Top 10 Network Security Thesis Topics
The term network security refers to securing the network from malicious attacks executed by the hackers to gain illegal access to the network, presume the password to exploit the sensitive packets by using the methods of spoofing, eavesdropping, etc.
“Network Security builds a soundproof wall against Eavesdropping.”
It prevents the network from hacker’s intention to harm the network, and securing the messages and message infrastructure that we are using is to share information or sensitive data. The network security tools intend to secure user privacy, network integration and authenticity, controlling access , etc.
“This article focuses on the generalized network attack categories and the role of network solutions to face the issues. It also provides an overview of the network security thesis topics and our approaches towards the effective thesis writing.”


GOALS OF NETWORK SECURITY
- Controlling access
- Reliability and Verification
- Securing the infrastructure of communication
Overall, cryptography and network security main objectives are based on the functions of preventing unauthorized use of the network, DoS attacks, Spoofing or Man-in-the-Middle attacks, Network Traffic Attacks, etc. We provide you with the overall functions of proper network security based on its primary action; the functions will differ.
Here is the overview of the security network as follows:
Overview of Network Security
- Solutions of Side Channel Attacks
- Solutions for Anti-Blocking
- Network Monitoring Mechanisms
- Energy supplied devices offloading
- Pre-computation methods
- Optimizations securing energy-aware
- Adaptations serving dynamic security
- Unauthenticated Relays
- External and internal attacks
- Side channel
- Spoofing / Eavesdropping
- Denial of Service
- Infection of malware
- Deadlock deauthentication
What are the Network Security Threats?
Risks in network security are very general and prevalent. Packet losses, network damage, reducing the confidence of the network packets are its main intentions. The rising level of the networks that are handling the network threats is accelerating. So the demand for the network security thesis topics deserves to be on the trend-setting level. As the generalization of threats in the network security , threats are also common. Let’s have a look at the types of Network Security Threats.
Types of Network Security Threats
- Attacks of Service Denial: It is a common and continual attack performed by an adversary to get access to the legal network. By this attack, Overloading unauthorized requests to crash the network normal functions.
- Phishing: Its intention is to take valuable information of user login or packets related information
- Attacks on Transport Security Layer / SSL: These attacks are the general form of threats, which makes the attackers the availability of sensitive data entry and to unencrypted information. This attack is accounted approximately 10% of every examined attack on networks.
- Spoofing Identity attack: In this attack, the regular host appears as the source, when the hackers made required changes to the packet headers. It is known as forging the IP address. The hackers use the intranet to create similar IP addresses of the user with the help of their specially designed program.
- Brute Force Attacks: In the hacker’s domain, this type of attack is a powerful one, where the hackers use the error and trial technique to attack the network security to presume the password of the system. This technique pays the hackers usual way in guessing the password.
The above security threats are the widespread patterns of adversaries. Network security risks and attacks can extremely influence a company’s economic sources, as discussed previously. Many reputed networks (SDN, 5G, and 6G networks) are struggling to secure their privacy over sensitive data. Having theoretical knowledge won’t help you to overcome such a crisis. Thus our developers suggest you some of the practical solutions for network security threats.
Solutions for Network Security Threats
- Proper network security update and maintenance
- Manage / monitor the networks security
- Designing security policies and rules
By that time, hackers are getting clever. Their malware implantation will dynamically change the source code of the threat, which delays the counteraction to respond to the attack without knowing the source code. A good network solution is needed to protect networks from different types of attacks to tackle this issue. How do you identify the ideal security solution? Here our research team has provided you some characteristic features of a good network solution.
What are the features of good network security model?
- Integration of different solutions : This provides you a strong protection from influential attacks and invasions on networks by integrating all your usage of network solutions and tools.
- Attacks Prevention : This type of network solution prevents the system against vigorous malware attacks and makes the attacker to find difficult to find the system’s source code.
- Continuous Observation and Response : This type of solution continuously monitors the user activity and alerts the user on the spot of its threat detection. This helps the user to prevent the system from attack.
- Detecting and Identifying threats: It helps to address the individual attack components by developing clear understanding of the threats entered into the network and helps in identifying and blocking them.
Though we categorized the various types of solutions, we suggest you that one solution to network security threat is not enough. You can get the different types of solutions from us with various features according to the network type and impact of the threat. But choosing a solution that integrally supports other security tools you bought from other vendors will be the best to implement information security thesis topics . When you are doing thesis in the relevant field, you can master in choosing and implanting the best to your device. Here we provide you some of the top Network Security Thesis Topics.
Network Security Thesis Topics
- Data Security and Privacy
- Protocols and Security Application functional assessments
- NLP for Protection and Ensure Security
- Security based on Artificial Intelligence and ML
- Managing and Recovering Key
- Securing Intellectual Property
- Integrity and Insider Threat Security
- Securing universal computing
- Watermarking and data hiding
- Confidential computing
- Solutions for security threats
- Protocols and Models of security
- Managing security and network
- Hiding of Data and security in Data Mining
Data Collection for Security Attacks Detection
Network security threats are patented to cause monetary loss. The data gathered in a network are used to identify the security threats like vulnerabilities and intrusions . Such data are called the data related to network security. Research Scholars can reach us in developing network security thesis topics based on data collection and detection. We were examining such data aids in identifying the security threats and is often useful in measuring the whole network’s security level. So, according to our technical team, gathering security-related data should be the primary step in detecting attacks . To gather such data in real-time detection, the following are the top datasets suggested by our research team.
Top 10 Datasets for Network Attacks Detection
- Aposemat IoT-23
- CTU-13 Dataset
- Network Data Set and Host Unification
- Datasets Detecting ADFA Intrusion
- Harmful URLs
- Malware Training Sets
Apart from the above-mentioned datasets, we have particularized a few data collecting tools and mechanisms for your reference in network security thesis topics . These are used to capture the network data in massive size with a wide range of collections.
- Online/offline Collecting tools
- Hardware/Software Collecting Tools
- Protocol Collecting Tools
- Collecting Direct/Indirect Tools
- Collecting Active/Passive Tools
- Flow/Packet focused Collection
- Inadequate/adequate collection
- Collection Of External/Internal Nodes
- Collection Of Integrated/Distributed Nodes

