
- Conferences
- Last updated April 30, 2020
- In AI Origins & Evolution

10 Popular Cybersecurity Presentations On Slideshare You Should Refer To

- Published on August 12, 2019
- by Ambika Choudhury

Securing networks and protecting data from breaching has become one of the crucial motives in an organisation. Cybercrime has eventually risen with the widespread use of emerging technologies and we have been witnessing data breaches and other hacks for a few years now. In this article, we list down 10 popular presentations on cybersecurity one must read on Slideshare.
(The list is in alphabetical order)
1| Artificial Intelligence And Cybersecurity
This presentation was published in March 2019 by Olivier Busolini, a cybersecurity professional who also works with AI in cybersecurity. This presentation includes a basic introduction to AI, an overview of AI technologies, an overview of machine learning underlying technologies, basics of deep learning, introduction to red and blue AI, emerging usages of blue AI, difficulties faced during developing AI solutions and tips for cybersecurity strategy.
2| Cyber Crime And Security
This powerpoint presentation was published by Lipsita Behera, a software developer and it has gathered more than 350,000 views till now. In this PPT, you can understand the basics of cybersecurity such as how cybersecurity emerged, know about cyber threat evolution, types of cybercrime, how to take preventive measures in order to control the threats, learn various security reasons as well as methods.
3| Cybersecurity
This presentation has got more than one lakh viewers and more than 700 clipping. Here, the author introduces the basics of cybersecurity and what is the actual need of cybersecurity, what are the major security problems, different viruses and worms and its solutions, brief introduction of hackers and measures to prevent hacking, what are malware and steps to stop malware, what are trojan horses and safety measures to avoid trojans, password cracking and securing password, cybersecurity strategy in India and much more.
4| Combating cybersecurity Using Artificial Intelligence
Combating Cybersecurity using Artificial Intelligence was published in January this year by Inderjeet Singh, Director – Strategic Accounts. This presentation discusses the threats with AI and machine learning. Here, you can learn about the advanced behavioural attacks, applications of emerging technologies in cybersecurity, various malicious activities, including the future of AI and machine learning in cybersecurity.
5| Cyber Crime And Security
This powerpoint presentation was published by Aeman Khan, an automation test engineer and it has crossed over 410,000 views till now. Here, the writer discusses the basics of cybersecurity such as its introduction, history, the various categories of cybercrime, its types, how cybersecurity threatens national security, advantages of cybercrime and other safety tips to cybercrimes including cyber law in India.
6| Cybersecurity
This ppt is published by Bijay Bhandari, an engineer and project manager by profession. It has been viewed for over 210,000 times where the author discusses how to take action against cybercrime. You will know about the basics of cybersecurity and cybercrime, what constitutes cyber crimes, protection measures for cybercrime, advantages of cybersecurity and various safety measures.
7| Cyber Crime
This presentation has been viewed for over 294,000 times and it includes a basic introduction to cybercrime. You will get to know about the variants of cybercrime such as phishing, vishing, cyberstalking, cost of cybercrime in India, cyber laws, various ACTs including the preventive measures for such activities.
8| Overview Of Artificial Intelligence In cybersecurity
This presentation, an overview of artificial intelligence in cybersecurity was published in June 2019 by Olivier Busolini, a cybersecurity professional. Here, he talks about artificial imitation augmented intelligence, basic types of AI and machine learning, difficulties to develop AI solutions, challenges in machine learning, AI in cybersecurity, key flaws of cybersecurity, AI risk framework, basic introduction to defensive AI, adversarial AI as well as offensive AI and much more.
9| Security Automation And Machine Learning
The security automation and machine learning ppt is published by Siemplify, a security platform in January this year and has got more than 100 viewers. It includes a basic introduction to cybersecurity and machine learning, types of machine learning techniques, security analysis for machine learning, threats on machine learning, machine learning for prevention, detection, incident response and SOC management.
10| The Role Of Big Data, AI And ML In Cyber Intelligence
The role of big data, AI and ML in cyber intelligence ppt was published by Aladdin Dandis, an information security manager who gives a brief introduction to cyber intelligence, raw threat data and threat intelligence, understanding AI and machine learning drivers, various kinds of cybersecurity options such as phishing, anti-malware, fraud detection, cyber intelligence framework and its challenges.
Access all our open Survey & Awards Nomination forms in one place
Ambika Choudhury

How Securonix is Building Cybersecurity for LLMs

AI Will Open a Pandora’s Box of Escalating Privacy and Security Woes: Splunk Report

Nearly 83% of Indian Firms Were Hit by Cyber Breaches in 2022

After WormGPT, FraudGPT Makes it Easier for Cybercriminals

Meta Needs You in Its Generative AI Gambit

Digital India Act Expectations & Concerns

OpenAI disables ‘Browse’ Feature after releasing it on ChatGPT App

Believe it or Not, 55% of Digital Frauds Happen Via UPI

CORPORATE TRAINING PROGRAMS ON GENERATIVE AI
Generative ai skilling for enterprises, our customized corporate training program on generative ai provides a unique opportunity to empower, retain, and advance your talent., upcoming large format conference, data engineering summit 2024, may 30 and 31, 2024 | 📍 bangalore, india, download the easiest way to stay informed.

Snowflake Releases Open Enterprise LLM, Arctic with 480 Billion Parameters
Arctic activates approximately 50% fewer parameters than DBRX, and 80% fewer than Grok-1 during inference or training.

Now Run Programs in Real Time with Llama 3 on Groq

Fibe Leverages Amazon Bedrock to Increase Customer Support Efficiency by 30%
Top editorial picks, six months old cognition labs raises $175 mn from founders fund at $2 bn valuation, apple releases four open source llms with openelm series of models, adobe launches firefly image 3 beta with auto stylisation, structure reference capabilities, c.p. gurnani & interglobe’s rahul bhatia announce ai business venture aionos , subscribe to the belamy: our weekly newsletter, biggest ai stories, delivered to your inbox every week., also in news.

Guardians of the Syntax: Securing Enterprise LLM Systems against Emerging Threats

This 18-Year-Old Programmer is Creating an Open Source Alternative to Redis

India will Need at least $200-300 Mn to Build GPT-5-level AI Model

Doctors Use Apple Vision Pro to Enhance Shoulder Arthroscopy Surgery

10 AI Tools to Complete Excel Tasks in Minutes

You Don’t Need a Degree to Get an AI Job

UAE Turns to India to Spearhead AI Innovations

Microsoft’s Phi-3 Outperforms Meta’s Llama 3 and Fits Perfectly on an iPhone
Ai courses & careers.

India is a Goldmine for AI Talent

Top 10 LMS Platforms for Enterprise AI Training and Development

AI Clock is Ticking: Wake Up Call for Education Institutions
Become a certified generative ai engineer, industry insights.

BCG Predicts AI to Drive 20% of 2024 Revenues, Doubling to 40% by 2026

AI Can Now Edit DNA of Human Cells

Genpact Launches AI Innovation Centre in Gurugram
Check our industry research reports.
AI Forum for India
Our discord community for ai ecosystem, in collaboration with nvidia. .
What is Computer Vision and How it Works?
"> "> Flagship Events
Rising 2024 | de&i in tech summit, april 4 and 5, 2024 | 📍 hilton convention center, manyata tech park, bangalore, machinecon gcc summit 2024, june 28 2024 | 📍bangalore, india, machinecon usa 2024, 26 july 2024 | 583 park avenue, new york, cypher india 2024, september 25-27, 2024 | 📍bangalore, india, cypher usa 2024, nov 21-22 2024 | 📍santa clara convention center, california, usa, genai corner.

