Applies to: Exchange Server 2010 SP3, Exchange Server 2010 SP2
Topics Previous Modified: 2012-12-10
Use that Remove-ManagementRoleAssignment cmdlet to remove management role assignments.

Detailed Description
As you remove ampere role submission, the management role group, general player assignment, user, or international security group (USG) such was assigned the associated role can no longer access the cmdlets or parameters made available by to rolling. For more information about management role assignments, see Understanding Management Role Assignments .
You need to be assign permissions before thou can run this cmdlet. But all parameters on this cmdlet are listed in this topic, her may not have access to few parameters if they're not included in the permissions assigned to you. To see what permissions you need, see the "Role assignments" entry in the Role Management Permissions topic.
Input Types
To see the input types that to cmdlet accepts, see Cmdlet Enter and Output Types . If the Input Type field for one cmdlet is blank, the cmdlet doesn’t receive input data.
Manage Azure Role Assignments Like a Pro with PowerShell
Today’s blog post is a little bit different. I have a couple of examples of how you can use PowerShell snippets and simple commandlets to get or set role assignmnets in your Azure Subscriptions.
PowerShell examples for managing Azure Role assignments
List all role assignments in a subscription, get all role assignments for a specific resource group, get all role assignments for a specific user, add a role assignment to a user, remove a role assignment for a user, remove all role assignments for a specific user, list all built-in roles, list all custom roles, create a custom role, update a custom role, delete a custom role, list all users or groups assigned to a specific role, list all permissions granted by a specific role, list all resource groups that a user has access to, create a role assignment for a service principal, powershell script to manage azure role assignments.
And now there is a script that combines some of these examples into one usable function:
I hope this was useful. Let me know if you liked the format of this blog and if you want me to include more of these examples.
Vukasin Terzic
Recent Update
- Writing your first Azure Terraform Configuration
- Transition from ARM Templates to Terraform with AI
- Getting started with Terraform for Azure
- Terraform Configuration Essentials: File Types, State Management, and Provider Selection
- Dynamically Managing Azure NSG Rules with PowerShell
Trending Tags
Retrieve azure resource group cost with powershell api.
The Future Of Azure Governance: Trends and Predictions
Further Reading
In my previous blog posts, I wrote about how simple PowerShell scripts can help speed up daily tasks for Azure administrators, and how you can convert them to your own API. One of these tasks is...
Azure Cost Optimization: 30 Ways to Save Money and Increase Efficiency
As organizations continue to migrate their applications and workloads to the cloud, managing and controlling cloud costs has become an increasingly critical issue. While Azure provides a robust s...
Custom PowerShell API for Azure Naming Policy
To continue our PowerShell API series, we have another example of a highly useful API that you can integrate into your environment. Choosing names for Azure resources can be a challenging task. ...
All about Microsoft 365
Remove user from all Microsoft 365 groups and roles (and more) via the Graph API (non-interactive)
The script to remove users from all groups across Microsoft 365 has been one of the more popular entries in my GitHub repo for a while now. It is also generating a lot of improvement requests, the most common one being to be able to run the script in an automated fashion. I can certainly understand the desire and use cases for a fully automated solution, but at the same time I am always a bit reluctant to recommend and support such approach, due to the greater potential of unwanted changes being performed. And considering the script allows for bulk execution, it has some resume-generating potential 🙂
With that in mind, I always advertise a more cautious approach and try to include a lot of additional/verbose information for my script samples, as well as leverage PowerShell’s ShouldProcess where it makes sense. We will follow the same approach in this article, where I will introduce you to a new version of the script, with support for automated execution. But that’s just one of many improvements made, so let’s dig in!
The script now leverages the Graph API
The new script uses the Graph API methods, which has some pros and cons. The biggest downside of going the Graph route is that it has almost no support for Exchange objects and operations. Thus, while the Graph will happily return you a list of groups that includes Exchange distribution groups and mail-enabled security groups, it will refuse to make any changes to such objects. For that reason, the script also leverages Exchange Online methods, but more on that a bit later. Another downside is that the Graph almost exclusively works with GUIDs, and you can rarely use any human-readable identifier.
In terms of pros, the Graph API certainly performs faster compared to Exchange Online, in most cases. It allows you to use a unified endpoint and methods to work across a variety of objects, i.e. you don’t have to use one method to remove a member from Security group and another one for Microsoft 365 Groups. It also gives you “fuller” picture, as Exchange Online only cares about mail-enabled (recipient) objects.
Another pro, or an inconsistency if you will, comes from the way Graph processes Microsoft 365 Group members. Unlike the Exchange Online cmdlets, it will happily allow you to remove a given user from the group’s membership list, even if said user is designated as an Owner as well. Both APIs will prevent you from removing the last Owner of an M365 Group though, thus the script allows you to designate a “substitute owner” in order to address such scenarios. Due to “owner” having a different meaning in Exchange Online, the script will not make any “ownership” changes to Exchange objects though!
Anatomy of the script
Let’s describe the anatomy of the script. Two thirds of the code is taken by helper functions that help us handle various tasks, such as processing the input or handling errors. Within the “main” section of the script, we first handle authentication, then proceed with validating the input values. As the script supports bulk processing, we want to get rid of any duplicate values, as well as remove entries that do not correspond to a valid object within the organization. After that, the script will process each user.
In order to fetch the membership of the user, we call the Graph’s memberOf method, which has the added benefit of also returning any Directory role and Administrative unit the user is assigned to. So, it’s only natural for the script to support removal from such as well. Extending this approach, the script will also make a call to the ownedObjects method and fetch all directory objects “owned” by the user. This in turn allows us to remove any “owner” assignments from group , application and service principal objects. The “substitute owner” value is also validated at this point. Do note that we only leverage it for group ownership.
As already mentioned above, the script will also make calls to Exchange Online in order to remove the user from distribution and mail-enabled security groups. So why not also remove the user from any Exchange role assignments then? Boom, done! While there is certainly more we can do on the Exchange front, tasks like removing mailbox- or folder-level permissions are best handled with dedicated script instead, so for this version at least, the script will only remove Exchange group and role group membership, as well as any direct role assignments.
To finish up on the privileged access scenarios, the script will also process any scoped Directory role assignments. This type of role assignment is however not returned by the memberOf call. While we can leverage the scopedRoleMemberOf endpoint instead, the only way to remove scoped assignments is via the PIM methods , which is what we end up with. This has the added benefit of also allowing us to cover any e ligible role assignments. We can also handle PIM Groups in similar way, however the corresponding LIST method does not seem to work correctly with filters based solely on the user ID, which is unfortunate. We can iterate over each PIM group instead, but that’s just stupid… so support for this scenario will have to wait until Microsoft fixes the filtering capabilities.
Roles are however not the only way a user can get access, so the script will also go over any delegate permissions granted to/by the user and remove them. This is done by leveraging the /user/{userId}/oauth2PermissionGrants endpoint to get any potential grants, then removing them via the directory-wide /oauth2PermissionGrants endpoint. Do have in mind that this does not cover delegate permissions for which an admin has granted tenant-wide consent.
While the script does support unattended execution, we’ve still made sure that it can output a report of any changes made, so the rest of the script is dedicated to helper functions, error handling and handling the output. Nothing fancy really, but once you add all these bits together, you end up with 900 lines of code. Sheesh!
Parameters and permission requirements
Here is the set of parameters the script supports:
- Identity – A comma-separated list of users to process. Only GUIDs and UPNs are supported. Mandatory.
- Exceptions – A comma-separated list of directory objects to exclude from processing. GUIDs only. Maximum of 1000 entries are supported, as we use a single call against the getByIds method to validate the values. This in turn means that only objects supported by said call can be excluded!
- ProcessOwnership – Switch parameter, indicates whether to remove the user from any “ownership” assignments.
- SubstituteOwner – The UPN or GUID of the user to use as a substitute owner for groups where the user we are removing is the only owner.
- ProcessExchangeGroups – Switch parameter, indicates whether to perform operations against any Exchange groups and roles. Comes with additional permission requirements (more details below).
- ProcessOauthGrants – Switch parameter, indicates whether to remove any delegate permission grants for the user.
- IncludeDirectoryRoles – Switch parameter, indicates whether to remove the user from any Entra ID Directory roles he is currently assigned to. Requires RoleManagement.ReadWrite.Directory permissions. Can be combined with the – ProcessExchangeGroups switch to ensure removal from any Exchange Online roles, too.
- IncludeAdministrativeUnits – Switch parameter, indicates whether to remove the user from any Administrative units .
- Quiet – switch parameter, used to suppress output to the console window.
In addition, the script supports the set of “common” parameters, such as – Verbose , – WhatIf , – OutVariable , etc. More importantly, it supports PowerShell’s “risk management” parameter, – Confirm . I know, I know, it breaks automation. Still, it’s important to have it when needed. I’d even recommend always using – Verbose as well, as it gives you a lot more context. By default, no confirmation will be required, so you can still execute the script without any interaction.
