
- Research Security Program at Penn State

Research Security Program
Protecting open global collaboration, why is research security important.
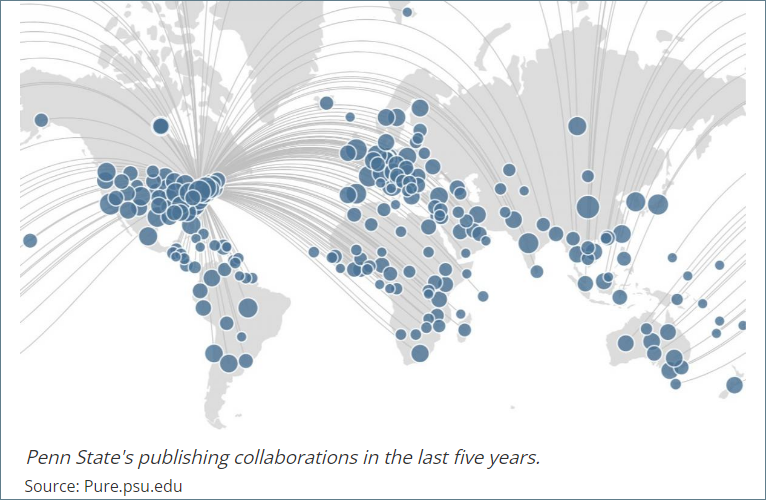
Open scientific and scholarly collaboration between scholars from all over the world is one of the cornerstones of innovation and technological advancement, and Penn State remains committed to fostering such collaboration. While the vast majority of international affiliations do not present a security risk, the Federal government has increased its attention to research in foreign countries. There have been cases at some universities in the United States where researchers have violated laws and policies aimed at preventing lapses in research security. In response to this, Penn State is establishing a Research Security Program.
What is Research Security?
Research security is a broad term that refers primarily to national security concerns surrounding research involving certain types of sensitive data, intellectual property, export controlled information, and other risks. An area which the federal government has focused on as critical to protecting the security of U.S. research is the disclosure of conflicts of interest and commitment, including relationships or affiliations with foreign entities, and research support provided by those entities.
Regulagory Background
Read more about the regulatory background as it relates to research security.
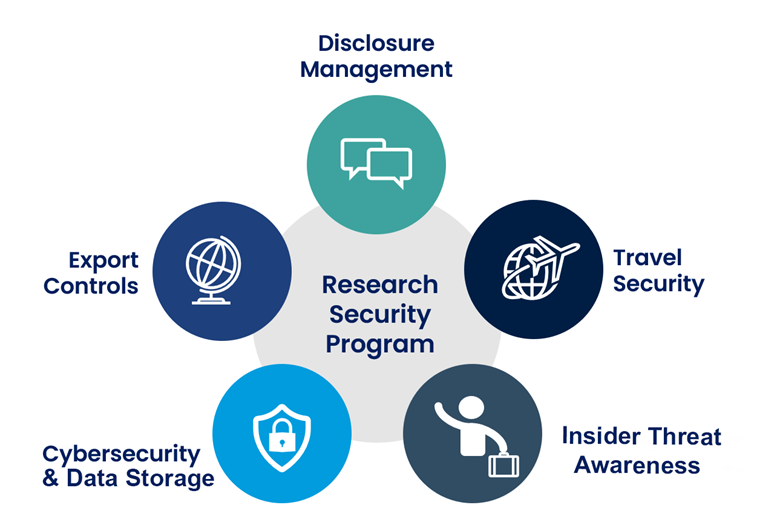
Penn State's Research Security Program
Below are the components of Penn State’s research security program, which is an interdisciplinary collaborative effort among various offices at the University. This program is a central point of contact for research security at Penn State. Please email [email protected] with any questions.
Cybersecurity
Cybersecurity is an expansive and complex area and its scope extends well beyond research. For purposes of research security, the following resources are helpful starting points.
- Office of Information Security
- Policy AD95
Research taking place under government contracts may be subject to additional security controls. For assistance with this type of research, please email the Office of Information Security (OIS) at [email protected] .
Digital Persistent Identifiers and Digital CVs
Digital Persistent Identifiers (DPIs) and Digital CVs make it easier for researchers to create and maintain a complete and up to date record of their publications and achievements in one location, thereby streamlining the grant proposal process. In addition, some federal agencies are now requiring investigators to register with a DPI service, such as ORCID, and submit biosketches and current & pending support via SciENcv. See the following University Libraries webpages for step-by-step guides that walk you through creating an ORCID ID, adding records to your profile from the PSU Researcher Metadata Database , and using SciENcv to create a biosketch:
- ORCID: Managing Your Identity
- SciENcv for Creating a Biosketch
Disclosure Management
As indicated above, disclosure and transparency surrounding relationships with, and research support from, foreign entities have been identified by the federal government as key to managing and protecting the security of our research. Researchers are expected to disclose outside financial interests and Outside Professional Activities through the Office for Research Protections (ORP). Similarly, researchers are required to disclose Other Support or Current & Pending Support in their grant and contract applications. The ORP and the Office of Sponsored Programs (OSP) work together to support the disclosure process and are available to answer questions as needed. See the following pages for more information and contacts.
- Conflict of Interest (COI)
- Conflict of Commitment (COC)
- Other Support/Current & Pending Support
- Resource : See the Faculty Outside Activities and Disclosure Guide for helpful information on what activities require disclosure, prior approval, or further review under polices RP06 and AC80.
Export Controls
The Export Compliance Officer maintains responsibility for establishing, implementing, and enforcing University-wide export compliance policies, procedures, and guidelines designed to meet or exceed the requirements of the various federal laws governing the export of goods, technology, and information, including compliance with ITAR, EAR, and OFAC regulations.
Foreign Visitors
A process for reviewing visitors to Penn State is part of the comprehensive approach to research security outlined in NSPM-33. The Visiting Scholars process is composed of reviews by a number of University offices to ensure that our esteemed visitors comply with regulatory requirements.
NOTE : Hosts of Visiting Scholars should be aware that effort from Visiting Scholars who have support from their home institutions may need to be disclosed as Other Support .
- Visiting Scholars Page
- Visiting Scholars Host Guidelines
- Policy AC01
Guidance for International Activities
- The U.S. Federal government has placed restrictions on researchers participating in Malign Foreign Talent Recruitment Programs. Review RSP's webpage on Foreign Talent Recruitment Programs for more information.
- Get started with building international relationships while staying incompliance with this helpful resource: Building Successful International Research Collaborations
Travel Security
Faculty, staff and students traveling for University purposes (regardless of the funding source) must record international travel in the Travel Safety Network database at least 30 days prior to departure as outlined in the University’s International Travel Requirements Policy TR01 . This includes travel for international research, conferences, and internships.
For more information and assistance with planning and conducting international travel, please visit Global Program’s website .
- Quick Links
- Find Info For
- Current Students
- Prospective Students
- Entrepreneurship and Commercialization
- Institutes & Centers
- Regulatory Affairs
- Sponsored Programs
- Communications
- Research Security
Purdue’s Research Security Program
Purdue University’s research security program is designed to protect intellectual capital, prevent research misappropriation, and ensure responsible management of U.S. taxpayer dollars while maintaining an open environment to foster research discoveries and innovation. The program promotes transparency, addresses conflicts of interest and commitment, provides training and information on research security, and implements processes to assess and manage potential risks associated with collaborations and data. The program includes cybersecurity, foreign travel reviews, research security training, export control training, and disclosure guidance.
Research security pertains to all Purdue research, including fundamental research and to officers, faculty, staff and students who are engaged in research at or on behalf of the University and any other individuals helping to conduct research at Purdue. This term includes graduate students, undergraduate students, postdoctoral researchers, fellows and visiting scholars. This program applies to Purdue personnel.
Protecting the Research Enterprise
All federal research funding agencies must improve and safeguard the research enterprise under White House Office of Science and Technology Policy (OSTP) National Security Presidential Memo-33 (NSPM-33) direction. Purdue and other institutions receiving over $50M in research and engineering funding must have a Research Security Program.
The US government has set forth several requirements that Purdue must comply with, which are intended to help ensure that our affiliations are protected against undue foreign influence.
Mandatory Research Security Training and Certification
Purdue is requiring any faculty members involved in federally-funded research to complete research security training and a foreign talent recruitment plan certification by Sept. 1. This mandatory training is necessary in order to satisfy new federal requirements that are intended to safeguard the academic research enterprise against the misappropriation of U.S. research and development.
Researchers who are applying for NSF or DoD federal funding will be required to certify that they are not a participant in a Malign Foreign Talent Recruitment Program during the proposal submission. The new requirement will be implemented by NSF on May 20, 2024 and by DoD on Aug. 9, 2024.
Take the training
Purdue’s Research Security Program Focus Areas
- Disclosures
Purdue employees who participate in federally funded projects must complete and update disclosures to their federal sponsors and Purdue disclosures. Learn about Purdue disclosure requirements on these sites: Reportable Outside Activities and Conflict of Interest.
Cybersecurity
New basic cybersecurity safeguards will be instituted for federally funded research in the next year. In the interim, be sure to review cybersecurity requirements in proposal guidance and award agreements.
Contact Purdue IT for guidance and questions at: IT Customer Service Center ([email protected]) .
Digitally Persistent Identifier: ORCID ID
ORCID ID is a digital persistent identifier used by Purdue University that your work is discoverable and connected to you throughout your career. ORCID ID ensures proper attribution and automates syncing with other profiles and ScienCV saving you from entering repetitive data.
If you do not already have ORCID ID, get started here .
Export Controls Training
Online export control training is available through the CITI program. Training is required for personnel to participate in a controlled project, however anyone interested may take the training.
International Travel
Foreign travel reporting will be a new federal requirement in late 2024-early 2025. Traveling abroad is an integral part of our international collaborations.
- Purdue’s best practices for international travel
- Federal travel guidance
It is important to be aware of US sanctions and restrictions when traveling.
If you have any questions or concerns prior to travel, please reach out to [email protected] .
Email: [email protected]
- Program Overview
- Research Security Training and Certification
- Policies and Guidance
- Definitions
COMMUNICATION
- OneCampus Portal
- Brightspace
- BoilerConnect
- Faculty and Staff
- Human Resources
- Colleges and Schools
INFORMATION
- Ethics & Compliance
- Purdue Postdoctoral Association
- Research Faculty Documents
- Purdue Policies
- Purdue Safety
- Purdue Hotline
- Undergraduate Research
- Office of Technology Commercialization
Purdue University, West Lafayette, IN 47907 (765) 494-4600
© 2024 Purdue University | An equal access/equal opportunity university | Copyright Complaints | Maintained by Office of Research
If you have trouble accessing this page because of a disability, please contact Office of Research at [email protected] .
Skip to Content
Other ways to search:
- Events Calendar
- Research Security
The Research & Innovation Office (RIO) is responsible for leading security and compliance efforts to ensure the campus’s adherence to security requirements, as well as supporting faculty and staff in their related responsibilities.
Research security has emerged as a top priority for US institutions receiving sponsored project funds from federal sponsors. The NSPM-33 Implementation Guidance, released in January 2022, requires any institution receiving over $50 million in federal research funding to establish a Research Security Program touching on four main areas of focus: research security training , cybersecurity , foreign travel security and export control training . In response to this guidance, the Research and Innovation Office, in collaboration with several other campus units, including the Office of Contracts and Grants and the Office of Information Technology, has established this page as a starting point in the development of our own Research Security Program.
What steps have recently been taken at CU Boulder?
- Completed an internal review of our approach to international collaborations and developed a framework for how we will continue to pursue international collaboration. As part of this review, we have issued the Guidelines for International Collaborations Memo .
- The Office of Export Controls has reviewed campus procedures regarding J-1 visiting scholars and have updated the campus procedures for review, management and out-processing.
- CU Boulder’s Research Innovation Office established the Campus Misconduct Advisory Group (CMAG) which meets collaboratively to inquire into allegations of misconduct (and may include activities concerning external affiliations, conflict of interest, international travel, and sponsor disclosures). CMAG is comprised of stakeholders across campus and occasionally hosts external partners for updates on evolving policies and potential risks scenarios.
- CU Boulder’s Conflicts of Interest & Commitment Office has implemented additional disclosure requirements which include $0 threshold for all significant foreign financial interests and foreign travel and a new Foreign Research Collaboration section which must be answered by everyone (which includes identification of any research collaborations with any foreign entity and reporting of any involvement with a foreign talent recruitment program).
- For additional information, please refer to Office of Science and Technology Policy’s Memorandum or contact RIO’s Office of Research Security.
CU Boulder’s Facility Security Officer, who is responsible for overseeing the university’s facility security clearance, is also housed within RIO. If you have questions about research security at the university, please contact Justin Mack : [email protected] .
What do you need help with?
Explore the topics below to connect with our experts.
Research Security Topics
- Classified Research
- Disclosing External Activities to Federal Sponsors
- Foreign Government Talent Recruitment Programs
- Insider Threat Awareness
- Screening Collaborators for Restricted Parties
- Undue Foreign Influence in Research
What is Classified Research?
Classified reserach is any research that bears a security classification from the federal government, such as top secret, secret, or confidential. Classified research restricts some or all of the results, procedures, and personnel working on the project under rules established by the agency for which the research is being conducted.
Contact [email protected] for support.
What External Activities Should Be Disclosed to Federal Sponsors?
Currently, each federal sponsor has their own guidelines specifying which activites need to be disclosed prior to funding, or during the period of performance, to remain compliant with the award's terms and conditions. For assistance in navigating those various requirements, use the resources below and ask your OCG Proposal Analyst.
Due to the release of the guidance outlined in National Security Presidential Memorandum (NSPM) 33, we anticipate that these requirements will be changing in the near future. Federal sponsors have been asked to develop uniform disclosure requirements to reduce confusion and administrative burden. Stay tuned for updates to external activity disclosure requirements.
- External Activities Disclosure Guide
- OCG's Disclosing Other Support page
- OCG's External Activities Disclosure page
- National Security Presidential Memorandum 33
Contact [email protected] or your OCG Proposal Analyst for support.
What is a Foreign Government (Sponsored) Talent Recruitment Program?
According to the NSPM-33 Implementation Guidance , a Foreign Government-Sponsored Talent Recruitment Program is defined as an "Effort organized, managed, or funded by a foreign government, or a foreign government instrumentality or entity, to recruit science and technology professionals or students (regardless of citizenship or national origin, or whether having a full-time or part-time position).
- Some foreign government-sponsored talent recruitment programs operate with the intent to import or otherwise acquire from abroad, sometimes through illicit means, proprietary technology or software, unpublished data and methods, and intellectual property to further the military modernization goals and/or economic goals of a foreign government.
- Many, but not all, programs aim to incentivize the targeted individual to relocate physically to the foreign state for the above purpose.
- Some programs allow for or encourage continued employment at United States research facilities or receipt of Federal research funds while concurrently working at and/or receiving compensation from a foreign institution, and some direct participants not to disclose their participation to United States entities.
- Compensation could take many forms including cash, research funding, complimentary foreign travel, honorific titles, career advancement opportunities, promised future compensation, or other types of remuneration or consideration, including in-kind compensation."
- Regent Policy 8: Conduct of Members of the University Community
- OCG's External Activities Disclosure & Foreign Talent Recruitment Programs page
- University of Wisconsin PPT on Foreign Talent Recruitment Programs
- Identifying Malign Foreign Talent Recruitment Programs
Contact [email protected] for support.
What is an Insider Threat?
According to the NSPM-33 Implementation Guidance, an Insider Threat is defined as "the potential for an insider to use their authorized access or understanding of an organization to harm that organization. This harm can include malicious, complacent, or unintentional acts that negatively affect the integrity, confidentiality, and availability of the organization, its data, personnel, or facilities."
- CISA Insider Threats 101 Infographic
- OCG Insider Threat Infographic
What is National Security Presidential Memorandum (NSPM) 33?
NSPM-33 is a directive from the President requiring all federal research funding agencies to strengthen and standardize disclosure requirements for federally funded awards. In addition, it also mandates the establishment of research security programs at major institutions receiving in excess of $50 million per year in federal research funding.
Due to the release of the NSPM-33 implementation guidance, we are anticipating changes in federal disclosure requirements and processes by 2023 or earlier.
- NSPM-33 August 2021 Briefing
- NSPM-33 January 2022 Briefing
- NSPM-33 Implementation Guidance
- OCG Webinar: NSPM-33 Status Update Slidedeck
- OCG Webinar: NSPM-33 Status Update Recording
- JSPURA Article - Summary of NSPM-33
Why Do We Sceen Our Research Collaborators?
In order to ensure that the University of Colorado Boulder is compliant with United States Federal regulations ( FAR Subpart 9.4 ), OCG must screen individuals and organizations that are contributing to our research to ensure they are appropriately vetted prior to receiving funding. This includes verification of the Department of Commerce Lists (which include the Denied Persons List, Unverified List, and Entity List), Nonproliferation Sanctions, AECA Debarred List, and Specially Designated Nationals List.
How Do We Sceen Our Research Collaborators?
OCG utilizes two tools to screen entities and individuals to ensure they are not debarred, suspended, or appear on Restricted and Denied Party lists.
When Are Potential Collaborators Screened by OCG?
There are several checkpoints for screening potential collaborators. All sponsors in OCG's research administration database (InfoEd) are screened by Visual Compliance before they are added to they system to create a proposal record. During contract negotiation, SBIRs/STTRs and agreements with international entities are also screened through Visual Compliance. During subcontract negotiation, all domestic entities are screened through SAM and all international entities are screened through Visual Compliance. If a screening tool returns a match for a potential collaborator, a risk mitigation plan is discussed.
- OCG's Restricted Party Screening Process
What are the concerns regarding undue foreign influence in research?
According to JCORE:
"Over the past several years there has been increasing concern about potential malign foreign influence and research security risk at U.S. research institutions. These concerns encompass a variety of activities such as:
- nondisclosure of foreign gifts to and contracts with U.S. academic institutions;
- nondisclosure of employment affiliations and appointments with foreign entities
- development of parallel (shadow) laboratories
- recruitment of U.S. scientists to participate in foreign government-sponsored talent programs (FGTPs) that support the development of critical emerging technologies;
- and theft of intellectual property and/or diversion of intellectual capital developed with U.S. government funds at U.S. research institutions.
While certain countries, including Russia, Iran, and others, have caused concern, the U.S. government’s primary focus has been on the People’s Republic of China (China), as illustrated by FBI Director Christopher Wray’s February 2018 address before the U.S. Senate Intelligence Committee in which he stated that the academic sector was naïve to the China threat."
- NIH: Protecting U.S. Biomedical Intellectual Innovation
- COGR: Federal Focus on Inappropriate Foreign Influence on Research
- JCORE Guidance: Recommended Practices for Strengthening the Security and Integrity of America's S&T Research Enterprise
Cybersecurity Topics
- Controlled Unclassified Information
- CMMC Requirements
- CU Office of Information Security Services
- Cyber Security Training & Awareness
- DOD Information Security Training
What is CUI?
CUI was defined in Executive Order 13556 as information held by or generated for the Federal Government that requires safeguarding or dissemination controls . Research data and other project information that a research team receives, possesses, or creates during the performance of federally funded research may be CUI. The obligation to determine whether or not an award will involve CUI belongs to the federal sponsor; award documents should specifically identify CUI and applicable security requirements.
- Management of CUI
- CU Boulder Controlled Unclassified Information (CUI) SkillSoft Course
- National Archives CUI Training Modules
- CDSE DoD Mandatory Controlled Unclassified Information (CUI) Training
- CDSE Controlled Unclassified Information Toolkit
Contact CU Boulder's Research Cybersecurity Program ( [email protected] ) for support.
What is CMMC?
The Cybersecurity Maturity Model Certification (CMMC) is a training, certification, and third party assessment program of cybersecurity in the United States government Defense Industrial Base aimed at measuring the maturity of an organization's cybersecurity processes toward demonstrating compliance with the protection of Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) that is shared with contractors and subcontractors of the Department through acquisition programs.
- CMMC Model
- Securing the Defense Industrial Base
Available Campus Resources:
- Secure Research Computing Services: The Preserve
University of Colorado Office of Information Security (OIS)
The OIS offers many services to help ensure the privacy and proper handling of university information assets. The following are provided in support of the university’s academic mission and the strategic vision of each campus.
- Security Posture Assessment
- Compliance Support
- Security Consulting and Review
- Awareness and Training
- Security Monitoring/Response
- Investigation Support
- Technology Solutions
- Policy and Governance
- OIS Services
Contact CU Office of Information Security ( [email protected] ) for support.
All CU community members have a stake in reducing risks that could impact the university’s financial, reputational, and legal standing. The mission of OIS is to provide you relevant and attainable guidance that will keep sensitive university information private and secure.
- OIS T raining and Awareness page
- CU Information Security Policies
Center for the Development of Security Excellence (CDSE)
The Center for the Development of Security Excellence (CDSE) offers several resources and trainings focused on topics related to Information Security and Cybersecurity, including:
- Introduction to Information Security
- Identifying and Safeguarding Personally Identifiable Information (PII)
- Cybersecurity Awareness
Foreign Travel Security Topics
- Airline Choice - Fly America Act
- OCG Foreign Travel Considerations
- Export Controls & Foreign Travel
- Foreign Travel Financial Guidance
What Is the Fly America Act?
The Fly America Act is a federal regulation that:
- Requires the use of U.S. carriers for travel that will be reimbursed from federal grants and contracts, regardless of cost or convenience.
- Allows for air transportation by or under a “code-sharing agreement” with a U.S. flag air carrier if service provided by such a carrier is available.
- Requires travel on a U.S. carrier as far as possible if there is no U.S. carrier to your destination.
- OCG Fly America Act page
- OCG's Fly America Act Decision Guide
- Procurement Service Center (PSC) Fly America Act page
Contact your OCG Grant or Contract Officer for support.
Considerations for Foreign Travel
Before you depart, be sure to evaluate risk, educate yourself on necessary safety precautions, and ensure compliance with export control regulations, sponsor requirements and University travel policies.
- OCG International Travel Guidance
- OCG Travel FAQs
Contact your OCG Contract or Grant Officer or [email protected] for support.
As a general rule, international travel should not involve export-controlled equipment, materials, software, or technology (together "items") without first consulting with OEC. If you are unsure as to whether your item is export-controlled, OEC can assist in both classifying the technology, as well as assessing the risk involved. We will work with you to identify ways to mitigate risks - looking at the countries, foreign parties, and technology involved - in a manner that continues to facilitate your research.
- OEC International Travel page
Contact the Office of Export Controls ( [email protected] ) for support.
When making international travel arrangements and purchases as a CU employee.
- PSC Travel Policies & Procedures
- PSC International Travel for CU Employees
- CCO Guidance on Charging Travel Expenditures to Sponsored Projects
Contact your CCO Area or Grant Accountant or [email protected] for support.
Export Control Topics
- Introduction to Export Controls
- Requesting Export Control Licenses
- International Collaborations
- Technology Control Plans (TCP)
What are Export Controls?
Export controls are federal laws that regulate the distribution of controlled devices, software, and information when such items are designated as “ defense articles ” or " dual use " commodities. Although these regulations frequently do not affect research activities, they can apply to the following situations:
- The nature of the technology in the research has actual or potential military applications,
- Foreign countries, organization(s), or individual(s) involved in the research are prohibited by law,
- The government regulates the potential end-use or the end-user of the technology resulting from the research.
- Introduction to Export Controls SkillSoft Course
- Advanced Export Compliance SkillSoft Course
- CITI Export Controls Course
- Export Control Guidance Resources
- Export Control FAQs
- Export Controls List of Definitions
Contact the Office of Export Controls ( [email protected] ) for support.
When Is an Export Control License Needed?
An Export License is a written authorization provided by the federal government granting permission for the release or transfer of export controlled information or item under a defined set of conditions. In many cases, basic and applied research may be included under one or more of the exemptions or exclusions provided in the Export Control regulations. In some cases, it may be necessary to apply for an export license or Technical Assistance Agreement.
If it is determined that your activity requires an export license, the Export Control Committee will coordinate the license application process. Contact the Export Control Committee at [email protected] . They will work with you and the Office of Legal Affairs to submit a license request to the appropriate regulatory body on your behalf. It is important to note that obtaining an export license can take 3-6 months and there is no guarantee that a license will be granted.
- Determine If an Export License is Required
- Export Controls License Request Process
Contact Your OCG Proposal Analyst or the Office of Export Controls ( [email protected] ) for support.
For most countries, collaborations with personnel and scholars at foreign institutions or organizations do not require export licenses unless there is export controlled or restricted technology involved. However, for a small number of sanctioned countries, and a growing list of restricted foreign universities and organizations in a slightly broader set of countries, U.S. universities must conduct due diligence to ensure that academic and research collaborations do not violate U.S. law.
- OEC International Collaborations page
- OEC Working with Iranian Collaborators page
What is a Technology Control Plan?
A Technology Control Plan (TCP) is a document drafted by the researcher in collaboration with the Export Control Committee and their department chair specifying procedures that will be taken in order to safeguard and control access to information or items that are export restricted.
In general, a TCP will outline what the restricted information/item is, who will have access to it, how access will be monitored and controlled, how the information/item will be physically and electronically stored, what information about it can be shared or presented, and what will be done with the information/item once the project is completed.
- Technology Control Plan Guidance
Research Administration
- Contracts & Grants
- Animal Care & Use Program
- Office of Export Controls
- Human Research & IRB
- Controlled Substances
- Conflicts of Interest & Commitment
- Responsible Research
- QA/QI Program
- Research Tools
- Research Professor Series & HR
- Reports & Strategic Planning
Search Faculty Experts
Research and expertise across CU Boulder.
- Research Institutes
Our 12 research institutes conduct more than half of the sponsored research at CU Boulder.
- Research Computing
A carefully integrated cyberinfrastructure supports CU Boulder research.
- Research Centers
More than 75 research centers span the campus, covering a broad range of topics.
Research Development, Institutes & Centers
- Research Development
- Shared Instrumentation Network
- Office of Postdoctoral Affairs
- Research & Innovation Office Bulletin
- Office of Contracts and Grants
- Research Integrity (Compliance)
- Office of Animal Resources
- Research Professor Series
Partnerships & Innovation
- Innovation & Entrepreneurship
- Venture Partners (formerly Technology Transfer Office)
- Industry & Foundation Relations
- AeroSpace Ventures
- Grand Challenge
- Center for National Security Initiatives

