- Skip to primary navigation
- Skip to main content
- Skip to footer

Texas A&M Cybersecurity Center
Texas A&M Engineering Experiment Station


Graduate Programs in Cybersecurity
Available academic programs currently include graduate certificates and degree programs in cybersecurity offered across the campus.
Texas A&M College of Engineering
Master of engineering in engineering with a specialization in cybersecurity.
This Master’s of Engineering degree with a specialization in cybersecurity in the department of interdisciplinary studies offers students a solid technical foundation in the field.
Certificate in Cybersecurity Engineering
The Certificate in Cybersecurity Engineering is technically oriented with two required courses in engineering, but also offers courses in cybersecurity law, policy, and management as options for the four-course program.
The Bush School of Government and Public Policy
Certificate in cybersecurity policy.
The Certificate in Cybersecurity Policy is a four-course program that requires two courses in cybersecurity policy to be taken at the Bush School but includes course options in the College of Engineering and the Mays Business School.
Mays Business School
Certificate in cybersecurity management.
The Certificate in Cybersecurity Management is a four-course program that requires three courses from the Mays Business school and a fourth elective to be chosen from courses in engineering, math, and public service and administration.
Texas A&M School of Law
Certificate in risk management and compliance.
The Certificate in Risk Management and Compliance is designed for risk management professionals to deliver specialized legal training for compliance and incidence response and an in-depth understanding of the industry’s changing complex legal aspects. It includes a cybersecurity law course as an elective.
Master of Legal Studies, emphasis in Cybersecurity Law and Policy
Texas A&M University School of Law’s online cybersecurity legal training helps build the kind of expertise you need to tackle cybersecurity legal complexities related to data privacy and compliance, policies and regulations. Offered in a flexible, online format, this cyber law degree could help prepare working non-lawyers for leadership opportunities that call for a mastery of cybersecurity law and policy.
phone: (979) 845-7398 email: [email protected]
200 Discovery Drive, Suite 117 4254 TAMU College Station, TX 77843-4252
link: TAMU Cybersecurity Center Facebook link: TAMU Cyber Security Twitter link: TAMU Cybersecurity Center LinkedIn page
Texas A&M IT Security Policy and Compliance
- Current Students
- Faculty + Staff
- Alumni + Friends
- Parents + Family
- Community + Visitors
- Bachelor's Degrees
- Master's Degrees
- Doctorate Degrees
- Certificates
- Arts & Design
- Business & Industry
- Communications & Media
- Data Analytics & Information
- Health & Wellness
- Humanities & Social Sciences
- Music & Performing Arts
- Public Service
- Multidisciplinary
- Still Exploring & Undetermined
- International
- Bienvenidos
- Featured Videos
- College Tour
- Tuition & Aid
- Student Life
- Search Type Search Search
- Quicklinks:
- STUDENT EMAIL
- UNT DIRECTORY
- INFO FOR CURRENT STUDENTS
- INFO FOR FACULTY + STAFF
- INFO FOR ALUMNI + FRIENDS
- INFO FOR PARENTS + FAMILY
- INFO FOR COMMUNITY + VISITORS
- UNT LIBRARIES
- UNT CALENDAR
- JOBS AT UNT

Information Science Ph.D. With a Concentration in Cybersecurity
Want more info.
We're so glad you're interested in UNT! Let us know if you'd like more information and we'll get you everything you need.
Why Earn an Information Science Ph.D. With a Concentration in Cybersecurity?
The UNT Information Science Ph.D. program with a concentration in Cybersecurity responds to the varied and changing needs of an information age, increasing recognition of the central role of information and information technologies in individual, social, economic and cultural affairs.
The mission of UNT's Information Science Ph.D. program is to provide a center of excellence in graduate education and research. Its primary goals are to:
- Nurture critical and reflective thinking on the fundamental issues and elements of problems of utilization of information
- Foster an environment of substantive and productive mentoring and apprenticeship
- Prepare scholars passionate about the role of information in human affairs
- Foster cross-disciplinary thinking and research.
Students are recruited to the program from a wide range of disciplines and encouraged to expand and refocus their expertise and skills in cutting-edge areas of information science that cross disciplinary boundaries. The multifaceted nature of information science warrants the focusing of resources, courses, and faculties from a broad range of academic units.
- Research and publication
- Pedagogical practices
- Critical thinking
- Leadership ability
- Data analysis
Cybersecurity Information Science Ph.D. Highlights
What can you do with an information science ph.d. with a concentration in cybersecurity.
Graduates of the program are prepared to contribute to the advancement and evolution of the information society in a variety of roles and settings as administrators, researchers, and educators.
Cybersecurity Information Science Ph.D. Courses You Could Take
Learn More About UNT
Explore more options.
Information Data Science Ph.D.
Consumer Behavior and Experience Management Information Science Ph.D.
It’s easy to apply online. Join us and discover why we’re the choice of nearly 47,000 students.
Jump to navigation
- UTCS Direct
Cybersecurity Concentration
The cybersecurity concentration is for computer science students who want to help protect the security of the future..
As our daily lives increasingly depend on technology, the security and privacy of that technology becomes ever more important. Gain a critical understanding of the technological needs, threats, and weaknesses in cybersecurity with the Cybersecurity Concentration.
PROGRAMMING HIGHLIGHTS

15 CREDIT HOUR CURRICULUM

CUTTING EDGE CURRICULUM WITH PRACTICAL APPLICATIONS

DOES NOT ADD TIME TO DEGREE
Cybersecurity touches multiple disciplines, careers, and nearly all aspects of society—from public policy to energy management to product design. In a time when connected devices could outnumber humans, there is an urgent need for cybersecurity professionals who can solve a multitude of challenges.
Systems U.S. News & World Report, 2018
Theory U.S. News & World Report, 2018
Austin - Cities with Best Paying Cybersecurity Jobs JOBS Indeed, 2016
Projected Market Growth

Projected cybersecurity market size from 2017 to 2022 (11.0% CAGR)
Cybersecurity in Demand

