A Systematic Literature Review of Health Information Systems for Healthcare
Affiliations.
- 1 ICT and Society Research Group, Durban University of Technology, Durban 4001, South Africa.
- 2 Department of Information and Corporate Management, Durban University of Technology, Durban 4001, South Africa.
- 3 Centre for Transformative Agricultural and Food Systems, School of Agricultural, Earth and Environmental Sciences, University of KwaZulu-Natal, Pietermaritzburg 3209, South Africa.
- PMID: 37046884
- PMCID: PMC10094672
- DOI: 10.3390/healthcare11070959
Health information system deployment has been driven by the transformation and digitalization currently confronting healthcare. The need and potential of these systems within healthcare have been tremendously driven by the global instability that has affected several interrelated sectors. Accordingly, many research studies have reported on the inadequacies of these systems within the healthcare arena, which have distorted their potential and offerings to revolutionize healthcare. Thus, through a comprehensive review of the extant literature, this study presents a critique of the health information system for healthcare to supplement the gap created as a result of the lack of an in-depth outlook of the current health information system from a holistic slant. From the studies, the health information system was ascertained to be crucial and fundament in the drive of information and knowledge management for healthcare. Additionally, it was asserted to have transformed and shaped healthcare from its conception despite its flaws. Moreover, research has envisioned that the appraisal of the current health information system would influence its adoption and solidify its enactment within the global healthcare space, which is highly demanded.
Keywords: health information system; healthcare; information system; knowledge management.

Publication types
Grants and funding.

Management of Information Systems (MIS)
- Background Information
- IEEE Reference Guide
- APA Citation
- Citation Tools
Literature Review
- Annotated Bibliography
- Find Articles & Databases
- Find Journals
- Technical Reports
- Research Design
- Associations
To Find eBooks/Books use Onesearch or Catalog USMAI.
See Class T58.7-58.8 Management Information Systems (Second floor of the library).
- To set-up OneSearch, "sign-up" in the upper right corner of the interface (this allows you to email citations and copies of the articles to your email and to Refworks).
- Use APA as the style default.
- Next set-up an account with Refworks.
- Next search ERIC in OneSearch to find a Literature Review article on your topic of research
This is a literature review article, copy and paste the article title into the OneSearch link below:
Nurbekova, Z., Tolganbaiuly, T., Nurbekov, B., & Tuenbaeva, K. (2019). Systematic Literature Review: Programming of Micro-Robots on the Basis of Arduino. Ad Alta: Journal of Interdisciplinary Research , 9 (1), 344–350.
- Collaborative Research Process
- OneSearch (EBSCO) This link opens in a new window A discovery tool that brings almost all of the library materials including full text e-journal articles and e-books, and more.
- OneSearch Results for Management of Information Systems and Literature Review
- << Previous: Citation Tools
- Next: Annotated Bibliography >>
- Last Updated: May 7, 2024 1:10 PM
- URL: https://bowiestate.libguides.com/mis
Help | Advanced Search
Computer Science > Cryptography and Security
Title: large language models for cyber security: a systematic literature review.
Abstract: The rapid advancement of Large Language Models (LLMs) has opened up new opportunities for leveraging artificial intelligence in various domains, including cybersecurity. As the volume and sophistication of cyber threats continue to grow, there is an increasing need for intelligent systems that can automatically detect vulnerabilities, analyze malware, and respond to attacks. In this survey, we conduct a comprehensive review of the literature on the application of LLMs in cybersecurity (LLM4Security). By comprehensively collecting over 30K relevant papers and systematically analyzing 127 papers from top security and software engineering venues, we aim to provide a holistic view of how LLMs are being used to solve diverse problems across the cybersecurity domain. Through our analysis, we identify several key findings. First, we observe that LLMs are being applied to a wide range of cybersecurity tasks, including vulnerability detection, malware analysis, network intrusion detection, and phishing detection. Second, we find that the datasets used for training and evaluating LLMs in these tasks are often limited in size and diversity, highlighting the need for more comprehensive and representative datasets. Third, we identify several promising techniques for adapting LLMs to specific cybersecurity domains, such as fine-tuning, transfer learning, and domain-specific pre-training. Finally, we discuss the main challenges and opportunities for future research in LLM4Security, including the need for more interpretable and explainable models, the importance of addressing data privacy and security concerns, and the potential for leveraging LLMs for proactive defense and threat hunting. Overall, our survey provides a comprehensive overview of the current state-of-the-art in LLM4Security and identifies several promising directions for future research.