7 AI Startups that Featured on Shark Tank India Season 3

Top 9 Semiconductor GCCs in India

Top 6 Devin Alternatives to Automate Your Coding Tasks

10 Free AI Courses by NVIDIA

Top 6 AI/ML Hackathons to Participate in 2024

What’s Devin Up to?

10 Underrated Women in AI to Watchout For

10 AI Startups Run by Incredible Women Entrepreneurs
Data dialogues.

Automation Anywhere Wants to Augment Humans with AI, Not Replace Them

Father of Computational Theory Wins 2023 Turing Award

Building Open Source LLMs is Not for Everyone

This 20-year-old AI Researcher Created the much-needed Indic LLM Leaderboard

NPCI is Exploring AI-Powered Futuristic Payment Frontiers: CTO

Prisma AI Has an ‘Eye on You’ at Adani Airports

Salesforce Chief Ethicist Deems Doomsday AI Discussions a ‘Waste of Time’

Zoho’s ManageEngine Invests $10 Mn in NVIDIA, Intel, and AMD GPUs
Future talks.

T-Hub Supported MATH is Launching AI Career Finder to Create AI Jobs

Quora’s Poe Eats Google’s Lunch

Zoho Collaborates with Intel to Optimise & Accelerate Video AI Workloads

Rakuten Certified as Best Firm for Data Scientists for the 2nd Time

This Indian Logistics Company Developed an LLM to Enhance Last-Mile Delivery

Perplexity AI Reviews with Pro Access

What to Expect at the ‘Absolutely Incredible’ Apple WWDC 2024

Will StarCoder 2 Win Over Enterprises?
Developer’s corner.

Japan is the Next Big Hub for Indian Tech Talent

Will TypeScript Wipe Out JavaScript?

Meta Forces Developers Cite ‘Llama 3’ in their AI Development

Why Developers Hate Jira
In case you missed it.

Which is the Most Frustrating Programming Language?

AI4Bharat Rolls Out IndicLLMSuite for Building LLMs in Indian Languages

Google Introduces Synth^2 to Enhance the Training of Visual Language Models

Infosys Founder Funds Meta’s Llama 2 Project with 22 Indian Languages

9 Best AI Tools for Excel and Google Spread Sheet Automation

8 Best Generative AI Courses for Executives and Managers


Top 8 AI Browser Extensions for Chrome Users in 2024

Top 5 Devin AI Alternatives for Coders and Developers

10 Best AI Code Generator Tools to Use for Free in 2024

What are the Responsibility of Developers Using Generative AI
Also in trends.

AWS Brings Meta’s Llama 3 Models on Amazon Bedrock

Cohere Unveils SnapKV to Cut Memory & Processing Time in LLMs
‘We May be Able to Create an Infinite Data Generation Engine with Synthetic Data,’ says Anthropic CEO

OpenAI Introduces New Enterprise-Grade Features for API Customers
India leads global ai project implementation: report reveals.

UiPath Launches New Data Centers in Pune, Chennai to Expand India Footprint

Perplexity AI Raises $63M at $1B Valuation, Expands to Enterprise Market

UAE continues to spearhead global collaborations with G42 selecting Qualcomm for AI Inference
World's biggest media & analyst firm specializing in ai, advertise with us, aim publishes every day, and we believe in quality over quantity, honesty over spin. we offer a wide variety of branding and targeting options to make it easy for you to propagate your brand., branded content, aim brand solutions, a marketing division within aim, specializes in creating diverse content such as documentaries, public artworks, podcasts, videos, articles, and more to effectively tell compelling stories., corporate upskilling, adasci corporate training program on generative ai provides a unique opportunity to empower, retain and advance your talent, with machinehack you can not only find qualified developers with hiring challenges but can also engage the developer community and your internal workforce by hosting hackathons., talent assessment, conduct customized online assessments on our powerful cloud-based platform, secured with best-in-class proctoring, research & advisory, aim research produces a series of annual reports on ai & data science covering every aspect of the industry. request customised reports & aim surveys for a study on topics of your interest., conferences & events, immerse yourself in ai and business conferences tailored to your role, designed to elevate your performance and empower you to accomplish your organization’s vital objectives., aim launches the 3rd edition of data engineering summit. may 30-31, bengaluru.
Join the forefront of data innovation at the Data Engineering Summit 2024, where industry leaders redefine technology’s future.
© Analytics India Magazine Pvt Ltd & AIM Media House LLC 2024
- Terms of use
- Privacy Policy
Subscribe to Our Newsletter
The Belamy, our weekly Newsletter is a rage. Just enter your email below.
What to know about cybercrime
It's hard to protect yourself online if you don't know where to start. These insightful, info-packed talks offer a jumping off point.

Where is cybercrime really coming from?

The 1s and 0s behind cyber warfare

Governments don't understand cyber warfare. We need hackers

Your smartphone is a civil rights issue

How (and why) Russia hacked the US election

Everyday cybercrime -- and what you can do about it
Types of Cyber crime
Aug 27, 2023
0 likes | 21 Views
Cybercrime encompasses a range of illicit activities conducted in the digital realm. Some prevalent types include phishing, where deceptive emails or messages trick users into revealing sensitive information; ransomware attacks, during which malicious software encrypts data until a ransom is paid; identity theft, where personal information is stolen for financial gain; hacking, the unauthorized intrusion into computer systems; and DDoS (Distributed Denial of Service) attacks, which overwhelm websites with excessive traffic, causing them to go offline. These crimes underscore the need for robus
Share Presentation

Presentation Transcript
- More by User

Types of Crime
Types of Crime. By Felix Romero. Introduction. There are six main types of crime: Crimes Against Persons Crimes Against Habitation Crimes Against Property Crimes Against Morality Modern Crimes Consensual Crimes. Crimes Against Persons. Also known as “violent crimes”
3.02k views • 11 slides

Cyber Crime
Cyber Crime. By: Benjamin Lewis, Alex Lesko , Patricia Di Pietro , & Gabbrielle Cadieux. Types of Cyber Crime. Targets Computers: Malware Viruses Code Hacking Spam Vandalism. Uses Computers ID Theft Internet Scams Cyber Stalking/Harassment/Child Pornography Fraud Drug Trafficking
357 views • 5 slides

TYPES OF CRIME
CRIMES AGAINST PEOPLE. ACTS THAT THREATEN, HURT, OR END A PERSON'S LIFEALSO CALLED VIOLENT CRIMES- MURDER, RAPE, ASSAULT ARE EXAMPLESASSAULT IS PLACING SOMEONE IN FEAR WITHOUT ACTUAL PHYSICAL CONTACTBATTERY IS ASSAULT WITH PHYSICAL CONTACTHOMICIDE = KILLING SOMEONETYPES OF HOMICIDE- 1. MURDER
427 views • 6 slides

Cyber-crime
Cyber-crime Science. 2. Crime. Behaviour commonly considered harmful to individuals and/or society, against:persons (e.g. rape, assault, murder, suicide)property (e.g. fraud, arson, theft, vandalism)the state (e.g. riot, treason, sabotage, terrorism)morality (e.g. gambling, drugs, obscenity)Dis
463 views • 26 slides