Which Method is Useful in Detection of an Attack?
Various Machine Learning algorithms like KNN and SVM are used as Intrusion Detection systems (IDS). The surface for the network attacks is on the rise as the network is multifaceted with successful technologies like cloud computing , IoT, etc. So, the need for predictive and reactive defense is increasing using different types of network simulator . The intrusion detection system is used as the base attack detecting mechanism in all research aspects to bond the gap . Below, we provide you the network security methodologies.
Network Security Methodologies
- Isolating Slices: Tostop misusing the packets and network vulnerabilities, the procedure of isolating the virtualization and mature cloud (Slices) are used.
- Managing Security: For the fast awareness on the network weak points, integrated management is used for network security
- Security Control: For automated counteraction on blocking threats, event attacks and fast recover assurance, it is important to organize the security strategies properly
- Analyzing Security: It is used to analyze the security on the basis of big data collection by circulating the several entities as MEC, Fog and RAN for detecting the DDoS attacks.
- Preventing data vulnerability: For securing privacy, network encryption and firewalls, this technology using the access of Network Slice-Specific Authentication and Authorization (NSSAA). In order to stop data abuse and key negotiation NSSAA have secondary verification to access the original network.
- Securing Slice Control: To assure the confidentiality and integrity, the slice management security functions on the basis of authorization technique and directional verification
Network security threats are targeted attacks to evade the defense mechanisms and the keys that are in place to avoid them. The two main types of network analysis are security and functional metrics . The objectives of each metrics vary according to its function and security as follows,
Network Simulation Performance Evaluation Tools
- Metrics of self- security and protecting privacy
- Metrics of Non-Denial and Verification
- Metrics of integrity and confidentiality
- Metrics of Cost and Non-Destructivity
- Metrics of Productivity and Generalization
- Metrics of flexibility and applicability
- Metrics of Adaptableness and Scalability
- Metrics of Constancy
The above-mentioned metrics have the basic functions to secure the models used in network security. Apart from the mentioned metrics, our teams of developers are experts in framing innovative metrics used to conduct an in-depth analysis of the time taken by the network security models and applications to identify and recover from the attacks performed. Let’s take a look at our objectives of thesis writing.
Our Objectives in thesis writing
- Contemplate Outlining and Structure
- Discovering initiating and maintaining writing approaches
- Concentrate on the writing method
- Constructing set of references to render final thesis
- Recognizing self-management methods to help progression
Along with the ideas that should be discuss inside the thesis chapters, a thesis generally have the power to decide your academic future and the effectiveness of every thesis is a debatable subject when you follow any profession related to your academic field. The practical explanation provided by our technical team will help you to understand the concept better to explain with others and it is notable that we provide you confidential service. Let’s have a look on the best network security thesis topics. For your convenience and clarification on our service, we also provide you the methodologies on how we structuring a dissertation.
WHAT ARE THE IMPORTANT SECTIONS IN THESIS WRITING?
- Abstract covers the significant descriptions about the research topic
- Introduction that describes the remaining chapters, literature review, terms definition, statement of the problem
- Techniques used includes the data structures, algorithms, requirements and specifications
- Chapters in the middle may vary on the chosen project (that discusses the major ideas of the proposed work)
- Conclusions stating the unsolved problems and obtained results by the proposed method
As earlier, we notify you to make use of this opportunity to work with our expert team, providing confidential service, customized research with benchmark references, and on-time service . We have 5000+ happy customers in the relevant research field. As a matter of fact, we provide you practical explanations over the simulators and testbeds used in network security thesis topics . We are glad to extend our support and guidance to introduce you to the various aspects of network security if you are interested.
Why Work With Us ?
Senior research member, research experience, journal member, book publisher, research ethics, business ethics, valid references, explanations, paper publication, 9 big reasons to select us.
Our Editor-in-Chief has Website Ownership who control and deliver all aspects of PhD Direction to scholars and students and also keep the look to fully manage all our clients.
Our world-class certified experts have 18+years of experience in Research & Development programs (Industrial Research) who absolutely immersed as many scholars as possible in developing strong PhD research projects.
We associated with 200+reputed SCI and SCOPUS indexed journals (SJR ranking) for getting research work to be published in standard journals (Your first-choice journal).
PhDdirection.com is world’s largest book publishing platform that predominantly work subject-wise categories for scholars/students to assist their books writing and takes out into the University Library.
Our researchers provide required research ethics such as Confidentiality & Privacy, Novelty (valuable research), Plagiarism-Free, and Timely Delivery. Our customers have freedom to examine their current specific research activities.
Our organization take into consideration of customer satisfaction, online, offline support and professional works deliver since these are the actual inspiring business factors.
Solid works delivering by young qualified global research team. "References" is the key to evaluating works easier because we carefully assess scholars findings.
Detailed Videos, Readme files, Screenshots are provided for all research projects. We provide Teamviewer support and other online channels for project explanation.
Worthy journal publication is our main thing like IEEE, ACM, Springer, IET, Elsevier, etc. We substantially reduces scholars burden in publication side. We carry scholars from initial submission to final acceptance.
Related Pages
Our benefits, throughout reference, confidential agreement, research no way resale, plagiarism-free, publication guarantee, customize support, fair revisions, business professionalism, domains & tools, we generally use, wireless communication (4g lte, and 5g), ad hoc networks (vanet, manet, etc.), wireless sensor networks, software defined networks, network security, internet of things (mqtt, coap), internet of vehicles, cloud computing, fog computing, edge computing, mobile computing, mobile cloud computing, ubiquitous computing, digital image processing, medical image processing, pattern analysis and machine intelligence, geoscience and remote sensing, big data analytics, data mining, power electronics, web of things, digital forensics, natural language processing, automation systems, artificial intelligence, mininet 2.1.0, matlab (r2018b/r2019a), matlab and simulink, apache hadoop, apache spark mlib, apache mahout, apache flink, apache storm, apache cassandra, pig and hive, rapid miner, support 24/7, call us @ any time, +91 9444829042, [email protected].
Questions ?
Click here to chat with us
Cybersecurity Guide
From scholar to expert: Cybersecurity PhD options
In this guide
- Industry demand
- 2024 rankings
- Preparation
- Considerations
- School listings
The cybersecurity landscape is not just growing—it’s evolving at a breakneck pace. And what better way to stay ahead of the curve than by pursuing a PhD in cybersecurity?
This advanced degree is no longer confined to the realm of computer science. Today, it branches into diverse fields like law, policy, management, and strategy, reflecting the multifaceted nature of modern cyber threats.
If you’re looking to become a thought leader in this dynamic industry, a PhD in cybersecurity offers an unparalleled opportunity to deepen your expertise and broaden your horizons.
This guide is designed to give prospective cybersecurity PhD students a general overview of available cybersecurity PhD programs. It will also outline some of the factors to consider when trying to find the right PhD program fit, such as course requirements and tuition costs.
Industry demand for PhDs in cybersecurity
Like other cutting-edge technology fields, until recently, cybersecurity PhD programs were often training grounds for niche positions and specialized research, often for government agencies (like the CIA, NSA, and FBI), or closely adjacent research organizations or institutions.
Today, however, as the cybersecurity field grows to become more pervasive and consumer-oriented, there are opportunities for cybersecurity PhDs to work at public-facing companies like startups and name-brand financial, software, infrastructure, and digital service firms.
One trend that is emerging in the cybersecurity field is that cybersecurity experts need to be well-versed in a variety of growing threats. If recent headlines about cybersecurity breaches are any indication, there are a number of new attack vectors and opportunities for cybercrime and related issues. Historically, committing cybercrime took resources and a level of sophistication that required specialized training or skill.
But now, because of the pervasiveness of the internet, committing cybercrime is becoming more commonplace. So training in a cybersecurity PhD program allows students to become an experts in one part of a growing and multi-layered field.
In fact, this trend of needing well-trained, but adaptable cybersecurity professionals is reflected by the move by cybersecurity graduate schools to offer specialized master’s degrees , and many companies and professional organizations offer certifications in cybersecurity that focus on particular issues related to cybersecurity technology, cybersecurity law , digital forensics , policy, or related topics.
That said, traditional research-oriented cybersecurity positions continue to be in demand in academia and elsewhere — a trend that will likely continue.
One interesting facet of the cybersecurity field is trying to predict what future cybersecurity threats might look like and then develop tools and systems to protect against those threats.
As new technologies and services are developed and as more of the global population begins using Internet services for everything from healthcare to banking — new ways of protecting those services will be required. Often, it’s up to academic researchers to think ahead and examine various threats and opportunities to insulate against those threats.
Another key trend coming out of academic circles is that cybersecurity students are becoming increasingly multidisciplinary.
As cybersecurity hacks impact more parts of people’s everyday lives, so too do the academic programs that are designed to prepare the next generation of cybersecurity professionals. This emerging trend creates an enormous amount of opportunity for students who have a variety of interests and who are looking to create a non-traditional career path.
The best cybersecurity PhD programs for 2024
Capella university, georgia institute of technology, northeastern university, marymount university, school of technology and innovation, nova southeastern university, college of computing & engineering, purdue university, stevens institute of technology, worcester polytechnic institute, university of illinois at urbana-champaign, mississippi state university, new york institute of technology.
These rankings were compiled from data accessed in November 2023 from the Integrated Post-Secondary Education Data System (IPEDS) and College Navigator (both services National Center for Education Statistics). Tuition data was pulled from individual university websites and is current as of November 2023.
What is required to get a PhD in cybersecurity?
Good news first: Obtaining a PhD in a field related to cybersecurity will likely create tremendous employment opportunities and lead to interesting and dynamic career options.
Bad news: Getting a PhD requires a lot of investment of time and energy, and comes with a big opportunity cost (meaning you have to invest four to five years, or longer, or pursue other opportunities to obtain a doctoral degree.
Here’s a quick breakdown of what is required to get a PhD in cybersecurity. Of course, specific degree requirements will vary by program. One growing trend in the field is that students can now obtain degrees in a variety of formats, including traditional on-campus programs, online degree programs , and hybrid graduate degree programs that combine both on-campus learning with online learning.
Related resources
- Online PhD in cybersecurity – A guide to finding the right program
- Cybersecurity degree programs
- Podcast episodes and expert interviews
Preparing for a cybersecurity doctorate program
Cybersecurity is a relatively new formalized technology field, nonetheless, there are several ways that students or prospective PhD candidates can get involved or explore the field before and during a graduate school program. A few examples of ways to start networking and finding opportunities include:
Join cybersecurity organizations with professional networks
Specialized professional organizations are a good place to find the latest in career advice and guidance. Often they publish newsletters or other kinds of information that provide insights into the emerging trends and issues facing cybersecurity professionals. A couple of examples include:
The Center for Internet Security (CIS) is a non-profit dedicated to training cybersecurity professionals and fostering a sense of collaboration. The organization also publishes information and analysis of the latest cybersecurity threats and issues facing the professional community.
The SANS Institute runs several different kinds of courses for students (including certification programs) as well as ongoing professional cybersecurity education and training for people working in the field. The organization has several options including webinars, online training, and live in-person seminars. Additionally, SANS also publishes newsletters and maintains forums for cybersecurity professionals to interact and share information.
Leverage your social network
Places like LinkedIn and Twitter are good places to start to find news and information about what is happening in the field, who the main leaders and influencers are, and what kinds of jobs and opportunities are available.
Starting a professional network early is also a great opportunity. Often professionals and members of the industry are willing to provide guidance and help to students who are genuinely interested in the field and looking for career opportunities.
Cybersecurity competitions
Cybersecurity competitions are a great way to get hands-on experience working on real cybersecurity problems and issues. As a PhD student or prospective student, cybersecurity competitions that are sponsored by industry groups are a great way to meet other cybersecurity professionals while getting working on projects that will help flesh out a resume or become talking points in later job interviews.
The US Cyber Challenge , for example, is a series of competitions and hackathon-style events hosted by the Department of Homeland Security Science and Technology Directorate and the Center for Internet Security to prepare the next generation of cybersecurity professionals.
Internships
Internships also continue to be a tried and true way to gain professional experience. Internships in technical fields like cybersecurity can also pay well. Like the industry itself, cybersecurity internships are available across a wide range of industries and can range from academic research-oriented to more corporate kinds of work.
Things to consider when choosing a cybersecurity PhD program
There are many considerations to evaluate when considering any kind of graduate degree, but proper planning is essential to be able to obtain a doctoral degree. It’s also important to note that these are just guidelines and that each graduate program will have specific requirements, so be sure to double-check.
What you will need before applying to a cybersecurity PhD program:
- All undergraduate and graduate transcripts
- A statement of intent, which is like a cover letter outlining interest
- Letters of reference
- Application fee
- Online application
- A resume or CV outlining professional and academic accomplishments
What does a cybersecurity PhD program cost?
Obtaining a PhD is a massive investment, both in terms of time and money. Cybersecurity PhD students are weighing the cost of becoming an expert in the field with the payoff of having interesting and potentially lucrative career opportunities on the other side.
