Log in to ask questions, share your expertise, or stay connected to content. Don’t have a login? Join now .

- Community Home
- Topic Thread

- Discussion 60.4K
- Library 1.9K

Dynamic VLAN assignment with a single enforcement profile
1. dynamic vlan assignment with a single enforcement profile.

I would like to dynamically assign a VLAN to a port without having an enforcement profile by using a variable for assigning the vlan.
my question is which variable I could/should use for that?
Is this possible via assigning a user role? If not, is there any other way I could assign a value to a variable during the authentication process and use that value for the vlan assignment?
2. RE: Dynamic VLAN assignment with a single enforcement profile
Try this: https://community.arubanetworks.com/t5/Security/ClearPass-best-practice-assigning-VLANs-with-multiple-sites/td-p/227426
3. RE: Dynamic VLAN assignment with a single enforcement profile
Hi cjoseph,
thanks for the link. That is actually the link that I found before that let me think this might be possible. However in that link the VLAN is preconfigured on the device, a switch.
I want to use this for users though, so if a user is authenticated the process would "somehow" pass the vlan-id value to the enforcement profile via a variable.... this "somehow" is unclear for me though how I could achieve this
4. RE: Dynamic VLAN assignment with a single enforcement profile
What exactly is your situation? I don't want to send you alot of information without knowing your problem.
5. RE: Dynamic VLAN assignment with a single enforcement profile
maybe I explained it too complicated, sorry.
I want to authenticate users via dot1x and MAB and assign the correct VLAN, a basic use case.
however I would like to avoid creating an enforcement profile for every single VLAN I would assign, I would much rather use a "Dynamic VLAN assignment" enforcement profile which would use a variable as the VLAN which I could somehow assign during the authentication process.
6. RE: Dynamic VLAN assignment with a single enforcement profile
What would determine the VLAN, then, the user group membership in AD?
7. RE: Dynamic VLAN assignment with a single enforcement profile
that depends on various things, could be a certain field in the certificate, the hostname, the AD user group or mac address. I would still need to "manually" assign the VLAN name/id but this way I could get by with a single enforcement profile and not have so much clutter...
using many enforcement profiles would work but doing it with a variable that gets assigned during the process is much cooler with a single enforcement profile
8. RE: Dynamic VLAN assignment with a single enforcement profile
@cjoseph is there a way to do this or do I have to stay with one enforcement profile per VLAN?
9. RE: Dynamic VLAN assignment with a single enforcement profile
I would need a detailed example to answer that. The regular if/then for roles and enforcement policies allows you to assign a VLAN. If you combine that with the namespaces in the link that I sent before, you can set VLANs based on the switch/device that the user is connected to.
10. RE: Dynamic VLAN assignment with a single enforcement profile
Example (location/switch independent!):
Laptop1 with company computer certificate XYZ connects and needs to go into VLAN 100.
Laptop2 with company computer certificate XYZ and hostname starting with ABC needs to go into VLAN101
Laptop3 with company computer certificate ZZZ connects and needs to go into VLAN102
Laptop4 without certificate but in local MAB database connects and needs to go into VLAN99
now is this possible with a single enforcement profile by assigning some kind of variable during the process that the enforcement profile can use?
11. RE: Dynamic VLAN assignment with a single enforcement profile
So would an attribute on the certificate would be the variable?
12. RE: Dynamic VLAN assignment with a single enforcement profile
no, i would need to create the variable in the process, e.g. with some rules?
I would still have the "manual" mapping of the VLAN but wouldnt have the clutter of several enforcement profiles.
if its not doable its no issue, I will stay with multiple enforcement profiles, i just thought after reading that post, that this might be doable.
13. RE: Dynamic VLAN assignment with a single enforcement profile
@cjoseph possible or does it need one profile per VLAN?
14. RE: Dynamic VLAN assignment with a single enforcement profile
@cjoseph possible?
15. RE: Dynamic VLAN assignment with a single enforcement profile
I honestly have re-read this thread twice to try to give you a good answer. Can you please give me a real-world example of what you are trying to do? Maybe I am just not understanding.
16. RE: Dynamic VLAN assignment with a single enforcement profile
Hi cjoseph, sorry, this was the real-world example...
I can try to re-explain with a more elaborate but fictional example:
MAC Authentication for all devices:
- if the MAC contains aabb then the device should go into VLAN 123
- if the MAC contains bbcc then the device should go into VLAN 234
- if the MAC contains ccdd then the device should go into VLAN 345
- if the MAC contains ddee then the device should go into VLAN 654
I can do this with four different Enforcement Profiles without an issue....
is there a way to do this with a single Enforcement profile instead somehow with the use of some kind of variable?
17. RE: Dynamic VLAN assignment with a single enforcement profile
@cjoseph am I explaining it too complicated?
18. RE: Dynamic VLAN assignment with a single enforcement profile
You would need only a single enforcement profile policy . You would need 4 lines in your policy statement, however...
19. RE: Dynamic VLAN assignment with a single enforcement profile
yes, that would be exactly what I would be looking for!
how could I do this?
20. RE: Dynamic VLAN assignment with a single enforcement profile
So an enforcement policy is a rule or list of rules to be checked to do an action. Enforcement profiles are what gets sent to a device to make that change. Essentially, you will have a single enforcement policy but 4 enforcement profiles tied to those policies, depending on what you want to send:

21. RE: Dynamic VLAN assignment with a single enforcement profile
yes, thats what I have now but was wondering if I could use just a single enforcement profile and pass the vlan ID somehow via a variable that is set during authorization?
22. RE: Dynamic VLAN assignment with a single enforcement profile
23. re: dynamic vlan assignment with a single enforcement profile.
How would the VLAN variable be defined? What would it be tied to, a location or a network device? How many different VLANs are we talking?
24. RE: Dynamic VLAN assignment with a single enforcement profile
Well, that was actually my question... is it possible and if so, how would the variable be defined during authorization.
Number of VLANs should of course be scalable.
I am guessing from the looks of it, it would work if the attribute is already assigned to the endpoint but not if it should be dynamically assigned as e.g. per the example I wrote.
25. RE: Dynamic VLAN assignment with a single enforcement profile
As far as I know that is correct.
New Best Answer

- Environmental Citizenship
- Support Services
- Contact Support
- Training & Certification
- Software Downloads
- Licensing Login
- Find a Partner
- Become a Partner
- Partner Ready for Networking
- Technology Partner Programs
- Privacy policy
- Terms of service
© Copyright 2024 Hewlett Packard Enterprise Development LP All Rights Reserved.
Meraki Community
- Community Platform Help
- Contact Community Team
- Meraki Documentation
- Meraki DevNet Developer Hub
- Meraki System Status
- Technical Forums
Dynamic VLAN Assignment on MR
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Report Inappropriate Content
Solved! Go to solution.