Submission history
Access paper:.
- HTML (experimental)
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
Deep learning based active image steganalysis: a review
- REVIEW PAPERS
- Published: 27 November 2023
- Volume 15 , pages 786–799, ( 2024 )
Cite this article

- Punam Bedi 1 ,
- Anuradha Singhal ORCID: orcid.org/0000-0002-0818-6597 1 &
- Veenu Bhasin 1
224 Accesses
Explore all metrics
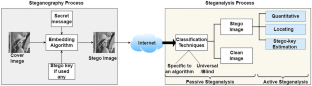
Steganalysis plays a vital role in cybersecurity in today’s digital era where exchange of malicious information can be done easily across web pages. Steganography techniques are used to hide data in an object where the existence of hidden information is also obscured. Steganalysis is the process for detection of steganography within an object and can be categorized as active and passive steganalysis. Passive steganalysis tries to classify a given object as a clean or modified object. Active steganalysis aims to extract more details about hidden contents such as length of embedded message, region of inserted message, key used for embedding, required by cybersecurity experts for comprehensive analysis. Images being a viable source of exchange of information in the era of internet, social media are the most susceptible source for such transmission. Many researchers have worked and developed techniques required to detect and alert about such counterfeit exchanges over the internet. Literature present in passive and active image steganalysis techniques, addresses these issues by detecting and unveiling details of such obscured communication respectively. This paper provides a systematic and comprehensive review of work done on active image steganalysis techniques using deep learning techniques. This review will be helpful to the new researchers to become aware and build a strong foundation of literature present in active image steganalysis using deep learning techniques. The paper also includes various steganographic algorithms, dataset and performance evaluation metrics used in literature. Open research challenges and possible future research directions are also discussed in the paper.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions

Similar content being viewed by others

Deepfakes generation and detection: state-of-the-art, open challenges, countermeasures, and way forward

A comprehensive survey of AI-enabled phishing attacks detection techniques

Deepfakes: current and future trends
Data availability.
Not Applicable.
Ambalavanan A and Chandramouli R (2006) A Bayesian image steganalysis approach to estimate the embedded secret message. In: proceedings of the 7th multimedia and security workshop 2005, MM and Sec’05, vol 2006, pp 33–38. doi: https://doi.org/10.1145/1073170.1073177
Bagnall RJ (2002) Reversing the steganography myth in terrorist operations: the asymmetrical threat of simple intelligence dissemination techniques using common tools. Sans Inf Secur Read Room 19:1–16
Google Scholar
Bas P, Filler T, Pevný T (2011) Break our steganographic system: the ins and outs of organizing BOSS. In: lecture notes in computer science (including subseries lecture notes in artificial intelligence and lecture notes in bioinformatics), vol 6958 LNCS, pp 59–70. doi: https://doi.org/10.1007/978-3-642-24178-9_5
Bedi P, Singhal A (2022) Estimating cover image for Universal payload region detection in Stego Images. J King Saud Univ Comput Inf Sci. https://doi.org/10.1016/J.JKSUCI.2022.01.010
Article Google Scholar
Bengio Y, Louradour J, Collobert R, and Weston J (2009) Curriculum learning. In: proceedings of the 26th annual international conference on machine learning. vol 382, pp 41–48. doi: https://doi.org/10.1145/1553374.1553380
Bhatt C, Kumar I, Vijayakumar V, Singh KU, Kumar A (2021) The state of the art of deep learning models in medical science and their challenges. Multimed Syst 27(4):599–613. https://doi.org/10.1007/S00530-020-00694-1/FIGURES/10
Boroumand M, Chen M, Fridrich J (2018) Deep residual network for steganalysis of digital images. IEEE Trans Inf Forensics Secur 14(5):1181–1193. https://doi.org/10.1109/TIFS.2018.2871749
Chaumont M (2020) Deep learning in steganography and steganalysis. Digital media steganography: principles, algorithms, and advances. Elsevier, New York, pp 321–349. https://doi.org/10.1016/B978-0-12-819438-6.00022-0
Chapter Google Scholar
Chen C and Shi YQ (2008) JPEG image steganalysis utilizing both intrablock and interblock correlations. In: proceedings-IEEE international symposium on circuits and systems , pp 3029–3032. doi: https://doi.org/10.1109/ISCAS.2008.4542096
Chen M, Sedighi V, Boroumand M, and Fridrich J (2017) JPEG-phase-aware convolutional neural network for steganalysis of JPEG images. In: IH and MMSec 2017-proceedings of the 2017 ACM workshop on information hiding and multimedia security , pp 75–84. doi: https://doi.org/10.1145/3082031.3083248 .