Degree requirements are usually satisfied in 60-75 hours, so the cost of a doctoral degree can be well into the six-figure range. Here’s a more specific breakdown:
Tuition rates
The Cybersecurity Guide research team looked at 26 programs that offer a cybersecurity-related PhD degree. Here’s a breakdown of tuition rates (all figures are based on out-of-state tuition).
$17,580 is the most affordable PhD program option and it is available at the Georgia Institute of Technology.
$86,833 is the average cost of a cybersecurity PhD and is based on tuition rates from all 26 schools.
$197,820 is the most expensive cybersecurity PhD program and is available at Indiana University Bloomington.
The good news is that by the time students get to the PhD level there are a lot of funding options — including some graduate programs that are completely funded by the university or academic departments themselves.
Additionally, funding in the form of research grants and other kinds of scholarships is available for students interested in pursuing cybersecurity studies.
One example is the CyberCorps: Scholarships for Service program. Administered by the National Science Foundation, PhD students studying cybersecurity are eligible for a $34,000 a year scholarship, along with a professional stipend of $6,000 to attend conferences in exchange for agreeing to work for a government agency in the cybersecurity space after the PhD program.
Frequently asked questions about cybersecurity PhD programs
Most traditional and online cybersecurity graduate programs require a minimum number of credits that need to be completed to obtain a degree. On average, it takes 71 credits to graduate with a PhD in cybersecurity — far longer (almost double) than traditional master’s degree programs. In addition to coursework, most PhD students also have research and teaching responsibilities that can be simultaneously demanding and great career preparation.
At the core of a cybersecurity doctoral program is a data science doctoral program, you’ll be expected to learn many skills and also how to apply them across domains and disciplines. Core curriculums will vary from program to program, but almost all will have a core foundation of statistics.
All PhD candidates will have to take a series of exams that act as checkpoints during the lengthy PhD process. The actual exam process and timing can vary depending on the university and the program, but the basic idea is that cybersecurity PhD candidates generally have to sit for a qualifying exam, which comes earlier in the program (usually the winter or spring of the second year of study), a preliminary exam, which a candidate takes to show they are ready to start the dissertation or research portion of the PhD program, and a final exam where PhD students present and defend their research and complete their degree requirements.
A cybersecurity PhD dissertation is the capstone of a doctoral program. The dissertation is the name of a formal paper that presents the findings of original research that the PhD candidate conducted during the program under the guidance of faculty advisors. Some example cybersecurity research topics that could potentially be turned into dissertation ideas include: * Policies and best practices around passwords * Ways to defend against the rise of bots * Policies around encryption and privacy * Corporate responsibility for employee security * Internet advertising targeting and privacy * The new frontier of social engineering attacks * Operation security (OpSec) strategy and policy * Network infrastructure and defense * Cybersecurity law and policy * The vulnerabilities of biometrics * The role of ethical hacking * Cybersecurity forensics and enforcement
A complete listing of cybersecurity PhD programs
The following is a list of cybersecurity PhD programs. The listing is intended to work as a high-level index that provides enough basic information to make quick side-by-side comparisons easy.
You should find basic data about what each school requires (such as a GRE score or prior academic work) as well as the number of credits required, estimated costs, and a link to the program.
Arizona State University
- Aim: Equip students with in-depth expertise in cybersecurity.
- Study Modules: Delve into advanced computer science subjects and specific cybersecurity courses.
- Research Component: Students undertake groundbreaking research in the cybersecurity domain.
Carnegie Mellon University
- CNBC Collaboration: A joint effort between Carnegie Mellon and the University of Pittsburgh to train students in understanding the brain's role in cognition.
- Training Program: Students take four main neuroscience courses and participate in seminars and ethics training.
- Course Integration: Whether students have a B.S. or M.S. degree, they can combine the CNBC and ECE Ph.D. courses without extra workload.
Colorado School of Mines
- Research Focus: Cybersecurity: Studying online security and privacy.
- Cost and Financial Aid: Provides details on program costs and available financial support.
- Current Mines Community: Offers specific information for those already affiliated with Mines.
Indiana University Bloomington
- Focus Areas: Options include Animal Informatics, Bioinformatics, Computer Design, and more.
- Information Sessions: The university holds events to guide potential students about admissions and study options.
- Minor Requirement: All Ph.D. students must complete a minor, which can be from within the Luddy School of Informatics or from another approved school at IU Bloomington.
Iowa State University
- Details: The program is open to both domestic and international students.
- Time to Complete: Ph.D.: About 5.2 years
- Goals: Students should gain deep knowledge, follow ethics, share their findings, and do advanced research if they're writing a thesis.
- Learning Goals: Master core areas of Computer Science, achieve in-depth knowledge in a chosen subfield, obtain expertise to perform original research, and demonstrate the ability to communicate technical concepts and research results.
- Duration: Median time to earn the doctorate is 5.8 years.
- Application Information: The program is open to both domestic and international students.
- Program's Aim: The Ph.D. program is tailored to produce scholars proficient in leading research initiatives, undertaking rigorous industrial research, or imparting high-level computer science education.
- Entry Routes: The program welcomes both students holding a B.S. degree for direct admission and those with an M.S. degree.
- Dissertation's Role: It stands as the pivotal component of the Ph.D. journey. Collaboration between the student, their dissertation director, and the guiding committee is essential.
Naval Postgraduate School
- Program Essence: The Computer Science Ph.D. is a top-tier academic program in the U.S.
- Admission Criteria: Open to military officers from the U.S. and abroad, U.S. governmental employees, and staff of foreign governments.
- Curriculum: Designed to deepen knowledge in computing, with a focus on the needs of the U.S. Department of Defense.
- Emphasis on Research: The college showcases its strength in research through sections dedicated to Research Areas, affiliated Institutes & Centers, ongoing Research Projects, and specialized Labs & Groups.
- Holistic Student Growth: The college promotes a comprehensive student experience, spotlighting Clubs & Organizations, campus Facilities, and tech Systems.
- Guidance for Future Students: Provides tailored insights for students considering joining at various academic levels, from Undergraduate to PhD.
- Broad Learning: The program covers many areas, from software and policy to psychology and ethics, reflecting the wide scope of cybersecurity.
- Course Design: Students learn foundational security topics first and then dive into specialized areas, like cyber forensics.
- Successful Alumni: Past students now work in places like NASA, Amazon, and Google.
- Feature: Students can apply to up to three different campuses and/or majors using a single application and fee payment.
- Preparing for a Globalized World: Courses such as Global Supply Chain Management equip students for international careers.
- Tech-Forward Curriculum: Purdue's commitment to advanced technology is evident.
Rochester Institute of Technology
- Cyberinfrastructure Focus: The program dives deep into how hardware, data, and networks work together to create secure and efficient digital tools.
- Broad Applications: The program uses computing to solve problems in fields like science, arts, and business.
- Success Rate: All RIT graduates from this program have found relevant roles, especially in the Internet and Software sectors.
Sam Houston State University
- Program's Objective: The course aims to nurture students to be technically adept and also to take on leadership roles in the digital and cyber forensic domain across various industries.
- Assessments: Students undergo comprehensive tests to evaluate their understanding.
- Research Paper (Dissertation): Once students reach the doctoral candidacy phase, they must produce and defend a significant research paper or dissertation.
- Funding: All Ph.D. students get financial help, so they can start their research right away.
- Teachers: The program has top experts, including those who've made big discoveries in computer science.
- Research Areas: Students can study the latest topics like AI, computer vision, and online security.
The University of Tennessee
- Study Areas: Options include Cybersecurity, Data Analytics, Computer Vision, and more.
- Tests: You'll have to pass a few exams, including one when you start, one before your final project, and then present your final project.
- Courses: Some specific courses are needed, and your main professor will help decide which ones.
- Big Exam: Before moving forward, you'll take a detailed exam about your research topic.
- Final Step: You'll present and defend your research project to experts.
- Overview: This program is for those with a degree in Computer Science or similar fields. It has special focus areas like Cybersecurity and Machine Learning.
University of Arizona
- Study Plan: Students start with learning research basics and then dive into modern tech topics.
- Support for Students: All PhD students get funding that covers their studies, a stipend, and health insurance. Money for travel to conferences is also available.
- After Graduation: Alumni work at top universities and big companies like Google and Microsoft.
University of California-Davis
- About the Program: Students engage in deep research, ending with a dissertation.
- Jobs After Graduation: Roles in companies or academic positions.
- Vibrant Community: Beyond academics, students join a supportive community, enriching their Ph.D. experience.
University of Colorado - Colorado Springs
- Recognition: UCCS is recognized by the National Security Agency (NSA) and the Department of Homeland Security for excellence in Information Assurance Education.
- Course Approval: The NSA has approved UCCS's courses as meeting national security training standards.
- Overview: This program focuses on vital areas like cyber security, physical security, and homeland security.
University of Idaho
- Partnership with NSA and DHS: The university is part of a program to boost cyber defense education.
- Recognition: The University of Idaho is among the institutions recognized as Centers of Academic Excellence in Cyber Defense.
- Objective: To minimize vulnerabilities in the national information infrastructure.
- Overview: This program is meticulously crafted to deliver premier legal education to its students.
- Courses: Encompasses a balanced mix of traditional legal doctrines, theoretical viewpoints, and hands-on practical experiences.
- Aim: The primary objective is to equip students with top-notch legal education.
University of Missouri-Columbia
- Seminars: PhD students should attend 20 seminars. If they were previously Master's students, their past attendance counts.
- Timeline Requirements: Comprehensive Exam must be completed within five years of starting the program.
- Dissertation and Publication: At least one journal paper must be submitted, accepted, or published.
University of North Carolina at Charlotte
- Faculty: The faculty members are renowned for their impactful research contributions on a global scale.
- Curriculum: The curriculum is versatile, catering to individuals aiming for academia as well as those targeting roles in the corporate, commerce, or public sectors.
- Program: A blend of theoretical and hands-on research is emphasized, offering a well-rounded educational experience.
Virginia Tech
- Seminars and Ethics: Students attend special seminars and complete training on scholarly ethics and diversity.
- Guidance: Each student gets a faculty advisor. A group of faculty members, called a committee, also guides them.
- Major Exams: Students go through four main stages: a qualifying process, a preliminary proposal, a research presentation, and a final defense.
- Strong Research: WPI's PhD program is recognized for its excellent research contributions.
- Practical Focus: The program teaches students to tackle real tech challenges.
- Modern Labs: Students use the latest labs like the Human-Robot Interaction Lab.
Dakota State University
- Program Goal: Train students to handle and prevent cyber threats.
- Awards: The university has received top cybersecurity awards.
- What You'll Learn: Research skills, cyber defense techniques, and ethical decision-making.
New Jersey City University, College of Professional Studies
- About: Focuses on best practices in areas like national security, cyber defense, and crisis communication.
- Recognitions: The program has been honored by the National Security Agency since 2009 and was recognized for excellence in intelligence studies.
- Jobs: Graduates are prepared for top roles in sectors like government and education.
- Program Content: The course dives deep into modern cybersecurity topics, from new tech and artificial intelligence to specialized research areas.
- Location Benefits: The university is near many cybersecurity companies and government agencies, giving students unique opportunities.
- For Working People: It's crafted for professionals, allowing them to experience various cybersecurity roles, from tech firms to government.
- Completion Time: Students have up to ten years from starting to finish their dissertation.
- Program: Trains students for roles in academia, government, and business.
- Multidisciplinary Approach: The program combines both technical and managerial aspects of cybersecurity, offering a comprehensive understanding of the field.
The University of Rhode Island
- Research Focus: The Ph.D. program is centered around a big research project in Computer Science.
- Qualifying Exams: Students take exams on core topics, but some might get exemptions if they're already skilled in certain areas.
- Equal Opportunity: The University of Rhode Island is committed to the principles of affirmative action and is an equal opportunity employer.
University of North Texas
- Team Effort: The program is a collaboration between various UNT departments for a well-rounded view of cybersecurity.
- Goals: The course aims to develop critical thinkers who are passionate about the role of information in our lives and can work across different fields.
- Skills Gained: Students will learn about research, teaching methods, decision-making, leadership, and analyzing data.
New York University Tandon School of Engineering
- Scholarships: Many students get scholarships that pay for tuition and give a monthly allowance.
- Research Interest: Research areas include cybersecurity, computer games, web search, graphics, and more.
- Experience: Students can also research in NYU's campuses in Shanghai or Abu Dhabi.
- One Degree for All: Every student gets the same Ph.D., regardless of their specific area of study.
- Research Focus: The program emphasizes deep research and prepares students for advanced roles.
- Major Project: Students work on a big research project, adding new knowledge to the computing world.
- Program: Prepares students for leadership roles in different sectors.
- Opportunities: Qualified students might get opportunities as Research or Teaching Assistants.
- Overview: Focuses on advanced research and modern technologies.
Augusta University
- Goal: The program prepares students for research roles and to make new discoveries in tech.
- Benefits: A Ph.D. opens up leadership opportunities in tech sectors.
- Overview: It focuses on new discoveries in areas like security, artificial intelligence, and virtual reality.
University of Texas at San Antonio
- Financial Support: Full-time students can get funding, which covers tuition and offers roles like teaching assistants.
- Job Prospects: UTSA trains students for jobs that are in high demand, using data from official sources.
- Overview: The program focuses on in-depth research and teaching.
University of Central Florida
- Mix of Subjects: Students can take courses from different areas, giving them a broad view of security topics.
- Many Job Options: Graduates can work in government, big companies, or teach in universities.
- Hands-on Learning: The program offers research, study projects, and internships for real-world experience.
Research Topics & Ideas: Cybersecurity
50 Topic Ideas To Kickstart Your Research

