Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 27 May 2024

Using machine learning algorithms to enhance IoT system security
- Hosam El-Sofany 1 ,
- Samir A. El-Seoud 2 ,
- Omar H. Karam 2 &
- Belgacem Bouallegue 1 , 3
Scientific Reports volume 14 , Article number: 12077 ( 2024 ) Cite this article
343 Accesses
9 Altmetric
Metrics details
- Computer science
- Information technology
The term “Internet of Things” (IoT) refers to a system of networked computing devices that may work and communicate with one another without direct human intervention. It is one of the most exciting areas of computing nowadays, with its applications in multiple sectors like cities, homes, wearable equipment, critical infrastructure, hospitals, and transportation. The security issues surrounding IoT devices increase as they expand. To address these issues, this study presents a novel model for enhancing the security of IoT systems using machine learning (ML) classifiers. The proposed approach analyzes recent technologies, security, intelligent solutions, and vulnerabilities in ML IoT-based intelligent systems as an essential technology to improve IoT security. The study illustrates the benefits and limitations of applying ML in an IoT environment and provides a security model based on ML that manages autonomously the rising number of security issues related to the IoT domain. The paper proposes an ML-based security model that autonomously handles the growing number of security issues associated with the IoT domain. This research made a significant contribution by developing a cyberattack detection solution for IoT devices using ML. The study used seven ML algorithms to identify the most accurate classifiers for their AI-based reaction agent’s implementation phase, which can identify attack activities and patterns in networks connected to the IoT. The study used seven ML algorithms to identify the most accurate classifiers for their AI-based reaction agent’s implementation phase, which can identify attack activities and patterns in networks connected to the IoT. Compared to previous research, the proposed approach achieved a 99.9% accuracy, a 99.8% detection average, a 99.9 F1 score, and a perfect AUC score of 1. The study highlights that the proposed approach outperforms earlier machine learning-based models in terms of both execution speed and accuracy. The study illustrates that the suggested approach outperforms previous machine learning-based models in both execution time and accuracy.
Similar content being viewed by others
A guide to artificial intelligence for cancer researchers
Impact of artificial intelligence on human loss in decision making, laziness and safety in education
Explainable chemical artificial intelligence from accurate machine learning of real-space chemical descriptors
Introduction.
Technology such as cloud computing, cloud edge, and software-defined networking (SDN) have significantly increased users’ reliance on their infrastructure. Consequently, the number of threats faced by these users has also risen. As a result, security management during IoT system development has become increasingly difficult and complex. The IoT can be described as an electrical network that connects physical objects, such as sensors, with software that makes it possible for them to exchange, examine, and gather data. Various sectors use IoT applications, including the military, personal healthcare, household appliances, and agriculture production infrastructure 1 . This research attempts to achieve the Sustainable Cities and Communities Goal (SDG 11) included in the UN Sustainable Development Goals (SDG) 2 . Addressing the challenges and finding solutions for the IoT require considering a wide range of factors. It is crucial for solutions to encompass the entire system to provide comprehensive security. However, most IoT devices operate without human interaction, making them susceptible to unauthorized access. Therefore, it is imperative to enhance the existing security techniques to safeguard the IoT environment 3 . ML techniques can offer potential alternatives for securing IoT systems, including:
Intrusion detection and prevention ML can create IoT intrusion detection and prevention (IDPS) tools. ML algorithms can analyze network traffic, device logs, and other data related to known attacks or suspicious activity.
Anomaly detection ML algorithms can learn IoT device behavior and network interactions through anomaly detection. ML models can detect unusual IoT activity using real-time data. This helps detect security breaches like unauthorized access or malicious acts and prompt appropriate responses.
Threat intelligence and prediction ML can analyze big security data sets and provide insights. ML models may discover new risks, anticipate attack pathways, and give actionable insight to IoT security practitioners by analyzing data from security feeds, vulnerability databases, and public forums.
Firmware and software vulnerability analysis Researchers may use ML to analyze IoT firmware and software for vulnerabilities. ML models may discover IoT device firmware and software security problems by training on known vulnerabilities and coding patterns. This helps manufacturers repair vulnerabilities before deployment or deliver security patches quickly.
Behavior-based authentication ML algorithms can learn IoT devices and user behavior. By analyzing device usage patterns, ML models may create predictable behavior profiles. ML can require extra authentication or warn for illegal access when a device or user deviates considerably from the learned profile.
Data privacy and encryption ML can assist in ensuring data privacy and security in IoT systems. ML algorithms may provide homomorphic encryption, which permits calculations on encrypted data. ML can perform data anonymization and de-identification to safeguard sensitive data and facilitate analysis and insights.
In general, ML techniques must be used in conjunction with other security measures to offer complete security for IoT systems. ML algorithms and methods have been applied in various tasks, including machine translation, regression, clustering, transcription, detection, classification, probability mass function, sampling, and estimation of probability density. Numerous applications utilize ML techniques and algorithms, such as spam identification, image and video recognition, customer segmentation, sentiment analysis, demand forecasting, virtual personal assistants, detection of fraudulent transactions, automation of customer service, authentication, malware detection, and speech recognition 4 .
In addition, IoT and ML integration can enhance the devices of IoT levels of security, thereby increasing their reliability and accessibility. ML’s advanced data exploration methods play an important role in elevating IoT security from only providing security for communication devices to intelligent systems with a high level of security 5 .
ML-based models have emerged as a response to cyberattacks within the IoT ecosystem, and the combination of Deep Learning (DL) and ML approaches represents a novel and significant development that requires careful consideration. Numerous uses, including wearable smart gadgets, smart homes, healthcare, and Vehicular Area Networks (VANET), necessitate the implementation of robust security measures to safeguard user privacy and personal information. The successful utilization of IoT is evident across multiple sectors of modern life 6 . By 2025, we expect that the IoT will have an economic effect of $2.70–$6.20 trillion. Research findings indicate that ML and DL techniques are key drivers of automation in knowledge work, thereby contributing to the economic impact. There have been many recent technological advancements that are shaping our world in significant ways. By 2025, we expect an estimated $5.2–$6.7 trillion in annual economic effects from knowledge labor automation 7 .
This research study addresses the vulnerabilities in IoT systems by presenting a novel ML-based security model. The proposed approach aims to address the increasing security concerns associated with the Internet of Things. The study analyzes recent technologies, security, intelligent solutions, and vulnerabilities in IoT-based smart systems that utilize ML as a crucial technology to enhance IoT security. The paper provides a detailed analysis of using ML technologies to improve IoT systems’ security and highlights the benefits and limitations of applying ML in an IoT environment. When compared to current ML-based models, the proposed approach outperforms them in both accuracy and execution time, making it an ideal option for improving the security of IoT systems. The creation of a novel ML-based security model, which can enhance the effectiveness of cybersecurity systems and IoT infrastructure, is the contribution of the study. The proposed model can keep threat knowledge databases up to date, analyze network traffic, and protect IoT systems from newly detected attacks by drawing on prior knowledge of cyber threats.
The study comprises five sections: “ Related works ” section presents a summary of some previous research. “ IoT, security, and ML ” section introduces the Internet of Things’ security and ML aspects. “ The proposed IoT framework architecture ” section presents the proposed IoT framework architecture, providing detailed information and focusing on its performance evaluation. “ Result evaluation and discussion ” section provides an evaluation of the outcomes and compares them with other similar systems. We achieve this by utilizing appropriate datasets, methodologies, and classifiers. “ Conclusions and upcoming work ” section concludes the discussion and outlines future research directions.
Related works
The idea of security in IoT devices has been recently articulated in studies that analyze the security needs at several layers of architecture, such as the application, cloud, network, data, and physical layers. Layers have examined potential vulnerabilities and attacks against IoT devices, classified IoT attacks, and explained layer-based security requirements 8 . On the other hand, industrial IoT (IIoT) networks are vulnerable to cyberattacks. Developing IDS is important to secure IIoT networks. The authors presented three DL models, LSTM, CNN, and a hybrid, to identify IIoT network breaches 9 . The researchers used the UNSW-NB15 and X-IIoTID datasets to identify normal and abnormal data, then compared them to other research using multi-class, and binary classification. The hybrid LSTM + CNN model has the greatest intrusion detection accuracy in both datasets. The researchers also assessed the implemented models’ accuracy in detecting attack types in the datasets 9 .
In Ref. 10 , the authors introduced the hybrid synchronous-asynchronous privacy-preserving federated technique. The federated paradigm eliminates FL-enabled NG-IoT setup issues and protects all its pieces with Two-Trapdoor Homomorphic Encryption. The server protocol blocks irregular users. The asynchronous hybrid LEGATO algorithm reduces user dropout. By sharing data, they assist data-poor consumers. In the presented model, security analysis ensures federated correctness, auditing, and PP. Their performance evaluation showed higher functionality, accuracy, and reduced system overheads than peer efforts. For medical devices, the authors of Ref. 11 developed an auditable privacy-preserving federated learning (AP2FL) method. By utilizing Trusted Execution Environments (TEEs), AP2FL reduces issues about data leakage during training and aggregation activities on both servers and clients. The authors of this study aggregated user updates and found data similarities for non-IID data using Active Personalized Federated Learning (ActPerFL) and Batch Normalization (BN).
In Ref. 12 , the authors addressed two major consumer IoT threat detection issues. First, the authors addressed FL’s unfixed issue: stringent client validation. They solved this using quantum-centric registration and authentication, ensuring strict client validation in FL. FL client model weight protection is the second problem. They suggested adding additive homomorphic encryption to their model to protect FL participants’ privacy without sacrificing computational speed. This technique obtained an average accuracy of 94.93% on the N-baIoT dataset and 91.93% on the Edge-IIoTset dataset, demonstrating consistent and resilient performance across varied client settings.
Utilizing a semi-deep learning approach, SteelEye was created in Ref. 13 to precisely detect and assign responsibility for cyberattacks that occur at the application layer in industrial control systems. The proposed model uses category boosting and a diverse range of variables to provide precise cyber-attack detection and attack attribution. SteelEye demonstrated superior performance in terms of accuracy, precision, recall, and Fl-score compared to state-of-the-art cyber-attack detection and attribution systems.
In Ref. 14 , researchers developed a fuzzy DL model, an enhanced adaptive neuro-fuzzy inference system (ANFIS), fuzzy matching (FM), and a fuzzy control system to detect network risks. Our fuzzy DL finds robust nonlinear aggregation using the fuzzy Choquet integral. Metaheuristics optimized ANFIS attack detection’s error function. FM verifies transactions to detect blockchain fraud and boost efficiency. The first safe, intelligent fuzzy blockchain architecture, which evaluates IoT security threats and uncertainties, enables blockchain layer decision-making and transaction approval. Tests show that the blockchain layer’s throughput and latency can reveal threats to blockchain and IoT. Recall, accuracy, precision, and F1-score are important for the intelligent fuzzy layer. In blockchain-based IoT networks, the FCS model for threat detection was also shown to be reliable.
In Ref. 15 , the study examined Federated Learning (FL) privacy measurement to determine its efficacy in securing sensitive data during AI and ML model training. While FL promises to safeguard privacy during model training, its proper implementation is crucial. Evaluation of FL privacy measurement metrics and methodologies can identify gaps in existing systems and suggest novel privacy enhancement strategies. Thus, FL needs full research on “privacy measurement and metrics” to thrive. The survey critically assessed FL privacy measurement found research gaps, and suggested further study. The research also included a case study that assessed privacy methods in an FL situation. The research concluded with a plan to improve FL privacy via quantum computing and trusted execution environments.
IoT, security, and ML
Iot attacks and security vulnerabilities.
Critical obstacles standing in the way of future attempts to see IoT fully accepted in society are security flaws and vulnerabilities. Everyday IoT operations are successfully managed by security concerns. In contrast, they have a centralized structure that results in several vulnerable points that may be attacked. For example, unpatched vulnerabilities in IoT devices are a security concern due to outdated software and manual updates. Weak authentication in IoT devices is a significant issue due to easy-to-identify passwords. Attackers commonly target vulnerable Application Programming Interfaces (APIs) in IoT devices using code injections, a man-in-the-middle (MiTM), and Distributed Denial-of-Service (DDoS) 16 . Unpatched IoT devices pose risks to users, including data theft and physical harm. IoT devices store sensitive data, making them vulnerable to theft. In the medical field, weak security in devices such as heart monitors and pacemakers can impede medical treatment. Figure 1 illustrates the types of IoT attacks (threats) 17 . Unsecured IoT devices can be taken over and used in botnets, leading to cyberattacks such as DDoS, spam, and phishing. The Mirai software in 2016 encouraged criminals to develop extensive botnets for IoT devices, leading to unprecedented attacks. Malware can easily exploit weak security safeguards in IoT devices 18 . Because there are so many connected devices, it may be difficult to ensure IoT device security. Users must follow fundamental security practices, such as changing default passwords and prohibiting unauthorized remote access 19 . Manufacturers and vendors must invest in securing IoT tool managers by proactively notifying users about outdated software, enforcing strong password management, disabling remote access for unnecessary functions, establishing strict API access control, and protecting command-and-control (C&C) servers from attacks.
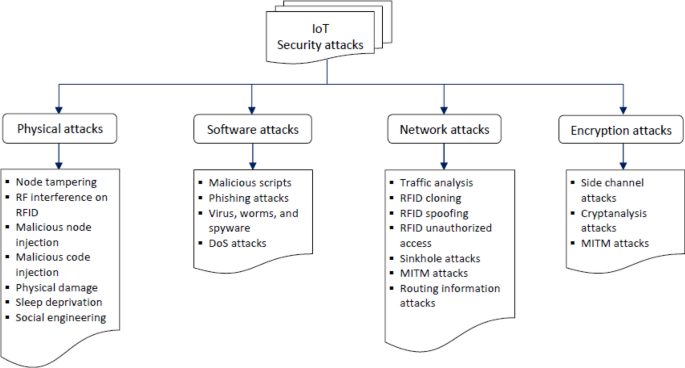
Types of IoT attacks.
IoT applications’ support security issues
Security is a major requirement for almost all IoT applications. IoT applications are expanding quickly and have impacted current industries. Even though operators supported some applications with the current technologies of networks, others required greater security support from the IoT-based technologies they use 20 . The IoT has several uses, including home automation and smart buildings and cities. Security measures can enhance home security, but unauthorized users may damage the owner’s property. Smart applications can threaten people’s privacy, even if they are meant to raise their standard of living. Governments are encouraging the creation of intelligent cities, but the safety of citizens’ personal information may be at risk 21 , 22 .
Retail extensively uses the IoT to improve warehouse restocking and create smart shopping applications. Augmented reality applications enable offline retailers to try online shopping. However, security issues have plagued IoT apps implemented by retail businesses, leading to financial losses for both clients and companies. Hackers may access IoT apps to provide false details regarding goods and steal personal information 23 . Smart agriculture techniques include selective irrigation, soil hydration monitoring, and temperature and moisture regulation. Smart technologies can result in larger crops and prevent the growth of mold and other contaminants. IoT apps monitor farm animals’ activity and health, but compromised agriculture applications can lead to the theft of animals and damage to crops. Intelligent grids and automated metering use smart meters to monitor and record storage tanks, improve solar system performance, and track water pressure. However, smart meters are more susceptible to cyber and physical threats than traditional meters. Advanced Metering Infrastructure (AMI) connects all electrical appliances in a house to smart meters, enabling communication and security networks to monitor consumption and costs. Adversary incursions into such systems might change the data obtained, costing consumers or service providers money 24 . IoT apps in security and emergency sectors limit access to restricted areas and identify harmful gas leaks. Security measures protect confidential information and sensitive products. However, compromised security in IoT apps can have disastrous consequences, such as criminals accessing banned areas or erroneous radiation level alerts leading to serious illnesses 25 .
IoT security attacks based on each layer
IoT devices’ architecture includes five layers: perception, network Layer, middleware (information processing), application, and business (system management). Figure 2 illustrates how the development of IoT ecosystems has changed from a three-layer to a five-layer approach. IoT threats can be physical or cyber, with cyberattacks being passive or active. IoT devices can be physically damaged by attacks, and various IoT security attacks based on each tier are described 26 . Perception layer attacks are intrusions on IoT physical components, for example, devices and sensors. Some of the typical perception layer attacks are as follows:
Botnets Devices get infected by malware called botnets, like Mirai. The bot’s main objectives are to infect improperly configured devices and assault a target server when given the order by a botmaster 27 .
Sleep deprivation attack Attacks from sleep deprivation are linked to battery-powered sensor nodes and equipment. Keeping the machines and devices awake for a long time is the aim of the sleep disturbances assault 28 .
Node tampering and jamming Node tampering attacks are launched by querying the machines to acquire accessibility to and change confidential data, like routing data tables and cryptographic shared keys. A node jamming assault, on the other hand, occurs when perpetrators breach the radio frequencies of wireless sensor nodes 29 .
Eavesdropping By allowing the attacker to hear the information being transferred across a private channel, eavesdropping is an exploit that puts the secrecy of a message in danger 30 .
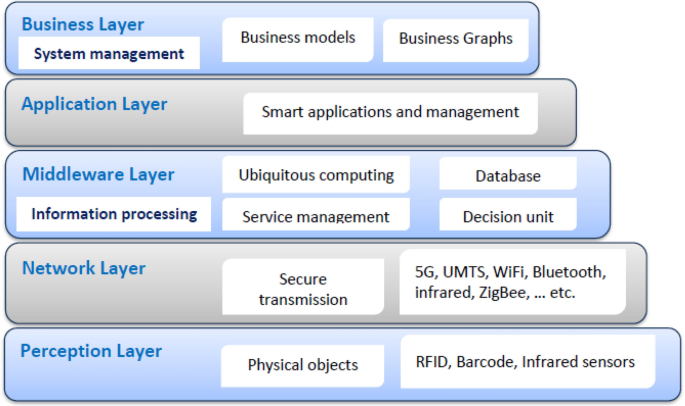
IoT ecosystem five-layer architecture.
These attacks can harm most or all IoT system physical components and can be prevented by implementing appropriate security measures.
Network layer attacks aim to interfere with the IoT space’s network components, which include routers, bridges, and others. The following are some examples of network layer attacks:
Man-in-the-middle (MiTM) This threat involves an attacker posing as a part of the communication networks and directly connecting to another user device 31 .
Denial of service (DoS) Attackers who use DoS techniques generate numerous pointless requests, making it challenging for the user to access and utilize IoT gadgets.
Routing attacks Malicious nodes engage in routing-type assaults to block routing functionality or to perform DoS activities.
Middleware attacks An assault on middleware directly targets the IoT system’s middleware components. Cloud-based attacks, breaches of authentication, and signature packaging attacks are the three most common forms of middleware attacks.
These attacks can be prevented by implementing appropriate security measures.
Smart cities, smart grids, and smart homes are some examples of apps included in the application layer. An application layer attack relates to the security flaws in IoT apps. Here are a few examples of application layer attacks 32 :
Malware The use of executable software by attackers to interfere with network equipment is known as malware.
Phishing attack This is a sort of breach that seeks to get users’ usernames and passwords by making them appear to be reliable entities.
Code injection attack The main goal of an injector attack into a program or script code is to inject an executable code into the memory space of the breached process.
Appropriate security measures can help prevent these attacks as well.
Overview of ML within the IoT
IoT systems are susceptible to hackers because they lack clear boundaries and new devices are always being introduced. There is a possibility to create algorithms that can learn about the behavior of objects and other IoT components inside such large networks by utilizing ML and DL approaches. By using these techniques to predict a system’s expected behavior based on past experiences, security protocols can be developed to a significant extent.
ML techniques and their applications in IoT
ML techniques play an essential role in analyzing and extracting insights from the massive amount of data produced by IoT devices. Here are some popular ML techniques and their applications in the IoT:
Supervised learning This type of algorithm learns from labeled training data. Various applications in the IoT can utilize supervised learning, such as:
Anomaly detection By training ML models to recognize abnormal patterns or behaviors in IoT sensor data, we can identify anomalies or potential security breaches.
Predictive maintenance By analyzing past sensor data, supervised learning algorithms can predict equipment failures or maintenance requirements. This enables the implementation of proactive maintenance measures, leading to a decrease in downtime.
Environmental monitoring ML models can learn from sensor data to predict environmental conditions like air quality, water pollution, or weather patterns.
Unsupervised learning Unsupervised learning algorithms extract patterns or structures from unlabeled data without predefined categories. In IoT, unsupervised learning techniques find applications such as:
Clustering ML models can group similar IoT devices or data points, facilitating resource allocation, load balancing, or identifying network segments.
Dimensionality reduction Unsupervised learning techniques like autoencoders or principal component analysis (PCA) make it easier to analyze IoT data.
Behavioral profiling Unsupervised learning can help in understanding the normal behavior of IoT devices or users, enabling the detection of deviations or anomalies.
Reinforcement learning Reinforcement learning aims to maximize a reward by training an agent how to interact with its environment and use feedback to improve its performance. The following applications use reinforcement learning on the IoT.
Energy management ML models can learn optimal energy allocation strategies for IoT devices to maximize energy efficiency or minimize costs.
Adaptive IoT systems Reinforcement learning can be used to optimize IoT system parameters or configurations based on real-time feedback and changing conditions.
Smart resource allocation ML models can learn to allocate resources dynamically based on demand, user preferences, or changing network conditions.
Deep learning DL algorithms, especially deep neural networks, excel at processing complex data and extracting high-level features. In IoT, DL has various applications, including:
Image and video analysis DL models can analyze images or video streams from IoT devices, enabling applications like object detection, surveillance, or facial recognition.
Natural language processing (NLP) DL techniques can process and understand text or voice data from IoT devices, enabling voice assistants, sentiment analysis, or chatbots.
Time-series analysis DL models, such as long short-term memory (LSTM) or recurrent neural networks (RNNs) networks, can analyze time-series sensor datasets for predicting future values or detecting anomalies.
ML for IoT security
ML is a promising approach for defending IoT devices against cyberattacks. It offers a unique strategy for thwarting assaults and provides several benefits, including designing sensor-dependent systems, providing real-time evaluation, boosting security, reducing the flowing data, and utilizing the large quantity of data on the Internet for all individualized user applications. The influence of ML on the IoT’s development is crucial for enhancing practical smart applications. ML has garnered scientific attention recently and is being applied to IoT security as well as the growth of numerous other industries. Effective data exploration methods for identifying “abnormal” and “normal” IoT components and behavior of devices inside the IoT ecosystem are DL and ML. Consequently, to transform the security of IoT systems from enabling secure Device-to-Device (D2D) connectivity to delivering intelligence security-based systems, ML/DL techniques are needed 33 .
Enhancing IoT security using the algorithms of ML
ML approaches, such as ensemble learning, k-means clustering, Random Forest (RF), Association Rule (AR), Decision Tree (DT), AdaBoost, Support Vector Machine (SVM), XGBoost, and K-Nearest Neighbor (KNN), have benefits, drawbacks, and applications in IoT security. DT, a natural ML technique, resembles a tree, with branches and leaves that serve as nodes in the model. In classification, SVM maximizes the distance between the closest points and the hyperplane to classify the class 34 . In identifying DDoS attacks, RF performs better than SVM, ANN, and KNN. A Principal Component Analysis (PCA) with KNN and classifier softmax has been suggested in Ref. 35 to develop a system that has great time efficiency while still having cheap computation, which enables it to be employed in IoT real-time situations.
Limitations of applying ML in networks of IoT
Using ML approaches for IoT networks has limitations because of dedicated processing power and IoT machines’ limited energy. IoT networks generate data with a variety of structures, forms, and meanings, and traditional ML algorithms are ill-equipped to handle these massive, continuous streams of real-time data. The semantic and syntactic variability in this data is evident, particularly in the case of huge data, and heterogeneous datasets with unique features pose problems for effective and uniform generalization. ML assumes that all the dataset’s statistical attributes are constant, and the data must first go through preprocessing and cleaning before fitting into a particular model. However, in the real world, data comes from multiple nodes and has different representations with variant formatting, which presents challenges for ML algorithms 36 .
The proposed IoT framework architecture
Fundamental concepts and methodologies.
Software defined networking (SDN) SDN is a cutting-edge networking model that separates the data plane from the control plane. This improves network programmability, adaptability, and management, and it also enables external applications to control how the network behaves. The SDN’s three basic components are communication interfaces, controllers, and switches. Cognitive judgments were imposed on the switches by a central authority (i.e., the SDN controller). It keeps the state of the system up to date by changing the flow rules of the appropriate switches. IoT systems’ success and viability depend on SDN adoption. To handle IoT networks’ huge data flows and minimize bottlenecks, SDN’s routing traffic intelligence and improving usage of the network are essential. This connection may be applied at many layers in the IoT network, including enabling end-to-end IoT traffic control, core, access, and cloud networks (where creation, processing, and providing of data takes place). SDN also enhances IoT security, for example, tenant traffic isolation, tracking centralized security based on the network’s global view, and dropping of traffic at the edge of the network to ward off malignant traffic.
Network function virtualization (NFV) Virtualization in network contexts is called network function virtualization (NFV). NFV separates software from hardware, adding value and reducing capital and operational costs. The European Telecommunications Standards Institute (ETSI) has standardized this approach’s novel design for use in telecommunications systems. The architecture of ETSI NFV has three basic components:
Virtualization infrastructure Virtualization technologies are found in this layer in addition to needed hardware that offers abstractions to resources for Virtualized Network Functions (VNFs). Cloud platforms handle networking, data processing, and storage.
Virtual network functions VNFs replace specific hardware equipment for network functions. They scale and cost-effectively handle network services across numerous settings.
Management and orchestration Block of Management and orchestration (MANO) is a component of ETSI NFV and is responsible for communicating with the VNF layer and the infrastructure layer. It manages monitoring VNFs, configuration, instantiation, and global resource allocation.
The ecosystem of the IoT is given value by virtualized resources of the network, explaining its variability and quick expansion. NFV and SDN can offer advanced virtual monitoring tools like Deep Packet Inspectors (DPIs) and Intrusion Detection Systems (IDSs). They can provide scalable network security equipment, as well as deploy and configure on-demand components, such as authentication systems and firewalls, to defend against attacks that have been identified by monitoring agents. When processing for security is offloaded from resource-constrained IoT devices to virtual instances, the resulting boost in efficiency and drop in energy consumption clear the way for other useful applications to be implemented. IoT security hardware lacks NFV’s flexibility and enhanced security. NFV’s value-added features improved IoT security, even if they did not replace current solutions.
Machine learning (ML) ML is an algorithmic artificial intelligence (AI) discipline that uses techniques to give intelligence to devices and computers. ML methods include unsupervised , supervised , and reinforcement learning. They are typically used in the security of networks. ML is used to specify and precisely identify the security regulations of the data plane. In mitigating a sort of attack given by tagging traffic networks or creating policies to access control, the difficulty is to fine-tune key security protocol parameters. Moreover, several ML approaches may prevent IoT attacks.
Supervised learning In algorithms of supervised learning, the model output is known even though the underlying relationships between the data are unknown. This model is often trained with two datasets: One for “testing” and “evaluating” the driven model and another to “learn” from. Within the context of security, it is common to compare a suspected attack to a database of known threats.
Unsupervised learning Data is not pre-labeled, and the model is unknown. It sets it apart from supervised learning. It aims to classify and find patterns in the data.
Reinforcement learning It looks at problems and methods to enhance its model through study. It employs trial and error and incentive mechanisms to train its models in a novel way. A metric known as the “value function” is determined by tracking the output’s success and applying the reward to its formula. This value tells the model how well it is evaluated, so it may adjust its behavior accordingly.
The proposed security model
Figure 3 illustrates the proposed ML-based security model to address IoT security issues based on NFV, SDN, and ML technologies. The figure displays the security component framework and interconnections, whereas Fig. 4 demonstrates the closed-loop automation phases, starting with detection and monitoring and ending with preventing threats. To ensure complete security, the system suggested integrating the enablers and countermeasures from the previous subsections. This framework enforces security policies beginning with the design and concluding with the application and maintenance. Two primary framework levels are shown in Fig. 3 (i.e., security orchestration and security enforcement layers). The two layers and their closed-loop automation intercommunications to detect and prevent attacks are discussed below.