View solution in original post
- All forum topics
- Previous Topic

- New May 24: Community Platform Update: Nav updates, full-width UI
- May 13: [CONTEST CLOSED] Join us in some fun wordplay for National Limerick Day, hooray!
- May 7: Community Platform Update: Reducing space within content
- Installation 209
- Interference 77
- RF Spectrum 97
- Community guidelines
- Cisco privacy
- Khoros privacy
- Terms of service
- Aruba Network
Dynamic port configuration in Aruba OS-CX switches
Aruba's OS-CX switches have the ability to profile devices connected to ports and dynamically assign roles and policies (ACLs) to those ports. The ACLs can include the usual stuff--filtering on source, destination and protocol. But, they can also include configuration parameters like VLAN assignment.
Here's a simple example that can be useful when deploying access points with bridged VLANs. In this example, the switch makes a profile of the connected device using LLDP (you can use CDP, too), parses the response and assigns a role to the port. The role has policies that assign VLANs.
To see how this would work, let’s say that we have an access point on port 1/1/10. Examining the LLDP query on the port, we get the following:
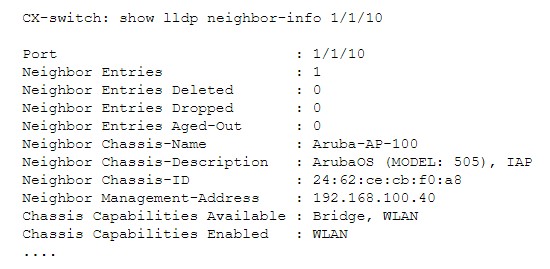
In our test for the presence of an AP, we will search the description for "IAP". To make the example a little more interesting, we will also skip any AP-305s we might find. The following are rules that will match our LLDP port access test. These are arranged like a sieve; the first pattern that matches wins.
Next, we define the role and the policies that we want to associate with access points that match the above port-access tests. The block below says that the role is called "lldp-AP," and that the policies "create a trunk and allow VLANs 12,22,40 and 100, and make 100 be the native VLAN."
This last section is the glue that pulls the port-access tests and the role assignment together. It says "if the device on port x matches AP-lldp-group tests then assign the role of lldp-AP."
Dynamic profiling can be applied to other kinds of devices too, including printers, projectors and phones. When used in conjunction with Aruba Central or NetEdit, elements of the policies and port-access tests can be described using variables, such as this:
When used in conjunction with ClearPass and controllers, the ports can implement enhanced profiling, role assignment and dynamic segmentation whereby VLANs that don’t even exist on the switch can be tunneled from other parts of the organization.
Just another HTMLy user.
Share this post
Related posts.
- The Need for Speed
- Network Segmentation
- AI in your Network
Networking | Cloud | DevOps | IaC
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server is an important element to networking in the real world. User location cannot be predicted as they may be at and out of a desk and up and about should they need to do so. Tying them to a local VLAN may only be helpful if they are bound to desks in those locations, although the most ideal outcome, it is not the most practical.
It is only wise to incorporate IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server in areas where you expect different teams to come to. Meeting rooms could for a moment have the accounting group or the development group meeting there and based on the intelligent and dynamic vlan assignmnet with 802.1x authentication, users port-access are defined their appropriate vlans for their respective access to resources on the network.
How to Provision 802.1 X Authentication Step By Step With Dynamic VLAN Assignment With Windows Radius Server For 802.1x Clients.
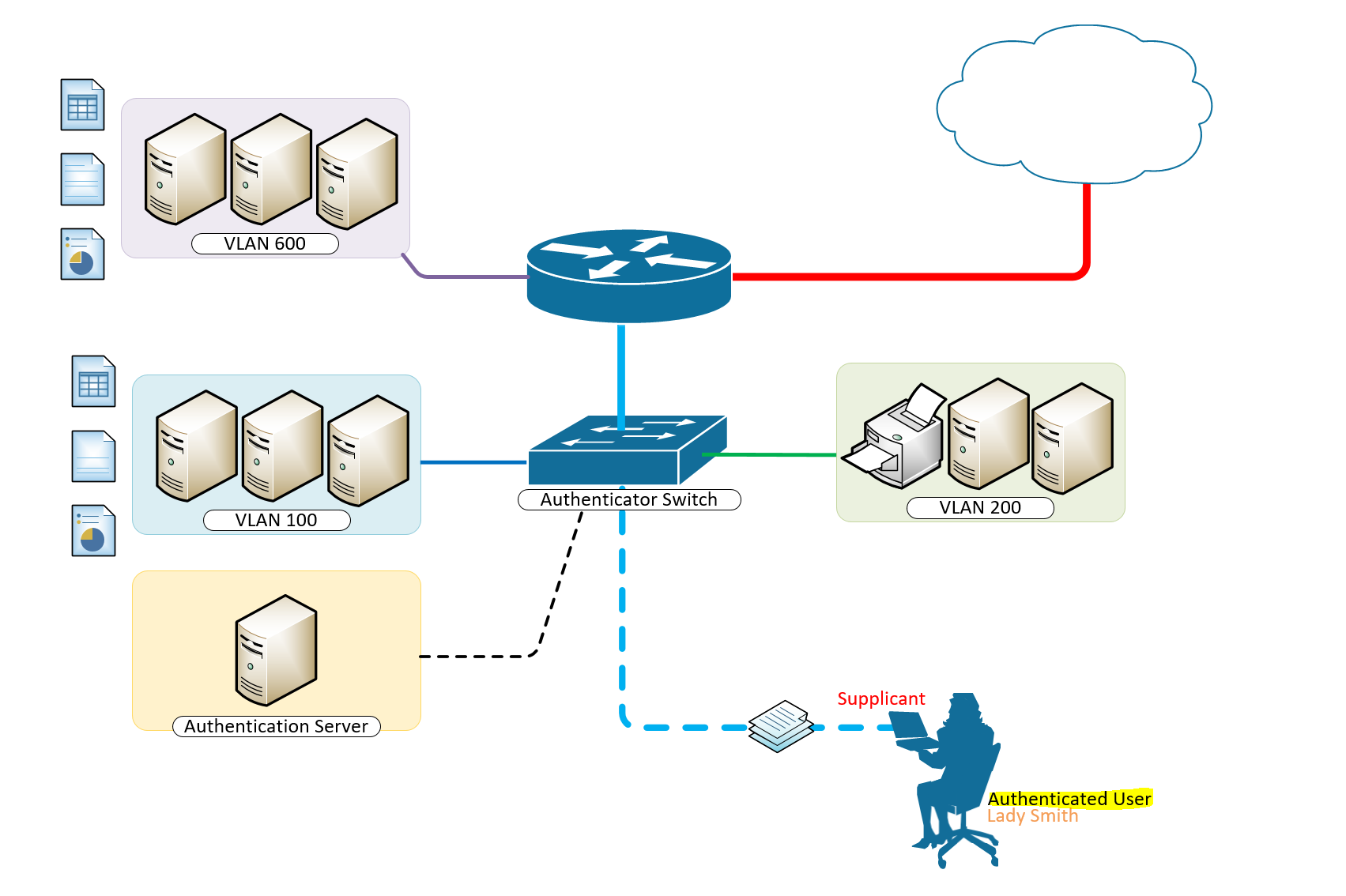
A typical configuration for a system under IEEE 802.1x Authentication control is shown in the following figure.
In this scenario, “Lady Smith” wishes to use services offered by servers on the LAN behind the switch. There are multiple VLANs with resources available based on user vlan membership. Her laptop computer is connected to a port on the Aruba 2920 Edge Switch that has 802.1x port authentication control enabled.
The laptop computer must therefore act in a supplicant role. Message exchanges take place between the supplicant and the authenticator which is the Aruba 2920 Switch, and the authenticator passes the supplicant’s credentials which is her (Windows Active Directory User Account Credentials) to the authentication server for verification. The NPS Server which is the authentication server then informs the authenticator whether or not the authentication attempt succeeded, at which point “Lady Smith” is either granted or denied access to the LAN behind the switch.
Setup Structure for IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
- Supplicant: Laptop running Microsoft Windows 10 or Windows 7
- Authenticator: HP Aruba 2920 Edge Switch
- Authentication Server: Microsoft NPS (Network Policy Server) running on Windows Server 2012 R2.
- User Database : Active Directory
For Windows Infrastructure
Create NPS Server – Add Role on Windows Server 2012 R2
- Create DHCP Scopes for VLANS
Create RADIUS Client on NAC using Network Policy Server
- Create Network Policies
- Configure a Network Policy for VLANs
- Start Wired Auto-Config Service
- Enable Network Authentication
Create the DHCP Scopes for VLAN100 and VLAN200 Groups
- Development Group Scope – VLAN 100
SVI: ip address 172.16.80.254 255.255.255.0 Scope Subnet: 172.16.80.1/24
- Accounting Group Scope – VLAN 200
SVI:ip address 172.16.70.254 255.255.255.0 Scope Subnet: 172.16.70.0/24
Secret Key: secret12
Add Edge Switch Management IP as the RADIUS Client
The Shared Secret Key: secret12 will be used in the Switch Configuration.
Create Network Policy Settings for Accounting Group for VLAN 200
Configuration Example
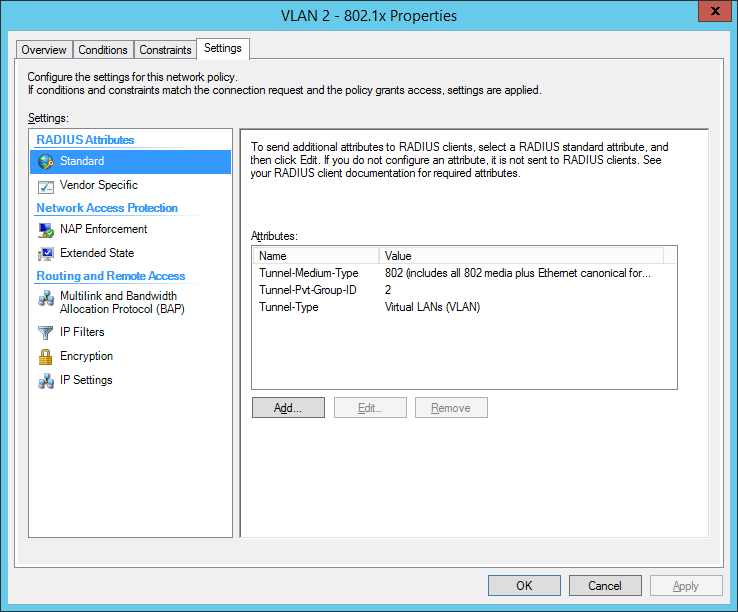
Here’s an example of how you might consider when configuring Microsoft NPS Server to assign users to a VLAN based on their user group, using NPS for the authentication and authorization of users. This configuration has worked flawlessly on the HP Aruba 2920 Switch. The key to getting this to work is the use of a RADIUS element called: ‘Tunnel-PVT-Group-ID’. This is a RADIUS attribute that may be passed back to the authenticator (i.e. the Aruba 2920 Switch) by the authentication server (i.e. Microsoft NPS Server) when a successful authentication has been achieved. There are a few other elements which need to accompany it, but this is the key element, as it specifies the VLAN number that the user should be assigned to.
The other elements that need to be returned by the NPS Server are as follows:
- Tunnel-PVT-Group-ID: 200
- Service-Type: Framed
- Tunnel-Type: VLAN
- Tunnel-Medium-Type: 802
For Client Infrastructure
On the Supplicant, Windows 7 or 10 configure the following steps on the Ethernet Adapter to enable IEEE 802.1X Authentication
For Network Infrastructure
Connect Server Infrastructure to VLAN 400
Create VLAN for Accounting Group
Create VLAN for Development Group
Create AAA Configuration on Switch for Radius Authentication
Download the Switch Configuration:
Test the IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
Verify Port-Access with the following user groups – VLAN 100 and VLAN 200
Think of what other clever things you can do from the information below;
Breakdown of Commands for RADIUS Authentication
Verification Commands
Thanks for reading. Please share your thoughts in the comment box below;
Published in Configuring , Design , Installing and Configuring , Networking , Security and Switching
- 802.1 x authentication step by step aruba
- 802.1 x authentication step by step cisco
- 802.1 x wireless authentication step by step
- 802.1x authentication process
- 802.1x authentication windows 10
- 802.1x authentication windows server 2012
- 802.1x certificate authentication
- assignment wlc
- cisco dot1x
- cisco ise dynamic vlan
- cisco ise dynamic vlan assignment wlc
- cisco wireless radius attributes
- configuration example
- dynamic vlan assignment cisco 2960 dynamic vlan configuration in packet tracer
- dynamic vlan assignment with windows radius server
- dynamic vlan cisco
- dynamic vlan ruckus
- meraki dynamic vlan assignment
- nps mac authentication wired
- nps policy for mac-based authentication
- radius multiple vlans
- vlan radius server
- vlan steering
- vmps server
Search Results
Creating VLAN Assignment Rules for Dynamic VLAN Assignment
To create a new VLAN Virtual Local Area Network. In computer networking, a single Layer 2 network may be partitioned to create multiple distinct broadcast domains, which are mutually isolated so that packets can only pass between them through one or more routers; such a domain is referred to as a Virtual Local Area Network, Virtual LAN, or VLAN. assignment rule for dynamic VLAN assignment in bridge mode, complete the following steps:
- To access the WLAN Wireless Local Area Network. WLAN is a 802.11 standards-based LAN that the users access through a wireless connection. SSID Service Set Identifier. SSID is a name given to a WLAN and is used by the client to access a WLAN network. configuration wizard for a new SSID profile or an existing SSID profile, see Configuring a WLAN SSID Profile in Bridge Mode or Creating a WLAN Profile in Tunnel and Mixed Mode .
- In the WLAN SSID configuration wizard, click the VLANs tab.
- Select the Bridge option in Traffic Forwarding Mode for a Bridge mode network. In a Bridge mode SSID, all the user traffic is bridged locally. All the wireless traffic is terminated locally at the AP and bridged onto the local Ethernet Ethernet is a network protocol for data transmission over LAN. segment.
- Select Dynamic in Client VLAN Assignment to specify a VLAN ID.
- Select an attribute from the Attribute drop-down list.
- Select either equals or not-equals from the Operator drop-down list, depending on your criteria.
- Enter a string in the String text box.
- Select a VLAN ID from the VLAN drop-down list.
- Click OK to save the changes.

- Communities
- Community Home
- Topic Thread
Instant On - Wireless
- Discussion 2.1K
- Members 491
Radius Server Assigned Vlans
owaishpn 10-14-2019 04:08 AM
owaishpn 10-14-2019 04:21 AM
chrisbi 10-18-2019 05:22 PM
prince 10-20-2019 11:13 PM
cendrulat 12-12-2020 07:50 PM
1. radius server assigned vlans.

2. RE: Radius Server Assigned Vlans
3. re: radius server assigned vlans.

4. RE: Radius Server Assigned Vlans

@owaishpn - Instant On currently doesn't support dynamic VLANs. That functionality is available with Aruba IAP solution. Instant On does offer the ability to assign static VLANs for each SSID/network.
5. RE: Radius Server Assigned Vlans

New Best Answer
- Privacy policy
- Terms of service

What is Dynamic VLAN Assignment?
Written by Sean Blanton on May 24, 2021
Share This Article
When it comes to the modern enterprise, few things are more important than network and identity security. With bad actors lurking around every corner (even inside of an organization itself), maintaining a strong, secure network along with keeping credentials safe is of utmost importance to the IT admin. Several network securing tools and techniques are being employed by IT admins today, especially during the global pandemic, but one that has been a foundational approach for many years is dynamic VLAN assignment. Since IT admins are dramatically stepping up the security of their IT environments, some are asking: what is dynamic VLAN assignment and how can it help secure the network?
Network Security with Dynamic VLAN Assignment
The simple answer is that dynamic VLAN assignment (or VLAN steering as it is sometimes called) is an excellent technique used to build on the underlying core strategy to control network access. VLAN assignments build on the use of RADIUS to control access to the network.
Via RADIUS integration, a WiFi access point (WAP) requires not only an SSID and passphrase, but a user’s unique set of credentials to access the network. Once a user has passed credentials through to the WAP to the RADIUS server and directory service, the RADIUS server will reply to the WAP that the user has been authenticated and inform what VLAN they are assigned to.
IT admins configure the system to identify which users and/or groups are assigned to which VLAN. Those VLANs can be set up on the WiFi network for any number of reasons including security and compliance. By segmenting users and authenticating them with their unique credentials, IT admins can increase security significantly. This approach helps separate out critical areas of the network, and can be especially helpful in compliance situations where, for example, the cardholder data environment (CDE) can be separated from the rest of the network making PCI Compliance far easier.
Challenges with Dynamic VLAN Assignments
The challenge with this approach is the overhead for IT admins. Traditionally, to implement dynamic VLAN assignments would require a great deal of infrastructure, configuration, and administration. For starters, IT organizations would need to set up their own FreeRADIUS server and connect that instance to the wireless access points and the identity provider (IdP), often, Microsoft ® Active Directory ® .
In many networks, the IT group would also need to configure endpoints with supplicants so that they could talk to the RADIUS server over the proper protocols. All of this ended up being a significant disincentive for IT admins, and that is why many WiFi networks are secured simply with an SSID and passphrase.
With the introduction of modern cloud RADIUS solutions, however, IT admins can virtually outsource the entire process for RADIUS authentication to WiFi and dynamic VLAN assignments. This Cloud RADIUS offering doesn’t focus on RADIUS only, but also acts as the identity management source of truth that can replace an on-prem Active Directory instance. It is available from the JumpCloud Directory Platform .
Cloud RADIUS and More
JumpCloud Directory Platform is everything a directory service was, and reimagines it for the cloud era. This includes endpoint management , identity and access management, single sign-on, multi-factor authentication, and network authentication tools such as Cloud RADIUS. Relatively new to the JumpCloud Suite is dynamic VLAN assignment functionality, so network administrators can better authorize their users’ access to crucial network resources. This feature just adds one more log to the bright flame of this cloud directory.
Interested in dynamic VLAN assignment and the rest of what the platform has to offer? Contact us , or check out our knowledge base to learn more.
- Remote Work
- User Access

