
Mickaël Derriey's blog
© 2024 Mickaël Derriey
Powered by Jekyll and GitHub Pages Theme based on Hyde by @mdo with modifications by @todthomson
The consequences of enabling the 'user assignment required' option in AAD apps
Introduction.
Applications in Azure Active Directory have an option labelled “user assignment required”. In this blog post, we’ll talk about how this affects an application.
💡 Quick heads-up — all the examples in this blog post are based on a web application using AAD as its identity provider through the OpenID Connect protocol.
By default, applications created in Azure Active Directory have the “user assignment required” option turned off, which means that all the users in the directory can access the application, both members and guests.
While this might sound like a sensible default, we find ourselves at Readify with a growing number of guests in the directory as we collaborate with people from other companies. Some of our applications contain data that should be available to Readify employees only, so we decided to make use of the “user assignment required” option.
To access this option, in the Azure portal, go to “Azure Active Directory > Enterprise applications > your application > Properties” and the option will be displayed there.
Some of the behaviour changes were expected, but others were not! Let’s go through them.
1. People not assigned to the application can’t use it
Well, duh, isn’t that what the option is supposed to do?!
You’re absolutely right! If someone that hasn’t been explicitly assigned to the application tries to access it, then AAD will reject the authorisation request with a message similar to the following:
AADSTS50105: The signed in user ‘Microsoft.AzureAD.Telemetry.Diagnostics.PII’ is not assigned to a role for the application ‘<application-id>’ (<application-name>)
The message is straightforward and the behaviour expected.
There are several ways to assign someone to the application. I typically use the Azure portal, navigate to “Azure Active Directory > Enterprise applications > my application > Users and groups” and add them there.
2. Nested groups are not supported
This is the first surpise we had. It’s our bad, because it’s well documented on that documentation page in the “Important” note: https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/groups-saasapps
In other words, if you assign a group to an application, only the direct members of that group will gain access to the application. So instead of using our top-level “all employees” type of group, we had to assign several lower-level groups which only had people inside of them.
3. All permissions need to be consented to by an AAD administrator
Applications in Azure Active Directory can request two types of permissions:
- the permissions which are scoped to the end user, like “Access your calendar”, “Read your user profile”, “Modify your contacts” — these permissions are shown to the user the first time they access an application, and they can consent to the application performing those actions on behalf of them;
- another type of permissions usually have a broader impact, outside of the user’s scope, like “Read all users’ profiles” or “Read and write all groups” — those permissions need to be consented to by an AAD administrator on behalf of all the users of the application.
When the access to the application is restricted via the “user assignment required”, an Azure Active Directory administrator needs to consent to all the permissions requested by the application, no matter whether users can normally provide consent for them.
As an example, I created an application with only one permission called “Sign in and read user profile”. After enabling the “user assignment required” option, I tried to log in through my web application and got prompted with a page similar to the screenshot below:
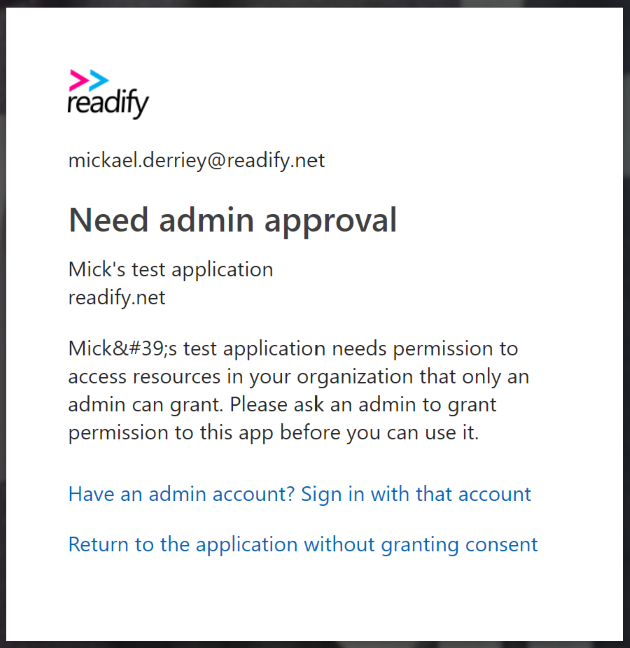
While I don’t fully understand that behaviour, it is alluded to in the tooltip associated with the “user assignment required” option, shortened for brevity and emphasis mine.
This option only functions with the following application types: […] or applications built directly on the Azure AD application platform that use OAuth 2.0 / OpenID Connect Authentication after a user or admin has consented to that application .
