Browse Course Material
Course info, instructors.
- Prof. Dimitri Bertsekas
- Prof. Eytan Modiano

Departments
- Electrical Engineering and Computer Science
- Aeronautics and Astronautics
As Taught In
- Computer Networks
- Telecommunications
Learning Resource Types
Data communication networks, course description.

You are leaving MIT OpenCourseWare
- Skip to content
- Skip to search
- Skip to footer

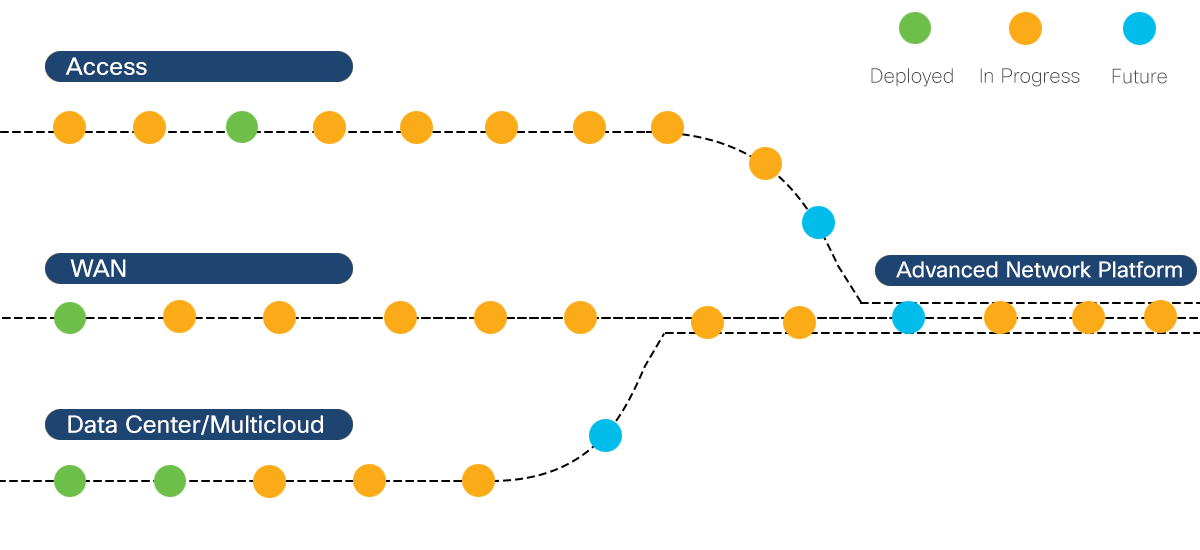
The network drives our business
Cisco's network is made up of systems that address the unique needs of each place in the network, connected by a common infrastructure. These systems help us speed new technology, protect network and data integrity, and improve employee productivity.
- See our IBN journey
Cisco IT Road to Intent-Based Networking
Cisco it shares insights and lessons learned from our own ongoing network transformation journey across access, wan, and data center/cloud..
In Progress
Mobile workplace
Flexible collaborative workplace designed to improve productivity and optimize workspace resources.
Telework/BYOD
Telework/ BYOD
AnyDevice program enabling employees to choose and own their own device, and secure it for safe business use.
Scalable access policy.
Cisco Software-Defined Access (SD-Access) for simplified, centralized, and automated policy management across converged LAN and Campus networks.
Work from anywhere.
Secure, seamless roaming across corporate and public Wi-Fi and mobile (LTE/5G) networks.
Coming soon..
Network segmentation
Automated, policy-based segmentation across campus and branch access networks for security, agility, and policy enablement within between and segments.
Ai-enabled analytics.
Artificial Intelligence and Machine Learning to provide accurate insights for reactive and proactive event management and faster remediation.
Iot/human telemetry.
Employing wireless and sensors to collect location and state information from people and devices for better workplace safety and efficiency and resource management.
Itsm integration.
Integration of full IT Service Management (in Cisco, ServiceNow / Cisco ESP) with other automated management systems for end to end infrastructure inventory...
AI-enabled policy automation
AI-enabled automation of intent translation, application classification and application performance policy creation and activation.
Autonomous access
Full cycle automation for onboarding all users and devices on any part of the private or public network, including user and deivce identification, authentication and policy definition and activation.
Combined WAN supporting voice, video and data across hybrid network connections for efficiency and cost.
CoLo enterprise backbone
A new WAN architecture (CloudPort) with Internet access & Security / WAN hub in CoLo Carrier Neutral Facility (CNF).
Cloud backbone.
Dual parallel backbone WAN of Leased and Internet connections enabling QoS route selection and overall lower cost.
Secure automated sd-wan.
Cisco Software-Defined WAN (SD-WAN) for simplified, centralized, and automated policy management of virtual overlay WANs across any WAN circuit(s).
Secure multi-cloud access
Secure multi-cloud access (SIG/SASE)
Multiple security functions integrated in one cloud service; flexibility to deploy security services how and where you choose; ability to secure direct-to-internet access...
View more >
WAN AI analytics
Provide AI-enabled insights across WAN, Internet and Cloud connections for reactive and proactive application service level optimization.
Autonomous WAN
AI / ML guided, fully reactive and proactive WAN as a Service automation.
Autonomous multi-cloud
Fully automated cloud-connected, SaaS/IaaS-connected WAN / Core as a Service.
E2e segmentation, automated policy-based segmentation for any user or device anywhere to any application or workload anywhere., e2e policy automation, automated policy-based application optimization for any user or device anywhere to any application anywhere., e2e assurance.
End to end application service monitoring and assurance with AI-enabled predictive trouble shooting and remediation.
E2e closed loop ibn.
End to end intent-based networking continuously aligns network to meet changing business needs, application requirements and user experience.
Data Center/Multicloud
Private cloud network.
CITEIS first generation private cloud VMWare IaaS / OpenShift PaaS cloud environment.
Elastic xaas.
Full service private cloud - supporting OpenStack, KVM Docker containers & Kubernetes, with full PaaS support for multiple combinations of Dev/Sec/Ops...
Automatation DC Network Operations
Automated DC network operations(ACI/ Segmentation)
A Software-Defined data center infrastructure, policy-based deployment and white-list security.
DC network assurance (NI)
Cisco network assurance engine helps network operations teams meet the agility, uptime, and security policy compliance requirements of modern data center networks., multicloud workload simplification.
Automate and assure consistent network policies for your distributed applications across multicloud environments.
Multicloud Workload Optimisation
Multicloud network workload optimization
Simplify network operations with policy automation and insights for your distributed application, managed centrally across your multicloud environment.

A flexible collaborative workplace designed to improve productivity and optimize workspace resources.
Prior to the 2020 pandemic, more than 70% of employees worked from home at least one day a week. this meant that on any given day, only 50% of our office space was occupied. we redesigned our office space to efficiently accommodate different work styles based on advanced wireless and collaboration technologies..
Icon signifies an area of technology that is continuously refreshed.
- Cisco Wi-Fi
- Cisco Collaboration
Related links:
- Cisco Connected Workplace: More Productivity and Satisfaction, Less Office Space and CO2
- Preparing the Enterprise for Wi-Fi 6
Cisco has gained multiple business benefits from secure mobility, starting with our first implementation of a WLAN in 2000, through VPN connectivity, Mobile Device Management (MDM), and the redesigned office spaces and BYOD policies of recent years. Learn about the benefits and details regarding what we have implemented in our mobility journey.
- Cisco AnyConnect
- Cisco Meraki Systems Manager (MDM)
- Five ways we’re improving telework with SD-WAN and telemetry
- Transforming the enterprise with secure mobility
- Mobile Device Management in the Meraki Cloud
- Scaling VPN when the global workforce moved home
Cisco IT manages thousands of switches and APs in more than 400 global offices. We’re always looking for ways to strengthen compliance with security policy, improve the user experience, and simplify our jobs to make more time for innovation. Enforcing security policies based on identity rather than location saves time for IT and gives people more flexibility to choose where they work.
- Cisco SD-Access
- Cisco DNA-Center Controller
- Catalyst 9K switches
- Cisco Aironet 4800 Wireless AP's
- Catalyst 9000 WLC's and AP's
- Measuring the impact of a software-defined access fabric network
- Journey to a software-defined access fabric network, part 2
- Journey to a software-defined access fabric network, part 1
- Secure flexible access with SD-Access
OpenRoaming will provide our mobile users with frictionless onboarding and secure access to resources across private and public Wi-Fi and 5G networks. Users need to sign on only once with a trusted identity provider. Afterward, they will be automatically connected to OpenRoaming networks whenever and wherever one is available.
- Cisco OpenRoaming
- Coming soon...
Enforcing security policies and automated segmentation based on identity rather than location saves time for IT, protects resources, and gives people more flexibility to choose where they work.
- Cisco Catalyst Center
- Cisco Identity Services Engine (ISE)
5 ways automating software image management is making Cisco IT engineers’ lives better
- Cisco Catalyst Center smooths network operations
By applying advanced analytics and machine learning across our own Data Center, WAN, and Access networks public Internet and Cloud networks we will be able to empower administrators to significantly improve performance and issue resolution.
- Cisco Catalyst Center Assurance
- Cisco vManage/vAnalytics
- Cisco Meraki Dashboard
- Cisco ThousandEyes
- Cisco IT—our future network
Employee safety is top of mind as we gradually welcome employees back to Cisco offices across the globe. Before allowing employees to return, our Workplace Resources team wants to make sure employees are practicing social distancing—not standing or sitting too close or gathering in large groups. Our network is vital in ensuring the resumption of safe, productive, and collaborative work.
- Cisco DNA Spaces
- Cisco Aironet APs
- Cisco Catalyst 9K APs
- Managing a safer return to work with Cisco DNA Spaces — An early report
- Helping to keep employees safe
Integration of full IT Service Management (in Cisco, ServiceNow / Cisco ESP) with other automated management systems for end to end infrastructure inventory and status management.
We are integrating our network controller systems ad itsm system in multiple ways to make it easier to find the right information to solve problems, streamline tasks for network changes, and allow routine operational tasks to run autonomously in an end-to-end automated workflow..
- Cisco DevNet
- 3 ways Cisco Catalyst Center and ServiceNow integration makes IT more efficient
- Using Catalyst Center as a Platform
AI-enabled automation of intent translation, application classification, and application performance policy creation and activation.
With low cost, fixed form factor iot endpoints becoming increasingly prevalent on our networks, there is an urgent need to automate identification and apply access policies. we need an automated method of finding, identifying, segmenting, and monitoring traffic for all types of connected devices..
- Cisco Catalyst Center AI Endpoint Analytics
Full cycle automation for onboarding all users and devices to any part of the private or public network, including user and device identification, authentication, and policy activation.
- Cisco Catalyst Center Policy Automation
To ensure consistently good voice, video and data application experiences for all users has traditionally required the integration of a comprehensive set of WAN traffic control and security features into our branch-office routers. Cisco IT has long used WAAS to optimize WAN bandwidth and improve performance for Cisco users when they access content-rich applications from remote offices.
- Cisco ISR 4000 Series Routers
- Secrets to Ensuring Application Performance at the Branch
- Reducing Cloud Application Bandwidth
IT must change WAN designs from centralized around internal DC to more disperse utilization of the ""Cloud"" and various Cloud Services. To do this Cisco IT has built secure CloudPorts in or near Carrier Neutral facilities which enable optimized connectivity to Cloud resources and allow to quickly & securely interconnect clouds.
- Cisco Catalyst 9K
- Cisco Nexus 7K
- Cisco Firepower
- Cisco IT Multicloud Backbone Securely Inter-connecting Clouds
In this age of multicloud, Cisco IT realized we needed a new WAN backbone that will allow us to operate more like a service provider for our internal clients. Built on the Cisco ASR 9000 Series Aggregation Services Routers running Cisco IOS-XR software, this highly scalable and programmable router provides a strong foundation for access to and between increasingly distributed applications and users.
- Cisco ASR 9K
- Cisco FirePower 9300s
- Cisco CSP 21xx & 55xx
- Cisco SD-WAN Cloud OnRamp
- How the network team’s bold steps + agile mindset launched a cloud-ready backbone
- As the Landscape Evolves, so must the Enterprise Backbone
We’re becoming a true multi-cloud company. We use almost 1000 cloud services, including Cisco Webex, Salesforce, Office365, and Box. Currently, more than 25% of traffic from our campuses and branch offices heads to public clouds. So we needed more capacity, operational consistency, and agility to keep delivering a great application experience to employees in our 450 branch offices.
- Cisco vManage
- ASR-1002-HX
- Meraki SD-WAN
- A simpler, more flexible SD-WAN design for branches, from Customer Zero. Top five benefits
- Network of the Future, Today. How We’re Growing WAN Capacity While Optimizing Costs
Multiple security functions integrated into one cloud service; the flexibility to deploy security services how and where you choose; ability to secure direct-to-internet access, cloud app usage, and roaming users; plus, no appliances to deploy.
- The SASE Story III
- The SASE Story II
- The SASE Story I
Provide AI-enabled insights across WAN, Internet, and Cloud connections for reactive and proactive application service-level optimization.
- Cisco AppDynamics
- Employees do their own performance troubleshooting with ThousandEyes
- Zeroing in on network performance issues with ThousandEyes
- Simple way to measure user experience? ThousandEyes on Raspberry Pis
AI / ML guided, fully reactive, and proactive WAN as a Service automation.
Ai-enabled sd-wan uses insights to identify application performance impacting network issues and dynamically takes action to achieve performance enhancements. it uses apm, public network telemetry, and sd-wan analytics to ensure a proactive response to dynamic network, application, and security conditions., a fully automated lifecycle for multicloud networking enabling agile and secure workload management and access. • applications: workloads including modern architectures composed of microservices and containers, supported by an agile, flexible, and elastically scalable network that delivers consistent and simple provisioning, management, and security. • access: highly available and responsive access to applications (including on premises, iaas, and saas) delivered with consistent security, reliability, and performance to users and devices anywhere..
- Cisco Multicloud Networking
- How Cisco IT is solving multi-cloud management: a single pane of glass
Automated policy-based segmentation consistently across all network domains (access, WAN, DC, multicloud). Allows automated zero-trust on-boarding, categorization, and access to only authorized resources.
End-to-end activation of stated business intent and application performance requirements from user or device to and between workloads consistently across all network domains (access, wan, dc, multicloud)..
- Cisco Nexus Dashboard
- Cisco Intersight
True end-to-end application visibility and assurance of stated business intent and policy from user or device to applications or between workload consistently across all network domains (access, WAN, DC, multicloud).
- Cisco ThousandEye
End to end intent-based networking continuously aligns the network to meet changing business needs, application requirements, and user experience demands.
In 2013 the cisco it elastic infrastructure services program, or citeis, was our internal implementation of infrastructure as a service (iaas) and platform as a service (paas) resources in a private cloud. citeis was designed to provide a consumer-type it experience to our developers while cisco it maintains governance and control over the infrastructure..
- Cisco IT Best Practices for Creating a Private Cloud
Full service private cloud - supporting OpenStack, KVM Docker containers & Kubernetes, with full PaaS support for multiple combinations of Dev/Sec/Ops platform tools for app designers.
In 2018 we extended the concepts behind citeis to an expanded internal cisco it cloud’s compute and storage service. this service is built upon a new private-cloud infrastructure utilizing cisco unified computing system™ (cisco ucs®) c-series servers and cisco application-centric infrastructure (aci), as well as openstack and other open-source software..
- Offering an Internal Cloud Service
Automated DC network operations (ACI/Segmentation)
A software-defined data center infrastructure, policy-based deployment, and white-list security., by moving our platform as a service (paas) application development and dev/ops private cloud to our aci fabric we are bringing greater automation, security, ease of use and cost-savings to our it data center infrastructure through open source and open apis..
- Cisco Nexus 9Ks
- Cisco Nexus 1000v
- Cisco UCS Manager
- Cisco UCS Director
- Cisco IT Nearing Final Phase of ACI Journey
Cisco IT uses NAE to transform ACI network operations from a reactive posture to a highly proactive approach. This approach substantially drives down MTTR for incidents, shrinks change windows, and optimizes planning in large scale data centers.
- Cisco Network Assurance Engine
- Cisco IT Advances Proactive, Predictive Operations with Cisco Nexus Dashboard
- Cisco IT Cisco Network Assurance Engine Deployment
Cisco is extending existing policies, governing tenants or workloads, across network fabrics that traverse on-premises and cloud environments, with centralized policy provisioning and management applied consistently across this multicloud network.
- Cisco Cloud ACI
Simplify network operations with policy automation and insights for your distributed applications, managed centrally across your multicloud environment
- Cisco Network Insights
- Explore journey
- Show overview
IT networking stories

Providing secure, easy access to the corporate network from anywhere, at any time, on any device.
Preparing the enterprise for Wi-Fi 6
Migrating to a new Cisco wireless infrastructure
Automating Cisco home and remote access router updates
Cost-effective connectivity for small offices

Connecting branches to data centers and multi-cloud environments through a single fabric.
Bringing SD-WAN to Our Branch Offices: Our Journey and Lessons Learned
Go anywhere with Catalyst 9000s

Software-defined network
Delivering a centralized, programmable network, making it more flexible and easier to manage
Cisco Catalyst Center: early results from intent-based networking
Using Cisco Catalyst Center for network as a platform
SDN and its role in automating and scaling in the data center
- Read all networking stories
Meet the IT bloggers
Read the latest news on what's happening in Cisco IT from those on the front lines. Read more

Zeroing in on network performance issues, with ThousandEyes
Network performance metrics for every hop from the branch to the cloud? They're at our fingertips, with ThousandEyes Enterprise Agent on Catalyst 9000 switches.

Journey Map – all paths lead to an intent-based network
Check out Cisco IT's interactive journey map to Intent-Based Networking. We share insights and lessons learned from our own ongoing network transformation journey.

Cisco IT is automating many steps in the device software upgrade process by leveraging the SWIM capability in Cisco Catalyst Center.
- Visit other IT blogs

Cisco retail store of the future
Cisco is updating an outdated retail space on its main campus with technologies that make the space easier to shop, easier to run, and capable of learning from customers.
- Cisco store and smart cameras (6:44)
Catalyst 9K in North Sydney
By deploying Catalyst 9000 on a parallel network, IT can learn about real-world challenges within the company and get a firsthand perspective of what Cisco customers experience.
- Catalyst 9K in North Sydney (7:57)