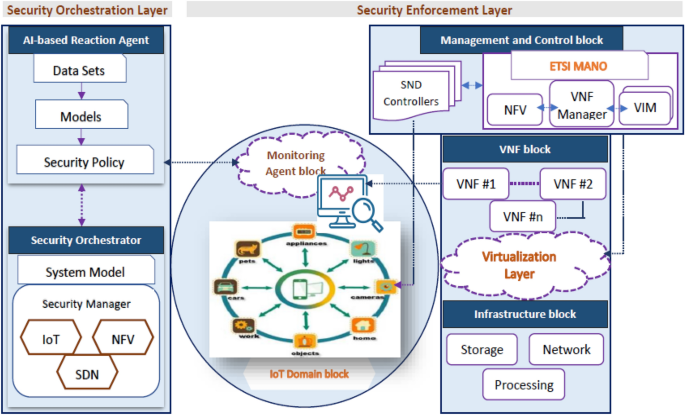
The proposed ML-based security model.
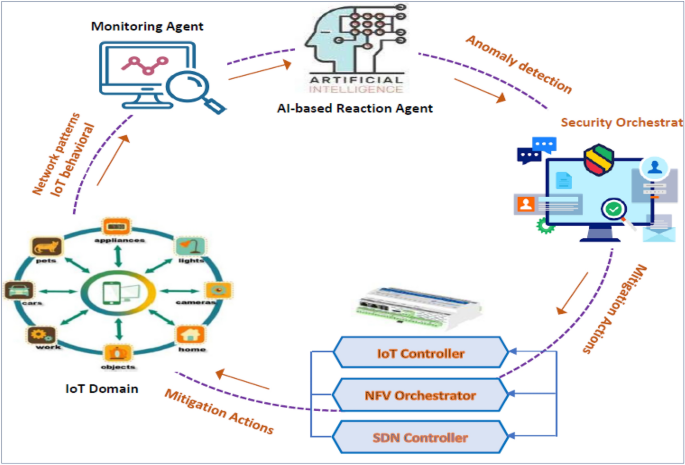
Automation with a closed loop, from detection to prevention.
Security enforcement layer Several VNFs implemented on many clouds, Physical Network Functions (PNFs), and edges facilitate interaction between IoT devices and end users. These network functions (PNFs and VNFs), end users, and IoT devices interact with each other over either a conventional or an SDN-based network. The research classifies attacks on the IoT as either internal or external . The internal attack is caused by compromised and malicious IoT devices, while the external attack is initiated from the end-user network and directed at the IoT domain. The external attack creates danger for the external network and/or other authorized IoT devices. Attacks would be primarily addressed at three levels: (1) IoT devices, via IoT controllers; (2) network, via SDN controllers; and (3) cloud, via an NFV orchestrator. By implementing VNF security and setting the interaction through SDN networking, the security framework features may be properly implemented within the IoT territory. The security enforcement plan was developed to match closely with ETSI and Open Networking Foundation (ONF) guidelines for NFV and SDN. As shown in Fig. 1 , the security enforcement mechanisms consist of five separate logical blocks.
Management and control block It analyzes the components required to manage NFV and SDN infrastructures. It uses SDN controllers and ETSI MANO stack modules for this. To implement efficient security functions, the SDN controllers and NFV orchestrator must work closely together as NFV is frequently used alongside SDN to alter programmatically the network based on policies and resources.
VNF block Taking into consideration the VNFs that have been implemented across the virtualization infrastructure to implement various network-based security measures, the threat and protection measures required by the rules of security will be met with a focus on the delivery of sophisticated VNF security (e.g., IDS/IPS, virtual firewalls, etc.).
Infrastructure block It includes every hardware component needed to construct an IaaS layer, including computers, storage devices, networks, and the software used to run them in a virtualized environment. In addition to the elements of the network that are in charge of transmitting traffic while adhering to the regulations that have been specified by the SDN controller, a set of security probes is included in this plane to gather data for use by the monitoring services.
Monitoring agents block Its primary duty is reporting network activity and IoT actions to identify and prevent various types of attacks. In the proposed model, the detection technique may make use of either network patterns or IoT misbehavior. Using SDN-enabled traffic mirroring, every bit of data that is being sent over the network can be seen. The Security Orchestration Plane hosts an AI-based response agent that receives logs from the monitoring agents describing malicious transactions.
The IoT domain block It refers to the interconnected system of cameras, sensors, appliances, and other physical objects that form the SDN. The proposed methodology considers the substantial risk these devices pose to data privacy and integrity, and it tries to enforce the security standards in this domain.
Security orchestration layer This layer has the task of setting up real-time rules of security depending on the current state of monitoring data and adjusting the policies dynamically based on their context. It is a novel part of the proposed framework that communicates with the security enforcement layer to request the necessary actions to be taken to enforce security regulations inside the IoT domain. Virtual security enablers must be created, configured, and monitored to deal with the present attack.
Figure 2 is a diagrammatic representation of the major cooperation that happens among various framework components. This study proposes a feedback automation mechanism control system consisting of an oversight agent, an AI-based reaction agent, and an orchestrator for security. The latter protects against dangers by utilizing an NFV orchestrator, SDN controller, and IoT controller (see Figs. 3 , 4 ).
AI-based reaction agent This part orders the security orchestrator to perform predetermined measures in response to an incident. This block, as shown in Fig. 4 , makes use of the information collected by the monitoring agent from IoT domains and the network. This part employs ML models that have been trained on network topologies and the actions of IoT devices to identify potential dangers. For the security orchestrator, these ML models will be able to prescribe the optimal template for policies of security. Figure 4 also shows how to identify security threats from observations of network patterns and/or IoT activities. The security orchestrator would then be informed of the discovered danger level (where every level from L1 to L5 belongs to a different predefined security policy). As shown in Fig. 4 , we developed an AI-based reaction agent that uses seven ML techniques to recognize IoT-related attack activities and/or patterns in a network. These techniques are Random Forest, Decision Tree, Naive Bayes, Backpropagation NN, XGBoost, AdaBoost, and Ensemble RF-BPNN.
Security orchestrator This part of closed-loop automation enforces the AI reaction agent’s security practices. It enforces IoT security regulations utilizing SDN and NFV with the control and management block. The security orchestrator instantiates, configures, and monitors virtual security devices, manipulates bad traffic through SDN, or directly controls IoT machines, like shutting off a hacked device.
We have addressed the IoT security threats using RF, NB, DT, NNs, XGBoost, AdaBoost, and Ensemble RF-BPNN, which involve leveraging ML algorithms to detect and mitigate potential risks. To highlight their effectiveness, we can compare some of these approaches to traditional security methods as follows:
RFs are an ensemble learning algorithm that combines multiple DTs to enhance accuracy and robustness. They applied to the proposed IoT security system as follows:
Ensemble construction RF consists of multiple DTs, each trained on a randomly selected subset of the training dataset. This randomness helps to reduce overfitting and increase generalization.
Classification When classifying new instances, each DT in the RF independently predicts the class. The last prediction depends on the majority vote or averaging of the individual tree predictions.
Decision trees (DTs) are a popular ML technique for classification and regression tasks. The proposed IoT security system uses a DT classifier to identify and address unique threats, and it works as follows:
Feature selection The first stage is to select relevant features from the IoT device data. These features can include network traffic patterns, device behavior, communication protocols, and more.
Training Using a labeled dataset, we train a DT classifier that contains instances of both normal and malicious behavior. The model learns to classify instances based on the selected features.
Detection Once trained, the DT can classify new instances as normal or malicious, depending on their feature values. If the DT classified an instance as malicious, it would take appropriate security measures, such as blocking network access or raising an alarm.
Neural networks NNs, particularly DL architectures, have gained significant popularity in various domains, including IoT security. Here’s how they can be used:
Multiple layers of interconnected nodes (neurons) form the architecture design of a neural network model. Each neuron applies a non-linear activation function to weighted inputs from the previous layer.
We train the neural network using a labeled dataset through a process known as backpropagation. To reduce the discrepancy between the expected and observed labels, we iteratively tweak the network’s biases and weights.
Prediction: Once trained, the neural network can classify new instances into different threat categories based on their input features.
Comparative analysis with traditional approaches Compared to traditional security approaches, such as rule-based systems or signature-based detection, ML techniques offer several advantages. Traditional methods rely on predefined rules or patterns, which might not be able to adapt to rapidly evolving threats. In contrast, ML methods can learn from data and adapt their behavior accordingly. They can detect anomalies, identify new attack patterns, and improve over time as they encounter new threats. However, traditional approaches often provide better interpretability and explainability.
Rule-based systems explicitly define security rules, making it easier for security analysts to understand and verify their behavior. However, ML models, especially complicated ones like neural networks, are black boxes, making their decision-making process difficult to comprehend.
In conclusion, ML techniques like DTs, RFs, XGBoost, AdaBoost, and neural networks provide powerful tools for addressing unique IoT security threats. They offer improved accuracy, adaptability, and the ability to handle complex and evolving attack patterns. However, they may trade off some interpretability compared to traditional security approaches. The approach is selected based on the specific requirements of the IoT security system and the trade-offs between accuracy, interpretability, and computational requirements.
Performance evaluation of the proposed model
The experimental methodology and analysis outcomes of the AI-based response agent are covered in this section. An AI-based response agent can identify potential threats by performing the following steps: (1) Evaluate network patterns. To identify various forms of network infiltration, the research presents a knowledge-based intrusion detection framework. (2) Examine the strange behaviors that have been seen in the IoT system. Here, attacks are uncovered through the investigation of strange actions taken by IoT devices. To appropriately categorize the degree of the attacks and select the right security solutions, the research has applied supervised learning algorithms. The AI-based reaction agent will employ many ML approaches, considering the appropriate inputs from the monitoring agents, to remove a specific attack.
Evaluating network patterns Intrusion system evaluation is the first stage in evaluating the framework’s effectiveness.
Several publicly available datasets, including the UNSW_NB15, IoT-23, DARPA, KDD 99, NSL-KDD, DEFCON, and balanced BoTNeT-IoT-L01 datasets, were used to build the proposed system (see the datasets link ( https://drive.google.com/drive/folders/1gjP-pQzFZsLh2QMsIa5GPhEh5etv9Jvc?usp=sharing )). These datasets contain information on IoT attacks in the form of (.csv) files. Table 1 shows the network traffic information from different IoT devices. Advantages of the NSL-KDD dataset compared with the initial KDD dataset: The train set does not contain duplicated data; therefore, classifiers are not biased toward more frequent records. BoTNeT-IoT-L01 is a recent dataset that consists of two Botnet assaults (Gafgyt and Mirai). Over a 10-s frame with a decay factor of (0.1), the mean, count, variance, radius, magnitude, correlation coefficient, and covariance were the seven statistical measures that were computed. The .csv file was used to extract four features: jitter, packet count, outbound packet size alone, and combined outbound and inbound packet size 37 . By computing three or more statistical measures for each of the four traits, a total of twenty-three features were obtained.
Furthermore, this study used the widely recognized NSL-KDD dataset as a benchmark. It served as a benchmark for assessing intrusion detection systems in this research. It is a much better version of dataset KDD 99 (see Table 2 ). The NSL-KDD dataset has over 21 distinct attack types, which serve as the foundation for the application of our proposed IDS model, such as teardrop, satan, rootkit, buffer-overflow, smurf DDoS, pod-dos, and Neptune-dos. The NSL-KDD dataset is primarily composed of preprocessed network traffic data. These data provide a more precise representation of the network traffic that occurs at present. There are two distinct collections of data inside the dataset: a set for testing and a set for training . Comparatively, the set of testing has around 23,000 records, whereas the training set contains approximately 125,000 records. Each entry in the dataset corresponds to a network connection and contains a set of 41 features, including the IP addresses of the source and destination, protocols, flags, and a label indicating whether the connection is normal or abnormal (anomalous). Each sample in the dataset corresponds to certain attacks as follows: DoS attacks, remote-to-local (R2L) attacks, user-to-root (U2R) attacks, and probing attacks 38 . There are many implementation tools available for analyzing IoT attack datasets, such as Wireshark, Snort, Zeek (formerly Bro), Jupyter Notebook, Python, and Weka. In this work, the researchers used Python programming and Weka data mining tools for ML and data analysis processing.
The proposed tools include a large collection of ML algorithms for classification, regression, clustering, and association rule mining, such as RF, NB, DT, NNs, XGBoost, AdaBoost, and Ensemble RF-BPNN, as well as tools for model evaluation and selection, including cross-validation and ROC analysis.
Certain ML algorithms are incapable of learning due to the wide range of features present in nature. The modeling process becomes more challenging when a feature is continuous. Hence, before constructing classification patterns, preprocessing is fundamental to optimize prediction accuracy. Specifically, a discretization technique is used to overcome this restriction. When applied to a continuous variable, the discretization data mining approach seeks to minimize the number of possible values by categorizing them into intervals. Two different kinds of discretization are discussed in the literature: (1) static variable discretization , in which variables are partitioned separately, and (2) dynamic variable discretization, in which all features are discretized concurrently 39 . The research discretized the attacks and then categorized them such that the research was left with only the most common types (UDP, Junk, Ack, and UDP plain from the balanced BoTNet-IoT-L01 dataset and DDoS, Probe, U2R, and R2L from NSL-KDD).
Metrics for comparing performance Choosing measures that can indicate the strength of an IDS is a major problem when evaluating an IDS. An IDS’s performance goes well beyond its classification results alone. Cost Per Example (CPE), precision, detection rate, and model accuracy are utilized to evaluate the effectiveness of the proposed system. When evaluating outcomes, the following metrics should be used in conjunction with one another 40 .
Equation ( 1 ) indicates Cost-Sensitive Classification (CSC) or CPE, where N is the total number of samples, CM refers to the classification’s Confusion Matrix algorithm, and C is the Cost Matrix (see Table 3 ) 41 .
Input data cleaning, feature extraction, and classification The research proposes a first method, which involves preparing the entire dataset and then categorizing it using a variety of techniques (Hoeffding Tree, RF, Bayes Net, and J48) as shown in Fig. 6 . Next, the research chooses the best classifier (algorithm) that generates a preferred accuracy (see Table 4 for the BoTNet-IoT-L01 dataset and Table 5 for the NSL-KDD dataset).
Backpropagation approach To investigate the multilayer neural net approach, the research utilized the capabilities of a backpropagation technique for learning. The research employed a multilayer neural network with three layers. The initial layer had 41 inputs, representing the features of the dataset. The final layer encompassed the classification responses, namely, U2L, U2R, Probe, DoS, and Normal. An extra hidden layer was incorporated to facilitate the learning process. This method uses 100 neurons and a single hidden layer. Experience has shown that the alternative hidden layer and neuron counts did not increase the mean squared error (MSE) (see Table 6 ).
Distributed classification module This module introduces a distributed categorization system in which the various types of attacks (DDoS, U2R, R2L, and Probe; UDP, UDP plain, Ack, and Junk) are all assigned to the Ensembled RF-BPNN algorithm. Finally, the AdaBoost method is used to combine the resulting models (see Table 7 ).
Result evaluation and discussion
The findings reported in Table 5 demonstrate both the accuracy rate and precision of the RF technique. Unfortunately, the results are not promising for either U2R or U2L attacks. There is a low misclassification rate (or CPE) and high accuracy when using J48 to identify attacks. When it comes to the accuracy required for U2R strikes, however, J48 falls short. Despite its consistent performance, the Hoeffding tree method has a low accuracy for U2R threats. Although it has a strong model accuracy, the Bayes Net method provides the lowest results, failing to identify the vast majority of U2R threats. As can be seen from Table 6 , the backpropagation process is generally as precise as its predecessors, if not somewhat more so. However, misclassification comes with a significant processing time penalty. AdaBoost, CPE, and detection rate produced a better detection accuracy model as shown in Table 7 .
The performance of ML algorithms used in the proposed system
A classification algorithm for IoT detection based on ensembles of backpropagation neural networks is trained on the BoTNet-IoT-L01 dataset (see Table 8 ). The novelty of the algorithm stems from the methodology employed for combining outputs of the backpropagation neural network ensembles. The backpropagation neural network Oracle 8i database tool is utilized to combine the ensemble outputs. As Fig. 5 shows, the neural network backpropagation Oracle is constructed with an RF algorithm that produces high classification accuracy and low classification error (see Table 4 ). The thresholds are not learned all at once in the RF model but rather hierarchically. The decrease in impurity will be enforced one directionally from the starting to the finishing index of the symbolic path; however, the research learned them simultaneously. The idea of hierarchical node splits will be represented by this one-directional impurity reduction. To do this, firstly, the research breaks up each node in the symbolic path into some votes for each class. Secondly, the research computes the impurity based on those votes. The third step is to gradually lower it by a certain amount using the Softmax activation method. Our proposed algorithm uses margin ranking loss as its objective function. It is important to maintain a minimum margin disparity between the intended result and the actual one. The margin difference is the ‘reduction in impurity’. The target is output shifted by one index to the right and the impurity at first split is initialized by the impurity of the batch (see Fig. 5 ).
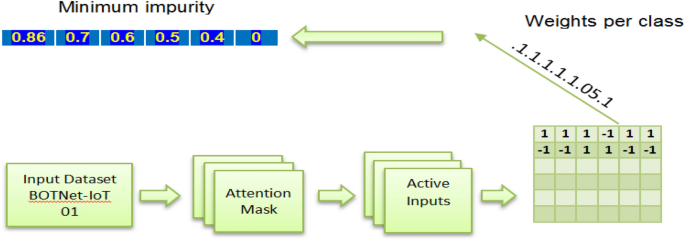
Architectural flow graph of the proposed RF with backpropagation NN (RF-BPNN).
When employing the AdaBoost classifier as a detection model, the research was limited to considering a single window size. Therefore, the research has successfully decreased the number of attributes in the BoTNeT-IoT-L01 dataset from 115 to 23. This significant decrease in the dimensionality of the dataset results in a significant acceleration of the detection process. Speaking of the BotNet-IoT dataset, the research discovered that just a small number of parameters have an important role in our system’s overall performance, and time windows of 10 s performed marginally better than those of shorter duration (see Fig. 6 ). Additionally, the research discovered that traffic heterogeneity greatly impacted RF classifier performance. However, when compared to the other classification algorithms, AdaBoost and RF-BPNN had the greatest and most stable results (see Table 7 ).
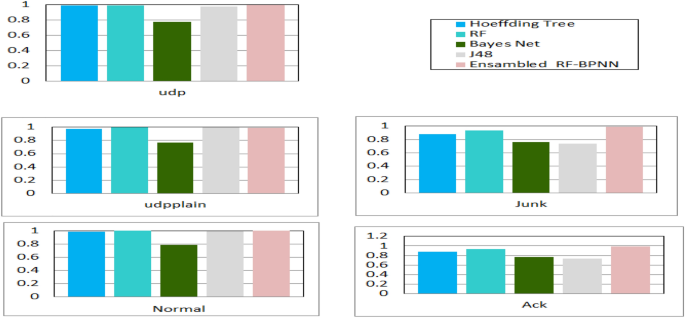
RF-BPNN accuracy evaluation for each attack type in the balanced BoTNet-IoT-L01 dataset.
Figure 7 shows the accuracy for detecting DoS , Fuzzers , Gene ric, Backdoor, and Exploit attacks in the UNSW_NB15 dataset using the RF classifier and SMOTE (where “ label” refers to the target variable and “attack_cat ” refers to the attack types).
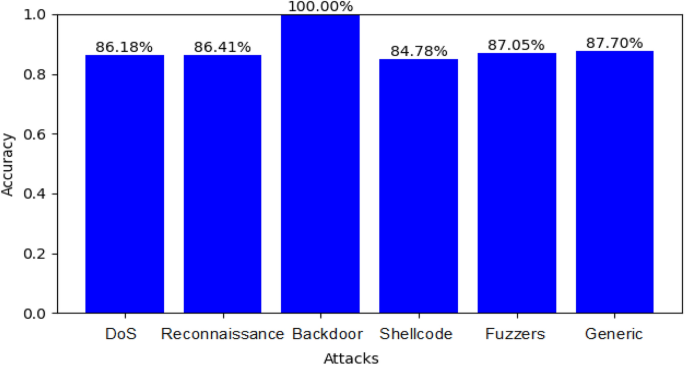
The accuracy for detecting some attacks in the UNSW_NB15 dataset, using RF Classifier.
Different experiments determine the system’s performance. Examining and validating each stage using the supplied classifiers is necessary to confirm the experimental results. Whether the classifier can discriminate across feature categories is also crucial. Accuracy, specificity, precision, recall, F1-score, and AUC measure the model’s performance and indicate the correctness of the system. Such measurements are based on the T P , F P , T N , and F N , as shown in Eqs. ( 2 ) to ( 6 ):
We use the following terms to describe the classification errors: true positive (TP) for attack instances, true negative (TN) for normal cases, false positive (FP) for incorrectly classified normal instances, and false negative (FN) for incorrectly classified attack instances.
Thus, the accuracy formula evaluates the classifier’s capacity to accurately categorize both positive and negative instances; precision denotes the classifier’s ability to avoid incorrectly labeling positive instances as negative, and specificity denotes its capacity to avoid incorrectly labeling negative instances as positive. In machine learning, recall is the rate at which a classifier can identify positive examples, whereas the F1-score is the weighted average of accuracy and recall.
Table 9 shows the performance of seven machine learning classifiers using the Synthetic Minority Oversampling Technique (SMOTE) on the UNSW_NB15 dataset. As you can see in Fig. 8 , the RF, XGBoost, AdaBoost, and Ensembled RF-BPNN classifiers did the best overall. They achieved an accuracy of 99.9%, an AUC of 1, and an F1 score of 99.9%. The Naive Bayes classifier, on the other hand, obtained the minimum accuracy and F1 score.
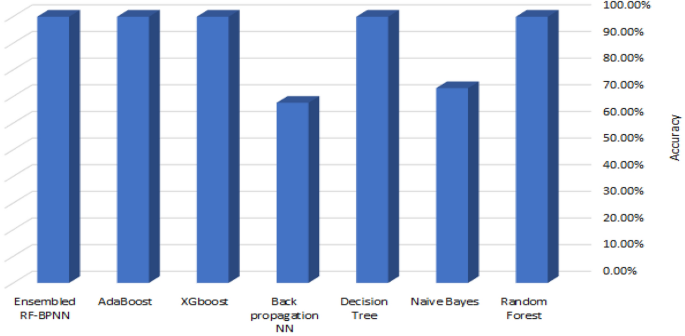
The accuracy of 7 ML algorithms using the UNSW-NB15 dataset and SMOTE.
Integration with existing IoT security frameworks and standards
The proposed model can integrate with existing IoT security frameworks and standards as follows:
Integration with IoT security frameworks The ML-based model can integrate with IoT security frameworks by aligning its functionalities with their security objectives and guidelines. For example:
The proposed model can integrate with existing authentication mechanisms recommended by IoT security frameworks, such as digital certificates or secure bootstrapping protocols. It can enhance device authentication by analyzing device behavior patterns and detecting anomalies that may indicate unauthorized access or compromised devices.
To align with data privacy requirements, the model can utilize encryption techniques and privacy-preserving algorithms recommended by the IoT security frameworks. It provides a guarantee of secure transmission and storage of data, protecting confidential information against illegal access.
The proposed model can integrate with existing access control mechanisms defined by IoT security frameworks. It can augment access control by providing intelligent decision-making capabilities based on historical data, user behavior analysis, or contextual information. This aids in assessing access requests and preventing unauthorized access to IoT resources.
Integration with IoT security standards The ML-based model can comply with IoT security standards by incorporating the required security controls and practices. For example:
The proposed model can align with ISO/IEC 27000 standards by implementing appropriate security controls for risk assessment, incident management, and data protection. It can follow the standards’ guidelines to ensure that the necessary security measures are in place.
The model can follow the NIST framework to enhance its threat detection and incident response capabilities.
Interoperability in IoT ecosystems By adhering to standard IoT protocols, data formats, and metadata standards, the ML-based model can ensure interoperability. For example:
The ML model can communicate with IoT devices and gateways using standard IoT protocols such as MQTT or CoAP, ensuring compatibility and interoperability across different devices and platforms.
The ML model can use commonly used data formats, such as JSON, or semantic data models, such as the Semantic Sensor Network (SSN) ontology, to facilitate seamless data sharing and interoperability with other components within the IoT ecosystem.
By integrating with existing IoT security frameworks and standards, the proposed model can enhance its adaptability and compatibility within IoT ecosystems. This integration allows the model to complement and enhance the existing security infrastructure, contributing to improved IoT security outcomes.
Comparisons with related systems
Table 10 highlights the proposed model’s performance outcomes by comparing it to previous systems. This study looked at existing literature and compared it to others based on standards, like the false positive rate (FPR), CPE, accuracy, and detection rate 38 , 38 , 39 , 40 , 41 , 42 , 43 , 44 , 45 , 47 . Through several experiments, the proposed system achieved the best evaluation metrics for accuracy, precision, detection rate, CPE, and lowest time complexity compared with previous solutions, as shown in Tables 10 and 11 .
Privacy concerns and data bias
The authors of this work have incorporated essential steps into the development and deployment of the proposed ML-based security model to effectively address privacy concerns and data bias, as well as ensure the technology’s ethical and responsible use within the IoT system.
The authors conducted a privacy impact assessment to determine if the proposed ML-based security model has any privacy issues or concerns.
To mitigate privacy concerns, the study implemented privacy-enhancing techniques . This process included data anonymization, encryption, differential privacy, or federated learning, which allows for training the proposed ML model without sharing raw data.
The study minimized the amount of personally identifiable information (PII) gathered and stored to reduce privacy risks. During the requirements engineering phase, we only collected the necessary data for the proposed machine learning-based security model, ensuring its safe storage and disposal when no longer required.
We implemented regular monitoring of the proposed ML model for potential biases in data and outcomes. Implementing a bias detection process is critical for identifying discriminatory patterns. We can take steps to mitigate detected biases , which may include adjusting training data, diversifying datasets, or utilizing bias correction algorithms.
Regularly monitor the proposed ML-based security model performance, including privacy aspects, and update it as needed to address emerging privacy concerns, mitigate biases, and ensure ongoing compliance with ethical standards.
Conclusions and upcoming work
This research introduces a new proposed ML-based security model to address the vulnerabilities in IoT systems. We designed the proposed model to autonomously handle the growing number of security problems associated with the IoT domain. This study analyzed the state-of-the-art security measures, intelligent solutions, and vulnerabilities in smart systems built on the IoT that make use of ML as a key technology for improving IoT security. The study illustrated the benefits and limitations of applying ML in an IoT environment and proposed a security model based on ML that can automatically address the rising concerns about high security in the IoT domain. The suggested method performs better in terms of accuracy and execution time than existing ML algorithms, which makes it a viable option for improving the security of IoT systems. This research evaluates the intrusion detection system using the BoTNet-IoT-L01 dataset. The research applied our proposed IDS model to a dataset that included more than 23 types of attacks. This study also utilized the NSL-KDD dataset to evaluate the intrusion detection mechanism and evaluated the proposed model in a real-world smart building environment. The presented ML-based model is found to have a good accuracy rate of 99.9% compared with previous research for improving IoT systems’ security. This paper’s contribution is the development of a novel ML-based security model that can improve the efficiency of cybersecurity systems and IoT infrastructure. The proposed model can keep threat knowledge databases up to date, analyze network traffic, and protect IoT systems from newly detected attacks by drawing on prior knowledge of cyber threats. This study presents a promising ML-based security approach to enhance IoT system security. However, future work and improvements remain possible. Expanding the dataset for the intrusion detection system evaluation could be one area of improvement. While the BoTNet-IoT-L01 and NSL-KDD datasets used in this study are comprehensive, they may not cover all possible types of attacks that could occur in an IoT environment. Therefore, our future research could focus on collecting and analyzing more diverse datasets to increase the performance of the proposed model. Furthermore, optimizing the proposed model’s execution time is crucial for real-world applications. Also, we could integrate the proposed model with other security solutions to create a more comprehensive and robust security system for IoT devices. Overall, the development of this novel ML-based security model is a significant contribution to the literature on ML security models and IoT security, and further work and improvements will continue to advance the field. Finally, the security analyst treats the AI-based IDS as a black box due to its inability to explain the decision-making process 48 . In our future work, we will expand our research by integrating blockchain-based AKA mechanisms with explainable artificial intelligence (XAI) to secure smart city-based consumer applications 49 . On the other hand, we can use the Shapley Additive Explanations (SHAP) mechanism to explain and interpret the prominent features that are most influential in the decision 50 .
Data availability
The corresponding author can provide the datasets used and/or analyzed in this work upon reasonable request.
Sharma, A., Singh, P. K. & Kumar, Y. An integrated fire detection system using IoT and image processing technique for smart cities. Sustain. Cities Soc. 61 , e4826 (2020).
Article Google Scholar
Sinan, K. SDG-11: Sustainable Cities and Communities. Emerging Technologies, Sustainable Development Goals Series 1st edn. (Springer, 2020).
Google Scholar
Hussain, F., Hussain, R., Hassan, S. A. & Hossain, E. Machine learning in IoT security: Current solutions and future challenges. IEEE Commun. Surv. Tutor. 22 (3), 1686–1721 (2020).
Bharati, S., Mondal, M. R. H., Podder, P. & Prasath, V. B. Federated learning: Applications, challenges and future directions. Int. J. Hybrid Intell. Syst. 18 (1–2), 19–35 (2022).
Shafiq, M., Tian, Z., Bashir, A. K., Du, X. & Guizani, M. Corrauc: A malicious BOT-IOT traffic detection method in IoT network using machine learning techniques. IEEE Internet Things J. 8 (5), 3242–3254 (2020).
Omolara, A. E. et al. The Internet of Things security: A survey encompassing unexplored areas and new insights. Comput. Secur. 112 , 102494 (2022).
Bharati, S., Podder, P., Mondal, M. R. H. & Paul, P. K. Applications and challenges of cloud integrated IoMT. In Cognitive Internet of Medical Things for Smart Healthcare 1st edn (eds Hassanien, A. E. et al. ) 67–85 (Springer, 2021).
Chapter Google Scholar
Özalp, A. N. et al . Layer-based examination of cyber-attacks in IoT. In 2022 International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA) (IEEE, 2022).
Altunay, H. C. & Albayrak, Z. A hybrid CNN+ LSTM—Based intrusion detection system for industrial IoT networks. Eng. Sci. Technol. Int. J. 38 , 101322 (2023).
Abbas, Y., Ali, D., Gautam, S., Hadis, K. & Reza, M. P. Hybrid privacy preserving federated learning against irregular users in next-generation Internet of Things. J. Syst. Archit. 148 , 103088 (2024).
Abbas, Y., Ali, D. & Gautam, S. AP2FL: Auditable privacy-preserving federated learning framework for electronics in healthcare. IEEE Trans. Consumer Electron. 99 , 1 (2023).
Danyal, N., Abbas, Y., Ali, D. & Gautam, S. Federated quantum-based privacy-preserving threat detection model for consumer Internet of Things. IEEE Trans. Consumer Electron. https://doi.org/10.1109/TCE.2024.3377550 (2024).
Sanaz, N., Behrouz, Z., Abbas, Y. & Ali, D. Steeleye: An application-layer attack detection and attribution model in industrial control systems using semi-deep learning. In 2021 18th International Conference on Privacy, Security and Trust (PST), IEEE Xplore (2021).
Abbas, Y., Ali, D., Reza, M. P., Gautam, S. & Hadis, K. Secure intelligent fuzzy blockchain framework: Effective threat detection in IoT networks. Comput. Ind. 144 , 103801 (2023).
Gopi, K. J., Abbas, Y., Reza, M. P. & Seyedamin, P. Exploring privacy measurement in federated learning. J. Supercomput. 1 , 43 (2023).
Otoum, Y. & Nayak, A. On securing IoT from deep learning perspective. In Proc. 2020 IEEE Symposium on Computers and Communications (ISCC) 1–7 (2020).
Butun, I., Sterberg, P. O. & Song, H. Security of the Internet of Things: Vulnerabilities, attacks, and countermeasures. IEEE Commun. Surv. Tutor. 22 (1), 616–644 (2020).
Tahsien, S. M., Karimipour, H. & Spachos, P. Machine learning based solutions for security of Internet of Things (IoT): A survey. J. Netw. Comput. Appl. 161 , 102630 (2020).