Reduce IT costs and complexity
Sean Blanton is the Director of Content at JumpCloud and has spent the past decade in the wide world of security, networking and IT and Infosec administration. When not at work Sean enjoys spending time with his young kids and geeking out on table top games.
Continue Learning with Related Posts
Continue learning with our newsletter.
Network Guys
Share your knowledge!
How to use 802.1x/mac-auth and dynamic VLAN assignment
Hello guys! Today I want to show you how to secure your edge-switches with 802.1x and mac-authentication fallback in combination with HPE comware-based switches. The 802.1x protocol is used for network access control. For devices like printers, cameras, etc. we will use mac-authentication as a fallback. We will also use dynamic VLAN assignment for the connected ports.
Our radius server will be Microsoft NPS. You can activate this role on the Windows server:
After the installation, open the NPS console and register the radius server in your Active Directory:
add your switches or your management network as a radius-client:
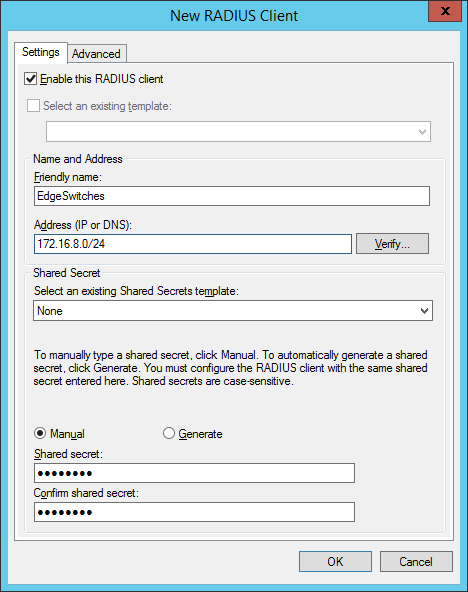
the shared secret will be used in the switch configuration. In created two groups within my test environment:
- “ VLAN2-802.1x ” containing computer accounts
- “ VLAN3-MAC-Auth ” containing user accounts (username+password = mac-address of the device)
So we will now configure two network policies for our network access control:
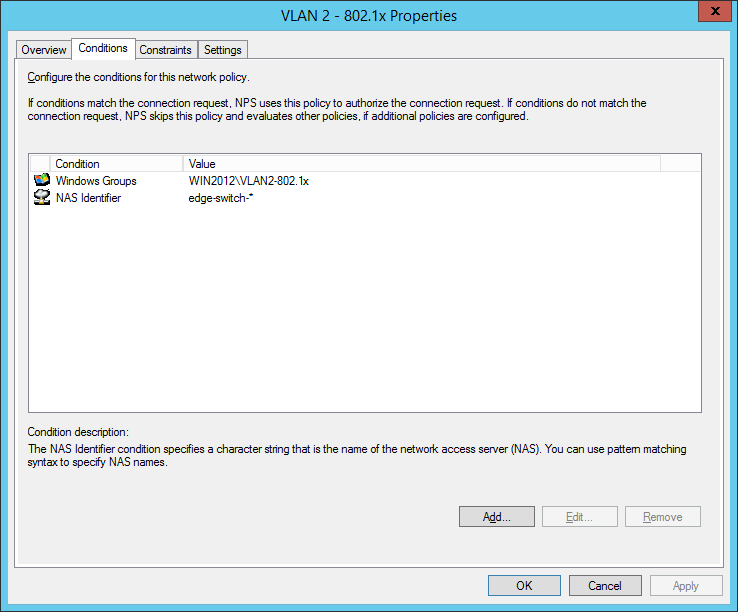
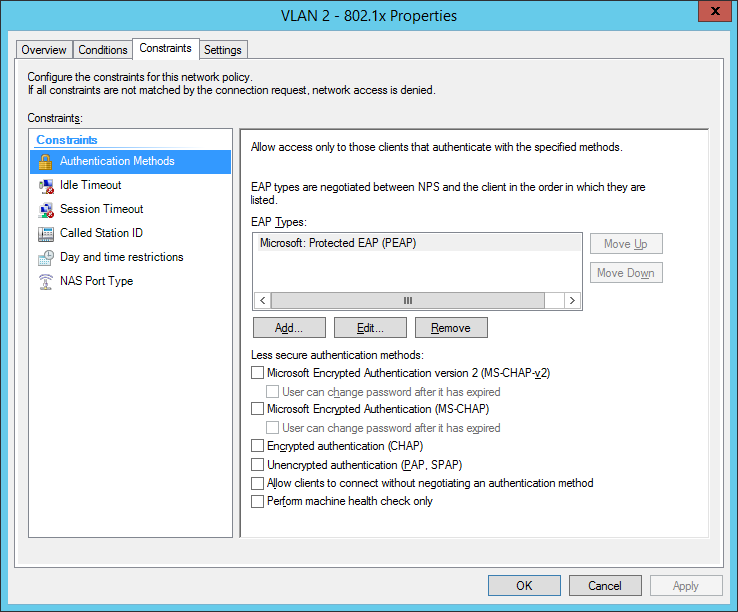
I also configured a NAS Identifier so no other device can use the radius server. The clients will use their computer certificate so you will need a running internal certification authority. Choose PEAP only as the authentication method:
the next step is for our dynamic VLAN assignment. Dot1x devices are bound to VLAN 2:
the final dot1x configuration in the NPS:
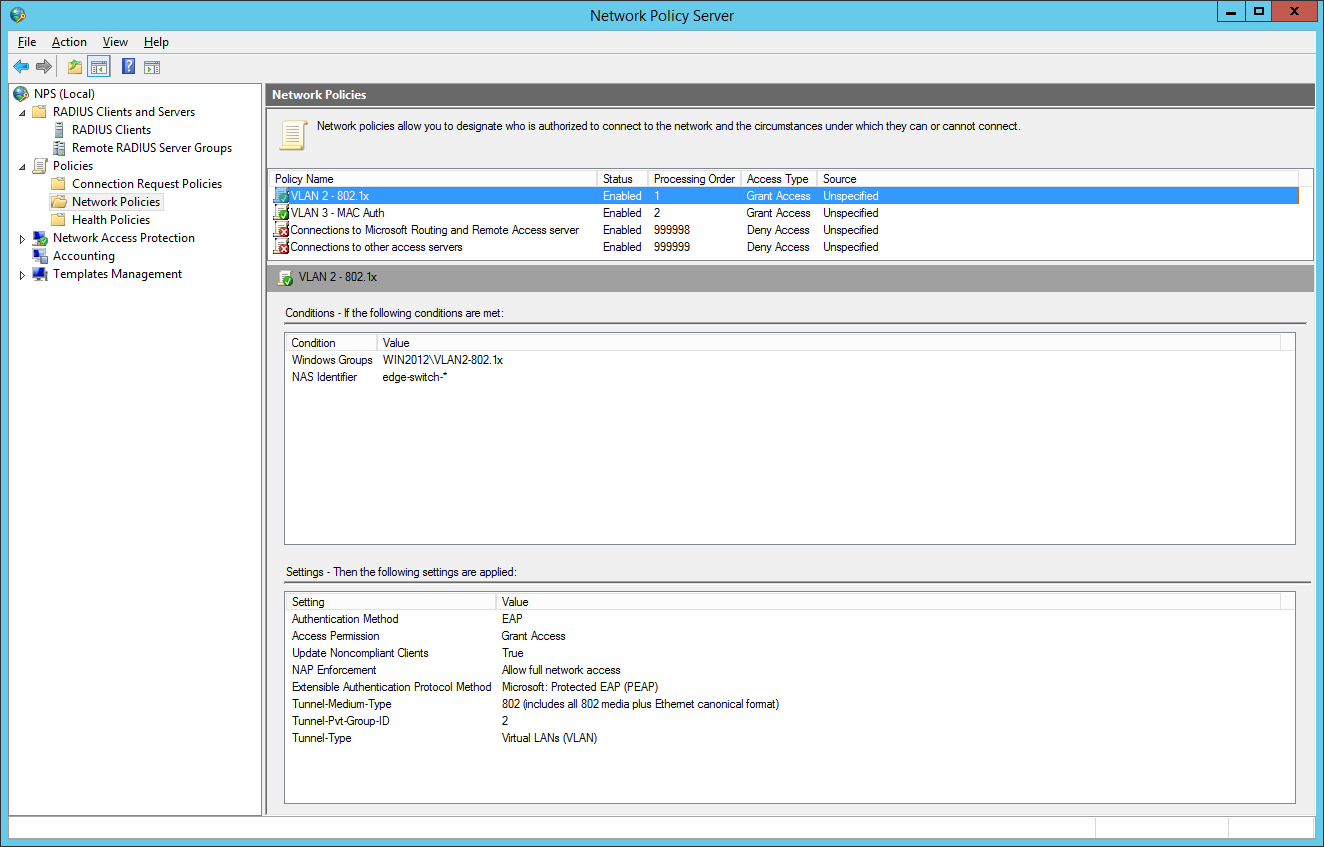
the second network policy is for the mac-based authentication:
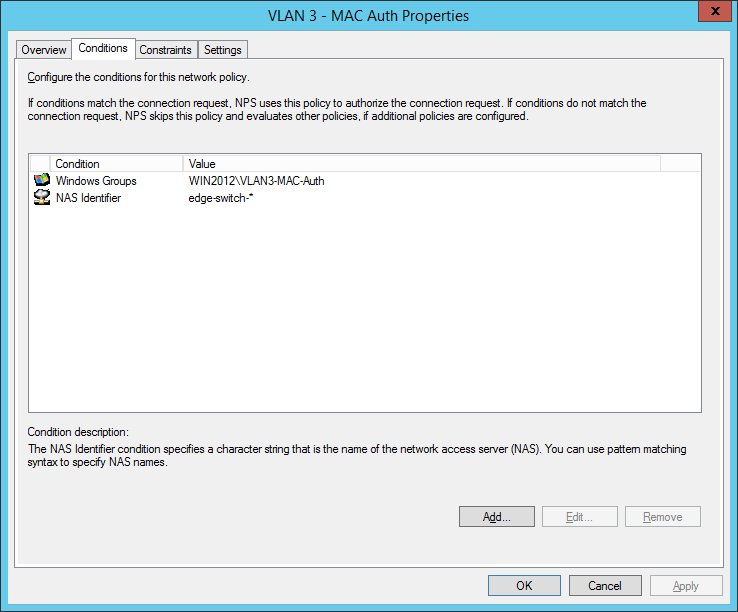
Comware switches are sending MAC-Auth-requests via PAP (maybe you know how to change it to CHAP):
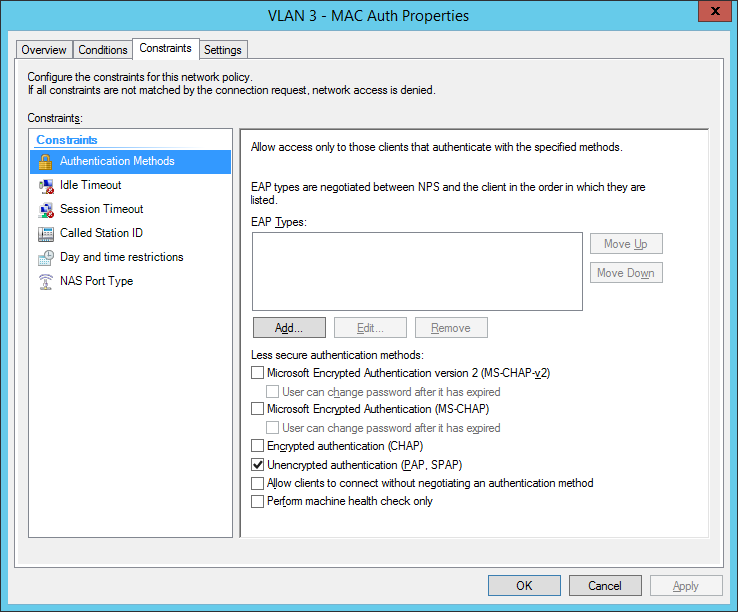
final MAC auth profile:
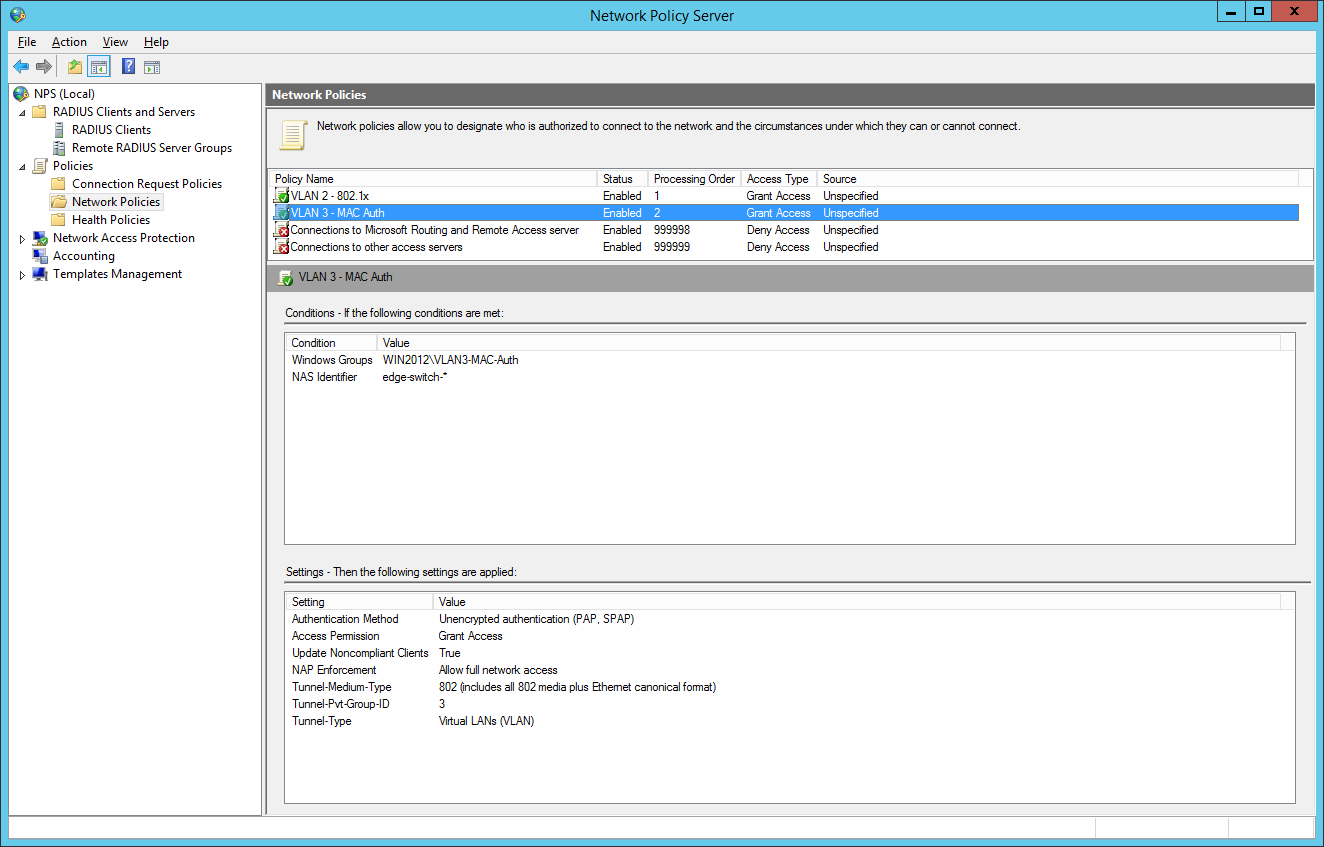
for now we have built up our authentication server. Now let’s go to the switch configuration. You have global configuration parameters and parameters for each interface. The best way is to use interface-range command to be safe at your configuration. Users who cant authenticate, will be forced to VLAN 999 (quarantine VLAN with no gateway). Here are the global parameters with explanations inline:
now we will configure the interfaces: Added 2 entries
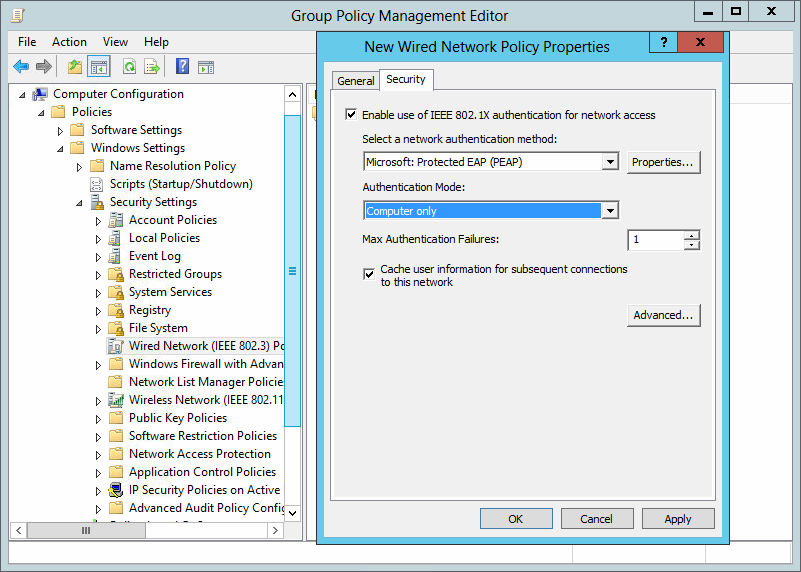
the last part is to configure all windows clients to send 802.1x auth data to the cable network. I’ve done this via a global group policy. You can find the settings under Computer Configuration / Policies / Windows Settings / Security Settings / Wired Network (IEEE 802.3) Policies:
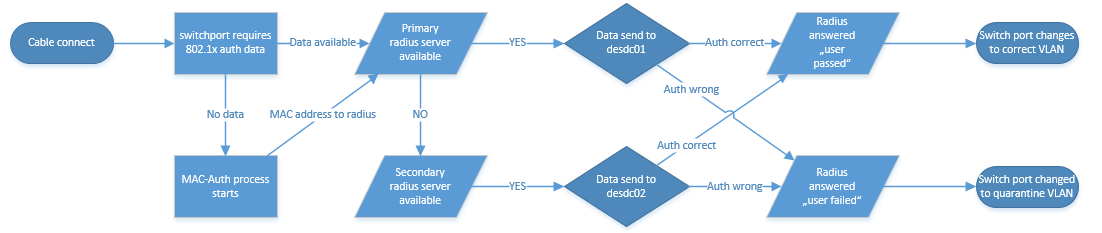
So how does a working 802.1x-auth looks like?
%Jan 3 01:59:59:531 2013 edge-switch-01 DOT1X/6/DOT1X_LOGIN_SUCC: -IfName=GigabitEthernet1/0/10-MACAddr=0023-2415-42a3-AccessVLANID=1- AuthorizationVLANID=2 -Username= host/PC123.mycompany.local ; User passed 802.1X authentication and came online.
Successful Mac-Authentication of a printer:
%Jan 3 01:31:28:782 2013 de-pad-l19-edg01 MACA/6/MACA_LOGIN_SUCC: -IfName=GigabitEthernet1/0/9-MACAddr=0017-c82d-e9bf-AccessVLANID=1- AuthorizationVLANID=3 -Username= 0017c82de9bf -UsernameFormat=MAC address; User passed MAC authentication and came online.
I tried to draw a flow chart which shows the authentication process, I hope it’s ok for you :)
Do you have questions? Feel free to write them into the comments and I will try to answer.
Have a nice and sunny day!
/edit: If you can’t see success and failure events, follow this instruction: NPS / Radius Server is not logging
/edit 2018-05-14: I corrected the global and interface configuration, we had problems with the old configuration
12 Responses
Thanks for this, I need to setup dynamic VLAN assignment in the near future but for Juniper equipment.
This at least gives me a good starting point, thanks for the write up.
Many thanks for the perfect tutorial on How to use 802.1x/Mac-Auth and dynamic VLAN assignment. Many of us can take help from it. Really nice.
Nice write-up. This was a great starting point for configuring the base for dynamic polices. Thanks!
hi Mike, how ‘s about hybrid port with voice-vlan? does it work?
thanks Tung Duong
we had several problems with this config, currently we are investigating hyprid ports with “port security” command. I will update this post if we have prooved this version.
Can you tell me why I would do this over conventional static VLANs? What are the benefits radius dynamic VLANs?
we have customers which want to divide the network for clients, printers and “special devices”. So you have different group/radius-policies to directly place the devices in the right VLAN. Dynamic VLAN is only a bonus feature which you can use. Of course, you can use only the 802.1x and Mac authentication for security purpose.
I’m on the desktop side of things, so apologies if I use any incorrect terminology here.
Our Infrastructure team are looking at introducing 8021x in our schools. They have a test setup where all 8021x devices pick up a data centre VLAN regardless of which building they’re in – eg 10.100.50.
Each building WIRED has its own unique IP – SchoolA=10.120, SchoolB = 10.130 and so on.
I’ve asked if the 8021x setup can be where 8021x devices in SchoolA will get 10.120.50; SchoolB will get 10.130.50
This would allow us to easily determine which building LaptopA actually is, in the same way as we can with our wired desktops. It also saves on SCCM boundary issues causing applications/updates to be pulled over the WAN rather than the LAN.
It’s been suggested that this may not be possible. Could someone confirm this?
Thanks in advance.
Hello! This is of course possible!
My idea (with examples):
SchoolA=10.120 (Location: Chicago) SchoolB=10.130 (Location: Dallas)
So at Chicago you will have VLAN 333, every device is getting an IP address with 10.120.x.x. At Dallas every device in VLAN 333 is getting an IP address with 10.130.x.x. So the VLAN ID “333” is the same at every school but the DHCP scope and default gateway has it’s own address. So the device is getting the VLAN 333 at every location but another IP address. It’s very simple.
It’s not working if all schools are connected via Layer2 so VLAN333 can’t be a “standalone VLAN” at each geographical location.
Ask me any questions, I will try to help you.
- Pingback: 802.1x, MAC-Authentication and VLAN assignment at ProCurve/aruba Switches – Network Guy
- Pingback: Port Auth, Dynamic VLAN and Radius | samuelnotes
- Pingback: HPE Comware problem with mac authentication and printer - Network Guy
Leave a Reply Cancel reply
Click on the button to load the content from jetpack.wordpress.com.
Load content
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Certificates