The solution is to have an AAD admin grant consent to the permissions for the whole directory. In the Azure portal, go to “Azure Active Directory > Enterprise application > your application > Permissions” and click the “Grant admin consent” button.
4. Other applications not assigned to the application can’t get an access token
It’s not uncommon to see integration between applications. As an example, an application “A” could run a background job every night and call the API of application “B” to get some data.
Before we enabled the “user assignment required” option in application “B”, it was possible for application “A” to request an access token to AAD, allowing it to call the API of application “B”. This is done using the client_credentials OAuth2 flow, where application “A” authenticates itself against AAD with either a client secret (it’s like a password, but an app can have different secrets) or a certificate.
However, after requiring users to be assigned to the application “A”, the token request returns the following error:
AADSTS501051: Application ‘<application-b-id>’ (<application-b-name>) is not assigned to a role for the application ‘<application-a-id>’ (<application-a-name>).
While it’s similar to the first error we talked about in this post, the resolution is different, as the Azure portal doesn’t let us assign applications to another application in the “User and groups” page.
I found the solution in this Stack Overflow answer which advises to take the following steps:
- create a role in application “A” that can be assigned to applications;
- have application “B” request this permission; and
- get an AAD admin to grant consent for the permissions requested by application “B”.
Let’s go through these steps one by one.
4.1 Create a role that can be assigned to applications
If you want to get some background information on AAD app roles, I highly suggest reading the following pages on docs.microsoft.com : Application roles and Add app roles in your application and receive them in the token .
To create a role aimed at applications, we’ll use the “Manifest” page and replace the appRoles property with the following:
4.2 Request that permission in application “B”
Wait, we were talking about creating a role and now we request a permission?
I agree, sorry about the confusion, but the following will hopefully make sense. There’s a change in the terminology we use because assigning that role to application “B” is actually done the other way around, by requesting that role from the settings of application “B”.
To do so, we navigate in the Azure portal to “Azure Active Directory > App registrations > application “B” > Required permissions” and then click on the “Add” button. In the new “Add API Access”, we look for application “A”, select it, then pick the “Access application A” application permissions we created in the previous step:
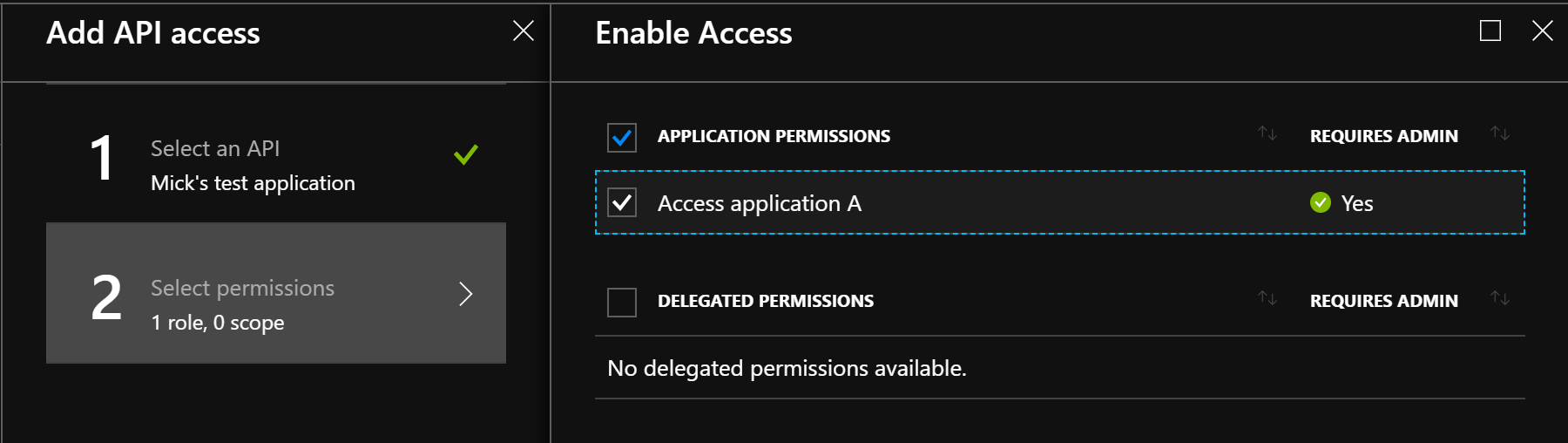
💡 Another heads-up — at the time of writing, the Azure portal has a new App registrations experience in preview. The steps mentioned above are for the GA App registrations blade, but the experience is pretty similar in the preview one. If you want to try it out, follow “App registrations (preview) > application “B” > API permissions > Add a permission > APIs my organization uses > application “A” > Application permissions”, then finally pick the “Access application A” one.