Forecasted unfilled jobs from 2016 to 2021
Cybersecurity Occupations

Cybersecurity unemployment rate through 2021
Cybersecurity concentration students will receive instruction on a wide range of cybersecurity related topics like network security and cryptography. Students will also have the opportunity explore the social ramifications of cybersecurity through courses such as Ethical Hacking.
FOUNDATION COURSES
To earn the Cybersecurity Concentration students will need to complete the following courses:
- CS 346 Cryptography
- CS 361S Network Security and Privacy or 378H Network Security and Privacy: Honors
CUTTING EDGE TOPICS
Students will also need to take any two of the following elective classes:
- CS 349 Contemporary Issues in Computer Science
- CS 378 Ethical Hacking
Maximum of one advanced systems course from this list:
- CS 350C Advanced Architecture
- CS 360V Virtualization
- CS 375 Compilers
- CS 378 Multicore Operating Systems Implementation
- CS 378(H) Concurrency
*In some cases, the graduate course CS395T: Cybersecurity and Law may be substituted for an elective. Please note that undergraduates must be approved to register for graduate classes, and that they may only do so the day before classes start. For more information on that process, please consult your advisor.
If you completed CS 429 during the Fall 2019 semester or before, you may complete this version of the UTCS Security Concentration.
These courses may change and additional courses may be added in the future.
- Undergraduate Office
- Graduate Office
- Office of External Affairs
- Mission Statement
- Emergency Information
- Site Policies
- Web Accessibility Policy
- Web Privacy Policy
Cybersecurity
Through access control, cryptography, networking, and more, Texas Computing researchers are improving the security and privacy of technology to make the world, and our lives, safer.
Research News

Computer Security Expert Named Simons Foundation Investigator

The Implications of Quantum Computing: Internet Security, Random Bits, and More

Building the Future of National Security Leadership Deep in the Heart of Texas
Featured research.
Networking Research Laboratory
Research activities of the laboratory span the entire development cycle of network protocols and security services.

Integrated Cybersecurity Studies
The Strauss Center’s Integrated Cybersecurity Studies program pioneers a uniquely-interdisciplinary approach to the study of cybersecurity issues.

The Cybersecurity Operations Center
A first-class facility designed to spur innovative cybersecurity-related research, improve cybersecurity education, and enhance the reputation of UT Austin as a creative leader in the research and operational realms.
MEET OUR FACULTY & RESEARCHERS
CYBERSECURITY
- Facts & Figures
- Accreditations
- Maps and Directions
- Faculty Distinctions, Awards and Honors
- Engineering Honors
- Computer Engineering
- Global Programs
- Student Organizations
- Peer Teachers
- Fast Track: Optimizing the transition from Undergraduate to Graduate Studies
- Admissions and Aid
- Entry to a Major Process
- Scholarships and Financial Aid
- Research Areas
- Undergraduate Research
- Seminars and Distinguished Lectures
- Industry Capstone Program
- Industrial Affiliates Program
Cybersecurity
Research faculty, riccardo bettati.
- Professor, Computer Science & Engineering
- Associate Department Head, Computer Science & Engineering
- Office: PETR 102B
- Phone: 979-845-5469
- Email: [email protected]

Martin Carlisle
- Professor of Practice, Computer Science & Engineering
- Office: PETR 102C and PETR 221
- Phone: 979-862-7928
- Email: [email protected]

Paula deWitte
- Professor of Practice, Computer Science & Engineering and Civil & Environmental Engineering
- Office: PETR 225
- Phone: 979-845-7398
- Email: [email protected]

- Office: PETR 429
- Phone: 979-845-4359
- Email: [email protected]

- Eppright Professor in Engineering
- Presidential Impact Fellow
- Office: PETR 239
- Phone: 979-845-2475
- Email: [email protected]

Drew Hamilton
- Director, Texas A&M Cybersecurity Center
- Office: PETR 223
- Phone: 979-845-2758
- Email: [email protected]

- Associate Professor, Computer Science & Engineering
- Office: PETR 236
- Phone: 979-845-5485
- Email: [email protected]

Robert Lightfoot
- Associate Professor of Practice, Computer Science & Engineering
- Office: PETR 422
- Phone: 979-845-2611
- Email: [email protected]

Jyh-Charn (Steve) Liu
- Office: PETR 435
- Phone: 979-845-8739
- Email: [email protected]

Dmitri Loguinov
- Office: PETR 209
- Phone: 979-845-0512
- Email: [email protected]

Nitesh Saxena
- Associate Director, Texas A&M Global Cyber Research Institute
- Engineering Dean’s Research Fellow
- Office: PETR 238
- Phone: 979-845-2776
- Email: [email protected]

Chia-Che Tsai
- Assistant Professor, Computer Science & Engineering
- Office: PETR 228
- Phone: 979-845-4460
- Email: [email protected]
Courtesy Appointments
- Professor, Electrical & Computer Engineering
- Affiliated Faculty, Computer Science & Engineering
- Office: WEB 333M
- Phone: 979-488-4551
- Email: [email protected]

J. Maurice Rojas
- Adjunct Faculty, Computer Science & Engineering
- Professor, Department of Mathematics, College of Arts and Science
- Office: BLOC 620C
- Phone: 979-845-6028
- Email: [email protected]

- Request Info
- Check Status
Information Technology PhD Program
Doctoral Program
The PhD in Information Technology provides a research-intensive focus in the interdisciplinary areas of information systems, cyber security, data analytics and Artificial Intelligence (AI). This program prepares individuals for careers in academia, government, and/or industry.
Start Your Bold Future
By submitting this form, I agree that UTSA may contact me by email, voice, pre-recorded message and/or text message using automated technology.
Please enable javascript in your browser

Why Pursue an Information Technology PhD
Commitment to research and a passion for teaching are two of the qualities that distinguish both our doctoral faculty and our graduates. Doctoral students work closely with faculty members in small classes, seminars, research projects and other assignments, aimed towards developing the analytical skills competencies to conduct independent quality research. Full-time professionals can balance career and education by completing the program as a part-time student.

Research Opportunities
In the Alvarez College of Business, faculty consistently publishes in premier information systems journals, such as MIS Quarterly , Information Systems Research , and Journal of Management Information Systems , and premier cyber security and data analytics journals such as IEEE Transactions on Dependable and Secure Computing , IEEE Transactions on Information Forensics and Security , and IEEE Transactions on Big Data . Faculty publications are also listed as highly cited (top 1% in discipline) and hot (top 0.1% in discipline) on the Thomson Reuters (now known as Clarivate Analytics) Web of Science database. In turn, this also helps students keep current and aware of trends/changes in the fields of Information Systems, Cyber Security, Data Analytics and AI.

Register for an Info Session
Interested in learning more about UTSA’s Carlos Alvarez College of Business Information Technology PhD program? Register to attend an upcoming Information Session where you’ll have the opportunity to review application procedures, learn admissions requirements and ask questions.

National Endorsements
UTSA has been designated as a Center for Academic Excellence (CAE) by the National Security Agency and the Department of Homeland Security in the areas of CAE-Education, CAE-Operations and CAE-Research and is one of only 10 institutions in the nation to achieve all three designations.