Post Categories
Post archives, recent posts.
- Sophos UTM 9.712-13 HA update problem 14. November 2022
- Sophos UTM 9.712-12 update released 24. August 2022
- Aruba OS Switch automatic vlan assignment for aruba APs 5. May 2022
- Sophos UTM 9.711-5 update released 22. April 2022
- Sophos UTM 9.710-1 update released 20. March 2022
Recent Comments
- Sophos Ssl Vpn Client Anmeldung - Login and Portal on Auto-Logon with Sophos SSL VPN Client (OpenVPN)
- Russell on Install Sophos UTM from USB Stick
- arno on Problems with incoming mails
- GigaTech IT on Installing Realtek Driver on ESXi 6.7
- Sophos User Portal Login Ssl Vpn - Online Login on Auto-Logon with Sophos SSL VPN Client (OpenVPN)
Franky’s Web Website from my friend Frank. News and Tricks about Microsoft products, primarly Exchange Server
Copyright by networkguy.de
Imprint · Privacy Policy
- Skip to content
- Skip to search
- Skip to footer
Configure Dynamic VLAN Assignment with ISE and Catalyst 9800 Wireless LAN Controller
Available Languages
Download options.
- PDF (2.6 MB) View with Adobe Reader on a variety of devices
- ePub (2.7 MB) View in various apps on iPhone, iPad, Android, Sony Reader, or Windows Phone
- Mobi (Kindle) (2.4 MB) View on Kindle device or Kindle app on multiple devices
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Introduction
This document describes how to configure the Catalyst 9800 WLC and Cisco ISE to assign Wireless LAN (WLAN).
Requirements
Cisco recommends that you have knowledge of these topics:
- Have basic knowledge of the Wireless LAN Controller (WLC and Lightweight Access Points (LAPs).
- Have functional knowledge of the AAA server such as Identity Services Engine (ISE).
- Have a thorough knowledge of wireless networks and wireless security issues.
- Have functional knowledge on dynamic Virtual LAN (VLAN) assignment.
- Have basic knowledge of Control and Provisioning for Wireless Access Point (CAPWAP).
Components Used
The information in this document is based on these software and hardware versions:
- Cisco Catalyst 9800 WLC (Catalyst 9800-CL) that runs firmware release 16.12.4a.
- Cisco 2800 Series LAP in local mode.
- Native Windows 10 supplicant.
- Cisco ISE that runs version 2.7.
- Cisco 3850 series switch that runs firmware release 16.9.6.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
Dynamic vlan assignment with radius server.
This document describes the concept of dynamic VLAN assignment and how to configure the Catalyst 9800 wireless LAN controller (WLC) and Cisco Identity Service Engine (ISE) to assign wireless LAN (WLAN) in order to accomplish this for the wireless clients.
In most Wireless Local Area Network (WLAN) systems, each WLAN has a static policy that applies to all clients associated with a Service Set Identifier (SSID). Although powerful, this method has limitations because it requires clients to associate with different SSIDs to inherit different QoS and security policies.
However, the Cisco WLAN solution supports identity networking. This allows the network to advertise a single SSID and allows specific users to inherit different QoS or security policies based on the user credential.
Dynamic VLAN assignment is one such feature that places a wireless user into a specific VLAN based on the credentials supplied by the user. The task to assign users to a specific VLAN is handled by a RADIUS authentication server, such as Cisco ISE. This can be used, for example, to allow the wireless host to remain on the same VLAN as it moves within a campus network.
Therefore, when a client attempts to associate to a LAP registered with a controller, the WLC passes the credentials of the user to the RADIUS server for validation. Once the authentication is successful, the RADIUS server passes certain Internet Engineering Task Force (IETF) attributes to the user. These RADIUS attributes decide the VLAN ID that must be assigned to the wireless client. The SSID of the client does not matter because the user is always assigned to this predetermined VLAN ID.
The RADIUS user attributes used for the VLAN ID assignment are:
- IETF 64 (Tunnel Type)—Set this to VLAN.
- IETF 65 (Tunnel Medium Type)—Set this to 802.
- IETF 81 (Tunnel Private Group ID)—Set this to VLAN ID.
The VLAN ID is 12-bits and takes a value between 1 and 4094, inclusive. Because the Tunnel-Private-Group-ID is of type string, as defined in RFC2868 for use with IEEE 802.1X, the VLAN ID integer value is encoded as a string. When these tunnel attributes are sent, it is necessary to enter them in the Tag field.
In this section, you are presented with the information to configure the features described in this document.
Network Diagram
This document uses this network setup:
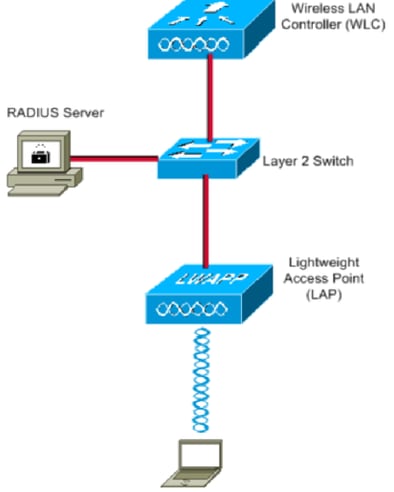
These are the configuration details of the components used in this diagram:
- The IP address of Cisco ISE (RADIUS) server is 10.10.1.24.
- The Management Interface address of the WLC is 10.10.1.17.