Typical Networking Architectures for Campus Networks and Case Practice
Huawei technologies co., ltd..
- Open Access
- First Online: 22 October 2022
20k Accesses
When readers study on campus, work in a company, or shop at the mall, they may notice that these places are all covered by networks. Through these networks, one can access internal school resources, use internal devices of the company such as printers, or access the Internet to browse news and information. These networks are classified as campus networks and are usually built by the companies or organizations themselves. Campus networks not only enhance the operational efficiency of enterprises, but also provide network access services to the outside world.
You have full access to this open access chapter, Download chapter PDF
This chapter will introduce the definition of campus network, explain the typical networking architecture of campus network, analyze the planning and design methods of small campus network, deployment and implementation methods, as well as the basic work required for operation, maintenance and optimization. At the end of this chapter, a network engineering project will be created based on enterprise requirements.
15.1 Basic Concepts of Campus Networks
15.1.1 what is a campus network.
A campus network is a local area network that connects people and things in a limited area, and usually has only one management body. If there are multiple management bodies, it will be considered as multiple campus networks.
A campus network can be large or small in size, ranging from smaller ones such as a small home office (SOHO) and wireless coverage in a coffee shop, to larger ones like networks for a campus, corporate campus, park and shopping center. The scale of the campus is limited, and the general size of large campuses, such as college campuses and industrial parks, is generally within a few square kilometers. Within this range, we can use LAN technology to build a network. A “campus” larger than this is usually regarded as a “metropolitan area” and needs to use WAN technology, and the corresponding network will be regarded as a MAN.
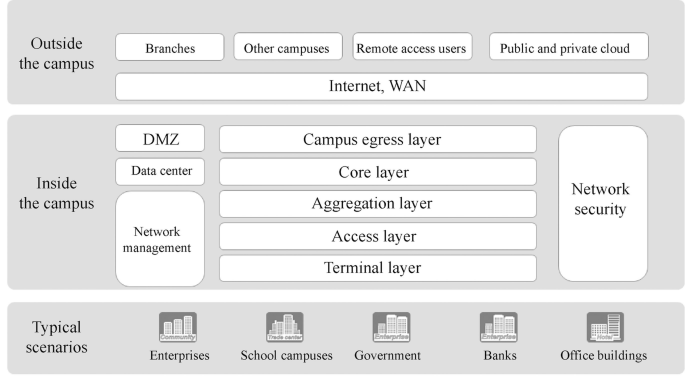
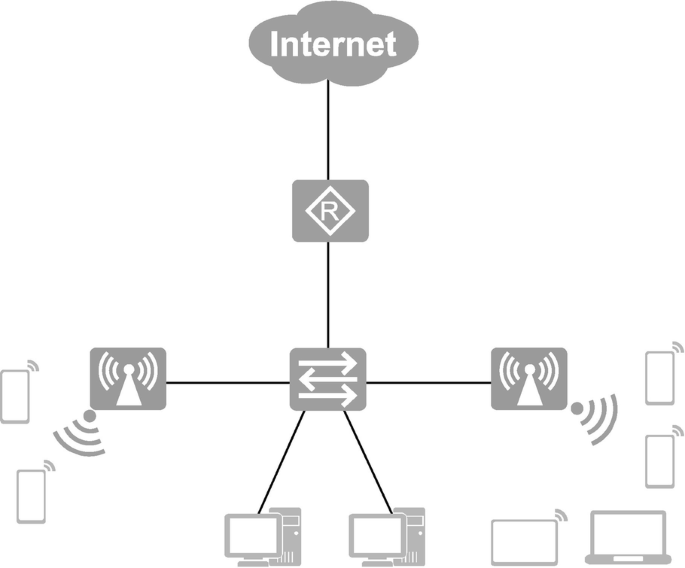
As shown in Fig. 15.1 , campus networks can be used in enterprises, school campuses, government, banks and office buildings. Inside the campus network is usually a hierarchical and regional design, which is the modular design we usually refer to. Hierarchical design by the location of devices in the network can divide the network devices into terminal layer (wireless devices such as computers and cell phones are in the terminal layer), access layer, aggregation layer and core layer. According to the functions achieved, network is divided into network management, network security, Demilitarized Zone (DMZ) and data center zone. The area connecting the outside of the campus is the campus egress layer, which connects other branches, other campuses, remote access users and private and public clouds via Internet and WAN (Wide Area Network).
Campus network
Typical LAN technologies used in the campus network include Ethernet technology (wired) following the IEEE 802.3 standard and Wi-Fi technology (wireless) following the IEEE 802.11 standard.
15.1.2 Typical Architecture of Campus Network
Campus networks generally follow the principles of hierarchical, regional and modular design. According to the number of end users or network elements (including routers, switches, wireless ACs, APs and other devices), campus networks can be divided into small campus networks, medium campus networks, and large campus networks. Figure 15.2 shows the typical architecture of a campus network.
The core layer is the backbone of the campus network and the core of data exchange in the campus。It connects various components of the campus network, such as the aggregation layer, data center, egress area and network management area.
The aggregation layer is in the middle level of the campus network, performing the function of data aggregation or exchange, and providing some key basic network functions, such as routing, QoS (Quality of Service) and security.
The access layer provides end users with campus network access services and is the border of the campus network.
The egress area is the border separating the internal campus network from the external network, and is used to realize internal users’ access to the public network as well as the external users’ access to the internal network. Generally, a large number of network security devices are deployed in this area to defend against attacks from external networks, such as IPS (Intrusion Prevention System), Anti-DDOS (traffic cleaning) devices and Firewall.
The data center area is the area where servers and application systems are deployed to provide data and application services for internal and external users.
Network management area is the area where network management system is deployed, including SDN controller, wireless controller, eLOG (log server), etc. It manages and monitors the whole campus network.
Small campus network architecture
Small campus networks are mostly used in scenarios where there are a small number of access users, generally supporting a few to dozens of users. The network is built to enable the access to internal resources. It only covers a single location, and is not hierarchical, with simple networking requirements. The architecture of small campus network is shown in Fig. 15.3 .
Medium campus network architecture
The number of end users of medium campus network is generally between 200 and 2000, and the number of network devices is generally between 25 and 100, which can support several hundreds to thousands of users to access. For medium networks, the concept of dividing areas by function is introduced, which is the modular design, but there are relatively few functional modules. Areas are generally flexibly divided according to business needs.
The medium campus network is used in the most scenarios, and its functional modules are shown in Fig. 15.4 . It generally adopts a Layer 3 network structure – core layer, aggregation layer, and access layer, and it is divided into two functional areas– the data center and egress layer. The data center is usually deployed with enterprise servers, such as Web sites of the intranet, office systems and database servers. The egress layer is connected to the Internet and the core layer, and usually deploys firewalls to control the traffic from the intranet to the Internet. In the meantime, it prevents attackers on the Internet from invading the intranet. In addition, the network address is also translated at the egress layer.
Large campus network architecture
A large campus network may be a network covering multiple buildings, or a network connecting multiple campuses within a city via WAN. It generally provides access services, such as allowing traveling users to access the company’s internal network through technologies such as VPN.
A large network has the following features: wide coverage, large number of users, complex network requirements, full functional modules and rich network hierarchy. The architecture of large campus network is shown in Fig. 15.5 . The functional modules of the headquarters campus are access layer, aggregation layer, core layer, egress layer, data center and network management area. At the egress layer, cloud data centers and branch campuses can be connected via Internet or WAN, and users on business trips and users working from home can access the network of the headquarters campus via Internet.
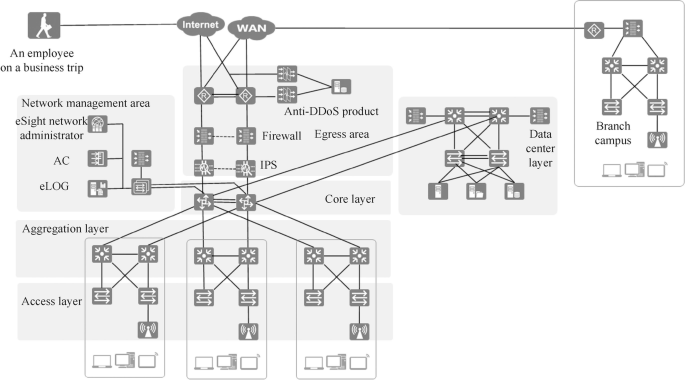
Typical campus network architecture
15.1.3 Protocols and Technologies Commonly Used in Campus Networks
Protocols or technologies that will be used in each layer and module of the campus network are shown in Fig. 15.6 .
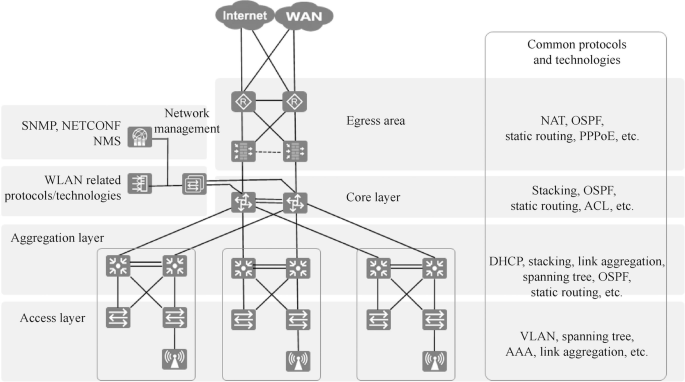
Protocols or technologies commonly used in campus networks
The technologies used in the core layer of the campus network are stacking, OSPF, static routing and ACL. The technologies used at the aggregation layer include DHCP, stacking, link aggregation, spanning tree, OSPF and static routing. The technologies used at the access layer are VLAN, spanning tree, AAA and link aggregation. The technologies used in the egress area are NAT, OSPF, static routing and PPPoE. And the technologies used in the network management area include SNMP.
To be specific, core layer switches, aggregation layer switches, egress area firewalls and routers all need to be configured with static routing or dynamic routing to enable network connections between the intranets and to access the Internet. Among them, the router in the egress area connected to the Internet is configured with NAT or NAPT to enable the intranet to access the Internet, and NAT Server can also be configured so that computers in the Internet can access the servers on the intranet. The link in the egress area connecting the ISP is usually a WAN link and may also use PPPoE or PPP protocol. The aggregation layer switches and access layer switches use Spanning Tree Protocol to prevent loops. Inter-VLAN routing is usually implemented on aggregation layer switches, and aggregation layer switches use DHCP to assign IP addresses to computers in the VLANs. The FIT APs of the campus network are configured on the AC through WLAN-related protocols. And devices in the network is managed and monitored on the network management server via SNMP protocol or NETCONF protocol.
15.2 Lifecycle of a Campus Network
Generally speaking, the life cycle of a campus network includes at least the whole process of planning and programming, deployment and implementation, operation and maintenance, and network optimization of the network system. The life cycle of a campus network is a cyclic iterative process, and each cyclic iteration is driven by changes in network application requirements. Each cycle of change is centered on four phases: planning and programming, deployment and implementation, operation and maintenance, and network optimization.
Planning and design.
Network planning and design is the starting point of a project. Perfect and detailed planning will lay a solid foundation for the specific subsequent work of the project. The work in this phase includes determining the physical topology of the network, the logical topology, technologies and protocols to be used, etc.
Deployment and implementation.
Project implementation is where engineers deliver the specific operation of the project. Systematic management and efficient processes are the fundamental elements to ensure the successful implementation of the project. The work in this phase includes equipment installation, stand-alone commissioning, interconnection testing, cutover and grid connection, etc.
Operation and maintenance.
To ensure the normal operation of network functions and thus support the successful provision of user services, daily maintenance and troubleshooting of the network are required. The work in this phase includes daily maintenance, software and configuration backup, centralized network management monitoring, software upgrade, etc.
Network optimization.
The user’s business is constantly evolving, so the user’s demand for network functions will change accordingly. When the existing network fails to meet the business needs, or when the network reveals certain hidden problems during the operation, network optimization is required to address the problems. The work in this phase includes improving the security of the network and enhancing the experience of network users.
15.3 Hands-On Practice of Campus Network Projects
15.3.1 network requirements.
A company (with about 200 employees) plans to create a new campus network due to business development needs, and the network requirements are as follows.
It can meet the current business needs of the company.
The network has a simple topology and is easy to maintain.
It provides wired access for employees to use in their offices and Wi-Fi service for visitors.
Simple network traffic management.
A certain level of security is ensured.
15.3.2 Planning and Design of Small Campus Networks
The planning and design of small and medium campus networks in this case need to take into consideration the following elements.
The design of networking plan, including equipment selection, physical topology and equipment naming.
Basic service design, including VLAN design and planning, IP address design and planning, IP address assignment method, and routing design.
WLAN design, including WLAN networking design, WLAN data forwarding mode design.
Network reliability design.
Layer 2 loop avoidance design.
Egress NAT design.
Security design, including traffic control, DHCP security and network management security.
Operation, maintenance management design, including the management using traditional equipment, and management based on the iMaster NCE platform.
The design of networking plan
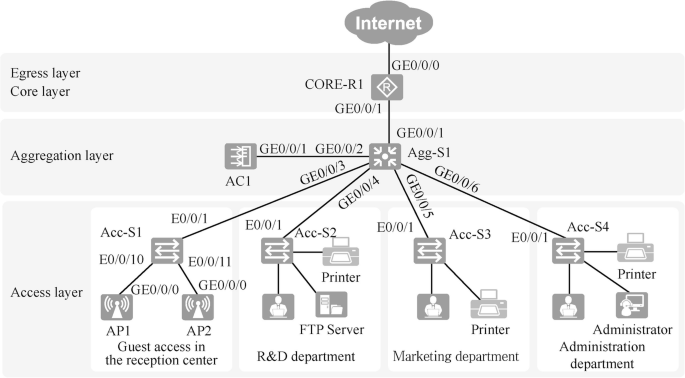
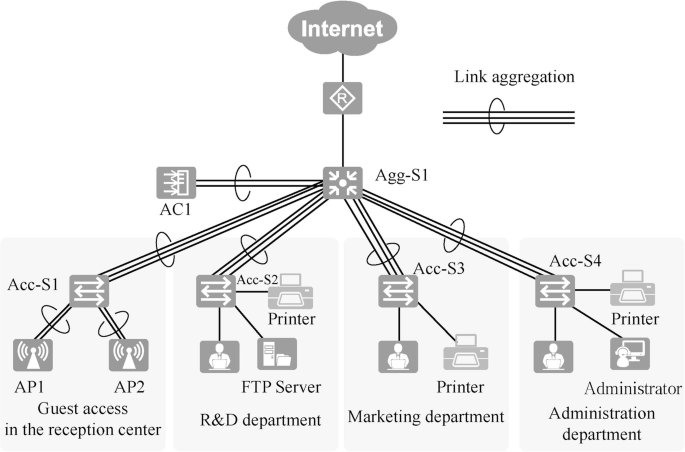
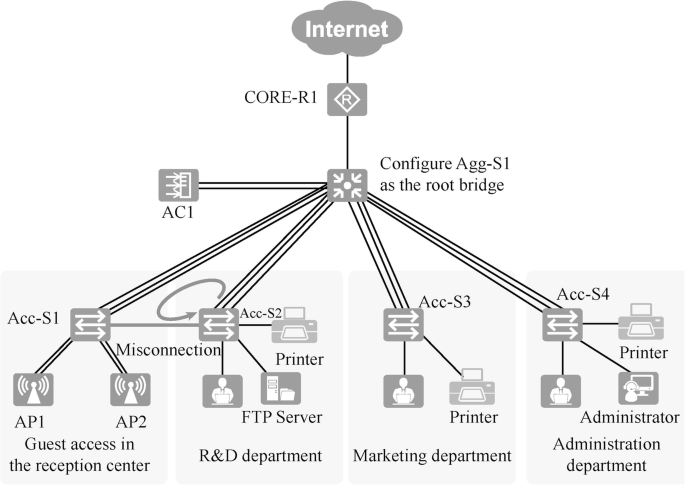
After taking into consideration the budget, business requirements and other factors, the physical layer topology in this case is designed as shown in Fig. 15.7 . The devices can be named according to a uniform method that is easy to remember and scalable. For example, the access layer switches are named Acc-S1, Acc-S2, Acc-S3, etc., and the aggregation layer switches are named Agg-S1, Agg-S2, etc. The selection of interfaces for interconnecting devices should meet the bandwidth requirements.
Note: Acc is the abbreviation of Access, which represents the access layer device; and Agg is the abbreviation of Aggregation, which represents the aggregation layer device.
The entire network adopts a Layer 3 architecture. The access layer switch is S3700, which provides 100-gigabit network access for employees’ PCs, printers and other terminals. The aggregation layer switch is an S5700, which serves as the gateway to the Layer 2 network. The core and egress layers are combined into one, and the router is AR2240, which functions as the egress of the whole campus network.
Basic service design
Design and planning of VLAN.
The design of VLANs is recommended as follows.
VLAN numbers are recommended to be assigned consecutively to ensure the reasonable use of VLAN resources.
VLAN division needs to distinguish between service VLAN, management VLAN and interconnection VLAN.
VLANs can be divided based on interfaces.
Service VLAN design can divide VLANs by geographical area, by logical area, by personnel structure and by service type.
Management VLANs are mostly used for remote management of network devices, and it is necessary to configure IP addresses, subnet masks and default routes for the devices to be managed. It is recommended that all switches belonging to the same Layer 2 network use the same management VLAN, with the managed address in the same network segment. Usually, Layer 2 switches use the VLANIF interface address as the managed address.
The VLAN planning for this case is as follows (see Table 15.1 ).
Management VLANs for Layer 2 devices are reserved.
Based on the personnel structure, the VLANs are divided into guest VLAN, R&D VLAN, marketing VLAN and administration VLAN.
Considering that Layer 3 switches need to be connected to routing through VLANIF, it is necessary to reserve interconnection VLANs.
The VLANs required to establish CAPWAP tunnel between AP and AC are reserved.
Design and planning of IP addresses.
The service IP address is the address allocated to servers, hosts, wireless devices, etc. The design and planning principles of the service IP address are as follows.
Gateway IP address is recommended to uniformly use the last or the first available address of this network segment, for example, for network segment 192.168.80.0/24, the address of the gateway is 192.168.80.254 or 192.168.80.1, so as to avoid conflict with the computer addresses of the network segment as far as possible.
The IP address range planning of each service VLAN should ensure that the IP address of each type of service terminal is continuous and aggregatable, which is convenient for routing aggregation.
It is recommended to use an IP address segment with a 24-bit mask.
Switches use VLANIF interfaces to configure the managed addresses, and it is recommended that all switches use the same network segment for their managed addresses.
It is recommended that network device interconnection IP addresses use IP addresses with 30-bit masks and core devices use IP addresses with smaller addresses.
When planning network segments and gateway addresses for each type of services, the number of access clients should be taken into account and sufficient IP addresses should be reserved. Table 15.2 lists the addresses, subnets and gateways of each network segment in this case.
IP address assignment method.
Dynamic IP address assignment or static IP address assignment can be adopted to assign IP addresses. In small and medium campus networks, the specific assignment principles of IP addresses are as follows.
IP addresses of WAN interfaces are assigned by the carriers, such as through static IP addressing and dynamic IP addressing (DHCP or PPPoE method). For IP addresses of WAN interfaces, communication with the carrier is required in advance in order to obtain them.
For servers and special terminal devices (such as punch-card machines, printers, IP video monitoring devices, etc.), it is recommended to use static IP address binding to assign them.
For user terminal devices (such as PCs in user’s offices, IP phones, etc.), their IP addresses are recommended to be dynamically assigned through DHCP by deploying a DHCP server on the gateway device in a unified manner.
The IP address assignment method in this case is shown in Table 15.3 . The WAN interface connected to the Internet can use PPPoE to obtain IP address. All terminals (office computers and devices that wirelessly access the network) can obtain IP addresses by DHCP. Servers and printers will be assigned fixed IP addresses. IP addresses of all network devices can be configured by a static method (except APs).
Route design.
The route design of small and medium campus network includes the internal route design and the campus egress route design.
The internal route design must meet communication requirements of devices and terminals on the campus network and enable communication with the external network. As the network of small and medium campus is relatively small and the network structure is comparatively simple, the internal route design is not complicated. By default, AP devices generate a default route after IP addresses are assigned by DHCP. Switches and gateway devices can meet the demand through static routes without deploying complex routing protocols.
The route design of the campus egress is mainly required to meet the demand of the internal users of the campus to access the Internet and WAN, and it is recommended to configure static default routes on the egress devices.
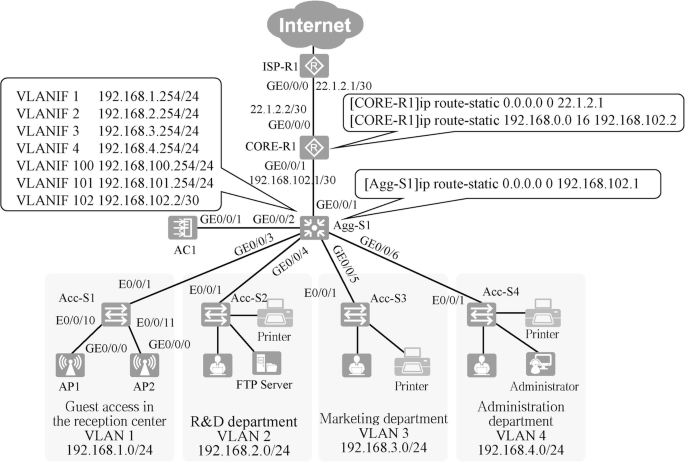
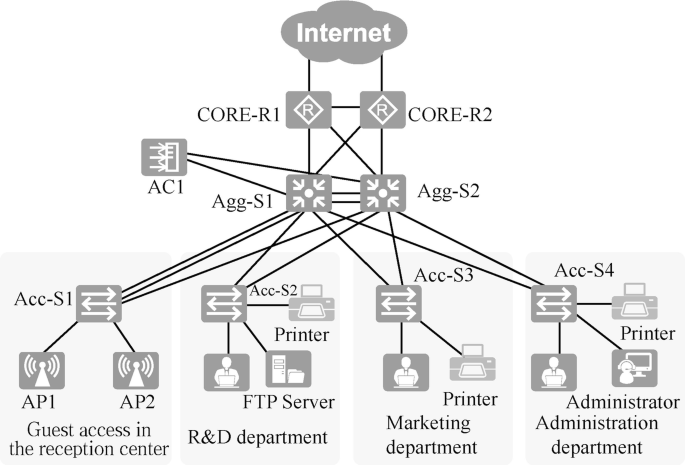
In this case, the routes on devices Agg-S1 and CORE-R1 are shown in Fig. 15.8 . Add a default route in device Agg-S1 to address 192.168.102.1 of interface GE0/0/1 of router CORE-R1. Add a default route in router CORE-R1 to IP address 22.1.2.1 of interface GE0/0/0 of router ISP-R1., and another static route to the intranet, which summarizes the intranet into a network segment 192.168.0.0/16, with the next hop pointing to IP address 192.168.102.2 of interface VLANIF 102 of device Agg-S1.
WLAN Design
WLAN networking design.
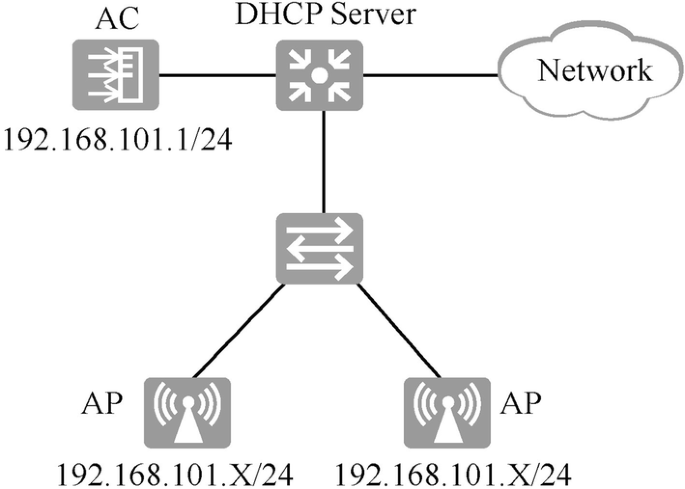
According to the IP addresses of AC and AP, and whether the data traffic passes through AC, the network can be divided into directly connected Layer 2 network, Layer 2 network in bypass mode, directly connected Layer 3 network, and Layer 3 network in bypass mode. As shown in Fig. 15.9 , this case adopts the Layer 2 networking in bypass mode.
WLAN data forwarding mode design.
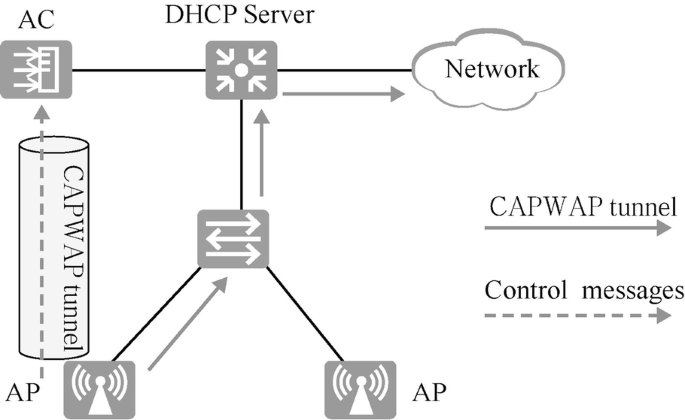
The data in WLAN includes control messages and data messages. Control messages are forwarded through CAPWAP tunnel, while data messages are forwarded by tunnel forwarding and direct forwarding. This case uses the direct forwarding, as shown in Fig. 15.10 .
Other designs.
In addition to planning the networking and data forwarding methods, the following designs are also necessary.
Network coverage design: the area covered by wireless network shall be designed and planned to ensure that the signal strength within the covered area can meet the requirements of users and solve the problem of co-channel interference between neighboring APs.
Network capacity design: the number of APs for the network shall be designed and deployed according to data such as the bandwidth requirements of wireless terminals, the number of terminals, concurrent volume and single AP performance to ensure that the wireless network performance can meet the Internet service needs of all terminals.
AP layout design: based on the network coverage design, the actual layout location of the AP, layout method and power supply alignment principle will be revised and confirmed according to the actual situation.
In addition, WLAN security design and roaming design are also vital, which are not listed in this chapter.
There are many items and contents to be configured when configuring WLAN. Before configuring WLAN, it is necessary to clarify the configuration options and contents. Table 15.4 shows the WLAN configuration items and configuration contents in this case. In the process of configuration, the configuration items should be configured with reference to the configuration content to avoid errors.
Network reliability design
The access layer and aggregation layer in this case both use a switch for networking. The reliability of switch networking is divided into port-level reliability and device-level reliability.
Port-level reliability. Using Ethernet link aggregation technology can enhance the reliability between the access switch and the aggregation switch, and also increase the link bandwidth. As shown in Fig. 15.11 , link aggregation is implemented between AC1 and Agg-S1, between AP1 and Acc-S1, and between the access layer switch and the aggregation layer switch.
Device-level reliability. This can be achieved by using dual aggregation layers and dual layers, as shown in Fig. 15.12 . You can also use iStack or CSS technology, which is not introduced in this case.
In this case, port-level reliability is chosen. Compared with device-level reliability, this scheme uses fewer devices and can save network cost.
Layer 2 loop avoidance design
According to the reliability design, this case chooses the port-level reliability design scheme. Redundant links are not introduced to the current network segment, and there is no loop, as shown in Fig. 15.13 . However, it is possible for office workers to connect two switches by mistake and form a loop. To prevent the loops caused by the maloperation of office workers, the switches can be configured to use spanning tree technology. The Rapid Spanning Tree Protocol (RSTP) is adopted, and in the meantime, it is recommended to manually configure Agg-S1 as the root bridge.
Egress NAT design
The intranet of the campus network usually uses private addresses, and network address translation (NAT) is needed for the intranet computers to access the Internet. The router connected to the Internet usually has a public address and is configured with NAT. NAT includes static NAT, dynamic NAT, NAPT, easy IP and NAT server, and the appropriate type of NAT can be selected according to the actual situation.
Static NAT is suitable for the scenario where there are a lot of static public IP addresses and the intranet computers need to use a fixed public address to access the Internet. In this scenario, computers on the Internet can also use the public address to directly access the corresponding private address.
An address pool is a concept for dynamic NAT, and the available addresses in the public address pool are chosen to enable the intranet computers to access the Internet. In this scenario, the intranet can initiate an access to the Internet, while the Internet is unable to initiate an access to the intranet through the public address. A public address can only translate the address for one computer on the intranet.
NAPT is suitable for scenarios where there are a limited number of IP addresses in the public address pool. If there are more computers on the intranet than the addresses in the public address pool, NAPT should be configured to save public network IP addresses and improve the utilization of public network IP addresses.
Easy IP is appropriate for scenarios where the address of the interface connected to the Internet is dynamically obtained. When using the public address of the interface as NAPT, there is no need to configure a public address pool.
NAT server is suitable for scenarios where computers on the intranet need to provide services to computers on the Internet. With NAT server configured, computers on the Internet can access specific services on the intranet, such as Web services on the intranet, through the public address of the router.
In this case, it is recommended to choose easy IP for egress NAT, and the NAT server does not need to be configured.
Security design
The security design in this case involves traffic control, DHCP security and network management security, which can be enabled by using routers and switches.
Traffic control.
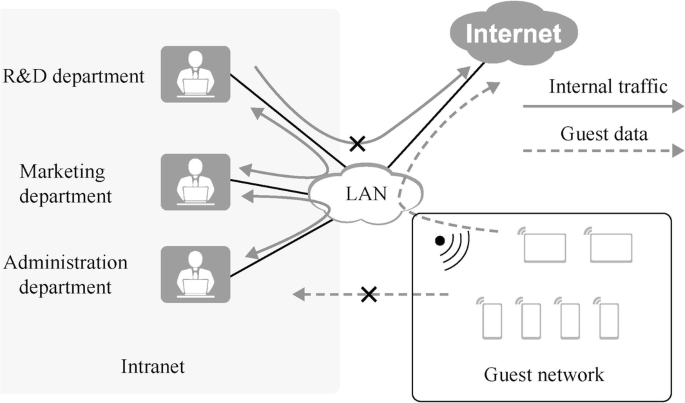
As shown in Fig. 15.14 , the computers in R&D department, marketing department and administration department are allowed to access each other, but not the Internet. Computers in the guest network can access the Internet, but not the internal campus network. We can use traffic-policy, traffic-filter and other technologies to control the traffic and allow the guest network to access the Internet by configuring NAPT. Configuring NAPT requires creating ACLs and defining the network segments that are allowed to access the Internet. In this case, only two rules need to be added to the ACL, one is to allow the guest traffic to pass and the other is to deny other traffic to pass. Then configure Easy IP at the router egress.
[CORE-R1]acl 2000 [CORE-R1-acl-basic-2000]rule 5 permit source 192.168.1.0 0.0.0.255 [CORE-R1-acl-basic-2000]rule 10 deny [CORE-R1-GigabitEthernet0/0/0]nat outbound 2000
DHCP security.
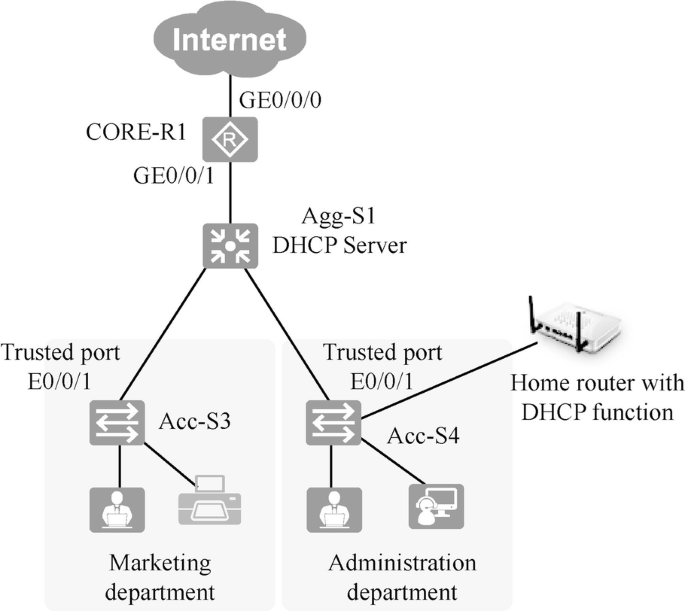
In campus networks, it is a common situation that employees connect to DHCP wireless router without permission, so that the intranet addresses become a mess, which results in address conflict and inability to access the Internet. At this time, DHCP Snooping can be adopted in the access layer switch to prevent this situation and ensure DHCP security.
As shown in Fig. 15.15 , to prevent the computers in the administration department from obtaining IP addresses from the home router, DHCP Snooping is enabled on the Acc-S4 switch and E0/0/1 is set as the Trusted port. so that DHCP requests sent by computers will only be sent to interface E0/0/1.
[Acc-S4]dhcp enable [Acc-S4]dhcp snooping enable [Acc-S4]vlan 4 [Acc-S4-vlan4]dhcp snooping enable [Acc-S4-vlan4]quit [Acc-S4]interface Ethernet 0/0/1 [Acc-S4-Ethernet0/0/1]dhcp snooping trusted
Network management security.
When using Telnet, Web or other methods for network management of the device, only fixed users (computers with fixed IP addresses) can be allowed to login for network management through ACL technology. For centralized network management [the administrator can get the working status of all the managed devices in time through the operation port of a management terminal program, and can configure all the managed devices through this port. Simple Network Management Protocol (SNMP) defines the standard for the management communication between the management terminal and the network devices]. SNMPv3 adds authentication and encryption processing, which can significantly improve the security of network management.
Operation, maintenance and management design
The operation, maintenance and management of small and medium campus network can be managed by traditional devices or on the iMaster NCE platform. Traditional device management is chosen in this case.
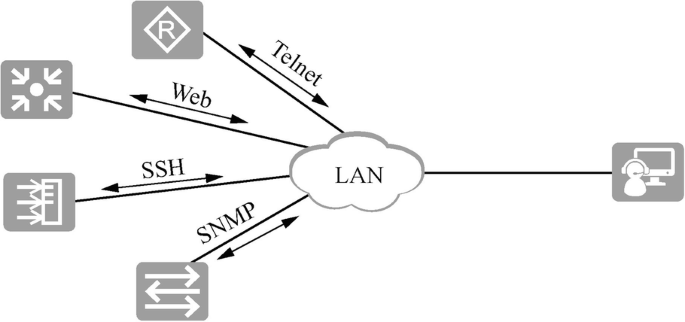
Management by traditional devices.
If the network administrator and the device IP are reachable, the device can be managed through Telnet, Web and SSH, as shown in Fig. 15.16 . When there are many network devices, SNMP protocol-based unified network management software can be deployed for network operation, maintenance and management.
Management based on iMaster NCE platform.
In addition to management by traditional devices based on SNMP, Huawei iMaster NCE platform can also be adopted for network operation, maintenance and management so as to achieve “autopilot” of the network. As shown in Fig. 15.17 , on iMaster NCE platform, network devices can be managed through OpenFlow, NETCONF and Telemetry protocols.
Network topology
Interface address and routing configuration
Layer 2 networking in bypass mode
Direct forwarding
Port-level reliability
Device-level reliability
Loop avoidance
Traffic control
DHCP security
Traditional device management
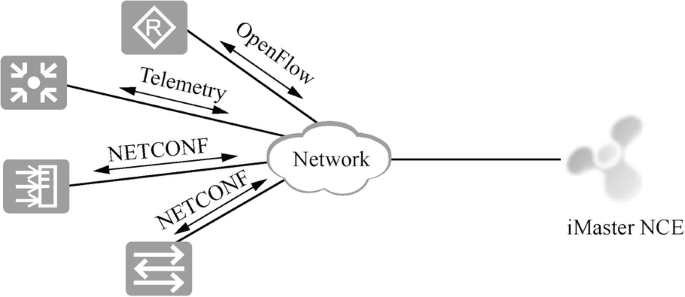
iMaster NCE platform management.
15.3.3 Deployment and Implementation of Small Campus Networks
In the deployment and implementation phase, a list of configuration contents is required before configuring the network devices, and then the devices are configured with reference to the list. After the configuration is completed, testing is performed to ensure that the configuration can achieve the designed functionality.
Network configuration
Configure the port.
After physical lines between the network devices are connected, you need to configure the link aggregation between the access layer switches and aggregation layer switches and add the port description. To avoid configuration errors, first, information including the link aggregation interface (Eth-Trunk) number, link aggregation mode, port members of the link aggregation port and link aggregation port description required for each switch shall be organized in the table. The Eth-Trunk ports that need to be created on the switch in this case and what needs to be configured are shown in Tables 15.5 and 15.6 .
Configure VLANs.
In this case, VLANs are created based on the personnel structure. Four service VLANs, two management VLANs and one interconnection VLAN need to be created for three departments and guests (see Table 15.1 ). After creating the port-based VLANs on the switch, you also need to configure the port type and the VLAN to which the access port belongs, and configure the PVID of the trunk port and the VLANs allowed to pass through.
In order to avoid errors in the configuration process, the information that needs to be configured can be listed in advance in tables. Tables 15.7 and 15.8 show the types of each port and the content that needs to be configured. As it can be seen from the table, we have configured the Eth-Trunk port type as Trunk, the same PVID is specified, and only the necessary VLANs are allowed to pass through the trunk.
Configure static addresses.
The addresses of the management ports of access layer switch and aggregation layer switch, and the ports of aggregation layer switch Agg-S1 and core layer router CORE-R1 are also statically configured. To avoid errors in the configuration, the address of each port needs to be planned in advance. The details of the IP address configuration of routers and switches in this case are shown in Table 15.9 . As it can be seen from the table, inter-VLAN routing is enabled by the aggregation layer switch Agg-S1, and the address configured for port VLANIF corresponds to the last address of the VLAN.
Configure DHCP.
Terminals and APs use DHCP to obtain addresses. In this case, Agg-S1, the aggregation layer switch, is configured as a DHCP server to assign addresses to computers in the VLANS of R&D department, marketing department, and administration department as well as for guests, and also to assign addresses to APs in the management VLAN of the WLAN. Therefore, four address pools need to be created on Agg-S1. Gateways and DNS have to be assigned to each address pool, and the lease duration needs to be specified based on the time the terminal stays after accessing the network. If a fixed address needs to be assigned to a specific device, the IP address and MAC address need to be bound. If there are addresses in the address pool that have already been taken, they will be excluded. In this case, the IP address taken by the AC needs to be excluded from the management VLAN of the WLAN.
The IP address pools created on Agg-S1, the gateway and DNS of each address pool, the excluded addresses and the bound addresses in this case also need to be planned and sorted in advance. The details can be found in Table 15.10 .
Configure routing.
This case uses static routing. In order to allow administrators to access the access layer switch and AC1 across network segments, it is necessary to configure default routes on the access layer switch and AC1. On the aggregation layer switch, you only need to add a default route to the core layer router CORE-R1, and on CORE-R1, you need to add a route to the intranet and then add a default route to the Internet. The configuration details can be found in Table 15.11 .
Network management configuration.
Telnet remote management is applied in this case, and the authentication mode is AAA. On the managed device, you need to create users, set passwords and configure to allow users for Telnet login. In addition, user privilege levels are set. The configuration details can be found in Table 15.12 .
Configure the network egress.
In this case, the port of the core layer router CORE-R1 connecting to the Internet uses PPPoE dial-up to obtain the public address. The public address obtained by each dial-up is not fixed, so easy IP should be selected for NAT. See Table 15.13 for configuration details.
Configure the WLAN.
You only need follow the WLAN design and planning content to configure.
Configure network security.
Network security in this case involves three aspects: traffic control, network management security and DHCP security. We can use different security measures in different devices. Traffic control can be enabled by creating basic ACLs and advanced ACLs on the core layer router CORE-R1. Network security management requires creating ACLs on each managed device to allow only specified IP addresses to remotely manage, and creating different users and setting strict privilege levels for different operators. DHCP security needs to be configured on the access layer switch, and the configured uplink port is the Trusted port. See Table 15.14 for the configuration details.
Network testing
After the network is configured, connectivity test, high reliability capability test and service performance test should be conducted.
The connectivity test includes basic link interconnection test, Layer 2 interconnection test, and Layer 3 interconnection test.
High reliability test includes loop avoidance function test and path switching test.
Service performance testing includes service traffic testing and access control testing.
15.3.4 Operation and Maintenance of Small Campus Networks
After the project goes online and runs, it enters the operation and maintenance phase of the network.
Network device operation and maintenance is a daily preventive work. It refers to the regular inspection and maintenance of the equipment in the normal operation of the equipment in order to timely detect and eliminate defects or hidden dangers to maintain the health of the equipment, so that the system can operate safely, stably and reliably for a long time.
Environmental requirements of the server room
Under normal circumstances, the temperature of the long-term working environment of the server room should be kept between 0 °C and 45 °C, and the temperature of the short-term working environment should be between −5 °C and 55 °C. If the temperature of the server room fails to meet the requirements in the long term, the maintenance personnel should consider overhauling or replacing the air-conditioning system of the server room, checking the cooling situation of air conditioners, the switch situation, etc. The air-conditioning refrigeration should function normally and the switch should be in good contact.
Under normal circumstances, the relative humidity (RH) of the long-term working environment of the server room should be kept between 10% RH and 95% RH, and the relative humidity of short-term working environment should be between 5% RH and 95% RH. If the relative humidity of the server room becomes excessive, the maintenance personnel should consider installing dehumidification equipment for the server room; if the server room is too dry, the maintenance personnel should consider installing humidification equipment for the server room.
Network equipment hardware maintenance requirements
The cleaning condition.
All equipment should be clean and tidy, with no obvious dust attached. Equipment shells, the inside of the equipment, and the inside of the rack have to be equipped with a dust net. Pay attention to the cleaning condition of the dust net of the cabinet, which should be timely cleaned or replaced, so as not to affect ventilation and heat dissipation of cabinet door and fan frame.
Heat dissipation condition.
When the equipment is working normally, it is required to keep the fan running (except during the cleaning of the fan). Turning off the fan without permission will cause the temperature of the equipment to rise and may damage the single board. It is not allowed to place sundris on the equipment shelves at the vents, and the fan’s dust net should be cleaned on a regular basis.
Cable laying.
Power cables and service cables are required to be laid separately. Power cables and service cables should be placed in a neat and orderly manner.
Cable labeling.
Pay attention to the cable labels inside the cabinet, which are required to be clear and accurate, and in line with the specifications.
Equipment appearance.
Observe whether the equipment is complete, and whether the free slot is protected by a dummy panel.
Network equipment alarms and data configuration maintenance requirements
Alarm information.
Under normal circumstances, there should be no alarm information. If there is an alarm, it needs to be records, and serious alarms need to be immediately analyzed and dealt with.
Log information.
Under normal circumstances, there should not be excessive duplicate information in the logs. If there is, it must be immediately analyzed and dealt with.
CPU occupancy status.
Under normal circumstances, the CPU occupancy should be less than 80%. If the CPU occupancy rate is too high for a long time, the device should be checked and the cause analyzed.
Memory occupancy.
Under normal circumstances, the occupancy rate of memory should be lower than 80%. If the occupancy rate is too high for a long time, the equipment should be checked and the cause determined.
Interface traffic.
Compare the current traffic with the interface bandwidth. If the utilization rate exceeds 80% of the port bandwidth, it needs to be recorded and confirmed. Check whether there are error statistics in the inbound and outbound directions of the interface, focusing on the growth of error statistics.
Interface and link status.
The status of interfaces and links in use is UP, and that of unused interfaces is SHUTDOWN.
Debug switch.
Check whether the switch of the current debugging information “debugging” is off. Under normal operating conditions, all switches of all debugging information are off.
Configuration file.
Check whether the current configuration information and the saved configuration information are consistent. The configuration being run needs to be the same as the configuration saved.
Remaining capacity of Flash.
All the files in Flash must be useful, otherwise the delete/unreserved command should be executed to delete them.
Administration level user control.
The system must set a password for the administration level user, and the password is required to be set in the cipher text format and longer than six digits.
Telnet login control.
Telnet users must be authenticated. The password must be in cipher text format and cannot be too simple.
Telnet and serial login.
Telnet and serial login are tested to ensure that users can login by both of the two methods.
Change the user password.
For system security, the user password of the device must be changed on a regular basis. Moreover, the password must be set in the cipher text format and longer than six digits. The password is recommended to be updated every quarter.
Interface configuration.
Check the status and the configuration of the interface. The interface whose status is DOWN (except SHUTDOWN) is not allowed to have configuration, and the interface whose status is UP must have configuration.
Interface description.
All activated interfaces are described using the specification. If there is no corresponding specification, it is recommended that the interface description specification be: Local device name_Local port number - >Peer device name_Peer port number_Port rate.
Interface mode.
Execute the display interface command to check the configuration of the interface. The local interface mode (including rate and duplex mode) must be consistent with the peer interface mode. The actual operating mode (Trunk or Access) of the local interface must be the same as that of the peer interface.
System time.
Execute the display clock command to query the system date and time. The time should be consistent with the actual local time (the time difference is no more than 5 min).
15.3.5 Network Optimization of Small Campus Networks
If there are changes in network requirements, a suitable optimization plan needs to be formulated with the actual situation taken into consideration. For example, in this case, the control and security requirements for guests accessing the Internet in the reception center have increased, and bandwidth restrictions are imposed on each guest accessing the Internet, so it is necessary to deploy firewall devices at the egress layer to set security policies and bandwidth restriction policies. Another example is that the number of guests in the reception center has increased, and the performance of the core layer device CORE-R1 is not satisfied, so it is necessary to upgrade the device.
Through network optimization, the overall security and reliability of the network can be improved to better support the development of enterprise services. Common optimization solutions include, but are not limited to, the following.
Device performance optimization, for example, upgrading hardware devices, replacing existing devices with higher performance devices, and updating the software versions of the devices.
Network infrastructure optimization, for example, network architecture optimization and routing protocol adjustment. Other examples of network architecture optimization include the shift from single-link to dual-link Internet access, and the adjustment of WLAN data forwarding method from direct forwarding to tunnel forwarding. Moreover, changing the static routes to dynamic routes on the intranet is a routing protocol adjustment.
Service quality optimization, for example, reserving higher bandwidth for specific guests to the Internet, or prioritizing traffic forwarding for voice and video services.
15.4 Exercises
What is the complete life cycle of a campus network?
What is the role of managed addresses?
Author information
Authors and affiliations, rights and permissions.
Open Access This chapter is licensed under the terms of the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License ( http://creativecommons.org/licenses/by-nc-nd/4.0/ ), which permits any noncommercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license and indicate if you modified the licensed material. You do not have permission under this license to share adapted material derived from this chapter or parts of it.
The images or other third party material in this chapter are included in the chapter's Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the chapter's Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder.
Reprints and permissions
Copyright information
© 2023 The Author(s)
About this chapter
Cite this chapter.
Huawei Technologies Co., Ltd.. (2023). Typical Networking Architectures for Campus Networks and Case Practice. In: Data Communications and Network Technologies. Springer, Singapore. https://doi.org/10.1007/978-981-19-3029-4_15
Download citation
DOI : https://doi.org/10.1007/978-981-19-3029-4_15
Published : 22 October 2022
Publisher Name : Springer, Singapore
Print ISBN : 978-981-19-3028-7
Online ISBN : 978-981-19-3029-4
eBook Packages : Computer Science Computer Science (R0)
Share this chapter
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research

- Free Case Studies
- Business Essays
Write My Case Study
Buy Case Study
Case Study Help
- Case Study For Sale
- Case Study Service
- Hire Writer
Case Study on Data Communication and Networking
Case study on data communication and networking:.
Data communication and networking is the connection of a great number of computers for the purpose of information exchange. Today information is the most important resource, because with its help one can receive education, learn something new, make a business, change the life of the country, etc. In order to maintain the process of information exchange numerous appliances and techniques have been invented. First of all it is the local networking or the worldwide Internet, which helps users produce, store, analysis and process information and exchange it form the different parts of the world. Information technology has become one of the most profitable and important spheres, because the IT analysts manage the process of communication and networking and improve this process constantly.
The whole information which can be found in the Internet is stored on the special databases and if one wants to get access to the certain type of data, he can surf the web and find it on a server. It is obvious that the technology of networking and data communication is constantly improving and the experts work hard to make the access to the information quicker and easier. Nearly every day new software and networking technologies appear and provide users with the high-quality and rapid means of information processing and communication. Today the web has become the core means of communication, because it is easier and cheaper to write an email or an instant message to any part of the world than to ring someone up or write a common paper letter. So the intention to save time is the main reason why so much attention is paid to the development of the IT.
We Will Write a Custom Case Study Specifically For You For Only $13.90/page!
Data communication and networking is quite an interesting but challenging topic, because one should be able to analyze the problem professionally combining his technical knowledge with the humanity disciplines. A good data communication and networking case study is supposed to explain the topic profoundly and solve the puzzle of the case successfully. One should evaluate the cause and effect of the problem and suggest the best methods to solve it well and demonstrate his analytical and critical thinking skills.In order to prepare a successful case study on the topic one should take advantage of the Internet and read a free example case study on data communication and networking written by an expert. It is fairly smart to look through a good free sample case study on data communication and networking analyzed by the real professional, because only with this kind of help a student will be able to learn something about the problem and fulfill the high-quality analysis of the problem and format the text according to the general requirements.
Related posts:
- Data Networking Devices
- Case Study on Verbal Communication
- Case Study on Social Networking Sites
- Case Study on Social networking in our lives
- Case Study on Data Mining
- Data Motors Case Study
- Case Study on Data Analysis
Quick Links
Privacy Policy
Terms and Conditions
Testimonials
Our Services
Case Study Writing Service
Case Studies For Sale
Our Company
Welcome to the world of case studies that can bring you high grades! Here, at ACaseStudy.com, we deliver professionally written papers, and the best grades for you from your professors are guaranteed!
[email protected] 804-506-0782 350 5th Ave, New York, NY 10118, USA
Acasestudy.com © 2007-2019 All rights reserved.

Hi! I'm Anna
Would you like to get a custom case study? How about receiving a customized one?
Haven't Found The Case Study You Want?
For Only $13.90/page

Bridge Builders: African Experiences With Information and Communication Technology (1996)
Chapter: case studies on electronic networking, case studies on electronic networking.
Perhaps no information technology generates as much interest as networking. Bringing electronic networking and Internet capability to a country opens avenues of communications that create hundreds of other opportunities. Computer-based communications provides a means to bridge time and distance to facilitate inter-personal communication. People who have the need or desire to communicate about a particular subject can do so without being either physically present in the same location (as in a conventional meeting), or even available at the same time (as in a telephone conference call or a video teleconference).
Electronic communication is in everyday use in many organizations in Africa; however, getting it into place in a new environment poses many challenges. Complex economic, social, political, and legal factors affect the use of the technology and present barriers to its successful implementation. The telecommunications systems in many African countries are suffering from deteriorating equipment and inadequate investment. Telecommunications costs are high in relation to other costs, and participation in some computer-based communication activities can require scarce foreign exchange.
Still progress is being made. In the last year or two several African countries have gained full Internet connectivity. Others are creating local networks and adding users one by one until they build a user base large enough to sustain an Internet connection. In the meantime, the users and the system operators are learning valuable skills.
The case studies in this section describe the difficult processes that five system operators have gone through in order to build the networking capability in
their countries. These five projects are interconnected since the project managers were introduced to the technology by many of the same people and through many of the same megaprojects. Their individual stories are unique, however, because each author overcame different technological, managerial, and infrastructural constraints.
As one author wrote, networking tends to sell itself. The more users you have online, the more users you have waiting to be connected. So, almost one user at a time, these authors are helping to build Africa's information highway.
Electronic Networking for the Research Community in Ethopia
by Lishan Adam