4.3 Grant consent for application “B” to access application “A”
Because there’s no user involved, application permissions automatically require admin consent. Follow the steps taken previously, but this time for application “B”. After doing so, the token request from application “B” to access application “A” will work as expected.
When we first used that “user assignment required” option, I was only expecting unassigned users to be bounced by AAD when trying to log in. Little did I know we would encounter all those “bumps” along the way 🤣.
This was a great learning opportunity, and hopefully it’ll be useful to others.
Related Posts
Ensure node.js opentelemetry instrumentations are compatible with installed packages 08 apr 2024, a new and easy way to use aad authentication with azure sql 23 jul 2021, how to lock down your csp when using swashbuckle 14 dec 2020.
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Azure AD application - User assignment required option enabled, newly added user can't login
We have an application setup to use Azure AD. The 'User Assignment Required' option is enabled because we wanted to restrict access to a specific set of AD users. It's working fine for existing users.
However, we recently added a new user from the Enterprise Applications section for that app, and he is not able to log in. He gets the 'Need admin approval' message. When we disable the 'User Assignment Required' option, it works fine for him as well.
Please advise.
- azure-activedirectory
When you enable the 'User Assignment Required' option you have to give Admin Consent for that Applications permissions. When enabling this option normal users can not give consent on their own anymore, they only can give consent when that option is off. But you probably want that option on so you can control who can access the Application so you need an Admin (Global admin, Cloud Application admin or Application Admin) to give the consent for that App.
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged azure azure-activedirectory ..
- The Overflow Blog
- Why configuration is so complicated
- Is GenAI the next dot-com bubble?
- Featured on Meta
- New Focus Styles & Updated Styling for Button Groups
- Upcoming initiatives on Stack Overflow and across the Stack Exchange network
- Google Cloud will be Sponsoring Super User SE
Hot Network Questions
- What is the formal version of the word "whopping"?
- What legal basis exists for challenging absurd (but technically-correct) invoices?
- How can I draw missing vertical lines in tabular?
- Make the number 606 50 percent bigger
- Why is home ownership so low in Switzerland?
- Braidings on Temperley-Lieb Category
- Transforming an sf feature without M-values into one with M-values
- Create a snail matrix
- What type of cable is this (optic fiber) connecting to router?
- What is this strake near the nose of the MD-80 for?
- Problems with the MIT license - does this fix it?
- Can hotel booking companies make up any "original price" they want, or does the claimed original price have to be somehow grounded in reality?
- Can a function have a set as its value?
- How do parallel reflected rays meet to form image at infinity? If they never meet then how is image formed?
- Booking hotel relative to local or home timezone
- Why is "creating jobs" seen as good and "destroying jobs" seen as bad, even when there are major labour shortages?
- Where can I get an earth-centric map of space?
- PhD supervisor wants to assume my apartment lease and buy my improvements to the apartment when I move out
- How do objects reach terminal velocity?
- Running basement wiring in floor joists
- Why does the USAF still use the C-17 Globemaster III?
- Determining a significant breakpoint in a slope
- How can we arrange data for ListLinePlot?
- Is there a standard which requires a high voltage warning label on a PCB?
- Microsoft Azure
- Google Cloud Platform
- Documentation
- Databricks administration introduction
- Manage users, service principals, and groups
- Sync users and groups from your identity provider
Configure SCIM provisioning using Microsoft Entra ID (formerly Azure Active Directory)
This article describes how to set up provisioning to Databricks using Microsoft Entra ID (formerly Azure Active Directory).
You can set up provisioning to Databricks using Microsoft Entra ID at the Databricks account level or at the Databricks workspace level.
Databricks recommends that you provision users, service principals, and groups to the account level and manage the assignment of users and groups to workspaces within Databricks. Your workspaces must be enabled for identity federation , in order to manage the assignment of users to workspaces. If you have any workspaces that are not enabled for identity federation, you should continue to provision users, service principals, and groups directly to those workspaces.
Provision identities to your Databricks account using Microsoft Entra ID
You can sync account-level users and groups from your Microsoft Entra ID tenant to Databricks using a SCIM provisioning connector.
If you already have SCIM connectors that sync identities directly to your workspaces, you must disable those SCIM connectors when the account-level SCIM connector is enabled. See Migrate workspace-level SCIM provisioning to the account level .
Requirements
Your Databricks account must have the Premium plan or above .
You must have the Cloud Application Administrator role in Microsoft Entra ID.
Your Microsoft Entra ID account must be a Premium edition account to provision groups. Provisioning users is available for any Microsoft Entra ID edition.