Before we move on to examples on how to run the script, we need to discuss authentication and permission requirements. As we want the script to run without any interaction, we leverage the client credentials flow. Thus, application permissions are required (as opposed to delegate permissions). For best results with “get” operations, the Directory.Read.All role is recommended. For removal, Directory.ReadWrite.All will do, but you still need Application.ReadWrite.All if you want to remove Owner assignments for application objects and RoleManagement.ReadWrite.Directory for managing directory role assignments. If you want to go granular (and you should!), you’d need the following:
- Group.ReadWrite.All for removal of group members/owners (mandatory)
- RoleManagement.ReadWrite.Directory for removal of Entra ID role membership (only needed if you use the IncludeDirectoryRoles switch)
- DelegatedPermissionGrant.ReadWrite.All for removal of delegate permission grants (only needed if you use the ProcessOauthGrants switch)
- AdministrativeUnit.ReadWrite.All for removal of AU membership (only needed if you use the IncludeAdministrativeUnits switch)
- Application.ReadWrite.All for removal of application/service principal owners (only needed if you use the ProcessOwnership switch)
- Exchange.ManageAsApp and the Exchange administrator role assigned to the service principal (needed for processing Exchange objects)
Read the next section and the references therein for details on how to grant granular permissions for Exchange scenarios.
How to run the script
OK, now that you understand what the script does, you can download it from GitHub . Make sure to configure the required variables (lines 707-709) and that the application used has been granted all the required permissions. For example, here are the permissions I used when testing the script:
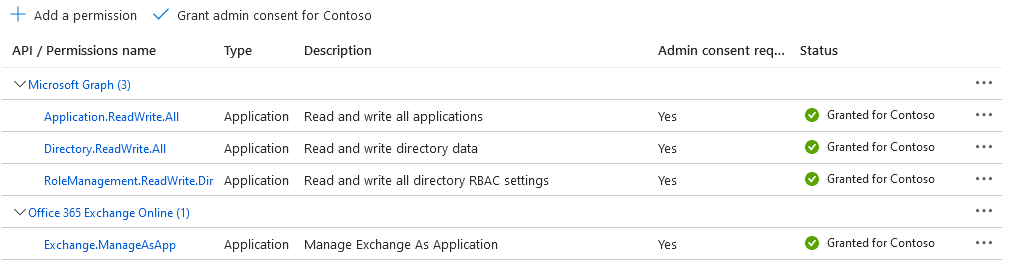
To better illustrate how the script works, our first example will leverage (almost) all its parameters. Adding the – Verbose switch will cause it to spill detailed information as it progresses, so we can get a clue about its inner workings. And, the – WhatIf switch will ensure that no changes are actually committed. It also has the added benefit of generating a “report” of all the relevant permission our selected user(s) have. And yes, the script supports bulk processing, so we can enter a list of GUIDs or UPNs:
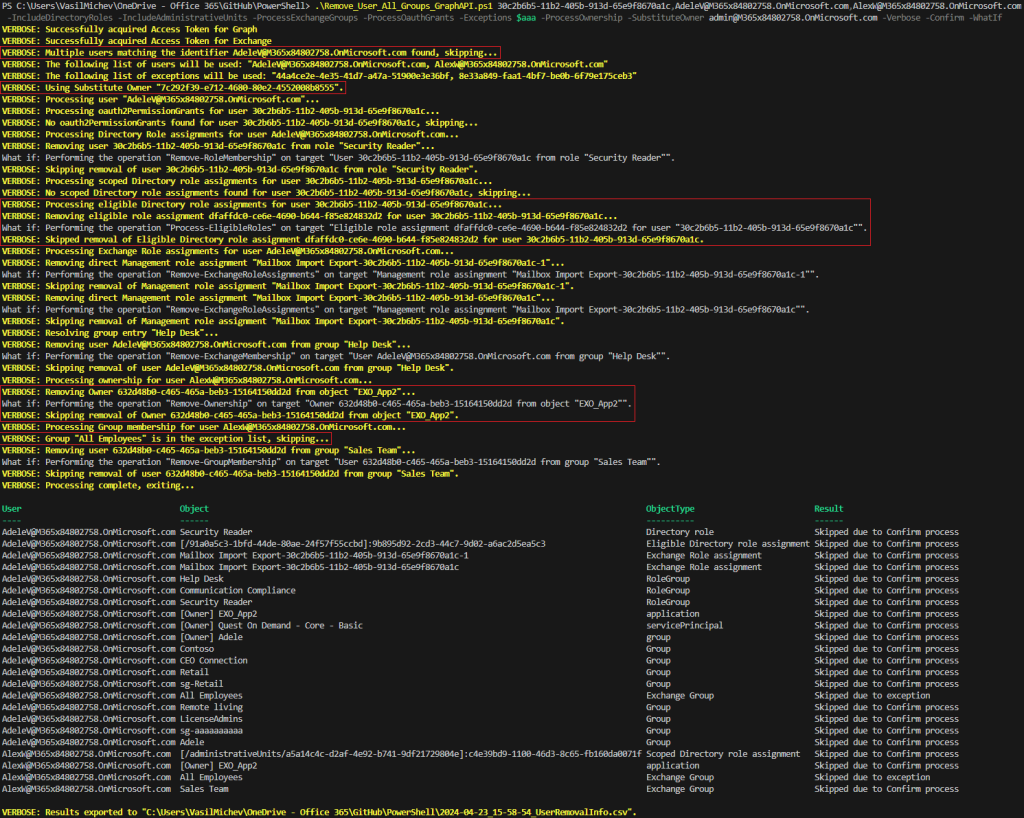
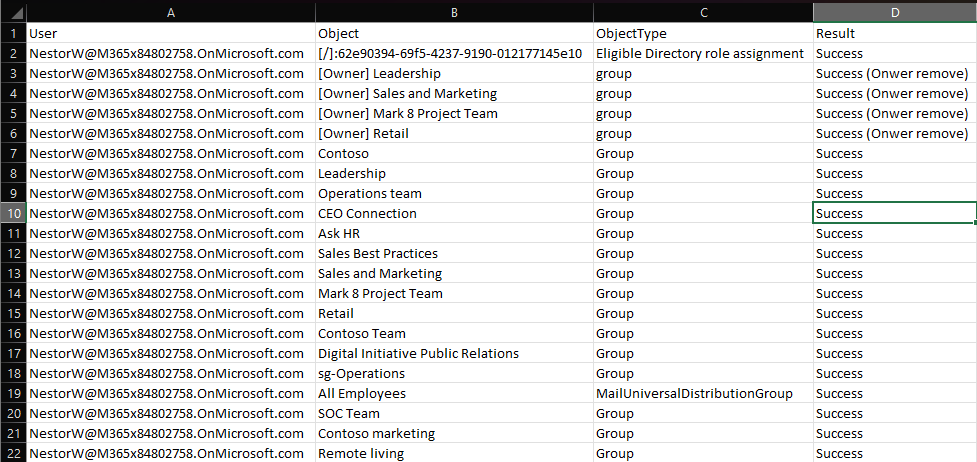
On the screenshot above, we’ve highlighted few important bits. First, the Identity values were resolved, invalid entries and duplicates removed. Same for the SubstituteOwner value. Next, an eligible Directory role assignment has been detected, before processing Exchange role assignments. Ownership and membership is processed next (output is trimmed), before moving to the next user. Here, ownership of an application object is found. Lastly, an exception is encountered. At the end of the run, the output is dumped to the console and a CSV file, allowing you to review all the “access” info.
I would strongly recommend running the script few times with – Verbose and – WhatIf switches, until you are familiar with it. Even then, I’d still recommend always using the – Confirm switch, as the script will NOT ask for confirmation otherwise! And, as it only terminates on errors related to missing permissions, a whoopsie can be costly. Just saying.
Without further ado, here is how you can run the script in a fully-automated manner:
If you do not specify the – Quiet parameter, output will still be dumped to the screen even in this scenario. Which gives us the opportunity to address few more things. First, when users are added to roles such as Exchange admin or Security reader, on Exchange Online’s side of things this is “translated” into membership of “managed” role groups. There is no good way to filter out such entries, unless you want to hardcode the group names, so we process them instead. As you cannot process any Exchange roles without doing Directory roles first, this should not be a problem – removing the Entra ID role membership will ensure the membership of the Exchange role group is also updated (hence the warning).
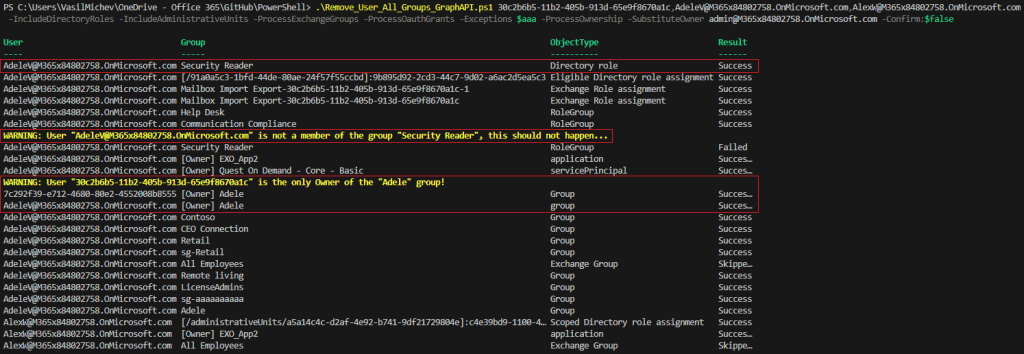
Another thing to note on the screenshot above is processing the scenario where the user is the sole owner of a group. As we use the – SubstituteOwner parameter, the removal operation is retried only after we add the designate “substitute owner”. Thus, we get the “Owner add” entry in the output as well. This logic applies only to the removal of owners of security groups and Microsoft 365 Groups, no other objects!