Lishan Adam has a B.Sc. in Electrical Engineering and a M.Sc. in Computer Information Systems. He is working towards his Ph.D at the University of Sheffield, United Kingdom. He has worked in the information field for the last six years, focusing mainly on technology for accessing information, which includes electronic communication networks. Currently, he is the coordinator for the Capacity Building for Electronic Communications in Africa (CABECA) project. His research interests include electronic communications for grassroots institutions, networking technologies, and techniques for building qualitative information systems and networks.
Background and Context of the Project
This case study describes the challenges faced in setting up a research communication network in Ethiopia. It covers the activities I undertook and the constraints I faced while expanding electronic connectivity to a research community. It also discusses the lessons I learned in the process.
Ethiopia is located in the horn of Africa and shares borders with Sudan, Kenya, Somalia, Eritrea, and Djibouti. Addis Ababa, the capital city, is often called ''a city for Africa" because it hosts two major organizations: the United Nations Economic Commission for Africa (UNECA) and the Organization of African Unity (OAU). UNECA is the African regional arm of the United Nations Economic and Social Council. UNECA has established and sponsors a number of African institutions to promote all aspects of socioeconomic development of the region.
The Pan African Development Information System (PADIS), one such regional institution under UNECA, was created to build both information and networking capability in African countries. PADIS was instrumental in setting up a national electronic network in Ethiopia and in connecting members of the research community to each other locally and with colleagues worldwide.
There are only a few advanced research institutions and two major universities in Ethiopia. Addis Ababa University, the country's largest university, administers most of the colleges. The Agriculture University of Alemaya, in Harar Province 500 kilometers east of Addis Ababa, is the next largest research center. Health research is undertaken by the medical faculty of Addis Ababa University and at two other research colleges in Gondor and Jimma. The country has several teacher training schools and research centers.
The level of scientific and technological information (STI) and infrastructure in these research centers varies. Some colleges lack the most essential resources, such as paper and ink. Others use computers and connect to the local electronic networking host. The need for STI and communication is great, especially by colleges outside of Addis Ababa.
The Current STI Environment in Ethiopia
Ethiopia is the second poorest country in Africa, having been devastated by long-lasting war, drought, and mismanagement. The national STI environment is generally weak, reflecting the poor economic situation in the country. The transition 1 economy is too weak to support the population, which is growing at an annual rate of 3.1 percent, with the fertility rate mounting to 7.5 percent. The STI environment has suffered from the poor economic performance during the last twenty years.
All STI centers, including university libraries, have been unable to expand and keep up with demands. There were hardly any books coming to the country during the previous socialist government. According to the head of the Addis Ababa University libraries "most collections are those of the 1960s." Those were the "golden years" of library collection development—when resources were made available to support new acquisitions.
Most colleges are not equipped with computers and other information technology tools. The more remote the college from the capital city, the less it is exposed to computing technology. (See Box 1 .) Under-use of existing equipment due to lack of training and low quality of maintenance is also common. Lack of knowledge about different hardware contributes to the under-use of computer accessories.
Computer equipment is generally expensive. A non-error correcting, 2400 bps modem that costs $ 40.00 in the United States costs the equivalent of $ 200 in Ethiopia. The local price of accessories is between 400 percent to 1500 percent more than the original cost. A bureaucracy for clearing equipment through customs
exasperates most possibilities of getting it through mail order or from friends residing in foreign countries.
One additional problem, unique to the country, is related to the use of Ethiopian script. Ethiopia is one of the oldest countries using its own script. The shortage of good, easy-to-use software that is adaptable to local script is a major problem. Generic native-language software interfaces that allow easier storage and retrieval of textual information in local languages and scripts are not well developed. Modern tools, such as Windows [Byte, 1994], that have features for processing data in all languages simultaneously are not readily available in Ethiopia.
A lack of good training schools and colleges in computing technology has created a chronic shortage of trained personnel in advanced networking, although Addis Ababa University now offers courses in computer applications and system design. Due to the lack of incentives and of an enabling environment, one seldom finds dedicated computer "gurus." The culture for competition and independent effort to solve complex computing problems is not well developed.
Several small computer companies were set up during the transition period but they have not become a source of objective advice in computing technology. Most companies focused on generating quick income through computer applications training. Qualitative and advanced services in networking and local area network (LAN) management are not available at these companies. Due to the lack of a good professional background, techniques such as application development, system integration, and networking are not practiced.
The telecommunication sector is another underdeveloped area in the country. National telecommunication service in Ethiopia is owned by the government. Analog telephone 2 , digital leased lines, and radio links to rural areas are major services of the national operator. There is no modern communication technology. Rural telecommunications is still operator assisted. Packet switching and ISDN (Integrated Services Digital Network) are under consideration.
A three to five year queue is usually the case for individual households that wish to install a telephone. Business and international organizations may get telephone lines within one to three months when lines are available. Some institutions have to wait for months to get direct lines.
The above national STI environment dictated the type of network technologies we chose to use, as well as the pace at which we could install and apply them. Policy, regulatory, management, and cultural problems were by far the most challenging—even when compared to the technical bottlenecks faced in setting up electronic mail links to the research community. All the same, electronic networking in Ethiopia was started during one of the most rigid governments in Africa. 3
Project Description
Networking activity in the country began under a project funded by International Development Research Centre (IDRC) entitled "Computer Networking in Africa." The aim of the project was to assess the viability of networking between
African institutions. The specific objectives of the project in Ethiopia were to:
- improve the exchange of scientific information within Ethiopia by establishing a working, efficient, and reliable electronic network that brings contact with other networks locally, regionally, and internationally;
- develop human resources in electronic networking through training, transfer of skills, and university teaching;
- develop corps of skilled users in the country through training, trouble-shooting, and ongoing technical support;
- establish a national scientific network that supports all levels of technologies (Fidonet, UUCP, and TCP/IP, which stands for transmission control protocol/Internet protocol and connotes a full, interactive Internet connection) for various categories of colleges and users under different situations; and
- set up an Internet link through development of the user base that justifies the cost of a TCP/IP connection.
Project Experience and Implementation
The first activity of the project in Ethiopia was initiated in September 1991, when the Ethiopian Science and Technology Commission, which coordinates the national STI networks, participated in the first African workshop on low cost networking. The workshop provided training on low cost communications technology and charted connectivity strategies among research institutions in Africa and those in Ethiopia. Subsequently other academic institutions (universities, colleges and faculties) began to link to the main national host. 4
To date the main national host serves over 1,000 users drawn from NGOs, research institutions, government, business, and others. Researchers evolved from network-"hesitant" to power users. For example, a connection was made to the chemistry department of Addis Ababa University at the beginning of 1993. At that time, a professor said openly "this is a waste of time and of computer resources." In 1995, the department became the top user of the national hub and a center for network support to Addis Ababa University users.
Network usage and development activity at the university intensified in October 1993, immediately after a workshop was organized for participants drawn from various departments of the Addis Ababa University. The workshop created conditions for setting up a steering committee to promote networking within the university. The steering committee evolved from a few actors to a full fledged university-wide networking group. It established a networking committee to promote networking in the country and develop connectivity to the Internet.
The research community became the second largest user of the national network (See Table 1 .) It constitutes 14 percent of PADIS installed sites and 26.2 percent of total local users.
TABLE 1 Composition of PADISnet Users (April 5 1995)
In addition to developing a sound user base that would eventually justify the upgrade to a full Internet connection, one of the major activities of the project at the beginning involved experimenting with a mix of technologies to select the hardware that was most appropriate for working with poor telephone lines. We conducted the experiments using a mix of technologies to arrive at appropriate solutions. We evaluated the following four connection techniques during the process:
- long distance dial-in to UNIX hosts in North America;
- UUCP 6 link through a leased line by running a gateway software;
- packet-radio connection to health institutions; and
- Fidonet 7 based mail connection to Internet using GnFido gateway in London.
Our first attempt to link researchers in the country used long distance dial-in to UNIX hosts in Canada and the United States. Access to large academic networks such as BITNET was the main interest at the time. A direct dial-in to a UNIX server at Carleton University in Canada was made every day to collect and send messages to the research community. Rudimentary terminal access programs such as Procomm were used to link to the Carleton server. This turned out to be one of the most frustrating means of making connections as the lines broke at almost every trial. Successful connections were so rare that the connection was discontinued after a few months. The cost of telecommunications mounted every month. The cost was made up of:
- long distance telephone charges;
- low speed connections (successful connections were at 300 bps); and
- additional procedures required as a result of long distance dialing and line breaks (i.e., transferring files several times after line breaks; login procedures to packet switching network in the U.S.).
Paying enormous bills every month for long distance connections forced PADISnet to switch to a more cost effective site. While exploring sites, a link using the United Nations Alternate Voice and Data (AVD) leased line to the Institute of Global Communications (IGC) became cheaper and more attractive. The IGC link enabled us to convert local Fidonet messages into UUCP format before leaving the PADIS host via a gateway software. This created conditions for developing local expertise in running gateway software and in experimenting with UUCP packets. However, since the line was devoted to UN communications (voice and fax), it became slow and inadequate for data communications. PADISnet was given only a 15 minute window to send and receive UUCP messages. This was an inconvenience and resulted in the final suspension of the connection after ten months of operation.
Another technology used for STI connectivity in Ethiopia was a HealthNet link. PADIS helped to establish this link and to secure its ground station license. The HealthNet ground station, which links to a low earth-orbiting (LEO) satellite operated by SatelLife, was licensed in April 1994—after 18 months of negotiation with the national telecommunications operator. The ground station was installed at a teaching hospital, one of the largest in the country. This connection was not used as effectively as hoped due to the following difficulties:
- Unreliable power supply. Fluctuation in electric current at the site of the ground station led the system to crash from time to time.
- Very complex software. A home-written Fidonet software made configuration difficult. Lack of documentation and troubleshooting tools heightened the problem.
- Synchronization of systems. The HealthNet system is composed of a receiver, transmitter, modem, antenna, microcomputer, satellite, and software. Failure in one or more of these systems resulted in a complete crash of the node from time to time.
- Lack of an overall plan for user support. The national HealthNet node did not come up with a plan for introducing the technology, connectivity, or regular user support.
- Low bandwidth. The uplink and downlink speed of the modem and satellite pass time was limited. With growing user demand for bandwidth-intensive documents, such as reports with graphics or images, the system became inadequate.
- Marketing. The failure to develop an expansion plan and lack of marketing of the services limited its use in the country.
A direct Fidonet connection to the Association for Progressive Communications (see description on page 189) in London using public telephone lines remained the most attractive of all the above techniques. This connection is currently our main link to the global networks and provides all store-and-forward Internet services. Due to a lack of knowledge about the potential of store-and-forward technology, researchers mainly use the email and bulletin board services of the linkage. Some students and a few researchers are exploring other potential services such as:
- searching the PADIS database using email query;
- accessing the Hornet bulletin board system (BBS);
- batch Internet services such as ftp, gopher, and archie through mail; and
- conferences and Fidonet echo mail.
The Hornet BBS is perhaps the most unique application of low cost technology in Ethiopia for information exchange. Hornet offers an introduction to the potentials of electronic information systems and provides a reservoir of background information and discussion on the Horn of Africa. [Parker, 1994] The bulletin board offers:
- Fidonet conferences (or echoes) to as wide an audience as possible, with no on-site software set-up necessary;
- a mechanism to exchange information and skills among users of the PADIS system; and
- a central store of information, files, help, useful Internet addresses, and so on.
Simplicity and minimum hardware requirements on the users' side make the BBS more popular. Prompted by this offering, a number of research institutions, including the Addis Ababa University and the Ethiopian Science and Technology Commission, are setting up a scientific bulletin board system. Local bulletin board systems connected to information reservoirs, such as databases and tools on CD-ROM, are found to be the most useful tools for STI networking under the local infrastructure.
During the last two years, increasing user demands for real time connections, the need for joining the Global Information Infrastructure (GII), and congestion of the host telephone line forced the national node to look for a better technology. At the time of this writing, the node is exploring full Internet connectivity and/or other intermediate solutions. The effort to get a full Internet (TCP/IP) connectivity is hampered by three major problems:
- high cost of leased lines;
- institutional and national constraints; and
- financial resources to cover implementation and running costs.
Leased Line Costs
The national telecom operator provides leased lines at a very high tariff. Table 2 shows approximate monthly charges for international leased lines to the United States and South Africa. 8
TABLE 2 Cost of Leased Line from Ethiopia to Selected Countries
National Infrastructure and Political Constraints
The low level of infrastructure as well as policy-specific problems continue to hamper the progress of setting up full connectivity to global networks in Ethiopia. Changing the attitude of the government and of the PT&T (the national telecommunication provider) remains one of the most challenging tasks. Some of the national infrastructure and political constraints we face include:
- competition and unwillingness of the national telecom operator to endorse operation of national cooperative or private nodes;
- low participation of government institutions in overall network implementation;
- lack of knowledge of electronic communication by government officials that results in delays to approve research network (see Box 2 );
- education structure and low value accorded to information management, transmission, exchange and use; and
- lack of a critical mass of trained UNIX experts or "gurus."
Despite the above problems, the project continued to work towards improving network access to researchers. The bottom-up approach for building a network (starting from users, soliciting institutional support, and then approaching the government) helped us bypass an often difficult bureaucratic structure in the country.
Eventually, the increase in the availability of local "hand holders" and troubleshooters encouraged expansion of the network. The local troubleshooters created
institutional champions and then the institutional champions helped users get around configuration problems. In time, we motivated others to get connected.
Reliability of the network has also contributed towards the diffusion of networking technology in Ethiopia. Network reliability is a function of good systems operators (sysops) running the node, advanced computing technology tools, and reliable telecommunication infrastructure. PADIS' effort to make the system reliable by hiring additional system operators 9 and acquiring the latest technologies favored the situation.
Other factors that contribute to further network expansion include:
- the availability of dedicated local champions and
- the availability of simple network learning tools, such as the Hornet Bulletin Board System.
PADIS management played a major role in leading and supporting networking in the country. The availability of information 10 at PADIS provided incentive for several users to seek connection to the network. PADIS made its resources available via the network to satisfy users who wanted to go beyond electronic mail.
Individual willingness—especially from top government officials—to embrace existing technology and their demand for better services are perhaps the major motivating factors for expansion to a full TCP/IP. Influenced by their former contacts (usually at universities or NGOs in developed countries) researchers who are not connected demand quicker and better connectivity. Contact requirements and realization of benefits of networking compelled several users to demand email services even under difficult circumstances. What are the major benefits that prompted researchers to look for electronic networking?
Results, Impact, and Benefits of the Project
Reduced communication costs.
The most outstanding benefit of electronic networking to the research community in Ethiopia was that of bringing a new tool for reducing high communications costs. Ethiopia is a country with one of the lowest pay scales in the world. The following vital figures shows the situation.
Electronic networking brought a considerable amount of communications cost savings compared to fax, telex, telephone, and courier service. Though email costs are complex and difficult to quantify, we do know that networking offers a far cheaper option to all existing transmission media. (See Table 3 .) The following tables and computations show a considerable comparative advantage of email over a fax—without involving costs of other elements such as hardware, or training.
Using compression tools, such as PKZIP, an average document can be compressed 2.5 times. The amount of bytes per minute after compression would be:
Compression factor 2.5
Total bytes per minute 2.5 x 103342 = 258357
High speed modems, with good error correction, synchronized to the receiving modem, can also increase the amount of bytes transmitted per minute. Using 28.8 Kbps modem the amount of bytes per minute would be: bytes per minute of 28.8 kbps modem (1.5 x 285357 = 387535)
Using the above figures, we can calculate the cost per kilobyte of different means of communication.
TABLE 3 Raw data used in computation
In addition to the reduction of communications costs, email made the following contributions to the research community in Ethiopia [Adam, 1994]:
- It facilitated the organization of international seminars, joint authorship, and the execution of joint projects that otherwise would have been expensive and time consuming. According to the Director of the Institute of Ethiopian Studies, Dr. Bahru Zewde, ''Global conferences in Ethiopia and those on Ethiopia in 1994 were cost effective and successful because of email connections."
- It inspired the introduction of standard computing operating systems such as UNIX. Recently the School of Information Science for Africa (SISA) purchased a UNIX server as a networking backbone. The Mathematics Department of Addis Ababa University received a UNIX computer in connection with its networking effort from Ethiopians residing in North America. Deans and department chairs were forced to plan to "wire" their offices and create local area networks (LANs) to cope with an increasing demand from researchers to have independent accounts on work stations.
- It facilitated a switch from the hierarchical model of organizational procedures to the informal interaction among researchers in the country and those worldwide. User feedback indicates that delays in signing regular correspondence were eliminated upon arrival of email. (See Table 4 .)
Email also brought about the reunification of the research communities in Ethiopia with those elsewhere. It improved family and informal ties between Ethiopians residing overseas and those at home. 11
Improved Training Options
Electronic networking facilitated the availability of more national and institutional trainers. It created the expansion of knowledge on the use and benefits of
TABLE 4 Cost Comparison Between Fax Message and Electronic Mail Between Addis Ababa and London
networking and TCP/IP connectivity. The methodology used in training contributed to improved skills in the country. The national host uses the following techniques to train users.
Introduction
Users are introduced to key features of networking. This covers basics of local networking, what it involves, cost, and types of services.
Site configuration and training
Site training is meant to connect researchers to the network. It involves configuring the hardware, setting up telephone lines, providing hands-on training on system usage, and training in basics of troubleshooting.
Ongoing assistance
The host provides continuous online assistance to improve users skills in dealing with different utilities and to work on improved and cost efficient techniques.
This is used both as marketing tool for the national node and for advanced training. Experience indicated that initial introductory workshops overload users with new concepts. Successful workshops could only be held after usage of the networks. Advanced workshops were found to be useful in promoting connectivity.
Improved Skills
Another considerable impact of the network was an increase and improvement of the skills at the main national node. We developed skills in managing networks, dealing with administrative problems, developing techniques to respond to users' problems, managing system malfunctions, developing tools and guidelines, and gathering data. The experience we gained was immense.
Improved Access from Rural Areas
The spread of the network to the rural area is one of the most significant achievements of the project. Despite technical problems, such as unreliable connections and more focus on the capital city, a number of users were able to link to the PADISnet from outside of Addis Ababa. NGOs with field offices outside of the capital found networking a convenient tool for sending logistical information and data on field situations.
Doctors with no telephone connections were able to use networking. Medical doctors from Medicins Sans Frontiers , headquartered in Belgium, who were working 800 kilometers from Addis Ababa were able to send messages and data to their correspondents all over the world. Lacking telephones at their field site, they send messages via small airplane to Addis Ababa for uploading to their host to resend to PADIS. All international messages received are sent back by the same plane the following day. Other mobile field researchers from the same location were able to link their modems to the nearest city where phones are available.
A number of colleges outside of Addis Ababa are discovering the value of networking. They face double isolation—from both the developed world and the country's capital where most of the activities and decisions take place. Everything in the country is hierarchical and centralized. Decisions at higher levels (at the capital) take a long time to reach institutions in remote areas. Networking can reduce the isolation and make communication more efficient.
Connectivity to the rural areas facilitated the coordination of resources and the diffusion of technology. Connectivity at the Mekelle College (710 kilometers from Addis) recently stimulated the establishment of a LAN for connecting individual professors to the global network. A project run by the Ethiopian Science and Technology Commission to link over thirty-six colleges outside of the capital stimulated further international cooperation between the colleges and other universities worldwide. The Commission intends to "wire" all colleges and high schools in the country while working on a full TCP/IP connection at the capital.
Analysis of Lessons Learned
The resources required for achieving access to knowledge and wider national coverage are a fraction of the benefits gained by building networks. Coordinating activities at a national level assists in realizing cost effectiveness and efficiency. Networks can subsidize themselves. Lack of an infrastructure should not be seen as a major bottleneck to networking.
There are two major goals of electronic networking of the research community:
- wider coverage of users by reaching many scientists, researchers, students etc.; and
- improving access to knowledge by bringing global information resources closer to the scientific community.
Attaining these two goals needed institutional and infrastructure readiness from the outset. When these two goals were first proposed to managers and policy
makers their initial reaction was that "there are no resources" and "we can not do it under our telecommunications situation"!
Training is the main element in infrastructure development. Do not start training on DOS based networking at universities, start with UNIX, which I believe to be the multi-user system of choice for networking universities.
Wider national coverage requires local infrastructure development. Local infrastructure means not only the physical set-up of machines and software, but also building a sense of awareness and increasing the participation of users. Training should cover a wide range of groups at different levels and should introduce all standard technologies such as UNIX to the academic community from the very beginning. Starting training in the DOS environment limits universities' capacity to move quickly on to sophisticated techniques. Using DOS for networking universities instead of UNIX is like using typewriters instead of word processing. Good documentation saves time.
Build as many local area networks as possible. A LAN is a building block for Internet connectivity.
Capacity building in universities requires setting up of a university-wide network for inter-connecting many LANs, serving individual departments, libraries, and administrative offices, and offering the connections to the Internet through gateways. LANs are building blocks for good research networks.
Good network management practices should begin when the number of users is very small. Good network administration can prevent user and donor frustration.
The professional management and administration of a network should begin as soon as you have two users. A well-run network needs a good billing structure, well developed methods for gathering data on the type and nature of users, and mechanisms to backup log files, document problems, and track progress. Put these systems in place before the number of users grows to an unmanageable size.
Networks should be interactive on both an inbound and outbound basis.
Interactive sysops are the best assets of good networks. Inbound interaction with local users and outbound links to other networkers worldwide assist in sharing knowledge, resources, and time. Documenting tips and passing them on to users helps networks to expand.
Using software with simpler user interface is important.
One of the major components in infrastructure building is the provision of simple tools to users. Users should get uncomplicated tools. Using software with good user interfaces reduces frustration and improves users' interests in networks. The community of Macintosh users should not be neglected.
Do not focus only on global information sources. Assist in building local capacity in STI exchange.
Improved knowledge access can be achieved by creating a collaborative atmosphere within a country and by connecting to global networks. National STI sources should be strengthened to enable local exchange of information and collaboration. Networking should be built with maximum participation of local STI providers and users.
Do not promote the concept of subsidy. Promote the concept of "pay a small amount to keep your network healthy."
Networks should sustain themselves. Income-generating should start at the beginning. Users should be told to pay for services. Subsidizing researchers is important; researchers should, however, know the costs and participate in paying for services from the beginning. The payment could come from university budgets or projects.
Conclusion and Recommendations
Scientific and technological information in Africa needs to be strengthened. African input to global information resources emerges from the local STI institutions. Databases and low cost networks will ultimately serve African information needs. This is especially true for local loops where telecommunications and other infrastructure continue to be problematic. The international link itself is also inadequate. Except in South Africa, the other eleven African countries with Internet connectivity have a maximum speed of (usually) 19.2 Kbps. Reaching the global community and providing African STI to global users need efforts in strengthening the local capabilities both in networking and in information generation, management and dissemination, while upgrading the bandwidth for international connectivity.
Quality, reliability, and sustainability of African STI and networks is becoming another critical focus. Surveys and experience indicate that databases on STI lack good quality and are mostly unreliable. Database and information systems development in the region need to build quality tools and strategies for sustainability of African STI databases. The quality and sustainability of low cost electronic networks serving STI in Africa should also be improved.
Electronic communication will become a major tool for distributing global information to Africa. This does not mean African researchers need and can afford full TCP/IP connectivity. The key questions become: Is the African STI environment ready for full Internet connectivity? Will communication be two-way (from Africa to developed world and vice versa)? What will be the overall implications of Internet for a few in the capital cities versus those who are isolated due to a poor infrastructure and who need to break the isolation?
The answers to these questions remain a challenge to STI providers in Africa. African STI institutions need Internet connectivity. Internet connectivity means full participation of local providers and STI institutions in information generation and usage on the global networks. The current trend in most African countries focuses on Internet "proximity": bringing Internet closer to the users with no expansion plans for wider connectivity using low bandwidth links. Encouraging STI institutions to participate in information exchange will become the next challenge after bringing an Internet link to a country.
The situation in Ethiopia, which is often similar to that in other countries in Africa, indicates that careful analysis of the national STI environment should be made to design the most appropriate solution to improve overall research capacity in a country.
Efforts should begin by building the capacity of national science and technology institutions, such as research institutions, colleges, and small STI service providers. They should be encouraged and trained to manage information and use global information sources. Interim innovative services, such as connections to major databases or Internet services via local Bulletin Board Systems, should be
available. Users should be made fully aware of the services available to them even through existing low-cost, store-and-forward technologies.
One of the major tasks facing African STI networks is a lack of knowledge of what is happening in the same region, the same country, or even the same institution. We should develop directories, dissemination tools, and guides on STI networking efforts. We should disseminate via our networks STI meta-information (information on scientific and technology information). Without a solid regional STI base, connectivity alone cannot serve its purpose.
Bibliography
Adam, Lishan. (1994) Sustainable Academic Networking in Africa: System Operator's Perspective, paper published by American Association for Advancement of Science, Accra, Ghana.
Beyond Windows: Globalization of Windows. Byte June 1994, pp. 177–183.
International Association of University (1991) University Based Critical Mass System for Information Technology .
National Research Council (1991) Status of Scientific and Technological Information Systems and Services in Selected African Countries . National Academy Press, Washington, D.C.
Parker, Ben. (1994) The Hornet: The Horn of Africa's Electronic Information Exchange. Addis Ababa, Ethiopia
Networking in West Africa
by Moussa Fall

Moussa Fall is network manager for ENDA-Dakar node in Dakar, Senegal. He also works for the CABECA project and through that project has installed electronic mail nodes in Morocco, Chad, and Mali. He has plans for working in Mauritania, the Gambia, Guinea, Guinea-Bissau, Niger, Togo, and Benin. He was an administrative assistant at ENDA before getting into the networking field in 1991. He asks that his case study be dedicated to "Pape, gone so early, and to Touti and the whole tribe for their help and support."
"Networking means connecting people to people and people to information; it does not mean connecting computers to computers."
Wendy D. White—Growing the Internet in Africa,
Internet Society News, 1994, Vol. 3, No. 2, p. 28 .
I work for an organization called Environment and Development Action in the Third World (ENDA). It was founded in 1972 in order to:
- work with grassroots groups on the basis of their needs and objectives;
- contribute to the search for alternative development possibilities at all levels as well as to the various kinds of training programs that will make this development possible; and
- contribute to intellectuals' and trained personnel's involvement in the setting up and implementation of development programs in the service of the largest number of people possible.
ENDA has also had a leading role in various global networks dedicated to habitat, energy, street youth, pesticides, and other issues that have an environmental
component. ENDA works in all parts of the Third World but the headquarters, where I work, is in Dakar, Senegal, in West Africa. Senegal is a francophone country.
Since 1975, my role at ENDA, among other administrative tasks, has consisted of organizing seminars, conferences, and training sessions. These outreach tasks have helped to put me in contact with many people and I believe that I started networking from there.
I first met Doug Rigby 1 in 1991, at an Interdoc meeting in Epe (Netherlands), at which there was an introduction to electronic networking. He spent considerable time talking to me about Fidonet technology and the NGOnet project. (See Box 1 .) Back in Dakar, I pushed my boss to get an email account with a European private email provider. We accessed this account through the Senegalese PTT X.25 and we extensively used it for email and for the fax service.
In June 1992, the NGOnet project organized a one week workshop in Dakar to introduce Fidonet to the non-governmental organization (NGO) community. Doug Rigby was the organizer and, of course, I was among the participants. To encourage NGO networking, the project donated one PC 386 for the node and four modems. ENDA was chosen to host the node because of its commitment to immediately acquire a dedicated phone line and to allow me to give part of my time to the networking project.
Here, I have to confess that I had no DOS skills—ENDA only used Macs. But, because I was really interested in this new technology, I bought books on DOS and computing in general and started learning. When you are very motivated you can ''move mountains"…
For three months, the four NGOs that had received training and modems started communicating just among themselves. There was no international traffic! Then, in August 1992, the network received another donation from the NGOnet project—a high speed modem (Telebit Trailblazer 2500)—which made us ready to connect to the rest of the world.
Fidonet—A Grassroots Network
My introduction to Fidonet was so important that I should take time here to describe this form of networking in more detail. Fidonet is a grassroots electronic communications community that has been hard at work for over a decade devising ever cheaper and increasingly sophisticated tools to serve its needs through dial-up, store-and-forward, and modem-based connections. Fidonet technology has proven to be a powerful do-it-yourself tool for establishing initial footholds into the world of electronic communications. It offers users an affordable option even if they lack institutional affiliations, financial resources, or are located in a country where the nearest electronic communications link requires an expensive dial-up call over international phone lines.
Because Fidonet technology emerged in an environment where individuals operated each system independently and covered their own costs for phone calls and equipment, it had to be very flexible, decentralized, and designed to operate inexpensively with standard modems and microcomputers connected over ordinary phone lines. The "handshaking" and file transfer protocols built into all Fidonet-compatible software incorporate compression, error correction, and error recovery capabilities that squeeze as much data as possible into the shortest transmission time that the hardware will allow. Instead of using packet-switching, these independent systems establish gateways with larger, international electronic mail systems using high speed modems. At regular intervals, the independent systems dial into the larger systems to swap incoming and outgoing messages. This approach keeps down the cost of international calls without requiring sophisticated computer equipment.
Fidonet messages are sent along a hierarchy. At the top are five very broad geographic zones. Africa is Zone number 5. The zones are divided into regions, then into hosts, then into hubs, and then into nodes. Just like all the levels above them in the chain, nodes offer local email, pass new messages to and from the hub, and collect messages to and from the point —the lowest level of the Fidonet hierarchy. Point operators have systems that are configured with all the software necessary to call (or poll) the node and upload and download messages and files whenever it is convenient. The computer can do all the work automatically, making the calls
into the central system at a time when the lines may have less traffic or the costs may be lower.
Fidonet is a communications technology that many consider to be less advanced and, therefore, less useful than other technologies. It does not offer all of the sophistication that other, more costly systems do. However, as you have electronic mail capabilities, you can access important Internet tools like file transfer protocol (FTP), Gophermail, World Wide Web (WWW), Veronica, Wide-Area Information Servers (WAIS), and listservs—even if you do not get the results immediately as in a direct Internet connection. (See Box 2 .) Fidonet technology has limited expansion capabilities, insofar as it will always remain a store-and-forward, modem-based network. It lacks the capability for online information retrieval, data-base searches, remote-login, and remote-execution that other systems offer. However, while the expansion of more advanced computer networking technologies is often constrained by prohibitively high costs and inadequate telecommunications infrastructure, Fidonet technology is not.
The Association for Progressive Communications (APC), a global network dedicated to NGOs, was involved in the NGOnet project. 2 The APC was our natural partner. Through the APC London-based member, greenest, we connect through their Fidonet gateway (GnFido) to the rest of the world. GnFido serves as a gateway for small Fidonet hosts not only from Africa, but also from Asia and Latin America.
Through this system we have been able to use email, download conferences, and use the GreenNet fax service, which costs very little compared to the national PTT charges. The computer conferences received were on various topics: environment, development, health, AIDS, and so on. We also followed the United Nations Environment Programme's preparatory conferences and the NGO discussions regarding these conferences. ENDA now runs a private conference for its own use, linking its various offices around the world.
How Users are Trained
Users are trained either on an individual or group basis. After only one hour, the trainees are able to send messages and check their mailboxes. Usually training is done gradually. It is better to have three sessions of one hour each than just one session of three hours. During the second session, users are shown how to encode files to be sent and how to decode the received ones. The last session teaches them how to subscribe to conferences, how to contribute to a conference, and how to quit a conference.
Because the point software we use is user-friendly, after the training sessions, users need very little help. This they can request by sending a message to the postmaster who will respond to them as simply as possible.
For organizations using desktop computers, training is organized on site. For individuals or organizations using laptops, we ask them to come to the ENDA offices where things will be easier in case there is a problem.
Development of the Network and Perspectives
Accessing our network is relatively cheap 3 . Since the host is a non-profit, non-governmental organization, it does not intend to make a profit from providing networking services.
Our active users are our best advertisers! They help us "sell" the benefits of networking. Presently the ENDA-DAK node has over 110 users—coming from national and international organizations, individuals, government agencies, universities, and even the private sector. Our users come not only from Senegal, but also from other neighboring countries, including the Gambia, Mali, and Burkina Faso. The demand is increasing locally and also in all the neighboring countries.
Connecting Problems
During the period of April-May-June 1995, we experienced problems in our connections with GnFido in London. The Senegalese phone system was not working properly and users complained that their mail had not been delivered in time. We tried several modems and, paradoxically, the modem with the worst reputation behaved better than all those of a supposed higher quality. Now the situation is better and we are presently using a Zyxel modem.
Regional Networking
In 1994, I was a consultant to the United Nations Environment Programme, Global Environment Facility Project, which consisted of linking national teams doing research on greenhouse gases in Senegal, the Gambia, Morocco, Uganda, Tanzania, Nigeria, and Kenya. My part of the work consisted of developing teaching tools for national teams in Senegal, Gambia, and Morocco. I also did system installation, provided training, and helped link these teams to the conference set up for them. They were thus able to exchange data on their research, exchange views on methodology and software used, and share experiences. It should be noted that this conference was bilingual and I did most of the translation into French.
Since 1994, I have also been involved in the PADIS/IDRC CABECA project (see Box 3 ), which tries to give access to countries where there is no connectivity at all or where the existing infrastructure is too expensive for the NGO community to afford. An agreement between the ENDA Executive Secretary and Nancy Hafkin, who is the head of PADIS and the CABECA project, allowed me to work full time in electronic networking.
This agreement was easier to reach than might be expected. I should point out here that first our two institutions shared a common goal: to give electronic access to communities at the grassroots level. This facilitated the collaboration. I should also note that Nancy Hafkin's devotion to African networking and her confidence in this continent and its human resources made this institutional collaboration possible.
Through the CABECA project, I installed nodes in Rabat, in Chad, and in Mali. Another CABECA goal is to train node operators who will themselves become trainers.
In the CABECA project, we are trying to implement a regional network that is badly needed in francophone West Africa. Among these countries the telephone exchange is relatively good and the costs are relatively low. The idea is to have a regional hub—ENDA-DAK—which will be the focal point for the region, through which all regional mail shall be routed. With this infrastructure, there is no need for mail addressed to the neighboring countries to be routed through European gateways. Putting our resources together will make regional networking more efficient and will reduce our costs for international traffic. We believe that once this
infrastructure is set up, the region will be a zone for intensive information exchange. Organizations in the region have a great deal of information to share, the countries have the same language, the same currency, participate in the same economic organizations, and often are in the same ecological zone. Common interests and experiences should encourage the growth of networking in West Africa.
Some international organizations understand this very well and are discussing with us how to connect their projects or field offices to this low cost infrastructure. We are presently discussing with HealthNet the best way to for Senegal and other countries in the region to collaborate with this project.
Methodology for Sensitizing
In each country visited under the CABECA project, we organized a half-day workshop to sensitize NGOs and individuals to electronic networking. Some workshops,
such as the one in Chad, brought together as many as 35 people. After a preliminary introduction to the technology, using a phone simulator I always carry with me, we split participants into three groups, each one sitting around a computer. That way, each group can prepare one or two messages addressed to the other two groups and then, through modems and the phone simulator, exchange mail. They can see how fast the message can go and also the other possibilities of the system.
After this hands-on training, all groups get together for a final discussion on how this technology can serve the national community, the advantages compared to technologies such as fax or even conventional mail. We always focus first on how this technology can serve information sharing and exchange within the country before opening up to regional and international networks.
Here we must not forget the context in which we work in many African countries: there are poor phone lines and electrical shortages and outages. In some of these countries, you can get a dial-tone only after working hours. In some others, it is even worse, as not only do you have to wait a long time for a dial tone but, once you get it, you are not sure your international call will succeed. In one of these countries you can dial directly only to France!
Difficulties in Sensitizing
There are people who are allergic to new technologies. In one of the countries I visited for sensitizing purposes, the Government computing department is now attached to a national service. During our meetings, the head of that service had been completely against the introduction of this new technology, despite the fact that minister and all his colleagues agreed that their country should be part of the process. They all wanted to join the growing networks and reap benefits from them. Yet, the head of the service was able to block progress. Every month, his office sends data concerning the country to their subscribers who pay for the information. The documents are sent by regular mail. After many demonstrations and taking into consideration the volume of information sent monthly to North America and Europe, that person still retains his original position—which makes his colleagues quite unhappy.
Some of our users told us that they were able to get rid of the international line they used to send faxes after they discovered our fax service. Now their fax machine is mainly receiving faxes from their correspondents who do not have email and this has dramatically reduced their communications costs.
NGOs have been changing their way of communicating—especially with their northern partners. They are not only sending faxes but they send and receive email
messages and files. Some of them have been subscribing to listservs while the others, because of language problems, wait for the opportunity to have access to conferences in French.
NGOs have also benefited from the technology by being better able to participate in the preparations for such events as the United Nations environment conference. Through the NGO forum, even small and isolated organizations can be heard. ENDA itself, during the UN Environment Conference, issued a daily newspaper in French giving accounts and comments on what was happening. The newspaper was uploaded to Dakar and issued in both places on the same day. The newspaper was broadly diffused among NGOs in Africa via networking technology. (For another example of the benefits of email, see Box 4 .)
- Sacrifices are necessary to begin a network. You must be prepared to work long hours, spend your own money, visit users who have problems that have nothing to do with the electronic communications system, and fix hardware and software problems.
- If you give people your home phone number, then you will be disturbed for anything.
- You also need to be patient with people. You may find people with laptops who will take minutes to write a single word.
- For strategic purposes, you will sometimes have to give free accounts.
- Fidonet is a simple technology to master for NGOs which do not have the resources and the time to invest in too sophisticated technologies. Presently this is an appropriate technology for some African countries taking into account the situation described above.
Fidonet has been criticized for its limitations, but for people who are interested in email only and fax services, this is no doubt often the best choice. In spite of all what is said, IT WORKS…
Conclusions and Recommendations
Here is probably the best recollection I have from networking. Two years ago, I was surprised to find a message in my mail box saying:"I have been searching the Internet for an electronic address in Africa and found yours for Senegal. My name is…, I am living in … of the USA and I am 12 years old." For a while this young boy and myself have corresponded.
This would surprise any African—as we have not yet reached this level of computer use in Africa. Taxes continue to make computers unaffordable for individual use. And because of this we have a very low level of computer literacy.
One should note also that almost all NGOs use computers only for word processing, which really shows lack of computer skills.
When you try to convince NGOs or individuals who have access to computers to join the network, they are afraid of investing a lot of time learning something new. Those who do not have access to computers do not understand the necessity to invest money in a new technology of which they are afraid.
At this level, those who are connected are only interested in email and sending faxes. This is understandable as communication costs are very expensive in our countries.
Acknowledgements
I am deeply grateful to Jacques Bugnicourt, ENDA's Executive Secretary for his generosity and his open mind. He understood very quickly how crucial this technology was for his own organization and for the NGO community. And without his personal commitment and his encouragement, I would not have been able to work in this field.
To Abou Thiam, from ENDA, who first mentioned email to me.
Thanks to Doug Rigby for the role he played in electronic communications in Africa. He is the one who introduced the technology to me and to many African system operators.
Thanks also to wonderful friends and colleagues who played and continue playing a crucial role in African networking: Bob Barad, Karen Banks, Mike Jensen, Cesare Dieni, Youba Sokona and Ann Heidenreich.
Thank you also to the very good friends in the APC networks.
Background Summary SatelLife and HealthNet
SatelLife is an international not-for-profit organization whose mission is to improve communications and the exchange of information in the fields of public health, medicine, and the environment. It is an initiative of the International Physicians for the Prevention of Nuclear War, recipient of the 1985 Nobel Peace Prize. Not wanting to see space become a battleground, Dr. Bernard Lown, IPPNW co-founder and co-president, suggested the creation of a satellite-based global health communications system as a means of demonstrating that space can unite rather than further divide humankind.
SatelLife works in developing countries where libraries, hospitals and other organizations often lack adequate funds or foreign currency to subscribe to medical journals or to maintain ongoing subscriptions. Where communications facilities are intermittent, of poor quality, or expensive, the use of direct "real-time" voice or fax connections can be inefficient and frustrating. Health workers can become isolated from one another because of the high cost of telephone calls, fax services, and travel. Even with today's improved networks, communication in remote and rural areas is still difficult or impossible, and always extremely expensive. SatelLife has thus put much of its efforts into providing and improving access to "store-and-forward" message systems.
HealthNet, administered by SatelLife, is an information service that connects health care workers around the world. Using the most affordable and appropriate technology, HealthNet offers electronic mail and conferences as well as access to several electronic journals and publications. It also provides access to databases
and experts. SatelLife initiated the Library Partnership Program to facilitate access to medical literature for libraries in the developing world. Finally, for its Internet users, HealthNet offers pointers to useful health mailing lists, Worldwide Web homepages, Gopher and FTP sites on the Internet. HealthNet is currently operational in the following African countries: Botswana, Burkina Faso, Cameroon, Eritrea, Ethiopia, Gambia, Ghana, Kenya, Malawi, Mali, Mozambique, South Africa, Sudan, Tanzania, Uganda, and Zimbabwe.
SatelLife began by linking medical education centers in Africa with medical libraries and other centers in the United States, Canada, and Europe via a low-earth orbiting (LEO) satellite. The satellite was expected to be an essential part of the solution to the communications problems in developing countries but, since its launch, modern telephone switch equipment has been installed in many cities in Africa, providing good international connections. Because of rapidly evolving technologies, dialed telephone circuits and error-correcting modems are often a more economical and efficient solution for international transfer of electronic data in developing countries than the LEO satellite.
Fidonet-based networks were in widespread use in Africa in the late 1980s and SatelLife joined the many NGOs supporting Fidonet use there. Fidonet provides an economical alternative to Internet email systems. The evolution of HealthNet has produced a large network of Fidonet nodes. The network is still growing rapidly, although much of its growth is in the ''points" connected to network nodes rather than nodes themselves. SatelLife is committed to supporting this low-cost access system along with advanced Internet services so that services can be brought as close as possible to the end-user.
Since 1993 SatelLife has operated the Internet domain "healthnet.org" to support access by its member networks. While the cost barriers to providing international permanent leased lines are still prohibitive for most public health and medical education programs in the developing world, there are now several cases in which full Internet access is a realistic alternative to store-and-forward networks. SatelLife is helping its member networks take advantage of these circumstances as they arise.
The HealthNet satellite system offers Internet message services to any remote area where the local telecommunication infrastructure is poor or inefficient. The ground equipment needed to contact the satellite consists of an IBM-PC compatible computer, a Terminal Node Controller (TNC), a satellite radio, and antennas. At this stage, SatelLife is field testing a new radio design that merges the satellite radio and the TNC in one single box that can be portable.
Advances in satellite technology, opportunities in radio technology, and the growth of Internet connectivity to Africa, all mean that SatelLife will become increasingly diverse and complex. The only practical approach to handling this complexity
is to base the system on a powerful software environment called UNIX. In the past two years, Linux, a public domain software for UNIX on personal computers, has become a stable and respected (and very low cost) alternative to commercial UNIX system software. SatelLife is working to bring together many different networking technologies (including full Internet, satellite packet radio, and Fidonet) into an automated system based on Linux. Its own engineering task will be to provide software to simplify the control and monitoring of this package so that the amount of training required is kept to a minimum.
This new network node technology will offer many new options in network services and will make HealthNet more useful and attractive to users of standard Internet mail systems. Using whatever technologies are available SatelLife and its HealthNet service network will continue to address the twin problems of an acute shortage of current health information and of the severe isolation of African health care workers from their colleagues.
MUKLA: Evolution of a Homegrown Network in Uganda
by Charles Musisi

