Numbers, Facts and Trends Shaping Your World
Read our research on:
Full Topic List

Regions & Countries
- Publications
- Our Methods
- Short Reads
- Tools & Resources
Read Our Research On:
Americans’ complicated feelings about social media in an era of privacy concerns
Amid public concerns over Cambridge Analytica’s use of Facebook data and a subsequent movement to encourage users to abandon Facebook , there is a renewed focus on how social media companies collect personal information and make it available to marketers.
Pew Research Center has studied the spread and impact of social media since 2005, when just 5% of American adults used the platforms. The trends tracked by our data tell a complex story that is full of conflicting pressures. On one hand, the rapid growth of the platforms is testimony to their appeal to online Americans. On the other, this widespread use has been accompanied by rising user concerns about privacy and social media firms’ capacity to protect their data.
All this adds up to a mixed picture about how Americans feel about social media. Here are some of the dynamics.
People like and use social media for several reasons
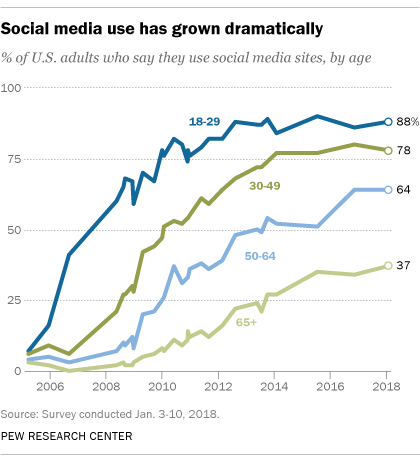
About seven-in-ten American adults (69%) now report they use some kind of social media platform (not including YouTube) – a nearly fourteenfold increase since Pew Research Center first started asking about the phenomenon. The growth has come across all demographic groups and includes 37% of those ages 65 and older.
The Center’s polls have found over the years that people use social media for important social interactions like staying in touch with friends and family and reconnecting with old acquaintances. Teenagers are especially likely to report that social media are important to their friendships and, at times, their romantic relationships .
Beyond that, we have documented how social media play a role in the way people participate in civic and political activities, launch and sustain protests , get and share health information , gather scientific information , engage in family matters , perform job-related activities and get news . Indeed, social media is now just as common a pathway to news for people as going directly to a news organization website or app.
Our research has not established a causal relationship between people’s use of social media and their well-being. But in a 2011 report, we noted modest associations between people’s social media use and higher levels of trust, larger numbers of close friends, greater amounts of social support and higher levels of civic participation.
People worry about privacy and the use of their personal information
While there is evidence that social media works in some important ways for people, Pew Research Center studies have shown that people are anxious about all the personal information that is collected and shared and the security of their data.
Overall, a 2014 survey found that 91% of Americans “agree” or “strongly agree” that people have lost control over how personal information is collected and used by all kinds of entities. Some 80% of social media users said they were concerned about advertisers and businesses accessing the data they share on social media platforms, and 64% said the government should do more to regulate advertisers.
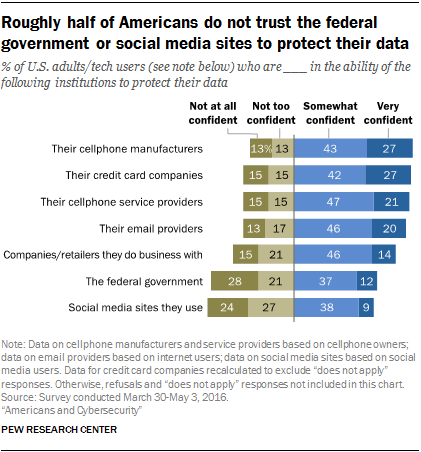
Another survey last year found that just 9% of social media users were “very confident” that social media companies would protect their data . About half of users were not at all or not too confident their data were in safe hands.
Moreover, people struggle to understand the nature and scope of the data collected about them. Just 9% believe they have “a lot of control” over the information that is collected about them, even as the vast majority (74%) say it is very important to them to be in control of who can get information about them.
Six-in-ten Americans (61%) have said they would like to do more to protect their privacy. Additionally, two-thirds have said current laws are not good enough in protecting people’s privacy, and 64% support more regulation of advertisers.
Some privacy advocates hope that the European Union’s General Data Protection Regulation , which goes into effect on May 25, will give users – even Americans – greater protections about what data tech firms can collect, how the data can be used, and how consumers can be given more opportunities to see what is happening with their information.
People’s issues with the social media experience go beyond privacy
In addition to the concerns about privacy and social media platforms uncovered in our surveys, related research shows that just 5% of social media users trust the information that comes to them via the platforms “a lot.”
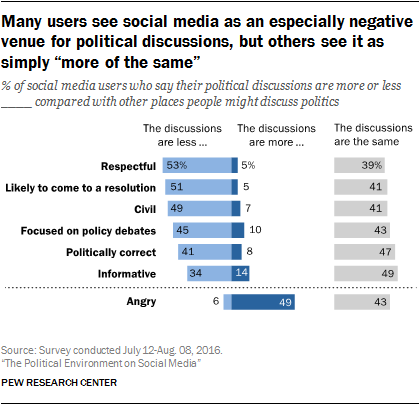
Moreover, social media users can be turned off by what happens on social media. For instance, social media sites are frequently cited as places where people are harassed . Near the end of the 2016 election campaign, 37% of social media users said they were worn out by the political content they encountered, and large shares said social media interactions with those opposed to their views were stressful and frustrating. Large shares also said that social media interactions related to politics were less respectful, less conclusive, less civil and less informative than offline interactions.
A considerable number of social media users said they simply ignored political arguments when they broke out in their feeds. Others went steps further by blocking or unfriending those who offended or bugged them.
Why do people leave or stay on social media platforms?
The paradox is that people use social media platforms even as they express great concern about the privacy implications of doing so – and the social woes they encounter. The Center’s most recent survey about social media found that 59% of users said it would not be difficult to give up these sites, yet the share saying these sites would be hard to give up grew 12 percentage points from early 2014.
Some of the answers about why people stay on social media could tie to our findings about how people adjust their behavior on the sites and online, depending on personal and political circumstances. For instance, in a 2012 report we found that 61% of Facebook users said they had taken a break from using the platform. Among the reasons people cited were that they were too busy to use the platform, they lost interest, they thought it was a waste of time and that it was filled with too much drama, gossip or conflict.
In other words, participation on the sites for many people is not an all-or-nothing proposition.
People pursue strategies to try to avoid problems on social media and the internet overall. Fully 86% of internet users said in 2012 they had taken steps to try to be anonymous online. “Hiding from advertisers” was relatively high on the list of those they wanted to avoid.
Many social media users fine-tune their behavior to try to make things less challenging or unsettling on the sites, including changing their privacy settings and restricting access to their profiles. Still, 48% of social media users reported in a 2012 survey they have difficulty managing their privacy controls.
After National Security Agency contractor Edward Snowden disclosed details about government surveillance programs starting in 2013, 30% of adults said they took steps to hide or shield their information and 22% reported they had changed their online behavior in order to minimize detection.
One other argument that some experts make in Pew Research Center canvassings about the future is that people often find it hard to disconnect because so much of modern life takes place on social media. These experts believe that unplugging is hard because social media and other technology affordances make life convenient and because the platforms offer a very efficient, compelling way for users to stay connected to the people and organizations that matter to them.
Note: See topline results for overall social media user data here (PDF).
- Emerging Technology
- Online Privacy & Security
- Privacy Rights
- Social Media
- Technology Policy Issues

Lee Rainie is director of internet and technology research at Pew Research Center .
Many Americans think generative AI programs should credit the sources they rely on
Americans’ use of chatgpt is ticking up, but few trust its election information, q&a: how we used large language models to identify guests on popular podcasts, computer chips in human brains: how americans view the technology amid recent advances, striking findings from 2023, most popular.
1615 L St. NW, Suite 800 Washington, DC 20036 USA (+1) 202-419-4300 | Main (+1) 202-857-8562 | Fax (+1) 202-419-4372 | Media Inquiries
Research Topics
- Age & Generations
- Coronavirus (COVID-19)
- Economy & Work
- Family & Relationships
- Gender & LGBTQ
- Immigration & Migration
- International Affairs
- Internet & Technology
- Methodological Research
- News Habits & Media
- Non-U.S. Governments
- Other Topics
- Politics & Policy
- Race & Ethnicity
- Email Newsletters
ABOUT PEW RESEARCH CENTER Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .
Copyright 2024 Pew Research Center
Terms & Conditions
Privacy Policy
Cookie Settings
Reprints, Permissions & Use Policy
Privacy Issues in Social Media
This essay about privacy issues in social media discusses the complexities and risks associated with the vast amounts of personal data shared on platforms like Facebook, Twitter, and Instagram. It highlights the lack of transparency in how companies use this data, often hidden behind dense privacy policies, and the risks of data being shared with third parties for purposes that range from benign to malicious. The essay also touches on the psychological impact of constant surveillance, particularly on younger users, and the broader societal implications, including political manipulation exemplified by the Cambridge Analytica scandal. It concludes with a call for robust regulatory measures, like the EU’s General Data Protection Regulation, and emphasizes the need for a systemic approach to protect privacy, involving not just users but also companies and governments in a collective effort to manage and safeguard personal information on social media.
How it works
When discussing privacy issues in social media, the landscape is complex and fraught with ethical dilemmas and potential risks. As the use of social platforms like Facebook, Twitter, and Instagram has become nearly ubiquitous, the line between private life and public exposure has significantly blurred. This merging raises profound questions about personal data’s collection, use, and security by these influential digital platforms.
At the heart of the privacy conundrum on social media is the sheer volume of personal information users willingly share online.
From birthdays and anniversaries to work history and family photos, the amount of intimate data circulating on these platforms is staggering. While it’s true that sharing this information can help maintain connections and even foster new ones, it also sets the stage for more insidious uses of our data.
One major issue is transparency—or the lack thereof. Social media companies have mastered the art of hiding their data practices behind dense privacy policies that are seldom read and even less frequently understood. This lack of clarity is not accidental; it serves to obscure the extent to which data is not just collected but also analyzed and monetized. Most users are unaware of how deep the data-mining goes and how their information contributes to vast economic networks that transcend simple social interactions.
The complications continue when considering how social media data is shared with third parties. The intentions of these third parties can vary widely, ranging from market research firms analyzing trends to advertisers targeting users with unnerving precision. The potential for misuse becomes clear when you consider incidents like the Cambridge Analytica scandal, where millions of Facebook users’ data was used without their explicit consent to influence political campaigns. Such breaches illustrate not only the potential for misuse but also the global impact that mishandled social media data can have.
Beyond the implications for individual privacy and global politics, there’s also a personal cost to this constant surveillance. The psychological impact of knowing one’s actions, interactions, and even inactions are constantly monitored can lead to a phenomenon known as ‘social cooling’—a form of social behavior and expression alteration due to the awareness of being watched. This effect is particularly concerning for younger generations, who are not only more active on these platforms but are also in critical stages of developing their identities.
Recognizing these issues, there has been a push for more robust regulatory measures. The European Union’s General Data Protection Regulation (GDPR) is one of the more prominent efforts to safeguard personal data and restore some control to users. The GDPR not only mandates that companies protect the personal information they gather but also empowers users with rights to access, correct, and delete their data. While this regulation is a step in the right direction, the global nature of the internet complicates enforcement, and many users around the world remain unprotected by such policies.
In the U.S., the response has been more fragmented, with calls for American equivalents to the GDPR growing louder in the wake of repeated data privacy scandals. These calls reflect a growing awareness that privacy cannot solely be managed by individual users adjusting their settings—a systemic approach is needed. However, creating and enforcing such regulations in a way that balances the benefits of social media with privacy rights remains a significant challenge.
The conclusion seems clear: as valuable as social media can be in connecting us, its role in our lives must be carefully managed to protect our privacy. This management is not just the responsibility of users but also of companies and governments. Users must educate themselves about their data rights and practice digital hygiene, companies should commit to ethical data practices and transparency, and governments need to enact and enforce regulations that hold these companies accountable.
Ultimately, addressing privacy issues in social media requires a collective effort and an ongoing dialogue among all stakeholders involved. Only through sustained engagement can we hope to harness the benefits of social media while safeguarding against its potential harms. As we move forward, it’s imperative to keep these conversations alive and active, ensuring that our digital environments reflect the values we hold dear in our offline lives.
Cite this page
Privacy Issues in Social Media. (2024, May 01). Retrieved from https://papersowl.com/examples/privacy-issues-in-social-media/
"Privacy Issues in Social Media." PapersOwl.com , 1 May 2024, https://papersowl.com/examples/privacy-issues-in-social-media/
PapersOwl.com. (2024). Privacy Issues in Social Media . [Online]. Available at: https://papersowl.com/examples/privacy-issues-in-social-media/ [Accessed: 12 May. 2024]
"Privacy Issues in Social Media." PapersOwl.com, May 01, 2024. Accessed May 12, 2024. https://papersowl.com/examples/privacy-issues-in-social-media/
"Privacy Issues in Social Media," PapersOwl.com , 01-May-2024. [Online]. Available: https://papersowl.com/examples/privacy-issues-in-social-media/. [Accessed: 12-May-2024]
PapersOwl.com. (2024). Privacy Issues in Social Media . [Online]. Available at: https://papersowl.com/examples/privacy-issues-in-social-media/ [Accessed: 12-May-2024]
Don't let plagiarism ruin your grade
Hire a writer to get a unique paper crafted to your needs.

Our writers will help you fix any mistakes and get an A+!
Please check your inbox.
You can order an original essay written according to your instructions.
Trusted by over 1 million students worldwide
1. Tell Us Your Requirements
2. Pick your perfect writer
3. Get Your Paper and Pay
Hi! I'm Amy, your personal assistant!
Don't know where to start? Give me your paper requirements and I connect you to an academic expert.
short deadlines
100% Plagiarism-Free
Certified writers
Social Media: The Privacy Issues
Sharing private information through social media is commonplace in today’s society and lifestyle. Individuals use numerous social networking sites such as Facebook and Instagram. These users share their private information, particularly upon registration to become a member of the sites. They also reveal their private information by making regular updates and posts that they put online. As a result, an individual can easily be traced and manipulated through the information offered on these websites making internet privacy a major concern. This sheds light on the importance of learning technological abilities to enable social media users deal with the issue of privacy on these websites. This argumentative essay will discuss the privacy issues that users may encounter on social media and argue that it is important to have a balance between privacy and online confidentiality to operate effectively in both the offline and online worlds.
One of the disadvantages of social media is its exposure of people’s private lives to the online world and worldwide audience. Users of social media sites, such as Facebook, have become more and more open as they willingly reveal too much of their personal information on these websites. Today, the issue of sharing too much personal information has become the societal standard, forgetting that this information can be utilized in a variety of ways, including negative methods such as stalking or identity theft (Kelly and Guskin). Users of social media sites must examine what information they are uploading or sharing online and with whom they are sharing it (Kelly and Guskin). Through this, a balance between privacy and internet disclosure of information must be achieved and maintained, as failure to do so may negatively affect online users.