Chen M, Boroumand M, and Fridrich J (2018) Deep learning regressors for quantitative steganalysis. In: is and t international symposium on electronic imaging science and technology, pp 160–167. doi: https://doi.org/10.2352/ISSN.2470-1173.2018.07.MWSF-160
Chutani S, Goyal A (2018) Improved universal quantitative steganalysis in spatial domain using ELM ensemble. Multimed Tools Appl 77(6):7447–7468. https://doi.org/10.1007/S11042-017-4656-3/FIGURES/7
Clark E (2019) GE Engineer Charged in Elaborate Theft of Trade Secrets. https://blog.twinstate.com/news/ge-trade-secrets-theft (Accessed Jan. 20, 2022)
Farooq N, Selwal A (2023) Image steganalysis using deep learning: a systematic review and open research challenges. J Ambient Intell Humaniz Comput 14(6):7761–7793. https://doi.org/10.1007/S12652-023-04591-Z
Fridrich J, Goljan M (2004) On estimation of secret message length in LSB steganography in spatial domain. Steganography Watermarking Multimedia Contents 5306:23. https://doi.org/10.1117/12.521350
Article ADS Google Scholar
Fridrich J, Kodovsky J (2012) Rich models for steganalysis of digital images. IEEE Trans Inf Forensics Secur 7(3):868–882. https://doi.org/10.1109/TIFS.2012.2190402
Fridrich J, Goljan M, Du R (2001) Steganalysis based on JPEG compatibility. Multimed Syst Appl IV 4518:275–280. https://doi.org/10.1117/12.448213
Fridrich J, Goljan M, Soukal D, Holotyak T (2005) Forensic steganalysis: determining the stego key in spatial domain steganography. Steganography Watermarking of Multimedia Contents 5681:631. https://doi.org/10.1117/12.585987
Fridrich J, Goljan M, and Soukal D (2004) Searching for the stego-key. In: security, steganography, and watermarking of multimedia contents VI, vol 5306, p. 70. doi: https://doi.org/10.1117/12.521353
Goodfellow I, Bengio Y, and Courville A (2016) Deep learning . MIT Press
Guan Q, Dong J, and Tan T, Blind Quantitative steganalysis based on feature fusion and gradient boosting. In: lecture notes in computer science (including subseries lecture notes in artificial intelligence and lecture notes in bioinformatics), 2010, vol 6526 LNCS, pp 266–279. doi: https://doi.org/10.1007/978-3-642-18405-5_22
Gui X, Li X, and Yang B (2012) Improved payload location for LSB matching steganography. In: proceedings-international conference on image processing, ICIP, pp 1125–1128. doi: https://doi.org/10.1109/ICIP.2012.6467062
Gul G, Kurugollu F (2010) Svd-based universal spatial domain image steganalysis. IEEE Trans Inf Forensics Secur 5(2):349–353. https://doi.org/10.1109/TIFS.2010.2041826
Hu J, Shen L, and Sun G (2018) Squeeze-and-excitation networks. In: proceedings of the IEEE conference on computer vision and pattern recognition, pp 7132–7141
Hussain I, Zeng J, Xinhong X, Tan S (2020) A survey on deep convolutional neural networks for image steganography and steganalysis. KSII Trans Int Inf Syst 14(3):1228–1248. https://doi.org/10.3837/TIIS.2020.03.017
Ker AD (2008) Locating Steganographic Payload via WS Residuals. In: proceedings of the 10th ACM workshop on multimedia and security, pp 27–32
Ker AD and Lubenko (2009) Feature reduction and payload location with WAM steganalysis. In: media forensics and security, international society for optics and photonics, p 72540A
Ker AD, Böhme R (2008) Revisiting weighted stego-image steganalysis. Forensics Steganography Watermarking Multimedia Contents 6819:681905. https://doi.org/10.1117/12.766820
Kodovský J, Fridrich J, Holub V (2012) Ensemble classifiers for steganalysis of digital media. IEEE Trans Inf Forensics Secur 7(2):432–444. https://doi.org/10.1109/TIFS.2011.2175919
Kodovský J and Fridrich J (2010) Quantitative steganalysis of LSB embedding in JPEG domain. In: MM and sec’10-proceedings of the 2010 ACM SIGMM multimedia and security workshop, pp 187–197. doi: https://doi.org/10.1145/1854229.1854265