Abiodun, O. I., Abiodun, E. O., Alawida, M., Alkhawaldeh, R. S. & Arshad, H. A review on the security of the Internet of Things: Challenges and solutions. Wirel. Person. Commun. 119 (3), 2603–2637 (2021).
Podder, P., Mondal, M. R. H., Bharati, S. & Paul, P. K. Review on the security threats of Internet of Things. Int. J. Comput. Appl. 176 (41), 37–45 (2020).
Hamad, Z. J. & Askar, S. Machine learning powered IoT for smart applications. Int. J. Sci. Bus. 5 (3), 92–100 (2021).
Xu, H. et al. A combination strategy of feature selection based on an integrated optimization algorithm and weighted K-nearest neighbor to improve the performance of network intrusion detection. Electronics 9 (8), 1206 (2020).
Bharati, S. & Mondal, M. R. H. Computational intelligence for managing pandemics. In 12 Applications and Challenges of AI-Driven IoHT for Combating Pandemics: A Review (eds Bharati, S. & Mondal, M. R. H.) 213–230 (De Gruyter, 2021).
Robel, M. R. A., Bharati, S., Podder, P. & Mondal, M. R. H. IoT driven healthcare monitoring system. In Fog, Edge, and Pervasive Computing in Intelligent IoT Driven Applications (eds Gupta, D. & Khamparia, A.) 161–176 (Wiley, 2020).
Podder, P., Mondal, M. R. H. & Kamruzzaman, J. Iris feature extraction using three-level Haar wavelet transform and modified local binary pattern. In Applications of Computational Intelligence in Multi-Disciplinary Research 1st edn (eds Elngar, A. A. et al. ) (Elsevier, 2022).
Chandavarkar, B. R. Hardcoded credentials and insecure data transfer in IoT: National and international status. In Proc. 2020 11th International Conference on Computing, Communication and Networking Technologies (ICCCNT) 1–7 (2020).
Ferrara, P., Mandal, A. K., Cortesi, A. & Spoto, F. Static analysis for discovering IoT vulnerabilities. Int. J. Softw. Tools Technol. Transf. 23 (1), 71–88 (2021).
Yu, Y., Guo, L., Liu, S., Zheng, J. & Wang, H. Privacy protection scheme based on CP-ABE in crowdsourcing-IoT for Smart Ocean. IEEE Internet Things J. 7 (10), 10061–10071 (2020).
Xiong, J. et al. A personalized privacy protection framework for mobile crowdsensing in IIoT. IEEE Trans. Ind. Inform. 16 (6), 4231–4241 (2020).
Jiang, X., Lora, M. & Chattopadhyay, S. An experimental analysis of security vulnerabilities in industrial IoT devices. ACM Trans. Internet Technol. 20 (1), 1–24 (2020).
Visoottiviseth, V., Sakarin, P., Thongwilai, J. & Choobanjong T. Signature-based and behavior-based attack detection with machine learning for home IoT devices. In Proc. 2020 IEEE Region 10 Conference (TENCON 2020) 829–834 (2020).
Turk, Z., Soto, B. G. D., Mantha, B. R. K., Maciel, A. & Georgescu, A. A systemic framework for addressing cybersecurity in construction. Autom. Construct. 133 (3), 103988 (2022).
Al Hayajneh, A., Bhuiyan, N. Z. A. & McAndrew, I. Improving internet of things (IoT) security with software defined networking (SDN). Computers 9 (1), 8 (2020).
Hussain, F., Hassan, S. A., Hussain, R. & Hossain, E. Machine learning for resource management in cellular and IoT networks: Potentials, current solutions, and open challenges. IEEE Commun. Surv. Tutor. 22 (2), 1251–1275 (2020).
IoT Dataset for Intrusion Detection Systems (IDS). https://www.kaggle.com/azalhowaide/iot-dataset-for-intrusion-detection-systems-ids (2023).
Nawir, M., Amir, A., Yaakob, N. & Lynn, O. B. Internet of Things (IoT): Taxonomy of security attacks. In Proc. 3rd International Conference in Electronic Design (ICED) 321–326 (2016).
Herzberg, B., Bekerman, D. & Zeifman, I. Breaking down mirai: An IoT DDoS botnet analysis. Incapsula Blog, Bots and DDoS, Security, (2016).
Ambusaidi, M. A., He, X., Nanda, P. & Tan, Z. Building an intrusion detection system using a filter-based feature selection algorithm. IEEE Trans. Comput. 65 (10), 2986–2998 (2016).
Article MathSciNet Google Scholar
Moustafa, N., Creech, G. & Slay, J. Big data analytics for intrusion detection system: Statistical decision-making using finite Dirichlet mixture models. In Data Analytics and Decision Support for Cybersecurity 1st edn (eds Moustafa, N. et al. ) 127–156 (Springer, 2017).
Tsai, C. F. & Lin, C. Y. A triangle area based nearest neighbors approach to intrusion detection. Pattern Recogn. 43 (1), 222–229 (2010).
Article ADS Google Scholar
Alom, M. Z., Bontupalli, V. & Taha, T. M. Intrusion detection using deep belief networks. In Proc. IEEE National Aerospace and Electronics Conference (NAECON) 339–344 (2015).
Yin, C., Zhu, Y., Fei, J. & He, X. A deep learning approach for intrusion detection using recurrent neural networks. IEEE Access 5 , 21954–21961 (2017).
Tang, T. A., Mhamdi, L., McLernon, D., Zaidi, S. A. R. & Ghogho, M. Deep learning approach for network intrusion detection in software defined networking. In Proc. 2016 International Conference on Wireless Networks and Mobile Communications (WINCOM) 258–263 (2016).
Ludwig, S. A. Intrusion detection of multiple attack classes using a deep neural net ensemble. In Proc. 2017 IEEE Symposium Series on Computational Intelligence (SSCI) 1–7 (2017).
Al-Hawawreh, M., Moustafa, N. & Sitnikova, E. Identification of malicious activities in industrial Internet of Things based on deep learning models. J. Inf. Secur. Appl. 41 , 1–11 (2018).
Shone, N., Ngoc, T. N., Phai, V. D. & Shi, Q. Deep learning approach to network intrusion detection. IEEE Trans. Emerg. Top. Comput. Intell. 2 (1), 41–50 (2018).
Subba, B., Biswas, S. & Karmakar, S. Enhancing performance of anomaly-based intrusion detection systems through dimensionality reduction using principal component analysis. In Proc. 2016 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS) 1–6 (2016).
Kumar, R. et al. Blockchain-based authentication and explainable AI for securing consumer IoT applications. IEEE Trans. Consumer Electron. https://doi.org/10.1109/TCE.2023.3320157 (2024).
Javeed, D., Gao, T., Kumar, P. & Jolfaei, A. An explainable and resilient intrusion detection system for industry 5.0. IEEE Trans. Consumer Electron. 70 (1), 1342–1350. https://doi.org/10.1109/TCE.2023.3283704 (2024).
Kumar, R. et al. Digital twins-enabled zero touch network: A smart contract and explainable AI integrated cybersecurity framework. Future Gener. Comput. Syst. https://doi.org/10.1016/j.future.2024.02.015 (2024).
Download references
Acknowledgements
The authors extend their appreciation to the Deanship of Research and Graduate Studies at King Khalid University for funding this work through small group research under Grant Number (RGP1/129/45).
Author information
Authors and affiliations.
College of Computer Science, King Khalid University, Abha, Kingdom of Saudi Arabia
Hosam El-Sofany & Belgacem Bouallegue
Faculty of Informatics and Computer Science, British University in Egypt-BUE, Cairo, Egypt
Samir A. El-Seoud & Omar H. Karam
Electronics and Micro-Electronics Laboratory (E. μ. E. L), Faculty of Sciences of Monastir, University of Monastir, Monastir, Tunisia
Belgacem Bouallegue
You can also search for this author in PubMed Google Scholar
Contributions
Hosam El-Sofany is responsible for developing the original research concept, design, methodology, and implementation. He is also responsible for writing, editing, reviewing, checking against plagiarism using the iThenticate program, and proofreading. Samir A. El-Seoud: methodology, writing, and proofreading. Omar H. Karam: methodology, writing, and proofreading. Belgacem Bouallegue: methodology, writing, reviewing, editing, and proofreading.
Corresponding author
Correspondence to Hosam El-Sofany .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
El-Sofany, H., El-Seoud, S.A., Karam, O.H. et al. Using machine learning algorithms to enhance IoT system security. Sci Rep 14 , 12077 (2024). https://doi.org/10.1038/s41598-024-62861-y
Download citation
Received : 13 November 2023
Accepted : 22 May 2024
Published : 27 May 2024
DOI : https://doi.org/10.1038/s41598-024-62861-y
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Internet of Things
- Sustainable development goals
- Sustainable cities and communities
- IoT security
- Machine learning
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing: AI and Robotics newsletter — what matters in AI and robotics research, free to your inbox weekly.
- Open access
- Published: 05 January 2022
A decade of research on patterns and architectures for IoT security
- Tanusan Rajmohan 1 ,
- Phu H. Nguyen ORCID: orcid.org/0000-0003-1773-8581 2 &
- Nicolas Ferry 3
Cybersecurity volume 5 , Article number: 2 ( 2022 ) Cite this article
11k Accesses
10 Citations
Metrics details
Security of the Internet of Things (IoT)-based Smart Systems involving sensors, actuators and distributed control loop is of paramount importance but very difficult to address. Security patterns consist of domain-independent time-proven security knowledge and expertise. How are they useful for developing secure IoT-based smart systems? Are there architectures that support IoT security? We aim to systematically review the research work published on patterns and architectures for IoT security (and privacy). Then, we want to provide an analysis on that research landscape to answer our research questions. We follow the well-known guidelines for conducting systematic literature reviews. From thousands of candidate papers initially found in our search process, we have systematically distinguished and analyzed thirty-six (36) papers that have been peer-reviewed and published around patterns and architectures for IoT security and privacy in the last decade (January 2010–December 2020). Our analysis shows that there is a rise in the number of publications tending to patterns and architectures for IoT security in the last three years. We have not seen any approach of applying systematically architectures and patterns together that can address security (and privacy) concerns not only at the architectural level, but also at the network or IoT devices level. We also explored how the research contributions in the primary studies handle the different issues from the OWASP Internet of Things (IoT) top ten vulnerabilities list. Finally, we discuss the current gaps in this research area and how to fill in the gaps for promoting the utilization of patterns for IoT security and privacy by design.
Introduction
The Internet of Things (IoT) is becoming more popular as many “things” are getting more intelligent and connected, e.g., smartphones, smart cars, smart energy grids, smart cities. The IEEE Standards Association defines an IoT system as “a system of entities (including cyber-physical devices, information resources, and people) that exchange information and interact with the physical world by sensing, processing information, and actuating” (IEEE SA 2018 ). In 2019, the International Data Corporation (IDC) made a forecast that there will be 41.6 billion IoT devices in the field by 2025. Footnote 1 Most of the critical infrastructures pointed in the EU’s Directive on security of network and information systems Footnote 2 such as for energy, water, transport, and healthcare are or will be IoT-based. For instance, smart cities are integrating IoT sensors with analytic to streamline spending, improve infrastructural efficiency. Footnote 3 Internet-connected pacemakers have been implanted for millions to help control their abnormal heart rhythms. The IoT will thus play a key role in the digitalization of the society and IoT security issues will “affect not only bits and bytes”, but also “flesh and blood” (Schneier 2017 ). Without solid security in place, attacks and malfunctions in IoT-based critical infrastructures may outweigh any of its benefits (Roman et al. 2011 ). On the other hand, privacy is also very important in the IoT. Many “things” that people use in daily activities at work and at home are now connected to the Internet. This means that sensitive private data can be exposed via the Internet. Privacy challenges are just as important to tackle in comparison to security challenges in the IoT. The heterogeneous networking technologies and resource-constrained devices of the IoT that can only afford lightweight security and privacy solutions are proven to be weak links for IoT systems (Porambage et al. 2016 ). It is also possible that security and privacy are often overlooked by IoT solutions providers (Richa 2021 ), e.g., because of complexity, time-to-market pressure, or due to a lack of knowledge. A way to address this issue could be based on security patterns, which have proven to be very valuable for practitioners, especially non-security experts (Schumacher et al. 2013 ; Fernandez-Buglioni 2013 ).
In the software engineering discipline, patterns document well-known solutions that contain domain-independent knowledge and expertise in a reusable way. The solutions documented by patterns are known to be sound because they are tested over time (Schmidt and Buschmann 2003 ). Moreover, the pros and cons of a pattern are often explicitly documented. Therefore, sketching a solution based on a pattern can provide a good baseline for building the system. Using patterns and architecture alone is not enough but can provide an important support in the development methods for secure systems such as the ones surveyed in Nguyen et al. ( 2015 ). Security patterns consist of domain-independent, time-proven security knowledge, and expertise. Security patterns can contribute to the security and privacy of systems because they offer invaluable help in applying solid design solutions that, for example, secure the user authentication, information processing and storing, secure communication with other devices and with the server. Books and catalogs of security patterns, such as Schumacher et al. ( 2013 ), Fernandez-Buglioni ( 2013 ), Nguyen et al. ( 2015 ) and Steel and Nagappan ( 2006 ) should be useful for users to unravel security challenges by utilizing time-proven security knowledge and expertise.
However, the IoT era introduces new security challenges that existing approaches and methods cannot address. Footnote 4 For example, the cross-domain cyber-to-physical (C2P) attack is the least understood one comparing to P2C, C2C, or P2P attack categories (Yampolskiy et al. 2013 ). IoT systems, especially mission-critical ones, having intrinsic complexity and heterogeneity, broader attack surfaces, often live under uncertainty, which exacerbates security issues (Ciccozzi et al. 2017 ). Indeed, nowadays IoT systems often span across the Cloud layer, the Fog/Edge layer, and the IoT field-devices layer consisting of many smart, connected devices. The explosion in connectivity created a larger attack surface area (Covington and Carskadden 2013 ). Besides, the IoT field-devices often operate under dynamic (physical) execution environments, involving dynamic actuation, but have limited data delivery and storage facilities. In other words, uncertainty is inherent in IoT systems. We are very much interested in examining the landscape of patterns and architectures being applied for the IoT domain, whose security (and privacy) challenges are huge. How have the existing security patterns been applied in tackling IoT security challenges? Are there any new security patterns that have been specifically introduced to address new security challenges in IoT?
To make sense of the research landscape of methodologies around patterns for security and privacy in IoT, we have conducted a systematic literature review (SLR) following the most popular guidelines from Kitchenham et al. ( 2011 ), Kitchenham and Charters ( 2007 ), Petersen et al. ( 2015 ) and Wohlin ( 2014 ). Our SLR has three fundamental objectives. First, we need to find out the approaches around patterns and architectures for IoT security and privacy, called the primary studies of our SLR. Second, by analyzing the primary studies, we can perceive gaps in the state-of-the-art of patterns and architectures for IoT security and privacy. We are particularly interested in how advanced patterns and architectures are, and their approaches to address IoT security. Third, based on the results, we identify the gaps to support security and privacy in modern IoT systems and propose further research to fill the gaps. The main contributions of this work are our responses to the accompanying research questions (RQ)s.
RQ1 What are the publication statistics of the research on patterns and architectures for IoT security and privacy?
RQ2 What are the technical details of these security patterns and architectures for addressing IoT security and privacy?
RQ3 What are the “gaps” to make security patterns and architectures more applicable for IoT?
From thousands of candidate papers initially found in our search process, we have systematically distinguished and analyzed 36 papers that have been published around patterns and architectures for IoT security in the last decade. Our analysis results show the trend of an increasing number of published papers in this research area in three recent years. We have performed our analysis based on a taxonomy that we built for this research area. Our analysis sheds some light on the state of the art around patterns and architectures for IoT security and the current limitations. Based on our analysis, we provides some suggestions for a way forward of this research topic. Specifically, the contributions in this paper include:
We have an exhaustive database search process. Moreover, we manually conducted snowballing (backward and forward as suggested in Wohlin 2014 ). We identified and included six new primary studies from this snowballing process. Therefore, our final set of primary studies reported in this paper is 36 (see “ Our systematic literature review approach ” section).
We have defined a clear taxonomy (see “ Taxonomy of the research area ” section) and provided in-depth analyses on the architectures and patterns from the primary studies (see “ Technical aspects of the primary studies (RQ2) ” section). For example, we summarize all the patterns from the primary studies and also discuss how the architectures from the primary studies cover the seven layers of the IoT World Forum Reference Model of the IoT architecture (Juxtology 2018 ).
We have provided discussion on the existing gaps and limitations in “ Gaps and limitations (RQ3) ” section. For example, we discuss the gaps in the research contributions from the primary studies regarding how they handle the different issues presented by the OWASP IoT top ten vulnerabilities list (OWASP 2018 ). Last but not least, we explicitly discuss the possible threats to validity of our study in “ Threats to validity ” section to give readers more insights in this work.
In the remainder of this paper: “ Background ” section gives some background definitions. In “ Our systematic literature review approach ” section, we present our SLR approach. To facilitate data extraction and comparison, “ Taxonomy of the research area ” section describes our classification schemes for the primary studies. We present the results of our SLR in “ Results ” section. Related work is discussed in “ Related work ” section. In “ Threats to validity ” section, we analyze possible threats to the validity of this work. Finally, we conclude the paper with summarizing the main findings in “ Conclusions ” section.
We give the definitions of SLR in the “ Systematic literature review ” section, (security) design patterns in the “ Design pattern ” section, and security architecture in the “ Security architecture ” section that were used to define the scope of this work.
Systematic literature review
A SLR is a study that “reviews all the primary studies relating to a specific research question”, and “uses a well-defined methodology to identify, analyze and interpret all available evidence related to that specific research question in a way that is unbiased and (to a degree) repeatable.” (Kitchenham et al. 2011 )
Design pattern
The primary understanding for a design pattern is that it is a reusable solution for a typical occurring issue in software design. A pattern is ordinarily abstract with the goal that it may be reused, and it is a proven solution for solving a software design problem. A design pattern is not a complete implementation that can be executed and utilized, but more a plan or template for how to take care of an issue that can serve in various circumstances/contexts (Gamma et al. 1994 ; Fernandez-Buglioni 2013 ).
According to Schumacher et al. ( 2013 ), “a security pattern describes a particular recurring security problem that arises in specific contexts, and presents a well-proven generic solution for it. The solution consists of a set of interacting roles that can be arranged into multiple concrete design structures, as well as a process to create one particular such structure.”
Note that there are key security patterns such as from Schumacher et al. ( 2013 ), Fernandez-Buglioni ( 2013 ) and Steel and Nagappan ( 2006 ) that provide guidance at the architecture level. These patterns may also be called security architectures but yet they are design patterns and should be considered as patterns. In other words, we clearly call architectural patterns as patterns, not architectures. This definition means that we only consider an architecture as a pattern if it is explicitly described as a pattern. Any architecture for IoT security that is not a pattern is called “security architecture” in this paper.
Security architecture
The term sofware architecture typically refers to the structure of a software system, including software elements and the relationships between them. Within our SLR, we want to include architectures for IoT security or architectures that were specifically designed with IoT security concerns in mind. When architectures are not formalized as a pattern, we call them IoT security architectures, as opposed to architectural patterns. When a security architecture is generic enough to be used in different contexts, it is called an IoT security reference architecture. It is worth discussing the relationship between IoT security reference architectures and IoT security patterns: (1) IoT security patterns can be extracted from an IoT security reference architecture, and (2) an IoT security reference architecture can leverage and be composed of one or several patterns, including IoT security patterns. By analyzing not only security patterns but also security architectures, our study aims to cover security aspects encompassing not only only one layer of IoT systems but also multiple layers when architectures are key to address.
Our systematic literature review approach
We conducted our SLR using the most popular guidelines from Kitchenham et al. ( 2011 ), Kitchenham and Charters ( 2007 ), Petersen et al. ( 2015 ) and Wohlin ( 2014 ). Three main phases of an SLR are: Planning the Review, Conducting the Review, Reporting the Review (see Fig. 1 ) (Kitchenham and Charters 2007 ).
The process of planning, conducting, and reporting a SLR (Kitchenham and Charters 2007 )
We map the stages associated with planning our SLR with where we present them in this paper:
Identification of the need for a review: In the “ Introduction ” section, we have presented the motivation of our SLR.
Specifying the research question(s): the “ Research questions ” section.
Developing a review protocol: Our review protocol is developed according to the guidelines in Kitchenham and Charters ( 2007 ). The main parts of our review protocol are the research questions (“ Research questions ” section), the inclusion and exclusion criteria (“ Inclusion and exclusion criteria ” section), the search and selection strategy (“ Search and selection strategy ” section), and the taxonomy for data extraction and synthesis (“ Taxonomy of the research area ” section).
The stages associated with conducting our SLR:
Identification of research: Search and selection strategy (“ Search and selection strategy ” section).
Selection of primary studies: Search and selection strategy (“ Search and selection strategy ” section).
Study quality assessment: We only selected peer-reviewed papers with enough details as the primary studies of this SLR (“ Inclusion and exclusion criteria ” section).
Data extraction and monitoring: We extracted data based on the taxonomy defined in “ Taxonomy of the research area ” section.
Data synthesis: We synthesized the extracted data to answer our research questions in “ Results ” section.
The stages associated with reporting our SLR:
Specifying dissemination mechanisms: We specified the journal to publish the results of our SLR.
Formatting the main report: This paper.
With the particular context and motivation displayed in “ Introduction ” section, we introduce our RQs for this paper in “ Research questions ” section. In “ Inclusion and exclusion criteria ” section, we explain the criteria for choosing primary studies to explicitly portray the scope of our SLR and diminish possible bias in our selection procedure. “ Search and selection strategy ” section shows our search strategy to locate the primary studies for answering the RQs.
Research questions
This SLR aims to answer the three RQs presented in “ Introduction ” section. Each is extended with sub-questions.
RQ1 includes three sub-RQs. RQ1.1 In which year(s) are the primary studies published? Answering this question allows us to know when this research topic became fascinating as well as how recent the research on this topic is. It could give an indicator of how much attention security patterns and secure architectures for IoT get from the research community. RQ1.2 — What are the types (i.e., Journal, Conference, Workshop) and target domains (e.g., IoT, Network, Cloud and Software Engineering (SE)) of the venues where the primary studies were published? Answering this question allows us to recognize the target domain for each paper. Note that security patterns are presented in publications across a few related research areas, e.g., IoT, Cloud, SE, Network. The type of paper can give a few hints on the maturity of the primary study. Journal papers should report more mature studies than conference papers. RQ1.3 — How is the distribution of publications in terms of papers affiliated with industry and the academic? We classify a paper as academic if all the associated authors are with a university or a research institute. Moreover, we group papers as industrial if all related authors are with an industrial organization, and characterize the papers as both if there is a coordinated effort of both academia and industry. Answering RQ1.3 will display the collaboration effort between industry and scholar communities. It also demonstrates the interest and needs of IoT security patterns in the industry.
RQ2 has three sub-RQs. RQ2.1 — What type (e.g., security pattern, architecture) of contribution do the primary studies create or use, and how the distribution is between them? Answering RQ2.1 shows how the distribution of patterns and architectures are, as well as how the contribution is used or for what purpose. RQ2.2 — How well do the patterns and architectures cover security and privacy issues? Answering this RQ shows what security patterns and architectures focus on IoT systems’ specific security and privacy concerns. It also shows us what current security and privacy concerns are most covered today. RQ2.3 — What application domains have been addressed by the security patterns and architectures? This RQ can help us to see what application domains have got more attention in the application of security patterns and architectures.
RQ3 also has two sub-RQs. RQ3.1 — What are the current limitations of the IoT security patterns and architectures research? RQ3.2 — What research directions could be recommended for tackling the current limitations? These RQs help to express and suggest the current issues and possible directions for future work.
Inclusion and exclusion criteria
Considering the RQs and the basis of our study introduced in “ Introduction ” section, we predefined the inclusion and exclusion criteria to decrease bias in our methodology of search and selection of primary studies. The primary studies must meet ALL the accompanying inclusion criteria (IC):
(IC1) Contain patterns or architectures (one or more) in some form relevant for IoT systems.
(IC2) Be specifically within the area of IoT, either in a generally applicable domain or in a specific application domain of IoT.
(IC3) Present security (or privacy) concerns explicitly in system design, architecture, or infrastructure.
(IC4) Have a minimum length of four pages in double-column format or six pages in single-column format.
Moreover, when a single approach is presented in more than one paper describing different parts of the approach (e.g., approach itself, empirical study, evaluation), we include all these papers, but still consider them as a single approach (study). When encountering more than one paper describing the same or similar approaches, which were published in different venues, we only include the most recent one that has the most complete description of the approach.
We excluded papers that are not written in English, non-peer-reviewed papers (e.g., “grey” literature, white papers in industry), and papers that are only accessible as extended abstracts, posters, or presentations (not full version). We also did not include multivocal surveys as primary studies because they are secondary studies. We do discuss the surveys on related topics as related work in “ Related work ” section. We also mainly focused our review for the publications in the duration 2010–2020 (see “ Search and selection strategy ” section).
Search and selection strategy
The search strategy utilized is a blend of various kinds, to thoroughly scan for IoT security pattern and architecture papers. The objective is to locate the most relevant papers and, along these lines, discover as many essential IoT security pattern and architecture papers as possible.
Database search
Using online inquiry components of popular publication databases is the most notable approach to scan for essential primary studies when directing supplemental studies (Kitchenham and Charters 2007 ). We used five of the popular publication databases IEEE Xplore, Footnote 5 ACM Digital Library, Footnote 6 ScienceDirect, Footnote 7 Web of Knowledge (ISI), Footnote 8 and Scopus Footnote 9 to search for potential primary studies. Scopus and ACM DL already index SpringerLink Footnote 10 (Tran et al. 2017 ). The five picked databases contain peer-reviewed articles, which give advanced search capacities. Following the guidelines from Kitchenham and Charters ( 2007 ), based on the research questions and keywords utilized in some related articles, we have defined our search keywords. The search query was adopted to fit each of the search engines of the five publication databases. Note that we did not include “misuse pattern” in the search query because misuse patterns (from the point of view of the attacker) are out of scope of this study.
( “Internet of Things” OR “IoT” OR “Cyber Physical Systems” OR “Web of Things” )
( “Security Pattern” OR “Design Pattern” OR “Security Design Pattern” OR “Privacy Pattern” OR “Security Architecture” OR “Secure Architecture” )
During our database search process, we did conduct many rounds of testing the search query on the search engines. On the one hand, this testing process helped us to improve our search query and customize it for better fit the search features. On the other hand, we also saw very few hits returned by the search engines for the duration 2000–2010. Therefore, we mainly focused our review for the publications in the duration 2010–2020.
For every candidate paper, we originally reviewed the paper’s title and abstract, trailed by skimming through the contents. On the off chance that an applicant paper shows up in more than one database, we show them in the other database results. When merging to the first set of primary studies, we consolidate the outcomes, so we get the right number of papers without copies. It is portrayed step by step in Fig. 2 .
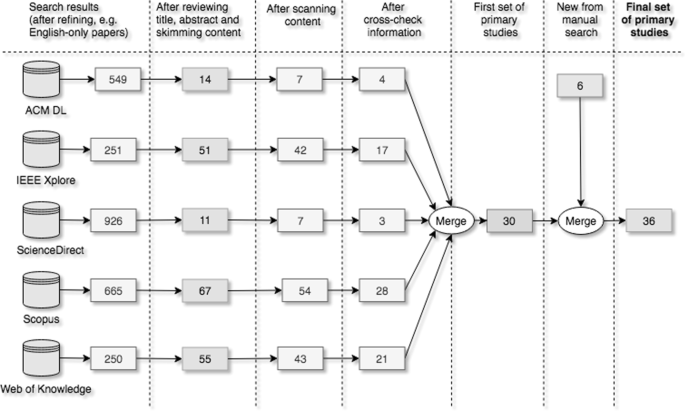
Overview of the search and selection steps
Manual search
It is unrealistic to guarantee the database search results can cover all IoT security patterns and architectures in our study. We have, therefore, attempted to supplement the database search by doing a manual search. We started by manually searching through published papers from previous journals and conferences. The conferences and journals we went through to find papers were: The International Conference on the Internet of Things, Footnote 11 Pattern Languages of Programs (PLoP), Footnote 12 EuroPLoP, Footnote 13 IEEE ICIOT, Footnote 14 ACM Transactions on Internet of Things (TIOT) Footnote 15 and IEEE Internet of Things Journal. Footnote 16 We also manually did snowballing (backward and forward) on all the primary studies found as suggested in Wohlin ( 2014 ). In the wake of looking through these journals and conferences as well as doing snowballing, we concluded that most of the relevant papers posted or found from our manual search were earlier discovered from the database search, or they did not satisfy our criteria. The papers from the manual search were checked against the automatic results, and vice versa. In the end, we had found six more primary studies from the manual search process.
Note that any candidate paper in doubt was kept for evaluation and cross-checked among the reviewers at each phase of our search and selection process. Our gathering conversations have finally yielded a set of 36 primary studies for data extraction and synthesis to answer the RQs Footnote 17 .
Taxonomy of the research area
In this section, we define a taxonomy for IoT security patterns and architectures. This taxonomy helps us to extract and synthesize data from the primary studies for answering the RQs. We applied a top-down strategy to process data from the literature around IoT, security patterns, IoT architectures, and design patterns to create a first version of the taxonomy. We also tried to validate and enrich the taxonomy by a bottom-up approach. The bottom-up approach is for extracting data from a test set of primary studies. This test set consists of the initial ten primary studies chosen. It helped us to characterize and determine the significant methods and terminology utilized in the primary studies.
Domain specificity