- Find My GCO
- IACUC applications (Cayuse Animal Management System)
- IBC Applications (eMUA)
- IRB Applications (RASS-IRB) External
- Institutional Profile & DUNS
- Rates and budgets
- Report external interests (COI)
- Join List Servs
- Ask EHS External
- Research Development Services
- Cornell Data Services External
- Find Your Next Funding Opportunity
- Travel Registry External
- RASS (Formerly Form 10 and NFA) External
- International research activities External
- Register for Federal and Non-Federal Systems
- Disclose Foreign Collaborations and Support
- Web Financials (WebFin2) External
- PI Dashboard External
- Research metrics & executive dashboards
- Research Financials (formerly RA Dashboard) External
- Subawards in a Proposal
- Proposal Development, Review, and Submission
- Planning for Animals, Human Participants, r/sNA, Hazardous Materials, Radiation
- Budgets, Costs, and Rates
- Collaborate with Weill Cornell Medicine
- Award Negotiation and Finalization
- Travel and International Activities
- Project Finances
- Project Modifications
- Research Project Staffing
- Get Confidential Info, Data, Equipment, or Materials
- Managing Subawards
- Animals, Human Participants, r/sNA, Hazardous Materials, Radiation
- Project Closeout Financials
- Project Closeout
- End a Project Early
- Protecting an Invention, Creation, Discovery
- Entrepreneurial and Startup Company Resources
- Gateway to Partnership Program
- Engaging with Industry
- Responsible Conduct of Research (RCR)
- Export Controls
- Research with Human Participants
Research Security
- Work with Live Vertebrate Animals
- Research Safety
- Regulated Biological Materials in Research
- Financial Management
- Conflicts of Interest
- Search
- Updates from Federal Sponsors
National Security Presidential Memorandum-33 (NSPM-33) directs federal agencies and departments to focus on improving research security in the following areas:
- Disclosure Requirements and Standardization
- Digital Persistent Identifiers
- Consequences for Violation of Disclosure Requirements
- Information Sharing
- Cybersecurity
- Foreign travel security
- Research security training
- Export control training
The federal agencies will apply NSPM-33 requirements to all research universities that receive an excess of 50 million dollars per year in federal research funding. Cornell University fits this criterion and as such is required to implement a research security program.
What is the purpose of NSPM-33?
The White House Office of Science Technology and Policy (OSTP) has stated three primary purposes:
- to protect America’s security and openness;
- to be clear so that well-intentioned researchers can easily and properly comply; and
- to ensure that policies do not fuel xenophobia or prejudice.
When does Cornell need to comply?
OSTP has been directed through the National Science and Technology Council to develop the implementation guidance with the goal of providing clear and effective rules for ensuring research security and researcher responsibilities. Research organizations will have one year from release of the OSTP guidance to fully implement their research security programs.
How is Cornell preparing?
Cornell is fully committed to timely and complete compliance with NSPM-33. We are closely monitoring the regulatory requirements and preparing for the anticipated OSTP guidance. We will be conducting broad outreach, so that researchers understand what will be required of them.
Where can I read more about NSPM-33?
- NSPM-33 Implementation Guidance
- OSTP Draft Requirements
Who can I contact with questions? Where can I get more information about Cornell's Program?
Please contact [email protected].
For additional information, the following policies and websites are relevant to NSPM-33 compliance and represent a portion of Cornell’s commitment to research security, integrity, and compliance:
Conflict of Interest and Commitment:
- Policy 1.7 – Financial Conflict of Interest Related to Research
- Policy 4.14 – Conflicts of Interest and Commitment
- Cornell’s COI Webpage
Research and Academic Integrity:
- Policy 1.2 – Research Integrity
- Policy 4.6 – Standards of Ethical Conduct
- Policy 4.21 - Research Data Retention
- Cornell’s Code of Academic Integrity
- Cornell’s Faculty Handbook
Export Control Compliance :
- Policy 4.22 – Export and Import Control Compliance
- Cornell’s Export Control Webpage
- Export Control Required Attestation
International Travel:
- Policy 8.5 – Risk Management for International Travel
- Cornell’s maintained list of elevated-risk destinations
- Cornell's Travel Registry & ITART Petition
- Fly America Act
- Cornell’s International Travel Webpage
Digital Persistent Identifiers:
- Cornell Library ORCHID page
Cybersecurity:
- IT Security and Privacy Page
- Cornell’s IT Device Loaner Program
Foreign Influence:
- Disclosing Foreign Collaborations and Support
Export Controls Office
Export controls frequently asked questions (faq), compliance, ethics, safety, sponsored projects: tiktok restrictions, cu601: responsible conduct of research and research security, chips and science act national security guardrails, research security and foreign engagements: helpful resources, malign foreign government talent recruitment programs, research security office, mark hurwitz (interim) - director of research integrity and security | export control and compliance officer.
Customize Your Path
Filters Applied
Customize Your Experience.
Utilize the "Customize Your Path" feature to refine the information displayed in myRESEARCHpath based on your role, project inclusions, sponsor or funding, and management center.
Research Security
Need assistance with protecting sensitive information and technologies?
Get help with protecting sensitive information and technologies.
Email: [email protected]
Research is a critical part of innovation and progress, but it also involves the handling of sensitive information and technologies. To ensure that this information remains protected and secure, it is essential to have a robust research security program in place. This page provides information on the key aspects of research security, including guidance from federal sponsors and other federal agencies involved in ensuring research security.
What is Research Security?
The NSPM-33 Implementation Guidance provides guidance to federal funding agencies (e.g., NIH, NSF, etc.) for protecting the nation's research and development infrastructure. This directive recognizes the critical role that research plays in advancing national security and economic competitiveness and outlines key elements of research security:
- Disclosure Requirements and Standardization
- Digital Persistent Identifiers
- Information Sharing
- Research Security Programs
The Research Security Program guidance is a set of requirements and best practices for institutions that have received at least $50 million per year in Federal science and engineering support to establish and maintain effective research security programs. The guidance covers the following areas:
- Overarching Research Security Program
- Foreign Travel Security
- Research Security Training
- Cybersecurity
- Export Control Training
The Federal Acquisition Regulatory (FAR) Council recently published an interim rule , effective immediately, that broadly prohibits contractors from having or using TikTok (and other successor applications by ByteDance Limited) on any “information technology” used in the performance of a government contract. The ban applies to technology owned by the government, Duke, or employees working on the contract.
What is expected of me to comply with this requirement?
Immediately remove TikTok and any ByteDance application from any information technology (see definition below) used in the performance of a federal contract or cease use of that information technology to perform the federal contract. Note that Personal cell phones not used in performance of a contract are not subject to this prohibition.
Information technology, as defined in 40 U.S.C. 11101(6)
- Of that equipment; or
- Of that equipment to a significant extent in the performance of a service or the furnishing of a product;
- Includes computers, ancillary equipment (including imaging peripherals, input, output, and storage devices necessary for security and surveillance), peripheral equipment designed to be controlled by the central processing unit of a computer, software, firmware and similar procedures, services (including support services), and related resources; but
- Does not include any equipment acquired by a Federal contractor incidental to a Federal contract.
- Note that Personal cell phones not used in performance of a contract are not subject to this prohibition.
How do I know if the research activities I engage in are subject to this ban?
The ban is being implemented through a new clause at FAR 52.204-27 that appears in the federal contract either in full text or by reference. The Office of Research Administration (ORA) or the Office of Research Support (ORS) will notify you if the contract clause appears in the federal contract that funds the research you are engaged in and is therefore applicable to you.
If so, all employees working on the federal contract whether compensated by the federal contract or not are required to remove TikTok and any ByteDance application from any equipment used in the performance of the federal contract or cease use of that equipment to perform the federal contract. Personal cell phones not used in performance of a contract are not subject to this prohibition.
Who can I contact if I have questions?
Questions regarding application of the prohibition can be directed to [email protected] .
The National Defense Authorization Act for Fiscal Year 2019 (NDAA 889) prohibits federal agencies from using certain telecommunications and video surveillance equipment and services produced by certain companies, including Huawei, ZTE, Hytera Communications Corporation, Hangzhou Hikvision Digital Technology Company, and Dahua Technology Company. Full details can be found on this General Services Administration (GSA) site .
This prohibition also extends to institutions that receive federal research funding. Institutions must ensure that any prohibited devices are not used in their research activities and should take steps to identify and mitigate any risks associated with the use of these devices. Duke has implemented procedures to mitigate these risks, but please ensure you are not using these prohibited devices and services within your units. Questions regarding NDAA 889 should be directed to [email protected] .
Warning message
- Log in (active tab)
- Reset your password
Welcome back! Log in to access your website