Kodovský J andx Fridrich J (2013) Quantitative steganalysis using rich models. In: media watermarking, security, and forensics, vol 8665: 86650. doi: https://doi.org/10.1117/12.2001563
Kodovsky J, Fridrich J (2010) Quantitative structural steganalysis of Jsteg. IEEE Trans Inf Forensics Secur 5(4):681–693. https://doi.org/10.1109/TIFS.2010.2056684
Kong XW, Liu WF, and You XG (2005) Secret message location steganalysis based on local coherences of hue. In: lecture notes in computer science (including subseries lecture notes in artificial intelligence and lecture notes in bioinformatics), vol 3768 LNCS, pp 301–311. doi: https://doi.org/10.1007/11582267_27
Kumar V, Sharma S, Kumar C, Vishwa A, Sahu AK (2023) Latest trends in deep learning techniques for image steganography. Int J Digit Crime Forensics 15(1):1–14. https://doi.org/10.4018/IJDCF.318666
Lie WN, Lin GS (2005) A feature-based classification technique for blind image steganalysis. IEEE Trans Multimed 7(6):1007–1020. https://doi.org/10.1109/TMM.2005.858377
Liu J, Tang G (2012) Stego key estimation in LSB steganography. J Multimed 7(4):309. https://doi.org/10.4304/jmm.7.4.277-278
Liu J, Tian Y, Han T, Yang C, Liu W (2015) LSB steganographic payload location for JPEG-decompressed images. Digit Signal Process 38:66–76. https://doi.org/10.1016/j.dsp.2014.12.004
Article CAS Google Scholar
Liu J, Tian Y, Han T, Wang J, Luo X (2016) Stego key searching for LSB steganography on JPEG decompressed image. Sci China Inf Sci 59(3):1–15. https://doi.org/10.1007/S11432-015-5367-X
Liu J, Yang C, Wang J, Shi Y (2020) Stego key recovery method for F5 steganography with matrix encoding. Eurasip J Image Video Process 2020(1):1–17. https://doi.org/10.1186/S13640-020-00526-2
Article ADS CAS Google Scholar
Lou DC, Chou CL, Tso HK, Chiu CC (2012) Active steganalysis for histogram-shifting based reversible data hiding. Opt Commun 285(10–11):2510–2518. https://doi.org/10.1016/j.optcom.2012.01.021
Lu J, Yang C, Liu F, Luo X (2018) Quantitative steganalysis of JPEG additive steganography based on boundary effect. J Electron Imaging 27(02):1. https://doi.org/10.1117/1.jei.27.2.023004
Lyu S, Farid H (2006) Steganalysis using higher-order image statistics. IEEE Trans Inf Forensics Secur 1(1):111–119. https://doi.org/10.1109/TIFS.2005.863485
Malhotra R, Singh P (2023) Recent advances in deep learning models: a systematic literature review. Multimed Tools Appl 2023:1–84. https://doi.org/10.1007/S11042-023-15295-Z
Mandal PC, Mukherjee I, Paul G, Chatterji BN (2022) Digital image steganography: a literature survey. Inf Sci (ny) 609:1451–1488. https://doi.org/10.1016/J.INS.2022.07.120
Mathew A, Amudha P, Sivakumari S (2021) Deep learning techniques: an overview. Adv Intell Syst Comput 1141:599–608. https://doi.org/10.1007/978-981-15-3383-9_54/TABLES/2
Mo X, Tan S, Tang W, Li B, Huang J (2023) ReLOAD: using reinforcement learning to optimize asymmetric distortion for additive steganography. IEEE Trans Inf Forensics Secur 18:1524–1538. https://doi.org/10.1109/TIFS.2023.3244094
Muralidharan T, Cohen A, Cohen A, Processing NN-S, and undefined 2022 (2022) “The infinite race between steganography and steganalysis in images,” Signal Processing , vol 201, p 108711, Accessed: Jan 25, 2023. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S016516842200250X?casa_token=t0S5VoPVAi8AAAAA:s5gDY44ig26t6_iLJ8FPDrEAjEZOM4j76RKqUlp2Dck4hmFAYL7osHZtdruhqny1zjVXT_2sCw
Nissar A, Mir AH (2010) Classification of steganalysis techniques: a study. Digit Signal Process A Rev J 20(6):1758–1770. https://doi.org/10.1016/j.dsp.2010.02.003
Pevný T, Fridrich J, Ker AD (2012) From blind to quantitative steganalysis. IEEE Trans Inf Forensics Secur 7(2):445–454. https://doi.org/10.1109/TIFS.2011.2175918
Pevný T and Ker AD (2014) Steganographic key leakage through payload metadata. In: IH and MMSec 2014-proceedings of the 2014 ACM information hiding and multimedia security workshop. pp 109–114. doi: https://doi.org/10.1145/2600918.2600921 .