- The internal DHCP server on the controller is used to assign the IP address to wireless clients.
- This document uses 802.1x with PEAP as the security mechanism.
- VLAN102 is used throughout this configuration. The username smith -102 is configured to be placed into the VLAN102 by the RADIUS server.
Configuration Steps
This configuration is separated into three categories:
- Cisco ISE Configuration.
- Configure the Switch for Multiple VLANs.
- Catalyst 9800 WLC Configuration.
Cisco ISE Configuration
This configuration requires these steps:
- Configure the Catalyst WLC as an AAA Client on the Cisco ISE Server.
- Configure Internal users on Cisco ISE.
- Configure the RADIUS (IETF) attributes used for dynamic VLAN Assignment on Cisco ISE.
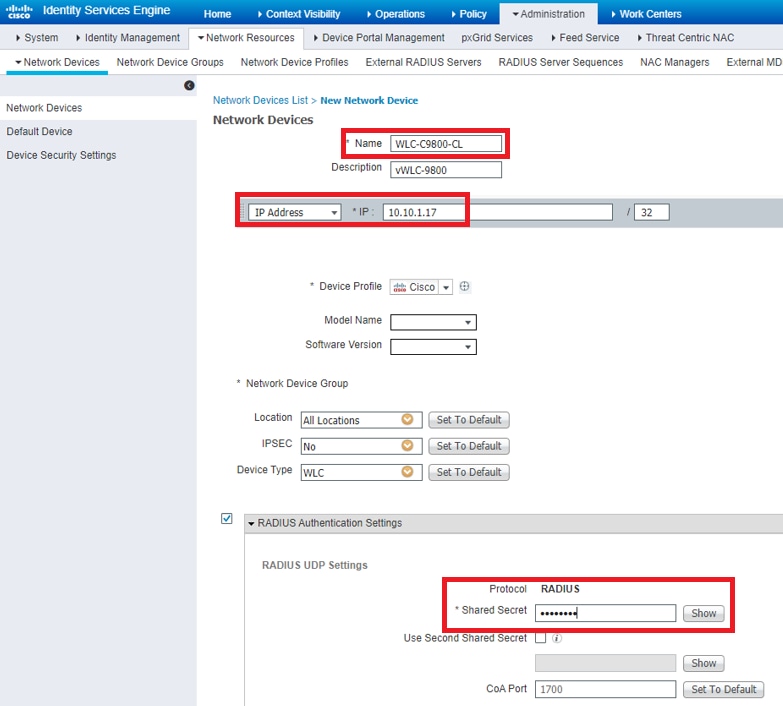
Step 1. Configure the Catalyst WLC as an AAA Client on the Cisco ISE server
This procedure explains how to add the WLC as a AAA client on the ISE server so that the WLC can pass the user credentials to ISE.
Complete these steps:
- From the ISE GUI, navigate to Administration > Network Resources > Network Devices and select Add .
- Complete the configuration with the WLC management IP address and RADIUS shared secret between WLC and ISE as shown in the image:
Step 2. Configure internal users on Cisco ISE
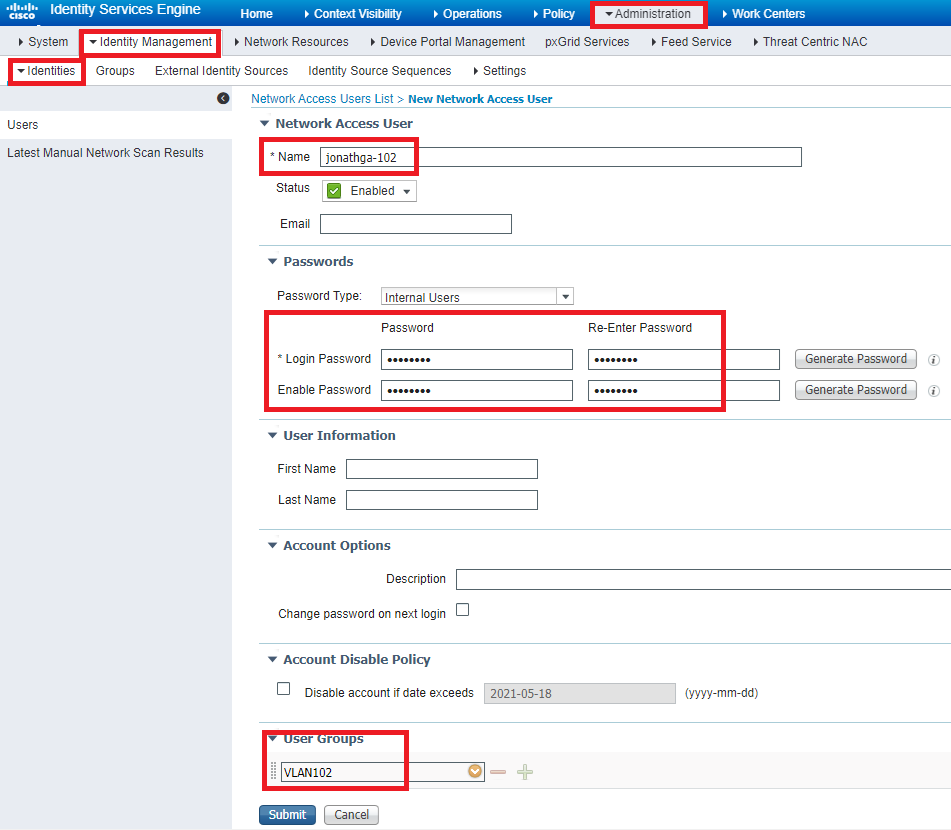
This procedure explains how to add the users on the internal user database of Cisco ISE.
- From the ISE GUI, navigate to Administration > Identity Management > Identities and select Add .
- Complete the configuration with the username, password, and user group as shown in the image:
Step 3. Configure the RADIUS (IETF) attributes used for dynamic VLAN Assignment
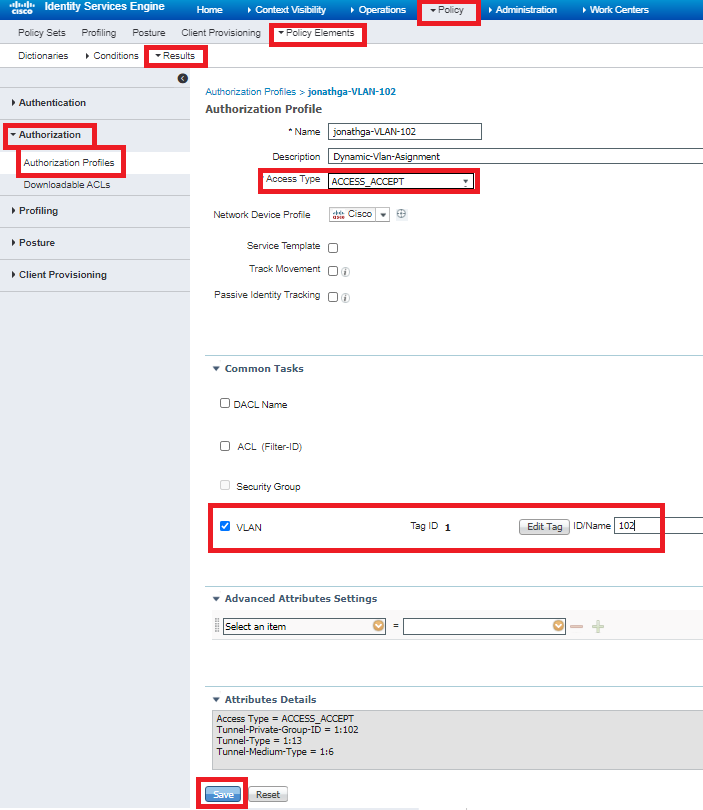
This procedure explains how to create an authorization profile and an authentication policy for wireless users.
- From the ISE GUI, navigate to Policy > Policy Elements > Results > Authorization > Authorization profiles and select Add to create a new profile.
- Complete the authorization profile configuration with VLAN information for the respective group. This image shows jonathga-VLAN-102 group configuration settings.
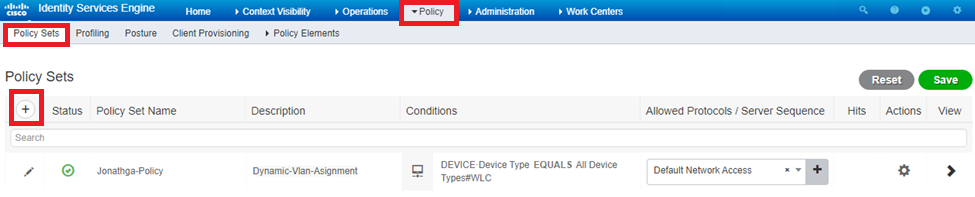
After the authorization profiles are configured, an authentication policy for wireless users needs to be created. You can use a new Custom policy or modify the Default Policy set. In this example, a custom profile is created.
- Navigate to Policy > Policy Sets and select Add to create a new policy as shown in the image:
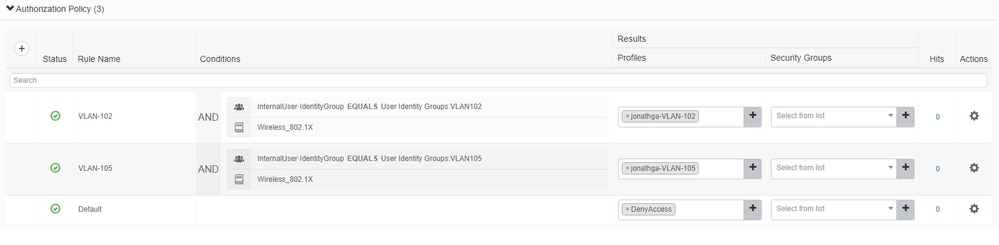
Now you need to create authorization policies for users in order to assign a respective authorization profile based on group membership.
- Open the Authorization policy section and create policies to accomplish that requirement as shown in the image:
Configure the Switch for Multiple VLANs
To allow multiple VLANs through the switch, you need to issue these commands to configure the switch port connected to the controller:
Note : By default, most of the switches allow all VLANs created on that switch via the trunk port. If a wired network is connected to the switch, then this same configuration can be applied to the switch port that connects to the wired network. This enables the communication between the same VLANs in the wired and wireless network.
Catalyst 9800 WLC Configuration
- Configure the WLC with the Details of the Authentication Server.
- Configure the VLANs.
- Configure the WLANs (SSID).
- Configure the Policy Profile.
- Configure the Policy tag.
- Assign the Policy tag to an AP.
Step 1. Configure the WLC with the Details of the Authentication Server
It is necessary to configure the WLC so it can communicate with the RADIUS server to authenticate the clients.
- From the controller GUI, navigate to Configuration > Security > AAA > Servers / Groups > RADIUS > Servers > + Add and enter the RADIUS server information as shown in the image:
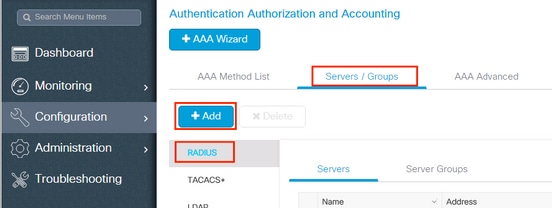
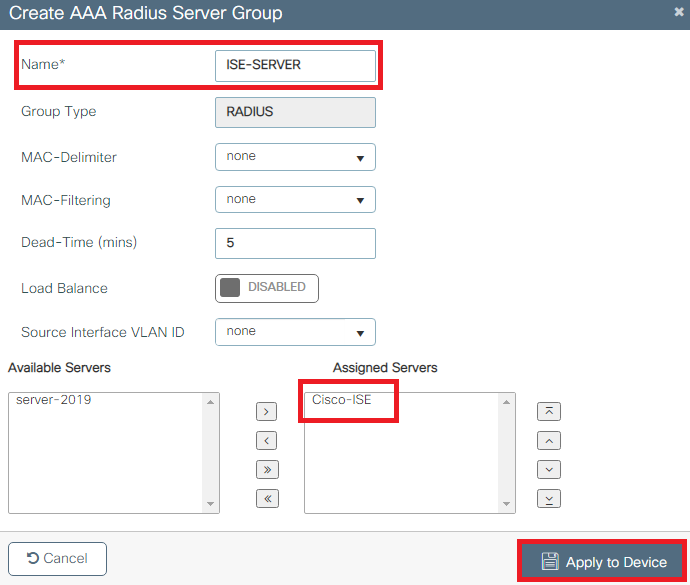
- In order to add the RADIUS server to a RADIUS group, navigate to Configuration > Security > AAA > Servers / Groups > RADIUS > Server Groups > + Add as shown in the image:
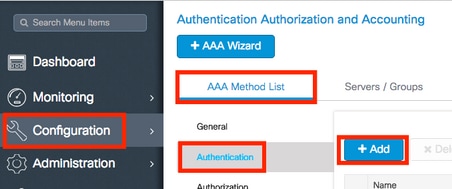
- In order to create an Authentication Method List, navigate to Configuration > Security > AAA > AAA Method List > Authentication > + Add as shown in the images:
Step 2. Configure the VLANs
This procedure explains how to configure VLANs on the Catalyst 9800 WLC. As explained earlier in this document, the VLAN ID specified under the Tunnel-Private-Group ID attribute of the RADIUS server must also exist in the WLC.
In the example, the user smith-102 is specified with the Tunnel-Private-Group ID of 102 (VLAN =102) on the RADIUS server.
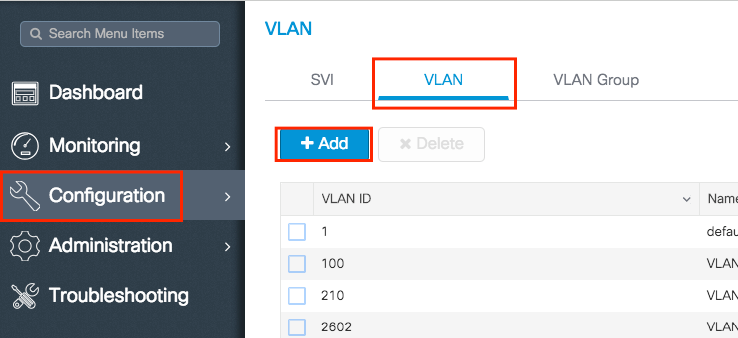
- Navigate to Configuration > Layer2 > VLAN > VLAN > + Add as shown in the image:
- Enter the needed information as shown in the image:
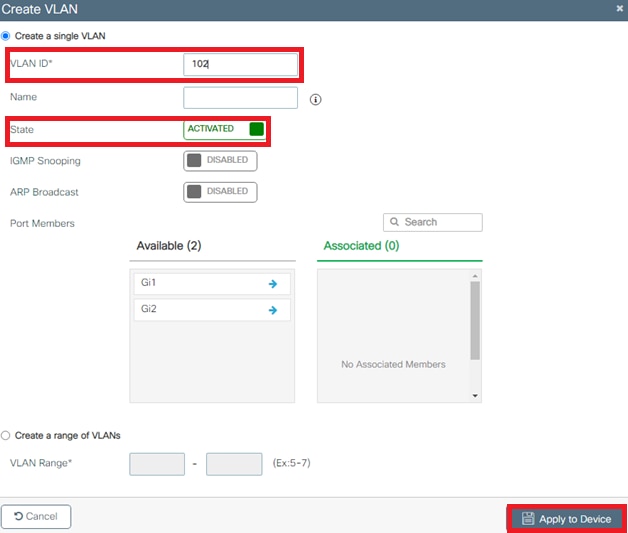