A thorough awareness of privacy concerns and social media is essential to comprehend this issue. Recently, many people have used and been drawn to social media sites as they allow users to communicate and relate in different ways. These websites enable individuals to create a network that characterizes their social contacts, share online content easily, provide platforms for online communication, and share their daily activities and experiences with their mates and the virtual communities (Ayaburi and Daniel 171). However, social media has led to several potential hazards to users’ privacy. This is evident when data about a user is being uploaded and further distributed in many circumstances without authorization, request, or approval (Ayaburi and Daniel 171). As a result, social media tests and distorts private information.
Furthermore, social media users have grown accustomed to sharing personal information, and as a result, they are unaware of the hazards and risks that they subject themselves to and confront online due to privacy concerns. It is enjoyable and great to share their daily activities and lifestyles with family and friends online, but as Kelly and Guskin point out, digital material is constantly permanent and may be duplicated, reused, and spread. Users will supply information about their location, region, mobile number, and birthdate, among other things, when building a social media profile. Such data is freely accessible by hackers and the general public, and it is one of the ways through which identity theft occurs (Ayaburi and Daniel 172). Since the information is shared and saved on social media networking sites, one’s identity can be stolen or viewed by anyone.
Stalking is another issue that arises due to privacy concerns. Users can choose to make their profiles private, but their group memberships and friendships links are usually available to their shared public (Ayaburi and Daniel 172). This is one of the ways that data leakage occurs; individuals who are not friends may see those postings in which they are tagged, and they can access and read users’ personal information even if their profile is configured to be private. Additionally, such data links may allow malicious actors to be aware of and track one’s internet activity. Such dangers might also arise when a person befriends other individuals online without taking the time to learn about their identities (Kelly and Guskin). Individuals sharing their everyday activities online is now the standard and trend (Ayaburi and Daniel 176). Users often post and share images while at the mall, and this is one of the ways that stalkers may track users’ every step, as well as their activities and routines on a daily basis.
Despite the need for discretion when it relates to exposing personal data, there are a lot of advantages to participating in online discussions. In real life, the establishment of social ties allows for selective disclosure of personal data, a sense of being closer to another person, and knowledge of each other (Ayaburi and Daniel 179). Individuals can now form and build social relationships with one another by doing so through social networking sites. This allows them to get to know other users better and create online friendships (Ayaburi and Daniel 179). Therefore, social media has provided people with a channel and network with which they can socialize and build social ties with others regardless of time or location.
In addition to this, social media has had a tremendous impact on today’s world, and it has transformed the way people think about the amount of data that should and should not be displayed or shared publicly (Kelly and Guskin). When computers and the internet first became common in the early 2000s, it was inconceivable for people to share their location, images, or their names online without considering their privacy and security. Users have allowed and encouraged this technology to transform and increase their zones of tolerance because of the flexibility it offers them to trade information online, making it pleasant and easy to do so over time, thanks to the development of social media in the mid-2000s (Kelly, and Guskin). Ayaburi and Daniel go so far as to say that privacy is no longer considered the social norm (181). Despite the benefits of online disclosure, such as the union of individuals and the formation of social relationships, users must remember and realize that they must use the majority of social media while preserving and prioritizing their privacy.
The relationship between social media and privacy has been highlighted and considered critical and necessary in sharing information on social media. The consequences and hazards of ignoring privacy concerns have been weighed against the social advantages of the disclosure. As a result, logical answers for social networking users include understanding how these media sites operate and function and making the most use of the media sites’ privacy policies and capabilities to create a safer online world for sharing personal data and talking to others. The ability of social media to improve social interactions must be welcomed and appreciated, but a balance between websites disclosure of information and privacy must be maintained on a regular basis.
Works Cited
Ayaburi, Emmanuel W., and Daniel N. Treku. “Effect of Penitence on Social Media Trust and Privacy Concerns: The Case of Facebook.” International Journal of Information Management, vol. 50, 2020, pp. 171-181, Web.
Kelly, Heather, and Emily Guskin. “Americans Widely Distrust Facebook, TikTok and Instagram with Their Data, Poll Finds.” The Washington Post, WP Company, Web.
Cite this paper
- Chicago (N-B)
- Chicago (A-D)
StudyCorgi. (2023, March 2). Social Media: The Privacy Issues. https://studycorgi.com/social-media-the-privacy-issues/
"Social Media: The Privacy Issues." StudyCorgi , 2 Mar. 2023, studycorgi.com/social-media-the-privacy-issues/.
StudyCorgi . (2023) 'Social Media: The Privacy Issues'. 2 March.
1. StudyCorgi . "Social Media: The Privacy Issues." March 2, 2023. https://studycorgi.com/social-media-the-privacy-issues/.
Bibliography
StudyCorgi . "Social Media: The Privacy Issues." March 2, 2023. https://studycorgi.com/social-media-the-privacy-issues/.
StudyCorgi . 2023. "Social Media: The Privacy Issues." March 2, 2023. https://studycorgi.com/social-media-the-privacy-issues/.
This paper, “Social Media: The Privacy Issues”, was written and voluntary submitted to our free essay database by a straight-A student. Please ensure you properly reference the paper if you're using it to write your assignment.
Before publication, the StudyCorgi editorial team proofread and checked the paper to make sure it meets the highest standards in terms of grammar, punctuation, style, fact accuracy, copyright issues, and inclusive language. Last updated: November 13, 2023 .
If you are the author of this paper and no longer wish to have it published on StudyCorgi, request the removal . Please use the “ Donate your paper ” form to submit an essay.
- Share full article
Advertisement
Supported by
The Battle for Digital Privacy Is Reshaping the Internet
As Apple and Google enact privacy changes, businesses are grappling with the fallout, Madison Avenue is fighting back and Facebook has cried foul.

By Brian X. Chen
Listen to This Article
SAN FRANCISCO — Apple introduced a pop-up window for iPhones in April that asks people for their permission to be tracked by different apps.
Google recently outlined plans to disable a tracking technology in its Chrome web browser.
And Facebook said last month that hundreds of its engineers were working on a new method of showing ads without relying on people’s personal data.
The developments may seem like technical tinkering, but they were connected to something bigger: an intensifying battle over the future of the internet. The struggle has entangled tech titans, upended Madison Avenue and disrupted small businesses. And it heralds a profound shift in how people’s personal information may be used online, with sweeping implications for the ways that businesses make money digitally.
At the center of the tussle is what has been the internet’s lifeblood: advertising .
More than 20 years ago, the internet drove an upheaval in the advertising industry. It eviscerated newspapers and magazines that had relied on selling classified and print ads, and threatened to dethrone television advertising as the prime way for marketers to reach large audiences.
Instead, brands splashed their ads across websites, with their promotions often tailored to people’s specific interests. Those digital ads powered the growth of Facebook, Google and Twitter, which offered their search and social networking services to people without charge. But in exchange, people were tracked from site to site by technologies such as “ cookies, ” and their personal data was used to target them with relevant marketing.
Now that system, which ballooned into a $350 billion digital ad industry, is being dismantled. Driven by online privacy fears, Apple and Google have started revamping the rules around online data collection. Apple, citing the mantra of privacy, has rolled out tools that block marketers from tracking people. Google, which depends on digital ads, is trying to have it both ways by reinventing the system so it can continue aiming ads at people without exploiting access to their personal data.

If personal information is no longer the currency that people give for online content and services, something else must take its place. Media publishers, app makers and e-commerce shops are now exploring different paths to surviving a privacy-conscious internet, in some cases overturning their business models. Many are choosing to make people pay for what they get online by levying subscription fees and other charges instead of using their personal data.
Jeff Green, the chief executive of the Trade Desk, an ad-technology company in Ventura, Calif., that works with major ad agencies, said the behind-the-scenes fight was fundamental to the nature of the web.
“The internet is answering a question that it’s been wrestling with for decades, which is: How is the internet going to pay for itself?” he said.
The fallout may hurt brands that relied on targeted ads to get people to buy their goods. It may also initially hurt tech giants like Facebook — but not for long. Instead, businesses that can no longer track people but still need to advertise are likely to spend more with the largest tech platforms, which still have the most data on consumers.
David Cohen, chief executive of the Interactive Advertising Bureau, a trade group, said the changes would continue to “drive money and attention to Google, Facebook, Twitter.”
The shifts are complicated by Google’s and Apple’s opposing views on how much ad tracking should be dialed back. Apple wants its customers, who pay a premium for its iPhones, to have the right to block tracking entirely. But Google executives have suggested that Apple has turned privacy into a privilege for those who can afford its products.
For many people, that means the internet may start looking different depending on the products they use. On Apple gadgets, ads may be only somewhat relevant to a person’s interests, compared with highly targeted promotions inside Google’s web. Website creators may eventually choose sides, so some sites that work well in Google’s browser might not even load in Apple’s browser, said Brendan Eich, a founder of Brave, the private web browser.
“It will be a tale of two internets,” he said.
Businesses that do not keep up with the changes risk getting run over. Increasingly, media publishers and even apps that show the weather are charging subscription fees, in the same way that Netflix levies a monthly fee for video streaming. Some e-commerce sites are considering raising product prices to keep their revenues up.
Consider Seven Sisters Scones, a mail-order pastry shop in Johns Creek, Ga., which relies on Facebook ads to promote its items. Nate Martin, who leads the bakery’s digital marketing, said that after Apple blocked some ad tracking, its digital marketing campaigns on Facebook became less effective. Because Facebook could no longer get as much data on which customers like baked goods, it was harder for the store to find interested buyers online.
“Everything came to a screeching halt,” Mr. Martin said. In June, the bakery’s revenue dropped to $16,000 from $40,000 in May.
Sales have since remained flat, he said. To offset the declines, Seven Sisters Scones has discussed increasing prices on sampler boxes to $36 from $29.
Apple declined to comment, but its executives have said advertisers will adapt. Google said it was working on an approach that would protect people’s data but also let advertisers continue targeting users with ads.
Since the 1990s, much of the web has been rooted in digital advertising. In that decade, a piece of code planted in web browsers — the “cookie” — began tracking people’s browsing activities from site to site. Marketers used the information to aim ads at individuals, so someone interested in makeup or bicycles saw ads about those topics and products.
After the iPhone and Android app stores were introduced in 2008, advertisers also collected data about what people did inside apps by planting invisible trackers. That information was linked with cookie data and shared with data brokers for even more specific ad targeting.
The result was a vast advertising ecosystem that underpinned free websites and online services. Sites and apps like BuzzFeed and TikTok flourished using this model. Even e-commerce sites rely partly on advertising to expand their businesses.
But distrust of these practices began building. In 2018, Facebook became embroiled in the Cambridge Analytica scandal, where people’s Facebook data was improperly harvested without their consent. That same year, European regulators enacted the General Data Protection Regulation , laws to safeguard people’s information. In 2019, Google and Facebook agreed to pay record fines to the Federal Trade Commission to settle allegations of privacy violations.
In Silicon Valley, Apple reconsidered its advertising approach. In 2017, Craig Federighi, Apple’s head of software engineering, announced that the Safari web browser would block cookies from following people from site to site.
“It kind of feels like you’re being tracked, and that’s because you are,” Mr. Federighi said. “No longer.”
Last year, Apple announced the pop-up window in iPhone apps that asks people if they want to be followed for marketing purposes. If the user says no, the app must stop monitoring and sharing data with third parties.
That prompted an outcry from Facebook , which was one of the apps affected. In December, the social network took out full-page newspaper ads declaring that it was “standing up to Apple” on behalf of small businesses that would get hurt once their ads could no longer find specific audiences.
“The situation is going to be challenging for them to navigate,” Mark Zuckerberg, Facebook’s chief executive, said.
Facebook is now developing ways to target people with ads using insights gathered on their devices, without allowing personal data to be shared with third parties. If people who click on ads for deodorant also buy sneakers, Facebook can share that pattern with advertisers so they can show sneaker ads to that group. That would be less intrusive than sharing personal information like email addresses with advertisers.
“We support giving people more control over how their data is used, but Apple’s far-reaching changes occurred without input from the industry and those who are most impacted,” a Facebook spokesman said.
Since Apple released the pop-up window, more than 80 percent of iPhone users have opted out of tracking worldwide, according to ad tech firms. Last month, Peter Farago, an executive at Flurry, a mobile analytics firm owned by Verizon Media, published a post on LinkedIn calling the “time of death” for ad tracking on iPhones.
At Google, Sundar Pichai, the chief executive, and his lieutenants began discussing in 2019 how to provide more privacy without killing the company’s $135 billion online ad business. In studies, Google researchers found that the cookie eroded people’s trust. Google said its Chrome and ad teams concluded that the Chrome web browser should stop supporting cookies.
But Google also said it would not disable cookies until it had a different way for marketers to keep serving people targeted ads. In March, the company tried a method that uses its data troves to place people into groups based on their interests, so marketers can aim ads at those cohorts rather than at individuals. The approach is known as Federated Learning of Cohorts, or FLOC.
Plans remain in flux. Google will not block trackers in Chrome until 2023 .
Even so, advertisers said they were alarmed.
In an article this year, Sheri Bachstein, the head of IBM Watson Advertising, warned that the privacy shifts meant that relying solely on advertising for revenue was at risk. Businesses must adapt, she said, including by charging subscription fees and using artificial intelligence to help serve ads.
“The big tech companies have put a clock on us,” she said in an interview.
Kate Conger contributed reporting.
Brian X. Chen is the lead consumer technology writer for The Times. He reviews products and writes Tech Fix , a column about the social implications of the tech we use. Before joining The Times in 2011, he reported on Apple and the wireless industry for Wired. More about Brian X. Chen
Feb 15, 2023
6 Example Essays on Social Media | Advantages, Effects, and Outlines
Got an essay assignment about the effects of social media we got you covered check out our examples and outlines below.
Social media has become one of our society's most prominent ways of communication and information sharing in a very short time. It has changed how we communicate and has given us a platform to express our views and opinions and connect with others. It keeps us informed about the world around us. Social media platforms such as Facebook, Twitter, Instagram, and LinkedIn have brought individuals from all over the world together, breaking down geographical borders and fostering a genuinely global community.
However, social media comes with its difficulties. With the rise of misinformation, cyberbullying, and privacy problems, it's critical to utilize these platforms properly and be aware of the risks. Students in the academic world are frequently assigned essays about the impact of social media on numerous elements of our lives, such as relationships, politics, and culture. These essays necessitate a thorough comprehension of the subject matter, critical thinking, and the ability to synthesize and convey information clearly and succinctly.
But where do you begin? It can be challenging to know where to start with so much information available. Jenni.ai comes in handy here. Jenni.ai is an AI application built exclusively for students to help them write essays more quickly and easily. Jenni.ai provides students with inspiration and assistance on how to approach their essays with its enormous database of sample essays on a variety of themes, including social media. Jenni.ai is the solution you've been looking for if you're experiencing writer's block or need assistance getting started.