If you’re just starting out exploring cybersecurity-related topics for your dissertation, thesis or research project, you’ve come to the right place. In this post, we’ll help kickstart your research by providing a hearty list of cybersecurity-related research topics and ideas , including examples from recent studies.
PS – This is just the start…
We know it’s exciting to run through a list of research topics, but please keep in mind that this list is just a starting point . These topic ideas provided here are intentionally broad and generic , so keep in mind that you will need to develop them further. Nevertheless, they should inspire some ideas for your project.
To develop a suitable research topic, you’ll need to identify a clear and convincing research gap , and a viable plan to fill that gap. If this sounds foreign to you, check out our free research topic webinar that explores how to find and refine a high-quality research topic, from scratch. Alternatively, consider our 1-on-1 coaching service .

Cybersecurity-Related Research Topics
- Developing machine learning algorithms for early detection of cybersecurity threats.
- The use of artificial intelligence in optimizing network traffic for telecommunication companies.
- Investigating the impact of quantum computing on existing encryption methods.
- The application of blockchain technology in securing Internet of Things (IoT) devices.
- Developing efficient data mining techniques for large-scale social media analytics.
- The role of virtual reality in enhancing online education platforms.
- Investigating the effectiveness of various algorithms in reducing energy consumption in data centers.
- The impact of edge computing on the performance of mobile applications in remote areas.
- The application of computer vision techniques in automated medical diagnostics.
- Developing natural language processing tools for sentiment analysis in customer service.
- The use of augmented reality for training in high-risk industries like oil and gas.
- Investigating the challenges of integrating AI into legacy enterprise systems.
- The role of IT in managing supply chain disruptions during global crises.
- Developing adaptive cybersecurity strategies for small and medium-sized enterprises.
- The impact of 5G technology on the development of smart city solutions.
- The application of machine learning in personalized e-commerce recommendations.
- Investigating the use of cloud computing in improving government service delivery.
- The role of IT in enhancing sustainability in the manufacturing sector.
- Developing advanced algorithms for autonomous vehicle navigation.
- The application of biometrics in enhancing banking security systems.
- Investigating the ethical implications of facial recognition technology.
- The role of data analytics in optimizing healthcare delivery systems.
- Developing IoT solutions for efficient energy management in smart homes.
- The impact of mobile computing on the evolution of e-health services.
- The application of IT in disaster response and management.
Cybersecurity Research Ideas (Continued)
- Assessing the security implications of quantum computing on modern encryption methods.
- The role of artificial intelligence in detecting and preventing phishing attacks.
- Blockchain technology in secure voting systems: opportunities and challenges.
- Cybersecurity strategies for protecting smart grids from targeted attacks.
- Developing a cyber incident response framework for small to medium-sized enterprises.
- The effectiveness of behavioural biometrics in preventing identity theft.
- Securing Internet of Things (IoT) devices in healthcare: risks and solutions.
- Analysis of cyber warfare tactics and their implications on national security.
- Exploring the ethical boundaries of offensive cybersecurity measures.
- Machine learning algorithms for predicting and mitigating DDoS attacks.
- Study of cryptocurrency-related cybercrimes: patterns and prevention strategies.
- Evaluating the impact of GDPR on data breach response strategies in the EU.
- Developing enhanced security protocols for mobile banking applications.
- An examination of cyber espionage tactics and countermeasures.
- The role of human error in cybersecurity breaches: a behavioural analysis.
- Investigating the use of deep fakes in cyber fraud: detection and prevention.
- Cloud computing security: managing risks in multi-tenant environments.
- Next-generation firewalls: evaluating performance and security features.
- The impact of 5G technology on cybersecurity strategies and policies.
- Secure coding practices: reducing vulnerabilities in software development.
- Assessing the role of cyber insurance in mitigating financial losses from cyber attacks.
- Implementing zero trust architecture in corporate networks: challenges and benefits.
- Ransomware attacks on critical infrastructure: case studies and defence strategies.
- Using big data analytics for proactive cyber threat intelligence.
- Evaluating the effectiveness of cybersecurity awareness training in organisations.
Recent Cybersecurity-Related Studies
While the ideas we’ve presented above are a decent starting point for finding a research topic, they are fairly generic and non-specific. So, it helps to look at actual studies in the cybersecurity space to see how this all comes together in practice.
Below, we’ve included a selection of recent studies to help refine your thinking. These are actual studies, so they can provide some useful insight as to what a research topic looks like in practice.
- Cyber Security Vulnerability Detection Using Natural Language Processing (Singh et al., 2022)
- Security for Cloud-Native Systems with an AI-Ops Engine (Ck et al., 2022)
- Overview of Cyber Security (Yadav, 2022)
- Exploring the Top Five Evolving Threats in Cybersecurity: An In-Depth Overview (Mijwil et al., 2023)
- Cyber Security: Strategy to Security Challenges A Review (Nistane & Sharma, 2022)
- A Review Paper on Cyber Security (K & Venkatesh, 2022)
- The Significance of Machine Learning and Deep Learning Techniques in Cybersecurity: A Comprehensive Review (Mijwil, 2023)
- Towards Artificial Intelligence-Based Cybersecurity: The Practices and ChatGPT Generated Ways to Combat Cybercrime (Mijwil et al., 2023)
- ESTABLISHING CYBERSECURITY AWARENESS OF TECHNICAL SECURITY MEASURES THROUGH A SERIOUS GAME (Harding et al., 2022)
- Efficiency Evaluation of Cyber Security Based on EBM-DEA Model (Nguyen et al., 2022)
- An Overview of the Present and Future of User Authentication (Al Kabir & Elmedany, 2022)
- Cybersecurity Enterprises Policies: A Comparative Study (Mishra et al., 2022)
- The Rise of Ransomware: A Review of Attacks, Detection Techniques, and Future Challenges (Kamil et al., 2022)
- On the scale of Cyberspace and Cybersecurity (Pathan, 2022)
- Analysis of techniques and attacking pattern in cyber security approach (Sharma et al., 2022)
- Impact of Artificial Intelligence on Information Security in Business (Alawadhi et al., 2022)
- Deployment of Artificial Intelligence with Bootstrapped Meta-Learning in Cyber Security (Sasikala & Sharma, 2022)
- Optimization of Secure Coding Practices in SDLC as Part of Cybersecurity Framework (Jakimoski et al., 2022)
- CySSS ’22: 1st International Workshop on Cybersecurity and Social Sciences (Chan-Tin & Kennison, 2022)
As you can see, these research topics are a lot more focused than the generic topic ideas we presented earlier. So, for you to develop a high-quality research topic, you’ll need to get specific and laser-focused on a specific context with specific variables of interest. In the video below, we explore some other important things you’ll need to consider when crafting your research topic.
Get 1-On-1 Help
If you’re still unsure about how to find a quality research topic, check out our Research Topic Kickstarter service, which is the perfect starting point for developing a unique, well-justified research topic.

You Might Also Like:

Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Print Friendly
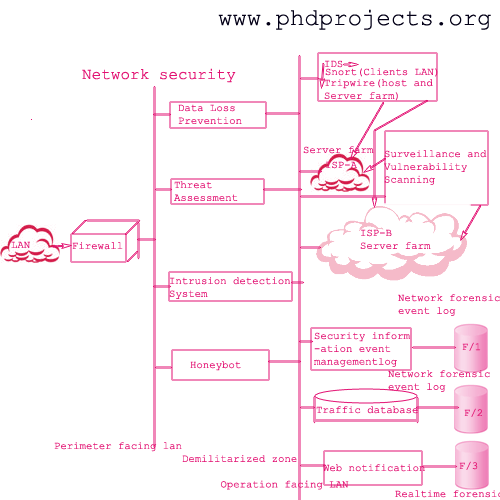
NETWORK SECURITY RESEARCH TOPICS
Network security research topics is also one of most accepted area for Research dealing with many protocols. Importance and necessitate of network security makes it admirable area for research. Why is Network Security so important, this question revolve around every one of us. It has also a simple answer which lies in its name i.e. SECURITY. Due to its interdisciplinary nature, we can also develop many security protocols to avoid the current network security violation. To perform an outstanding research, we also need to review recent security violations and also explore related methods and also techniques for it.
We can also work on network forensic and analyze best technique and algorithm for it.
Internet, the word which changed the world depends on Network-security as it is prone to many security attacks, malicious activities, also misleading information and unintelligible communication. Hence, there is also a need for effective security solution which can also be taken as a challenge by young scholars and work on it. Network security research topics which are currently undergoing are cyber-insurance, cumulative Metric for an information network etc. Most commonly also used security mechanisms are Encipherment, Digital signature, also coding-decoding etc. But these are also fundamentals of Network security. It is also fast growing field which needs current update and latest algorithm also for enhance the research. For this, we have a wide collection of Network security research topics with its tool
RESEARCH ISSUES IN NETWORK-SECURITY:
RFID technologies Security in Ad hoc network Security also in telecommunication network Wireless security Collaborative network security Defining network security protocols Network security also in protection measures Network forensics Embedded also in network security IPV6 network security Malware detection etc.
SOFTWARE AND TOOL DETAILS ========================== 1)NeSSi(JAVA) 2)NST(C) 3)JAVASNOOP(JAVA) 4)EXata (C++) 5)NETwork Attacks (also in NETA-omnet++)
Purpose of the every software and tool =======================================.
NeSSi–> novel network simulation tool also used for security research and evaluation purposes due to its varied capability.
NST–> performs routine security, networking diagnostic and also monitoring tasks.
JAVASNOOP–> Security tool also used to test the security of Java applications.
EXata–> network emulator which also provides network security and cyber warfare features
ETwork Attacks (NETA)–>Framework also to simulate attack behaviors in heterogeneous networks using OMNeT++.
Related Search Terms
network security research issues, network security research topics, phd projects in network security, Research issues in network security
Funding support: Army Research Office (ARO), and the Army Educational Outreach Program (AEOP) .
3. Security and Privacy in Dynamic Spectrum Sharing
4. Security and Privacy Protection of Data Collection and Analysis
On the other hand, in recent years large companies are already collecting many users' data for analytics/advertisement purposes and providing better services. To protect users' privacy, encryption may not be the best solution in this scenario since the service provider must be able to query statistical information from the data. Data obfuscation/perturbation techniques have became promising as they aim at hiding the secrets of individual users while still allowing statistical analysis. Differential privacy is a formal notion to quantify the privacy level of users in this setting. However, how to achieve a good balance between privacy and data utility is always a challenge, especially in the local setting where the service provider is untrusted. Our recent research focus on developing context-aware privacy notions and mechanisms to enhance the utility-privacy tradeoff, by leveraging statistical and information-theoretic approaches.
Funding support: National Science Foundation (NSF) and Amazon Web Services. Project Websites: Secure data service outsourcing (completed)
5. Cyber-Physical System Security: Autonomous and Connected Vehicles & Unmanned Aerial Systems.
Vehicular automation is now appearing that promises a new era of transportation technology. Although automation introduces opportunities to optimize the efficiency and safety of transportation systems, it also exposes users to new security risks due to increased reliance on computers, sensors and networked communication. The goal of this research is to provide a secure foundation for a transportation system that increasingly relies on cooperative automation strategies and vehicle connectedness to achieve increases in safety, efficiency, and capacity. We anticipate a three phase deployment of automation technologies: (1) autonomous vehicles without connectivity will use local sensing to form and maintain platoons, (2) vehicles will begin to incorporate traffic-related information shared via vehicle-to-vehicle communication into their decision making processes, and (3) a trusted infrastructure will emerge that supplies guidance to vehicles via vehicle-to-infrastructure communication to achieve safe, optimal, and adaptive system-wide traffic flows. Our work examine the vulnerabilities of inter-vehicular and intra-vehicular systems from both communication and controls perspectives, then propose defense mechanisms that are practical and low-overhead, for example, by deriving security and trust from the physical layer. Unmanned Aircraft Systems (UAS) have received significant attention in the past decade due to their utility in intelligence, reconnaissance, and recreational applications at a fraction of the cost of employing manned aircraft. UAS systems are an advancing technology with tremendous potential, but which also raise serious concerns with regard to safety, security, and privacy. As UASs continue to proliferate, aviation regulatory agencies around the world are facing a challenging dilemma in terms of safely integrating UAS operations into their respective national airspace systems and enforcing their compliance to relevant regulations. The significance of the dilemma is exacerbated by the lack of technical approaches for effectively countering the threats posed by nefarious or unintentionally noncompliant UAS operations and enforcing the relevant regulations to safeguard controlled/restricted airspace. This project aims to address this critical need by developing offensive and defensive measures for detecting and bringing down UASs that violate controlled/restricted airspace in an automated, controlled, and reliable manner. Our project team proposes to develop a set of systematic approaches for countering the threat posed by nefarious or noncompliant UASs. The multi-disciplinary team consists of exertise that include UAS flight control systems, CPS security, wireless communications and networking, and reinforcement learning and intelligent control. Funding support: National Science Foundation (NSF). Project Websites: Security in autonomous vehicular transportation News coverage: The Epoch Times, Driverless transportation , The Atlantic , 163 Tech News (网易科技新闻) , 爬车网
Funded Research Projects
- DURIP: A Millimeter-Wave Communication System for Wireless Security and Networking Research and Education, $249,934, Army Research Office, 04/21/2021 - 04/20/2022, PI (Co-PI: Loukas Lazos).
- Undergraduate Research Apprentice Program (URAP)/High School Apprentice Program (HSAP) Supplement, $15,000, Army Research Office, 05/15/2021 - 08/15/2021, PI (Co-PI: Loukas Lazos).
- In-band Wireless Trust Establishment Resistant to Advanced Signal Manipulations, Army Research Office, 01/01/2019 - 12/31/2021, PI (Co-PI: Loukas Lazos).
- SaTC: CORE: Medium: Collaborative: Enforcement of Geofencing Policies for Commercial Unmanned Aircraft Systems, National Science Foundation, 09/01/2018 - 08/31/2021, PI.
- SpecEES: Secure and Fair Spectrum Sharing for Heterogeneous Coexistent Systems , National Science Foundation, 10/1/2017-9/30/2020, Co-PI (with PI Loukas Lazos and Co-PI Marwan Krunz) (Project website)
- Toward High Performance Tactical Multi Hop Wireless Networks via Exploiting Antenna Reconfigurability, Office of Naval Research, 6/1/2016-5/31/2019.
- EARS: Collaborative Research: Crowdsourcing-Based Spectrum Etiquette Enforcement in Dynamic Spectrum Access , National Science Foundation, $360,000, 1/1/2015-12/31/2018, PI (Co-PIs: Ryan Gerdes and Bedri Cetiner). (Project website)
- TWC: Medium: Secure and Resilient Vehicular Platooning , National Science Foundation , 8/1/2014-7/31/2019, $1,229,923, Co-PI (PI: Ryan Gerdes) (Project website)
- CAREER: Toward Cooperative Interference Mitigation for Heterogeneous Multi-hop MIMO Wireless Networks , $489,999, National Science Foundation, 7/1/2014-6/31/2019, PI (Project website) .
- CSR: Small: Collaborative Research: Towards User Privacy in Outsourced Cloud Data Services , $175,000, National Science Foundation, 10/1/2012-9/31/2015, PI.
- Proving the Possession of Multi-Owner Data in the Cloud, $2,500, Amazon AWS Research Grant, 2014-2016
We thank the generous support of:

- [email protected]
- +91-97 91 62 64 69
Network Security Project Topics
Network security is the method towards ensuring safety and protection to shield the fundamental system administration from getting affected by unapproved access, data alterations, physical damage, obliteration, and many other potential attacks. Network security project ideas are gaining importance due to the causes arising out of large-scale network usage . Reach our expert panel team for interesting novel network security project topics . Because issues in network security can lead to many problems which include the following
- Loss of data
- Disruptions in the system functioning due to virus and hacking
- Breach in security leading to malfunctioning
Think about a virtual private network. It is one of the important mechanisms that establish a safe connection to secure the data sent and got. Let us first start by understanding the constraints in network security.