Note : If you do not specify a name, the VLAN automatically gets assigned the name of VLANXXXX, where XXXX is the VLAN ID.
Repeat steps 1 and 2 for all the needed VLANs, once done you can continue to step 3.
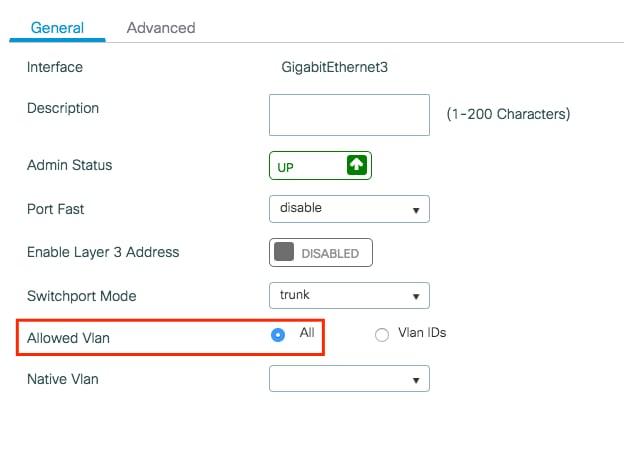
- If you have a port channel in use, navigate to Configuration > Interface > Logical > PortChannel name > General . If you see it configured as Allowed VLAN = All you are done with the configuration. If you see Allowed VLAN = VLANs IDs , add the needed VLANs and after that select Update & Apply to Device .
- If you do not have port channel in use, navigate to Configuration > Interface > Ethernet > Interface Name > General . If you see it configured as Allowed VLAN = All you are done with the configuration. If you see Allowed VLAN = VLANs IDs , add the needed VLANs and after that select Update & Apply to Device .
This images show the configuration related to the interface setup if you use All or specific VLAN IDs.
Step 3. Configure the WLANs (SSID)
This procedure explains how to configure the WLANs in the WLC.
- In order to create the WLAN. Navigate to Configuration > Wireless > WLANs > + Add and configure the network as needed, as shown in the image:
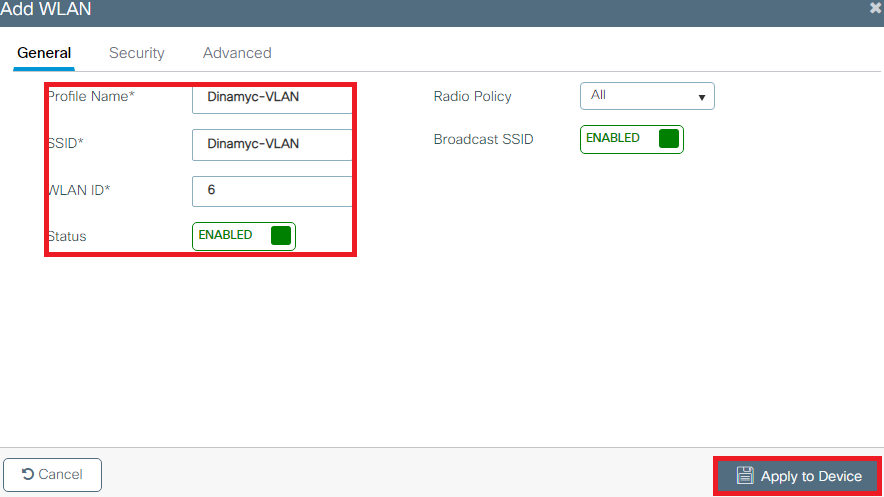
- Enter the WLAN information as shown in the image:
- Navigate to Security tab and select the needed security method. In this case WPA2 + 802.1x as shown in the images:
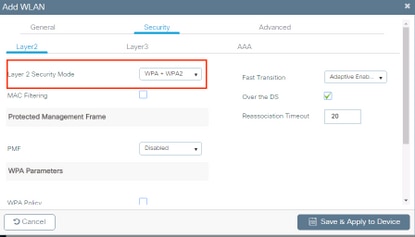
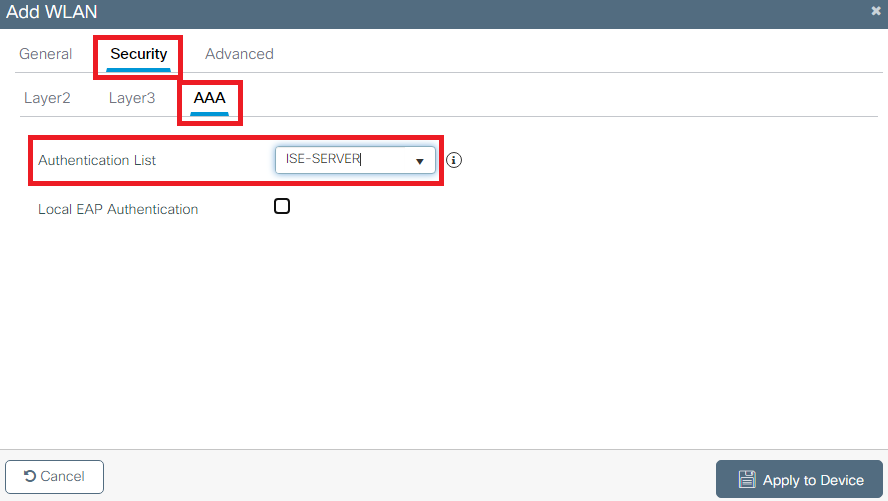
From Security > AAA tab, select the authentication method created on step 3 from Configure the WLC with the Details of the Authentication Server section as shown in the image:
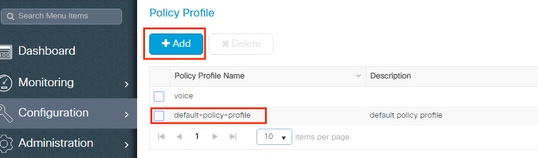
Step 4. Configure the Policy Profile
This procedure explains how to configure the Policy Profile in the WLC.
- Navigate to Configuration > Tags & Profiles > Policy Profile and either configure your default-policy-profile or create a new one as shown in the images:
- From the Access Policies tab assign the VLAN to which the wireless clients are assigned when they connect to this WLAN by default as shown in the image:
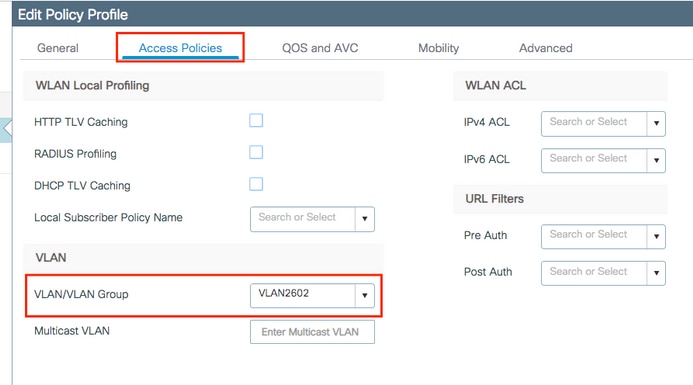
Note : In the example provided, it is the job of the RADIUS server to assign a wireless client to a specific VLAN upon successful authentication, therefore the VLAN configured on the policy profile can be a black hole VLAN, the RADIUS server overrides this mapping and assigns the user that comes through that WLAN to the VLAN specified under the user Tunnel-Group-Private-ID field in the RADIUS server.
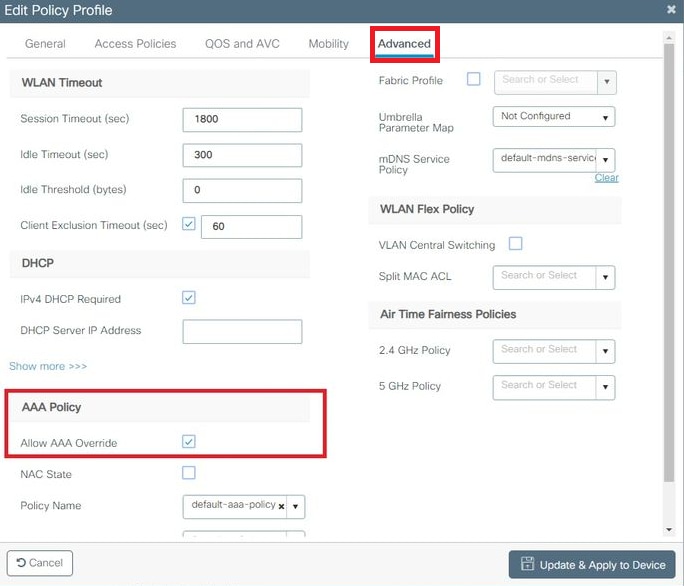
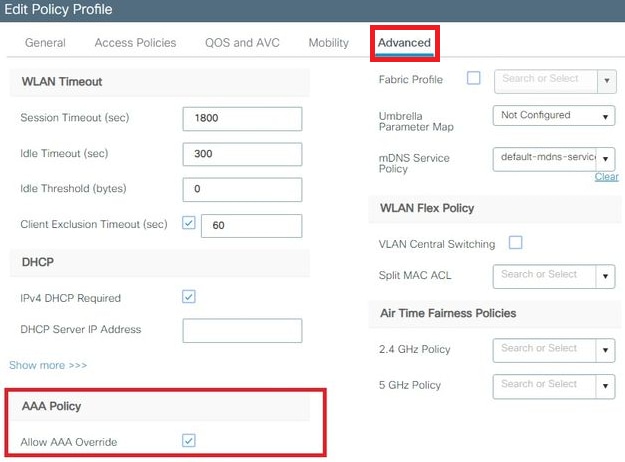
- From the Advance tab, enable the Allow AAA Override check box to override the WLC configuration when the RADIUS server returns the attributes needed to place the client on the proper VLAN as shown in the image:
Step 5. Configure the Policy Tag
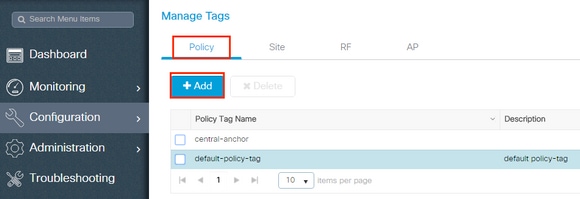
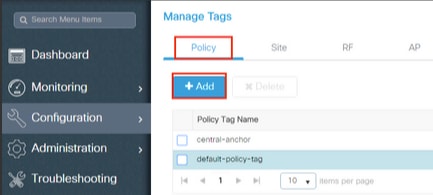
This procedure explains how to configure the Policy tag in the WLC.
- Navigate to Configuration > Tags & Profiles > Tags > Policy and add a new one if needed as shown in the image:
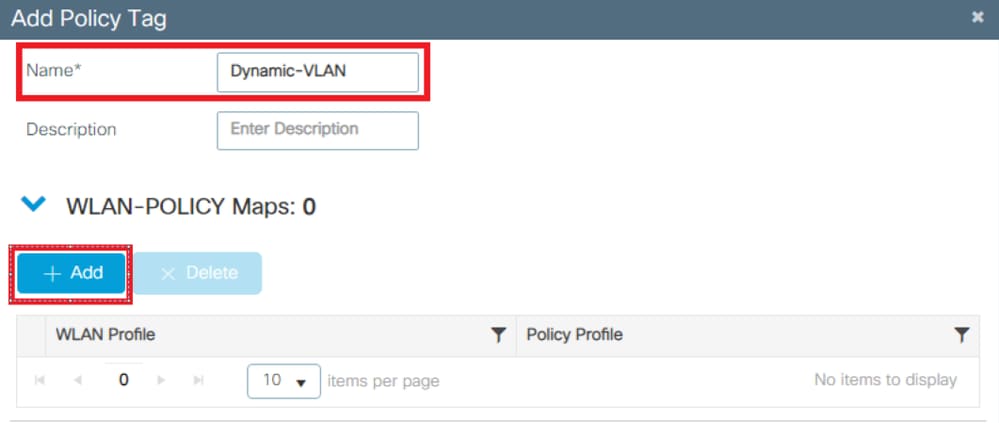
- Add a name to the Policy Tag and select +Add , as shown in the image:
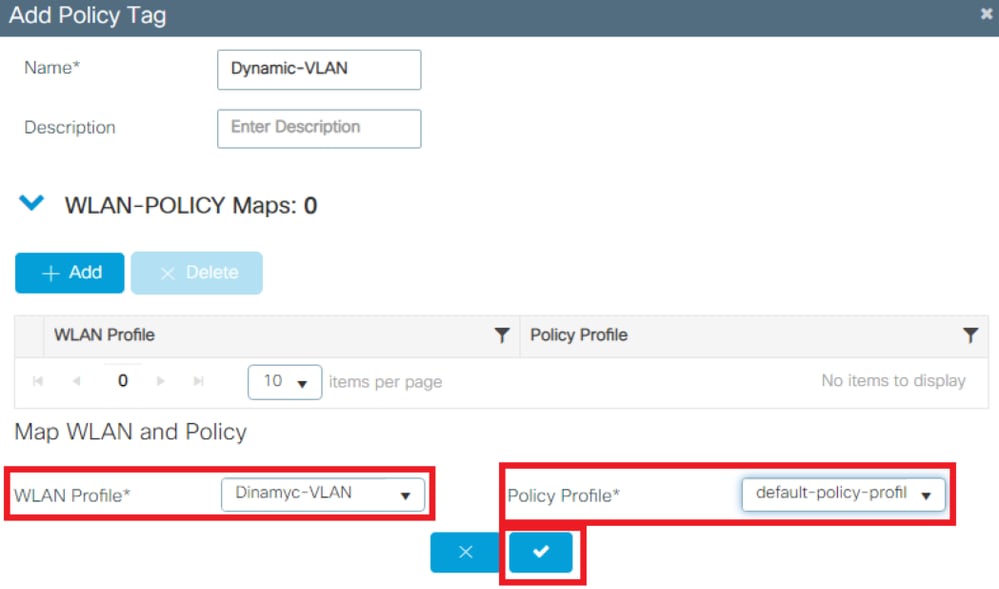
- Link your WLAN Profile to the desired Policy Profile as shown in the images:
Step 6. Assign the Policy Tag to an AP
- Navigate to Configuration > Wireless > Access Points > AP Name > General Tags and assign the relevant policy tag and then select Update & Apply to Device as shown in the image:
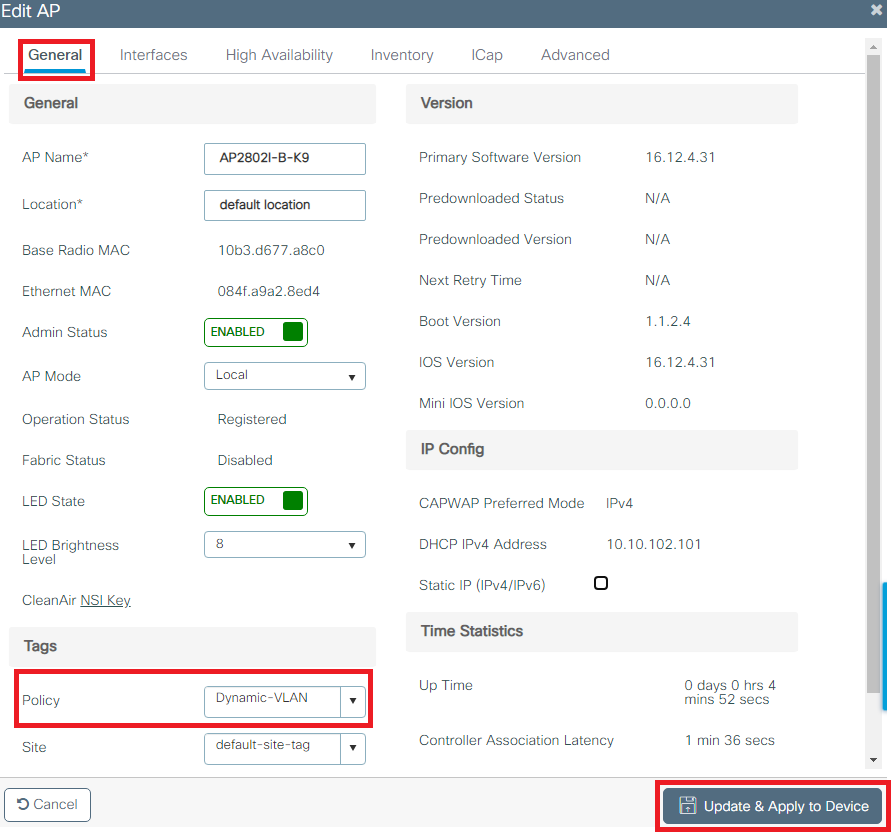
Caution : Be aware that changing the policy tag on an AP results in the AP disconnecting from the WLC and then reconnecting.
Flexconnect
The Flexconnect feature allows APs to send wireless client data to egress through the AP LAN port when configured as a trunk. This mode, known as Flexconnect Local Switching, allows the AP to segregate client traffic by tagging it in separate VLANs from its management interface. This section provides instructions on how to configure Dynamic VLAN assignment for the local switching scenario.
Note : The steps outlined in the previous section are applicable to the Flexconnect scenario as well. To complete the configuration for Flexconnect, please do the additional steps provided in this section.
To allow multiple VLANs through the switch, you need to issue the next commands to configure the switch port connected to the AP:
- Switch(config-if)# switchport mode trunk
- Switch(config-if)# switchport trunk encapsulation dot1q
Note : By default, most of the switches allow all VLANs created on the switch via the trunk port.
Flexconnect Policy Profile configuration
- Navigate to Configuration > Tags & Profiles > Policy Profile > +Add and create a new policy.
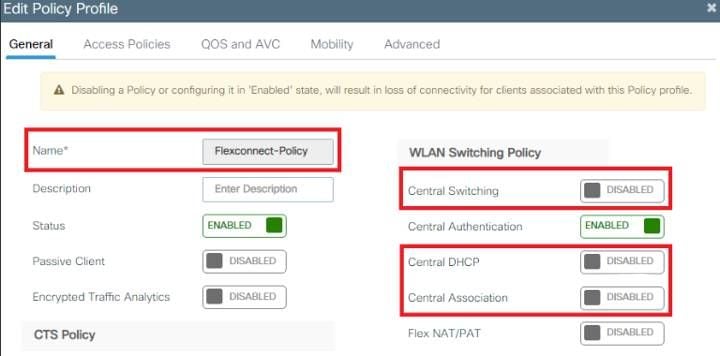
Note : Starting with the 17.9.x code, the policy-profile appearance has been updated as depicted in the picture.

