other smart cards to computers, with hopes that one day this could result in low-power/high-speed memory devices and computers that turn on faster. The researchers, from Cornell University, Penn State University and Northwestern University, reported their findings in the journal Science on April 17 in an article titled “A Ferroelectric Oxide Made Directly on Silicon.” The researchers have put strontium titanate on silicon in such a way that the material has been “squeezed into a ferroelectric state,” according to the NSF. More research needs to be done to develop faster booting computers, but the researchers are encouraged by initial results.
Violent video games good for your eyesight
More evidence that video games are good for you : A Tel Aviv University and University of Rochester researchers have found that playing violent video games can improve teens’ vision. In particular, the games (such as first-person shooter games) have been found to help players train their brains to better discern subtle differences in color or shades of gray. “We think that the games are taking the brain’s visual cortex to the limits, forcing it to adapt to the added stimuli of the action games,” said Uri Polat of Tel Aviv University’s Goldschlager Eye Institute, in a statement.
Another recent study out of Michigan State University found that video games could deliver skills to players that could help them perform delicate acts such as surgery. In fact, one researcher suggested that the fact more boys play video games gives them an upper hand over girls in this area.Another recent study found that the tools used to build 3D shooter games can also be applied to designing systems to help people evacuate burning buildings.
Defining cloud computing obstacles and opportunities
UC Berkeley researchers have outlined their view of cloud computing , which they say has great opportunity to exploit unprecedented IT resources if vendors can overcome a litany of obstacles.The 11 researchers’ cloud computing forecast is documented in a paper called “Above the Clouds: A Berkeley View of Cloud Computing.” The research group works in the Reliable Adaptive Distributed Systems Laboratory (RAD Lab), a 3-year-old outfit funded by companies such as Google, Microsoft, IBM and Sun. “We argue that the construction and operation of extremely large-scale, commodity-computer datacenters at low-cost locations was the key necessary enabler of Cloud Computing,” they write.
But to take full advantage of the opportunity, vendors need to rethink the way they build their products. Application developers need to ensure their offerings can not only scale up, but scale down quickly to satisfy the needs of customers who resort to cloud computing to meet short-term needs. Developers of applications and infrastructure software also need pay-as-you-go licensing models that conform to the reality of cloud computing. Makers of infrastructure software must also craft products designed to run on virtual machines, a foundation technology in large-scale data centers used by cloud computing suppliers.
Researchers tout wireless microgrippers
In the not-too-distant future, your surgeon may be someone who — instead of wielding a scalpel — injects you with a flock of dust-sized wireless devices that grab and remove infected or damaged tissue in response to chemical signals. These microgrippers, less than 1/254th of an inch (1/10th of a millimeter) in diameter, have been developed by researchers at John Hopkins University, and tested in biopsy-like procedures with animal tissue. One writer described them as working like a hand: a “palm” surrounded by six “fingers” that can open and close around an object. The crab-like devices are moved and guided by external magnets, and grab or release in response to non-toxic biochemicals or temperature changes.
Arizona State, HP dare you to break their electronic displays
HP and Arizona State University researchers have introduced the first prototype of a paper-like computer display made mostly from plastic that has a lot going for it: it’s affordable, flexible and takes it easy on the power. Applications could include electronic paper and signage, according to the two outfits. The displays are based on self-aligned imprint lithography (SAIL) technology from HP Labs. Other organizations, such as DuPont Jeijin Films and E Ink, also made possible the first prototype.
Researchers target software freezes with “Gadara”
University of Michigan researchers have devised a controller they say can anticipate when software programs might freeze up in order to make sure they don’t. This issue is becoming more important than ever as multicore and shared systems crank up the number of processes being handled at any time. Their Gadara system uses feedback techniques comparable to those used by cruise control in cars as well as control logic, and is designed to fix things without needing to have the original programmer get involved. “This is a totally different approach to what people had done before for deadlock. Previously, engineers would try to identify potential deadlocks through testing or program analysis and then go back and rewrite the program. The bug fixes were manual, and not automatic. Gadara automates the process,” said Stéphane Lafortune, a professor in the Department of Electrical Engineering and Computer Science and a Gadara developer.
Talk-powered cell phones? Nanoscale piezoelectrics could make it real
It’s possible that in the future your voice conversations on your cell phone could generate enough electrical power to run the phone, without batteries. And not just phones. The technology , which converts mechanical stress like vibrations into electrical energy, could power a whole range of low-power mobile devices and sensors. That’s one possible outcome of recent work by a team of Texas A&M and University of Houston researchers, who appear to have discovered that by building a certain type of piezoelectric material to a specific thickness (about 21 nanometers, compared to a typical human hair of 100,000 nanometers), you can boost its energy production by 100 percent.
Building brainier computers
IBM Research is working to bring the brain’s processing power to computers, in an effort to make it easier for PCs to process vast amounts of data in real time. The researchers want to put brain-related senses like perception and interaction into hardware and software so that computers are able to process and understand the data quicker while consuming less power, said Dharmendra Modha, a researcher at IBM. The researchers are bringing the neuroscience, nanotechnology and supercomputing fields together in an effort to create the new computing platform, he said. The goal is to create machines that are mind-like and adapt to changes, which could allow companies to find more value in their data. Right now, a majority of information’s value is lost, but relevant data can allow businesses or individuals to make rapid decisions in time to have significant impact, he said. “If we could design computers that could be in real-world environments and sense and respond in an intelligent way, it would be a tremendous step forward,” Modha said.
Researchers show off advanced network control technology
Researchers can adjust network infrastructure to boost bandwidth, optimize latency and save power using an experimental technology called OpenFlow. OpenFlow is in the proof-of-concept stage but someday could be used in business networks to engineer traffic, says Nick McKeown, an associate professor of electrical engineering and computer science at Stanford University. OpenFlow is part of the Clean Slate initiative set up to consider how the Internet might be re-engineered to make it more responsive to how it is actually used. Researchers devised OpenFlow as a way to test out new network protocols on existing networks without disrupting production applications. The only other option is to set up separate infrastructure on which to run experiments, a costly alternative.Open source laptop Lojack system released by university researchers
A new open source tool called Adeona has been released by researchers at two universities in an effort to recover lost or stolen laptops on campus, at airports and elsewhere. Adeona, in fact, is named after the Roman goddess of safe returns.University of Washington and University of California, San Diego researchers say the tool enables laptop owners to track the whereabouts of their Windows, Apple and Linux machines without letting anyone else know. Once Adeona is loaded on a machine, it will every so often send scrambled information such as IP address to OpenDHT, a free online storage network, that can be used to determine a laptop’s general location. On Macs, Adeona can even exploit the internal camera to take pictures to send to the OpenDHT server.The information could then be used by cops to try to track down the machine.
New router algorithm offers hope for old routers
A team of computer scientists has proposed a new algorithm that makes routers operate more efficiently by automatically limiting the number of network route or link-state updates they receive. The algorithm could be important in large heterogeneous corporate networks where the oldest, slowest routers make all the others wait while they absorb updates and recalculate their path tables. The Approximate Link State (XL) algorithm suppresses the updates so only those routers that are directly affected receive them, says Professor Stephan Savage, who along with three other computer scientists at the University of California at San Diego developed the algorithm.
Separately, researchers at Cornell University and AT&T Labs are breathing new life into routers via a method they say doesn’t require changes to routing software or protocols. In a paper titled “Making Routers Last Longer with ViAggre,” the researchers outline Virtual Aggregation (ViAggre), which they describe as a configuration-only approach to squeezing ISPs’ routing tables that works in part by limiting the how much of the global routing table each router maintains. It also is an incremental approach that can be executed by individual ISPs without the need to synch up with others, the researchers explain. The researchers examined how ViAggre would work on tier 1 and 2 ISPs’ networks and found that routing tables could be reduced drastically without loading them down with traffic. They also gave ViAggre a whirl on Cisco routers in a testbed.
A way to sniff keystrokes from thin air
That PC keyboard you’re using may be giving away your passwords. Researchers say they’ve discovered new ways to read what you’re typing by aiming special wireless or laser equipment at the keyboard or by simply plugging into a nearby electrical socket. Two separate research teams, from the Ecole Polytechnique Federale de Lausanne and security consultancy Inverse Path, have taken a close look at the electromagnetic radiation that is generated every time a computer keyboard is tapped. It turns out that this keystroke radiation is actually pretty easy to capture and decode — if you’re a computer hacker-type, that is. The Ecole Polytechnique team did its work over the air. Using an oscilloscope and an inexpensive wireless antenna, the team was able to pick up keystrokes from virtually any keyboard, including laptops.
Squeezing storage
Nanotechnology researchers say they have achieved a breakthrough that could fit the contents of 250 DVDs on a coin-sized surface and might also have implications for displays and solar cells. The scientists, from the University of California at Berkeley and the University of Massachusetts Amherst, discovered a way to make certain kinds of molecules line up in perfect arrays over relatively large areas.. One of the researchers said the technology might be commercialized in less than 10 years, if industry is motivated.
Separately, Computerworld reported that “researchers at Rice University have demonstrated a new data storage medium made out of a layer of graphite only 10 atoms thick. The technology could potentially provide many times the capacity of current flash memory and withstand temperatures of 200 degrees Celsius and radiation that would make solid-state disk memory disintegrate.”
Researchers seek advanced network prioritization, security technology
Researchers are looking to build self-configuring network technology that would identify traffic, let the network infrastructure prioritize it down to the end user, reallocate bandwidth between users or classes of users, and automatically make quality of service decisions. The system will have a minimum of 32 levels of prioritization. These prioritization levels will be configurable and changeable at the system level in an authenticated method. Data with a higher priority will be handled more expeditiously than traffic with a lower priority. If that sounds like a major undertaking, it is, but consider who wants to develop such a beast: the Defense Advanced Research Projects Agency (DARPA).
This advanced prioritization system is part of DARPA’s Military Networking Protocol (MNP) program which is looking to develop an authenticated and attributable identification system for packet based, military and government data networks, the agency said. Military or government data sent with the MNP will be compatible with normal Internet equipment to allow MNP traffic to pass through legacy network or encryption equipment, DARPA said.
IDG News Service contributed to this report.
Related content
Apple earnings: about that iphone 'slump' in china, microsoft begins to phase out ‘classic’ teams, apple confirms it will open up the ipad in europe this fall, udacity offers laid-off us workers free access to its courses for 30 days, from our editors straight to your inbox, more from this author, bill gates blows away other techies with his als ice bucket challenge video, mark zuckerberg, satya nadella get freezing wet for als, tricks and tips that will help you get the most out of those new xmas gadgets, target’s statement to customers on massive data breach, most popular authors.

Show me more
Why you’ll soon have a digital clone of your own.

Workers with these AI skills are getting cash premiums

Atlassian Rovo brings AI smarts to enterprise search

Why tech workers are struggling to find jobs

TikTok ban in place, but how long before it's gone?

After 10 years of progress, does mixed reality (XR) have a future? | Ep. 147

After 10 years of progress, does mixed reality (XR) have a future?

Browse Course Material
Course info.
- Prof. Hari Balakrishnan
Departments
- Electrical Engineering and Computer Science
As Taught In
- Computer Networks
Learning Resource Types
As you know, one of the major goals of this class is to understand how networking research is done. To this end, the term project is a major component of 6.829, since that’s where you draw upon your knowledge and experience from the course readings and elsewhere to actually do research. This document is intended to ease the process of figuring out what to work on and writing a short proposal explaining what you want to work on. A separate document handed out in class describes some project suggestions we came up with.
Please feel free to come up with your own ideas, or modify our suggestions in any way you want. Our suggestions are simply that; and they’re usually incomplete. They are usually not complete specifications of projects.
Teams : As far as possible, you should work in teams of two unless you are doing the M-to-N fast file transfer protocol project. Working with others is a lot more fun, is often a lot more productive, and the resulting work a lot sounder than if you were working in isolation. The nature of the networking field is one that fosters collaboration and often makes it essential for high impact work, and you should develop the ability to collaborate on projects. Unless there is a very good and compelling reason for you to work alone, we won’t agree to it! For large enough projects, we will be happy to allow teams of three, provided the proposal makes it clear why it is a large enough project (and ideally also what the approximate task assignment is).
Schedule : One- to two-page proposals (details below) are due before Lecture 8. Print out three hard copies and bring them to class. We will read the proposals carefully over the following few days and get back to you by email if we have any questions. In some cases, we may want to meet with teams to understand better exactly what you are doing, perhaps because it is not focused enough or because you are trying to accomplish too much. Please do not wait for us to get back to you; get started as soon as possible! You have about two months to carry out the project, which is ample if your proposal is focused and you start early, but not otherwise .
Project presentations have been scheduled for the sessions after Lecture 22. Your paper is due on the last class. It is important that you read important background material before turning in the proposal!
Proposal : A crisp one-page write-up that should contain the following items. Three hard copies per group.
Project title (a detailed title is better than a vague one; you can always change it later if you don’t like it!) and names of investigators with email addresses.
A clear statement of the research problem: a one-sentence summary followed by a one-paragraph explanation (the paragraph should not be more than 10-12 lines long). This should identify clearly the research question you are addressing (for example, implementing a TCP/IP networking stack, while a lot of work, is not research, unless of course you are doing it differently from today’s approaches).
A clear statement of your research methodology, i.e., how are you going to solve the problems you have raised and motivated in the previous paragraph?
A statement of plan and schedule, to convince us (and yourself!) that you can complete this by the end of the term (exact due dates are here ).
A list of resources you need to accomplish your work, with special emphasis on important pieces you don’t yet have access to. Be as clear as you can in your requirements and we will work towards getting what you need as quickly as possible. If your request can’t be accommodated for any reason, we will try to get back to you about it as soon as we find out.
Any other questions you have or clarifications you need from us.
Background : In a one-semester class, one can only cover a fraction of networking topics, and there are sure to be projects where the background material won’t be covered in too much detail. And even for topics that we do cover, there will almost certainly be other relevant related work that you should be familiar with. Part of doing something new is figuring out what’s already been done or is known, so you should search the related literature and Web pages as extensively as you can. Keep an eye out for useful software or research methodology or tools that you can leverage; this will save you tremendous amounts of time later in the term. You might find some of the course links in the related resources section actually useful.
Standards : Aim high in a focused way, and do the best you can! The best projects are sure to be publishable (as they have in past years) in top ACM or IEEE conferences in the area, such as SIGCOMM, INFOCOM, or MOBICOM, or appear as articles in journals like SIGCOMM’s Computer Communications Review (CCR). I have a strong feeling that you will far surpass my already high expectations with wonderful work that will further the state-of-the-art in network research.
Where do you get a project? You are free to come up with your own, and the staff will be happy to discuss your proposal ideas by email (or in person) over the next few days. Or, you might want to pursue one of our suggestions (feel free to modify them in your proposal if you like).