WHAT ARE THE LIMITATIONS OF NETWORK SECURITY?
There are a few limitations existing in present-day network security systems which demand in-depth research and analysis to be carried out to get them solved. The following is a detailed description of certain important network security constraints.
- A large number of methods used for the authentication of users are not entirely reasonable for safe system operations.
- The absence of multifaceted validation plans lead to a less protected CPS framework
- As a result, unapproved claims can access the network
- The firewall arrangements are not truly pertinent and appropriate in many work areas of cyber-physical systems
- Dynamic firewall solutions like next-generation application-oriented firewalls can be the best replacement option
- Only the methods that are proposed recently can be explicitly embraced to ensure security frameworks like CPS
- Notwithstanding the recent methods, honeypot approaches in industry 4.0 needed much advancement.
- Assets and latency in overhead is introduced
- Due to the asymmetric nature of cryptography, the constant working of the CPS is in the client to organize some overhead issues and latency in the network because of the encryption and decoding deferral
- The different types of intrusion detection systems based on behavior, signature, and anomaly are available in network security systems
- Even though these systems are present they are not by and large applied inside the internet of things based areas and or not explicitly intended for securing the CPS framework
From the research works that happened recently in network security, our technical team enriched themselves with the possible solutions suggested overcoming the above limitations . It can be quoted here that such efforts of our technical team are retaining us still in the mainstay of cyber security research guidance. Now let us see about the various factors that are prominent in detecting cyber-attacks.
This article will give you a complete picture of network security concepts and implementations that are successful among researchers in different parts of the world.
WHAT ARE THE FACTORS IMPORTANT IN THREAT DETECTION?
Detection of threat is the major part of any network security system to be declared more efficient by network users . The following five factors are common to all threats which should be identified efficiently by any attack detection mechanisms
- Accidental threats are those dangers that were cost and intentionally through some real network organization segments
- Adversarial threats present vindictive expectations of the people, associations, a state, or a nation
- The environmental dangers incorporate the following.
- Events of calamities like floods and seismic tremors
- Destructions caused by humans like blasts and flames
- Failures due to supporting frameworks like the malfunctioning of broadcast communication and power loss
- The objective of the attackers is the motive to any network security threats
- Criminal and terrorist actions
- Political intentions
- Components of the networks
- Network applications
- Interception, intrusion, alteration, and fabrication are the different mechanisms based on which any network security attack rely
- Network integrity
- Confidentiality of information
- Availability and accessibility
So creating the best framework for protecting a network from malicious attacks involves many different types of measures and strategies . Look into the following threats and proper strategies used to overcome such issues in network layer security.
- Hijacking the session
- Collection of data by unauthorized users
- Classifying the security zones
- Maintaining remote security
- Detecting invasions
- Isolation of firewall
It is as a result of our professional online research guidance on network security project topics that many PhD candidates around the world reported higher accuracy and performance of their model . We are always happy to extend you the necessary support for your research work. Get in touch with us to avail one of the top reliable research guidance in the world. Now let us have a detailed outline of network security systems.
OUTLINE OF NETWORK SECURITY
As you might know, there are various technologies involved in cyber security systems . It becomes now important for us to understand such technologies and the various elements involved in ensuring network security along with their benefits.
- Internet of things
- Big data analytics
- Machine learning protocols
- Augmented reality
- Cloud computing applications
- Artificial intelligence
- Theft of intellectual property
- Physical damages in cyber networks
- Production loss
- Spear phishing
- Ransomware attacks
- Threats by malware
- Reliability loss
- Threats to safety and health of the network
- Issues related to the integrity of network and data
- Other common cyber attacks
- Security in application
- Securing the data
- Planning the continuation of business
- Security in operations
- End-user about cyber security mechanisms
- Network security protocols
With these elements, researchers include many new technologies into network security projects for enhancing the system as a whole. Why should one do research in cyber security? The answer to this question lies in its benefits. Let us see the merits of network security systems below.
- Improving the confidence of an organization
- Protecting the end-users from potential attacks on networks
- Enhancing the time of recovery after meeting with a security breach
- Protecting the network and information
- Cyber security mechanism to prevent malware attacks, phishing threats, and ransomware
The advantages of cyber security systems extend well beyond this list and researchers must take the responsibility of exploring and expanding the scope of network security systems existing these days. For this purpose, you need to have access to a high level of research data with multidimensional objectives.
You can reach out to our technical team at any time and get the necessary literature need to carry out your research. We will also provide you with all essential information in formulating network security project topics. Now let us look into the vulnerabilities existing in a network that has to be rectified by network security researchers.
VULNERABILITIES OF NETWORKS
Here we categorize the network vulnerabilities into different heads as listed below.
- Vulnerabilities of devices and networks
- Susceptibility due to flaws in the system security
- Man in the middle attacks
- Threats in manipulating packets
- Network layer
- Application layer
- DoS and DDoS attacks
- Back door attacks
- Eavesdropping
The wired and wireless communications security features are compromised due to cyber security flaws.
- Configuration
- Absence of guidelines due to security
- Procedure lack
- Deficiency of policies of security
Having looked into the above aspects of vulnerabilities present in any network, you should now understand the practical and real-time faults that can become potentially vulnerable zones.
VULNERABILITIES IN REAL-TIME NETWORK APPLICATIONS
The cyber-physical systems and their vulnerabilities are listed below. Have a look into the following aspects of vulnerabilities in which we gained the enormous potential to solve them.
- Protocols for open communication
- Attacks based on web
- Wired and wireless communications
- Insecure protocols
- Interconnected devices (exposed)
- RTOS and OS insecurity
- Insecurity in secondary access points
- Physical sabotage of different network equipment
- Software vulnerabilities
- DoS attacks (software)
- Invasion of privacy of the patients
- Noise issues
- Injection attacks
- Replay issues
- Communication protocols
- Field devices that are interconnected
- Smart meters that are insecure
- Physical sabotage of the equipment
- Insecure algorithms
- Intrusion into privacy
- Tracing GPS
- CAN bus insecurity
- Flaws in communication software
- Components that are not protected (physically)
- Exploitations of the media player
- Flaw due to authentication of Bluetooth
The vulnerabilities are the checkpoints that act as the mode of entry for an attacker to have access to network data. So your network security project topics should be modeled in such a way as to act as a barrier for major attacks. Now let us talk about different kinds of attacks on network security
WHAT ARE NETWORK SECURITY ATTACKS?
A network security attack is nothing but an attempt to compromise the defense system deployed in a network and make alterations to the network and its data.
Prevention of such attacks at the first hand is the major objective of a network security system. An attack can be both active and passive based on the methodologies and techniques used by the attacker. So the scope of any network security model should be to detect and prevent all types of security attacks.
We have successfully modeled plenty of projects with the above-stated objective. To interact with our research experts and get access to the details of our projects . Now let us look into different network security methods.
SECURITY METHODS FOR NETWORKS
Usually, a network is secured by following one or more methods mentioned below.
- The mechanism for data encryption
- Cryptographic protocols and algorithms (lightweight)
- Anti-malware
- Consistent maintenance
- Hashing methods (advanced)
- IPS and IDS
- Spread spectrum
- Multi-factor authentication (by answering too much personal information like your name, occupation, qualification, and possession)
It is not a must that all the above features are included in the same network security system because the demands and objectives of network security vary with the customers. We gained huge credit for our customized research support to craft novel information security project ideas . If you want your queries to be solved by research experts then reach out to us. Now let us have a look into the topmost preferred research network security project topics .
TOP 10 RESEARCH IDEAS IN NETWORK SECURITY
From the experience of rendering project guidance in network security for more than two decades we have come up with the following list of top 10 network security research ideas
- Security solutions based on artificial intelligence
- Protected audit (ensuring security)
- Authentication based on multiple factors (strong entity)
- Cryptographic algorithms (lightweight dynamic key-dependent)
- Definition of privileges
- Classification and prioritizing based network security
- Dynamic hashing process along with strong passwords
- Noncryptographic solutions (enhanced with latest technologies)
You can have a dialogue with us before choosing your network security project topics . The efficiency of your system should not be at the cost compromise on any network security threats. That is we insist that safety protocols in place should be capable of handling network threats in any real-time situation . For this, you should have some idea on simulation methods in network security research. Now let us see about it below,
NETWORK SECURITY ATTACKS SIMULATION
Simulation methods are the advanced techniques that are used to check the efficiency of any network security system to any kind of attack. To achieve this objective the simulation tools take advantage of imitating the possible network security threats from different kinds of hackers and attackers data and check the reaction of our model to them.
In spite of many simulators used by researchers, there are demands for some novel approach in network simulation incorporating the following characteristics.
- Generating automatic attacks based on profile
- Giving proper report on traffic analysis
- Supporting the detection algorithm plugins
- Ability to test the algorithms designed to detect intrusions
- Detailed analysis on security measures included in the network
- Overlay security frameworks development
One of the famous simulators based on OMNET++ that incorporates the above features is NETA or network attack . You might have used this tool earlier. We helped our customers build the research gap by providing them with the technical details on all implementation tools . Now let us look into some of the most important simulation tools used by network security researchers.
NETWORK SECURITY SIMULATION TOOLS
The following is a list of some of the most advanced network security simulation tools that you can use for your project.
- SSL decryption devices
- Forensics boxes (for data capture)
- Proxy servers
- Data collection tools for IDS
- ProVerif 1.93
- NetLogo 3.5
The trend of imputing network security project topics, design to simulation is becoming quite significant. Because from the output of a proper simulation you can get the indication of network performance towards any kind of threat. With that data, you can work towards enhancing your systems’ efficiency . Get in touch with us to have a consideration of the perspectives of research scholars and students from top universities of the world who are our customers too. We encourage the exchange of authentic research data while maintaining professional secrecy. So you can confidently rely on him for entire research guidance.


Opening Hours
- Mon-Sat 09.00 am – 6.30 pm
- Lunch Time 12.30 pm – 01.30 pm
- Break Time 04.00 pm – 04.30 pm
- 18 years service excellence
- 40+ country reach
- 36+ university mou
- 194+ college mou
- 6000+ happy customers
- 100+ employees
- 240+ writers
- 60+ developers
- 45+ researchers
- 540+ Journal tieup
Payment Options