Charles Musisi is Network Manager of MUKLA (Makerere University in Kampala) and pioneer of electronic networking in Uganda. He has an electrical engineering background. He has shared his networking expertise with colleagues in Kenya, Tanzania, Nigeria, and Ghana.
This paper tells the story of the establishment of the MUKLA Electronic Network in Uganda. There is much in the establishment and growth of an electronic network that can be learned from our experiences. MUKLA is an example of a sustainable network bred from a homegrown desire to network. I say this because:
- Our primary emphasis is on self-sustainability;
- We are now in our fourth year of operation, with an increasing base of users, expanding facilities, and a financially viable operation;
- Starting from a university and grassroots NGO base, we now have established strong working relationships with various levels of government and other sections of the community;
- We are internationally connected to the Internet, the Association for Progressive Communications networks, United Nations organizations, major commercial networks, and facilities around the world; and
- All of this was accomplished with very little donor funding and no government grants whatsoever to commence operations. A small team of dedicated individuals in a unique government institution is running a sound business-based electronic mail service.
The need to communicate across distances on vital issues is far from new. An ever-increasing range of technologies has been applied to this need, from rudimentary tools before the age of transport to the constantly emerging suite of sophisticated services offered by the information age.
The ESANET Project
The MUKLA node began with the Eastern and Southern Africa Networking (ESANET) Project. Inspired by the communication needs mentioned above, the IDRC-funded ESANET research project was aimed at investigating various microcomputer-based methodologies for communications. The countries of the five participating institutions are all members of the Preferential Trade Agreement (PTA) region. The participating institutions themselves were the Institutes of Computer Science at the University of Nairobi and Makerere University, and the Computing Centers at the University of Dar es Salaam, the University of Zambia, and the University of Zimbabwe. The long-term goals of the ESANET project are given in Box 1 below; the specific objectives of ESANET were to:
- experiment with alternative techniques for data communications between the five nodes in five countries;
- evaluate the technical, economic, sociological, and management aspects of the communication network experiments;
- disseminate information to the research community within the region about the development and the results of the project with a view to increasing the awareness of possibilities, stimulating new and wider applications, and inviting feedback on related topics; and
- make recommendations to the research community (users and telecommunications authorities in the region) on cost-effective data communication modalities, and appropriate network models and policies for specific environments and applications.
The introduction of electronic networking to the wider community in Uganda began in May 1991 as a natural spin-off from the ESANET project. MUKLA was mandated to provide email services to non-governmental organizations (NGOs) within the NGOnet-Africa project, which is described more fully in Fall's case study on page 142. We also sought collaboration with the HealthNet project whose aim was to facilitate communication among health professionals within the African region and with their peers elsewhere. (See information on page 153.) While the mode of communication chosen by HealthNet was a store-and-forward, low-earth orbiting satellite (LEO) with tracking ground stations, the regional interconnection of the ESANET and NGOnet nodes was to be across regular, dial-up telephones lines using Fidonet technology.
Activities of ESANET
A start-up meeting for ESANET in November 1990 brought together representatives from all the participating institutions, as well as those from IDRC, SatelLife, and the Nirv Centre/Web of Canada. The start-up workshop focused on identifying suitable methods of communication and on drawing up preliminary lists of hardware and software requirements. We decided that the project would support a series of workshops in the different participating countries.
At a design workshop held in May 1991, in Harare, Zimbabwe we formally adopted Fidonet technology as the technology of implementation. Our review of the status of licensing of the HealthNet ground station revealed only Zambia at the time had obtained a license. Other highlights of that meeting included confirmation of lists of requirements by different nodes and the topology of regional mail traffic exchange. The nodes in Uganda and Tanzania were to route their regional traffic and international traffic via Nairobi, while Zambia would poll (or generate a computer call to) Harare, which would in turn poll Nairobi for regional mail.
The University of Zambia (UNZA) hosted an experimentation and review workshop in November 1992. Our aim then was to enhance internode telephone calls (polling) and review the progress of the project to date. At the time of the review workshop, we observed that some interesting trends had clearly emerged and we realized that the assumption upon which the topology had been drawn was evidently unattainable. For instance, the interregional polling in East Africa was not possible due to several factors: delayed arrival of equipment purchased from overseas suppliers; wrong power specification supplied; or poor telephone lines at
the node on an old analog exchange. Hence, while activity was well under way in Uganda by February 1991 and a little later in Tanzania, the MUKLA node only became operational in August 1992.
MANGO, the NGO network in Zimbabwe, was an established Fidonet bulletin board by the time the ESANET project began and so only needed to integrate the ESANET activity early in 1991. UNZA was also fully operational early in 1991 but routed its regional and international traffic through Rhodes University in South Africa. Interregional polling between these two was never reliably successful owing to poor interconnecting telephone infrastructure between Zambia and Zimbabwe. All of the ESANET participating institutions and bodies met in September 1993 at an evaluation and closeup workshop held in Uganda.
As it happened, Doug Rigby, a networking consultant at the Environmental Liaison Center in Nairobi but also working for the NGOnet-Africa Project, visited Kampala in February 1991. I was then a final year student of Engineering at Makerere University but on forced vacation as a result of student riots that caused the closure of the campus.
My meeting with Rigby was helped by the student riots as much as by my volunteer work at an environmental NGO, called JEEP, a grassroots network organization. JEEP staff asked me to meet Rigby at the Entebbe airport. This was perhaps my longest wait at an airport for any visitor coming from abroad—as the scheduled flight, I later learned, had been a phantom one. All the same, I persevered until he arrived on a late evening plane and took the 35 kilometer journey back with him to Kampala. After hearing his stories enroute, I never regretted the long wait and I slept that night dreaming about this intriguing new concept of electronic mail! The following week was to usher in many more exciting ideas that have led, as it turns out, to a new and unforeseen career.
With Rigby, we went through the drills of Fidonet: installing a modem; communication software for end users; and even basic DOS commands. The team of trainees had now grown to five: the then three folks from the Institute of Computer Sciences; one representative from the Developmental Network of Voluntary Associations (DENIVA), an umbrella network body for local and indigenous NGOs in Uganda; and myself. A windup workshop of Rigby's mission brought together the first batch of potential users from different organizations. Among them were people from CARE (the relief agency), the Centre for Basic Research, the Makerere Medical School, a handful of DENIVA members, JEEP itself, the Makerere University's Vice Chancellor, and other independent participants.
While I may not have been the most conspicuous participant, I had apparently caught the eye of some people and I was chosen as the person to carry the mantle of making it work.
The Critical Years
I quickly realized that my new role would have to be accommodated within my academic life when campus reopened. That I did by working at the node after classes, not an easy thing to do for an engineering student. The next thing was that I had to do to this work as a volunteer. There would be no pay at first. I still remember those first meetings with prospective users—environment groups, missionaries, and other NGOs. This was new to all of us. Even as I crawled under desks to connect modems to telephones, and even as I made test polls to Nairobi, not one of us was sure that we were not going to get enormous telephone bills. I wasn't all that sure that I would be able to pay the actual telephone bills, even if they were not enormous! (See Box 2 .)
The harder electronic networking seemed the more determined I was to prove that it worked. It was the best thing I could have done. The process taught me a great deal, refined my thoughts considerably, and led me into contact with many people whose expertise I would need if this was going to succeed.
Originally, I had planned to set up a non-profit network for NGOs to run parallel to MUKLA. That might have been ideal but, with my unfinished engineering degree in the way and a lack of clear institutional support from the NGO community, this seemed a formidable task. I labored to convince the director at the ICS that there was more to be gained in merging ESANET with NGOnet activities than there was in operating them separately.
Shortly after the university reopened, however, we reached agreement and installed the ESANET equipment and procured a dedicated telephone line. The MUKLA node got under way and the real fun began! At the end of our first year of operation, we had nearly 50 users, quite a remarkable achievement and a good omen for an exciting future. We were beginning to fulfill many people's dreams for use of this media. At this point, I stood as the systems operator (sysop) and manager of an ever-growing network. I was confident that I had established a sound management structure to introduce cost recovery. The director's secretary would handle billing and accounting while I concentrated on software and hardware developments as well as other technical matters.
Project Synergy
The ESANET project, with its idea of electronic networking at the Institute of Computer Science, took second place to the higher profile and better funded UNESCO Intergovernmental Informatics Project (IIP). The IIP was aimed at sensitizing decision makers in government and other sectors of society on the use of informatics tools in decision making and management. The attention paid to the IIP reduced high-level interference in the day-to-day running of MUKLA. Electronic networking nevertheless benefited from the many IIP workshops organized where email was always on display.
As the rush to sign on to MUKLA grew, so too did the pressure on the hardware—then a 386 SX, 2 RAM 80 megabyte hard drive personal computer. So, by July 1992, with the user base standing at well over 150, the node personal computer was upgraded to a 486DX 33 MHz, 8 RAM and 170 megabyte hard disk from the IIP project consignment.
At this level of expansion, MUKLA posed a real management challenge. With technical capacity to handle new installations and user support overstretched, we made a decision to get more members of the teaching staff involved. One person was put in charge of documentation and promotions, while a technical assistant was assigned to help me. (See Box 3 .)
Billing and accounting were firmly put in the hands of an accounts clerk who also doubled as the director's secretary. I believe that the stability of our network caught the attention of other regional networking projects, based mainly in Nairobi, and that they borrowed ideas from our experience. We then had over 10 groups or users dialing-in on long distance trunk phone calls from Nairobi and other parts of Kenya.
Around this time I was drafted into a number of regional initiatives. I, for instance, participated in the design and implementation of the UNEP/Global Environment Facility (GEF) Greenhouse Gases project to link up researchers in six
African countries, namely: Uganda, Tanzania, Nigeria, Senegal, Morocco and the Gambia. I was also hired as an independent consultant for the CABECA project to setup and train systems operators in Uganda, Nigeria, and Ghana. (See CABECA box on page 147)
Between the UNEP/GEF and the CABECA project I have established a total of nine nodes in the above mentioned countries. I have also trained a score of in-country technical support people and have installed several end-user sites for access to email and the Internet. I have also set up email access for the UN's World Food Programme (WFP) offices in Dar es Salaam, Mombasa, and Kampala. Only recently I was on mission to war torn Burundi on an International Alert of London mission. There, I set up email so that the UN's special Representative to Burundi could access information and participate in discussions aimed at better informing the world and also the warring factions in conflict resolution.
Present Situation
From around mid-1993 to the present, we began routing MUKLA's international traffic through the GreenNet's GnFido node in London via four daily polls. This link works satisfactorily well, though disruptions in the past often occurred due to factors such as adverse weather conditions. Lately, the unreliability of the GnFido node can be attributed to over-stressed hardware facilities coupled with lack of support staff.
As of January 1995, MUKLA had an installed user base of over 300 sites. The majority of these are around Kampala but there are about 15 sites in Entebbe (35 Km from Kampala), five in Jinja (80 Km east), three in Mbale (150 Km east, close to the Kenya border), three in Mbarara (220 Km southwest), and three in Kabale (400 Km southwest, close to the Rwanda, Tanzania, and Zaire borders). The upcountry installations all have to make long distance calls to Kampala.
It therefore became imperative to set up local access points in these towns. In February 1995, a node was established in Entebbe at the Uganda Virus Research Institute with equipment supplied by the HealthNet project. Similar nodes are planned for Mbarara, Kabale, Mbale and Jinja during the first half of 1996.
Even now a few users call in from Nairobi, though the majority of regional traffic flows to MUKLA via Sasa Communications System. This company, based in Nairobi, is an initiative of the East Africa Internet Association. (See Box 4 .)
Recent Developments
Throughout 1995, I consulted for a commercial enterprise (StarCom) to help establish a full Internet (IP) link for the Uganda market. In August 1995, another company (InfoMail) opened full IP access from Uganda—thus becoming the first site in East Africa and the Horn of Africa region to give full access to the Internet, including facilities such as World Wide Web. Starcom became operational in November
1995. It is noteworthy that both these companies implemented international access using very small aperture terminal (VSAT) satellite technology in preference to the overpriced and unreliable digital leased lines from the Uganda Posts and Telecommunication Corporation (UP&TC).
As seen from the information in Appendix A , the electronic network market in Uganda is now fully liberalized with not less than five providers with services ranging from email access to full Internet. However, the usage charges remain high. The charges given are accurate as of January 1996.
Results, Impacts, and Benefits of the Project
Beyond email.
While the bulk of our traffic on MUKLA remains electronic mail, there is a new trend towards user participation in electronic conferences. MUKLA at the moment carries over 50 different conferences mostly from the Internet and APC networks, with a few specifically regional or local ones. Perhaps the most notable among these is a discussion list on Uganda-related issues and news, appropriately called Ugandanet. Through this conference, over 600 Ugandans from all over the world link with each other on a daily basis to interact with lively discussions on various topics ranging from the constitutional process, to entertainment, to sports and news.
Perhaps responsible for the bulk of growth in the beginning was the email/fax service that MUKLA provided. Users are able to send, at the price of email, faxes to destinations all over the world. Its popularity was mainly due to the exorbitant international charges levied by Uganda Post & Telecommunication.
Sectoral Involvement
Electronic mail has had a particular attraction for research activities to many researchers. Students are also increasingly getting to use email. About 25 percent of MUKLA traffic is for university related activities.
Non-Governmental Organizations
These form the single largest group of MUKLA users accounting for over 40 percent.
The involvement of government in any major way has not come yet, although from the early days government departments were interested in what we were doing and, in 1992, we were approached by many government bodies for connectivity. Presently, however, only isolated projects within government departments are connected, usually for very specific reasons, such as easy access to a donor office abroad. We have been approached by the Ministry of Foreign Affairs to explore possibilities for linking Ugandan embassies, especially in particularly hard-to-reach places like Zaire and Rwanda.
Business Sector
This perhaps remains a weak and under-represented section of the network. Nevertheless, from the early days, business users concerned with sustainable development issues began to join us.
There are many other individuals and independent groups that MUKLA knows are interested in electronic networking. We have yet to tap this group.
Though MUKLA benefited from the ESANET research fund as seed capital, cost recovery was instituted at an early stage to supplement this. As of now, and at completion of the ESANET project, MUKLA is fully self-financing through fees
levied on users. A check is put on users via shadow billing whereby an itemized bill for all users is prepared at the end of the billing quarter to check on excessive use and possible abuse of our lenient terms. There is no additional charge for the fax facility though strict monitoring is done for each of categories above. When excessive use is noticed, the user is upgraded to the higher billing group.
The ESANET project introduced the idea of electronic mail communication to researchers and other users at Makerere University campus—though the focus of the project was then on experimenting with various computer-based communication technologies and working out the technical bugs involved with poor telephone lines, erratic management of the telephone long-distance dialing system, and hardware and software equipment.
As of September 1993, most of these problems had been ironed out. The electronic mail system using the GnFido system has reached a level of reliability that surpasses that of fax machines. A cost-effectiveness analysis was carried out at the end of the ESANET project and this provided the evidence needed to prove that this venture could be sustainable, given the proper setting and management.
The ESANET project established that microcomputer-based electronic communication was a viable, sustainable technology and appropriate to the context of the region in which it has operated. There is a proven demand for electronic communication, both regionally and internationally. Following are the recommendations from the ESANET project:
To the research community, we recommended that:
- Relevant institutions be encouraged to consolidate and expand their user base.
- We should undertake more research into improving and expanding technologies used.
- Manpower requirements for this activity be consolidated into the establishment of the institutions concerned.
- Appropriate mechanisms be established for operational cost recovery and institutional funding to cover system operation and expansion.
- Cognizance be taken of the ever-improving nature of electronic communication worldwide and relevant upgrading be considered.
To the telecommunication authorities, we requested:
- Further investment be made in improving regional telecommunication links to enhance electronic viability of using national telecommunication infrastructure for modem related activities
- Special tariffs be applied to the academic and research communities for packet switching and leased line facilities thus enabling greater access to computer based communications regionally and internationally.
- Liberalization of user terminal equipment connected to national telecommunication networks be encouraged.
- Pragmatic policies be established with regard to licensing of alternative communication methodologies such as packet radio and low earth orbit satellite.
To the donor community, we recommended that:
- In view of the fact that national communication networks are an indispensable component of national development, providing as they do for an efficient and effective information delivery system in diverse sectors, continued funding be made available for establishing infrastructure related to computer-based communications for capacity building in order to facilitate transfer of technology.
To regional governments, we recommended that:
- They recognize the importance of national and regional networks for all aspects of development and for human resource and manpower interactions. The final meeting of the ESANET project paid tribute to the invaluable contribution that IDRC had made through this project in furthering the case of electronic communication within academic, health, and other related communities. We accordingly asked IDRC to:
- Ensure that ESANET nodes be covered in any forthcoming regional electronic network support programs.
- Share the findings of this project with other donor and development agencies.
- Be receptive to future requests from ESANET community to consolidate and expand what has been achieved so far.
The ESANET project provided the participating institutions the opportunity to experiment with regional and international microcomputer-based communication. The aim of the experimentation was to establish the viability of the regional computer networking for data communication from the technical and management perspectives. We acquired data and experience from the experimentation phase of the project using Fidonet and packet satellite technologies. Based on this experience and data, we made the following specific observation on hardware, software, connectivity, network management and research activities.
For modems, we have observed that:
- 9600 baud or higher modems (e.g., Telebit Worldblazer) perform better for international connections, while 2400 baud modems (e.g., GVC 2400) are sufficient for local connections.
- External modems perform better and are easier to handle than internals.
- Modem power supply should be 240V AC.
- Modems should be Hayes compatible.
For the node computer, we recommend a machine with the following specifications:
- 386 or higher,
- a minimum of 4 megabytes RAM,
- 120 megabyte hard drive minimum (max 12 ms cached),
- dual floppy,
- fast serial ports,
- 220 V AC supply, and
- UPS with stabilizer.
There is always a need to have a backup computer.
We used the following software packages in most of the our node operations:
- FrontDoor 2.1+—mailer
- Gecho—conference mail processor
- Msgtrack—mail tracker,
- ReDir—mail redirection
- GUS, Echovol—for conference tracking,
- AC—for accounting and billing
Connectivity
We observed that GnFido, Rhodes University, or WorkNet polling into ESANET nodes was cheaper and easier than direct polling between ESANET nodes. This has been the case for regional as well as international traffic. We thus disproved the earlier assumption on which the interconnectivity topology had been based.
We also observed that:
- A massive effort was required to develop and support a user base. We needed advertising, workshops, and maintenance visits.
- There was a need to clarify to the users what installation and support imply and discourage frivolous requests.
Network Management
To sustain the network it is important to:
- train system operators and establish official positions for system operators at various universities and
- put into place efficient and cost effective cost recovery mechanisms.
Some Fidonet management tools are available in basic node software. Additional software was developed during the project period to supplement these basic tools. Examples are: AC (accounting) from the Zimbabwe node and MTMON and HISMON (monitoring) from the Zambia node. However there is still need to develop more tools. Whereas there was sufficient documentation for point operation (the lowest level of the Fidonet hierarchy), there was need to develop more documentation for node operation. Nodes are the individual systems that belong to Fidonet. They are responsible for passing mail between the points and the next hierarchical level of Fidonet—the hub.
Research and Development
We need to encourage technical innovations to improve the system and we can use student resources for such projects. Technical innovations are required in the following areas:
- Terminal Node Controller (TNC)
- The packet satellite upload program (PG)
- Modems and modem testing/evaluation
- Mailer interfaces
Beyond the ESANET Project: Future Developments at MUKLA
While the interest in using electronic mail among researchers is strong, the technical capacity to meet this demand remains severely constrained due to lack of adequate funding. Additional funding is needed both for the personnel involved in
its spread and for the purchase of hardware upgrades for the present installation. Although a number of groups and individuals have expressed interest in using and learning more about electronic mail, there are no adequate pedagogical materials nor the funding to have technical experts available to advise on both hardware and software problems as well as to do the installation and training.
Given the lessons learned from the experimentation phase, with the outlined constraints, it is imperative that MUKLA seek to improve its institutional capacity to effectively spearhead a development plan. We will seek support for recruiting trainers whose job will be to build on the achievements to date and enhance the existing network amongst all these groups. We will also seek support to update the hardware at the existing nodes and to create a pool of modems to serve as seed investments in new areas where electronic communication is to be introduced.
Specific goals should be towards:
- upgrading the hardware and software at the MUKLA node to full Internet status via leased line;
- developing appropriate educational materials and formats for workshops and short-courses;
- providing technical assistance and training; and
- facilitating communication via email amongst users within the country and region.
There are two sets of activities to look at in the process. The first would involve the acquisition of the necessary funding and identification and purchase of the necessary hardware for a full IP connection. Simultaneously, we would prepare training materials for the use of electronic mail, instruction on both hardware specification and troubleshooting, and hands-on training with the software. The second set of activities will include the provision of regular and ongoing technical support to users. This will be necessary both to iron out technical problems encountered in the daily operations of the electronic mail, as well as to sensitize and train new users.
We expect that the user base will have grown to an estimated 2000 installed sites by the end of 1996. It is time now to consider new nodes to improve services in areas outside of Kampala. Some possible sites for expansion of MUKLA are given below.
Entebbe is a major seat of government ministries and headquarters to many international United Nations bodies and NGOs. It is ripe to have a node established that could serve as hub to all users in and around Entebbe. This node would periodically poll MUKLA to transfer national, regional and international traffic.
There is potential for up to 150 installed sites within one year; this would also relieve the pressure on MUKLA.
Kabale located about 400 Km from Kampala has good potential to play a node role for Rwanda, Burundi, and some parts of Western Tanzania that fall within the Kagera Basin. Kabale is the gateway to these countries that have traditionally used the northern corridor trans-Africa highway to link them to the Kenyan seaport of Mombasa. There is an automatic exchange that is part of a large telecommunications project linking the countries that comprise the Kagera Basin Organization (KBO): Burundi, Rwanda, Tanzania and Uganda. With 3,000 lines, the exchange is the most modern to be installed in Uganda. The KBO regional telecommunications project consists of a microwave transmission system interconnecting the four countries. It is aimed at the promotion and development of agriculture, forestry resources, and telecommunications links between member states that share the river Kagera.
Goals of Expansion
The nodes in Entebbe and Kabale, together with a series of training workshops for users in Jinja and Mbale, would constitute the first phase of the expansion program.
Existing national and international mechanisms of information processing and exchange, and of related technical assistance, would be strengthened to ensure effective and equitable availability of information generated at the local, provincial, national, and international levels, subject to national sovereignty and relevant intellectual property rights.
National capacities would be strengthened, as would capacities within governments, non-governmental organizations and the private sector, in information handling and communication, particularly within the East African region.
Improved Services
MUKLA would offer its clientele the full benefit of a wide range of Internet services. Electronic mail and conferencing, public and private access to Internet mail and other worldwide networks might be provided via partnership with the Association for Progressive Communications. MUKLA can also provide consultancy services on network establishment for organizations and government departments.
Future Needs and Possibilities
One of the difficulties we face as we prepare for future developments is to clarify the role of what is essentially a well meaning private enterprise with the responsibilities in this area of various tiers of government and public in Uganda.
The question of appropriate ownership structures for networks like ours is quite complex. Our decision to operate as a private company was indicated at the time of our birth. The people are sufficiently interested to devote time and financial energy to the project and do not have any particular philosophical attachment to a mode of operation.
However the structure has served us well amidst the politics of governments and NGOs. We have always regarded ourselves as the carriers of information related to these issues, rather than as a policy body or an arbiter of truth and best practice. In the early days, this structure and philosophy allowed us to engender cooperation between NGOs who did not see eye-to-eye on all issues. In later days, the same stance has allowed us to assist cooperation between tiers of government and government departments, which have been known to jealously guard their own interests rather than cooperate. And, more importantly, we have managed to remain credible with both government and its more radical opponents. It is probably our strongest point, that we can operate independent of the political will of any tier of government or its funding priorities.
The future holds many specific problems to address—questions of cooperation, questions of standards, and questions of access to information will have to be addressed. Much work will have to be done towards these ends by both ourselves and government bodies.
Regional Interconnectivity
There will be immense savings by sharing costs and collaborating with other regional providers. The East African Internet Association (EAIA) effort could be one way to foster further regional interconnectivity. (See Box 4 on page 164 for more information about EAIA.)
My experience suggests that there is far more to establishing a successful network than purchasing and learning the technology. Indeed, technology expenses have been a minor part of our budget. Outlined below are some basic principles I believe are essential in establishing viable networks.
User Friendliness
Experience indicates that the issue of user friendliness is one where there should be no compromise. Simplicity of interface is crucial; however, simpler interfaces, those that use graphics, for example, also require more computing power. It is important to have machines with adequate power, memory, and speed to perform the necessary tasks. This is where a full needs analysis is necessary. The simplest looking interface may not do the job; nor will old or obsolete equipment provide enough sophistication to run programs such as Windows.
Adherence to Standards
The only trade off in user friendliness that might occur would be in the area of adherence to standards. Here, important standards have to be considered if contact with global networks and global relevance of data collected are concerns.
Promotion and Education
The most common mistake we can make in large scale electronic messaging installations is believing that somehow the system will ''introduce itself." Not so! You can only successfully train the converted. The network has to be actively promoted. Its benefits have to be known before people will use it. Its applications to work areas and advantages have to be received with enthusiasm. Without this, the basic aims will not be achieved.
Equally, training is an absolute must for a successful implementation. Links should be made to existing training organizations. Training materials must be available for any software used. (See Box 5 .)
Product Champions
The concept of a "product champion" is often mentioned in sales literature. It essentially refers to enthusiasts who promote concepts and products willingly because they believe in them. All networks need them. Product champions sometimes create problems for organizations with their over-enthusiasm and are rarely popular with administrators. But they are totally necessary and need to be identified and supported.
Adequate Funding
An under-funded initiative that fails can delay a concept such as sustainable development networks in a country by a decade or more, and a few failures can
ruin the concept altogether. It is far too easy to attempt to stretch available funds too far and to leave behind a string of underdeveloped projects with little chance of success. It is also far too easy to get carried away by enthusiasm and to start a project without sensible financial plans to ensure viability.

Appropriate Ownership Patterns
This is a difficult question for which there is no immediate formula. An appropriate ownership pattern has to be one which will not restrict the participation of any governmental or non-governmental body whose cooperation is needed.
Plans for Financial Sustainability
Unless the venture is to be a continual financial burden to funding organizations, a realistic business plan has to be adopted to ensure that the network is self sustaining within a given period (perhaps 2–4 years).
Managerial, Sales and Technical Expertise—in that order!
The need for managerial expertise must be obvious, as is the need for technical expertise. What is less obvious is the need for sales expertise. Even if a facility is not expected to raise revenue, it surely is expected to engender use and that's a sales job.
In conclusion, I would state that the world is not a series of isolated ecosystems bearing no relationship to one another and capable of resolving their own problems. National sovereignty does not rule the atmosphere, nor the oceans, nor indeed the rivers that meander happily across borders with no care to the politics of the government of the day. Global cooperation is vital, and access to the experiences and knowledge of others is essential if we are to solve the problems facing us.
Indeed, this paper is written in the belief that what we have achieved and learned in Uganda is valuable, and may be of assistance to people in other countries wishing to establish similar facilities. We would be happy to assist and advise based on our experiences here.
Appendix—Internet/Email Providers in Uganda
1. MUKLA Institute of Computer School
Makerere University, P.O. Box 7062, Kampala
Contact: Charles Musisi, Network Manager
Services offered: Electronic Mail, Listservs, APC conferences/Usenet, Faxing
Usage charges
2. StarLight Communications (U) Ltd (STARCOM)
Sheraton Complex, 14 th Floor, Ternan Ave., P.O. Box 10524, Kampala
Contact: Kiggundu Mukasa, Internet Manager
Services offered: Email and email fax, World Wide Web, Telnet, FTP
Usage charges:
3. Infomail (U) Ltd Plot 2 Clement Hill Rd. P.O. Box 11465, Kampala
Contact: M.M. Otyek, Manager
Services offered: Email, World Wide Web, Telnet, FTP
4. Transmail Ltd Blacklines House, Suite 2B4, P.O. Box 7482, Kampala
Contact: Patrick Mawanda, Manager
Services offered: Email, Electronic Fax, Mail Broadcasting, Conferencing
5. InfomaNet 4 th Floor Impala House, P.O. Box 8945, Kampala
[email protected] Contact:
Christine Nantongo
Services offered: Email, Fax
Quick start plan:
Power user plan:
The UNIMA Fidonet Network: Computer Networking for Communications in Malawi
by Paulos Nyirenda