So, whether you're a student looking to better your essay writing skills or want to remain up to date on the latest social media advancements, Jenni.ai is here to help. Jenni.ai is the ideal tool for helping you write your finest essay ever, thanks to its simple design, an extensive database of example essays, and cutting-edge AI technology. So, why delay? Sign up for a free trial of Jenni.ai today and begin exploring the worlds of social networking and essay writing!
Want to learn how to write an argumentative essay? Check out these inspiring examples!
We will provide various examples of social media essays so you may get a feel for the genre.
6 Examples of Social Media Essays
Here are 6 examples of Social Media Essays:
The Impact of Social Media on Relationships and Communication
Introduction:.
The way we share information and build relationships has evolved as a direct result of the prevalence of social media in our daily lives. The influence of social media on interpersonal connections and conversation is a hot topic. Although social media has many positive effects, such as bringing people together regardless of physical proximity and making communication quicker and more accessible, it also has a dark side that can affect interpersonal connections and dialogue.
Positive Effects:
Connecting People Across Distances
One of social media's most significant benefits is its ability to connect individuals across long distances. People can use social media platforms to interact and stay in touch with friends and family far away. People can now maintain intimate relationships with those they care about, even when physically separated.
Improved Communication Speed and Efficiency
Additionally, the proliferation of social media sites has accelerated and simplified communication. Thanks to instant messaging, users can have short, timely conversations rather than lengthy ones via email. Furthermore, social media facilitates group communication, such as with classmates or employees, by providing a unified forum for such activities.
Negative Effects:
Decreased Face-to-Face Communication
The decline in in-person interaction is one of social media's most pernicious consequences on interpersonal connections and dialogue. People's reliance on digital communication over in-person contact has increased along with the popularity of social media. Face-to-face interaction has suffered as a result, which has adverse effects on interpersonal relationships and the development of social skills.
Decreased Emotional Intimacy
Another adverse effect of social media on relationships and communication is decreased emotional intimacy. Digital communication lacks the nonverbal cues and facial expressions critical in building emotional connections with others. This can make it more difficult for people to develop close and meaningful relationships, leading to increased loneliness and isolation.
Increased Conflict and Miscommunication
Finally, social media can also lead to increased conflict and miscommunication. The anonymity and distance provided by digital communication can lead to misunderstandings and hurtful comments that might not have been made face-to-face. Additionally, social media can provide a platform for cyberbullying , which can have severe consequences for the victim's mental health and well-being.
Conclusion:
In conclusion, the impact of social media on relationships and communication is a complex issue with both positive and negative effects. While social media platforms offer many benefits, such as connecting people across distances and enabling faster and more accessible communication, they also have a dark side that can negatively affect relationships and communication. It is up to individuals to use social media responsibly and to prioritize in-person communication in their relationships and interactions with others.
The Role of Social Media in the Spread of Misinformation and Fake News
Social media has revolutionized the way information is shared and disseminated. However, the ease and speed at which data can be spread on social media also make it a powerful tool for spreading misinformation and fake news. Misinformation and fake news can seriously affect public opinion, influence political decisions, and even cause harm to individuals and communities.
The Pervasiveness of Misinformation and Fake News on Social Media
Misinformation and fake news are prevalent on social media platforms, where they can spread quickly and reach a large audience. This is partly due to the way social media algorithms work, which prioritizes content likely to generate engagement, such as sensational or controversial stories. As a result, false information can spread rapidly and be widely shared before it is fact-checked or debunked.
The Influence of Social Media on Public Opinion
Social media can significantly impact public opinion, as people are likelier to believe the information they see shared by their friends and followers. This can lead to a self-reinforcing cycle, where misinformation and fake news are spread and reinforced, even in the face of evidence to the contrary.
The Challenge of Correcting Misinformation and Fake News
Correcting misinformation and fake news on social media can be a challenging task. This is partly due to the speed at which false information can spread and the difficulty of reaching the same audience exposed to the wrong information in the first place. Additionally, some individuals may be resistant to accepting correction, primarily if the incorrect information supports their beliefs or biases.
In conclusion, the function of social media in disseminating misinformation and fake news is complex and urgent. While social media has revolutionized the sharing of information, it has also made it simpler for false information to propagate and be widely believed. Individuals must be accountable for the information they share and consume, and social media firms must take measures to prevent the spread of disinformation and fake news on their platforms.
The Effects of Social Media on Mental Health and Well-Being
Social media has become an integral part of modern life, with billions of people around the world using platforms like Facebook, Instagram, and Twitter to stay connected with others and access information. However, while social media has many benefits, it can also negatively affect mental health and well-being.
Comparison and Low Self-Esteem
One of the key ways that social media can affect mental health is by promoting feelings of comparison and low self-esteem. People often present a curated version of their lives on social media, highlighting their successes and hiding their struggles. This can lead others to compare themselves unfavorably, leading to feelings of inadequacy and low self-esteem.
Cyberbullying and Online Harassment
Another way that social media can negatively impact mental health is through cyberbullying and online harassment. Social media provides a platform for anonymous individuals to harass and abuse others, leading to feelings of anxiety, fear, and depression.
Social Isolation
Despite its name, social media can also contribute to feelings of isolation. At the same time, people may have many online friends but need more meaningful in-person connections and support. This can lead to feelings of loneliness and depression.
Addiction and Overuse
Finally, social media can be addictive, leading to overuse and negatively impacting mental health and well-being. People may spend hours each day scrolling through their feeds, neglecting other important areas of their lives, such as work, family, and self-care.
In sum, social media has positive and negative consequences on one's psychological and emotional well-being. Realizing this, and taking measures like reducing one's social media use, reaching out to loved ones for help, and prioritizing one's well-being, are crucial. In addition, it's vital that social media giants take ownership of their platforms and actively encourage excellent mental health and well-being.
The Use of Social Media in Political Activism and Social Movements
Social media has recently become increasingly crucial in political action and social movements. Platforms such as Twitter, Facebook, and Instagram have given people new ways to express themselves, organize protests, and raise awareness about social and political issues.
Raising Awareness and Mobilizing Action
One of the most important uses of social media in political activity and social movements has been to raise awareness about important issues and mobilize action. Hashtags such as #MeToo and #BlackLivesMatter, for example, have brought attention to sexual harassment and racial injustice, respectively. Similarly, social media has been used to organize protests and other political actions, allowing people to band together and express themselves on a bigger scale.
Connecting with like-minded individuals
A second method in that social media has been utilized in political activity and social movements is to unite like-minded individuals. Through social media, individuals can join online groups, share knowledge and resources, and work with others to accomplish shared objectives. This has been especially significant for geographically scattered individuals or those without access to traditional means of political organizing.
Challenges and Limitations
As a vehicle for political action and social movements, social media has faced many obstacles and restrictions despite its many advantages. For instance, the propagation of misinformation and fake news on social media can impede attempts to disseminate accurate and reliable information. In addition, social media corporations have been condemned for censorship and insufficient protection of user rights.
In conclusion, social media has emerged as a potent instrument for political activism and social movements, giving voice to previously unheard communities and galvanizing support for change. Social media presents many opportunities for communication and collaboration. Still, users and institutions must be conscious of the risks and limitations of these tools to promote their responsible and productive usage.
The Potential Privacy Concerns Raised by Social Media Use and Data Collection Practices
With billions of users each day on sites like Facebook, Twitter, and Instagram, social media has ingrained itself into every aspect of our lives. While these platforms offer a straightforward method to communicate with others and exchange information, they also raise significant concerns over data collecting and privacy. This article will examine the possible privacy issues posed by social media use and data-gathering techniques.
Data Collection and Sharing
The gathering and sharing of personal data are significant privacy issues brought up by social media use. Social networking sites gather user data, including details about their relationships, hobbies, and routines. This information is made available to third-party businesses for various uses, such as marketing and advertising. This can lead to serious concerns about who has access to and uses our personal information.
Lack of Control Over Personal Information
The absence of user control over personal information is a significant privacy issue brought up by social media usage. Social media makes it challenging to limit who has access to and how data is utilized once it has been posted. Sensitive information may end up being extensively disseminated and may be used maliciously as a result.
Personalized Marketing
Social media companies utilize the information they gather about users to target them with adverts relevant to their interests and usage patterns. Although this could be useful, it might also cause consumers to worry about their privacy since they might feel that their personal information is being used without their permission. Furthermore, there are issues with the integrity of the data being used to target users and the possibility of prejudice based on individual traits.
Government Surveillance
Using social media might spark worries about government surveillance. There are significant concerns regarding privacy and free expression when governments in some nations utilize social media platforms to follow and monitor residents.
In conclusion, social media use raises significant concerns regarding data collecting and privacy. While these platforms make it easy to interact with people and exchange information, they also gather a lot of personal information, which raises questions about who may access it and how it will be used. Users should be aware of these privacy issues and take precautions to safeguard their personal information, such as exercising caution when choosing what details to disclose on social media and keeping their information sharing with other firms to a minimum.
The Ethical and Privacy Concerns Surrounding Social Media Use And Data Collection
Our use of social media to communicate with loved ones, acquire information, and even conduct business has become a crucial part of our everyday lives. The extensive use of social media does, however, raise some ethical and privacy issues that must be resolved. The influence of social media use and data collecting on user rights, the accountability of social media businesses, and the need for improved regulation are all topics that will be covered in this article.
Effect on Individual Privacy:
Social networking sites gather tons of personal data from their users, including delicate information like search history, location data, and even health data. Each user's detailed profile may be created with this data and sold to advertising or used for other reasons. Concerns regarding the privacy of personal information might arise because social media businesses can use this data to target users with customized adverts.
Additionally, individuals might need to know how much their personal information is being gathered and exploited. Data breaches or the unauthorized sharing of personal information with other parties may result in instances where sensitive information is exposed. Users should be aware of the privacy rules of social media firms and take precautions to secure their data.
Responsibility of Social Media Companies:
Social media firms should ensure that they responsibly and ethically gather and use user information. This entails establishing strong security measures to safeguard sensitive information and ensuring users are informed of what information is being collected and how it is used.
Many social media businesses, nevertheless, have come under fire for not upholding these obligations. For instance, the Cambridge Analytica incident highlighted how Facebook users' personal information was exploited for political objectives without their knowledge. This demonstrates the necessity of social media corporations being held responsible for their deeds and ensuring that they are safeguarding the security and privacy of their users.
Better Regulation Is Needed
There is a need for tighter regulation in this field, given the effect, social media has on individual privacy as well as the obligations of social media firms. The creation of laws and regulations that ensure social media companies are gathering and using user information ethically and responsibly, as well as making sure users are aware of their rights and have the ability to control the information that is being collected about them, are all part of this.
Additionally, legislation should ensure that social media businesses are held responsible for their behavior, for example, by levying fines for data breaches or the unauthorized use of personal data. This will provide social media businesses with a significant incentive to prioritize their users' privacy and security and ensure they are upholding their obligations.
In conclusion, social media has fundamentally changed how we engage and communicate with one another, but this increased convenience also raises several ethical and privacy issues. Essential concerns that need to be addressed include the effect of social media on individual privacy, the accountability of social media businesses, and the requirement for greater regulation to safeguard user rights. We can make everyone's online experience safer and more secure by looking more closely at these issues.
In conclusion, social media is a complex and multifaceted topic that has recently captured the world's attention. With its ever-growing influence on our lives, it's no surprise that it has become a popular subject for students to explore in their writing. Whether you are writing an argumentative essay on the impact of social media on privacy, a persuasive essay on the role of social media in politics, or a descriptive essay on the changes social media has brought to the way we communicate, there are countless angles to approach this subject.
However, writing a comprehensive and well-researched essay on social media can be daunting. It requires a thorough understanding of the topic and the ability to articulate your ideas clearly and concisely. This is where Jenni.ai comes in. Our AI-powered tool is designed to help students like you save time and energy and focus on what truly matters - your education. With Jenni.ai , you'll have access to a wealth of examples and receive personalized writing suggestions and feedback.
Whether you're a student who's just starting your writing journey or looking to perfect your craft, Jenni.ai has everything you need to succeed. Our tool provides you with the necessary resources to write with confidence and clarity, no matter your experience level. You'll be able to experiment with different styles, explore new ideas , and refine your writing skills.
So why waste your time and energy struggling to write an essay on your own when you can have Jenni.ai by your side? Sign up for our free trial today and experience the difference for yourself! With Jenni.ai, you'll have the resources you need to write confidently, clearly, and creatively. Get started today and see just how easy and efficient writing can be!
Try Jenni for free today
Create your first piece of content with Jenni today and never look back
- Undergraduate
- High School
- Architecture
- American History
- Asian History
- Antique Literature
- American Literature
- Asian Literature
- Classic English Literature
- World Literature
- Creative Writing
- Linguistics
- Criminal Justice
- Legal Issues
- Anthropology
- Archaeology
- Political Science
- World Affairs
- African-American Studies
- East European Studies
- Latin-American Studies
- Native-American Studies
- West European Studies
- Family and Consumer Science
- Social Issues
- Women and Gender Studies
- Social Work
- Natural Sciences
- Pharmacology
- Earth science
- Agriculture
- Agricultural Studies
- Computer Science
- IT Management
- Mathematics
- Investments
- Engineering and Technology
- Engineering
- Aeronautics
- Medicine and Health
- Alternative Medicine
- Communications and Media
- Advertising
- Communication Strategies
- Public Relations
- Educational Theories
- Teacher's Career
- Chicago/Turabian
- Company Analysis
- Education Theories
- Shakespeare
- Canadian Studies
- Food Safety
- Relation of Global Warming and Extreme Weather Condition
- Movie Review
- Admission Essay
- Annotated Bibliography
- Application Essay
- Article Critique
- Article Review
- Article Writing
- Book Review
- Business Plan
- Business Proposal
- Capstone Project
- Cover Letter
- Creative Essay
- Dissertation
- Dissertation - Abstract
- Dissertation - Conclusion
- Dissertation - Discussion
- Dissertation - Hypothesis
- Dissertation - Introduction
- Dissertation - Literature
- Dissertation - Methodology
- Dissertation - Results
- GCSE Coursework
- Grant Proposal
- Marketing Plan
- Multiple Choice Quiz
- Personal Statement
- Power Point Presentation
- Power Point Presentation With Speaker Notes
- Questionnaire
- Reaction Paper
- Research Paper
- Research Proposal
- SWOT analysis
- Thesis Paper
- Online Quiz
- Literature Review
- Movie Analysis
- Statistics problem
- Math Problem
- All papers examples
- How It Works
- Money Back Policy
- Terms of Use
- Privacy Policy
- We Are Hiring
Social Media Is a Threat to Privacy, Essay Example
Pages: 3
Words: 860
Hire a Writer for Custom Essay
Use 10% Off Discount: "custom10" in 1 Click 👇
You are free to use it as an inspiration or a source for your own work.
Introduction
Social networking has been a global phenomenon with the proliferation of various social networking platforms such as Facebook, Twitter, and Instagram. In many ways, social media has replaced conventional modes of communication such as the telephone and email. People can keep in touch with others by sharing experiences and photographs, and most cases exchange personal information. Social media users usually post private information as part of the process of knowing one another. Since social media is associated with having a large number of users unknown to the client, there is an increased risk of exposing personal details to cybercriminals.