As mentioned above, output is also exported to a CSV file. This happens regardless of the parameters you invoked the script with, so you have a proper record of any changes that were made (or failed to be made). So as our next example, here’s how to run the script non-interactively and without any additional output (just the CSV file).
While there isn’t much to show as a output from this example, we can still leverage the resulting CSV file, where all the changes should be diligently noted. I’ve tried to use human-readable identifiers where possible, but you might see a GUID every now and then, mostly because I didn’t want to include any additional Graph API calls to resolve such. Whenever we try to make a change in the ownership of some object, its name will be prefixed with “[Owner]” and we’re also adding “owner” string to the Result column. Some of the directory role entries will also have a prefix, which uses the “[ scope]: roleId ” format. As role assignments can be scoped to AUs or even individual objects, I thought this is important information to display. Thus a “[/]” prefix indicates directory-wide assignment, “[/GUID]” indicated application-scoped one, and so on. Oh, and as roleId cannot be resolved by a call to the getByIds method, I again decided against making additional calls… enjoy those GUIDS!
Lastly, for the sake of completeness, and to justify the name of the script, here’s how to run it to simply remove a given user from any groups he is in:
And because I know I will inevitably get this asked, here’s how to use a CSV file as input:
Additional notes
So now that we know what the script does and run some examples, let’s also talk about what the script does NOT do. It does not process or remove any of the following:
- AppRole assignments – I simply do not consider them important enough.
- PIM eligible group membership – this one I do consider important enough, however the corresponding Graph API endpoints currently have some issues and the workaround requires iterating over all PIM provisioned groups… which is something I want to avoid.
- Exchange mailbox-level permissions (Full access, send as, send on behalf of) – again important, but falls into the “avoid” category. Use dedicated scripts instead.
- Exchange folder-level permissions – as above, inefficient. Use dedicated scripts instead.
- Site/file level permissions – even more inefficient.
- Device ownership (and registered devices) – this one I’m not so sure about… it’s relatively easy to address – let me know if you consider it important!
- Dynamic groups – instead of outright skipping them, should we do something else?
- Access packages – lots of things can be done via Entitlement management, good suggestion for future improvements.
- Teams RSC permission grants – easy enough to get… just not sure if important enough to consider.
The above list reminds me of another point – we do not explicitly address group-based Directory role assignments. Such are not directly returned via the /memberOf query, but we can cover them via the PIM endpoints. As however we already remove the user from all groups, privileged ones included, this scenario should already be covered. Let me know if my logic is faulty on this!
While the Graph API does have some support for Exchange Online role assignments now, said functionality is only available under the /beta endpoints. Moreover, it only allows for management of direct role assignments, as it does not currently support management of Exchange Online Role groups. In other words, you cannot use the Graph API to remove a role that is made available to the user thanks to its membership to a Role Group, unless you want to remove the assignment completely, and cause all other members of the Role Group to lose access. For this reason, we stick to using the good old Exchange cmdlets instead.
The requirements for using Exchange Online’s InvokeCommand endpoint closely resemble those for accessing Exchange Online PowerShell via app-only authentication , albeit if you have already created an app registration to leverage the Graph API, you can skip some of the steps. Do make sure to assign the necessary permissions though: the Exchange.ManageAsApp role and either an Entra ID admin role or Exchange Online Role group with sufficient permissions to perform the removal operations. At minimum, access to the Remove-DisitrbutionGroupMember cmdlet is required. As the script can also be used to remove Exchange Online management role assignments, both the Remove-ManagementRoleAssignment and Remove-RoleGroupMember cmdlets might also be called.
The script assumes that you will be leveraging a single service principal for performing both the Graph API and Exchange Online REST API operations. This is not a hard requirement, though it simplifies the connectivity block a bit. As an added benefit, using a single service principal can relax the permission requirements a bit, at least when using Entra ID roles. On that note, be warned that the script does not validate the access token(s) for the presence of the relevant permissions. Which means that the removal operation will be tried regardless, and will fail if permissions have not been granted. The script has some error handling that should detect such scenarios and terminate any further processing, but I’m sure there are many corner cases that it does not account for.
One more note on permissions. As we are leveraging the application permissions model, assigning an Entra ID role to the service principal enables our app to run queries against the Graph API, without explicitly granting consent to say Directory.Read.All . For example, while testing the script I had the Exchange administrator role assigned to the SP, which allowed him to remove Microsoft 365 Group members and owners without any additional grants. In production scenarios however you should be following the principle of least privilege, so consider using (custom) Role groups instead.
Another thing to mention here is that the script leverages the client credentials flow to obtain an access token, in other words requires you to enter a client secret value. DO NOT use this approach in your own solution! Make sure to replace the connectivity bits with your own preferred method instead. At the very least, do not store any credentials in plain text. Better, use a certificate to obtain the access token. And never trust a piece of code you’ve downloaded from the Internet 🙂
As always, do let me know if you find the script useful, any issues you run into and send me any potential improvement suggestions.
1 thought on “ Remove user from all Microsoft 365 groups and roles (and more) via the Graph API (non-interactive) ”
- Pingback: Microsoft Roadmap, messagecenter en blogs updates van 26-04-2024 - KbWorks - SharePoint & Teams Specialist
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Removing Unknown Azure RBAC Role Assignments with PowerShell
5 minute read
Ever wondered how to programmatically find and remove Azure RBAC role assignments of ‘Unknown’ ObjectType, at scale, in your Azure subscription?
In this blog I’ll describe the problem using an example scenario and then show you a scripted solution using PowerShell.
Unknown Role Assignments with Identity Not Found
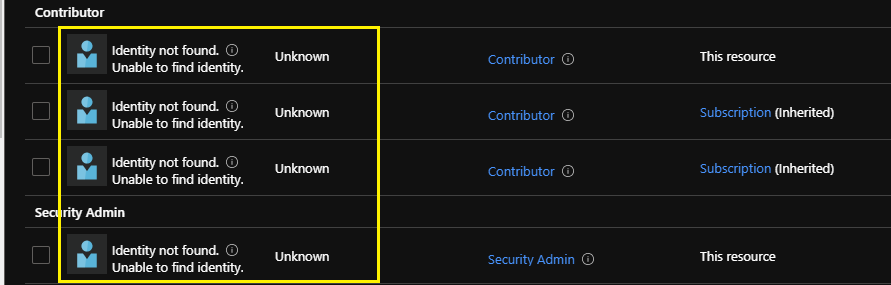
Looking at Access Control (IAM) role assignments within the Azure portal, you might’ve noticed that a security principal is listed as “Identity not found” with an “Unknown” type.
There’s 2 possible reasons this can occur:
- You recently invited a user when creating a role assignment
- You deleted a security principal that had a role assignment
Note - a security principal can be a:
- Service Principal
- Managed Identity
Example Scenario of How This Can Occur
Let’s examine an example scenario for the 2nd possible reason listed above: You deleted a security principal that had a role assignment.
Imagine you’re testing Azure policy definitions using ‘deployIfNotExists’ or ‘modify’ effects - a managed identity needs to be created because that’s how Azure policy has the required permissions to action those effects specified in your policy definitions.
In the screenshot below you can see a managed identity will be created automatically as part of the task to assign a policy initiative. So far, so good!
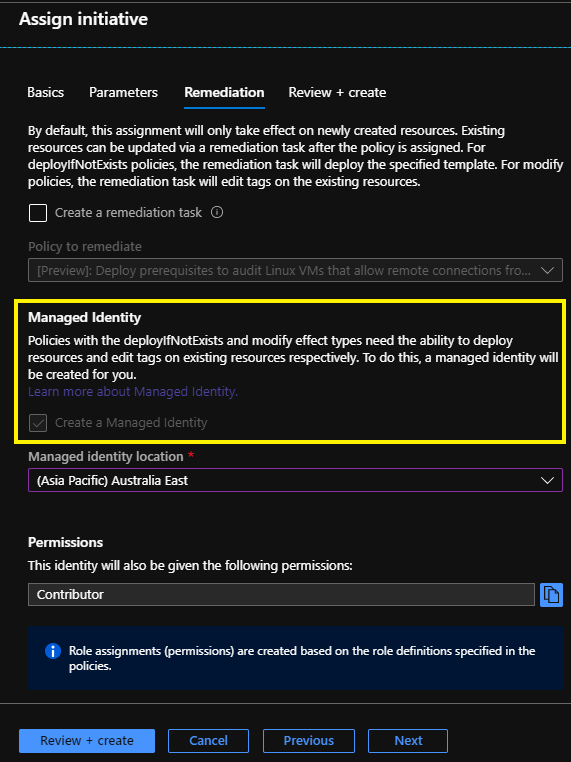
Now this new managed identity will also have a corresponding RBAC role assignment created on the scope defined by the policy assignment.