We characterize the domain specificity in the same manner as (Washizaki et al. 2020 ) with minor tweaks. It is essential to examine the applicability and reusability of each IoT security pattern.
General IoT security design patterns, and security architectures, which apply to any IoT system and software.
Specific IoT security design patterns, and security architectures that address specific problem domains (such as healthcare) and technical domains (such as the brain-computer interaction).
Categorization of security pattern research
We classify security patterns according to the main categories presented in Yskout et al. ( 2006 ). First, we distinguish security patterns based on how they affect the software application or the environment (e.g., infrastructure, middleware) in which the application will eventually be deployed.
Application architecture (AA): A pattern’s introduction can affect an extensive part of the application, e.g., by introducing new components in the application, or modifying existing components.
Application design (AD): A pattern’s introduction only has local implications. For example, a pattern can introduce some form of encapsulation of security data.
System (S)/Execution environment: A pattern’s introduction only affects the environment in which the application will be deployed.
We classify the (security, privacy) objectives of the patterns as presented below in “ Security and privacy concerns ” section. More importantly, we detail the patterns by their main properties from the software design pattern template by the Gang of Four (Gamma et al. 1994 ):
Intent: What (in what context) is the pattern used for? What is the purpose of the pattern?
Problem: What problem that the pattern can address. This may also include the different forces (and context) that lead to the problem.
Solution: A description of the solution provided by the pattern.
We also characterize patterns by purpose , method , and research implementation , which is similar to how Washizaki et al. ( 2018 ) did in their paper.
C1 purpose: This part includes the topics addressed by the research, software life-cycle, and the intended users.
C2 method: This part refers to the methodology and modeling methods to define the pattern’s structure and design.
C3 research implementation/validation: This part includes where, how and if the contributions were implemented and tested/validated, and in which context. It also includes analysis of a test case or scenario. Whether the results are automated and encapsulated in a tool, and whether case studies or experiments are conducted to evaluate the results relevant to the original research purpose.
IoT architecture
Many IoT architecture exist in the literature, all decomposed in a different number of layers. In our taxonomy, we leverage the IoT World Forum Reference Model of the IoT architecture (Juxtology 2018 ). This architecture provides a fine-grained granularity over the different layers that typically compose an IoT system. It has recently been adopted in many large scale IoT systems, for instance, as indicated in Create-IoT ( 2018 ), all of the H2020 IoT large scale pilots at the exception of one, have adopted this architecture. It consists of the following seven layers:
L1 physical devices and controllers: Physical layer consisting of devices or “things” of the IoT. The “things”, sensors, and Edge Node devices are classified within this layer.
L2 connectivity: Connectivity spans from the “middle” of an Edge Node device up through transport to the Cloud. This layer maps data from the logical and physical technologies used, the communication between the physical layer and the computing layer, and above.
L3 edge computing: Layer that brings computation and data storage closer to the location it is needed. Protocol conversion, routing to higher-layer software functions, and even “fast path” logic for low latency decision making will be implemented at this layer.
L4 data accumulation: Intermediate storage of incoming storage and outgoing traffic queued for delivery to lower layers. Pure SQL is what the layer is implemented with, but it may require more advanced solutions, i.e., Hadoop & Hadoop File System, Mongo, Cassandra, Spark, or other NoSQL solutions.
L5 data abstraction: Data is made clear and understandable, centers around rendering data and its storage in manners that enable developing more straightforward, performance-enhanced applications. This layer speeds up high priority traffic or alarms, and sort incoming data from the data lake into the appropriate schema and streams for upstream processing. Likewise, application information bound for downstream layers is reformatted appropriately for device communication and queued for processing.
L6 application layer: At the application layer, information interpretation of multiple IoT sensors or measurements occur, and logic is executed. Monitoring, process optimization, alarm management, statistical analysis, control logic, logistics, consumer patterns, are just a few examples of IoT applications.
L7 collaboration and processes: Application processing to its users, and data processed at lower layers are integrated with business applications. This layer consists of human interaction with all the layers of the IoT system, and economic value is delivered.
Another simpler IoT architecture largely adopted in the literature consists of three layers: perception (L1), network (grouping L2 and L3), and application (grouping L4, L5, L6, L7, and L8). We map how the contributions of today fit in both the IoT World Forum Reference Model of the IoT architecture and the three-layer IoT architecture.
Security and privacy concerns
We analyze the primary studies according to the following security and privacy concerns: confidentiality, integrity, availability (CIA), accountability, and privacy (Ross et al. 2016 ; Kuhn et al. 2001 ; Yskout et al. 2006 ). These concerns are what we consider essential to IoT systems and devices. We also classify security mechanisms such as authentication and authorization when such information are available in the primary studies. We want to see what patterns and architectures uphold and protect against these security and privacy concerns. Their definitions are as follows.
Confidentiality: Ensures the property that information is not made available or disclosed to unauthorized individuals, entities, or processes.
Integrity: Maintains and ensures the accuracy and completeness of the data during its life-cycle.
Availability: The information/service is available when needed.
Authentication: The system/device can verify a claim of identity.
Authorization: The system can determine what resources the entities that have been identified and authenticated can access and what actions they can perform within/on the system.
Accountability: Enables the tracing of important (or all) actions performed on the system back to a particular user, usually by means of logging.
Privacy: The data collected is legally collected and stored, how data is shared, and follow regulatory restrictions from the GDPR (mostly EU), and HIPAA (Office for Civil Rights 2013 ), GLBA (Federal Trade Commission 1999 ) (mostly in the US).
This section presents the main results of our SLR and how our research questions are answered. Table 1 shows an overview of the primary studies that have been found in this review regarding patterns and architectures for IoT security and privacy. Based on the taxonomy in “ Taxonomy of the research area ” section, we have extracted and synthesized the primary studies’ data to answer the RQs. “ High-level statistics (RQ1) ” section shows high-level statistics that help us to answer RQ1. Then, we present low-level details of the primary studies in “ Technical aspects of the primary studies (RQ2) ” section that help us to answer RQ2. Based on our answers to RQ1 and RQ2, we discuss the gaps and limitations as our answer to RQ3.
High-level statistics (RQ1)
In this section, we provide our answers to the RQ1- What are the publication statistics of the research on patterns and architectures for IoT security and privacy?
Answering RQ1.1 In which year(s) are the primary studies published? Fig. 3 shows a rise in the number of conference (C) and journal (J) publications related to IoT security patterns and architectures in the recent three years (2018: 7C, 2019: 5C, 4J and 2020 Footnote 18 : 5C, 5J). This spike shows that security patterns and architectures are gaining more focus over the years and that there is a demand for IoT security pattern and architecture research.
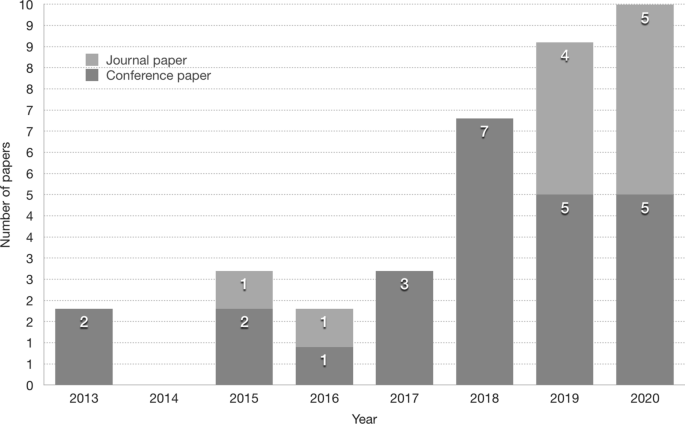
Publications per year, per venue type
Answering RQ1.2 What are the types (i.e., Journal, Conference, Workshop) and target domains (e.g., IoT, Network, Cloud and Software Engineering (SE)) of the venues where the primary studies were published? Research on the IoT, with its heterogeneous nature, traverses through various important research areas, among which we perceived Software Engineering (SE), Cloud, Blockchain, Network, and recently specialized IoT research (Borgia et al. 2016 ). Figure 4 shows the research focus areas of the publication venues where the primary studies have been published. The main research areas that we found are between IoT: 36, Cloud: 4, Network: 7, Blockchain: 7. Note that publication venues often have several research areas in their calls for papers, e.g., IoT, network. Therefore a portion of the papers could be classified in several research areas at the same time (e.g., IoT, network). These numbers do reflect the different dimensions of IoT research, with IoT research domain getting progressively more visible. In other words, IoT-oriented conferences and journals are becoming more popular and have attracted research contributions on patterns and architectures for IoT security and privacy.
The number of primary studies that are published as conference papers are more than double the number of primary studies published in journals. From the number of publications found, we distinguished the distribution of conference papers ( \(\sim\) 69%) and journal papers ( \(\sim\) 31%). It is reasonable that conference papers tend to be published more often and quickly. But, we also see that the number of journal papers has increased since our last study (Rajmohan et al. 2020 ). We do, however, believe and encourage a continued increase of journal papers around this topic. Especially seeing that the growth of IoT is increasing rapidly and that journal papers contribute to more detailed and elaborated contributions.
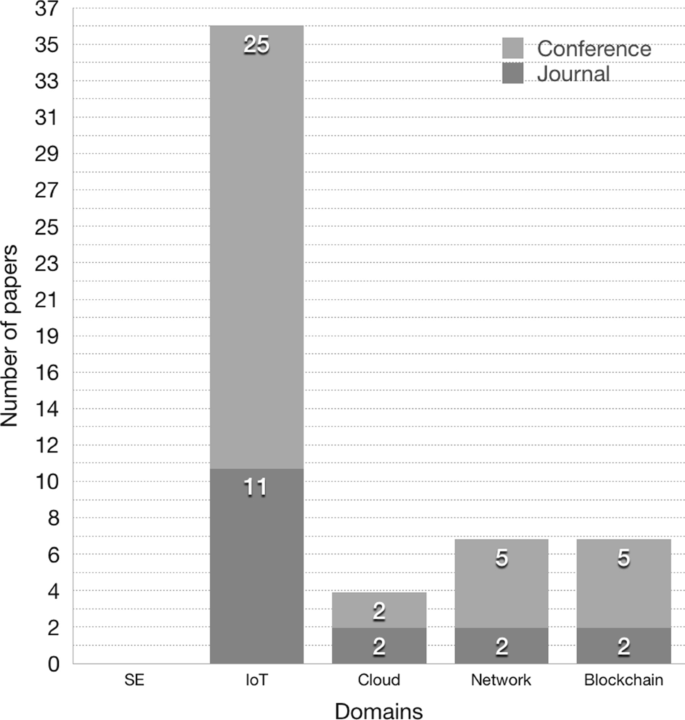
Research topics per publication venue
Answering RQ1.3 How is the distribution of publications in terms of papers affiliated with industry and the academic? Because IoT systems and devices are broadly utilized and growing in the industry and consumer market, we explored how the affiliations of the authors are dispersed from the primary studies. Would the affiliations of the authors have any implication on the publication of security patterns and architectures for IoT? From our analysis, we see that a significant amount of the authors who have published results on IoT security patterns or architectures are from academia ( \(\sim\) 75%). While there are no contributions exclusively from industry, authors working in industry do publish in joint efforts with co-authors from academia. In this work, we call the papers that have such joint efforts of academia-industry collaboration as “joint papers”. We discovered some papers of this type ( \(\sim\) 25%). The percentage of joint papers here is not high, but still remarkable compared to less than 10% of joint papers as primary studies reported in another review on security for cyber-physical systems (Nguyen et al. 2017 ).
Joint papers tend to have more usage examples and illustration contrasted with papers purely from academia. We saw in our study that 89% of the joint papers had graphical illustrations of their contribution in terms of architectural structure or pattern usage areas. The number of joint papers among academia and industry shows a promising collaboration level. We trust that this number continues to grow. The collaboration is win-win for the state of the art and practice, which can lead to the utilization of patterns and architectures proposed to improve products, production process, and internal processes that use IoT devices or systems further. We would be intrigued to see more implementations or examples of security patterns or architectures used by industry in the future.
Technical aspects of the primary studies (RQ2)
All the patterns and architectures in Table 1 have been examined according to our taxonomy (“ Taxonomy of the research area ” section), to give us meaningful information as well as pinpoint how the papers are relevant and where they contribute. The taxonomy was used to ensure that the primary studies have information relevant to this study. We can draw out some key examples, such as papers (Vijayakumaran et al. 2020 ; Vithya Vijayalakshmi and Arockiam 2020 ; Jerald et al. 2019 ; Pacheco et al. 2018 ), which are the ones who cover most security concerns (“ Security and privacy concerns ” section). We based on the (more fine-grained) data extracted from the primary studies to answer RQ2 : What are the technical details of these security patterns and architectures for addressing IoT security and privacy?
Answering RQ2.1 What type (e.g., security pattern, architecture) of contribution do the primary studies create or use, and how the distribution is between them? After finalizing the primary studies set, we found that the primary studies’ main contributions are either architectures ( \(\sim\) 81%) or patterns ( \(\sim\) 19%). These contributions are mostly solution proposals, where some have proper testing and validation ( \(\sim\) 57%) of their concept. Other papers have use case examples ( \(\sim\) 23%) in some form, and some papers even have implementations of their concept ( \(\sim\) 20%). As we presented in “ Security architecture ” section, papers describing frameworks are categorized as architectures (not patterns, if patterns are not explicitly mentioned). Therefore, we see a more significant contribution and more focus on architectures compared to patterns.
Claiming security solely based on a good architecture can be inadequate because it is typically not enough for end-to-end IoT security. We have seen other cases where architectures are not enough to solve the specific issues regarding e.g., user verification on the devices, firmware manipulation, and an attacker disconnects the devices upon will. Such issues are hard to handle only with security architecture solutions. The lack of security patterns is a result of its youth within the domain and security not being the main priority when developing IoT systems. Certain areas of an IoT system may need more attention than others regarding security, and architectures may not solve those issues. From our experience and information gathering, we have seen that the architecture solutions for IoT security have focused a lot on the whole system and all its layers (e.g., Cloud, Edge, IoT devices Juxtology 2018 ), more general system issues, and can target specific domains, but are very seldom enough to solve a specific problem. The architectures tend to focus on multiple layers (e.g., Cloud, Edge Juxtology 2018 ) and are harder to address a single layer issue or an issue in a small part of one of the architectural layers, where some specific security patterns may apply well.
As mentioned, a good architecture is only part of the solution and can be inadequate if we encounter specific security issues for a smaller area rather than the whole system, e.g., the breach on a casino’s thermostat in a fish tank to access customer data (Williams-Grut 2018 ). This breach shows the challenge to ensure end-to-end security for IoT systems, especially at their weakest links, e.g., a thermostat. Therefore, it would be exaggerating to tackle security only at the architectural level. A more straightforward solution would have been a security pattern for authentication of users or networks not to allow external communication to pass through IoT devices or verify the device when communication is sent. A more complete solution would be to employ suitable specific security patterns in a well-designed architecture. In other words, a high-level architecture supporting IoT security is only one side of the coin. The other side of the coin is to address specific IoT security challenges at any weak links such as IoT devices where some specific security patterns can help.
Table 2 shows which concerns regarding security and privacy for IoT are addressed by each of the 36 primary studies. When we compare the number of primary studies to the number of candidate papers we first found while doing the automatic search, there is a big difference. This means that security and IoT are popular keywords in many publications but “security patterns” for IoT is not. However, we still believe 36 is a reasonable amount, yet it ought to be higher with the goal that security patterns become increasingly frequent and accessible for industry and users who want to develop secure IoT systems.
Table 2 also shows us the distribution of the specificity of the various contributions. We see that most contributions fall under the “Generic” regarding application domains (“ Domain specificity ” section), which means that a substantial number of papers are adaptable for a widespread of IoT systems. These “Generic” solutions cover the core functionalities of an IoT system, which is why we labeled them “Generic” compared to the domain-specific solutions, which work within a specific domain for a specific purpose (e.g., smart cars, smart meters, and healthcare systems). As we can see, most of the contributions cover authentication, which is a crucial aspect of any system. One may link the amount of authentication coverage to the fact that several smart devices have been hacked due to a lack of authentication (Wright 2020 ). Even though authentication is the most focused concern in the primary studies, more efforts are needed for end-to-end security, including weak links in IoT systems. We would like to see more of such solutions and solutions for IoT pressing problems, e.g., communication, compatibility, integration, and scalability.
Answering RQ2.2 How well do the patterns and architectures cover security and privacy issues?
Table 2 shows a more detailed list of the concerns mentioned previously and what type of application domain the contributions have. We marked the concerns with an “x” if the concern was directly mentioned in the paper. The concern regarding privacy was only marked if it was explicitly mentioned, and not if they handle only the security concerns even they can contribute to privacy coverage.
Figure 5 displays the mapping of our security concerns based on the contribution. We weight how much each (security or privacy) concern was addressed in the primary studies compared to each other. We do so by simply calculating the percentage of how many times a concern was addressed compared to the total number of the times that all concerns were addressed. Note that as shown in Table 2 , most primary studies address more than one concern. As Fig. 5 shows, there is a widespread of focus between the security concerns (Confidentiality \(\sim\) 16%, Integrity \(\sim\) 19%, Availability \(\sim\) 8%, Authentication \(\sim\) 25%, and Authorization \(\sim\) 17%). Privacy ( \(\sim\) 15%) is relatively focused comparing to the security issues in terms of coverage within the primary studies. The low coverage for the availability concern could come from a lack of explicit explanation in the primary studies or availability was not considered in their solutions at all. In the first case, this is comprehensible as availability is a concern whose scope is broader than the only security domain. Indeed, preserving the availability of a system is tightly coupled to the ability of scaling it. Load scalability is the ability of a service to sustain variable workload while fulfilling quality of service (QoS) requirements, possibly by consuming a variable amount of underlying resources (Ferry et al. 2014 ). It is a core concern when engineering and designing complex system, and, as a result, many design patterns, including architectural patterns, have been defined in the literature from other fields (e.g., Big data, Cloud computing, large-scale systems, middleware).
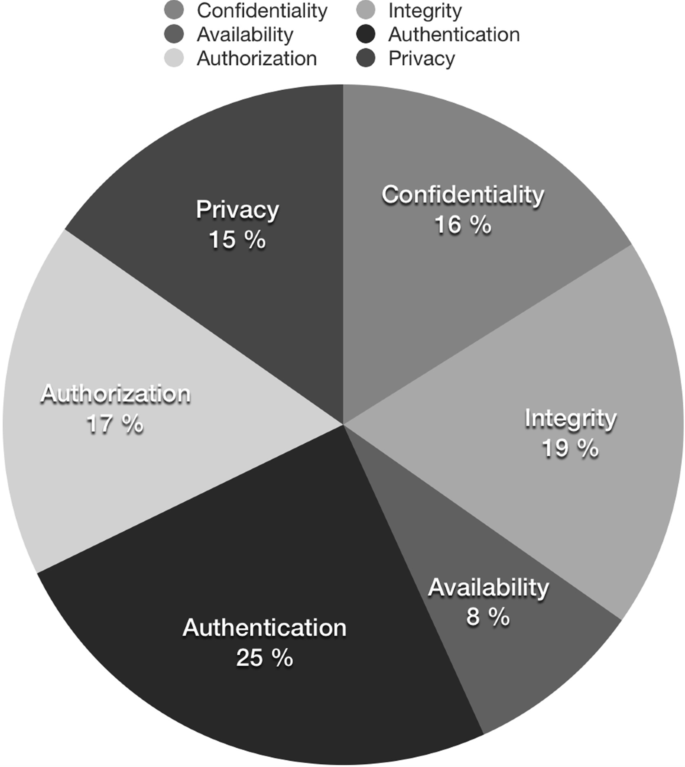
Security concerns based on the contribution
Table 2 can give a closer look on how many contributions of patterns and architectures focusing on the various concerns. For patterns, we see that only two papers out of seven security pattern papers cover the whole CIA (Confidentiality, Integrity, and Availability) triad, while security architecture papers have two out of 29 papers. Availability is the least covered concern in the primary studies. We are unsure if it is because the contributions focus mostly on authentication, but since many of these systems process or share information, we would argue that the basic CIA triad should be focused. Figure 6 illustrates the different security considerations and privacy, and shows which ones are more focused on in the papers found. Authentication is most focused by the primary studies. This point is understandable because authentication is often the foundation for building other security mechanisms such as for authorization, confidentiality, or privacy. But, the low focus on availability is something that should be drawn attention to because availability is crucial in many IoT systems, especially critical ones.
Another thing to notice is that privacy is considered in 18 out of the 36 papers. This number shows that privacy has gained nearly as much attention as security concerns in the primary studies. As mentioned previously, some papers and concerns may contribute indirectly to privacy, e.g., concerns such as authentication and authorization that verify and provide the correct access to users, which can be one way to preserve users’ privacy. But, we only count for privacy if a primary study does mention privacy explicitly.
Architectures and patterns with focus on each security concern
Table 3 shows the IoT security and privacy patterns that are presented in the primary studies. It is worth to note that there is one primary study (Pape and Rannenberg 2019 ) dedicated to IoT privacy patterns. There are seven patterns for IoT privacy presented in Pape and Rannenberg ( 2019 ), which describe different possibilities of privacy violation and the corresponding solutions. We summarize these patterns according to the main elements of security pattern in Table 3 . There is another paper that even presents a misuse pattern (Syed et al. 2018 ). Paper Syed et al. ( 2018 ) shows a misuse pattern for Distributed Denial of Service (DDoS) in IoT. They specify appropriate countermeasures for mitigating it, contributing to a specific problem in many IoT systems. Paper Fysarakis et al. ( 2019 ) discusses a pattern-driven framework solution to encode dependencies between the security concerns mentioned in “ Security and privacy concerns ” section. More specifically, paper Fysarakis et al. ( 2019 ) presents orchestration models required for IoT and IIoT applications to guarantee quality properties including security, privacy. In the same direction but more on the trustfulness, paper Pahl et al. ( 2018 ) proposes an architecture pattern based on blockchain to ensure the identity of hardware devices and software applications, the origin and integrity of data and the contractual nature of orchestration. There is only one paper (Schuß et al. 2018 ) that proposes a pattern at the hardware layer for IoT security. Schuß et al. ( 2018 ) show a pattern to secure the device through hardware, by implementing exchangeable cryptographic co-processors. This paper provides security features that can be implemented to a general IoT system, but it requires changes or additions to the hardware. The hardware-based approach in Schuß et al. ( 2018 ) aims at allowing even constrained devices to utilize state-of-the-art cryptographic functions.
While the papers mentioned so far present IoT-specific patterns, the last two papers (Lee and Law 2017 ; Ur-Rehman and Zivic 2015 ) in Table 3 focus more on how generic security patterns can be applied for IoT. For example, both of them show how the well-known Secure Logger pattern can be used in IoT. Paper Lee and Law ( 2017 ) shows multiple patterns in which they describe and explain some usage areas, but they do not show results in these usage areas. It is more for cataloging purposes including other generic security patterns such as Secure Directory, Secure Adapter Pattern, Exception Manager Pattern, and Input Validation Pattern. Paper Ur-Rehman and Zivic ( 2015 ) presents the patterns that are adopted for smart metering systems. The Secure Remote Readout pattern is presented in details in Ur-Rehman and Zivic ( 2015 ). The other patterns are name checked only such as Secure Logger, Key Manager, Wakeup Service, and Transport Layer Security.
As mentioned in the previous section, patterns target more specific parts of an IoT system, which also makes it easier to implement a pattern for that section of the system. In most cases, architectures are harder to implement/adopt because they propose a solution for multiple parts or the whole system but often lack security details for specific parts. We discuss some representative examples of the papers we found that explicitly address, propose, or use security architectures such as Vithya Vijayalakshmi and Arockiam ( 2020 ), Witti and Konstantas ( 2018 ) and Pacheco et al. ( 2018 ). Paper Vithya Vijayalakshmi and Arockiam ( 2020 ) discusses an architecture that protects the data security at all the layers of data flow, the transmission of data is essential in this contribution. Paper Witti and Konstantas ( 2018 ) shows architectures in use-cases where they apply and discuss how they are used and the results. Paper Witti and Konstantas ( 2018 ) also explains how architecture can help securing a smart city while preserving citizens’ privacy in that city. A good example of security architecture can be found in paper Pacheco et al. ( 2018 ) by Pacheco et al. ( 2018 ), which proposes a security framework for a smart water system. That paper displays security issues at most of the IoT layers and proposes security algorithms for these issues to make developers consider security early rather than an ad-hoc or afterthought manner.
Answering RQ2.3 What application domains have been addressed by the security patterns and architectures? From Table 2 we see that nine primary studies have presented the application of IoT security patterns/architectures for some specific IoT application domains. The specific IoT application domains can help our analysis in the way they elaborate on the issues and how to mitigate them. Explicitly mentioning IoT application domain has the tendency to show that the patterns can be applied in the domain and can address the requirements in this IoT domain. Some patterns could be more important for some specific domains. For example, for smart city applications, patterns for scalability is important. For e-health, patterns for privacy are important. The primary studies that do explicitly present IoT application domains would address more clearly the IoT-specific requirements or challenges. The domain-specific solutions are created for the domains mentioned, but they may still be applicable in other domains. However, these domains usually take the initiative to incorporate IoT, which explains why these areas have specific solutions before others. We also saw that many of these domain-specific studies had graphical figures describing their contribution to show how they work or the different layers of their architectures.
We consider that domain-specific contributions may not necessarily have a more significant impact on IoT security, but it is better portrayed when having a real case scenario or issue. Both the generic and specific domain contributions cover approximately three security concerns per paper, so they both stand approximately equally strong in security concerns coverage. We believe these domain-specific contributions are getting more attention, but it may still not be a better solution than the general solutions that can apply to more systems or handle more generic issues. It is still good to see more security patterns and architectures in real cases to better grasp the contribution and the issues around these domains.
Table 2 can give us some ideas on any difference in terms of addressing security and privacy concerns between the papers by academic authors and the papers authored by both academia and industry. The joint papers on average cover \(\sim 3,2\) concerns per paper, while the “academic-only” papers on average cover \(\sim 3,3\) concerns per paper. We see that both types of paper cover at least over half of our security concerns on average. To better compare the difference between academic-only papers and joint papers in terms of addressing security and privacy concerns, we visualize the number of papers addressing each concern in Fig. 7 . The first glance at Fig. 7 may give us an impression that the papers from academia have a broader coverage than the joint. This impression makes sense because academic-only papers are nearly three times more than joint papers. However, the number of academic-only papers addressing privacy (15) is five times the number of joint papers addressing privacy (three). Would this comparison imply that privacy (compared to other concerns) has gained more focus in academic-only papers than in industry-oriented papers? On the other hand, the number of academic-only papers addressing availability (eight) is four times the number of joint papers addressing availability (two). Would this comparison imply that availability has also gained more focus in academic-only papers than industry-oriented papers? The data that we have so far is not significant to make any strong statement to answer these questions. As previously mentioned, we do, however, want to highlight joint papers as more practical for industry. If we compare the amounts of academic and joint papers, we see that the number of joint papers is still low. We hope the number of joint papers will grow in the years to come with the current trend.
Difference between academic-only and joint papers in terms of security and privacy concerns
In terms of validation, implementation and execution testing, five (Portal et al. 2020 ; Karaarslan et al. 2020 ; Koshy et al. 2020 ; Attia et al. 2019 ; Pacheco et al. 2016 ) out of the nine domain-specific contributions do testing to verify their contribution in some form, while the generic domain contributions have 16 out of 24 papers doing testing, or some form of validation or analysis of a case. These numbers can be found in Table 4 representing “ Categorization of security pattern research ” section and “ IoT architecture ” section and by “testing”, we are referring to item C3 (research implementation/validation). We also see from this table that there are limited number of papers that discuss their purpose with their contribution. Four papers from the domain-specific category and 12 from the general domain category specified their purpose (item C1 ). However for describing their work with figures and diagrams we found 30 contributions (10 specific, 20 general) where in average the domain-specific studies have a higher ratio of including figures (item C2 ).
Table 4 also shows where the primary studies operate in the different layers of the IoT architecture presented in “ IoT architecture ” section. If we look at the numbers from the three-layer IoT architecture point of view, all three layers perception, network, and application have been almost completely covered by the different primary studies. However, the seven-layer IoT World Forum Reference Model of the IoT architecture can offer a closer view. We can see that the studies that explicitly address specific IoT application domains again have a higher average (4,33 layers per contribution) when it comes to layer coverage while general papers display a lower number (2,96 layers per contribution). In total, we see the coverage of 3,3 layers per contribution, which seems a little low considering there are seven layers in the architecture from the World Forum Reference Model (Juxtology 2018 ). In particular, we found that most of the primary studies do not work in all the layers, but rather operate in the Physical Devices and Controller ( L1 ), Connectivity ( L2 ), and Application ( L6 ) layers. There are four layers that have lower coverage in terms of the number of primary studies addressing IoT security challenges in those layers: Edge Computing ( L3 ), and especially, Data Accumulation ( L4 ), Data Abstraction ( L5 ), Collaboration and Processes ( L7 ).
Gaps and limitations (RQ3)
This section gives our answers to the RQ3.1 and RQ3.2 that are supported by the findings presented above. RQ3.1 — What are the current limitations of the IoT security patterns and architectures research? RQ3.2 — What research directions could be recommended for tackling the current limitations? Although there is a spike in the number of primary studies on IoT security patterns and architectures recently as presented in our answer for RQ1.1, our analyses show that IoT security patterns and architectures research is still in its beginning stages. This topic is yet to bloom, both in the industrial and academic universes. There are fundamental gaps and open issues to be handled.
The last decade was only the beginning of research efforts
