Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 30 August 2023

A Huffman code LSB based image steganography technique using multi-level encryption and achromatic component of an image
- Shahid Rahman 1 ,
- Jamal Uddin 1 ,
- Hameed Hussain 2 ,
- Aftab Ahmed 3 ,
- Ayaz Ali Khan 4 ,
- Muhammad Zakarya 3 , 5 ,
- Afzal Rahman 2 &
- Muhammad Haleem 6
Scientific Reports volume 13 , Article number: 14183 ( 2023 ) Cite this article
2207 Accesses
1 Citations
Metrics details
- Data processing
- Image processing
In the recent couple of years, due to the accelerated popularity of the internet, various organizations such as government offices, military, private companies, etc. use different transferring methods for exchanging their information. The Internet has various benefits and some demerits, but the primary bad mark is security of information transmission over an unreliable network, and widely uses of images. So, Steganography is the state of the art of implanting a message in the cover objects, that nobody can suspect or identify it. Therefore, in the field of cover steganography, it is very critical to track down a mechanism for concealing data by utilizing different blends of compression strategies. Amplifying the payload limit, and robustness, and working on the visual quality are the vital factors of this research to make a reliable mechanism. Different cover steganography research strategies have been recommended, and each adores its benefits and impediments but there is a need to foster some better cover steganography implements to accomplish dependability between the essential model of cover steganography. To handle these issues, in this paper we proposed a method in view of Huffman code, Least Significant Bits (LSB) based cover steganography utilizing Multi-Level Encryption (MLE) and colorless part (HC-LSBIS-MLE-AC) of the picture. It also used different substitution and flicking concepts, MLE, Magic matrix, and achromatic concepts for proving the proficiency, and significance of the method. The algorithm was also statistically investigated based on some Statistical Assessment Metrics (SAM) such as Mean Square Error (MSE), Peak Signal Noise Ratio (PSNR), Normalized Cross Correlation (NCC), Structural Similarity Index Metric (SSIM), etc. and different perspectives. The observational outcomes show the likelihood of the proposed algorithm and the capacity to give unwavering quality between security, payload, perception, computation, and temper protection.
Similar content being viewed by others
A vision chip with complementary pathways for open-world sensing
Low-latency automotive vision with event cameras
Radiative cooling and indoor light management enabled by a transparent and self-cleaning polymer-based metamaterial
Introduction.
For data transmission, the Internet has become an excellent system, due to its accelerated popularity, inexpensiveness, and efficiency of it 1 . Therefore, for sharing information in digital form over the Internet, one file image is widely used and becomes very easy to send over the Internet 2 . In addition, it is very easy to copy or modify the transmitted data over the internet by unauthorized persons or attackers. There are various identified tools available to make the exploitation of secret information, security, privacy, etc. being transmitted and also to make the possibility of different vulnerabilities, attacks, and hateful threats such are scaling, cropping, tempering, spoofing, phishing, eavesdropping, privilege escalation, clickjacking, social engineering, bot, backdoor, viruses, botnet, malware and many more 3 , 4 .To deal with secure correspondence over the Internet, various techniques are proposed in the recent couple of years but each has related pros and cons. Thus, to satisfy the requirement for secure correspondence, it is important to make superior ways of making a safe framework to satisfy the requirement for transmission over the web between users. However, the ancient method used for secure communication in order to provide a safe way of transferring data over the internet is Encryption 5 , 6 , 7 . It converts normal text means plain text to cipher text using some keys. So, encryption is a way of converting plain text into cipher text within any cover media used for encryption, that there is no clue of the existing data and no one can suspect the encrypted information. Furthermore, the recipient might involve a mystery key for encryption and just the key supervisors can unscramble the mystery message utilizing the key which is to be given by the source. Using the encryption concepts there are some multimedia information mediums used such are image, text, audio, video, network, etc. 8 .
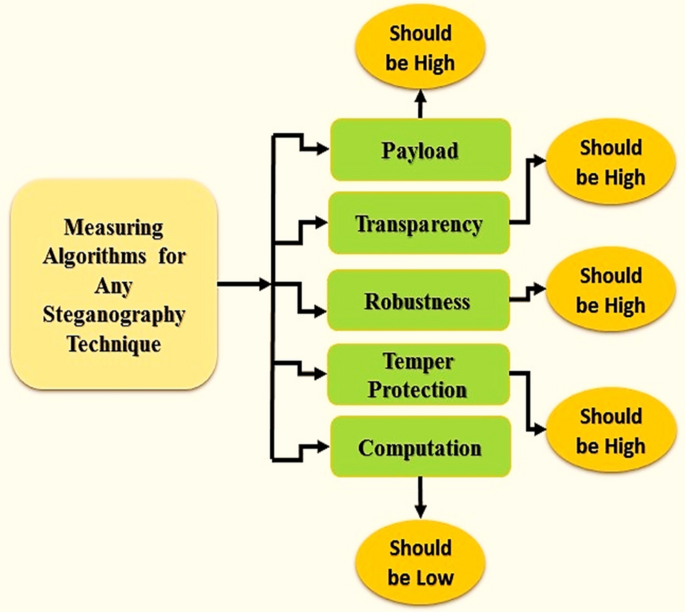
Therefore, the main idea of encryption is the notion of steganography which hides secret information within the cover objects without knowing the existence of the information within it. Steganography is the part of data concealing that encodes the mystery message that nobody can identify it. Image steganography shows an essential part of protected communication in this digital world because one file type that is rapidly used is the image 9 . Furthermore, image steganography uses an image as a cover object and inserts the secret information using different reported methods such as spatial domain, frequency domains, etc. The extensive surveys of image steganography are presented in various works as described later in “ Summary of the related works ” 10 , 11 , 12 , 13 , 14 . Every existing method has its own advantages and disadvantages in terms of payload, security, perception, temper protection, and computation which are the basic criteria of steganography, as well as, the basic needs for any steganographic methods as shown in Fig. 1 6 .
The need for image steganography techniques.
Though, we have proposed an improved and novel technique based on Multi-Level Encryption (MLE), an achromatic component of an image, and Huffman LSB. The proposed method also used some transposition, and magic matrix concepts to expand the significance and inspiration of the proposed technique. For embedding the secret message, the proposed algorithm used the Huffman coding priority concept and made the Huffman encrypted sequences, and then embedded them into the cover media. After making the Huffman encrypted sequences, different encrypted operations applied to it made the method outperform others. This is because the proposed algorithm used an embedded procedure of the cover data within the image in a manner that if anyone suspects the stego image or extracts the message, then they will not extract the encoded message version. Only the holders of the Huffman table or tree can regain the secret message correctly because the communication is between the two parties. Therefore, the proposed research work has a novel and improved contribution in terms of security, transparency, payload, and temper protection in order to make it significant. Some main objectives and contributions of the said method are given as follows.
A proposed technique that uses the Huffman coder priority for encrypting the secret message and the result is the form of Huffman encrypted sequences to improve the reliability between basic criteria such as temper protection and security.
Achromatic components of an image Hue Saturation Intensity (HSI) variety model are utilized rather than the RGB pictures variety model to decrease the handling time and increment the security.
For making deciphering the mystery message testing, and thought-provoking, the proposed method divided the I channel or plane (I-Plane) into four equal blocks and shuffled the blocks using Magic Matrix, and the method also used MLE for giving the tough time to attackers and to increase the security.
The proposed strategy was fundamentally dissected in the opinion of various key view-points (i.e. different sizes of images with different sizes of text, different images with the same text size, and different format images) to work on the proficiency and viability of the scheme.
In sum-up, the basic criterion of cover steganography is presented in Fig. 1 , which elaborates the payload maximum amount of furtive data to be implanted within the cover object. Transparency shows the quality of the image. Furthermore, robustness spectacles the retreat of the stego image, that the stego object is undamaged after embedding even if attacked. shows the opposition against various assaults of the cover object. While computation explains the time intricacy of the implanting system into the cover object 15 . The rest of the paper is organized into various sub-sections as follows. Section 2 elaborates on the abstract details of the related reported research works. Section 3 explains the proposed methodology and algorithms. Sections 4 describes experimental parameters and obtained results. Finally, Sect. 5 concludes this work along with directions for future work.
Summary of the related works
For secure communication between sender and receiver in this digital world over the internet, cover steganography plays a vital role and flourishing research area. For digital steganography, many research works have been proposed over the last decades such as LSB, pixel value differencing, randomization, cyclic, etc. and each has their related pros and cons. Notably, for inserting the mystery message inside the cover media the most well-known and habitually utilized strategy is the LSB technique 5 . The wide use of this technique is due to its simplicity and straightforwardness. Therefore, this section elaborates on the basic concepts of RGB and HSI color model, Least Significant Bit (LSB), and critical analysis of some methods presented in the literature 16 . However, how about we make sense of RGB and HSI variety models; one of the main parts of any item is its tone.
The utilization of variety in picture handling is persuaded by standard two aspects.
From a scene, that often streamlines object identification and abstraction, a color is a powerful descriptor.
Contrasted with about just too many shades of gray the people can discern thousands of color shades and intensities.
The second is predominantly significant in physical image analysis (i.e. when performed by people). The purpose of a color model or color system is to facilitate the specification of colors in some standard, and generally accepted way when working in image processing because it is the main part of it. Each color tone is addressed by a solitary point because color mode is a description of a coordinate system and subspace within that system. In practice most commonly used color models; Red, Green, Blue (RGB) model used for monitors and a broad class of color video cameras because it is the hardware-oriented models in terms of digital image processing. For printing the second color model used is Cyan, Magenta, Yellow and Black (CMYK), Cyan, Magenta, Yellow (CMY). To correspond closely with the way humans, describe and interpret color, the third color model Hue, Saturation, Intensity (HSI) is used. So, the main focus of this study is the HSI model. In HSI color Model, changing from one model to the other is an open process while creating colors in the RGB and CMY models 17 . For hardware implementations, this ideally suited this color system. The RGB framework coordinates pleasantly with the way that the natural eye is firmly viewpoint to red, green, and blue primaries. Yet, the RGB, CMY, and other comparable variety models are not appropriate for depicting colors in wording that are pragmatic for human translation.
For instance, one doesn't allude to the shade of color by giving the level of every one of the primaries creating its tone. Besides, we don't consider a variety of pictures as being made out of three essential pictures that join to frame that solitary picture 18 . So, we describe by its hue, saturation, and brightness, when humans view a color object. Hue is a color aspect that defines a clean color (i.e. Yellow, red, and orange), while saturation gives a measure of the degree to which a pure color is diluted by a white light. Whereas intensity is a particular descriptor that is basically difficult to gauge. It is one of the key aspects in describing the color sensation, and it also exemplifies the colorless thought of intensity. This quantity absolutely is measurable and simply interpretable because it is the utmost convenient descriptor of monochromatic images. In a color image, the HSI model decouples the intensity component from the color-carrying information (hue and saturation). Based on color descriptions HSI color model is an ideal tool for developing image processing algorithms because they are naturally intuitive to humans. For color generation, we can say that RGB is an ideal tool, but for color description, it is significantly more restricted. Hereafter, from the RGB image, we should be capable to excerpt intensity 19 , 20 . So, the HSI color model plays a vital role in secret information camouflage because the Intensity plane (I Plane) does not grieve the other planes, unique RGB diverts in which all planes are unequivocally co-related with one another. Besides, handling an image in the HSI model is somewhat more economical based on LSB-based techniques, etc. due to its unique properties. So, LSB is the process of embedding the secret message into cover image pixels of LSBs either randomly or sequentially shown in Fig. 2 3 , 9 , 21 . The given figure explores the concept of LSB by taking the cover image converting it into its corresponding American Standard Code Information Interchange (ASCII) values then converting it into binary values 22 . After reading the image pixels’ values and their binary forms it converts the secret message values to binary form 23 . Furthermore, it is the procedure of implanting secret data bit K replaced with cover image pixels K LSB. Equation ( 1 ) represents the embedding process.