Social media is a threat to privacy
Social media has increased privacy concerns with online platforms. Although they are effective in connecting with family and friend, social media can also endanger private information. Individuals create social media profiles that may expose their private information. According to research conducted by Carnegie Mellon University, information found in social media is sufficient to guess one’s social security number, which can lead to identity theft. With the advent of mobile banking applications, more people are login their sensitive data to smartphones, which can endanger their privacy.
Another group whose privacy is in danger is teenagers. Teenagers post a significant amount of information online, which makes it vitally for them to understand the people they share information with or use privacy settings. However, most teenagers are interested with capturing the attention of their peers and in the process posting information that may enhance their status. This information may not seem harmful, but it can be exploited by cyber criminals to get access to the parents.
Several articles have argued about the threat of privacy in online platforms such as social media. In “online privacy: current health 2 by given (2009),” the author argues that online predators can figure out information posted in online platforms, which can be used against the user. Additionally, employers can use the online platform to check out their employees. With the proliferation of electronic health registers, cyber criminals can access an individual’s health information. It presents a significant danger to the individuals concerned because such registers contain vital information such as social security number and insurance details.
In her article titled” should you panic about online privacy?” Palmer (2010) notes that online platforms are a threat to privacy and individual must take measures to protect their personal data. Due to the threat posed by online environments to privacy, Palmer suggests various strategies that user can use to safeguard their privacy. One way of doing this is by removing the birth year from a personal profile in social media networks because the full birth year is often used by banks to categorize their clients. Cyber criminals can use such information to access online banking systems that can compromise user’s safety. Another suggestion given by Palmer is to use antivirus and anti-spyware. These techniques will prevent criminals from exploiting them to access confidential information.
In the piece carried by the New Yorker tiled “the face of Facebook” by José Vargas may present information about Mark Zuckerberg that is public domain, it illustrates how Facebook profiles reveal private and confidential information to virtually anyone on the site. FACEBOOK is a directory of global citizens that affords people the chance to create public identities. Friends can access this information; friends of friends can also access some while some information is also available to anyone interested in them. Although the company has changed it privacy policies severally, it still exposes private information in several ways. From Zuckerberg’s profile, it is possible to know that he has three sisters, where he schooled in, he favorite comedian and musicians, and his interests. His friends can also access his cell-phone number and email address. Additionally, the addition of a feature known as Places, which allows users to mark their location means that someone interested in Zuckerberg’s location can know it anytime. The article by Vargas reveals how easy it is to access one’s private information in Facebook.
Plagiarism, which is using another person’s ideas or creations without giving credit to that person, is another concern in social media. Individuals take information from other sources or individuals and use them as their own, which a common practice in social media. The lack of attribution and fabrication of content are the real issues because users seldom give credit to the source of the content. Despite the fact that social media is for connecting with friends and family, it has been used as social aggregators, which makes it important to give links to the sources of the content.
Social media platforms raise concerns over privacy issues because others can exploit information that is innocently posted on these sites. Cyber criminals can exploit the information to harm the user. It is important to note that different people can access information posted online. Users must take significant steps to protect their information by using anti-spyware software and emitting sensitive information in their profiles.
Given M. (2008). online privacy. Current health 2 . Retrieved from academic search complete.
Palmer L. (2010, 08) should you panic about online privacy? Redbook , Vol. 215 Issue 2, p130
Vargas,J.A. ( 2010, sep20). The face of Facebook. The New Yorker. Retrieved from http://www.newyorker.com/magazine/2010/09/20/the-face-of-facebook
Stuck with your Essay?
Get in touch with one of our experts for instant help!
Vitamin C Experiment, Essay Example
The Professionalization of Ujwai Bharati, Essay Example
Time is precious
don’t waste it!
Plagiarism-free guarantee
Privacy guarantee
Secure checkout
Money back guarantee

Related Essay Samples & Examples
Voting as a civic responsibility, essay example.
Pages: 1
Words: 287
Utilitarianism and Its Applications, Essay Example
Words: 356
The Age-Related Changes of the Older Person, Essay Example
Pages: 2
Words: 448
The Problems ESOL Teachers Face, Essay Example
Pages: 8
Words: 2293
Should English Be the Primary Language? Essay Example
Pages: 4
Words: 999
The Term “Social Construction of Reality”, Essay Example
Words: 371
- Search Menu
- Advance Articles
- Author Guidelines
- Submission Site
- Open Access
- Self-Archiving Policy
- Why Submit?
- About Communication Theory
- About International Communication Association
- Editorial Board
- Advertising & Corporate Services
- Journals Career Network
- Journals on Oxford Academic
- Books on Oxford Academic

The Social Media Privacy Model: Privacy and Communication in the Light of Social Media Affordances
- Article contents
- Figures & tables
- Supplementary Data
Sabine Trepte, The Social Media Privacy Model: Privacy and Communication in the Light of Social Media Affordances, Communication Theory , Volume 31, Issue 4, November 2021, Pages 549–570, https://doi.org/10.1093/ct/qtz035
- Permissions Icon Permissions
Privacy has been defined as the selective control of information sharing, where control is key. For social media, however, an individual user’s informational control has become more difficult. In this theoretical article, I review how the term control is part of theorizing on privacy, and I develop an understanding of online privacy with communication as the core mechanism by which privacy is regulated. The results of this article’s theoretical development are molded into a definition of privacy and the social media privacy model. The model is based on four propositions: Privacy in social media is interdependently perceived and valued. Thus, it cannot always be achieved through control. As an alternative, interpersonal communication is the primary mechanism by which to ensure social media privacy. Finally, trust and norms function as mechanisms that represent crystallized privacy communication. Further materials are available at https://osf.io/xhqjy/
Email alerts
Citing articles via.
- Recommend to Your Librarian
- Advertising and Corporate Services
Affiliations
- Online ISSN 1468-2885
- Copyright © 2024 International Communication Association
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.
Social Media and Privacy
- Open Access
- First Online: 09 February 2022
Cite this chapter
You have full access to this open access chapter

- Xinru Page 7 ,
- Sara Berrios 7 ,
- Daricia Wilkinson 8 &
- Pamela J. Wisniewski 9
17k Accesses
4 Citations
4 Altmetric
With the popularity of social media, researchers and designers must consider a wide variety of privacy concerns while optimizing for meaningful social interactions and connection. While much of the privacy literature has focused on information disclosures, the interpersonal dynamics associated with being on social media make it important for us to look beyond informational privacy concerns to view privacy as a form of interpersonal boundary regulation. In other words, attaining the right level of privacy on social media is a process of negotiating how much, how little, or when we desire to interact with others, as well as the types of information we choose to share with them or allow them to share about us. We propose a framework for how researchers and practitioners can think about privacy as a form of interpersonal boundary regulation on social media by introducing five boundary types (i.e., relational, network, territorial, disclosure, and interactional) social media users manage. We conclude by providing tools for assessing privacy concerns in social media, as well as noting several challenges that must be overcome to help people to engage more fully and stay on social media.
You have full access to this open access chapter, Download chapter PDF
Similar content being viewed by others

Privacy and Empowerment in Connective Media

Privacy in Social Information Access

The Socio-economic Impacts of Social Media Privacy and Security Challenges
1 introduction.
The way people communicate with one another in the twenty-first century has evolved rapidly. In the 1990s, if someone wanted to share a “how-to” video tutorial within their social networks, the dissemination options would be limited (e.g., email, floppy disk, or possibly a writeable compact disc). Now, social media platforms, such as TikTok, provide professional grade video editing and sharing capabilities that give users the potential to both create and disseminate such content to thousands of viewers within a matter of minutes. As such, social media has steadily become an integral component for how people capture aspects of their physical lives and share them with others. Social media platforms have gradually altered the way many people live [ 1 ], learn [ 2 , 3 ], and maintain relationships with others [ 4 ].
Carr and Hayes define social media as “Internet-based channels that allow users to opportunistically interact and selectively self-present, either in real time or asynchronously, with both broad and narrow audiences who derive value from user-generated content and the perception of interaction with others” [ 5 ]. Social media platforms offer new avenues for expressing oneself, experiences, and emotions with broader online communities via posts, tweets, shares, likes, and reviews. People use these platforms to talk about major milestones that bring happiness (e.g., graduation, marriage, pregnancy announcements), but they also use social media as an outlet to express grief and challenges, and to cope with crises [ 6 , 7 , 8 ]. Many scholars have highlighted the host of positive outcomes from interpersonal interactions on social media including social capital, self-esteem, and personal well-being [ 9 , 10 , 11 , 12 ]. Likewise, researchers have also shed light on the increased concerns over unethical data collection and privacy abuses [ 13 , 14 ].
This chapter highlights the privacy issues that must be addressed in the context of social media and provides guidance on how to study and design for social media privacy. We first provide an overview of the history of social media and its usage. Next, we highlight common social media privacy concerns that have arisen over the years. We also point out how scholars have identified and sought to predict privacy behavior, but many efforts have failed to adequately account for individual differences. By reconceptualizing privacy in social media as a boundary regulation, we can explain these gaps from previous one-size-fits-all approaches and provide tools for measuring and studying privacy violations. Finally, we conclude with a word of caution about the consequences of ignoring privacy concerns on social media.
2 A Brief History of Social Media
Section highlights.
Social media use has quickly increased over the past decade and plays a key role in social, professional, and even civic realms. The rise of social media has led to “networked individualism.”
This enables people to access a wider variety of specialized relationships , making it more likely they can meet a variety of needs. It also allows people to project their voice to a wider audience.
However, people have more frequent turnover in their social networks , and it takes much more effort to maintain social relations and discern (mis)information and intention behind communication.
The initial popularity of social media harkened back to the historical rise of social network sites (SNSs). The canonical definition of SNSs is attributed to Boyd and Ellison [ 15 ] who differentiate SNSs from other forms of computer-mediated communication. According to Boyd and Ellison, SNS consists of (1) profiles representing users and (2) explicit connections between these profiles that can be traversed and interacted with. A social networking profile is a self-constructed digital representation of oneself and one’s social relationships. The content of these profiles varies by platform from profile pictures to personal information such as interests, demographics, and contact information. Visibility also varies by platform and often users have some control over who can see their profile (e.g., everyone or “friends”). Most SNSs also provide a way to leave messages on another’s profile, such as posting to someone’s timeline on Facebook or sending a mention or direct message to someone on Twitter.
Public interest and research initially focused on a small subset of SNSs (e.g., Friendster [ 16 ] and MySpace [ 17 , 18 , 19 ]), but the past decade has seen the proliferation of a much broader range of social networking technologies, as well as an evolution of SNSs into what Kane et al. term social media networks [ 20 ]. This extended definition emphasizes the reach of social media content beyond a single platform. It acknowledges how the boundedness of SNSs has become blurred as platform functionality that was once contained in a single platform, such as “likes,” are now integrated across other websites, third parties, and mobile apps.
Over the past decade, SNSs and social media networks have quickly become embedded in many facets of personal, professional, and social life. In that time, these platforms became more commonly known as “social media.” In the USA, only 5% of adults used social media in 2005. By 2011, half of the US adult population was using social media, and 72% were social users by 2019 [ 21 ]. MySpace and Facebook dominated SNS research about a decade ago, but now other social media platforms, such as YouTube, Instagram, Snapchat, Twitter, Kik, TikTok, and others, are popular choices among social media users. The intensity of use also has drastically increased. For example, half of Facebook users log on several times a day, and three-quarters of Facebook users are active on the platform at least daily [ 21 ]. Worldwide, Facebook alone has 1.59 billion users who use it on a daily basis and 2.41 billion using it at least monthly [ 22 ]. About half of the users of other popular platforms such as Snapchat, Instagram, Twitter, and YouTube also report visiting those sites daily. Around the world, there are 4.2 billion users who spend a cumulative 10 billion hours a day on social networking sites [ 23 ]. However, different social networking sites are dominant in different cultures. For example, the most popular social media in China, WeChat (inc. Wēixìn 微信), has 1.213 billion monthly users [ 23 ].
While SNS profiles started as a user-crafted representation of an individual user, these profiles now also often consist of information that is passively collected, aggregated, and filtered in ways that are ambiguous to the user. This passively collected information can include data accessed through other avenues (e.g., search engines, third-party apps) beyond the platform itself [ 24 ]. Many people fail to realize that their information is being stored and used elsewhere. Compared to tracking on the web, social media platforms have access to a plethora of rich data and fine-grained personally identifiable information (PII) which could be used to make inferences about users’ behavior, socioeconomic status, and even their political leanings [ 25 ]. While online tracking might be valuable for social media companies to better understand how to target their consumers and personalize social media features to users’ preferences, the lack of transparency regarding what and how data is collected has in more recent years led to heightened privacy concerns and skepticism around how social media platforms are using personal data [ 26 , 27 , 28 ]. This has, in turn, contributed to a loss of trust and changes in how people interact (or not) on social media, leading some users to abandon certain platforms altogether [ 26 , 29 ] or to seek alternative social media platforms that are more privacy focused.
For example, WhatsApp, a popular messaging app, updated its privacy policy to allow its parent company, Facebook, and its subsidiaries to collect WhatsApp data [ 30 ]. Users were given the option to accept the terms or lose access to the app. Shortly after, WhatsApp rival Signal reported 7.5 million installs globally over 4 days. Recent and multiple social media data breaches have heightened people’s awareness around potential inferences that could be made about them and the danger in sensitive privacy breaches. Considering the invasive nature of such practices, both consumers and companies are increasingly acknowledging the importance of privacy, control, and transparency in social media [ 31 ]. Similarly, as researchers and practitioners, we must acknowledge the importance of privacy on social media and design for the complex challenges associated with networked privacy. These types of intrusions and data privacy issues are akin to the informational privacy issues that have been investigated in the context of e-commerce, websites, and online tracking (see Chap. 9 ).
While early research into social media and privacy largely focused on these types of concerns, researchers have uncovered how the social dynamics surrounding social media have led to a broader array of social privacy issues that shape people’s adoption of platforms and their usage behaviors. Rainie and Wellman explain how the rise of social technologies, combined with ubiquitous Internet and mobile access, has led to the rise of “networked individualism” [ 32 ]. People have access to a wider variety of relationships than they previously did offline in a geographically and time-bound world. These new opportunities make it more likely that people can foster relationships that meet their individual needs for havens (support and belonging), bandages (coping), safety nets (protect from crisis), and social capital (ability to survive and thrive through situation changes). Additionally, social media users can project their voice to an extended audience, including many weak ties (e.g., acquaintances and strangers). This enables individuals to meet their social, emotional, and economic needs by drawing on a myriad of specialized relationships (different individuals each particularly knowledgeable in a specific domain such as economics, politics, sports, caretaking). In this way, individuals are increasingly networked or embedded within multiple communities that serve their interests and needs.
