If you're seeing this message, it means we're having trouble loading external resources on our website.
If you're behind a web filter, please make sure that the domains *.kastatic.org and *.kasandbox.org are unblocked.
To log in and use all the features of Khan Academy, please enable JavaScript in your browser.

Computers and the Internet
Course: computers and the internet > unit 3, computer networks.
- Wires, cables, and WiFi
- Physical network connections
- Bit rate, bandwidth, and latency
- Bit rate and bandwidth
Building a network
- The ring topology looks like a circle of connected devices, where each device is connected to two neighbors (one on either side).
- The mesh topology looks like a circle with lines inside it, showing that every device is connected to every other device.
- The star topology has a device at the center and then a connection between that center device and the other five devices.
- The bus topology shows a center line with connections coming off the line for each device. No device is directly connected to another device, but they are all connected via the central line.
- The tree topology starts with a single device at the top which branches to connect with two more devices. The left child device branches to connect with two more devices, while the right child only has one branch connecting it to a child device. There are three layers to the tree.
Types of networks
- (Choice A) DCN A DCN
- (Choice B) WAN B WAN
- (Choice C) LAN C LAN
Networking protocols
Want to join the conversation.
- Upvote Button navigates to signup page
- Downvote Button navigates to signup page
- Flag Button navigates to signup page


An Introduction to Computer Networks - Second Edition
(6 reviews)
Peter Lars Dordal, Loyola University of Chicago
Copyright Year: 2014
Last Update: 2020
Publisher: Peter L Dordal
Language: English
Formats Available
Conditions of use.
Learn more about reviews.
Reviewed by Stuart Anderson, Adjunct Instructor, Norfolk State University on 11/13/23
The textbook is complete and thorough. The index correctly points to the material in the chapters. read more
Comprehensiveness rating: 5 see less
The textbook is complete and thorough. The index correctly points to the material in the chapters.
Content Accuracy rating: 5
The information in the book is accurate as it applies to networking concepts.
Relevance/Longevity rating: 5
The book's content is current.
Clarity rating: 4
The material is clear however, it does make assumptions about the reader's level of current knowledge about the material.
Consistency rating: 5
The material is consistent and flows in a good order.
Modularity rating: 4
The is very good in how the information is broken down into specific modules. Some modules need more information to make them more complete.
Organization/Structure/Flow rating: 5
The information is organized in a fashion that allows future topics to build on the previous topics.
Interface rating: 5
There were no interface issues.
Grammatical Errors rating: 5
There are no grammatical errors.
Cultural Relevance rating: 5
The test is inclusive of all cultures.
This is a good textbook for networking information. Some of the material could be explained in more detail to make it more of an introductory topic. A reader with networking experience would find this book a good reference, however, a reader new to the networks might find some of the material a bit light. As a network engineer, I found the information thorough and would work well with other networking material.
Reviewed by Terri Devlin, Instructor, Aims Community College on 7/23/19
Even though the title of the text is "An Introduction to Networking", the author seems to assume that the student or reader knows a lot about the subject matter and terminology. Topics and some definitions are presented, however the author does a... read more
Comprehensiveness rating: 3 see less
Even though the title of the text is "An Introduction to Networking", the author seems to assume that the student or reader knows a lot about the subject matter and terminology. Topics and some definitions are presented, however the author does a deep dive into the topic area quickly. This text would not be beneficial to students seeking CompTia Network + Certification because many of the terms and concepts tested in the certification exam are not covered in this text.
The author presents the material in an unbiased manner. Errors were not identified
Relevance/Longevity rating: 2
Out-of-date information was identified. The text is written in a manner that updates could be made in a straightforward manner.
Clarity rating: 2
The text was difficult to read because precise definitions and content were not provided. Other textbooks and internet sources were used to look up definitions and refresh understanding of technical terms and concepts
Consistency rating: 4
The terminology, framework, and chapter exercises followed a consistent approach.
The layout of the book is easy to understand and follow.
Organization/Structure/Flow rating: 3
The topics were organized in a logical fashion. It was a challenge to determine the network “big picture” and how the components fit into the picture. The topics make sense to people familiar with Networks. This text would be challenging to people new to Computer Network concepts.
Interface rating: 3
The text is free of navigation problems. The figures and tables were easily identified. An improvement could be made with providing better images or pictures.
Grammatical Errors rating: 4
The text was free of grammatical errors.
The text is appropriate for globally-based students.
Many computer concept textbooks have associated software that helps student learn topics and practice. Computer Networks is an area where practice helps students learn. This text did not have associated software available.
Reviewed by Audrey Styer, Instructor, CIS/CPS, Morton College on 12/21/18
This textbook provides a very comprehensive and in-depth introduction to computer networking. read more
This textbook provides a very comprehensive and in-depth introduction to computer networking.
All information presented is accurate.
This textbook is continually being updated to accommodate the ever-changing nature of computer networking.
Clarity rating: 5
Material is presented in a clear manner, but does require a prior basic understanding of computer networking.
Consistency of presentation and methodology is maintained throughout the text.
Modularity rating: 5
The chapters are well defined by topic
The material is presented in a logical manner that helps learners develop their understanding.
The PDF version is easy to read and navigate. The linked Table of Contents and Index make finding and moving to specific topics simple.
I found no grammatical errors.
This is not applicable to this topic.
The callout boxes provide a visual break for readers and increase learning with interesting facts and supporting information. Unfortunately, this textbook is too advanced for my undergraduate learners and does not map to CompTIA’s Network+ certification.
Reviewed by Sunho Lim, Assistant Professor, Texas Tech University on 3/27/18
The text covers all five layers (phy, link, net, trans, and app) and their associated algorithms and communication protocols in the network, and provides an effective index and/or golssary. read more
The text covers all five layers (phy, link, net, trans, and app) and their associated algorithms and communication protocols in the network, and provides an effective index and/or golssary.
The content is accurate and unbiased.
Relevance/Longevity rating: 3
The most content is up-to-date and the text is written in a way to easily be updated. Since network technology is time-sensitive, some sections in the text should be updated.
The text is easy to read but some advanced sections (e.g., network simulator ns-2 and ns-3) would be challenging to read and understand technical terminology used.
The text is consistent in using terminology and framework.
The text is well divided into a set of sections. It is easy to selectively choose a section depending on the level of class or students.
Organization/Structure/Flow rating: 4
The topics in the text are presented in a bottom-up way, but grouping sections in terms of layer would be great.
The text has an interface issue, such as some contents are displayed out of page or cut off.
The text contains no grammatical errors.
Cultural Relevance rating: 1
The text is not related to any culture.
The text is appropriate to both undergraduate to graduate students. A set of selective chapters can be used depending on the instructor. The text is good to use for a reference book.
Reviewed by Lisa Bain, Professor, Rhode Island College on 2/1/18
The book covers all the major topics required for a computer networking course. read more
The book covers all the major topics required for a computer networking course.
Yes, this book is accurate in the major areas that the reviewer read. The entire text was not reviewed.
Relevance/Longevity rating: 4
Yes, the book is up-to-date with the major concepts that do not change (e.g. TCP, IP, UDP) and also includes the latest standards for Wi-Fi. However, some networking technologies will need to be updated as advancements are made (e.g. newer Wi-Fi standards).
Yes, the text is clearly written. However, the content is very technical and would be challenging for a non-technical person to understand all aspects. It is very straight-forward and appropriate for a technical audience.
Yes, the book is consistent and uses the same technical terminology throughout.
Yes the book is very modular and provides many small sections within each chapter for specific topics.
The flow of the book is similar to other networking books in that is starts with an introduction then provides additional details in following chapters.
The interface in PDF is easy to navigate using the table of contents and embedded links.
Of the information read, no grammar errors were found.
This is not relative to this book.
This book would be appropriate for an instructor with a strong background in teaching networking and using a more technical approach.
Reviewed by Luke Osterritter, Adjunct Instructor, Penn State New Kensington on 2/1/18
This text does a great job of covering the basics of computer networks while also presenting in-depth information, as well as diving into some somewhat tangential, but important, areas (e.g. security). read more
This text does a great job of covering the basics of computer networks while also presenting in-depth information, as well as diving into some somewhat tangential, but important, areas (e.g. security).
There are some terms here that I have seen presented differently than I have learned them or encountered in industry, but nothing inaccurate.
It would seem that this book is kept rather up-to-date, though much of the content is so fundamental as to not have too much of an expiration date, even in this field.
I believe the text is clear in most cases. However, I do feel many of the topics become very in-depth, very fast. It would be nice to have some concepts factored out to their basics early in the chapters, then expounded upon later.
The text does not appear to have any major inconsistencies.
When viewing online, the table of contents makes the content very browsable. However, when viewing in PDF, the large amount of subheadings for any one chapter can be a bit tough to navigate.
As the author notes, there isn't much agreement in how to present this topic, and it can be very difficult to explain one portion without referencing another topic that may not have been presented. I think factoring out some basics and explaining them up front, as this book has done, is a clever way of handling this.
I did not encounter any issues with the text interface.
I did not see any obvious grammatical errors.
This book is very matter-of-fact, with little in the way of irreverence. Likewise, there isn't much to work with here to be proactively inclusive. I think it works to be somewhat inert in this manner.
Overall, I think that this book is a great resource to have given its open availability. It's not the simplest book, so using this in a first level class or in a more general IT, CS, or survey course will take some shepherding on the part of the instructor. The comprehensiveness does suggest to me that this might be able to fill two courses worth of content, as well. It would be nice to have some of the information factored out, with some of the highlights available as lecture materials. On its own though, I feel this would be a strong resource to use in a computer networking course.
Table of Contents
- 1 An Overview of Networks
- 3 Other LANs
- 6 Abstract Sliding Windows
- 7 IP version 4
- 8 IP version 6
- 9 Routing-Update Algorithms
- 10 Large-Scale IP Routing
- 11 UDP Transport
- 12 TCP Transport
- 13 TCP Reno and Congestion Management
- 14 Dynamics of TCP Reno
- 15 Newer TCP Implementations
- 16 Network Simulations: ns-2
- 17 The ns-3 Network Simulator
- 19 Queuing and Scheduling
- 20 Quality of Service
- 21 Network Management and SNMP
- 22 Security
- 23 Bibliography
- 24 Selected Solutions
Ancillary Material
- Peter L Dordal
About the Book
An Introduction to Computer Networks is a free and open general-purpose computer-networking textbook, complete with diagrams and exercises.It covers the LAN, internetworking and transport layers, focusing primarily on TCP/IP. Particular attention is paid to congestion; other special topics include queuing, real-time traffic, network management, security and the ns simulator.
The book is suitable as the primary text for an undergraduate or introductory graduate course in computer networking, as a supplemental text for a wide variety of network-related courses, and as a reference work.
About the Contributors
Peter Lars Dordal is an associate professor within the Department of Computer Science at Loyola University of Chicago. His research interests are in programming languages and computer networks.
Contribute to this Page
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
- Computer Network Tutorial
Basics of Computer Network
- Basics of Computer Networking
- Introduction to basic Networking Terminology
- Goals of Networks
- Basic characteristics of Computer Networks
- Challenges of Computer Network
- Physical Components of Computer Network
Network Hardware and Software
Types of Computer Networks
- LAN Full Form
- How to Set Up a LAN Network?
- MAN Full Form in Computer Networking
- MAN Full Form
- WAN Full Form
- Introduction of Internetworking
- Difference between Internet, Intranet and Extranet
- Protocol Hierarchies in Computer Network
- Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter)
- Introduction of a Router
- Introduction of Gateways
- What is a network switch, and how does it work?
Network Topology
- Types of Network Topology
- Difference between Physical and Logical Topology
- What is OSI Model? - Layers of OSI Model
- Physical Layer in OSI Model
- Data Link Layer
- Session Layer in OSI model
- Presentation Layer in OSI model
- Application Layer in OSI Model
- Protocol and Standard in Computer Networks
- Examples of Data Link Layer Protocols
- TCP/IP Model
- TCP/IP Ports and Its Applications
- What is Transmission Control Protocol (TCP)?
- TCP 3-Way Handshake Process
- Services and Segment structure in TCP
- TCP Connection Establishment
- TCP Connection Termination
- Fast Recovery Technique For Loss Recovery in TCP
- Difference Between OSI Model and TCP/IP Model
Medium Access Control
- MAC Full Form
- Channel Allocation Problem in Computer Network
- Multiple Access Protocols in Computer Network
- Carrier Sense Multiple Access (CSMA)
- Collision Detection in CSMA/CD
- Controlled Access Protocols in Computer Network
SLIDING WINDOW PROTOCOLS
- Stop and Wait ARQ
- Sliding Window Protocol | Set 3 (Selective Repeat)
- Piggybacking in Computer Networks
IP Addressing
- What is IPv4?
- What is IPv6?
- Introduction of Classful IP Addressing
- Classless Addressing in IP Addressing
- Classful Vs Classless Addressing
- Classless Inter Domain Routing (CIDR)
- Supernetting in Network Layer
- Introduction To Subnetting
- Difference between Subnetting and Supernetting
- Types of Routing
- Difference between Static and Dynamic Routing
- Unicast Routing - Link State Routing
- Distance Vector Routing (DVR) Protocol
- Fixed and Flooding Routing algorithms
- Introduction of Firewall in Computer Network
Congestion Control Algorithms
- Congestion Control in Computer Networks
- Congestion Control techniques in Computer Networks
- Computer Network | Leaky bucket algorithm
- TCP Congestion Control
Network Switching
- Circuit Switching in Computer Network
- Message switching techniques
- Packet Switching and Delays in Computer Network
- Differences Between Virtual Circuits and Datagram Networks
Application Layer:DNS
- Domain Name System (DNS) in Application Layer
- Details on DNS
- Introduction to Electronic Mail
- E-Mail Format
- World Wide Web (WWW)
- HTTP Full Form
- Streaming Stored Video
- What is a Content Distribution Network and how does it work?
CN Interview Quetions
- Top 50 Networking Interview Questions (2024)
- Top 50 TCP/IP interview questions and answers
- Top 50 IP addressing interview questions and answers
- Last Minute Notes - Computer Networks
- Computer Network - Cheat Sheet
- Network Layer
- Transport Layer
- Application Layer
Pre-Requisite: Computer Networking
A computer network is a cluster of computers over a shared communication path that works to share resources from one computer to another, provided by or located on the network nodes.
Uses of Computer Networks
- Communicating using email, video, instant messaging, etc.
- Sharing devices such as printers, scanners, etc.
- Sharing files.
- Sharing software and operating programs on remote systems.
- Allowing network users to easily access and maintain information.
There are mainly five types of Computer Networks
Personal Area Network (PAN)
Local Area Network (LAN)
Campus Area Network (CAN)
Metropolitan Area Network (MAN)
Wide Area Network (WAN)
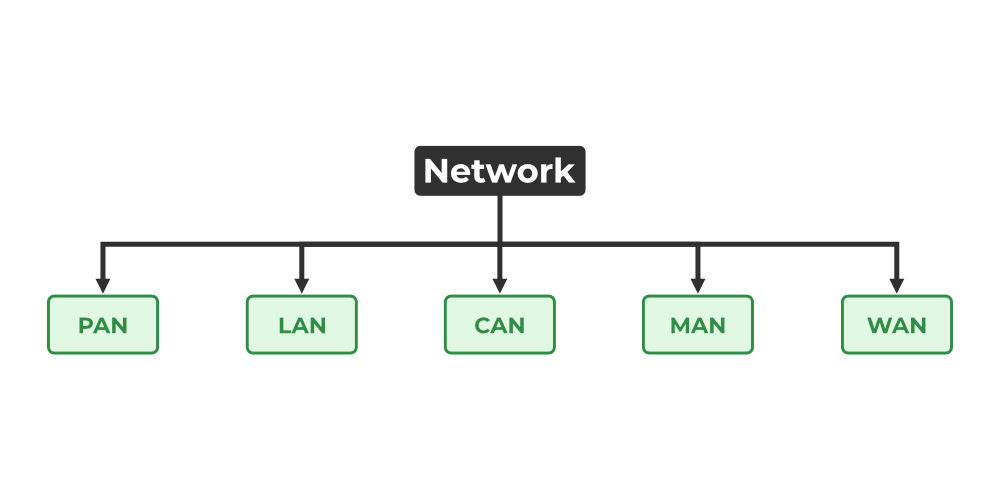
These are explained below.
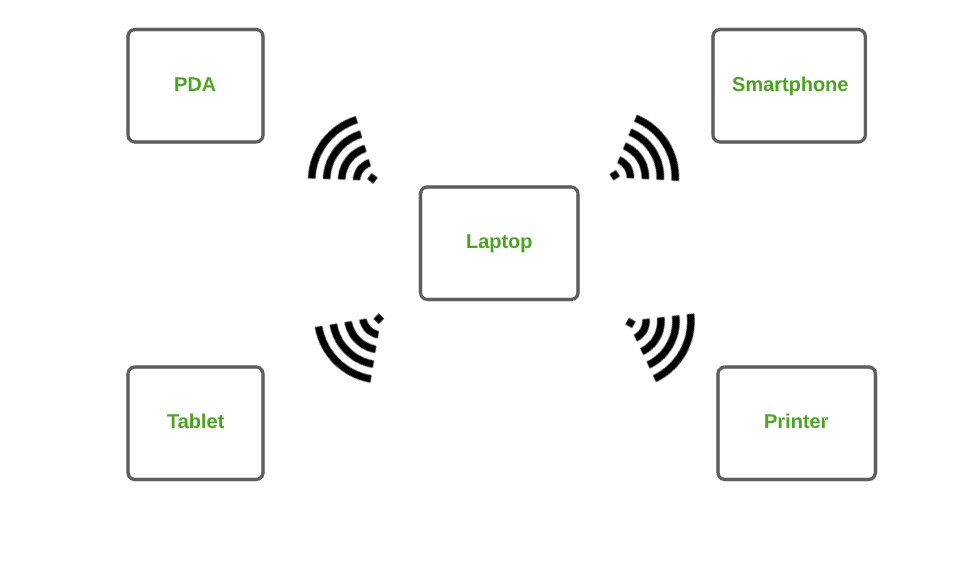
1. Personal Area Network (PAN)
PAN is the most basic type of computer network. This network is restrained to a single person, that is, communication between the computer devices is centered only on an individual’s workspace. PAN offers a network range of 1 to 100 meters from person to device providing communication. Its transmission speed is very high with very easy maintenance and very low cost.
This uses Bluetooth , IrDA , and Zigbee as technology.
Examples of PAN are USB, computer, phone, tablet, printer, PDA, etc.
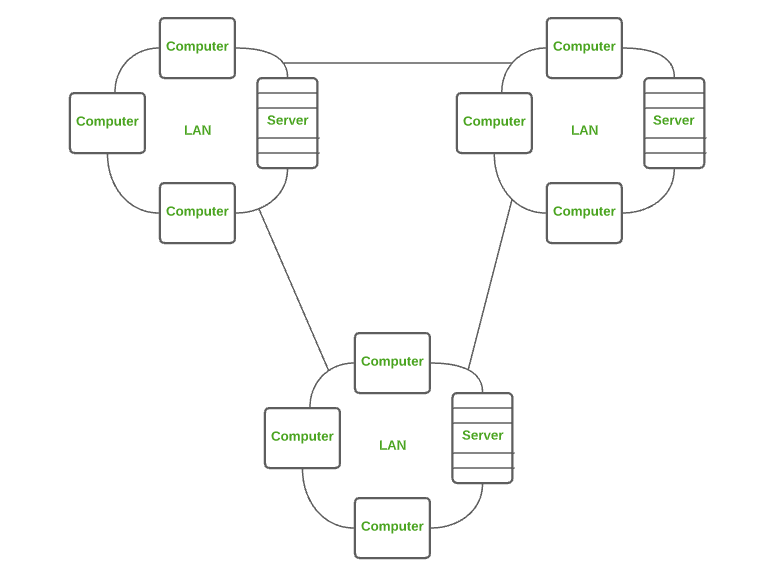
2. Local Area Network (LAN)
LAN is the most frequently used network. A LAN is a computer network that connects computers through a common communication path, contained within a limited area, that is, locally. A LAN encompasses two or more computers connected over a server. The two important technologies involved in this network are Ethernet and Wi-fi . It ranges up to 2km & transmission speed is very high with easy maintenance and low cost.
Examples of LAN are networking in a home, school, library, laboratory, college, office, etc.