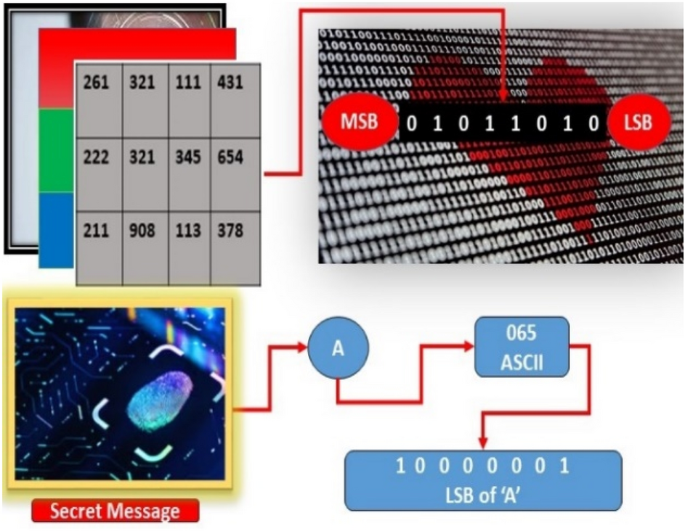
The basic concept of least significant bit (LSB).
Where SIM (i, j) presents the stego image i, where j represents row and column, CI is the cover image, and SM secret message. Different LSB-based methods are proposed recently but they still have issues to improve this research area. The human eye is very naked and has the properties to detect or suspect little change in any smooth area of the images 24 . So, encrypting the secret message with the image either randomly or sequentially, and not all pixel values are used for embedding so the change may be happening on only the embedding area of the image. Therefore, various image steganographic reported works are adapted to embed a suitable amount of message in appropriate cover objects 25 .
Lee et al. recommended a high implanting message-based image steganography where they embedded 12 KB of cover information inside the cover image and the technique focused only on the payload 26 . Zang and Wang et al. introduced proficient steganographic inserting by taking advantage of the alteration course. The author focused on embedding more messages and also try to get security 27 .
Khan et al. offered a cyclic image-based steganography method using randomization. In this paper, authors struggled to get consistency among the basic criteria and embedded 4 to 8 KB secret messages. Karim suggested a new image steganography technique in light of LSB using a secret key and achieving the security, payload but broke down the other criteria 28 . Muhammad and Sajjad proposed and magic LSB method using multi-level encryption and HSI image. It is a better technique in image steganography but has some limitations to different attacks such as scaling, noising, cropping, etc. 29 .
Rustad et al. developed a novel image steganography for improving the perceptual transparency of the image. It is an inverted LSB method using an adaptive pattern. This research achieved a high-quality stego image but the payload limit is too low 30 .
Cheng and Huang proposed a novel method of reversible encrypted image-based steganography using interpolation image and histogram shifting. In this study, the author used double scrambles operation on the pixel of the image by changing the positions of the pixels. The experimental results achieved a high embedding capacity and security 31 .
Shwe Sin et al. presents an LSB and Huffman code-based steganography. The investigational outcomes presented that the algorithm got high embedding capacity and better security 32 .
Tsai et al. presented another LSB-based image steganography algorithm in light of MSB prediction and the Huffman base method. The main objectives of the paper are high payload and secrecy and to increase the inserting pace of the mystery message inside the cover picture 33 .
M. Shahu et al. presented a novel technique, LBP-based reversible information stowing away effectively accomplishes better HC, SI quality, and strength to different assaults. Be that as it may, besides these benefits, the proposed method can be improved concerning HC. Since the proposed work utilizes the LBP-based strategy, subsequently, it considers the surface and smooth pictures as unclear while embedding the EBs. Regardless, the pixel power of surface pictures makes it more sensible to introduce more EBs when appeared differently in relation to smooth pictures. Thusly, the proposed work can be contacted to achieve higher HC in surface pictures by brushing LBP with the PVDS-based technique 34 .
Dhivya et al. proposed a proficient variable bit information embedding method founded on combined chaotic system (CCS) and integer wavelet transform (IWT). With the plan to boost the security level, CCS is created by joining chaotic maps of two 1D. The developed combined tent-logistic (CTL), combined sine-logistic (CSL) and combined sine-tent (CST) maps with improved chaotic behavior are utilized to generate the key sequences. From CTL, CSL and CS, these chaotic key sequences are then quantized to embed the secret bits in high-high, high-low and low–high sub-bands of the IWT transformed cover image, respectively. The fundamental benefit of this plan is that the number of bits to be implanted in every single sub-band coefficient is profoundly chaotic and very delicate to the underlying seeds 35 .
Ramapriya et al. proposed a clinical picture steganography technique by taking advantage of Double Tree-Complex Wavelet Change based change and picture encryption system. Then a better SSOA enhancement calculation is locked in to distinguish smooth edge blocks. Subsequently, the determination of pixels for inserting is worked with. Installing the Restricted information into the cover picture is then done utilizing a twofold network XOR encoding. After the inserting system, the stego picture is created. Subsequently, the proposed strategy shows the best outcomes with high pay load limit, security, and picture quality than the current techniques. Testing was performed on PSNR, MSE, IF, and SSIM measurements to confirm the presentation of the proposed techniques 36 .
Sahu et al. proposed a better method for two delicate watermarking plans to perform altering recognition and limitation in a picture. The proposed plans were outwardly disabled and the watermark pieces were created using the turbulent system-based determined map at both the source and getting end. Further, the chief contrives saw a constraint of ± 1 contrast between the host and watermarked pixels. As such, the idea of the watermarked picture was far superior to that of various plans. Finally, surprising results were achieved in regard to the adjusted area and limitation limit of the proposed plans. Later on, the proposed work can be connected with self-recovery of the modified pieces, and growing both spatial and change spaces to extra overhaul the force. There are different reported works presented in the literature based on image steganography, and each method has its related advantages and disadvantages depending on its embedding procedures and selection of the cover object 36 . Moreover, every examination work has attempted to cover the rudiments standards of picture steganography such are payload, strength, discernment, temper insurance, and computation. Some examination of existing techniques is introduced in Table 1 .
In sum-up, Table 1 illustrated the analysis of the diverse existing methods using the basic criterion of steganography. It also expounded the techniques used, pros and cons, main focus, embedding procedure, and limitations of each method. Though, after a detailed analysis of the existing methods many points come to mind, but some point is very vital; one is selecting an appropriate cover object and the second is the reliability between the essential criterion of steganography. Because some tried for making a reliable method but get one or two parameters but broke down the other criteria and also the reliability between the criterion which is an essential part of steganography. However, to tackle these vital needs, the proposed algorithm is designed in a manner that shows which dimension of the image is better for which size of secret message and also to make a reliable method. However, the detailed whole process of the proposed algorithm is presented in the next section.
The proposed algorithms
This section presents the whole process of the proposed algorithm, embedding and extraction process, Magic matrix, MLEA, Huffman encryption, and extraction process shown in Fig. 3 . The mathematical notations which are used throughout the paper are presented in Table 2 .
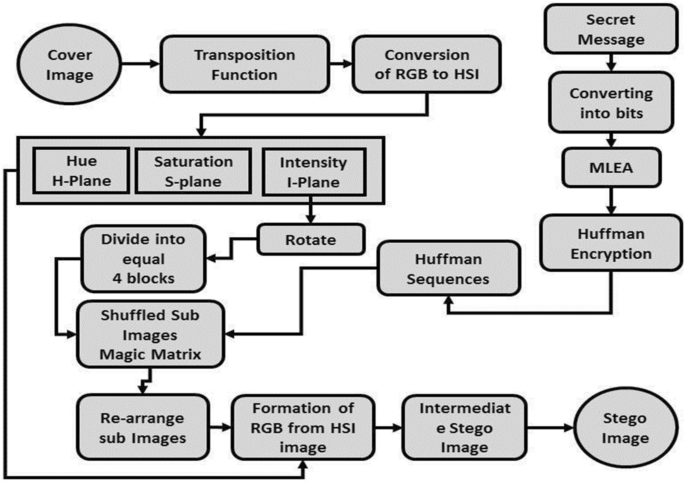
The process of encrypted algorithm used in the proposed method.
The step-by-step procedures of embedding, the extraction process, MLEA, Magic Matrix (MgMtx), and Huffman code algorithms are presented given in Algorithms 2, 3, 4, and 5 respectively. The proposed algorithm used two stages in which first we encrypt the mystery message using Huffman code priority. For mapping the one secret word to one code word the optimal codes are Huffman code mapping. Since Huffman designates a parallel worth or code to each brightness of the cover picture. For applying the Huffman code, first, we convert the 2D image with size C × R to 1D array bits’ stream with length of LHuff fewer than or equal to C × R (LHuff ≤ C × R). The given bit’s stream is used for building the Huffman table or sequences HFCS because extracting the original message bits’ stream is totally dependent on the same Huffman building table bits’ stream. To lessen the size of the cover picture performs lossless pressure of the Huffman inserting is utilized. After the size of that image is reduced because Huffman encrypts shrinkages the image size. In the context of embedding, Huffman encrypted bit stream cannot reveal or show the message bits of the cover image or anything about it. Huffman is one type of verification because the secret message bit stream is only extracted using the same Huffman table or sequences which are used for embedding. If a little bit of error occurs the Huffman table or sequences can’t extract and is unable to recover the secret message. The proposed method used MLEA, Magic Matrix, and Huffman code-based encryption to prove the efficiency, effectiveness, and dominancy of the proposed. Let’s first elaborate on numerous important concepts which are used in the proposed algorithm.
The Multi-Level Encryption (MLE) is used for the proposed algorithm having different encryption operations to improve the security and give hardness to the attackers 49 , 53 . It is used on secret data before embedding to the cover object or image for increasing security using some XOR operation to make the message unrecoverable for any assailants. While Magic matrix is used to make a matrix having no repeated numbers and the summation of that matrix either each row, each column, and both diagonals are remaining the same. It can be used for applying different operations on secret data or cover images due to its properties in terms of improving security and also giving the hard-hitting time to attackers shown in Figs. 4 , 5 , 6 , 7 and 8 sequentially 47 , 48 , 54 . Let’s try to elaborate with the help of the example given below.
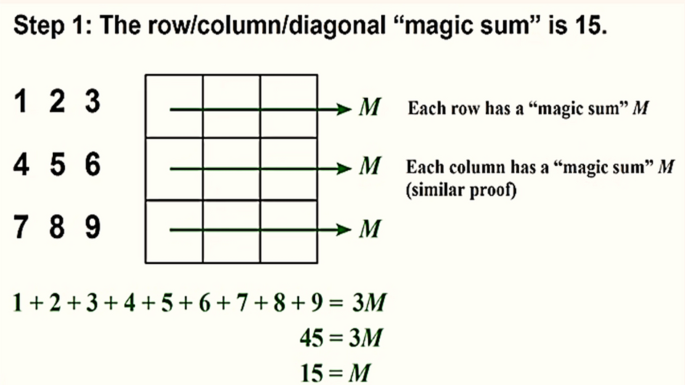
An example of the magic matrix (Steps: 1 & 2).
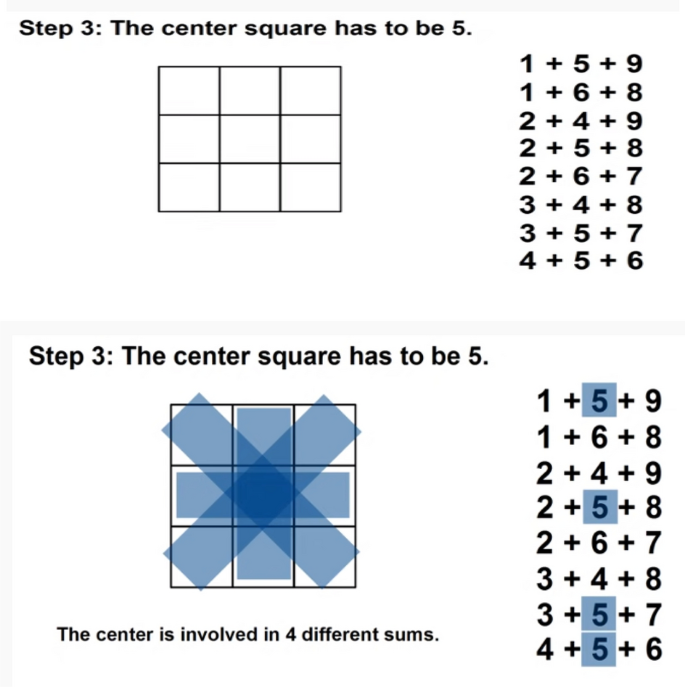
An example of the magic matrix example (Step: 3).
An example of the magic matrix example (Steps: 4a & 4b).
An example of the magic matrix example (Step: 5).
An example of the magic matrix example (Step: 6).
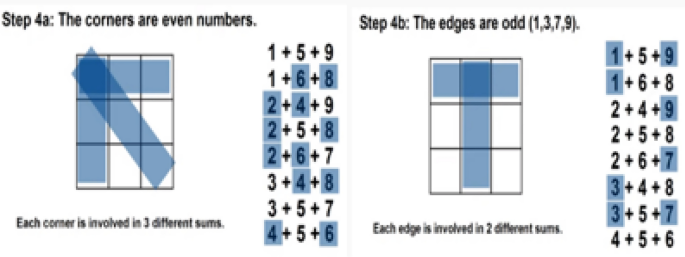
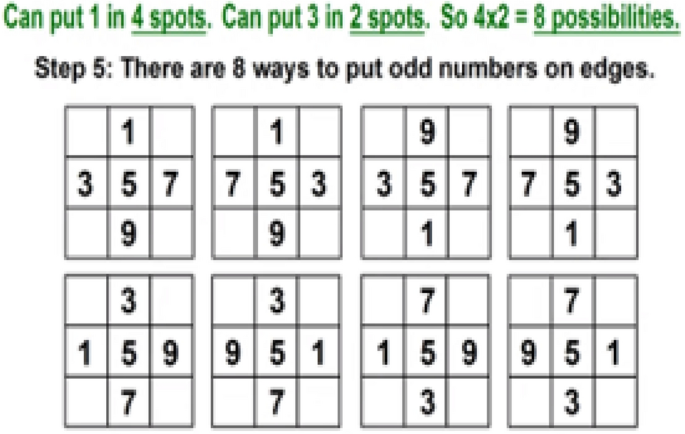
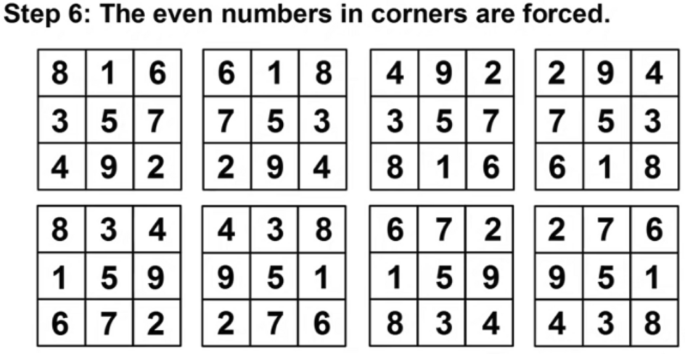
However, the Magic matrix is a special type of MATLAB function used for applying different shuffling, rotation, or reflecting properties. The above example in Figs. 4 , 5 , 6 , 7 and 8 respectively shows us the detailed explanation of the matrix by taking the magic matrix 3 by 3 and the required magic sum is 15. Now perform different calculations on the matrix to make the matrix magic. Either trying from the center point, starting left–right corners, or even–odd numbers to make the matrix magic. So take the value in terms of 3 by 3 and make the summation diagonally, each row and column, and check the properties of the magic matric, if found correct then the matrix is said to be magic shown in Figs. 5 , and 6 . The above example from steps 1–6 elaborates on the step by steps method that how to making the matrix magic. You can see in the above Fig. 6 , taking the square center to be 5 but the center involved 4 different sums, and if we take even numbers from the corners then each corner involved 3 different sums shown in step 4. And if we take the edges to be odd numbers then each sums involved 2 different sums. Now try to with some other numbers; suppose can we put 1 in 4 spots, or put 3 in 2 spots, so if we 2 multiply 4 then 8 possibilities occur. So there are 8 possibilities to put odd numbers on edges because we tried different ways but the result is not near to the magic matrix properties with odd numbers the different sums are low so we take the odd edges shown in step 5. Finally, the even numbers are placed at corners, and the odd numbers are placed on edges.