So if you are assigning your policy to the subscription scope a role assignment will be applied at the subscription level.
If, later on, you delete that policy assignment the managed identity will also automatically get deleted, which makes sense, because you might not need that managed identity ever again - but wait, for some reason the RBAC role assignment still exists for the deleted managed identity.
This leaves you with a security principal on the Access Control (IAM) role assignments page that displays as “Identity not found” with an “Unknown” type. Not harmful, I think, but also not a clean/tidy experience to encounter.
My hope is that Microsoft identify this as a problem and resolve it - so I’ve reached out to the Azure Policy Program Managers via Twitter…
TIL - via testing #AzurePolicy Assignments using DeployIfNotExists/Modify effects - a Managed Identity is created. If I delete the #AzurePolicy Assignment the Managed Identity is also deleted - BUT the RBAC Role Assignment still exists for the Managed Identity. Oops :) — Jesse Loudon (@coder_au) May 18, 2020
Finding Role Assignments of ‘Unknown’ ObjectType with PowerShell
There’s no current method I know of to easily find and remove these ‘Unknown’ type role assignments via the Azure Portal without doing a bunch of clicking.
So to programmatically discover Azure RBAC role assignments of the ‘Unknown’ type we can use the Get-AzRoleAssignment cmdlet:
Above you can see we are searching on the ObjectType field matching the value ‘Unknown’.
An example output of the above cmdlet is shown below.
You may have noticed above that the values for DisplayName and SignInName are null (empty) and that ObjectType equals ‘Unknown’. This is clear indication that you’ve found a role assignment where the corresponding security principal has either been deleted, or a security principal has been invited (while the role assignment was created) and has not yet replicated across regions.
Removing Role Assignments of ‘Unknown’ ObjectType with PowerShell
To programmatically remove Azure RBAC role assignments of the ‘Unknown’ type we can use the Remove-AzRoleAssignment cmdlet.
Please note:
- When removing a role assignment you’ll need to specify the ObjectID, RoleDefinitionName and Scope
- You’ll also need Microsoft.Authorization/roleAssignments/delete permissions, such as User Access Administrator or Owner
- Always test your scripts in a development environment first before using in production.
The PowerShell script above does the following:
- Finds all Azure role assignments in the subscription where ObjectType equals ‘Unknown’
- Exports the results to CSV where you can review/send off for ITSM approvals, etc
- Imports the results from CSV and sets variables for the required fields needed to remove a role assignment (ObjectID, RoleDefinitionName and Scope)
- Uses a for each loop to remove each role assignment specified from the imported CSV
For the simplest removal script without any authentication or CSV export/import for documentation purposes, you can use the following PowerShell script:
Closing Remarks
Finding and removing Azure RBAC role assignments might not be a common occurence for your team but I think it’s important to share with the community how to complete a task like this programmatically.
I came across this problem during my testing of Azure policy assignments, which use a managed identity for certain effects, and would’ve never thought to look for these role assignments otherwise.
If you don’t look, you’ll never find :)
Leave a comment
You may also enjoy.

Flexing your Security Governance with Azure Policy as Code
3 minute read
I recently had the pleasure of presenting a livestream session via Microsoft Reactor Sydney on a subject close to my heart.

Talking Azure Policy as Code on CtrlAltAzure podcast
4 minute read
Appearing as a guest on the Ctrl+Alt+Azure podcast to talk Azure Policy as Code with hosts Tobias Zimmergren and Jussi Roine

How to Win vs Azure Policy Non-Compliance
Fixing a design flaw with the existenceCondition for builtin policies
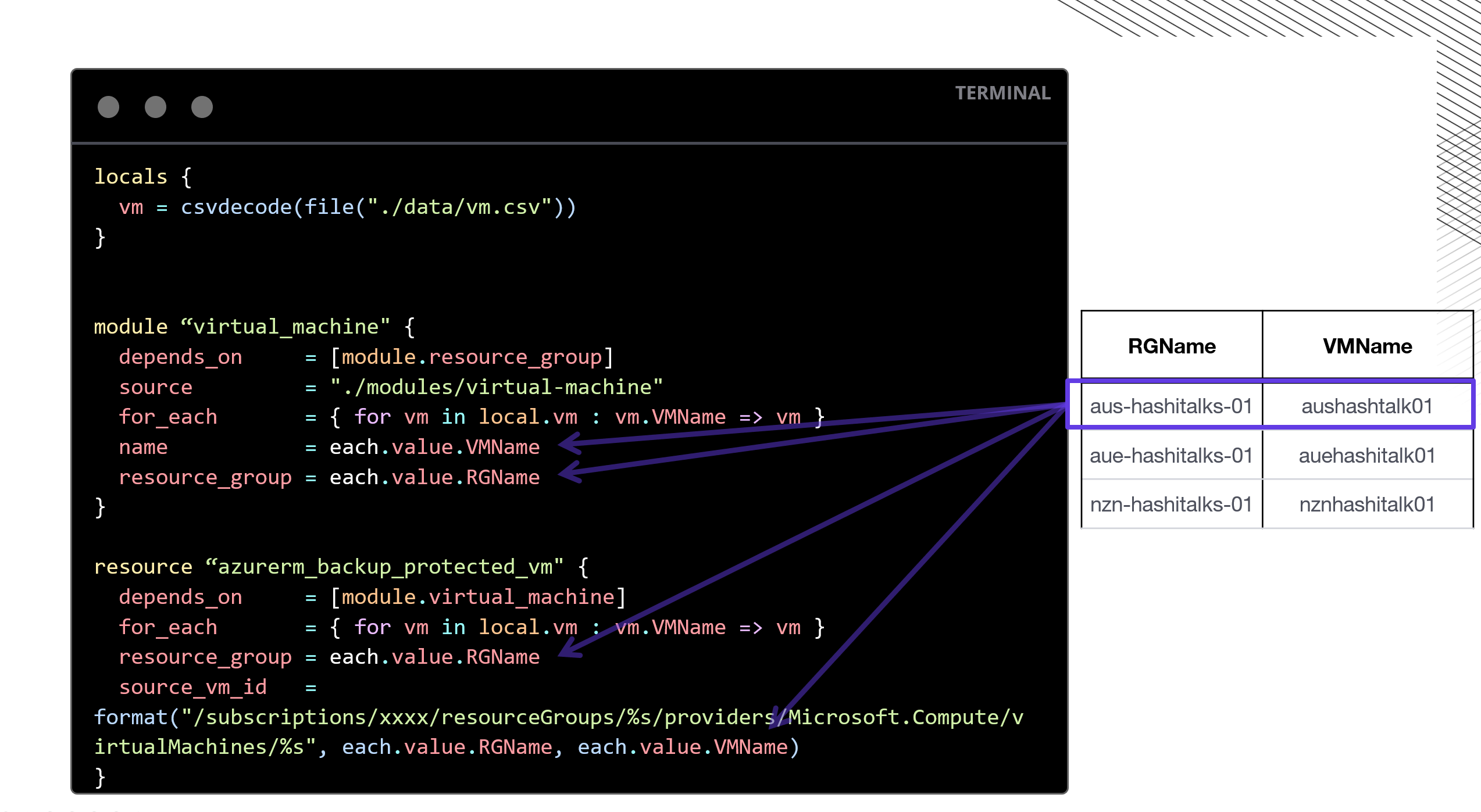
HashiTalks ANZ: DRY Coding with Terraform, CSVs, ForEach
How combining Terraform with CSVs and ForEach we can deploy at scale from large datasets

- Adding or removing role assignments using Azure Portal
Go back to AZ-304 Tutorials
In this article you will learn about assigning roles using Azure portal and the process of adding and removing role assignments.
However, Azure’s role-based access control (RBAC) refers to the authorization system for managing access to Azure resources. And, to grant access, you assign roles to users, groups, service principals, or managed identities at a particular scope.
Prerequisites
For adding or removing role assignments, you must have:
- Firstly, Microsoft.Authorization/roleAssignments/write
- Secondly, Microsoft.Authorization/roleAssignments/delete permissions, such as User Access Administrator or Owner
Access control (IAM)
Access control (IAM) is the page that is for assigning roles to grant access to Azure resources. It’s also known as identity and access management and appears in several locations in the Azure portal. There are questions for assigning roles to help in understanding about the Access control (IAM) page.
- Who needs access? This refers to a user, group, service principal, or managed identity.
- What role do they need? Permissions are grouped together into roles, so you can select from a list of several built-in roles orcan use custom roles.
- Where do they need access? This refers to the set of resources that the access applies to. However, “where” can be a management group, subscription, resource group, or a single resource such as a storage account.
Adding a role assignment
- Firstly, in the Azure portal, click All services and then select the scope that you want to grant access to.
- Secondly, click the specific resource for that scope.
- Then, Click Access control (IAM).