Inversely, networked individualism has also made people less likely to have a single “home” community, dealing with more frequent turnover and change in their social networks. Rainie and Wellman describe how people’s social routines are different from previous generations that were more geographically bound – today, only 10% of people’s significant ties are their neighbors [ 32 ]. As such, researchers have questioned and studied the extent to which people can meaningfully maintain interpersonal relationships on social media. The upper limit for doing so has been estimated at 150 connections or “friends” [ 33 ], but social media connections often well exceed this number. With such large networks, it also takes users much more effort to distinguish (mis)information, when communication is intended for the user, and the intent behind that communication. The technical affordances of social media can also help or hinder their (in)ability to capture the nuances of the various relationships in their social network. On many social media platforms, relationships are flattened into friends and followers, making them homogenous and lacking differentiation between, for instance, casual acquaintance and trusted confidant [ 16 , 34 ]. These characteristics of social media lead to a host of social privacy issues which are crucial to address. In the next section, we summarize some of the key privacy challenges that arise due to the unique characteristics of social media.
3 Privacy Challenges in Social Media
Information disclosure privacy issues have been a dominant focus in online technologies and the primary focus for social media. It focuses on access to data and defining public vs. private disclosures . It emphasizes user control over who sees what.
With so many people from different social circles able to access a user’s social media content, the issues of context collapse occur. Users may post to an imagined audience rather than realizing that people from multiple social contexts are privy to the same information.
The issues of self-presentation jump to the foreground in social media. Being able to manage impressions is a part of privacy management.
The social nature of social media also introduces the issues of controlling access to oneself , both in terms of availability and physical access.
Despite all of these privacy concerns, there is a noted privacy paradox between what people say they are concerned about and their resulting behaviors online.
Early focus of social media privacy research was focused on helping individuals meet their privacy needs in light of four key challenges: (1) information disclosure, (2) context collapse, (3) reputation management, and (4) access to oneself. This section gives an overview of these privacy challenges and how research sought to overcome them. The remainder of this chapter shows how the research has moved beyond focusing on the individual when it comes to social media and privacy; rather, social media privacy has been reconceptualized as a dynamic process of interpersonal boundary regulation between individuals and groups.
3.1 Information Disclosure/Control over Who Sees What
A commonality among early social media privacy research is that the focus has been on information privacy and self-disclosure [ 35 ]. Self-disclosure is the information a person chooses to share with other people or websites, such as posting a status update on social media. Information privacy breaches occur when a website and/or person leaks private information about a user, sometimes unintentionally. Many studies have focused on informational privacy and on sharing information with, or withholding it from, the appropriate people [ 36 , 37 , 38 ] on social media. Privacy settings related to self-disclosure have also been studied in detail [ 39 , 40 , 41 ]. Generally, social media platforms help users control self-disclosure in two ways. First is the level of granularity or type of information that one can share with others. Facebook is the most complex, allowing users to disclose and control more granular information for profile categories such as bio, website, email addresses, and at least eight other categories at the time of writing this chapter. Others have fewer information groupings, which make user profiles chunkier, and thus self-disclosure boundaries less granular. The second dimension is one’s access level permissions, or with whom one can share personal information. The most popular social media platforms err on the side of sharing more information to more people by allowing users to give access to categories such as “Everyone,” “All Users,” or “Public.” Similarly, many social media platforms give the option for access for “friends” or “followers” only.
Many researchers have highlighted how disclosures can be shared more widely than intended. Tufekci examined disclosure mechanisms used by college students on MySpace and Facebook to manage the boundary between private and public. Findings suggest that students are more likely to adjust profile visibility rather than limiting their disclosures [ 42 ]. Other research points out how users may not want their posts to remain online indefinitely, but most social media platforms default to keeping past posts visible unless the user specifies otherwise [ 43 ]. Even when the platform offers ways to limit post sharing, there are often intentional and unintentional ways this content is shared that negates the users’ wishes. For example, Twitter is a popular social media platform where users can choose to have their tweets available only to their followers. However, millions of private tweets have been retweeted, exposing private information to the public [ 44 ]. Even platforms like Snapchat, which make posts ephemeral by default, are susceptible to people taking screenshots of a snap and distributing through other channels. Thus, as social media companies continue to develop social media platforms, they should consider how to protect users from information disclosure and teach people to practice privacy protective habits.
Although some users adjust their privacy settings to limit information disclosures, they may be unaware of third-party sites that can still access their information. Scholars have emphasized the importance of educating users on the secondary use of their data, such as when third-party software takes information from their profiles [ 45 ]. Data surveillance continues to expand, and the business model of social media corporations tends to favor getting more information about users, which makes it difficult for users that want to control their disclosure [ 46 ]. Third-party apps can also access information about social media users’ connections without consent of the person whose information is being stored [ 47 ].
3.2 Unique Considerations for Managing Disclosures Within Social Media
As mentioned earlier, social media can expand a person’s network, but as that network expands and diversifies, users have less control over how their personal information is shared with others. Two unique privacy considerations for social media that arise from this tension are context collapse and imagined audiences, which we describe in more detail in the subsections below. For example, as Facebook has become a social gathering place for adults, one’s “friends” may include family members, coworkers, colleagues, and acquaintances all in one virtual social sphere. Social media users may want to share information with these groups but are concerned about which audiences are appropriate for sharing what types of information. This is because these various social spheres that intersect on Facebook may not intersect as readily in the physical world (e.g., college buddies versus coworkers) [ 48 ]. These distinct social circles are brought together into one space due to social media. This concept is referred to as “context collapse” since a user’s audience is no longer limited to one context (e.g., home, work, school) [ 15 , 49 , 50 ]. We highlight research on the phenomenon of the privacy paradox and explain how context collapse and imagined audiences may help explain the apparent disconnect between users’ stated privacy concerns and their actual privacy behavior.
Context Collapse
Nuanced differences between one’s relationships are not fully represented on social media. While real-life relationships are notorious for being complex, one of the biggest criticisms of social media platforms is that they often simplify relationships to a “binary” [ 51 ] or “monolithic” [ 52 ] dimension of either friend or not friend. Many platforms just have one type of relationship such as a “friend,” and all relationships are treated the same. Once a “friend” has been added to one’s network, maintaining appropriate levels of social interactions in light of one’s relationship context with this individual (and the many others within one’s network) becomes even more problematic [ 53 ]. Since each friend may have different and, at times, mutually exclusive expectations, acting accordingly within a single space has become a challenge. As Boyd points out, for instance, teenagers cannot be simultaneously cool to their friends and to their parents [ 53 ]. Due to this collapsed context of relationships within social media, acquaintances, family, friends, coworkers, and significant others all have the same level of access to a social media user once added to one’s network – unless appropriately managed.
Research reveals that the way people manage context collapses varies. Working professionals might deal with context collapse by limiting posts containing personal information, creating different accounts, and avoiding friending those they worked with [ 54 ]. As another example, many adolescents manage context collapse by keeping their family members separate from their personal accounts [ 55 ]. Other mechanisms for managing context collapse include access-level permission to request friendship, denying friend requests, and unfriending. While there is limited support for manually assigning different privileges to each friend, the default is to start out the same and many users never change those defaults.
Privacy incidents resulting from mixing work and social media show the importance of why context collapse must be addressed. Context collapse has been shown to negatively affect those seeking employment [ 56 ], as well as endangering those who are employed. For example, a teacher in Massachusetts lost her job because she did not realize her Facebook posts were public to those who were not her friends; her complaints about parents of students getting her sick led to her getting fired from her job [ 57 ]. Many others have shared anecdotes about being fired after controversial Facebook and Twitter posts [ 58 , 59 ]. Even celebrities who live in the public eye can suffer from context collapse [ 60 , 61 ]. Kim Kardashian, for example, received intense criticism from Internet fans when she posted a photo on social media of her daughter using a cellphone and wearing makeup while Kim was getting ready for hair and wardrobe [ 62 ]. Many online users criticized her parenting style for not limiting screen time and Kim subsequently shared a photo of a stack of books that the kids have access to while she works.
Nevertheless, context collapse can also increase bridging social capital, which is the potential social benefit that can come through having ties to a wider audience. Context collapse enables this to occur by allowing people to increase their connections to weak ties and creating serendipitous situations by sharing with people beyond whom one would normally share [ 60 ]. For example, job hunters may increase their chances of finding a job by using social media to network and connect with those they would not normally be associated with on a daily basis. Getting out a message or spreading the word can also be accomplished more easily. For instance, finding people to contribute to natural disaster funds can be effective on social media because multiple contexts can be easily reached from one account [ 63 ]. In addition to managing context collapse, social media users also have to anticipate whether they are sharing disclosures with their intended audiences.
Imagined Audiences
The disconnect between the real audience and the imagined audience on social media poses privacy risks. Understanding who can see what content, how, when, and where is key to deciding what content to share and under what circumstances. Yet, research has consistently demonstrated how users do not accurately anticipate who can potentially see their posts. This manifests as wrongly anticipating that a certain person can see content (when they cannot), as well as not realizing when another person can access posted content. Users have an “imagined audience” [ 64 , 65 ] to whom they are posting their content, but it often does not match the actual audience viewing the user’s content. Social media users typically imagine that the audience for their social media posts are like-minded people, such as family or close friends [ 65 ]. Sometimes, online users think of specific people or groups when creating content such as a daughter, coworkers, people who need cleaning tips, or even one’s deceased father [ 65 ]. Despite these imagined audiences, privacy settings may be set so that many more people can see these posts (acquaintances, strangers, etc.). While users do tend to limit who sees their profile to a defined audience [ 44 , 66 , 67 ], they still tend to believe their posts are more private than they actually are [ 49 , 68 ].
Some users adopt privacy management strategies to counter potential mismatch in audience. Vitak identified several privacy management tactics users employ to disclose information to a limited audience [ 69 ]:
Network-based . Social media users decide who to friend or follow, therefore filtering their network of people. Some Facebook users avoid friending people they do not know. Others set friends’ profiles to “hidden,” so that they do not have to see their posts, but avoid the negative connotations associated with “unfriending.”
Platform-based . Some users choose to use the social media sites’ privacy settings to control who sees their posts. A common approach on Facebook is to change the setting to be “friends only,” so that only a user’s friends may see their posts.
Content-based . These users control their privacy by being careful about the information they post. If they knew that an employer could see their posts, then they would avoid posting when they were at work.
Profile-based . A less commonly used approach is to create multiple accounts (on a single platform or across platforms). For example, a professional, personal, and fun account.
As another example, teenagers often navigate public platforms by posting messages that parents or others would not understand their true meaning. For instance, by posting a song lyric or quote that is only recognized by specific individuals as a reference to a specific movie scene or ironic message, they therefore creatively limit their audience [ 49 , 70 ]. Others manage their audience by using more self-limiting privacy tactics like self-censorship [ 70 ], choosing just to not post something they were considering in the first place. These various tactics allow users to control who can see what on social media in different ways.
3.3 Reputation Management Through Self-Presentation
Technology-mediated interactions have led to new ways of managing how we present ourselves to different groups of friends (e.g., using different profiles on the same platform based on the audience) [ 71 ]. Being able to control the way we come across to others can be a challenging privacy problem that social media users must learn to navigate. Features to limit audience can also help with managing self-presentation. Nonetheless, reputation or impression management is not just about avoiding posts or limiting access to content. Posting more content, such as selfies, is another approach used to control the way others perceive a user [ 72 ]. In this case, it is important to present the content that helps convey a certain image of oneself. Research has revealed that those who engage more in impression management tend to have more online friends and disclose more personal information [ 73 ]. Those who feel online disclosures could leave them vulnerable to negativity, such as individuals who identify as LGBTQ+, have also been found to put an emphasis on impression management in order to navigate their online presence [ 74 ]. However, studies still show that users have anxieties around not having control over how they are presented [ 75 ]. Social media users worry not only about what they post, but are concerned about how others’ postings will reflect on them [ 42 ].
Another dimension that affects impression management attitudes is how social media platforms vary in their policies on whether user profiles must be consistent with their offline identities. Facebook’s real name policy, for instance, requires that people use their real name and represent themselves as one person, corresponding to their offline identities. Research confirms that online profiles actually do reflect users’ authentic personalities [ 76 ]. However, some platforms more easily facilitate identity exploration and have evolved norms encouraging it. For example, Finsta accounts popped up on Instagram a few years after the company started. These accounts are “Fake Instagram” accounts often sharing content that the user does not want to associate with their more public identity, allowing for more identity exploration. This may have arisen from the social norm that has evolved where Instagram users often feel like they need to present an ideal self. Scholars have observed such pressure on Instagram more than on other platforms like Snapchat [ 77 ]. While the ability to craft an online image separate from one’s offline identity may be more prevalent on platforms like Instagram, certain types of social media such as location-sharing social networks are deeply tied to one’s offline self, sharing actual physical location of its users. Users of Foursquare, a popular location-sharing app, have leveraged this tight coupling for impression management. Scholars have observed that users try to impress their friends or family members about the places they spend their time while skipping “check-in” at places like McDonald’s or work for fear of appearing boring or unimpressive [ 78 ].
Regardless of how tightly one’s online presence corresponds with their offline identity, concerns about self-presentation can arise. For example, users may lie about their location on location-sharing platforms as an impression management tactic and have concerns about harming their relationships with others [ 79 ]. On the other hand, Finstas are meant to help with self-presentation by hiding one’s true identity. Ironically, the content posted may be even more representative of the user’s attitudes and activities than the idealized images on one’s public-facing account. These contrasting examples illustrate how self-presentation concerns are complicated.
What further complicates reputation management is that social media content is shared and consumed by a group of people and not just individuals or dyads. Thus, self-presentation is not only controlled by the individual, but by others who might post pictures and/or tag that individual. Even when friends/followers do not directly post about the user, their actions can reflect on the user just by virtue of being connected with them. The issues of co-owned data and how to negotiate disclosure rules are a key area of privacy research on the rise. We refer you to Chap. 6 , which goes in-depth on this topic.
3.4 Access to Oneself
A final privacy challenge many social media users encounter is controlling accessibility others have to them. Some social media platforms automatically display when someone is online, which may invite interaction whether users want to be accessible or not. Controlling access to oneself is not as straightforward as limiting or blocking certain people’s access. For instance, studies have also shown that social pressures influence individuals to accept friend requests from “weak ties” as well as true friends [ 53 , 80 ]. As a result, the social dynamics on social media are becoming more complex, creating social anxiety and drama for many social media users [ 52 , 53 , 80 ]. Although a user may want to control who can interact with him or her, they may be worried about how using privacy features such as “blocking” other accounts may send the wrong signal to others and hurt their relationships [ 81 ]. In fact, an online social norm called “hyperfriending” [ 82 ] has developed where only 25% of a user’s online connections represent true friendship [ 83 ]. This may undermine the privacy individuals wished they had over who interacts with them on their various accounts. Due to social norms or etiquette, users may feel compelled to interact with others online [ 84 ]. Even if users do not feel like they need to interact, they can sometimes get annoyed or overwhelmed by seeing too much information from others [ 85 ]. Their mental state is being bombarded by an overload of information, and they may feel their attention is being captured.