Results and discussion
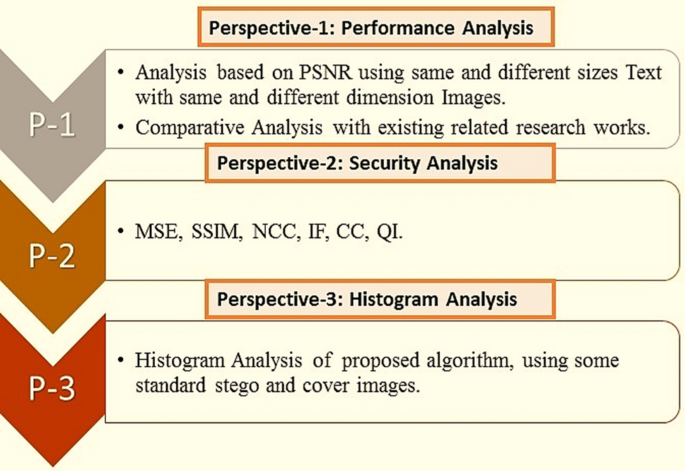
The section demonstrates the investigational results based on different perspectives, and some statistical assessment matrices to demonstrate the effectiveness and enactment of the planned work. For analysis, we used some standard images namely, Lena, Mandrill, Girl, etc. for the analysis of the method shown in Fig. 9 . It is also critically analyzed in relation to safety and enactment analysis based on three distinct perspectives shown in Fig. 10 .

Datasets of standard images 70 , 71 .
Experimental evaluation perspectives for the proposed algorithm.
Before going to the performance and security analysis of the proposed algorithm, we first explain the Quality assessment metrics used for critical analysis of the proposed algorithm shown in Table 3 55 , 56 , 57 .
Perspective 1
The performance analysis using P1 is given as follows. Using P1 the planned work is evaluated on different images of distinct dimensions with 14 kb’s secret message. Other hand, it is also analyzed based on different sizes of secret messages embedded into similar dimension images. So, the results demonstrate the connotation of the technique in view of PSNR values displayed in Table 4 . While Table 5 shows the performance of the proposed method compared with relevant existing methods using PSNR values which 6.22% outer performed.
Perspective 2
Security Analysis of the Proposed algorithm based on P2 is given. Table 6 elaborate the significance, resistance against to different attacks, quality, and performance of the propose method using different quality assessment parameters.
Results analysis
In this part, we described some enactment of the proposed method. Figure 11 a and d address the cover picture through the outcome tests. Figure 11 b, and e are stego pictures that are completely impalpable. Figure 11 c and f are decoded pictures that are vague to cover pictures. We preference the normal selection of cover pictures ''peppers'' and ''lake'' with the size of 256 × 256 as experimental tests.