3. Campus Area Network (CAN)
CAN is bigger than a LAN but smaller than a MAN. This is a type of computer network that is usually used in places like a school or colleges. This network covers a limited geographical area that is, it spreads across several buildings within the campus. CAN mainly use Ethernet technology with a range from 1km to 5km.
Its transmission speed is very high with a moderate maintenance cost and moderate cost.
Examples of CAN are networks that cover schools, colleges, buildings, etc.

4. Metropolitan Area Network (MAN)
A MAN is larger than a LAN but smaller than a WAN. This is the type of computer network that connects computers over a geographical distance through a shared communication path over a city, town, or metropolitan area. This network mainly uses FDDI, CDDI, and ATM as the technology with a range from 5km to 50km. Its transmission speed is average. It is difficult to maintain and it comes with a high cost.
Examples of MAN are networking in towns, cities, a single large city, a large area within multiple buildings, etc.
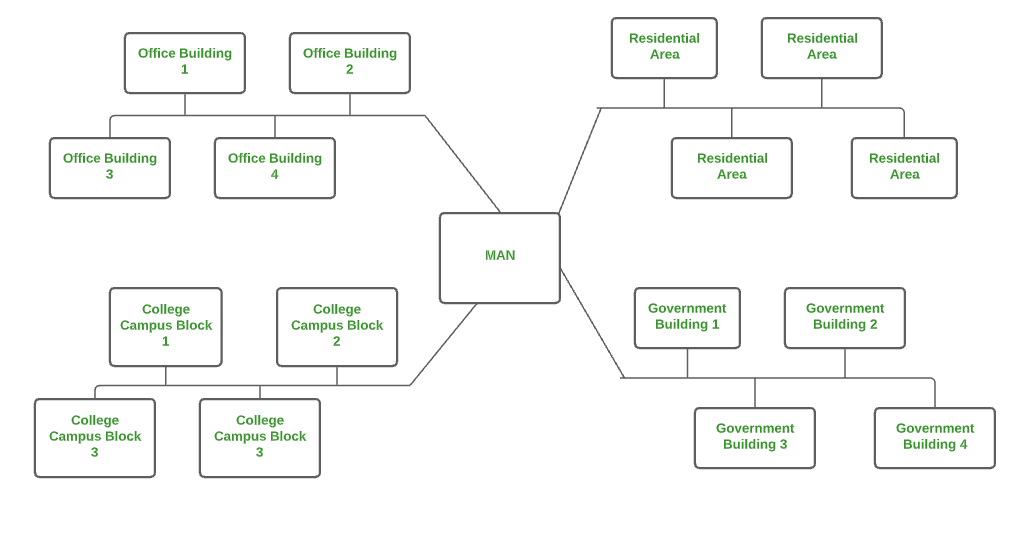
5. Wide Area Network (WAN)
WAN is a type of computer network that connects computers over a large geographical distance through a shared communication path. It is not restrained to a single location but extends over many locations. WAN can also be defined as a group of local area networks that communicate with each other with a range above 50km.
Here we use Leased-Line & Dial-up technology. Its transmission speed is very low and it comes with very high maintenance and very high cost.
The most common example of WAN is the Internet.
Comparison between Different Computer Networks
Other types of computer networks.
Wireless Local Area Network (WLAN)
Storage Area Network (SAN)
- System-Area Network (SAN)
Passive Optical Local Area Network (POLAN)
Enterprise Private Network (EPN)
Virtual Private Network (VPN)
Home Area Network (HAN)
1. Wireless Local Area Network (WLAN)
WLAN is a type of computer network that acts as a local area network but makes use of wireless network technology like Wi-Fi. This network doesn’t allow devices to communicate over physical cables like in LAN but allows devices to communicate wirelessly.
The most common example of WLAN is Wi-Fi.