Cyber Crime. MSIT 458: Information Security & Assurance By Curtis Pethley. Selection. Selecting a Firewall. There are 6 General Steps Identify your topology, applications, and protocol needs. Analyze trust relationships within your organization.
480 views • 21 slides

Cyber Crime. What is Cyber Crime?. Cyber crime has become a serious threat to anyone who especially use Internet. Steal personal data Hack into computer Identify fraud Pornography Terrorism embezzlement Theft stalking. Privacy OR Security ?.
457 views • 7 slides

Cyber Crime: Cyber-Bullying
Kaitlyn Deutsch Jordan Wright Becky Thompson Joe Yosten. Cyber Crime: Cyber-Bullying. Definitions. Wikipedia “Involves the use of information and communication technology to support deliberate, repeated, and hostile behavior by an individual or group that is intended to harm others.”.
967 views • 27 slides

CYBER CRIME
CYBER CRIME. Cyber crime. is a CRIMINAL activity done using COMPUTERS and INTERNET. Cyber crime basically are committed against individuals or groups of individuals with a CRIMINAL MOTIVE
611 views • 21 slides

CYBER CRIME. e-rule e-safety e-care. PREPARED BY: CA 11132 KANGESWARY A/P KUPPUSAMY KE 11058 SHOBANA A/P SINNIAH. E-RULE. E-SAFETY. Internet threats can come in various forms or attacks. The Internet can create the illusion that strangers are actually “friends”.
401 views • 7 slides

Types of crime
Types of crime. So far we have been looking at the kinds of offenses most people think about with they think of crime. We now look at some types of crime that tend to be forgotten or not thought of as crime. What is crime.
1.68k views • 15 slides

Cyber Crime. Statistics. The 2000 Computer Security Institute/FBI Computer Crime and Security Survey Ninety percent of the study's 585 respondents reported computer security breaches within the last twelve months
203 views • 6 slides
STAY SAFE ONLINE. Cyber Crime. What is Cyber Crime?. Cyber Crime is an online or Internet-based illegal act. Bahayanya Cyber Crime…. Types of Cyber Crime. Types of Cyber Crime. Nak buat macamana ni..?. How To Prevent Cyber Crime. Protect Your Personal Information.
817 views • 9 slides

CYBER CRIME. What is computer crime?. Computer crime refers to any crime that involves a computer and a network . The computer may have been used in the commission of a crime.
396 views • 16 slides
STAY SAFE ONLINE. Cyber Crime. What is Cyber Crime?. Cyber Crime is an online or Internet-based illegal act. Why Are System Vulnerable?. Contemporary Security Challenges and Vulnerabilities. Cyber Crime Trends. Criminal Gangs. Criminal Organizations. Friends. Lone Ranger.
690 views • 16 slides

CYBER CRIME. WHAT IS CYBER CRIME???. Also known a computer crime, digital crime , e-crime, and electronic crime.
676 views • 13 slides

Crime and Cyber-crime
Crime and Cyber-crime. Pieter Hartel. Crime. Acts or missions forbidden by law that can be punished […] , against: persons (e.g. rape, assault, murder, suicide) property (e.g. fraud, arson, theft, vandalism) the state (e.g. riot, treason, sabotage, terrorism)
512 views • 18 slides

CYBER CRIME. (COMPUTER CRIME). What is Computer Crime?. All crimes performed or resorted to by Abuse of electronic media or otherwise, with the purpose of influencing the functioning of computer or computer system. IN SHORT COMPUTER CRIME is any crime where- Computer is a TARGET .
510 views • 12 slides

Cyber Crime. Internet Banking Fraud. PREPARED BY : TEOH YI THENG & LOH CHEE JIA. T he criminal obtains customer's account access data. logon name . Pass-word. T he criminal uses this information to transfer money to other accounts and withdrawals of the funds .
296 views • 10 slides

Cyber Law And Cyber Crime
Cyber Law And Cyber Crime. Certificate ETHICAL HACKING FCCH. Authorized Learning Partner. Suryayusra, M.Kom Email: [email protected] Website: blog.binadarma.ac.id/suryayusra/ YM: [email protected]. FORESEC. Lembaga sertifikasi berstandar international
532 views • 14 slides

Cyber Crime. Special Thanks to Special Agent Martin McBride for sharing most of this information in his talk at Siena last semester. Criminal Activity Today. has shifted to the Internet. Canadian Lottery Scam. A call from Canada: You’ve won the Canadian Lotto
748 views • 64 slides

And. CYBER LOW. CYBER CRIME. Zaenal Abidin (12122175). LATAR BELAKANG. Seiring dengan perkembangan teknologi internet, menyebabkan munculnya kejahatan yang disebut dengan cyber crime dan cyber law atau kejahatan melalui jaringan internet. Munculnya beberapa kasus cyber crime di Indonesia.
1.21k views • 11 slides

Cyber crime
Cyber crime. Phishing. The internet is a hunting ground. FACEBOOK HIJACKED TO SPREAD CHROME, FIREFOX BROWSER MALWARE. 40% INCREASE IN ANDROID MALWARE CASES IN 2013. PHISHERS CAST A WIDE NET AND CATCH A WHALE. ...and YOU are the target!.
431 views • 17 slides

- Cyber Security
Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Business PPT
Digital Marketing
- Digital Transformation
Human Resources
Product Management
- Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories
Download Cyber Security PPT Presentation, Template & Slides
- Sub Categories
- 5G Technology
- Agile and Scrum
- Big Data Analytics
- Cloud Computing
- Cryptocurrency
- Data Analytics
- Green Energy
- Internet Of Things
- IT Certification
- Machine Learning
- Microprocessors
- Nanotechnology
- Robotic Process Automation
- Software Testing
- Technology Project Management
- Technology Quality Assurance
- Technology Stack
- Virtualization

EduDecks are professionally-created comprehensive decks that provide complete coverage of the subject under discussion. These are also innovatively-designed for a powerful learning experience and maximum retention

Ready to use PowerPoint sample assist you in saving both your time and effort. Luxury to add or remove content in the design. Transmute the PPT layout with industry information i.e. banner and icon. Flexible as can be adapted in JPEG or PDF documents. Text and font can be easily reformed as the presentation need. Presentation template design shown in both standard and widescreen slide

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Cyber Security It Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the eighty one slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

Presenting this set of slides with name - Data Governance Powerpoint Presentation Slides. This PPT deck displays twenty-five slides with in-depth research. We provide a ready to use deck with all sorts of relevant topics subtopics templates, charts and graphs, overviews, analysis templates. This template is compatible with Google Slides, which makes it accessible at once. Can be converted into various formats like PDF, JPG, and PNG. The slide is easily available in both 4:3 and 16:9 aspect ratio.
Enthrall your audience with this Enterprise Cyber Security Awareness Employees Training Complete Deck. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising fifty four slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Privacy IT Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the sixty five slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

Presenting our Cyber Security for Organization Proposal PowerPoint Presentation Slides. This is a completely adaptable PPT slide that allows you to add images, charts, icons, tables, and animation effects according to your requirements. Create and edit your text in this 100% customizable slide. It is also available in widescreen. You can change the orientation of any element in your presentation according to your liking. The slide is available in both 4:3 and 16:9 aspect ratio. These PPT slides are also compatible with Google slides.

This complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on How To Present Cyber Security To Senior Management Complete Deck and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of fifty five slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.

Enthrall your audience with this Cloud Security IT Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising eighty nine slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.

SlideTeam introduces Cybersecurity Incident Management Powerpoint Presentation Slides. Build a visually-stunning presentation by downloading this deck of 55 professionally-designed PPT slides. Each PowerPoint template features 100% customizability. Personalize text, font, orientation, colors, patterns, background, and shapes as desired. Convert the file format from PPT to PDF, PNG, or JPG as and when necessary. This presentation works well with widescreen and standard resolutions. Use Google Slides for easy access.
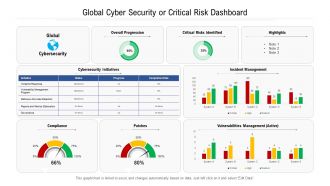
Presenting this set of slides with name Global Cyber Security Or Critical Risk Dashboard. The topics discussed in these slides are Global, Cybersecurity, Overall Progression, Critical Risks Identified, Highlights. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Enthrall your audience with this Cloud Security Model Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising eighty slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.

Presenting our cyber security and phishing awareness training PowerPoint presentation slides. This PowerPoint design contains fifty slides in it which can be completely customized and edited. It is available for both standard as well as for widescreen formats. This PowerPoint template is compatible with all the presentation software like Microsoft Office, Google Slides, etc. It can be downloaded in varying formats like JPEG, PDF, PNG, etc. You can download this PPT layout by clicking on the button below.

Presenting our well-structured Analysis Of NIST Cyber Security Framework. The topics discussed in this slide are Identify, Protect, Detect, Respond, Recover. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.

SlideTeam brings Implementing Cybersecurity Management Framework Powerpoint Presentation Slides. There are 55 visually-gripping PowerPoint templates in this 100% editable deck. Customize font, text, patterns, shapes, colors, orientation, and background as required. Convert the PPT file format into PDF, PNG, and JPG according to your convenience. Use Google slides to view this presentation. It also works well with standard and widescreen resolutions.

Presenting IT security PowerPoint presentation slide. It covers total of 19 professionally designed PPT slides. Our PowerPoint experts have included all the necessary layouts, diagrams and templates to meet the needs of the customers. This content ready deck is completely customizable. Edit the color, text and icon as per your requirement. You can also add or delete the content from the presentation as per your need. You can easily download this presentation. They are high resolution PPT templates and are perfectly compatible with Google Slides.
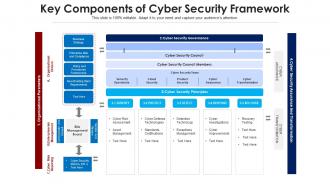
Introducing our Key Components Of Cyber Security Framework set of slides. The topics discussed in these slides are Cyber Risk Reporting, Organizational Drivers, Enterprise Risk Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.

Presenting our cybersecurity awareness training PowerPoint presentation slides. This PowerPoint design contains fifty-one slides in it which can be completely customized and edited. It is available for both standard as well as for widescreen formats. This PowerPoint template is compatible with all the presentation software like Microsoft Office, Google Slides, etc. It can be downloaded in varying formats like JPEG, PDF, PNG, etc. You can download this PPT layout by clicking on the button below.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Firewall Implementation For Cyber Security Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the seventy one slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

If you require a professional template with great design, then this Security Controls Management Cyberattacks Organization Infrastructure Investments is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.

Deliver an informational PPT on various topics by using this Phishing Attacks And Strategies To Mitigate Them Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with one hundred one slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.

This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fifty six slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.

Presenting computer security PowerPoint presentation slides. This deck comprises of 17 slides. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts and every slide consists of an appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed computer security presentation to save yourself from cybercrime.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Case Competition Overcome The Challenge Of Cyber Security In Healthcare Complete Deck is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the fourty nine slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of seventy eighjt slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this SASE IT Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the eighty slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

If you require a professional template with great design, then this Cyber Threat Powerpoint PPT Template Bundles is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twenty three slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
Keep your audience glued to their seats with professionally designed PPT slides. This deck comprises of total of twelve slides. It has PPT templates with creative visuals and well researched content. Not just this, our PowerPoint professionals have crafted this deck with appropriate diagrams, layouts, icons, graphs, charts and more. This content ready presentation deck is fully editable. Just click the DOWNLOAD button below. Change the colour, text and font size. You can also modify the content as per your need. Get access to this well crafted complete deck presentation and leave your audience stunned.

Presenting How To Handle Cybersecurity Risk Powerpoint Presentation Slides. This complete PPT deck is composed of 55 visually-stunning templates. Build a presentation faster using our 100% customizable PowerPoint slideshow. Edit text, font, colors, orientation, shapes, background, and patterns however you choose. Change the file format into PDF, PNG, or JPG as and when convenient. This presentation works well with standard and widescreen resolutions. Use Google Slides for a quick view.

Deliver an informational PPT on various topics by using this Ethical Hacking IT Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with eighty seven slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.

Engage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Cybersecurity Organizational Network Protection Measures is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.

Deliver an informational PPT on various topics by using this Implementing Effective Tokenization Strategies Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with fifty seven slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts,this Information Technology Security Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the eighty one slides are editable and modifiable,so feel free to adjust them to your business setting. The font,color,and other components also come in an editable format making this PPT design the best choice for your next presentation. So,download now.

Introducing cyber threat and security management PowerPoint slide. Well researched PPT template design with completely reform able styles, images, tables, graphs, context, sizes etc. Relevant for IT business professionals such as managers, executives, and researchers etc. Genuine and admissible PPT Image with pliant options to add the company name, brand, or emblem. Adequately compatible with all operating software and all Google Slides.
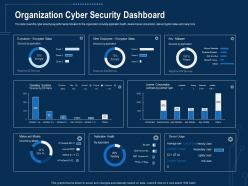
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an outstanding presentation on the topic using this Corporate Data Security Awareness Organization Cyber Security Dashboard Ppt Powerpoint Guidelines. Dispense information and present a thorough explanation of Executives, License Consumption, Operating Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
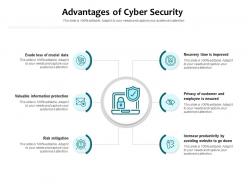
Presenting this set of slides with name Advantages Of Cyber Security. This is a six stage process. The stages in this process are Valuable Information Protection, Risk Mitigation, Recovery Time Is Improved, Evade Loss Of Crucial Data, Privacy Of Customer And Employee Is Ensured. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Data Security IT Powerpoint Powerpoint Presentation is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the eighty slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

Enthrall your audience with this Enterprise Governance Of Information Technology EGIT Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising seventy eight slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.

Introducing a Visual PPT on Many Types Frauds. Every slide in this PowerPoint is meticulously designed by our Presentation Experts. Modify the content as you see fit. Moreover, the PowerPoint Template is suitable for screens and monitors of all dimensions, and even works seamlessly with Google Slides. Download the PPT, make necessary changes, and present with confidence.