Experimental results of cover images ( a , d ), cipher images ( b , e ) and decrypted images ( c , f ).
To analyze whether the proposed encryption method can oppose differential assaults; two significant assessment factors for differential assaults investigation are used which is Unified Average Changing Intensity (UACI), and Number of Pixels Changing Rate (NPCR) 58 , 59 . The value of UACI and NPCR of “Lake” and “Pepper” are presented in Tables 7 and 8 below. We can see that UACI is close the hypothetical value of 34.5742% and NPCR is near the hypothetical value of 99.7183%, and that implies that our plan can oppose difference assaults. In the meantime, our calculation is better than the literature 60 , 61 .
Now to check the proposed algorithm on differential attack two attacks are; Noise Attack (NA), NA is used to check either the algorithm can resist against some noise attacks are not, because a good embedding algorithm should be able to resist against NA. We analyzed some standard images using noise attacks with the value of 0.01, 0.1 and 0.5 of salt and pepper noise. It can be seen in Fig. 12 by adding 0.1 salt and pepper noise are still detectible. Therefore, our algorithm has good toughness and can proficiently oppose commotion assaults.
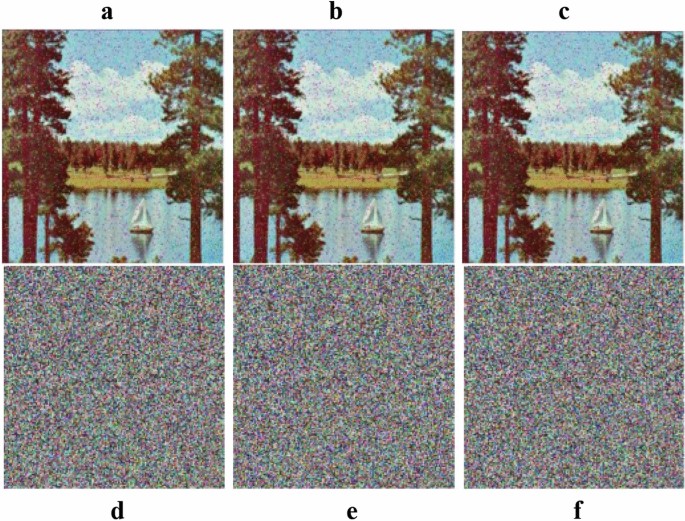
Noise attack (NA) analysis: ( a ) is decrypted image of ( d , b ) decrypted image of ( e , c ) decrypted image of ( f , d ) adding 0.01 salt and pepper noise, ( e ) adding 0.01 salt and pepper noise, ( f ) adding 0.01 salt and pepper noise.
While Cropping Attacks (CA), An ideal cryptosystem ought to be against information CA by transmission and capacity 62 , 63 . To assess its power in opposing trimming assaults, leaves behind 64 × 64, 64 × 128, 128 × 128, and 128 × 256 are obliterated from the embedded image ''Lake '' as displayed in Fig. 13 e–h. The extracted image is displayed in Fig. 13 a–d, and they can still be perceived. It demonstrates that our algorithm can oppose information editing assaults.
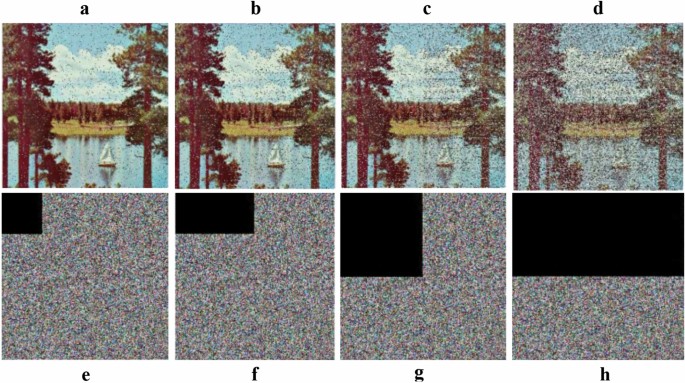
Cropping Attack (CA) analysis ( a ) decrypted image of ( e , b ) decrypted image of ( f , c ) decrypted image of ( g , d ) decrypted image of ( h , e ) 1/16 CA, ( f ) 1/8 CA, ( g ) 1/4 CA, ( h ) 1/2 CA.
Perspective 3
Histogram Analysis of the proposed algorithm based on P3 is given. Histogram Examination shows the real contrast between both stego and cover images. Due to its properties, a little difference between images can be founded, because it shows the extracted occurrences of the pixels of the image. Figure 14 shows the analysis of the proposed algorithm using three standard images namely, Lena, Mandrill, and House as both stego and cover image histograms.
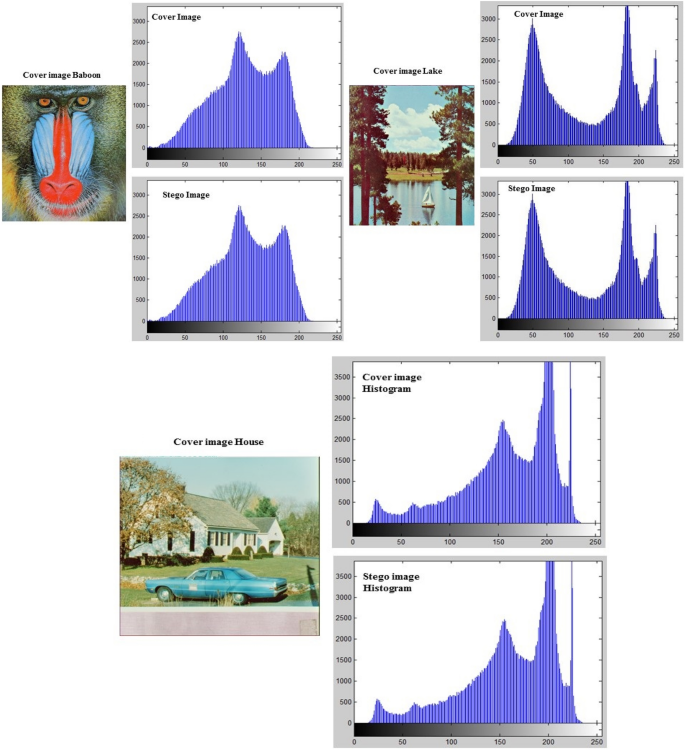
Histogram analysis of the proposed algorithm based on three standard cover and stego images.
However, the empirical results of the proposed algorithm grounded on diverse viewpoints using assessment metrics prove the improvement, efficiency, and effectiveness of the method. Our method improves the payload, high-level security, temper protection, and better visual quality of the image. Suppose attackers or any naked eye suspects the technique used in the proposed algorithm which is LSB and some improved technique of steganalysis. Then attacker can’t extract the actual contents of the secret message because the proposed method used Huffman code 64 , 65 , MLE 66 , Magic matrix 67 , 68 , and HSI (achromatic components of an image) 69 . If an attacker extracts the message up to some limits then the contents are useless, because, for extraction of the full message text, attackers need to use Huffman code, MLE, etc. for getting the actual message.
Conclusions and future research directions
In this study we proposed a novel method using Huffman code, HSI color model, MLEA, Magic matrix, and LSB substitution. Embedding the secret message, the I-plane of the HSI variety model is utilized as the cover image rather than the RGB model, for expanding the safety and reducing extra computational upstairs or processing time. The empirical outcomes of the proposed technique secure a normal of PSNR 79.29 dB over 165 standard images and also proves the control, and efficiency of the proposed method compared with some stated correlated works. The uses of the way of embedding the secret message in cover object is to makes this algorithm dreadful and abstruse and also unclear and foolish the steganalysis process. Our proposed method also used Huffman code which makes it more robust than existing methods. However, we infer that it is capable of shaping the stego picture practically identical and also has the fitness to give adeptness, and effectiveness and justify the encouraging demands of the current system and user to generate better quality stego images. So our method is easy to program, simple, and a better combination in terms of transparency and robustness. The results from different perspectives show the achievability and outperforming of our method to others. The main demerit of the proposed method is the amount of embedding the secret message not more than 20 KBs. Because for reliability, we analyzed the algorithm from different perspectives to achieve the basic criterion of steganography up to some acceptable limits. But still needs some reasonable improvements by functioning on magic matrix and MLEA extension to make the technique more dependable and also implementation of the method into the transform domain 70 , 71 . We are also now involved in an outcome further such ways as unsupervised learning (ML), related concepts of Deep Learning to grab some boundaries, and statistical and image processing assaults to produce excellent and dependable free stego images.
Data availability
The datasets produced and/or analyzed during the current study are openly accessible in the Kaggle repository, and SIPI, and can be gotten to at [ https://www.kaggle.com/datasets/mnavaidd/image-segmentation-dataset ]. Further, different pictures utilized inside the exploratory work are freely accessible on the web. All the codes used for this method will be provided for research purposes if requested by researchers.
Nabi, S. T., Kumar, M., Singh, P., Aggarwal, N. & Kumar, K. A comprehensive survey of image and video forgery techniques: Variants, challenges, and future directions. Multimed. Syst. 28 (3), 939–992. https://doi.org/10.1007/s00530-021-00873-8 (2022).
Article Google Scholar
LakshmiSirisha, B. & ChandraMohan, B. Review on spatial domain image steganography techniques. J. Discret. Math. Sci. Cryptogr. 24 (6), 1873–1883. https://doi.org/10.1080/09720529.2021.1962025 (2021).
Dhawan, S. & Gupta, R. Analysis of various data security techniques of steganography: a survey. Inf. Secur. J. 30 (2), 63–87 (2021).
Google Scholar
Bansal, K., Agrawal, A., & Bansal, N. (2020). A survey on steganography using least significant bit (lsb) embedding approach. in 2020 4th International Conference on Trends in Electronics and Informatics (ICOEI) (48184) , 64–69. https://doi.org/10.1080/19393555.2020.1801911.IEEE .
Sahu, A. K. & Swain, G. A review on LSB substitution and PVD based image steganography techniques. Indon. J. Electr. Eng. Comput. Sci. 2 (3), 712–719 (2016).
Hussain, M., Wahab, A. W. A., Idris, Y. I. B., Ho, A. T. & Jung, K. H. Image steganography in spatial domain: A survey. Signal Process. Image Commun. 65 , 46–66. https://doi.org/10.1016/j.image.2018.03.012 (2018).
Prajapati, H. A. & Chitaliya, N. G. Secured and robust dual image steganography: A survey. Int. J. Innov. Res. Comput. Commun. Eng. 3 (1), 30–37 (2015).
Subhedar, M. S. & Mankar, V. H. Current status and key issues in image steganography: A survey. Comput. Sci. Rev. 13 , 95–113. https://doi.org/10.1016/j.cosrev.2014.09.001 (2014).
Article MATH Google Scholar
Vaidya, K., Kargathara, A., & Kumbharana, C. K. Classification of Image Steganography in Substitution Technique. in Rising Threats in Expert Applications and Solutions , 253–261. (Springer, 2021).
Aslam, M. A. et al . Image Steganography using Least Significant Bit (LSB)-A Systematic Literature Review. in 2022 2nd International Conference on Computing and Information Technology (ICCIT) , 32–38. https://doi.org/10.1109/ICCIT52419.2022.9711628 .
Suresh, K. S., & Kamalakannan, T. Image Steganography Based on LSB Using Various Scanning Methods in Spatial Domain .
Alatiyyat, B. F., & Narmatha, C. Survey on image steganography techniques. in 2022 2nd International Conference on Computing and Information Technology (ICCIT) , 57–64. (IEEE, 2022).
Hameed, R. S., Abd Rahim, B. H. A., Taher, M. M. & Mokri, S. S. A literature review of various steganography methods. J. Theor. Appl. Inf. Technol. 100 (5), 1–10 (2022).
Kaur, S., Singh, S., Kaur, M. & Lee, H. N. A systematic review of computational image steganography approaches. Arch. Comput. Methods Eng. 1 , 1–23 (2022).
ADS Google Scholar
Tanya Bindu, R. & Kavitha, T. A survey on various crypto-steganography techniques for real-time images. In Intelligent Cyber Physical Systems and Internet of Things: ICoICI 2022 365–373 (Springer, 2023).
Chapter Google Scholar
Sharda, S. & Budhiraja, S. Image steganography: A review. Int. J. Emerg. Technol. Adv. Eng. (IJETAE) 3 (1), 707–710 (2013).
Upendra Raju, K. & Amutha Prabha, N. Dual images in reversible data hiding with adaptive color space variation using wavelet transforms. Int. J. Intell. Unmanned Syst. 11 (1), 96–108 (2023).
Inan, Y. Quality metrics of LSB image steganography technique for color space HSI. in 11th International Conference on Theory and Application of Soft Computing, Computing with Words and Perceptions and Artificial Intelligence-ICSCCW-2021 , 67–74. (Springer, 2022).
Hassan, F. S. & Gutub, A. Improving data hiding within colour images using hue component of HSV colour space. CAAI Trans. Intell. Technol. 7 (1), 56–68 (2022).
Kumar, A., Rani, R. & Singh, S. A survey of recent advances in image steganography. Secur. Privacy 6 , e281 (2023).
Tang, L., Wu, D., Wang, H., Chen, M. & Xie, J. An adaptive fuzzy inference approach for color image steganography. Soft. Comput. 25 (16), 10987–11004 (2021).
Elshoush, H. T., Mahmoud, M. M. & Altigani, A. A new high capacity and secure image realization steganography based on ASCII code matching. Multimed. Tools Appl. 81 (4), 5191–5237 (2022).
Hemeida, F., Alexan, W. & Mamdouh, S. A comparative study of audio steganography schemes. Int. J. Comput. Dig. Syst. 10 , 555–562 (2021).
Setiadi, D. R. I. M. PSNR vs SSIM: Imperceptibility quality assessment for image steganography. Multimed. Tools Appl. 80 (6), 8423–8444 (2021).
Zhang, Y. J. Image engineering. in Handbook of Image Engineering , 55–83. (Springer, 2021).
Lee, Y. K. & Chen, L. H. High capacity image steganographic model. IEE Proc. Vis. Image Signal Process. 147 (3), 288–294 (2000).
Zhang, X. & Wang, S. Efficient steganographic embedding by exploiting modification direction. IEEE Commun. Lett. 10 (11), 781–783 (2006).
Muhammad, K., Ahmad, J., Rehman, N. U., Jan, Z. & Qureshi, R. J. A secure cyclic steganographic technique for color images using randomization. Arxiv 19 (3), 57–64 (2015).
Muhammad, K. et al. A secure method for color image steganography using gray-level modification and multi-level encryption. KSII Trans. Internet Inf. Syst. 9 (5), 1938–1962 (2015).
Rustad, S., Setiadi, D. R. I. M., Syukur, A. & Andono, P. N. Inverted LSB image steganography using adaptive pattern to improve imperceptibility. J. King Saud Univ. Comput. Inf. Sci. 34 (6), 3559–3568 (2021).
Ye, H., Su, K., Cheng, X. & Huang, S. Research on reversible image steganography of encrypted image based on image interpolation and difference histogram shift. IET Image Proc. 16 (7), 1959–1972 (2022).
Than, S. S. M. Secure data transmission in video format based on LSB and Huffman coding. Int. J. Image Graph. Signal Process. 12 (1), 10–17 (2020).
Tsai, Y. Y., Liu, H. L., Kuo, P. L. & Chan, C. S. Extending multi-MSB prediction and huffman coding for reversible data hiding in encrypted HDR images. IEEE Access 10 , 49347–49358 (2022).
Sahu, M., Padhy, N., Gantayat, S. S. & Sahu, A. K. Local binary pattern-based reversible data hiding. CAAI Trans. Intell. Technol. 7 (4), 695–709 (2022).
Dhivya, R., Padmapriya, V., Sundararaman, R., Rayappan, J. B. B. & Amirtharajan, R. Chaos assisted variable bit steganography in transform domain. Electron. Lett. 54 (23), 1332–1334 (2018).
Article ADS Google Scholar
Ramapriya, B., & Kalpana, Y. A competent medical image steganography using improved optimization algorithm with Huffman encoding techniques. in 2023 7th International Conference on Computing Methodologies and Communication (ICCMC) , 1065–1073. (IEEE, 2023).
Sahu, A. K., Hassaballah, M., Rao, R. S. & Suresh, G. Logistic-map based fragile image watermarking scheme for tamper detection and localization. Multimed. Tools Appl. 1 , 1–32 (2022).
Bhavani, Y., Kamakshi, P., Kavya Sri, E., & Sindhu Sai, Y. A survey on image steganography techniques using least significant bit. in Intelligent Data Communication Technologies and Internet of Things , 281–290. (Springer, 2022).
Sun, S. A novel edge based image steganography with 2k correction and Huffman encoding. Inf. Process. Lett. 116 (2), 93–99 (2016).
Article MathSciNet MATH Google Scholar
Das, R. & Tuithung, T. (2012). A novel steganography method for image based on Huffman Encoding. in 2012 3rd National Conference on Emerging Trends and Applications in Computer Science , 14–18. (IEEE, 2012).
Nag, A., Singh, J. P., Biswas, S., Sarkar, D. & Sarkar, P. P. A Huffman code based image steganography technique. in Applied Algorithms: First International Conference, ICAA 2014, Kolkata, India, January 13–15, 2014. Proceedings 1 , 257–265. (Springer, 2014).
Yi, X., Yang, K., Zhao, X., Wang, Y. & Yu, H. AHCM: Adaptive Huffman code mapping for audio steganography based on psychoacoustic model. IEEE Trans. Inf. Forensics Secur. 14 (8), 2217–2231 (2019).
Sari, C. A., Ardiansyah, G. & Rachmawanto, E. H. An improved security and message capacity using AES and Huffman coding on image steganography. TELKOMNIKA (Telecommun. Comput. Electron. Control) 17 (5), 2400–2409 (2019).
Sharma, N. & Batra, U. An enhanced Huffman-PSO based image optimization algorithm for image steganography. Genet. Program Evolvable Mach. 22 , 189–205 (2021).
Taha, M. S., Mahdi, M. H., Khalid, H. N., Aman, A. H. M. & Attarbashi, Z. S. A steganography embedding method based on P single/P double and Huffman coding. in 2021 3rd International Cyber Resilience Conference (CRC) , 1–6. (IEEE, 2021).
Abed, M. K., Kareem, M. M., Ibrahim, R. K., Hashim, M. M., Kurnaz, S., & Ali, A. H. Secure medical image steganography method based on pixels variance value and eight neighbors. in 2021 International Conference on Advanced Computer Applications (ACA) , 199–205. (IEEE, 2021).
Tayyeh, H. K. & Al-Jumaili, A. S. A. A combination of least significant bit and deflate compression for image steganography. Int. J. Electr. Comput. Eng. 12 (1), 358–364 (2022).
Abbas, N. A. F., Abdulredha, N., Ibrahim, R. K. & Ali, A. H. Security and imperceptibility improving of image steganography using pixel allocation and random function techniques. Int. J. Electr. Comput. Eng. 12 (1), 2088–8708 (2022).
Almazaydeh, W. E. I. A. Image steganography to hide unlimited secret text size. Int. J. Comput. Sci. Netw. Secur. 22 (4), 73–82 (2022).
MathSciNet Google Scholar
Taha, M. S., Rahem, M. S. M., Hashim, M. M. & Khalid, H. N. High payload image steganography scheme with minimum distortion based on distinction grade value method. Multimed. Tools Appl. 81 (18), 25913–25946 (2022).
Gao, G., Zhang, L., Lin, Y., Tong, S. & Yuan, C. High-performance reversible data hiding in encrypted images with adaptive Huffman code. Dig. Signal Process. 133 , 103870 (2023).
Alkhliwi, S. Huffman encoding with white tailed eagle algorithm-based image steganography technique. Eng. Technol. Appl. Sci. Res. 13 (2), 10453–10459 (2023).
Kadhem, E. L. & Baawi, S. S. A secure and high capacity image steganography approach using Huffman coding and RSA encryption. J. Al-Qadisiyah Comput. Sci. Math. 15 (2), 35 (2023).
Zairi, M., Boujiha, T. & Ouelli, A. Secure fragile watermarking based on Huffman encoding and optimal embedding strategy. Indon. J. Electr. Eng. Comput. Sci. 29 (2), 1132–1139 (2023).
Yang, Y., He, H., Chen, F., Yuan, Y. & Mao, N. Reversible data hiding in encrypted images based on time-varying Huffman coding table. IEEE Trans. Multimed. 1 , 1–12 (2023).
CAS Google Scholar
Muazu, A. A., Maiwada, U. D., Garba, A. R. I., Qabasiyu, M. G., & Danyaro, K. U. Secure data hiding and extraction using RSA Algorithm. in Advancements in Interdisciplinary Research: First International Conference, AIR 2022, Prayagraj, India, May 6–7, 2022, Revised Selected Papers , 14–28. (Springer, 2023).
Mahdi, M. H. et al. Improvement of image steganography scheme based on LSB value with two control random parameters and multi-level encryption. in IOP Conference Series: Materials Science and Engineering , vol. 518, No. 5, 052002. (IOP Publishing, 2019).
Seyedzadeh, S. M., Norouzi, B., Mosavi, M. R. & Mirzakuchaki, S. A novel color image encryption algorithm based on spatial permutation and quantum chaotic map. Nonlinear Dyn. 81 (1–2), 511–529 (2015).
Di, X., Li, J., Qi, H., Cong, L. & Yang, H. A semi-symmetric image encryption scheme based on the function projective synchronization of two hyperchaotic systems. PLoS ONE 12 (9), e0184586 (2017).
Article PubMed PubMed Central Google Scholar
Praveenkumar, P., Amirtharajan, R., Thenmozhi, K. & Rayappan, J. B. B. ‘Triple chaotic image scrambling on RGB: A random image encryption approach’. Secur. Commun. Netw. 8 (18), 3335–3345 (2015).
Chai, X.-L., Gan, Z.-H., Lu, Y., Zhang, M.-H. & Chen, Y.-R. A novel color image encryption algorithm based on genetic recombination and the four-dimensional memristive hyperchaotic system. Chin. Phys. B 25 (10), 100503 (2016).
Li, X., Zhou, C. & Xu, N. A secure and efficient image encryption algorithm based on DNA coding and spatiotemporal chaos. IJ Netw. Secur. 20 (1), 110–120 (2018).
Norouzi, B. & Mirzakuchaki, S. A fast color image encryption algorithm based on hyper-chaotic systems. Nonlinear Dyn. 78 (2), 995–1015 (2014).
Wang, X., Chang, C. C., Lin, C. C. & Chang, C. C. On the multi-level embedding of crypto-image reversible data hiding. J. Vis. Commun. Image Represent. 87 , 103556 (2022).
Yousif, S. F., Abboud, A. J. & Radhi, H. Y. Robust image encryption with scanning technology, the El-Gamal algorithm and chaos theory. IEEE Access 8 , 155184–155209 (2020).
Yousif, S. F., Abboud, A. J. & Alhumaima, R. S. A new image encryption based on bit replacing, chaos and DNA coding techniques. Multimed. Tools Appl. 81 (19), 27453–27493 (2022).
https://en.wikipedia.org/wiki/Magic_square
https://www.mathworks.com/help/matlab/ref/magic.html
Alabaichi, A., Al-Dabbas, M. A. A. A. K. & Salih, A. Image steganography using least significant bit and secret map techniques. Int. J. Electr. Comput. Eng. 10 (1), 2088–8708 (2020).
https://sipi.usc.edu/database/ .
https://www.imageprocessingplace.com/ .
Download references
Acknowledgements
This research is supported, in parts, by the University of Peshawar and, in parts, by the Abdul Wali Khan University Mardan (AWKUM), Pakistan.
Author information
Authors and affiliations.
Qurtuba University of Science and Information Technology, Peshawar, Pakistan
Shahid Rahman & Jamal Uddin
University of Buner, Khyber Pakhtunkhwa, Pakistan
Hameed Hussain & Afzal Rahman
Abdul Wali Khan University, Mardan, Pakistan
Aftab Ahmed & Muhammad Zakarya
University of Lakki Marwat, Khyber Pakhtunkhwa, Pakistan
Ayaz Ali Khan
Sohar University, Sohar, Sultanate of Oman
Muhammad Zakarya
Kardan University, Kabul, Afghanistan
Muhammad Haleem
You can also search for this author in PubMed Google Scholar
Contributions
Shahid Rahman:- Research, Methodology, Writing - Original Draft; Jamal Uddin:- Conceptualization, Methodology, Software, Writing - Review & Editing; Hameed Hussain:- Conceptualization, Visualization, Validation, Investigation; Aftab Ahmed:- Visualization, Validation, Proofreading; Ayaz Ali Khan:- Writing - Review & Editing, Revisions; Muhammad Zakarya:- Visualization, Data Curation, Proofreading; Afzal Rahman:- Visualization, Writing - Review & Editing; Muhammad Haleem:- Writing - Revised Draft, Data Curation;
Corresponding author
Correspondence to Muhammad Haleem .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Rahman, S., Uddin, J., Hussain, H. et al. A Huffman code LSB based image steganography technique using multi-level encryption and achromatic component of an image. Sci Rep 13 , 14183 (2023). https://doi.org/10.1038/s41598-023-41303-1
Download citation
Received : 12 February 2023
Accepted : 24 August 2023
Published : 30 August 2023
DOI : https://doi.org/10.1038/s41598-023-41303-1
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
This article is cited by
Four enhanced algorithms for full size image hiding in chest x-ray images.
- Apichat Heednacram
- Yossawee Keaomanee
Multimedia Tools and Applications (2024)
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing: AI and Robotics newsletter — what matters in AI and robotics research, free to your inbox weekly.
image steganography Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
Image Steganography Technique Based on Integer Wavelet Transform Using Most Significant Bit Categories
Security and imperceptibility improving of image steganography using pixel allocation and random function techniques.
Information security is one of the main aspects of processes and methodologies in the technical age of information and communication. The security of information should be a key priority in the secret exchange of information between two parties. In order to ensure the security of information, there are some strategies that are used, and they include steganography and cryptography. An effective digital image-steganographic method based on odd/even pixel allocation and random function to increase the security and imperceptibility has been improved. This lately developed outline has been verified for increasing the security and imperceptibility to determine the existent problems. Huffman coding has been used to modify secret data prior embedding stage; this modified equivalent secret data that prevent the secret data from attackers to increase the secret data capacities. The main objective of our scheme is to boost the peak-signal-to-noise-ratio (PSNR) of the stego cover and stop against any attack. The size of the secret data also increases. The results confirm good PSNR values in addition of these findings confirmed the proposed method eligibility.