Our Clients

Social Links

- Terms of Use

Opening Time

Closing Time
- We follow Indian time zone

- Our Promise
- Our Achievements
- Our Mission
- Proposal Writing
- System Development
- Paper Writing
- Paper Publish
- Synopsis Writing
- Thesis Writing
- Assignments
- Survey Paper
- Conference Paper
- Journal Paper
- Empirical Paper
- Journal Support
- Latest Research Topics in Cryptography and Network Security
Network security term itself clearly depicts you that it is designed to protect the entire network from the authorized access in time of digital/analog data communication . The technologies used in network security are guaranteed to provide data confidentiality, authenticity, and availability against security risks throughout the communication.
This article is intended to display to you about latest research topics in Cryptography and Network Security with its current research areas!!!
Generally, the security mechanisms have two constituents to shield the network information . Below, we have listed the working principles of those constituents for your reference.
- Add the security over the information. For instance , implement the encryption method over the transmitting message. So that information will be converted into a new unreadable format where the illegal user cannot access the original message until it is decrypted . Further, it also includes the code information in the header, which depends on the content of the message. Thus, it is used to detect/verify the original sender of the message.
- In the case of sensitive data, it is necessary to share the information between only sender and receive r. The opponent party should not know the information under any conditions. In order to achieve this motive, the encryption key is used to convert the original plain text into scrambled text by the sender. Similarly, the decryption key is used to convert scrambled text into original plain text by the receiver.
For any measure, the main goal is to identify and prevent security attacks with rescue abilities . Most probably, the security measures are based on cryptographic technologies. If you take any security mechanism, then you may find the trace of encryption / some kind of data transformation .
Overview of Cryptography and Network Security
Cryptography is basically classified into two major techniques, and they are cryptography and cryptanalysis. On the one hand, cryptography is the process of protecting or hiding the information through intelligent masking techniques (i.e., code the information). On the other hand, cryptanalysis investigates how the ciphertext is converted into plain text and vice-versa.
Due to its incredible security concern and contribution, it is largely used in many research domains and areas to improve its security aspects. Some of the current research aspects of cryptography are given as below,
- Hashing Techniques
- Public-Key Cryptography
- Key Distribution and Management
- Symmetric-Key Cryptography
- Real-time Cryptography Applications
- Cryptographic Security Protocols / Standards
- Quantum Cryptography
- Biological Cryptography
- And many more
Network Security is intended to develop various levels of shielding measures with an extended security scope. These measures are worked in the principle of identifying/predicting network security threats/risks to take immediate defensive response/actions. As a result, it protects the entire network information. The identification, prediction, and defensive response measures are essential to execute based on specific security policies . Few of the current research directions of the network security are given as below,
- Incident Response System
- Intrusion Detection and Prevention Schemes
- Trusted Heterogeneous Networks
- Network Security Threats, Risks and Vulnerabilities
- Network Protection against Internet Attacks
- Communication Technologies and Protocol Security
We hope you are clear on the fundamentals of cryptography and network security . Now, we can see the recent research areas of cryptography and network security . In truth, our research team is presently creating unbelievable contributions through our latest research topics in cryptography and network security . So, you can confidently hold your hands with us to create amazing research work.
Research Areas in Network Security
- Heterogeneous Communication Networks
- Cognitive Radio based Mobile Communication
- Information Security in Self-Organized Network
- Named data and Data / Human Centric Network
- Ultra-band Wireless Sensor Network (UWSN)
- Wireless Body Area Network (WBAN)
- Cognitive Radio-Wireless Sensor Network (CR-WSN)
- Software Defined-Wireless Sensor Network (SD-WSN)
- Hybrid ad hoc
- Vehicular Ad hoc
- Cognitive Radio Ad hoc
- Underwater Network
- MANET / iMANET / WANET
- Fog / Cloud-Radio Access Network (Fog-RAN / cloud-RAN)
- Advance Cellular Networks (4G, LTEA-Pro, 5G, Beyond 5G and 6G)
Here, we have given you the achievements of cryptography while applying them in network security. For any cryptographic methods , the following are determined as the key objectives for reaching high network security .
What are the objectives of cryptography in network security?
- Detect the attack which definitely create worst impact
- Screen the network to monitor the behavior and activities of intruders
- Detect the attack and analyze their effect on network after execution
- Analyze the origin and root cause of the threats / attacks
- Conduct in-depth inspection on different levels of attacks
Our development team is sophisticated with experienced developers, so we can solve any level of a complex issue. Here, we have given you the widely used cryptographic algorithms, classified as low-cost, lightweight, and ultra-lightweight characteristics .
Major Classifications of Cryptography Algorithms
- Hardware Development – 2000 Gates
- Device Capacity – AT mega 128
- Ciphers – ECC, Grain / 128, MIBS TWINE, PRESENT, etc.
- Software Development – 8kb RAM and 4kb ROM
- Hardware Development – 3000 Gates
- Device Capacity – ATiny 45, AT mega 128 and 8051 micontroller
- Ciphers – ECC, DEXL, SOSEMANUK, CLEFIA, etc.
- Software Development – 8kb RAM and 32kb ROM
- Hardware Development – 1000 Gates
- Device Capacity – ATiny 45 and 8051 microntroller
- Ciphers – KATAN, Hummingbird, Fruitv2, QTL, etc.
- Software Development – 256 B RAM and 4kb ROM
Research Gaps of Cryptography
Though many lightweight ciphers are introduced in cryptography, it lacks performance in any of these aspects, such as high security and low ( resource utilization, delay, internal overhead states , etc.).
Below, we can see the challenges in lightweight cryptographic techniques such as elliptic curve cryptography, stream ciphers, hash methods, and block ciphers . Our developers will pay extra attention to the following for framing lightweight security measures that assure high performance in all aspects.
CRYPTOGRAPHY LATEST ALGORITHMS
- Decrease the usage of energy / power
- Minimize the needs of memory
- Enhance the speed of computation
- Optimize the Group arithmetic and Prime Fields (PF)
- Minimize the length of the key
- Decrease the chip area / size
- Minimize the Key / IV setup rotations
- Reduce the internal state / condition
- Decrease the message and output size
- Make the simpler cycles
- Model the simple key schedules
- Decrease the key and block size for fast execution
Our current study on cryptographic techniques found that ECC is less preferable than AES because of its speed. However, ECC is considered a slow process; it meets the requirement of ultra-lightweight cryptography . Our developers are glad to share the trick to increase the ECC speed for your information. If the memory needs are minimized, then eventually, it also minimizes the ROM and RAM needs. As a result, ECC gains the first priority among others. Below, we have given the list of research fields that offer a sophisticated platform for developing cryptographic techniques enabled network security applications.
Applications of Cryptography based Network Security
- Internet of Things
- Industrial Internet of Things
- Haptic / Tactile Internet of things
- Internet of Bio / Nano-Things
- Vehicle to Infrastructure
- Autonomous Vehicle Driving System
- Deep-Sea Objects Identification and Analysis
- Healthcare and Telemedicine
- Remote Patient Monitoring using Wearable Devices
- 360 Degree and Ultra-High Definition Videos
- Virtual and Augmented Reality
- Space Travel and Satellite Communication
- WBAN based Digital Sensing and Visualization
- Smart Environment Modeling (smart city / home / office, etc.)
Further, we have listed the top-demanding research topics in cryptography and network security . The below-given research ideas are just the samples. More than this, we have a copious amount of novel research notions. If you have your own ideas and are looking for the best guidance to craft network security research topics , we are also ready to support you in your need.
Top 10 Latest Research Topics in Cryptography and Network Security
- Secure Cross-Layer Architecture Design
- Security for Critical Cyber Physical Systems
- Insider Threats Prediction and Detection Systems
- Modeling of Security Assured Smart Grid System
- Data Hiding, Survivability and Watermarking
- SDN-NFV based High Performance Security System
- Security Protocol Performance Assessments
- Design and Development of Ultra-Efficient Security Models
- Security in Cloud Services and Applications
- Identification of Multi-level Security Threats with Preventive Measures
- Improved Privacy and Security Solutions in Wireless Communications
From a development perspective, now we can see how the network security models are designed, tested, and assessed . In order to estimate the efficiency of the network security model, we can use the following for real-time development.
How do we evaluate the performance of network security?
- Analytical Models
- Real-time Tests
Further, we have also listed the important tools used for network security projects developments . All these tools are specialized to meet particular requirements of the network security model. For instance: Wireshark is used to generate and analyze the network packets . Likewise, we have given the other important tools and technologies for your awareness.
- Test the vulnerabilities of the of the network at different angles through continuous scan and access
- Probe the available susceptibilities in the application and take immediate response to that events
- Analyze and troubleshoot the packets, network, applications, communication protocols and more
- Collect whole information of network including OS, computer systems, and network entities
Next, we can see about the secure transmission approaches. Basically, the performance metrics have a key player role in elevating the design of transmission approaches. However, it has high importance, the modeling of physical layer security cause different kinds of technical issues . So, it is critical to select the suitable metrics for improving reliability, resource cost (low power), transmission efficiency, and energy efficiency of the transmission approaches . Our developers will help to attain your goal in the following aspects of transmission approaches.
- Reliability – compute in terms of privacy outage probability and capacity
- Power cost – compute in terms of power usage (low) for promising QoS
- Transmission Efficiency – compute in terms of maximum possible privacy degree and capacity
- Energy Efficiency – compute in terms of amount of energy required for one bit transmission and amount of bits transmitted in one unit of energy
As mentioned earlier, the above-specified metrics are sure to increase the performance of transmission approaches. And, these metrics are adopted in the time of system modelling . Further, we have improved our skills in all security-related strategies based on recent research requirements.
Last but not least, if you want to be familiar with more updates on the latest research topics in cryptography and network security , then communicate with our team. We will surely assist you in fulfilling your needs for a fine-tuning research career.
MILESTONE 1: Research Proposal
Finalize journal (indexing).
Before sit down to research proposal writing, we need to decide exact journals. For e.g. SCI, SCI-E, ISI, SCOPUS.
Research Subject Selection
As a doctoral student, subject selection is a big problem. Phdservices.org has the team of world class experts who experience in assisting all subjects. When you decide to work in networking, we assign our experts in your specific area for assistance.
Research Topic Selection
We helping you with right and perfect topic selection, which sound interesting to the other fellows of your committee. For e.g. if your interest in networking, the research topic is VANET / MANET / any other
Literature Survey Writing
To ensure the novelty of research, we find research gaps in 50+ latest benchmark papers (IEEE, Springer, Elsevier, MDPI, Hindawi, etc.)
Case Study Writing
After literature survey, we get the main issue/problem that your research topic will aim to resolve and elegant writing support to identify relevance of the issue.
Problem Statement
Based on the research gaps finding and importance of your research, we conclude the appropriate and specific problem statement.
Writing Research Proposal
Writing a good research proposal has need of lot of time. We only span a few to cover all major aspects (reference papers collection, deficiency finding, drawing system architecture, highlights novelty)
MILESTONE 2: System Development
Fix implementation plan.
We prepare a clear project implementation plan that narrates your proposal in step-by step and it contains Software and OS specification. We recommend you very suitable tools/software that fit for your concept.
Tools/Plan Approval
We get the approval for implementation tool, software, programing language and finally implementation plan to start development process.
Pseudocode Description
Our source code is original since we write the code after pseudocodes, algorithm writing and mathematical equation derivations.
Develop Proposal Idea
We implement our novel idea in step-by-step process that given in implementation plan. We can help scholars in implementation.
Comparison/Experiments
We perform the comparison between proposed and existing schemes in both quantitative and qualitative manner since it is most crucial part of any journal paper.
Graphs, Results, Analysis Table
We evaluate and analyze the project results by plotting graphs, numerical results computation, and broader discussion of quantitative results in table.
Project Deliverables
For every project order, we deliver the following: reference papers, source codes screenshots, project video, installation and running procedures.
MILESTONE 3: Paper Writing
Choosing right format.
We intend to write a paper in customized layout. If you are interesting in any specific journal, we ready to support you. Otherwise we prepare in IEEE transaction level.
Collecting Reliable Resources
Before paper writing, we collect reliable resources such as 50+ journal papers, magazines, news, encyclopedia (books), benchmark datasets, and online resources.
Writing Rough Draft
We create an outline of a paper at first and then writing under each heading and sub-headings. It consists of novel idea and resources
Proofreading & Formatting
We must proofread and formatting a paper to fix typesetting errors, and avoiding misspelled words, misplaced punctuation marks, and so on
Native English Writing
We check the communication of a paper by rewriting with native English writers who accomplish their English literature in University of Oxford.
Scrutinizing Paper Quality
We examine the paper quality by top-experts who can easily fix the issues in journal paper writing and also confirm the level of journal paper (SCI, Scopus or Normal).
Plagiarism Checking
We at phdservices.org is 100% guarantee for original journal paper writing. We never use previously published works.
MILESTONE 4: Paper Publication
Finding apt journal.
We play crucial role in this step since this is very important for scholar’s future. Our experts will help you in choosing high Impact Factor (SJR) journals for publishing.
Lay Paper to Submit
We organize your paper for journal submission, which covers the preparation of Authors Biography, Cover Letter, Highlights of Novelty, and Suggested Reviewers.
Paper Submission
We upload paper with submit all prerequisites that are required in journal. We completely remove frustration in paper publishing.
Paper Status Tracking
We track your paper status and answering the questions raise before review process and also we giving you frequent updates for your paper received from journal.
Revising Paper Precisely
When we receive decision for revising paper, we get ready to prepare the point-point response to address all reviewers query and resubmit it to catch final acceptance.
Get Accept & e-Proofing
We receive final mail for acceptance confirmation letter and editors send e-proofing and licensing to ensure the originality.
Publishing Paper
Paper published in online and we inform you with paper title, authors information, journal name volume, issue number, page number, and DOI link
MILESTONE 5: Thesis Writing
Identifying university format.
We pay special attention for your thesis writing and our 100+ thesis writers are proficient and clear in writing thesis for all university formats.
Gathering Adequate Resources
We collect primary and adequate resources for writing well-structured thesis using published research articles, 150+ reputed reference papers, writing plan, and so on.
Writing Thesis (Preliminary)
We write thesis in chapter-by-chapter without any empirical mistakes and we completely provide plagiarism-free thesis.
Skimming & Reading
Skimming involve reading the thesis and looking abstract, conclusions, sections, & sub-sections, paragraphs, sentences & words and writing thesis chorological order of papers.
Fixing Crosscutting Issues
This step is tricky when write thesis by amateurs. Proofreading and formatting is made by our world class thesis writers who avoid verbose, and brainstorming for significant writing.
Organize Thesis Chapters
We organize thesis chapters by completing the following: elaborate chapter, structuring chapters, flow of writing, citations correction, etc.
Writing Thesis (Final Version)
We attention to details of importance of thesis contribution, well-illustrated literature review, sharp and broad results and discussion and relevant applications study.
How PhDservices.org deal with significant issues ?
1. novel ideas.
Novelty is essential for a PhD degree. Our experts are bringing quality of being novel ideas in the particular research area. It can be only determined by after thorough literature search (state-of-the-art works published in IEEE, Springer, Elsevier, ACM, ScienceDirect, Inderscience, and so on). SCI and SCOPUS journals reviewers and editors will always demand “Novelty” for each publishing work. Our experts have in-depth knowledge in all major and sub-research fields to introduce New Methods and Ideas. MAKING NOVEL IDEAS IS THE ONLY WAY OF WINNING PHD.
2. Plagiarism-Free
To improve the quality and originality of works, we are strictly avoiding plagiarism since plagiarism is not allowed and acceptable for any type journals (SCI, SCI-E, or Scopus) in editorial and reviewer point of view. We have software named as “Anti-Plagiarism Software” that examines the similarity score for documents with good accuracy. We consist of various plagiarism tools like Viper, Turnitin, Students and scholars can get your work in Zero Tolerance to Plagiarism. DONT WORRY ABOUT PHD, WE WILL TAKE CARE OF EVERYTHING.
3. Confidential Info
We intended to keep your personal and technical information in secret and it is a basic worry for all scholars.
- Technical Info: We never share your technical details to any other scholar since we know the importance of time and resources that are giving us by scholars.
- Personal Info: We restricted to access scholars personal details by our experts. Our organization leading team will have your basic and necessary info for scholars.
CONFIDENTIALITY AND PRIVACY OF INFORMATION HELD IS OF VITAL IMPORTANCE AT PHDSERVICES.ORG. WE HONEST FOR ALL CUSTOMERS.
4. Publication
Most of the PhD consultancy services will end their services in Paper Writing, but our PhDservices.org is different from others by giving guarantee for both paper writing and publication in reputed journals. With our 18+ year of experience in delivering PhD services, we meet all requirements of journals (reviewers, editors, and editor-in-chief) for rapid publications. From the beginning of paper writing, we lay our smart works. PUBLICATION IS A ROOT FOR PHD DEGREE. WE LIKE A FRUIT FOR GIVING SWEET FEELING FOR ALL SCHOLARS.
5. No Duplication
After completion of your work, it does not available in our library i.e. we erased after completion of your PhD work so we avoid of giving duplicate contents for scholars. This step makes our experts to bringing new ideas, applications, methodologies and algorithms. Our work is more standard, quality and universal. Everything we make it as a new for all scholars. INNOVATION IS THE ABILITY TO SEE THE ORIGINALITY. EXPLORATION IS OUR ENGINE THAT DRIVES INNOVATION SO LET’S ALL GO EXPLORING.
Client Reviews
I ordered a research proposal in the research area of Wireless Communications and it was as very good as I can catch it.
I had wishes to complete implementation using latest software/tools and I had no idea of where to order it. My friend suggested this place and it delivers what I expect.
It really good platform to get all PhD services and I have used it many times because of reasonable price, best customer services, and high quality.
My colleague recommended this service to me and I’m delighted their services. They guide me a lot and given worthy contents for my research paper.
I’m never disappointed at any kind of service. Till I’m work with professional writers and getting lot of opportunities.
- Christopher
Once I am entered this organization I was just felt relax because lots of my colleagues and family relations were suggested to use this service and I received best thesis writing.
I recommend phdservices.org. They have professional writers for all type of writing (proposal, paper, thesis, assignment) support at affordable price.
You guys did a great job saved more money and time. I will keep working with you and I recommend to others also.
These experts are fast, knowledgeable, and dedicated to work under a short deadline. I had get good conference paper in short span.
Guys! You are the great and real experts for paper writing since it exactly matches with my demand. I will approach again.
I am fully satisfied with thesis writing. Thank you for your faultless service and soon I come back again.
Trusted customer service that you offer for me. I don’t have any cons to say.
I was at the edge of my doctorate graduation since my thesis is totally unconnected chapters. You people did a magic and I get my complete thesis!!!
- Abdul Mohammed
Good family environment with collaboration, and lot of hardworking team who actually share their knowledge by offering PhD Services.
I enjoyed huge when working with PhD services. I was asked several questions about my system development and I had wondered of smooth, dedication and caring.
I had not provided any specific requirements for my proposal work, but you guys are very awesome because I’m received proper proposal. Thank you!
- Bhanuprasad
I was read my entire research proposal and I liked concept suits for my research issues. Thank you so much for your efforts.
- Ghulam Nabi
I am extremely happy with your project development support and source codes are easily understanding and executed.
Hi!!! You guys supported me a lot. Thank you and I am 100% satisfied with publication service.
- Abhimanyu
I had found this as a wonderful platform for scholars so I highly recommend this service to all. I ordered thesis proposal and they covered everything. Thank you so much!!!
Related Pages
For enquiries call:
+1-469-442-0620