Careers in Higher Education and Research
The primary focus of a doctoral program is to prepare qualified candidates for academic careers in higher education, teaching, and research. Data predicts a strong demand for business school faculty for the next 15 years. Becoming a university faculty member is a gratifying experience that offers collaboration with students and other faculty, as well as fair compensation.
When you earn your degree, you will be prepared to start your professional career as an assistant professor at an academic institution. Faculty mentors at UTSA can assist you with finding the perfect job upon graduation. Program graduates are also qualified to hold research positions in government and industry.
- Admission Requirements
Application Deadlines
Funding opportunities, career options, admission & application requirements.
Applications are submitted through the UTSA Graduate Application . Please upload all required documents (listed below) on your UTSA Graduate Application. It is the applicant’s responsibility to ensure completion and submission of the application, a nonrefundable application fee, and all required supporting documents are on file with UTSA by the appropriate application deadline.
Applicants are encouraged to have their admission file completed as early as possible. All applications, required documents and letters of recommendation, if applicable, must be submitted by 5:00 PM U.S. Central Time on the day of the deadline. Deadlines are subject to change.
Full-time PhD students are generally funded with our financial package which consists of a research or teaching assistantship with paid tuition and fees for up to four (4) years. Part-time PhD students do not qualify for guaranteed funding however additional resources may be available.
For more information about graduate funding, click below.
UTSA prepares you for future careers that are in demand. The possible careers below is data pulled by a third-party tool called Emsi, which pulls information from sources like the U.S. Bureau of Labor Statistics, U.S. Census Bureau, online job postings, other government databases and more to give you regional and national career outlook related to this academic program.
Earning a Master's Degree
While in a doctoral program, a student may earn a master’s degree provided the following conditions are satisfied:
- A student must be admitted to candidacy.
- A student is eligible to receive a master’s degree upon completion of University-wide requirements and any additional degree requirements specific to the program.
- The Doctoral Studies Committee, Department Chair, and the Graduate Associate Dean of the College must recommend students for the degree.
- The student must apply for graduation by the published deadline the semester prior to awarding the doctoral degree.
- All required coursework in the doctoral program at the time of admission to candidacy must have been taken within the previous six years.
- If the master’s degree requires a thesis, the degree cannot be awarded on the basis of the doctoral qualifying examination.
- Students will not be approved for an additional master’s degree in the same field in which an individual has previously received a master’s degree.
Course Offerings & Schedule
The Ph.D. in Information Technology can be either a full or part-time program.
Most courses are offered during the day and full-time students must enroll for nine hours in the fall semester, nine hours in the spring semester and three hours in the summer semester. We do not recommend working full-time if you plan to pursue the full-time program.
This program is does not offer a hybrid or fully online modality. All PhD programs in the college are in-residence and admitted students are expected to complete the program in-person.
PhD full-time students normally serve as either a teaching assistant or research assistant throughout the program. These experiences are an important part of the training and overall doctoral experience.
Graduate Placements
- Binghamton University – SUNY
- Bissantz Software Co. Augsburg, Germany
- California Polytechnic University
- Ernst & Young
- Kennesaw State University
- Idaho State University
- Kansas State University
- Lamar University
- Louisiana Tech University
- LSU Shreveport
- San Diego State University
- Southwestern University of Finance & Economics, China
- Tecnológico de Monterrey
- University Al Ain Abu Dhabi, UAE
- University of Alabama at Birmingham
- University of Colorado – Denver
- University of Health at Bethesda
- University of Houston
- University of Montana – Missoula
- University of Nevada at Reno
- University of Portland
- University of Texas Rio Grande Valley
- Uniformed Services University of the Health Sciences
- U.S. Government
Frequently Asked Questions
Admission process, what are the key factors on which admissions are based, and who decides.
Admission is based on
- Undergraduate transcripts (and graduate, if applicable)
- Standardized test scores
- Recommendations from former professors or employers who can speak to your ability to do doctoral-level work at UTSA
The admission committee is looking for evidence that you understand the specific nature of the program that you are applying for, that you can articulate your scholarly intentions that fit with the research interests of current faculty and that you are academically prepared to succeed in the program.
The most important part of your application is your statement of purpose. Although outstanding grades and test scores are important, you should construct a clear, persuasive, well-written statement of purpose in order to be competitive.
I am completing an undergraduate degree. Am I eligible to apply?
Yes; however, you must take additional leveling courses and complete any graduate coursework where your academic background is insufficient. The catalog states that the PhD requirement is “66 hours beyond the master’s degree.” Therefore, the time required to complete a PhD will most likely be much longer for a candidate without a master’s degree than for a candidate with a master’s degree.
When are admission decisions made?
Admission decisions are typically made in March; however, exceptionally qualified candidates are considered earlier.
Can I submit GMAT/GRE test scores after the application deadline?
No. All application documents must be received by the application deadline and incomplete applications will not be considered. You will be required to upload unofficial copies within the Graduate Admissions Application.
Can I wait to submit the foreign credential evaluation (ECE transcript) until after I am accepted to UTSA?
No. Foreign credential evaluations must be received by the application deadline for your application to be processed. Processing time may take up to three weeks, and students should plan accordingly with the admission deadlines of the programs for which they are applying.
Do you accept WES transcript evaluations?
All NACES accredited evaluators are accepted.
Program Expectations
What should i expect as a doctoral student.
Your role and the expectations will change as you progress in the program. Initially, your role will be as a student with the expectation that you attend and participate in doctoral seminars with other students. Expect to read a great deal and write papers.
To prepare to become a university professor, you will work closely with faculty members to learn how to teach. You will start as a teaching assistant and work toward teaching classes independently.
Conducting research is another area of focus where you will work closely with faculty on research projects. Under the direction of a faculty committee, you will conduct original research that will be the basis for your dissertation.
How long does this program take to complete?
Most students will need four years. Plan for at least two years to complete the coursework. Add another year to pass the comprehensive exams, develop a dissertation topic and defend your dissertation proposal. Dedicate your final year(s) to dissertation research.
Are PhD students required to teach?
Teaching is crucial to your academic career and job prospects. Every PhD student should gain teaching experience before graduating. Initially, students may work as research assistants for faculty members and may also assist in teaching various courses. For students who receive stipends, they will most likely teach an undergraduate course at the Carlos Alvarez College of Business during their program.
What are the research requirements of the PhD program?
The PhD program requires students to research while they complete formal coursework and during the summers. As research assistants, students work with faculty members in joint research activities and pursue their research objectives under the supervision of faculty members. The goal is to create papers to present at academic meetings and submit to research publications by the time the student is ready to begin their dissertation research. To be competitive in the academic job market, students should prioritize producing papers and publications while in the program.
As a PhD student, who will advise me?
Your program admission will identify an initial PhD advisor. However, as your interests and research agenda develop toward preparing a dissertation proposal, a different faculty member may emerge as the appropriate advisor for your dissertation research. Your initial advisor will help you assemble a program committee of faculty, who will advise you regarding your dissertation.
Can you waive my application fee?
You may request an application waiver if
- You are a McNair Scholar
- Active-duty military or a veteran of the US Armed Forces
- If you are an applicant who has attended a PhD Project Conference
Please complete the Request to Waive Doctoral Application Fee if you meet one or more of the above criteria.
Approved applicants will receive a single-use coupon code to enter into the payment field of the online application.
Can you waive the GMAT/GRE test score requirement?
We do not offer waivers for standardized test scores.
Is there a waiver for the TOEFL/IELTS exam requirement?
TOEFL scores may be waived for international students from countries where English is the official language or for non-citizens of the United States who have earned a regionally accredited bachelor’s degree or higher in the United States (or other countries where English is the official language) as indicated in the Graduate Catalog ( https://catalog.utsa.edu/policies/admission/graduate/internationalgraduatestudents/ ).