You must be a Databricks account admin.
Step 1: Configure Databricks
As a Databricks account admin, log in to the Databricks account console .
Click User Provisioning .
Click Enable user provisioning .
Copy the SCIM token and the Account SCIM URL. You will use these to configure your Microsoft Entra ID application.
The SCIM token is restricted to the Account SCIM API /api/2.0/accounts/{account_id}/scim/v2/ and cannot be used to authenticate to other Databricks REST APIs.

Step 2: Configure the enterprise application
These instructions tell you how to create an enterprise application in the Azure portal and use that application for provisioning. If you have an existing enterprise application, you can modify it to automate SCIM provisioning using Microsoft Graph . This removes the need for a separate provisioning application in the Azure Portal.
Follow these steps to enable Microsoft Entra ID to sync users and groups to your Databricks account. This configuration is separate from any configurations you have created to sync users and groups to workspaces.
In your Azure portal, go to Microsoft Entra ID > Enterprise Applications .
Click + New Application above the application list. Under Add from the gallery, search for and select Azure Databricks SCIM Provisioning Connector .
Enter a Name for the application and click Add .
Under the Manage menu, click Provisioning .
Set Provisioning Mode to Automatic.
Set the SCIM API endpoint URL to the Account SCIM URL that you copied earlier.
Set Secret Token to the Databricks SCIM token that you generated earlier.
Click Test Connection and wait for the message that confirms that the credentials are authorized to enable provisioning.
Click Save .
Step 3: Assign users and groups to the application
Users and groups assigned to the SCIM application will be provisioned to the Databricks account. If you have existing Databricks workspaces, Databricks recommends that you add all existing users and groups in those workspaces to the SCIM application.
Go to Manage > Properties .
Set Assignment required to No . Databricks recommends this option, which allows all users to sign in to the Databricks account.
Go to Manage > Provisioning .
To start synchronizing Microsoft Entra ID users and groups to Databricks, set the Provisioning Status toggle to On .
Go to Manage > Users and groups .
Click Add user/group , select the users and groups, and click the Assign button.
Wait a few minutes and check that the users and groups exist in your Databricks account.
Users and groups that you add and assign will automatically be provisioned to the Databricks account when Microsoft Entra ID schedules the next sync.
If you remove a user from the account-level SCIM application, that user is deactivated from the account and from their workspaces, regardless of whether or not identity federation has been enabled.
Provision identities to your Databricks workspace using Microsoft Entra ID (legacy)
This feature is in Public Preview .
If you have any workspaces not enabled for identity federation , you should provision users, service principals, and groups directly to those workspaces. This section describes how to do this.
In the following examples, replace <databricks-instance> with the workspace URL of your Databricks deployment.
You must be a Databricks workspace admin.
Step 1: Create the enterprise application and connect it to the Databricks SCIM API
To set up provisioning directly to Databricks workspaces using Microsoft Entra ID, you create an enterprise application for each Databricks workspace.
As a workspace admin, log in to your Databricks workspace.
Generate a personal access token and copy it. You provide this token to Microsoft Entra ID in a subsequent step.
Generate this token as a Databricks workspace admin who is not managed by the Microsoft Entra ID enterprise application. If the Databricks admin user who owns the personal access token is deprovisioned using Microsoft Entra ID, the SCIM provisioning application will be disabled.
Click + New Application above the application list. Under Add from the gallery , search for and select Azure Databricks SCIM Provisioning Connector .
Enter a Name for the application and click Add . Use a name that will help administrators find it, like <workspace-name>-provisioning .
Set Provisioning Mode to Automatic .
Enter the SCIM API endpoint URL. Append /api/2.0/preview/scim to your workspace URL:
Replace <databricks-instance> with the workspace URL of your Databricks deployment. See Get identifiers for workspace objects .
Set Secret Token to the Databricks personal access token that you generated in step 1.
Optionally, enter a notification email to receive notifications of critical errors with SCIM provisioning.
Step 2: Assign users and groups to the application
Set Assignment required to Yes . Databricks recommends this option, which syncs only users and groups assigned to the enterprise application.
In the future, users and groups that you add and assign are automatically provisioned when Microsoft Entra ID schedules the next sync.
Do not assign the Databricks workspace admin whose personal access token was used to configure the Azure Databricks SCIM Provisioning Connector application.
(Optional) Automate SCIM provisioning using Microsoft Graph
Microsoft Graph includes authentication and authorization libraries that you can integrate into your application to automate provisioning of users and groups to your Databricks account or workspaces, instead of configuring a SCIM provisioning connector application.