Note : The VLAN configured on this step is not required to be present on the VLAN list of the WLC. Necessary VLANs are added on the Flex-Profile later, which creates the VLANs on the AP itself.
Assign the Flexconnect policy profile to a WLAN and Policy tag
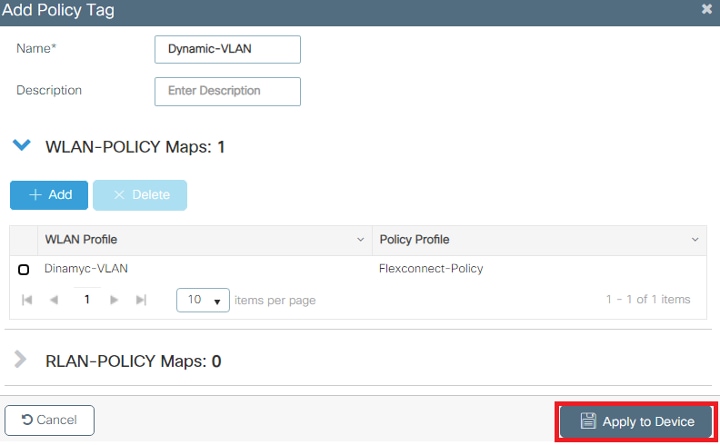
Note : A Policy Tag is used to link the WLAN with the Policy Profile. You can either create a new Policy Tag or use the default-policy tag.
- Click on the Apply to Device button.
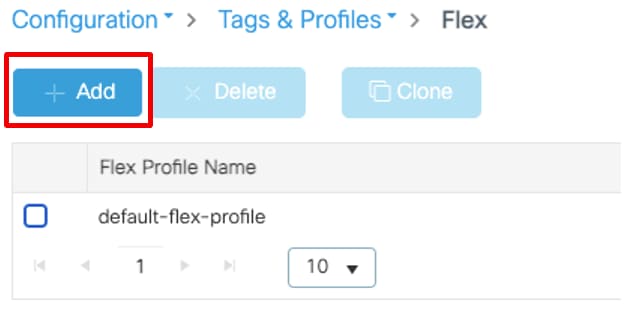
Configure the Flex Profile
To dynamically assign a VLAN ID via RADIUS on a FlexConnect AP, it is necessary for the VLAN ID mentioned in the Tunnel-Private-Group ID attribute of the RADIUS response to be present on the access points. The VLANs are configured on the Flex profile.
Note : The native VLAN ID refers management VLAN for the AP, so it must match the native VLAN configuration of the switch the AP is connected to
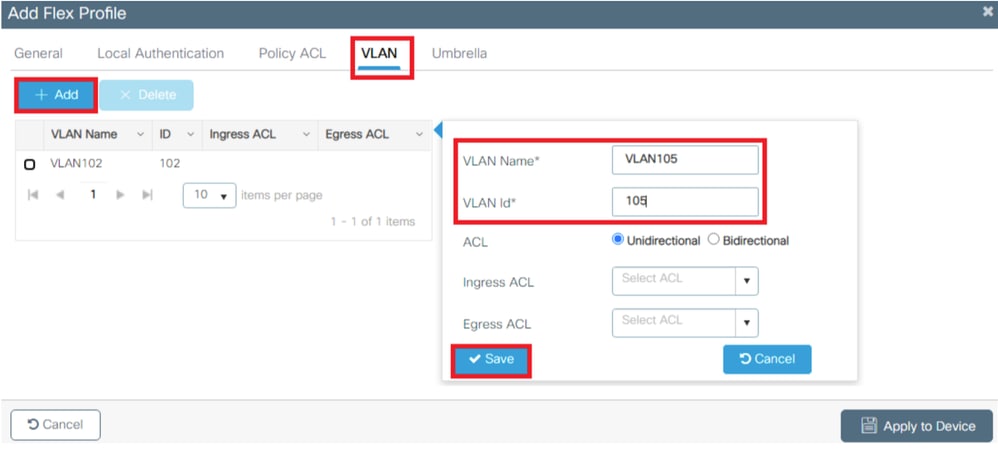
Note : In step 3 of the section Flexconnect Policy Profile Configuration, you configured the default VLAN assigned to the SSID. If you use a VLAN name on that step, ensure that you use the same VLAN name on the Flex Profile configuration, otherwise, clients are not able to connect to the WLAN.
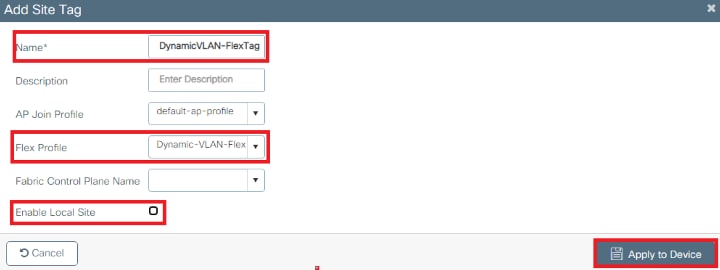
Flex Site tag configuration
- Navigate to Configuration > Tags & Profiles > Tags > Site > +Add, to create a new site tag .
Assign the Policy and Site Tag to an AP.
- Navigate to Configuration > Wireless > Access Points > AP Name > General Tags, assign the relevant policy and site tag and then click Update & Apply to Device.
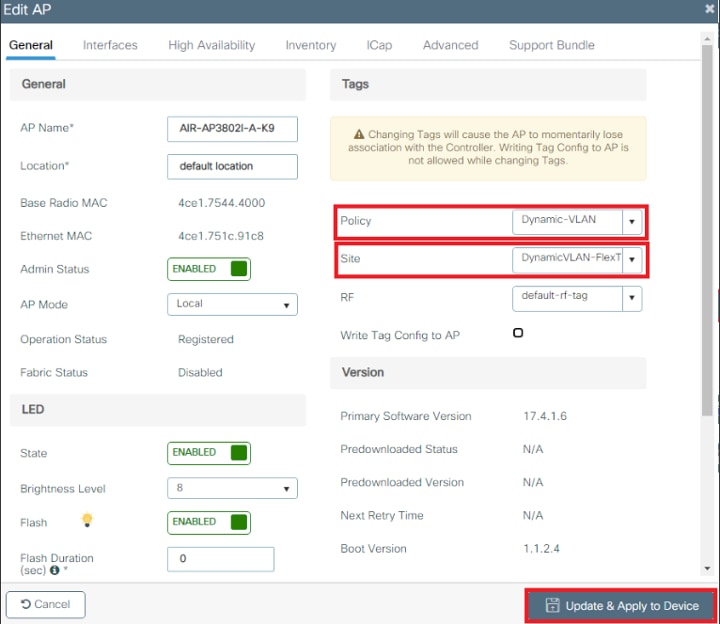
Caution : Be aware that changing the policy and site tag on an AP results in the AP disconnecting from the WLC and then reconnecting.
Note : If the AP is configured in Local mode (or any other mode) and then it gets a Site Tag with the "Enable Local Site" setting disabled, the AP reboots and comes back in FlexConnect mode
Use this section to confirm that your configuration works properly.
Configure the test client SSID profile using the proper EAP protocol and credentials defined in ISE that can return a Dynamic VLAN assignment. Once you are prompted for a username and password, enter the information of the user mapped to a VLAN on ISE.
In the previous example, notice that smith-102 is assigned to the VLAN102 as specified in the RADIUS server. This example uses this username to receive authentication and to be assigned to a VLAN by the RADIUS server:
Once the authentication is completed, you need to verify that your client is assigned to the proper VLAN as per the RADIUS attributes sent. Complete these steps to accomplish this task:
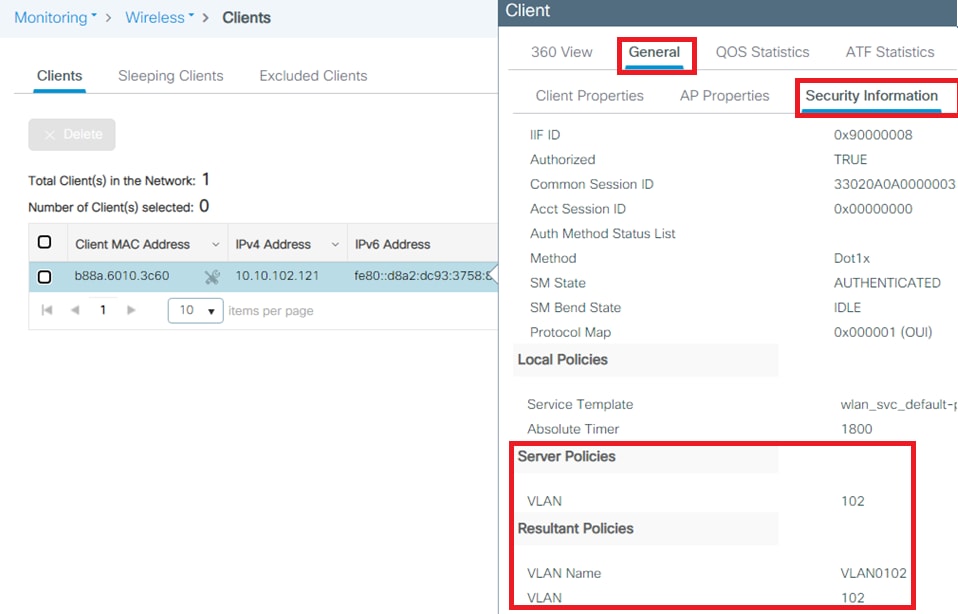
From this window, you can observe that this client is assigned to VLAN102 as per the RADIUS attributes configured on the RADIUS server.
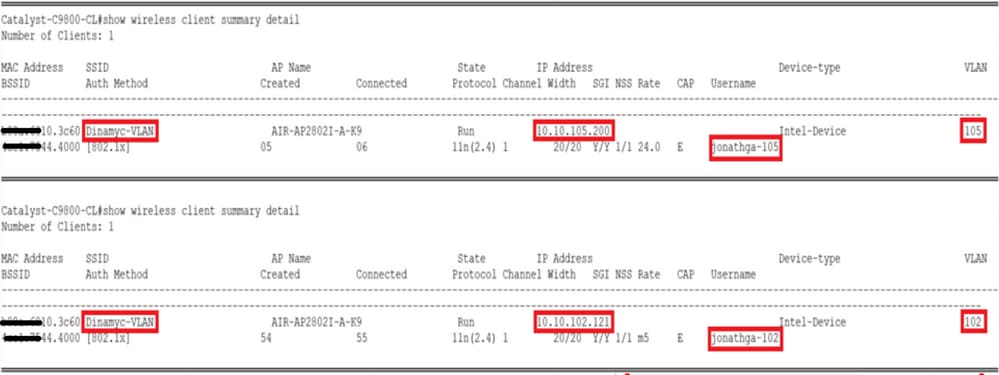
From the CLI you can use the show wireless client summary detail to view the same information as shown in the image:
- From the controller GUI, navigate to Troubleshooting > Radioactive Trace > +Add .
- Enter the Mac Address of the wireless client.
- Select Start .
- Connect the client with the WLAN.
- Navigate to Stop > Generate > Choose 10 minutes > Apply to Device > Select the trace file to download the log .
This portion of the trace output ensures a successful transmission of RADIUS attributes:
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
Related Information
- End User Guide
- Cisco Technical Support & Downloads
Revision History
Contributed by Cisco Engineers
- Jonathan de Jesus Garcia Cisco TAC Engineer
- Jose Pablo Munoz Cisco TAC Engineer
Was this Document Helpful?