This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of seventy nine slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Enterprise Security Operations Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the fifty five slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
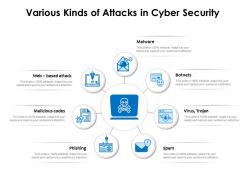
Presenting this set of slides with name Various Kinds Of Attacks In Cyber Security. This is a seven stage process. The stages in this process are Web Based Attack, Phishing, Botnets, Malicious Codes, Spam, Malware. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Deliver a credible and compelling presentation by deploying this Information Security Governance Information Planning Stakeholders Framework. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twelve slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Information Security Governance Information Planning Stakeholders Framework PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.

This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Data Breach Prevention And Mitigation Strategies For Businesses Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of seventy five slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.

Enthrall your audience with this Quantum Computing IT Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising eighty four slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.

Presenting our readily available Organization Cyber Protection Proposal PowerPoint Presentation Slides for your bidding needs. This is a completely adaptable PPT theme that lets you add images, charts, icons, and tables according to your need. The template is available in both 4:3 and 16:9 aspect ratios. It can be downloaded in PDF, JPG, and PNG formats. So download and captivate your audience.
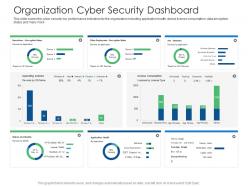
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an outstanding presentation on the topic using this Organization Cyber Security Dashboard Cyber Security Phishing Awareness Training Ppt Pictures. Dispense information and present a thorough explanation of Organization Cyber Security Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
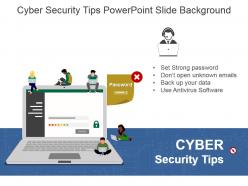
Presenting cyber security tips powerpoint slide background. This is a cyber security tips powerpoint slide background. This is a one stage process. The stages in this process are set strong password, don?t open unknown emails, back up your data, use antivirus software, cyber security tips.
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Present the topic in a bit more detail with this Cyber Security IT Dashboard For Threat Tracking In Cyber Security Ppt Powerpoint Tutorials. Use it as a tool for discussion and navigation on Monthly Threat Status, Threats By Owners, Risk By Threats, Current Risk Status, Threats Based On Role, Threat Report. This template is free to edit as deemed fit for your organization. Therefore download it now.

This complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Data Security Powerpoint Presentation Slides and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of twenty two slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.

This complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Technology Security Process Framework Assessment Management Awareness and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of twelve slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.

Presenting this set of slides with name Key Statistics Of Cyber Security In Small Businesses. The topics discussed in these slides are Business, Manufacturers, Cost Of Data, Ransomware, Identity Theft. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Data Privacy Compliance Awareness Planning Strategy Assessment Methodology Framework and has templates with professional background images and relevant content. This deck consists of total of twelve slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
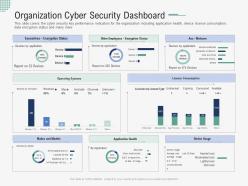
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Present the topic in a bit more detail with this Organization Cyber Security Dashboard Implementing Security Awareness Program Ppt Clipart. Use it as a tool for discussion and navigation on Organization Cyber Security Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
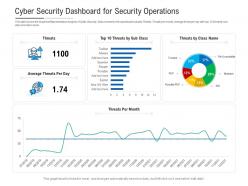
This slide Covers the Graphical Representation Analysis of Cyber Security. Data covered in this dashboard snapshot includes Threats, Threats per month, Average threat per day with top 10 threat by sub class and class name. This is a Cyber Security Dashboard Snapshot For Security Operations Powerpoint Template drafted with a diverse set of graphics, that can be reformulated and edited as per your needs and requirements. Just download it in your system and make use of it in PowerPoint or Google Slides, depending upon your presentation preferences.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Managing Cyber Risk In A Digital Age Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fifty six slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.

Engage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Information Security Risk Management Powerpoint Ppt Template Bundles is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With sixteen slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.

Enthrall your audience with this Encryption For Data Privacy In Digital Age IT Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising two hundred fourty one slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
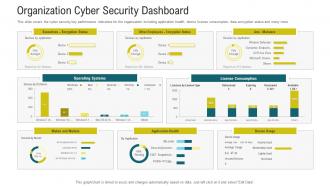
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an outstanding presentation on the topic using this Cybersecurity Awareness Training Organization Cyber Security Dashboard Ppt Model Graphics. Dispense information and present a thorough explanation of Executives, License Consumption, Operating Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.

Deliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this IT Security Operations Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the fifty nine slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
Item 1 to 60 of 540 total items
- You're currently reading page 1

Got any suggestions?
We want to hear from you! Send us a message and help improve Slidesgo
Top searches
Trending searches

suicide prevention
8 templates

46 templates

tropical rainforest
29 templates

spring season
34 templates

american football
16 templates

32 templates
Cybercrime Minitheme
Cybercrime minitheme presentation, free google slides theme and powerpoint template.
We spend many hours in front of the computer screen, browsing the net, so we have to be careful with our eyes, to avoid straining them too much... but we also have to be careful with cybercrime! Educate your audience on the various types of phishing and hacking! To do so, customize this template and fill it with your own informative content. We've used backgrounds with gradients, some linear icons and some photos of masked hackers (they're just models, not actual hackers!).
Features of this template
- 100% editable and easy to modify
- 21 different slides to impress your audience
- Contains easy-to-edit graphics such as graphs, maps, tables, timelines and mockups
- Includes 500+ icons and Flaticon’s extension for customizing your slides
- Designed to be used in Google Slides and Microsoft PowerPoint
- 16:9 widescreen format suitable for all types of screens
- Includes information about fonts, colors, and credits of the free resources used
How can I use the template?
Am I free to use the templates?
How to attribute?
Attribution required If you are a free user, you must attribute Slidesgo by keeping the slide where the credits appear. How to attribute?
Related posts on our blog.

How to Add, Duplicate, Move, Delete or Hide Slides in Google Slides
How to Change Layouts in PowerPoint
How to Change the Slide Size in Google Slides
Related presentations.

Premium template
Unlock this template and gain unlimited access

Register for free and start editing online
Home PowerPoint Templates Cyber Crime
Cyber Crime
Cyber Security Awareness PowerPoint Template

Cybersecurity Presentation Template

Cyber Crime PowerPoint Template

Cyber Technology PowerPoint Template

Cyber Security PowerPoint Slides
Download unlimited content, our annual unlimited plan let you download unlimited content from slidemodel. save hours of manual work and use awesome slide designs in your next presentation..
- Preferences