Many social media sites now include location-sharing features to be able to tell people where they are by checking in to various locations, tag photos or posts, or even share location in real time. Therefore, privacy issues may also arise when sharing one’s location on social media and receiving undesirable attention. Studies point out user concerns about how others may use knowledge of that location to reach out and ask to meet up, or even to physically go find the person [ 86 ]. In fact, research has found that people may not be as concerned about the private nature of disclosing location as they are concerned for disturbing others or being disturbed oneself as a result of location sharing [ 87 ]. This makes sense given that analysis of mobile phone conversations reveals that describing one’s location plays a big role in signaling availability and creating social awareness [ 87 , 88 ].
Some scholars focus on the potential harm that may come because of sharing their location. Tsai et al. surveyed people about perceived risks and found that fear of potential stalkers is one of the biggest barriers to adopting location-sharing services [ 89 ]. Nevertheless, studies have also found that many individuals believe that the benefits of using location sharing outweigh the hypothetical costs. Foursquare users have expressed fears that strangers could use the application to stalk them [ 78 ]. These concerns may explain why users share their location more often with close relationships [ 37 ].
Geotagging is another area of privacy concern for online users. Geotagging is when media (photo, website, QR codes) contain metadata with geographical information. More often the information is longitudinal and latitudinal coordinates, but sometimes even time stamps are attached to photos people post. This poses a threat to individuals that post online without realizing that their photos can reveal sensitive information. For example, one study assessed Craigslist postings and demonstrated how they could extract location and hours a person would likely be home based on a photo the individual listed [ 90 ]. The study even pinpointed the exact home address of a celebrity TV host based on their posted Twitter photos. Researchers point out how many users are unaware that their physical safety is at risk when they post photos of themselves or indicate they are on vacation [ 22 , 90 , 91 ]. Doing so may make them easy targets for robbers or stalkers to know when and where to find them.

3.5 Privacy Paradox
While researchers have investigated these various privacy attitudes, perceptions, and behaviors, the privacy paradox (where behavior does not match with stated privacy concerns) has been especially salient on social media [ 92 , 93 , 94 , 95 , 96 , 97 ]. As a result, much research focuses on understanding the decision-making process behind self-disclosure [ 98 ]. Scholars that view disclosure as a result of weighing the costs and the benefits of disclosing information use the term “privacy calculus” to characterize this process [ 99 ]. Other research draws on the theory of bounded rationality to explain how people’s actions are not fully rational [ 100 ]. They are often guided by heuristic cues which do not necessarily lead them to make the best privacy decisions [ 101 ]. Indeed, a large body of literature has tried to dispel or explain the privacy paradox [ 94 , 102 , 103 ].
4 Reconceptualizing Social Media Privacy as Boundary Regulation
By reconceptualizing privacy in social media as a boundary regulation , we can see that the seeming paradox in privacy is actually a balance between being too open or disclosing too much and being too inaccessible or disclosing too little. The latter can result in social isolation which is privacy regulation gone wrong.
In the context of social media, there are five different types of privacy boundaries that should be considered.
People use various methods of coping with privacy violations , many not tied to disclosing less information.
Drawing from Altman’s theories of privacy in the offline world (see Chap. 2 ), Palen and Dourish describe how, just like in the real world, social media privacy is a boundary regulation process along various dimensions besides just disclosure [ 104 ]. Privacy can also involve regulating interactional boundaries with friends or followers online and the level of accessibility one desires to those people. For example, if a Facebook user wants to limit the people that can post on their wall, they can exclude certain people. Research has identified other threats to interpersonal boundary regulation that arise out of the unique nature of social media [ 42 ]. First, as mentioned previously, the threat to spatial boundaries occurs because our audiences are obscured so that we no longer have a good sense of whom we may be interacting with. Second, temporal boundaries are blurred because any interaction may now occur asynchronously at some time in the future due to the virtual persistence of data. Third, multiple interpersonal spaces are merging and overlapping in a way that has caused a “steady erosion of clearly situated action” [ 5 ]. Since each space may have different and, at times, mutually exclusive behavioral requirements, acting accordingly within those spaces has become more of a challenge to manage context collapses [ 42 ]. Along with these problems, a major interpersonal boundary regulation challenge is that social media environments often take control of boundary regulation away from the end users. For instance, Facebook’s popular “Timeline” automatically (based on an obscure algorithm) broadcasts an individual’s content and interactions to all of his or her friends [ 41 ]. Thus, Facebook users struggle to keep up to date on how to manage interactions within these spaces as Facebook, not the end user, controls what is shared with whom.
4.1 Boundary Regulation on Social Media
One conceptualization of privacy that has become popular in the recent literature is viewing privacy on social media as a form of interpersonal boundary regulation. These scholars have characterized privacy as finding the optimal or appropriate level of privacy rather than the act of withholding self-disclosures. That is, it is just as important to avoid over disclosing as it is to avoid under disclosing. Therefore, disclosure is considered a boundary that must be regulated so that it is not too much or too little. Petronio’s communication privacy management (CPM) theory emphasizes how disclosing information (see Chap. 2 ) is vital for building relationships, creating closeness, and creating intimacy [ 105 ]. Thus, social isolation and loneliness resulting from under disclosure can be outcomes of privacy regulation gone wrong just as much as social crowding can be an issue. Similarly, the framework of contextual integrity explains that context-relative informational norms define privacy expectations and appropriate information flows and so a disclosure in one context (such as your doctor asking you for your personal medical details) may be perfectly appropriate in that context but not in another (such as your employer asking you for your personal medical details) [ 106 ]. Here it is not just about an information disclosure boundary but about a relationship boundary where the appropriate disclosure depends on the relationship between the discloser and the recipient.
Drawing on Altman’s theory of boundary regulation, Wisniewski et al. created a useful taxonomy detailing the various types of privacy boundaries that are relevant for managing one’s privacy on social media [ 107 ]. They identified five distinct privacy boundaries relevant to social media:
Relationship . This involves regulating who is in one’s social network as well as appropriate interactions for each relationship type.
Network . This consists of regulating access to one’s social connections as well as interactions between those connections.
Territorial . This has to do with regulating what content comes in for personal consumption and what is available in interactional spaces.
Disclosure . The literature commonly focuses on this aspect which consists of regulating what personal and co-owned information is disclosed to one’s social network.
Interactional . This applies to regulating potential interaction with those within and outside of one’s social network.
Of these boundary types, Wisniewski et al. emphasize the most important is maintaining relationship boundaries between people. Similarly, Child and Petronio note that “one of the most obvious issues emerging from the impact of social network site use is the challenge of drawing boundary lines that denote where relationships begin and end” [ 108 ]. Making sure that social media facilitates behavior appropriate to each of the user’s relationships is a major challenge.
Each of these interpersonal boundaries can be further classified into regulation of more fine-grained dimensions. In Table 7.1 , we summarize the different ways that each of these five interpersonal boundaries can be regulated on social media.
Next, we describe each of these interpersonal boundaries in more detail.
Self- and Confidant Disclosures
The information disclosure concerns described in the previous “Privacy Challenges” section are the focus of privacy around disclosure boundaries. Posting norms on social media platforms often encourage the disclosure of one’s personal information (e.g., age, sexual orientation, location, personal images) [ 109 , 110 ]. Disclosing such information can leave one open to financial, personal, and professional risks such as identity theft [ 46 , 111 ]. However, there are motivations for disclosing personal information. For example, research suggests that posting behaviors on social media platforms have a significant relationship with a desire for positive self-presentation [ 112 , 113 ]. Privacy management is necessary for balancing the benefits of disclosure and its associated risks. This involves regulating both self-disclosure for information about one’s self and confidant-disclosure boundaries for information that is “co-owned” with others [ 105 ] (e.g., a photograph that includes other people, or information about oneself that is shared with another in confidence).
There are a variety of disclosure boundary regulation mechanisms on social media interfaces. Many platforms offer users the freedom to selectively share various types of information, create personal biographies, share links to their websites, or post their birthday. Self-disclosure can also be maintained through privacy settings such as granular control over who has access to specific posts. The level of information one wishes to disclose could be managed by various privacy settings. Many social media platforms encourage multiparty participation with features such as tagging, subtweeting, or replying to others’ posts. This level of engagement promotes the celebration of shared moments or co-owned information/content. At the same time, it increases possibilities for breaching confidentiality and can create unwanted situations such as posting congratulations to a pregnancy that has not yet been announced to most family members or friends. Some ways that people manage violations of disclosure boundaries are to reactively confront the violator in private or to stop using the platform after the unexpected disclosure [ 114 ].
Relationship Connection and Context
Relationship boundaries have to do with who the user accepts into his or her “friend group” and consequently shapes the nature of online interactions within a person’s social network. Social media platforms have embedded the idea of “friend-based privacy” where information and interactional access is primarily dependent on one’s connections. The structure of one’s network can affect the level of engagement and the types of disclosures made on a platform. Individuals with more open relationship boundaries may have higher instances of weak ties compared to others who may employ stricter rules for including people into their inner circles. For example, studies have found people who engage in “hyper-adding,” namely, adding a significant number of persons to their network which could result in a higher distribution of “weak ties” [ 53 , 82 ].
After users accept friends and make connections, they must manage overlapping contexts such as work, family, or acquaintances. This leads to the types of privacy issues discussed under “Context Collapse” in the previous “Privacy Challenges” section. Research shows that boundary violations are hardly remedied by blocking or unfriending unless in extreme cases [ 115 ]. Furthermore, users rarely organize their friends into groups (and some social media platforms do not offer that functionality) [ 114 ]. People are either unaware of the feature, think it takes too much time, or are concerned that the wrong person would still see their information. As a result, users often feel they have to sacrifice being authentic online to control their privacy.
Network Discovery and Interaction
An individual’s social media network is often public knowledge, and there are advantages and disadvantages of having friends being aware of one’s social connections (aka friends list or followers). Network boundary mechanisms enable people to identify groups of people and manage interactions between the various groups. We highlight two types of network boundaries, namely, network discovery and network intersection boundaries. First, network discovery boundaries are primarily centered around the act of regulating the type of access others have to one’s network connections. Implementing an open approach to network discovery boundaries may create problems that may arise including competition as competitors within the same industry could steal clients by carefully selecting from a publicly facing friend list. Another issue arises when a person’s friend does not have a good reputation and that connection is negatively received by others within that social group. Sometimes the result is positive, for example, when friends or family find they have mutual connections, thus building social capital. Some social media platforms offer the ability to hide friend groups from everyone.
Network intersection boundaries involve the regulation of the interactions among different friend groups within one’s social network. Social media users have expressed the benefits of engaging in discourse online with people who they may not personally know offline [ 116 ]. In contrast, clashes within one’s friend list due to opposing political views or personal stances could create tensions that would make moderating a post difficult. These boundaries could be harder to control and sometimes lead to conflict if one is forced to choose which friends can participate in discussions.
Inward- and Outward-Facing Territories
Territorial boundaries include “places and objects in the environment” to indicate “ownership, possession, and occasional active defense” [ 117 ]. Within social media, there are features that are either inward-facing territories or outward-facing territories. Inward-facing territories are commonly characterized as spaces where users could find updates on their friends and see the content their connections were posting (such as the “news feed” on Facebook or “updates” on LinkedIn). To control their inward-facing territories, individuals could hide posts from specific people, adjust their privacy settings, and use filters to find specific information.
These territories are constantly being updated with photos, videos, and news articles that are personalized and not public facing which contributes to an overall low priority for territorial management [ 114 ]. Most choose to ignore content that is irrelevant to them rather than employing privacy features. In addition, once privacy features are used to hide content from particular friends, users rarely revisit that decision to reconsider including content within that territory from that person.
It is important to note that the key characteristic of outward-facing territory management is the regulation of potentially unsatisfactory interactions rather than a fear of information exposure. One example of an outward-facing territory is Facebook’s wall/timeline, where a person’s friend may contribute to your social media presence. Outward-facing territories fall between a public and private place, which creates more risk of unintended boundary violations. Altman argues that “because of their semipublic quality [outward-facing territories] often have unclear rules regarding their use and are susceptible to encroachment by a variety of users, sometimes inappropriately and sometimes predisposing to social conflict” [ 117 ]. Similar to confidant disclosure described above, connections may post (unwanted) content on a user’s wall that could lead to turbulence if that content is later deleted.
Interactional Disabling and Blocking
Interactional boundaries limit the need for other boundary regulations discussed because a person reduces access to oneself by disabling features [ 114 ]. For example, a user may deactivate Facebook Messenger to avoid receiving messages but reactivate the app when they deem that interaction to be welcomed. In a similar regard, disabling semipublic features of the interface (such as the wall on Facebook) could assist users in having a greater sense of control. This manifestation of interaction withdrawal is typically not directed at reducing interaction with a specific person; rather, it may be motivated by a high desire to control one’s online spaces. As such, disabling features are associated with perceptions of mistrust within one’s network and a desire to limit interruptions [ 115 ]. On the more extreme end, blocking could also be employed to regulate interactional boundaries. Unlike other withdrawal mechanisms such as disabling your wall, picture tagging, or chat, blocking is inherently targeted. The act represents the rejection and revocation of access to oneself from a particular party. Some social media platforms allow users to block other people or pages, meaning that the blocked person may not contact or interact with the user in any form. Generally, blocking a person results from a negative experience such as stalking or being bombarded with unwanted content [ 118 ].
4.2 Coping with Social Media Privacy Violations
Overtime, many social media platforms have implemented new privacy features that attempt to address evolving privacy risks and users’ need for more granular control online. While this effort is commendable, Ellison et al. argue that “privacy behaviors on social networking sites are not limited to privacy settings” [ 41 ]. Thus, social media users still venture outside the realm of privacy settings to achieve appropriate levels of social interactions. Coping mechanisms can be viewed as behaviors utilized to maintain or regain interpersonal boundaries [ 107 ]. Although these coping approaches may often be suboptimal, Wisniewski et al.’s framework of coping strategies for maintaining one’s privacy provides insight into the struggles many social media users face in maintaining these boundaries.
This approach is often defined as the “reduction of intensity of inputs” [ 117 ]. Filtering includes selecting whom one will accept into their online social circle and is often used in the management of relational boundaries. Filtering techniques may include relying on social cues (e.g., viewing the profile picture or examining mutual friends) before confirming the addition of a new connection. Other methods leverage non-privacy-related features that are repurposed to manage interactions based on relation context, for example, creating multiple accounts on the same platform to separate professional connections from personal friends.
The vast amount of information on social media could easily become overwhelming and difficult to consume. Therefore, social media users may opt to ignore posts or skim through information to decide which ones should receive priority for engagement. Ignoring is most common for inward-facing territories such as your “Feed” page. The overreliance on this approach might increase the chances of missing critical moments that connections shared.