There are several computer networks available; more information is provided below.
2. Storage Area Network (SAN)
SAN is a type of computer network that is high-speed and connects groups of storage devices to several servers. This network does not depend on LAN or WAN. Instead, a SAN moves the storage resources from the network to its high-powered network. A SAN provides access to block-level data storage.
Examples of SAN are a network of disks accessed by a network of servers.
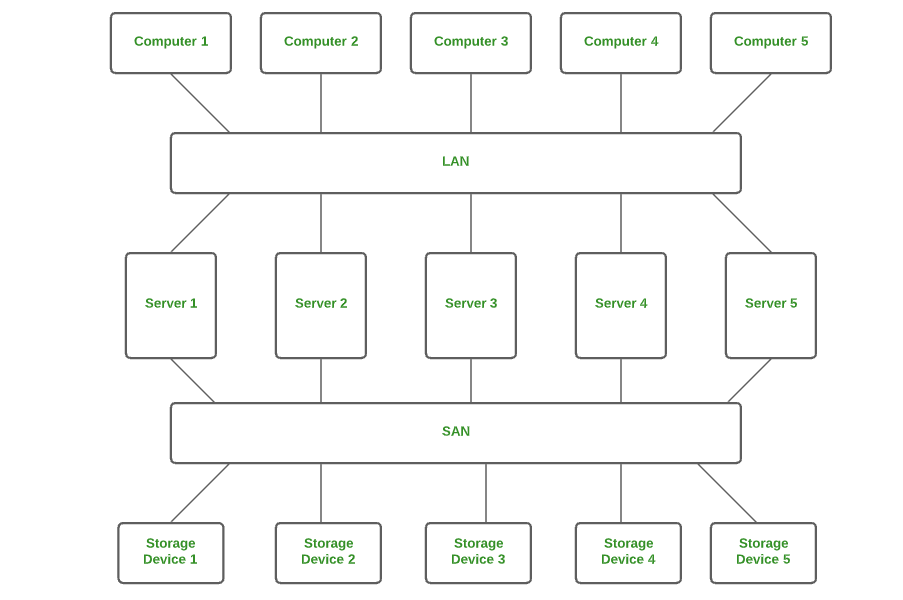
3. System Area Network (SAN)
A SAN is a type of computer network that connects a cluster of high-performance computers. It is a connection-oriented and high-bandwidth network. A SAN is a type of LAN that handles high amounts of information in large requests. This network is useful for processing applications that require high network performance.
Microsoft SQL Server 2005 uses SAN through a virtual interface adapter.

System Area Network (SAN)
4. Passive Optical Local Area Network (POLAN)
A POLAN is a type of computer network that is an alternative to a LAN. POLAN uses optical splitters to split an optical signal from a single strand of single-mode optical fiber to multiple signals to distribute users and devices. In short, POLAN is a point to multipoint LAN architecture.

5. Enterprise Private Network (EPN)
EPN is a type of computer network mostly used by businesses that want a secure connection over various locations to share computer resources.

6. Virtual Private Network (VPN)
A VPN is a type of computer network that extends a private network across the internet and lets the user send and receive data as if they were connected to a private network even though they are not. Through a virtual point-to-point connection users can access a private network remotely. VPN protects you from malicious sources by operating as a medium that gives you a protected network connection.

7. Home Area Network (HAN)
Many of the houses might have more than a computer. To interconnect those computers and with other peripheral devices, a network should be established similar to the local area network (LAN) within that home. Such a type of network that allows a user to interconnect multiple computers and other digital devices within the home is referred to as Home Area Network (HAN). HAN encourages sharing of resources, files, and programs within the network. It supports both wired and wireless communication.

Advantages of Computer Network
Some of the main advantages of Computer Networks are:
- Central Storage of Data: Files are stored on a central storage database which helps to easily access and available to everyone.
- Connectivity: A single connection can be routed to connect multiple computing devices.
- Sharing of Files: Files and data can be easily shared among multiple devices which helps in easily communicating among the organization.
- Security through Authorization: Computer Networking provides additional security and protection of information in the system.
Disadvantages of Computer Network
Some of the main disadvantages of Computer Networks are:
- Virus and Malware: A virus is a program that can infect other programs by modifying them. Viruses and Malware can corrupt the whole network.
- High Cost of Setup: The initial setup of Computer Networking is expensive because it consists of a lot of wires and cables along with the device.
- loss of Information: In case of a System Failure, might lead to some loss of data.
- Management of Network: Management of a Network is somehow complex for a person, it requires training for its proper use.
Please Login to comment...
Similar reads.
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
Looking for a Tutor Near You?

We use cookies
Our website use cookies, which help us to improve our site and enables us to deliver the best possible service and customer experience. By clicking accept you are agreeing to our cookies policy. Find out more
Choose Country Code
Ask a question.
- Bhubaneswar
- Gandhinagar
- Navi Mumbai
- Outside India
- Secundrabad
- Thiruchirappalli
- Thiruvananthapuram
- Visakhapatnam
Introduction To Computer Networking

A computer network is a set of computers connected together for the purpose of sharing resources. The most common resource shared today is connection to the Internet. Other shared resources can include a printer or a file server.

Prantik S / Kolkata
11 years of teaching experience
Qualification: MCA (Jaipur National University - [JNU], Jaipur - 2017)
Teaches: Basic Computer, Computer for official job, MS Office, School level computer, ICT Training, Computer Science, Information Practice, IT & Computer Subjects, BCA Tuition, IT, Computer, C, C++, C# (C Sharp), Java And J2EE, Python Programming, Visual Basic, BCA Subjects, Hardware Training, Networking, Java Script
- Peer-to-peer Server-based Introduction to Networking
- What is a Network? A network consists of 2 or more computers connected together, and they can communicate and share resources (e.g. information) D
- Why Networking? Sharing information — i.e. data communication Do you prefer these? , Or this?
- Sharing hardware or software E.g. print document Centralize administration and support E.g. Internet-based, so everyone can access the same administrative or support application from their PCs Modem Modem Modem Modem
- How many kinds of Networks? ' Depending on one's perspective, we can classify networks in different ways Based on transmission media: Wired (UTP, coaxial cables, fiber-optic cables) and Wireless Based on network size, LAN and WAN (and MAN) Based on management method: Peer-to-peer and Client/Server Based on topology (connectivity): Bus, Star, Ring ,
- Transmission Media Two main categories: Guided — wires, cables Unguided — wireless transmission, e.g. radio, microwave, infrared, sound, sonar t We will concentrate on guided media here: Twisted-Pair cables: Unshielded Twisted-Pair (UTP) cables Shielded Twisted-Pair (STP) cables Coaxial cables Fiber-optic cables
- Twisted-Pair Cables If the pair of wires are not twisted, electromagnetic noises from, e.g., motors, will affect the closer wire more than the further one, thereby causing errors 4 3 4 3 Noise source O 4 3 he total effect i 4 3 7
- Unshielded Twisted-Pair (UTP) Typically wrapped inside a plastic cover (for mechanical protection) A sample UTP cable with 5 unshielded twisted pairs of wires Plastic cover Twisted pairs (5 pairs) Insulator Metal 8
- Shielded Twisted-Pair (STP) STP cables are similar to UTP cables, except there is a metal foil or braided-metal-mesh cover that encases each pair of insulated wires Plastic cover Metal shield Insulation Copper
- Categories of UTP Cables EIA classifies UTP cables according to the quality: Category 1 — the lowest quality, only good for voice, mainly found in very old buildings, not recommended now Category 2 — good for voice and low data rates (up to 4Mbps for low-speed token ring networks) Category 3 — at least 3 twists per foot, for up to 10 Mbps (common in phone networks in residential buildings) Category 4 — up to 16 Mbps (mainly for token rings) Category 5 (or 5e) — up to 100 Mbps (common for networks targeted for high-speed data communications) Category 6 — more twists than Cat 5, up to 1 Gbps
- Coaxial Cables In general, coaxial cables, or coax, carry signals of higher freq (IOOKHz-500MHz) than IJTP cables Outer metallic wrapping serves both as a shield against noise and as the second conductor that completes the circuit Plastic cover Insulator Outer conductor Inner conductor (shield) 11
- Advantages and Disadvantages o Noise resistance — external light is blocked by outer jacket o Less signal attenuation —a signal can run for miles without regeneration (currently, the lowest measured loss is about or 0.16dB per km) o Higher bandwidth — currently, limits on data rates come from the signal generation/ reception technology, not the fiber itself Cost — Optical fibers are expensive Installation/maintenance — any crack in the core will degrade the signal, and all connections must be perfectly aligned
- Fiber-Optic Cables Light travels at 3x108 ms-I in free space and is the fastest possible speed in the Universe Light slows down in denser media, e.g. glass Refraction occurs at interface, with light bending away from the normal when it enters a less dense medium Beyond the critical angle total internal reflection
- An optical fiber consists of a core (denser material) and a cladding (less dense material) Simplest one is a multimode step-index optical fiber Multimode = multiple paths, whereas step-index = refractive index follows a step-function profile (i.e. an abrupt change of refractive index between the core and the cladding) Light bounces back and forth along the core Common light sources: LEDs and lasers Core Cladding
- LAN and WAN Local Area Network (LAN) Small network, short distance A room, a floor, a building Limited by no. of computers and distance covered ' Usually one kind of technology throughout the LAN Serve a department within an organization Examples: Network inside the Student Computer Room Network inside CF502 Network inside your home
- Wide Area Network (WAN) A network that uses long-range telecommunication links to connect 2 or more LANs/computers housed in different places far apart. Towns, states, countries Examples: Network of our Campus Internet WAN Student Computer Centre Your home USA 16
- , Example WAN technologies: , ISDN — Integrated Service Digital Network Basic rate: 192 Kbps Primary rate: 1.544Mbps T-Carriers — basically digital phone lines , Tl: 1.544Mbps T3: Frame relay Each link offers 1.544Mbps or even higher ATM — Asynchronous Transfer Mode , Support B-ISDN: 155Mbps or 622Mbps or higher , SONET — Synchronous Optical Network , Basic rate OCI: 51.84Mbps ' Support OC12 and up to OC192 (9953.28Mbps) or even higher in the future
- , Example of WAN: Broadband Cable Network , Cable TV services have been extensively developed in most modern cities Cable TV companies try to make use of their coaxial cable installed (that are supposed to carry TV signals) to deliver broadband data services Many cable network wiring has been replaced with hybrid fiber-coax (HFC) — i.e. use of fiber-optic cable to connect to the subscribers' buildings, and then the original coaxial cable to connect to each household 18
- PC TV oaxla Cable glÉÅ The connection is shared by a number of subscribers, hence may raise performance and security problems able Drop Cable company 19
- ' Cable is an asymmetrical technology Downstream: max 36 Mbps ' Upstream: max 10 Mbps May be reduced to 3 — 10 Mbps downstream and 2 Mbps upstream, depending on no. of subscribers Need a special cable modem Teryon Cable Modem Coaxial link from cable TV socket Ethernet link to PC 20
- Peer-to-peer Networks Peer-to-peer network is also called workgroup No hierarchy among computers all are equal No administrator responsible for the network Peer-to-peer
- Advantages of peer-to-peer networks: Low cost ' Simple to configure ' User has full accessibility of the computer Disadvantages of peer-to-peer networks: May have duplication in resources Difficult to uphold security policy Difficult to handle uneven loading Where peer-to-peer network is appropriate: 10 or less users No specialized services required ' Security is not an issue Only limited growth in the foreseeable future
- Clients and Servers Network Clients (Workstation Computers that request network resources or services Network Servers Computers that manage and provide network resources and services to clients ' Usually have more processing power, memory and hard disk space than clients , Run Network Operating System that can manage not only data, but also users, groups, security, and applications on the network Servers often have a more stringent requirement on its performance and reliability 23
- Advantages of client/server networks Facilitate resource sharing — centrally administrate and control Facilitate system backup and improve fault tolerance Enhance security — only administrator can have access to Server ' Support more users — difficult to achieve with peer-to- peer networks Disadvantages of client/server networks High cost for Servers Need expert to configure the network Introduce a single point of failure to the system 24
- Topology — 3 basic types How so many computers are connected together? Bus Topology Star Topology Hub Ring Topology
- , Bus Topology ' Simple and low-cost A single cable called a trunk (backbone, segment Only one computer can send messages at a time Passive topology - computer only listen for, not regenerate data Star Topology Each computer has a cable connected to a single point More cabling, hence higher cost All signals transmission through the hub; if down, entire network down Depending on the intelligence of hub, two or more computers may send message at the same time 26
- How to construct a network with Bus / Star Topology? Bus Topology Coaxial cable Network Card Distribution rack and shelves Expandable patch panels Star Topology BNC T-Connector
- Ring Topology Every computer serves as a repeater to boost signals Typical way to send data: Token passing only the computer who gets the token can send data Disadvantages Difficult to add computers More expensive Ack data Ack Ack If one computer fails, whole network fails data Ack 28