Contact Cisco
- (Requires a Cisco Service Contract )
This Document Applies to These Products
- Wireless LAN Controller Software

IMAGES
VIDEO
COMMENTS
VLAN 1 has a static IP address, while VLAN 2 has a dynamic IP address assigned via DHCP or PPPoE from the uplink device. Figure 1 IP Address Assignment to VLAN via DHCP or PPPoE. Configuring Multiple Wired Uplink Interfaces (Active-Standby) You can assign up to four VLAN interfaces to operate in active-standby topology.
Dynamic VLAN assignment. 1. Dynamic VLAN assignment. We've come from Extreme to Aruba and recently purchased several AP505s. We would like to set up a dynamic vlan assignment based on a MPSK Local passphrase. I believe I've got most of the settings correct, but when I try to connect, obtaining an IP address from our external DHCP server fails.
Creating VLAN Assignment Rules for Dynamic VLAN Assignment in Bridge Mode. To create a VLAN Virtual Local Area Network. In computer networking, a single Layer 2 network may be partitioned to create multiple distinct broadcast domains, which are mutually isolated so that packets can only pass between them through one or more routers; such a domain is referred to as a Virtual Local Area Network ...
To specify a VLAN ID, select Dynamic in Client VLAN Assignment.; If a named VLAN is not available in the VLAN ID drop-down list, expand Show Named VLAN to view all the named VLANs mapped to the VLAN ID.; Click + Add Named VLAN to add a new named VLAN. The Add Named VLAN window is displayed.; Enter the VLAN name and VLAN ID in the VLAN Name and VLAN text boxes respectively.
Figure 1 IP Address Assignment to VLAN via DHCP or PPPoE. The following sections describe: Enabling the DHCP Client. The DHCP Dynamic Host Configuration Protocol. A network protocol that enables a server to automatically assign an IP address to an IP-enabled device from a defined range of numbers configured for a given network.
Table 1: IP and VLAN Assignment for WLAN SSID Clients Client IP Assignment Client VLAN Assignment; Virtual Controller assigned. If the Virtual Controller assigned is selected for client IP assignment, the Virtual Controller creates a private subnet and VLAN on the IAP for the wireless clients. The network address translation for all client traffic that goes out of this interface is carried out ...
A video tutorial to address Dynamic VLAN assignment using the Aruba Instan access points
The regular if/then for roles and enforcement policies allows you to assign a VLAN. If you combine that with the namespaces in the link that I sent before, you can set VLANs based on the switch/device that the user is connected to. 10. RE: Dynamic VLAN assignment with a single enforcement profile. 0 Kudos.
Dynamic VLAN Assignment on MR I am working on seeing if we can transition from our existing Aruba environment to Meraki for wireless only. ... Once they have their role, we have several contiguous vlans for each role which our Aruba Controller dynamically assigns - that is to say, there are 16 student vlans and the controller "load balances ...
Aruba's OS-CX switches have the ability to profile devices connected to ports and dynamically assign roles and policies (ACLs) to those ports. The ACLs can include the usual stuff--filtering on source, destination and protocol. But, they can also include configuration parameters like VLAN assignment.
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server is an important element to networking in the real world. User location cannot be predicted as they may be at and out of a desk and up and about should they need to do so. ... hostname "Edge Switch Aruba 2920" radius-server host 10.10.10.10 key "secret12" aaa ...
Creating VLAN Assignment Rules for Dynamic VLAN Assignment. To create a new VLAN Virtual Local Area Network. In computer networking, a single Layer 2 network may be partitioned to create multiple distinct broadcast domains, which are mutually isolated so that packets can only pass between them through one or more routers; such a domain is referred to as a Virtual Local Area Network, Virtual ...
So we have 2 main issues when competing with Unifi (prime competitors are Unifi and Meraki as per Aruba) 1) Both of them support dynamic Vlans - Aruba doesnt. Too bad, need to add it as a feature 2) Static Vlan assignment based on SSID - Aruba doesnt (or atleast i didnt see any such option).
The simple answer is that dynamic VLAN assignment (or VLAN steering as it is sometimes called) is an excellent technique used to build on the underlying core strategy to control network access. VLAN assignments build on the use of RADIUS to control access to the network. Via RADIUS integration, a WiFi access point (WAP) requires not only an ...
I'm looking for indoor and outdoor APs that can be managed and can support VLAN Steering or Dynamic VLAN Assignment for user whether they are outdoors or not without more equipment (other than the APs). Aruba Instant On seems to have a method of dynamically assigning VLANs using the APs themselves without the need of a controller.
the next step is for our dynamic VLAN assignment. Dot1x devices are bound to VLAN 2: the final dot1x configuration in the NPS: the second network policy is for the mac-based authentication: Comware switches are sending MAC-Auth-requests via PAP (maybe you know how to change it to CHAP): final MAC auth profile:
Complete these steps: From the ISE GUI, navigate to Administration > Identity Management > Identities and select Add. Complete the configuration with the username, password, and user group as shown in the image: Step 3. Configure the RADIUS (IETF) attributes used for dynamic VLAN Assignment.
In the VLAN tab, select any of the following options for Client IP Assignment:. Virtual Controller Assigned - When selected, the client obtains the IP address from the VC.. Network Assigned - When selected, the client obtains the IP address from the network.. Based on the type of client IP assignment mode selected, user can configure the VLAN assignment for clients as described in the ...
Dynamic VLAN assignment allows clients to connect to the network anywhere and, based on their credentials, they get placed in the correct VLAN irrespective of the ports to which they are connected. MAC authentication and 802.1X authentication support dynamic VLAN assignment, where a port can be placed in one or more VLANs based on the attribute ...