Graduate Advisor of Record
Philip Menard, PhD
210-458-8023
Center for Information and Cyber Security (CICS)
Search form.
- Service/Events
You are here
Sfs phd program.
NOTE: The scholarships described below are for DOCTORAL students only.
NSF granted this award under the title ‘SFS-NEW: Advancing Learning and Leadership Through an Integrated Multidisciplinary Doctoral Program in Information Assurance’. See the documents below for more details.
Cybersecurity Guide
Everything is bigger in Texas, including cybersecurity educational opportunities
- Associate degree
- Bachelor’s degree
- Master’s degree
- Cybersecurity certifications
Cybersecurity in Texas
- Jobs in Texas
This guide discusses cybersecurity schools in Texas. It contains information about cybersecurity training programs and career opportunities.
Finally, there is extensive information about getting an online cybersecurity degree in Texas.
Cybersecurity is a growing field all across the country, but certain states are definitively more prepared for the new digital frontier and are taking steps to ensure their place as leaders as the national economy develops.
Texas is one of the strongest contenders for the leader of cybersecurity development and continuation, largely thanks to its excellent digital infrastructure and economic advantages that allow the state’s various public and private organizations to pour money into this industry.
Silicon Valley might be the current cybersecurity and overall digital tech hub in the world, but Texas has been at the forefront of technological development and new innovations for much longer.
As a result, it’s no surprise that cybersecurity has a strong foothold in Texas both in terms of educational opportunities and economic foundations.
With a GDP of $1.6 trillion, Texas has lots of money to fund higher education opportunities and cybersecurity developments. As a result of the surplus, many industries have a home in Texas, offering ample appointment opportunities for graduates fresh out of college.
Part of this growing success is owed to the Texas Cybersecurity Council , which was created specifically to forge partnerships between public sector organizations and private industries in the realm of cybersecurity.
Aside from economic or educational development, there are lots of cybersecurity workshops and conferences in Texas where professionals can network or improve their skills.
The most important organization is CyberTexas , an organization that sponsors younger cybersecurity enthusiasts and allows for easy networking.
The Texas Cyber Summit is another good event, as it features several contests and opportunities to prove yourself among other cybersecurity talents.
Cybersecurity education in Texas
There’s no doubt that cybersecurity education in Texas is in a league of its own. Out of all of the Lone Star State’s universities, the University of Texas at San Antonio is often the number one choice for budding cybersecurity professionals.
UT San Antonio consistently ranks high among the nation’s top universities for studying cybersecurity.
While UTSA’s cybersecurity program is robust and effective, there are plenty of other schools and opportunities available to provide a plethora of training pathways for new professionals.
UT Dallas is another important cybersecurity University in Texas, in part due to a renewed focus on cybersecurity starting in 2012. In 2016, UT Dallas formed the Center for Engaging Women in Cybersecurity , which emphasizes closing or narrowing the gender gap in cybersecurity.
Related resources
- Cybersecurity programs in Dallas
- Certs, and training in San Antonio
- Master’s degree options in Houston
- How to spot and protect yourself from a phishing attack
- Your roadmap for finding the right cybersecurity job
UT Austin has the Center for Identity, which is partnered with Equifax and focuses on identity theft, fraud, and privacy. Southern Methodist University has the Darwin Deason Institute for Cybersecurity , which is partnered with Raytheon, a well-known tech defense company with a significant presence in Texas.
Angelo State University Regional Security Operations Center (RSOC) has with the Texas Department of Information Resources that will provide cybersecurity services to local, regional, and state entities to strengthen the region’s cybersecurity posture.
Several universities in Texas receive special CyberCorps Scholarships , offering free tuition and a worthwhile stipend for any students who manage to earn the scholarship.
The Texas Cybersecurity Council illustrates Texas’ commitment to cybersecurity. This broad organization helps to organize university curriculums and ensure that Texas education remains at the forefront of cybersecurity development for the foreseeable future. This has resulted in many of the cybersecurity degrees and certificates offered in Texas also being offered in online formats.
Cybersecurity associate degrees in Texas
There are about ten schools that offer associate degrees in cybersecurity . Most two-year schools in Texas don’t offer their cybersecurity associate programs online.
However, many classes that can count toward a cybersecurity degree are offered in an online format, potentially allowing students to complete a hybrid version of the degree or take distance classes while working toward a bachelor’s degree in the long-term future.
Amarillo College
Collin county community college district, el paso community college, hill college, richland college, san antonio college, san jacinto community college, south texas college, st philip’s college, texas state technical college williamson county, southern new hampshire university, cybersecurity bachelor’s degrees in texas.
Bachelor’s degrees in cybersecurity are offered at several universities. The time and resource investment needed to attain a four-year degree is not insignificant, and this decision can change your life.
There are various options for earning a bachelor’s degree that will open a career in cybersecurity. This section lists Texas’s most relevant degree programs if this is your chosen field.
Campus-based bachelor’s degree
Angelo state university, university of north texas, online bachelor’s degree, cybersecurity master’s degrees in texas.
If your educational goal is to specialize in a particular aspect of cybersecurity or if you want to advance to the top levels of the profession, a master’s degree in cybersecurity might be your best option.
Campus-based master’s degree