- Support Research
Christopher S King Associate Vice President for Research 706-542-4016 [email protected] 214 Tucker Hall 310 East Campus Road Athens, GA 30602
Research Security
What is NSPM-33?
NSPM-33 (National Security Presidential Memorandum-33) was a directive from President Trump that was subsequently endorsed by President Biden. NSPM-33 requires all federal research funding agencies to strengthen and standardize disclosure requirements for federally funded awards. NSPM-33 also mandates the establishment of research security programs at research institutions receiving federal funds. NSPM-33 will also require oversight and enforcement activity in the form of administrative actions as well as civil or criminal penalties.
Why is NSPM-33 required?
There is an increasing need to protect U.S-funded scientific research from undue foreign influence, including exploitation of the open university research environment and intellectual property theft.
What are the goals of NSPM-33?
- To protect America’s national security while promoting openness in the research community
- To make it clear so that well-intentioned researchers can easily and properly comply
- To ensure that policies do not fuel xenophobia or prejudice
NSPM-33 requires a certification from research organizations awarded more than $50 million per year in total Federal research funding, that they have implemented a research security program that includes the four elements:
- Cybersecurity
- Foreign travel security
- Research security training
- Export control training
How will NSPM-33 impact UGA?
For qualifying research organizations such as UGA, a research security program should be established as soon as possible, but UGA will have one year from date of issuance of the formal requirement to comply. The Office of Research Security and Export Control anticipates the issuance of formal requirements will take place in late 2022 or early to mid-2023, with any new or modified university process or policy to follow.
Currently, the Accounts Payable Travel Policy requires prior approval of international Travel Authorizations, and the Office of Global Engagement international travel registration is required to be completed prior to international Travel Authorization approval. Additional programmatic aspects of the research security program, such as travel security briefings or loaner electronic devices may be required in the final agency guidance. The university will develop a formal research security training program based on agency guidance and existing export control training requirements will continue and may be modified or expanded as needed.
NSPM-33 Implementation Guidance
Clear Rules for Research Security and Researcher Responsibility
University of Rochester updating research security program as required by federal mandates
- Facebook Share on Facebook
- X/Twitter Share on Twitter
- LinkedIn Share on LinkedIn
This message was sent to the University research community on January 18, 2023.
Research security has emerged as a priority for US research institutions receiving sponsored project funds from federal agencies. Research security is a broad term that refers primarily to national security concerns surrounding research involving certain types of sensitive data, intellectual property, export-controlled information, and other risks.
In effort to start to establish more secure, uniform, and transparent processes for funding and conducting federally sponsored research, the White House issued the National Security Presidential Memorandum-33 (NSPM-33) in January 2021, which was followed up in January 2022 with Guidance for Implementing National Security Presidential Memorandum 33 (NSPM-33) on National Security Strategy for United States Government-Supported Research and Development , issued by the White House Office of Science and Technology Policy (OSTP).
OSTP’s guidance specifies how high research activity institutions like Rochester need to establish a research security program. As an original requirement of NSPM-33, any research institution receiving $50 million or more in federal research funding for the previous two fiscal years must establish such a program touching on four main areas of focus: research security training , cybersecurity , foreign travel security, and (as appropriate) export control training .
As one of the nation’s leading research universities, the University of Rochester is expanding its research security program to align with these requirements. The effort is aimed at upholding safety and security in our research endeavors while continuing to foster the open global exchange of ideas.
In the coming months, the University’s Office of the Vice President of Research will be fully developing the components of a robust research security program in collaboration with several other campus units, including the Office for Global Engagement, the Office of Research and Project Administration (ORPA), University IT, and Finance and University Audit.
Review additional information about the University’s Research Security Program below.
Regards, Steve
Steve Dewhurst, PhD Interim Vice President for Research
Why is a research security program needed now?
The U.S. government is concerned that some foreign governments do not demonstrate a reciprocal dedication to open scientific exchange, and in some cases increasingly seek to exploit open United States and international research environments to avoid the costs and risks of conducting research. While continuing to recognize the importance and benefits of international research collaboration and the discoveries and innovation that benefit the global community, the US government has indicated that now is the time to strengthen the security of research development in order to protect intellectual capital, discourage research misappropriation, and ensure responsible management of United States tax-funded resources. These actions and strategies are meant to protect federally funded research while still maintaining and encouraging productive collaborations with international researchers.
What is meant by research security training, cybersecurity, foreign travel security and export control training?
- Cybersecurity: Research organizations should apply basic safeguarding protocols and procedures that include providing regular cybersecurity awareness training for authorized users of information systems, including in recognizing and responding to social engineering threats and cyber breaches; limiting information system access to authorized users; controlling any non-public information posted or processed on publicly accessible information systems; and providing protection of scientific data from ransomware and other data integrity attack mechanisms, among additional safeguards.
- Foreign travel security: Research organizations should maintain international travel policies for faculty and staff traveling for organization business, teaching, conference attendance, research purposes, or any offers of sponsored travel that would put a person at risk. These policies should include an organizational record of covered international travel by faculty and staff and, as appropriate, a disclosure and authorization requirement in advance of international travel, security briefings, assistance with electronic device security (smartphones, laptops, etc.), and pre-registration requirements.
- Research security training: Research organizations need to provide training to relevant personnel on research security threat awareness and identification. Research organizations should consider incorporating relevant elements of research security into existing training on responsible and ethical conduct of research for faculty and students. In addition to periodic training, research organizations should conduct tailored training in the event of a research security incident.
- Export control training: Research organizations conducting R&D that is subject to export control restrictions need to provide training to relevant personnel on requirements and processes for reviewing foreign sponsors, collaborators and partnerships, and for ensuring compliance with federal export control requirements and restricted entities lists.
What steps is the University taking to expand its research security program?
The federal government is to provide standardized technical assistance to support development of training content and programmatic guidelines, tools, and best practices to be made available to organizations for incorporation into research security programs. Additionally, flexibility has been granted for institutions to structure the organization’s research security program to best serve its specific needs, and to leverage existing programs and activities where relevant, provided that the organization implements all required program components.
Currently, the University’s Office of the Vice President for Research already provides information on research security , including in the areas of disclosing research collaborations and travel guidelines. These components will be further built out and added to in the coming months as more guidance is issued by the federal government.
When will these new requirements go into effect?
The federal government will be providing additional guidance on implementation, but we estimate that these requirements will go into effect during the first or second quarter of calendar year 2024.
Where can I go for updated information?
Check back to our Research Security page , which will be updated as new information is available. Communications will also be broadly distributed about any new requirements of researchers or departments as part of the research security program, including at monthly CLASP meetings for research administrators.
- Uncategorized
- Research Security Program identifies risks…
Research Security Program identifies risks and provides tools and strategies to prevent and mitigate them

John Miller
One year into his role as interim director of the Research Security Program , John Miller is working across campus to apply research security principles and best practices to safeguard research domestically and abroad.
The program, housed in the Office of the Vice Chancellor for Research , uses an integrated approach, including monitoring the changing research security landscape, providing education and building systems to better evaluate and mitigate risks, Miller says. Operating a successful research security program protects the public’s investment in research as well as UW–Madison’s stake in federal research dollars.
To meet the evolving research security landscape and federal requirements, Miller leads a team with representatives from across campus — from legal services to risk management, International Safety and Security, export control, cyber security and Research and Sponsored Programs — who play a role in key research security areas.
The Research Security Program helps researchers safeguard their research and innovation in both the short and long-term. Having a strong research security program helps UW–Madison maintain its excellence in cutting-edge research and innovation on the world stage by fostering international collaborations essential to solving complex issues.
Since December of 2021 and the adoption of National Security Presidential Memorandum 33 , UW–Madison has been required to operate its Research Security Program as an institution receiving more than $50 million annually in federal grants. But prior to NSPM-33, UW already had many aspects of a research security program in place, says Miller, and has a good foundation for meeting federal requirements such as in the areas of export control , conflict of interest, outside activities reporting and data security.
But in response to NSPM-33, there is more work to do. An initial step was to develop a research security webpage to provide a one-stop shop with resources for the university community. The webpage also serves as a platform for ongoing program development and implementation.
The webpage includes links to:
- A researcher toolkit that points to campus policies and procedures as they relate to laws, regulations and policies in science and security; data retention guidelines; disclosure requirements; and more.
- Outside activities reporting
- International Division’s unit of International Safety and Security for help when preparing for international travel.
- DoIT’s guidance and resources to protect data and devices when traveling.
- Office of Cybersecurity resources for protecting against intellectual property theft and academic espionage, protecting sensitive personal information and preventing undue foreign government influence or actions that infringe on core academic values such as free speech and scientific integrity.
- Research and Sponsored Programs , which reviews agreements that support sponsored research. Faculty also are required to report connections with foreign institutions and to report on research funding which does not flow through UW–Madison.
Miller says new federal guidelines will necessitate new and revised university policies and procedures that will need to be in place by 2025, and he opened the door for developing new educational opportunities related to research security.
“Our goal is to offer guidance to researchers on how to protect their work, enhance transparency and collaboration, responsibly disclose research findings and take other proactive steps to ensure the integrity of our research enterprise,” Miller says. “That means — together — implementing a continuous cycle of identifying vulnerabilities, recommending and implementing solutions and assessing our effectiveness in these areas.”
By Natasha Kassulke, [email protected]
Categorized under:
Research Security and Foreign Interference at U.S. Academic Institutions
Over the past decade, Congress, federal science agencies, and the media have highlighted concerns about the impact of undue foreign influence on federally funded research in the United States. For institutions, this means an increased focus on research security and the need to update internal policies and processes, while maintaining a focus on the value of a global workforce and international scientific collaborations. This page provides background information, the latest updates on relevant federal government policies and activities, and considerations and resources for institutional leadership, administrators, and researchers as they address this issue on their campus.
Latest Federal Policy Updates
Updates on nih activity and policies for the grantee community.
The National Institutes of Health (NIH) has been actively involved in the issue of foreign influence since an August 2018 letter sent out to grantee institutions on agency concerns. Since that time, NIH staff have contacted institutions regarding 255 cases where there were likely foreign interference concerns with scientific or budgetary overlap, overcommitment, or undisclosed financial conflicts of interest.
The NIH posts the latest updates on how the agency is handling this issue on its Foreign Interference page. Details about these agency policies and activities are below.
September 2022. The NIH issued a notice to remind the extramural community about existing policies and regulations around financial conflicts of interest and other support.
June 2022. The NIH updated a table which extensively details the required pre- and post-award disclosures relating to the Biographical Sketch and Other Support.
December 2021. The NIH issued a guide notice , “Maintaining Security and Confidentiality in NIH Peer Review: Rules, Responsibilities and Possible Consequences,” to remind all participants and invested parties in the NIH peer review process of federal statutes, regulations, and NIH policies regarding peer review security and confidentiality; their responsibilities for abiding by those rules; and possible actions that the NIH (in coordination with other offices) may take and consequences that may ensue from a violation of those rules.
July 2021. The NIH published a summary of findings on foreign research interference from 2016 to 2021, highlighting the major issue areas and sharing four scenarios based on real cases, outlining the situation and the consequences/corrective actions taken.
December 2019. During an update at the Dec. 13 meeting of the NIH Advisory Committee to the Director (ACD), NIH Deputy Director for Extramural Research Mike Lauer, MD, listed several updates the agency had taken to carry out recommendations from the ACD report (see December 2018, below), including clarifying other support, working with the National Science Foundation (NSF), and implementing peer review training and systems controls.
September 2019. The Department of Health and Human Services (HHS) Office of Inspector General released three reports related to financial conflicts of interest (FCOI), foreign influence, and the steps the NIH is taking to protect research integrity.
NIH Has Made Strides in Reviewing FCOIs in Extramural Research, But Could Do More
The NIH Has Limited Policies, Procedures, and Controls in Place for Helping to Ensure That Institutions Report All Sources of Research Support, Financial Interests, and Affiliations
Vetting Peer Reviewers at NIH's Center for Scientific Review: Strengths and Limitations
July 2019. The NIH released a guide notice and FAQs noting that institutions receiving extramural funding from the NIH are subject to several relevant policies and regulations:
The NIH Grants Policy Statement (NIHGPS) requires grant applicants to disclose Other Support to ensure no scientific, budgetary or commitment overlap, including “all financial resources, whether Federal, non-Federal, commercial or institutional, available in direct support of an individual's research endeavors.” (Section 2.5.1).
The NIHGPS also requires recipients to determine whether activities it supports include a foreign component, which may or may not involve the direct use of NIH grant funds (e.g., performance of work by a researcher or recipient in a foreign location or a collaborator outside of the United States who performs experiments in support of an NIH-funded project or with an expected co-authorship).
Federal conflict of interest regulations ( 42 CFR Part 50, Subpart F ) include a requirement for researchers to disclose to their intuitions significant financial interests (SFIs) in addition to any reporting required by NIH policy (learn more on the AAMC's Conflicts of Interest and Transparency Initiatives page).
The NIH clarified in 2018 that while these regulations do not require disclosure of certain SFIs from “an Institution of higher education,” this is only for U.S. institutions, and remuneration from foreign institutions is a disclosable SFI.
A related FAQ updated July 11, 2019, confirms that these policies and regulations are already in place and that the guide notice serves as a reminder to the community, not an expansion of the Other Support policy.
A blog post from the NIH Office of Extramural Research (OER), provides additional context for the timing of the guide notice and states that “depending on the severity and duration of the noncompliance … [the office] may contact the affected institutions, impose specific award conditions, disallow costs, withhold future awards for the project or program, suspend the award activities, make a referral for investigator suspension or debarment, or terminate the award.”
December 2018. An NIH Advisory Committee to the Director released a report on foreign influences and research integrity, containing recommendations for recipient organizations related to:
Communicating with investigators (education campaigns on disclosure requirements and guidelines for visitors).
Mitigating risk (assessment of internal controls, proactively notifying the NIH about breaches).
Ongoing monitoring (developing flags for audit, considering post-travel questionnaires for select countries, and working with federal security agencies on best practices).
August 2018. NIH Director Francis Collins, MD, PhD, issued a statement and sent a letter (PDF) to over 10,000 grantee institutions, outlining three areas of concern for the agency:
Diversion of intellectual property to other entities, including other countries.
Sharing of confidential information on grant applications by NIH peer reviewers with others.
Failure by researchers working at NIH-funded institutions to disclose substantial resources from other organizations.
The letter also noted that the NIH OER would reach out to specific institutions “regarding grant administration or oversight questions or requests about specific applications, progress reports, policies, or personnel.”
White House OSTP and Government-Wide Coordination
The National Science and Technology Council (NSTC), overseen by the White House Office of Science and Technology Policy (OSTP), launched the Joint Committee on Research Environments (JCORE) in May 2019. A subcommittee focused on research security, comprised of 17 agencies from across the government, is working on coordinating federal outreach to research institutions, developing guidance and best practices, and standardizing conflict of interest and commitment disclosure requirements and enforcement. The National Science Foundation is a key agency partner in this effort and maintains a collection of resources on this topic. As of early 2024, we are waiting on the release of a final requirement for a research security program and will update this page when it is released.
February 2024. The OSTP released updated guidance on two key topics:
Policy Regarding Use of Common Disclosure Forms for the "Biographical Sketch" and the "Current and Pending (Other) Support" Sections of Applications by Federal Research Funding Agencies
Guidelines for Federal Research Agencies Regarding Foreign Talent Recruitment Programs
January 2024. The NSF released four interactive online research security training modules covering (1) an introduction to research security, (2) the importance of disclosure, (3) managing and mitigating risk, and (4) the importance of international collaboration.
June 2023. The AAMC responded to a request for information from the OSTP regarding a draft National Security Presidential Memorandum 33 (NSPM-33) research security programs standard requirement . This requirement is described in the memorandum’s implementation guidance (PDF) released last year, which expands on the provision that “research institutions receiving Federal science and engineering support in excess of 50 million dollars per year certify to the funding agency that the institution has established and operates a research security program. Institutional research security programs should include elements of cyber security, foreign travel security, insider threat awareness and identification, and, as appropriate, export control training.”
October 2022. The AAMC submitted comments to the NSF requesting feedback on behalf of the NSTC subcommittee on proposed common disclosure forms for the Biographical Sketch and Current and Pending (Other) Support sections of a research application, intended to clarify what is expected of senior personnel applying for research funding from federal agencies. The association additionally submitted a joint letter (PDF) with partner higher education organizations, highlighting the importance of clarifying definitions, ensuring a transparent and uniform process for updating the common forms, and limiting agency variation in required disclosure data elements and instructions.
January 2022. The NSTC JCORE research security subcommittee released a report (PDF) containing guidance for federal departments and agencies regarding their implementation of NSPM-33. The five key areas covered in the document are: disclosure requirements and standardization, digital persistent identifiers, consequences for violation of disclosure requirements, information sharing, and research security programs.
September 2021. The AAMC sent a joint letter on Sept. 30 in response to a request for feedback from the White House OSTP on implementing the research security guidelines in the NSPM-33. The comments emphasized building on existing policies created by institutions to address research security; recognizing that the vast majority of university research is open and unrestricted and should not be subject to research standards from the commercial sector; and incorporating the use of pilot programs and continued community engagement as any new policies are implemented.
January 2021. The White House issued NSPM-33 , which “directs action to strengthen protections of United States Government-supported Research and Development (R&D) against foreign government interference and exploitation.”
At the same time, the NSTC JCORE subcommittee on research security released recommended practices for research organizations to strengthen the security and integrity of the research enterprise.
January 2020. The AAMC sent a letter to the OSTP in response to a request for information on actions that federal agencies can take, working in partnership with private industry, academic institutions, and nonprofit/philanthropic organizations, to maximize the quality and effectiveness of the research environment, including protecting the security and integrity of the research enterprise.
November 2019. the AAMC participated in the JCORE summit to discuss research security and other issues, a summary of which is available online (PDF).
September 2019. White House OSTP Director Kelvin Droegemeier, PhD, sent an open letter (PDF) to the research community, reaffirming the importance of using a risk-based framework to evaluate research security concerns and highlighting the progress of the OSTP in coordinating federal efforts.
The AAMC previously joined over 60 organizations on a Sept 4 letter (PDF) to the OSTP and federal research funding agencies (the NIH, the NSF, the departments of defense and energy) stressing the importance of balancing “an openly collaborative scientific environment and protecting our economic and national security.”
Fundamental Research Security from the NSF and JASON.
People’s Republic of China (PRC) Targeting of COVID-19 Research Organizations from the FBI and the Cybersecurity and Infrastructure Security Agency.
Threats to the U.S. Research Enterprise: China’s Talent Recruitment Plans (PDF) from the U.S. Senate, the Permanent Subcommittee on Investigations, the Committee on Homeland Security and Governmental Affairs.
NIH Should Take Further Action to Address Foreign Influence (PDF) by the U.S. Government Accountability Office.
A New Institutional Approach to Research Security in the United States from Georgetown’s Center for Security and Emerging Technology.
Research Security and Compliance Committee from Cornell University.
Research and Foreign Engagement from New York University.
International Relationships and Activities from Penn State University,
Academic Integrity and Undue Foreign Interference from Stanford University.
Research Security Program from Stony Brook University.
Research Security Office from the Texas A&M University System.
Research Security Governance Board from The Ohio State University.
Ethics, Compliance and Audit Services from the University of California.
Research Security Program from the University of Illinois Chicago.
Research Security and Compliance from the University of Missouri System.
Guidance on Science and Security from the University of North Carolina at Chapel Hill.
- Medical Schools
- Research & Technology
- Research Training
Compliance News: Update on Research Security
©Miller: Courtesy of NYU Photo Bureau
Nancy Daneau, Associate Vice Provost for Research
The federal government remains concerned that some foreign governments do not demonstrate, as we do in the U.S., a dedication to open scientific exchange and seek to exploit U.S. and international research environments. With continued commitment to openness in fostering research discoveries and innovation, the federal government is taking steps to protect intellectual capital, discourage research misappropriation, and ensure proper stewardship of funds.
In January 2021, National Security Presidential Memo-33 (NSPM-33) outlined the Administration’s expectations for protection against foreign government interference and exploitation in federally funded research and development. In January 2022, the Office of Science and Technology Policy issued guidance to federal agencies to guide implementation of NSPM-33. Over the coming months, we expect federal agencies to respond by modifying policies and procedures with which universities will need to comply, and complete their plans for implementation of NSPM-33 by Fall 2022.
The five areas of research security addressed by NSPM-33 that will impact research and sponsored programs include disclosure requirements and standardization, digital persistent identifiers, consequences for disclosure requirement violations, information sharing, and research security programs.
Regarding disclosure requirements and research data security, t ools and resources have been developed and faculty have been engaged through various outreach efforts to: 1) facilitate understanding of agency specific disclosure requirements for sponsored research; 2) communicate NYU policies and procedures along with best practices around data management planning; and 3) conduct research data risk assessments, categorize research data, and provide secure environments for research data.
In the next 12-18 months, guidance, policies and procedures will again be updated to achieve compliance with agency implementations for disclosure and the use of digital persistent identifiers. In addition, an institutional research security program will be developed to address requirements related to: 1) cybersecurity, 2) foreign travel security, 3) research security training, and 4) export control training.
The Offices of Research Administration, Research IT, Libraries, and Compliance and Risk Management, with input from faculty and researchers at WSQ, NYUAD and NYUSH, will conduct a gap analysis, create tools and training modules, and develop guidance to meet the federal standards for compliance with NSPM-33 and certification of NYU’s research security program. We will continue to support the critical research and network of international collaborations across NYU while achieving compliance with government requirements around foreign interference.
Cookie Notice
This website uses cookies. Contact us for questions or requests.