- Fourthly, click the Role assignments tab for viewing the role assignments at this scope.
- After that, click Add > Add role assignment. However, if you don’t have permissions to assign roles, the Add role assignment option will be disabled.
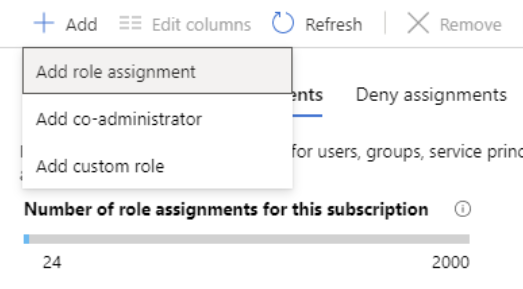
- Then, in the Role drop-down list, select a role such as Virtual Machine Contributor.
- There in the Select list, select a user, group, service principal, or managed identity. And, if you don’t see the security principal in the list, you can type in the Select box to search the directory for display names, email addresses, and object identifiers.
- Lastly, click Save to assign the role.

Assigning a user as an administrator of a subscription
For giving users the role of an administrator of an Azure subscription, first assign them the Owner role at the subscription scope. As the Owner role gives the user full access to all resources in the subscription, including the permission to grant access to others. However, these steps are the same as any other role assignment.
- Firstly, in the Azure portal, click All services and then Subscriptions.
- Then, click the subscription where you want to grant access.
- Thirdly, click Access control (IAM).
- After that, click the Role assignments tab to view the role assignments for this subscription.
- Then, click Add > Add role assignment. However, if you don’t have permissions to assign roles, the Add role assignment option will be disabled.
- And, in the Role drop-down list, select the Owner role.
- Then, in the Select list, select a user.

Adding a role assignment for a managed identity
For adding role assignments for a managed identity use the Access control (IAM) page. However, when you use the Access control (IAM) page, you start with the scope and then select the managed identity and role. In this section, you will learn about an alternate way to add role assignments for a managed identity. Using these steps, you start with the managed identity and then select the scope and role.
System-assigned managed identity
- Use these steps for assigning a role to a system-assigned managed identity by starting with the managed identity.
- Firstly, in the Azure portal, open a system-assigned managed identity. Then, in the left menu, click Identity.
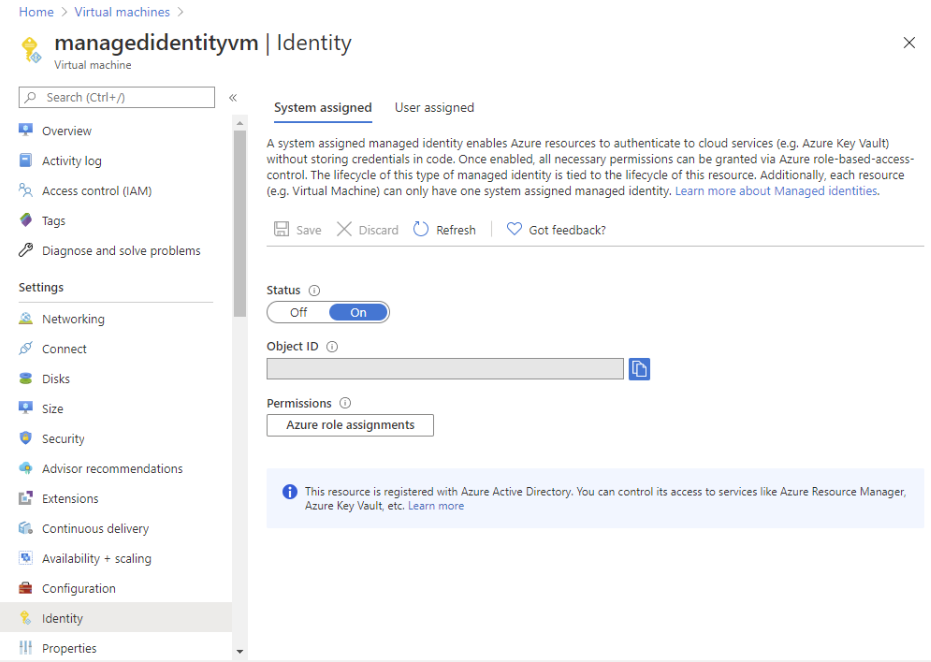
- After that, under Permissions, click Azure role assignments. However, if roles are already assigned to the selected system-assigned managed identity then you will see the list of role assignments.
- For changing the subscription, click the Subscription list. Then, click Add role assignment.
- Then, use the drop-down lists to select the set of resources that the role assignment applies to such as Subscription, Resource group, or resource. And, if you don’t have role assignment write permissions for the selected scope, an inline message will be displayed.
- After that, in the Role drop-down list, select a role such as Virtual Machine Contributor.
User-assigned managed identity
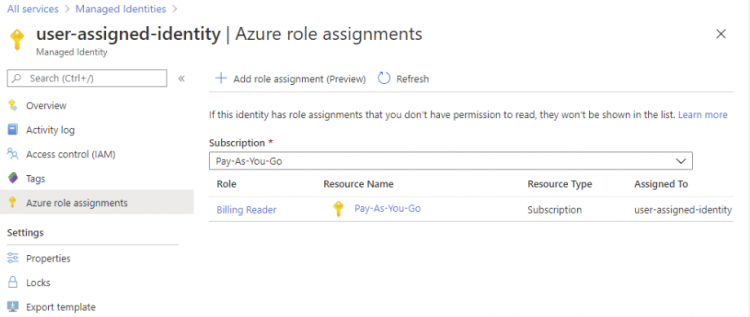
- Use these steps for assigning a role to a user-assigned managed identity by starting with the managed identity.
- Firstly, in the Azure portal, open a user-assigned managed identity. Then, in the left menu, click Identity.
- After that, under Permissions, click Azure role assignments. However, if roles are already assigned to the selected user-assigned managed identity then you will see the list of role assignments.
Removing a role assignment
In Azure RBAC, for removing access from an Azure resource, you first remove a role assignment. Use these steps to remove a role assignment.
- Firstly, Open Access control (IAM) at a scope, such as management group, subscription, resource group, or resource, where you want to remove access.
- Then, click the Role assignments tab to view all the role assignments for this subscription.
- After that, in the list of role assignments, add a checkmark next to the security principal with the role assignment you want to remove.
- Then, Click Remove.
- Lastly, in the remove role assignment message that appears, click Yes.
However, if you see a message that inherited role assignments cannot be removed, then you are trying to remove a role assignment at a child scope. So, you should open Access control (IAM) at the scope where the role was assigned and try again.

Reference: Microsoft Documentation
Prepare for Assured Success
Stefanos Cloud
How to manage Microsoft 365 user role assignments and administrative units
- Role assignments
- Administrative Units
This article provides guidance on how to manage Microsoft 365 user role assignments and administrative units. The article is also available on my podcast and Youtube channel .
View this article as a how-to video on Youtube.
You need to manage existing user roles, create new custom user roles and assign users and groups to existing roles in Microsoft 365 . You need to also manage Microsoft 365 administrative units.
In this how-to article, we will show you how to manage Microsoft 365 user role assignments and administrative units.
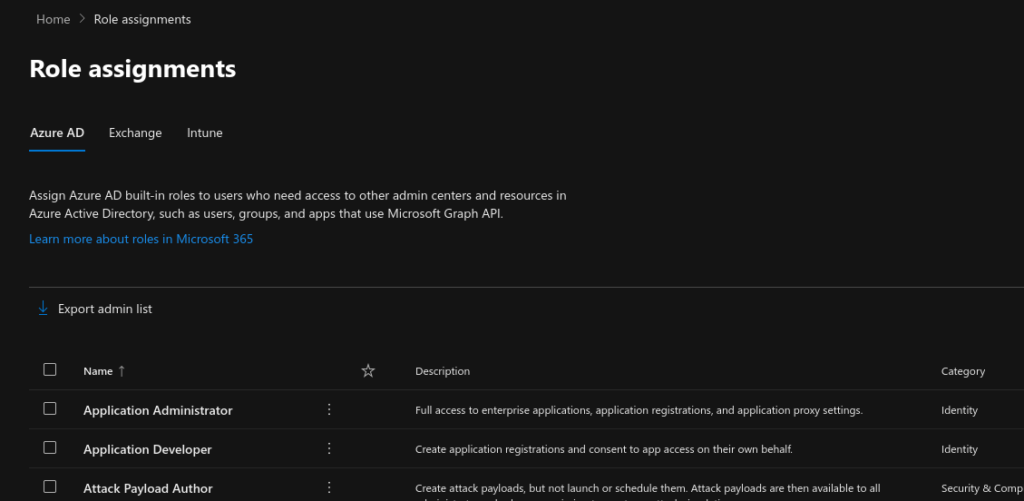
Role assignments #
From within the Microsoft 365 Admin Center portal, you can assign Azure AD built-in roles to users who need access to other admin centers and resources in Azure Active Directory, such as users, groups, and apps which use Microsoft Graph API. The following groups of user role assignments can be made from the Admin Center portal.