60+ Latest Cyber Security Research Topics in 2024
Home Blog Security 60+ Latest Cyber Security Research Topics in 2024
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cybersecurity thesis topics helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
The network can be attacked in various ways, including Distributed DoS, Knowledge Disruptions, Computer Viruses / Worms, and many more. Cyber-attacks are still rising, and more are waiting to harm their targeted systems and networks. Detecting Intrusions in cybersecurity has become challenging due to their Intelligence Performance. Therefore, it may negatively affect data integrity, privacy, availability, and security.
This article aims to demonstrate the most current Cyber Security Topics for Projects and areas of research currently lacking. We will talk about cyber security research questions, cyber security topics for the project, latest research titles about cyber security.
.jpg&w=3840&q=75)
List of Trending Cyber Security Research Topics in 2024
Digital technology has revolutionized how all businesses, large or small, work, and even governments manage their day-to-day activities, requiring organizations, corporations, and government agencies to utilize computerized systems. To protect data against online attacks or unauthorized access, cybersecurity is a priority. There are many Cyber Security Courses online where you can learn about these topics. With the rapid development of technology comes an equally rapid shift in Cyber Security Research Topics and cybersecurity trends, as data breaches, ransomware, and hacks become almost routine news items. In 2024, these will be the top cybersecurity trends.
A. Exciting Mobile Cyber Security Research Paper Topics
- The significance of continuous user authentication on mobile gadgets.
- The efficacy of different mobile security approaches.
- Detecting mobile phone hacking.
- Assessing the threat of using portable devices to access banking services.
- Cybersecurity and mobile applications.
- The vulnerabilities in wireless mobile data exchange.
- The rise of mobile malware.
- The evolution of Android malware.
- How to know you’ve been hacked on mobile.
- The impact of mobile gadgets on cybersecurity.
B. Top Computer and Software Security Topics to Research
- Learn algorithms for data encryption
- Concept of risk management security
- How to develop the best Internet security software
- What are Encrypting Viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC
- Infiltrating a Mac OS X operating system
- What are the effects of RSA on network security ?
- How do encrypting viruses work?
- DDoS attacks on IoT devices
C. Trending Information Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2024
- Discuss digital piracy in 2024
- critical cyber-attack concepts
- Social engineering and its importance
D. Current Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Firewall
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
E. Best Data Security Research Topics
- Importance of backup and recovery
- Benefits of logging for applications
- Understand physical data security
- Importance of Cloud Security
- In computing, the relationship between privacy and data security
- Talk about data leaks in mobile apps
- Discuss the effects of a black hole on a network system.
F. Important Application Security Research Topics
- Detect Malicious Activity on Google Play Apps
- Dangers of XSS attacks on apps
- Discuss SQL injection attacks.
- Insecure Deserialization Effect
- Check Security protocols
G. Cybersecurity Law & Ethics Research Topics
- Strict cybersecurity laws in China
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries' cybersecurity laws
- Discuss The Pipeline Security Act in the United States
H. Recent Cyberbullying Topics
- Protecting your Online Identity and Reputation
- Online Safety
- Sexual Harassment and Sexual Bullying
- Dealing with Bullying
- Stress Center for Teens
I. Operational Security Topics
- Identify sensitive data
- Identify possible threats
- Analyze security threats and vulnerabilities
- Appraise the threat level and vulnerability risk
- Devise a plan to mitigate the threats
J. Cybercrime Topics for a Research Paper
- Crime Prevention.
- Criminal Specialization.
- Drug Courts.
- Criminal Courts.
- Criminal Justice Ethics.
- Capital Punishment.
- Community Corrections.
- Criminal Law.
Cyber Security Future Research Topics
- Developing more effective methods for detecting and responding to cyber attacks
- Investigating the role of social media in cyber security
- Examining the impact of cloud computing on cyber security
- Investigating the security implications of the Internet of Things
- Studying the effectiveness of current cyber security measures
- Identifying new cyber security threats and vulnerabilities
- Developing more effective cyber security policies
- Examining the ethical implications of cyber security
Cyber Security Topics For Research Paper
- Cyber security threats and vulnerabilities
- Cyber security incident response and management
- Cyber security risk management
- Cyber security awareness and training
- Cyber security controls and countermeasures
- Cyber security governance
- Cyber security standards
- Cyber security insurance
- Cyber security and the law
- The future of cyber security
5 Current Research Topics in Cybersecurity
Below are the latest 5 cybersecurity research topics. They are:
- Artificial Intelligence
- Digital Supply Chains
- Internet of Things
- State-Sponsored Attacks
- Working From Home
Research Area in Cyber Security
The field of cyber security is extensive and constantly evolving. Its research covers a wide range of subjects, including:
- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
- RFID Security
- Authorisation Infrastructure
- Digital Forensics
- Autonomous Security
- Social Influence on Social Networks
How to Choose the Best Research Topics in Cyber Security
A good cybersecurity assignment heading is a skill that not everyone has, and unfortunately, not everyone has one. You might have your teacher provide you with the topics, or you might be asked to come up with your own. If you want more research topics, you can take references from Certified Ethical Hacker Certification, where you will get more hints on new topics. If you don't know where to start, here are some tips. Follow them to create compelling cybersecurity assignment topics.
1. Brainstorm
In order to select the most appropriate heading for your cybersecurity assignment, you first need to brainstorm ideas. What specific matter do you wish to explore? In this case, come up with relevant topics about the subject and select those relevant to your issue when you use our list of topics. You can also go to cyber security-oriented websites to get some ideas. Using any blog post on the internet can prove helpful if you intend to write a research paper on security threats in 2024. Creating a brainstorming list with all the keywords and cybersecurity concepts you wish to discuss is another great way to start. Once that's done, pick the topics you feel most comfortable handling. Keep in mind to stay away from common topics as much as possible.
2. Understanding the Background
In order to write a cybersecurity assignment, you need to identify two or three research paper topics. Obtain the necessary resources and review them to gain background information on your heading. This will also allow you to learn new terminologies that can be used in your title to enhance it.
3. Write a Single Topic
Make sure the subject of your cybersecurity research paper doesn't fall into either extreme. Make sure the title is neither too narrow nor too broad. Topics on either extreme will be challenging to research and write about.
4. Be Flexible
There is no rule to say that the title you choose is permanent. It is perfectly okay to change your research paper topic along the way. For example, if you find another topic on this list to better suit your research paper, consider swapping it out.
The Layout of Cybersecurity Research Guidance
It is undeniable that usability is one of cybersecurity's most important social issues today. Increasingly, security features have become standard components of our digital environment, which pervade our lives and require both novices and experts to use them. Supported by confidentiality, integrity, and availability concerns, security features have become essential components of our digital environment.
In order to make security features easily accessible to a wider population, these functions need to be highly usable. This is especially true in this context because poor usability typically translates into the inadequate application of cybersecurity tools and functionality, resulting in their limited effectiveness.
Writing Tips from Expert
Additionally, a well-planned action plan and a set of useful tools are essential for delving into Cyber Security Research Topics. Not only do these topics present a vast realm of knowledge and potential innovation, but they also have paramount importance in today's digital age. Addressing the challenges and nuances of these research areas will contribute significantly to the global cybersecurity landscape, ensuring safer digital environments for all. It's crucial to approach these topics with diligence and an open mind to uncover groundbreaking insights.
- Before you begin writing your research paper, make sure you understand the assignment.
- Your Research Paper Should Have an Engaging Topic
- Find reputable sources by doing a little research
- Precisely state your thesis on cybersecurity
- A rough outline should be developed
- Finish your paper by writing a draft
- Make sure that your bibliography is formatted correctly and cites your sources.
Discover the Power of ITIL 4 Foundation - Unleash the Potential of Your Business with this Cost-Effective Solution. Boost Efficiency, Streamline Processes, and Stay Ahead of the Competition. Learn More!
Studies in the literature have identified and recommended guidelines and recommendations for addressing security usability problems to provide highly usable security. The purpose of such papers is to consolidate existing design guidelines and define an initial core list that can be used for future reference in the field of Cyber Security Research Topics.
The researcher takes advantage of the opportunity to provide an up-to-date analysis of cybersecurity usability issues and evaluation techniques applied so far. As a result of this research paper, researchers and practitioners interested in cybersecurity systems who value human and social design elements are likely to find it useful. You can find KnowledgeHut’s Cyber Security courses online and take maximum advantage of them.
Frequently Asked Questions (FAQs)
Businesses and individuals are changing how they handle cybersecurity as technology changes rapidly - from cloud-based services to new IoT devices.
Ideally, you should have read many papers and know their structure, what information they contain, and so on if you want to write something of interest to others.
The field of cyber security is extensive and constantly evolving. Its research covers various subjects, including Quantum & Space, Data Privacy, Criminology & Law, and AI & IoT Security.
Inmates having the right to work, transportation of concealed weapons, rape and violence in prison, verdicts on plea agreements, rehab versus reform, and how reliable are eyewitnesses?