Information for:
- Current Students
- Faculty & Staff
- Degrees & Programs
- Campus Maps
- Jobs & Careers
- Campus Shuttles
- Student Life
- Giving
- Augusta University
- Ethics & Compliance
Research Security
Research security has emerged as a top priority for U.S. institutions receiving sponsored project funds from federal sponsors.
National Security Presidential Memorandum 33 (NSPM-33) on National Security Strategy for United States Government-Supported Research and Development was released in January 2021 with the goal of securing federally funded research and protecting U.S. innovation. NSPM-33 directs funding agencies to require research institutions receiving more than $50 million per year in federal funding to certify that they have established and operate a Research Security Program as a condition of funding. This program, at a minimum, will include four main areas of focus: research security training, cybersecurity, foreign travel security and export control training.
Implementation Guidance for NSPM-33 defines research security as “safeguarding the research enterprise against the misappropriation of research and development to the detriment of national or economic security, related violations of research integrity, and foreign government interference.”
This webpage serves as a resource for guidance regarding foreign influence in research and research security, including sponsor-specific guidance, investigator responsibilities, and steps that Augusta University is taking to develop its Research Security Program. Content will be updated as additional information becomes available.
Town Hall Presentation on Research Security at AU
Foreign Influence in Research
Augusta University seeks to promote principled international collaborations which enable cutting-edge research that no nation can achieve alone, train up minds capable of solving global problems, and strengthen scientific and diplomatic relations.
Federal and state concerns about transfers of federally funded research and other IP from U.S. universities and businesses to foreign entities have escalated in recent years. Such transfers are often not illegal, but the failure to disclose foreign activities can be, especially as federal funders, and particularly the National Institutes of Health (NIH) and the National Science Foundation (NSF), are interpreting and supplementing their requirements.
The Office of Science and Technology Policy (OSTP) and federal sponsors such as the NSF, the NIH, Department of Defense (DoD), and the Department of Energy (DoE) have issued communications with the research community about research security and have expressed concerns regarding foreign influence in research due to:
- Failure by some investigators to disclose financial support from other organizations, including foreign governments
- Diversion of intellectual property to foreign entities
- Sharing of confidential information by peer reviewers with others, including some instances with foreign entities.
If the government can show that a funded researcher failed to disclose foreign activities as part of a grant application, then the government can take (and, increasingly, is taking) legal action against the researcher not because the underlying activity was illegal, but rather because the failure to disclose fully may constitute fraud. This same approach is being used with U.S. universities that receive federal funding. In short, existing, and new disclosure requirements are being interpreted to require more disclosure of foreign activities and research support, and to require universities to have a higher level of awareness about our faculty’s foreign activities than ever before.
Disclosure of Foreign Relationships and Activities & Other Investigator Responsibilities
Transparency in disclosure.
All foreign components of federally funded research should be disclosed during proposals, progress reports, and final technical reports. Investigators with external funding should carefully review the sponsor’s current disclosure requirements and contact the Division of Sponsored Program Administration for assistance or further guidance. In addition, investigators should:
Review and update ‘Current and Pending Support’ information and ‘Other support’ information in pending proposals and active awards per sponsor-specific guidance
Review and update biosketches and ensure all professional appointments and collaborations, both foreign and domestic, paid and unpaid, are disclosed according to sponsor requirements in proposals and reports.
Ensure appropriate disclosure of foreign components for NIH-supported projects.
Faculty and staff should also familiarize themselves with AU’s Individual Conflict of Interest Policy and Outside Activities and Off-Campus Duty policy and be fully transparent in disclosing outside interests and commitments. Please refer to Tools for Researchers for current policies.
The federal government has directed research institutions to exercise extreme caution related to involvement with foreign talent recruitment programs due to the concern they may be used by foreign governments to acquire U.S. government-funded scientific research and valuable intellectual property. Please contact the Director, Research Ethics and Compliance or the Research Security Officer for Restricted Party Screening if you are considering participation in a foreign recruitment or talent program. This proposed activity should also be disclosed to your academic leadership as with any other Outside Activity.
Export Controls
Export controls are federal laws that regulate the distribution of controlled devices, software, and information when such items are designated as “defense articles” or "dual use" commodities. AU adheres to regulations set by the Department of Commerce (Export Administration Regulation - EAR), Department of State (International Traffic in Arms Regulations - ITAR), and the Treasury Department (Office of Foreign Assets Control - OFAC). These regulations apply when there is a transfer of these items overseas and/or to foreign persons within the United States. Export regulations may affect collaborations with international research partners, how research results are disseminated, international travel, and purchase or procurement transactions with restricted countries/individuals. Please contact the Research Security Officer or the Director, Research Ethics and Compliance for export compliance assistance if you plan to:
- Ship or hand carry research materials, technology, or data outside the country
- Enter into a research contract or agreement with publication restrictions
- Enter into a research grant or contract restricted to U.S. citizens
- Engage with or travel to a sanctioned country
- Travel outside the U.S. on university business or with AU equipment
- Ship any item valued at $2500 or more outside the country
- You suspect a violation of export control laws or regulations has occurred
- Engage with foreign partners/entities (including sponsoring visiting scholars and researchers).
There are sometimes exclusions to export regulations for “fundamental research.” Fundamental research is basic and applied research…, where the resulting information is ordinarily published and shared broadly within the scientific community. Such research can be distinguished from proprietary research and from industrial development, design, production, and product utilization, the results of which ordinarily are restricted for proprietary reasons or specific national security reasons . . . University research can be considered fundamental to the extent that researchers do not accept restrictions on the publication of scientific and technical information resulting from the research. AU research topics will typically fall within this exclusion, but not always. The FRE does not apply to physical equipment used during fundamental research or to the export of physical equipment or materials. Additionally, a sponsor may provide background technical data that is export controlled for use during fundamental research activities.
If you have any questions or concerns about exports or potential exports, please contact the AU Research Security Officer. For more information on Export Control Compliance at AU, please refer to the manual in Tools for Researchers .
Security of Materials, Data and Confidential Information
Investigators should utilize a Data Use Agreement (DUA), Material Transfer Agreement (MTA) or Non-Disclosure Agreement (NDA) when sharing or exchanging data or materials. Note that all agreements must be reviewed and signed by institutional officials with the appropriate signature authority. Accepting controlled information or restrictions under research agreements may require the use of Technology Control Plans (TCP) or heightened cybersecurity. If you accept or anticipate accepting controlled information, contact the Director, Research Ethics and Compliance or the Research Security Officer to request a review and establish a TCP.

Cybersecurity
AU implements several baseline safeguarding protocols and procedures used to store, transmit, and conduct federally funded R&D. These protocols are designed to protect scientific data from ransomware and other data integrity attack mechanisms. All AU community members have a stake in reducing risks that could impact the university’s financial, reputational, and legal standing. Further information may be requested through AU’s IT department.
Intellectual Property
Investigators should review AU’s Intellectual Property policy and ensure all University IP is appropriately disclosed and protected. Please refer to Tools for Researchers for current policies.
International Travel Policy
Augusta University has established a policy on international travel and is creating travel briefs for researchers traveling outside of the United States. AU’s foreign travel policy can be found in the Tools for Researchers . AU’s Research Security office will maintain records of international travel and export control determinations associated with international travel. Individuals traveling internationally for organizational business, teaching, conference attendance, research purposes, or who receive offers of sponsored travel for research or professional purposes will be required to register their travel with AU. The policy also applies to personal international travel when the individual plans on taking an AU electronic device or accessing AU systems (i.e., via email). Individuals accessing AU networks or taking AU issued electronic devices for business or personal travel will now have a requirement to have a consultation with the Research Security Office and IT prior to travel. As noted in the policy, certain destinations will have different considerations, both in terms of security concerns and actions required of the traveler. More information can be found in the policy, and the Research Security office is available to help.
* Helpful Checklist for International Travel*
International Travel Checklist
Steps to be taken prior to international travel as described in AU’s International Travel Policy and other locations:
- InfoED Travel Registry – log into infoed.augusta.edu and complete the International Travel Registry form.
- AU InfoEd Travel Registry User Guide
If Traveling with AU device such as a laptop, or if you require AU network access (i.e., for checking emails):
- Information you provided on the InfoED Travel Registry will be shared with IT who will conduct a review of the device and provide feedback.
- Submit a DUO International Access Request .
If any portion of your travel will be paid by/through AU:
- Complete a Travel Authorization prior to travel.
- Supervisor and Executive VP level approval is required for international travel.
- Review by Division of Sponsored Programs is required if any portion of the travel will be paid with grant funds.
If your travel is related to an outside professional activity:
- Obtain prior approval from your supervisor for any outside professional activity via an OA-1 form.
If any portion of your travel will be paid/reimbursed by an external entity:
- Update your conflict-of-interest disclosure to include all travel paid/sponsored by an external entity (possible exceptions include: US federal government and other US Universities).
Insider Threat Awareness
According to the NSPM-33 Implementation Guidance, an Insider Threat is defined as "the potential for an insider to use their authorized access or understanding of an organization to harm that organization. This harm can include malicious, complacent, or unintentional acts that negatively affect the integrity, confidentiality, and availability of the organization, its data, personnel, or facilities."
Specific trainings for Insider Threat Awareness are currently under development.
Jesse White, Research Security Officer
1120 15th Street, CJ-1021 Augusta, GA 30912
706-737-1589
Additional Resources
Frequently Asked Questions
What is a travel security consultation and what does it entail?
Part of the new international travel policy requires that travelers have a consultation with the Research Security Officer prior to travel. This starts with submitting a request in InfoEd. Depending on the travel, further consultation may be necessary. Typically, a consultation will provide the traveler with useful information about their destination and how to ensure AU devices function as desired there.
How can I access DUO internationally?
The Information Technology department has a wealth of resources for Duo specific questions. It can be found here . International access requests can be found on the linked page. ( https://www.augusta.edu/it/duo.php ).
I requested international DUO access, but I have not received any emails saying it will work. How do I know my International Access request is complete?
From the IT FAQ page : An email will be sent from AU ServiceNow upon submission of the request to notify the request was received. When international access is granted, a second email regarding the task closure will be sent. This automated process occurs two days before the travel date submitted in your request. Please check your Augusta University email for messages from AU ServiceNow regarding your request. A third email will be sent regarding the removal of international access two days following the submitted travel return date.
Should AU researchers avoid international collaborations?
International collaboration is valued by AU and remains an essential part of the research and educational missions of the University. There are many options to pursue international collaborations at AU via university-to-university agreements, research sponsorship agreements, visitor and student exchange, etc. Support for research must be disclosed and any personal contracts or agreements between yourself and another institution must be disclosed in the COI system.
How is AU addressing Foreign Influence?
AU is engaged with federal agencies, research sponsors and national organizations and will continue to ask for disclosures from researchers.
What are specific concerns regarding foreign influence in the academic setting?
The FBI and other federal government agencies have expressed concern that some foreign actors, particularly foreign state adversaries, are seeking to acquire U.S. academic research and information illicitly or illegitimately in order to advance their scientific, economic, and military development goals through the exploitation of the culture of collaboration and openness on university campuses. More specifically, NIH has identified three areas of concern : diversion of intellectual property; peer reviewers inappropriately sharing confidential information on grant applications; and failure of researchers at NIH-funded U.S. institutions to disclose foreign affiliations and collaborations, and/or substantial resources received from other organizations, including foreign governments and universities.
Do these issues apply only to NIH Grants?
The Department of Defense, the National Science Foundation, the National Aeronautics and Space Administration, and the Department of Energy have also issued statements regarding this issue. Given the current U.S. Government focus on this issue, we anticipate similar guidance, statements, or requirements will be forthcoming from other funding agencies.
What are “foreign talent recruitment programs” and why is there concern about them?
The federal government is concerned that foreign talent recruitment programs may be used by foreign governments to acquire, legally and illegally, U.S. government-funded scientific research in order to dominate high technology sectors currently led by U.S. entities. As described by the FBI, these programs target individuals who are working in technological fields of interest to the foreign government, offering competitive salaries, state-of-the-art research facilities and/or honorific titles in an effort to encourage the transfer of ideas and intellectual property. The Department of Energy defines a foreign talent recruitment program as an effort directly or indirectly organized, managed, or funded by a foreign government to recruit science and technology professionals or students (regardless of citizenship or national origin, and whether having a full-time or part-time position).
What is the federal government doing to address concerns about foreign talent recruitment programs?
At present, there is no generally applicable U.S. legal or regulatory prohibition on participation in a foreign recruitment program. However, the Department of Energy (DOE) recently issued and that prohibits DOE employees and contractor employees from participating in certain foreign talent recruitment programs to ensure protection of U.S. competitive and national security interests as well as DOE program objectives. Similarly, NSF announced a policy prohibiting NSF personnel and Intergovernmental Personnel Act (IPA) detailees to NSF from participating in foreign government talent recruitment programs due to risk concerns. While there is no legal prohibition on participating in these programs, it is important to fully disclose participation in any foreign talent recruitment program to the University as well as any governmental agency, if asked.
What steps must I take in response to these concerns?
- Adhere to AU’s new Research Security program, Tools for Researchers
- Make your sponsors aware of your collaborations and interactions with foreign entities that support or contribute to your research program; federal agencies are expecting a thorough account of touchpoints between your research program and any foreign entity. Be familiar with the terms and conditions of your award. Prior approval by the sponsor may be required prior to foreign travel or the addition of a foreign component to the project.
- If you are NIH funded: In July 2019 the NIH published FAQs regarding “Other Support and Foreign Components,” which provide more detail on NIH’s expectations regarding what qualifies as “other support” and when a project includes a “foreign component.” These clarifications address how to account appropriately for visiting scholars, start-up and other internal funds, and foreign collaborations, even if no grant funds are expended on the collaboration. Additionally, Michael Lauer, NIH’s Deputy Director for Extramural Research, has blogged on the topic of “other support,” providing examples of what should be disclosed. Additional information can be found on the NIH website Protecting U.S. Biomedical Intellectual Innovation .
- If you are NSF funded: The Proposal and Award Policies and Procedures Guide (PAPPG) issued in June 2020 clarifies the type of support that must be disclosed in the current and pending support . In July 2020, the NSF also issued FAQs s about what and how to disclosure current and pending support.
Do I need to end my foreign collaborations and/or stop welcoming foreign students and visitors into my lab?
Augusta University has always and will continue to encourage and support foreign collaborations. However, consistent with federal agency guidance you must obtain prior approval prior to foreign travel or adding a foreign component if required by the terms and conditions of the award and you should provide information to your research sponsors about all foreign collaborations and ensure that all foreign Research Visitors are screened through the Export Controls Compliance, confirming that there are no restrictions upon hosting such visitors. That said, there remains considerable concern with foreign talent programs. If you are involved in or are invited to participate in such a program, you should disclose this involvement and obtain guidance from your school/college or departmental research administration staff, or AU’s Research Administration
Do I need to make disclosures related to the work of graduate students if they are Foreign Persons?
In most cases, there is no reason to disclose participation of foreign students or postdocs on sponsored research, especially if all such work will be performed in the U.S. However, classified and export-controlled projects will be subject to foreign national restrictions. It may be possible to employ certain foreign persons on controlled projects after appropriate licenses and/or exemptions are secured. Please contact the Research Security office for more information on such cases. There are no foreign national restrictions on “Fundamental Research” projects. However, there may be cases where working with a student or postdoc might be considered a “foreign component,” if that student or postdoc is performing effort in a foreign country. NIH defines a foreign component as “any significant scientific element or segment of a project outside of the United States, either by the recipient or by a researcher employed by a foreign organization, whether or not grant funds are expended."
I have a visitor in my lab who is supported by his/her foreign institution. S/he is not funded by any of my federal grants. Do I need to account for this visitor in proposals or progress reports? If so, how?
We do not have specific guidance from all sponsors on this topic, however, per NIH guidelines, this person’s work on the project should be documented as follows:
- As “Other Support” because the externally funded individual is a “resource available in direct support of [your] research endeavors.” The NIH recently clarified that “all research resources including, but not limited to, foreign financial support, research or laboratory personnel, lab space, scientific materials, … must be reported.”
- As a “Participant” in the progress report if the person worked on a project for more than a month in any given year (see 4 Section D – Participants). Additionally, the person’s “primary affiliation” is determined by where the work was done for the project: if the individual is affiliated with a foreign organization but worked on the award solely in the U.S., the “primary affiliation” is not foreign; if work was performed while outside of the U.S., the primary affiliation should be noted as foreign.
As a “Foreign Component” if the individual performed part of the work while in your AU lab, but also made a significant contribution to the project a from his/her home institution, or any other foreign location (e.g., collecting data at a foreign site, running samples on instrumentation there, and/or will be a co-author on publications arising from the grant). In accordance with NIH policy, the addition of a foreign component requires NIH prior approval.
I have family in countries outside the United States and I travel for personal reasons. Do I need to disclose all travel to the University – even if it is unrelated to my AU work?
If you intend to travel internationally with your work laptop or other AU device, you should be mindful of any sensitive data that the device may contain and take steps to ensure the security of those data. Please contact the Research Administration office with any questions and refer to AU’s current travel policy.
How do I know if a company, university, or other entity creates risk? Do you have examples of entities that I should not work with or that invite extra scrutiny?
The federal government maintains lists of entities that are higher risk, information that changes frequently. AU uses software called Visual Compliance to screen proposed partners of AU against these lists, including sponsors of research, proposed vendors or subcontractors, and others. One well-publicized example of a company that has received federal government attention is Huawei, which the federal government recently placed on a restricted list. Please contact the Research Administration if you have any questions about engaging with foreign entities – including accepting gifts.
I have been invited to a foreign institution to present at a conference. If I attend, do I need to disclose my participation to sponsors? To AU?
If that travel establishes a relationship with a foreign university, government, or other entity (e.g., results in an honorary or visiting appointment or an offer to set up laboratory space at that institution), then that may need to be disclosed, depending on the sponsor and their specific guidelines.
Yes, you should disclose the relationship with the foreign institution to AU via the disclosures system. Provide as many details as possible in the disclosure form.
I am getting ready to submit a paper with many – possibly hundreds – of co-authors, some of which are foreign and were undoubtedly funded by grants in their home country (i.e., foreign funding). Does each of those individuals need to be accounted for as a Foreign Component?
Please reach out to your NIH/NSF Program Officer to confirm whether these individuals constitute a foreign component. When required, disclosure of foreign co-authors to the NIH should occur prior to working with the foreign co-author(s). Other sponsors have not specifically commented on this; should you have questions, please consult your sponsor point of contact.