St. mary’s university, stephen f. austin state university, university of houston, uc berkeley school of information, online master’s degree, our lady of the lake university, southern methodist university, the university of texas at tyler, university of dallas, georgia tech.
Cybersecurity certifications in Texas
S ome certificates in cybersecurity specialize in Information Assurance , Computer Networking, and other related fields or interests. These certifications can open entry-level doors for students who wish to learn the basics of cybersecurity and jump into the job market quickly.
Central Texas College
Texas a&m university, the university of texas at dallas, the university of texas at el paso, university of texas at dallas, university of texas at el paso, cybersecurity bootcamps in texas.
In addition to the programs outlined above, cybersecurity boot camps are another viable option for people interested in quickly jumping into the cybersecurity profession.
Often, cybersecurity boot camps are designed for professionals who already have some technical background in computer science or information technology but are quickly looking to retool and learn cybersecurity-specific tools and technologies.
Whether a recent graduate or a seasoned professional, cybersecurity boot camps are designed to teach in-demand skills.
In addition to helping jumpstart a cybersecurity professional network, which can lead to future job opportunities, cybersecurity boot camps also give participants the skills needed to take popular certifications such as the CompTIA Security+ or Certified Ethical Hacker .
Rice University
Texas a&m international university, university of texas–austin, university of texas–san antonio, cybersecurity jobs in texas.
Texas has lots of educational opportunities for cybersecurity professionals, but what about after graduation?
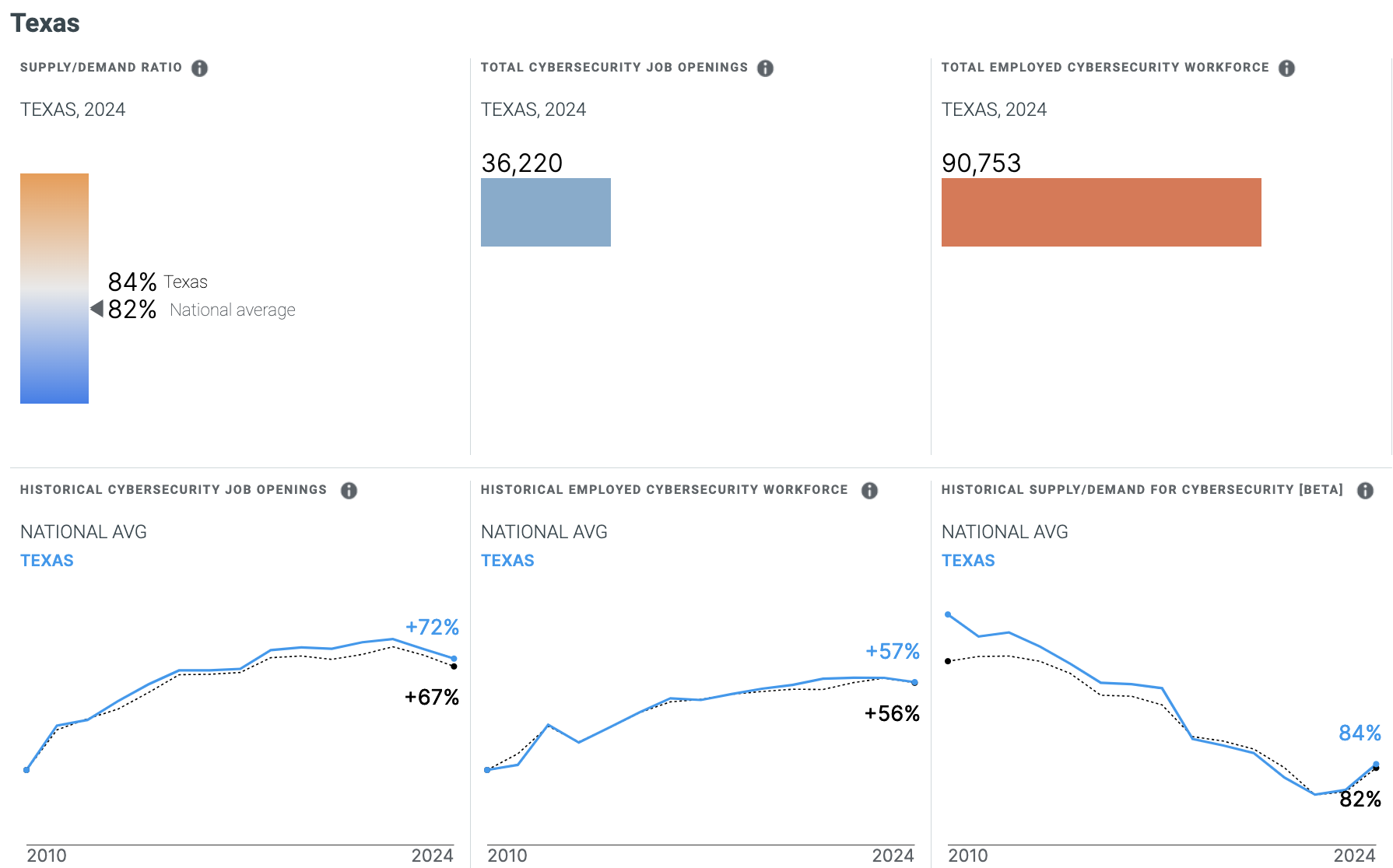
According to CyberSeek , a leading cybersecurity supply and demand website, there are currently around 36,220 cybersecurity job openings in Texas alone, compared to a cybersecurity workforce of over 90,753.
These jobs range from entry-level positions up to full-on managers and architects. Some of the more common jobs for cybersecurity professionals in Texas include cybersecurity engineers , analysts , security consultants , IT auditors, vulnerability analysts, network engineers, and architects .
This is great news for any cybersecurity professionals who want to stay in the field for their careers. It’s entirely possible to start at the bottom of a company’s ladder and work your way up to a management position thanks to how many open spots are currently available.
What do Texan cybersecurity jobs offer in terms of salary? It’s all good news. The Bureau of Labor Statistics indicates that average information security analysts earn an annual wage of about $119,480 per year.
These numbers accurately reflect how much Texas is willing to pay for skilled cybersecurity professionals and should provide plenty of incentive to attract new talent in the coming years.
Because some places in Texas offer extremely low costs of living, the above salaries could potentially stretch even farther, boosting the standard of living of those cybersecurity techs who can work remotely and live in affordable towns.
Cybersecurity in Texas at the city level
San antonio and new braunfels.
There’s no doubt that San Antonio is arguably the best place for new cybersecurity professionals to check out. It’s gained Military City USA and Cyber City USA titles because of its economic development and focus in those spheres; indeed, the military has many cybersecurity recruitment centers in San Antonio to locate graduates fresh out of college.
In addition, the Air Force has a significant presence in San Antonio, so both private sector and government job opportunities are likely to be plenty.
CyberSeek has more data to analyze:
- 4,541 cybersecurity jobs open
- 10,935 currently employed cybersecurity workers
- 83 percent supply/demand ratio for cybersecurity workers
Austin and Round Rock
Austin is another rapidly developing metropolitan area, both in terms of cybersecurity and in general employment. As a tech center and one of the most modern cities in the state, it has more than doubled its cybersecurity workforce within the last ten years.
As Austin is the capital of the state, you can bet that this growth will only continue as long as Texas remains on an upward trend.
Let’s examine what the CyberSeek data shows:
- 5,152 cybersecurity job openings
- 12,676 currently employed cybersecurity workers
- 84 percent apply/demand ratio for cybersecurity workers
Houston area
Houston is developing rapidly in the cybersecurity sphere, as well, although its metropolitan area supports a larger number of suburban neighborhoods and smaller cities and towns.
As a result, it’s possible to find more affordable housing within a drivable distance of the Houston metropolitan area in one of these surrounding territories.
CyberSeek has some more data we can examine:
- 6,063 total cybersecurity job openings
- 15,176 currently employed cybersecurity workers
- 92 percent supply/demand ratio for cybersecurity workers
Dallas, Fort Worth, and Arlington area
Dallas’ metropolitan area is similarly bustling. Its proximity to the Fort Worth airport offers many economic opportunities for many airlines, specifically American Airlines and Southwest Airlines, which keep primary hangers in this region.
In other words, this area should be a key job opportunity for cybersecurity professionals who want to segue into aviation or government contracts; Lockheed Martin keeps a presence here, as well.
Let’s look at the CyberSeek data for this region:
- 16,217 job openings
- 33,978 currently employed cybersecurity workers
- 81 percent supply/demand for cybersecurity workers
While any of these large metropolitan areas will be a good choice for new cybersecurity professionals, San Antonio, Austin, and Dallas are the three where employment is most likely.
Texas and cybersecurity
All in all, Texas has been a state defined by the frontier for all of its history. While the physical frontier may have faded into the annals of history, the digital frontier is still being trailblazed at this very moment.
Young cybersecurity professionals who want to reach their highest potential and maximize their chances for employment would do well to study in Texas and seek jobs there after graduation.
Post Graduate Program in Cybersecurity
The texas mccombs cybersecurity program equips students with industry-ready skills to combat cyber threats.
- 20 Weeks Online
- Certificate of Completion from UT Austin
- Live mentorship with experts
Enquire: +1 512-212-4186