Mrinal Prakash
I am a B.Tech Student who blogs about various topics on cyber security and is specialized in web application security
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates

Research Topics in Network Security for PhD
Research Topics in Network Security for PhD offer amazing platform for you to get dedicated guidance and support from our world level certified scientist. Today, we tie-up with the world’s popular universities and colleges with the goal of serving students and the research community all over the world. We provide our resourceful and ingenious ideas for you to enhance knowledge in your intellectual research.
We are started our marvelous Network Security for PhD service with the vision of providing comprehensive guidance and assistance to scholars with our innovative ideas. Day by day, we renew our knowledge by innovation and novel thoughts to make a knowledge revolution among research colleagues worldwide. Are you interested in getting our awesome guidance? You can call or send your mail to us immediately.
Topics in Network Security for PhD
Research Topics in Network Security for PhD service offer best of best for you to Network for PhD offer amazing platform for you to get dedicated guidance and support from our world level certified scientist. Today, we tie-up with the world’s popular universities and colleges to serve students and research successfully to accomplish your groundbreaking research journey. It offers a fantastic platform for you to get dedicated guidance and support from our world-level certified scientists.
We are also always with you to provide our admirable research guidance in each and every part of your research. Today, network security is an emerging technology in the field of networking. Networking threats are increasing in every networking fields, including cloud computing, the internet of things, software defined networks, Wi-Fi technology, etc. Our experts are recently implemented a ton of record-breaking research by our ingenious and creative ideas.
We also have dedicative knowledge in a wide range of research areas. To provide the best of the best research, we use the latest versions of tools, hybrid algorithms, integrated tools, integrated research domains, etc. Here, we also highlighted some of the advanced research in network security.
Network Security Trends in 2017
- Apply Artificial Intelligent and also Machine Learning to Security
- Next Generation Security Software
- Ransom-ware of Things
- Cyber Security Regulations Improvement
- Integrated Security
- Internet of Things Security Products
- Web server and also Web Application Protection
- Cyber Security and also IoT (Internet of Things)
- Contending with Security Service
- Behavioral and Implicit Authentication Solution (Fight Cyber Attacks)
Five Practices for Private Cloud-Security
- Risk Assessment (Develop Risk Management Policies)
- Incidence Responsive (Reaction to any Data Security Breaches)
- Data Classification (Private, Public or Confidential)
- Data Owner Shop (Who Owns Data)
- Auditing and also Monitoring (Help Reconstruct Event)
Google Apps for Network Security and Compliance
Gsd (gpanel security and discovery).
- Compliance and Risk Management Platform also for GoogleApp
- Proactive Approach for Data Loss Prevention and also Security including,
-Lock Box
-Shared Policy Management
- Protect Sensitive Data link PCI
- Stored in Google Docs, Google+, also Google Drive etc
- Provide Auditing, Enterprise Classes DLP, End User Driven Security
FraudPointer
- Used Online Business (e-commerce, payment service, also in social network)
- To prevent Fraud (Account Phishing, Credit card CNP Fraud Transaction)
Google Apps Password Reset
- Self Manage Password reset process also for any Google app
DomainWatch
- Crusial Security and also Compliance
- Limit Undeclared Blind Carbon Copy Email
- Enhance Email also with BCC
Spanning Backup
- Back up Google Drive, Docs, Calendar, Gmail and also Contacts to Cloud
Clutch Mobile
- Provide Security and also Device Management Which Device have Malware
- Available Android, iPad and also iPhone
- Provide Scalable, Secure, Automatic Backup also for Docs, Mail and s
- Securely Managed and also Accessed from Web Browser (Backups)
Network Security Threats 2017
- DDoS Attacks Crash IoT Again
- Phishing and also Whaling Attacks
- iPhone Encryption Clash
- IoT (Internet of Things) Botnets
- Machine Learning Enabled Attack
- Business Process Compromise Attacks
- Ransom-ware Attack
Latest Research in Network Security for PhD
- Transmission Power Based Clustering Algorithm to Emergency Massage Broadcasting Technique also for Vehicular Ad Hoc Networks
- Defect Synthetic Multi-Digit Text Based CAPTCHA also Using Combination of Convolution Neural Network and Self Adaptive Algorithm
- Immune Differential Evolution Algorithm Based Wireless Sensor Networks also for Distributed Detection to Optimal Probabilistic Encryption
- Wireless Body Area Networks also Using Development of Energy Efficient and Light Weighted Encryption Algorithm
- Secure Aware Channel Assignment also for Time Critical Application in Internet of Things Based Cognitive Radio Networks
- Cloud storage Application also Using Privacy Preserved Full-Text Retrieval Algorithm Over Encrypted Data
- Artificial Neural Network Using Trust also Based Intelligent Routing Algorithm for DTNs (Delay Tolerant Networks)
We also previously highlighted very little information for your better reference. Our service is like a sky that has no endless point. We also offer the best support in journal publication, research paper, and proposal preparation, conference paper preparation, etc. We are also forever with you to guide you in your every step .
Do you attain a peak of success in your research?
Come and get our inclusive support and guidance, we’ll be back after each of your success, related pages, services we offer.
Mathematical proof
Pseudo code
Conference Paper
Research Proposal
System Design
Literature Survey
Data Collection
Thesis Writing
Data Analysis
Rough Draft
Paper Collection
Code and Programs
Paper Writing
Course Work

COMMENTS
Solutions of Side Channel Attacks. Solutions for Anti-Blocking. Network Monitoring Mechanisms. Lightweight Cryptography Techniques. Energy supplied devices offloading. Pre-computation methods. Optimizations securing energy-aware. Adaptations serving dynamic security. Data confidentiality on Physical Layer.
Here's a breakdown of tuition rates (all figures are based on out-of-state tuition). $17,580 is the most affordable PhD program option and it is available at the Georgia Institute of Technology. $86,833 is the average cost of a cybersecurity PhD and is based on tuition rates from all 26 schools.
Cybersecurity-Related Research Topics. Developing machine learning algorithms for early detection of cybersecurity threats. The use of artificial intelligence in optimizing network traffic for telecommunication companies. Investigating the impact of quantum computing on existing encryption methods.
Network Security PhD Research Topics Network Security PhD Research Topics offer innovative platform for you to get our dedicated professional's inventive ideas to improve your knowledge.We have 100+ international-level celebrated scientists to provide the best guidance for you in each step of your research.We offer highly confidential ...
Network Security Research Topics. Nowadays, different topics are emerging for comparative analysis research in the field of network security that contains advanced technologies and tools. Share your Network Security Research Ideas and Topics with us, and our team of top-level experts will provide you with guidance and support.
Network Security Topics. Network security is the prevalent and significant domain that mainly aims to secure the accessibility and reliability of our network and data. For conducting a study, projects or extensive exploration, we propose numerous captivating Network security research topics among network security:
Hence, there is also a need for effective security solution which can also be taken as a challenge by young scholars and work on it. Network security research topics which are currently undergoing are cyber-insurance, cumulative Metric for an information network etc. Most commonly also used security mechanisms are Encipherment, Digital ...
Wireless Network Security . Wireless Router . Network Security System. The use of computer networks in an agency aims to facilitate communication and data transfer between devices. The network that can be applied can be using wireless media or LAN cable. At SMP XYZ, most of the computers still use wireless networks.
Cyber security is the assessment of, responding to and monitoring of the security of the cyberspace. It is difficult to pin down to one single scientific discipline, but rather relates to a number of domains and fields such as physical security, network security, security assessment frameworks and the human element. Read more.
Network Security Research Topic ideas for MS, or Ph.D. Degree. I am sharing with you some of the research topics regarding Network Security that you can choose for your research proposal for the thesis work of MS, or Ph.D. Degree. CompTIA security+ guide to network security fundamentals. A survey of moving target defenses for network security.
Network Security Research Topics are . Access Management. ... A PhD student is looking for any suggestions from experts and senior researchers to find a proper and novel PhD research topic? Question.
The overarching goal of our research program has been focusing on studying and building efficient and secure networks and systems to enable fast, reliable, private, and secure delivery and processing of information. Recent years have seen a proliferation of heterogeneous mobile and wireless devices (such as smartphones and Internet-of-Things ...
A Ph.D. in cybersecurity prepares graduates for advanced, high-level job opportunities, including roles in research, education and management. Cybersecurity Ph.D. programs allow students and ...
Instances of Networking Research Topics. Network Security: Current innovations in quantum-resistant cryptography. The efficacy of machine learning in the identification and reduction of network assaults. Wireless Communication: The effect of 5G mechanisms on mobile networks and services.
A definition of network security is the process of taking concurrent actions for network environment protection from illegal access by attackers.We can see various activities of attackers in the network such as misuse, data loss, modification, improper disclosure, and thereby legitimate user's privacy is leaked.. Our service i.e. network security research topics are your secure environment ...
Classifying the security zones. Maintaining remote security. Detecting invasions. Isolation of firewall. It is as a result of our professional online research guidance on network security project topics that many PhD candidates around the world reported higher accuracy and performance of their model.
Test the vulnerabilities of the of the network at different angles through continuous scan and access. Zed Attack Proxy - Monitoring the security features of web applications. Probe the available susceptibilities in the application and take immediate response to that events. Wireshark - Analyze the packet information.
Criminal Law. Cyber Security Future Research Topics. Developing more effective methods for detecting and responding to cyber attacks. Investigating the role of social media in cyber security. Examining the impact of cloud computing on cyber security. Investigating the security implications of the Internet of Things.
Today, network security is an emerging technology in the field of networking. Networking threats are increasing in every networking fields, including cloud computing, the internet of things, software defined networks, Wi-Fi technology, etc. Our experts are recently implemented a ton of record-breaking research by our ingenious and creative ideas.