One of the main limitations is that research on security patterns is still relatively “young” for IoT domain and premature, e.g., in terms of addressing all the different levels of IoT architecture reference model as presented in Table 4 , proper documentation and usage areas, as well as usage examples. Before conducting the review, we expected to see how existing security patterns being applied/adopted for IoT, and even more if new security patterns specific for IoT had emerged. But, based on the results of our review so far, we can say that the last decade has only marked the beginning of the research effort in this direction. The lack of evaluation in use cases or application in case studies as presented in our answer for RQ2.3 is one of the indicators of the premature work in most of the primary studies. Most of the contributions in the primary studies would only be ranked at the low levels (less than level five) in terms of the technology readiness levels (TRL). Footnote 19 We believe that (empirical) evaluations on the application of security patterns in IoT can make a substantial positive impact if more contributed to this research area. Empirical studies can provide more insights for any potential adopters of patterns to create more secure systems, or at least find a proven solution for a common problem.
Security patterns have proven to be very valuable for practitioners, especially non-security experts to adopt and build secure (IT) systems (Schumacher et al. 2013 ; Fernandez-Buglioni 2013 ). We would expect a similar impact of using security patterns in building secure IoT systems. Security patterns can help to mitigate the lack of knowledge from developers without security expertise, who are often under time-to-market pressure and as a result may contribute to more breaches and malicious usage, leading to more catastrophic incidents. Because, security patterns consist of domain-independent time-proven security knowledge, and expertise, they should be helpful, especially for addressing such limitations early in the development of IoT systems. We believe that security patterns can continue to be very valuable for practitioners, especially non-security experts, in building secure IoT systems. It would be even more so with a systematic understanding of different security patterns for addressing the heterogeneity of the IoT domain that our study could be a starting point for more comprehensive IoT domains. In other words, new research efforts could aim at building a catalog of security (and privacy) patterns more specifically and systematically for IoT.
The lack of addressing IoT-specific security and privacy challenges
Compatibility and complexity issues in IoT are other limitations that make security patterns and architectures less practical. An IoT system often makes use of multiple devices connected to a system(s) via a network(s). For example, one device could use a of protocols to communicate between nearby networks and other protocols to communicate with the service provider via IP. The heterogeneity of various communication protocols often used in IoT raises more security issues, which even get worse for complex IoT systems. So far, we have found patterns and architectures for mostly general issues and some specific issues that should work for their stated purposes. However, we have not encountered research that fulfills both types of issues that security patterns and architectures handle. In other words, we have not seen any approach that proposes a (systematic) top-down application of security patterns, first at the architectural level, then to more low-level details for addressing specific challenges in the heterogeneity of IoT, for example sometimes ad-hoc network, and weak links caused by tiny IoT devices.
From the results (see Table 2 ), we found that the quantity of security pattern approaches is less than the number of security architectures for IoT, and way too few compared to the initial numbers of the search results displayed in Fig. 2 . The quantity of existing papers that directly address security patterns for IoT is very low comparing to the explosion of the IoT as estimated by Gartner. Footnote 20 From the papers found, very few had characterized the patterns or architectures accordingly to the taxonomy categorization we constructed or characterized clearly in what layers of the IoT World Forum Reference Model Footnote 21 the contribution tackles (Fig. 8 ). We would, therefore, recommend that further research that should address thoroughly and systematically security pattern aspects for IoT systems.
Contributions distributed over the seven layers (Juxtology 2018 )
The status of addressing the top ten most common vulnerabilities within IoT
We also accumulated how the research contributions in the primary studies handle the different issues presented by the OWASP IoT top ten vulnerabilities list (OWASP 2018 ) as shown in Table 5 . This extraction was done to highlight more of this topic’s gaps to see how the existing contributions handle the top ten most common vulnerabilities within IoT (OWASP 2018 ). As we see from the extraction, vulnerabilities such as Insecure Network Services (I2), Insecure Ecosystem Interfaces (I3), and Insecure Data Transfer and Storage (I7) are the most covered vulnerabilities by the contributions. This spread of coverage is fair in terms of what the contributions present. Most of the solutions found are either in the communication part of the system or when interacting with multiple devices/systems. Most of the contributions are also descriptions proposing high-level architectural solutions and not detailing actual (physical) IoT products or devices. The other types of vulnerabilities, such as Weak, Guessable, or Hardcoded Passwords (I1), Insecure Default Settings (I9), Lack of Physical Hardening (I10), and so forth were not visible in the contributions of the primary studies. I2, I3, and I7 are appropriate vulnerabilities that these contributions should mitigate, however Insufficient Privacy Protection (I6) and Lack of Device Management (I8) should be more highlighted due to its natural occurrence within security patterns and architectures.
The need for new security patterns specifically for IoT
Other directions we recommend is to keep up the research on existing patterns and architectures, but also find out new security patterns specifically for IoT. The dominance of academia-only and a few joint collaboration in IoT security pattern research (see our answer to RQ1.3) suggests that there should be even more collaboration between academia and industry. Especially since the IoT market is blossoming and making the industry more aware, there should be approaches that are more practical and closer to the needs in the industry. This research should be both of research nature but should also aim to create an interest for industry and business owners. This way, we can get more test cases, gain more knowledge, and spread awareness around IoT security patterns in general. However, the ultimate goal of promoting IoT security patterns is to make it easier to improve and implement security features early in the development of IoT systems.
Related work
There have been some recent surveys focusing on different aspects of IoT engineering, from the deployment support (Nguyen et al. 2019 ) to actuation conflict management (Lavirotte et al. 2020 ). In Nguyen et al. ( 2019 ), the authors present the state of the art of IoT deployment approaches in which most approaches do not properly support software deployment and orchestration at the tiny IoT device level. Besides, trustworthiness aspects including security were not addressed properly in the existing approaches for IoT systems deployment and orchestration. The new challenges in the IoT domain can also be seen in the physical layer of IoT actuators. The SMS in Lavirotte et al. ( 2020 ) brings attention to the risk of actuation effects to safety and trustworthiness, and analyzes approaches for actuation conflicts management. However, these two recent surveys do not focus on security patterns for IoT.
There exist some other surveys that have addressed IoT security and IoT patterns, but none has systematically, specifically investigated security pattern approaches for IoT. Oracevic et al. ( 2017 ) surveyed IoT security. They want to shed light on this topic and spread awareness, with examples of IoT security solutions. The authors provide different measures on different levels to secure the systems but do not go into details. They also do not offer any form of architectures or patterns to solve common recurring problems for IoT security. Nguyen et al. ( 2015 ) has also reviewed security patterns-based approaches for new systems design and development. However, the reviewed approaches are not specific for IoT systems, which the focus of this work.
Washizaki et al. ( 2020 ) present a collection of papers that either describe IoT architectures or design patterns, or both. They also classify the patterns that are being used in detail as well as in which paper. They present a security column and specify which papers from their study have patterns that cover security. We looked through these papers, but not all of the papers did meet our criteria described in “ Inclusion and exclusion criteria ” section. The papers from Washizaki et al. ( 2020 ) that we analyzed and included as primary studies are Pape and Rannenberg ( 2019 ), Pahl et al. ( 2018 ), Lee and Law ( 2017 )) and Ntuli and Abu-Mahfouz ( 2016 ).
Reinfurt et al. ( 2016 ) give details of IoT patterns by investigating a large number of production-ready IoT offerings to extract recurring proven solution principles into patterns. These patterns show and describe how to help other individuals to understand different aspects of IoT, and also make it easier.
Qanbari et al. ( 2016 ) elaborates on how to design, build, and engineer applications for IoT systems and have created patterns to do these steps in an IoT system. They do not highlight security as one of their focus points, which is our main concern for this paper.
In general, these studies’ results not only address the functional aspects of IoT patterns but also some quality aspects, such as security and development, that we even considered in our work. However, they were not systematically and explicitly conducted to analyze the patterns and architectures for IoT security similar to our work. Note that we have clearly defined the scope of our SLR, which only considered peer-reviewed publications, not white papers from the industry. Thus, our SLR reports state of the art in IoT security pattern research, not including the state of practice in the industry.
Threats to validity
We mainly found the primary studies of this work from the database search process. The search features provided by the five online publication databases are very different from each other. We had to adapt our search string to make use of the provided search features of the publication databases. We tried to use the keywords and built search strings that were not too strict to obtain as many relevant papers as possible. However, it would be impossible to have perfect search strings for the database search process.
There is a possibility that we missed some studies that should have been included in the final set of primary studies. We have tried to mitigate possible missing primary studies of the database search process by the manual search process. While doing snowballing, we saw again some primary studies that we already found from the database search process. Removing the duplicates, we managed to get six more new primary studies that have not been found from the database search process. There were some other relevant papers from snowballing, but they finally did not pass our selection criteria. These few studies may have fulfilled our criteria but may have failed to detail what they did or did not detail enough to include them according to our criteria confidently. We ended our search and selection process in the beginning of December 2020, which means that our review does not completely cover all the publications in 2020, but a major part of them.
The primary studies that passed our selection criteria could still have limitations that make their contributions unreliable or flawed. Because many of the contributions do not have test cases or examples, it can be hard to know if the patterns and architectures do what they are supposed to. It also creates uncertainty regarding how good the patterns preserve or contain the security in already existing systems. To mitigate this risk, we conducted cross-checks between at least two reviewers for some papers in doubt to remove any papers that do not have enough scientific contributions according to our selection criteria.
Conclusions
In this paper, we have presented our systematic review on patterns and architectures for IoT security. After systematically recognizing and reviewing 36 primary studies out of thousands of relevant papers in this domain, we have discovered that there is a slight rise in the number of publications addressing security patterns and architectures in the two recent years. However, our analysis has shown that security patterns are relatively “young” for the IoT domain and we have found more papers with main contributions categorized as architectures rather than patterns. This indicates that more efforts are needed in terms of formalization, proper documentation and adoption. We have not seen any approaches that combine architectural patterns or even IoT security reference architectures with other design patterns. Similarly, we have not seen architectural patterns or IoT security reference architectures referring to any design pattern they would be composed of. This includes patterns at the IoT “weak links”: the network and IoT devices levels. Most of the primary studies do not work in all the seven layers of the IoT World Forum Reference Model for IoT architecture. They mainly operate in the Physical Devices and Controller ( L1 ), Connectivity ( L2 ), and Application ( L6 ) layers. There are four layers that have little coverage in terms of patterns and architectures for addressing IoT security challenges: Edge Computing ( L3 ), Data Accumulation ( L4 ), Data Abstraction ( L5 ), Collaboration and Processes ( L7 ). We also accumulated how the research contributions in the primary studies handle the different issues presented by the OWASP IoT top ten vulnerabilities list.
New IoT systems development should concentrate more on tending to security, which can be improved with progressively relevant security patterns to apply and reuse. In other words, we need to promote the utilization of patterns for IoT security (and privacy) by design. To make security patterns for IoT approaches more viable, we consider the research collaboration between academia and industry is key in this domain. Security patterns in literature can be researched and applied in developing secure IoT systems with industrial context. Vice versa, experiences gained from securing industrial IoT systems can help to improve existing security patterns for IoT, or even new ones can emerge.
Availability of data and materials
All the data of our work is available in Google Drive https://drive.google.com/drive/folders/19CbTTYauf4ijpcSSlN0yySZLz8QIgscJ?usp=sharing .
https://www.idc.com/ .
NIS Directive, https://ec.europa.eu/digital-single-market/en/network-and-information-security-nis-directive .
A. Dasgupta, The Continuum: Big Data, Cloud & Internet of Things, IBM Internet of Things blog, 2017.
Gartner, The Death of IoT Security as You Know It, Gartner, 2017.
https://ieeexplore.ieee.org .
https://dlnext.acm.org .
https://sciencedirect.com/ .
http://apps.webofknowledge.com .
https://scopus.com .
https://www.springer.com .
https://iot-conference.org/iot2020/ .
https://hillside.net/conferences .
https://www.europlop.net/ .
https://conferences.computer.org/iciot/2019/ .
https://dl.acm.org/journal/tiot .
https://ieee-iotj.org/ .
Our search and selection process for the primary studies concluded in December 2020
Our search and selection process covers the period until December 2020.
The use of TRLs in the Horizon 2020 Work Programmes ( https://ec.europa.eu/info/funding-tenders/opportunities/portal/screen/support/faq/2890 ).
Gartner, November 2018 ( https://www.gartner.com/en/newsroom/press-releases/2018-11-07-gartner-identifies-top-10-strategic-iot-technologies-and-trends ).
Juxtology - IoT: Architecture ( https://www.m2mology.com/iot-transformation/iot-world-forum/ ).
Abbreviations
- Internet of Things
Alphand O, Amoretti M, Claeys T, Dall’Asta S, Duda A, Ferrari G, Rousseau F, Tourancheau B, Veltri L, Zanichelli F (2018) IoTChain: a blockchain security architecture for the Internet of Things, vol. 2018-April, pp 1–6. https://doi.org/10.1109/WCNC.2018.8377385
Attia O, Khoufi I, Laouiti A, Adjih C (2019) An IoT-blockchain architecture based on hyperledger framework for healthcare monitoring application. In: 2019 10th IFIP international conference on new technologies, mobility and security (NTMS), pp 1–5. https://doi.org/10.1109/NTMS.2019.8763849
Borgia E, Gomes DG, Lagesse B, Lea RJ, Puccinelli D (2016) Special issue on “internet of things: research challenges and solutions”. Comput Commun 89:1–4
Ciccozzi F, Crnkovic I, Di Ruscio D, Malavolta I, Pelliccione P, Spalazzese R (2017) Model-driven engineering for mission-critical iot systems. IEEE Softw 34(1):46–53
Article Google Scholar
Covington MJ, Carskadden R (2013) Threat implications of the internet of things. In: 2013 5th international conference on cyber conflict (CYCON 2013), pp 1–12
Create-IoT (2018) Deliverable D6.02—Recommendations for commonalities and interoperability profiles of IoT platforms. https://european-iot-pilots.eu/wp-content/uploads/2018/11/D06_02_WP06_H2020_CREATE-IoT_Final.pdf . Accessed 30 Sept 2021
Dhieb N, Ghazzai H, Besbes H, Massoud Y (2020) Scalable and secure architecture for distributed iot systems. In: 2020 IEEE technology engineering management conference (TEMSCON), pp 1–6. https://doi.org/10.1109/TEMSCON47658.2020.9140108
Dougherty C, Sayre K, Seacord RC, Svoboda D, Togashi K (2009) Secure design patterns. Technical report, Carnegie-Mellon Univ Pittsburgh PA Software Engineering Inst
Durresi M, Subashi A, Durresi A, Barolli L, Uchida K (2019) Secure communication architecture for internet of things using smartphones and multi-access edge computing in environment monitoring. J Ambient Intell Humaniz Comput 10(4):1631–1640. https://doi.org/10.1007/s12652-018-0759-6
Federal Trade Commission (1999) How to comply with the privacy of consumer financial information rule of the Gramm-Leach-Bliley Act. https://www.ftc.gov/tips-advice/business-center/guidance/how-comply-privacy-consumer-financial-information-rule-gramm . Accessed 29 Sept 2020
Fernandez-Buglioni E (2013) Security patterns in practice: designing secure architectures using software patterns. Wiley, Hoboken
Google Scholar
Ferry N, Brataas G, Rossini A, Chauvel F, Solberg A (2014) Towards bridging the gap between scalability and elasticity. CLOSER 10:0004975307460751
Fysarakis K, Spanoudakis G, Petroulakis N, Soultatos O, Broring A, Marktscheffel T (2019) Architectural patterns for secure iot orchestrations. In: 2019 Global IoT Summit (GIoTS), pp 1–6. https://doi.org/10.1109/GIOTS.2019.8766425
Gamma E, Helm R, Johnson R, Vlissides JM (1994) Design patterns: elements of reusable object-oriented software, 1st edn. Addison-Wesley Professional, Boston
MATH Google Scholar
Garcia-Morchon O, Keoh SL, Kumar S, Moreno-Sanchez P, Vidal-Meca F, Ziegeldorf JH (2013) Securing the ip-based internet of things with hip and dtls. In: Proceedings of the sixth ACM conference on security and privacy in wireless and mobile networks. WiSec ’13. Association for Computing Machinery, New York, NY, USA, pp 119–124. https://doi.org/10.1145/2462096.2462117
Goncalves F, Macedo J, Nicolau MJ, Santos A (2013) Security architecture for mobile e-health applications in medication control. In: 2013 21st international conference on software, telecommunications and computer networks—(SoftCOM 2013), pp 1–8. https://doi.org/10.1109/SoftCOM.2013.6671901
IEEE SA, S.A. (2018) IEEE draft standard for an architectural framework for the internet of things (IoT). IEEE P2413/D0.4.5, December 2018, pp 1–264
Jerald AV, Rabara SA, Arun Gnana Raj A (2019) Secured architecture for integrated iot enabled smart services. Int J Recent Technol Eng 8(3):7384–7393. https://doi.org/10.35940/ijrte.C6145.098319
Juxtology (2018) IoT: architecture. https://www.m2mology.com/iot-transformation/iot-world-forum/ . Accessed 27 July 2020
Karaarslan E, Karabacak E, Cetinkaya C (2020) Design and implementation of sdn-based secure architecture for iot-lab. In: Hemanth DJ, Kose U (eds) Artificial intelligence and applied mathematics in engineering problems. Springer, Cham, pp 877–885
Chapter Google Scholar
Karmakar KK, Varadharajan V, Nepal S, Tupakula U (2019) SDN enabled secure IoT architecture, pp 581–585. https://www.scopus.com/inward/record.uri?eid=2-s2.0-85066971444&partnerID=40&md5=c0f52e2ce49d38dad5d181190e28e795
Kitchenham BA, Charters S (2007) Guidelines for performing systematic literature reviews in software engineering. Technical Report EBSE 2007-001, Keele University and Durham University Joint Report . https://doi.org/10.1145/2372233.2372235
Kitchenham BA, Budgen D, Brereton OP (2011) Using mapping studies as the basis for further research—a participant-observer case study. Inf Softw Technol 53(6):638–651. https://doi.org/10.1016/j.infsof.2010.12.011 ( Special Section: Best papers from the APSEC )
Koo J, Oh SR, Lee SH, Kim YG (2020) Security architecture for cloud-based command and control system in iot environment. Appl Sci 10:1035. https://doi.org/10.3390/app10031035
Koshy P, Babu S, Manoj BS (2020) Sliding window blockchain architecture for internet of things. IEEE Internet Things J 7(4):3338–3348. https://doi.org/10.1109/JIOT.2020.2967119
Kuhn DR, Hu VC, Polk WT, Chang S-J (2001) NIST SP 800-32, introduction to public key technology and the federal PKI infrastructure. National Institute of Standards & Technology, p 54. https://doi.org/10.6028/NIST.SP.800-32
Lavirotte S, Rocher G, Tigli J, Gonnin T (2020) IoT-based systems actuation conflicts management towards DevOps: a systematic mapping study. In: Proceedings of the 5th international conference on internet of things, big data and security, vol 1. IoTBDS, pp 227–234. SciTePress. https://doi.org/10.5220/0009355102270234 . INSTICC
Lee W, Law P (2017) A case study in applying security design patterns for iot software system. In: 2017 international conference on applied system innovation (ICASI), pp 1162–1165. https://doi.org/10.1109/ICASI.2017.7988402
Lessa dos Santos G, Guimaraes VT, da Cunha Rodrigues G, Granville LZ, Tarouco LMR (2015) A dtls-based security architecture for the internet of things. In: 2015 IEEE symposium on computers and communication (ISCC), pp 809–815. https://doi.org/10.1109/ISCC.2015.7405613
Nguyen PH, Yskout K, Heyman T, Klein J, Scandariato R, Le Traon Y (2015) Sospa: a system of security design patterns for systematically engineering secure systems. In: 2015 ACM/IEEE 18th international conference on model driven engineering languages and systems (MODELS), pp 246–255. https://doi.org/10.1109/MODELS.2015.7338255
Nguyen PH, Kramer M, Klein J, Traon YL (2015) An extensive systematic review on the model-driven development of secure systems. Inf Softw Technol 68:62–81. https://doi.org/10.1016/j.infsof.2015.08.006
Nguyen PH, Ali S, Yue T (2017) Model-based security engineering for cyber-physical systems: a systematic mapping study. Inf Softw Technol 83:116–135. https://doi.org/10.1016/j.infsof.2016.11.004
Nguyen P, Ferry N, Erdogan G, Song H, Lavirotte S, Tigli J, Solberg A (2019) Advances in deployment and orchestration approaches for IoT—a systematic review. In: 2019 IEEE international congress on Internet of Things (ICIOT), pp 53–60. https://doi.org/10.1109/ICIOT.2019.00021
Ntuli N, Abu-Mahfouz A (2016) A simple security architecture for smart water management system. Procedia Comput Sci 83:1164–1169. https://doi.org/10.1016/j.procs.2016.04.239 . The 7th international conference on ambient systems, networks and technologies (ANT 2016)/The 6th international conference on sustainable energy information technology (SEIT-2016)/Affiliated workshops
Office for Civil Rights (2013) Summary of the HIPAA security rule. https://www.hhs.gov/hipaa/for-professionals/security/laws-regulations/index.html . Accessed 29 Sept 2020
Oracevic A, Dilek S, Ozdemir S (2017) Security in internet of things: a survey. In: 2017 international symposium on networks, computers and communications (ISNCC), pp 1–6 . https://doi.org/10.1109/ISNCC.2017.8072001
OWASP (2018) Internet of Things (IoT) Top 10 2018. https://owasp.org/www-pdf-archive/OWASP-IoT-Top-10-2018-final.pdf . Accessed 30 Sept 2020
Pacheco J, Ibarra D, Vijay A, Hariri S (2018) IoT security framework for smart water system. In: 2017 IEEE/ACS 14th international conference on computer systems and applications (AICCSA), vol 2017-October, pp 1285–1292. https://doi.org/10.1109/AICCSA.2017.85
Pacheco J, Satam S, Hariri S, Grijalva C, Berkenbrock H (2016) IoT security development framework for building trustworthy smart car services, pp 237–242. https://doi.org/10.1109/ISI.2016.7745481
Pacheco J, Tunc C, Hariri S (2019) Security framework for IoT cloud services, vol 2018-November . https://doi.org/10.1109/AICCSA.2018.8612808
Pahl C, Ioini NE, Helmer S, Lee B (2018) An architecture pattern for trusted orchestration in iot edge clouds. In: 2018 third international conference on fog and mobile edge computing (FMEC), pp 63–70. https://doi.org/10.1109/FMEC.2018.8364046
Paillier P (1999) Public-key cryptosystems based on composite degree residuosity classes. In: Stern J (ed) Advances in cryptology—EUROCRYPT ’99. Springer, Berlin, Heidelberg, pp 223–238
Pape S, Rannenberg K (2019) Applying privacy patterns to the internet of things’ (iot) architecture. Mobile Netw Appl 24(3):925–933. https://doi.org/10.1007/s11036-018-1148-2
Park C (2020) Security architecture for secure multicast coap applications. IEEE Internet Things J 7(4):3441–3452. https://doi.org/10.1109/JIOT.2020.2970175
Perera C, Barhamgi M, Bandara AK, Ajmal M, Price B, Nuseibeh B (2020) Designing privacy-aware internet of things applications. Inf Sci 512:238–257. https://doi.org/10.1016/j.ins.2019.09.061
Petersen K, Vakkalanka S, Kuzniarz L (2015) Guidelines for conducting systematic mapping studies in software engineering: an update. Inf Softw Technol 64:1–18
Petroulakis NE, Lakka E, Sakic E, Kulkarni V, Fysarakis K, Somarakis I, Serra J, Sanabria-Russo L, Pau D, Falchetto M, Presenza D, Marktscheffel T, Ramantas K, Mekikis P, Ciechomski L, Waledzik K (2019) Semiotics architectural framework: End-to-end security, connectivity and interoperability for industrial iot. In: 2019 Global IoT Summit (GIoTS), pp 1–6. https://doi.org/10.1109/GIOTS.2019.8766399
Porambage P, Ylianttila M, Schmitt C, Kumar P, Gurtov A, Vasilakos AV (2016) The quest for privacy in the internet of things. IEEE Cloud Comput 3(2):36–45
Portal G, de Matos E, Hessel F (2020) An edge decentralized security architecture for industrial iot applications. In: 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), pp 1–6. https://doi.org/10.1109/WF-IoT48130.2020.9221176
Qanbari S, Pezeshki S, Raisi R, Mahdizadeh S, Rahimzadeh R, Behinaein N, Mahmoudi F, Ayoubzadeh S, Fazlali P, Roshani K, Yaghini A, Amiri M, Farivarmoheb A, Zamani A, Dustdar S (2016) IoT design patterns: computational constructs to design, build and engineer edge applications. In: 2016 IEEE first international conference on Internet-of-Things design and implementation (IoTDI), pp 277–282. https://doi.org/10.1109/IoTDI.2015.18
Rajmohan T, Nguyen PH, Ferry N (2020) Research landscape of patterns and architectures for iot security: a systematic review. In: 2020 46th Euromicro conference on software engineering and advanced applications (SEAA), pp 463–470. https://doi.org/10.1109/SEAA51224.2020.00079
Reinfurt L, Breitenbücher U, Falkenthal M, Leymann F, Riegg A (2016) Internet of things patterns. In: Proceedings of the 21st European conference on pattern languages of programs. EuroPlop ’16. ACM, New York, NY, USA. https://doi.org/10.1145/3011784.3011789
Richa E (2021) Iot: security issues and challenges. In: Senjyu T, Mahalle PN, Perumal T, Joshi A (eds) Information and communication technology for intelligent systems. Springer, Singapore, pp 87–96
Robles Enciso A, Zarca A, Garcia Carrillo D, Hernandez-Ramos J, Bernal Bernabe J, Skarmeta A, Matheu Garcia SN (2020) Security architecture for defining and enforcing security profiles in dlt/sdn-based iot systems. Sensors 20:1882. https://doi.org/10.3390/s20071882
Roman R, Najera P, Lopez J (2011) Securing the internet of things. Computer 44(9):51–58
Ross R, McEvilley M, Oren J (2016) NIST SP 800-160, systems security engineering considerations for a multidisciplinary approach in the engineering of trustworthy secure systems. National Institute of Standards & Technology, p 243. https://doi.org/10.6028/NIST.SP.800-160v1
Schmidt DC, Buschmann F (2003) Patterns, frameworks, and middleware: their synergistic relationships. In: 25th international conference on software engineering, 2003. Proceedings, pp 694–704
Schneier B (2017) Iot security: what’s plan b? IEEE Secur Privacy 15(05):96. https://doi.org/10.1109/MSP.2017.3681066
Schumacher M, Fernandez-Buglioni E, Hybertson D, Buschmann F, Sommerlad P (2013) Security patterns: integrating security and systems engineering. Wiley, Hoboken
Schuß M, Iber J, Dobaj J, Kreiner C, Boano CA, Römer K (2018) Iot device security the hard(ware) way. In: Proceedings of the 23rd European conference on pattern languages of programs. EuroPLoP ’18. ACM, New York, NY, USA, pp 20–1204. https://doi.org/10.1145/3282308.3282329
Steel C, Nagappan R (2006) Core security patterns: best practices and strategies for J2EE”, web services, and identity management. Pearson Education, London
Syed MH, Fernandez EB, Moreno J (2018) A misuse pattern for ddos in the iot. In: Proceedings of the 23rd European conference on pattern languages of programs. EuroPLoP ’18. ACM, New York, NY, USA, pp 34–1345. https://doi.org/10.1145/3282308.3282343
Tiburski RT, Moratelli CR, Johann SF, Neves MV, Matos ED, Amaral LA, Hessel F (2019) Lightweight security architecture based on embedded virtualization and trust mechanisms for iot edge devices. IEEE Commun Mag 57(2):67–73. https://doi.org/10.1109/MCOM.2018.1701047
Tran NK, Sheng QZ, Babar MA, Yao L (2017) Searching the web of things: state of the art, challenges, and solutions. ACM Comput Surv (CSUR) 50(4):55
Ur-Rehman O, Zivic N (2015) Secure design patterns for security in smart metering systems. In: 2015 IEEE European modelling symposium (EMS), pp 278–283. https://doi.org/10.1109/EMS.2015.49
Vijayakumaran C, Senthil M, Manickavasagam B (2020) A reliable next generation cyber security architecture for industrial internet of things environment. Int J Electr Comput Eng: IJECE 10:387. https://doi.org/10.11591/ijece.v10i1.pp387-395
Vithya Vijayalakshmi A, Arockiam L (2020) A secured architecture for iot healthcare system. In: Pandian AP, Senjyu T, Islam SMS, Wang H (eds) Proceeding of the international conference on computer networks, big data and IoT (ICCBI-2018). Springer, Cham, pp 904–911
Vučinić M, Tourancheau B, Rousseau F, Duda A, Damon L, Guizzetti R (2015) Oscar: object security architecture for the internet of things. Ad Hoc Netw 32:3–16. https://doi.org/10.1016/j.adhoc.2014.12.005 ( Internet of Things security and privacy: design methods and optimization )
Washizaki H, Ogata S, Hazeyama A, Okubo T, Fernandez EB, Yoshioka N (2020) Landscape of architecture and design patterns for iot systems. In: IEEE Internet of Things Journal 2020 (early Access), p 1. https://doi.org/10.1109/JIOT.2020.3003528
Washizaki H, Xia T, Kamata N, Fukazawa Y, Kanuka H, Yamaoto D, Yoshino M, Okubo T, Ogata S, Kaiya H, Kato T, Hazeyama A, Tanaka T, Yoshioka N, Priyalakshmi G (2018) Taxonomy and literature survey of security pattern research. In: 2018 IEEE conference on application, information and network security (AINS), pp 87–92. https://doi.org/10.1109/AINS.2018.8631465
Williams-Grut O (2018) Hackers once stole a casino’s high-roller database through a thermometer in the lobby fish tank. https://www.businessinsider.com/hackers-stole-a-casinos-database-through-a-thermometer-in-the-lobby-fish-tank-2018-4?r=US&IR=T . Accessed 20 Aug 2020
Witti M, Konstantas D (2018) A secure and privacy-preserving internet of things framework for smart city. In: Proceedings of the 6th international conference on information technology: IoT and smart city. ICIT 2018. Association for Computing Machinery, New York, NY, USA, pp 145–150. https://doi.org/10.1145/3301551.3301607
Wohlin C (2014) Guidelines for snowballing in systematic literature studies and a replication in software engineering. In: Proceedings of the 18th international conference on evaluation and assessment in software engineering. ACM, p 38
Wright M (2020) Default passwords banned for smart devices as part of hacking crackdown. https://www.telegraph.co.uk/news/2020/01/27/default-passwords-banned-smart-devices-part-hacking-crackdown/ . Accessed 20 June 2020
Yampolskiy M, Horvath P, Koutsoukos XD, Xue Y, Sztipanovits J (2013) Taxonomy for description of cross-domain attacks on cps. In: Proceedings of the 2nd ACM international conference on high confidence networked systems. HiCoNS ’13. Association for Computing Machinery, New York, NY, USA, pp 135–142. https://doi.org/10.1145/2461446.2461465
Ye F, Qian Y (2017) A security architecture for networked Internet of Things devices, vol 2018-January, pp 1–6. https://doi.org/10.1109/GLOCOM.2017.8254021
Yskout K, Heyman T, Scandariato R, Joosen W (2006) A system of security patterns. CW Reports. http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.142.4538
Zhang J, Jin H, Gong L, Cao J, Gu Z (2019) Overview of IoT security architecture, pp 338–345. https://doi.org/10.1109/DSC.2019.00058
Zhu X, Badr Y (2018) Fog computing security architecture for the internet of things using blockchain-based social networks. In: 2018 IEEE international conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), pp 1361–1366
Download references
Acknowledgements
The research leading to these results has partially received funding from the European Commission's H2020 Programme under the grant agreement numbers 958363 (Dat4.ZERO), and 958357 (InterQ).
Author information
Authors and affiliations.
Capgemini, Oslo, Norway
Tanusan Rajmohan
SINTEF, Oslo, Norway
Phu H. Nguyen
Université Côte d’Azur, I3S/INRIA Kairos, Sophia Antipolis, France
Nicolas Ferry
You can also search for this author in PubMed Google Scholar
Contributions
All authors contributed to all the steps of conducting this work and writing this manuscript. All the authors read and approved the final manuscript.
Corresponding author
Correspondence to Phu H. Nguyen .