What makes the Cybersecurity Program Unique
Promising career.
- 93% of leaders observe a yearly rise in skill shortage
- 3.5 million job positions in cybersecurity by 2025
- Cybersecurity professionals earn a median salary of $103,590
Comprehensive Curriculum
- Total duration: 20 Weeks
- 60 hours of recorded learning material
- 18 hours of live classes
Hands-on Learning
- Mentored learning sessions with industry practitioners , focusing on doubt-resolution and application based practice
- Supervised lab sessions to practice concepts and experiment in a safe environment
- 12+ hands-on industry projects and an optional capstone project to consolidate your learnings and demonstrate these to potential recruiters
Apply core foundational skills to industry projects with expert guidance.
Gain the most relevant knowledge in the market through a carefully designed curriculum., get industry insights through mentored learning sessions with cybersecurity experts, experience personalized support throughout your learning journey, join ut austin's cybersecurity program for working professionals.
Live Virtual Sessions by UT Austin's Faculty | Mentorship from Experts | 20 Weeks
Earn a Professional UT Austin Cybersecurity Certificate
Enhance your resume with the certificate of completion from the university of texas at austin, executive education - custom programs.
Financial Times, 2022
Information Systems Graduate Programs

US News & World report, 2022

Syllabus designed for professionals
The Post Graduate Program in Cybersecurity comprises 5 milestones: a strong foundation in cybersecurity, network security, in-depth exploration of various cyber attacks, designing security controls for resilience, and GRC (Governance, Risk and Compliance).
This course is suitable for individuals with limited experience in IT and Technology or those outside these fields. It provides the essential fundamentals needed for the program, enabling a streamlined learning journey.
Acquire essential knowledge in Risk Management, Cryptography, and emerging trends in cybersecurity.
- Careers in Cybersecurity
- Introduction to CIA triad
- Basics of Authentication
- Risk Management
- Emerging trends - Artificial Intelligence & Cybersecurity, Operations Technology & Internet Of Things,
- Global Cyber warfare
- Understanding Cryptography
- Cryptocurrency & blockchain
- Gain insights on Importance of Cybersecurity
- Develop the ability to choose the appropriate authentication methods
- Identify & assess different types of Risks
- Gain hands-on experience or practical exercises using AI-driven tools for cybersecurity use cases
- Discover the different patterns in the Cyber Attacks going on as a part of Global Cyber Warfare
- Familiarize yourself with the cryptocurrency transactions & the crypto payment ecosystem in today's cyber world.
Skill yourself with Network security concepts and experience network security tools such as firewall for safeguarding your assets.
- Networking basics - OSI Model, IP addressing, TCP/IP, Network services, Public/ Private IP, load balancing, Proxy
- Network segmentation
- Virtual Private Network (VPN)
- Next Generation Firewall (NGFW)
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
- Develop the most in demand skills in a majority of IT job roles such as Networking & Network security
- Practice the skill of capturing and analyzing network traffic for cyber investigations & troubleshooting
- Understand the implementation of VPN for securing the remote workforce
- Explore the Next Generation Firewall (NGFW) for network security
- Distinguish between security technologies like IDS & IPS and their usage
Discover the cyber attack methodology and learn to view attacks from the lens of an attacker.
- MITRE ATT&CK
- Cyber Kill Chain
- APT (Advanced Persistent Threats)
- Ransomware Attacks & Cyber Insurance
- Attacks on Cryptography
- Attacks on Users
- Attacks on Networks
- Attacks on Endpoint
- Attacks on Applications
- Attacks on Data
- Attacks on Cloud
- Understand adversary Tactics,Techniques and Procedures to enhance threat detection and response strategies.
- Identify and disrupt cyber threats by understanding the different stages of a cyber attack
- Recognize and defend against highly skilled and motivated attackers with persistent access
- Mitigate financial risks from ransomware incidents through effective cyber insurance strategies
- Secure cryptographic systems by identifying and mitigating vulnerabilities and weaknesses
- Develop comprehensive security strategies to protect critical components against various attack vectors.
Discover effective methods for recognizing and applying appropriate cybersecurity strategies to combat diverse cyber threats.
- Types of security controls
- Endpoint security controls- Antivirus, Endpoint Detection and Response (EDR), Extended Detection and Response (XDR)
- Identity and Access Management (IDAM)
- Security Awareness
- Data Security Controls - Data Loss Prevention (DLP), Cloud Access Security Broker (CASB), Data Encryption, Masking
- Authentication Implementation
- Deep dive into Security Information and Event Management (SIEM)
- Threat Intelligence
- Incident Response
- Incident Response Playbooks
- Differentiate between the types of security controls & their implementation
- Delve deeper into the protection mechanisms for endpoints such as Laptops, Desktops & Servers
- Identify & classify different types of Data. Configure policies for preventing data leakage from enterprise networks
- Monitor the signs of ongoing cyber attacks within a network with alerts from authentication servers
- Learn about continuous security monitoring with advanced threat detection
- Learn to proactively gather actionable intelligence & stay informed about the threat landscape
- Plan to respond to incidents and understand the incident response lifecycle
Gain understanding of various standards, regulations and frameworks to help build a strong organizational security posture.