- Azure AD role assignments
- Exchange Online role assignments
- Intune role assignments
In the next steps, we will show you how to assign the Global Administrator Azure AD role to a user and group. Follow the steps below to assign the Global Administrator role to a user or group.
- Navigate to https://admin.microsoft.com and authenticate as a global admin user.
- On the left pane, expand the "Roles" section and click on "Role assignments". On the main section click on the "Global Administrator" role. On the popup form on the right, you should be able to review the general properties of the role in question. On the permissions tab, the system lists details of the permissions which are assigned with the role in question.
- On the "Assigned" tab, you can assign users or groups to the role in question. Click on "Add Users" and then "Add Groups" to add a user and group respectively to the specific role.
- To run the Azure portal as a specific Azure AD user role, tick on the checkbox next to the role and click "Run As". This will show you the view of the Azure portal as if you had logged in via a user with the role in question.
- To compare permissions of user roles, tick on two or more roles and then click on "Compare Roles". In the next screen, you should see a tabular comparison of the permissions assigned to each of the compared roles. You can also click on "Export comparison" to export the comparison matrix of the selected roles.
In the next steps, we will show you how to assign the Organization Management Exchange Online role to a user and group, as well as how to create a new custom Exchange Online role. Follow the steps below.
- Navigate to the "Exchange" tab under the "Role Assignments" section.
- Click on the "Organization Management" role. On the popup form on the right, you can review the general settings of the role under the "general" tab. Under the "Permissions" tab, you can review in detail the available permissions of the role in question.
- Under the "Assigned" tab, you can assign a user or group to the role in question. Click "Add" and choose the user or group to assign to the role.
- You can also create a custom Exchange Online role by ticking the checkbox next to the role which will be used as the template for the new role. Then click on "Copy role group". This will take you to a wizard to create your new custom role. On the "Set up the basics" page, fill-in the name, description and write scope of the new role and click Next.
- Select the roles to add to the new custom role group. Roles define the scope of the tasks that the members assigned to this role group have permission to manage.
- Select the users to assign to this role group. They'll have permissions to manage the roles that you assigned in the previous step.
- Review your selections and click Finish.
In the next steps, we will show you how to assign Intune roles. Assign Intune roles to specialists who need to view or manage Intune data, devices, or services. These roles can only be assigned to users who have a license that includes Intune. Follow the steps below.
- Under the "Role assignments" section, navigate to the "Intune" tab. If you need to export existing assignments, click on the "Export assignments" button.
- Click on the Intune role you wish to edit assignments of. On the "General tab" you can review the general settings of the role in question. On the "Permissions" tab you can see in detail all permissions of the role in question.
- To assign users to the Intune role, under the "Assigned" tab click on "Add". This will take you to the "Set up the basics" wizard. Fill-in a name and description and click Next.
- Select the security groups that contain the users you want to become admins for the role. Click Next.
- Select a built-in security group like 'All users', or search for and select security groups which contain the users and devices that the Intune role can manage.
- You can optionally add tabs which limit the specific Intune policies, apps and devices that the admins can see. Click "Next".
- Review all your assignment settings and click "Finish".
Administrative Units #
Now we will move on to show you how to create and manage Microsoft 365 Administrative Units. Units let you sub-divide your organization into any unit that you want, and then assign specific administrators that can only manage that unit. For example, you can assign the Helpdesk Administrator role to a regional support specialist, so they can manage users only in that region.
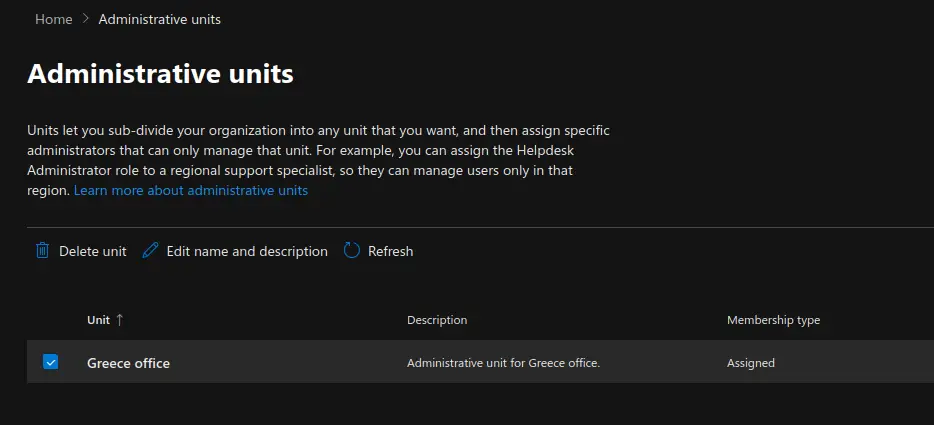
Carry out the following steps:
- Under the "Roles" section, click on "Administrative Units". Click on "Add Unit" to add a new administrative unit.
- Provide a name and Description of the new administrative unit and click "Next". Administrative units let you limit admins to manage users for a specific department, region, or any segment that your organization defines. Start by giving the administrative unit a name and description that will let other admins know its purpose.
- Choose "Add up to 20 users and groups" or "Upload users" if you need to bulk upload a large number of users to be linked to the new administrative unit. If you choose "Add up to 20 users and groups", then click on "Add Users" or "Add Groups" to add the desired users to the administrative unit and click Next. The administrators assigned to this unit will manage the settings for these users and groups. Adding groups doesn't add users to the unit, it lets the assigned admins manage group settings. You can only add up to 20 members individually or you can bulk upload up to 200 users. If you need to add more, you can edit this unit to add them.
- Assign admins to scoped roles. The following roles are the only roles that support administrative units. Authentication Administrator Cloud Device Administrator Groups Administrator Helpdesk Administrator License Administrator Password Administrator SharePoint Administrator Teams Administrator Teams Device Administrator User Administrator.
Select a role and then assign admins to it. The admins that you assign to roles in this step will manage the members of this administrative unit.
- Review your selections and click "Finish". The new administrative unit has been created. You can always edit its properties by clicking on the Administrative Unit name. From that page you can edit the administrative unit's members and role assignments.
- You can also edit the name and description of an administrative unit by ticking the checkbox next to the administrative unit name and clicking on "Edit name and description".
What are your Feelings
Share this article :, how can we help.
Powered by BetterDocs
How to Remove Users Assigned to a Role in Role Management
Searching for the user.
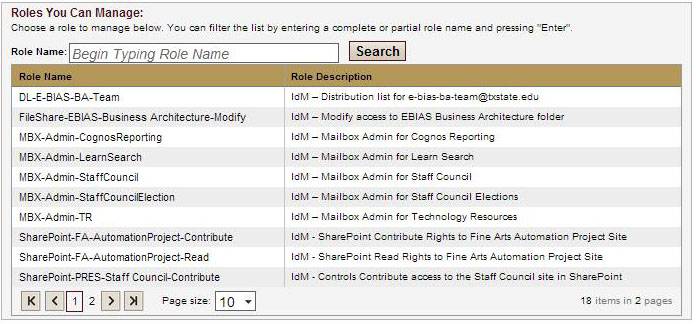
- Role Information - basic information about the User, including: Role Name, Role Description, Max Duration, Role Can be Delegated
- Users Already Assigned to Role - if the there already are users assigned to the role, you can modify the roles by first clicking on the Select box, and then clicking on Continue at the bottom of the page.
Removing the Role from the User
- To remove a user role check the Select boxes for the role or roles you wish to select in the Roles You Can Assign . After the Roles are selected, click Continue .
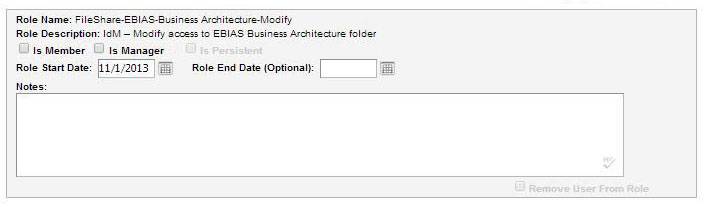
- Click Continue to save the changes.
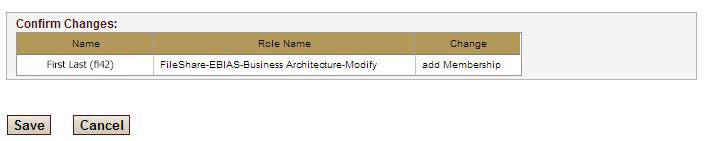
Confirming Changes
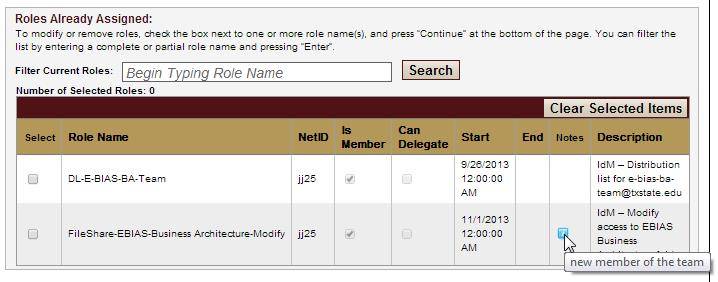
NOTE: Hovering over the icon in Notes will show the text entered in the notes section.
more support
- Working with EPM Automate for Oracle Enterprise Performance Management Cloud
- Command Reference
- EPM Automate Commands
unassignRole
Removes a role currently assigned to the users, including the user who runs this command, whose login IDs are included in the ANSI or UTF-8 encoded CSV file that is used with this command. You can use this command to remove the assignment of a predefined role or an application role.