A combination of least significant bit and deflate compression for image steganography
Steganography is one of the cryptography techniques where secret information can be hidden through multimedia files such as images and videos. Steganography can offer a way of exchanging secret and encrypted information in an untypical mechanism where communicating parties can only interpret the secret message. The literature has shown a great interest in the least significant bit (LSB) technique which aims at embedding the secret message bits into the most insignificant bits of the image pixels. Although LSB showed a stable performance of image steganography yet, many works should be done on the message part. This paper aims to propose a combination of LSB and Deflate compression algorithm for image steganography. The proposed Deflate algorithm utilized both LZ77 and Huffman coding. After compressing the message text, LSB has been applied to embed the text within the cover image. Using benchmark images, the proposed method demonstrated an outperformance over the state of the art. This can proof the efficacy of using Deflate as a data compression prior to the LSB embedding.
Hybrid image steganography method using Lempel Ziv Welch and genetic algorithms for hiding confidential data
Quality metrics of lsb image steganography technique for color space hsi, blockchain-based secure data sharing scheme using image steganography and encryption techniques for telemedicine applications, reference-free differential histogram-correlative detection of steganography: performance analysis.
<span lang="EN-US">Recent <span>research has demonstrated the effectiveness of utilizing neural networks for detect tampering in images. However, because accessing a database is complex, which is needed in the classification process to detect tampering, reference-free steganalysis attracted attention. In recent work, an approach for least significant bit (LSB) steganalysis has been presented based on analyzing the derivatives of the histogram correlation. In this paper, we further examine this strategy for other steganographic methods. Detecting image tampering in the spatial domain, such as image steganography. It is found that the above approach could be applied successfully to other kinds of steganography with different orders of histogram-correlation derivatives. Also, the limits of the ratio stego-image to cover are considered, where very small ratios can escape this detection method unless </span> modified.</span>
Securing the COVID Patients’ Medical Records Using Encrypted Image Steganography
Gan-based spatial image steganography with cross feedback mechanism, cnn auto-encoder network using dilated inception for image steganography, export citation format, share document.