Guidance for Implementing the National Security Presidential Memorandum 33 (NSPM-33) on National Security Strategy for United States Government-Supported Research and Development - Jan. 2022
Privacy Act of 1974; System of Records
Nov. 9, 2021
NSPM-33: Presidential Memorandum on United States Government-Supported Research and Development National Security Policy
Jan. 19, 2021
Research Security at the National Science Foundation(NSF)
Jcore: recommended practices for strengthening the security and integrity of america's science and technology research enterprise (pdf).
Jan. 15, 2021
OSTP Regional Webinar on Research Security | Enhancing the Security and Integrity of America's Research Enterprise (PDF)
Ostp letter to the united states research community (pdf), research security training for the united states (u.s.) research community, insider threats 101 what you need to know.
Research Security Program
The Office of Research and Innovation has created this web page to help MSU faculty and staff stay current with emerging federal guidelines. The page will be updated as new information, guidelines, and resources become available. MSU values its international collaborators and inter-institutional affiliations. Preservation of important international relationships will be facilitated by our careful attention to federal requirements of transparency in research and related activity.
Requirements
To comply with the research security requirements outlined in the Presidential Memorandum on United States Government-Supported Research and Development National Security Policy (NSPM-33) and other applicable regulations, a research security committee has been formed at Michigan State University. This committee will provide recommendations to the Vice President for Research and Innovation for implementing a Research Security Program.
Heads of funding agencies shall require that research institutions receiving Federal science and engineering support in excess of 50 million dollars per year certify to the funding agency that the institution has established and operates a research security program. Institutional research security programs should include elements of cyber security, foreign travel security, insider threat awareness and identification, and, as appropriate, export control training. Heads of funding agencies shall consider whether additional research security program requirements are appropriate for institutions receiving Federal funding for R&D in critical and emerging technology areas with implications for United States national and economic security. Section 4(g) of NSPM-33
The following requirements, as outlined in the Guidance for Implementing National Security Presidential Memorandum 33 (NSPM-33) on National Security Strategy for United States Government-supported Research and Development , are highlighted below:
- Cybersecurity
- Foreign Travel Security
- Research Security Training
- Export Control Training
- Research Security Point of Contact (POC)
In addition to NSPM-33, the Department of Defense (DoD) has launched CMMC 2.0 , a comprehensive framework designed to protect the defense industrial base from increasingly frequent and complex cyberattacks.
Communications
Presentation on cybersecurity to university council.
September 26, 2023
- Chief Information Officer & Executive Vice President for Administration Melissa Woo
- Vice President for Research and Innovation Doug Gage
Contact ODNI
The ODNI Office of Strategic Communications is responsible for managing all inquiries and correspondence from the public and the media. Before contacting ODNI, please review www.dni.gov to see if we have already posted the information you need.
Contact ODNI by Postal Mail
Please send your questions, comments, or suggestions to:
Office of the Director of National Intelligence
Office of Strategic Communications
Washington, D.C. 20511
By Fax: 703-275-1225
Send Correspondence to the Director of National Intelligence
Please send correspondence to:
The Honorable Avril Haines
Director of National Intelligence
Employment Verification
Need to verify an employee’s employment? Contact ODNI Human Resources
If you are a mortgage company, creditor, or potential employer, you may submit your request by fax or mail to ODNI.
ODNI does not provide verbal responses, nor itemize pay by overtime, bonuses, and awards. ODNI will not provide pay information that includes employer information.
Request by Fax: Please send employment verification requests to 703-275-1217
Please allow three to five business days for ODNI to process requests sent by fax.
If you prefer to mail an employment verification request please send to:
Human Resource Management
Please allow ten business days for ODNI to process requests by mail.
The Intelligence Community Inspector General
In accordance with Title 50 U.S.C.A. Section 3033, the Inspector General of the Intelligence Community (IC IG) conducts independent and objective audits, investigations, inspections, and reviews to promote economy, efficiency, effectiveness, and integration across the Intelligence Community.
Questions or comments about oversight of the Intelligence Community? Contact the Office of the Intelligence Community Inspector General .
Privacy and Civil Liberties
The Office of Civil Liberties, Privacy and Transparency (CLPT) leads the integration of civil liberties and privacy protections into the policies, procedures, programs and activities of the Intelligence Community (IC). Its overarching goal is to ensure that the IC operates within the full scope of its authorities in a manner that protects civil liberties and privacy, provides appropriate transparency, and earns and retains the trust of the American people.
To report a potential civil liberties and privacy violation or file a complaint, please review the requirements at the CLPT homepage .
Equal Employment Opportunity Complaints
The Intelligence Community Equal Employment Opportunity and Diversity (EEOD) Office is responsible for the overall management of the ODNI EEO and Diversity Program, and provides IC-wide oversight and guidance in developing, implementing, and measuring progress in EEO, diversity, and inclusion.
The IC EEOD Office is committed to providing equal employment opportunity for all employees and applicants based on merit and without regard to race, color, religion, sex, age, national origin, sexual orientation, and physical or mental disability.
Applicants or employees who believe they have been discriminated against on the bases of race, color, religion, sex/gender (sexual orientation and gender identity), national origin, age, disability, genetic information (including family medical history) and/or reprisal for prior participation in the EEO process may raise their concerns to the IC EEOD Office .
Prepublication Classification Review
If you have worked for the ODNI in a staff or contract capacity and are intending to share intelligence-related information with the public through social media posts, books or television and film productions, you will need to submit the materials for approval.
For guidance and instructions, please email ODNI Prepublication Review at [email protected] .
Freedom of Information Act Requests
The goal of the ODNI Freedom of Information Act / Privacy Act Office is to keep the public better informed about the agency’s efforts and to ensure U.S. security through the release of as much information as possible, consistent with the need to protect classified or sensitive information under the exemption provisions of these laws.
FOIA Resources
Careers and Employment
The Intelligence Community provides dynamic careers to talented professionals in almost every career category . The ODNI is a senior-level agency that provides oversight to the Intelligence Community. ODNI is primarily a staff organization that employs subject-matter experts in the areas of collection, analysis, acquisition, policy, human resources, and management.
- Career Opportunities
- Student Opportunities
Conducting Research with the Intelligence Community
Intelligence Advanced Research Projects Activity tackles some of the most difficult challenges across the intelligence agencies and disciplines, and results from its programs are expected to transition to its IC customers. IARPA does not have an operational mission and does not deploy technologies directly to the field.
If you would like to learn more about engaging with IARPA on their highly innovative work that is already positively impacting the U.S. Intelligence Community and society in general, please follow the link below.
Working with IARPA
Latest Updates from the ODNI
Track the latest developments and stories of interest from the Office of the Director of National Intelligence:

You are leaving our Website
You have selected to open
If you would like to not see this alert again, please click the "Do not show me this again" check box below
- Organization
- Mission, Vision & Values
- Related Links
- Related Content
- Operating Status
- What is Intelligence?
- Members of the IC
- IC Policies & Directives
- IC Assessments & Reports
- IC Technical Standards
- FOIA Reading Room
- Transparency
- Objectivity
- Accountability
- Collaboration
- Special Programs
- Careers Features
- Reports & Publications
- Press Releases
- Speeches & Interviews
- Congressional Testimonies
- News Articles
- NCTC Newsroom
- NCSC Newsroom
- NCBC Newsroom
- CTIIC Newsroom
- FMIC Newsroom
- Seals & Graphics
- Principles of Artificial Intelligence Ethics for the IC
- 53 HPSCI Transcripts
- Private Sector Engagement
- National Strategy for Counterterrorism
- The AIM Initiative
- Declassified Tet Offensive Documents
- ICIG Semiannual Report Apr-Sept 2018
- Introducing IC Whistleblowing
- See More Features
Office of the Director of National Intelligence
- Safeguarding Science
- Research Security
- " onclick="window.open(this.href,'win2','status=no,toolbar=no,scrollbars=yes,titlebar=no,menubar=no,resizable=yes,width=640,height=480,directories=no,location=no'); return false;" rel="nofollow"> Print