Ethics declarations
Ethics approval and consent to participate.
Not applicable.
Consent for publication
Competing interests.
The authors declare that they have no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Rajmohan, T., Nguyen, P.H. & Ferry, N. A decade of research on patterns and architectures for IoT security. Cybersecurity 5 , 2 (2022). https://doi.org/10.1186/s42400-021-00104-7
Download citation
Received : 30 April 2021
Accepted : 17 November 2021
Published : 05 January 2022
DOI : https://doi.org/10.1186/s42400-021-00104-7
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Architecture
Internet of Things (IoT) Cybersecurity Research: A Review of Current Research Topics
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
- Skip to content
- Skip to search
- Skip to footer
Products, Solutions, and Services
Want some help finding the Cisco products that fit your needs? You're in the right place. If you want troubleshooting help, documentation, other support, or downloads, visit our technical support area .
Contact Cisco
- Get a call from Sales
Call Sales:
- 1-800-553-6387
- US/CAN | 5am-5pm PT
- Product / Technical Support
- Training & Certification
Products by technology

- Software-defined networking
- Cisco Silicon One
- Cloud and network management
- Interfaces and modules
- Optical networking
- See all Networking

Wireless and Mobility
- Access points
- Outdoor and industrial access points
- Controllers
- See all Wireless and Mobility

- Secure Firewall
- Secure Endpoint
- Secure Email
- Secure Access
- Multicloud Defense
- See all Security

Collaboration
- Collaboration endpoints
- Conferencing
- Cisco Contact Center
- Unified communications
- Experience Management
- See all Collaboration

Data Center
- Servers: Cisco Unified Computing System
- Cloud Networking
- Hyperconverged infrastructure
- Storage networking
- See all Data Center
- Nexus Dashboard Insights
- Network analytics
- Cisco Secure Network Analytics (Stealthwatch)

- Video endpoints
- Cisco Vision
- See all Video

Internet of Things (IoT)
- Industrial Networking
- Industrial Routers and Gateways
- Industrial Security
- Industrial Switching
- Industrial Wireless
- Industrial Connectivity Management
- Extended Enterprise
- Data Management
- See all industrial IoT
- Cisco+ (as-a-service)
- Cisco buying programs
- Cisco Nexus Dashboard
- Cisco Networking Software
- Cisco DNA Software for Wireless
- Cisco DNA Software for Switching
- Cisco DNA Software for SD-WAN and Routing
- Cisco Intersight for Compute and Cloud
- Cisco ONE for Data Center Compute and Cloud
- See all Software
- Product index
Products by business type