It appears you don't have a PDF plugin for this browser. click here to download the PDF file.
Cryptology for Christ: Steganography, Evangelism, and Closed Access Countries
Christopher Jaus
Liberty University
Digital steganography is rooted in the ancient practice of hiding messages and has evolved dramatically with technology. In the Christian worldview, modern technology's ethical application is rooted i..
Digital steganography is rooted in the ancient practice of hiding messages and has evolved dramatically with technology. In the Christian worldview, modern technology's ethical application is rooted in the creation mandate, where Genesis 1:28 commands mankind to subdue the earth and have dominion over it. The Bible tells of examples where God directly instructs time-period specific technological application. For example, in Exodus 36, two men were charged with the task of using their technological skills to create objects for the purpose of housing the unique presence of God. Exodus 36:1 says, “Bezalel and Oholiab and every craftsman in whom the Lord has put skill and intelligence to know how to do any work in the construction of the sanctuary shall work in accordance with all that the Lord has commanded.” If Christians today are craftsmen in whom the Lord has put skill and intelligence, then the technology available today can help to fulfill God’s mandate to them in the Great Commission to spread the Gospel, especially where traditional methods of evangelism face constraints or persecution. Digital steganography offers secure, covert channels for data transmission, presenting unique applications for Christian evangelism in restricted regions. This paper explores the versatility of file-appending methods in digital steganography, which bypass traditional limitations on data size and type. Utilizing a full copy of the Bible in text form and a sample image in .png form, we showcased the efficacy and security of this steganography method. Results demonstrate not only high levels of data integrity but also an incredibly easy to use methodology for implementation, making it an effective tool for discreetly disseminating religious texts. This paper argues for the ethical application of these techniques in the spread of the Christian Gospel, particularly where traditional evangelistic efforts are hindered by legal or social constraints.
https://digitalcommons.liberty.edu/context/research_symp/article/2509/viewcontent
http://digitalcommons.liberty.edu/research_symp/2024/oral_presentations/18
3708ce20-fbfc-4b55-ab16-3cb017fad3b8
2024-04-15T20:00:00Z
Oral - Basic
https://digitalcommons.liberty.edu/cgi/viewcontent.cgi?article=2509&context=research_symp
CNN based Image Steganography Techniques: A Cutting Edge/State of Art Review
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.