Follow the instructions for registering an application with Microsoft Graph . Make a note of the Application ID and the Tenant ID for the application
Go to the applications’s Overview page. On that page:
Configure a client secret for the application, and make a note of the secret.
Grant the application these permissions:
Application.ReadWrite.All
Application.ReadWrite.OwnedBy
Ask a Microsoft Entra ID administrator to grant admin consent .
Update your application’s code to add support for Microsoft Graph .
Provisioning tips
Users and groups that existed in the Databricks workspace prior to enabling provisioning exhibit the following behavior upon provisioning sync:
Are merged if they also exist in Microsoft Entra ID
Are ignored if they don’t exist in Microsoft Entra ID
User permissions that are assigned individually and are duplicated through membership in a group remain after the group membership is removed for the user.
Users removed from a Databricks workspace directly, using the Databricks workspace admin settings page:
Lose access to that Databricks workspace but may still have access to other Databricks workspaces.
Will not be synced again using Microsoft Entra ID provisioning, even if they remain in the enterprise application.
The initial Microsoft Entra ID sync is triggered immediately after you enable provisioning. Subsequent syncs are triggered every 20-40 minutes, depending on the number of users and groups in the application. See Provisioning summary report in the Microsoft Entra ID documentation.
You cannot update the username or email address of a Databricks workspace user.
The admins group is a reserved group in Databricks and cannot be removed.
You can use the Databricks Groups API or the Groups UI to get a list of members of any Databricks workspace group.
You cannot sync nested groups or <entra-service-principal>s from the Azure Databricks SCIM Provisioning Connector application. Databricks recommends that you use the enterprise application to sync users and groups and manage nested groups and service principals within Databricks. However, you can also use the Databricks Terraform provider or custom scripts that target the Databricks SCIM API in order to sync nested groups or <entra-service-principal>s.
Troubleshooting
Users and groups do not sync.
If you are using the Azure Databricks SCIM Provisioning Connector application:
For workspace-level provisioning: In the Databricks admin settings page, verify that the Databricks user whose personal access token is being used by the Azure Databricks SCIM Provisioning Connector application is still a workspace admin user in Databricks and that the token is still valid.
For account-level provisioning: In the account console verify that the Databricks SCIM token that was used to set up provisioning is still valid.
Do not attempt to sync nested groups, which are not supported by Microsoft Entra ID automatic provisioning. For more information, see this FAQ .
<entra-service-principal>s do not sync
The Azure Databricks SCIM Provisioning Connector application does not support syncing service principals.
After initial sync, the users and groups stop syncing
If you are using the Azure Databricks SCIM Provisioning Connector application: After the initial sync, Microsoft Entra ID does not sync immediately after you change user or group assignments. It schedules a sync with the application after a delay, based on the number of users and groups. To request an immediate sync, go to Manage > Provisioning for the enterprise application and select Clear current state and restart synchronization .
Microsoft Entra ID provisioning service IP range not accessible
The Microsoft Entra ID provisioning service operates under specific IP ranges. If you need to restrict network access, you must allow traffic from the IP addresses for AzureActiveDirectory in this IP range file . For more information, see IP Ranges .


- Intro to Decisions
- Installing Decisions
- Organize a Meeting & Create Agenda
- Run a Meeting
- Meeting Roles & Access
- Meeting List
- Agenda Builder
- Agenda sub-items
- Manage Participants
- Tasks (Microsoft Planner)
- Logging a Decision
- In-meeting Experience
- Meeting Minutes
- Meeting Engagement Score™️
- Time Tracker
- Meeting Book
- Meeting Planner
- Ordered Speaker List
- Meeting Feedback Score
- Functionality
- Recurring meetings
- Delegate Access & Shared Calendar/Mailbox
- AI tools (MeetingCulture.ai)
- Secure Voting
- Case Submission
- Annotations
- Decisions for Teams
- Decisions for Outlook
- Decisions Mobile Apps
- Vote Now for Teams
- Speak Now for Teams
- Using Office 365
- Troubleshoot
- Customization
- Initial setup and Configurations
- Settings and Customizations
- Requirements
- Admin Portal
- Microsoft Intune
- Microsoft App Source / Marketplace
- Security & Trust
- Public Meetings
- Executive Assistant
- Meeting Attendee
- Product Updates
- Help Center
Managing access for users and groups in Azure Active Directory
If you want to limit access to decisions to only a few selected users, this guide shows you how to do so using existing security controls in azure active directory (ad)..