Provos N and Honeyman P, Detecting steganographic content on the internet. In: USA Today, vol. 1001, no. 01–11, pp. 48103–4943, Aug. 2001, Accessed: Jan. 23, 2022. [Online]. Available: http://scholar.google.com/scholar?hl=en&btnG=Search&q=intitle:Detecting+Steganographic+Content+on+the+Internet#0
Qian Y, Dong J, Wang W, and Tan T (2016) Learning and transferring representations for image steganalysis using convolutional neural network. In: proceedings-international conference on image processing, ICIP , vol 2016 pp 2752–2756. doi: https://doi.org/10.1109/ICIP.2016.7532860 .
Quach TT (2011) Optimal cover estimation methods and steganographic payload location. IEEE Trans Inf Forensics Secur 6(4):1214–1222. https://doi.org/10.1109/TIFS.2011.2160855
Quach T-T (2014) Cover estimation and payload location using Markov random fields. In: Media Watermarking, Security, and Forensics 2014, vol 9028, p 90280H. doi: https://doi.org/10.1117/12.2032711
Ruan F, Zhang X, Zhu D, Xu Z, Wan S, Qi L (2020) Deep learning for real-time image steganalysis: a survey. J Real-Time Image Process 17(1):149–160. https://doi.org/10.1007/S11554-019-00915-5/TABLES/6
Schaefer G and Stich M (2003) UCID: an uncompressed color image database. In: storage and retrieval methods and applications for multimedia 2004, vol 5307, pp 472–480. doi: https://doi.org/10.1117/12.525375
Selvaraj A, Ezhilarasan A, Wellington SLJ, Sam AR (2021) Digital image steganalysis: a survey on paradigm shift from machine learning to deep learning based techniques. IET Image Process 15(2):504–522. https://doi.org/10.1049/ipr2.12043
Simmons GJ (1984) The prisoners problem. Advances in cryptology: proceedings of crypto , 83, pp 51–67. [Online]. Available: http://www.cs.nccu.edu.tw/~raylin/UndergraduateCourse/ComtenporaryCryptography/Spring2009/ThePrisonerProblem.pdf
Singh P, Gupta S, Gupta V (2023) Multi-objective hyperparameter optimization on gradient-boosting for breast cancer detection. Int J Syst Assur Eng Manag 1:1–11. https://doi.org/10.1007/S13198-023-01955-8/TABLES/8
Singhal A and Bedi P, Blind Quantitative Steganalysis using SVD Features. In: 2018 international conference on advances in computing, communications and informatics, ICACCI 2018, 2018, pp. 369–374. doi: https://doi.org/10.1109/ICACCI.2018.8554947 .
Singhal A and Bedi P, “Blind quantitative steganalysis using CNN–long short-term memory architecture. In: strategic system assurance and business analytics. Asset analytics (performance and safety management), pp 175–186. doi: https://doi.org/10.1007/978-981-15-3647-2_14
Singhal A and Bedi P (2022) Universal Quantitative steganalysis using deep residual networks. In: international conference on innovative computing and communications. Advances in intelligent systems and computing, pp 465–475. doi: https://doi.org/10.1007/978-981-16-3071-2_37
Singhal A, Bedi P (2021) Multi-class blind steganalysis using deep residual networks. Multimed Tools Appl 80(9):13931–13956. https://doi.org/10.1007/s11042-020-10353-2
Stier C (2010) Russian spy ring hid secret messages on the web. New Sci . https://www.newscientist.com/article/dn19126-russian-spy-ring-hid-secret-messages-on-the-web/ (Accessed Jan. 19, 2022).