You are leaving MIT OpenCourseWare
Networking Research Group
Inventing networking & sensing technologies
The Networking Research Group focuses on basic and applied research in all areas related to networked systems, mobile computing, sensing, and Internet of Things. Researchers build proof-of-concept systems, engage with academia , publish scientific papers , release software for the research community, and transfer cutting-edge technologies to Microsoft’s product groups.
Our research has created significant impact on Microsoft products, including Azure Networking, with features such as data center network architecture and virtualization , software-driven wide-area network (SWAN) , Data Center TCP (DCTCP) , Data Center QCN (DCQCN) , cloud-scale network emulator , and most recently intra-region RDMA , XBOX, such as the XBOX Wireless Controller Protocol, the Windows Networking Stack, with VirtualWiFi, and many more.

Networking for AI

Zero Trust & Zero Management

Networking for Industry

We strive to find a balance between long term research and product impact. You may know about our research from the papers we publish and the talks we give, but we also have a broad impact on Microsoft products, including:
- Follow on Twitter
- Like on Facebook
- Follow on LinkedIn
- Subscribe on Youtube
- Follow on Instagram
- Subscribe to our RSS feed
Share this page:
- Share on Twitter
- Share on Facebook
- Share on LinkedIn
- Share on Reddit
Research Group
Networks at mit.
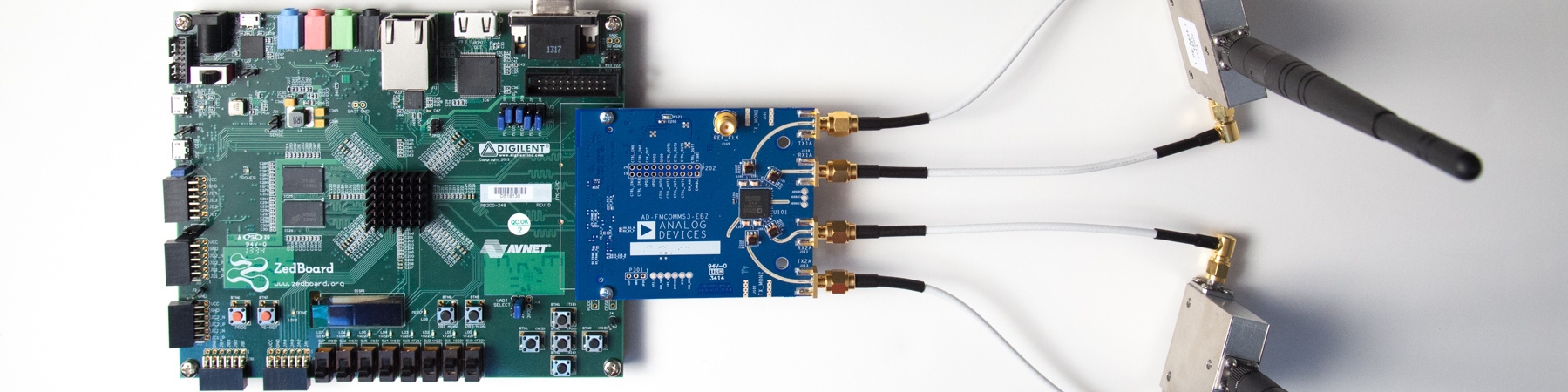
At NETMIT we draw on advanced mathematical models to create systems for networks and wireless applications. Recent projects have focused on such topics as spectrum usage, sparse FFT, mobile networks and crowdsourcing. We have a particular interest in adapting tools from various fields of applied mathematics such as control theory, coding theory, and machine learning to solve problems in networks.
Related Links
If you would like to contact us about our work, please refer to our members below and reach out to one of the group leads directly.
Last updated Oct 13 '17
Research Areas
Impact areas.

Dina Katabi
Eq-radio: emotion recognition using wireless signals.

Katabi earns SIGCOMM Lifetime Achievement Award

Dina Katabi elected to the National Academy of Sciences for 2023

What can your dishwasher tell you about your health?

A step toward personalized, automated smart homes

A "GPS for inside your body"
Mit professor wins association for computing machinery prize in computing.

Tracking patients’ progress with radio signals and machine learning
4 more.
NETWORKING BASED PROJECTS
“This article highly focuses on networking based projects for both students and scholars to pursue their thesis by providing knowledge on an overview of networking, its functions, and purposes, our contributions on project service, and the future scope of networking projects.” Networking is a term that plays a vital role in the field of communication network , where it includes all types of data transmission between entities and sharing or displaying any type of information from an individual to a group of people or transmitting data from one device to a group of devices . The sharing of data also includes every wired or wireless device, particularly linked with the internet.
“Every digital device has become to connect with a computer network in the current scenario.”
And the data can also be a message, media files, and displaying through the internet is also called Networking. Thus any type of communication over the internet is known as Networking. Some of the important aspects of Networking can be as follows.
- Routing by fault Tolerance
- Improving performance
- Controlling Traffic
- Techniques in routing
- Network infrastructures
What you can learn from us?
Satisfying your demands by our new networking facilities and our engineering team has assured to suggest the following services. By adjusting the above utilities in our service updating, you can learn,
- Networking algorithms and protocols
- Various functions of Networking
- Networking significance
- Fundamental / advanced / updated networking concepts
Overview of Networking
Networking is used to transmit data (packets) among two or more electronic devices by various networks like wireless, LAN, WAN, MAN , etc., that use the computer as the source device. Here the geographical site that outlines the physical space provides the coverage area of the network.
So, LAN stands for Local Area Network that can be used inside a particular construction and WAN stands for Wide Area Network helps in communication through wireless technologies. These are two vital computer networks that are able to connect a huge number of devices across the world.
How does networking works?
The process of Networking has some procedures, which state the way of data sharing. These types of procedures are called protocols that permit the devices for communication purposes. Every networking device is provided with a unique IP (Internet Protocol) address that helps identify a communication device .
In devices (digital/electronic), Networking is taking place by linking the nodes of the router, devices with the help of fiber optics or signals physically or virtually . The router enables communication among various LANs, and they estimate the best mode to share data, and switching helps to connect nodes for communication inside LAN.
Top 2 limitations of networking
- Controlling traffic
- Specified Packet distribution
- Partial data operations
- Various concerns of data for evaluation
- Traffic (burst)
The limitation of Networking is very high when comparing to the other domains because open issues are rising due to the growth . But these are very significant in the networking process that can be rectified with appropriate solutions/approaches/protocols design . To overcome such issues, the following features are needed in a network.
Networking Requirements
- Troubleshooting
- Get used to network updates
- Resolving hosts
- Active responding
The above-mentioned features are necessary to frame any type of network for communication purposes. Let’s see the layers of Networking. Networking based projects are most relevant to the OSI models of Networking, and each layer is affected by crucial issues and affects the network stack’s performance . According to OSI, communication is divided into seven conceptual layers as follows
What are the seven layers of networking?
- Application
- Performance
- Linked data
- Transmission
It is very significant for the students to understand the network methods and the wide range of purposes in designing . Here are the mechanisms for Networking based projects to have the understanding for fast and secure data transmission.
Mechanisms for networking projects
- Scheduling packets: dealing to queue the packets in order to prevent data traffic
- Protocols: ensuring the users are following the contract
- Controlling access: discards unchecked traffics
- Signaling protocol: approves service needed signals
The Networking based projects enable and widen the knowledge of students and scholars to get familiarity in Networking. With the formation of data packets and the process involved in access control and the procedures, the advanced Networking works are done. In addition to the above information, we provide you the areas that are based on the process of Networking .
Applications of Networking
- Media streaming
- Transportation of content
- Communications to any devices
- File distributing Networks
The functions of Networking are on the rise, and every new type of network traffic is updating to the function on the basis of software defined Networking . So the students who have chosen this field are blessed with an excellent scope because Networking cannot exhaust the endpoint. Let’s see the domains that are based on networking services and applications . As a result of real-time applications growth, a number of ideas are established in this domain. Get to know such real-time applications in Networking based projects first.
Real-Time Applications of Networking
- Hostile and Military Environments
- Smart Grid – Power Management
- Connected Vehicles- Intelligence Transport Service
- Video Transmission Analysis And Streaming Of Videos
- Real-time Events in WSN
- Healthcare Applications
Now, let’s see some of the Networking based infrastructures where the applications mentioned above are applied. Many cities are engineering with the ‘smart’ caption, which really is meant to enable the networking service by all means. Here are the network integrated environments that are soon implemented in the practical life of systems.
Network Integrated Environments
- Ad-hoc: handling data traffic in mobile devices
- MEC: integrates the function of cloud on the edge of networking with OpenStack
- Cloud: handling application delivery and traffic management
- Edge-servers: distribution of application at the edge of network
- Fog servers: arranges networking services for Internet of Things by absolute QoS
Along with the environments integrated with networks, our developers have come up with suggestions on the major research areas of networking among the Networking based projects in the current scenario
Top 3 Research areas in Networking:
- Controlling Real-Time Process: Industrial and aircraft system control
- Network applications : VR and other online games, networking between World Wide Web and Peer-to –Peer, network system files, managing distributed data systems.
- Telecommunication Networks: routing algorithm, wireless networks sensor, internet related electronic devices etc.
The above-mentioned research areas are on trending on networking projects . Suppose you want to be more informative on networking projects. In that case, we are here to introduce you to the recent developing networking technologies , and our research teams are here to link the real-life requirement with the networking technologies, which will be useful to choose your project title.
Currently emerging network technologies
- Wireless mobile networks enabling SDN and NFV
- Services for V2X (vehicle to everything)
- Vehicular ad hoc network
- IoT and Broadband technologies and internet access
- Wireless heterogeneous networks
- Communication through fiber optics
- Uniting 5G, IoT and Artificial Intelligence
- 5G and 5G beyond mobile networking
Most of the networking topics we mentioned above are intended to link with 5G technology because we constantly want to update you with novel ideas and innovative techniques using in the networking based projects . We know how people in this area want to conduct their research, and we are here to provide you the research topic beyond their estimation on updates.
Research topics in networking
- Wireless networks and network protocols
- Performance and measurement analytics
- Managing spectrum distribution
- Techniques and algorithms of Routing, switching and addressing
- Resource management, QoS, Traffic and Congestion control
In general, a simulation tool is important for every networking domain. But the simulators of the Operating system and modules are different. The behaviors of modules depending on the norms of considering the ‘networking services are the outcomes of finest strength,’ and so the network simulators don’t have the capacity to define the delay. In general, simulators are analytic tools used as follows.
Network simulation overview
- Testing the protocol’s performance
- Innovative network protocol Assessments
- The distributed system developments
- Balancing mathematical analysis in multifaceted systems
The functions of the network are expected to provide quick functions and results, but as the escalation of rapidity in the network is not complete by the software difficulty. Thus, the simulators must equate the space between the network speed and software to provide a 0’s time node events. Thus the qualities of the best simulation tool are as follows.
How to pick the best simulation tool for networking?
- Providing precision at high level
- Having the capability to parallel the timing between networking and software
- Attributed with precision tools to cope up the simulating process and ending application mainly for the simulating applications
The simulation tools are purposed to enhance the functions of networking and other simulation and software applications. Apart from all the mentioned metrics, the Quality of Service (QoS) is very important . The reason for the importance of QoS and its metric levels are as follows.
How to evaluate the performance of networks?
Quality of Service (QoS) is an important metric in improving an organization / or the network of entities to prove service accuracy and timing . It preserves the reputation of their network quality, and thus it has the qualities of the best metrics to evaluate the functions , and it improves the quality of the networking or software functions . The other significant functions of QoS are Follows,
- Controlling network traffic
- Locating and regulates the procedures of network traffic
- Improving more foreseeable service in networking
- Network bottleneck management
- Appropriate bandwidth association
- Enabled with Numerous features to make end- to- end delay
- Losing data to ease the network traffic mainly in data rupture scenario
- Reduces the bandwidth size to handle oversubscription in network
- Capability to host WAN with application recognized real-time delay
In order to empower the above qualities in a networking service , the cooperation of the QoS metric is important. It helps and relieves the networking system to handle the overloading , and it caters to the expectation of servicing speed and clearing congestion in Networking, etc. here are the parameters of QoS that varies according to the network layers as follows.
Network QoS parameters
- Physical Layer: relays on the sensor elements’ ability
- MAC layer: proficient energy, reliable transmission, throughput, range of communication
- Coverage maintenance layer: preserving coverage, its calculation, strength, consistency
- Connectivity preserving layer: sustaining and strengthening connectivity, capability and diameter of network, average path cost
- Network layer: maintains and strengthens routing, path delay, probable congestion
- Transport layer: cost, delay, bandwidth, consistency
- Application layer: maintains resolution, consistency and newness of data, upholds the lifetime of system, response timing and chance of detection.
Our research team has more ideas than we are displaying in front of your eyes. You need not hesitate to approach our project service. We notify you that we would help you complete your networking based projects on time, even if you are in your project stage. We are having technically updated engineers , who are also updated with the academic knowledge of project expectations . So we ensure our quality service and we glad to provide it to you with price conveniences. Just confirm your acceptance, sit back and relax, and we will take care of the rest.
e-mail address: [email protected]
Tel 7639361621

A network is a group of two or more network devices is used for communication. These devices and nodes in the question are connected through physical wired or wireless connections . The key purpose of the network is that connects at least two or three components and connected. If you are looking for innovative network project topics , then look at this page to know more about the networks.
Important Stages of Research
- Carried out literature review
- Determine the research problems
- Conducts research and collect results
- Produce the original research
- Start writing research work
There are several problems raised in-network for communication. In particular real-time applications such as video, transmission require high QoS performance and QoE results . Hence, we must know the important problems in networks.