2024 Environmental Performance Index: A Surprise Top Ranking, Global Biodiversity Commitment Tested
The Baltic nation of Estonia is No. 1 in the 2024 rankings, while Denmark, one of the top ranked countries in the 2022 EPI dropped to 10 th place, highlighting the challenges of reducing emissions in hard-to-decarbonize industries. Meanwhile, “paper parks” are proving a global challenge to international biodiversity commitments.
Listen to Article
In 2022, at the UN Biodiversity Conference, COP 15, in Montreal over 190 countries made what has been called “the biggest conservation commitment the world has ever seen.” The Kunming-Montreal Global Biodiversity Framework called for the effective protection and management of 30% of the world’s terrestrial, inland water, and coastal and marine areas by the year 2030 — commonly known as the 30x30 target. While there has been progress toward reaching this ambitious goal of protecting 30% of land and seas on paper, just ahead of World Environment Day, the 2024 Environmental Performance Index (EPI) , an analysis by Yale researchers that provides a data-driven summary of the state of sustainability around the world, shows that in many cases such protections have failed to halt ecosystem loss or curtail environmentally destructive practices.
A new metric that assesses how well countries are protecting important ecosystems indicated that while nations have made progress in protecting land and seas, many of these areas are “paper parks” where commercial activities such as mining and trawling continue to occur — sometimes at a higher rate than in non-protected areas. The EPI analyses show that in 23 countries, more than 10% of the land protected is covered by croplands and buildings, and in 35 countries there is more fishing activity inside marine protected areas than outside.
“Protected areas are failing to achieve their goals in different ways,” said Sebastián Block Munguía, a postdoctoral associate with the Yale Center for Environmental Law and Policy (YCELP) and the lead author of the report. “In Europe, destructive fishing is allowed inside marine protected areas, and a large fraction of the area protected in land is covered by croplands, not natural ecosystems. In many developing countries, even when destructive activities are not allowed in protected areas, shortages of funding and personnel make it difficult to enforce rules.”
The 2024 EPI, published by the Yale Center for Environmental Law and Policy and Columbia University’s Center for International Earth Science Information Network ranks 180 countries based on 58 performance indicators to track progress on mitigating climate change, promoting environmental health, and safeguarding ecosystem vitality. The data evaluates efforts by the nations to reach U.N. sustainability goals, the 2015 Paris Climate Change Agreement, as well as the Kunming-Montreal Global Biodiversity Framework. The data for the index underlying different indicators come from a variety of academic institutions and international organizations and cover different periods. Protected area coverage indicators are based on data from March 2024, while greenhouse emissions data are from 2022.
Estonia has decreased its GHG emissions by 59% compared to 1990. The energy sector will be the biggest contributor in reducing emissions in the coming years as we have an aim to produce 100% of our electricity consumption from renewables by 2030.”
The index found that many countries that were leading in sustainability goals have fallen behind or stalled, illustrating the challenges of reducing emissions in hard-to-decarbonize industries and resistant sectors such as agriculture. In several countries, recent drops in agricultural greenhouse gas emissions (GHG) have been the result of external circumstances, not policy. For example, in Albania, supply chain disruptions led to more expensive animal feed that resulted in a sharp reduction in cows and, consequentially, nitrous oxide and methane emissions.
Estonia leads this year’s rankings with a 40% drop in GHG emissions over the last decade, largely attributed to replacing dirty oil shale power plants with cleaner energy sources. The country is drafting a proposal to achieve by 2040 a CO2 neutral energy sector and a CO2 neutral public transport network in bigger cities.
“Estonia has decreased its GHG emissions by 59% compared to 1990. The energy sector will be the biggest contributor in reducing emissions in the coming years as we have an aim to produce 100% of our electricity consumption from renewables by 2030,” said Kristi Klaas, Estonia’s vice-minister for Green Transition. Klaas discussed some of the policies that led to the country's success as well as ongoing challenges, such as reducing emissions in the agriculture sector, at a webinar hosted by YCELP on June 3. Dr. Abdullah Ali Abdullah Al-Amri, chairman of the Environment Authority of Oman, also joined the webinar to discuss efforts aimed at protecting the county's multiple ecosystems with rare biodiversity and endangered species, such as the Arabian oryx, and subspecies, such as the Arabian leopard.

Subscribe to “YSE 3”
Biweekly, we highlight three news and research stories about the work we’re doing at Yale School of the Environment.
Denmark, the top ranked country in the 2022 EPI dropped to 10th place, as its pace of decarbonization slowed, highlighting that those early gains from implementing “low-hanging-fruit policies, such as switching to electricity generation from coal to natural gas and expanding renewable power generation are themselves insufficient,” the index notes. Emissions in the world’s largest economies such as the U.S. (which is ranked 34th) are falling too slowly or still rising — such as in China, Russia, and India, which is ranked 176th.
Over the last decade only five countries — Estonia, Finland, Greece, Timor-Leste, and the United Kingdom — have cut their GHG emissions over the last decade at the rate needed to reach net zero by 2050. Vietnam and other developing countries in Southeast and Southern Asia — such as Pakistan, Laos, Myanmar, and Bangladesh — are ranked the lowest, indicating the urgency of international cooperation to help provide a path for struggling nations to achieve sustainability.
“The 2024 Environmental Performance Index highlights a range of critical sustainability challenges from climate change to biodiversity loss and beyond — and reveals trends suggesting that countries across the world need to redouble their efforts to protect critical ecosystems and the vitality of our planet,” said Daniel Esty, Hillhouse Professor of Environmental Law and Policy and director of YCELP.
- Daniel C. Esty
- Sebastián Block Munguía
- Ecosystem Management and Conservation
- Environmental Policy Analysis
Media Contact

Fran Silverman
Associate Director of Communications
Research in the News

Climate Change Threatens Resilience of Sri Lankan Rainforests

An Inside Look at Beech Leaf Disease

Achieving Sustainable Urban Growth on a Global Scale
Connect with us.
- Request Information
- Register for Events
SPM: estimating payload locations of QIM-based steganography in low-bit-rate compressed speeches
- Published: 07 June 2024
Cite this article

- Cheng Zhang 1 , 2 ,
- Shujuan Jiang ORCID: orcid.org/0000-0003-0643-0565 1 , 2 &
- Zhong Chen 3
Steganography, adopted to hide secret information into multiple digital carriers, has been widely used by lawbreakers for spiteful purposes, posing a threat to cyber security. Recently, VoIP speech (compressed speech) has been determined as a suitable carrier for steganography. Among the existing VoIP steganography algorithms, QIM-based VoIP steganography has great stealthiness, making it hard to detect. Although some existing studies have been conducted on detecting QIM-based VoIP steganography, some major challenges still exist that need to be addressed. First, no previous study attempts to estimate the payload locations of QIM-based VoIP steganography, a potential research direction, and a practical way of reducing the search space to recover hidden information. Second, the detection performance of existing models on QIM-based VoIP steganography still has a huge room for improvement. To address the above issues, this paper proposes a novel method called the Steganography Payload-localization Model (SPM) as a countermeasure for QIM-based VoIP steganography. Experimental results show that SPM can estimate the payload locations and perform real-time steganalysis regarding QIM-based VoIP steganography with superb performance.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions

Availability of data and materials
All of the materials including figures is owned by the authors and no permissions are required. The initial dataset is the VoIP steganalysis benchmark dataset which was published in [ 5 ] ( https://github.com/fjxmlzn/RNN-SM ). Editorial Policies for: Springer journals and proceedings: https://www.springer.com/gp/editorial-policies Nature Portfolio journals: https://www.nature.com/nature-research/editorial-policies Scientific Reports : https://www.nature.com/srep/journal-policies/editorial-policies BMC journals: https://www.biomedcentral.com/getpublished/editorial-policies
Wang Y, Li W, Zhang W et al (2021) Bbc++: Enhanced block boundary continuity on defining non-additive distortion for jpeg steganography. IEEE Trans Circuits Syst Video Technol 31(5):2082–2088. https://doi.org/10.1109/TCSVT.2020.3010554
Article Google Scholar
Lu W, Xue Y, Yeung Y et al (2021) Secure halftone image steganography based on pixel density transition. IEEE Trans Dependable Secure Comput 18(3):1137–1149. https://doi.org/10.1109/TDSC.2019.2933621
AL-Hagree S, Hadwan M, Aqlan A, et al (2021) A survey on different arabic text steganography techniques. In: 2021 1st International Conference on Emerging Smart Technologies and Applications (eSmarTA), pp 1–8, https://doi.org/10.1109/eSmarTA52612.2021.9515740
Huang Y, Lei Z, Song Z, et al (2021) A video steganography scheme based on post-quantum cryptography. In: 2021 IEEE International Conference on Information Communication and Software Engineering (ICICSE), pp 83–87, https://doi.org/10.1109/ICICSE52190.2021.9404087
Lin Z, Huang Y, Wang J (2018) Rnn-sm: Fast steganalysis of voip streams using recurrent neural network. IEEE Trans Inf Forensics Secur 13(7):1854–1868. https://doi.org/10.1109/TIFS.2018.2806741
Li S, Wang J, Liu P et al (2021) Detection of multiple steganography methods in compressed speech based on code element embedding, bi-lstm and cnn with attention mechanisms. IEEE/ACM Trans Audio, Speech, Lang Process 29:1556–1569. https://doi.org/10.1109/TASLP.2021.3074752
Kraetzer C, Dittmann J (2007) Mel-cepstrum based steganalysis for voip steganography. In: Security, Steganography, and Watermarking of Multimedia Contents IX, pp 54–65, https://doi.org/10.1117/12.704040
Liu Q, Sung A, Qiao M (2009) Temporal derivative-based spectrum and mel-cepstrum audio steganalysis. IEEE Trans Inf Forensics Secur 4(3):359–368. https://doi.org/10.1109/TIFS.2009.2024718
Kocal O, Yuruklu E, Avcibas I (2008) Chaotic-type features for speech steganalysis. IEEE Trans Inf Forensics Secur 3(4):651–661. https://doi.org/10.1109/TIFS.2008.2004289
Avcibas I (2006) Audio steganalysis with content-independent distortion measures. IEEE Signal Process Lett 13(2):92–95. https://doi.org/10.1109/LSP.2005.862152
Paulin C, Selouani S, Hervet E (2016) Audio steganalysis using deep belief networks. Int J Speech Technol 19(3):585–591. https://doi.org/10.1007/s10772-016-9352-6
Paulin C, Selouani S, Hervet E (2016) Speech steganalysis using evolutionary restricted boltzmann machines. In: 2016 IEEE Congress on Evolutionary Computation (CEC), pp 4831–4838, https://doi.org/10.1109/CEC.2016.7744409
Rekik S, Selouani SA, Guerchi D, et al (2012) An autoregressive time delay neural network for speech steganalysis. In: 2012 11th International Conference on Information Science, Signal Processing and their Applications (ISSPA), pp 54–58, https://doi.org/10.1109/ISSPA.2012.6310612
Chen B, Luo W, Li H (2017) Audio steganalysis with convolutional neural network. In: Proceedings of the 5th ACM Workshop on Information Hiding and Multimedia Security, p 85-90, https://doi.org/10.1145/3082031.3083234
Yang H, Yang Z, Bao Y, et al (2020) Hierarchical representation network for steganalysis of qim steganography in low-bit-rate speech signals. In: Information and Communications Security, pp 783–798, https://doi.org/10.1007/978-3-030-41579-2_45
Yang H, Yang Z, Bao Y, et al (2020) Fcem: A novel fast correlation extract model for real time steganalysis of voip stream via multi-head attention. In: ICASSP 2020 - 2020 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), pp 2822–2826, https://doi.org/10.1109/ICASSP40776.2020.9054361
Hu Y, Huang Y, Yang Z et al (2021) Detection of heterogeneous parallel steganography for low bit-rate voip speech streams. Neurocomputing 419:70–79. https://doi.org/10.1016/j.neucom.2020.08.002
Xiao B, Huang Y, Tang S (2008) An approach to information hiding in low bit-rate speech stream. In: IEEE GLOBECOM 2008 - 2008 IEEE Global Telecommunications Conference, pp 1–5, https://doi.org/10.1109/GLOCOM.2008.ECP.375
Wei M, Li S, Liu P et al (2023) Frame-level steganalysis of qim steganography in compressed speech based on multi-dimensional perspective of codeword correlations. J Ambient Intell Hum Comput 14:8421–8431. https://doi.org/10.1007/s12652-021-03608-9
Chen B, Wornell G (2001) Quantization index modulation: a class of provably good methods for digital watermarking and information embedding. IEEE Trans Inf Theory 47(4):1423–1443. https://doi.org/10.1109/18.923725
Article MathSciNet Google Scholar
O’Shaughnessy D (1988) Linear predictive coding. IEEE Potentials 7(1):29–32
Union IT (2007) G.729: Coding of speech at 8 kbit/s using conjugate structure algebraic-code-excited linear-prediction (cs-acelp). https://www.itu.int/rec/T-REC-G.729
Boroumand M, Chen M, Fridrich J (2019) Deep residual network for steganalysis of digital images. IEEE Trans Inf Theory 14(5):1181–1193. https://doi.org/10.1109/TIFS.2018.2871749
Huang Y, Tang S, Zhang Y (2011) Detection of covert voice-over internet protocol communications using sliding window-based steganalysis. IET Commun 5(7):929–936
Qiu Y, Tian H, Tang L et al (2022) Steganalysis of adaptive multi-rate speech streams with distributed representations of codewords. J Inf Secur Appl 68:103250. https://doi.org/10.1016/j.jisa.2022.103250
Li S, Jia Y, Kuo C (2017) Steganalysis of qim steganography in low-bit-rate speech signals. IEEE/ACM Trans Audio, Speech, Lang Process 25(5):1011–1022. https://doi.org/10.1109/TASLP.2017.2676356
Wu Z, Li R, Yin P, et al (2020) Steganalysis of quantization index modulation steganography in g.723.1 codec. Future Internet 12(1). https://doi.org/10.3390/fi12010017
Yang Z, Yang H, Chang C et al (2022) Real-time steganalysis for streaming media based on multi-channel convolutional sliding windows. Knowl Based Syst 237:107561. https://doi.org/10.1016/j.knosys.2021.107561
Download references
The authors wish to thank the anonymous reviewers and editors. This work was supported in part by the National Natural Science Foundation of China under grant No. 61673384.
Author information
Authors and affiliations.
School of Computer Science and Technology, China University of Mining and Technology, Da Xue Road, Xuzhou, Jiang Su, 221116, China
Cheng Zhang & Shujuan Jiang
Engineering Research Center of Mine Digitalization, China University of Mining and Technology, Ministry of Education, Da Xue Road, Xuzhou, Jiang Su, 221116, China
School of Information and Control Engineering, China University of Mining and Technology, Da Xue Road, Xuzhou, Jiang Su, 221116, China
You can also search for this author in PubMed Google Scholar
Contributions
All authors reviewed the manuscript. Cheng, Zhang wrote the code, ran the experiment, and wrote this manuscript. Shujuan, Jiang supervised Cheng, Zhang and provided the necessary help with the idea, code, and writing. Zhong, Chen inspected the code and reviewed the manuscript.
Corresponding author
Correspondence to Shujuan Jiang .
Ethics declarations
Ethical approval.
This declaration is not applicable.
Competing interests
I declare that all authors have no competing interests as defined by Springer, or other interests that might be perceived to influence the results and discussion reported in this paper.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Zhang, C., Jiang, S. & Chen, Z. SPM: estimating payload locations of QIM-based steganography in low-bit-rate compressed speeches. Multimed Tools Appl (2024). https://doi.org/10.1007/s11042-024-19501-4
Download citation
Received : 23 June 2023
Revised : 17 April 2024
Accepted : 26 May 2024
Published : 07 June 2024
DOI : https://doi.org/10.1007/s11042-024-19501-4
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Steganography
- Audio steganalysis
- Compressed speech.
- Find a journal
- Publish with us
- Track your research