- ISO 27001:2022
- Regulations, standards, and legislation
- General Data Protection Regulation (GDPR)
- Digital Data Protection Act (DPDP)
- Payment Card Industry Data Security Standard (PCI DSS)
- Digital Operational Resilience Act (DORA)
- Understanding Audit Process
- Conducting an internal audit
- Certification Audits
- Third-party risk management
- Comprehend the compliance requirements in relation to the security standards such as ISO 27001
- Have technical expertise in documenting the requirements for dat protection standards & laws such as GDPR, and DPDP
- Recognize the need for security specific to Financial sector by studying the intricacies of DORA
- Practice the preparation of internal audits and how to conduct them yourself confidently
- Recognize and treat the risks associated with supply chain management
Delve deeper into cloud security controls and understand the methodology behind securing data on cloud.
- Cloud Security in different platforms
- Cloud platform and Infrastructure Security
- Securing Data on Cloud
- Incident Detection and Response in Cloud
- Implement robust security measures tailored to Microsoft Azure for enhanced protection
- Safeguard cloud infrastructure against cyber threats and vulnerabilities through effective security controls.
- Ensure the confidentiality, integrity, and availability of data stored on cloud platforms through encryption, access controls, and data loss prevention measures.
- Detect and respond to security incidents in cloud environments promptly to minimize impact and protect sensitive assets
Equip yourself with a solid grasp of penetration testing methodologies and gain hands-on experience through interactive video and workbooks, ensuring industry readiness.
- Introduction to Penetration Testing
- Techniques of Penetration Testing
- Infrastructure Penetration Testing
- OWASP Top 10 & Application Security
- Web Application Penetration Testing
- Practice the fundamental skills of penetration testing
- Differentiate between different methods used while performing the penetration tests
- Scanning the internal infrastructure and exploiting vulnerabilities to secure the network
- Have an understanding of application security vulnerabilities such as OWASP Top 10
- Understand how pentesting of a web application differs from Infrastructure penetration testing
Test your knowledge from the cybersecurity program.
- Setting up Security Operations & Monitoring using SIEM
- Planning Security Operations & Monitoring using Risk Control mapping
- Research and Prepare your analysis whether ChatGPT or Gemini should be allowed by an organization
Get ready for the CompTIA Security+ certification exam.
- General Security Concepts
- Threats, Vulnerabilities, and Mitigations
- Security Architecture
- Security Operations
- Security Program Management
- Prepare for the Security+ exam by learning about the key concepts.
- Get complete coverage of the domains measured in the Security+ examination.
- Recap the concepts learned in the mandatory modules with a specific focus on the Security+ certification exam
- Utilize the question bank to practice important concepts
Learn to use Python for cybersecurity
- Introduction to Python
- Network analysis with Python
- Cracking passwords with Python
- Encryption with Python
- Learn to use python to perform and automate tasks.
- Understand the usage of python programming for network analysis, password cracking and encryption.
Learn in-demand Cybersecurity Tools
Master latest tools and languages used by cybersecurity specialists.
Meet your UT Faculty and Industry Experts
Learn from the top, world-renowned faculty at UT Austin

Dr. Kumar Muthuraman
Faculty Director, Centre for Research and Analytics

Aniket Amdekar
General Manager - Cyber Defence Education

Abdul Mateen
Information Security Analyst

Vikas Singh Yadav
Chief Information Security Officer

Peter Christy
Tech Lead (Security)

Thomas Mulroy
Cybersecurity Program Manager and Engineer in Automotive Industry

Matthew lindwall
Senior Cybersecurity Risk Analyst | GCIH | GCFA

Prashant Gupta
Technical Lead

Mayan Mohan

Farhad Sajid

Ravindra Joshi
Partner Build Consultant

Anurag Goyal
Senior Security Associate

The Great Learning Advantage
Gain industry expertise from renowned academics and professionals. Hands-on projects and lab sessions go beyond theoretical concepts, ensuring practical knowledge. Stay motivated and on track with personalized support from program managers, and expand your network through valuable connections.
BUILD YOUR CYBERSECURITY EXPERTISE
Learn from Industry Leaders
- Curated content featuring renowned academics and industry leaders, blending theoretical knowledge with practical examples and demonstrations
- Interactive mentor sessions led by industry professionals, offering concept revision, doubt clarification, and case-based learning opportunities
GAIN REAL-WORLD INSIGHTS
Hands-on, Practical Training
- Lab sessions to learn real-world applications of concepts
- Case Studies, 8 lab sessions and 12+ projects that help implement concepts
- Optional Capstone project to consolidate your learnings
TAILORED LEARNING EXPERIENCE
Personalized Support and Guidance
- Dedicated Program Manager to track your learning progress
- Feedback on submissions and periodic interaction with your program manager to ensure you stay motivated and on track
- Timely resolution of academic and non academic queries
Who is this program for?
The Post Graduate program in cybersecurity empowers you to align your learning with your professional aspirations, whether you aim to pursue a cybersecurity career or advance as a strategic leader.

Young professionals:
Learn the core concepts of cybersecurity and build a solid foundation using the in-demand market skills. You will benefit from this if you are:
- A professional looking to transition their career in cybersecurity.
- A fresh graduate wanting to break into the cyber security domain.