Need a Tutor or Coaching Class?
Post an enquiry and get instant responses from qualified and experienced tutors.
Related PPTs
Upload ppts.
If you have your own PowerPoint Presentations which you think can benefit others, please upload on LearnPick. For each approved PPT you will get 50 Credit Points and 50 Activity Score which will increase your profile visibility.
- Post Learning Requirement
- How it Works
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Fundamentals of computer networking
You learn the fundamental principles of computer networking to prepare you for the Azure admin and developer learning paths.
Learning objectives
In this module, you will:
- List the different network protocols and network standards.
- List the different network types and topologies.
- List the different types of network devices used in a network.
- Describe network communication principles like TCP/IP, DNS, and ports.
- Describe how these core components map to Azure networking.
Prerequisites
- Introduction min
- Network types and topologies to use when you design a network min
- Types of network devices to use when you build a network min
- Network protocols to use when you implement a network min
- IP address standards and services min
- Summary min

Introduction to Computer Network
Nov 06, 2019
380 likes | 558 Views
Introduction to Computer Network. Dr. Rania R Ziedan. Agenda. Introduction Network types Network topology Network connection models OSI model. Computer network. A collection of computing devices that are connected in various ways in order to communicate and share resources or files
Share Presentation
- client server
- physical topology
- client server model
- fully connected mesh network

Presentation Transcript
Introduction to Computer Network Dr. Rania R Ziedan
Agenda • Introduction • Network types • Network topology • Network connection models • OSI model
Computer network • A collection of computing devices that are connected in various ways in order to communicate and share resources or files • Wired network: the connections between computers in a network are made using physical wires or cables • Wireless network: the connections between computers in a network are made using radio waves or infrared signals
Computer network • Each computer in the network is known as: node or host • Data transfer rate: is the speed with which data is moved from one place on a network to another, which is a key feature in computer networks
Network Types • Local Area Network (LAN): two or more computers connected together, the computers are physically near each other (for example: in the same building) • LANs are inexpensive to install • LANs provide higher speeds
Network Types • Metropolitan Area Network (MAN): usually span tens of kilometers (for example: in the same city) • The cost of installation and operation is higher. • MANs use high-speed connections such as fiber optics to achieve higher speeds
Network Types • Wide Area Network (WAN): is a connection of LANs (for example : the Internet) • WANs span a larger area than a single city. • These use long distance telecommunication networks for connection, thereby increasing the cost.
The Internet • It is a large group of computers that are connected to each other and used to send information quickly between computers around the world
Physical topology of a network • The term physical topology refers to the way in which a network is laid out physically. • The topology of a network is the geometric representation of the relationship of all the links and linking devices • There are four basic topologies possible: mesh, star, bus, and ring
Physical topology of a network • Mesh Topology • In a mesh topology, every device has a dedicated point-to-point link to every other device. • The term dedicated means that the link carries traffic only between the two devices it connects. • The number of physical links in a fully connected mesh network with n nodes n(n-1)/2 • The mesh topology used in the connection of telephone regionaloffices in which each regional office needs to be connected to every other regional office.
Physical topology of a network • Mesh Topology • Advantages: • Each link can carry its own data load, thus eliminating the traffic problems that can occur with shared links. • A mesh topology is robust. If one link becomes unusable, it does not incapacitate the entire system. • Every message travels along a dedicated line, only the intended recipient sees it. Physical boundaries prevent other users from gaining access to messages. • Point-to-point links make fault identification and fault isolation easy. Traffic can be routed to avoid links with suspected problems. • Disadvantage: • The amount of cabling and the number of I/O ports required.
Physical topology of a network • Star Topology • Each device has a dedicated point-to-point link only to a central controller, usually called a hub. • A star topology does not allow direct traffic between devices. • The controller acts as an exchange: If one device wants to send data to another, it sends the data to the controller, which then relays the data to the other connected device. • The star topology is used in local-area networks (LANs)
Physical topology of a network • Star Topology • Advantages: • less expensive than a mesh topology, each device needs only one link and one I/O port to connect it to any number of others. • Easy to install and reconfigure. • Robustness, if one link fails, only that link is affected, all other links remain active. • As long as the hub is working, it can be used to monitor link problems and bypass defective links • Disadvantage: • the dependency of the whole topology on one single point, the hub. If the hub goes down, the whole system is dead
Physical topology of a network • Bus Topology • A bus topology is multipoint connection. • One long cable acts as a backbone to link all the devices in a network. • Nodes are connected to the bus cable by drop lines and taps. • There is a limit on the number of taps a bus can support and on the distance between those taps. As a signal travels along the backbone, some of its energy is transformed into heat. Therefore, it becomes weaker and weaker as it travels farther and farther. • Bus topology was the one of the first topologies used in the design of early local area networks. • The cable has two end terminals that dampen the signal so that it does not keep moving from one end of the network to the other.
Physical topology of a network • Bus Topology • Advantages: • Ease of installation • Bus uses less cabling than mesh or star topologies. • Disadvantages: • Difficult reconnection and fault isolation. • Difficult to add new devices. • Signal reflection at the taps can cause degradation in quality. This degradation can be controlled by limiting the number and spacing of devices connected to a given length of cable. • Adding new devices may therefore require modification or replacement of the backbone. • In addition, a fault or break in the bus cable stops all transmission, even between devices on the same side of the problem. The damaged area reflects signals back in the direction of origin, creating noise in both directions.
Physical topology of a network • Ring Topology • Each device has a dedicated point-to-point connection with only the two devices on either side of it. • A signal is passed along the ring in one direction, from device to device, until it reaches its destination. • Each device in the ring incorporates a repeater. When a device receives a signal intended for another device, its repeater regenerates the bits and passes them along
Physical topology of a network • Ring Topology • Advantages: • easy to install and reconfigure • Fault isolation is simplified. • Generally in a ring, a signal is always circulating . If one device does not receive a signal within a specified period, it can issue an alarm. The alarm alerts the network operator to the problem and its location. • To add or delete a device requires changing only two connections. The only constraints are media and traffic considerations (maximum ring length and number of devices). • Disadvantages: • Unidirectional traffic • a break in the ring can disable the entire network. • This weakness can be solved by using a dual ring or a switch capable of closing off the break.
Network connection models • Networks can also be classified according to the roles that the networked computers play in the network’s operation. • Peer-to-peer, • server-based, • and client-based.
Network connection models Peer-to-peer model all computers are considered equal. Each computer controls its own information and is capable of functioning as either a client or a server depending upon the requirement. • Peer-to-peer networks are inexpensive and easy to install. • They are popular as home networks and for use in small companies. • Most operating systems come with built-in peer-to-peer networking capability. • The maximum number of peers that can operate on a peer-to-peer network is ten. • Each peer shares resources and allows others open access to them. • Shares can be document folders, printers, peripherals, and any other resource that they control on their computers.
Network connection models Peer-to-peer network
Network connection models • client-server model is a software that consists of two parts, client systems and server systems, both communicate over a computer network
Network connection models • The client-server relationship describes the relation between the client and how it makes a service request to the server, and how the server can accept these requests, process them, and return the requested information to the client
Page request How the Web Works? • WWW use classical client / server architecture • HTTP is text-based request-response protocol HTTP HTTP Server response Server running Web Server Software (IIS, Apache, etc.) Client running a Web Browser
Client/Server • There are two types of servers: • File serverA computer that stores and manages files for multiple users on a network • Web serverA computer that responds to requests for web pages (from the browser client)
Web servers and browsers • web server: software that listens for web page requests • Apache • Microsoft Internet Information Server (IIS) (part of Windows) • web browser: fetches/displays documents from web servers • Mozilla Firefox • Microsoft Internet Explorer (IE) • Apple Safari • Google Chrome • Opera
OSI Architecture The OSI 7-layer Model OSI – Open Systems Interconnection
Description of Layers • Physical Layer • Handles the transmission of raw bits over a communication link • Data Link Layer • Collects a stream of bits into a larger aggregate called a frame • Network adaptor and device drivers in OS implement the protocol in the datalink layer • Frames are actually delivered to hosts • Network Layer • Handles routing between nodes within a packet-switched network • Unit of data exchanged between nodes in this layer is called a packet The lower three layers are implemented on all network nodes
Description of Layers • Transport Layer • Implements a process-to-process channel • Unit of data exchanges in this layer is called a message • Session Layer • Provides a name space that is used to tie together the potentially different transport streams that are part of a single application • Presentation Layer • Concerned about the format of data exchanged between peers • Application Layer • Standardize common type of exchanges The transport layer and the higher layers typically run only on end-hosts and not on the intermediate switches and routers
Summary • A computer network consists of two or more computers that are connected and are able to communicate. • The basic purpose of networks is to enable effective communication, share resources, and facilitate centralized management of data. • Networks can be classified according to their geographical boundaries or their component roles. • The topology of a network is the geometric representation of the relationship of all the links and linking devices
Questions???
- More by User

15-349 Introduction to Computer and Network Security
15-349 Introduction to Computer and Network Security. Iliano Cervesato 7 September 2008 – Beyond Encryption. Where we are. Course intro Cryptography Intro to crypto Modern crypto Symmetric encryption Asymmetric encryption Beyond encryption Cryptographic protocols Attacking protocols
610 views • 36 slides

15-349 Introduction to Computer and Network Security. Iliano Cervesato 14 September 2008 – Attacking Cryptographic Protocols. Where we are. Course intro Cryptography Intro to crypto Modern crypto Symmetric encryption Asymmetric encryption Beyond encryption Cryptographic protocols
413 views • 30 slides

15-349 Introduction to Computer and Network Security. Iliano Cervesato 26 August 2008 – Modern Cryptography. Where we are. Course intro Cryptography Intro to crypto Modern crypto Symmetric encryption Asymmetric encryption Beyond encryption Cryptographic protocols Attacking protocols
379 views • 23 slides

Computer and Network Security Introduction
Computer and Network Security Introduction. Dr. Ron Rymon Efi Arazi School of Computer Science IDC, Herzliya. 2010/11. Today’s Lecture. Introduction A Few Nightmare Scenarios Statistics and Impact Course Plan and Administrativia Models of Computer Security.
585 views • 37 slides

15-349 Introduction to Computer and Network Security. Iliano Cervesato 24 August 2008 – Introduction to Cryptography. Where we are. Course intro Cryptography Intro to crypto Modern crypto Symmetric encryption Asymmetric encryption Beyond encryption Cryptographic protocols
454 views • 31 slides

INTRODUCTION TO COMPUTER & NETWORK SECURITY
INTRODUCTION TO COMPUTER & NETWORK SECURITY. Instructor: Dania Alomar. Why S tudy Security ?. Security threats are real… And need protection against Keeping information secure from modification and unauthorized access. Keeping it available is getting increasingly difficult.
1.07k views • 15 slides

INTRODUCTION TO COMPUTER
INTRODUCTION TO COMPUTER . Lecture #10 COMPUTER SOFTWARE. By Shahid Naseem (Lecturer). COMPUTER SOFTWARE. A set of instructions given to the computer to solve a particular problem is called software. Software is also called computer program.
553 views • 12 slides

Introduction to Computer
Introduction to Computer . Waqas Ali Sahito Lecturer Department of Computer Science. Subject Distribution. Theory 100 Marks Paper marks = 75 Sessional Marks = 25 Practical 50 Marks Objective = 10 Viva = 20 Sessional Marks = 20 Sessional Marks.
681 views • 41 slides

INTRODUCTION TO COMPUTER . Lecture #12 FILES FORMAT. By Shahid Naseem (Lecturer). FILES. A collection of data or information that has a name , called the filename .