In February 2024, the White House Office of Science and Technology Policy (OSTP) issued a memorandum on Policy Regarding Use of Common Disclosure Forms , which outlines guidelines on the use of common disclosure forms for federal agencies to use when evaluating proposals. These will help the government identify conflicts of commitment and potential duplication with the work of foreign governments. OSTP also released Guidelines for Federal Research Agencies Regarding Foreign Talent Recruitment Programs . This guidance provides a definition of foreign talent recruitment programs, guidelines for federal employees regarding foreign talent recruitment programs, and guidelines for individuals involved in malign foreign talent recruitment programs in federal projects.
In August 2023, the National Institute of Standards and Technology (NIST) released the " Safeguarding International Science Research Security Framework ," which is designed to enable organizations to implement a mission-focused, integrated, risk-balanced program through the application of research security principles and best practices that fosters the safeguarding of international science while mitigating risks to the integrity of the open collaborative environment. This NIST Framework is a living document and will continue to be updated and improved as its users provide feedback on implementation of review procedures or to address new or emerging risks. This will ensure it is meeting the needs of Research Security practitioners in a dynamic and challenging environment of new threats, risks, and creative solutions.
The National Science Foundation is committed to maintaining the integrity of international scientific collaborations. They have developed resources to enhance research security practices that are reliable and adaptive to emerging and evolving threats. You can find these resources below and visit the NSF Research Security site for more information.
Quick Reference
Introduction
- Research Security Background Documents
- Research Security Actions and Practices
- White House Documents
- Documents on Disclosure Requirements and Standardization
- Documents on Digital Persistent Identifiers (DPIs)
- Documents on Research Security Programs
- Risk Assessment and Mitigation
- Value of Principled International Collaboration
- Research Security Guidance from International Entities
- Research Security Guidance from Associations and Societies
Introduction
Below is a collection of documents for reference collected by the National Science Foundation’s (NSF) Office of the Chief of Research Security Strategy and Policy (OCRSSP) regarding best practices in research security for the academic community. As stated by the NSPM-33 Implementation Guidance, research security is defined as “safeguarding the research enterprise against the misappropriation of research and development to the detriment of national or economic security, related violations of research integrity, and foreign government interference.”
This research security toolkit is intended to serve as a resource for the academic community to understand initiatives currently underway and rationale for published guidance. Beginning with documents intended to outline key emerging concerns in the fundamental research security ecosystem (see Section I and Section II ) and documents published by the White House (see Section III ), resources are then categorized into seven groups: resources related to disclosure requirements and standardization (see Section IV ); digital persistent identifiers (DPIs) (see Section V ); research security programs (see Section VI ); risk assessment and mitigation (see Section VII ); the value of principled collaboration (see Section VIII ); research security guidance from international entities (see Section IX ); and research security guidance from associations and societies (see Section X ).
I. Research Security Background Documents
- NSDD-189 – National Security Decision Directive 189 (NSDD-189) (Established in 1985, reaffirmed in 2001 and 2010) Directive Short Description: NSDD-189 remains a cornerstone of the fundamental research enterprise, making a clear distinction between fundamental and classified research and stating that products of fundamental research should remain “remain unrestricted” to the “maximum extent possible.”
- JASON/NSF – JASON Report on Fundamental Research Security (Dec 2019) Full Report Short Description: “NSF has charged JASON to produce an unclassified report that can be widely disseminated and discussed in the academic community, providing technical or other data about specific security concerns in a classified appendix.” Of the 6 questions NSF charged JASON to answer relevant to openness in fundamental research, principles of scientific openness, areas of fundamental research necessitating more control, controls on information, and best practices researchers can put in place, this report details “the results from the ensuing inquiry, discussions, and debates engaged with NSF, senior university administrators, the intelligence community, law enforcement, and others.” NSF Response to JASON Report Short Description: This document includes NSF’s response to JASON’s nine recommendations on fundamental science and security.
- The Association of American Universities (AAU), Association of Public and Land-Grant Universities (APLU), Council on Government Relations (COGR) – University Actions to Address Concerns about Security Threats and Undue Foreign Government Influence on Campus (May 2020) Document Short Description: “APLU and AAU have previously identified and shared effective practices universities are employing to ensure the security of research, protect against intellectual property theft and academic espionage, and prevent actions or activities by foreign governments and/or other entities that seek to exert undue foreign government influence or infringe on core academic values (e.g. free speech, scientific integrity, etc.)...The following incorporates new and existing activities universities are pursuing, according to the recent survey collection. We encourage all universities to review these examples and to consider implementing practices that might prove effective on their own campuses to protect against research security threats and undue foreign government.”
- NSF – Research Security Website Website Short Description: The NSF Research Security website includes updates on research security activities being conducted by the Office of the CRSSP, summaries of issues relevant to foreign interference and risk mitigation, and additional resources for reference.
- NSF – Webpage on NSTC Research Security Subcommittee, NSPM-33 Implementation Guidance Disclosure Requirements & Standardization Website Short Description: “The National Science and Technology Council (NSTC) Research Security Subcommittee has worked to develop consistent disclosure requirements for use by senior personnel, as well as to develop proposed common disclosure forms for the Biographical Sketch and Current and Pending (Other) Support sections of an application for Federal research and development (R&D) grants or cooperative agreements. NSF has agreed to serve as steward for these common forms as well as for posting and maintenance of the table entitled, NSPM-33 Implementation Guidance Pre- and Post-award Disclosures Relating to the Biographical Sketch and Current and Pending (Other) Support.” This website provides up-to-date information on disclosure requirements.
- COGR – Matrix of Science & Security Laws, Regulations, and Policies (Sep 2022) Webpage with Matrix Short Description: “COGR has developed a comprehensive chart that summarizes and compares federal laws, regulations, and policies in the area of science and security. The chart is divided into three separate tabs that cover (a) major federal-wide legislation or policy (e.g., National Presidential Security Memorandum 33, CHIPS and Science Act of 2022); (b) agency disclosure requirements for researchers and research institutions; and (c) agency conflict of interest policies. The chart will be updated as new laws, policy and guidance are published."
Back to top of page
II. Research Security Actions and Practices
- NSF – Former NSF Director Dr. France A. Córdova’s Dear Colleague Letter to the Academic Community (Jul 2019) Letter Short Description: Short Description: This Dear Colleague Letter, addressed to the academic community, identifies emerging risks to the nation’s science and engineering enterprise and identifies actions NSF is undertaking to uphold the values of “openness, transparency, and reciprocal collaboration.”
- AAU, APLU, COGR – University Actions to Address Concerns about Security Threats and Undue Foreign Government Influence on Campus (May 2020) Document Short Description:
- NSTC – Recommended Practices for Strengthening the Security and Integrity of America’s Science and Technology Research Enterprise (Jan 2021) Document Short Description: “This document was developed by the Subcommittee on Research Security, in coordination with the National Security Council staff, and was reviewed by JCORE [the Joint Committee on the Research Environment]. The document outlines recommended guidelines for organizations that conduct research.”
- American Council on Education (ACE) – Letter to ACE Member Presidents and Chancellors Regarding Growing Concerns about Foreign Influence/Interference (May 2019) Letter Short Description: This letter to ACE member Presidents and Chancellors highlights growing concerns regarding foreign influence and foreign interference in the U.S. research environment. In addition to citing steps federal entities are taking to secure the fundamental research environment, the letter offers suggestions and actions institutions can take to further enhance the security of their international partnerships.
- AAU – Actions Taken to Address Foreign Security Threats, Undue Foreign Interference, and Protect Research Integrity at U.S. Universities (Jun 2022) Document Short Description: This document summarizes “actions that have already been taken or are currently being taken by both universities and federal entities regarding research security.” Sections include 1) actions taken by universities; 2) actions taken by Congress; 3) actions taken by the Executive branch and federal agencies; and 4) existing federal research security requirements.
III. White House Documents
- National Security Presidential Memorandum on United States Government-Supported Research and Development National Security Policy 33 (NSPM-33) (Jan 2021) Memorandum Short Description: “This memorandum directs action to strengthen protections of United States Government-supported Research and Development (R&D) against foreign government interference and exploitation. The United States Government provides significant support to R&D across a broad spectrum of research institutions and programs conducted both within and outside of the United States and its territories. This R&D, including both basic and applied research, is a key contributor to American science and technology (S&T) innovation and is essential to United States economic and national security.”
- NSTC – NSPM-33 Implementation Guidance (Jan 2022) Implementation Guidance Short Description: “The purpose of this document is to provide guidance to Federal departments and agencies regarding their implementation of National Security Presidential Memorandum 33 on National Security Strategy for U.S. Government-Supported Research and Development.”
IV. Documents on Disclosure Requirements and Standardization
- Government Accountability Office (GAO) – Federal Research: Agencies Need to Enhance Policies to Address Foreign Influence (Dec 2020) Report Short Description: “GAO was asked to review federal agency and university COI policies and disclosure requirements. In this report, GAO examines (1) COI policies and disclosure requirements at selected agencies and universities that address potential foreign threats, (2) mechanisms to monitor and enforce policies and requirements, and (3) the views of selected stakeholders on how to better address foreign threats to federally funded research. GAO reviewed laws, regulations, federal guidance, and agency and university COI policies and requirements. GAO also interviewed agency officials, university officials, and researchers.” See full report for information relevant to disclosure requirements and standardization.
- NSPM-33 (Jan 2021) Memorandum Short Description: For information relevant to disclosure requirements and standardization, see Section 4.
- NSTC – NSPM-33 Implementation Guidance (Jan 2022) Document Short Description: For information relevant to disclosure requirements and standardization, see pp. 2-7.
- NSF – NSF Proposal and Award Policies and Procedures Guide (PAPPG) (NSF 22-1) (Oct 2021) Document Short Description: “The PAPPG is comprised of information relating to NSF’s proposal and award process for the assistance programs of NSF.” The PAPPG is designed to set forth NSF’s proposal preparation and submission guidelines, as well as set forth NSF policies and procedures regarding the award, administration, and monitoring of grants and cooperative agreements. For information relevant to disclosure requirements and standardization, see Chapters II.C.1.e, II.C.2.f, and II.C.2.h.
- NSF – Draft Common Disclosure Forms for the Biographical Sketch and Current and Pending (Other) Support Federal Register Notice NSF Website Short Description: “NSF, on behalf of the National Science and Technology Council's (NSTC) Research Security Subcommittee, is soliciting public comment on common disclosure forms for the Biographical Sketch and Current and Pending (Other) Support sections of a research application. An excel spreadsheet that summarizes all of the data elements that will be collected in both the Biographical Sketch and Current and Pending (Other) Support, as well as their associated attributes, also is included for public comment.” All comments must be received by October 31, 2022, to be assured consideration. For updated information relevant to disclosure requirements and standardization, visit the NSF website.
- National Institutes of Health (NIH) – Requirements for Disclosure of other Support, Foreign Components, and Conflicts of Interest Website Short Description: “Full transparency in NIH applications and throughout the life of an NIH grant is critical. NIH requires the disclosure of all sources of research support, foreign components, and financial conflicts of interest for senior/key personnel on research applications and awards. NIH uses this information when making its funding decisions to determine if the research being proposed is receiving other sources of funding that could be duplicative, has the necessary time allocation, or if financial interests may affect objectivity in the conduct of the research.” This webpage provides information on applicant and recipient institution responsibilities, a chart on disclosure requirements, and details NIH’s responsibilities in the grant award process. For information relevant to disclosure requirements and standardization, see full webpage.
- Department of Energy (DOE) – PF 2022-32 Department of Energy Current and Pending Support Disclosure Requirements for Financial Assistance (Jun 2022) Website Financial Assistance Letter Short Description: “Information and guidance regarding the Department of Energy’s (DOE’s) implementation of National Security Presidential Memorandum 33 (NSPM-33) on National Security Strategy for United States Government-Supported Research and Development, issued January 2022 is provided by the attached Financial Assistance Letter.” For information relevant to disclosure requirements and standardization, see the Financial Assistance Letter
V. Documents on Digital Persistent Identifiers (DPIs)
- NSPM-33 (Jan 2021) Memorandum Short Description: For information relevant to DPIs, see Section 4.
- NSTC – NSPM-33 Implementation Guidance (Jan 2022) Implementation Guidance Short Description: For information relevant to DPIs, see pp. 8-10.
- COGR – Summary of NSTC Guidance for Implementing NSPM-33: Provisions Regarding DPIs, Consequences, Information Sharing and Research Programs (Jan 2022) Summary Short Description: “This summary highlights key points of the NSPM-33 Guidance that address the other topics covered by the document: DPIs, consequences, information sharing, and research security programs.” For information relevant to DPIs, see pp. 1-2.
VI. Documents on Research Security Programs
- NSPM-33 (Jan 2021) Memorandum Short Description: For information relevant to research security programs, see Section 4.
- NSTC – NSPM-33 Implementation Guidance (Jan 2022) Implementation Guidance Short Description: For information relevant to research security programs, see pp. 18-21.
- GAO – Federal Research: Agencies Need to Enhance Policies to Address Foreign Influence (Dec 2020) Report Short Description: For information relevant to research security programs, see pp. 25-26.
- AAU, APLU, COGR – University Actions to Address Concerns about Security Threats and Undue Foreign Government Influence on Campus (May 2020) Document Short Description: For information relevant to research security programs, see pp. 2-5.
- COGR – Summary of NSTC Guidance for Implementing NSPM-33: Provisions Regarding DPIs, Consequences, Information Sharing and Research Programs (Jan 2022) Summary Short Description: For information relevant to research security programs, see pp. 5-6, 8-9.
VII. Risk Assessment and Mitigation
- NSF/JASON – JASON Report on Fundamental Research Security (Dec 2019) Full Report Short Description: See full report for information relevant to risk assessment and mitigation. See Section 7.3 for samples of questions that may be used for risk assessment.
- NSF – Research Security Website Website Short Description: For information relevant to risk assessment and mitigation, see section on “Foreign Interference and Risk Mitigation.”
- NSTC – Recommended Practices for Strengthening the Security and Integrity of America’s Science and Technology Research Enterprise (Jan 2021) Document Short Description: For information relevant to risk assessment and mitigation, see pp. 14-15, items 18-21.
- AAU, APLU – Principles and Values to Guide Actions Relevant to Foreign Government Interference in University Research (May 2021) Document Short Description: This document summarizes “fundamental principles and values of the AAU and APLU member institutions that are relevant to their approach to foreign government interference. The goal of articulating these principles and values is to foster protection against foreign government interference without damaging the contributions to national and economic security that the United States derives from the university research enterprise.” The document covers three components: 1) common values of AAU and APLU universities relevant to foreign government interference in research; 2) principles for government actions in protecting and ensuring the future of the U.S. university research enterprise, and 3) principles for universities in responding to foreign government interference. For information relevant to risk assessment and mitigation, see pp. 6-7.
- ACE – Letter to ACE Member Presidents and Chancellors Regarding Growing Concerns about Foreign Influence/Interference (May 2019) Letter Short Description: For information relevant to risk assessment and mitigation, see pp. 4-7.
- ACE – Letter to ACE Member Presidents Hosting Confucius Institutes (Jul 2018) Letter Short Description: This letter to ACE member presidents of institutions with Confucius Institutes provides recommendations on how to proactively assess the security of these specific programs, increase transparency, and enhance the security of research with national and economic security implications.
VIII. Value of Principled International Collaboration
- American Academy of Arts and Sciences (AAAS) – America and the International Future of Science, Challenges for International Scientific Partnerships Initiative (Dec 2020) Report Short Description: “This report takes a broad view of international scientific partnerships, on all scales and levels of formality, and identifies elements that are integral to successful collaboration.” For information relevant to principled international collaboration, see pp. 33-35.
IX. Research Security Guidance from International Entities
- Australia – “Guidelines to Counter Foreign Interference in the Australian University Sector”, University Foreign Interference Taskforce (Nov 2019, modified in Nov 2021) Guidelines Short Description: “These Guidelines support universities to develop new or examine existing tools, frameworks and resources to use for assessing and mitigating risks from foreign interference, proportionate to risk. They also promote greater consistency across the sector. They offer principle-based and specific advice to universities on how to manage risk in their institution. The advice recognises that risk is not uniform across the sector, and universities may implement additional or existing leading-practice mitigation actions proportionate to their own risks of foreign interference. Universities are encouraged to consider whether the Guidelines can be applied to transnational education business models or offshore campuses, where appropriate.”
- Australia – Australian Strategic Policy Institute, China Defence Universities Tracker (launched Nov 2019, updated May 2021) Tracker Report Short Description: “The China Defence Universities Tracker is a database of Chinese institutions engaged in military or security-related science and technology research. The updated Tracker – and accompanying report – continue to be a tool that enables universities, governments, the business community and scholars to conduct due diligence as they engage with entities from China…the Tracker should be used to inform due diligence of Chinese institutions, however, the fact that an institution is not included here does not indicate that it should not raise risks or is not involved in defence research. Similarly, entries in the database may not reflect the full range and nature of an institution’s defence and security links.”
- Canada – Safeguarding Your Research Website Website Short Description: This website provides researchers guidance on how to safeguard their research and innovation, covering topics such as 1) why researchers should safeguard research, 2) who they are at risk from, 3) what risks exist, 4) steps that can be taken to protect research, and more.
- Denmark – “Guidelines for International Research and Innovation Cooperation” (May 2022) Guidelines Short Description: “These guidelines have been prepared by the Committee on guidelines for international research and innovation cooperation…[and are intended to] help Danish institutions achieve a balanced approach to international cooperation on research and innovation, aiming to reduce ethical, financial and security risks and to protect their own long-term interests within such cooperation.”
- Global Research Council – Statement of Principles and Practices for Research Ethics, Integrity, and Culture in the Context of Rapid-Results Research (May 2022) Statement Short Description: “This Statement outlines eight principles and practices that frame the collective responsibility of funding agencies; researchers; public and private research organizations (both for- and non-profit); and national governments in ensuring the integrity of rapid-results research. This statement addresses all aspects of national and international research enterprises, from ideation to dissemination and commercialization, and has the potential to strengthen research outcomes.”
- G7 – Common Values and Principles on Research Security and Research Integrity (June 2022) Paper Short Description: This collaborative paper among G7 members emphasizes “the continuation of a collaborative research system where the importance of all talent – domestic and international – is acknowledged. Openness and security are not contradictory but complementary and mutually reinforcing.” This paper provides the G7’s common vision and principles in research security and integrity; defines important concepts; and describes current activities aimed at addressing existing concerns in the research enterprise.
- Japan – Policy Directions for Ensuring Research Integrity in Response to New Risks Associated with Increasing Internationalization and Openness of Research Activities (April 2021) Document Short Description: This document outlines steps the Japanese government is taking “in collaboration with researchers, universities, research institutions, and research funding agencies to support [and] autonomously secure the soundness and fairness of research (research integrity) of researchers, universities, and research institutions.” Efforts discussed include initiatives relevant to disclosure and outreach to organizations.
- New Zealand – Due Diligence Assessments: For Espionage and Foreign Interference Threats (May 2022) Guide Short Description: “This guidance outlines potential Foreign Interference risks to New Zealand business, research, and investment. It has practical approaches to due diligence, including identifying and making informed decisions about potential risks.”
- Organization for Economic Co-operation and Development (OECD) – OECD Report on Integrity and Security in the Global Research Ecosystem (June 2022) Report Short Description: “This report describes policy initiatives and actions to safeguard national and economic security whilst protecting freedom of inquiry, promoting international research cooperation, and ensuring openness and non-discrimination. It includes examples of actions that are being taken to prevent foreign interference, manage risks, and help ensure trust in science in the future, offering recommendations to help countries develop effective policies to strengthen research security as part of a broader framework of research integrity.”
- Sweden – Swedish Foundation for International Cooperation in Research and Higher Education (STINT), Responsible Internationalisation: Guidelines for Reflection on International Academic Collaboration (2020) Document Short Description: “The document is intended to serve as support for reflection and as the basis for discussion of strategic decisions on internationalisation. The purpose is to aid researchers, research directors, department heads, and university administration in assessing collaborations and structuring discussions on how the HEI [higher education institution], department or research group should approach international collaboration.”
- United Kingdom – Website on Trusted Research Website Short Description: Trusted Research, “a campaign to raise awareness of the risks to research collaborations which may occur when working with organisations or research partners with links to nations whose democratic and ethical values are different from our own”, aims to support the integrity of the system of international research collaboration. “Advice has been produced in consultation with the research and university community and is designed to help the U.K.’s world-leading research and innovation sector get the most out of international scientific collaboration whilst protecting intellectual property, sensitive research and personal information.” The U.K. Government’s National Technical Authority for Physical and Personnel Protective Security has developed an interactive website that provides guidance and checklists for academia and industry.
X. Research Security Guidance from Associations and Societies
- AAU, APLU, COGR – University Actions to Address Concerns about Security Threats and Undue Foreign Government Influence on Campus (May 2020) Document Short Description
- AAU, APLU – Principles and Values to Guide Actions Relevant to Foreign Government Interference in University Research (May 2021) Document Short Description
- ACE – Letter to ACE Member Presidents and Chancellors Regarding Growing Concerns about Foreign Influence/Interference (May 2019) Letter Short Description
- ACE – Letter to ACE Member Presidents Hosting Confucius Institutes (Jul 2018) Letter Short Description
- Association of American Medical Colleges (AAMC) – Research Security and Foreign Interference at U.S. Academic Institutions Webpage Webpage Short Description: “This page provides background information [on research security and foreign interference], the latest updates on relevant federal government policies and activities, and considerations and resources for institutional leadership, administrators, and researchers as they address this issue on their [campuses].”
- COGR – Matrix of Science & Security Laws, Regulations, and Policies (Sep 2022) Webpage with Matrix Short Description
- Academic Resources
- Cybersecurity
- Operations Security
- Counterintelligence
- Insider Risk
- Supply Chain Risk Management
- Threat Information
- Information Security
- Personnel Security
- Physical Security
National Counterintelligence and Security Center
- Contact NCSC
- Regulations
- CI References
- Travel Tips
An official website of the United States government
Here's how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS. A lock ( Lock Locked padlock ) or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure websites.

NSF 2022 Research Security Training for the United States Research Community awardees announced
Research security is integral to national security. Addressing knowledge gaps, strengthening training in research security, managing and mitigating risk in international collaborations, and adhering to research security best practices help safeguard scientific progress and protect U.S. research interests from foreign and domestic risks and threats.
The U.S. National Science Foundation announced four awards under the Research Security Training for the United States Research Community program. The program is a cornerstone of the NSF mandate to strengthen research security in the U.S. while encouraging principled international collaboration. NSF has long worked in partnership with federal agencies that fund research to improve the development and implementation of research security. In addition to NSF, the research security training module series is also supported by funding from the National Institutes of Health, the Department of Energy, and the Department of Defense.
Awardees will receive financial support to establish research security training frameworks that address U.S.-funded research and development security concerns, risks and threats. The four awardees will focus on developing training modules that detail research security insights and best practices, address the importance of disclosure, identify and remedy knowledge gaps in risk management and mitigation, and provide training on principled international collaboration.
The 2022 Research Security Training for the United States Research Community awardees are listed below.
- Research Security Training: The Importance of Research Security , The University of Alabama in Huntsville. The team will develop research security training that provides information and insights about best practices in designing, developing and evaluating educational tools for the adult learner. The training module will focus on the importance of research security, enhance awareness and provide online training about existing and emerging risks and threats to the global research ecosystem. This project is funded with a contribution from NSF’s EPSCoR program.
- Research Security Training: The Importance of Disclosure , Texas A&M University System. The team will design and develop a training module about research security that will focus on the importance of properly disclosing information when proposing for and conducting federally funded research, increase awareness and understanding of the current disclosure process, and clarify the importance of transparency and risks associated with non-disclosure. The Texas A&M team is part of a consortium that includes the Texas A&M Engineering Experiment Station, the Texas A&M University System Administrative and General Offices and Redcliff Enterprises.
- Research Security Training: Risk Management and Mitigation , University of Pennsylvania. The team will develop a research security training module based on an assessment of current research security understanding and knowledge gaps among researchers. The module will examine actions researchers and their institutions can take to assess, reduce and manage security risks to ongoing, planned and unpublished research data. Institutions will be able to modify the training module to incorporate local practices. The University of Pennsylvania team is part of a consortium that includes the University of Madison at Wisconsin, the University of Chicago, Regents University of Michigan and the University of Pittsburgh.
- Research Security Training: International Collaboration , Associated Universities, Inc., and AUI Labs The team will create an online research security training module focused on the importance of principled international collaboration and ongoing threats posed to scientific research security by improper foreign government influence. The training module will be customized for specific stakeholder groups in the U.S. research ecosystem and use hypothetical scenarios and real-world case studies to propel learners through advanced levels of knowledge and skills.
The modules the awardees develop will be available to the appropriate researchers, stakeholders, students, academics, research security experts and leaders, government agencies and national laboratories.
Research areas
University of Houston Key Part of First National Workshop on Research Security
Experts To Focus on Both Human and AI External Influence
By Kevin Quinn — 713-743-7898
- Science, Energy and Innovation

In a first-of-its-kind national workshop, The University of Houston, Rice University, IPTalons and the Society of Research Administrators International, hope to shape the future laws, policies and guidelines that will enhance research security.
In recent years, concerns have grown over persistent compliance failures which sometimes enable foreign governments and entities, particularly China and Russia, to exploit national and international science and technology research.
“UH is an integral partner in the Rice-led, NSF-funded workshop where the goal is to take a rational approach to research security that is based on evidence and balances the various risks without jeopardizing our highly valued international collaborations,” said Claudia Neuhauser, interim vice chancellor/vice president for research at UH. “We are excited to be a part of this group and to contribute to this developing field of research.”
“With our colleagues at Rice, we are convening with global academic and government leaders to come up with ideas for protecting the fruit of research projects from theft by malevolent parties,” said Chris Bronk, associate professor at UH’s Hobby School of Public Affairs and a cybersecurity expert. “But more importantly, we are engaging in a dialog on research ethics and international collaboration at the frontiers of science.”
Supported by the National Science Foundation’s Office of the Chief of Research Security, Strategy and Policy , this two-part event included a virtual workshop held May 2 and an in-person workshop scheduled May 23-24 at Rice’s Baker Institute for Public Policy in Houston. Rebecca Keiser, NSF chief of research security strategy and policy, will deliver a keynote address at the in-person event.
“People assume our primary concern is to guard against forms of espionage, but this is a much bigger issue than mere spying,” Bronk said. “At UH, we have a degree program in the cybersecurity of transportation, and as we integrate AI into that sector, we must protect code and algorithms from outside manipulation. So, to me, research security is a cybersecurity problem as well.”
“Notably, there is little available data or public understanding of these activities due to the sensitive nature of the information and the desire of research-producing entities to avoid reputational risk,” said Tam Dao , assistant vice president for research security at Rice and the workshop’s lead organizer.
On July 12, 2023, the NSF launched its Research on Research Security Program (RoRS) designed to study the field of research security as required in the CHIPS and Science Act and following the federal requirements outlined in the National Security Presidential Memorandum 33 and its accompanying implementation guidelines .
The findings and recommendations from the workshop will be summarized in a comprehensive report to be shared with the NSF and published by the Baker Institute for broad distribution. To learn more about the workshop, click here .
Top Stories
May 10, 2024
Tomas Bryan to Serve as UHS Student Regent
The University of Houston System Board of Regents will soon welcome a new student voice to the table. UH graduate student Tomas Bryan was announced as its student regent and will be formally sworn in at a future board meeting.
- Student, Faculty and Staff Success
May 08, 2024
Getting Involved Key to UH Grads’ Success
This spring, 6,655 Cougars are crossing the finish line during UH's commencement ceremonies. Among these graduates are Coogs who balanced their studies with extracurricular activities that enhanced their university experience and prepared them for the journey ahead.
May 07, 2024
UH Professor Cristina Rivera Garza Wins 2024 Pulitzer Prize
University of Houston Professor Cristina Rivera Garza has won a 2024 Pulitzer Prize for her memoir “Liliana’s Invincible Summer: A Sister’s Search for Justice.” The Pulitzer Prize is regarded as the highest national honor in journalism, letters and drama, and music.
Official websites use .gov
Secure .gov websites use HTTPS