What significant problem do wireless networks have?
- Low bandwidth with packet collisions and interference
- Low transmission strength
- Lack of network management
Previously, we listed three problems in networks, and the following discusses one of the important issues in the network. Now the network management problem to craft innovative network project topics is in detail here.
Why Network Management is important?
- To improve the network availability and improves the maintenance of the network
- To enrich the utilization of tools for network manage, and monitor of the network troubleshooting
- To reduce the network complexity by centralize the control of all network components
- To reduce the cost of network management and maintenance and operational expenses.
- To minimize the network, link and node failures in network and manage the network resources
Trending Network Research Topics
Network / information security
- Sensor & mobile ad hoc network security
- Internet security & applications
- Service and systems
- QoS network security
- Intrusion detection & prevention
Mobile and Wireless Network
- Wireless & mobile network operations
- Wireless sensor networks
- Wireless & mobile network architectures
- Wireless multimedia systems
- Mobile internet and web applications
Ubiquitous 5G Technologies
- Cognitive radio and cooperative systems
- Standardization and regulation
- Smart city and industry
- Hardware architecture and implementation
Wireless Networking
- Services and applications
- Network architectures
- Network protocols
- Network modeling, analysis and operation
- Network security a nd privacy
- Wireless and wireless systems
- Network operations & management
Sensor Networks or Systems
- Learning of models from sensor networks
- Synchronization and localization
- Data storage and query processing
For useful illustration, we study many research articles and literature reviews to find the performance of any research network project topics . Research methodology and novelty are tested using the performance evaluation. Now, we provide specific information for defining network performance management .
How network performance is measured?
- Scalability: Network scale is measured for the large scale and small scale network devices and the largest network with sending huge volume of packets with diverse of nature proves the network has obtained the greater performance.
- Throughput: For the network’s performance validation, throughput is evaluated and amount of data packets must be reached to the destination by the defined time periods can be the network has obtained the higher throughput
- Packet loss: It represents the number of packets transmission from one end to the other end. However, packet losses degrade the network performance.
In above, we have shortened the network performance parameters , and also in the following, we describe all network performance metrics by OSI layer-wise as physical, MAC and routing layers , etc. However, evaluate performance metrics makes the network intelligent and realizes the network topology and link conditions.
Further, it is achieved when appropriate protocol selection and management control have been taken. For instance, cognitive radio networks (CRN) and software-defined networks (SDN) require global network management.
What are network performance metrics?
- Network Architecture: network scale, network connectivity , centralized, or distributed, and network topology (cluster , star or mesh), and node density
- Channel Modeling: channel quality, channel bandwidth, holding time, channel switching time and handoff channel sequence
- Application and Traffic: QoE and QoS parameters
- MAC layer: Backoff time, Link BER, Access Collision Rate, Access Type, Error Correction Rate, and robustness
- Phy layer: SNR, Shannon capacity, Modulation mode and coding method
- Node property: Mobility mode, Mobility Speed, Packet Processing Time, Max Hop Distance, and Transmission Power
- Routing layer: Number of Hops, Path Delay, packet drop rate and re-routing time , and path throughput
- Transport layer: Queue size, congestion level, sliding window size, reliability level, retransmission timeout setup, etc.
If you contact us for your network project topics , you can assume that it is finished because we start to guide you from the initial step to the final step. We value your time by giving our efforts and deep research knowledge to your research networking topics. Thus, you can prefer your network project topics with complete professional guidance with exceptional guidance from us.
Computer networking research projects
Cici: ce: implementing cybex-p: helping organizations to share with privacy preservation.
- National Science Foundation
- PI: Shamik Sengupta, co-PI: Mehmet Gunes, Nancy LaTourette, Jeff Springer
- January 2018 - December 2019
In response to the increasing number of attacks on cyberspace, public and private organizations are encouraged to share their cyber-threat information and data with each other. Although there are long-term interests in sharing security related information, it places organizations at risk regarding the protection of their data and exposure of other vulnerabilities. This project designs, develops and implements a CYBersecurity information EXchange with Privacy (CYBEX-P) platform using trusted computing paradigms and privacy-preserving information sharing mechanisms for cybersecurity enhancement and development of a robust cyberinfrastructure. The outcome of this project has a broader impact on the development of a novel cybersecurity information-sharing platform with privacy preservation and a robust governance structure. The project also has direct impact on undergraduate and graduate student education and training, emphasizing the engineering development of minorities and women, by providing a real-world platform for investigation and management of cyber threats.
Envisioning that effective and privacy-preserving threat intelligence sharing can be instrumental for auditing the state of the threat landscape and helping to predict and prevent major cyber-attacks, this project provides a service for structured information exchange. The CYBEX-P platform provides valuable measurable information about the security status of systems and devices together with data about incidents stemming from cyber-attacks. To develop and implement such an environment across statewide organizations, then across the nation, this research project incorporates blind processing, privacy preservation and integrity of shared incident data by ensuring that only trusted processes access the raw data and only anonymized data are shared with other operators. Blind processing enables the advantages of additional information exchange while respecting organizational constraints and trust boundaries. This research also establishes a flexible governance framework that includes both policies and procedures to protect the data and provide all customers with the tools to demonstrate they are complying with both regulatory and internal data governance requirements. Specifically, the outcomes of the project demonstrate: i) CYBEX-P infrastructure development with affordable scalability, secure data exchange, and analytic components, ii) Privacy-preserving information sharing via blind processing and anonymization, and an iii) CYBEX-P governance framework.
Establishing market based mechanisms for CYBer security information EXchange (CYBEX)
- Funding Agency: NSF
- PI: Shamik Sengupta
- Amount: $329,658
- September 2015 - August 2019
Robust cybersecurity information sharing infrastructure is required to protect the firms from future cyber attacks which might be difficult to achieve via individual effort. The United States federal government clearly encourage the firms to share their discoveries on cybersecurity breach and patch related information with other federal and private firms for strengthening the nation's security infrastructure. The goal of this project is to develop an interdisciplinary research platform to investigate the framework and benefits of breach-related vulnerability information sharing and analyze the effect of not participating in the process of information exchange. The outcome of this project has a profound impact on the evolution of CYBer security information EXchange (CYBEX) architecture and the level of interaction desired among firms (private, public or federal) to defend proactively in the ever-growing cyberspace. The research has both direct and indirect impact on mentoring, hands-on learning, education and training. Graduate and Undergraduate students (including minority and women) participating in this project are involved in interdisciplinary research and learning problem solving skills taking into account different viewpoints, namely, cybersecurity, information-exchange, economics, decision analysis and practical system implementation.
By using micro and macro-economic theory as a substrate, this project establishes market based mechanisms for enabling cyber security information exchange (CYBEX) among firms to protect the cyberspace proactively against cyber attacks. This research investigates how cyberinsurance can be modeled and thereafter can be augmented with the information sharing format and framework to encourage firms to participate in CYBEX more effectively. The transformative nature of the proposed research lies in its potential to identify, model, and analyze the multi-dimensional robust cybersecurity information sharing infrastructure along with development of CYBEX emulator environment. The information sharing framework is also extended to the cloud domain that carries challenges to model the cloud attackers and incentive mechanisms to motivate the firms toward such sharing behavior. More Specifically, the outcomes of the project demonstrate: a) the potential of CYBEX in sharing the burden of cybersecurity and making the cyberspace more robust; b) multi-layer competitions and dynamics among CYBEX entities infiltrated with malicious entities; c) necessity of cyberinsurance and market oriented approach for better cybersecurity information utilization; and, d) the far-reaching impacts of interdisciplinary CYBEX research in terms of socio-economic value, technology and educational outreach programs
Longitudinal Injection of Interdisciplinary Cybersecurity Awareness into Engineering Curricula
- PI: Shamik Sengupta, co-PI: Mehmet Gunes, Nancy LaTourette
- September 2017 - August 2019
Upcoming smart technologies such as Smart Cities, Internet of Things, and Unmanned Aerial Vehicles digitize current technologies and require cybersecurity-aware multi-disciplinary engineering experts to ensure the security of such devices. As devices become smart and interconnected to provide improved services, they also become greater targets of cyber-attacks. Ensuring proper operation of smart technologies requires well-trained, proactive engineers, who are knowledgeable on core engineering principles, cybersecurity risks associated with their designs, and risks from other interconnected disciplines. The goal of this collaborative project is to develop and adopt interdisciplinary cybersecurity curriculum by fostering a holistic approach through collaboration across engineering disciplines. By bringing scholars from different engineering disciplines, this project explores unique ways to engage students in interdisciplinary cybersecurity-aware engineering education. The knowledge units developed at the University of Nevada, Reno will be disseminated to engineering colleges nationwide to sustain long-term research and education partnerships in secure engineering.
Cybersecurity research and its applications are highly relevant in all areas of engineering, including computer, electrical, mechanical, civil and biomedical disciplines. Researchers will develop knowledge units to introduce and reinforce the importance of cybersecurity to undergraduate students across several engineering disciplines with a focus on Smart Cities, Internet of Things, and Unmanned Aerial Vehicles. These three broad technological areas require expertise in multiple engineering fields and go from macro-level view to micro-level view where each of the sectors encompass the next one. Cybersecurity awareness will be injected organically in a boot camp for incoming engineering freshman, a freshman experience course on Introduction to Engineering, and discipline-specific technical engineering courses, typically during junior and senior years. The project will bring together engineering faculty to develop knowledge units that can be seamlessly adopted across various engineering disciplines. Instruction will be augmented with hands-on activities to create an interactive cybersecurity education environment and stimulate learning. A "Connected Cities" playing arena will be developed, comprising various cyber physical systems that are integrated for hands-on cybersecurity engagement. Through interdisciplinary educational modules and hands-on activities developed via this project, students will obtain a solid grasp on the interplay between different engineering disciplines and obtain critical knowledge and skills needed to engineer smart technologies that are resilient to cyber-attacks.
RET Site: Cyber Security Initiative for Nevada Teachers (CSINT)
- PI: Shamik Sengupta, co-PI: David Feil-Seifer
This funding establishes a new Research Experience for Teachers (RET) Site at the University of Nevada, Reno (UNR). The primary objective of this RET site is to explore unique ways to engage middle and high school teachers in summer research experiences that emphasize cybersecurity. The teachers will spend six weeks in the summer participating in research experiences and developing classroom modules and materials which will be implemented in their classrooms during the academic year. The UNR team will use inter-personal role-playing and cybersecurity games to help the teachers learn about cybersecurity and its importance to our nation. The project involves a partnership between the university, the school districts in the surrounding Nevada counties, industrial associates, and the Nevada Department of Education. The project will develop a community of teachers who are passionate about cybersecurity and who can translate this excitement to their students through engaging, high-quality inquiry learning experiences. This RET Site is co-funded by the Secure and Trustworthy Cyberspace (SaTC) program.
The project is anchored by a research area this is compelling and exciting for teachers and K-12 students and by faculty team that has demonstrated expertise in both research and education. The goals of the project are to: recruit a cohort of middle and high school teachers interested in introducing cybersecurity and computer science topics into their classrooms; engage the recruited teachers in research experiences with applications in various modern day systems and security; develop instructional modules that can be incorporated into a variety of grades/classes; initiate collaboration and engagement with all schools in Nevada and other stakeholders in the country to promote and disseminate the results to a large group of middle and high school teachers; and sustain long term partnerships between the RET Site teacher participants, the UNR mentor team and industry partners, in order to bring the excitement of computing, problem solving and research to students and encourage them to pursue STEM related careers. The site features projects that are teacher accessible as well as connected to current research and practice. The RET site includes sound evaluation and dissemination plans that will provide models for integrating cybersecurity concepts into the middle and high school curricula. Teachers will develop and hone their research, communication, and presentation skills, all of which are essential to their professional growth and success. The project will build the technical capacity of teachers so they are capable of developing and implementing new, exciting inquiry-based learning activities at their schools. The project team will disseminate the project materials through the TeachEngineering digital library and a dedicated local website and server repository that will be shared with a wider audience of teachers at annual workshops and meetings. The team will also disseminate project results through high-quality journals and professional meetings.
- Our Promise
- Our Achievements
- Our Mission
- Proposal Writing
- System Development
- Paper Writing
- Paper Publish
- Synopsis Writing
- Thesis Writing
- Assignments
- Survey Paper
- Conference Paper
- Journal Paper
- Empirical Paper
- Journal Support
- Top 5 Interesting Computer Network Research Topics
A computer network is a network of diverse computing hardware linked through different communication technologies to share various resources . The communication links of the network can be either wired (cables) or wireless (radio waves / IR signals).
This page shows you useful information on Computer Network Research Topics, Projects with Source Code, Research Areas, Project Topics, and Tools!!!
Moreover, the network can be differentiated in the characteristics of constrained resources, network structure, requests history/demand, communication technologies , and more. However, it is flexible to share resources, and it has some technical challenges in real-time development. Here, we have given you the common services that we offer for overcoming network issues.
Our Approaches and Services to Solving Computer Network Issues
- Communication technologies selection
- Communication protocols in the network
- Performing both conceptual and practical research
- Study in qualitative and quantitative aspects
- Simulation Models
- Proofs / Theorems / Prototypes Testing / Use Cases
- Experiments for Various Simulation Scenarios
- Graphical / Tabular Representation of Results
- Developing New Techniques
- Thinking Novel Ideas
- Multiple Evaluations
- IEEE Standards Refinement
The layering approach in networking is used to divide the message into various chunks . Basically, there are seven layers in the networking process where each layer has unique responsibilities. All these layers co-operatively work together to transfer the message from one end to another (i.e., source to destination ). Now, we can see the available layers and their function in sequential order.
What are the layers of computer networks?
- Physical Layer – Used for offering mechanical / electrical needs, distribute the bits through transmission medium
- Data Link Layer – Used for offering hop-to-hop distribution, arrange the bits into frames
- Network Layer – Used for offering internetworking, pass over the packets between source and destination
- Transport Layer – Used for offering error correction and process-to-process distribution
- Session Layer – Used for launching and manage temporary sessions
- Presentation Layer – Used for data translation, compression, and encryption
- Application Layer – User for users to access the network resources / services
With an aim to support wireless communications, numerous different technologies have been launched. Before selecting this technology, one should undergo deep study on which is more suitable for their computer network projects . Our research team will help you in both business/individual if you need the best guidance over that selection of innovative computer network research topics . Usually, we recommend the technology based on the requirement of your selected networking projects for final year students . For your information, here we have given you a few lists of communication technologies,
Communication Technologies in Computer Networks
- Wi-Fi and Wi-Max
- Radio Frequency Identification (RFID)
- Ultra-Wideband, Bluetooth and Zigbee
- Global Positioning System (GPS)
- Mobile Communication (4G, 5G, 5G Beyond and 6G)
- Radar and Satellite Communication
- 3GPP – LTE-M, EC-GSM and Narrowband-IoT
- Non-3GPP – Sigfox, Wieghtless and LoRa
In recent days, you can witness the gradual growth of computer networks in networking industries through many new developments. It includes so many technologies to portrait the actual networking industry’s performance. Here, we have given you some new networking technologies that are expected to master the next networking industries. .
Current Technologies in Computer Networks
- Artificial Intelligence (AI) and Cloud Repatriation
- Software Defined Networks
- Fog-Edge Computing
- UAV-Wireless Data Links
- Responsive Internet Architecture
- Multiple Cloud Services Technology
- Internet of Things and Inter-Networking
- Quantum and Serverless Computing
- 5G enabled Nano Technology
- Digital Twin and Machine Learning (ML)
- Digital Communications
- Network Communications Protocols
For illustrative purpose, Digital Communication work in accordance with enabling communication technologies, modulation, signal processing projects, channel modeling, and error control . Similarly, Network Communications Protocols take an in-charge of routing, resource allocation, data distribution, and medium access control.
Both technologies/areas have high capabilities in a different dimension of the networking process. And they are network designing, model construction, networking testing on testbeds, experimental analysis, and performance assessments. Our researchers have given you the currently ongoing of innovative computer network research topics mentioned below for your reference.
Latest Computer Network Research Topics
- Enhancing System Robustness in Decentralized Network
- Improving Network Quality of Services and Resource Usage
- SLA–Aware Resource Scheduling and Provisioning
- Network Architectures Design and Processes Management
How to develop computer networks projects with source code?
Basically, networking is a widespread process where network construction and deployment in the real world is a challenging job. So, the entire process is fragmented into different tasks where they are performed by a set of skilled networking engineers as follows,
- Software Developer – Design and build software applications
- Networking Experts – modeling the network structure
- Database Admin – Store and manage the network information
- Support Specialist – Analyze the connected entities of the system
- Programmer – Develop the suitable code works for achieving required performance
For research purposes, we can simulate the original network behavior and performance inappropriate simulation tools. Most importantly, it reduces the cost of real-time implementation and deployment.
Our developers have long-term experience in handling networking concepts . So, if you need the best Computer Networks Projects with Source Code support , you can approach our team. Below, we have also mentioned our qualified services in your project.
- We do both conceptual and practical study on recent research topics
- We design unique network simulation models, proof-of-concept prototypes and investigational testbeds
- We employ result guaranteed new technologies to upgrade and assess the existing standard of networking systems
- We develop own algorithm, protocols and hybrid techniques based on project requirements
- We precisely access the network performance using suitable network parameters for comparative study of different systems
Performance Analysis of Computer Networks
Now, we can see the performance measurement of the networking model. Through the sophisticated simulation tool / experimental testbeds , we can develop any kind of network scenario. Once the model is processed, then the efficiency of the model is verified by several metrics. Here, we have given you the metrics along with different modelling techniques .
- Medium Access Control – Retransmissions Delay, Collisions and Packet loss
- Network Protocols – Latency, Throughput and Packet loss
- RF Channel Models – Noise, Shadowing and Fading
- Spectrum (Sense and Observation) – Latency and Detection Trustworthiness
- Links and Transceivers – Block error ratio and Signal-to-Noise Ratio (SNR)
What is computer network simulation?
Simulate the network model based on the code of the software application . Through code, we can instruct the model to perform our project requirements. At the end of the simulation, it yields the overall performance and behaviour of the network in different dimensions and metrics. Further, it also measures the communication between the network entities.
Purposes of source code
The source code of software has the main responsibility to create strong basements for designing and simulating the network model . Through the code only, the developers can make the smart work to tackle the problem in a simplified way. Effective code work is also a part of the contribution in research.
Since your code can help for learning or reusability (other application development), for your clarity, our developers will explain the implementation of research methodologies while delivering Computer Networks Projects with Source Code . Below, we have given you the different simulations of real-time network models,
How does computer network simulation works?
- Plan and design the model
- Develop the suitable hypothesis model
- Forecast the hypothetical aspects
- Perform comparative study to improve the hypothesis
- Simulate the developed model
- Based on experimental results, relate and enhance the hypothesis / model
- Do the experiments and get the results
So far, we have discussed computer networks, network layers, communication technologies, current research areas, computer network research topics, project simulation, and performance estimation . Now, our development team has a list of widely used network simulator tools.
Network simulators let the users modify the simulator operations for their project needs. Then the users can analyze the system performance and entity behavior under different circumstances. Further, it supports communication standards/protocols like TCP, WLAN, CR, Wi-Max, WSN , and many more. Here, we have given you the list of a few best result yielding simulators which is more apt for computer network simulations,
- Component-based network simulator with graphical user interface support
- Allow to design traffic models, decentralized system, protocols, computer networks, multi-processors, and many more
- Further, it enables animated and responsive simulation in modular environs
- Empower to design and deploy network application, device and infrastructure
- Develop predictive model, protocol and communication networks to interpret the network functionalities
- Support both real-time wired and wireless models
- Allow to create Finite State Automata for figuring out the network behavior
- Easy to design and develop traffic models
- Utilize QualNet analyzer to understand the obtained simulated outcome
- Enabled OS: Linux and Windows
For instance, NS3 (network Simulator 3) is detailed here.
NS3 is one of the best simulation tools to design and simulate networking projects . With the help of this tool, we can virtually design different nodes through Helper classes. By the by, it enables the installation of internet stacks, applications, devices, and many more. Further, we can insert parameters in the channel for performance evaluation in implementing computer network research topics . And let them produce traffic at runtime and pass the packets from source to destination through the selected route path. The other special features are given as follows,
- Create pcap file to get the core information of the transmitting packets. For instance: Source IP, Sequence no, Destination IP, etc. Employ Wireshark tool to view the pcap.
- Trace the network route for assess number of packets send/receive. For this purpose, the trace files will be produced automatically to monitor whole network.
- Easy to plot the graph from obtained simulation outcome in with assurance of preciseness.
- Network Animator is released to depict the realistic view of the network through animation. It shows you the real structure and how the data are transferred between nodes.
To sum up, we have sufficient technical professionals to support you in all the latest research areas of computer networks . In addition, our developments also give you the best assistance in project development from tool selection to result in an assessment. So, if you need our reliable service computer network research topics, projects with source code then communicate our team.
MILESTONE 1: Research Proposal
Finalize journal (indexing).
Before sit down to research proposal writing, we need to decide exact journals. For e.g. SCI, SCI-E, ISI, SCOPUS.
Research Subject Selection
As a doctoral student, subject selection is a big problem. Phdservices.org has the team of world class experts who experience in assisting all subjects. When you decide to work in networking, we assign our experts in your specific area for assistance.
Research Topic Selection
We helping you with right and perfect topic selection, which sound interesting to the other fellows of your committee. For e.g. if your interest in networking, the research topic is VANET / MANET / any other
Literature Survey Writing
To ensure the novelty of research, we find research gaps in 50+ latest benchmark papers (IEEE, Springer, Elsevier, MDPI, Hindawi, etc.)
Case Study Writing
After literature survey, we get the main issue/problem that your research topic will aim to resolve and elegant writing support to identify relevance of the issue.
Problem Statement
Based on the research gaps finding and importance of your research, we conclude the appropriate and specific problem statement.
Writing Research Proposal
Writing a good research proposal has need of lot of time. We only span a few to cover all major aspects (reference papers collection, deficiency finding, drawing system architecture, highlights novelty)
MILESTONE 2: System Development
Fix implementation plan.
We prepare a clear project implementation plan that narrates your proposal in step-by step and it contains Software and OS specification. We recommend you very suitable tools/software that fit for your concept.
Tools/Plan Approval
We get the approval for implementation tool, software, programing language and finally implementation plan to start development process.
Pseudocode Description
Our source code is original since we write the code after pseudocodes, algorithm writing and mathematical equation derivations.
Develop Proposal Idea
We implement our novel idea in step-by-step process that given in implementation plan. We can help scholars in implementation.
Comparison/Experiments
We perform the comparison between proposed and existing schemes in both quantitative and qualitative manner since it is most crucial part of any journal paper.
Graphs, Results, Analysis Table
We evaluate and analyze the project results by plotting graphs, numerical results computation, and broader discussion of quantitative results in table.
Project Deliverables
For every project order, we deliver the following: reference papers, source codes screenshots, project video, installation and running procedures.