By Kiramat Rahman Department of Computer & Software Technology. Introduction to Computer. Input / Output (I/O) devices Commonly used input devices Commonly used output devices Other concepts related to I/O devices. Outline. Provide means of communication between a computer
893 views • 61 slides

INTRODUCTION TO COMPUTER. EVOLUTION OF THE COMPUTER. EVOLUTION OF THE COMPUTER. The history and evolution of computer are divided into two eras : before 1940 after 1940. BEFORE 1940. In the beginning, human do calculation by fingers, stones, small woods etc.
536 views • 8 slides

Introduction to Computer. By: Maria Mullen. Objectives. Identify and use computer hardware Identify the pieces that make up the desktop Open and close desired programs Switch back and forth between open windows Create and save a document Print a document.
724 views • 23 slides

Introduction to computer
Introduction to computer. Submitted by : aashish.c ashish.m Abhijeet.g Ankit.j abhay.j . CONTENT. WHAT IS COMPUTER? WHY COMPUTER? COMPUTER COMPONENT DATA & INFORMATION
846 views • 32 slides

INTRODUCTION TO COMPUTER. Lecture #15 ARRAYS. By Shahid Naseem (Lecturer). ARRAYS DEFINITION. An array is a sequence of objects of same data type. The objects in an array are also called “elements of array”.
342 views • 16 slides

INTRODUCTION TO COMPUTER. Lecture #9 OPERATING SYSTEM. By Shahid Naseem (Lecturer). LECTURE OUTLINES. DATA. A collection of raw (unprepared or unprocessed) facts ( things, people, objects, events) and figures, collected for a specific purpose is called data.
365 views • 19 slides
Introduction to Computer and Network Architectures (Networks)
Introduction to Computer and Network Architectures (Networks). Module introduction. Staff. Ivailo Chakarov- Module leader/tutor/Cisco Academy Director/Part man/part labrador [email protected]. Module content. Module assessment. The assessment for Networks part of the module is:
278 views • 8 slides

Introduction to Network
Introduction to Network. What is a Network?. A network consists of 2 or more computers connected together, and they can communicate and share resources (e.g. information). How many kinds of Networks?. Depending on one ’ s perspective, we can classify networks in different ways.
413 views • 26 slides

15-349 Introduction to Computer and Network Security. Iliano Cervesato 2 September 2008 – Public-key Encryption. Where we are. Course intro Cryptography Intro to crypto Modern crypto Symmetric encryption Asymmetric encryption Beyond encryption Cryptographic protocols
410 views • 27 slides

Introduction to COMPUTER
Introduction to COMPUTER. February 22, 2010. ADB Grant 0133-CAM: Public Financial Management in Rural Development Ministries (Component 1). AN INTRODUCTION TO COMPUTER TECHNOLOGY.
818 views • 31 slides


Introduction To Computer
Introduction To Computer. Hardware. Mr. Garel. St. BACHS. What is a Computer?. a computer can be. defined as a machine for processing and storing information electronically. it must have a way for us to get information into the machine, and some way to get it out afterwards so we can
806 views • 13 slides

Introduction to Computer. Computers are everywhere!. Computers are showing up everywhere you look, and even in places you can't see. Computers check out your groceries, pump your gas, dispense money at the ATM, turn the heat on and off, control the way your car runs. They're everywhere!.
1.15k views • 64 slides

305171 Computer Programming Rattapoom Waranusast Department of Electrical and Computer Engineering Faculty of Engineering, Naresuan University. Introduction to Computer. What is computer?. A COMPUTER is an electronic device that can: Receive information Perform processes
1.68k views • 66 slides
What Is a Computer Network? Definition, Objectives, Components, Types, and Best Practices
A computer network is a system that connects two or more computing devices to transmit and share information.
A computer network is defined as a system that connects two or more computing devices for transmitting and sharing information. This article explains computer network in detail, along with its types, components, and best practices for 2022.
Table of Contents
What is a computer network, key components of a computer network, types of computer networks, key objectives of creating and deploying a computer network, top 10 best practices for computer network management in 2022.
A computer network is a system that connects two or more computing devices for transmitting and sharing information. Computing devices include everything from a mobile phone to a server. These devices are connected using physical wires such as fiber optics, but they can also be wireless.
The first working network, called ARPANET, was created in the late 1960s and was funded by the U.S. Department of Defense. Government researchers used to share information at a time when computers were large and difficult to move. We have come a long way today from that basic kind of network. Today’s world revolves around the internet, which is a network of networks that connects billions of devices across the world. Organizations of all sizes use networks to connect their employees’ devices and shared resources such as printers.
An example of a computer network at large is the traffic monitoring systems in urban cities. These systems alert officials and emergency responders with information about traffic flow and incidents. A simpler example is using collaboration software such as Google Drive to share documents with colleagues who work remotely. Every time we connect via a video call, stream movies, share files, chat with instant messages, or just access something on the internet, a computer network is at work.
Computer networking is the branch of computer science that deals with the ideation, architecture, creation, maintenance, and security of computer networks. It is a combination of computer science, computer engineering, and telecommunication.
See More: Building a Disaster Preparedness Strategy? Here’s How Leading Service Providers Can Help
From a broader lens, a computer network is built with two basic blocks: nodes or network devices and links. The links connect two or more nodes with each other. The way these links carry the information is defined by communication protocols. The communication endpoints, i.e., the origin and destination devices, are often called ports.

Main Components of a Computer Network
1. Network Devices
Network devices or nodes are computing devices that need to be linked in the network. Some network devices include:
- Computers, mobiles, and other consumer devices : These are end devices that users directly and frequently access. For example, an email originates from the mailing application on a laptop or mobile phone.
- Servers : These are application or storage servers where the main computation and data storage occur. All requests for specific tasks or data come to the servers.
- Routers : Routing is the process of selecting the network path through which the data packets traverse. Routers are devices that forward these packets between networks to ultimately reach the destination. They add efficiency to large networks.
- Switches : Repeaters are to networks what transformers are to electricity grids—they are electronic devices that receive network signals and clean or strengthen them. Hubs are repeaters with multiple ports in them. They pass on the data to whichever ports are available. Bridges are smarter hubs that only pass the data to the destination port. A switch is a multi-port bridge. Multiple data cables can be plugged into switches to enable communication with multiple network devices.
- Gateways : Gateways are hardware devices that act as ‘gates’ between two distinct networks. They can be firewalls, routers, or servers.
Learn More: Why a Network Management Card Is Essential to Secure Enterprise Networks from Cyber Threats
Links are the transmission media which can be of two types:
- Wired : Examples of wired technologies used in networks include coaxial cables, phone lines, twisted-pair cabling, and optical fibers. Optical fibers carry pulses of light to represent data.
- Wireless : Network connections can also be established through radio or other electromagnetic signals. This kind of transmission is called ‘wireless’. The most common examples of wireless links include communication satellites, cellular networks , and radio and technology spread spectrums. Wireless LANs use spectrum technology to establish connections within a small area.
3. Communication protocols
A communication protocol is a set of rules followed by all nodes involved in the information transfer. Some common protocols include the internet protocol suite (TCP/IP), IEEE 802, Ethernet, wireless LAN, and cellular standards. TCP/IP is a conceptual model that standardizes communication in a modern network. It suggests four functional layers of these communication links:
- Network access layer : This layer defines how the data is physically transferred. It includes how hardware sends data bits through physical wires or fibers.
- Internet layer : This layer is responsible for packaging the data into understandable packets and allowing it to be sent and received.
- Transport layer : This layer enables devices to maintain a conversation by ensuring the connection is valid and stable.
- Application layer : This layer defines how high-level applications can access the network to initiate data transfer.
Most of the modern internet structure is based on the TCP/IP model, though there are still strong influences of the similar but seven-layered open systems interconnection (OSI) model.
IEEE802 is a family of IEEE standards that deals with local area networks (LAN) and metropolitan area networks (MAN). Wireless LAN is the most well-known member of the IEEE 802 family and is more widely known as WLAN or Wi-Fis.
4. Network Defense
While nodes, links, and protocols form the foundation of a network, a modern network cannot exist without its defenses. Security is critical when unprecedented amounts of data are generated, moved, and processed across networks. A few examples of network defense tools include firewall , intrusion detection systems (IDS), intrusion prevention systems (IPS), network access control (NAC), content filters, proxy servers, anti-DDoS devices, and load balancers.
See More: What Is Local Area Network (LAN)? Definition, Types, Architecture and Best Practices
Computer networks can be classified based on several criteria, such as the transmission medium, the network size, the topology, and organizational intent. Based on a geographical scale, the different types of networks are:
- Nanoscale networks : These networks enable communication between minuscule sensors and actuators.
- Personal area network (PAN) : PAN refers to a network used by just one person to connect multiple devices, such as laptops to scanners, etc.
- Local area network (LAN) : The local area network connects devices within a limited geographical area, such as schools, hospitals, or office buildings.
- Storage area network (SAN) : SAN is a dedicated network that facilitates block-level data storage. This is used in storage devices such as disk arrays and tape libraries.
- Campus area network (CAN) : Campus area networks are a collection of interconnected LANs. They are used by larger entities such as universities and governments.
- Metropolitan area network (MAN) : MAN is a large computer network that spans across a city.
- Wide area network (WAN) : Wide area networks cover larger areas such as large cities, states, and even countries.
- Enterprise private network (EPN): An enterprise private network is a single network that a large organization uses to connect its multiple office locations.
- Virtual private network (VPN) : VPN is an overlay private network stretched on top of a public network.
- Cloud network : Technically, a cloud network is a WAN whose infrastructure is delivered via cloud services.
Based on organizational intent, networks can be classified as:
- Intranet : Intranet is a set of networks that is maintained and controlled by a single entity. It is generally the most secure type of network, with access to authorized users alone. An intranet usually exists behind the router in a local area network.
- Internet : The internet (or the internetwork) is a collection of multiple networks connected by routers and layered by networking software. This is a global system that connects governments, researchers, corporates, the public, and individual computer networks.
- Extranet : An extranet is similar to the intranet but with connections to particular external networks. It is generally used to share resources with partners, customers, or remote employees.
- Darknet : The darknet is an overlay network that runs on the internet and can only be accessed by specialized software. It uses unique, customized communication protocols.
See More: Wide Area Network (WAN) vs. Local Area Network (LAN): Key Differences and Similarities
There is no industry—education, retail, finance, tech, government, or healthcare—that can survive without well-designed computer networks. The bigger an organization, the more complex the network becomes. Before taking on the onerous task of creating and deploying a computer network, here are some key objectives that must be considered.