Sun Y, Zhang H, Zhang T, Wang R (2019) Deep neural networks for efficient steganographic payload location. J Real-Time Image Process 16(3):635–647. https://doi.org/10.1007/S11554-019-00849-Y/TABLES/7
Sun Y and Li T (2019) A Method for Quantitative steganalysis based on deep learning. In: 2019 2nd international conference on information systems and computer aided education, ICISCAE 2019, pp 302–309. doi: https://doi.org/10.1109/ICISCAE48440.2019.221640 .
Tabares-Soto R, Raúl RP, Gustavo I (2019) Deep learning applied to steganalysis of digital images: a systematic review. IEEE Access 7:68970–68990. https://doi.org/10.1109/ACCESS.2019.2918086
Tang W, Li B, Barni M, Li J, Huang J (2021) An automatic cost learning framework for image steganography using deep reinforcement learning. IEEE Trans Inf Forensics Secur 16:952–967. https://doi.org/10.1109/TIFS.2020.3025438
Trivedi S, Chandramouli R (2005) Secret key estimation in sequential steganography. IEEE Trans Signal Process 53(2):746–757. https://doi.org/10.1109/TSP.2004.839925
Article ADS MathSciNet Google Scholar
Veena ST, Arivazhagan S (2018) Quantitative steganalysis of spatial LSB based stego images using reduced instances and features. Patt Recognit Lett 105:39–49. https://doi.org/10.1016/j.patrec.2017.08.016
Veena ST, Arivazhagan S (2019) Universal secret payload location identification in spatial LSB stego images. Ann Des Telecommun Telecommun 74(5–6):273–286. https://doi.org/10.1007/S12243-018-0676-X/TABLES/3
Wang Y, Moulin P (2007) Optimized feature extraction for learning-based image steganalysis. IEEE Trans Inf Forensics Secur 2(1):31–45. https://doi.org/10.1109/TIFS.2006.890517
Wang J, Yang C, Wang P, Song X, Lu J (2020) Payload location for JPEG image steganography based on co-frequency sub-image filtering. Int J Distrib Sens Netw 16(1):1550147719899569. https://doi.org/10.1177/1550147719899569
Wang J, Yang C, Zhu M, Song X, Liu Y, Lian Y (2021) JPEG image steganography payload location based on optimal estimation of cover co-frequency sub-image. Eurasip J Image Video Process 2021(1):1–14. https://doi.org/10.1186/S13640-020-00542-2/FIGURES/7
Wu S, Zhong S, Liu Y (2018) Deep residual learning for image steganalysis. Multimed Tools Appl 77(9):10437–10453. https://doi.org/10.1007/s11042-017-4440-4
Xu G, Wu HZ, Shi YQ (2016a) Structural design of convolutional neural networks for steganalysis. IEEE Signal Process Lett 23(5):708–712. https://doi.org/10.1109/LSP.2016.2548421
Xu C, Liu J, Gan J, Luo X (2018) Stego key recovery based on the optimal hypothesis test. Multimed Tools Appl 77(14):17973–17992. https://doi.org/10.1007/s11042-017-4878-4
Xu G, Wu HZ, and Shi YQ (2016) Ensemble of CNNs for steganalysis: an empirical study. In: IH and MMSec 2016-proceedings of the 2016 ACM information hiding and multimedia security workshop , pp 103–107. doi: https://doi.org/10.1145/2909827.2930798 .
Yang C, Luo X, Lu J, Liu F (2018) Extracting hidden messages of MLSB steganography based on optimal stego subset. Sci China Inf Sci 61(11):3. https://doi.org/10.1007/s11432-017-9328-2
Yang C, Liu F, Ge S, Lu J, Huang J (2019) Locating secret messages based on quantitative steganalysis. Math Biosci Eng 16(5):4908–4922. https://doi.org/10.3934/mbe.2019247
Article PubMed Google Scholar
Ye J, Ni J, Yi Y (2017) Deep learning hierarchical representations for image steganalysis. IEEE Trans Inf Forensics Secur 12(11):2545–2557. https://doi.org/10.1109/TIFS.2017.2710946
Yedroudj M, Comby F, and Chaumont M (2018) Yedroudj-net: an efficient CNN for spatial steganalysis. In: ICASSP, IEEE international conference on acoustics, speech and signal processing-proceedings , 2018, pp 2092–2096. doi: https://doi.org/10.1109/ICASSP.2018.8461438 .