Blocking is a more extreme approach to interactional boundary management compared to filtering and ignoring, which contributes to lower levels of reported usage [ 119 ]. As an alternative, users have developed other technology-supported mechanisms that would allow them to avoid unwanted interactions. As an example, Wisniewski et al. describe using pseudonyms on Facebook to make it more difficult to find a user on the platform [ 107 ]. Another method for blocking unwanted interactions is to use the account of a close friend or loved one to enjoy the benefits of the content on the platform without the hassle of expected interactions. Page et al. highlight this type of secondary use for those who avoid social media because of social anxieties, harassment, and other social barriers [ 120 ].
When some users feel they are losing control, they withdraw from social media by doing one of the following: deleting their account, censoring their posts, or avoiding confrontation. As a result, a common technique is limiting or adjusting the information shared (even avoiding posts that may be received negatively) [ 121 ]. Das and Kramer found that “people with more boundaries to regulate censor more; people who exercise more control over their audience censor more content; and, users with more politically and age diverse friends censor less, in general” [ 122 ]. Withdrawal suggests that some users think the risks outweigh the benefits of social media.
Unlike offensive coping mechanisms such as filtering, blocking, or withdrawal, social media users resort to more defensive mechanisms when the intention is to create interactions that may be confrontational. Aggressive behavior is displayed when the goal is to seek revenge or garner attention from specific people or groups. Some users may choose to exploit subliminal references in their posts to indirectly address or offend specific persons (e.g., an ex-partner, coworker, family member).
Compliance is giving in to pressures (external or internal) and adjusting one’s interpersonal boundary preferences for others. Altman describes this as “repeated failures to achieve a balance between achieved and desired levels of privacy” [ 117 ]. Relinquishing one’s interactional privacy needs to accommodate pressures of disclosure, nondisclosure, or friending preferences could result in a perceived loss of control over social interactions.
A healthy strategy for managing social media boundary violations is communicating with the other person involved and finding a resolution. Prior work indicates that most users that compromise do so offline [ 107 ]. These compromises are mostly with closer friends who the user can contact through email, phone call, or messaging. These more private scenarios avoid other people becoming involved online. Also, many compromises are about tagging someone in photos or sharing personal information about another user (i.e., confidant disclosure).
In addition to this coping framework for social media privacy, Stutzman examined the creation of multiple profiles on social media websites, primarily Facebook, as an information regulation mechanism. Through grounded theory, he identified three types of information boundary regulation within this context (pseudonymity, practical obscurity, and transparent separations) and four overarching motives for these mechanisms (privacy, identity, utility, and propriety) [ 71 ]. Lampinen et al. created a framework of strategies for managing private versus public disclosures. It defined three dimensions by which strategies differed: behavioral vs. mental, individual vs. collaborative, and preventative vs. corrective [ 71 , 123 ]. The various coping frameworks conceptualize privacy as a process of interpersonal boundary regulation. However, they do not solve the problem of managing privacy on these platforms. They do attempt to model the complexity of privacy management in a way that better reflects the complex nature of interpersonal relationships rather than as a matter of withholding versus disclosing private information.
5 Addressing Privacy Challenges
Rather than just measuring privacy concerns, researchers and designers should focus on understanding attitudes towards boundary regulation. Validated tools for measuring boundary preservation concern and boundary enhancement expectations are provided in this chapter.
Privacy features need to be designed to account for individual differences in how they are perceived and used. While some feel features like untag, unfriend, and delete are useful, others are worried about how using such features will impact their relationships.
Unaddressed privacy concerns can serve as a barrier to using social media. It is crucial to design for not only functional privacy concerns (e.g., being overloaded by information, guarding from inappropriate data access) but social privacy concerns as well (e.g., unwelcome interactions, pressures surrounding appropriate self-presentation).
This section describes how to better identify privacy concerns by measuring them from a boundary regulation perspective. We also emphasize the importance of individual differences when designing privacy features. Finally, we elaborate on a crucial set of social privacy issues that we feel are a priority to address. While many social media users may feel these types of social pressures to some degree, these problems have pushed some of society’s most vulnerable to complete abandonment of social media despite their desire for social connection. We call on social media designers and researchers to focus on these problems which are a side effect of the technologies we have created.
5.1 Understanding People and Their Privacy Concerns
Understanding social media privacy as a boundary regulation allows us to better conceptualize people’s attitudes and behaviors. It helps us anticipate their concerns and balance between too little or too much privacy. However, many existing tools for measuring privacy come from the information privacy perspective [ 124 , 125 , 126 ] and focus on data collection by organizations, errors, secondary use, or technical control of data. In detailing the various types of privacy boundaries that are relevant for managing one’s privacy on social media, Wisniewski et al. [ 114 ] emphasized that the most important is maintaining relationship boundaries between people.
Page et al. [ 86 , 127 ] similarly found that concerns about damaging relationship boundaries are actually at the root of low-level privacy concerns such as worrying about who sees what, being too accessible, or being bothered or bothering others by sharing too much information. For instance, a typically cited privacy concern such as being worried about a stranger knowing one’s current location turns out to be a privacy concern only if an individual expects that a stranger might violate typical relationship expectations. Their research revealed that many people were unconcerned about strangers knowing their location and explained that no one would care enough to use that information to come find them. They did not expect anyone to violate relationship boundaries and so were privacy unconcerned. On the other hand, those who felt there was a likelihood of someone using their location for nefarious purposes were privacy concerned. Social media enabling a negative change in relationship boundaries and the types of interactions that are now possible (such as strangers now being able to locate me) drives privacy concerns.
In fact, while scholars have used many lower-level privacy concerns such as being worried about sharing information to predict social media usage and adoption, they have met with mixed success leading to the commonly observed privacy paradox. However, research shows that preserving one’s relationship boundaries is at the root of these low-level online privacy concerns (e.g., informational, psychological, interactional, and physical privacy concerns) and is a significant predictor of social media usage [ 86 , 127 ]. In other words, concerns about social media damaging one’s relationships (aka relationship boundary regulation) are what drives privacy concerns.
5.2 Measuring Privacy Concerns
Boundary regulation plays a key role in maintaining the right level of privacy on social media, but how do we evaluate whether a platform is adequately supporting it? A popular scale for testing users’ awareness of secondary access is the Internet Users’ Information Privacy Concerns (IUIPC) scale, which measures their perceptions of collection, control, and awareness of user data [ 125 ]. An important finding is that users “want to know and have control over their information stored in marketers’ databases.” This indicates that social media should be designed such that people know where their data goes. However, throughout this chapter, it is evident that research on social media privacy has found concerns about social privacy more salient. In fact, the focus on relationship boundaries is a key privacy boundary to consider and measure in evaluating privacy concerns. Thus, having a scale to measure relationship boundary regulation would allow researchers and designers to better evaluate social media privacy.
Here we present validated relationship boundary regulation survey items developed by Page et al. which predict adoption and usage for various social media including Facebook, Twitter, LinkedIn, Instagram, and location-sharing social media [ 127 , 128 ]. These survey items can be used to evaluate privacy concerns for use of existing social media platforms, as well as capturing attitudes about new features or platforms. The survey items capture attitudes about one’s ability to regulate relationship boundaries when using a social media platform and are administered with a 7-point Likert scale (−3 = Disagree Completely, −2 = Disagree Mostly, −1 Disagree Slightly, 0 = Neither agree nor disagree, 1 = Agree Slightly, 2 = Agree Mostly, 3 = Agree Completely). These items measure both concerns and positive expectations.
When evaluating a new or existing social media platform, the relationship boundary preservation concern (BPC) items can be used to gauge user’s concerns about harming their relationships. A higher score would indicate that more support for privacy management is needed on a given platform. The relationship boundary enhancement expectation (BEE) items can also be used to evaluate whether users expect that using the platform will improve the user’s relationships. A high score is important to driving adoption and usage – having low concerns alone is not enough to drive usage. Along similar lines, even if users have high concerns, they may be counteracted by a perceived high level of benefits and so users remain frequent users of a platform. For instance, Facebook, one of the most widely used platforms, was shown to both invoke high levels of concern as well as high levels of enhancement expectation [ 127 ]. However, note that high frequency of use does not necessarily mean high levels of engagement (e.g., posting, commenting) or that users do not employ suboptimal workarounds (e.g., being vague in their posts) [ 81 ]. On the other hand, Twitter has a higher level of concerns compared to perceived enhancement and, accordingly, lower levels of usage [ 127 ].
In the validation studies, the set of survey items representing BPC were treated as a scale and factor analysis used to compute a single score. Similarly, the ones representing BEE were used to generate a single factor score to represent that construct. These could be used to evaluate new features or platforms in the lab or after deployment. For instance, after performing tasks on a new feature or platform, the user can answer these questions and the designer can compare the responses between different designs in A/B testing, or to predict usage frequency and adoption intentions (e.g., see [ 127 , 129 ] for detailed examples). Moreover, by correlating BPC or BEE with demographics or other customer segmentations (e.g., age, whether they are new customers, purpose for using the platform), product designers may be able to identify attitudes that are connected with certain segments of their customer base and address it directly.
5.3 Designing Privacy Features
When designing for privacy features, a crucial aspect to consider is individual differences. Privacy is not one-size-fits-all: there are many variations in how people feel, what they expect, and how they behave. Because social media connects individuals with diverse needs and expectations, and from a myriad of contexts, a necessity in addressing social media privacy is understanding individual differences in privacy attitudes and behaviors. Many individual differences have been identified that shape privacy needs and preferences [ 15 ] and behaviors [ 6 , 24 , 99 ].
Scholars have established that privacy as a construct is not limited to informational privacy (i.e., understanding the flow of data) but also includes social privacy concerns that may be more interactional (e.g., accessibility) or psychological in nature (e.g., self-presentation) [ 111 , 130 ]. Thus, a host of attitudes and experiences could shape an individual’s view on what it means to have privacy online. For example, people’s preferences for privacy tools could be heavily influenced by the type of data being shared or the recipient of that data [ 36 , 131 , 132 ]. Likewise, prior experiences (negative or positive) could shape how people interact online which could affect disclosure [ 133 ]. Context and relevance have also been found to significantly influence privacy behavior online. Drawing from the contextual integrity framework, many researchers argue that when people perceive data collection to be reasonable or appropriate, they are more likely to share information [ 134 ]. On the other hand, research has shown that when faced with uncomfortable scenarios, people employ privacy protective behaviors such as nondisclosure or falsifying information [ 135 ]. Research has also pointed to personal characteristics that could shape digital privacy behavior such as personality, culture, gender, age, and social norms [ 64 , 106 , 136 , 137 , 138 , 139 , 140 ].
While identifying concerns about damaging one’s relationships is important to measure, understanding the individual differences that can lead someone to be concerned can provide insight into addressing these concerns. For instance, through a series of investigations, Page et al. uncovered a communication style that predicts concerns about preserving relationship boundaries on many different social media platforms [ 127 , 128 , 129 ]. This communication style is characterized by wanting to put information out there so that the individual does not need to proactively inform others. Those who prefer an FYI (For Your Information) communication style are less concerned about relationship boundary preservation and, as a result, exhibit higher levels of engagement, interactions, and use of social media than low FYI communicators. For example, the survey items that capture an FYI communication style preference for location-sharing social media are: “I want the people I know to be aware of my location, without having to bother to tell them,” “I would prefer to make my location available to the people I know, so that they can see it whenever they need it,” and “The people I know should be able to get my location whenever they feel they need it.” Each item is administered with a 7-point Likert scale (Disagree strongly, Disagree moderately, Disagree slightly, Neutral, Agree slightly, Agree moderately, Agree strongly). For other social media platforms, the information type is adjusted (i.e., “what I’m up to” instead of “my location”).
Consequently, this raises concern over implications for non-FYI communicators since the design of major social media platforms is catered to FYI communicators [ 127 , 128 ]. Drawing on this insight, Page demonstrated how considering the user’s communication style when designing location-sharing social media interfaces can alleviate boundary preservation concerns [ 129 ]. Certain design choices such as choosing a request-based location-sharing interaction can lower concerns for non-FYI communicators, while continuous location-sharing and check-in type interactions that are typical in social media may be fine for FYI communicators.
This demonstrates that researchers should consider in the design of social media individual differences that affect privacy attitudes. Another individual difference in attitudes towards privacy features is a user’s apprehension that using common features such as untag, delete, or unfriend/unfollow can act as a hindrance in their relationships with others. Page et al. identified that while many use privacy features and perceive them as a tool useful for protecting their privacy, there are also many who are concerned about how using privacy features could hurt their relationships with others (e.g., being worried about offending others by untagging or unfriending) [ 81 ]. Instead, those individuals would use alternative privacy management tactics such as vaguebooking (not sharing specific details and using vague posts). Designers need to be aware that privacy features also need to be catered to individual variations in attitudes as well or else they may be ineffective and unused by certain segments of the user population.
5.4 Privacy Concerns and Social Disenfranchisement
A significant amount of research within the domain of social media nonuse has been focused on functional barriers that hinder adoption. In many cases, nonuse is traced to a lack of access (e.g., limited access to technology, financial resources, or the Internet). However, the push against adoption and subsequent usage can be voluntary [ 141 ] due to functional privacy concerns such as concerns about data breaches, information overload, or annoying posts [ 120 ]. Several social media companies have also implemented features such as time limits to help users counter overuse [ 142 ].
Likewise, it is equally important to consider social barriers that prevent social media engagement for people who really could use the social connection. Sharing about distressing experiences can be beneficial and reduce stigma, improve connection and interpersonal relationships with one’s network, and enhance well-being [ 6 , 7 , 143 , 144 ]. However, Page et al. identified a class of barriers that highlight social privacy concerns rooted in social anxiety or concerns about being overly influenced by others on social media. This is in contrast to the prior school of thought that focused primarily on functional motivations as barriers that influence nonuse (see Fig. 7.1 ) [ 120 ]. They point out that many who are already vulnerable avoid social media due to social barriers such as online harassment or paralysis over making decisions pertaining to online social interactions. Yet, they are also the ones who could benefit greatly from social connection and who end up losing touch with friends and social support by being off social media. They term this lose-lose situation of negative social consequences that arise when using social media as well as consequences from not using it, social disenfranchisement . They call on designers to address such social barriers and to realize that in designing the user experience to connect users so well, they are implicitly designing the nonuser experience of being left out. Given that social media usage may not always be a viable option, designers should design to alleviate the negative consequences of nonuse.
Extension of Wyatt’s frame that divided nonusers along the dimensions of whether someone has used the technology in the past and the motivation for adoption (extrinsic, e.g., organizationally imposed, versus intrinsic, e.g., desire to communicate through technology). Page et al. differentiate between functional motivations/barriers of use (which has been the focus of much research) versus social motivations/barriers to use. Other frameworks consider additional temporal states of adoption (whether they are currently using and whether they will in the future). See [ 120 ] for more detailed descriptions
5.5 Guidelines for Designing Privacy-Sensitive Social Media
Now that you have learned about various privacy problems related to social media use, how do you apply that to designing or studying social media? Here are some practical guidelines.
Identifying Privacy Attitudes
Measuring privacy attitudes is a tricky task. Using existing informational privacy scales, users often say they are concerned, but this does not end up matching their actual behavior. By approaching it from a boundary regulation perspective, it will be easier to identify the proper balance between sharing too much and sharing too little. The survey items described in this chapter offer a way to measure concerns about boundary regulation as well as positive expectations. Considering both are key to more accurately predicting user behaviors.