Service providers

Small business

Midsize business
Cisco can provide your organization with solutions for everything from networking and data center to collaboration and security. Find the options best suited to your business needs.
- By technology
- By industry
- See all solutions
CX Services
Cisco and our partners can help you transform with less risk and effort while making sure your technology delivers tangible business value.
- See all services
Design Zone: Cisco design guides by category
Data center
- See all Cisco design guides
End-of-sale and end-of-life
- End-of-sale and end-of-life products
- End-of-Life Policy
- Cisco Commerce Build & Price
- Cisco Software Central
- Cisco Feature Navigator
- See all product tools
- Cisco Mobile Apps
- Design Zone: Cisco design guides
- Cisco DevNet
- Marketplace Solutions Catalog
- Product approvals
- Product identification standard
- Product warranties
- Cisco Security Advisories
- Security Vulnerability Policy
- Visio stencils
- Local Resellers
- Technical Support
Role of Artificial Intelligence in the Internet of Things (IoT) cybersecurity
- Open access
- Published: 24 February 2021
- Volume 1 , article number 7 , ( 2021 )
Cite this article
You have full access to this open access article

- Murat Kuzlu 1 ,
- Corinne Fair 2 &
- Ozgur Guler 3
47k Accesses
99 Citations
21 Altmetric
Explore all metrics
In recent years, the use of the Internet of Things (IoT) has increased exponentially, and cybersecurity concerns have increased along with it. On the cutting edge of cybersecurity is Artificial Intelligence (AI), which is used for the development of complex algorithms to protect networks and systems, including IoT systems. However, cyber-attackers have figured out how to exploit AI and have even begun to use adversarial AI in order to carry out cybersecurity attacks. This review paper compiles information from several other surveys and research papers regarding IoT, AI, and attacks with and against AI and explores the relationship between these three topics with the purpose of comprehensively presenting and summarizing relevant literature in these fields.
Similar content being viewed by others

AI-Driven Cybersecurity: An Overview, Security Intelligence Modeling and Research Directions

RETRACTED ARTICLE: A Review and State of Art of Internet of Things (IoT)

Cybersecurity data science: an overview from machine learning perspective
Avoid common mistakes on your manuscript.
1 Introduction
Since around 2008, when the Internet of Things (IoT) was born [ 1 ], its growth has been booming, and now IoT is a part of daily life and has a place in many homes and businesses. IoT is hard to define as it has been evolving and changing since its conception, but it can be best understood as a network of digital and analog machines and computing devices provided with unique identifiers (UIDs) that have the ability to exchange data without human intervention [ 2 ]. In most cases, this manifests as a human interfacing with a central hub device or application, often a mobile app, that then goes on to send data and instructions to one or multiple fringe IoT devices [ 3 ]. The fringe devices are able to complete functions if required and send data back to the hub device or application, which the human can then view.
The IoT concept has given the world a higher level of accessibility, integrity, availability, scalability, confidentiality, and interoperability in terms of device connectivity [ 4 ]. However, IoTs are vulnerable to cyberattacks due to a combination of their multiple attack surfaces and their newness and thus lack of security standardizations and requirements [ 5 ]. There are a large variety of cyberattacks that attackers can leverage against IoTs, depending on what aspect of the system they are targeting and what they hope to gain from the attack. As such, there is a large volume of research into cybersecurity surrounding IoT. This includes Artificial Intelligence (AI) approaches to protecting IoT systems from attackers, usually in terms of detecting unusual behavior that may indicate an attack is occurring [ 6 ]. However, in the case of IoT, cyber-attackers always have the upper hand as they only need to find one vulnerability while cybersecurity experts must protect multiple targets. This has led to increased use of AI by cyber-attackers as well, in order to thwart the complicated algorithms that detect anomalous activity and pass by unnoticed [ 7 ]. AI has received much attention with the growth of IoT technologies. With this growth, AI technologies, such as decision trees, linear regression, machine learning, support vector machines, and neural networks, have been used in IoT cybersecurity applications to able to identify threats and potential attacks.
Authors in [ 8 ] provide a comprehensive review of the security risks related to IoT application and possible counteractions as well as compare IoT technologies in terms of integrity, anonymity, confidentiality, privacy, access control, authentication, authorization, resilience, and self-organization. The authors propose deep learning models using CICIDS2017 datasets for DDoS attack detection for the cybersecurity in IoT (Internet of Things), which provide high accuracy, i.e., 97.16% [ 9 ]. In [ 10 ], the authors evaluate the Artificial Neural Networks (ANN) in a gateway device to able to detect anomalies in the data sent from the edge devices. The results show that the proposed approach can improve the security of IoT systems. The authors in [ 11 ] propose an AI-based control approach for detection and estimation as well as compensation of cyber attacks in industrial IoT systems. In [ 12 ], The authors provide a robust pervasive detection for IoT Environments and develop a variety of adversarial attacks and defense mechanisms against them as well as validate their approach through datasets including MNIST, CIFAR-10, and SVHN. In [ 13 ], the authors analyze the recent evolution of AI decision-making in cyber physical systems and find that such evolution is virtually autonomous due to the increasing integration of IoT devices in cyber physical systems, and the value of AI decision-making due to its speed and efficiency in handling large loads of data is likely going to make this evolution inevitable. The authors of [ 14 ] discuss new approaches to risk analytics using AI and machine learning, particularly in IoT networks present in industry settings. Finally, [ 15 ] discusses methods of capturing and assessing cybersecurity risks to IoT devices for the purpose of standardizing such practices so that risk in IoT systems may be more efficiently identified and protected against.
This review paper covers a variety of topics regarding cybersecurity, the Internet of Things (IoT), Artificial Intelligence (AI), and how they all relate to each other in three survey-style sections and provides a comprehensive review of cyberattacks against IoT devices as well as provides recommended AI-based methods of protecting against these attacks. The ultimate goal of this paper is to create a resource for others who are researching these prevalent topics by presenting summaries of and making connections between relevant works covering different aspects of these subjects.
2 Methods of attacking IoT devices
Due to the lax security in many IoT devices, cyberattackers have found many ways to attack IoT devices from many different attack surfaces. Attack surfaces can vary from the IoT device itself, both its hardware and software, the network on which the IoT device is connected to, and the application with which the device interfaces; these are the three most commonly used attack surfaces as together they make up the main parts of an IoT system. Figure 1 illustrates a basic breakdown of a common IoT system; most of the attacks discussed in this paper occur at the network gateway and/or cloud data server connections, as these connections are generally where IoT security is most lacking.
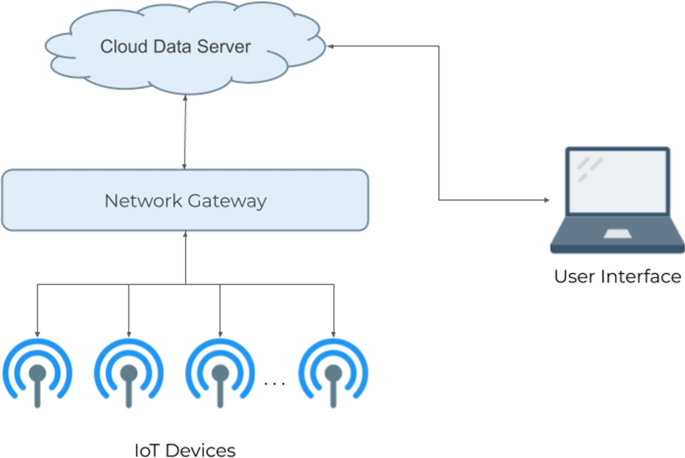
A high-level breakdown of typical IoT structure
2.1 Initial reconnaissance
Before IoT attackers even attempt cyberattacks on an IoT device, they will often study the device to identify vulnerabilities. This is often done by buying a copy of the IoT device they are targeting from the market. They then reverse engineer the device to create a test attack to see what outputs can be obtained and what avenues exist to attack the device. Examples of this include opening up the device and analyzing the internal hardware—such as the flash memory—in order to learn about the software, and tampering with the microcontroller to identify sensitive information or cause unintended behavior [ 16 ]. In order to counter reverse engineering, it is important for IoT devices to have hardware-based security. The application processor, which consists of sensors, actuators, power supply, and connectivity, should be placed in a tamper-resistant environment [ 16 ]. Device authentication can also be done with hardware-based security, such that the device can prove to the server it is connected to that it is not fake.
2.2 Physical attacks
An often low-tech type category of attacks includes physical attacks, in which the hardware of the target device is used to the benefit of the attacker in some way. There are several different types of physical attacks. These include attacks such as outage attacks, where the network that the devices are connected to are shut off to disrupt their functions; physical damage, where devices or their components are damaged to prevent proper functionality; malicious code injection, an example of which includes an attacker plugging a USB containing a virus into the target device; and object jamming, in which signal jammers are used to block or manipulate the signals put out by the devices [ 17 ]. Permanent denial of service (PDoS) attacks, which are discussed later in this paper, can be carried out as a physical attack; if an IoT device is connected to a high voltage power source, for example, its power system may become overloaded and would then require replacement [ 18 ].
2.3 Man-in-the-Middle
One of the most popular attacks on IoTs is Man-in-the-Middle (MITM) attack. With regards to computers in general, an MITM attack intercepts communication between two nodes and allows the attacker to take the role of a proxy. Attackers can perform MITM attacks between many different connections such as a computer and a router, two cell phones, and, most commonly, a server and a client. Figure 2 shows a basic example of an MITM attack between a client and a server. In regards to IoT, the attacker usually performs MITM attacks between an IoT device and the application with which it interfaces. IoT devices, in particular, tend to be more vulnerable to MITM attacks as they lack the standard implementations to fight the attacks. There are two common modes of MITM attacks: cloud polling and direct connection. In cloud polling, the smart home device is in constant communication with the cloud, usually to look for firmware updates. Attackers can redirect network traffic using Address Resolution Protocol (ARP) poisoning or by altering Domain Name System (DNS) settings or intercept HTTPS traffic by using self-signed certificates or tools such as (Secure Sockets Layer) SSL strip [ 19 ]. Many IoT devices do not verify the authenticity or the trust level of certificates, making the self-signed certificate method particularly effective. In the case of direct connections, devices communicate with a hub or application in the same network. By doing this, mobile apps can locate new devices by probing every IP address on the local network for a specific port. An attacker can do the same thing to discover devices on the network [ 19 ]. An example of an MITM IoT attack is that of a smart refrigerator that could display the user’s Google calendar. It seems like a harmless feature, but attackers found that the system did not validate SSL certificates, which allowed them to perform an MITM attack and steal the user’s Google credentials [ 19 ].

A simple representation of a Man-in-the-Middle attack
2.3.1 Bluetooth Man-in-the-Middle
A common form of MITM attack leveraged against IoT devices is via Bluetooth connection. Many IoT devices run Bluetooth Low Energy (BLE), which is designed with IoT devices in mind to be smaller, cheaper, and more power-efficient [ 20 ]. However, BLE is vulnerable to MITM attacks. BLE uses AES-CCM encryption; AES encryption is considered secure, but the way that the encryption keys are exchanged is often insecure. The level of security relies on the pairing method used to exchange temporary keys between the devices. BLE specifically uses three-phase pairing processes: first, the initiating device sends a pairing request, and the devices exchange pairing capabilities over an insecure channel; second, the devices exchange temporary keys and verify that they are using the same temporary key, which is then used to generate a short-term key (some newer devices use a long-term key exchanged using Elliptic Curve Diffie-Hellman public-key cryptography, which is significantly more secure than the standard BLE protocol); third, the created key is exchanged over a secure connection and can be used to encrypt data [ 20 ]. Figure 3 represents this three-phase pairing process.
A diagram illustrating the basic BLE pairing process
The temporary key is determined according to the pairing method, which is determined on the OS level of the device. There are three common pairing methods popular with IoT devices. One, called Just Works, always sets the temporary key to 0, which is obviously very insecure. However, it remains one of if not the most popular pairing methods used with BLE devices [ 20 ]. The second, Passkey, uses six-digit number combinations, which the user must manually enter into a device, which is fairly secure, though there are methods of bypassing this [ 20 ]. Finally, the Out-of-Band pairing method exchanges temporary keys using methods such as Near Field Communication. The security level of this method is determined by the security capabilities of the exchange method. If the exchange channel is protected from MITM attacks, the BLE connection can also be considered protected. Unfortunately, the Out-of-Band method is not yet common in IoT devices [ 20 ]. Another important feature of BLE devices is the Generic Attribute Profile (GATT), which is used to communicate between devices using a standardized data schema. The GATT describes devices’ roles, general behaviors, and other metadata. Any BLE-supported app within the range of an IoT device can read its GATT schema, which provides the app with necessary information [ 20 ]. In order for attackers to perform MITM attacks in BLE networks, the attacker must use two connected BLE devices himself: one device acting as the IoT device to connect to the target mobile app, and a fake mobile app to connect to the target IoT device. Some other tools for BLE MITM attacks exist, such as GATTacker, a Node.js package that scans and copies BLE signals and then runs a cloned version of the IoT device, and BtleJuice, which allows MITM attacks on Bluetooth Smart devices which have improved security over BLE [ 20 ].
2.3.2 False data injection attacks
Once an attacker has access to some or all of the devices on an IoT network via an MITM attack, one example of an attack they could carry out next is a False Data Injection (FDI) attack. FDI attacks are when an attacker alters measurements from IoT sensors by a small amount so as to avoid suspicion and then outputs the faulty data [ 21 ]. FDI attacks can be perpetrated in a number of ways, but in practice doing so via MITM attacks is the most practical. FDI attacks are often leveraged against sensors that send data to an algorithm that attempts to make predictions based on the data it has received or otherwise uses data to make conclusions. These algorithms, sometimes referred to as predictive maintenance systems, are commonly used in monitoring the state of a mechanical machine and predicting when it will need to be maintained or tuned [ 21 ]. These predictive maintenance algorithms and similar would also be a staple feature of smart cities, FDI attacks against which could be disastrous. An example of an FDI attack on a predictive maintenance system is sensors on an airplane engine that predict when the engine will need critical maintenance. When attackers are able to access even a small portion of the sensors, they are able to create a small amount of noise that goes undetected by faulty data detection mechanisms but is just enough to skew the algorithm’s predictions [ 21 ]. In testing, it would even be enough to delay critical maintenance to the system, potentially causing catastrophic failure while in use, which could cause a costly unplanned delay or loss of life.
2.4 Botnets
Another kind of common attack on IoT devices is recruiting many devices to create botnets and launch Distributed Denial of Service (DDoS) attacks. A denial of service (DoS) attack is characterized by an orchestrated effort to prevent legitimate use of a service; a DDoS attack uses attacks from multiple entities to achieve this goal. DDoS attacks aim to overwhelm the infrastructure of the target service and disrupt normal data flow. DDoS attacks generally go through a few phases: recruitment, in which the attacker scans for vulnerable machines to be used in the DDoS attack against the target; exploitation and infection, in which the vulnerable machines are exploited, and malicious code is injected; communication, in which the attacker assesses the infected machines, sees which are online and decides when to schedule attacks or upgrade the machines; and attack, in which the attacker commands the infected machines to send malicious packets to the target [ 22 ]. One of the most popular ways to gain infected machines and conduct DDoS attacks is through IoT devices due to their high availability and generally poor security and maintenance. Figure 4 shows a common command structure, in which the attacker’s master computer sends commands to one or more infected command and control centers, who each control a series of zombie devices that can then attack the target.
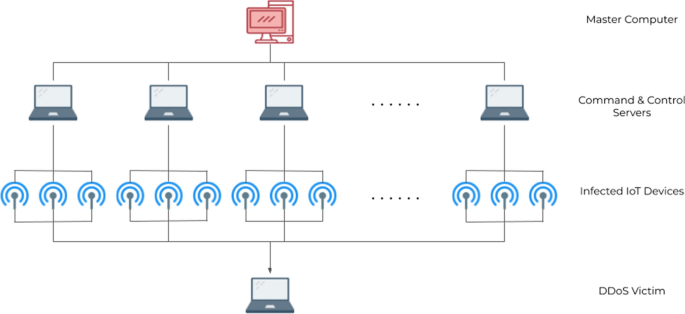
A graphical representation of a common botnet hierarchy
One of the most famous malware, the Mirai worm, has been used to perpetrate some of the largest DDoS attacks ever known and is designed to infect and control IoT devices such as DVRs, CCTV cameras, and home routers. The infected devices become part of a large-scale botnet and can perpetrate several types of DDoS attacks. Mirai was built to handle multiple different CPU architectures that are popular to use in IoT devices, such as x86, ARM, Sparc, PowerPC, Motorola, etc., in order to capture as many devices as possible [ 23 ]. In order to be covert, the virus is quite small and actually does not reside in the device’s hard disk. It stays in memory, which means that once the device is rebooted, the virus is lost. However, devices that have been infected once are susceptible to reinfection due to having already been discovered as being vulnerable, and reinfection can take as little as a few minutes [ 23 ]. Today, many well-known IoT-targeting botnet viruses are derived from Mirai’s source code, including Okiru, Satori, and Reaper [ 23 ].
2.5 Denial of service attacks
IoT devices may often carry out DoS attacks, but they themselves are susceptible to them as well. IoT devices are particularly susceptible to permanent denial of service (PDoS) attacks that render a device or system completely inoperable. This can be done by overloading the battery or power systems or, more popularly, firmware attacks. In a firmware attack, the attacker may use vulnerabilities to replace a device’s basic software (usually its operating system) with a corrupted or defective version of the software, rendering it useless [ 18 ]. This process, when done legitimately, is known as flashing, and its illegitimate counterpart is known as “phlashing”. When a device is phlashed, the owner of the device has no choice but to flash the device with a clean copy of the OS and any content that might’ve been put on the device. In a particularly powerful attack, the corrupted software could overwork the hardware of the device such that recovery is impossible without replacing parts of the device [ 18 ]. The attacks to the device’s power system, though less popular, are possibly even more devastating. One example of this type of attack is a USB device with malware loaded on it that, when plugged into a computer, overuses the device’s power to the point that the hardware of the device is rendered completely ruined and needs to be replaced [ 18 ].
One example of PDoS malware is known as BrickerBot. BrickerBot uses brute force dictionary attacks to gain access to IoT devices and, once logged in to the device, runs a series of commands that result in permanent damage to the device. These commands include misconfiguring the device’s storage and kernel parameters, hindering internet connection, sabotaging device performance, and wiping all files on the device [ 24 ]. This attack is devastating enough that it often requires reinstallation of hardware or complete replacement of the device. If the hardware survives the attack, the software certainly didn’t and would need reflashing, which would lose everything that might have been on it. Interestingly enough, BrickerBot was designed to target the same devices the Mirai botnet targets and would employ as bots, and uses the same or a similar dictionary to make its brute force attacks. As it turns out, BrickerBot was actually intended to render useless those devices that Mirai would have been able to recruit in an effort to fight back against the botnet [ 24 ].
Due to the structure of IoT systems, there are multiple attack surfaces, but the most popular way of attacking IoT systems is through their connections as these tend to be the weakest links. In the future, it is advisable that IoT developers ensure that their products have strong protections against such attacks, and the introduction of IoT security standards would prevent users from unknowingly purchasing products that are insecure. Alternatively, keeping the network that the IoT system resides on secure will help prevent many popular attacks, and keeping the system largely separated from other critical systems or having backup measures will help mitigate the damage done should an attack be carried out.
3 Artificial Intelligence in cybersecurity
In order to dynamically protect systems from cyber threats, many cybersecurity experts are turning to Artificial Intelligence (AI). AI is most commonly used for intrusion detection in cybersecurity by analyzing traffic patterns and looking for an activity that is characteristic of an attack.
3.1 Machine learning
There are two main kinds of machine learning: supervised and unsupervised learning. Supervised learning is when humans manually label training data as malicious or legitimate and then input that data into the algorithm to create a model that has “classes” of data that it compares the traffic it is analyzing. Unsupervised learning forgoes training data and manual labeling, and instead the algorithm groups together similar pieces of data into classes and then classifies them according to the data coherence within one class and the data modularity between classes [ 25 ]. One popular machine learning algorithm for cybersecurity is naïve Bayes, which seeks to classify data based on the Bayesian theorem wherein anomalous activities are all assumed to originate from independent events instead of one attack. Naïve Bayes is a supervised learning algorithm, and once it is trained and has generated its classes will analyze each activity to determine the probability that it is anomalous [ 25 ]. Machine learning algorithms can also be used to create the other models discussed in this section
3.2 Decision trees
A decision tree is a type of AI that creates a set of rules based on its training data samples. It uses iterative division to find a description (often simply “attack” or “normal”) that best categorizes the traffic it is analyzing. An example of this approach in cybersecurity is detecting DoS attacks by analyzing the flow rate, size, and duration of traffic. For example, if the flow rate is low, but the duration of the traffic is long, it is likely to be an attack and will, therefore, be classified as such [ 25 ]. Decision trees can also be used to detect command injection attacks in robotic vehicles by categorizing values from CPU consumption, network flow, and volume of data written [ 25 ] as shown in Fig. 5 . This technique is popular as it is intuitive in that what the AI does and doesn’t consider anomalous traffic is known to the developer. Additionally, once an effective series of rules is found, the AI can analyze traffic in real-time, providing an almost immediate alert if unusual activity is detected.
An example of a decision tree for classifying network traffic
Another approach to decision trees is the Rule-Learning technique, which searches for a set of attack characteristics in each iteration while maximizing some score that denotes the quality of the classification (i.e., the number of incorrectly classified data samples) [ 25 ]. The main difference between traditional decision trees and the rule-learning techniques is that traditional decision trees look for characteristics that will lead to a classification, whereas the rule-learning technique finds a complete set of rules that can describe a class. This can be an advantage as it can factor in human advice when generating rules, which creates an optimized set of rules [ 25 ].
3.3 K-nearest neighbors
The k-nearest neighbor (k-NN) technique learns from data samples to create classes by analyzing the Euclidean distance between a new piece of data and already classified pieces of data to decide what class the new piece should be put in, to put it simply [ 25 ]. For example, the new piece of data when k, the number of nearest neighbors, equals three (3) would be classified into class two (2), but when k equals nine (9), the new piece would be classified in class 1 as shown in Fig. 6 . The k-NN technique is attractive for intrusion detection systems as it can quickly learn from new traffic patterns to notice previously unseen, even zero-day attacks. Cybersecurity experts are also researching applications of k-NN for real-time detection of cyberattacks [ 25 ]. The technique has been employed to detect attacks such as false data injection attacks and performs well when data can be represented through a model that allows the measurement of their distance to other data, i.e., through a Gaussian distribution or a vector.