Objectives of Deploying a Computer Network
1. Resource sharing
Today’s enterprises are spread across the globe, with critical assets being shared across departments, geographies, and time zones. Clients are no more bound by location. A network allows data and hardware to be accessible to every pertinent user. This also helps with interdepartmental data processing. For example, the marketing team analyzes customer data and product development cycles to enable executive decisions at the top level.
2. Resource availability & reliability
A network ensures that resources are not present in inaccessible silos and are available from multiple points. The high reliability comes from the fact that there are usually different supply authorities. Important resources must be backed up across multiple machines to be accessible in case of incidents such as hardware outages.
3. Performance management
A company’s workload only increases as it grows. When one or more processors are added to the network, it improves the system’s overall performance and accommodates this growth. Saving data in well-architected databases can drastically improve lookup and fetch times.
4.Cost savings
Huge mainframe computers are an expensive investment, and it makes more sense to add processors at strategic points in the system. This not only improves performance but also saves money. Since it enables employees to access information in seconds, networks save operational time, and subsequently, costs. Centralized network administration also means that fewer investments need to be made for IT support.
5. Increased storage capacity
Network-attached storage devices are a boon for employees who work with high volumes of data. For example, every member in the data science team does not need individual data stores for the huge number of records they crunch. Centralized repositories get the job done in an even more efficient way. With businesses seeing record levels of customer data flowing into their systems, the ability to increase storage capacity is necessary in today’s world.
6. Streamlined collaboration & communication
Networks have a major impact on the day-to-day functioning of a company. Employees can share files, view each other’s work, sync their calendars, and exchange ideas more effectively. Every modern enterprise runs on internal messaging systems such as Slack for the uninhibited flow of information and conversations. However, emails are still the formal mode of communication with clients, partners, and vendors.
7. Reduction of errors
Networks reduce errors by ensuring that all involved parties acquire information from a single source, even if they are viewing it from different locations. Backed-up data provides consistency and continuity. Standard versions of customer and employee manuals can be made available to a large number of people without much hassle.
8. Secured remote access
Computer networks promote flexibility, which is important in uncertain times like now when natural disasters and pandemics are ravaging the world. A secure network ensures that users have a safe way of accessing and working on sensitive data, even when they’re away from the company premises. Mobile handheld devices registered to the network even enable multiple layers of authentication to ensure that no bad actors can access the system.
See More: What Is Wide Area Network (WAN)? Definition, Types, Architecture, and Best Practices
Network management is the process of configuring, monitoring, and troubleshooting everything that pertains to a network, be it hardware, software, or connections. The five functional areas of network management are fault management, configuration management, performance management, security management, and (user) accounting management.
Computer networks can quickly become unruly mammoths if not designed and maintained from the beginning. Here are the top 10 practices for proper computer network management.

Network Management Best Practices
1. Pick the right topology
Network topology is the pattern or hierarchy in which nodes are connected to each other. The topology can speed up, slow down, or even break the network based on the company’s infrastructure and requirements. Before setting up a network from scratch, network architects must choose the right one. Some common topologies include:
- Bus network : Each node is linked to only one other node.
- Ring network : Each node is linked to two other nodes, thus forming a ring.
- Mesh network : Each node must strive to be connected to every other node in the system.
- Star network : A central node server is linked to multiple other nodes. This is faster since data doesn’t have to travel through each node.
- Tree network : Here, nodes are arranged in hierarchies.
2. Document & update constantly
Documentation of the network is vital since it is the backbone of operations. The documentation must include:
- Technical specifications of equipment, including wires, cables, and connectors
- The software used to enable the hardware and the smooth and secure flow of data
- A formal record of policies and procedures with respect to network operators and users
This must be audited at scheduled intervals or during rehauls. Not only does this make network management easier, but it also allows for smoother compliance audits.
3. Use the right tools
The network topology is just the first step toward building a robust network. To manage a highly available and reliant network, the appropriate tools must be placed at the right locations. Must-have tools in a network are:
- Network monitoring solutions : A network monitoring solution gives complete visibility into the network. Visual maps help gauge network performance. It can track packets, provide a granular look into network traffic, and help spot anomalies. Newer monitoring systems leverage artificial intelligence to predict scaling requirements and cyber threats using historic and real-time data.
- Configuration management tools : A network contains many components that interface with each other. This results in a lot of configuration parameters to keep track of. Configuration management tools resolve this by providing configuration tools that span across the entire network. They also allow network managers to ensure that all compliance requirements have been fulfilled.
- IP address managers : Bigger networks need to have an IP address manager (IPAM) to plan, track, and manage information associated with a network’s IP addresses.
- Security solutions : Firewalls , content filtering systems , intrusion detection and prevention systems—these are all tools that safeguard networks that are carrying increasingly sensitive loads. No network is complete without them. However, just acquiring these tools is not enough. They must also be properly placed within the network. For example, a firewall must be placed at every network junction. Anti-DDoS devices must be placed at the perimeters of the network. Load balancers need to be placed at strategic locations based on the infrastructure, such as before a cluster of database servers. This must be an explicit part of the network architecture.
4. Establish baseline network & abnormal behavior
A baseline allows admins to know how the network normally behaves in terms of traffic, user accesses, etc. With an established baseline, alerts can be set up in appropriate places to flag anomalies immediately. The normal range of behavior must be documented at both, user and organizational levels. Data required for the baseline can be acquired from routers, switches, firewalls, wireless APs, sniffers, and dedicated collectors.
5. Protect the network from insider threats
Firewalls and intrusion prevention systems ensure that bad actors remain out of the network. However, insider threats need to be addressed as well, particularly with cybercriminals targeting those with access to the network using various social engineering ploys. One way of doing this is to operate on a least-privilege model for access management and control. Another is to use stronger authentication mechanisms such as single sign-on (SSO) and two-factor authentication (2FA) . Besides this, employees also need to undergo regular training to deal with security threats. Proper escalation processes must be documented and circulated widely.
6. Use multiple vendors for added security
While it makes sense to stick to one hardware vendor, a diverse range of network security tools is a major plus for a large network. Security is a dynamic and ever-involving landscape. Hardware advancements are rapid and cyber threats also evolve with them. It is impossible for one vendor to be up to date on all threats. Additionally, different intrusion detection solutions use different detection algorithms. A good mix of these tools strengthens security; however, you must ensure that they are compatible and allow for common logging and interfacing.
7. Segregate the network
Enterprise networks can become large and clunky. Segregation allows them to be divided into logical or functional units, called zones. Segregation is usually done using switches, routers, and virtual LAN solutions. One advantage of a segregated network is that it reduces potential damage from a cyberattack and keeps critical resources out of harm’s way. Another plus is that it allows for more functional classification of networks, such as separating programmer needs from human resources needs.
8. Use centralized logging
Centralized logs are key to capturing an overall view of the network. Immediate log analysis can help the security team flag suspicious logins and IT admin teams to spot overwhelmed systems in the network.
9. Consider using honeypots & honeynets
Honeypots are separate systems that appear to have legitimate processes and data but are actually a decoy for insider and outsider threats. Any breach of this system does not cause the loss of any real data. A honeynet is a fake network segment for the same cause. While this may come at an additional cost to the network, it allows the security team to keep an eye out for malicious players and make appropriate adjustments.
10. Automate wherever possible
New devices are added to systems regularly, and old ones are retired. Users and access controls keep changing frequently. All of these must be automated to ensure that human error does not occur and there are no vulnerable zombie systems in the network, costing money and security. Automation with respect to security is also crucial. It is a good practice to automate responses to attacks, including blocking IP addresses, terminating connections, and gathering additional information about attacks.
See More: What Is Network Security? Definition, Types, and Best Practices
A successful network enhances productivity, security, and innovation with the least overhead costs. This comes only with robust design and implementation with a clear picture of the business needs. While network creation may purely seem like a technical endeavor, it requires business input, especially in the beginning stages. Network management also involves evolving workflows and growing and morphing with evolving technologies.
Did this article help you understand computer networks in detail? Tell us on LinkedIn Opens a new window , Twitter Opens a new window , or Facebook Opens a new window . We would love to hear from you!
MORE ON NETWORKING
- What Is Network Software? Definition, Types, Components, and Best Practices
- What Is Network Hardware? Definition, Architecture, Challenges, and Best Practices
- What Is Network Management? Definition, Key Components, and Best Practices
- Top 10 Network Management and Monitoring Tools in 2022
- Top 10 Best Practices for Network Monitoring in 2022
Share This Article:
IT Specialist

Recommended Reads

The Future is Flexible: The Key to Modernizing the Telecom Industry

An Intentional Approach to Reducing Tool Proliferation

What Is a Fully Qualified Domain Name (FQDN)? Meaning, Elements, Importance, and Examples

Future Trends of AI-driven Network Optimization

What Is Universal Asynchronous Receiver-Transmitter (UART)? Meaning, Working, Models, and Uses

On-premise to 5G-powered SD-WAN: Adaptability for a Future-Proof Network

- My presentations
Auth with social network:
Download presentation
We think you have liked this presentation. If you wish to download it, please recommend it to your friends in any social system. Share buttons are a little bit lower. Thank you!
Presentation is loading. Please wait.
TYPES OF NETWORK.
Published by Devyn Pitman Modified over 10 years ago
Similar presentations
Presentation on theme: "TYPES OF NETWORK."— Presentation transcript:

Shape of a Network.

Chapter 4 Computer Networks

Data Communications and Networking

COMPUTER NETWORK TOPOLOGIES

Computer Network Topologies
Networks & Components Discuss the components required for successful communications Explain the purpose of communications software Identify various sending.

Nilesh Agre Wedashree Jalukar Neelima Shahi Group Members.

INTRODUCTION TO COMPUTER NETWORKS Zeeshan Abbas. Introduction to Computer Networks INTRODUCTION TO COMPUTER NETWORKS.

Saeed Darvish Pazoki – MCSE, CCNA Abstracted From: Sybex – Network+ Study Guide Network Fundamentals 1.

Network Topologies CS 1202.
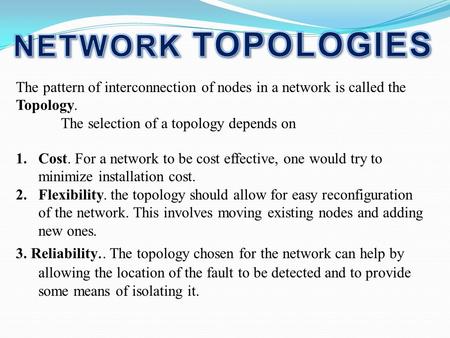
NETWORK TOPOLOGIES The pattern of interconnection of nodes in a network is called the Topology. The selection of a topology depends on Cost. For a network.

Shalini Bhavanam. Key words: Basic Definitions Classification of Networks Types of networks Network Topologies Network Models.

1 Chapter 9 Computer Networks. 2 Chapter Topics OSI network layers Network Topology Media access control Addressing and routing Network hardware Network.

Network topology.

1 Chapter 10 Introduction to Metropolitan Area Networks and Wide Area Networks Data Communications and Computer Networks: A Business User’s Approach.

Introduction to Metropolitan Area Networks and Wide Area Networks TDC 362 / TDC 460.

Copyright©2008 N.AlJaffan®KSU1 Chapter 8 Communications and Networks.

Core 3: Communication Systems. On any network there are two types of computers present – servers and clients. By definition Client-Server architecture.

INTRODUCTION TO COMPUTER NETWORKS INTRODUCTION Lecture # 1 (
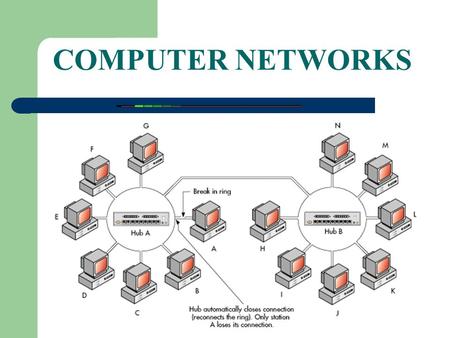
COMPUTER NETWORKS.
About project
© 2024 SlidePlayer.com Inc. All rights reserved.
We have the answers to your questions! - Don't miss our next open house about the data universe!