Cyber Crime - PowerPoint PPT Presentation

Cyber Crime
Cyber crime is the crime that which have a computer or internet. – powerpoint ppt presentation.
- Cyber Crime is the crime
- that have a computer, a
- network or network
- devices. These types of
- crimes include viruses and
- DOS (denial-of-service)
- Crimes thats use computer
- network to progression criminal activities.
- It can be classified into four major categories as
- Cyber crime against individual
- Cyber crime against property
- Cyber crime against organization
- Cyber crime against society
- Email spoofing It is one in which email header is forget so that pass to originate one source but actually sent another source.
- Spamming it means send multiple copies of unsolicited mails.
- Cyber Defamation it occur when defamation take place with the help of computers or internet.
- Harassment and Cyber stalking it means following moves of an individuals activity over the internet.
- Credit card fraud
- Intellectual property
- crimes These include
- Software piracy
- Copyright infringement
- Trademarks violations
- Theft of computer source Code
- III. Internet time theft it usage internet hours by unauthorized person which is actually paid by another person.
- Unauthorized Accessing of computer
- Denial of service
- Virus Attack
- Trojan Horse
- Email Bombing
- Salami Attack
- Data diddling
- Forgery currency notes, marks-sheets and stamps etc can be forged by computers and high quality Scanner and printer.
- Cyber Terrorism Use of computer resources to intimidate pr coerce others.
- Web Jacking Hackers gain access or control over the websites of another,
- Cyber bullying
- Cyber stalking
- Virus dissemination
- Cyber Security is the
- potential activity by
- which information and
- other communications
- systems are protected
- from against unauthorized
- use or modifications or even theft.
- Keep your operating system and all system software updated regularly.
- Do proper password management
- keep antivirus software updated regularly
- Use firewall and other security software
- Avoid untrusted Wi-Fi connections
- Have data backup , update it regularly
- Avoid surfing untrusted websites.
PowerShow.com is a leading presentation sharing website. It has millions of presentations already uploaded and available with 1,000s more being uploaded by its users every day. Whatever your area of interest, here you’ll be able to find and view presentations you’ll love and possibly download. And, best of all, it is completely free and easy to use.
You might even have a presentation you’d like to share with others. If so, just upload it to PowerShow.com. We’ll convert it to an HTML5 slideshow that includes all the media types you’ve already added: audio, video, music, pictures, animations and transition effects. Then you can share it with your target audience as well as PowerShow.com’s millions of monthly visitors. And, again, it’s all free.
About the Developers
PowerShow.com is brought to you by CrystalGraphics , the award-winning developer and market-leading publisher of rich-media enhancement products for presentations. Our product offerings include millions of PowerPoint templates, diagrams, animated 3D characters and more.

116 CyberCrime Topics & Essay Samples
If you are writing a cybercrime essay, our team prepared this article just for you. Here, you will find 115 unique topics for any type of paper.
140 Interesting Cybercrime Research Topics To Focus On
Table of Contents
Do you have to submit a cybercrime research paper? Are you looking for the best cybercrime research topics for your law assignments? Well, to help you out, here, we have compiled a list of interesting essays and research topic ideas on cybercrimes. Continue reading this blog post and gain unique ideas for writing a cybercrime research paper or an essay.
What is a Cybercrime?
Cybercrime is a criminal activity that is committed using a computer, a network, or a networked device. In recent times, the internet plays a vital role in the daily life of an individual. Particularly, a lot of financial transactions and data sharing are happening over the internet. So, considering that many cybercrimes are being carried out by cybercriminals for generating a profit. Basically, cybercrimes are of three categories.
- Crimes in which the computer is used as a weapon. E.g., launching a denial-of-service (DoS) attack, or malware attack.
- Crimes in which a computer or networked device is a target. E.g., gaining network access.
- Crimes in which a computer is used as an accessory to a crime. E.g., data theft, cyberstalking.
Under the above-mentioned categories, different types of cybercrimes are being carried out by cybercriminals. Cybercrimes include both monetary and non-monetary offenses. Mostly, cybercrimes result in damage to an individual, a device, or a government.
List of Cybercrimes
In the entire world, plenty of cybercrimes are happening. The masterminds behind all those dangerous crimes are the hackers with strong hacking and technical knowledge. Mainly, cybercrimes are carried out at locations where there is digital data.

Here is a list of some widely carried out cybercrimes across the world.
- Cyber Bullying
- Cyber Grooming
- Child Pornography
- Cyber Stalking
- Online Job Fraud
- Online Sextortion
- SIM Swap Scam
- Credit Card/Debit Card Fraud
- Impersonation/Identity Theft
- Viruses, Trojans, and Worms
- Online Drug Trafficking
- Data Breach
- Cryptojacking
- Cyber-Squatting
- Website Defacement
In order to prevent cybercrimes and reduce the risk of cyberattacks, cyber security is practiced. Also, to handle all the cybercrimes, each country has a separate cybercrime department and they follow strict cyber laws.
Cybercrime Research Topics and Ideas
Nowadays, a lot of questions are being raised about cybercrimes. To get answers for them all, conducting research is the only option. In case, you are asked to craft a cybercrime research paper on the topic of your preference, consider any topic related to common cybercrime cases such as personal data theft, financial theft, cyber-extortion, drug trafficking, and terrorism.