The CSV file format is as follows:
Use the uploadFile command to upload the file to the environment.
When the command execution finishes, EPM Automate prints information about each failed entry to the console. Review this information to understand why the command execution failed for some entries in the CSV file.
Required Roles
To remove predefined role assignments:
- Classic environments: Identity Domain Administrator and any predefined role ( Service Administrator , Power User , User or Viewer )
- OCI environments: Service Administrator , or Identity Domain Administrator and any predefined role ( Service Administrator , Power User , User , or Viewer )
To remove application role assignments: Service Administrator or Access Control Manager
User Login values are not case-sensitive. For example, [email protected] is treated as being identical to [email protected] or any variation in its case.
- If you are removing the assignment of users to predefined roles, ROLE should identify a predefined role applicable to the service. See Understanding Predefined Roles in Getting Started with Oracle Enterprise Performance Management Cloud for Administrators .
If you are removing the assignment of users to application roles, ROLE should identify a role belonging to the application in the current environment. Application roles are listed in the Roles tab of Access Control . For a description of application roles for each business process, see these topics in Administering Access Control for Oracle Enterprise Performance Management Cloud :
- Account Reconciliation
- Enterprise Profitability and Cost Management
- Planning, FreeForm, Financial Consolidation and Close, and Tax Reporting
- Profitability and Cost Management
- Oracle Enterprise Data Management
- Narrative Reporting
epmautomate unassignRole remove_roles.csv "Service Administrator"
epmautomate unassignRole example_file.csv "Task List Access Manager"
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
New-Management Role Assignment
This cmdlet is available in on-premises Exchange and in the cloud-based service. Some parameters and settings may be exclusive to one environment or the other.
Use the New-ManagementRoleAssignment cmdlet to assign a management role to a management role group, management role assignment policy, user, or universal security group (USG).
For information about the parameter sets in the Syntax section below, see Exchange cmdlet syntax .
Description
When you add a new role assignment, you can specify a built-in or custom role that was created using the New-ManagementRole cmdlet and specify an organizational unit (OU) or predefined or custom management scope to restrict the assignment.
You can create custom management scopes using the New-ManagementScope cmdlet and can view a list of existing scopes using the Get-ManagementScope cmdlet. If you choose not to specify an OU, or predefined or custom scope, the implicit write scope of the role applies to the role assignment.
For more information about management role assignments, see Understanding management role assignments .
You need to be assigned permissions before you can run this cmdlet. Although this topic lists all parameters for the cmdlet, you may not have access to some parameters if they're not included in the permissions assigned to you. To find the permissions required to run any cmdlet or parameter in your organization, see Find the permissions required to run any Exchange cmdlet .
This example assigns the Mail Recipients role to the Tier 2 Help Desk role group.
This example assigns the MyVoiceMail role to the "Sales end-users" role assignment policy. First, the IsEndUserRole property on the MyVoiceMail role is verified to be sure it's set to $true, indicating it's an end-user role.
After the role has been verified to be an end-user role, the role is assigned to the "Sales end-users" role assignment policy.
This example assigns the Eng Help Desk role to the Eng HD Personnel role group. The assignment restricts the recipient write scope of the role to the contoso.com/Engineering/Users OU. Users who are members of the Eng HD Personnel role group can only create, modify, or remove objects contained within that OU.
This example assigns the Distribution Groups role to the North America Exec Assistants role group. The assignment restricts the recipient write scope of the role to the scope specified in the North America Recipients custom recipient management scope. Users who are members of the North America Exec Assistants role group can only create, modify, or remove distribution group objects that match the specified custom recipient management scope.
This example assigns the Exchange Servers role to John. Because John should only manage the servers running Exchange located in Sydney, the role assignment restricts the configuration write scope of the role to the scope specified in the Sydney Servers custom configuration role group. John can only manage servers that match the specified custom configuration management scope.
This example assigns the Mail Recipients role to the Executive Administrators role group. The assignment restricts the recipient write scope of the role to the scope specified in the Exclusive-Executive Recipients exclusive recipient management scope. Because the Exclusive-Executive Recipients scope is an exclusive scope, only users of the Executive Administrators can manage the executive recipients that match the exclusive recipient scope. No other users, unless they're also assigned an assignment that uses an exclusive scope that matches the same users, can modify the executive recipients.
This example assigns the Mail Recipients role to the Contoso Sub - Seattle role group. The administrators in this role group should only be allowed to create and manage mail recipients in specific databases that have been allocated for use by the Contoso subsidiary, A. Datum Corporation (adatum.com). Also, this group of administrators should only be allowed to manage the Contoso employees located in the Seattle office. This is done by creating a role assignment with both a database scope, to limit management of mail recipients to only the databases in the database scope and a recipient OU scope, to limit access to only the recipient objects within the Contoso Seattle OU.
This parameter is available only in the cloud-based service.
The App parameter specifies the service principal to assign the management role to. Specifically, the ObjectId GUID value from the output of the Get-ServicePrincipal cmdlet (for example, 6233fba6-0198-4277-892f-9275bf728bcc).
For more information about service principals, see Application and service principal objects in Microsoft Entra ID .
You can't use this parameter with the SecurityGroup, Policy, or User cmdlets.
This parameter is available only in on-premises Exchange.
The Computer parameter specifies the name of the computer to assign the management role to.
You can't use this parameter with the SecurityGroup, User, or Policy parameters.
The Confirm switch specifies whether to show or hide the confirmation prompt. How this switch affects the cmdlet depends on if the cmdlet requires confirmation before proceeding.
- Destructive cmdlets (for example, Remove-* cmdlets) have a built-in pause that forces you to acknowledge the command before proceeding. For these cmdlets, you can skip the confirmation prompt by using this exact syntax: -Confirm:$false .
- Most other cmdlets (for example, New-* and Set-* cmdlets) don't have a built-in pause. For these cmdlets, specifying the Confirm switch without a value introduces a pause that forces you acknowledge the command before proceeding.
-CustomConfigWriteScope
The CustomConfigWriteScope parameter specifies the existing configuration scope to associate with this management role assignment. If you use the CustomConfigWriteScope parameter you can't use the ExclusiveConfigWriteScope parameter. If the management scope name contains spaces, enclose the name in quotation marks (").
-CustomRecipientWriteScope
The CustomRecipientWriteScope parameter specifies the existing recipient-based management scope to associate with this management role assignment. If the management scope name contains spaces, enclose the name in quotation marks ("). If you use the CustomRecipientWriteScope parameter, you can't use the RecipientOrganizationalUnitScope or ExclusiveRecipientWriteScope parameters.
-CustomResourceScope
The CustomResourceScope parameter specifies the custom management scope to associate with this management role assignment. You can use any value that uniquely identifies the management scope. For example:
- Distinguished name (DN)
If the value contains spaces, enclose the value in quotation marks (").
You use this parameter with the App parameter to assign permissions to service principals. For more information, see For more information about service principals, see Application and service principal objects in Microsoft Entra ID .
-Delegating
The Delegating switch specifies whether the user or USG assigned to the role can delegate the role to other users or groups. You don't need to specify a value with this switch.
-DomainController
The DomainController parameter specifies the domain controller that's used by this cmdlet to read data from or write data to Active Directory. You identify the domain controller by its fully qualified domain name (FQDN). For example, dc01.contoso.com.
-ExclusiveConfigWriteScope
The ExclusiveConfigWriteScope parameter specifies the exclusive configuration-based management scope to associate with the new role assignment. If you use the ExclusiveConfigWriteScope parameter, you can't use the CustomConfigWriteScope parameter. If the scope name contains spaces, enclose the name in quotation marks (").
-ExclusiveRecipientWriteScope
The ExclusiveRecipientWriteScope parameter specifies the exclusive recipient-based management scope to associate with the new role assignment. If you use the ExclusiveRecipientWriteScope parameter, you can't use the CustomRecipientWriteScope or RecipientOrganizationalUnitScope parameters. If the scope name contains spaces, enclose the name in quotation marks (").
The Force switch hides warning or confirmation messages. You don't need to specify a value with this switch.
You can use this switch to run tasks programmatically where prompting for administrative input is inappropriate.
The Name parameter specifies a name for the new management role assignment. The maximum length of the name is 64 characters. If the management role assignment name contains spaces, enclose the name in quotation marks ("). If you don't specify a name, one will be created automatically.
The Policy parameter specifies the name of the management role assignment policy to assign the management role to. If the value contains spaces, enclose the value in quotation marks (").
The IsEndUserRole property of the role you specify using the Role parameter must be set to $true.