Network protocols are rules and standards that enable computers to communicate with each other and share data. These protocols are used in different types of networks, such as the local area network (LAN) and the wide area network (WAN), to ensure communication and collaboration between users.
But what are network protocols? Why are they important? What are the different types of network protocol? Answers to your questions in this article.
What is a network protocol?
Before delving into the details, it is important to understand what a network protocol is. A network protocol is a standard or set of rules that defines how computers communicate with each other.
Network protocols define the data formats, message types, authentication methods and access control methods that are used to ensure secure and reliable communication.
They are essential for communication between computers and thousands of different protocols have been developed over time.
What role do network protocols play in communication?
Network protocols are essential for communication between computers, as they enable standardised and efficient messages to be sent.
Without network protocols, computers would find it difficult to communicate consistently and reliably. They also guarantee the security and confidentiality of data.
There are different types of network protocol, each with its own characteristics and functions. For example, TCP (Transmission Control Protocol) is used to ensure reliable communication between computers, while UDP (User Datagram Protocol) is used for faster but less reliable communication.
In addition, network protocols are used in many fields, such as telecommunications, computing, industry and medicine. For example, DICOM (Digital Imaging and Communications in Medicine) is used for medical images, while VoIP (Voice over Internet Protocol) is used for voice communications over the Internet.
Network protocols are often detailed according to the OSI layer to which they belong.
The layers of the OSI model
The OSI (Open Systems Interconnection) model is a representation of Internet working communications. Most network protocols are based on the OSI model . It contains 7 layers:
- The application layer: the human-computer interaction layer, which enables applications to access network services.
- The presentation layer: encodes and decodes data, ensuring that data can be used in different systems.
- The session layer: maintains connections and manages user sessions.
- The transport layer: manages protocol delivery (more on this in the next section).
- The network layer: routes data through suitable network resources.
- The data link layer: defines the format of the data on the network.
- The physical layer: defines the electrical, mechanical and optical characteristics. It acts as the interface between the network and the devices.
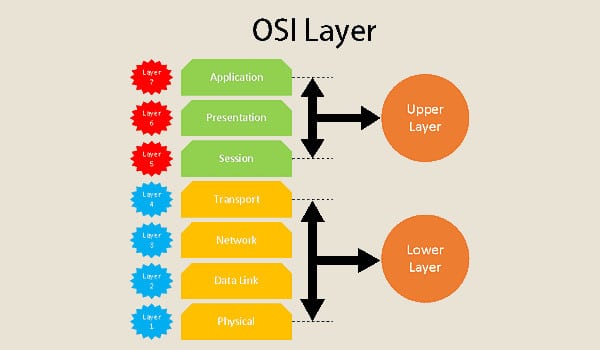
Related articles
What is the Grad CAM method?

Demystifying Regular Expressions (Regex): Definition and Practical Usage

Kubernetes training: Learn how to use this orchestration tool
What is automatic learning?

Get monthly insider insights from experts directly in your mailbox
Network Powerpoint Templates and Google Slides Themes
Discover a wide range of professionally designed presentation templates tailored to showcase your network and captivate your audience.
Explore Free Network Presentation Templates

Retro SEO Specialist Resume
Boost your portfolio with our colourful, retro Y2K inspired PowerPoint template. This pastel-hued design is perfect for education, marketing, or ... Read more

Illustrated Blue Connections
Dive into Blue-Inspired corporate powerpoints, perfect for modern businesses, schools, and tech-savvy individuals. These powerpoint and google slides templates, designed ... Read more

Blue Connections
Create a professional presentation fast with this easy-to-edit and free template. The background design fits social media, connection, internet or science related topics. ... Read more

Tech Illustrated
Give a presentation on cloud computing, SaaS development, servers and networks, cyber security or other technology related topics with this free template. It includes a set of isometric techie illustrations that you can arrange to explain specific concepts. ... Read more

Technology Connections
If you need to create a presentation about internet, blockchain, machine learning, cloud computing or other technology related topics, then this theme is perfect for the job. ... Read more

Hexagonal Tech
With an hexagons and icons pattern this theme is great for techy content. A dark background and bright blue color palette gives a professional look, so you can use it in business and corporate meetings. ... Read more
Professional designs for your presentations
SlidesCarnival templates have all the elements you need to effectively communicate your message and impress your audience.
Suitable for PowerPoint and Google Slides
Download your presentation as a PowerPoint template or use it online as a Google Slides theme. 100% free, no registration or download limits.
- Google Slides
- Editor’s Choice
- All Templates
- Frequently Asked Questions
- Google Slides Help
- PowerPoint help
- Who makes SlidesCarnival?
Our approach
- Responsibility
- Infrastructure
- Try Meta AI
RECOMMENDED READS
- 5 Steps to Getting Started with Llama 2
- The Llama Ecosystem: Past, Present, and Future
- Introducing Code Llama, a state-of-the-art large language model for coding
- Meta and Microsoft Introduce the Next Generation of Llama
- Today, we’re introducing Meta Llama 3, the next generation of our state-of-the-art open source large language model.
- Llama 3 models will soon be available on AWS, Databricks, Google Cloud, Hugging Face, Kaggle, IBM WatsonX, Microsoft Azure, NVIDIA NIM, and Snowflake, and with support from hardware platforms offered by AMD, AWS, Dell, Intel, NVIDIA, and Qualcomm.
- We’re dedicated to developing Llama 3 in a responsible way, and we’re offering various resources to help others use it responsibly as well. This includes introducing new trust and safety tools with Llama Guard 2, Code Shield, and CyberSec Eval 2.
- In the coming months, we expect to introduce new capabilities, longer context windows, additional model sizes, and enhanced performance, and we’ll share the Llama 3 research paper.
- Meta AI, built with Llama 3 technology, is now one of the world’s leading AI assistants that can boost your intelligence and lighten your load—helping you learn, get things done, create content, and connect to make the most out of every moment. You can try Meta AI here .
Today, we’re excited to share the first two models of the next generation of Llama, Meta Llama 3, available for broad use. This release features pretrained and instruction-fine-tuned language models with 8B and 70B parameters that can support a broad range of use cases. This next generation of Llama demonstrates state-of-the-art performance on a wide range of industry benchmarks and offers new capabilities, including improved reasoning. We believe these are the best open source models of their class, period. In support of our longstanding open approach, we’re putting Llama 3 in the hands of the community. We want to kickstart the next wave of innovation in AI across the stack—from applications to developer tools to evals to inference optimizations and more. We can’t wait to see what you build and look forward to your feedback.
Our goals for Llama 3
With Llama 3, we set out to build the best open models that are on par with the best proprietary models available today. We wanted to address developer feedback to increase the overall helpfulness of Llama 3 and are doing so while continuing to play a leading role on responsible use and deployment of LLMs. We are embracing the open source ethos of releasing early and often to enable the community to get access to these models while they are still in development. The text-based models we are releasing today are the first in the Llama 3 collection of models. Our goal in the near future is to make Llama 3 multilingual and multimodal, have longer context, and continue to improve overall performance across core LLM capabilities such as reasoning and coding.
State-of-the-art performance
Our new 8B and 70B parameter Llama 3 models are a major leap over Llama 2 and establish a new state-of-the-art for LLM models at those scales. Thanks to improvements in pretraining and post-training, our pretrained and instruction-fine-tuned models are the best models existing today at the 8B and 70B parameter scale. Improvements in our post-training procedures substantially reduced false refusal rates, improved alignment, and increased diversity in model responses. We also saw greatly improved capabilities like reasoning, code generation, and instruction following making Llama 3 more steerable.

*Please see evaluation details for setting and parameters with which these evaluations are calculated.
In the development of Llama 3, we looked at model performance on standard benchmarks and also sought to optimize for performance for real-world scenarios. To this end, we developed a new high-quality human evaluation set. This evaluation set contains 1,800 prompts that cover 12 key use cases: asking for advice, brainstorming, classification, closed question answering, coding, creative writing, extraction, inhabiting a character/persona, open question answering, reasoning, rewriting, and summarization. To prevent accidental overfitting of our models on this evaluation set, even our own modeling teams do not have access to it. The chart below shows aggregated results of our human evaluations across of these categories and prompts against Claude Sonnet, Mistral Medium, and GPT-3.5.

Preference rankings by human annotators based on this evaluation set highlight the strong performance of our 70B instruction-following model compared to competing models of comparable size in real-world scenarios.
Our pretrained model also establishes a new state-of-the-art for LLM models at those scales.

To develop a great language model, we believe it’s important to innovate, scale, and optimize for simplicity. We adopted this design philosophy throughout the Llama 3 project with a focus on four key ingredients: the model architecture, the pretraining data, scaling up pretraining, and instruction fine-tuning.
Model architecture
In line with our design philosophy, we opted for a relatively standard decoder-only transformer architecture in Llama 3. Compared to Llama 2, we made several key improvements. Llama 3 uses a tokenizer with a vocabulary of 128K tokens that encodes language much more efficiently, which leads to substantially improved model performance. To improve the inference efficiency of Llama 3 models, we’ve adopted grouped query attention (GQA) across both the 8B and 70B sizes. We trained the models on sequences of 8,192 tokens, using a mask to ensure self-attention does not cross document boundaries.
Training data
To train the best language model, the curation of a large, high-quality training dataset is paramount. In line with our design principles, we invested heavily in pretraining data. Llama 3 is pretrained on over 15T tokens that were all collected from publicly available sources. Our training dataset is seven times larger than that used for Llama 2, and it includes four times more code. To prepare for upcoming multilingual use cases, over 5% of the Llama 3 pretraining dataset consists of high-quality non-English data that covers over 30 languages. However, we do not expect the same level of performance in these languages as in English.
To ensure Llama 3 is trained on data of the highest quality, we developed a series of data-filtering pipelines. These pipelines include using heuristic filters, NSFW filters, semantic deduplication approaches, and text classifiers to predict data quality. We found that previous generations of Llama are surprisingly good at identifying high-quality data, hence we used Llama 2 to generate the training data for the text-quality classifiers that are powering Llama 3.
We also performed extensive experiments to evaluate the best ways of mixing data from different sources in our final pretraining dataset. These experiments enabled us to select a data mix that ensures that Llama 3 performs well across use cases including trivia questions, STEM, coding, historical knowledge, etc.
Scaling up pretraining
To effectively leverage our pretraining data in Llama 3 models, we put substantial effort into scaling up pretraining. Specifically, we have developed a series of detailed scaling laws for downstream benchmark evaluations. These scaling laws enable us to select an optimal data mix and to make informed decisions on how to best use our training compute. Importantly, scaling laws allow us to predict the performance of our largest models on key tasks (for example, code generation as evaluated on the HumanEval benchmark—see above) before we actually train the models. This helps us ensure strong performance of our final models across a variety of use cases and capabilities.
We made several new observations on scaling behavior during the development of Llama 3. For example, while the Chinchilla-optimal amount of training compute for an 8B parameter model corresponds to ~200B tokens, we found that model performance continues to improve even after the model is trained on two orders of magnitude more data. Both our 8B and 70B parameter models continued to improve log-linearly after we trained them on up to 15T tokens. Larger models can match the performance of these smaller models with less training compute, but smaller models are generally preferred because they are much more efficient during inference.
To train our largest Llama 3 models, we combined three types of parallelization: data parallelization, model parallelization, and pipeline parallelization. Our most efficient implementation achieves a compute utilization of over 400 TFLOPS per GPU when trained on 16K GPUs simultaneously. We performed training runs on two custom-built 24K GPU clusters . To maximize GPU uptime, we developed an advanced new training stack that automates error detection, handling, and maintenance. We also greatly improved our hardware reliability and detection mechanisms for silent data corruption, and we developed new scalable storage systems that reduce overheads of checkpointing and rollback. Those improvements resulted in an overall effective training time of more than 95%. Combined, these improvements increased the efficiency of Llama 3 training by ~three times compared to Llama 2.
Instruction fine-tuning
To fully unlock the potential of our pretrained models in chat use cases, we innovated on our approach to instruction-tuning as well. Our approach to post-training is a combination of supervised fine-tuning (SFT), rejection sampling, proximal policy optimization (PPO), and direct preference optimization (DPO). The quality of the prompts that are used in SFT and the preference rankings that are used in PPO and DPO has an outsized influence on the performance of aligned models. Some of our biggest improvements in model quality came from carefully curating this data and performing multiple rounds of quality assurance on annotations provided by human annotators.
Learning from preference rankings via PPO and DPO also greatly improved the performance of Llama 3 on reasoning and coding tasks. We found that if you ask a model a reasoning question that it struggles to answer, the model will sometimes produce the right reasoning trace: The model knows how to produce the right answer, but it does not know how to select it. Training on preference rankings enables the model to learn how to select it.
Building with Llama 3
Our vision is to enable developers to customize Llama 3 to support relevant use cases and to make it easier to adopt best practices and improve the open ecosystem. With this release, we’re providing new trust and safety tools including updated components with both Llama Guard 2 and Cybersec Eval 2, and the introduction of Code Shield—an inference time guardrail for filtering insecure code produced by LLMs.
We’ve also co-developed Llama 3 with torchtune , the new PyTorch-native library for easily authoring, fine-tuning, and experimenting with LLMs. torchtune provides memory efficient and hackable training recipes written entirely in PyTorch. The library is integrated with popular platforms such as Hugging Face, Weights & Biases, and EleutherAI and even supports Executorch for enabling efficient inference to be run on a wide variety of mobile and edge devices. For everything from prompt engineering to using Llama 3 with LangChain we have a comprehensive getting started guide and takes you from downloading Llama 3 all the way to deployment at scale within your generative AI application.
A system-level approach to responsibility
We have designed Llama 3 models to be maximally helpful while ensuring an industry leading approach to responsibly deploying them. To achieve this, we have adopted a new, system-level approach to the responsible development and deployment of Llama. We envision Llama models as part of a broader system that puts the developer in the driver’s seat. Llama models will serve as a foundational piece of a system that developers design with their unique end goals in mind.