Are you a law student who has a keen interest to analyze and study cybercrimes? If yes, then the list of the best cybercrime research topics recommended below will be helpful to you. Without any hesitation, explore the full list and select any topic that is comfortable for you to analyze and write about.
Best Cybercrime Research Topics
- What is the role of America in protecting corporations from cybercrime?
- Have a close look at cybercrime, cyber forensics, and digital evidence.
- Is cybercrime the top IT threat?
- Write about the necessity of cyber security in preventing cybercrimes.
- Discuss the international laws and regulations related to cybercrime.
- Explain the effects of the UAE Cybercrime policy.
- What are the toolkits used in cybercrimes?
- Discuss the cybercrimes in Singapore.
- Write about UAE cybercrime laws.
- Explain the impact of cybercrime on the global criminal justice system.
- Have a detailed look at international cyberwar.
- Talk about Cybercrimes in the US.
- Discuss identity theft and cybercrime in contemporary society.
- Explain the significance of digital education and creating awareness of cybercrime.
- What are the effects of cybercrime on the world’s major countries?
- Explain UAE cybercrime laws.
- What is the need for cyber security in preventing cybercrimes?
- Discuss the role of America in protecting corporations from cybercrime.
- Importance of raising cybercrime awareness and digital education
- Analyze some recent cases of cybercrime in the banking industry and its consequences
- Discuss the impact of IP (intellectual property) rights, cyber piracy, and cybercrime on domestic and international business with the latest examples
- Critically analyze the degree and frequency of cybercrime in the United States
- Analyse the Cybercrime Legislation Amendment Act 2012(Cth) (CLAA)
- Compare and contrast the cybercrime prevention laws in India and the United Kingdom
- Analyze the Cybersecurity Laws and Regulations Report 2023 USA
- What are the key measures to undertake by a company to protect the cloud computing environment from cybersecurity issues?
- Identify and analyze the components of broadband industry structure and cybercrime
- Discuss the relationship between cybercrime, the economy, privacy, hacking, and terrorism
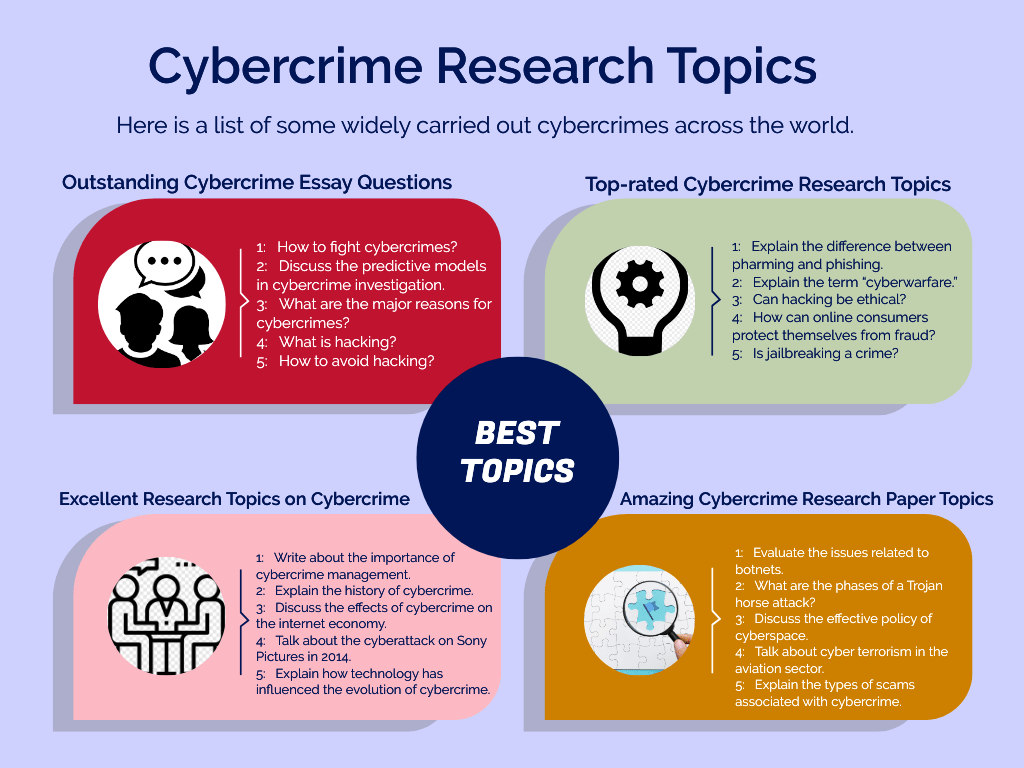
Good Cybercrime Essay Topics
- What are all the effects of cybercrime on the world’s major countries?
- Discuss the cybercrimes in the healthcare industry.
- Explain the developments in hacking.
- Discuss the trends of the future of good cybercrime.
- Write about Cybercrimes in Australia.
- What are the impacts of cybercrime on the banking industry?
- Is identity theft a cybercrime?
- Should capital punishment be given for cybercrime?
- Discuss the solutions for cybercrimes in Information Technology.
- Talk about cybercrime and social media.
- Explain the cybercrime challenges in public universities.
- Have a closer look at business fraud and cybercrime.
- Write about cybercrimes in India.
- Discuss terrorist cyberattacks with an example.
- Explain the impact of cybercrime on a government.
- Discuss the five biggest cyber security trends in 2022
- Remote working risks of cybersecurity
- Importance of Password-only Authentication in restricting cybercrime
- The Rise of Ransomware: Discuss
Unique Cybercrime Research Topics
- How to explain cybercrime using criminological theories ?
- How does crypto jacking work?
- Track the evolution of online scams.
- Analyze the implications of the Cyberpunk 2077 leak.
- How do cybercrimes afflict retail shops?
- What are man-in-the-middle attacks?
- What are the various phases of a DDoS attack?
- How to mitigate a denial-of-service attack?
- Analyze the success rate of email scams.
- Describe the working of WannaCry malware.
- Describe what happens during a Brute Force attack.
- How does ransomware work?
- How to protect children from cyberbullying?
- Have a closer look at big data and increased cybercrimes.
- Compare various types of fraud methods.
- What are identity theft and cybercrime in contemporary society
- Discuss the statistics on cybercrime as well as Fraud
Outstanding Cybercrime Essay Questions
- How to fight cybercrimes?
- Discuss the predictive models in cybercrime investigation.
- What are the major reasons for cybercrimes?
- What is hacking?
- How to avoid hacking?
- Whose responsibility is cybercrime?
- Discuss the cost of cybercrime and digital spying.
- How does cybercrime affect domestic and foreign business?
- How to investigate cybercrime?
- Discuss the link between fraud and invisible attackers.
Top-rated Cybercrime Research Topics
- Explain the difference between pharming and phishing.
- Explain the term “cyberwarfare.”
- Can hacking be ethical?
- How can online consumers protect themselves from fraud?
- Is jailbreaking a crime?
- How can parents monitor their children’s behavior on the web?
- How to prevent cyberbullying in the online learning environment?
- Would cyber communism decrease bullying?
- Discuss the connection between political protests and hacking.
- Talk about the mental health effects of internet bullying.
- Who is responsible for online misbehavior?
- Who are white hat and black hat hackers?
- Explain the effects and solutions of catfishing.
- Should schools teach online etiquette?
- Does internet anonymity bring out the worst in people?
- How to stay safe online?
- How does a firewall help to protect the network?
- Explain how cyberbullying differs from in-person harassment.
- How to cope with online harassment?
- Write about phishing and scam on the internet.
Also read: Best Cybersecurity Research Topics for Students to Consider
Excellent Research Topics on Cybercrime
- Write about the importance of cybercrime management.
- Explain the history of cybercrime.
- Discuss the effects of cybercrime on the Internet economy.
- Talk about the cyberattack on Sony Pictures in 2014.
- Explain how technology has influenced the evolution of cybercrime.
- Discuss the social effects of cyberbullying on children.
- What are the signs of phishing attempts?
- What emergency action should an individual take after being hacked?
- Research and explain the significant cyber threats to US national security.
- Different types of cybercriminals.
- How do private sectors battle cybercrimes?
- Discuss the impacts of mobile devices on cyber security.
- Take a closer look at cyberfeminism and social media.
- Compare the functions of various antivirus programs.
- Discuss the pros and cons of various InfoSec certificates.
Amazing Cybercrime Research Paper Topics
- Evaluate the issues related to botnets.
- What are the phases of a Trojan horse attack?
- Discuss the effective policy of cyberspace.
- Talk about cyber terrorism in the aviation sector.
- Explain the types of scams associated with cybercrime.
- Discuss the potential effects the cyber currencies have on South African Businesses.
- How the automotive software of smart cars can be protected from cyberattacks?
- Discuss the effects of cyberbullying on teen suicides.
- Have a closer look at the cyber policy and strategy of the United Kingdom.
- What are the dangers of public Wi-Fi networks?
High-quality Cybercrime Research Ideas
- Describe the technology of unlocking a phone through facial recognition and the fingerprint of the owner of the phone
- Select a company from the United States and discuss their efforts and strategies to ensure cyber security
- Discuss the reasons that make every individual aware when it comes to safeguarding and protecting personal data and information from hackers
- Face recognition vs. a simple security code vs. fingerprint: Which is the safest locking option for smart devices and why?
- The increasing use of the internet consecutively increases the likelihood of adolescents and young adults engaging in cybercrime-related activities (e.g., email and internet fraud, identify fraud)
- Compare and contrast the effects of Phishing Emails, DoS (Denial of Service) Attacks, and Social Engineering
- Describe the history of cybercrime and the way cybercriminals have introduced different strategies to commit such crimes over the past decades
- Discuss the similarities and differences between distributed denial-of-service (DDoS) attacks and DoS (Denial of service) attacks
- Examination of the consequences a community or society would have to bear in case a hacker targeted the entire state
- Is purchasing from e-commerce sites such as eBay, Amazon, and Craigslist more ethical and safe compared to buying from other online marketplaces? Explain with reasons and the cyber security strategies of the aforementioned sites.
Impressive Cybercrime Research Topics
- Explain the importance of parental control mechanisms on children’s computers.
- What are effective strategies to cope with online harassment?
- Establish a link between feminism and the fight against cyberstalking.
- Analyze online gaming behavior from a psychological standpoint.
- How did industrial espionage evolve into hacking?
- Describe how an SQL injection attack unfolds.
- What are the safest ways to ensure data integrity?
- Discuss the pros and Cons of various cryptographic methods.
- How can a person reach maximum technological security?
- Explain the mechanics of password protection.
Final Words
From the list of ideas suggested above, choose any topic that matches your requirements and craft a detailed cybercrime research paper with proper citations and proofs to prove your thesis statement. In case, you need an expert to offer you help with cybercrime research paper topic selection and writing, get in touch with us immediately. We have numerous professional writers who are experts in the field of law and cybercrime to provide assignment help online according to your needs.
If you wish to make use of our cybercrime research paper writing service, just write your requirements in the order form and submit it. Based on the specifications you send us, our cybercrime research paper helpers will craft and dispatch a well-structured and plagiarism-free academic paper on time. Also, you can opt for endless paper revisions and round-the-clock customer support by availing of our assignment writing services.