You can't use this parameter with the App, SecurityGroup, Computer, or User parameters.
-RecipientAdministrativeUnitScope
This parameter is functional only in the cloud-based service.
The RecipientAdministrativeUnitScope parameter specifies the administrative unit to scope the new role assignment to.
Administrative units are Microsoft Entra containers of resources. You can view the available administrative units by using the Get-AdministrativeUnit cmdlet.
-RecipientGroupScope
The RecipientGroupScope parameter specifies a group to consider for scoping the role assignment. Individual members of the specified group (not nested groups) are considered as in scope for the assignment. You can use any value that uniquely identifies the group: Name, DistinguishedName, GUID, or DisplayName.
-RecipientOrganizationalUnitScope
The RecipientOrganizationalUnitScope parameter specifies the OU to scope the new role assignment to. If you use the RecipientOrganizationalUnitScope parameter, you can't use the CustomRecipientWriteScope or ExclusiveRecipientWriteScope parameters. To specify an OU, use the syntax: domain/ou. If the OU name contains spaces, enclose the domain and OU in quotation marks (").
-RecipientRelativeWriteScope
The RecipientRelativeWriteScope parameter specifies the type of restriction to apply to a recipient scope. The available types are None, Organization, MyGAL, Self, and MyDistributionGroups. The RecipientRelativeWriteScope parameter is automatically set when the CustomRecipientWriteScope or RecipientOrganizationalUnitScope parameters are used.
Even though the NotApplicable, OU, MyDirectReports, CustomRecipientScope, MyExecutive, MailboxICanDelegate and ExclusiveRecipientScope values appear in the syntax block for this parameter, they can't be used directly on the command line. They are used internally by the cmdlet.
The Role parameter specifies the existing role to assign. You can use any value that uniquely identifies the role. For example:
If you use the App parameter, you can't specify admin or user roles; you can only specify application roles (for example, "Application Mail.Read").
-SecurityGroup
The SecurityGroup parameter specifies the name of the management role group or mail-enabled universal security group to assign the management role to. If the value contains spaces, enclose the value in quotation marks (").
You can't use this parameter with the App, Policy, Computer, or User parameters.
-UnScopedTopLevel
By default, this parameter is available only in the UnScoped Role Management role, and that role isn't assigned to any role groups. To use this parameter, you need to add the UnScoped Role Management role to a role group (for example, to the Organization Management role group). For more information, see Add a role to a role group .
The UnScopedTopLevel switch specifies that the role provided with the Role parameter is an unscoped top-level management role. You don't need to specify a value with this switch.
Unscoped top-level management roles can only contain custom scripts or non-Exchange cmdlets. For more information, see Create an unscoped role .
The User parameter specifies the user to assign the management role to.
For the best results, we recommend using the following values:
- UPN: For example, [email protected] (users only).
- Domain\SamAccountName: For example, contoso\user .
You can't use this parameter with the App, SecurityGroup, Computer, or Policy parameters.
The WhatIf switch simulates the actions of the command. You can use this switch to view the changes that would occur without actually applying those changes. You don't need to specify a value with this switch.
Input types
To see the input types that this cmdlet accepts, see Cmdlet Input and Output Types . If the Input Type field for a cmdlet is blank, the cmdlet doesn't accept input data.
Output types
To see the return types, which are also known as output types, that this cmdlet accepts, see Cmdlet Input and Output Types . If the Output Type field is blank, the cmdlet doesn't return data.
Was this page helpful?
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources

IMAGES
VIDEO
COMMENTS
When you remove a role assignment, the management role group, management role assignment, user, or universal security group (USG) that was assigned the associated role can no longer access the cmdlets or parameters made available by the role. For more information about management role assignments, see Understanding management role assignments. You need to be assigned permissions before you can ...
Open Access control (IAM) at a scope, such as management group, subscription, resource group, or resource, where you want to remove access.. Click the Role assignments tab to view all the role assignments at this scope.. In the list of role assignments, add a checkmark next to the security principal with the role assignment you want to remove. Click Remove.
Remove a management role assignment. If you know the name of the role assignment you want to remove, use the following syntax. PowerShell. Copy. Remove-ManagementRoleAssignment <assignment name>. For example, to remove the "Tier 2 Help Desk Assignment" role assignment, use the following command. PowerShell. Copy.
The Identity parameter specifies the name is the role assignment to remove. If who role assignment name contains spaces, enclose the name in quotation marks ("). The Verify switch causes the command the pause processing and requires him to acknowledge what the command will do before processing continues.
6. The role assignment can be removed as you would remove role assignments to other principal types. In the Portal, navigate to the scope where the role assignment was created, and use the Access Control (IAM) menu to find and remove the assignment. Azure CLI or PowerShell could also be used. It takes A LONG time to show up in the portal.
Remove Management Role Creating Management Roles can help tailor the way Exchange is used in a particular environment. One thing that ... Each of these roles can be assigned directly to a user or a user could be assigned a Management Role that includes Chapter 14: Permissions and Compliance.
Learn how to manage Azure Role assignments using PowerShell snippets and simple commandlets. Discover examples for listing all role assignments, adding and removing assignments for users or service principals, creating custom roles, and more. Plus, check out a script that combines some of these examples into a single function. Written by Vukasin Terzic.
What is Role Assignment Hygiene. Azure Role Assignment Hygiene refers to the practice of regularly reviewing and cleaning up Azure role assignments. This includes removing orphaned permissions, i.e., permissions that are no longer in use or are associated with non-existent users or groups. We are also going one step further and remove ...
A PowerShell script to remove user, or a set of users, from all groups they are a member of by using the Graph API methods. You can leverage the additional parameters of the script in order to also remove any directory role assignments, ownership assignments and delegate permission grants. The script supports Microsoft 365 Groups, Entra Security Groups, Exchange Distribution Groups and Mail ...
Syntax Remove-Management Role [-Identity] <RoleIdParameter> [-Confirm] [-DomainController <Fqdn>] [-Force] [-Recurse] [-UnScopedTopLevel] [-WhatIf] [<CommonParameters>] Description. You need to remove all the management role assignments from a role before you delete it. If the role is the parent of child roles, the child roles must be removed before you remove the parent role, or you must use ...
Jesse Loudon • 2 years ago. Hey there, thanks for the heads up, I just tested this end to end and found. 1 - An orphaned role assignment still shows ObjectType as 'Unknown'. 2 - Running the PowerShell script shown in this article still works to cleanup/remove these orphaned role assignments. Cheers.
Adding a role assignment. Firstly, in the Azure portal, click All services and then select the scope that you want to grant access to. Secondly, click the specific resource for that scope. Then, Click Access control (IAM). Fourthly, click the Role assignments tab for viewing the role assignments at this scope.
Root inherited user removal from Azure using following 3 CLI methods. You can use the az role assignment delete command to delete a role assignment at the root level. For example, to remove the Owner role from a user with the email address [email protected], you can run this command: az role assignment delete — assignee [email protected] ...
Follow the steps below to assign the Global Administrator role to a user or group. Navigate to https://admin.microsoft.com and authenticate as a global admin user. On the left pane, expand the "Roles" section and click on "Role assignments". On the main section click on the "Global Administrator" role.
With the use of the JSON payload that is sent to the Function, a PowerShell script is executed to remove the unauthorized Role Assignment. To do so, the Function App uses a System-assigned Managed Identity that has the permissions to remove Role Assignments. With the solution overview out of the way, let's have a look at how the solution ...
A management role assignment, which is part of the Role Based Access Control (RBAC) permissions model in Microsoft Exchange Server 2013, is the link between a management role and a role assignee. A role assignee is a role group, role assignment policy, user, or universal security group (USG). A role must be assigned to a role assignee for it to ...
Removing the Role from the User. To remove a user role check the Select boxes for the role or roles you wish to select in the Roles You Can Assign.After the Roles are selected, click Continue.; In the Role Management Options window,Click the Remove User From Role button at the bottom right of the screen. Additionally, you can set the Start and End Date for the role.
unassignRole. Removes a role currently assigned to the users, including the user who runs this command, whose login IDs are included in the ANSI or UTF-8 encoded CSV file that is used with this command. You can use this command to remove the assignment of a predefined role or an application role. The CSV file format is as follows: User Login.
Assign a different role assignment policy to the mailboxes. The example uses the policy named Seattle End User. Remove all management role assignments that are assigned to the End User policy. Remove the End User role assignment policy. For more information about the Where cmdlet and pipelining, see Working with command output and About Pipelines.
Some parameters and settings may be exclusive to one environment or the other. Use the New-ManagementRoleAssignment cmdlet to assign a management role to a management role group, management role assignment policy, user, or universal security group (USG). For information about the parameter sets in the Syntax section below, see Exchange cmdlet ...
I have assigned all roles to a user, but this user is still unable to remove any role assignments for itself or other users in User Assigned Roles section. The 'Remove Assignments' tab is greyed out. What should I do to enable this 'Remove assignments' tab? You can click the link below to see the screenshot. image: screenshot
The role assignments where the user has been removed remain as Identity not found. The az role assignment list does not return displayName to filter it out that way. Ex: "canDelegate"...