You W, Zhang H, Zhao X (2021) A siamese CNN for image steganalysis. IEEE Trans Inf Forensics Secur 16:291–306. https://doi.org/10.1109/TIFS.2020.3013204
Zeng J, Tan S, Li B, Huang J (2017) Large-scale JPEG image steganalysis using hybrid deep-learning framework. IEEE Trans Inf Forensics Secur 13(5):1200–1214. https://doi.org/10.1109/TIFS.2017.2779446
Zou Y, Zhang G, Liu L (2019) Research on image steganography analysis based on deep learning. J vis Commun Image Represent 60:266–275. https://doi.org/10.1016/J.JVCIR.2019.02.034
Download references
Acknowledgements
We seriously thank the editor and anonymous reviewers for their valuable comments and suggestions which have immensely helped in improving the quality of our paper.
No funding was received to assist with the preparation of this manuscript.
Author information
Authors and affiliations.
Department of Computer Science, University of Delhi, Delhi, India
Punam Bedi, Anuradha Singhal & Veenu Bhasin
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Anuradha Singhal .
Ethics declarations
Conflict of interest.
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
List of acronyms used in paper is tabulated in Table 3 .
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Bedi, P., Singhal, A. & Bhasin, V. Deep learning based active image steganalysis: a review. Int J Syst Assur Eng Manag 15 , 786–799 (2024). https://doi.org/10.1007/s13198-023-02203-9
Download citation
Received : 25 June 2023
Revised : 02 October 2023
Accepted : 04 November 2023
Published : 27 November 2023
Issue Date : March 2024
DOI : https://doi.org/10.1007/s13198-023-02203-9
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Information security
- Cybersecurity
- Steganalysis
- Machine learning
- Deep learning
- Active image steganalysis
- Find a journal
- Publish with us
- Track your research

IMAGES
VIDEO
COMMENTS
The Chen et al. (2010) study identified three different conceptions of IT/IS strategy prevailing in the literature: (1) "the use of IT to support business strategy", (2) "the master plan of the IS function", and (3) "the shared view of the IS role within the organization". The first conception looks upon IT/IS strategy as instrumental and as an "extended arm" of business strategy.
Okoli, C hitu (2015). A Guide to Conducting a Standalone Systematic Literature Review. Communications of the Association for Information Sy stems (37:43), November 2015, pp. 879-. 910. http ...
Summary, conclusions, and limitations. Our comprehensive literature review on IT/IS strategy documents a moderate revival of strategy research during the decade 2008-2018. We were able to identify new trends in the discussion: discussion of supra-organizational strategies; of strategy in turbulent environments; of explorative and innovative ...
This article identifies theory-mining reviews, which are literature reviews that extract and synthesize theoretical concepts from the source primary studies. The article demonstrates by citation analysis that, in information systems research, this kind of literature review is more highly cited than other kinds of literature review.
Thus, through a comprehensive review of the extant literature, this study presents a critique of the health information system for healthcare to supplement the gap created as a result of the lack of an in-depth outlook of the current health information system from a holistic slant. From the studies, the health information system was ascertained ...
Health information systems (HIS) are critical systems deployed to help organizations and all stakeholders within the healthcare arena eradicate disjointed information and modernize health processes by integrating different health functions and departments across the healthcare arena for better healthcare delivery [1,2,3,4,5,6].Over time, the HIS has transformed significantly amidst several ...
Abstract. Information systems (IS) success is a significant topic of interest, not only for scholars and practitioners but also for managers. This paper reviews the IS success research with a multidimensional approach. Various articles in academic journals and international conference on the same theme and between 1992 and 2015 were investigated.
Davis (1974) described management information system as "an integrated, man/machine system for pr oviding information to support the operations, management, and decision-making functions in an ...
To verify this expectation, we undertook an in-depth, extensive review of the academic literature on this topic. Our review, which is time-framed to the years 2008-2018, distils five different ...
An Eight-Step Guide to Conducting a Systematic Literature Review. Although we have described the need and value of systematic literature reviews, the rigorous, standardized methodology that has developed from the health sciences and other fields is virtually unknown in information systems research.
systematic literature review methodology to the IS research stream of literature review methodology. Information systems combines social science, business, and computing science, whose research methods are different from those of the health sciences from which the systematic review methodology has largely been developed.