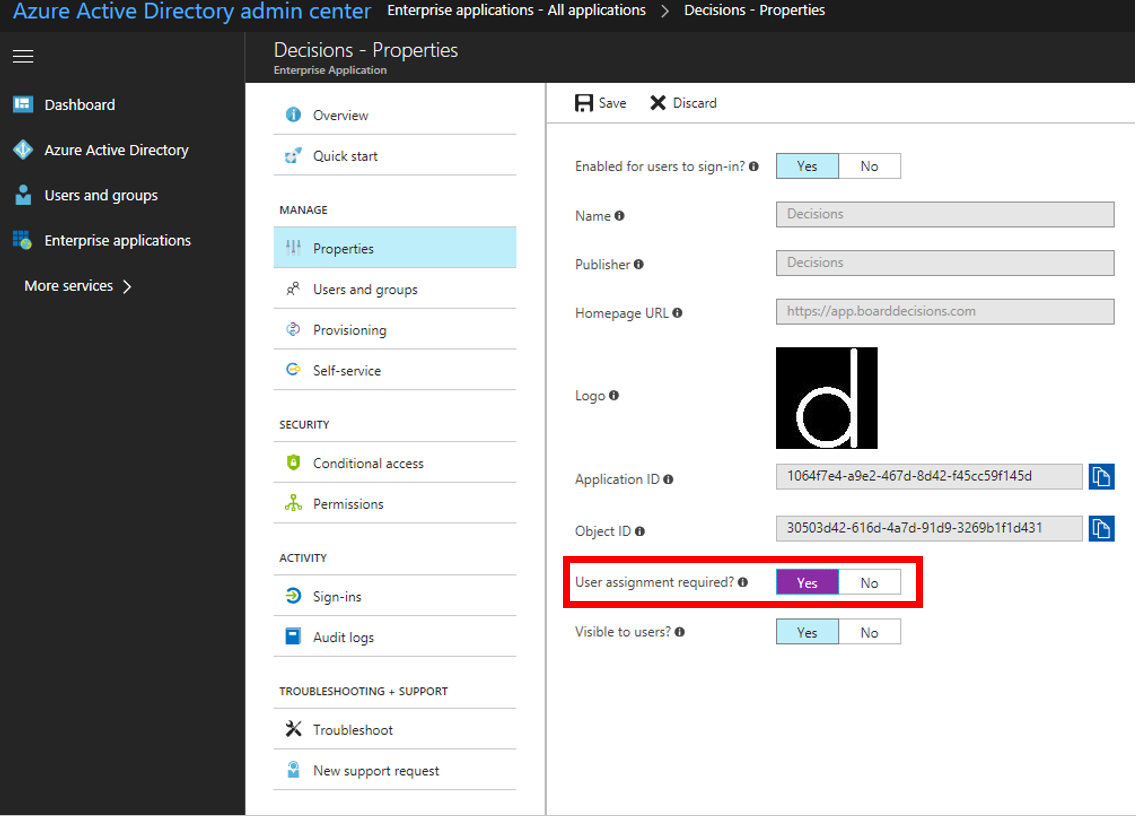
Limiting access to Decisions this way is only recommended when you have a limited set of people using Decisions. To manage access to Decisions using Azure AD you need to have the role of either global administrator or application owner. Step I: Go to the Azure Admin portal at https://portal.azure.com Step II: Select the "Azure AD" tab and then select the Decisions application under enterprise applications Step III: Go to properties and set the “User assignment required” to “Yes” and hit “Save”
Step IV: Select “Users and groups” Step V: Add the users and/or groups who should have access to the Decisions application
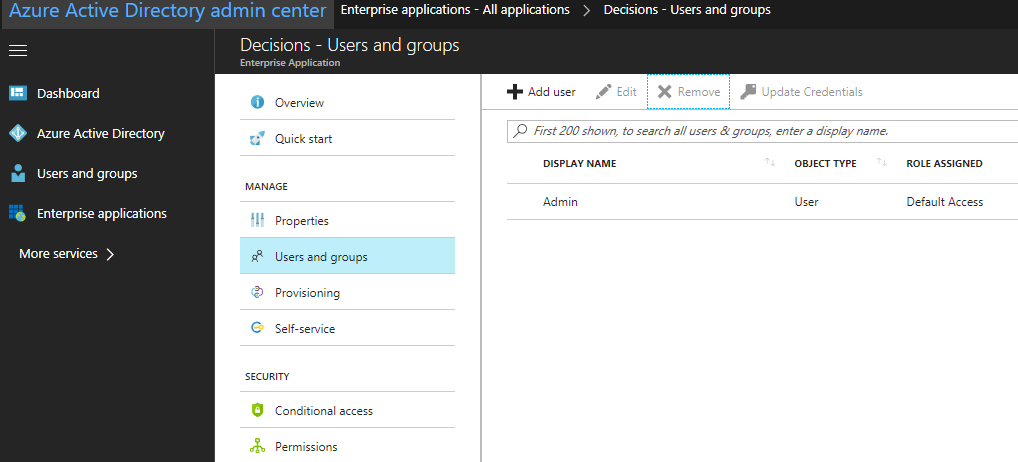
Note: Only users (or groups) listed here will have access to use Decisions. When someone not granted access to Decisions tries to use Decisions, it will present them with an authentication error and message informing them that the role assignment is missing. Learn more from Microsoft: Assign users and groups to an application in Azure Active Directory
Tip: To simplify user administration for Decisions, you can turn off User assignment required for the Decisions enterprise application in Azure AD, and instead use the Decisions License Admin. Read more

This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Managing user account provisioning for enterprise apps in the Microsoft Entra admin center
- 10 contributors
This article describes the general steps for managing automatic user account provisioning and deprovisioning for applications that support it. User account provisioning is the act of creating, updating, and/or disabling user account records in an application’s local user profile store. Most cloud and SaaS applications, as well many on-premises applications store the role and permissions in the application's own local user profile store. The presence of such a user record in the application's local store is required for single sign-on and access to work. To learn more about automatic user account provisioning, see Automate User Provisioning and Deprovisioning to SaaS Applications with Microsoft Entra ID .