How k-NN technique can classify a data point differently given different k values
3.4 Support vector machines
Support vector machines (SVMs) are an extension of linear regression models that locates a plane that separates data into two classes [ 25 ]. This plane can be linear, non-linear, polynomial, Gaussian, sigmoid, etc., depending on the function used in the algorithm. SVMs can also separate data into more than two classes by using more than one plane. In cybersecurity, this technique is used to analyze Internet traffic patterns and separate them into their component classes such as HTTP, FTP, SMTP, and so on [ 25 ]. As SVM is a supervised machine learning technique, it is often used in applications where attacks can be simulated, such as using network traffic generated from penetration testing as training data.
3.5 Artificial neural networks
Artificial neural networks (ANNs) are a technique derived from the way that neurons interact with each other in the brain in order to pass and interpret information. In ANNs, a neuron is a mathematical equation that reads data and outputs a target value, which is then passed along to the next neuron based on its value. The ANN algorithm then iterates until the output value is acceptably close to the target value, which allows the neurons to learn and correct their weights by measuring the error between the expected value and the previous output value. Once this process is finished, the algorithm presents a mathematical equation that outputs a value that can be used to classify the data [ 25 ].
A large benefit of ANNs is that they are able to adjust their mathematical models when presented with new information, whereas other mathematical models may become obsolete as new types of traffic and attacks become common [ 25 ]. This also means that ANNs are adept at catching previously unseen and zero-day attacks as they take new information into heavier consideration than static mathematical models can. Because of this, ANNs make solid intrusion detection systems and have performed well with attacks such as DoS [ 25 ].
At present, using AI in cybersecurity is a small but rapidly growing field. It is also expensive and resource intensive, so using AI to protect a small system may not be feasible. However, businesses that have large networks may benefit from these solutions, especially if they are considering or have already introduced IoT devices into their network. AI cybersecurity would also be beneficial in the massive systems one would find in a smart city, and the AI would be able to give very quick response times that are important in systems like traffic management. In the future, AI cybersecurity could also be integrated into smaller systems such as self-driving cars or smart homes. Additionally, many AI cybersecurity measures detect or thwart attacks in progress rather than preventing attacks in the first place, meaning that other preventative security measured should also be in place.
4 AI to attack IoT
Not all AI is used for the purposes of cybersecurity; cybercriminals have begun using malicious AI to aid attacks, often to thwart the intrusion detection algorithms in the case of IoT, or attacking beneficial AI in such a way that the AI works against its own system.
4.1 Automation of vulnerability detection
Machine learning can be used to discover vulnerabilities in a system. While this can be useful for those trying to secure a system to intelligently search for vulnerabilities that need to be patched, attackers also use this technology to locate and exploit vulnerabilities in their target system. As technology soars in usage, especially technologies with low-security standards such as IoT devices, the number of vulnerabilities that attackers are able to exploit has soared as well, including zero-day vulnerabilities. In order to identify vulnerabilities quickly, attackers often use AI to discover vulnerabilities and exploit them much more quickly than developers can fix them. Developers are able to use these detection tools as well, but it should be noted that developers are at a disadvantage when it comes to securing a system or device; they must find and correct every single vulnerability that could potentially exist, while attackers need only find one, making automatic detection a valuable tool for attackers.
4.1.1 Fuzzing
Fuzzing, at its core, is a testing method that generates random inputs (i.e., numbers, chars, metadata, binary, and especially “known-to-be-dangerous” values such as zero, negative or very large numbers, SQL requests, special characters) that causes the target software to crash [ 26 ]. It can be divided into dumb fuzzing and smart fuzzing. Dumb fuzzing simply generates defects by randomly changing the input variables; this is very fast as changing the input variable is simple, but it is not very good at finding defects as code coverage is narrow [ 26 ]. Smart fuzzing, on the other hand, generates input values suitable for the target software based on the software’s format and error generation. This software analysis is a big advantage for smart fuzzing as it allows the fuzzing algorithm to know where errors can occur; however, developing an efficient smart fuzzing algorithm takes expert knowledge and tuning [ 26 ].
4.1.2 Symbolic execution
Symbolic execution is a technique similar to fuzzing that searches for vulnerabilities by setting input variables to a symbol instead of a real value [ 26 ]. This technique is often split into offline and online symbolic execution. Offline symbolic execution chooses only one path to explore at a time to create new input variables by resolving the path predicate [ 26 ]. This means that each time one wishes to explore a new path, the algorithm must be run from the beginning, which is a disadvantage due to the large amount of overhead due to code re-execution. Online symbolic execution replicates states and generates path predicates at every branch statement [ 26 ]. This method does not incur much overhead, but it does require a large amount of storage to store all the status information and simultaneous processing of all the states it creates, leading to significant resource consumption.
4.2 Input attacks
When an attacker alters the input of an AI system in such a way that causes the AI to malfunction or give an incorrect output, it is known as an input attack. Input attacks are carried out by adding an attack pattern to the input, which can be anything from putting tape on a physical stop sign to confuse self-driving cars to adding small amounts of noise to an image that is imperceptible to the human eye but will confuse an AI [ 27 ]. Notably, the actual algorithm and security of the AI does not need to be compromised in order to carry out an input attack—only the input that the attacker wants to compromise the output of must be altered. In the case of tape on a stop sign, the attacker may not need to use technology at all. However, more sophisticated attacks are completely hidden from the human eye, wherein the attacker may alter a tiny part of the image in a very precise manner that is designed to misdirect the algorithm. That being said, input attacks are often categorized based on where they rest on two axes: perceivability and format.
The perceivability of an input attack is the measure of how noticeable the attack is to the human eye, while the format is the measure of how digital versus physical the attack is [ 27 ]. On one end of the perceivability axis is perceivable attacks. Altering targets, such as by deforming, removing part of, or changing its colors, and adding to the target, such as affixing physical tape or adding digital marks, are types of perceivable attacks [ 27 ]. While perceivable attacks are perceivable by humans, humans may not notice slight changes like tape on a stop sign or consider them important. A human driver still sees a stop sign with tape or scratches as a stop sign, even though a self-driving car may not. This lends itself to the effectiveness of perceivable attacks, allowing them to, in many cases, hide in plain sight. Conversely, imperceivable attacks are invisible to the human eye. This can include things such as “digital dust,” which is a small amount of noise added to the entire image that is not visible to the human eye but significant enough to an AI to change its output or an imperceptible pattern on a 3D printed object that can be picked up by AI [ 27 ]. Imperceivable attacks can also be made through audio, such as playing audio at ranges outside of the human hearing range that would be picked up by a microphone [ 27 ]. Imperceivable attacks are generally more of a security risk, as there is almost no chance that a human would notice the attack before the AI algorithm outputs an incorrect response.
The format of an attack is usually either digital or physical, without many attacks that are a combination of both [ 27 ]. In many cases of physical attacks, the attack pattern must be more obvious rather than imperceivable as physical objects must be digitized to be processed and, in that process, may lose some finer detail [ 27 ]. Some attacks are still difficult to perceive even with the detail loss, however, as with the case of 3D printed objects with a pattern that blends into the structure of the object such that it is imperceptible to humans [ 27 ]. Opposite of physical attacks are digital attacks, which attack digital inputs such as images, videos, audio recordings, and files. As these inputs are already digitized, there is no process wherein detail is lost, and as such attackers can make very exact attacks, allowing them to be more imperceptible to the human eye than physical attacks [ 27 ]. Digital attacks are not necessarily imperceptible. However—photoshopping glasses with a strange pattern over a celebrity, for example, may cause the AI to identify the image as a different person, but still a person nonetheless. An example of input attacks specific to IoT smart cars and, more broadly, smart cities. As mentioned earlier, simply placing pieces of tape in a specific way on a stop sign is enough for an algorithm to not recognize the stop sign or even classify it as a green light—this is harmful for passengers in the car if the car does not heed the stop sign, and at a larger scale could alter traffic pattern detectors in smart cities. Additionally, noise-based input attacks could cause smart assistants to malfunction and carry out unintended commands.
4.3 Data poisoning/false data injection
Data poisoning attacks and input attacks are very similar, but while the goal of input attacks is simply to alter the output of the affected input, the goal of data poisoning is to alter inputs over a long enough period of time that the AI that analyzes data has shifted and is inherently flawed; because of this, data poisoning is usually carried out while the AI is still being trained before it is actually deployed [ 27 ]. In many cases, the AI learns to fail on specific inputs that the attacker chooses; for example, if a military uses AI to detect aircraft, the enemy military may poison the AI so that it does not recognize certain types of aircraft like drones [ 27 ]. Data poisoning can also be used on AIs that are constantly learning and analyzing data in order to make and adjust predictions, such as in predictive maintenance systems. There are three main methods attackers can use to poison an AI.
4.3.1 Dataset poisoning
Poisoning the dataset of an AI is perhaps the most direct method of data poisoning—as AI gain all of their knowledge from the training datasets they are provided, any flaws within those datasets will subsequently flaw the AI’s knowledge. A basic example of this is shown in Fig. 7 : a significant portion of the data is corrupted in the second dataset, leading the resultant machine learning model to be flawed. Dataset poisoning is done by including incorrect or mislabeled information in the target dataset [ 27 ]. As AI learn by recognizing patterns in datasets, poisoned datasets break patterns or may introduce new incorrect patterns, causing the AI to misidentify inputs or identify them incorrectly [ 27 ]. Many datasets are very large, so finding poisoned data within datasets can be difficult. Continuing the example of traffic patterns, an attacker could change dataset labels in such a way that the AI no longer recognizes stop signs or add data and labels that cause the AI to classify a red light as a green light.
A visual representation of dataset poisoning
4.3.2 Algorithm poisoning
Algorithm poisoning attacks take advantage of weaknesses that may be in the learning algorithm of the AI. This method of attack is very prominent in federated learning, which is a method of training machine learning while protecting data privacy of an individual. Federated learning, rather than collecting potentially sensitive data from users and combining it into one dataset, trains small models directly on users’ devices and then combines these models to form the final model. The users’ data never leaves their devices, and so is more secure; however, if an attacker is one of the users that the algorithm is using the data of, they are free to manipulate their own data in order to poison the model [ 27 ]. The poisoned algorithm, when combined with the rest of the algorithms, has the potential to poison the final model. They could degrade the model or even install a backdoor in this manner.
One example of federated learning is Google’s Gboard, which used federated learning to learn about text patterns in order to train predictive keyboards [ 28 ]. Although Google has extensive data vetting measures, in a less careful approach, users could potentially type nonsensical messages to confuse the predictive text or, more sinisterly, inject code into the algorithm to give themselves a backdoor. Similarly, some cutting-edge IoT devices are beginning to employ federated learning in order to learn from each other. One example of this is using machine learning to predict air pressure changes as it flows through gradually clogging filters, allowing the IoT sensor to predict when the filter will need to be changed [ 29 ]. This learning process would take a long enough time to make the study infeasible with just a few filters, but with federated learning the process is able to be sped up significantly. However, users could easily manipulate the process with their own filters in order to poison the algorithm. Although this is a relatively innocent example of algorithm poisoning, as federated learning increases in IoT, so will the potentially harmful applications of federated learning.
4.3.3 Model poisoning
Finally, some attackers simply replace a legitimate model with an already poisoned model prepared ahead of time; all the attacker has to do is get into the system which stores the model and replace the file [ 27 ]. Alternatively, the equations and data within the trained model file could be altered. This method is potentially dangerous as even if a model trained model is double-checked and data is verified to be not poisoned, the attacker can still alter the model at various points in its distribution, such as while the model is still in company’s network awaiting placement on an IoT device or on an individual IoT device once it has been distributed [ 27 ].
Many of the attacks as described above can be mitigated or prevented by properly sanitizing inputs and checking for unusual data. However, some attacks are subtle and can bypass the notice of humans and even other AI, especially when the attacks are created by malevolent AI systems. These attacks and how to defend against effectively them are at the forefront of current research as the popularity of these attacks grow, but at present many attacks do not use AI for the same reason that many security systems do not: AI is resource intensive and a good algorithm requires high-level knowledge to build, making it inaccessible and infeasible to many attackers.
5 Summary of attacks and their defenses
The various attacks discussed in this paper are listed in Table 1 , and are paired with one or more ways of protecting an IoT system from the attack. While comprehensively protecting an IoT system can be a challenging task due to the number of attack surfaces present, many of the methods listed will defend against many types of attacks; for example, as many of the attacks listed are carried out by first conducting MITM attacks, protecting the network on which an IoT system resides will protect the system from many common attacks.
6 Conclusion
Due to the nature of IoT systems to have many attack surfaces, there exists a variety of attacks against these systems, and more are being discovered as IoT grows in popularity. It is necessary to protect systems against these attacks as effectively as possible. As the number and speed of attacks grow, experts are turning to AI as a means of protecting these systems intelligently and in real-time. Of course, attackers find ways to thwart these AI and may even use AI to attack systems. This paper explores popular techniques to attempt to disrupt or compromise IoT and explains at a surface level how these attacks are carried out. Where applicable, examples are also provided in order to clarify these explanations. Next, several AI algorithms are introduced, and their applications in cybersecurity are investigated. In many cases, these models are not yet common in commercial applications but rather are still undergoing research and development or are still difficult to implement and thus rare. Nonetheless, the models discussed are promising and may become common attack detection systems within just a couple of years. Methods of attacking AI and using AI to attack are also discussed, with the frame of IoT systems. The growth of IoT systems will see these types of attacks become more and more of a threat, especially as massive networks such as smart cities begin experimentation; both as massive networks are harder to protect with a multitude of attack surfaces, and as daily life and safety revolve around AI which needs to be more or less failure-proof. This is followed by a chart reiterating the threats covered in this paper, paired with common or recommended methods of protecting against each attack. Having covered all these topics, this paper aims to provide a useful tool with which researchers and cybersecurity professionals may study IoT in the context of cybersecurity and AI in order to secure IoT systems. Additionally, it also aims to emphasize the implications of up and coming technology and the impacts that each of these fields will have on the others. It is important to consider all the potential consequences of a technological development both before and after it is made public, as cyberattackers are constantly looking to use new technologies to their benefit, whether this means diverting the technology from its original purpose or using the technology as a tool to perpetuate other attacks. This paper discusses how IoT and AI have been taken advantage of for criminal purposes or have had weaknesses exploited as an example of this, which will help readers understand current risks and help cultivate an understanding such that these weaknesses are accounted for in the future in order to prevent cyberattacks.
Evans D. The Internet of Things: how the next evolution of the internet is changing everything. Cisco Internet Business Solutions Group: Cisco; 2011.
Google Scholar
Rouse M. What is IoT (Internet of Things) and how does it work? IoT Agenda, TechTarget. http://www.internetofthingsagenda.techtarget.com/definition/Internet-of-Things-IoT . Accessed 11 Feb 2020.
Linthicum D. App nirvana: when the internet of things meets the API economy. https://techbeacon.com/app-dev-testing/app-nirvana-when-internet-things-meets-api-economy . Accessed 15 Nov 2019.
Lu Y, Xu LD. Internet of Things (IoT) cybersecurity research: a review of current research topics. IEEE Internet Things J. 2019;6(2):2103–15.
Article Google Scholar
Vorakulpipat C, Rattanalerdnusorn E, Thaenkaew P, Hai HD. Recent challenges, trends, and concerns related to IoT security: aan evolutionary study. In: 2018 20th international conference on advanced communication technology (ICACT), Chuncheon-si Gangwon-do, Korea (South); 2018. p. 405–10.
Lakhani A. The role of artificial intelligence in IoT and OT security. https://www.csoonline.com/article/3317836/the-role-of-artificial-intelligence-in-iot-and-ot-security.html . Accessed 11 Feb 2020.
Pendse A. Transforming cybersecurity with AI and ML: view. https://ciso.economictimes.indiatimes.com/news/transforming-cybersecurity-with-ai-and-ml/67899197 . Accessed 12 Feb 2020.
Meneghello F, Calore M, Zucchetto D, Polese M, Zanella A. IoT: internet of threats? A survey of practical security vulnerabilities in real IoT devices. IEEE Internet Things J. 2019;6(5):8182–201.
Roopak M, Yun Tian G, Chambers J. Models deep learning, for cyber security in IoT networks. In: IEEE 9th annual computing and communication workshop and conference (CCWC), Las Vegas, NV, USA. 2019;2019:0452–7.
Cañedo J, Skjellum A. Using machine learning to secure IoT systems. In: 2016 14th annual conference on privacy, security and trust (PST), Auckland; 2016. p. 219–22, https://doi.org/10.1109/PST.2016.7906930 .
Farivar F, Haghighi MS, Jolfaei A, Alazab M. Artificial intelligence for detection, estimation, and compensation of malicious attacks in nonlinear cyber-physical systems and industrial IoT. IEEE Trans Ind Inf. 2020;16(4):2716–25. https://doi.org/10.1109/TII.2019.2956474 .
Wang S, Qiao Z. Robust pervasive detection for adversarial samples of artificial intelligence in IoT environments. IEEE Access. 2019;7:88693–704. https://doi.org/10.1109/ACCESS.2019.2919695 .
Radanliev P, De Roure D, Van Kleek M, Santos O, Ani U. Artificial intelligence in cyber physical systems. AI & society. 2020; p. 1–14.
Radanliev P, De Roure D, Page K, Nurse JR, Mantilla Montalvo R, Santos O, Maddox LT, Burnap P. Cyber risk at the edge: current and future trends on cyber risk analytics and artificial intelligence in the industrial internet of things and industry 4.0 supply chains. Cybersecurity. 2020;3:1–21.
Radanliev P, De Roure DC, Nurse JR, Montalvo RM, Cannady S, Santos O, Burnap P, Maple C. Future developments in standardisation of cyber risk in the Internet of Things (IoT). SN Appl Sci. 2020;2(2):169.
Woo S. The right security for IoT: physical attacks and how to counter them. In: Minj VP, editor. Profit From IoT. http://www.iot.electronicsforu.com/headlines/the-right-security-for-iot-physical-attacks-and-how-to-counter-them/ . Accessed 13 June 2019.
Akram H, Dimitri K, Mohammed M. A comprehensive iot attacks survey based on a building-blocked reference mode. Int J Adv Comput Sci Appl. 2018. https://doi.org/10.14569/IJACSA.2018.090349 .
Herberger C. DDoS fire & forget: PDoS—a permanent denial of service. Radware Blog, Radware Ltd. http://www.blog.radware.com/security/2015/10/ddos-fire-forget-pdos-a-permanent-denial-of-service/ . Accessed 12 Sept 2016.
Cekerevac Z, Dvorak Z, Prigoda L, Čekerevac P. Internet of things and the man-in-the-middle attacks–security and economic risks. Mest J. 2017;5:15–25. https://doi.org/10.12709/mest.05.05.02.03 .
Melamed T. An active man-in-the-middle attack on bluetooth smart devices. WIT Press, International Journal of Safety and Security Engineering. http://www.witpress.com/elibrary/sse-volumes/8/2/2120 . Accessed 1 Feb 2018.
Mode G, Calyam P, Hoque K. False data injection attacks in Internet of Things and deep learning enabled predictive analytics; 2019.
De Donno M, Dragoni N, Giaretta A, Spognardi A. Analysis of DDoS-capable IoT malwares. In: 2017 federated conference on computer science and information systems (FedCSIS), Prague; 2017. p. 807–16. https://doi.org/10.15439/2017F288 .
Mirai Botnet DDoS Attack. Corero, Corero. http://www.corero.com/resource-hub/mirai-botnet-ddos-attack/ . Accessed 9 Dec 2019.
BrickerBot Malware emerges, permanently bricks iot devices. Trend Micro, Trend Micro Incorporated. http://www.trendmicro.com/vinfo/us/security/news/internet-of-things/brickerbot-malware-permanently-bricks-iot-devices . Accessed 19 Apr 2017.
Zeadally S, Adi E, Baig Z, Khan IA. Harnessing artificial intelligence capabilities to improve cybersecurity. IEEE Access. 2020;8:23817–37.
Jurn J, Kim T, Kim H. An automated vulnerability detection and remediation method for software security. Sustainability. 2018;10:1652. https://doi.org/10.3390/su10051652 .
Comiter M. Attacking artificial intelligence. Belfer Center for Science and International Affairs, Belfer Center for Science and International Affairs. http://www.belfercenter.org/sites/default/files/2019-08/AttackingAI/AttackingAI.pdf . Accessed 25 Aug 2019.
McMahan B, Daniel R. Federated learning: collaborative machine learning without centralized training data. Google AI Blog, Google. http://www.ai.googleblog.com/2017/04/federated-learning-collaborative.html . Accessed 6 Apr 2017.
Rojek M. Federated learning for IoT. Medium, becoming human: artificial intelligence magazine. http://www.becominghuman.ai/theres-a-better-way-of-doing-ai-in-The-iot-era-feabbbc1b589 . Accessed 16 Apr 2019.
Porter E. What is a botnet? And how to protect yourself in 2020. SafetyDetectives, Safety Detectives. http://www.safetydetectives.com/blog/what-is-a-botnet-and-how-to-protect-yourself-in/#review-2 . Accessed 28 Dec 2019.
Hendrickson J. What is the mirai botnet, and how can i protect my devices? How to geek, LifeSavvy media. http://www.howtogeek.com/408036/what-is-the-mirai-botnet-and-how-can-i-protect-my-devices/ . Accessed 22 Mar 2019.
Understanding denial of service attacks. Cybersecurity and infrastructure security agency CISA. http://www.us-cert.cisa.gov/ncas/tips/ST04-015 . Accessed 20 Nov 2019.
Moisejevs I. Poisoning attacks on machine learning. Towards data science, medium. http://www.towardsdatascience.com/poisoning-attacks-on-machine-learning-1ff247c254db . Accessed 15 July 2019.
Fang M et al. Local model poisoning attacks to Byzantine-Robust federated learning. In: Usenix security symposium. arXiv:1911.11815 . Accessed 6 Apr 2020.
Download references
Acknowledgements
This work was supported in part by the Commonwealth Cyber Initiative, an investment in the advancement of cyber R&D, innovation and workforce development in Virginia, USA. For more information about CCI, visit cyberinitiative.org.
Author information
Authors and affiliations.
Batten College of Engineering and Technology, Old Dominion University, Norfolk, VA, USA
Murat Kuzlu
Computer Science, Christopher Newport University, Newport News, VA, USA
Corinne Fair
eKare, Inc, Fairfax, VA, USA
Ozgur Guler
You can also search for this author in PubMed Google Scholar
Contributions
MK, and CF conceived and designed the work as well as contributed to the acquisition, analysis, and interpretation of data. All authors discussed the results and wrote the final manuscript. All authors read and approved the final manuscript.
Corresponding author
Correspondence to Murat Kuzlu .
Ethics declarations
Competing interests.
The authors declare that they no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Kuzlu, M., Fair, C. & Guler, O. Role of Artificial Intelligence in the Internet of Things (IoT) cybersecurity. Discov Internet Things 1 , 7 (2021). https://doi.org/10.1007/s43926-020-00001-4
Download citation
Received : 29 September 2020
Accepted : 30 November 2020
Published : 24 February 2021
DOI : https://doi.org/10.1007/s43926-020-00001-4
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Artificial Intelligence
- Internet of Things (IoT)
- Cybersecurity
- Find a journal
- Publish with us
- Track your research

IMAGES
VIDEO
COMMENTS
This paper reviews the threat challenges and IoT security models at each level of the Internet of Things in recent years and discusses some of the past and future solutions. At first, the IoT security threats are systematically introduced from the perspectives of physics, network and data. In addition, the mainstream IoT security model is ...
Therefore, the research in various IoT security is gaining necessary momentum with the help of di ff erent simulation tools as well as multiple computational platforms [ 12 ].
The paper proposes an ML-based security model that autonomously handles the growing number of security issues associated with the IoT domain. This research made a significant contribution by ...
Security is one of the main issues for IoT technologies, applications, and platforms. In order to cover this key aspect of IoT, this paper reviews the research progress of IoT, and found that ...
The objective is to locate the most relevant papers and, along these lines, discover as many essential IoT security pattern and architecture papers as possible. Database search. ... The dominance of academia-only and a few joint collaboration in IoT security pattern research (see our answer to RQ1.3) suggests that there should be even more ...
IoT devices are incorporated into various products, ranging from ordinary household items to complex industrial appliances. Despite the increasing demand for IoT, security concerns have impeded its development. This article systematically reviews IoT security research, focusing on vulnerabilities, challenges, technologies, and future directions.
The Internet of Things (IoT) opens opportunities for wearable devices, home appliances, and software to share and communicate information on the Internet. Given that the shared data contains a large amount of private information, preserving information security on the shared data is an important issue that cannot be neglected. In this paper, we begin with general information security ...
This paper provides an insight into the latest security research trends, which will prove beneficial in the development of IoT security. The research outcomes can benefit the research community in IoT by integrating IoT-based devices' best security aspects.
Abstract—The use of IoT in society is perhaps already ubiqui-tous, with a vast attack surface offering multiple opportunities for malicious actors. This short paper first presents an introduction to IoT and its security issues, including an overview of IoT layer models and topologies, IoT standardisation efforts and protocols.
Moreover, the paper sheds light on the available ML and DL techniques for IoT IDS and offers an overview of datasets suitable for IoT security-related research. In conclusion, the authors identified several ongoing challenges, suggesting that the available IDS for IoT are still imperfect and require further refinement.
This paper systematically reviews IoT security research, focusing on vulnerabilities, challenges, technologies, and future directions. It surveys 171 recent publications in the field, providing a ...
research. With the great potential of IoT, there comes many types of issues and challenges. Security is one of the main issues for IoT technologies, applications, and platforms. In order to cover this key aspect of IoT, this paper reviews the research progress of IoT, and found that several security issues and challenges
The present paper will survey the current development of IoT security research from 2016 to 2018. Challenges in applying security mechanisms in IoT and its attack vectors will also be evaluated. Simulators or IoT modellers that may be used by new researchers to further develop the IoT security field will be highlighted.
The Internet of Things (IoT) is exponentially growth, however privacy and security vulnerabilities are major concerns against rapid adoption of this technology. Due to mainly its decentralized topology and the resource constraints of the majority of its devices, conventional security and privacy approaches are inapplicable for IoT. Interaction and communication between a large number of ...
The purpose of this systematic research review is to provide a comprehensive analysis of various research studies and techniques used by researchers to protect IoT networks from large-scale attacks. This paper aims to investigate research trends for the applications of machine learning in IoT security.
1.1 Overview. Internet of Things (IoT) has received a lot of research attention over the last few decades in addition to being a most important emerging technology [1,2,3].A physical perception layer of IoT observes the physical environment through sensors, whereas a network layer connects to other smart things and processes observed data [].Finally, an application layer provides a user with ...
Defining the IoT. When writing about his first use of the term IoT, Ashton remarked that the term 'is still often misunderstood'. Indeed, today there exist many definitions and interpretations of the IoT (Atzori, Iera, and Morabito Citation 2010; Bandyopadhyay and Sen Citation 2011; Malina et al. Citation 2016).This might be expected when considering the general public, or researchers with ...
The Internet of Things (IoT) is the next era of communication. Using the IoT, physical objects can be empowered to create, receive, and exchange data in a seamless manner. Various IoT applications focus on automating different tasks and are trying to empower the inanimate physical objects to act without any human intervention. The existing and upcoming IoT applications are highly promising to ...
This survey paper introduced an overview of IoT technology, architecture, and applications and a detailed analysis comparing all cryptographic algorithms and their use in day-to-day life activities. ... The aim of this study was met by providing a comprehensive overview of research trends in IoT security between 2017 and 2022, as well as ...
The smart mobile Internet-of-things (IoT) network lays the foundation of the fourth industrial revolution, the era of hyperconnectivity, hyperintelligence, and hyperconvergence. As this revolution gains momentum, the security of smart mobile IoT networks becomes an essential research topic. This study aimed to provide comprehensive insights on IoT security. To this end, we conducted a ...
Exploring such factors highlights the contributions and limitations of the reviewed papers with the intention of delineating novel concepts in IoT security and the underpinnings of future research. In summary, this paper presents the state of the art of different levels of IoT's security by analyzing various existing research proposals and ...
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications. ... As the field of IoT security ...
As an emerging technology, the Internet of Things (IoT) revolutionized the global network comprising of people, smart devices, intelligent objects, data, and information. The development of IoT is still in its infancy and many related issues need to be solved. IoT is a unified concept of embedding everything. IoT has a great chance to make the world a higher level of accessibility, integrity ...
The discussion also includes opportunities and challenges in standardizing IoT; developing energy‑efficient and affordable technologies; and improving data collection, transfer, storage, processing, security, anonymity, and privacy. This paper further calls for collaborative research in sensor and communication technologies in the ...
A layered perspective was used to highlight the security issues faced in IoT. A comparison of anomaly detection techniques and the most recent Intrusion Detection System (IDS) was utilized to improve IoT security. Noor [21] presented information on recent research trends in IoT security from 2016-2018. This paper looked at relevant tools and ...
Cisco+ (as-a-service) Cisco buying programs. Cisco Nexus Dashboard. Cisco Networking Software. Cisco DNA Software for Wireless. Cisco DNA Software for Switching. Cisco DNA Software for SD-WAN and Routing. Cisco Intersight for Compute and Cloud. Cisco ONE for Data Center Compute and Cloud.
This review paper compiles information from several other surveys and research papers regarding IoT, AI, and attacks with and against AI and explores the relationship between these three topics with the purpose of comprehensively presenting and summarizing relevant literature in these fields. ... The right security for IoT: physical attacks and ...
The present paper will survey the current development of IoT security research from 2016 to 2018. Challenges in applying security mechanisms in IoT and its attack vectors will also be evaluated. Simulators or IoT modellers that may be used by new researchers to further develop the IoT security field will be highlighted.