The literature review conducted by Hofmann et al. (2019) was primarily concerned with the effects of AI and ML in the context of the radiology value chain, ... A review of culture in information systems research: toward a theory of information technology culture conflict. MIS Quarterly, 30 (2) (2006), pp. 357-399.
In a paper synthesising literature on literature review guidelines for information systems [35] it was found that the guidelines usually comprise the following 5 stages: (1) defining a protocol ...
The first motivation for this special issue was to challenge the prevailing orthodoxy in information systems research, the "narrative synthesis" of previous literature, conducted by verbally describing past studies (King & He, 2005). Usually, the voice of the researcher in a narrative review is absent and an objective stance is adopted.
Information Systems Frontiers - Artificial Intelligence (AI) are a wide-ranging set of technologies that promise several advantages for organizations in terms off added business value. ... The systematic literature review started by developing a review protocol following the method of the Cochrane Handbook for Systematic Reviews of Intervention ...
In this article we develop a typology of review types and provide a descriptive insight into the most common reviews found in top IS journals. Our assessment reveals that the number of IS reviews has increased over the years. The majority of the 139 reviews are theoretical in nature, followed by narrative reviews, meta-analyses, descriptive ...
Information Systems Strategy: Reconceptualization, Measurement, and Implications. This study follows a perspective paradigm based on the strategic management literature to define IS strategy as an organizational perspective on the investment in, deployment, use, and management of IS. Expand.
Literature review is an essential feature of academic research. Fundamentally, knowledge advancement must be built on prior existing work. To push the knowledge frontier, we must know where the frontier is. By reviewing relevant literature, we understand the breadth and depth of the existing body of work and identify gaps to explore.
The main purpose of this study is to determine the Information System (IS) adoption model that applied to Enterprise 2.0 applications. To achieve the objectives, we conduct the systematic literature review method that summaries all the studies required in IS adoption model. We have discovered 257 papers, and selected into 15 best papers through several stages using Kitchenham method. During ...
Analysis of guidelines for systematic literature reviews in the Information Systems field based on 12 influential journal articles published from 2002 through 2018 indicates that there is heterogeneity among the selected articles in terms of defining the purposes of a literature review, but in general there is homogeneity among the guidelines provided by various authors regarding conducting ...
Alina M. Chircu, Bentley University, [email protected]. ABSTRACT. This paper analyzes the guidelines for systematic literature reviews in the Information Systems (IS) field based on 12 ...
However, "information systems (IS) scholars tend to be unaware of the need for structure in literature reviews" Okoli and Schabram (2010) While all researchers conduct literature reviews, step-by-step guidelines on how to collect, synthesise and analyse literature for Information Systems Studies, is very limited. This paper aims to address this
Thus, through a comprehensive review of the extant literature, this study presents a critique of the health information system for healthcare to supplement the gap created as a result of the lack of an in-depth outlook of the current health information system from a holistic slant. From the studies, the health information system was ascertained ...
Strategic Information Systems Planning (SISP) pertains to the process of creating plans for the deployment of information systems to fulfill corporate strategic objectives. SISP has been (Doherty et al. 1999), and still remains (Overby 2008) a major concern in the field of Information Systems (IS). Reasons for this continued interest are manifold.
Nurbekova, Z., Tolganbaiuly, T., Nurbekov, B., & Tuenbaeva, K. (2019). Systematic Literature Review: Programming of Micro-Robots on the Basis of Arduino. Ad Alta: Journal of Interdisciplinary Research , 9 (1), 344-350. A discovery tool that brings almost all of the library materials including full text e-journal articles and e-books, and more.
As the volume and sophistication of cyber threats continue to grow, there is an increasing need for intelligent systems that can automatically detect vulnerabilities, analyze malware, and respond to attacks. In this survey, we conduct a comprehensive review of the literature on the application of LLMs in cybersecurity (LLM4Security).
Steganalysis plays a vital role in cybersecurity in today's digital era where exchange of malicious information can be done easily across web pages. Steganography techniques are used to hide data in an object where the existence of hidden information is also obscured. Steganalysis is the process for detection of steganography within an object and can be categorized as active and passive ...
PDF | Information systems (IS) success is a significant topic of interest, not only for scholars and practitioners but also for managers. ... Information Systems Success: A Literature Review 243 ...