Academic Research Security
The Department of Defense greatly values its partnership with the academic community. Of paramount importance to the integrity and effectiveness of the academic research community has been the open, transparent, and merit-based nature of research collaborations. In recent years the Department, along with other federal research funding agencies, has become concerned that foreign governments may try to undermine the integrity of the academic research enterprise. This site is a resource for the actions that the Department and the interagency are taking to ensure the integrity of fundamental research in academia as well as steps that the academic community has taken. This site does not cover security measures for research that is not designated as fundamental research, which may include CUI or classified research that require additional protection. The Department welcomes dialogue with our partners in academia about ways to mitigate risks to academic research.
On June 8, 2023, the Under Secretary of Defense for Research and Engineering signed a Department of Defense-wide policy on reviewing fundamental research projects for conflicts of interest arising from foreign influence. The policy is part of the Department’s implementation of National Security Presidential Memorandum 33.
The Department values its relationship with the academic community and has benefited greatly from funding fundamental research at universities. This policy will protect fundamental research from foreign influence without stifling the progress of science, hindering international collaboration, or excluding talented foreign students and researchers from the research the Department funds. The goal in developing this policy is to ensure consistent and transparent implementation across the Department, set realistic expectations for DOD-funded researchers and institutions, abide by law and regulation, and be non-discriminatory.
The policy is posted to Defense.gov at : https://media.defense.gov/2023/Jun/29/2003251160/-1/-1/1/COUNTERING-UNWANTED-INFLUENCE-IN-DEPARTMENT-FUNDED-RESEARCH-AT-INSTITUTIONS-OF-HIGHER-EDUCATION.PDF
The policy is accompanied by two documents – the “Decision Matrix to Inform Fundamental Research Proposal Mitigation Decisions” and the “FY22 Lists Published in Response to Section 1286 of the John S. McCain National Defense Authorization Act for Fiscal Year 2019 (Public Law 115-232) as amended.”
The “Decision Matrix to Inform Fundamental Research Proposal Mitigation Decisions” is a guide to assist program managers and DOD Components in reviewing fundamental research proposals for potential conflicts of interest. The document also describes conditions under which mitigation is required or recommended, depending on the type of conflict and the timeframe in which it occurs. The Department is making this document public to be as transparent as possible about the types of behaviors the Department finds problematic and to give DOD-funded researchers a better understanding about how their proposals may be received. The Office of the Under Secretary of Defense for Research and Engineering will update the decision matrix as necessary to incorporate changes in law and policy, account for lessons learned, and ensure consistency with other Federal agencies.
The “FY22 Lists Published in Response to Section 1286 of the John S. McCain National Defense Authorization Act for Fiscal Year 2019 (Public Law 115-232) as amended” identifies foreign institutions that have been confirmed as engaging in problematic activity as described in Section 1286(c)(8)(A) of the referenced law. It also identifies problematic foreign talent programs. It is one of the sources that supplements the decision matrix document.
Questions, concerns, or feedback on the policy and accompanying documents should be emailed to the Academic Liaison at [email protected]
DoD Documents
“The Department of Defense (DoD) fully supports free scientific exchanges and dissemination of research results to maximum extent possible” - ATL Memorandum, DoD Policy on Fundamental Research, May 24, 2010
“The National Defense Authorization Act (NDAA) for FY 2019, Section 1286, pages 443-445, directs the Secretary of Defense to establish an initiative to work with academic institutions who perform defense research and engineering activities.” - USD(R&E) Memorandum, “Collecting Assistance Award Information As Required in Section 1281(d)(1) of the National Defense Authorization Act for Fiscal Year 2020”, June 29 th , 2020
“For decades, scientist at universities and research centers, supported by the Department of Defense (DoD), have made ground-breaking scientific discoveries that underpinned dramatic commercial and national security advances, significantly improving the lives of citizens here and abroad. Yet today, the ability to make similar advances is at risk, and research integrity is jeopardized through foreign governments’ exploitation that internationally target U.S. and allied partner research and intellectual capital. Let us redouble our efforts to protect research integrity and intellectual capital while seeking a long-term competitive advantage and premier innovation enterprise” USD(R&E) Letter to Academia, October 10 th , 2019
This memorandum directs action to strengthen protections of United States Government-supported Research and Development (R&D) against foreign government interference and exploitation . “ National Security Presidential Memorandum – 33, Presidential Memorandum on United States Government-Supported Research and Development National Security Policy”, January 14 th , 2021
“ Initiative to Support Protection of National Security Academic Researchers from Undue Influence and Other Security Threats (10 U.S.C. 2358 note)”
An act to authorize appropriations for fiscal year 2021 for military activities of the Department of Defense, for military construction, and for defense activities of the Department of Energy, to prescribe military personnel strengths for such fiscal year, and for other purposes. NDAA 2021 Section 1049 “Confucius Institutes”
Confucius Institute Waiver Program
Section 1062 of the National Defense Authorization Act (NDAA) for Fiscal Year (FY) 2021 prohibits the Department from providing funding to any U.S. institution of higher education hosting a Confucius Institute unless that institution receives a waiver from the Secretary of Defense. This prohibition does not apply to direct funding to students attending U.S. institutions of higher education. International institutions that host Confucius Institutes are not subject to the prohibition in section 1062 of the NDAA for FY 2021 and thus do not require waivers to receive Department of Defense (DoD) funding. The prohibition on funding goes into effect on October 1, 2023.
The DoD Office of the Under Secretary of Defense for Research and Engineering Confucius Institute Waiver Program is responsible for considering and approving or denying waiver applications from any U.S. institution of higher education that is hosting a Confucius Institute and desires a waiver from the prohibition on funding required by Section 1062 of the NDAA for FY 2021. The CIWP uses the NDAA for FY 2021 definition of Confucius Institute, which is: a cultural institute funded either directly or indirectly by the Government of the People’s Republic of China.
The Department has a separate process for reviewing and adjudicating waiver requests of the prohibition in Section 1091 of the NDAA for FY 2019 on obligating or spending funds for Chinese language instruction provided by a Confucius Institute. U.S. institutions of higher education hosting a Confucius Institute granted a waiver of the prohibition in Section 1062 of the NDAA for FY 2021 may still be subject to the prohibition in Section 1091 of the NDAA for FY 2019.
Guidance for applying to the Confucius Institute Waiver Program can be found here .
Academic Documents
“AAU and APLU have previously identified and shared effective practices universities are employing to ensure the security of research, protect against intellectual property theft and academic espionage, and prevent actions or activities by foreign government and/or other entities that seek to exert undue foreign government influence or infringe on core academic values (e.g. free speech, scientific integrity, etc.).” AAU-APLU Report: University Actions to Address Concerns about Security Threats and Undue Foreign Government Influence on Campus (May 2020)
Interagency Documents
OSTP “education brief” on conflicts of interest and conflicts of commitment. Enhancing the Security and Integrity of America’s Research Enterprise.
“The Biden-Harris Administration holds a strong commitment to protecting research security and maintaining the core values behind America’s scientific leadership, including openness, transparency, honesty, equity, fair competition, objectivity, and democratic values. During its final week in office, the previous administration issued a National Security Presidential Memorandum (NSPM-33) to “strengthen protections of United States Government-supported R&D against foreign government interference and exploitation” while “maintaining an open environment to foster research discoveries and innovation that benefit our nation and the world.”” OSTP blog post: “Clear Rules for Research Security and Researcher Responsibility”, August 10 th , 2021
For more information e-mail the DoD Academic Liaison at [email protected]

Time Is Up: The Research Security Program Standards Won’t Save the Waiting Research Organizations

The following guest blog by IPTalons was originally published at IPTalons.com
If you are like other university research executives, you probably have been waiting for more definitive guidance to come out of Washington, DC, regarding the National Security Presidential Memorandum 33 (or NSPM-33). Most research institutions in the higher education community have been hoping that the Office of Science and Technology Policy (OSTP) will tell them exactly how to protect their research from foreign influence threats. Unfortunately, the NSPM-33 final ruling, which should be published soon and details Research Security Program Standards (the “Standards”), will not provide the solution many organizations desire.
The Standards will likely be vague, leaving the direct requirements to the federal research grant funding agencies. The Standards are also unlikely to directly benefit research grant awardee organizations, as the federal government remains reluctant to commit funding and personnel to assist in building research security programs. However, the consequences of not establishing a research security program could be dire. Organizations receiving federal funding that want to stay competitive must design, implement, and manage their internal research security programs capable of meeting the various requirements mandated by individual funding agencies, such as the National Institutes of Health (NIH), the National Science Foundation (NSF), the Department of Energy (DoE), and others.
Over the past five years, Congress and funding agencies have published new requirements and guidelines to address research security concerns, including foreign influence and unreported conflicts of interest and commitment (COI/C). The requirements outlined in the NSPM-33, the CHIPS and Science Act, the National Defense Authorization Act (NDAA), and grant policy statements from federal research grant funding agencies did not provide standardized guidelines to instruct research universities on what or how to implement research security program components. Instead, the requirements highlighted that organizations must establish adequate research security programs, leaving the specific standards to meet the federal agencies providing the research funding. Many research universities and organizations responded to the requirements by waiting for further guidance from the federal government through the Research Security Program Standards. The reality, however, is that specific guidance will not be available.
One aspect is certain. The forthcoming Research Security Program Standards will not change the underlying practical requirements already written into the NSPM-33 and encoded into law by the passage of the CHIPS and Science Act: Every research university should implement a formal research security program, led by a professional research security officer, to identify, assess, investigate, and remediate research security risks. The proverbial clock to self-certify has started ticking, and research universities should anticipate that research security requirements will be showing up in the terms and conditions of their grant awards and contracts.
It’s crucial for organizations not to wait for specific implementation guidance from the federal government. U.S. research organizations have already faced fines or funding denials due to research security violations. Congress and the funding agencies expect organizations to take a proactive, risk-based approach to tackle potential COI/C and Foreign Influence. The institutions that will benefit the most will be those that are proactive about these requirements, understand the specifications of each funding agency, and implement a research security program accordingly. By taking the initiative, these institutions are ensuring their compliance and securing their future funding opportunities. Conversely, those who wait to establish a research security program will gravely affect their institution’s ability to receive funding.
Featured Resource:

6 ways to minimize risk in research administration
Get ebook >>

May. 21, 2024
Nsf chief of research security to speak at rice baker institute may 23, virtual keynote speech open to public.

Rebecca Keiser , the National Science Foundation’s (NSF) chief of research security strategy and policy (CORSSP), will deliver a virtual keynote address May 23 on the origins of the foundation’s research on research security (RoRS) program with Rice University’s Baker Institute for Public Policy.
The keynote address will kick off an invite-only, first-of-its-kind global workshop to examine the burgeoning field of RoRS, hosted by Rice, the University of Houston, IPTalons, Inc. and the Society of Research Administrators International. Participants will identify current themes, major issues and challenges in research security as well as chart a road map for the future of the NSF’s RoRS program. The workshop is led by Rice’s Office of Research Security and the Baker Institute’s Science and Technology Policy Program .

Keiser is head of the Office of International Science & Engineering (OISE) at the NSF. She has served as head of OISE since coming to the NSF in 2015. The office promotes an integrated, international strategy and manages internally focused programs that are innovative, catalytic and responsive to a broad range of NSF and national interests.
What : Keynote address – Responsible Collaboration Through Appropriate Research Security .
When : Thursday, May 23, 8:30-9:15 a.m.
Where : Virtual – register for the livestream here .
Keiser is the first CORSSP, a position established in March 2020 to ensure the security of federally funded research while maintaining open international collaboration. In this role, Keiser provides the NSF director with policy advice on all aspects of research security strategy. She also leads NSF’s efforts to develop and implement strategies to improve research security and the agency’s coordination with other federal agencies and the White House.
Prior to her post at the NSF, Keiser was a special adviser to the National Aeronautics and Space Administration (NASA) administrator and an executive-in-residence at American University. She held several positions with NASA, including associate deputy administrator for strategy and policy, associate deputy administrator for policy integration and executive officer to the deputy administrator.
Keiser also served as assistant to the director for international relations at the White House Office of Science and Technology Policy, where she provided policy guidance to the president’s science adviser. Her experience covers science and technology policy, agreements and other cooperative efforts.
2 Promising UCF Researchers Earn 2024 NSF CAREER Awards
Early-career professors Fan Yao and Li Fang are receiving significant research funding to continue catalyzing their work as part of an annual NSF grant program.
By Eddy Duryea ’13 | May 20, 2024

UCF assistant professors Li Fang and Fan Yao have been named 2024 U.S. National Science Foundation (NSF) Faculty Early Career Development program (CAREER) award winners. The recipients were awarded funding through five years for their submitted projects.
Fang, who is an assistant professor in UCF’s Department of Physics within the College of Sciences , is using the CAREER award to study the precise movement of electrons induced by light and to help educate others in her field.
Yao is an assistant professor in UCF’s Department of Electrical and Computer Engineering within the College of Engineering and Computer Science and a member of the Cyber Security and Privacy faculty cluster. He’ll use his CAREER award to identify lapses in computer processing security at the micro level and find ways to defend against them.
The annual award supports an estimated 500 early-career STEM faculty from either institutes of higher education or academic nonprofit organizations who have the potential to serve as academic role models in research and education and to lead advances in the mission of their department or organization.
Through their NSF CAREER awards, both Fang and Yao are continuing to build upon their research and contribute to key components of their respective fields.
Capturing Energy in a Fraction of a Second
Department of Physics
Title: Photo-induced Ultrafast Electron-nuclear Dynamics in Molecules
Award: $813,981 over five years
Li Fang is examining some of the smallest components of matter in some of the shortest amounts of time.
She studies how electrons move after their initial absorption of photo-energy as they attempt to interact, break or form a bond with other molecular components. The purpose of examining these molecular dynamics is crucial in better understanding physics and energy, Fang says.
“The dynamics of these charged particles will provide fundamental knowledge about energy absorption, dissipation and rearrangement in building blocks of materials and therefore is relevant to energy storage and harvest,” Fang says. “We implement spectroscopic tools to track the extremely fast motion of these charges. An electron’s motion is the first step in all chemical and photo reactions and ions are the subjects of chemical bonds that exist basically in all materials.”
Fang measures these movements in attoseconds and femtoseconds, which are one billion billionths of a second and one million billionths of a second, respectively.
Attoseconds are the natural time scale for electrons moving inside an atom while femtoseconds are the natural time scale for measuring nuclei moving within a molecule.
Fang’s NSF CAREER project will help her further uncover and measure how light can instigate changes at the molecular level and then share her research with the greater scientific community.
“The goal is to understand the ultrafast electron motion induced by intense laser beams and its correlation with the motion of the nuclei in a molecule,” she says. “An equally important part of my NSF CAREER award is the educational subproject, the goal of which is to introduce my research field ‘ultrafast science’ to a broader audience through media and local events and enhance diversity of workforce in science.”
Fang came to UCF in 2020 from the Ohio State University.
Since arriving, she has garnered significant funding and support for her projects. In 2020, Fang was one of 76 recipients – and the only recipient from Florida – to be awarded an early career research program grant from the U.S. Department of Energy .
She also was instrumental in securing NSF funding of nearly $2 million for a powerful laser in 2021, aiming to build a user facility at UCF to continue studying electrons and molecular bonds using precise measurements in attoseconds.
Fang says it was extremely gratifying to earn her NSF CAREER award, and it represents a culmination of her previous scientific endeavors.
“It definitely fit into my career and will help me fulfill my goals as a researcher and an educator,” she says.
Fang is thankful for the assistance of her peers and collaborators in cultivating her studies and developing her NSF CAREER proposal.
“The NSF CAREER program at UCF organized by Saiful Khondaker is very helpful with improving the writing of the educational subproject, which is crucial to the NSF CAREER project,” she says.
UCF has provided Fang with the opportunity to excel in her research, and she anticipates many more impactful discoveries to come.
“I am looking forward to carrying out real scientific experiments and discovering new findings with the state-of-the-art lasers and the spectroscopy systems we have,” Fang says. “Getting a prestigious CAREER award is just the start.”
Department of Electrical and Computer Engineering
Title: Understanding and Ensuring Secure-by-design Microarchitecture in Modern Era of Computing
Award: $556,875
Effective computer system security requires searching high and low within its infrastructure to address vulnerabilities that could be overlooked and exploited.
Fan Yao has dedicated his research to thoroughly poring through potential weaknesses within the architectural and microarchitectural designs of computing and memory units to see how they can be safeguarded against malicious hacks and data breaches.
“In today’s interconnected digital landscape, we depend on computing devices to store and process our sensitive and personal data,” he says. “Given that hardware forms the foundational bedrock of all computing systems, its security is paramount. A computer with compromised hardware security is akin to a skyscraper built on shaky ground.”
Specifically, Yao is using his NSF CAREER project to examine computer processors and analyze side channel leakage, which is compromised access to information or infrastructure through indirect means.
“Through the automation of microarchitectural security analysis, we aim to uncover hidden hardware-level states prone to leakage, as well as to develop software-level patterns that can exploit these vulnerabilities to quantify their leakage potential,” he says. “Subsequently, the project will focus on designing robust defense strategies to prevent microarchitectural information leakage, thereby ensuring stronger protection for future generations of processors.”
The awarded funds will continue to catalyze Yao’s research and allow him to further challenge the limits of computer security. He is hopeful that the results will serve as an educational cornerstone to both aspiring students and his peers, he says.
“This grant allows us to explore innovative security solutions more deeply and to train the next generation of researchers in this critical field,” Yao says. “This award fits perfectly into my career goals, as it enables me to establish a sustainable research program that can make meaningful contributions to both academia and industry.”
Yao arrived at UCF in the fall of 2018 after receiving his doctoral degree in computer engineering from the George Washington University.
The support and mentorship from UCF’s academic community and administration at UCF has been crucial to helping him achieve his research aspirations, he says.
“UCF has been extremely supportive in junior faculty career development,” Yao says. “Many of the preliminary results for this project were achieved through experiments facilitated by this support. I am also profoundly grateful for the comprehensive assistance received during the development of this proposal. This includes invaluable guidance from the UCF CAREER mentoring program and the insightful feedback on my proposal provided by senior faculty members in our department.”
Yao is proud to have been awarded an NSF CAREER grant, and says he is excited to further his research.
“Receiving the NSF CAREER grant is an incredible honor and a pivotal moment in my career,” he says. “It not only validates the importance and potential impact of our work on microarchitecture security, but also provides a substantial platform to expand our research efforts.”
More Topics
Pegasus magazine.

For a decade, UCF-based nonprofit Limbitless Solutions has transformed kids’ lives through bionic limbs.


- University Statistics
- University Leadership
- Events & Venues
- University Strategic Plan
- Bethlehem & the Lehigh Valley
- Maps & Directions
- Diversity, Inclusion & Equity
- COVID-19 Information Center
- Undergraduate Studies
- Majors & Undergraduate Programs
- Graduate Studies
- Interdisciplinary Studies
- Entrepreneurship and Innovation
- Creative Inquiry
- Continuing Education
- Provost & Academic Affairs
- International
- University Catalog
- Summer Programs
Our Colleges:
- College of Arts and Sciences
- College of Business
- College of Education
- College of Health
- P.C. Rossin College of Engineering and Applied Science
- Research Centers & Institutes
- Student Research Experience
- Office of Research
- Graduate Education & Life

- Undergraduate Admissions
- Apply to Lehigh
- Visits & Tours
- Tuition, Aid & Affording College
- Admission Statistics
- Majors & Programs
- Academics at Lehigh
- Student Life at Lehigh
- Student Profiles
- Success After Graduation
- Lehigh Launch
- Contact Us & Admissions Counselors
Information for:
- Transfer Students
- International Students
- School Counselors
- Graduate Admissions
Student Life
- Clubs & Organizations
- Housing & Dining
- Student Health & Campus Safety
- Arts & Athletics
- Advocacy Centers
- Student Support & Transition to College
- Prospective Student Athletes
- Radio & TV Broadcasts
- Camps & Clinics
- Venues & Directions
- Campus Athletics
- GO Beyond: The Campaign for Future Makers
- Ways to Give
- Students, Faculty & Staff
The Center for Catastrophe Modeling and Resilience was recently named a University Research Center. Illustration by Ana Kova.
Lehigh's First University Research Center to Focus on Catastrophe Modeling
The first of three new University Research Centers, The Center for Catastrophe Modeling and Resilience aims to explore how hurricanes, pandemics and other large-scale events impact communities.
Christina Tatu
- University Research Center
- Interdisciplinary Research
In 2005, Hurricane Katrina caused catastrophic flooding in Louisiana, killing more than 1,800 people and leading to $108 billion in property damage, including the destruction of fiber optic cables and microwave antennas essential for transmitting and receiving signals for cellular, radio and television broadcasts.
In 2017, Hurricane Harvey slammed into the Texas coast, killing more than 70 people and damaging more than 850 power transmission structures and more than 745 miles of transmission and distribution conductors. More than 200,000 people, including many in the Houston area, were without power for days.