Instruction fine-tuning also plays a major role in ensuring the safety of our models. Our instruction-fine-tuned models have been red-teamed (tested) for safety through internal and external efforts. Our red teaming approach leverages human experts and automation methods to generate adversarial prompts that try to elicit problematic responses. For instance, we apply comprehensive testing to assess risks of misuse related to Chemical, Biological, Cyber Security, and other risk areas. All of these efforts are iterative and used to inform safety fine-tuning of the models being released. You can read more about our efforts in the model card .
Llama Guard models are meant to be a foundation for prompt and response safety and can easily be fine-tuned to create a new taxonomy depending on application needs. As a starting point, the new Llama Guard 2 uses the recently announced MLCommons taxonomy, in an effort to support the emergence of industry standards in this important area. Additionally, CyberSecEval 2 expands on its predecessor by adding measures of an LLM’s propensity to allow for abuse of its code interpreter, offensive cybersecurity capabilities, and susceptibility to prompt injection attacks (learn more in our technical paper ). Finally, we’re introducing Code Shield which adds support for inference-time filtering of insecure code produced by LLMs. This offers mitigation of risks around insecure code suggestions, code interpreter abuse prevention, and secure command execution.
With the speed at which the generative AI space is moving, we believe an open approach is an important way to bring the ecosystem together and mitigate these potential harms. As part of that, we’re updating our Responsible Use Guide (RUG) that provides a comprehensive guide to responsible development with LLMs. As we outlined in the RUG, we recommend that all inputs and outputs be checked and filtered in accordance with content guidelines appropriate to the application. Additionally, many cloud service providers offer content moderation APIs and other tools for responsible deployment, and we encourage developers to also consider using these options.
Deploying Llama 3 at scale
Llama 3 will soon be available on all major platforms including cloud providers, model API providers, and much more. Llama 3 will be everywhere .
Our benchmarks show the tokenizer offers improved token efficiency, yielding up to 15% fewer tokens compared to Llama 2. Also, Group Query Attention (GQA) now has been added to Llama 3 8B as well. As a result, we observed that despite the model having 1B more parameters compared to Llama 2 7B, the improved tokenizer efficiency and GQA contribute to maintaining the inference efficiency on par with Llama 2 7B.
For examples of how to leverage all of these capabilities, check out Llama Recipes which contains all of our open source code that can be leveraged for everything from fine-tuning to deployment to model evaluation.
What’s next for Llama 3?
The Llama 3 8B and 70B models mark the beginning of what we plan to release for Llama 3. And there’s a lot more to come.
Our largest models are over 400B parameters and, while these models are still training, our team is excited about how they’re trending. Over the coming months, we’ll release multiple models with new capabilities including multimodality, the ability to converse in multiple languages, a much longer context window, and stronger overall capabilities. We will also publish a detailed research paper once we are done training Llama 3.
To give you a sneak preview for where these models are today as they continue training, we thought we could share some snapshots of how our largest LLM model is trending. Please note that this data is based on an early checkpoint of Llama 3 that is still training and these capabilities are not supported as part of the models released today.

We’re committed to the continued growth and development of an open AI ecosystem for releasing our models responsibly. We have long believed that openness leads to better, safer products, faster innovation, and a healthier overall market. This is good for Meta, and it is good for society. We’re taking a community-first approach with Llama 3, and starting today, these models are available on the leading cloud, hosting, and hardware platforms with many more to come.
Try Meta Llama 3 today
We’ve integrated our latest models into Meta AI, which we believe is the world’s leading AI assistant. It’s now built with Llama 3 technology and it’s available in more countries across our apps.
You can use Meta AI on Facebook, Instagram, WhatsApp, Messenger, and the web to get things done, learn, create, and connect with the things that matter to you. You can read more about the Meta AI experience here .
Visit the Llama 3 website to download the models and reference the Getting Started Guide for the latest list of all available platforms.
You’ll also soon be able to test multimodal Meta AI on our Ray-Ban Meta smart glasses.
As always, we look forward to seeing all the amazing products and experiences you will build with Meta Llama 3.
Our latest updates delivered to your inbox
Subscribe to our newsletter to keep up with Meta AI news, events, research breakthroughs, and more.
Join us in the pursuit of what’s possible with AI.

Product experiences
Foundational models
Latest news
Meta © 2024

IMAGES
VIDEO
COMMENTS
4. Local Area Network (LAN) • A LAN is a network that is used for communicating among computer devices, usually within an office building or home. • LAN's enable the sharing of resources such as files or hardware devices that may be needed by multiple users. • Is limited in size, typically spanning a few hundred meters, and no more than a mile.
Personal Area Network (PAN) •A personal area network (PAN) is a computer network used for communication among computer devices, including telephones and personal digital assistants, in proximity to an individual's body. •The devices may or may not belong to the person in question. The reach of a PAN is typically a few meters.
The best-known computer network is the internet. 3. Based on the size and the coverage area, networks are categorized into the following types: Personal Area Networks (PANs) Local Area Networks (LANs) Metropolitan Area Networks (MANs) Wide Area Networks (WANs) 4. A personal area network (PAN) is a computer network used for communication among ...
• A network refers to two or more connected computers that can share resources such as data, a printer, an Internet connection, applications, or a combination of these ... Presentation Session Transport Network Data Link ... MAN and WAN networks • Possible media types for LAN and WAN connections
Lecture 13: Introduction to Networking Networking is simply communicating between two computers connected on a network. You can actually set up a network connection on a single computer, as well. A network requires one computer to act as the server , waiting patiently for an incoming connection from another computer, the client .
To learn the fundamentals of computer networks 2. Learn how the Internet works • What really happens when you "browse the web"? • TCP/IP, DNS, HTTP, NAT, VPNs, 802.11 etc. 3. Understand why the internet is designed how it is designed • SDN, Load Balancers, Architectures.
Google Classroom. The Internet is the world's largest computer network. Let's break that down: A computer network is any group of interconnected computing devices capable of sending or receiving data. A computing device isn't just a computer—it's any device that can run a program, such as a tablet, phone, or smart sensor.
An Introduction to Computer Networksis a free and open general-purpose computer-networking textbook, complete with diagrams and exercises.It covers the LAN, internetworking and transport layers, focusing primarily on TCP/IP. Particular attention is paid to congestion; other special topics include queuing, real-time traffic, network management, security and the ns simulator.
These are explained below. 1. Personal Area Network (PAN) PAN is the most basic type of computer network. This network is restrained to a single person, that is, communication between the computer devices is centered only on an individual's workspace. PAN offers a network range of 1 to 100 meters from person to device providing communication.
Introduction To Computer Networking. A computer network is a set of computers connected together for the purpose of sharing resources. The most common resource shared today is connection to the Internet. Other shared resources can include a printer or a file server.
The computers on a network may be linked through cables, telephone lines, radio waves, satellites, or infrared light beams. 3 Different Types of Networks. Depending upon the geographical area covered by a network, it is classified as: Local Area Network (LAN) Metropolitan Area Network (MAN) Wide Area Network (WAN) Personal Area Network (PAN)
Learning objectives. In this module, you will: List the different network protocols and network standards. List the different network types and topologies. List the different types of network devices used in a network. Describe network communication principles like TCP/IP, DNS, and ports. Describe how these core components map to Azure networking.
1 TYPES OF NETWORKS Three types of networks: 1. Local Area Network (LAN) 2. Metropolitan Area Network (MAN) 3. Wide Area Network (WAN) 2 LAN Local Area NEtwork. . 1.Covers a small region of space, typically a single building. . 2. LAN is the smallest network compared to other two networks.
Download presentation. Presentation on theme: "Chapter 1: Introduction to Networks and Networking Concepts."—. Presentation transcript: 1 Chapter 1: Introduction to Networks and Networking Concepts. 2 Guide to Networking Essentials, Fourth Edition2 Learning Objectives Understand basic networked communications and services Identify essential ...
Introduction to Computer Network Dr. Rania R Ziedan. Agenda • Introduction • Network types • Network topology • Network connection models • OSI model. Computer network • A collection of computing devices that are connected in various ways in order to communicate and share resources or files • Wired network: the connections between computers in a network are made using physical ...
Types of Computer Networks. Computer networks can be classified based on several criteria, such as the transmission medium, the network size, the topology, and organizational intent. Based on a geographical scale, the different types of networks are: Nanoscale networks: These networks enable communication between minuscule sensors and actuators.
1 TYPES OF NETWORK. 2 A computer network, often simply referred to as a network, is a collection of computers and devices interconnected by communications channels that facilitate communications among users and allows users to share resources. 3 LAN - Local Area Network. A LAN connects network devices over a relatively short distance.
As for the presentation and session layer network protocols, two of them are worth knowing: RPC (session): used to request a service from a program located in another remote computer via a network, without having to understand the details of the network. LPP (presentation): used for simplified support of applications based on TCP/IP networks.
This diagram slide has been designed with graphic of computer network and devices. This diagram contains the wireless and wired networking of computers. Download this diagram for computer networking related topics and to build professional presentation for your viewers. Slide 1 of 3.
Suitable for PowerPoint and Google Slides. Download your presentation as a PowerPoint template or use it online as a Google Slides theme. 100% free, no registration or download limits. Get these network templates to create dynamic presentations that showcase the interconnectedness of your ideas. No Download Limits Free for Any Use No Signups.
Today, we're introducing Meta Llama 3, the next generation of our state-of-the-art open source large language model. Llama 3 models will soon be available on AWS, Databricks, Google Cloud, Hugging Face, Kaggle, IBM WatsonX, Microsoft Azure, NVIDIA NIM, and Snowflake, and with support from hardware platforms offered by AMD, AWS, Dell, Intel ...