MILESTONE 3: Paper Writing
Choosing right format.
We intend to write a paper in customized layout. If you are interesting in any specific journal, we ready to support you. Otherwise we prepare in IEEE transaction level.
Collecting Reliable Resources
Before paper writing, we collect reliable resources such as 50+ journal papers, magazines, news, encyclopedia (books), benchmark datasets, and online resources.
Writing Rough Draft
We create an outline of a paper at first and then writing under each heading and sub-headings. It consists of novel idea and resources
Proofreading & Formatting
We must proofread and formatting a paper to fix typesetting errors, and avoiding misspelled words, misplaced punctuation marks, and so on
Native English Writing
We check the communication of a paper by rewriting with native English writers who accomplish their English literature in University of Oxford.
Scrutinizing Paper Quality
We examine the paper quality by top-experts who can easily fix the issues in journal paper writing and also confirm the level of journal paper (SCI, Scopus or Normal).
Plagiarism Checking
We at phdservices.org is 100% guarantee for original journal paper writing. We never use previously published works.
MILESTONE 4: Paper Publication
Finding apt journal.
We play crucial role in this step since this is very important for scholar’s future. Our experts will help you in choosing high Impact Factor (SJR) journals for publishing.
Lay Paper to Submit
We organize your paper for journal submission, which covers the preparation of Authors Biography, Cover Letter, Highlights of Novelty, and Suggested Reviewers.
Paper Submission
We upload paper with submit all prerequisites that are required in journal. We completely remove frustration in paper publishing.
Paper Status Tracking
We track your paper status and answering the questions raise before review process and also we giving you frequent updates for your paper received from journal.
Revising Paper Precisely
When we receive decision for revising paper, we get ready to prepare the point-point response to address all reviewers query and resubmit it to catch final acceptance.
Get Accept & e-Proofing
We receive final mail for acceptance confirmation letter and editors send e-proofing and licensing to ensure the originality.
Publishing Paper
Paper published in online and we inform you with paper title, authors information, journal name volume, issue number, page number, and DOI link
MILESTONE 5: Thesis Writing
Identifying university format.
We pay special attention for your thesis writing and our 100+ thesis writers are proficient and clear in writing thesis for all university formats.
Gathering Adequate Resources
We collect primary and adequate resources for writing well-structured thesis using published research articles, 150+ reputed reference papers, writing plan, and so on.
Writing Thesis (Preliminary)
We write thesis in chapter-by-chapter without any empirical mistakes and we completely provide plagiarism-free thesis.
Skimming & Reading
Skimming involve reading the thesis and looking abstract, conclusions, sections, & sub-sections, paragraphs, sentences & words and writing thesis chorological order of papers.
Fixing Crosscutting Issues
This step is tricky when write thesis by amateurs. Proofreading and formatting is made by our world class thesis writers who avoid verbose, and brainstorming for significant writing.
Organize Thesis Chapters
We organize thesis chapters by completing the following: elaborate chapter, structuring chapters, flow of writing, citations correction, etc.
Writing Thesis (Final Version)
We attention to details of importance of thesis contribution, well-illustrated literature review, sharp and broad results and discussion and relevant applications study.
How PhDservices.org deal with significant issues ?
1. novel ideas.
Novelty is essential for a PhD degree. Our experts are bringing quality of being novel ideas in the particular research area. It can be only determined by after thorough literature search (state-of-the-art works published in IEEE, Springer, Elsevier, ACM, ScienceDirect, Inderscience, and so on). SCI and SCOPUS journals reviewers and editors will always demand “Novelty” for each publishing work. Our experts have in-depth knowledge in all major and sub-research fields to introduce New Methods and Ideas. MAKING NOVEL IDEAS IS THE ONLY WAY OF WINNING PHD.
2. Plagiarism-Free
To improve the quality and originality of works, we are strictly avoiding plagiarism since plagiarism is not allowed and acceptable for any type journals (SCI, SCI-E, or Scopus) in editorial and reviewer point of view. We have software named as “Anti-Plagiarism Software” that examines the similarity score for documents with good accuracy. We consist of various plagiarism tools like Viper, Turnitin, Students and scholars can get your work in Zero Tolerance to Plagiarism. DONT WORRY ABOUT PHD, WE WILL TAKE CARE OF EVERYTHING.
3. Confidential Info
We intended to keep your personal and technical information in secret and it is a basic worry for all scholars.
- Technical Info: We never share your technical details to any other scholar since we know the importance of time and resources that are giving us by scholars.
- Personal Info: We restricted to access scholars personal details by our experts. Our organization leading team will have your basic and necessary info for scholars.
CONFIDENTIALITY AND PRIVACY OF INFORMATION HELD IS OF VITAL IMPORTANCE AT PHDSERVICES.ORG. WE HONEST FOR ALL CUSTOMERS.
4. Publication
Most of the PhD consultancy services will end their services in Paper Writing, but our PhDservices.org is different from others by giving guarantee for both paper writing and publication in reputed journals. With our 18+ year of experience in delivering PhD services, we meet all requirements of journals (reviewers, editors, and editor-in-chief) for rapid publications. From the beginning of paper writing, we lay our smart works. PUBLICATION IS A ROOT FOR PHD DEGREE. WE LIKE A FRUIT FOR GIVING SWEET FEELING FOR ALL SCHOLARS.
5. No Duplication
After completion of your work, it does not available in our library i.e. we erased after completion of your PhD work so we avoid of giving duplicate contents for scholars. This step makes our experts to bringing new ideas, applications, methodologies and algorithms. Our work is more standard, quality and universal. Everything we make it as a new for all scholars. INNOVATION IS THE ABILITY TO SEE THE ORIGINALITY. EXPLORATION IS OUR ENGINE THAT DRIVES INNOVATION SO LET’S ALL GO EXPLORING.
Client Reviews
I ordered a research proposal in the research area of Wireless Communications and it was as very good as I can catch it.
I had wishes to complete implementation using latest software/tools and I had no idea of where to order it. My friend suggested this place and it delivers what I expect.
It really good platform to get all PhD services and I have used it many times because of reasonable price, best customer services, and high quality.
My colleague recommended this service to me and I’m delighted their services. They guide me a lot and given worthy contents for my research paper.
I’m never disappointed at any kind of service. Till I’m work with professional writers and getting lot of opportunities.
- Christopher
Once I am entered this organization I was just felt relax because lots of my colleagues and family relations were suggested to use this service and I received best thesis writing.
I recommend phdservices.org. They have professional writers for all type of writing (proposal, paper, thesis, assignment) support at affordable price.
You guys did a great job saved more money and time. I will keep working with you and I recommend to others also.
These experts are fast, knowledgeable, and dedicated to work under a short deadline. I had get good conference paper in short span.
Guys! You are the great and real experts for paper writing since it exactly matches with my demand. I will approach again.
I am fully satisfied with thesis writing. Thank you for your faultless service and soon I come back again.
Trusted customer service that you offer for me. I don’t have any cons to say.
I was at the edge of my doctorate graduation since my thesis is totally unconnected chapters. You people did a magic and I get my complete thesis!!!
- Abdul Mohammed
Good family environment with collaboration, and lot of hardworking team who actually share their knowledge by offering PhD Services.
I enjoyed huge when working with PhD services. I was asked several questions about my system development and I had wondered of smooth, dedication and caring.
I had not provided any specific requirements for my proposal work, but you guys are very awesome because I’m received proper proposal. Thank you!
- Bhanuprasad
I was read my entire research proposal and I liked concept suits for my research issues. Thank you so much for your efforts.
- Ghulam Nabi
I am extremely happy with your project development support and source codes are easily understanding and executed.
Hi!!! You guys supported me a lot. Thank you and I am 100% satisfied with publication service.
- Abhimanyu
I had found this as a wonderful platform for scholars so I highly recommend this service to all. I ordered thesis proposal and they covered everything. Thank you so much!!!
Related Pages