Microsoft Entra ID has a gallery that contains thousands of pre-integrated applications that are enabled for automatic provisioning with Microsoft Entra ID. You should start by finding the provisioning setup tutorial specific to your application in the List of tutorials on how to integrate SaaS apps with Microsoft Entra ID . You'll likely find step-by-step guidance for configuring both the app and Microsoft Entra ID to create the provisioning connection.
Finding your apps in the portal
Steps in this article might vary slightly based on the portal you start from.
Use the Microsoft Entra admin center to view and manage all applications that are configured for single sign-on in a directory. Enterprise apps are apps that are deployed and used within your organization. Follow these steps to view and manage your enterprise applications:
Sign in to the Microsoft Entra admin center as at least a Application Administrator .
Browse to Identity > Applications > Enterprise applications .
A list of all configured apps is shown, including apps that were added from the gallery.
Select any app to load its resource pane, where you can view reports and manage app settings.
Select Provisioning to manage user account provisioning settings for the selected app.

Provisioning modes
The Provisioning pane begins with a Mode menu, which shows the provisioning modes supported for an enterprise application, and lets you configure them. The available options include:
Automatic - This option is shown if Microsoft Entra ID supports automatic API-based provisioning or deprovisioning of user accounts to this application. Select this mode to display an interface that helps administrators:
- Configure Microsoft Entra ID to connect to the application's user management API
- Create account mappings and workflows that define how user account data should flow between Microsoft Entra ID and the app
- Manage the Microsoft Entra provisioning service
Manual - This option is shown if Microsoft Entra ID doesn't support automatic provisioning of user accounts to this application. In this case, user account records stored in the application must be managed using an external process, based on the user management and provisioning capabilities provided by that application (which can include SAML Just-In-Time provisioning).
Configuring automatic user account provisioning
Select the Automatic option to specify settings for admin credentials, mappings, starting and stopping, and synchronization.
Admin Credentials
Expand Admin Credentials to enter the credentials required for Microsoft Entra ID to connect to the application's user management API. The input required varies depending on the application. To learn about the credential types and requirements for specific applications, see the configuration tutorial for that specific application .
Select Test Connection to test the credentials by having Microsoft Entra ID attempt to connect to the app's provisioning app using the supplied credentials.
Expand Mappings to view and edit the user attributes that flow between Microsoft Entra ID and the target application when user accounts are provisioned or updated.
There's a preconfigured set of mappings between Microsoft Entra user objects and each SaaS app’s user objects. Some apps also manage group objects. Select a mapping in the table to open the mapping editor, where you can view and customize them.
Supported customizations include:
Enabling and disabling mappings for specific objects, such as the Microsoft Entra user object to the SaaS app's user object.
Editing the attributes that flow from the Microsoft Entra user object to the app's user object. For more information on attribute mapping, see Understanding attribute mapping types .
Filtering the provisioning actions that Microsoft Entra ID runs on the targeted application. Instead of having Microsoft Entra ID fully synchronize objects, you can limit the actions run.
For example, only select Update and Microsoft Entra-only updates existing user accounts in an application but doesn't create new ones. Only select Create and Azure only creates new user accounts but doesn't update existing ones. This feature lets admins create different mappings for account creation and update workflows.