Dr. Paulos Nyirenda is Head of the Department of Physics and Electronics at the University of Malawi. He has a Ph.D. in electrical engineering from the University of New South Wales. He has been working on networking at the University of Malawi since 1992. He asks that this chapter be dedicated to his late wife, Gemma .
Malawi is a landlocked country located on the southeast side of Africa. It shares boundaries with Mozambique, Tanzania, and Zambia. The country has a population of about 9 million, of which about 90 percent live off subsistence farming. Malawi's economy is agricultural-based, with few manufacturing or mining industries.
The University of Malawi is the only university in the country. It is made up of five colleges spread out over a wide geographical area in the central and southern sections of the country. There are many research institutions in the country, most of which are linked to the agricultural sector and, as such, are located in remote locations across the country. Most of these research centers have access to direct exchange telephones that work most of the time but are of relatively poor quality, just as in some other African countries. Also, as in other African countries, the telephone penetration into the population in Malawi is very low.
Communications in Malawi is difficult and expensive. Research and data communications have been achieved primarily by physical travel to a site—often over seasonal roads in poor condition—or by fax where available. This is also the case for most governmental and private sector communications. Most needed research and other data and information do not reach the people and decision makers who require this data to make important national and international decisions.
However, even as early as 1992, most research, governmental, and major commercial offices had computers. Most of these were IBM-compatible desktop computers or Apple Macintosh computers.
Realizing the difficulty of communicating among widely separated university colleges and research institutions, I proposed a project titled Study of Computer and Telephone Network Based Communications in Malawi . The proposal was submitted for funding to the University of Malawi (UNIMA) Research and Publications Committee (RPC) in February, 1992. The original budget was for Malawi Kwacha (MK) 5123 1 or roughly $1,000. The main objectives of the project were to:
- investigate the feasibility of establishing computer and telephone-based communications in Malawi; and
- demonstrate more efficient and effective communications among researchers and academics within Malawi as well as among those in Malawi and outside.
With these objectives and minimal base funding, the Malawi Fidonet network was started. The network, now called UNIMA , has grown to be a public, nationwide network serving all sectors—government, non-governmental, and commercial—of the Malawi economy. It thus serves a much wider population than the academic and research communities originally envisioned and for which I had budgeted. It is a public network in the sense that anyone and any organization in Malawi can be linked to the network—provided they have the basic resources required for such linkage. The project has since attracted funding from various national and international organizations.
The proposal I made to the University led to the establishment of the UNIMA Fidonet network. The specific objectives of the proposal were to:
- experiment with modems, microcomputers, and the telephone network for data communications within the University of Malawi;
- design and build electronic interface devices for connecting direct telephone lines and switchboard (PABX) extensions to one computer and modem node to handle both local college and direct line connections;
- evaluate the quality of the Malawi telephone network for data communications; and
- evaluate the cost of computer communications using modems and the telephone network and compare it to other electronic communications modalities.
At the time the UNIMA project was started, there was a regional project called the East and Southern Africa Network (ESANET) funded by the International Research Development Centre (IDRC) of Canada. (For a complete description of the ESANET project, see Charles Musisi's case study on page 158.) The UNIMA project had similar general objectives to ESANET, which linked university computer centers in Zimbabwe, Zambia, Tanzania, Uganda, and Kenya. Because I was involved in these activities, the UNIMA project benefited considerably from the ESANET project in the beginning, even though Malawi was not a participating country in ESANET. The startup modems and non-commercial Fidonet software that enabled UNIMA to take off were obtained under ESANET.
My proposal to study computer and telephone-based communications in Malawi was accepted by the RPC in January 1993. I next needed to request security clearance from the Malawi Government, as well as from the Malawi Posts and Telecommunications to start the project. The government issued the security clearance on 15 June 1993, one day after citizens passed the referendum that introduced multiparty politics into Malawi. The Malawi Posts and Telecommunications Department then cleared the project in July 1993. The direct telephone line required for the node or hub of the telephone-based computer communications network was installed at Chancellor College in Zomba on 24 September 1993.
We next installed the equipment for the node: an IBM-compatible 386 computer running at 20 MHz with a disk space of 40 megabytes (borrowed from the Physics Department at Chancellor College); a VIVA 2400 baud modem donated by IDRC under the ESANET project; and non-commercial Fidonet communications software (FrontDoor 2.02) obtained under ESANET and tested earlier. This startup setup was then used to negotiate the network address, initial mail routing, and initial polling procedures required for the network. In the startup phase, the network address was negotiated under ESANET to be a Fidonet point address off the University of Zambia electronic mail network. Malawi now has its own network number and the node established has the Fidonet address 5:7231/1. 2
Connecting to the University of Zambia Fidonet node was very difficult and, when the connection was finally made, the line quality was poor. We decided in November 1993, to switch connections to the Africa Zone Gate directly at Rhodes University in South Africa. This improved the connection success rate as well as the quality of the connections. In May 1994, the UNIMA network started receiving funding from the Capacity Building for Electronic Communications in Africa (CABECA) project also funded by IDRC but managed under the Pan African Development Information System (PADIS) in Addis Ababa, Ethiopia. (For more information about the CABECA project, see Fall's case study on page 147.)
Under CABECA, the UNIMA network received more modems and assistance from the Southern Africa Non-Governmental Network (SANGONET) in Johannesburg. SANGONET polled the UNIMA system twice a day at first but this was upgraded to three times a day to cater to the increased volume. Also under CABECA, we upgraded the node with the installation of a Telebit WorldBlazer high speed modem. This modem was eventually replaced by a US Robotics modem.
Figure 1 shows the general Malawi Fidonet network and its linkage to other networks in the world. The number of points running off the node has increased
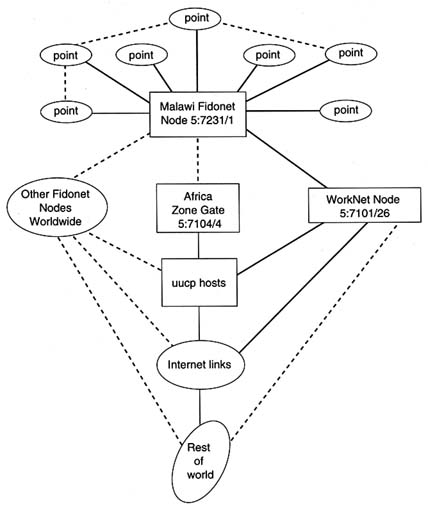
FIGURE 1 Fidonet structure in Malawi.
rapidly even though the single most important constraint to the growth in the user base has been the availability of modems at an affordable price within Malawi.
We replaced the computer borrowed from the Physics Department with a dedicated computer borrowed from UNIMA RPC. This was also an IBM compatible 386 computer with the same speed but with a 104 megabyte hard disk and more memory. This computer made it possible to perform multitasking using Desq View and QEMM. This allowed us to operate two telephone lines, using intermail as the communications program on the node. With this setup the node is now able to handle two data connections simultaneously, one on a direct exchange telephone line and another on a PABX telephone extension that caters to the local Chancellor College campus computers. Putting in the line from the local PABX helped to reduce congestion considerably on the direct line.
The use of a multiline mailer that enabled the node to handle more than one telephone connection at the same time made it unnecessary to develop hardware devices to achieve the same results. However, there were problems with rescanning the mail every time it was collected from the node. As the message base and user base grew, this mail rescanning took more and more time and eventually led to lengthy in-between call processing, leading to delays in answering calls at the node.
After observing the significant contribution that the Fidonet UNIMA network was making towards improving data communications in Malawi, the World University Service of Canada (WUSC) provided funds to the UNIMA network in February 1995 to purchase a Gateway 2000 IBM compatible 486 DX2 computer with 730 megabyte hard disk and running at 66 MHz. This has considerably improved the performance of the node, which can now process mail much faster and has removed the waiting that users experienced between calls while the node computer was processing received mail and extracting billing information. In addition the network has also received support from the Canada Fund of the Canadian High Commissioner to Malawi to purchase modems to assist the public sector in getting connected to the network so as to improve their communications.
UNIMA Network Operation
Under Fidonet, electronic messages and files are prepared offline to reduce telephone connection costs. The messages and computer files are then transferred onto the network in compressed files or packets to reduce the time of the telephone connections and to improve efficiency. When a point has a message to send, the message is normally sent to the node to be routed to its destination. If the message is destined for another point on the UNIMA network, the message waits at the node to be picked up by the destination point. Before April 1994, the node originated international calls to the Africa Zone Gate at Rhodes University for delivery and collection of international mail. All international mail is now routed via SANGONET, which polls the UNIMA node three times a day. International mail from Malawi is made to wait at the Malawi node in Zomba for international delivery during one of the polls from SANGONET.
When mail is received at the UNIMA node, it is processed by the non-commercial Fidonet mailer and other mail processors. Gecho.exe (version 1.01) is used as a mail and conference processor and also for mail compression and decompression. Netmanager, Netmgr.exe (version 0.99), is used as a general message processor for message-by-message identification, distribution, and redirection. Message tracking is done by msgtrack.exe, which produces a message-by-message log indicating such data as message origin, destination, dates, and volume.
I have written additional software to produce bills sent to users for cost recovery and network sustainability. Most of the billing information is obtained from the data produced by msgtrack.exe. Other data used to evaluate the performance of the network and the telephone system is collected from the various log files produced by the mailer and mail processors and analyzed using tools developed at the UNIMA node.
Network Performance
The network performance reported here was monitored at the UNIMA Fidonet node. As outlined above, the node software produces log-files (logs) for the day-to-day, telephone call-by-call, as well as the message-by-message activities that the node performs in sending and receiving electronic mail and files. The collection of the data presented here started in October 1993 and ended in March 1994. Much more data has been collected at the node but this has yet to be analyzed. By processing the log files, the monthly international mail volume can be determined. This is shown in Figure 2 .
Cost of the Service
Shown in Figure 3 are the costs of sending or receiving one kilobyte volume of mail and the monthly telephone bill in Malawi kwacha, as charged by Malawi Posts and Telecommunications Department. This calculation was done on a month-to-month basis as well as on a cumulative basis where the total bill and the total volume, up to the dates shown, were used to calculate the cost per kilobyte of mail. As shown in Figure 3 , the cost of operating the network per kilobyte of mail has dropped from MK4.68 (four Malawi kwacha and sixty-eight Malawi tambala) in October 1993 to MK0.88 in March 1994 on a month-to-month basis and from MK4.68 to MK1.10 on the cumulative basis. Using these data, the node has recommended that users be charged at the rate of MK1.00 per kilobyte of mail sent or received internationally. This charge rate was still in place at the writing of this chapter.
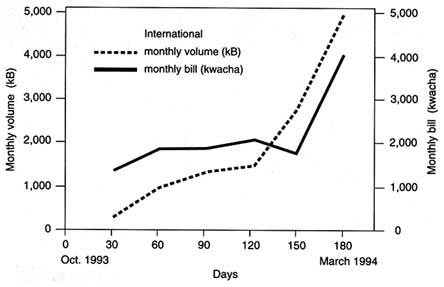
FIGURE 2 International email volume and telephone bill using a 2400 baud modem.
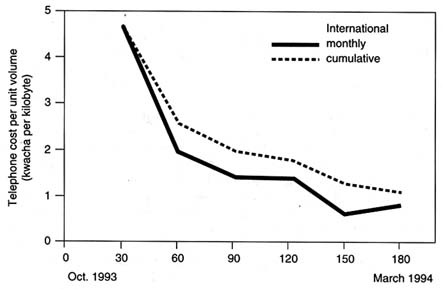
FIGURE 3 Cost per kilobyte of international telephone calls for email transfers using a 2400 baud modem.
Although the modem used for collecting the data changed from a 2400 baud modem to a 14400 baud one (with most good connections at 9600), the Malawi telephone charge per minute also changed upwards considerably from about $1.00 to $3.00 per minute in January 1995. We are currently collecting and analyzing data to check the effect of the modem speed change versus the telephone charge rate change.
A comparison between the cost of using the email system and using a fax to transfer text messages can be made based on the above data. One full page of text (as on this page) uses nearly 3 kilobytes and would therefore take MK3.00 to send by email. After examining several fax transmissions at Chancellor College, we found that such a page would take more than one minute to send but often less than two minutes. (The Malawi Posts and Telecommunications would therefore charge two minutes.) Most of the international mail transferred during the observation period has been for contacts outside Africa. The cost of sending such text messages internationally by email is therefore about 20 times cheaper than faxing similar messages at the current telephone rates and email charges at the UNIMA node.
Billing Users
Using the data collected from message tracking, a bill is sent from the Bursar of Chancellor College in the University of Malawi to each user once every three months. In addition to the volume fee outlined above, which now stands at roughly seven cents per kilobyte, each user account held outside the university is charged at 70 cents per month for account maintenance. Experience has shown that although these rates are very low, most Malawian users and organizations still have difficulties paying. I am currently proposing to conduct a study to find out whether this is due to genuine financial difficulties. I hope that user perception of ''user pays" electronic communications will be better understood following the survey and analysis of the results.
I have shown in Figures 2 and 3 that even though the monthly bill and the monthly volume of mail sent and received internationally are increasing rapidly from month to month, the cost of sending mail per kilobyte has steadily approached a constant value. I expect that the speed of the modem used at the node will play a crucial role in determining the cost per kilobyte of international mail transferred at the node. At the moment this has been complicated by the international charge rate change made in January 1995. I hope that the further data analysis now being carried out will assist in clarifying the situation.
All the money raised from the bills is paid into a project account held at the Chancellor College Bursar office. Money in project accounts does not get absorbed into the University's pool account; although the money does not generate interest in such accounts, it is available when required to pay the bills incurred by the project. It also helps cover equipment maintenance and staff costs.
Failure Rates
Figure 4 shows the failure rate of telephone calls for data transfer as monitored at the node. All the calls at the node involve the Malawi Telephone system. Data transmitted during a call that fails in some cases have to be re-transmitted because the decompression of the data at the receiving side fails due to incomplete packets or files. Thus a failed call is a major concern to a user on the network. As can be seen from Figure 4 , the proportion of calls that fail has come down considerably from nearly 100 percent in October 1993 to about 18 percent in March 1994. This improvement in performance can be attributed to various factors. The international mail route changed in November 1993 from via Zambia to via South Africa. We observed that fewer calls fail on the new route. We have also learned when to make the international calls in order to achieve higher success rates. This information was not available during the startup phase of the network.
The number of calls to the node from Fidonet points within Malawi has grown considerably as a proportion of the total number of calls recorded by fdstats.exe at the node. This means that while the performance reported in Figure 4 applied more to international calls in the startup phase of the network, it applies both to national and international calls in March 1994. We can estimate from Figure 4 that on the Malawi telephone system about 18 percent of the calls for data transfer
FIGURE 4 Failure rate of telephone connections using a 2400 baud modem.
using modems will fail. More data needs to be collected and analyzed to determine the separate failure rates of national and international calls on the Malawi telephone system and to determine the rate which the graph in Figure 4 settles down to.
Network Use
The main services on the Malawi Fidonet network are electronic mail and file transfer. No remote login of any kind is currently supported. We need to conduct a survey to determine and categorize the purposes of sending mail by users within the University of Malawi and outside. During the experimental phase of the network, we have sought such information from users in the University and outside. The message tracking software at the node collects information on the sources and destinations of mail. We have observed that University of Malawi users use the Fidonet network mostly for the following reasons:
- contacts with academic colleagues and supervisors;
- negotiating links with other universities at department level;
- submission of research papers, proposals and reports;
- applying for further studies abroad;
- coordinating research for staff on study leave abroad;
- library contacts;
- seeking funding for research and other projects;
- discussion of issues pertinent to Malawi;
- ordering equipment from suppliers outside Malawi;
- personal mail; and
- file transfer using archie and ftp by email.
In using the network, University staff and other users are finding it easier and more efficient than before to request and access information from colleagues and institutions outside Malawi. I hope that as the network grows inside Malawi it will also become easier and more efficient to access colleagues and information sources within the country.
A number of users on UNIMA were already on email in Malawi but they used to make international calls to access email facilities abroad, such as CompuServe or CGNET. Since the UNIMA Fidonet network was established, many of these users have switched to using the UNIMA network and are finding it cheaper and more convenient since it only involves a local telephone call. (See Box 1 .)
Toward the end of 1994 and the beginning of 1995, users in non-governmental organizations and commercial companies began making up a fast-growing proportion
of the user base. These are high volume users who request and send large amounts of data over the network—mostly involving business related information. I expect that in the near future these users will be the main revenue generators for the running of the network.
Growing the Internet
With more than one hundred points on the UNIMA Fidonet network and over six hundred users, it is time for the establishment of a full Internet link in Malawi. The user base is there to support the network and our experience has shown that the users would also be able to pay the fees that such an installation would demand. At the point of writing, a leased line to South Africa seems too expensive and so we are suggesting that a VSAT connection be tried instead. VSATs or very small aperture terminals are satellites that provide two-way, high data rate services. VSATs appear to offer a low-cost telecommunication solution in developing countries.
Users on the UNIMA network indicate that they would not like flat billing. They would prefer message-by-message billing so that they pay for what they use. We will, therefore, have to carefully examine the current billing practices on UNIMA before full Internet connectivity is installed.
Equipment Shortages
The main constraint on the expansion of networks in Malawi will remain equipment based, with modems topping the list. I recommend to donors that, when projects are funded in a country like Malawi, each project should have an information technology section providing for the supply of computers and modems, when and where these are not available. Donors should also consider the expense of the installation and training of users of the information technology within the project. The minimum here should include electronic mail in any project proposal and implementation.
A project to study computer and telephone network based communications in Malawi has been in progress in the University of Malawi since 1993. Under this project a nationwide electronic network using Fidonet technology has been installed and is being expanded. The network supports electronic mail and file transfer. This is a public network in the sense that anyone or organization with the required resources can link into the network. Most of the objectives of the project have been accomplished.
The project has shown that using the installed network for electronic communications is cheaper and more convenient than existing methods, such as fax and voice telephone. It has also shown that the Fidonet software can be used to generate data on a local telephone system that can be used to monitor the performance of the local telephone network. We expect that such data will be useful to the telecommunications operating corporation.
We have had many positive and congratulatory comments on the network performance and about how it has improved the communication efficiency of our users. So while the project began as a scholarly undertaking, mostly to determine the feasibility of establishing computer and telephone-based communications at the University of Malawi, it has resulted in the provision of improved communication services throughout the country. The small amount of seed money that we received from the University has been effectively multiplied and the impact of the project has been felt far beyond what we had originally intended.
Background Summary A Global Computer Network for Change
The Association for Progressive Communications (APC) is an extensive global computer network, dedicated specifically to serving non-governmental organizations (NGOs) and activists working for social change. Composed of a consortium of international member networks, APC provides effective and efficient communications and information-sharing tools to NGOs and individuals. Member networks exchange email and participate in selected electronic conferences with over 50 partner networks worldwide. Many of these partner networks provide the only email access for NGOs in their countries. Through this global partnership, APC offers vital communication links to tens of thousands of NGOs, activists, educators, policy-makers, and community leaders in 133 countries.
APC member networks develop and maintain an informational system that allows for geographically dispersed groups to coordinate activities online at a much cheaper rate than can be done by fax, telephone, or for-profit computer networks. APC wants to assure that electronic communication tools are available to people from all regions in the world. By collaborating with over fifty partner systems in Southern countries, APC helps to increase the information flow between South and South. To further assure equitable access to computer technology, APC initiated a Women's Networking Support Program, which focuses on increasing access to networking technologies and information sources for women and women's NGOs.
The APC Networks are distinguished by the depth and quality of their information resources, by the global reach of their communication services, and by the diversity of their membership. APC developed from a dedicated grass-roots constituency
and has become a true global community. The Network provides information in several languages, including Spanish, Portuguese, Estonian, Serbian, Macedonian, Bosnian, Croation, Slovenian, Russian, English, Swedish, German, Polish, French, and Esperanto. In addition, APC provides extensive user support and training to help people access the system easily and learn to use it efficiently.
The APC Networks are designed for use by NGOs, United Nations agencies, research organizations, government departments, educational institutions, multi-stakeholder groups, and individuals who communicate with NGOs. People use APC as an information and organizing tool for a wide range of issues, including peace, human rights, public health, environmental issues, population, social and economic justice, development, education, poverty, and demilitarization.
Dial Locally, Act Globally
All APC member networks provide users with an Internet email address. APC users can communicate with any of the over 40 million people who have an Internet email address; as well as with most commercial, academic and other networks. Many APC networks provide navigational tools to help their users access information that is otherwise difficult to locate on the Internet. For example, users can access any public computer on the Internet, including universities, libraries, research institutions, and public databases. Several APC networks make information publicly available on the Internet via the Worldwide Web (WWW) and via Gopher P—a user-friendly, text-based, menu-driven information search tool. Several APC networks offer SLIP and PPP access which allows the use of a graphic interface to Internet services.
APC provides the following networking tools:
- Electronic Mail (email)
- Electronic Conferences, both private and public
- Fax and Telex
- Internet Navigation Tools: Gopher, Telnet, Worldwide Web, FTP, WAIS
- News and Information Services
- International User Directory
The APC is a community without borders. NGOs and activists worldwide use APC Networks for both their internal organizational communications as well as their public organizing efforts. In addition, many progressive news services distribute their publications electronically on the APC Networks.
Bringing the Internet to Zambia
by Neil Robinson

Neil Robinson is a Senior Communication Software Engineer with ZAMNET Communication Systems Ltd. He has been working in Zambia for six years. This case study describes the work that led to installing a full Internet link in Zambia and the attempts to make the provision of Internet services a sustainable enterprise, independent of external donor funding.
On 22 November 1994, Zambia became the fifth country in Africa (and the very first sub-Saharan country outside of South Africa) to have full access to the Internet, the world's biggest computer network. This achievement was made despite Zambia's official status as one of Africa's poorest nations and followed three years of development by the University of Zambia of an electronic mail network serving non-commercial interests within the country. It was also achieved in a country that lacks a Computer Science degree course and where advanced computer skills are scarce. However, the technological achievement is perhaps less important than the ability to meet the considerable costs of Internet connectivity from within and thus to establish a sustainable service. ZAMNET Communication Systems Limited is the company that has been established to do this.
Computer Skills in Zambia
Despite a steady increase in the numbers of computers in use in both government institutions and private companies, the number of skilled computer specialists working in Zambia is still desperately small. Top quality staff command high salaries and other benefits (housing and transport) that are beyond the reach of government-funded institutions and the majority of Zambian companies. Most of
the top computer specialists work in the financial sector or for Zambia Consolidated Copper Mines in the (up until now) well-funded mining sector. There is a growing number of small computer sales and support companies in the capital, Lusaka, but the quality of service they provide is variable. Against such a background, the number of expatriate computer specialists working within Zambia is relatively high.
Zambia's highest national qualification in computing is a three-year computer studies diploma taught by Evelyn Hone College. The University of Zambia has no computer science department so people who wish to advance to degree level have to go outside of the country. The Mathematics Department in the School of Natural Sciences does provide a Mathematics and Computing degree but their department is desperately short of computers and is unable to provide the practical experience necessary in such a course. The locally produced graduates with the strongest computing background come from the Electronic Engineering Department of the School of Engineering. Many who succeed in acquiring the necessary skills and qualifications during training overseas fail to return to Zambia for very long, if at all.
The University of Zambia
The University of Zambia (UNZA) is the larger of Zambia's two universities (the other being the Copperbelt University in Kitwe). It has a student body of some 5,000 and approximately 500 academic staff. UNZA is wholly dependent on the Zambian government for its funding, although several schools within the University benefit from international donor support for their equipment requirements.
The University uses an old IBM 4361 mainframe computer for administrative computing requirements. The systems that run on this computer (personnel, payroll, admissions, examination systems, and so on) have all been written and are maintained by the University Computer Centre, a department of about 50 staff. Some 15 of these are technical programming and analysis staff. The rest are involved in the considerable data entry and computer operations requirements of such a mainframe-based system.
The Computer Centre is also responsible for providing technical support to computer users throughout the University. Up until about four years ago, this was largely confined to support for the mainframe computer to which students and staff were given access through a small terminal room at the Computer Centre. However, as elsewhere in Zambia, the number of microcomputers in use around campus has been growing steadily and the support requirement for the repair of hardware components and for the maintenance of microcomputer applications has also grown.
The vast majority of microcomputers within the University are donated and as such there is a diverse range of models and types of computers. However, in general, there are still far too few microcomputers to distribute access to the student
level, and even in the mathematics department most student computer project work is carried out on the mainframe.
UNZA has recently embarked on a major project to downsize its administrative systems to a microcomputer-based network. A campus-wide fibre optic network is being installed to distribute the administrative tasks to the schools themselves. Once again donor supported (through the Dutch government), this should provide access to the first of the systems (student records) by the end of this year. It will also provide access for members of staff through departmental networks to the Internet, although the extent to which this happens will largely depend on the ability of each school to extend its own section of the campus network through its own buildings.
Since 1991, the Computer Centre at the University of Zambia has been the focal point for academic, non-governmental organization (NGO), and health-based email networks in Zambia. In that year, as a result of the International Development Research Centre (IDRC)-funded ESANET 1 project, Zambia was given a microcomputer and modem to provide the hub or "host" of the first University email system. The very first recorded message through this system was sent to the Baobab, an African interests network based in Washington, D.C., on 30 September 1991. This and other international messages were initially routed through the Association for Progressive Communication (APC) network in London. The first recorded user of the system was the School of Medicine's Medical Library.
The rapid growth and development of what was then known as UNZANET was assisted by an arrangement with Rhodes University of Grahamstown, South Africa which, in November 1991, began providing a link with Internet via thrice-daily, computer-to-computer telephone calls. These were paid for by UNINET, the South African Universities Network funded by the Foundation for Research and Development (FRD). This arrangement remained until December 1994, when full Internet access was achieved and by which time some 270 email points were linked to the network.
The Early Technology
From the beginning UNZANET was a Fidonet system using dial-up telephone lines to transmit messages via dedicated host computers. When UNZANET was first established in 1991, Fidonet has been successfully tried and tested in Zimbabwe and in Kenya for NGO networks. 2 Thus UNZANET was able to learn from the experiences of similar networks in the region and benefit from cooperation with them.
The UNZANET host system was configured to handle simultaneously three telephone lines attached to three separate modems. Two of these lines were direct
external lines, while the third was an internal switchboard line for users on campus and with access to an internal telephone extension. The configuration of the Fidonet system remains in place today, primarily to serve rural users and those whose telephone lines are inadequate for interactive communication. It also serves users in advance of the completion of the campus network.
UNZANET'S Traditional Users
The original users of UNZANET were the schools and departments of the University. From the very beginning, a single site address or point number 3 was allocated to each school and administrative department. In the majority of cases, computers already existed in those departments and the email facility was installed using modems supplied as part of the ESANET project. Some of the computers used were old IBM personal computers, which were still perfectly adequate for email.
From very early on, it appeared to be inevitable and desirable that initiatives in academic networking would lead to collaborations with other sectors. Without expansion of the service into other, better-funded areas, the UNZANET system could never be sustainable. The development of a non-academic user base was encouraged especially for those users who had an immediate need for communication and for those who would have a growing need for communication in the future. These users would want to be part of a longer-term, more sustainable solution. However, with UNZANET's dependence upon donor support in mind, and particularly that of UNINET, the emphasis was always on non-commercial applications.
In Zambia, following the use at the University itself, there was widespread growth in the use of email among NGOs, health institutions, and aid or development agencies. Encouragement for the first two came about through external support, while the majority of aid and development agencies were able to fund the necessary infrastructure (modems, computers and telephone lines) themselves.
UNZANET'S Free Service
One of the reasons for the rapid growth of UNZANET was the fact that it was provided as a free service. Users only had to cover the cost of local calls into the UNZANET host or access the system through the University's internal switchboard. This allowed users to ''taste" email and to experiment with it before they had to commit themselves to paying for the service. We feel that the growth of UNZANET would have been considerably slower had it been necessary to charge users from the beginning, although a culture of non-payment can have its disadvantages when a subscriber-funded service is introduced.
The Need for ZAMNET
Through the technical success of UNZANET, it was clear that email was a viable technology within Zambia. This was true not just for a rich urban elite, but also for smaller, less-wealthy organizations within Lusaka, the Copperbelt, and further afield. We had shown that email had the capacity to remove some of the communications barriers that otherwise engender a feeling of international isolation in professional communities. At the same time it was attractive to a large community of users outside of the academic sector. Email offered a fast, easy, and highly cost effective method of communicating compared to any other available technology. (See Box 1 .)
However, a free service—provided through the generosity of others—could not be sustainable. The Computer Centre of the University, with its responsibilities to the University administration, was not in a position to sell and maintain a commercial service to customers from outside of the University, nor to pay the salaries of the high quality staff that such a service would require.
By the end of 1993, users were transmitting large volumes of international messages to and from the Internet, and there was a strong desire among users of UNZANET to expand the horizons of the system. The Internet was already expanding very rapidly: more and more data, journals, and information became available in electronic from; the nature of the information being offered broadened beyond the bounds of academic interest into business and recreation; and publicity about it was reaching the popular public media. The ability to transfer large files to and from other users; to directly access remote databases and electronic libraries; and to participate in electronic conferences and other peer group discussions had become of considerable interest both within and outside of the University.
To accommodate this growth and change in direction, the basic infrastructure of the UNZANET system and the way it was funded needed to be reviewed. The Computer Centre had already perceived the need for collaboration between the University and its fellow research institutions, as well as with the commercial and
international organizations that had the resources to pay for the high quality, high volume access to information. Some of these other organizations were using UNZANET but, because they needed to transmit larger volumes of information more quickly, many had made their own direct links to their international head offices using a variety of electronic mail systems. Pooled access for these organizations to the Internet through a single service provider would clearly bring considerable cost savings, while improvements in speed and efficiency of communication, as well as the extra services available, would allow international organizations to better service their target communities.
The ZAMNET Proposal
By the middle of 1993, we made a decision to submit a proposal for donor funding to enable the University of Zambia to establish a direct link to the Internet. This was circulated among a number of major international donors but failed to attract any direct support. At the beginning of 1994, the University decided to establish a private campus company (ZAMNET Communication Systems Ltd.) to put in place the connection to the Internet and to sell access to the services that the Internet provides. Then the World Bank expressed interest in funding the ZAMNET project and agreed to fund 80 percent of the first year operating costs of the new company.
As a young campus company with no working capital aside from the grant from the World Bank, ZAMNET issued a nominal share holding, the major and controlling shareholder being the University itself. The board of directors is comprised of senior administrators from the University and the Deputy Minister of Health, with the Director of the Computer Centre as Managing Director.
The project budget was estimated at $ 150,000 and covered the cost of:
- the leased data circuit to the chosen (cheapest) point of Internet access;
- subscription paid to the service provider at that point;
- extra hardware required to provide the Internet link and to provide a service to ZAMNET's customers;
- hardware required to provide a training facility for ZAMNET's customers;
- consultancy fees for technical Internet experts to assist in the configuration of the service; and
- salaries for one administrator and two technical staff (to be met from customer fees from the beginning).
The Proposed Service
We intended to distribute Internet services to users throughout Zambia using a variety of methods including:
- local leased lines providing full Internet access to regular high-volume users with their own local area networks (LANs);
- dial-up interactive access using SLIP or PPP for urban users on good quality telephone lines; and
- Fidonet and perhaps UUCP access for users in rural areas where poor telephone quality prohibited interactive access.
We anticipated that Fidonet would continue to play an important role within Zambia providing as it did a quick, easy-to-use entry to electronic mail. It had already proved to be relatively cheap on remote trunk lines and generally reliable in a rural setting.
The Project Objectives
ZAMNET Communication Systems Ltd. came into being officially in February 1994, although it was unable to employ staff or provide a service to its customers until the following year. ZAMNET has the following objectives:
- establish a reliable link between the UNIX network at the University Computer Centre and an Internet service provider;
- procure, install, and configure all necessary hardware to provide an Internet service;
- provide an access point for customers to dial into the Internet with sufficient capacity to avoid congestion;
- provide a software package for customers to use to access the Internet through ZAMNET;
- connect the existing Fidonet service to the new Internet service, thus removing the dependence on the Fidonet-Internet gateway at Rhodes University;
- develop locally based information services for local and international access;
- provide a training facility and develop training courses for customers; and
- produce or obtain user documentation for the system.
- set up a computerized accounts system;
- determine a pricing system; and
- produce marketing materials (pamphlets, brochures, price lists, advertisements).
Although ZAMNET has been operating commercially for less than five months (at the time this report was written), the financial support from the World Bank is soon to come to an end. Thus, while in many ways the project is still ongoing, this is a good time to review progress on the ZAMNET objectives during the establishment of the Internet service to date.
Establishing the Link to the Internet
The establishment of the data communications link between Lusaka and Cape Town, critical to our service, proved very slow and time consuming. The Internet Company of South Africa or TICSA (now Internet Africa) of Cape Town had already generously agreed to carry our Internet traffic for free (for the time being) when, in April 1994, we submitted the application to the Zambian PTT for a leased, four-wire, 9600 baud, designated data circuit between our own offices in Lusaka and the TICSA offices. After the necessary surveying work, we were notified that it would be commissioned in July 1994. However technical problems over the satellite link between the Zambian earth station at Mwembeshi and Johannesburg meant that the line was not available to us to test until October of that year. Unfortunately our problems were not over.
Our original choice of modem to serve both ends of our Internet link was the Telebit Worldblazer. We had good experience with Worldblazers through our work with the Fidonet system. However when we installed the leased four-wire data circuit between Lusaka and Cape Town, we did not know that the Worldblazer is purely a two-wire modem and, therefore, unsuitable for the type of circuit that we were using. Unfortunately our email messages (our cheapest and what should have been the easiest route to assistance) to Telebit often failed to solicit a response and it required several long distance telephone and fax calls to establish the facts and to find out what options were available to overcome this problem.
Our first solution was to install hybrids to convert the four-wire circuit to two-wire over the local segment of the circuit in Cape Town and Lusaka. Both the Zambian and South African PTTs were extremely helpful in immediately inserting hybrids into their circuits. However, the resulting signal contained too much echo
for the Worldblazers to cope with and, despite the further insertion of echo suppressors into the circuit by the PTTs, the resulting signal was inadequate for the Worldblazers at either end of the circuit to communicate with each other.
Eventually, after seeking advice from various sources, we decided to purchase two (quite expensive at $1,100 each) Telebit Fastblazer modems through their South African agents. Despite the availability of email, communication with them proved as frustrating as trying to communicate with Telebit in the United States. However, eventually, two modems were purchased and installed. Alas our problems did not end there.
The line between Cape Town and Lusaka uses microwave technology as far as Johannesburg, satellite to the Lusaka earth station, microwave once again as far as Lusaka's main exchange, but then uses copper wire for the last six or seven kilometers to the University. The signal loss over this section is high and the signal coming from South Africa was already quite low. Over such a long distance, the quality of the line allocated between central Lusaka and the ZAMNET office was highly variable and it required some intensive work from the Zambian PTT to identify the very best connections to provide for our circuit. However on 22 November 1994 the line was finally strong enough to carry a signal from our mail server to the Internet and vice versa.
The line has since been quite reliable (above 95 percent), the modems training up to 14,400 baud. Although capable of connecting at 19,200 baud, it appears that the signal loss over the circuit as a whole will prevent us from achieving such speeds. When the data circuit does fail, the technical staff at the two PTTs (ZAMTEL in Zambia and TELKOM in South Africa) have been quick to respond and restore our circuit.
Procuring, Installing, and Configuring the Internet Hardware
Most problems encountered during the installation and configuration of the hardware were due to our own inexperience with UNIX and our ignorance of much of the technology with which we were dealing. The staff involved were subjected to a very steep learning curve and inevitably much of that learning was through our own mistakes. (See Box 2 .)
The Mail Server
Through the RINAF (Regional Informatics Network for Africa) project, the University Computer Centre had received two identical Olidata (Olivetti) 486 computers. One of these was pressed into service as a new Fidonet host to cope with the rapidly growing number of users accessing that host. The other was set up on the Computer Centre network as a prospective mail server (puku.unza.zm).
A copy of SCO UNIX was installed on puku and this machine was configured to run SENDMAIL (for mail delivery), to run a POP (post office protocol) server (for mail collection by ZAMNET's customers), and to exchange mail with the Fidonet host using UUCP. We experienced some difficulty finding free Internet applications software to run under SCO UNIX (a commercial product) and, when we employed an expert to assist in the configuration of our mail server, we were advised to switch to FreeBSD-2.0. This was done in December 1994—after the Internet connection had been commissioned.
FreeBSD is a relatively easy operating system to configure and to manage, but finding precompiled binary versions of Internet applications has proved difficult. Compilation of ports and patches is cumbersome for those inexperienced in UNIX and keeping abreast of the constant updates is time consuming. The only alternative free UNIX system that runs on a 486 personal computer is Linux. Having already started with FreeBSD, there are few advantages in switching at this stage.
Puku is now running as the ZAMNET name server, as well as the server for mail/POP, Gopher, and WWW. All of these services appear to be running quite well. However from a hardware point of view we have discovered that a system with eight megabytes of RAM and a 400 megabyte hard disk is insufficient to tackle the range of tasks and to serve the number of users that we are asking of puku. A gigabyte hard drive and 32 megabytes of RAM is essential on such a pivotal system within an Internet service.
The router required to connect ZAMNET to the rest of the Internet—a Cisco 3000—was provided as part of the funding of the Zambian regional node by the RINAF project. ZAMNET itself purchased a transceiver to connect this router to the ethernet network. The Cisco gave no problems in terms of configuration; however since its installation two problems have arisen.
First, one of the primary requirements of the router is to provide statistics that can be used to bill ZAMNET customers who link their networks with ZAMNET's using locally leased data circuits. Such customers are billed for all traffic carried. The data to enable this kind of billing needs to be analyzed on another computer on the network that is running UNIX. We have yet to find any software to analyze this data that will run under the FreeBSD operating system on puku, our mail server. The only such software that we have found is written for the SUN operating system
(SUNOS) and we have since been advised that nobody would attempt to do Cisco accounting on a FreeBSD system!
The second problem is in trying to increase the speed of our link to the Internet. That link currently operates at 14,400 baud. It seems that by switching to an asynchronous connection using data compression it should be possible to increase the throughout of data on our link. To do this, however, the Cisco needs to have its auxiliary port configured to operate in asynchronous mode, which in turn requires a memory upgrade and a new version of the operating system to be loaded into the increased memory. With our whole system dependent on that one router we are somewhat reluctant to attempt this upgrade.
Providing Customer Access
To provide access to the Internet service to as many of ZAMNET's customers as possible simultaneously, 20 dial-up telephone lines configured as a hunting group were installed by the Zambian PTT, and a Livingston Portmaster 2e-30 with 30 configurable ports was purchased along with 20 Zyxel U-1496 modems to connect these lines to ZAMNET.
The telephone lines were installed when a new cable was being laid into the University and there were no problems in finding 20 new lines for ZAMNET. The hunting group is functioning well, although up until now (with 193 active, paying users as at the end of June 1995), we have rarely seen as many as seven of the lines in use at one time.
The modems that the ZAMNET customers dial into were purchased by mail order directly from Zyxel in California. Dealings with that company by email were very easy. The modems were purchased before the V34 (28,800 baud) standard had been ratified and they are all set to a maximum speed of 14,400 baud. However, given that this is also maximum speed on our data circuit to the Internet, and that as yet there is no congestion on the dial-up lines, there is no disadvantage in restricting our customers to connections at this speed.
The Postmaster was chosen over a Telebit Netblazer on the grounds of its cheaper price and that its range of features was closer to our requirements. However we were unaware when purchasing the Postmaster that some of the software that is provided with it and that enables easy configuration and backup of the system would not run under the FreeBSD operating system that we are using on our mail server. The inability to back up the tables used to store user names and passwords has proved a serious weakness on two occasions when part of the user table was lost and had to be manually re-entered.
Provisions of End User Software
For ZAMNET users continuing to use the existing Fidonet service or leasing local data circuits between their own LANs and ZAMNET, we did not need to
provide any new software. The Fidonet installation had already been developed and proven over a number of years, while those linking through their own networks were responsible for their own software.
However, for our dial-up interactive customers we needed to find an easy-to-install, easy-to-use package for Windows, DOS, and Macs. When we found a set of books for each of these three categories, complete with software diskettes, we thought we had found the solution. However, we discovered that the DOS software contained a hard-coded login script that did not match the prompts provided by our Portmaster; the Mac software would not run on the systems on which we attempted to install it; and the Windows software contained frustrating bugs in its Mail program.
Software for DOS
The package distributed to DOS users is a slightly modified version of the SLIP/MINUET package developed by the University of Minnesota. While not as attractive as the Windows software, it does contain an easy-to-use mail program and a Gopher client. It lacks a WWW client and we are investigating how DOSLynx (a WWW client for DOS) might be integrated into the installation.
Software for Windows
After the frustrations encountered above, we borrowed the package distributed by GreenNet in London for their own PPP customers. Their package is based on shareware versions of the Trumpet Winsocket Manager, Eudora as a mail client, Netscape as a WWW client, plus FTP and Telnet clients. We modified this package for our own system and developed our own installation program. This package is stable, easy-to-install and has been found to be easy to use by our customers.
Software for Macs
The vast majority of computer users in Zambia use DOS-based computers. Consequently, providing support for the few Mac customers that ZAMNET has, has proved very difficult. The package distributed to Mac users is a combination of the diskette provided with the Internet Tour Guide and a second diskette obtained from GreenNet that they distribute to their own Mac users. The resulting package includes the Eudora mail client and Netscape and is very similar in its two main components to the Windows package. ZAMNET still does not possess its own Mac and so streamlining the installation is still some way off. Even copying the two distribution diskettes requires a visit to one of the two private individuals on campus who use Macs!
Integration of Fidonet and the Internet
When the Internet link was established in November 1994, we had just three weeks in which to commission the gateway between the Fidonet host and the mail server before UNINET started charging us for the use of their own gateway. On the recommendation of Bob Barad of the Baobab, we installed the new GIGO package and were pleased to find that it was very easy to install and configure, and what's more, it worked. Rhodes University had given us an experimental UUCP account and, for the three weeks prior to cutover, we polled (generated a computer call to) the Rhodes UUCP host on a regular basis. We encountered no problems with this link and the modification of the software to enable connections between the Fidonet host and our own mail server went equally well.
The only disadvantage of the link at this stage is that it requires a modern and telephone line to be dedicated to the mail server for the UUCP connections (none of our users use UUCP directly). Even using local phone calls at 14,400 baud the telephone bill for this exchange of mail between adjacent personal computers is quite high. It would be better to move this mail over the LAN if possible.
Development of Local Information Services
The zamnet gopher.
In December 1994, a Gopher server was set up (gopher.zamnet.zm) with a menu structure covering Agriculture, Engineering, Health, Communications and Networking, and ZAMNET News and Information. This proved to be a very useful way of publicizing our work and making contact and service information available to potential customers and other interested parties around the world. We also found the Gopher useful for advising our customers of the latest developments (or problems) on ZAMNET.
As customers became aware of the potential of the ZAMNET Gopher for the distribution of local information, they expressed an interest in storing their own information within its menus. To date a number of customers are paying for disk space on our Gopher server at the nominal rate of $1.00 per megabyte per month. For example:
- the National Farmers Union is providing weekly Agricultural Commodity Exchange prices;
- the Ministry of Agriculture posts regular food security and marketing bulletins; and
- the Engineering Institute of Zambia is publishing a range of information about the institute and its activities.
The Worldwide Web Server
Our knowledge of the Internet has grown and we are aware of the rapid growth of the Worldwide Web (WWW) and the trend towards storing more information in hypertext form. Around April 1995, we installed our own WWW server. The ZAMNET homepage is accessible as www.zamnet.zm and contains pointers to information about Zambia, about ZAMNET, to the ZAMNET Gopher, and to a small but growing number of pages developed for ZAMNET's customers. For example:
- articles from the Post Newspaper are currently published twice weekly before the paper actually reaches the streets;
- the Zambia National Tourist Board has published information about travel and tourism; and
- the University of Zambia has published the text of a short leaflet giving background information about the University.
We plan to develop all of these areas. In particular several commercial customers are interested in posting information about their companies and services within our WWW pages.
Provision of Training Facilities and Courses
When ZAMNET was formed in 1994, it occupied one small office within the Computer Centre. In April 1995 we got our own offices that include a training room with capacity for nine networked personal computers. The room was equipped in May with seven multimedia Compaq personal computers and we have set aside three mornings per week to provide training to ZAMNET customers.
In addition, this facility has been used to provide sensitization seminars to the staff, deans, and administration from each of the schools at the University. When not in use for training, it is open for these members of University staff to book for an hour at a time, and is also open for members of the public to use at a rate of $7.00 per hour.
User Documentation
The Internet is a new concept to many people in Zambia and there are few books or magazines about it in the bookshops in the country. Since it is important for customers to have access to information that helps them make the best use of the service they are buying, we decided to provide a book, The Internet Tour Guide , with the ZAMNET subscription. In practice, as explained above, the software included with the books has not been very useful and the books are very American in style and language. However, there are few alternatives until we can produce our own software specific guides. We have spent some time producing detailed
installation instructions for the software that we distribute and these certainly appear to have reduced the number of queries that we field during customer installation.
Computerized Accounting
The initial chart of accounts was put together by an accountant who has subsequently kept an eye on our progress. We are using Mind Your Own Business (MYOB) , a small business accounting package developed in the United States. While quite easy to use, it has been not been adaptable to the multicurrency system we operate (we accept payment in Zambian Kwacha and in U.S. Dollars). We are considering replacing it with a package better suited to our own particular requirements.
Determining a Pricing System
No two Internet service providers use the same method to charge for their services. Our own method of arriving at our fees was to draw up the budget over the next few years; decide how much emphasis we wanted to put on the basic subscription, the cost of international electronic mail, and the cost of connect time; estimate the number of customers and projected growth rate in each category; and to fiddle with the parameters until we could be sure of breaking even within one year.
Since we need to support our traditional users, we added a two-tier pricing structure for commercial and one for non-commercial customers. The resulting fee structure—which entails a signing-on fee, a basic monthly subscription, a per kilobyte charge for international email, and a per hour charge for connect time—has been well received within the country, although we have received some criticism from without. We are always reviewing these fees and plan to increase the free connect time to two hours per month. As yet ZAMNET is not sufficiently financially sound for any radical discounting of the prices.
Marketing of the Product
To promote ZAMNET to a largely unaware population, we employed a graphic artist to produce a leaflet and eight page brochure. This determined the ''corporate image" of ZAMNET and its style has been copied on price lists, business cards, and advertisements. Over 1,000 brochures have been distributed so far. Advertisements have been placed in the Times of Zambia, Productive Farming, and Profit Magazine . However such has been the interest in the Internet that ZAMNET has benefited from free publicity in articles in all three of Zambia's leading newspapers, plus a lead article in Profit Magazine .
Staff Recruitment
The recruitment of the administrator/bookkeeper with a full Association of Accounting Technicians qualification and solid accounting experience proved a lot easier than the recruitment of the technical staff, although an initial plan to recruit a part time administrator was revised when it was fully appreciated just how much would be involved in administering the ZAMNET service. (See Box 3 .)
Of only 30 applicants for the post of communications technician, six were suitable to interview. Few of these had UNIX experience, and none had any practical experience with internetworking technology. While one member of staff was recruited from the Computer Centre and had been involved in the development of the system from the beginning, the only external recruit is very much learning as he goes along.
Results, Impact and Benefits of the Project
As part of the billing process it has been necessary to gather comprehensive statistics about the use of the ZAMNET system from the very beginning. A very simple analysis of the connection time and email statistics reveals very rapid growth of the service. ZAMNET is growing at roughly the rate of one new account each day and at the current rate this will lead to ZAMNET more than doubling in size over the next twelve months.
Table 1 shows the growth in the number of interactive accounts and the connect time that those accounts have generated. Growth has been constant—with accounts connecting to ZAMNET for an average of just over four hours per month, although the average number of connections per month has increased from 38 in March to 46 in June. This increase perhaps reflects the increased regular use of the system for electronic mail rather than Internet browsing.
Table 2 shows the steady growth in the volume of email, although it should be noted that the mail volumes include mail from the Fidonet system which, unlike the connect time data, would have been present before March. Nonetheless the
TABLE 1 Growth of ZAMNET by Month, January 1995 to June 1995
TABLE 2 Growth of ZAMNET by Month, March 1995 to May 1995
volume of international mail being sent has nearly doubled in two months. This does not include incoming mail. Interestingly, while the volume of mail to international destinations has increased steadily the volume of mail to local users has remained nearly constant, perhaps reflecting the international requirements of the newer users, and the benefits of ZAMNET in economizing over traditional communication methods (fax, telephone and courier).
A Breakdown of the Users
The majority of urban users of the non-commercial Fidonet service prior to ZAMNET's formation have now subscribed to the Interactive service. Those remaining with Fidonet include:
- Users in rural areas (notably the health community) from where telephone calls to Lusaka are expensive, and telephone line quality is often too weak to support interactive communication.
- University users who will remain on the Fidonet system until the installation of the campus network has been completed.
- Long term users of the Fidonet system who are due to leave Zambia shortly and therefore do not wish to upgrade to the new interactive service.
- Some United Nations agencies that are currently planning to connect their own network directly to ZAMNET with a local leased data circuit but, in the interim, would prefer to continue to use the technology with which their users are familiar.
Looking at the geographical and categorical breakdown of the Fidonet and interactive subscribers, it is clear that the vast majority of users of both systems are Lusaka based. (See Table 3 .) While this is not surprising, the significantly smaller concentration of users on the Copperbelt, Zambia's other major urban area, is more unusual and perhaps can be explained by the greater difficulty in fully supporting a service to users who are based outside of Lusaka. It will be necessary to consider a point of presence on the Copperbelt to rectify this and also to consider ways in which greater support can be provided to rural users.
TABLE 3 Users by Province
Analysis of the new interactive subscribers by category is particularly difficult. (See Table 4 .) Beyond learning that companies are commercial, no attempt has been made to determine the line of work in which a subscribing company is involved. Many of the private individuals joining ZAMNET as non-commercial subscribers are attached to development organizations or international NGOs and use their points professionally. Again we have made no attempt to survey the uses made of email and so further analysis is impossible.
TABLE 4 Users by Category
Apart from the 55 private individual accounts and 46 commercial accounts, the largest category among the rest of the accounts is in health. As indicated by the number of accounts still using Fidonet, many health and agriculture accounts were users of the previous non-commercial service. Since the new ZAMNET service was put in place there has been a growing interest from a number of religious organizations active in Zambia (most of whom have head offices in the United States or Europe), and encouragingly recent interest from the Ministries of Finance and of Foreign Affairs.
ZAMNET has received very positive feedback from its customers within and outside of Zambia. Zambian expatriates write to us saying how proud they feel that Zambia is only the fifth African country to establish a full Internet service. Starved on information about their home country, they are eager to see expanded news and information services through ZAMNET.
ZAMNET customers within Zambia are particularly pleased with the cost savings that communicating by email has brought. With international telephone calls to North America and Europe billed at $7.00 per minute, the ability to make a cheap local telephone call and send an email message for about 20 cents per page is very attractive. To find that this message is delivered reliably and within minutes is an added bonus. (See Box 4 .)
Media Coverage
As the Internet has received more and more coverage in the international media, ZAMNET has correspondingly come under the spotlight within Zambia.
The Zambia Daily Mail , the Times of Zambia , and the Weekly Post have all published articles about the Internet and its arrival in Zambia (the Post subsequently subscribing to the ZAMNET service). Profit Magazine , Zambia's leading business magazine published a full leading article about ZAMNET complete with a front page image of some example WWW pages captured from the Internet.
The Zambia National Broadcasting Corporation has regular computing and business programs that make reference to information technology and the Internet. We hope that a full interview with the Managing Director of ZAMNET will be broadcast soon, while plans exist to connect ZNBC to ZAMNET in the near future.
Further afield, the efforts that Zambia has made to provide an email service and to establish a full Internet connection have been mentioned several times on the African service of the BBC World Service. In fact when the BBC began using email and started accepting questions to their Pop Science program, the very first email question that they received came from an email user in Ndola, Zambia.
Just four months after the ZAMNET product was made available to the public, its existing infrastructure is already creaking. Its communications link to the rest of the Internet is becoming congested at certain times of the day. Its mail server is overloaded and does not have the memory or disk capacity to cope with a significant increase in either the number of ZAMNET customers, or in the number of Internet users from outside of Zambia accessing its information services. Without a doubt the main area where ZAMNET might have been launched differently was in its technical capacity.
Capital Funding
ZAMNET's initial budgets should have been significantly higher and included items vital to the provision of a high quality, high volume, large customer base service. Namely, in hindsight, we should have begun with a SUN workstation, VSAT communications, a router capable of handling asynchronous communication, and a full set of equipment to provide backup in the event of system failures. While these items would have increased the initial cost of ZAMNET significantly, repayment of that cost could have been spread over a number of years.
Staff Training
Providing technical support from a position of considerable inexperience has been difficult. While the staff currently in place are learning fast, sustainability of the ZAMNET service is not only dependent upon them but also on the availability of suitable staff to supplement and replace the existing staff in the future. With this
in mind there needs to be greater opportunities for Zambians to learn about Internet technology without having to travel outside of the region.
ZAMNET is providing an important and much needed service to all sectors of Zambian society:
- businesses and industries need a fast, reliable and economical communications system in order to compete within the newly liberalized Zambian economy;
- international development organizations need to keep in regular touch with their projects in the field and their head offices overseas;
- the academic sector and researchers need access to the latest research and need to keep abreast of international developments in their field;
- government ministries need an efficient means of communication with district and provincial offices in the fields of agriculture, health and education; and
- private individuals wish to keep in touch with their friends abroad or simply wish to use the Internet as a vast encyclopedia.
Both commercial and non-commercial customers have shown a willingness to pay the fees that ZAMNET has set in order to cover the considerable costs of its service.
Because its customers now rely upon its service, ZAMNET needs to ensure its future both technically and economically. At the current, very fast growth rate, the system will be overstretched within twelve months, by which time the customer base should have more than doubled to over 600 accounts. The resulting reduced performance could seriously damage the positive image of ZAMNET. Meanwhile the lack of technical backup within the system leaves the whole service vulnerable in the event of an equipment failure. The downside of this is the capital expenditure involved in safeguarding against possible disasters. ZAMNET urgently needs to look at ways it can improve and upgrade its services.
Increasing the Bandwidth
The capacity of the Internet link between Lusaka and Cape Town will not be able to support 20 simultaneously connected users without a significant and noticeable deterioration in performance. The most promising option for increasing the capacity of this link appears to be a direct VSAT link from the ZAMNET offices in Lusaka to our Internet service provider in Cape Town, or failing that, an alternative link direct to the United States or United Kingdom. Although continued cooperation with counterparts in the region would be desirable, progress in
negotiations with Telkom (the South African PTT) have not been productive so far.
Based on the cost estimates provided so far, we know that the hardware costs of a VSAT link, plus annual rental and license fees should prove cheaper than the line we are leasing from ZAMNET and TELKOM at a cost of over $60,000 per year. The disadvantages of this strategy will be the expertise expected of the technical support staff and the cost of paying for both the existing and the VSAT link during the transition. Indeed it may be desirable to maintain the existing link to provide redundancy in the event of failure of the VSAT connection.
Increasing Dial-up Access
With the current customer base, we have rarely observed more than eight ports on the Portmaster modem server active simultaneously. Further expansion to serve 600 customers, while also accommodating increased activity among the existing users, is likely to put severe pressure on our dial-up. This expansion can only be accommodated through the purchase of a second modem server and a further batch of dial-up telephone lines. Over the next year a number of leased line customers will also subscribe to ZAMNET thus putting further pressure on the number of free ports available on the existing system.
Covering for Equipment Failures
The current system is highly vulnerable in the event of any kind of equipment failure. ZAMNET service would be lost in the event of:
- the loss of the leased line modem at either end of the data circuit that links ZAMNET to the Internet;
- the loss of the router linking the ZAMNET LAN to the Internet; or
- the loss of the Portmaster providing local access to the Internet to ZAMNET customers.
None of this equipment is readily available within Zambia and, even if finances were available, the resulting loss of service while replacements were being shipped from abroad could last for several days and have a serious impact on the image of ZAMNET among its customers. Spare items to replace those listed above would cost about $8,000.
Increase Capacity on Mail and Information Servers
The current mail server is running on a 40 MHz 486 PC with just 8 megabytes of RAM and a 400 megabyte hard disk and is already overloaded. As the number of customers and the volume of local information being provided to users outside of Zambia increases, the burden on this machine will also increase. A
second machine is currently being configured as a News Server to accommodate the growing number of useful log files that the system generates. However this machine is itself only a 25 MHz personal computer, albeit with a one gigabyte hard drive.
ZAMNET needs to invest in a much more powerful personal computer with at least 32 megabytes of RAM and another high capacity hard drive. Ideally ZAMNET would seek to obtain a SUN workstation or equivalent, which is capable of running some of the software needed for maintaining the Portmaster and for monitoring traffic passing through the Cisco router. However the cost of such a SUN machine would be $10,000 or more!
Expanding the Range of Provided Services
There is an immediate need to provide a News Server to enable ZAMNET's customers to participate in the many discussion groups available over the Internet. Work to configure such a Server is currently under way, although the impact of a full news feed on the limited bandwidth of the Internet connection has yet to be determined. It is likely that such a feed would be dependent on the implementation of the VSAT link.
As the Internet develops further, other applications will be developed and ZAMNET needs to be in a position to make these applications available to its customers (within the limitations of the bandwidth of its Internet connection). Current examples include "Real Audio" and the ability to communicate by voice over the Internet.
Increasing Technical and Administrative Support
ZAMNET currently employs just three staff, one administrator and two technical support staff. This team is severely stretched in its efforts to provide support and to develop the ZAMNET staff. We have decided to employ an assistant administrator to ease the workload.
With the anticipated growth, it will be important for ZAMNET to employ at least one additional skilled and experienced technical member of staff within the next twelve months. With both the contracts of the ZAMNET technical staff due for renewal at the same time, the possible impact of these employees departing at the end of their contracts also needs to be anticipated.
Looking Forward
This chapter was written in June 1995 and I want to provide a quick update. By January 1996, ZAMNET had grown to accommodate 417 interactive accounts. These accounts generated 9,558 connections totalling 1,600 hours of connect time and 12,862 international messages. This is a growth rate of 100 percent in just
eight months. We have taken several steps to ease the growing congestion on both the Internet link and the server computers and to provide protection in the event of system failures:
We ordered the VSAT terminal equipment and it has been shipped from the United States. We need to complete some administrative procedures before it can be used but we hope that a 64 kilobaud VSAT connection direct from ZAMNET's offices to Johannesburg will be operational before the end of March 1996.
We maintain the Portmaster users table on the WWW server machine using Livington's Radius software.
We moved the WWW server from the mail server to a second computer, which has been configured as a News Server, although we still do not receive a full news feed from the Internet. We just ordered a new mail server (a Pentium 120 with 32 megabytes of RAM and a 2 gigabyte hard drive).
We have recruited a new assistant administrator.
Within the next year ZAMNET plans to increase the number of access telephone lines to 40 and purchase an extra 20 V34 modems and a second Portmaster to serve these lines; employ two additional technical staff, a marketing manager, and another junior administrator; and provide local telephone access to customers based in the Copperbelt.
We have proven that the provision of an Internet service is viable and can pay for itself. The costs of expansion require capital expenditure and, ultimately, an injection of capital from investors either in the form of loans or in the broadening of shareholding is required. Most importantly, however, several months before the end of the World Bank funding, ZAMNET is self-sufficient and is able to buy new equipment from its own funds and to guarantee repayment on any loans it requires. This healthy position should enable ZAMNET to significantly reduce its fees within the next three months and to continue to expand services to meet it customers' demands.
This volume tells 16 remarkable stories—first person accounts of how information and communication technologies have been successfully introduced into institutions for the benefit of scientists and engineers in sub-Saharan Africa. These case studies focus on the lessons learned in designing and implementing projects dealing with scientific and technological information and examine the impact.
READ FREE ONLINE
Welcome to OpenBook!
You're looking at OpenBook, NAP.edu's online reading room since 1999. Based on feedback from you, our users, we've made some improvements that make it easier than ever to read thousands of publications on our website.
Do you want to take a quick tour of the OpenBook's features?
Show this book's table of contents , where you can jump to any chapter by name.
...or use these buttons to go back to the previous chapter or skip to the next one.
Jump up to the previous page or down to the next one. Also, you can type in a page number and press Enter to go directly to that page in the book.
Switch between the Original Pages , where you can read the report as it appeared in print, and Text Pages for the web version, where you can highlight and search the text.
To search the entire text of this book, type in your search term here and press Enter .
Share a link to this book page on your preferred social network or via email.
View our suggested citation for this chapter.
Ready to take your reading offline? Click here to buy this book in print or download it as a free PDF, if available.
Get Email Updates
Do you enjoy reading reports from the Academies online for free ? Sign up for email notifications and we'll let you know about new publications in your areas of interest when they're released.
Networking Success Stories: Case Studies