IMAGES
VIDEO
COMMENTS
Image Steganography is the process of hiding information which can be text, image or video inside a cover image. The secret information is hidden in a way that it not visible to the human eyes. Deep learning technology, which has emerged as a powerful tool in various applications including image steganography, has received increased attention recently. The main goal of this paper is to explore ...
A number of future directions are presented that can assist researchers in determining the direction of future research in image steganography. With the rapid growth of multimedia technologies, many images are communicated over public channels. ... Publication year range is selected between 2011 to 2022 from reputable databases only. Papers in ...
The modern steganography can be modeled by Simmons [11] in the famous prisoner's problem. The paper explains about the competencies and virtues of steganography in an insecure channel that involves three parties: Alice, Bob, and Wendy. Assume, Alice and Bob are the two prisoners who work together for an escape plan.
This review paper explores the use of optimization techniques in steganography, the art of hiding secret information within other data. Steganography is a field that has gained significant attention in recent years due to the increasing need for secure communication and data protection. Optimization techniques have been shown to be effective in improving the performance of steganography ...
Steganography is the art of concealing information in a cover media in such a way that the presence of the information is unknown. Digital image steganography accomplishes the potential for protected communication that is crucial in most of the applications nowadays. Steganography has several beneficial applications.
file formats, steganography methods have been developed for almost all types of possible cover messages. The main ones include images, audio, and text (for a video cover message, image and audio steganography systems can be applied independently). Text steganography is the family of steganographic systems that use text as the cover message ...
In this review paper, we delve into various aspects of steganography, explor ing its. techniques, detection methods, evaluation criteria, and practical applications. We analyze. steganalysis ...
In image steganography, the statistical model of an image is crucial for hiding information in less detectable pixels and attaining better protection. This paper aims to present a systematic review of image steganography approaches. Articles are selected from reputable databases such as IEEE Explore, Web of Science (WOS), ACM, and Willey.
A review of the deep learning based image steganography techniques is presented in this paper. For completeness, the recent traditional steganography techniques are also discussed briefly. The three key parameters (security, embedding capacity, and invisibility) for measuring the quality of an image steganographic technique are described.
Multimodal steganography and watermarking are less studied and are likely to become a hot direction of research in the future with the continuous progress of multimodal deep learning. 6. Conclusion. In this paper, we thoroughly investigate image steganography and watermarking models based on deep learning methods.
In the past few years, the Generative Adversarial Network (GAN), which proposed in 2014, has achieved great success. There have been increasing research achievements based on GAN in the field of computer vision and natural language processing. Image steganography is an information security technique aiming at hiding secret messages in common digital images for covert communication. Recently ...
Development of an effective and efficient data hiding technique using steganography: The research paper proposes a method that combines steganography and encryption algorithms to ensure the confidentiality and integrity of the transmitted data. The goal is to hide the message inside a cover medium to remain undetectable to attackers.
Steganography is a technique for covert communication between two parties. With the rapid development of deep neural networks (DNN), more and more steganographic networks are proposed recently, which are shown to be promising to achieve good performance. Unlike the traditional handcrafted steganographic tools, a steganographic network is relatively large in size. It raises concerns on how to ...
This research paper explores the use of image steganography for data communication. It provides an overview of data communication and steganography and focuses on the specific area of image steganography. It surveys various algorithms, including traditional and recent techniques, such as least significant bit insertion and neural network-based approaches. The importance of security ...
To handle these issues, in this paper we proposed a method in view of Huffman code, Least Significant Bits (LSB) based cover steganography utilizing Multi-Level Encryption (MLE) and colorless part ...
Image Pixels . Lsb Technique. Steganography is one of the cryptography techniques where secret information can be hidden through multimedia files such as images and videos. Steganography can offer a way of exchanging secret and encrypted information in an untypical mechanism where communicating parties can only interpret the secret message.
generation approach presented in this paper. 2.2 Steganography ... Current research in steganography is not only cen- ... 35:26565-26577, 2022. 20Yan Ke, Min-qing Zhang, Jia Liu, Ting-ting Su, and Xiao-yuan Yang. Generative steganog-raphy with kerckhoffs' principle. Multimedia Tools and Applications, 78(10):13805-13818,
We reviewed several articles on steganography methods in this research paper. Steganography is an ancient and robust technique used in a variety of applications, including confidential data sharing. When used in conjunction with cryptography, steganography becomes more powerful. ... Cite this paper. Paul, T., Ghosh, S., Majumder, A. (2022). A ...
Steganography, the art and science of concealing messages within other data, has a rich history spanning centuries. In this review paper, we delve into various aspects of steganography, exploring ...
Image steganography refers to hiding information i.e. text, images or audio files in another image or video files. The current project aims to use steganography for an image with another image ...
Text steganography is the art and science of concealing hidden messages inside ordinary text without raising red flags. It's an intriguing field. Because of the increasing dependence on digital communication and the urgent need for secure and confidential information transfer, text steganography has attracted a lot of attention as a dependable means of establishing covert communication and ...
Section 2 presents the state of the art of neural style transfer and deep learning-based image steganography technologies. Section 3 presents the proposed image steganography frameworks for neural style transfer in detail. Then, Section 4 carries out the experiment comparison and analysis. Section 5 gives the conclusion and future research ...
DOI: 10.23919/cje.2022.00.366 Corpus ID: 270182941; IP-Pealing: A Robust Network Flow Watermarking Method Based on IP Packet Sequence @article{Feng2024IPPealingAR, title={IP-Pealing: A Robust Network Flow Watermarking Method Based on IP Packet Sequence}, author={Wangxin Feng and Xiangyang Luo and Tengyao Li and Chunfang Yang}, journal={Chinese Journal of Electronics}, year={2024}, url={https ...
Steganography is the art of concealing data into any multimedia for covert communication [].Steganography can be divided into many types based on the cover object used to attain security, like text, image, audio, video, and network [26,27,28,29,30,31].Further, the steganography can be divided into two domains based on the techniques used to hide data in any multimedia, i.e., spatial domain ...
2022 Research Week Awards 2023 Research Week Awards 2024 Research Week Awards. Home; 2024 Research Week Awards; Graduate Oral Presentations; Cryptology for Christ: Steganography, Evangelism, and Closed Access Countries ... Digital steganography is rooted in the ancient practice of hiding messages and has evolved dramatically with technology. In ...
Data security is essential for information distribution in the world of information and communication tools today. Data concealing has grown more and more important with the rise of intense multimedia sharing and secret discussions. Steganography is a method of obscuring data in a way that makes it nearly impossible to find. According to a recent study, when the networks between the layers ...
203-436-4842. The Baltic nation of Estonia is No. 1 in the 2024 rankings, while Denmark, one of the top ranked countries in the 2022 EPI dropped to 10th place, highlighting the challenges of reducing emissions in hard-to-decarbonize industries. Meanwhile, "paper parks" are proving a global challenge to international biodiversity commitments.
Steganography, a technique for hiding the trace of communication, can conceal confidential messages into various digital carriers such as images [1, 2], texts [], videos [], etc. Voice over Internet Protocol (VoIP) has been recognized as a suitable carrier for real-time steganography [5, 6].The enormous payloads and popularity of VoIP provide extraordinary information embedding volume and ...