Adding a new attribute mapping. Select Add New Mapping at the bottom of the Attribute Mapping pane. Fill out the Edit Attribute form and select Ok to add the new mapping to the list.
Expand Settings to set an email address to receive notifications and whether to receive alerts on errors. Also select the scope of users to sync. Choose to sync all users and groups or only users that are assigned.
Provisioning Status
If provisioning is being enabled for the first time for an application, turn on the service by changing the Provisioning Status to On . This change causes the Microsoft Entra provisioning service to run an initial cycle. It reads the users assigned in the Users and groups section, queries the target application for them, and then runs the provisioning actions defined in the Microsoft Entra ID Mappings section. During this process, the provisioning service stores cached data about what user accounts it's managing. The service stores cached data so nonmanaged accounts inside the target applications that were never in scope for assignment aren't affected in deprovisioning operations. After the initial cycle, the provisioning service automatically synchronizes user and group objects on a forty-minute interval.
Change the Provisioning Status to Off to pause the provisioning service. In this state, Azure doesn't create, update, or remove any user or group objects in the app. Change the state back to On and the service picks up where it left off.
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources

IMAGES
VIDEO
COMMENTS
Regardless of whether assignment is required or not, only assigned users are able to see this application in the My Apps portal. If you want certain users to see the application in the My Apps portal, but everyone to be able to access it, assign the users in the Users and Groups tab, and set assignment required to No. Notes
Some of our applications contain data that should be available to Readify employees only, so we decided to make use of the "user assignment required" option. To access this option, in the Azure portal, go to "Azure Active Directory > Enterprise applications > your application > Properties" and the option will be displayed there.
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
So I go to the Enterprise Application settings of the Azure Function app, changed its properties to "User Assignment Required". Then under Users/Groups, I can add users/groups that are allowed to authenticate. Here I found out that I can only add regular AAD users. The managed identity service principals (i.e., the system assigned managed ...
What is the whole point of the "User Assignment Required" option in AAD Enterprise Applications' properties? Every app that I have configured to use SSO has required an account to be created in the actual application before a user can sign into it, so this just seems like an extra pointless step (I have been configuring as YES anyway, but I'm just now wondering why).
However, we recently added a new user from the Enterprise Applications section for that app, and he is not able to log in. He gets the 'Need admin approval' message. When we disable the 'User Assignment Required' option, it works fine for him as well. Please advise.
Set Assignment required to Yes. Databricks recommends this option, which syncs only users and groups assigned to the enterprise application. Go to Manage > Provisioning. To start synchronizing Microsoft Entra ID users and groups to Databricks, set the Provisioning Status toggle to On. Click Save. Go to Manage > Users and groups.
Step I: Go to the Azure Admin portal at https://portal.azure.com. Step II: Select the "Azure AD" tab and then select the Decisions application under enterprise applications. Step III: Go to properties and set the "User assignment required" to "Yes" and hit "Save". Step IV: Select "Users and groups". Step V: Add the users and/or ...
ANCOR ANCOR is committed to satisfying our customers needs to the utmost, ensuring prompt compliance with assignments, providing quality search and selection of the required personnel and adhering to the highest ethical standards.
Business/Operation. The owner of a taxicab, pedicab or carriage service must license the business and each vehicle. Vehicle inspections, insurance and fees are required. This annual application is renewal and the forms are listed on the right side of this page or may be picked up at the Moscow Police Department.
The "registered application" is just a notification to the AAD that this application uses AAD for authentication. Once your user logs in, you can check that the user belongs to a security group that is allowed permission to use the application. There may be a better way to do this, but I check in the application itself.
As an owner of an enterprise application in Microsoft Entra ID, a user can manage the organization-specific configuration of the application, such as single sign-on, provisioning, and user assignment. An owner can also add or remove other owners. Unlike Global Administrators, owners can manage only the enterprise applications they own.
Download forms and permit applications from the Streets and Engineering Divisions. Online Permit Portal; Engineering & Streets Permits; Contact Us. City of Moscow 206 E Third Street Moscow, ID 83843 Phone: 208-883-7000 Helpful Links. Intranet. Email. City Code. Utility Services /QuickLinks.aspx. Using This Site. Home.
1. To focus on humans and creating the conditions for a full-fledged, high-quality, and happy life for all categories of residents. Participation of residents. in city governance. 2. To develop conditions for active involvement of residents in social life and making decisions on citywide issues; open digital government. Artificial intelligence.
The presence of such a user record in the application's local store is required for single sign-on and access to work. ... Browse to Identity > Applications > Enterprise applications. ... The service stores cached data so nonmanaged accounts inside the target applications that were never in scope for assignment aren't affected in deprovisioning ...