Learning from the Best: Insights and Inspiration from Networking Success Stories
You might be wondering how networking can amplify your business reach and success. Given the digital age, leveraging connections—both online and offline—is crucial for professional growth.
This article delves into six case studies exploring how companies have utilized networking to acquire innovation, manage customer data, gain competitive advantages and more. Ready? Let’s dive into success stories that will inspire you to bring your networking game to new levels!
Key Takeaways
- Successful networking can open doors to opportunities and resources that accelerate professional growth.
- Social media platforms have revolutionized networking, allowing professionals to connect with colleagues, clients, and partners across the globe.
- Networking has played a crucial role in the success of companies like Epic Games, Salesforce, Scuderia Ferrari, and NatWest Bank.
- Leveraging networking can drive innovation, create competitive advantages, personalize customer experiences, optimize operational costs, enhance security measures, and improve service delivery.
Importance of Networking
Networking plays a crucial role in professional growth, connecting individuals to opportunities and resources that can accelerate their careers.
The role of connections in professional growth
Networking holds the key to professional growth. Strong connections can open doors to opportunities that would otherwise remain closed. Extensive networks allow professionals to exchange ideas, discuss challenges, and share expertise with peers across industries or around the globe.
The result is an increase in knowledge and competencies that drive career progression. Many successful companies such as Epic Games have leveraged their business networks for innovation, demonstrating the significant role of connections in driving professional growth and success.
The power of social media in networking
Social media platforms have revolutionized the networking landscape. With just a click, professionals can now connect with colleagues, clients, or potential partners across the globe.
Companies like 99Bridges and COVID-19 have effectively used social media to expand their network and collaborate without geographical barriers.
Twitter allows influencers in every industry to share insights on trending topics. LinkedIn facilitates business relationships development while Instagram gives brands an opportunity to visually engage with customers.
Facebook not only offers advertising options but also enables businesses to create groups where they can interact directly with their consumers. Indeed, these dynamic interactions fostered by social media play a crucial role in digital transformation, ultimately leading toward greater success for companies wide and far-reaching into diverse regions and industries.
Case Study 1: Epic Games
Epic Games demonstrates how leveraging networking has led to innovation, with a key role played by AWS in their success.
How leveraging networking led to innovation
Epic Games utilized their extensive network to drive innovation, creating industry trends instead of just following them. Through collaborations with strategic partners like AWS, they explored uncharted territories in gaming technology.
This specific approach unveiled new opportunities for growth and diversification, allowing the company to maintain a leading position within its sector. Leveraging networking also fostered a culture of idea sharing and teamwork that propelled further advancement within Epic Games.
The role of AWS in Epic Games’ success
Epic Games, the company behind the popular Fortnite game, dramatically increased their networking capabilities due to a strategic partnership with AWS. Utilizing high-performance and low-latency connections provided by AWS, Epic Games successfully cultivated an online gaming environment capable of supporting millions of players simultaneously.
This robust infrastructure not only improved user experience but also allowed the gaming giant to concentrate on innovation and game development. The secure and scalable solutions offered by AWS played a vital role in propelling Epic Games towards monumental success in the competitive gaming market.
Case Study 2: Salesforce
Salesforce utilized networking as a tool for customer data management, leveraging the power of connections to create a single source of truth and drive their success.
The power of a single source of truth
A single source of truth can be incredibly powerful for organizations. It ensures that everyone has access to accurate and consistent data, leading to improved decision-making and streamlined processes.
Companies like Salesforce have implemented a single source of truth through their platform, allowing businesses to eliminate data discrepancies and redundancies. This not only improves efficiency but also enhances data integrity, which is crucial for making informed business decisions.
By centralizing information in one place, organizations can harness the power of a single source of truth to drive success and achieve their goals more effectively.
Networking as a tool for customer data management
Networking plays a crucial role in customer data management, as highlighted in Case Study 2: Salesforce. By leveraging networking strategies, companies can effectively collect, store, and analyze customer data to gain valuable insights and enhance their overall business operations.
Implementing IoT solutions, monitoring and analytics tools, and cloud computing solutions are just some of the ways organizations can optimize their network infrastructure for efficient customer data management.
This enables businesses to provide personalized experiences, improve decision-making processes, and ultimately drive customer satisfaction and loyalty.
Case Study 3: Scuderia Ferrari
Scuderia Ferrari leveraged networking for competitive advantage and utilized AI and ML to enhance their networking strategies.
Networking for competitive advantage
Scuderia Ferrari understands the power of networking to gain a competitive advantage in the fast-paced world of racing. By collaborating with AWS, they are able to analyze race data in real-time and make strategic decisions that optimize their performance on the track.
This partnership allows Scuderia Ferrari to leverage advanced technologies like AI and ML, which enable them to extract valuable insights from their race data. Through networking and utilizing cutting-edge tools, Scuderia Ferrari proves that staying ahead in the competitive sports industry requires continuous innovation and collaboration with technology experts.
The role of AI and ML in networking
AI and ML technologies have a pivotal role in networking, including the operations of Scuderia Ferrari. These advanced technologies enable the team to analyze and optimize network traffic and data flow, improving overall network performance and efficiency.
By leveraging AI and ML, real-time adjustments can be made to ensure better race performance. Additionally, these technologies play a crucial role in facilitating reliable and secure communication between team members and drivers.
The use of AI and ML in networking not only enhances connectivity but also enables teams like Scuderia Ferrari to stay ahead in their competitive arena.
Case Study 4: NatWest Bank
NatWest Bank personalized customer experience through networking and reduced operational costs.

Personalizing customer experience through networking
NatWest Bank is committed to providing a personalized customer experience through networking. By implementing networking solutions, they have tailored their services to meet the individual needs of each customer.
Through this approach, NatWest Bank has been able to offer a more seamless and customized banking experience. Networking has played a pivotal role in helping them better understand and anticipate customer preferences, resulting in stronger relationships and increased customer loyalty.
The impact on operational costs
NatWest Bank’s implementation of networking solutions has had a significant impact on their operational costs. By leveraging these solutions, the bank has been able to improve operational efficiency and streamline processes, resulting in cost savings.
While the specific networking solutions used by NatWest Bank are not mentioned in the article, it is clear that their adoption has yielded positive outcomes for the bank’s bottom line.
This case study underscores the importance of implementing effective networking solutions to optimize operational costs and drive financial success.
Networking Challenges and Solutions
Staying connected: strategies for maintaining networks, the value of meaningful interactions in networking, and asking the right questions to ensure effective networking.
Staying connected: strategies for maintaining networks
Staying connected is crucial for maintaining networks. Here are some strategies to help you stay connected:
- Regularly reach out to your network: Make it a habit to connect with your contacts on a regular basis. This can be through email, phone calls, or even meeting up in person.
- Attend networking events: Take advantage of industry conferences, seminars, and other events to meet new people and expand your network. These events provide opportunities for meaningful interactions and potential collaborations.
- Utilize social media: Social media platforms like LinkedIn, Twitter, and Facebook can be powerful tools for staying connected with your network. Stay active by sharing relevant content, engaging with others’ posts, and joining relevant groups or communities.
- Nurture relationships: Building strong relationships requires effort and time. Take the time to follow up with contacts, show genuine interest in their work, and offer support whenever possible.
- Provide value to your network: Offer assistance or share valuable resources with your contacts whenever you can. This helps build trust and establishes you as a valuable connection.
- Seek out mentorship opportunities: Mentors can provide guidance, advice, and support throughout your career journey. Actively seek out mentors within your industry who can help you navigate challenges and provide insight.
- Stay updated on industry trends: Keeping yourself informed about the latest developments in your field allows you to engage in meaningful conversations with others within your network.
The value of meaningful interactions in networking
Meaningful interactions play a crucial role in networking. It is not just about collecting contacts or making surface-level connections; it’s about building relationships that have a lasting impact.
When professionals engage in meaningful conversations, they create opportunities for collaboration, mentorship, and growth. Meaningful interactions allow individuals to exchange ideas, gain insights from others’ experiences, and even find new career opportunities.
By fostering genuine connections with others in their industry or field, professionals can expand their knowledge base and access valuable resources. These interactions can lead to partnerships, referrals, and ultimately contribute to long-term success in networking endeavors.
Asking the right questions: a key to effective networking
Asking the right questions is a crucial skill for successful networking. By understanding what to ask and how to ask it, you can gather valuable information, establish meaningful connections, and open up opportunities for collaboration.
Effective questioning helps you delve deeper into conversations, uncover common interests or goals, and demonstrate genuine interest in others. By asking thoughtful and relevant questions, you show that you value the perspectives of others and are actively engaged in building relationships.
This not only strengthens your network but also allows you to gather insights and knowledge that can contribute to your professional growth.
In order to make the most out of your networking interactions, it is important to approach conversations with curiosity and an open mind. By focusing on asking insightful questions rather than simply talking about yourself or making small talk, you can foster meaningful connections that go beyond surface-level interactions.
Case Study 5: Alpha Omega
Alpha Omega, a tech company focused on meeting public demands, utilized networking to upskill its workforce in AWS and drive professional development.
Upskilling in AWS to meet public demands
Alpha Omega Integration recognized the importance of staying updated with the latest technologies in the networking industry. To meet the increasing demands of the public sector, they upskilled their employees using AWS Partner Training and Certification.
This commitment to continuous improvement allowed Alpha Omega to showcase their ability to address unique challenges and requirements in networking, ultimately leading to client satisfaction and business success.
By implementing AWS solutions, Alpha Omega demonstrated their dedication to meeting public demands effectively in a rapidly evolving industry.
The role of networking in professional development
Networking plays a crucial role in professional development, both for individuals and organizations. Building and maintaining a strong network of connections can open doors to new opportunities, collaborations, and resources.
Networking allows professionals to exchange knowledge, skills, and experiences with others in their field, helping them stay updated on industry trends and best practices. By connecting with experts and influencers, professionals can gain valuable insights and guidance that can accelerate their growth.
Additionally, networking provides a platform for showcasing one’s expertise and accomplishments, which can enhance career prospects and visibility within the industry. Ultimately, networking serves as a catalyst for continuous learning, personal growth, and advancement in the professional world.
Case Study 6: DeepThink Health
DeepThink Health strengthened their security through networking, resulting in improved healthcare service delivery.
Strengthening security through networking
DeepThink Health, a case study focused on strengthening security through networking, showcases the implementation of cloud and computing solutions, security solutions, and networking solutions.
By leveraging Cisco’s products and services, DeepThink Health has successfully enhanced their security measures. They have implemented cloud and computing solutions as well as monitoring and analytics solutions to strengthen their overall network security.
Collaboration, customer experience improvement, and digital transformation play crucial roles in achieving this goal. The case study demonstrates the effectiveness of Cisco’s offerings in the healthcare industry by highlighting successful implementations of networking solutions to enhance security measures at DeepThink Health.
The impact on healthcare service delivery
DeepThink Health has had a remarkable impact on healthcare service delivery. This case study showcases how networking solutions have transformed the way healthcare providers operate and deliver care.
While specific details are not provided, it is clear that DeepThink Health addresses challenges faced by healthcare providers in terms of networking, ultimately leading to improved efficiency, communication, and patient outcomes.
The positive influence of these networking solutions highlights the immense potential for technology to revolutionize the healthcare industry and enhance overall service delivery.
The Future of Networking
The future of networking is shaped by emerging trends and the role of technology in connecting individuals and businesses.
Emerging trends in networking
- Networking is evolving with emerging trends that are shaping the future of connectivity.
- Cloud computing is playing a vital role in networking, providing scalable and flexible solutions for businesses.
- Software – defined networking (SDN) is gaining popularity, allowing organizations to manage and control their networks through software rather than hardware.
- The Internet of Things (IoT) is revolutionizing networking by connecting devices and enabling real – time data exchange.
- Network automation is streamlining operations, reducing manual tasks, and improving efficiency.
- Artificial intelligence (AI) and machine learning (ML) are being integrated into networks to enhance security, detect anomalies, and optimize performance.
- Edge computing is becoming essential as more data is generated at the edge of networks, requiring processing closer to the source.
- 5G technology is set to revolutionize networking by providing faster speeds, lower latency, and increased capacity for connected devices.
- Network virtualization allows for the creation of virtual networks within physical infrastructures, offering flexibility and cost savings.
- Cybersecurity remains a top concern in networking, leading to advancements in network security solutions and practices.
- Emerging trends in networking are showcased through the “This Is My Architecture” program by AWS
- The architectural solutions showcased in “This Is My Architecture” demonstrate the technical capabilities of AWS
The role of technology in shaping networking
Technology plays a pivotal role in shaping networking strategies and success. With advancements in IoT, monitoring and analytics, cloud computing, collaboration tools, and security solutions, organizations have the power to transform their networking environments.
Technologies like Meraki Firewalls and Wireless Access Points cater specifically to the needs of small businesses, offering reliable and scalable networking solutions. Additionally, solutions such as Duo for secure authentication and Umbrella for enhanced network security contribute to creating robust and safe networking environments.
By leveraging technology effectively, businesses can optimize their networks for efficiency, productivity, and growth while staying ahead in today’s digital landscape.
Discovering the power of networking through real-life case studies can be inspiring and eye-opening. These success stories from companies like Epic Games, Salesforce, Scuderia Ferrari, NatWest Bank, Alpha Omega, and DeepThink Health demonstrate how strategic networking can lead to innovation, competitive advantage, personalized customer experiences, professional development, enhanced security, and improved service delivery.
By leveraging connections and staying connected in meaningful ways, organizations can unlock new opportunities for growth and success in the ever-evolving business landscape.

Data Communication and Networking Notes, PDF | B Tech (2024)
- Post last modified: 11 January 2023
- Reading time: 28 mins read
- Post category: B Tech Study Material

Download Data Communication and Networking Notes PDF, syllabus for B Tech, BCA, MCA (2024). We provide complete data communication and networking pdf . Data Communication and Networking lecture notes include data communication and networking notes, data communication and networking book , data communication and networking courses, data communication and networking syllabus , d ata communication and networking question paper , MCQ, case study, questions and answers and available in data communication and networking pdf form.

Data Communication and Networking subject are included in B Tech CSE, BCA, MCA, M Tech. So, students can able to download data communication and networking notes pdf.
Table of Content
- 1 Data Communication and Networking Syllabus
- 2 Data Communication and Networking PDF
- 3.1 What is Data Communication and Networking?
- 4 Data Communication and Networking Interview Questions
- 5 Data Communication and Networking Question Paper
- 6 Data Communication and Networking Book
Data Communication and Networking Notes can be downloaded in data communication and networking pdf from the below article
Data Communication and Networking Syllabus
Detailed data communication and networking syllabus as prescribed by various Universities and colleges in India are as under. You can download the syllabus in data communication and networking pdf form.
Introduction : Data Communications, Networks, Network Types, Internet History, Standards and Administration, Networks Models: Protocol Layering, TCP/IP Protocol suite, The OSI model, Introduction to Physical Layer-1: Data and Signals, Digital Signals, Transmission Impairment, Data Rate limits, Performance, Digital Transmission: Digital to digital conversion (Only Line coding: Polar, Bipolar and Manchester coding).
Physical Layer : Analog to digital conversion (only PCM), Transmission Modes, Analog Transmission: Digital to analog conversion, Bandwidth Utilization: Multiplexing and Spread Spectrum, Switching: Introduction, Circuit Switched Networks and Packet switching.
Error Detection and Correction : Introduction, Block coding, Cyclic codes, Checksum, Forward error correction, Data link control: DLC services, Data link layer protocols, HDLC, and Point to Point protocol (Framing, Transition phases only).
Media Access control: Random Access, Controlled Access and Channelization, Wired LANs Ethernet: Ethernet Protocol, Standard Ethernet, Fast Ethernet, Gigabit Ethernet and 10 Gigabit Ethernet. Unit V – Wireless Networks WIMAX, Cellular Telephony, Satellite networks, Wireless LANs: Introduction, IEEE 802.11 Project and Bluetooth.
Data Communication and Networking PDF
Data communication and networking notes, what is data communication and networking.
Data communications refer to the transmission of this digital data between two or more computers and a computer network or data network is a telecommunications network that allows computers to exchange data.

Data Communication and Computer Network (DCN) and will also take you through various advance concepts related to Data Communication and Computer Network.
Data Communication and Networking Interview Questions
Some of the data communication and networking questions and answers are mentioned below. You can download the QnA in data communication and networking pdf form.
- What Is Data Communications?
- What Is The Effect Of Noise?
- What Is Crosstalk?
- Explain Modulation?
- What Is Analog?
- Explain Data Encryption?
- What is Data Compression?
- Explain Parity And Checksums?
- Explain Asynchronous Vs. Synchronous Transmission?
- Explain Communications Channels?
Data Communication and Networking Question Paper
If you have already studied the data communication and networking notes , now it’s time to move ahead and go through previous year data communication and networking question paper .
It will help you to understand question paper pattern and type of data communication and networking questions and answers asked in B Tech, BCA, MCA, M Tech data communication and networking exam. You can download the syllabus in data communication and networking pdf form.
Data Communication and Networking Book
Below is the list of data communication and networking book recommended by the top university in India.
- Behrouz A. Forouzan, Sophia Chung Fegan, “Data Communications and Networking”, Fifth Edition, Science Engineering & Math Publications, 2012.
- William Stallings, “Data and Computer Communications”, Eighth Edition, Pearson Education India, 2007.
Download B Tech (CS) Study Material
Computer Networks Notes ✅ [2020] PDF – Download
Computer Networks Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Computer Networks Notes )
Computer Graphics Notes ✅ [2020] PDF – Download
Computer Graphics Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Computer Graphics Notes )
Operating System Notes ✅ [2020] PDF – Download
Operating System Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Operating System Notes )
Compiler Design Notes ✅ [2020] PDF – Download
Compiler Design Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Compiler Design Notes )
Data Structures Notes ✅ [2020] PDF – Download
Data Structures Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Data Structures Notes )
Digital Image Processing Notes ✅ [2020] PDF – Download
Digital Image Processing Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Digital Image Processing Notes )
Theory of Computation Notes ✅ [2020] PDF – Download
Theory of Computation Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Theory of Computation Notes )
Computer Organization and Architecture Notes ✅ [2020] PDF – Download
Computer Organization and Architecture Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Computer Organization and Architecture Notes )
Cloud Computing Notes ✅ [2020] PDF – Download
Cloud Computing Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Cloud Computing Notes )
Data Communication and Networking Notes ✅ [2020] PDF – Download
Data Communication and Networking Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Data Communication and Networking Notes )
Software Engineering Notes ✅ [2020] PDF – Download
Software Engineering Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Software Engineering Notes )
Web Technologies Notes ✅ [2020] PDF – Download
Web Technologies Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Web Technologies Notes )
Microprocessor and Microcontrollers Notes ✅ [2020] PDF – Download
Microprocessor and Microcontrollers Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Microprocessor and Microcontrollers Notes )
Design and Analysis of Algorithm Notes ✅ [2020] PDF – Download
Design and Analysis of Algorithm Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Design and Analysis of Algorithm Notes )
Operation Research Notes ✅ [2020] PDF – Download
Operation Research Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Operation Research Notes )
Database Management Systems Notes ✅ [2020] PDF – Download
Database Management Systems Notes [2020] PDF, Syllabus, PPT, Book, Interview questions, Question Paper ( Download Database Management Systems Notes )
In the above article, a student can download data communication and networking notes for B Tech, BCA, MCA, M Tech . Data Communication and Networking lecture notes and study material include data communication and networking notes , data communication and networking books , data communication and networking syllabus , data communication and networking question paper , data communication and networking case study , data communication and networking interview questions , data communication and networking courses in data communication and networking pdf form.
Go On, Share & Help your Friend
Did we miss something in B.Tech Computer Science Notes or You want something More? Come on! Tell us what you think about our post on Data Communication and Networking Notes | PDF, Syllabus, Book | B Tech, M Tech in the comments section and Share this post with your friends.
You Might Also Like
Digital communication notes | pdf, syllabus | b tech 2021.