- PROJECTS ON COMPUTER NETWORKS
Computer networks are established using different communication technologies like software and crucial network elements such as transceiver antennas. Projects on computer networks are gaining huge importance among final year students and researchers owing to the fact that technological advancements are happening every day. This article will give you a complete picture of computer network projects , and here we provide you with expert answers to many important research questions. Let us first start by understanding the working of computer networks.
WHAT DOES A COMPUTER NETWORK DO?
- The open system interconnection model is the basis on which a device in a computer network incorporates itself into it. The device may include any type of hardware’s which ranges from a switch to a Smartphone.
- For example, a request from a Smartphone for establishing a video call is first forwarded to a switch from where it reaches the server, and finally, the receiver gets the task executed.
The type of network and traffic primary depends on the objective of your research. Based on the aim of your projects on computer networks , the network deployment method also differs. What are the different types of network deployment methods?

COMPUTER NETWORK DEPLOYMENT METHODS
The different types of network deployment methods are listed below
- Incremental
- Deployment based on virtual force
- Based on increment
- Delaunay triangulation
- Random deploymentBased on random distributionAir dropping
In general, the method that you might choose is primarily dependent on your project needs. As we have guided 1000+ projects on computer networks , we are very well aware of the demands, issues, and solutions under various circumstances . If you want to have the list of major project ideas on computer networks, then go through the following.
Our Skills in Computer Networks
The following are the major skills of our experts in computer networks domain .
- Architecture of the network
- Programming and analysis of network
- Novel technological advancements (computer networks)
- Technologies involved in communication
- Networked systems
- Management and operations of network
- Modelling data and networking
- Advanced solutions (next generation)
- Interdisciplinary networking
The above research topics in computer networks are the latest and trending ones. You can expect complete search support from us on all these computer network topics . We are famous among researchers around the world for our devotion and professionalism. Generally, we insist upon building up ‘A grade’ technical understanding about your topic of network attack research. In this regard latest now talk about the important functions while implementing projects on computer networks .
WHAT ARE THE MAJOR FUNCTIONS OF COMPUTER NETWORKS?
A computer network consists of different layers, and each layer is indulged in specific functions as listed below.
- Controlling power
- Managing interference
- Allocation of channels
- CSI acquisition
- Managing network resources
- Sharing spectrum
- Offloading data
- Multiple connections
Innovations are expanding day by day to enhance the computer network functioning at different levels mentioned above. Quite importantly, it becomes necessary for a researcher to have complete knowledge of recent innovations . We are here to give you ultimate guidance for all these research essentials. Now let us understand the use cases of computer network projects.
Interesting Computer Networks Applications
The following are the major applications of computer networks
- Social networking (sharing files, Instantaneous messaging etc)
- Multimedia (video, audio and gaming)
- Other applications (climate data, browsing over web)
The applications of computer networks are not limited to this list. Our customers have successfully implemented their projects on computer networks in real-time with the help of our technical experts. Those implementations can also be added to the interesting Applications of computer networks as mentioned above. Are there any issues that we would have faced while guiding our customers in the design and implementation of computer network projects ?
RESEARCH ISSUES OF COMPUTER NETWORKS
Let us now look into the common research issues for projects on computer networks
- Managing buffer
- Scheme for allocation of resources (and caching)
- Predicting and detecting community
- Enhance the quality
- Improving service grade
- Efficiency in managing power
- Reducing the failure of links
- Forwarding packets
- Methods for evicting content
- Mechanism of duty cycle
- Lightweight cryptography
- Increased speed for transmission
- Controlling the congestion among nodes
In addition to this many research, issues are associated with specific applications for which your project is being designed. In such cases, you might need technical advice from experts to overcome such problems. So you can directly connect with our team of experts at any time to get your query solved. We provide you complete support starting from the very basics.
Major Networking Concepts
Let us now talk about the major networking concepts below
- Handling packets
- Management of network
For more details on these concepts, talk to our research team of experts. Now let us look into the various applications of computer networks !!!
Applications of Computer Networks
Computer networks find major applications in all aspects of daily life. Some of the most important applications of computer networks are listed below
- Security aspects
- QoS essentials
- MAC or multi access control
- Streaming media
- Efficiency of energy
- Wireless access (Fiber)
- Coding in wireless networks
- Wireless multicast
For instance, the Security topic is discussed below.
In the field of wireless communication , computer networks are expected to ensure reliable Security . Consider the following three points while designing network security systems,
- Methods to detect cyber attacks
- Ways of protecting or defending your network
- Methods to prevent such attacks
When you make a planned approach towards your research requirements, you can surely reach out to proper solutions to implement projects on computer networks . In this regard, our team of experts has listed some of the important points that you can go through to find out the best possible solution for many of the research issues.
- Deploying cryptography techniques to avoid eavesdropping attacks
- Cryptography systems (symmetric and asymmetric) provides for sign messages
- Safe distribution of keys
- User authentication and authorizing the user actions
- Holistic security (wireless, email and transport level security applications)
- Intrusion and malware detection
- Management of traffic
Let us now see how artificial intelligence is used in different network operations.
- Data compression (fusing data from multiple sensors and aggregating sensory information)
- Data security (authenticating users and intrusion and spoofing detection)
- Data privacy (differential approach and user location)
As the technology is expanding exponentially it becomes necessary for experts to keep themselves updated. So our dedicated team of research experts always learns about innovations regularly.
Similar to Security, now it is important to have some idea on network routing!!!
OUTLINE OF NETWORK ROUTING
The major purpose of network routing is to find the most suitable route . The following are also main requirements of network routing
- Provides for scaling
- Latency control
- Mobility management
- Reliability
- QoS requirements
The types of network routing are listed below.
- Tables are fixed
- Do not handle changes efficiently and its not suited for dynamic topology
- It cannot be scaled
- Human errors are more
- LCAD (delays in delivery)
- Data centric (cluster based issues and query response network overloading)
- MLHR (capacity problems and single point failure at CH)
- Hard implementation in dynamic networks
- TORA (provisionally non valid results may be produced)
- ZRP (congestion of traffic between the zones and complexity increases with increased difficulty in maintaining UAV vehicles)
- Updated table maintenance
- It is not to be used by networks limited by bandwidth
- Delay is increased due to topology changes
- DSDV (high bandwidth, overheads and updated are used)
- B.A.T.M.A.N (lower performance with network reliability and packet loss dependent)
- GSR, OLSR, FSR (routing loops and increased overheads)
- BABEL (higher bandwidth as a result of regular updates and increased overheads)
- Route finding process leads to increase the latency
- Larger the size of the network, reduced is the scalability while the overhead increases
- Routing table is needed for intermittent nodes
- AODV (with increase in network size band width also increases, delicious expand with more link failure and reduced overhead due to delay in route construction)
- DSR (dynamic networking and killing are are the important issues, provides full address between the source and destination)
- GDSTR – 3D (topology is static)
- GRG (inefficiency in random walk recovery and messages are not delivered)
- GHG (location data is required)
Generally, you should choose the routing protocols to suit your network objectives . You can reach out to our technical team regarding any kinds of doubts on network routing mentioned above. Now let us look into the important research topics in computer networks below.
RESEARCH AREAS ON COMPUTER NETWORKS
The following are the trending areas of research in computer networks.
- Networking defined by software’s
- Named Data Networking
- Cognitive radio networks
- Radio access network
- Wireless sensor networks
- Ad hoc networks like FANET, MANET, VANET
- Optical Communication switching networks
- Cellular networks like LTE, 5G, 6g and LTE A
- Hybrid networks (vehicular sensor networks, SD – WSN and VNDN)
We are here to give you all the essentials to do computer network research projects on the above topics. It is a must for a researcher to have a complete picture of the standards and processes involved in these networks for which authentic sources of references are required. We generally provide benchmark references for you to understand the elements and topology suitable for different computer networks .
MAJOR NETWORK ELEMENTS
Let us now look into the important elements of a network.
- Firewalls (and also IPS, Trusted servers and IDS)
- Interfaces (routers, switches, AP and GW)
- Bridges (remote, local and wireless)
- Nodes (mobiles, sensors, vehicles etc)
Technological advancements can be incorporated into all these important network elements. Reach out to our experts to know the major breakthroughs that happened over time in your research topic . What are the major computer network research topics?
CURRENT TOPICS FOR PROJECTS ON COMPUTER NETWORKS
Let us now look into the current research topics in computer networks.
- Traffic-aware service orchestration (over NFV and SDN)
- Secure integration of MANET and IoT
- Clustering headed by artificial intelligence
- Routing over internet of things
- Resource Management using fog and cloud RAN (over LTE)
- RAN slicing securely
- Secure handoff in 5G core
- Controlling the dissemination of information (in NDN – VANET)
- Energy harvesting wireless sensor networks (for transmitting multimedia)
- RPL amendments (for 6TiSCH IIOT networks)
We are giving research support on all the above topics. Our technical experts are ready to give you complete assistance on all aspects of the above trending computer network projects . Network simulators play a key role in all projects on computer networks. Let us see the best simulation tools below.
BEST NETWORK SIMULATORS
The following are the best network simulation tools that are commonly used by researchers.
- QualNet (configuration of command line and subnet properties)
- OMNET ++ (Compound modules in NED files and parameters with numeric values)
- OPNET (ATM files and Tivoli Net View)
- NS 3 (provides for BRITE interface integration and uses ASCII)
Generally, we focus on the objectives of the research projects on computer networks in order to choose a suitable network simulation tool. We also update our cells regularly regarding new innovations in the simulators . So you can reach out to us regarding any technical support on any kind of simulation tool.
Network simulators are primarily used to understand the outcome or implications of our ideas . Even before making real-time implementations, one can easily get the results of the project performance under various circumstances using simulators . The major purpose for which network simulation tools are used are listed below
WHY TO USE NETWORK SIMULATIONS?
- Visualization of packet flow in a network
- Analyzing the network performance in different situations
- Conducting tests on novel network topologies
- Hybrid network designing and validation
- Evaluating the project performance under different metrics
Usually, researchers prefer to use one or more simulation tools in their projects . This is to complement one another’s limitations. In such cases, researchers reach out to experts for their viewpoint. We have handled so many such situations successfully. So you can interact with our technical team to get guidance regarding the use of simulation tools.
HOW TO CHOOSE THE BEST TOOL FOR COMPUTER NETWORK PROJECTS?
Researchers usually prefer update and simulation tools for their computer network projects. Updates on the grounds of flexibility, visualization, protocol, and G.U.I. support are expected. There are some other expectations that must be fulfilled by a simulation tool to be qualified as the best. Refer to the following points about a good simulator, so it becomes easy for you to choose the best simulation tool.
- Network nodes and their deployment
- Channels and links
- Updates in user interface for visualization (GUI)
- Supportive two different network parameters
- Easy to integrate (flexible)
Finding the best tool for simulation becomes an easy task with the help of our experts. Our customers are highly satisfied with the regular updates on both theoretical and practical explanations that we provide regarding the latest advancements in different simulators. Connect with us to avail one of the topmost research guidance to implement projects on computer networks with source code (Guaranteed satisfaction).
Related Pages
Services we offer.
Mathematical proof
Pseudo code
Conference Paper
Research Proposal
System Design
Literature Survey
Data Collection
Thesis Writing
Data Analysis
Rough Draft
Paper Collection
Code and Programs
Paper Writing
Course Work