Authorities rescue those stranded during Hurricane Katrina which made landfall as a category four hurricane along the Gulf Coast of Louisiana in 2005.
In 2018, a massive wildfire in Northern California, ignited by a fault in a power line and fueled by strong winds, burned through more than 153,000 acres, destroyed 18,804 buildings and killed 85 people. The Camp Fire was California’s deadliest wildfire to date.
What these disasters have in common is that they force a closer examination of the resilience of the country’s infrastructure and utility systems. As such disasters become more frequent, they raise questions about what can be done to ensure communities can withstand catastrophes and quickly rebuild.
Catastrophe modeling and resilience, the focus of Lehigh’s first University Research Center—announced earlier this year as part of Lehigh’s strategic plan, Inspiring the Future Makers —attempts to assess the risk of these kinds of events and plan for them.
The Center for Catastrophe Modeling and Resilience , led by Paolo Bocchini , professor of civil and environmental engineering, brings together a team of faculty from across disciplines, leveraging a wealth of experience and expertise in their respective fields who attempt to predict catastrophes and assess their associated risks.
Lehigh has had teams of researchers studying disaster resilience for years. Over time, they have developed relationships with collaborators in government, industry and academia and secured funding for a variety of projects.
“We at Lehigh created an area of strength in community and infrastructure resilience,” Bocchini said. “We started about 15 years ago to work on this. We have reached critical mass, and I think we’ve established ourselves as relevant players in the field.”
Lehigh’s leaders hope the University Research Center designation and investment will help Bocchini and his team secure more research funding to expand efforts and crystallize Lehigh’s status as a leader in the field of catastrophe modeling and resilience.
“The goal of these centers is to achieve national and international prominence in a specific area of work so that when people who are interested in a particular topic ask, ‘Where is the best or most interesting research being done on the issue,’ Lehigh comes to mind as a great place where that work is being done,” said Dominic Packer, associate vice provost for research.
The goal of these centers is to achieve national and international prominence in a specific area of work so that when people [...]ask, 'Where is the best or most interesting research being done on the issue,' Lehigh comes to mind as a great place where that work is being done.
Dominic Packer, Associate Vice Provost for Reserach
The Center for Catastrophe Modeling and Resilience will also help advance Lehigh’s goal of doubling its research over the next 10 years.
Being named a University Research Center means that the Lehigh faculty involved will invest at least 50% of their research efforts there, Packer said. For some faculty, all of their research could revolve around the center. The backing also will make Lehigh’s researchers more competitive with other institutions vying for large-scale funding. Such grants often require interdisciplinarity with a strong sense of institutional commitment, Packer said.
Several projects have already been carried out or are underway .
Research led by Bocchini explores wildfire risk assessment . Under strong wind and dry weather, California power companies can enact public safety power shutoffs, but the shutoffs cause blackouts affecting millions of people. Bocchini’s team has explored ignition probability, which is increased when conductor cables oscillate in such a way that they encroach on surrounding vegetation. Bocchini’s research provided a methodology for predicting at what point during a high wind storm powerline ignition becomes likely.

In May 2014, San Diego County was hit with unprecedented wildfires fueled by drought.
Ethan Yang , associate professor of civil and environmental engineering, is collaborating with Florida Atlantic University, and the University of Tokyo and Kyoto University, both in Japan, to develop an inclusive human-centered methodology comparing similarities and differences in how the United States and Japan deal with disasters and mitigate them. Funded by the National Science Foundation, the project will mainly look at flooding, which often causes the most extensive damage to communities, Yang said.
David Casagrande , an anthropology professor, is studying U.S. Census data from 2000 and 2010 to examine how neighborhoods in New Orleans changed as a result of Hurricane Katrina in 2005. The data helps illustrate “social vulnerability,” that is, which members of a population may be more vulnerable and have less resilience to recover after a disaster, he said. That could be influenced by factors such as race, age, income and whether the person is a homeowner or renter.
“You can’t just treat the population as homogenous if you really want to understand,” said Casagrande, who is assisted by a graduate researcher. “You have pockets of poverty, and other issues that are going to affect a community’s ability to recover after a disaster.”
The catastrophe modeling team was a clear frontrunner among proposals for the designation as a University Research Center because, in addition to their exciting work, they were among the most established teams to submit a proposal, Packer said.
“Paolo is very impressive as a leader and he has a vision, and he and his team have been working toward this for quite a few years now,” he said. “This is not something that happened overnight. They’ve really been working toward creating a center-like structure.”
What is Catastrophe Modeling?
Catastrophe Modeling, or CatModeling, attempts to predict the likelihood of potentially catastrophic events, such as natural disasters, pandemics, financial crises, as well as political unrest and the associated risks that include financial losses, damage to buildings and other infrastructure.
CatModeling is particularly important for insurance companies who often cover the cost of disasters. The speed with which insurers can make payments can impact the long-term recovery of a region. Despite the importance of CatModeling, the field has not previously been treated as a traditional discipline explored systematically in academia.
While the private sector has moved forward research in CatModeling, it can benefit from stronger collaborations with the fundamental and interdisciplinary research done in academia, Bocchini says. The Center for Catastrophe Modeling and Resilience envisions a thriving University Research Center that expands the role of academia in CatModeling and interacts with major stakeholders in industry, government and researchers at other universities to address the most relevant problems in the field.
Some of these problems are related to the influence of climate change on catmodels, rapid response and recovery after disasters, as well as climate, environmental and social justice applied to disaster resilience.
Resilience refers to a community’s ability to withstand and recover from a disaster. The role insurance companies play in resilience is critical, Bocchini said.
“Insurance companies are really fueling the recovery effort,” he said. “Making sure that they are still in the black after these events, and they can provide resources, is important. In the past, we had examples where some insurance companies went bankrupt before catastrophe modeling became a science.”
Center researchers have decided to continue their efforts from a public sector perspective, but also add new focus on the private sector, specifically the insurance industry, he said.
Bocchini’s background is in probabilistic modeling applied to civil engineering. Since his early research years, Bocchini has applied probabilistic modeling to natural disasters.
“I saw students get immediately excited when I pitched this type of application, because we are dealing with the biggest threats to our society,” Bocchini said. He and his colleagues realized such models could be applied to other events as well. They began trying to predict epidemics before the COVID pandemic hit.

A worker sanitizes a theater in New Delhi, India, on Oct. 14, 2020.
I saw students get immediately excited when I pitched this type of application, because we are dealing with the biggest threats to our society.
Paolo Bocchini, Associate Professor of Civil and Environmental Engineering
“These are measures of threats our society faces, and in some cases they are existential threats,” Bocchini said. “Trying to do something about it, for me as an engineer, is very fascinating. I’m not trying to cure diseases, but I think this is the best approximation of trying to help our society defend against its threats.”
An Interdisciplinary Team
The catastrophe modeling group at Lehigh have also catalyzed a broader catastrophe modeling coordination network, for which Lehigh’s University Research Center will serve as hub. It includes founding members from Rice University in Houston, Stanford University in Palo Alto and Florida Atlantic University in Boca Raton. There are additional members from Washington State, Missouri University of Science and Technology and Columbia University in New York.
Lehigh currently has eight core faculty members involved in the center from across various disciplines, including engineering, mathematics, science and social sciences. They include Bocchini, Casagrande and Yang, as well as:
– Daniel Conus , associate professor and associate chair of the Department of Mathematics – Brian Davison , professor and chair of the Department of Computer Science and Engineering – Benjamin Felzer , associate professor of Earth and environmental sciences – Thomas McAndrew , assistant professor with the College of Health – Maryam Rahnemoonfar , an associate professor with the Department of Computer Science and Engineering, and the Department of Civil and Environmental Engineering
Bocchini hopes to at least double the number of center-affiliated researchers in the next few years. The center is also in the process of hiring an industry liaison to work with those in the insurance sector. A master’s degree program in catastrophe modeling and resilience has been introduced along with a certificate program. The first students in those programs are starting in the Fall 2024 semester.
“This problem requires multiple kinds of expertise to answer it well,” said Davison, who is also one of the founding members of the center.
“The insurance industry and finance industry have their areas of expertise, but they might not know how to plan for and repair certain kinds of infrastructure,” Davison said. “I would argue it’s necessary for catastrophe modeling to be interdisciplinary because we’re going to miss something pretty significant if we are not considering the human aspects.”
[...] It's necessary for catastrophic modeling to be interdisciplinary because otherwise we're going to miss something pretty significant if we are not considering the human aspects.
Brian Davison, Professor and Chair of the Department of Computer Science and Engineering
Davison and his colleagues at the center say they are in a unique position to bring government and private industry together.
Yang said government agencies have their attention divided by issues such as inflation and housing prices, while the insurance companies are for-profit corporations and need to worry about their finances and their competitive edge. Those in academia don’t have such constraints.“We are in a good spot and can serve as a neutral venue that brings everyone together,” he said.
Lehigh Launches its University Research Centers
The development of University Research Centers marks an important milestone in Lehigh’s strategic plan to invest in interdisciplinary research. University leaders have been seeking and developing ideas for the formation of research centers. The goal is to create multiple centers of national and international prominence in the next five to 10 years.
The process began with the strategic planning effort during fall 2022 when the “Research for Impact” working group solicited creative ideas from across campus, which helped inform and create the notion of interdisciplinary research centers in three areas: assessing and improving health by working outside of healthcare settings; interdisciplinary research and creative work to understand conflict and change; innovation for sustainable and resilient infrastructure and communities.
In August 2023, university leaders solicited proposals for University Research Centers. They received 17 letters of intent and 12 white papers, each of which presented ideas with potential for further development.
Each proposal was reviewed by experts, including Lehigh faculty, staff, deans, content experts from academia and industry, and experts in federal research priorities. Lehigh hopes to designate more University Research Centers in the near future, including in the areas of assessing and improving health by working outside of healthcare settings, and interdisciplinary research and creative work to understand conflict and change.
“We identified a set of themes, areas where it seems like we have existing strengths and it would be good to grow,” Packer said.
A location for the Center for Catastrophe Modeling and Resilience is still being determined, though Packer believes it will most likely be on the Mountaintop Campus.
“I think our perspective is that this is a really important and exciting area of research that is only going to grow in importance,” Packer said.
Related Stories

Nursing Home Industry May Obscure Some of its Profits, Lehigh Researcher Finds
Andrew Olenski, assistant professor of economics, publishes finding in a National Bureau of Economic Research working paper.

Research Promotes Equitable Reclassification for Multilingual Learners with Disabilities
Sara Kangas, associate professor of special education, presents policy brief to special education state agency leaders from across the U.S.

Lehigh’s Center for Catastrophe Modeling and Resilience Receives NSF Planning Grant to Pursue Industry-University Cooperative Research Center
Grant will strengthen Lehigh’s Center for Catastrophe Modeling and Resilience as a nationally recognized research center.

IMAGES
VIDEO
COMMENTS
Penn State's Research Security Program. Below are the components of Penn State's research security program, which is an interdisciplinary collaborative effort among various offices at the University. This program is a central point of contact for research security at Penn State. Please email [email protected] with any questions.
Research Security Program Requirements. Institutions receiving > $50 million/year in federal science & engineering support must establish a research security program. Required Elements: Cybersecurity. Foreign Travel Security. Research Security Training (insider threat awareness & identification) Export Control Training (as appropriate) Program ...
Purdue University's research security program is designed to protect intellectual capital, prevent research misappropriation, and ensure responsible management of U.S. taxpayer dollars while maintaining an open environment to foster research discoveries and innovation. The program promotes transparency, addresses conflicts of interest and ...
The Research Security Program is a collaboration between many university-wide departments based on campus policies and federal regulations. The Director of Research Security, reporting to the Vice-President for Research, serves as the university's research security program's point of contact. This website has been developed to (1) provide ...
A Research Security Program is required by the federal government to protect against foreign government interference and exploitation at research institutions receiving federal funds. National Security Presidential Memorandum 33 (NSPM-33) is an executive branch directive intended to safeguard the security and integrity of federally funded ...
Research security has emerged as a top priority for US institutions receiving sponsored project funds from federal sponsors. The NSPM-33 Implementation Guidance, released in January 2022, requires any institution receiving over $50 million in federal research funding to establish a Research Security Program touching on four main areas of focus: research security training, cybersecurity ...
Foreign travel security; Research security training; Export control training; The federal agencies will apply NSPM-33 requirements to all research universities that receive an excess of 50 million dollars per year in federal research funding. Cornell University fits this criterion and as such is required to implement a research security program.
The Research Security Program guidance is a set of requirements and best practices for institutions that have received at least $50 million per year in Federal science and engineering support to establish and maintain effective research security programs. The guidance covers the following areas: Overarching Research Security Program
Research Security Program. Stanford is committed to ensuring the security and integrity of the research ecosystem and complying with federal requirements including the requirement to establish an institutional Research Security Program as described in National Security Presidential Memorandum 33 (NSPM-33). The office of the Vice Provost and ...
The University of Houston is required to have a research security program because it receives more than $50 million in annual federal research funding. The research security program is jointly administered by the Office of Research Integrity and Oversight (RIO) and the Office of Contracts and Grants (OCG).
The university will develop a formal research security training program based on agency guidance and existing export control training requirements will continue and may be modified or expanded as needed. Resources: NSPM-33 Implementation Guidance. Clear Rules for Research Security and Researcher Responsibility. NSPM-33
Research Security Programs. To strengthen research security programs, SRS has worked to clarify and further specify the requirements detailed in the NSPM-33 implementation guidance, as well as the ...
As one of the nation's leading research universities, the University of Rochester is expanding its research security program to align with these requirements. The effort is aimed at upholding safety and security in our research endeavors while continuing to foster the open global exchange of ideas. In the coming months, the University's ...
The Research Security Program helps researchers safeguard their research and innovation in both the short and long-term. Having a strong research security program helps UW-Madison maintain its excellence in cutting-edge research and innovation on the world stage by fostering international collaborations essential to solving complex issues.
Academic Integrity and Undue Foreign Interference from Stanford University. Research Security Program from Stony Brook University. Research Security Office from the Texas A&M University System. Research Security Governance Board from The Ohio State University. Ethics, Compliance and Audit Services from the University of California.
In the next 12-18 months, guidance, policies and procedures will again be updated to achieve compliance with agency implementations for disclosure and the use of digital persistent identifiers. In addition, an institutional research security program will be developed to address requirements related to: 1) cybersecurity, 2) foreign travel ...
Research security has emerged as a top priority for U.S. institutions receiving sponsored project funds from federal sponsors. National Security Presidential Memorandum 33 (NSPM-33) on National Security Strategy for United States Government-Supported Research and Development was released in January 2021 with the goal of securing federally ...
Heads of funding agencies shall require that research institutions receiving Federal science and engineering support in excess of 50 million dollars per year certify to the funding agency that the institution has established and operates a research security program. Institutional research security programs should include elements of cyber ...
NSF. NSF is committed to safeguarding the integrity and security of science while also keeping fundamental research open and collaborative. The agency seeks to address an age of new threats and challenges through close work with partners in academia, law enforcement, intelligence and other federal agencies. By fostering transparency, disclosure ...
Short Description: For information relevant to research security programs, see pp. 25-26. AAU, APLU, COGR - University Actions to Address Concerns about Security Threats and Undue Foreign Government Influence on Campus (May 2020) Document Short Description: For information relevant to research security programs, see pp. 2-5.
Research security program requirements include the research security training requirement described in Sec. 10634 of P.L. 117-167, commonly known as the CHIPS and Science Act. Establishing a research
Research Security Training: The Importance of Research Security, The University of Alabama in Huntsville. The team will develop research security training that provides information and insights about best practices in designing, developing and evaluating educational tools for the adult learner.
In a first-of-its-kind national workshop, The University of Houston, Rice University, IPTalons and the Society of Research Administrators International, hope to shape the future laws, policies and guidelines that will enhance research security. ... On July 12, 2023, the NSF launched its Research on Research Security Program ...
Academic Research Security. The Department of Defense greatly values its partnership with the academic community. Of paramount importance to the integrity and effectiveness of the academic research community has been the open, transparent, and merit-based nature of research collaborations. In recent years the Department, along with other ...
The forthcoming Research Security Program Standards will not change the underlying practical requirements already written into the NSPM-33 and encoded into law by the passage of the CHIPS and Science Act: Every research university should implement a formal research security program, led by a professional research security officer, to identify ...
The George Washington University is committed to enhancing the global reach of our research and therefore supports and encourages international collaborations, interdisciplinary research, and the global exchange of ideas. GW values our partnerships with universities and organizations worldwide and appreciates the value these collaborations have ...
Rebecca Keiser, the National Science Foundation's (NSF) chief of research security strategy and policy (CORSSP), will deliver a virtual keynote address May 23 on the origins of the foundation's research on research security (RoRS) program with Rice University's Baker Institute for Public Policy.. The keynote address will kick off an invite-only, first-of-its-kind global workshop to ...
If you have any questions regarding the below, please contact Torrey Truszkowski, Assistant Director, Research Security and Export Control at [email protected] . "A malign foreign talent recruitment program is: (A) any program, position, or activity that includes compensation in the form of cash, in-kind compensation, including ...
Fang came to UCF in 2020 from the Ohio State University. Since arriving, she has garnered significant funding and support for her projects. In 2020, Fang was one of 76 recipients - and the only recipient from Florida - to be awarded an early career research program grant from the U.S. Department of Energy.
The first of three new University Research Centers, The Center for Catastrophe Modeling and Resilience aims to explore how hurricanes, pandemics and other large-scale events impact communities. In 2005, Hurricane Katrina caused catastrophic flooding in Louisiana, killing more than 1,800 people and leading to $108 billion in property damage ...