Senior and mid-level managers:
Enhance your expertise in safeguarding IT and Cloud infrastructures with advanced cybersecurity skills, preparing you to adeptly navigate and mitigate evolving digital threats.
- An IT infrastructure manager wanting to upskill with cybersecurity
- A senior and mid-level manager involved in cybersecurity governance and decision making for your organization
Why Our Learners Choose the Post Graduate Program in Cybersecurity

I have spent the last 20 years working in Healthcare and made the decision to change careers. After lots of research, I decided on Cybersecurity. This is a growing field that will provide lots of opportunities in the future for myself. Great Learning has provided me with the education needed to take this next step forward in to a new career. Along with the lectures, the provided lab environment allows me to perform hands on activities to further my learning. This is invaluable to me as I am a hands on type of learner.
Jamie Washington
Respiratory therapist, Athens Limestone Hospital
.jpg)
This program has been a great learning experience. I am really pleased with the trainers and the criteria. The hands-on labs are excellent and will really teach you a lot. I recommend taking this program with Great Learning.
Troy Marshall
Systems Support Specialist III, Texas Water Development Board
.jpg)
Having heard a lot about this field, I decided to challenge myself with the PGPCS program. The lab sessions have been an intriguing revelation. My awareness in cybersecurity is now backed by concrete practical studies. It has been great with Great Learning.
Eric Aggrey-Quashie
Colonel, Ghana Armed Forces
.jpg)
As a legal professional, I highly recommend PGPCS. The program is a great option for a 21st Century lawyer. It has noticeably helped me gauge how cyber criminals plan and execute their malicious activities.
Modicai Donga
Chief Operations Manager/Lawyer, SV MDLADLA AND ASSOCIATES

I came across the program through Great Learning's LinkedIn page in May 2022. The flexible payment options, live lectures and the hands on lab projects have helped me become a cybersecurity expert.
Abiola Olufunke Famoroti
CEO, Abbatoir Services
.jpg)
The Post Graduate Program in Cybersecurity has gone far beyond my expectations. The self-paced course allows me to accurately understand the concepts. I feel confident that after completing this program, I can begin a career in cybersecurity.
Kristen Sharp
General Director, Loc’VTT Sanc’R

After being in the security space for 3 years, I realized that I didn't have any hands-on experience which is an important requirement for a cybersecurity expert. The PGPCS program ensures that the students have a great experience.
Asuzu Oluchukwu Justina
Head, Operational Resilience, AXA Mansard
.jpg)
What I liked about PGPCS was the structure and content. Though cybersecurity is mile wide and a foot deep, I found that the pace, combination of classes and assignments helped me learn all concepts quite seamlessly.
Sri Arepally
Platform Engineering , DataTechies
Program Fees
Certificate from

- High-quality learning content from UT Austin & Global Faculty
- Live Mentored Learning in Micro-classes (up to 30 learners)
- Personalized Academic & Non-Academic Support
Start learning cybersecurity with easy monthly installments, with flexible payment tenures as per your convenience. Reach out to the admissions office at +1 512-212-4186 to know more.

*Subject to approval by payment partners based on applicable regions & eligibility. e.g: dLocal - applicable for learners from Brazil, Colombia & Mexico only
Admission Process
Apply by filling a simple online application form
Attend an application screening call
An offer letter will be rolled out to selected candidates. Secure your seat by paying the admission fee
Upcoming Application Deadline
Our admissions close once the requisite number of participants enroll for the upcoming batch. Apply early to secure your seat
Deadline: 9 th May 2024
Cohort start dates.
18 th May 2024
Frequently Asked Questions
The University of Texas at Austin’s (UT Austin) McCombs School of Business offers a Post Graduate Program in Cybersecurity that equips students with the knowledge and skills required to interpret cyber attacks and create reliable Cybersecurity systems using real-world resources and industry standards. The course is taught using a mix of engaging lectures, hands-on lab sessions, and a capstone project.
Students will have the chance to use their newly acquired knowledge to address current cybersecurity problems. They also gain access to committed mentors and career advice to aid in their transition into a lucrative career in Cybersecurity. The course is a fantastic way to network with thought leaders in the field and learn how to secure digital infrastructure for those passionate about cyber defense.
UT Austin is ranked #6 university worldwide in the category of Executive Education - Custom Programs by Financial Times 2022 rankings and ranked #6 in the category of Information Systems Graduate Programs by the U.S. News & World Report 2022.
Yes, at the end of this Cybersecurity course, students will have the option to execute a 2-week capstone project. Practitioners and decision-makers are taken into consideration when choosing the capstone project.
Learners can showcase their abilities and knowledge through the capstone project. They will make use of a combination of hands-on knowledge and expertise from security research.
(Note: However, it is optional for students to take the capstone project.)
The faculty members are highly accomplished academicians and practitioners in the field of Cybersecurity from UT Austin McCombs School of Business and other prestigious companies like EY and Ignite Technologies, among many others.
Great Learning collaborates with UT Austin McCombs School of Business and provides industry experts, student counselors, dedicated program support, and guidance to ensure students get hands-on training and live personalized mentorship on applying concepts taught by UT Austin and other faculty members.
The services include:
- A dedicated program manager will monitor your learning progress throughout the program.
- You will receive feedback on your submissions and regular communication with your program manager to keep you motivated and on track.
- You will receive timely resolutions to all inquiries, both academic and non-academic.
The coursework comprises live and self-paced hands-on activities. For the self-paced hands-on activities, ensure the following minimum recommended system specifications are met.
For Windows OS:
- Processor (CPU): Multi-core Processor (quad-core or higher processor). E.g., Intel Core i5 or AMD Ryzen 5
- Storage: 256 GB (SSD recommended)
- Operating system specification: A 64-bit version of Windows 10 (or above) is recommended as the host operating system. [Note: Windows 10 Home edition is not supported]
- CPU should support virtualization technology (Intel VT-x or AMD-V)
For Mac OS:
- Processor (CPU): Multi-core Processor (quad-core or higher processor). E.g., Intel Core i5 or higher.
- Operating system specification: MacOS version that supports virtualization. Eg. macOS 10.13 High Sierra and later
Applicants should have 1+ years of work experience in the IT domain. For graduates & non-IT candidates, we offer a free pre-work course to build your fundamentals in hardware, operating systems, virtualization, databases, & cloud essentials.
Still have queries? Contact Us
Please fill in the form and a Program Advisor will reach out to you. You can also reach out to us at [email protected] or +1 512-212-4186 .
Download Brochure
Check out the program and fee details in our brochure
Oops!! Something went wrong, Please try again.
- --> --> Yes--> --> --> No--> -->