Quick links
- Find a course
- Request a prospectus
- Undergraduate
Computer Networks and Security BSc
Search the website.
Develop high-level skills for designing and building secure computer networks. Gain industry-recognised certifications, and first-class placement and career opportunities
Register your interest
- Book an open day
/0x0:2200x1610/prod01/channel_3/media/middlesex-university/courses-images/ug---course-masthead-images/2024X2f25/science-and-technology/Computer-Networks-and-Security-BSc-Masthead.jpg)
Viewing course details for 2024 year of entry
- Course overview
About your course
- Teaching and learning
- Facilities and Support
Entry Requirements
- Fees and Funding
- Download prospectus
Why choose Computer Networks and Security BSc at Middlesex?
In an increasingly interconnected digital world, strong computer networks are more important than ever. This course will help you build the skills and confidence to handle real-world IT issues including Cyber security.
You’ll develop your professional skills with a year-long, paid work experience placement as part of a four-year study option.
We have strong links with industry giants like Cisco, Lucent Technologies, Huawei, Xilinx and Jupiter Networks. We are an accredited Cisco and Huawei training Centre.
What you will gain
After graduating from this course, you will have developed in-demand skills which will help you adapt to the ever-changing computer networking landscape.
You'll gain practical competencies in network design and security and learn how to develop mobile internet applications and services.
You'll also have the opportunity to achieve industry-recognised certifications, including Cisco's CCNA and CCNP.
At a time when cyber security is of utmost importance, you will learn to strengthen and defend your networks from malicious attacks.
What you will learn
You’ll learn how to reduce security threats to networks, and develop the skills to design and implement internet and network applications.
Throughout your Computer Networks and Security degree, you’ll put your skills to the test with hands-on experiments in our Cisco, Xilinx, and mobile communication labs. And you'll also have access to observation control rooms andtest areas in the networking labs.
We have taken a more radical approach to teaching this course than other universities, in order to improve your learning.
Our approach includes:
- Using practical, problem-led sessions that reflect the way Computer Networking occurs in the real world, to help you develop an appreciation of the key topics of the discipline
- Integrating Security throughout the course and using programming to set up and control operation of routers and switches
- Using examples, challenges, mini-projects and case studies in the first year to provide an opportunity for multiple topics to be introduced and investigated
- Allowing you to dictate the pace of learning.
The course explores the principles of up-to-date network systems and focuses on key operational and technical aspects. Core modules such as Data Communications, Computer Networks, and Programming and Problem Solving for Communications are covered in this course. You will have the opportunity to put what you've learned to practical use and make valuable industry contacts; even more so if you decide to complete a work experience placement in your second year.
- Placement year - Optional
Computer Systems Architecture and Operating Systems (30 credits) - Compulsory
This module provides you with fundamental knowledge and principles of computer hardware and operating systems in order to understand the structure and operation of modern computers.
The module aims to provide you with an understanding of the fundamental behaviour and components (hardware and software) of a typical computer system, and how they collaborate to manage resources and provide services in scales from small embedded devices up to the global internet.
The module will focus on the understanding of concepts, theory and associated terminology of two core components: ‘Computer Architecture’ and ‘Operating Systems and Networks’. Practical hands-on laboratory experiments will be used to illustrate the application of theory and concepts.
The lab work ranges between using C code, Batch, Bash and Python. This will allow you to develop a range of programming skills that will support your knowledge and skills not only in this module but in future studies as well.
Computer Networks (30 credits) - Compulsory
This module provides you with the basic skills needed to succeed in networking-related degree programs and also helps you develop the skills necessary to fulfil the job responsibilities of network technicians, network administrators, and network engineers. It provides a theoretically-rich, hands-on introduction to networking and the Internet.
You will learn both the practical and conceptual skills that build the foundation for understanding basic networking. And you will gain an understanding of the “layered” approach to networks by examining the OSI and TCP/IP models in detail. Among the topics covered will be the various network devices, network addressing schemes and the types of media used to carry data across the network.
You will also gain a better understanding of routing protocols and learn how to configure, verify, and troubleshoot routing operations.
Science, Technology, Engineering and Mathematics (STEM) (30 credits) – Compulsory
The overall aim of the module is to provide you with the knowledge and skills required for the theoretical understanding of inter-communicating computer systems. This is achieved through the study of relevant general mathematical and scientific principles. These principles are applied to illustrate the operation of hardware components such as logic gates, processors, controllers and data storage devices; communication channels and network concepts.
The module ensures that you are suitably equipped with the theoretical underpinnings needed for the proper understanding of subsequent course modules.
Programming for Data Communication and Networks (30 credits) – Compulsory
This module introduces fundamental computational concepts and programming constructs relevant to understanding and use of a range of widely used programming languages.
The main aim is to provide you with the opportunity to learn programming effectively. This takes place in the context of learning to solve a range of problems arising in the context of the processing, storing and transmitting data.
You will understand the role of a basic but important range of data structures and types, and their use. Several data structures of interest within the networking and security fields will be considered, for example those to represent RTP packets (and associated operations on these), and how audio-visual data can be sent using transport protocols such as the UDP protocol.
The concept of an algorithm is introduced early on together with the techniques for program implementation. You will be encouraged and supported in undertaking - both individually and within a small group setting - a variety of problem solving tasks.
Project Management and Professional Practice (30 credits) - Compulsory
The aim of this module is for you to gain knowledge of professional project management in the context of your degree and future profession.
You will use your newly acquired professional project management knowledge to participate in a ‘real world’ group project, relevant to your level of study.
The module will focus on all aspects of professional practice including project management. In addition, you will study ethical, legal, regulatory, organisational and business issues in order to further your employability within the computer and networking world.
Network Practices and Operations (30 credits) - Compulsory
This module provides you with the skills needed to succeed in networking-related degree programs and also helps you develop the skills necessary to fulfil the job responsibilities of network technicians, network administrators, and network engineers.
The primary focus of this module is regarding the architecture, components, operations of routers and switches, the WAN technologies, and network services in a large and complex network.
You will also develop knowledge regarding networking and network security trends, including Cloud, virtualisation, and SDN.
Network and Protocol Analysis (30 credits) - Compulsory
The module looks at Network and Protocol Analysis and attempts to cover all aspects of Networking and Protocols including Internet Protocols, Network Services and Cloud Environments as well as Network Monitoring and Analysis.
The main goal of the module is to equip you with the ability to build and analyse any networking environment independent of the underlying physical networking technology.
Internet Protocols are the backbone of global communications and will be thoroughly examined in this course: including ARP, IP, UDP and TCP.
This is then followed by the examination of the use of Network services including DNS, DHCP and CIFS as well as Cloud Environments.
The course then looks at the Y-Comm Framework, which combines communication, mobility, quality-of-service and security. The course finishes by looking at issues of network monitoring, network analysis and network performance.
Data Communications (30 credits) - Compulsory
This module addresses the fundamental principles of electronic communication, particularly in relation to digital data.
A key development in the last decade has been the seamless integration of many different data types (documents, images, speech etc.) onto common communication platforms.
These communication platforms (legacy hardwired telephone connections, wired and wireless computer networks, broadcast television, mobile phone systems to name but a few) have themselves spawned new functionality so that we are now able to access any data/function on any device, almost anywhere.
The main aim of the module is to provide you with an operational understanding of how current communication systems work, and specifically how we can communicate information over any distance with a high degree of accuracy and reliability. As part of this, encoding data, capacity, data compression, bandwidth, security and cryptography are covered.
Supervised Industrial Placement (120 credits)
The overall aim of the module is to provide a minimum of nine months and a maximum of 15 months experience in a relevant work placement.
The specific aims of this module are to enable you to:
- Experience a technical employment role in a real work setting
- Apply theoretical knowledge to the solution of practical problems
- Build your skills to assess practical problems effectively and provide well-grounded solutions
- Develop and enhance your professional qualities, to work in a management structure, to develop team skills and communication skills;
- Develop the maturity that will enable you to perform well in your final year;
- Develop the skills of autonomous learning
Individual Project (30 credits) - Compulsory
The primary aim of this module is to give you the opportunity to demonstrate how effectively you have consolidated your knowledge and skills from all other modules via an individual project, which must involve a computer / network / communication solution or a cyber security solution or a digital forensic investigation method.
Network Security (30 credits) - Compulsory
This module aims to examine some of the weaknesses that are found in network systems and the methods and attacks that threaten networks today.
It also examines ways to secure such networks through network design and available tools to resist attackers.
Advanced Networking (30 credits) - Compulsory
This module is designed to equip you with the knowledge and skills needed to plan, implement, secure, maintain, and troubleshoot converged enterprise networks.
You will learn how to implement complex enterprise LAN and WAN routing and switching solutions.
Comprehensive labs emphasise hands-on learning and practice to reinforce configuration skills using a range of routing protocols in IPv4 and IPv6 environments and the secure integration of VLANs, WLANs, voice, and video into campus networks.
The course also covers the configuration of secure routing solutions to support branch offices and mobile workers.
The module reflects the job skills and responsibilities that are associated with professional-level job roles such as network engineer, systems engineer, network support engineer, network administrator, and network consultant.
Enterprise Networking and Automation (30 credits) - Optional
This module is designed to equip you with the knowledge and skills related to designing, securing, operating, and troubleshooting enterprise networks.
This module also covers wide area network (WAN) technologies, introduces software-defined networking, virtualisation, and automation concepts that support the digitalisation of networks.
Extensive labs emphasise hands-on learning and practice to reinforce the skills to configure and troubleshoot enterprise networks.
Network Management & Disaster Recovery (30 credits) - Optional
This module is designed to equip you with the knowledge and skills needed to consolidate many computer networking concepts and introduces elements of network design, equipment selection and configuration, and LAN and WAN addressing.
An integrated case study presents critical thinking scenarios to help you develop skills such as analysing business objectives, determining technical requirements and constraints, planning timelines and resources, and preparing and delivering customer presentations.
This module also shows you how to ensure that a network is restored to its normal state as rapidly as possible.
The module reflects the job skills and responsibilities that are associated with entry-level career opportunities in networking.
Security and Network Forensics (30 credits) - Optional
This aim of the module is to provide an understanding of both general and advanced areas related to network security, cyber security, and network forensics.
It looks at issues, such as, threats and security attacks, vulnerabilities, cryptography, security tools, software security, network attacks and defences, countermeasures, web-based security, network forensic analysis, and security in cloud computing.
Sign up to receive the latest information about studying at Middlesex University London.
Our communications are designed to support you in deciding your future and keep you up to date about student finance, employment opportunities and student activities available at Middlesex University.
We're taking an innovative approach to teaching computer networks at Middlesex, which uses practical, problem-led sessions to reflect the way computer networks exist in the real world. Programming is integrated throughout the year, and you will attend lectures, workshops and tutorials. You will also learn through practical experience during supervised laboratory work, as well as your own guided research. You'll be taught by an experienced teaching team who have a wide range of expertise and professional experience, and who are also Cisco certified (CCNA, CCNP) instructors You will learn your subject by attending lectures, seminars and practical workshops. Staff-Student contact time on Hendon campus is 12 hours per week, normally timetabled over 3 days. Your work will be divided into credits. Each credit is equal to 10 hours of study time. You will complete 120 credits per year of study, which are broken down into modules of typically 30 credits.
- How we'll teach you
Coursework and assessments
Teaching vs independent learning.
Outside of teaching hours, you’ll learn independently through self-study which will involve reading articles and books, working on projects, undertaking research, and preparing for assessments including coursework, presentations and exams.
Your independent learning is supported by the library and study hub, laptop hire, and with online materials in MyUniHub.
Here is an indication of how you will split your time.
Academic support
Our excellent teaching and support teams will help you develop your skills from research and practical skills to critical thinking. Our Sheppard Library is open 24 hours a day during term time. And we offer free 24-hour laptop loans with full desktop software, free printing and Wi-Fi to use on or off campus.
The balance between the two will depend on which modules you are taking. The table below is a good approximate guide.
We'll test your understanding and progress with informal and formal tests.
The informal tests usually take place at least once per module, from which you’ll receive feedback from your tutor. The grades from these tests don’t count towards your final marks.
There are formal assessments for each module, usually at the end, which will count towards your module and your final marks.
Assessments are reviewed annually and may be updated based on student feedback or feedback from an external examiner.
To help you achieve the best results, we will provide regular feedback.
/0x0:1050x1407/prod01/channel_3/media/middlesex-university/courses-images/ug-courses/facilities/north-london-campus-banner.jpg)
North London campus
Our north London campus is 23 minutes away by underground train, travelling from London Kings Cross.
Course Facilities
You will have access to a wide range of advanced equipment and software. Facilities include internetworking labs equipped with Cisco units, blade servers and high-end simulation software, as well as state-of-the-art telecommunications equipment.
/prod01/channel_3/media/middlesex-university/courses-images/ug-courses/science-and-technology/computer-science/Computing-and-Communication-Engineering-Labs-body.jpg)
Student support
We offer lots of support to help you while you're studying including financial advice, wellbeing, mental health and disability support.
Additional needs
We'll support you if you have additional needs such as sensory impairment or dyslexia. And if you want to find out whether Middlesex is the right place for you before you apply, get in touch with our Disability and Dyslexia team .
Our specialist teams will support your mental health. We have free individual counselling sessions, workshops, support groups and useful guides.
Work while you study
Our Middlesex Unitemps branch will help you find work that fits around uni and your other commitments. We have hundreds of student jobs on campus that pay the London Living Wage and above.
Financial support
You can apply for scholarships and bursaries and our MDX Student Starter Kit to help with up to £1,000 of goods, including a new laptop or iPad.
We have also reduced the costs of studying with free laptop loans, free learning resources and discounts to save money on everyday things. Check out our guide to student life on a budget .
How can the BSc Computer Networks support your career?
This course opens the door to a career in the rapidly growing network industry. This includes fields such as network design and implementation, network consultancy, internet software applications development and network security. Recent graduates have progressed onto masters courses or have secured jobs with global companies.
As a Computer Networks and Security graduate, you'll have excellent career prospects. The range of potential employers is across the private, public and not-for-profit sectors, and you will be put in contact with Networking recruitment specialists during your final year of study. You'll also have the potential to start your own business.
Graduate roles
Below are just a few examples of the types of careers that you could pursue after graduating with us:
Applications developer
As an applications developer your role will include writing specifications and designing, building, testing, implementing and sometimes supporting applications using computer languages and development tools. You may also specialise in a specific development environment, such as computer games or e-commerce, and you will have in-depth knowledge of a few relevant computer languages.
ICT manager
The role of the ICT manager is to ensure that information technology resources are aligned with the organisation's mission, corporate goals, and the corporate strategic plan. Your role will include developing, maintaining, facilitating and implementing information frameworks in line with a corporate ICT strategy, and supporting policies and defining standards associated with information management.
Network engineer
A network engineer is responsible for installing, maintaining and supporting computer communication networks within an organisation or between organisations. Your role will be to ensure the smooth operation of communication networks in order to provide maximum performance and availability for their users (staff, clients, customers and suppliers).
Software engineer
Software engineers research, design, test, implement and maintain software systems to meet client or employer needs. In this role you will use a variety of computer programming languages and applications, working in teams with other IT professionals, or alone.
Systems developer
Systems developers test systems, diagnose and fix faults, write diagnostic programs, and design and write code for operating systems and software to ensure that they function more efficiently. In this role you may also create systems in response to technical specifications supplied by an IT analyst, often integrating off-the-shelf software packages into existing systems.
IT project manager
An IT project manager specialises in information technology but also in sectors unrelated to IT that rely on IT systems. Their role is to manage the development and implementation of plans to meet business needs and the change control procedures to ensure a smooth transition during the implementation period.
Our Careers and Employability Service , MDXworks will launch you into the world of work from the beginning of your course, with placements, projects and networking opportunities through our 1000+ links with industry and big-name employers in London and globally.
Our dedicated lifetime career support, like our business start-up support programme and funding for entrepreneurs, has been recognized with the following awards:
- The top 20 UK universities for business leaders and entrepreneurs – Business Money, 2023
- A top 10 university for producing CEOs – Novuana, 2023
MDXcelerator Student Start-Up Support
Want to be your own boss? You'll have the chance to pitch your business to gain mentoring and grants of up to £15,000.
Global network
You’ll study with students from 122 countries who’ll hopefully become part of your global network. And after you graduate, we'll still support you through our alumni network to help you progress in your chosen career.
Work placements
Work placements increase your success in the job market – as well as being a fantastic experience. You can further develop your interpersonal skills, build your confidence, and make contact with industry leaders.
By making a good impression during your placement year, you greatly increase your chances of securing a job with the company after graduation. Research shows that 70% of placements result in a graduate job offer.
Our specialist employability service and London location ensure that every year our students and graduates gain prestigious placement opportunities. Past placements have included Thales, IBM, Exponential-e and Reed Exhibitions.
Placements normally run for 8-12 months, and typical salaries paid are £18-22,000 pa or pro rata.
Our entry requirements provide a guide to the qualifications that you’ll need to study our courses. We have a personalised admissions approach and we make fair but aspirational offers. We want you to aim high and achieve great results.
- International entry
- How to apply
Qualifications
At Middlesex, we're proud of how we recognise the potential of future students like you. We make fair and aspirational offers because we want you to aim high, and we’ll support you all the way.
We’ll always be as flexible as possible and take into consideration any barriers you may have faced in your learning. And, if you don’t quite get the grades you hoped for, we’ll also look at more than your qualifications. Things like your work experience, other achievements and your personal statement.
We'll accept T Levels for entry onto our undergraduate degree courses (including our extended courses with a foundation year) with standard application of science requirements and GCSEs in line with UCAS tariff calculation.
Our general entry requirements page outlines how we make offers where we have given a range (e.g. BBB – BBC in A levels), and how you will be made an offer if you are studying a combination of qualifications (e.g. BTEC and A level). In both cases, we will base this on information you’ve provided on your application. Applications from mature candidates without formal qualifications are welcomed, provided they can demonstrate appropriate levels of relevant ability and experience.
Mature students (over 21)
We welcome applications from mature candidates, including those without formal qualifications, provided you can demonstrate relevant experience and ability.
Academic credit
If you have a qualification such as a foundation degree or HND, or have gained credit at another university, you may be able to enter a Middlesex University course in year two or three. Find out how you can transfer courses .
Find out if you have relevant qualifications or work experience we may be able to count this towards your entry requirements.
We don’t offer interviews for this course for entry to foundation year or first year entry. We interview applicants for direct entry in to second and third year.
We welcome students from the UK, EU and all over the world. Join students from over 122 countries and discover why so many international students call our campus home:
- Quality teaching with top facilities plus flexible online learning
- Welcoming north London campus that's only 30 minutes from central London
- Work placements and networking with top London employers
- Career support to get you where you want to go after university
- Global alumni network and connections
112 UCAS points
In addition to qualifications such as A level and International Baccalaureate, we accept a wide range of international qualifications.
Find out more on the relevant country support page . And if you are unsure about the suitability of your qualifications or would like help with your application, please contact your nearest regional office .
English language
You'll need good English language skills to study with us. The most common qualification we accept is the IELTS 6.0 (with minimum 5.5 in all sections). We also normally require Grade C GCSE or an equivalent qualification.
Find out more at our English language requirements page. And, don’t worry If you don't meet our minimum English language requirements, as we offer an intensive pre-sessional English course.
To study with us in the UK, you will need a student route visa .
Please apply via UCAS using UCAS code I124 .
Need help with your application? Check out our undergraduate application page.
Fees & Funding
The fees below are for the 2024/25 academic year:
UK students 1
Full-time: £9,250
Part-time: £77 per taught credit
International students 2
Full-time students: £16,600
Part-time students: £138 per taught credit
Additional costs included
The following course-related costs are included in the fees:
- Free access to the resources, learning materials and software you need to succeed on your course
- Free laptop loans for up to 24 hours
- Free printing for academic paperwork
- Free online training with LinkedIn Learning.
Fees disclaimers
1. UK fees: The university reserves the right to increase undergraduate tuition fees in line with changes to legislation, regulation and any government guidance or decisions. The tuition fees for part-time UK study are subject to annual review and we reserve the right to increase the fees each academic year by no more than the level of inflation.
2. International fees: Tuition fees are subject to annual review and we reserve the right to increase the fees each academic year by no more than the level of inflation.
Any annual increase in tuition fees as provided for above will be notified to students at the earliest opportunity in advance of the academic year to which any applicable inflationary rise may apply.
Student testimonials " Middlesex graduate Damian Milkins is president and co-founder of Control Circle, a global IT services company. Watch a video of Damian discussing his time at Middlesex and his thoughts on our investment in the latest facilities and equipment. " Damian Milkins Alumni
Speak directly with one of our Unibuddy student ambassadors
Unistats information.
Discover Uni provides applicants with Unistats statistics about undergraduate life at Middlesex.
Please select 'see course data' on the following course option to view the full Unistats data for Computer Networks and Security.
- How to apply arrow_forward_ios
- Book an open day arrow_forward_ios
- Get in touch arrow_forward_ios
Explore your prospectus
Take your first step towards the future you want with our guide
Why not explore
Join us to discover more about our range of courses, and get a feel for life at Middlesex for yourself
Accommodation
We’ll help you find your new home in London while you study at Middlesex
Student life
Find out more about what life is like on campus and discover what student life is all about
The university promotes research and encourages students to participate in research projects
Modal video
Monitoring and Evaluation of Kelp Forest Ecosystems in the MLPA Marine Protected Area Network: 2024-2026
The overarching goal of the project is to inform the evaluation and adaptive management of California's network of MPAs. Our specific goals and objectives are largely defined by the evaluation questions identified in Appendix B of the MPAMAP and refined by the Decadal Evaluation Working Group (DEWG), that pertain to shallow rocky reef and kelp forest ecosystems. Guided by these evaluation questions, our proposed approach includes the following elements: (i) continue long-term kelp forest monitoring, (ii) QA/QC collected data and append to the long-term kelp forest dataset, (iii) use these historic and future datasets to reassess and update statistical analyses on MPA performance conducted for the 2022 Decadal Management Review, (iv) reproduce selected updated graphic and textual summaries of analyses, and (v) document datasets and analysis code and submit to appropriate repositories.