Related Post

220 Amazing Religious Research Paper Topics and Ideas

Read and Understand How to Write a Research Proposal

100+ Controversial Research Topics and Ideas to Focus On
About author.
Jacob Smith
I am an Academic Writer and have affection to share my knowledge through posts’. I do not feel tiredness while research and analyzing the things. Sometime, I write down hundred of research topics as per the students requirements. I want to share solution oriented content to the students.
Comments are closed.
- Featured Posts
140 Unique Geology Research Topics to Focus On
200+ outstanding world history topics and ideas 2023, 190 excellent ap research topics and ideas, 150+ trending group discussion topics and ideas, 170 funny speech topics to blow the minds of audience, who invented exams learn the history of examination, how to focus on reading 15 effective tips for better concentration, what is a rhetorical analysis essay and how to write it, primary school teacher in australia- eligibility, job role, career options, and salary, 4 steps to build a flawless business letter format, get help instantly.
Raise Your Grades with Assignment Help Pro

IMAGES
VIDEO
COMMENTS
Cybercrime.ppt - Download as a PDF or view online for free. Cybercrime.ppt - Download as a PDF or view online for free. Submit Search. Upload. Cybercrime.ppt • Download as PPTX, PDF • 603 likes • 737,250 views. Aeman Khan Follow. Social Media Technology. Report. Share. Report. Share. 1 of 20. Download now. Recommended. Cyber-crime PPT.
Introduce your topic and host expert discussion sessions with this Cyber Crime Powerpoint Ppt Template Bundles. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twelve slides included in this template.
Module 13 examines the types of crimes that are considered as cyber organized crime and the types of organized criminal groups that engage in cybercrime. This Module further explores the measures used to counter cyber organized crime. Module 14 examines topics, such as hacktivism, terrorism, espionage, disinformation
7| Cyber Crime. This presentation has been viewed for over 294,000 times and it includes a basic introduction to cybercrime. You will get to know about the variants of cybercrime such as phishing, vishing, cyberstalking, cost of cybercrime in India, cyber laws, various ACTs including the preventive measures for such activities.
The presentation includes sections on cyberbullying, cyber stalking, financial cyber crimes, cyber terrorism, selling illegal articles online, and software piracy. It is presented by 5 students and addresses topics like how these crimes are committed, examples of related crimes, prevention methods, and potential penalties. Read less
The 1s and 0s behind cyber warfare. Chris Domas is a cybersecurity researcher, operating on what's become a new front of war, "cyber." In this engaging talk, he shows how researchers use pattern recognition and reverse engineering (and pull a few all-nighters) to understand a chunk of binary code whose purpose and contents they don't know.
Premium Google Slides theme and PowerPoint template. Every day we do more and more things online: shopping, booking vacations, bank transactions, etc. Without a doubt, it makes things much easier for us and gives us convenience and flexibility, but the Internet is full of cybercriminals ready to give us a hard time. That is why it is important ...
Fascinate your viewers with our innovative Cyber Crime presentation template, designed for PowerPoint and Google Slides, and make an impact like never before! Utilize it to explain criminal misconduct, such as phishing and data theft, done on a company's network using the internet. You can further discuss the economic, reputational, and other ...
The slides of cybercrime concepts could help present complex topics about internet world that affect people worldwide. The Cyber Crime PowerPoint Template provides a visual illustration of data breach, unauthorized access, and other online crimes. Therefore, this PowerPoint template is a good start of technology and cyber security.
Types of Cyber crime. Cybercrime encompasses a range of illicit activities conducted in the digital realm. Some prevalent types include phishing, where deceptive emails or messages trick users into revealing sensitive information; ransomware attacks, during which malicious software encrypts data until a ransom is paid; identity theft, where ...
Types of cybercrime. Cybercrime ranges across a spectrum of activities. At one end are crimes that involve fundamental breaches of personal or corporate privacy, such as assaults on the integrity of information held in digital depositories and the use of illegally obtained digital information to harass, harm, or blackmail a firm or individual. These new cybercapabilities have caused intense ...
Deliver an outstanding presentation on the topic using this Action Plan To Combat Cyber Crimes Cyber Attacks Faced By Organization. Dispense information and present a thorough explanation of Cyber Attacks Faced By Organization, IT Operations And System Downtime, Remote Desktop using the slides given.
🔵 Intellipaat Training Courses: https://intellipaat.com/pg-certification-cyber-security-ethical-hacking-mnit/In this session on CyberCrime, you will learn ...
Below you'll see thumbnail sized previews of the title slides of a few of our 63 best cyber crime templates for PowerPoint and Google Slides. The text you'll see in in those slides is just example text. The cyber crime-related image or video you'll see in the background of each title slide is designed to help you set the stage for your ...
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an outstanding presentation on the topic using this Corporate Data Security Awareness Organization Cyber Security Dashboard Ppt Powerpoint Guidelines.
Free Google Slides theme and PowerPoint template. We spend many hours in front of the computer screen, browsing the net, so we have to be careful with our eyes, to avoid straining them too much... but we also have to be careful with cybercrime! Educate your audience on the various types of phishing and hacking! To do so, customize this template ...
Cyber Crime. Cyber Security Awareness PowerPoint Template. Diagrams. Cybersecurity Presentation Template. Business PowerPoint Templates. Cyber Crime PowerPoint Template ... Save hours of manual work and use awesome slide designs in your next presentation. Subscribe Now #1 provider of premium presentation templates for PowerPoint & Google Slides ...
Cyber Crime. Description: Cyber crime is the crime that which have a computer or internet. - PowerPoint PPT presentation. Number of Views: 52162. Slides: 13. Provided by: Parveen-Bala. Category: Medicine, Science & Technology.
116 CyberCrime Topics & Essay Samples. Updated: Mar 2nd, 2024. 9 min. If you are writing a cybercrime essay, our team prepared this article just for you. Here, you will find 115 unique topics for any type of paper. We will write. a custom essay specifically for you by our professional experts. 809 writers online.
Excellent Research Topics on Cybercrime. Write about the importance of cybercrime management. Explain the history of cybercrime. Discuss the effects of cybercrime on the Internet economy. Talk about the cyberattack on Sony Pictures in 2014. Explain how technology has influenced the evolution of cybercrime.