Web Technologies Notes | PDF, Syllabus, Book | B Tech 2021
Analog communication pdf | notes, syllabus b tech 2021, network programming notes | pdf, syllabus | b tech 2021, business intelligence notes | pdf, syllabus | b tech 2021, signals and systems notes | pdf, syllabus, book | b tech (2024), java programming notes pdf, syllabus | b tech 2021.

Theory of Computation Notes | PDF, Syllabus | B Tech 2021
How to download notes on geektonight.

Database Management Systems Notes | PDF | B Tech 2021

Computer Networks Notes | PDF, Syllabus, Books | B Tech (2024)
![case study on data communication and networking Read more about the article Operating Systems Notes | PDF, Book, Syllabus | B Tech [2021]](https://www.geektonight.com/wp-content/uploads/2020/03/Operating-Systems-Notes-300x150.jpg)
Operating Systems Notes | PDF, Book, Syllabus | B Tech [2021]
Leave a reply cancel reply.
You must be logged in to post a comment.
World's Best Online Courses at One Place
We’ve spent the time in finding, so you can spend your time in learning
Digital Marketing
Personal growth.

Development
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Sensors (Basel)

Study and Investigation on 5G Technology: A Systematic Review
Ramraj dangi.
1 School of Computing Science and Engineering, VIT University Bhopal, Bhopal 466114, India; [email protected] (R.D.); [email protected] (P.L.)
Praveen Lalwani
Gaurav choudhary.
2 Department of Applied Mathematics and Computer Science, Technical University of Denmark, 2800 Lyngby, Denmark; moc.liamg@7777yrahduohcvaruag
3 Department of Information Security Engineering, Soonchunhyang University, Asan-si 31538, Korea
Giovanni Pau
4 Faculty of Engineering and Architecture, Kore University of Enna, 94100 Enna, Italy; [email protected]
Associated Data
Not applicable.
In wireless communication, Fifth Generation (5G) Technology is a recent generation of mobile networks. In this paper, evaluations in the field of mobile communication technology are presented. In each evolution, multiple challenges were faced that were captured with the help of next-generation mobile networks. Among all the previously existing mobile networks, 5G provides a high-speed internet facility, anytime, anywhere, for everyone. 5G is slightly different due to its novel features such as interconnecting people, controlling devices, objects, and machines. 5G mobile system will bring diverse levels of performance and capability, which will serve as new user experiences and connect new enterprises. Therefore, it is essential to know where the enterprise can utilize the benefits of 5G. In this research article, it was observed that extensive research and analysis unfolds different aspects, namely, millimeter wave (mmWave), massive multiple-input and multiple-output (Massive-MIMO), small cell, mobile edge computing (MEC), beamforming, different antenna technology, etc. This article’s main aim is to highlight some of the most recent enhancements made towards the 5G mobile system and discuss its future research objectives.
1. Introduction
Most recently, in three decades, rapid growth was marked in the field of wireless communication concerning the transition of 1G to 4G [ 1 , 2 ]. The main motto behind this research was the requirements of high bandwidth and very low latency. 5G provides a high data rate, improved quality of service (QoS), low-latency, high coverage, high reliability, and economically affordable services. 5G delivers services categorized into three categories: (1) Extreme mobile broadband (eMBB). It is a nonstandalone architecture that offers high-speed internet connectivity, greater bandwidth, moderate latency, UltraHD streaming videos, virtual reality and augmented reality (AR/VR) media, and many more. (2) Massive machine type communication (eMTC), 3GPP releases it in its 13th specification. It provides long-range and broadband machine-type communication at a very cost-effective price with less power consumption. eMTC brings a high data rate service, low power, extended coverage via less device complexity through mobile carriers for IoT applications. (3) ultra-reliable low latency communication (URLLC) offers low-latency and ultra-high reliability, rich quality of service (QoS), which is not possible with traditional mobile network architecture. URLLC is designed for on-demand real-time interaction such as remote surgery, vehicle to vehicle (V2V) communication, industry 4.0, smart grids, intelligent transport system, etc. [ 3 ].
1.1. Evolution from 1G to 5G
First generation (1G): 1G cell phone was launched between the 1970s and 80s, based on analog technology, which works just like a landline phone. It suffers in various ways, such as poor battery life, voice quality, and dropped calls. In 1G, the maximum achievable speed was 2.4 Kbps.
Second Generation (2G): In 2G, the first digital system was offered in 1991, providing improved mobile voice communication over 1G. In addition, Code-Division Multiple Access (CDMA) and Global System for Mobile (GSM) concepts were also discussed. In 2G, the maximum achievable speed was 1 Mpbs.
Third Generation (3G): When technology ventured from 2G GSM frameworks into 3G universal mobile telecommunication system (UMTS) framework, users encountered higher system speed and quicker download speed making constant video calls. 3G was the first mobile broadband system that was formed to provide the voice with some multimedia. The technology behind 3G was high-speed packet access (HSPA/HSPA+). 3G used MIMO for multiplying the power of the wireless network, and it also used packet switching for fast data transmission.
Fourth Generation (4G): It is purely mobile broadband standard. In digital mobile communication, it was observed information rate that upgraded from 20 to 60 Mbps in 4G [ 4 ]. It works on LTE and WiMAX technologies, as well as provides wider bandwidth up to 100 Mhz. It was launched in 2010.
Fourth Generation LTE-A (4.5G): It is an advanced version of standard 4G LTE. LTE-A uses MIMO technology to combine multiple antennas for both transmitters as well as a receiver. Using MIMO, multiple signals and multiple antennas can work simultaneously, making LTE-A three times faster than standard 4G. LTE-A offered an improved system limit, decreased deferral in the application server, access triple traffic (Data, Voice, and Video) wirelessly at any time anywhere in the world.LTE-A delivers speeds of over 42 Mbps and up to 90 Mbps.
Fifth Generation (5G): 5G is a pillar of digital transformation; it is a real improvement on all the previous mobile generation networks. 5G brings three different services for end user like Extreme mobile broadband (eMBB). It offers high-speed internet connectivity, greater bandwidth, moderate latency, UltraHD streaming videos, virtual reality and augmented reality (AR/VR) media, and many more. Massive machine type communication (eMTC), it provides long-range and broadband machine-type communication at a very cost-effective price with less power consumption. eMTC brings a high data rate service, low power, extended coverage via less device complexity through mobile carriers for IoT applications. Ultra-reliable low latency communication (URLLC) offers low-latency and ultra-high reliability, rich quality of service (QoS), which is not possible with traditional mobile network architecture. URLLC is designed for on-demand real-time interaction such as remote surgery, vehicle to vehicle (V2V) communication, industry 4.0, smart grids, intelligent transport system, etc. 5G faster than 4G and offers remote-controlled operation over a reliable network with zero delays. It provides down-link maximum throughput of up to 20 Gbps. In addition, 5G also supports 4G WWWW (4th Generation World Wide Wireless Web) [ 5 ] and is based on Internet protocol version 6 (IPv6) protocol. 5G provides unlimited internet connection at your convenience, anytime, anywhere with extremely high speed, high throughput, low-latency, higher reliability and scalability, and energy-efficient mobile communication technology [ 6 ]. 5G mainly divided in two parts 6 GHz 5G and Millimeter wave(mmWave) 5G.
6 GHz is a mid frequency band which works as a mid point between capacity and coverage to offer perfect environment for 5G connectivity. 6 GHz spectrum will provide high bandwidth with improved network performance. It offers continuous channels that will reduce the need for network densification when mid-band spectrum is not available and it makes 5G connectivity affordable at anytime, anywhere for everyone.
mmWave is an essential technology of 5G network which build high performance network. 5G mmWave offer diverse services that is why all network providers should add on this technology in their 5G deployment planning. There are lots of service providers who deployed 5G mmWave, and their simulation result shows that 5G mmwave is a far less used spectrum. It provides very high speed wireless communication and it also offers ultra-wide bandwidth for next generation mobile network.
The evolution of wireless mobile technologies are presented in Table 1 . The abbreviations used in this paper are mentioned in Table 2 .
Summary of Mobile Technology.
Table of Notations and Abbreviations.
1.2. Key Contributions
The objective of this survey is to provide a detailed guide of 5G key technologies, methods to researchers, and to help with understanding how the recent works addressed 5G problems and developed solutions to tackle the 5G challenges; i.e., what are new methods that must be applied and how can they solve problems? Highlights of the research article are as follows.
- This survey focused on the recent trends and development in the era of 5G and novel contributions by the researcher community and discussed technical details on essential aspects of the 5G advancement.
- In this paper, the evolution of the mobile network from 1G to 5G is presented. In addition, the growth of mobile communication under different attributes is also discussed.
- This paper covers the emerging applications and research groups working on 5G & different research areas in 5G wireless communication network with a descriptive taxonomy.
- This survey discusses the current vision of the 5G networks, advantages, applications, key technologies, and key features. Furthermore, machine learning prospects are also explored with the emerging requirements in the 5G era. The article also focused on technical aspects of 5G IoT Based approaches and optimization techniques for 5G.
- we provide an extensive overview and recent advancement of emerging technologies of 5G mobile network, namely, MIMO, Non-Orthogonal Multiple Access (NOMA), mmWave, Internet of Things (IoT), Machine Learning (ML), and optimization. Also, a technical summary is discussed by highlighting the context of current approaches and corresponding challenges.
- Security challenges and considerations while developing 5G technology are discussed.
- Finally, the paper concludes with the future directives.
The existing survey focused on architecture, key concepts, and implementation challenges and issues. In contrast, this survey covers the state-of-the-art techniques as well as corresponding recent novel developments by researchers. Various recent significant papers are discussed with the key technologies accelerating the development and production of 5G products.
2. Existing Surveys and Their Applicability
In this paper, a detailed survey on various technologies of 5G networks is presented. Various researchers have worked on different technologies of 5G networks. In this section, Table 3 gives a tabular representation of existing surveys of 5G networks. Massive MIMO, NOMA, small cell, mmWave, beamforming, and MEC are the six main pillars that helped to implement 5G networks in real life.
A comparative overview of existing surveys on different technologies of 5G networks.
2.1. Limitations of Existing Surveys
The existing survey focused on architecture, key concepts, and implementation challenges and issues. The numerous current surveys focused on various 5G technologies with different parameters, and the authors did not cover all the technologies of the 5G network in detail with challenges and recent advancements. Few authors worked on MIMO (Non-Orthogonal Multiple Access) NOMA, MEC, small cell technologies. In contrast, some others worked on beamforming, Millimeter-wave (mmWave). But the existing survey did not cover all the technologies of the 5G network from a research and advancement perspective. No detailed survey is available in the market covering all the 5G network technologies and currently published research trade-offs. So, our main aim is to give a detailed study of all the technologies working on the 5G network. In contrast, this survey covers the state-of-the-art techniques as well as corresponding recent novel developments by researchers. Various recent significant papers are discussed with the key technologies accelerating the development and production of 5G products. This survey article collected key information about 5G technology and recent advancements, and it can be a kind of a guide for the reader. This survey provides an umbrella approach to bring multiple solutions and recent improvements in a single place to accelerate the 5G research with the latest key enabling solutions and reviews. A systematic layout representation of the survey in Figure 1 . We provide a state-of-the-art comparative overview of the existing surveys on different technologies of 5G networks in Table 3 .

Systematic layout representation of survey.
2.2. Article Organization
This article is organized under the following sections. Section 2 presents existing surveys and their applicability. In Section 3 , the preliminaries of 5G technology are presented. In Section 4 , recent advances of 5G technology based on Massive MIMO, NOMA, Millimeter Wave, 5G with IoT, machine learning for 5G, and Optimization in 5G are provided. In Section 5 , a description of novel 5G features over 4G is provided. Section 6 covered all the security concerns of the 5G network. Section 7 , 5G technology based on above-stated challenges summarize in tabular form. Finally, Section 8 and Section 9 conclude the study, which paves the path for future research.
3. Preliminary Section
3.1. emerging 5g paradigms and its features.
5G provides very high speed, low latency, and highly salable connectivity between multiple devices and IoT worldwide. 5G will provide a very flexible model to develop a modern generation of applications and industry goals [ 26 , 27 ]. There are many services offered by 5G network architecture are stated below:
Massive machine to machine communications: 5G offers novel, massive machine-to-machine communications [ 28 ], also known as the IoT [ 29 ], that provide connectivity between lots of machines without any involvement of humans. This service enhances the applications of 5G and provides connectivity between agriculture, construction, and industries [ 30 ].
Ultra-reliable low latency communications (URLLC): This service offers real-time management of machines, high-speed vehicle-to-vehicle connectivity, industrial connectivity and security principles, and highly secure transport system, and multiple autonomous actions. Low latency communications also clear up a different area where remote medical care, procedures, and operation are all achievable [ 31 ].
Enhanced mobile broadband: Enhance mobile broadband is an important use case of 5G system, which uses massive MIMO antenna, mmWave, beamforming techniques to offer very high-speed connectivity across a wide range of areas [ 32 ].
For communities: 5G provides a very flexible internet connection between lots of machines to make smart homes, smart schools, smart laboratories, safer and smart automobiles, and good health care centers [ 33 ].
For businesses and industry: As 5G works on higher spectrum ranges from 24 to 100 GHz. This higher frequency range provides secure low latency communication and high-speed wireless connectivity between IoT devices and industry 4.0, which opens a market for end-users to enhance their business models [ 34 ].
New and Emerging technologies: As 5G came up with many new technologies like beamforming, massive MIMO, mmWave, small cell, NOMA, MEC, and network slicing, it introduced many new features to the market. Like virtual reality (VR), users can experience the physical presence of people who are millions of kilometers away from them. Many new technologies like smart homes, smart workplaces, smart schools, smart sports academy also came into the market with this 5G Mobile network model [ 35 ].
3.2. Commercial Service Providers of 5G
5G provides high-speed internet browsing, streaming, and downloading with very high reliability and low latency. 5G network will change your working style, and it will increase new business opportunities and provide innovations that we cannot imagine. This section covers top service providers of 5G network [ 36 , 37 ].
Ericsson: Ericsson is a Swedish multinational networking and telecommunications company, investing around 25.62 billion USD in 5G network, which makes it the biggest telecommunication company. It claims that it is the only company working on all the continents to make the 5G network a global standard for the next generation wireless communication. Ericsson developed the first 5G radio prototype that enables the operators to set up the live field trials in their network, which helps operators understand how 5G reacts. It plays a vital role in the development of 5G hardware. It currently provides 5G services in over 27 countries with content providers like China Mobile, GCI, LGU+, AT&T, Rogers, and many more. It has 100 commercial agreements with different operators as of 2020.
Verizon: It is American multinational telecommunication which was founded in 1983. Verizon started offering 5G services in April 2020, and by December 2020, it has actively provided 5G services in 30 cities of the USA. They planned that by the end of 2021, they would deploy 5G in 30 more new cities. Verizon deployed a 5G network on mmWave, a very high band spectrum between 30 to 300 GHz. As it is a significantly less used spectrum, it provides very high-speed wireless communication. MmWave offers ultra-wide bandwidth for next-generation mobile networks. MmWave is a faster and high-band spectrum that has a limited range. Verizon planned to increase its number of 5G cells by 500% by 2020. Verizon also has an ultra wide-band flagship 5G service which is the best 5G service that increases the market price of Verizon.
Nokia: Nokia is a Finnish multinational telecommunications company which was founded in 1865. Nokia is one of the companies which adopted 5G technology very early. It is developing, researching, and building partnerships with various 5G renders to offer 5G communication as soon as possible. Nokia collaborated with Deutsche Telekom and Hamburg Port Authority and provided them 8000-hectare site for their 5G MoNArch project. Nokia is the only company that supplies 5G technology to all the operators of different countries like AT&T, Sprint, T-Mobile US and Verizon in the USA, Korea Telecom, LG U+ and SK Telecom in South Korea and NTT DOCOMO, KDDI, and SoftBank in Japan. Presently, Nokia has around 150+ agreements and 29 live networks all over the world. Nokia is continuously working hard on 5G technology to expand 5G networks all over the globe.
AT&T: AT&T is an American multinational company that was the first to deploy a 5G network in reality in 2018. They built a gigabit 5G network connection in Waco, TX, Kalamazoo, MI, and South Bend to achieve this. It is the first company that archives 1–2 gigabit per second speed in 2019. AT&T claims that it provides a 5G network connection among 225 million people worldwide by using a 6 GHz spectrum band.
T-Mobile: T-Mobile US (TMUS) is an American wireless network operator which was the first service provider that offers a real 5G nationwide network. The company knew that high-band 5G was not feasible nationwide, so they used a 600 MHz spectrum to build a significant portion of its 5G network. TMUS is planning that by 2024 they will double the total capacity and triple the full 5G capacity of T-Mobile and Sprint combined. The sprint buyout is helping T-Mobile move forward the company’s current market price to 129.98 USD.
Samsung: Samsung started their research in 5G technology in 2011. In 2013, Samsung successfully developed the world’s first adaptive array transceiver technology operating in the millimeter-wave Ka bands for cellular communications. Samsung provides several hundred times faster data transmission than standard 4G for core 5G mobile communication systems. The company achieved a lot of success in the next generation of technology, and it is considered one of the leading companies in the 5G domain.
Qualcomm: Qualcomm is an American multinational corporation in San Diego, California. It is also one of the leading company which is working on 5G chip. Qualcomm’s first 5G modem chip was announced in October 2016, and a prototype was demonstrated in October 2017. Qualcomm mainly focuses on building products while other companies talk about 5G; Qualcomm is building the technologies. According to one magazine, Qualcomm was working on three main areas of 5G networks. Firstly, radios that would use bandwidth from any network it has access to; secondly, creating more extensive ranges of spectrum by combining smaller pieces; and thirdly, a set of services for internet applications.
ZTE Corporation: ZTE Corporation was founded in 1985. It is a partially Chinese state-owned technology company that works in telecommunication. It was a leading company that worked on 4G LTE, and it is still maintaining its value and doing research and tests on 5G. It is the first company that proposed Pre5G technology with some series of solutions.
NEC Corporation: NEC Corporation is a Japanese multinational information technology and electronics corporation headquartered in Minato, Tokyo. ZTE also started their research on 5G, and they introduced a new business concept. NEC’s main aim is to develop 5G NR for the global mobile system and create secure and intelligent technologies to realize 5G services.
Cisco: Cisco is a USA networking hardware company that also sleeves up for 5G network. Cisco’s primary focus is to support 5G in three ways: Service—enable 5G services faster so all service providers can increase their business. Infrastructure—build 5G-oriented infrastructure to implement 5G more quickly. Automation—make a more scalable, flexible, and reliable 5G network. The companies know the importance of 5G, and they want to connect more than 30 billion devices in the next couple of years. Cisco intends to work on network hardening as it is a vital part of 5G network. Cisco used AI with deep learning to develop a 5G Security Architecture, enabling Secure Network Transformation.
3.3. 5G Research Groups
Many research groups from all over the world are working on a 5G wireless mobile network [ 38 ]. These groups are continuously working on various aspects of 5G. The list of those research groups are presented as follows: 5GNOW (5th Generation Non-Orthogonal Waveform for Asynchronous Signaling), NEWCOM (Network of Excellence in Wireless Communication), 5GIC (5G Innovation Center), NYU (New York University) Wireless, 5GPPP (5G Infrastructure Public-Private Partnership), EMPHATIC (Enhanced Multi-carrier Technology for Professional Adhoc and Cell-Based Communication), ETRI(Electronics and Telecommunication Research Institute), METIS (Mobile and wireless communication Enablers for the Twenty-twenty Information Society) [ 39 ]. The various research groups along with the research area are presented in Table 4 .
Research groups working on 5G mobile networks.
3.4. 5G Applications
5G is faster than 4G and offers remote-controlled operation over a reliable network with zero delays. It provides down-link maximum throughput of up to 20 Gbps. In addition, 5G also supports 4G WWWW (4th Generation World Wide Wireless Web) [ 5 ] and is based on Internet protocol version 6 (IPv6) protocol. 5G provides unlimited internet connection at your convenience, anytime, anywhere with extremely high speed, high throughput, low-latency, higher reliability, greater scalablility, and energy-efficient mobile communication technology [ 6 ].
There are lots of applications of 5G mobile network are as follows:
- High-speed mobile network: 5G is an advancement on all the previous mobile network technologies, which offers very high speed downloading speeds 0 of up to 10 to 20 Gbps. The 5G wireless network works as a fiber optic internet connection. 5G is different from all the conventional mobile transmission technologies, and it offers both voice and high-speed data connectivity efficiently. 5G offers very low latency communication of less than a millisecond, useful for autonomous driving and mission-critical applications. 5G will use millimeter waves for data transmission, providing higher bandwidth and a massive data rate than lower LTE bands. As 5 Gis a fast mobile network technology, it will enable virtual access to high processing power and secure and safe access to cloud services and enterprise applications. Small cell is one of the best features of 5G, which brings lots of advantages like high coverage, high-speed data transfer, power saving, easy and fast cloud access, etc. [ 40 ].
- Entertainment and multimedia: In one analysis in 2015, it was found that more than 50 percent of mobile internet traffic was used for video downloading. This trend will surely increase in the future, which will make video streaming more common. 5G will offer High-speed streaming of 4K videos with crystal clear audio, and it will make a high definition virtual world on your mobile. 5G will benefit the entertainment industry as it offers 120 frames per second with high resolution and higher dynamic range video streaming, and HD TV channels can also be accessed on mobile devices without any interruptions. 5G provides low latency high definition communication so augmented reality (AR), and virtual reality (VR) will be very easily implemented in the future. Virtual reality games are trendy these days, and many companies are investing in HD virtual reality games. The 5G network will offer high-speed internet connectivity with a better gaming experience [ 41 ].
- Smart homes : smart home appliances and products are in demand these days. The 5G network makes smart homes more real as it offers high-speed connectivity and monitoring of smart appliances. Smart home appliances are easily accessed and configured from remote locations using the 5G network as it offers very high-speed low latency communication.
- Smart cities: 5G wireless network also helps develop smart cities applications such as automatic traffic management, weather update, local area broadcasting, energy-saving, efficient power supply, smart lighting system, water resource management, crowd management, emergency control, etc.
- Industrial IoT: 5G wireless technology will provide lots of features for future industries such as safety, process tracking, smart packing, shipping, energy efficiency, automation of equipment, predictive maintenance, and logistics. 5G smart sensor technology also offers smarter, safer, cost-effective, and energy-saving industrial IoT operations.
- Smart Farming: 5G technology will play a crucial role in agriculture and smart farming. 5G sensors and GPS technology will help farmers track live attacks on crops and manage them quickly. These smart sensors can also be used for irrigation, pest, insect, and electricity control.
- Autonomous Driving: The 5G wireless network offers very low latency high-speed communication, significant for autonomous driving. It means self-driving cars will come to real life soon with 5G wireless networks. Using 5G autonomous cars can easily communicate with smart traffic signs, objects, and other vehicles running on the road. 5G’s low latency feature makes self-driving more real as every millisecond is essential for autonomous vehicles, decision-making is done in microseconds to avoid accidents.
- Healthcare and mission-critical applications: 5G technology will bring modernization in medicine where doctors and practitioners can perform advanced medical procedures. The 5G network will provide connectivity between all classrooms, so attending seminars and lectures will be easier. Through 5G technology, patients can connect with doctors and take their advice. Scientists are building smart medical devices which can help people with chronic medical conditions. The 5G network will boost the healthcare industry with smart devices, the internet of medical things, smart sensors, HD medical imaging technologies, and smart analytics systems. 5G will help access cloud storage, so accessing healthcare data will be very easy from any location worldwide. Doctors and medical practitioners can easily store and share large files like MRI reports within seconds using the 5G network.
- Satellite Internet: In many remote areas, ground base stations are not available, so 5G will play a crucial role in providing connectivity in such areas. The 5G network will provide connectivity using satellite systems, and the satellite system uses a constellation of multiple small satellites to provide connectivity in urban and rural areas across the world.
4. 5G Technologies
This section describes recent advances of 5G Massive MIMO, 5G NOMA, 5G millimeter wave, 5G IOT, 5G with machine learning, and 5G optimization-based approaches. In addition, the summary is also presented in each subsection that paves the researchers for the future research direction.
4.1. 5G Massive MIMO
Multiple-input-multiple-out (MIMO) is a very important technology for wireless systems. It is used for sending and receiving multiple signals simultaneously over the same radio channel. MIMO plays a very big role in WI-FI, 3G, 4G, and 4G LTE-A networks. MIMO is mainly used to achieve high spectral efficiency and energy efficiency but it was not up to the mark MIMO provides low throughput and very low reliable connectivity. To resolve this, lots of MIMO technology like single user MIMO (SU-MIMO), multiuser MIMO (MU-MIMO) and network MIMO were used. However, these new MIMO also did not still fulfill the demand of end users. Massive MIMO is an advancement of MIMO technology used in the 5G network in which hundreds and thousands of antennas are attached with base stations to increase throughput and spectral efficiency. Multiple transmit and receive antennas are used in massive MIMO to increase the transmission rate and spectral efficiency. When multiple UEs generate downlink traffic simultaneously, massive MIMO gains higher capacity. Massive MIMO uses extra antennas to move energy into smaller regions of space to increase spectral efficiency and throughput [ 43 ]. In traditional systems data collection from smart sensors is a complex task as it increases latency, reduced data rate and reduced reliability. While massive MIMO with beamforming and huge multiplexing techniques can sense data from different sensors with low latency, high data rate and higher reliability. Massive MIMO will help in transmitting the data in real-time collected from different sensors to central monitoring locations for smart sensor applications like self-driving cars, healthcare centers, smart grids, smart cities, smart highways, smart homes, and smart enterprises [ 44 ].
Highlights of 5G Massive MIMO technology are as follows:
- Data rate: Massive MIMO is advised as the one of the dominant technologies to provide wireless high speed and high data rate in the gigabits per seconds.
- The relationship between wave frequency and antenna size: Both are inversely proportional to each other. It means lower frequency signals need a bigger antenna and vise versa.

Pictorial representation of multi-input and multi-output (MIMO).
- MIMO role in 5G: Massive MIMO will play a crucial role in the deployment of future 5G mobile communication as greater spectral and energy efficiency could be enabled.
State-of-the-Art Approaches
Plenty of approaches were proposed to resolve the issues of conventional MIMO [ 7 ].
The MIMO multirate, feed-forward controller is suggested by Mae et al. [ 46 ]. In the simulation, the proposed model generates the smooth control input, unlike the conventional MIMO, which generates oscillated control inputs. It also outperformed concerning the error rate. However, a combination of multirate and single rate can be used for better results.
The performance of stand-alone MIMO, distributed MIMO with and without corporation MIMO, was investigated by Panzner et al. [ 47 ]. In addition, an idea about the integration of large scale in the 5G technology was also presented. In the experimental analysis, different MIMO configurations are considered. The variation in the ratio of overall transmit antennas to spatial is deemed step-wise from equality to ten.
The simulation of massive MIMO noncooperative and cooperative systems for down-link behavior was performed by He et al. [ 48 ]. It depends on present LTE systems, which deal with various antennas in the base station set-up. It was observed that collaboration in different BS improves the system behaviors, whereas throughput is reduced slightly in this approach. However, a new method can be developed which can enhance both system behavior and throughput.
In [ 8 ], different approaches that increased the energy efficiency benefits provided by massive MIMO were presented. They analyzed the massive MIMO technology and described the detailed design of the energy consumption model for massive MIMO systems. This article has explored several techniques to enhance massive MIMO systems’ energy efficiency (EE) gains. This paper reviews standard EE-maximization approaches for the conventional massive MIMO systems, namely, scaling number of antennas, real-time implementing low-complexity operations at the base station (BS), power amplifier losses minimization, and radio frequency (RF) chain minimization requirements. In addition, open research direction is also identified.
In [ 49 ], various existing approaches based on different antenna selection and scheduling, user selection and scheduling, and joint antenna and user scheduling methods adopted in massive MIMO systems are presented in this paper. The objective of this survey article was to make awareness about the current research and future research direction in MIMO for systems. They analyzed that complete utilization of resources and bandwidth was the most crucial factor which enhances the sum rate.
In [ 50 ], authors discussed the development of various techniques for pilot contamination. To calculate the impact of pilot contamination in time division duplex (TDD) massive MIMO system, TDD and frequency division duplexing FDD patterns in massive MIMO techniques are used. They discussed different issues in pilot contamination in TDD massive MIMO systems with all the possible future directions of research. They also classified various techniques to generate the channel information for both pilot-based and subspace-based approaches.
In [ 19 ], the authors defined the uplink and downlink services for a massive MIMO system. In addition, it maintains a performance matrix that measures the impact of pilot contamination on different performances. They also examined the various application of massive MIMO such as small cells, orthogonal frequency-division multiplexing (OFDM) schemes, massive MIMO IEEE 802, 3rd generation partnership project (3GPP) specifications, and higher frequency bands. They considered their research work crucial for cutting edge massive MIMO and covered many issues like system throughput performance and channel state acquisition at higher frequencies.
In [ 13 ], various approaches were suggested for MIMO future generation wireless communication. They made a comparative study based on performance indicators such as peak data rate, energy efficiency, latency, throughput, etc. The key findings of this survey are as follows: (1) spatial multiplexing improves the energy efficiency; (2) design of MIMO play a vital role in the enhancement of throughput; (3) enhancement of mMIMO focusing on energy & spectral performance; (4) discussed the future challenges to improve the system design.
In [ 51 ], the study of large-scale MIMO systems for an energy-efficient system sharing method was presented. For the resource allocation, circuit energy and transmit energy expenditures were taken into consideration. In addition, the optimization techniques were applied for an energy-efficient resource sharing system to enlarge the energy efficiency for individual QoS and energy constraints. The author also examined the BS configuration, which includes homogeneous and heterogeneous UEs. While simulating, they discussed that the total number of transmit antennas plays a vital role in boosting energy efficiency. They highlighted that the highest energy efficiency was obtained when the BS was set up with 100 antennas that serve 20 UEs.
This section includes various works done on 5G MIMO technology by different author’s. Table 5 shows how different author’s worked on improvement of various parameters such as throughput, latency, energy efficiency, and spectral efficiency with 5G MIMO technology.
Summary of massive MIMO-based approaches in 5G technology.
4.2. 5G Non-Orthogonal Multiple Access (NOMA)
NOMA is a very important radio access technology used in next generation wireless communication. Compared to previous orthogonal multiple access techniques, NOMA offers lots of benefits like high spectrum efficiency, low latency with high reliability and high speed massive connectivity. NOMA mainly works on a baseline to serve multiple users with the same resources in terms of time, space and frequency. NOMA is mainly divided into two main categories one is code domain NOMA and another is power domain NOMA. Code-domain NOMA can improve the spectral efficiency of mMIMO, which improves the connectivity in 5G wireless communication. Code-domain NOMA was divided into some more multiple access techniques like sparse code multiple access, lattice-partition multiple access, multi-user shared access and pattern-division multiple access [ 52 ]. Power-domain NOMA is widely used in 5G wireless networks as it performs well with various wireless communication techniques such as MIMO, beamforming, space-time coding, network coding, full-duplex and cooperative communication etc. [ 53 ]. The conventional orthogonal frequency-division multiple access (OFDMA) used by 3GPP in 4G LTE network provides very low spectral efficiency when bandwidth resources are allocated to users with low channel state information (CSI). NOMA resolved this issue as it enables users to access all the subcarrier channels so bandwidth resources allocated to the users with low CSI can still be accessed by the users with strong CSI which increases the spectral efficiency. The 5G network will support heterogeneous architecture in which small cell and macro base stations work for spectrum sharing. NOMA is a key technology of the 5G wireless system which is very helpful for heterogeneous networks as multiple users can share their data in a small cell using the NOMA principle.The NOMA is helpful in various applications like ultra-dense networks (UDN), machine to machine (M2M) communication and massive machine type communication (mMTC). As NOMA provides lots of features it has some challenges too such as NOMA needs huge computational power for a large number of users at high data rates to run the SIC algorithms. Second, when users are moving from the networks, to manage power allocation optimization is a challenging task for NOMA [ 54 ]. Hybrid NOMA (HNOMA) is a combination of power-domain and code-domain NOMA. HNOMA uses both power differences and orthogonal resources for transmission among multiple users. As HNOMA is using both power-domain NOMA and code-domain NOMA it can achieve higher spectral efficiency than Power-domain NOMA and code-domain NOMA. In HNOMA multiple groups can simultaneously transmit signals at the same time. It uses a message passing algorithm (MPA) and successive interference cancellation (SIC)-based detection at the base station for these groups [ 55 ].
Highlights of 5G NOMA technology as follows:

Pictorial representation of orthogonal and Non-Orthogonal Multiple Access (NOMA).
- NOMA provides higher data rates and resolves all the loop holes of OMA that makes 5G mobile network more scalable and reliable.
- As multiple users use same frequency band simultaneously it increases the performance of whole network.
- To setup intracell and intercell interference NOMA provides nonorthogonal transmission on the transmitter end.
- The primary fundamental of NOMA is to improve the spectrum efficiency by strengthening the ramification of receiver.
State-of-the-Art of Approaches
A plenty of approaches were developed to address the various issues in NOMA.
A novel approach to address the multiple receiving signals at the same frequency is proposed in [ 22 ]. In NOMA, multiple users use the same sub-carrier, which improves the fairness and throughput of the system. As a nonorthogonal method is used among multiple users, at the time of retrieving the user’s signal at the receiver’s end, joint processing is required. They proposed solutions to optimize the receiver and the radio resource allocation of uplink NOMA. Firstly, the authors proposed an iterative MUDD which utilizes the information produced by the channel decoder to improve the performance of the multiuser detector. After that, the author suggested a power allocation and novel subcarrier that enhances the users’ weighted sum rate for the NOMA scheme. Their proposed model showed that NOMA performed well as compared to OFDM in terms of fairness and efficiency.
In [ 53 ], the author’s reviewed a power-domain NOMA that uses superposition coding (SC) and successive interference cancellation (SIC) at the transmitter and the receiver end. Lots of analyses were held that described that NOMA effectively satisfies user data rate demands and network-level of 5G technologies. The paper presented a complete review of recent advances in the 5G NOMA system. It showed the comparative analysis regarding allocation procedures, user fairness, state-of-the-art efficiency evaluation, user pairing pattern, etc. The study also analyzes NOMA’s behavior when working with other wireless communication techniques, namely, beamforming, MIMO, cooperative connections, network, space-time coding, etc.
In [ 9 ], the authors proposed NOMA with MEC, which improves the QoS as well as reduces the latency of the 5G wireless network. This model increases the uplink NOMA by decreasing the user’s uplink energy consumption. They formulated an optimized NOMA framework that reduces the energy consumption of MEC by using computing and communication resource allocation, user clustering, and transmit powers.
In [ 10 ], the authors proposed a model which investigates outage probability under average channel state information CSI and data rate in full CSI to resolve the problem of optimal power allocation, which increase the NOMA downlink system among users. They developed simple low-complexity algorithms to provide the optimal solution. The obtained simulation results showed NOMA’s efficiency, achieving higher performance fairness compared to the TDMA configurations. It was observed from the results that NOMA, through the appropriate power amplifiers (PA), ensures the high-performance fairness requirement for the future 5G wireless communication networks.
In [ 56 ], researchers discussed that the NOMA technology and waveform modulation techniques had been used in the 5G mobile network. Therefore, this research gave a detailed survey of non-orthogonal waveform modulation techniques and NOMA schemes for next-generation mobile networks. By analyzing and comparing multiple access technologies, they considered the future evolution of these technologies for 5G mobile communication.
In [ 57 ], the authors surveyed non-orthogonal multiple access (NOMA) from the development phase to the recent developments. They have also compared NOMA techniques with traditional OMA techniques concerning information theory. The author discussed the NOMA schemes categorically as power and code domain, including the design principles, operating principles, and features. Comparison is based upon the system’s performance, spectral efficiency, and the receiver’s complexity. Also discussed are the future challenges, open issues, and their expectations of NOMA and how it will support the key requirements of 5G mobile communication systems with massive connectivity and low latency.
In [ 17 ], authors present the first review of an elementary NOMA model with two users, which clarify its central precepts. After that, a general design with multicarrier supports with a random number of users on each sub-carrier is analyzed. In performance evaluation with the existing approaches, resource sharing and multiple-input multiple-output NOMA are examined. Furthermore, they took the key elements of NOMA and its potential research demands. Finally, they reviewed the two-user SC-NOMA design and a multi-user MC-NOMA design to highlight NOMA’s basic approaches and conventions. They also present the research study about the performance examination, resource assignment, and MIMO in NOMA.
In this section, various works by different authors done on 5G NOMA technology is covered. Table 6 shows how other authors worked on the improvement of various parameters such as spectral efficiency, fairness, and computing capacity with 5G NOMA technology.
Summary of NOMA-based approaches in 5G technology.
4.3. 5G Millimeter Wave (mmWave)
Millimeter wave is an extremely high frequency band, which is very useful for 5G wireless networks. MmWave uses 30 GHz to 300 GHz spectrum band for transmission. The frequency band between 30 GHz to 300 GHz is known as mmWave because these waves have wavelengths between 1 to 10 mm. Till now radar systems and satellites are only using mmWave as these are very fast frequency bands which provide very high speed wireless communication. Many mobile network providers also started mmWave for transmitting data between base stations. Using two ways the speed of data transmission can be improved one is by increasing spectrum utilization and second is by increasing spectrum bandwidth. Out of these two approaches increasing bandwidth is quite easy and better. The frequency band below 5 GHz is very crowded as many technologies are using it so to boost up the data transmission rate 5G wireless network uses mmWave technology which instead of increasing spectrum utilization, increases the spectrum bandwidth [ 58 ]. To maximize the signal bandwidth in wireless communication the carrier frequency should also be increased by 5% because the signal bandwidth is directly proportional to carrier frequencies. The frequency band between 28 GHz to 60 GHz is very useful for 5G wireless communication as 28 GHz frequency band offers up to 1 GHz spectrum bandwidth and 60 GHz frequency band offers 2 GHz spectrum bandwidth. 4G LTE provides 2 GHz carrier frequency which offers only 100 MHz spectrum bandwidth. However, the use of mmWave increases the spectrum bandwidth 10 times, which leads to better transmission speeds [ 59 , 60 ].
Highlights of 5G mmWave are as follows:

Pictorial representation of millimeter wave.
- The 5G mmWave offer three advantages: (1) MmWave is very less used new Band, (2) MmWave signals carry more data than lower frequency wave, and (3) MmWave can be incorporated with MIMO antenna with the potential to offer a higher magnitude capacity compared to current communication systems.
In [ 11 ], the authors presented the survey of mmWave communications for 5G. The advantage of mmWave communications is adaptability, i.e., it supports the architectures and protocols up-gradation, which consists of integrated circuits, systems, etc. The authors over-viewed the present solutions and examined them concerning effectiveness, performance, and complexity. They also discussed the open research issues of mmWave communications in 5G concerning the software-defined network (SDN) architecture, network state information, efficient regulation techniques, and the heterogeneous system.
In [ 61 ], the authors present the recent work done by investigators in 5G; they discussed the design issues and demands of mmWave 5G antennas for cellular handsets. After that, they designed a small size and low-profile 60 GHz array of antenna units that contain 3D planer mesh-grid antenna elements. For the future prospect, a framework is designed in which antenna components are used to operate cellular handsets on mmWave 5G smartphones. In addition, they cross-checked the mesh-grid array of antennas with the polarized beam for upcoming hardware challenges.
In [ 12 ], the authors considered the suitability of the mmWave band for 5G cellular systems. They suggested a resource allocation system for concurrent D2D communications in mmWave 5G cellular systems, and it improves network efficiency and maintains network connectivity. This research article can serve as guidance for simulating D2D communications in mmWave 5G cellular systems. Massive mmWave BS may be set up to obtain a high delivery rate and aggregate efficiency. Therefore, many wireless users can hand off frequently between the mmWave base terminals, and it emerges the demand to search the neighbor having better network connectivity.
In [ 62 ], the authors provided a brief description of the cellular spectrum which ranges from 1 GHz to 3 GHz and is very crowed. In addition, they presented various noteworthy factors to set up mmWave communications in 5G, namely, channel characteristics regarding mmWave signal attenuation due to free space propagation, atmospheric gaseous, and rain. In addition, hybrid beamforming architecture in the mmWave technique is analyzed. They also suggested methods for the blockage effect in mmWave communications due to penetration damage. Finally, the authors have studied designing the mmWave transmission with small beams in nonorthogonal device-to-device communication.
This section covered various works done on 5G mmWave technology. The Table 7 shows how different author’s worked on the improvement of various parameters i.e., transmission rate, coverage, and cost, with 5G mmWave technology.
Summary of existing mmWave-based approaches in 5G technology.
4.4. 5G IoT Based Approaches
The 5G mobile network plays a big role in developing the Internet of Things (IoT). IoT will connect lots of things with the internet like appliances, sensors, devices, objects, and applications. These applications will collect lots of data from different devices and sensors. 5G will provide very high speed internet connectivity for data collection, transmission, control, and processing. 5G is a flexible network with unused spectrum availability and it offers very low cost deployment that is why it is the most efficient technology for IoT [ 63 ]. In many areas, 5G provides benefits to IoT, and below are some examples:
Smart homes: smart home appliances and products are in demand these days. The 5G network makes smart homes more real as it offers high speed connectivity and monitoring of smart appliances. Smart home appliances are easily accessed and configured from remote locations using the 5G network, as it offers very high speed low latency communication.
Smart cities: 5G wireless network also helps in developing smart cities applications such as automatic traffic management, weather update, local area broadcasting, energy saving, efficient power supply, smart lighting system, water resource management, crowd management, emergency control, etc.
Industrial IoT: 5G wireless technology will provide lots of features for future industries such as safety, process tracking, smart packing, shipping, energy efficiency, automation of equipment, predictive maintenance and logistics. 5G smart sensor technology also offers smarter, safer, cost effective, and energy-saving industrial operation for industrial IoT.
Smart Farming: 5G technology will play a crucial role for agriculture and smart farming. 5G sensors and GPS technology will help farmers to track live attacks on crops and manage them quickly. These smart sensors can also be used for irrigation control, pest control, insect control, and electricity control.
Autonomous Driving: 5G wireless network offers very low latency high speed communication which is very significant for autonomous driving. It means self-driving cars will come to real life soon with 5G wireless networks. Using 5G autonomous cars can easily communicate with smart traffic signs, objects and other vehicles running on the road. 5G’s low latency feature makes self-driving more real as every millisecond is important for autonomous vehicles, decision taking is performed in microseconds to avoid accidents [ 64 ].
Highlights of 5G IoT are as follows:

Pictorial representation of IoT with 5G.
- 5G with IoT is a new feature of next-generation mobile communication, which provides a high-speed internet connection between moderated devices. 5G IoT also offers smart homes, smart devices, sensors, smart transportation systems, smart industries, etc., for end-users to make them smarter.
- IoT deals with moderate devices which connect through the internet. The approach of the IoT has made the consideration of the research associated with the outcome of providing wearable, smart-phones, sensors, smart transportation systems, smart devices, washing machines, tablets, etc., and these diverse systems are associated to a common interface with the intelligence to connect.
- Significant IoT applications include private healthcare systems, traffic management, industrial management, and tactile internet, etc.
Plenty of approaches is devised to address the issues of IoT [ 14 , 65 , 66 ].
In [ 65 ], the paper focuses on 5G mobile systems due to the emerging trends and developing technologies, which results in the exponential traffic growth in IoT. The author surveyed the challenges and demands during deployment of the massive IoT applications with the main focus on mobile networking. The author reviewed the features of standard IoT infrastructure, along with the cellular-based, low-power wide-area technologies (LPWA) such as eMTC, extended coverage (EC)-GSM-IoT, as well as noncellular, low-power wide-area (LPWA) technologies such as SigFox, LoRa etc.
In [ 14 ], the authors presented how 5G technology copes with the various issues of IoT today. It provides a brief review of existing and forming 5G architectures. The survey indicates the role of 5G in the foundation of the IoT ecosystem. IoT and 5G can easily combine with improved wireless technologies to set up the same ecosystem that can fulfill the current requirement for IoT devices. 5G can alter nature and will help to expand the development of IoT devices. As the process of 5G unfolds, global associations will find essentials for setting up a cross-industry engagement in determining and enlarging the 5G system.
In [ 66 ], the author introduced an IoT authentication scheme in a 5G network, with more excellent reliability and dynamic. The scheme proposed a privacy-protected procedure for selecting slices; it provided an additional fog node for proper data transmission and service types of the subscribers, along with service-oriented authentication and key understanding to maintain the secrecy, precision of users, and confidentiality of service factors. Users anonymously identify the IoT servers and develop a vital channel for service accessibility and data cached on local fog nodes and remote IoT servers. The author performed a simulation to manifest the security and privacy preservation of the user over the network.
This section covered various works done on 5G IoT by multiple authors. Table 8 shows how different author’s worked on the improvement of numerous parameters, i.e., data rate, security requirement, and performance with 5G IoT.
Summary of IoT-based approaches in 5G technology.
4.5. Machine Learning Techniques for 5G
Various machine learning (ML) techniques were applied in 5G networks and mobile communication. It provides a solution to multiple complex problems, which requires a lot of hand-tuning. ML techniques can be broadly classified as supervised, unsupervised, and reinforcement learning. Let’s discuss each learning technique separately and where it impacts the 5G network.
Supervised Learning, where user works with labeled data; some 5G network problems can be further categorized as classification and regression problems. Some regression problems such as scheduling nodes in 5G and energy availability can be predicted using Linear Regression (LR) algorithm. To accurately predict the bandwidth and frequency allocation Statistical Logistic Regression (SLR) is applied. Some supervised classifiers are applied to predict the network demand and allocate network resources based on the connectivity performance; it signifies the topology setup and bit rates. Support Vector Machine (SVM) and NN-based approximation algorithms are used for channel learning based on observable channel state information. Deep Neural Network (DNN) is also employed to extract solutions for predicting beamforming vectors at the BS’s by taking mapping functions and uplink pilot signals into considerations.
In unsupervised Learning, where the user works with unlabeled data, various clustering techniques are applied to enhance network performance and connectivity without interruptions. K-means clustering reduces the data travel by storing data centers content into clusters. It optimizes the handover estimation based on mobility pattern and selection of relay nodes in the V2V network. Hierarchical clustering reduces network failure by detecting the intrusion in the mobile wireless network; unsupervised soft clustering helps in reducing latency by clustering fog nodes. The nonparametric Bayesian unsupervised learning technique reduces traffic in the network by actively serving the user’s requests and demands. Other unsupervised learning techniques such as Adversarial Auto Encoders (AAE) and Affinity Propagation Clustering techniques detect irregular behavior in the wireless spectrum and manage resources for ultradense small cells, respectively.
In case of an uncertain environment in the 5G wireless network, reinforcement learning (RL) techniques are employed to solve some problems. Actor-critic reinforcement learning is used for user scheduling and resource allocation in the network. Markov decision process (MDP) and Partially Observable MDP (POMDP) is used for Quality of Experience (QoE)-based handover decision-making for Hetnets. Controls packet call admission in HetNets and channel access process for secondary users in a Cognitive Radio Network (CRN). Deep RL is applied to decide the communication channel and mobility and speeds up the secondary user’s learning rate using an antijamming strategy. Deep RL is employed in various 5G network application parameters such as resource allocation and security [ 67 ]. Table 9 shows the state-of-the-art ML-based solution for 5G network.
The state-of-the-art ML-based solution for 5G network.
Highlights of machine learning techniques for 5G are as follows:

Pictorial representation of machine learning (ML) in 5G.
- In ML, a model will be defined which fulfills the desired requirements through which desired results are obtained. In the later stage, it examines accuracy from obtained results.
- ML plays a vital role in 5G network analysis for threat detection, network load prediction, final arrangement, and network formation. Searching for a better balance between power, length of antennas, area, and network thickness crossed with the spontaneous use of services in the universe of individual users and types of devices.
In [ 79 ], author’s firstly describes the demands for the traditional authentication procedures and benefits of intelligent authentication. The intelligent authentication method was established to improve security practice in 5G-and-beyond wireless communication systems. Thereafter, the machine learning paradigms for intelligent authentication were organized into parametric and non-parametric research methods, as well as supervised, unsupervised, and reinforcement learning approaches. As a outcome, machine learning techniques provide a new paradigm into authentication under diverse network conditions and unstable dynamics. In addition, prompt intelligence to the security management to obtain cost-effective, better reliable, model-free, continuous, and situation-aware authentication.
In [ 68 ], the authors proposed a machine learning-based model to predict the traffic load at a particular location. They used a mobile network traffic dataset to train a model that can calculate the total number of user requests at a time. To launch access and mobility management function (AMF) instances according to the requirement as there were no predictions of user request the performance automatically degrade as AMF does not handle these requests at a time. Earlier threshold-based techniques were used to predict the traffic load, but that approach took too much time; therefore, the authors proposed RNN algorithm-based ML to predict the traffic load, which gives efficient results.
In [ 15 ], authors discussed the issue of network slice admission, resource allocation among subscribers, and how to maximize the profit of infrastructure providers. The author proposed a network slice admission control algorithm based on SMDP (decision-making process) that guarantees the subscribers’ best acceptance policies and satisfiability (tenants). They also suggested novel N3AC, a neural network-based algorithm that optimizes performance under various configurations, significantly outperforms practical and straightforward approaches.
This section includes various works done on 5G ML by different authors. Table 10 shows the state-of-the-art work on the improvement of various parameters such as energy efficiency, Quality of Services (QoS), and latency with 5G ML.
The state-of-the-art ML-based approaches in 5G technology.
4.6. Optimization Techniques for 5G
Optimization techniques may be applied to capture NP-Complete or NP-Hard problems in 5G technology. This section briefly describes various research works suggested for 5G technology based on optimization techniques.
In [ 80 ], Massive MIMO technology is used in 5G mobile network to make it more flexible and scalable. The MIMO implementation in 5G needs a significant number of radio frequencies is required in the RF circuit that increases the cost and energy consumption of the 5G network. This paper provides a solution that increases the cost efficiency and energy efficiency with many radio frequency chains for a 5G wireless communication network. They give an optimized energy efficient technique for MIMO antenna and mmWave technologies based 5G mobile communication network. The proposed Energy Efficient Hybrid Precoding (EEHP) algorithm to increase the energy efficiency for the 5G wireless network. This algorithm minimizes the cost of an RF circuit with a large number of RF chains.
In [ 16 ], authors have discussed the growing demand for energy efficiency in the next-generation networks. In the last decade, they have figured out the things in wireless transmissions, which proved a change towards pursuing green communication for the next generation system. The importance of adopting the correct EE metric was also reviewed. Further, they worked through the different approaches that can be applied in the future for increasing the network’s energy and posed a summary of the work that was completed previously to enhance the energy productivity of the network using these capabilities. A system design for EE development using relay selection was also characterized, along with an observation of distinct algorithms applied for EE in relay-based ecosystems.
In [ 81 ], authors presented how AI-based approach is used to the setup of Self Organizing Network (SON) functionalities for radio access network (RAN) design and optimization. They used a machine learning approach to predict the results for 5G SON functionalities. Firstly, the input was taken from various sources; then, prediction and clustering-based machine learning models were applied to produce the results. Multiple AI-based devices were used to extract the knowledge analysis to execute SON functionalities smoothly. Based on results, they tested how self-optimization, self-testing, and self-designing are done for SON. The author also describes how the proposed mechanism classifies in different orders.
In [ 82 ], investigators examined the working of OFDM in various channel environments. They also figured out the changes in frame duration of the 5G TDD frame design. Subcarrier spacing is beneficial to obtain a small frame length with control overhead. They provided various techniques to reduce the growing guard period (GP) and cyclic prefix (CP) like complete utilization of multiple subcarrier spacing, management and data parts of frame at receiver end, various uses of timing advance (TA) or total control of flexible CP size.
This section includes various works that were done on 5G optimization by different authors. Table 11 shows how other authors worked on the improvement of multiple parameters such as energy efficiency, power optimization, and latency with 5G optimization.
Summary of Optimization Based Approaches in 5G Technology.
5. Description of Novel 5G Features over 4G
This section presents descriptions of various novel features of 5G, namely, the concept of small cell, beamforming, and MEC.
5.1. Small Cell
Small cells are low-powered cellular radio access nodes which work in the range of 10 meters to a few kilometers. Small cells play a very important role in implementation of the 5G wireless network. Small cells are low power base stations which cover small areas. Small cells are quite similar with all the previous cells used in various wireless networks. However, these cells have some advantages like they can work with low power and they are also capable of working with high data rates. Small cells help in rollout of 5G network with ultra high speed and low latency communication. Small cells in the 5G network use some new technologies like MIMO, beamforming, and mmWave for high speed data transmission. The design of small cells hardware is very simple so its implementation is quite easier and faster. There are three types of small cell tower available in the market. Femtocells, picocells, and microcells [ 83 ]. As shown in the Table 12 .
Types of Small cells.
MmWave is a very high band spectrum between 30 to 300 GHz. As it is a significantly less used spectrum, it provides very high-speed wireless communication. MmWave offers ultra-wide bandwidth for next-generation mobile networks. MmWave has lots of advantages, but it has some disadvantages, too, such as mmWave signals are very high-frequency signals, so they have more collision with obstacles in the air which cause the signals loses energy quickly. Buildings and trees also block MmWave signals, so these signals cover a shorter distance. To resolve these issues, multiple small cell stations are installed to cover the gap between end-user and base station [ 18 ]. Small cell covers a very shorter range, so the installation of a small cell depends on the population of a particular area. Generally, in a populated place, the distance between each small cell varies from 10 to 90 meters. In the survey [ 20 ], various authors implemented small cells with massive MIMO simultaneously. They also reviewed multiple technologies used in 5G like beamforming, small cell, massive MIMO, NOMA, device to device (D2D) communication. Various problems like interference management, spectral efficiency, resource management, energy efficiency, and backhauling are discussed. The author also gave a detailed presentation of all the issues occurring while implementing small cells with various 5G technologies. As shown in the Figure 7 , mmWave has a higher range, so it can be easily blocked by the obstacles as shown in Figure 7 a. This is one of the key concerns of millimeter-wave signal transmission. To solve this issue, the small cell can be placed at a short distance to transmit the signals easily, as shown in Figure 7 b.

Pictorial representation of communication with and without small cells.
5.2. Beamforming
Beamforming is a key technology of wireless networks which transmits the signals in a directional manner. 5G beamforming making a strong wireless connection toward a receiving end. In conventional systems when small cells are not using beamforming, moving signals to particular areas is quite difficult. Beamforming counter this issue using beamforming small cells are able to transmit the signals in particular direction towards a device like mobile phone, laptops, autonomous vehicle and IoT devices. Beamforming is improving the efficiency and saves the energy of the 5G network. Beamforming is broadly divided into three categories: Digital beamforming, analog beamforming and hybrid beamforming. Digital beamforming: multiuser MIMO is equal to digital beamforming which is mainly used in LTE Advanced Pro and in 5G NR. In digital beamforming the same frequency or time resources can be used to transmit the data to multiple users at the same time which improves the cell capacity of wireless networks. Analog Beamforming: In mmWave frequency range 5G NR analog beamforming is a very important approach which improves the coverage. In digital beamforming there are chances of high pathloss in mmWave as only one beam per set of antenna is formed. While the analog beamforming saves high pathloss in mmWave. Hybrid beamforming: hybrid beamforming is a combination of both analog beamforming and digital beamforming. In the implementation of MmWave in 5G network hybrid beamforming will be used [ 84 ].
Wireless signals in the 4G network are spreading in large areas, and nature is not Omnidirectional. Thus, energy depletes rapidly, and users who are accessing these signals also face interference problems. The beamforming technique is used in the 5G network to resolve this issue. In beamforming signals are directional. They move like a laser beam from the base station to the user, so signals seem to be traveling in an invisible cable. Beamforming helps achieve a faster data rate; as the signals are directional, it leads to less energy consumption and less interference. In [ 21 ], investigators evolve some techniques which reduce interference and increase system efficiency of the 5G mobile network. In this survey article, the authors covered various challenges faced while designing an optimized beamforming algorithm. Mainly focused on different design parameters such as performance evaluation and power consumption. In addition, they also described various issues related to beamforming like CSI, computation complexity, and antenna correlation. They also covered various research to cover how beamforming helps implement MIMO in next-generation mobile networks [ 85 ]. Figure 8 shows the pictorial representation of communication with and without using beamforming.

Pictorial Representation of communication with and without using beamforming.
5.3. Mobile Edge Computing
Mobile Edge Computing (MEC) [ 24 ]: MEC is an extended version of cloud computing that brings cloud resources closer to the end-user. When we talk about computing, the very first thing that comes to our mind is cloud computing. Cloud computing is a very famous technology that offers many services to end-user. Still, cloud computing has many drawbacks. The services available in the cloud are too far from end-users that create latency, and cloud user needs to download the complete application before use, which also increases the burden to the device [ 86 ]. MEC creates an edge between the end-user and cloud server, bringing cloud computing closer to the end-user. Now, all the services, namely, video conferencing, virtual software, etc., are offered by this edge that improves cloud computing performance. Another essential feature of MEC is that the application is split into two parts, which, first one is available at cloud server, and the second is at the user’s device. Therefore, the user need not download the complete application on his device that increases the performance of the end user’s device. Furthermore, MEC provides cloud services at very low latency and less bandwidth. In [ 23 , 87 ], the author’s investigation proved that successful deployment of MEC in 5G network increases the overall performance of 5G architecture. Graphical differentiation between cloud computing and mobile edge computing is presented in Figure 9 .

Pictorial representation of cloud computing vs. mobile edge computing.
6. 5G Security
Security is the key feature in the telecommunication network industry, which is necessary at various layers, to handle 5G network security in applications such as IoT, Digital forensics, IDS and many more [ 88 , 89 ]. The authors [ 90 ], discussed the background of 5G and its security concerns, challenges and future directions. The author also introduced the blockchain technology that can be incorporated with the IoT to overcome the challenges in IoT. The paper aims to create a security framework which can be incorporated with the LTE advanced network, and effective in terms of cost, deployment and QoS. In [ 91 ], author surveyed various form of attacks, the security challenges, security solutions with respect to the affected technology such as SDN, Network function virtualization (NFV), Mobile Clouds and MEC, and security standardizations of 5G, i.e., 3GPP, 5GPPP, Internet Engineering Task Force (IETF), Next Generation Mobile Networks (NGMN), European Telecommunications Standards Institute (ETSI). In [ 92 ], author elaborated various technological aspects, security issues and their existing solutions and also mentioned the new emerging technological paradigms for 5G security such as blockchain, quantum cryptography, AI, SDN, CPS, MEC, D2D. The author aims to create new security frameworks for 5G for further use of this technology in development of smart cities, transportation and healthcare. In [ 93 ], author analyzed the threats and dark threat, security aspects concerned with SDN and NFV, also their Commercial & Industrial Security Corporation (CISCO) 5G vision and new security innovations with respect to the new evolving architectures of 5G [ 94 ].
AuthenticationThe identification of the user in any network is made with the help of authentication. The different mobile network generations from 1G to 5G have used multiple techniques for user authentication. 5G utilizes the 5G Authentication and Key Agreement (AKA) authentication method, which shares a cryptographic key between user equipment (UE) and its home network and establishes a mutual authentication process between the both [ 95 ].
Access Control To restrict the accessibility in the network, 5G supports access control mechanisms to provide a secure and safe environment to the users and is controlled by network providers. 5G uses simple public key infrastructure (PKI) certificates for authenticating access in the 5G network. PKI put forward a secure and dynamic environment for the 5G network. The simple PKI technique provides flexibility to the 5G network; it can scale up and scale down as per the user traffic in the network [ 96 , 97 ].
Communication Security 5G deals to provide high data bandwidth, low latency, and better signal coverage. Therefore secure communication is the key concern in the 5G network. UE, mobile operators, core network, and access networks are the main focal point for the attackers in 5G communication. Some of the common attacks in communication at various segments are Botnet, message insertion, micro-cell, distributed denial of service (DDoS), and transport layer security (TLS)/secure sockets layer (SSL) attacks [ 98 , 99 ].
Encryption The confidentiality of the user and the network is done using encryption techniques. As 5G offers multiple services, end-to-end (E2E) encryption is the most suitable technique applied over various segments in the 5G network. Encryption forbids unauthorized access to the network and maintains the data privacy of the user. To encrypt the radio traffic at Packet Data Convergence Protocol (PDCP) layer, three 128-bits keys are applied at the user plane, nonaccess stratum (NAS), and access stratum (AS) [ 100 ].
7. Summary of 5G Technology Based on Above-Stated Challenges
In this section, various issues addressed by investigators in 5G technologies are presented in Table 13 . In addition, different parameters are considered, such as throughput, latency, energy efficiency, data rate, spectral efficiency, fairness & computing capacity, transmission rate, coverage, cost, security requirement, performance, QoS, power optimization, etc., indexed from R1 to R14.
Summary of 5G Technology above stated challenges (R1:Throughput, R2:Latency, R3:Energy Efficiency, R4:Data Rate, R5:Spectral efficiency, R6:Fairness & Computing Capacity, R7:Transmission Rate, R8:Coverage, R9:Cost, R10:Security requirement, R11:Performance, R12:Quality of Services (QoS), R13:Power Optimization).
8. Conclusions
This survey article illustrates the emergence of 5G, its evolution from 1G to 5G mobile network, applications, different research groups, their work, and the key features of 5G. It is not just a mobile broadband network, different from all the previous mobile network generations; it offers services like IoT, V2X, and Industry 4.0. This paper covers a detailed survey from multiple authors on different technologies in 5G, such as massive MIMO, Non-Orthogonal Multiple Access (NOMA), millimeter wave, small cell, MEC (Mobile Edge Computing), beamforming, optimization, and machine learning in 5G. After each section, a tabular comparison covers all the state-of-the-research held in these technologies. This survey also shows the importance of these newly added technologies and building a flexible, scalable, and reliable 5G network.
9. Future Findings
This article covers a detailed survey on the 5G mobile network and its features. These features make 5G more reliable, scalable, efficient at affordable rates. As discussed in the above sections, numerous technical challenges originate while implementing those features or providing services over a 5G mobile network. So, for future research directions, the research community can overcome these challenges while implementing these technologies (MIMO, NOMA, small cell, mmWave, beam-forming, MEC) over a 5G network. 5G communication will bring new improvements over the existing systems. Still, the current solutions cannot fulfill the autonomous system and future intelligence engineering requirements after a decade. There is no matter of discussion that 5G will provide better QoS and new features than 4G. But there is always room for improvement as the considerable growth of centralized data and autonomous industry 5G wireless networks will not be capable of fulfilling their demands in the future. So, we need to move on new wireless network technology that is named 6G. 6G wireless network will bring new heights in mobile generations, as it includes (i) massive human-to-machine communication, (ii) ubiquitous connectivity between the local device and cloud server, (iii) creation of data fusion technology for various mixed reality experiences and multiverps maps. (iv) Focus on sensing and actuation to control the network of the entire world. The 6G mobile network will offer new services with some other technologies; these services are 3D mapping, reality devices, smart homes, smart wearable, autonomous vehicles, artificial intelligence, and sense. It is expected that 6G will provide ultra-long-range communication with a very low latency of 1 ms. The per-user bit rate in a 6G wireless network will be approximately 1 Tbps, and it will also provide wireless communication, which is 1000 times faster than 5G networks.
Acknowledgments
Author contributions.
Conceptualization: R.D., I.Y., G.C., P.L. data gathering: R.D., G.C., P.L, I.Y. funding acquisition: I.Y. investigation: I.Y., G.C., G.P. methodology: R.D., I.Y., G.C., P.L., G.P., survey: I.Y., G.C., P.L, G.P., R.D. supervision: G.C., I.Y., G.P. validation: I.Y., G.P. visualization: R.D., I.Y., G.C., P.L. writing, original draft: R.D., I.Y., G.C., P.L., G.P. writing, review, and editing: I.Y., G.C., G.P. All authors have read and agreed to the published version of the manuscript.
This paper was supported by Soonchunhyang University.
Institutional Review Board Statement
Informed consent statement, data availability statement, conflicts of interest.
The authors declare no conflict of interest.
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Case Study Hub | Samples, Examples and Writing Tips
Case study on data communication and networking, case study on data communication and networking:.
Data communication and networking is the connection of a great number of computers for the purpose of information exchange. Today information is the most important resource, because with its help one can receive education, learn something new, make a business, change the life of the country, etc. In order to maintain the process of information exchange numerous appliances and techniques have been invented. First of all it is the local networking or the worldwide Internet, which helps users produce, store, analysis and process information and exchange it form the different parts of the world. Information technology has become one of the most profitable and important spheres, because the IT analysts manage the process of communication and networking and improve this process constantly. The whole information which can be found in the Internet is stored on the special databases and if one wants to get access to the certain type of data, he can surf the web and find it on a server.
We can write a Custom Case Study on Data Communication & Networking for you!
It is obvious that the technology of networking and data communication is constantly improving and the experts work hard to make the access to the information quicker and easier. Nearly every day new software and networking technologies appear and provide users with the high-quality and rapid means of information processing and communication. Today the web has become the core means of communication, because it is easier and cheaper to write an email or an instant message to any part of the world than to ring someone up or write a common paper letter. So the intention to save time is the main reason why so much attention is paid to the development of the IT.
Data communication and networking is quite an interesting but challenging topic, because one should be able to analyze the problem professionally combining his technical knowledge with the humanity disciplines. A good data communication and networking case study is supposed to explain the topic profoundly and solve the puzzle of the case successfully. One should evaluate the cause and effect of the problem and suggest the best methods to solve it well and demonstrate his analytical and critical thinking skills.
In order to prepare a successful case study on the topic one should take advantage of the Internet and read a free example case study on data communication and networking written by an expert. It is fairly smart to look through a good free sample case study on data communication and networking analyzed by the real professional, because only with this kind of help a student will be able to learn something about the problem and fulfill the high-quality analysis of the problem and format the text according to the general requirements.
At EssayLib.com writing service you can buy a custom case study on Data Communication and Networking topics. Your case study will be written from scratch. We hire top-rated Ph.D. and Master’s writers only to provide students with professional case study help at affordable rates. Each customer will get a non-plagiarized paper with timely delivery. Just visit our website and fill in the order form with all paper details:

Related Posts:
- Case Study – Amazon: One E-Store to Rule Them All
- Case Study – Zara International: Fashion at…
- Apple Inc Case Study Sample
- Health Management: Business Case Study
- Case Study on Zappos – How They Did It
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *

IMAGES
VIDEO
COMMENTS
Business Data Communications and Networking, 14th Edition presents a classroom-tested approach to the subject, combining foundational concepts, practical exercises, and real-world case studies. The text provides a balanced, well-rounded presentation of data communications while highlighting its importance to nearly every aspect of modern business.
University of Melbourne. Data Center Networking. Cisco Nexus 9000 Series Switches. Cisco Data Center Network Manager (DCNM) Education. APJC. Find out how real businesses have used Cisco Data Center Networking solutions to enable transformation and reach their goals.
6.263J / 16.37J focuses on the fundamentals of data communication networks. One goal is to give some insight into the rationale of why networks are structured the way they are today and to understand the issues facing the designers of next-generation data networks. Much of the course focuses on network algorithms and their performance. Students are expected to have a strong mathematical ...
3.3 Distributed Data; 3.4 Networking Implications of DDP; 3.5 Big Data Infrastructure Considerations; 3.6 Summary; 3.7 Key Terms, Review Questions, and Problems; Case Study III Managing Massive Data Warehouses at MasterCard International (ONLINE) PART TWO DATA COMMUNICATIONS. Chapter 4 Data Transmission. 4.1 Signals for Conveying Information
Abstract. A computer network, sometimes known as a data network, is a kind of telecommunications network that enables computers to communicate with one another. Data is passed between networked computing devices through data links in computer networks. Cable or wireless media are used to establish connections (network links) between nodes.
The network drives our business. Cisco's network is made up of systems that address the unique needs of each place in the network, connected by a common infrastructure. These systems help us speed new technology, protect network and data integrity, and improve employee productivity. See our IBN journey.
Business Data Communications and Networking, 14 th Edition presents a classroom-tested approach to the subject, combining foundational concepts, practical exercises, and real-world case studies. The text provides a balanced, well-rounded presentation of data communications while highlighting its importance to nearly every aspect of modern business.
Data communication in agricultural IoT systems could include different technologies, such as analog or digital communication technologies, program-controlled data exchange technology, networking technology, broadband IP technology, access network and access technology, and many more. In an IoT system, the networked devices could receive input ...
The authors discuss data communications networks (DCNs) used by operating telephone companies to interconnect large numbers of telecommunications network elements with operations systems and ...
Abstract. A computer network, sometimes known as a data network, is a kind of telecommunications network that enables computers to communicate with one another. Data is passed between networked ...
Data Communication and Networking. DP Nagpal. S. Chand Publishing, 2011 - Computers - 568 pages. Second Edition 2014 The book is intended for both an academic and a professional audience. This book also serves as a basic reference volume and is suitable for self study for those who have little or no background knowledge of the subject.
Figure 15.2 shows the typical architecture of a campus network. 1. The core layer is the backbone of the campus network and the core of data exchange in the campus。. It connects various components of the campus network, such as the aggregation layer, data center, egress area and network management area. 2.
Computer Networking: Case Study Analysis. By: GPDCM Jayasekara. 2. Case Overview. To understand the Local and Wide Area Network technologies, materials and protocols relate. them to develop ...
RAD has supplied over 150 global service providers with more than 16 million units, making RAD a proven leader in data communication networking solutions. Review our case studies. RAD is a global leader for telecom access solutions. As an industry pioneer for over 40 years, RAD reliably supplies worldwide communications service providers and ...
For You For Only $13.90/page! Data communication and networking is quite an interesting but challenging topic, because one should be able to analyze the problem professionally combining his technical knowledge with the humanity disciplines. A good data communication and networking case study is supposed to explain the topic profoundly and solve ...
Conclusion 1 was developed in Chapters 2 and 3 and summarized in Tables 2-1, 2-2, and 3-1 and the discussions surrounding them. It sets the stage for the committee's inquiry into the state of knowledge about these networks. Conclusion 2. Fundamental knowledge about the prediction of the properties of complex networks is primitive.
The ESANET project provided the participating institutions the opportunity to experiment with regional and international microcomputer-based communication. The aim of the experimentation was to establish the viability of the regional computer networking for data communication from the technical and management perspectives.
Business Data Communications and Networking, 14 th Edition presents a classroom-tested approach to the subject, combining foundational concepts, practical exercises, and real-world case studies. The text provides a balanced, well-rounded presentation of data communications while highlighting its importance to nearly every aspect of modern business.
wireless media. The best-known computer network is the Internet. Data communication is said to be local if communicating devices are in the same building or a similarly restricted geographical area. A simple data communication system has shown in Fig-1. There are three types of data communications networks exist.
Networking as a tool for customer data management. Networking plays a crucial role in customer data management, as highlighted in Case Study 2: Salesforce. By leveraging networking strategies, companies can effectively collect, store, and analyze customer data to gain valuable insights and enhance their overall business operations.
Data Communication and Networking Book. Below is the list of data communication and networking book recommended by the top university in India. Behrouz A. Forouzan, Sophia Chung Fegan, "Data Communications and Networking", Fifth Edition, Science Engineering & Math Publications, 2012.
1. Introduction. Most recently, in three decades, rapid growth was marked in the field of wireless communication concerning the transition of 1G to 4G [1,2].The main motto behind this research was the requirements of high bandwidth and very low latency. 5G provides a high data rate, improved quality of service (QoS), low-latency, high coverage, high reliability, and economically affordable ...
The three journals in this series are: Communications in Statistics: Case Studies, Data Analysis and Applications. Communications in Statistics - Simulation and Computation. Communications in Statistics - Theory and Methods. The prestigious and experienced members of our international Editorial Board will guide you from submission to publication.
A good data communication and networking case study is supposed to explain the topic profoundly and solve the puzzle of the case successfully. One should evaluate the cause and effect of the problem and suggest the best methods to solve it well and demonstrate his analytical and critical thinking skills. In order to prepare a successful case ...
To narrow the gap in transport development between cities and achieve sustainable development in regional transport, this study took the Shandong Peninsula urban agglomeration as the research object and using real-time path planning data assessed accessibility of the traffic network under two travel scenarios: cars and car-connected train.