- Research Overview
- Research Activities
- Research Resources
- Training & Education
- Collaborate With NCATS
- Funding Overview
- Open Funding Opportunities
- Small Business Programs
- Funding Policy & Operating Guidelines
- Grant Information
- Challenges and Prize Competitions
- Scientific Review
- Conference Grant Information
- Resources for You
- Resources for Researchers
- Resources for Trainees
- Resources for Rare Disease Patients and Advocates
- News & Events Overview
- Newsletters
- Scientific Publications
- Infographics & Fact Sheets
- NCATS Overview
- About Translational Science
- Advisory Committees
- Careers at NCATS
- Director's Corner
- Divisions & Offices
Rare Disease Day at NIH 2024: Showcasing Voices and New Opportunities
April 23, 2024

Attendees at Rare Disease Day at NIH. ( NCATS )
On Feb. 29, 2024 — the rarest day of the year — patients, clinicians, researchers, drug developers and advocates traveled to the NIH main campus or tuned in to NIH VideoCast for Rare Disease Day (RDD) at NIH. More than 2,000 people attended RDD at NIH. Co-sponsored by NCATS and the NIH Clinical Center, the annual event raises awareness about rare diseases and the people they affect. It also highlights NIH partnerships that advance research and new treatments. This year’s event included scientific sessions, patient stories, scientific posters and exhibits, and art and film exhibits.
NIH is working hard to address the significant and often unmet needs of those affected by rare diseases. In her remarks, NIH Director Monica M. Bertagnolli, M.D., emphasized that rare diseases span across NIH’s research portfolio.
“We at NIH believe that caring for people with rare diseases is at the heart of everything that we do,” she said.
RDD at NIH speakers addressed a wide range of topics, including the rare disease diagnostic odyssey, drug repurposing and development, gene therapy, artificial intelligence (AI), and public-private partnerships. Many of their stories highlighted NIH’s integral role in addressing rare diseases from all angles — research, therapeutic development and information sharing.

NCATS Director Joni L. Rutter, Ph.D., talking with Rare Disease Day at NIH attendees. ( NCATS )
“Rare Disease Day is a day to celebrate our successes, to honor those we hold dear and honor those we’ve lost,” said NCATS Director Joni L. Rutter, Ph.D. “And today, we pause, granting ourselves the space for creativity and contemplation, so that tomorrow, we can speed up with a renewed sense of purpose.” Rutter recently published a guest NIH blog post that highlights the need to communicate about rare diseases research.
The Diagnostic Odyssey: Through the Lens of Patients and Caregivers
Dominique C. Pichard, M.D., director of the NCATS Division of Rare Diseases Research Innovation, shared the obstacles she faced in obtaining a diagnosis and treatment for her daughter, who has Rett syndrome . Pichard — a clinician and leader in rare diseases research — advocated for her daughter’s diagnosis. She had recognized that her daughter showed signs of Rett syndrome — a neurodevelopmental condition that is often marked by loss of developmental abilities between 6 to 18 months of age.
Pichard’s concerns were largely dismissed by her daughter’s physicians. “I was not seen; I was not heard,” she recounted. “But in my gut, I knew.”
Almost one year after raising concerns, Pichard finally received a diagnosis for her daughter. Her experience — known as the “diagnostic odyssey” — reflects the struggles faced by families in the rare diseases community. Patients may wait as long as 15 years to receive a correct diagnosis .
Jessica Swanson shared the challenges that her family faced in finding a diagnosis for her daughter, Isla, who began experiencing tonic-clonic seizures at age 7 months. After years without answers, Swanson turned to the Undiagnosed Diseases Network (UDN) . Just before her 10th birthday, Isla was diagnosed with CDKL5-deficiency disorder .

Jessica Swanson shares about her family’s journey to diagnosis at Rare Disease Day at NIH. ( NCATS )
Swanson explained that the diagnosis provided the family with a label, a community and hope for the future. She emphasized the value of building connections with other patients and families. “The absence of a diagnosis left us in a state of perpetual uncertainty, exasperating an emotional toll on our family,” Swanson recounted. “The rare disease community, however, taught us ‘rare’ does not equal ‘alone.’ And there is strength in shared experiences.”
The UDN is a research program that combines basic and clinical research to help individuals who have sought a clinical diagnosis without success — and their families — understand their health conditions. The program is supported by 17 institutes and centers at NIH, including NCATS. It is led by the National Institute of Neurological Disorders and Stroke.
Shortening the diagnostic odyssey is only part of the challenge. Helping all people with rare diseases access treatments in an equitable way is another major effort. Seema R. Lalani, M.D., spoke on Project GIVE (Genetic Inclusion by Virtual Evaluation) , which is funded by NCATS . Project GIVE focuses on a community-based partnership to reduce health disparities and improve access to care for children in Texas’ Rio Grande Valley, a historically underserved region.
Project GIVE uses Consultagene, a patient referral platform that provides educational resources and genetics health care services that have helped families obtain diagnoses and begin treatments. To date, 109 patients have been enrolled in Project GIVE, and 61 families have received whole-genome sequencing results. Thus far, 17 families have received a resolved diagnosis, and 2 have received a partially resolved diagnosis.
Project GIVE is just one example of NCATS’ efforts to foster community engagement, educate providers, and help to reduce health disparities for families affected by rare diseases. During her remarks, Lalani quoted parents of children with rare diseases in the Rio Grande Valley, including this reflection: “Project GIVE gave [us] not only hope but peace of mind. We were able to finally receive a diagnosis after years of trying to find an answer … I can’t put into words how thankful we all are.”
Artificial Intelligence for Rare Diseases: Exploring New Possibilities

Manisha Balwani, M.D., M.S., FACMG; Kimberly A. Moran, Ph.D., M.B.A., CDP; Ewy A. Mathé, Ph.D.; Christine Cutillo, M.M.C.i. ( NCATS )
Speakers also explored AI and its role in rare diseases research. NIH has recognized that AI can assist with data-driven discovery in various areas of biomedical research, including rare diseases. The speakers discussed ways to make AI tools more inclusive and equitable. They shared stories that demonstrated using AI to shorten the diagnostic odyssey, identify patients for clinical trials, and build tools for drug repurposing. They also discussed how to protect patient privacy and enhance data sharing.
Kimberly A. Moran, Ph.D., M.B.A., explained how she uses AI to identify patterns within groups of people with myasthenia gravis , a rare autoimmune neuromuscular disease. Insights from these data may help identify patients who have not yet received a diagnosis for this disorder. Moran explained that AI can help clinicians predict patients’ symptoms and develop personalized treatments. She also emphasized the importance of discussing AI technologies with patients.
Moran noted doctors should explain the implications and potential of patients’ sharing their data. “It’s going to take this entire community — to be educated, to be literate in terms of data and understanding the power,” she said. “We see the rare disease community willing to give their data … but this will come to be a personal choice in the future.”
AI may improve diagnoses, predict the effects of treatments, and match patients to the right treatment, explained Ewy A. Mathé, Ph.D., director of informatics in the NCATS Division of Preclinical Innovation. AI can also help researchers ask new questions to test, find new treatments, and study many diseases at once. Mathé explained how CURE ID , an AI-driven data collection tool built by NCATS and the U.S. Food and Drug Administration (FDA), can help researchers find rare disease treatments among existing drugs.
Public-Private Partnerships: Leveraging Unique Funding Models

Eric P. Hoffman, Ph.D., and Sharon Hesterlee, Ph.D., with Dominique C. Pichard, M.D. ( NCATS )
Public-private partnerships are another key approach that NCATS uses to speed the development of treatments for rare diseases. Eric P. Hoffman, Ph.D., and Sharon Hesterlee, Ph.D., shared how a partnership between NCATS and ReveraGen BioPharma, Inc., led to FDA approval of vamorolone , a drug used to treat Duchenne muscular dystrophy (DMD) .
ReveraGen’s business model for developing vamorolone used venture philanthropy partners rather than venture capital investors. ReveraGen also had a different kind of partnership with NCATS, through its Therapeutics for Rare and Neglected Diseases (TRND) program . TRND supports preclinical development of drugs to treat rare or neglected disorders. With help from the TRND program, ReveraGen demonstrated that the steroid compound VBP15 could be used to treat DMD symptoms with minimal side effects.
Hesterlee explained that the philanthropic model helped ReveraGen obtain funding for a drug that had great potential but had not captured the interest of more traditional investors.
“The community recognized that this was a need, and it was worth doing,” she said. “And so, from that sense, it really worked well to have the nonprofit investment.” Hesterlee and Hoffman emphasized that this partnership model can be used for efforts focused on other rare diseases.
Rare Diseases Research and Resources
The personal and powerful stories from RDD at NIH underscored the breadth and impact of NIH and NCATS rare diseases research and other activities. They also showcased many great research and educational resources, including those below, that the community can access any time.
- Genetic and Rare Diseases (GARD) Information Center
- Platform Vector Gene Therapy (PaVe-GT) Pilot Project
- Bespoke Gene Therapy Consortium
- Rare Diseases Registry Program (RaDaR)
- Somatic Cell Genome Editing Program
- NCATS Toolkit for Patient-Focused Therapy Development
- RARe-SOURCE
Last updated on April 23, 2024
Help | Advanced Search
Computer Science > Computer Vision and Pattern Recognition
Title: embedded representation learning network for animating styled video portrait.
Abstract: The talking head generation recently attracted considerable attention due to its widespread application prospects, especially for digital avatars and 3D animation design. Inspired by this practical demand, several works explored Neural Radiance Fields (NeRF) to synthesize the talking heads. However, these methods based on NeRF face two challenges: (1) Difficulty in generating style-controllable talking heads. (2) Displacement artifacts around the neck in rendered images. To overcome these two challenges, we propose a novel generative paradigm \textit{Embedded Representation Learning Network} (ERLNet) with two learning stages. First, the \textit{ audio-driven FLAME} (ADF) module is constructed to produce facial expression and head pose sequences synchronized with content audio and style video. Second, given the sequence deduced by the ADF, one novel \textit{dual-branch fusion NeRF} (DBF-NeRF) explores these contents to render the final images. Extensive empirical studies demonstrate that the collaboration of these two stages effectively facilitates our method to render a more realistic talking head than the existing algorithms.
Submission history
Access paper:.
- HTML (experimental)
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .

IMAGES
VIDEO
COMMENTS
Ghost-USB-Honeypot project. This effort, focused on nixing malware like Flame that spreads from computer to computer via USB storage drives, got its start based on research from Sebastian Poeplau ...
To associate your repository with the computer-networks topic, visit your repo's landing page and select "manage topics." GitHub is where people build software. More than 100 million people use GitHub to discover, fork, and contribute to over 420 million projects.
Sun, J. (2022) "Computer Network Security Technology and prevention strategy analysis," Procedia Computer Science, 208, pp. 570-576. Zhang, YLiang, R. and Ma, H. (2012) "Teaching innovation in computer network course for undergraduate students with a packet tracer," IERI Procedia, 2, pp. 504-510.
Explore the latest M.Tech project topics in Computer Networks for 2024, featuring trending IEEE base papers. Elevate your research with cutting-edge projects covering diverse aspects of networking, from advanced algorithms to emerging technologies. Discover innovative titles, abstracts, and base papers to stay ahead in the dynamic field of Computer Networks.
Network World is out with a list of the 25 "coolest" computer networking research projects: University labs, fueled with millions of dollars in funding and some of the biggest brains around, are bursting with new research into computer and networking technologies. Wireless networks, computer security and a general focus on shrinking things and making them faster are among the hottest areas ...
Software-Driven Wide Area Networks. Established: February 5, 2014. This project re-imagines and re-engineers wide area networks, to more than double their efficiency and allow flexible sharing of resources. The production WANs at Microsoft are an instantiation of several of the ideas in these publications.
This project will work as mentioned below.First, Client will send a join request to the server to join the multicast group.After that Server will provide station list, site info to the client through TCP. Then whichever station it selects from the station list, it is connected to that station.All the stations are sending data, irrespective of ...
Computer Networks. Computer networks allow computers to communicate with one another, and provide the fundamental infrastructures supporting our modern society. Research on computer networks at Yale improves on essential network system properties such as efficiency, robustness, and programmability. The research spans all networking layers ...
Security. While start-up funding and the emergence of exciting new network startups has fizzled over the past year, research projects at university and other labs continue to sizzle. Here's look ...
Welcome. The Computer Networking Research Lab in the Department of Computer Sciences and Engineering at the University of Minnesota is led by Professor Zhi-Li Zhang. We conduct research on a broad range of topics related to computer and communication networks, helping transform the current best-effort Internet to a more reliable, available, and ...
Projects. As you know, one of the major goals of this class is to understand how networking research is done. To this end, the term project is a major component of 6.829, since that's where you draw upon your knowledge and experience from the course readings and elsewhere to actually do research. This document is intended to ease the process ...
The Networking Research Group focuses on basic and applied research in all areas related to networked systems, mobile computing, sensing, and Internet of Things. Researchers build proof-of-concept systems, engage with academia, publish scientific papers, release software for the research community, and transfer cutting-edge technologies to ...
We develop practical solutions in wireless networks, network security, traffic engineering, congestion control, and routing. At NETMIT we draw on advanced mathematical models to create systems for networks and wireless applications. Recent projects have focused on such topics as spectrum usage, sparse FFT, mobile networks and crowdsourcing.
Along with the environments integrated with networks, our developers have come up with suggestions on the major research areas of networking among the Networking based projects in the current scenario. Top 3 Research areas in Networking: Controlling Real-Time Process: Industrial and aircraft system control
Network research projects are essential for advancing the field of computer networking and solving real-world challenges. However, comparing different projects can be tricky, as they may have ...
Network operations & management. Sensor Networks or Systems. Learning of models from sensor networks. Synchronization and localization. Data storage and query processing. For useful illustration, we study many research articles and literature reviews to find the performance of any research network project topics.
Here's a whirlwind look at some of the wildest and potentially most useful technology research projects from university and vendor labs related to computer networking. Topics Newsletters
PI: Shamik Sengupta, co-PI: David Feil-Seifer. $540,000. September 2015 - August 2019. This funding establishes a new Research Experience for Teachers (RET) Site at the University of Nevada, Reno (UNR). The primary objective of this RET site is to explore unique ways to engage middle and high school teachers in summer research experiences that ...
A computer network is a network of diverse computing hardware linked through different communication technologies to share various resources.The communication links of the network can be either wired (cables) or wireless (radio waves / IR signals).. This page shows you useful information on Computer Network Research Topics, Projects with Source Code, Research Areas, Project Topics, and Tools!!!
Examples of networks may include computer networks [2], social networks [3], the network of things as the Internet of Things (IoT) [4]. The adoption of machine learning is a requirement to bring ...
Technologies involved in communication. Networked systems. Management and operations of network. Modelling data and networking. Advanced solutions (next generation) Interdisciplinary networking. The above research topics in computer networks are the latest and trending ones.
On our Computer Networks and Security BSc degree develop the skills to build secure computer networks, gain industry certifications and placement opportunities, Develop high-level skills for designing and building secure computer networks. ... working on projects, undertaking research, and preparing for assessments including coursework ...
Masked Spatial Propagation Network for Sparsity-Adaptive Depth Refinement. Jinyoung Jun, Jae-Han Lee, Chang-Su Kim. The main function of depth completion is to compensate for an insufficient and unpredictable number of sparse depth measurements of hardware sensors. However, existing research on depth completion assumes that the sparsity -- the ...
Mamba, a recent selective structured state space model, performs excellently on long sequence modeling tasks. Mamba mitigates the modeling constraints of convolutional neural networks and offers advanced modeling capabilities similar to those of Transformers, through global receptive fields and dynamic weighting. Crucially, it achieves this without incurring the quadratic computational ...
The overarching goal of the project is to inform the evaluation and adaptive management of California's network of MPAs. Our specific goals and objectives are largely defined by the evaluation questions identified in Appendix B of the MPAMAP and refined by the Decadal Evaluation Working Group (DEWG), that pertain to shallow rocky reef and kelp forest ecosystems.
Inspired by the Kolmogorov-Arnold representation theorem, we propose Kolmogorov-Arnold Networks (KANs) as promising alternatives to Multi-Layer Perceptrons (MLPs). While MLPs have fixed activation functions on nodes ("neurons"), KANs have learnable activation functions on edges ("weights"). KANs have no linear weights at all -- every weight parameter is replaced by a univariate function ...
Project GIVE uses Consultagene, a patient referral platform that provides educational resources and genetics health care services that have helped families obtain diagnoses and begin treatments. To date, 109 patients have been enrolled in Project GIVE, and 61 families have received whole-genome sequencing results.
The talking head generation recently attracted considerable attention due to its widespread application prospects, especially for digital avatars and 3D animation design. Inspired by this practical demand, several works explored Neural Radiance Fields (NeRF) to synthesize the talking heads. However, these methods based on NeRF face two challenges: (1) Difficulty in generating style ...