Understanding Your Target Population
Some key characteristics are described in this chapter. Identifying these in your target population can help you be aware of individual differences that might affect privacy preferences on social media. When you are measuring privacy concerns, matching the preferences of your audience makes it more likely that they will have a good user experience. Pay particular attention to traits that have been identified as being related to usage and adoption of social media platforms, such as the FYI communication style which can be measured using the survey items provided in this chapter.
Evaluating Privacy Features
Focus on understanding whether users perceive your privacy features as useful or perhaps as posing a relational hindrance. The survey items provided in this chapter can help you do so. When anticipating privacy needs of your social media users, make sure you identify features that may impact boundary regulation both positively and negatively. You can compare attitudes between the existing feature and the newer version of the feature that will/has been deployed. You can also correlate attitudes towards privacy features with individual characteristics – some subpopulation of users may see privacy features as useful, while others may consider them a relational hindrance.
6 Chapter Summary
Social media has been widely adopted and quickly become an integral part of social, personal, economic, political, professional, and instrumental welfare. Understanding how mediated social interactions change the assumptions around audience management, disclosure, and self-presentation is key to working towards reconciling offline privacy assumptions with new realities. Moreover, given the rapidly changing landscape of widely available social media platforms, researchers and designers need to continually re-evaluate the privacy implications of new services, features, and interaction modalities.
With the rise of networked individualism, an especially strong emphasis must be placed on understanding individual characteristics and traits that can shape a user’s privacy expectations and needs. Given the inherently social nature of social media, understanding social norms and the influence of larger cultural and structural factors is also important for interpreting expectations of privacy and the significance around various social media behaviors.
Privacy does not have a one-size-fits-all solution. It is a normative construct that is context dependent and can change over time, from culture to culture, and person to person. It needs to be weighed across different individuals and against other important goals and values of the larger group or society. Because people and their social interactions can be complex, designing for social media privacy is usually not a straightforward task. However, the consequences of not addressing privacy issues can range from irritating to devastating. Using this chapter as a guide and taking the steps to think through privacy needs and expectations of your social media users is an integral part of designing for social media.
Quan-Haase, Anabel, and Alyson L. Young. 2010. Uses and gratifications of social media: A comparison of Facebook and instant messaging. Bulletin of Science, Technology & Society 30 (5): 350–361.
Article Google Scholar
Gruzd, Anatoliy, Drew Paulin, and Caroline Haythornthwaite. 2016. Analyzing social media and learning through content and social network analysis: A faceted methodological approach. Journal of Learning Analytics 3 (3): 46–71.
Yang, Huining. 2020. Secondary-school Students’ Perspectives of Utilizing Tik Tok for English learning in and beyond the EFL classroom. In 2020 3rd International Conference on Education Technology and Social Science (ETSS 2020) , 163–183.
Google Scholar
Van Dijck, José. 2012. Facebook as a tool for producing sociality and connectivity. Television & New Media 13 (2): 160–176.
Grudin, Jonathan. 2001. Desituating action: Digital representation of context. Human–Computer Interaction 16 (2–4): 269–286.
Andalibi, Nazanin, Oliver L. Haimson, Munmun De Choudhury, and Andrea Forte. 2016. Understanding social media disclosures of sexual abuse through the lenses of support seeking and anonymity. In Proceedings of the 2016 CHI conference on human factors in computing systems , 3906–3918.
Andalibi, Nazanin, Pinar Ozturk, and Andrea Forte. 2017. Sensitive self-disclosures, responses, and social support on Instagram: The case of #depression. In Proceedings of the 2017 ACM Conference on Computer Supported Cooperative Work and Social Computing , 1485–1500.
Lin, Han, William Tov, and Qiu Lin. 2014. Emotional disclosure on social networking sites: The role of network structure and psychological needs. Computers in Human Behavior 41: 342–350.
Burke, Moira, Cameron Marlow, and Thomas Lento. 2010. Social network activity and social well-being. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems , ACM, 1909–1912.
Ellison, Nicole B., Charles Steinfield, and Cliff Lampe. 2007. The benefits of Facebook “Friends:” Social capital and college students’ use of online social network sites. Journal of Computer-Mediated Communication 12 (4): 1143–1168.
———. 2011. Connection strategies: social capital implications of Facebook-enabled communication practices. New Media & Society 13 (6): 873–892.
Koroleva, Ksenia, Hanna Krasnova, Natasha Veltri, and Oliver Günther. 2011. It’s all about networking! Empirical investigation of social capital formation on social network sites. In ICIS 2011 Proceedings .
Fischer-Hübner, Simone, Julio Angulo, Farzaneh Karegar, and Tobias Pulls. 2016. Transparency, privacy and trust–technology for tracking and controlling my data disclosures: Does this work? In IFIP International Conference on Trust Management , Springer, 3–14.
Xu, Heng, Hock-Hai Teo, Bernard C.Y. Tan, and Ritu Agarwal. 2012. Research note-effects of individual self-protection, industry self-regulation, and government regulation on privacy concerns: A study of location-based services. Information Systems Research 23 (4): 1342–1363.
Boyd, Danah. 2002. Faceted Id/Entity: Managing Representation in a Digital World . Retrieved August 14, 2020 from https://dspace.mit.edu/handle/1721.1/39401 .
Boyd, Danah M., and Nicole B. Ellison. 2007. Social network sites: Definition, history, and scholarship. Journal of Computer-Mediated Communication 13 (1): 210–230.
Dwyer, C., S.R. Hiltz, M.S. Poole, et al. 2010. Developing reliable measures of privacy management within social networking sites. In System Sciences (HICSS), 2010 43rd Hawaii International Conference on , 1–10.
Hargittai, E. 2007. Whose space? Differences among users and non-users of social network sites. Journal of Computer-Mediated Communication 13: 1.
Tufekci, Zeynep. 2008. Grooming, Gossip, Facebook and Myspace. Information, Communication & Society 11 (4): 544–564.
Kane, Gerald C., Maryam Alavi, Giuseppe Joe Labianca, and Stephen P. Borgatti. 2014. What’s different about social media networks? A framework and research agenda. MIS Quarterly 38 (1): 275–304.
Pew Research Center. 2019. Social Media Fact Sheet . Pew Research Center: Internet, Science & Technology. Retrieved November 27, 2020 from https://www.pewresearch.org/internet/fact-sheet/social-media/ .
Fire, M., R. Goldschmidt, and Y. Elovici. 2014. Online social networks: Threats and solutions. IEEE Communications Surveys Tutorials 16 (4): 2019–2036.
Social Media Users. DataReportal – Global Digital Insights . Retrieved March 16, 2021 from https://datareportal.com/social-media-users .
Alalwan, Ali Abdallah, Nripendra P. Rana, Yogesh K. Dwivedi, and Raed Algharabat. 2017. Social media in marketing: A review and analysis of the existing literature. Telematics and Informatics 34 (7): 1177–1190.
Binns, Reuben, Jun Zhao, Max Van Kleek, and Nigel Shadbolt. 2018. Measuring third-party tracker power across web and mobile. ACM Transactions on Internet Technology 18 (4): 52:1–52:22.
Barnard, Lisa. 2014. The cost of creepiness: How online behavioral advertising affects consumer purchase intention.
Dolin, Claire, Ben Weinshel, Shawn Shan, et al. 2018. Unpacking perceptions of data-driven inferences underlying online targeting and personalization. In Proceedings of the 2018 CHI Conference on Human Factors in Computing Systems , ACM, 493.
Ur, Blase, Pedro Giovanni Leon, Lorrie Faith Cranor, Richard Shay, and Yang Wang. 2012. Smart, useful, scary, creepy: Perceptions of online behavioral advertising. In Proceedings of the eighth symposium on usable privacy and security , ACM, 4.
Dogruel, Leyla. 2019. Too much information!? Examining the impact of different levels of transparency on consumers’ evaluations of targeted advertising. Communication Research Reports 36 (5): 383–392.
Hamilton, Isobel Asher, and Dean Grace. Signal downloads skyrocketed 4,200% after WhatsApp announced it would force users to share personal data with Facebook. It’s top of both Google and Apple’s app stores. Business Insider . Retrieved February 1, 2021 from https://www.businessinsider.com/whatsapp-facebook-data-signal-download-telegram-encrypted-messaging-2021-1 .
Wilkinson, Daricia, Moses Namara, Karishma Patil, Lijie Guo, Apoorva Manda, and Bart Knijnenburg. 2021. The Pursuit of Transparency and Control: A Classification of Ad Explanations in Social Media .
Lee, Rainie, and Barry Wellman. 2012. Networked . Cambridge, MA: MIT Press.
Dunbar, Robin. 2011. How many" friends" can you really have? IEEE Spectrum 48 (6): 81–83.
Carr, Caleb T., and Rebecca A. Hayes. 2015. Social media: Defining, developing, and divining. Atlantic Journal of Communication 23 (1): 46–65.
Xu, Heng, Tamara Dinev, H. Smith, and Paul Hart. 2008. Examining the Formation of Individual’s Privacy Concerns: Toward an Integrative View.
Consolvo, Sunny, Ian E Smith, Tara Matthews, Anthony LaMarca, Jason Tabert, and Pauline Powledge. 2005. Location disclosure to social relations: Why, when, & what people want to share. 10.
Wiese, Jason, Patrick Gage Kelley, Lorrie Faith Cranor, Laura Dabbish, Jason I. Hong, and John Zimmerman. 2011. Are you close with me? Are you nearby?: Investigating social groups, closeness, and willingness to share. UbiComp 10.
Xu, Heng, and Sumeet Gupta. 2009. The effects of privacy concerns and personal innovativeness on potential and experienced customers’ adoption of location-based services. Electronic Markets 19 (2–3): 137–149.
Acquisti, A., and R. Gross. 2006. Imagined communities: Awareness, information sharing, and privacy on the Facebook. Privacy Enhancing Technologies : 36–58.
Debatin, Bernhard, Jennette P. Lovejoy, Ann-Kathrin Horn, and Brittany N. Hughes. 2009. Facebook and online privacy: Attitudes, behaviors, and unintended consequences. Journal of Computer-Mediated Communication 15 (1): 83–108.
Ellison, Nicole B., Jessica Vitak, Charles Steinfield, Rebecca Gray, and Cliff Lampe. 2011. Negotiating privacy concerns and social capital needs in a social media environment. In Privacy Online: Perspectives on Privacy and Self-Disclosure in the Social Web , ed. S. Trepte and L. Reinecke, 19–32. Berlin: Springer.
Chapter Google Scholar
Tufekci, Z. 2008. Can You See Me Now? Audience and Disclosure Regulation in Online Social Network Sites . Retrieved January 29, 2021 from https://journals.sagepub.com/doi/abs/10.1177/0270467607311484 .
Ayalon, Oshrat and Eran Toch. 2013. Retrospective privacy: Managing longitudinal privacy in online social networks. In Proceedings of the Ninth Symposium on Usable Privacy and Security – SOUPS ’13 , ACM Press, 1.
Meeder, Brendan, Jennifer Tam, Patrick Gage Kelley, and Lorrie Faith Cranor. 2010. RT @IWantPrivacy: Widespread Violation of Privacy Settings in the Twitter Social Network . 12.
Padyab, Ali, and Tero Pã. Facebook Users Attitudes towards Secondary Use of Personal Information . 20.
van der Schyff, Karl, Stephen Flowerday, and Steven Furnell. 2020. Duplicitous social media and data surveillance: An evaluation of privacy risk. Computers & Security 94: 101822.
Symeonidis, Iraklis, Gergely Biczók, Fatemeh Shirazi, Cristina Pérez-Solà, Jessica Schroers, and Bart Preneel. 2018. Collateral damage of Facebook third-party applications: A comprehensive study. Computers & Security 77: 179–208.
Binder, Jens, Andrew Howes, and Alistair Sutcliffe. 2009. The problem of conflicting social spheres: Effects of network structure on experienced tension in social network sites. In Proceedings of the 27th international conference on Human factors in computing systems – CHI 09 , ACM Press, 965.
Marwick, Alice E., and Danah Boyd. 2011. I tweet honestly, I tweet passionately: Twitter users, context collapse, and the imagined audience. New Media & Society 13 (1): 114–133.
Sibona, Christopher. 2014. Unfriending on Facebook: Context collapse and unfriending behaviors. In 2014 47th Hawaii International Conference on System Sciences , 1676–1685.
Boyd, Danah Michele. 2004. Friendster and publicly articulated social networking. In Extended Abstracts of the 2004 Conference on Human Factors and Computing Systems – CHI ’04 , ACM Press, 1279.
Brzozowski, Michael J., Tad Hogg, and Gabor Szabo. 2008. Friends and foes: Ideological social networking. In Proceeding of the Twenty-Sixth Annual CHI Conference on Human Factors in Computing Systems – CHI ’08 , ACM Press, 817.
Boyd, Danah. 2006. Friends, Friendsters, and MySpace Top 8: Writing community into being on social network sites. First Monday .
Vitak, Jessica, Cliff Lampe, Rebecca Gray, and Nicole B Ellison. “Why won’t you be my Facebook friend?”: Strategies for Managing Context Collapse in the Workplace . 3.
Dennen, Vanessa P., Stacey A. Rutledge, Lauren M. Bagdy, Jerrica T. Rowlett, Shannon Burnick, and Sarah Joyce. 2017. Context collapse and student social media networks: Where life and high school collide. In Proceedings of the 8th International Conference on Social Media & Society - #SMSociety17 , ACM Press, 1–5.
Pike, Jacqueline C., Patrick J. Bateman, and Brian S. Butler. 2018. Information from social networking sites: Context collapse and ambiguity in the hiring process. Information Systems Journal 28 (4): 729–758.
Heussner, Ki Mae and Dalia Fahmy. Teacher loses job after commenting about students, parents on Facebook. ABC News . Retrieved November 19, 2020 from https://abcnews.go.com/Technology/facebook-firing-teacher-loses-job-commenting-students-parents/story?id=11437248 .
Torba, Andrew. 2019. High school teacher fired for tweets criticizing illegal immigration. Gab News . Retrieved November 19, 2020 from https://news.gab.com/2019/09/16/high-school-teacher-fired-for-tweets-criticizing-illegal-immigration/ .
Hall, Gaynor, and Courtney Gousman. 2020. Suburban teacher’s social media post sparks outrage, internal investigation | WGN-TV. WGNTV . Retrieved November 19, 2020 from https://wgntv.com/news/chicago-news/suburban-teachers-social-media-post-sparks-outrage-internal-investigation/ .
Davis, Jenny L., and Nathan Jurgenson. 2014. Context collapse: Theorizing context collusions and collisions. Information, Communication & Society 17 (4): 476–485.
Kaul, Asha, and Vidhi Chaudhri. 2018. Do celebrities have it all? Context collapse and the networked publics. Journal of Human Values 24 (1): 1–10.
Donnelly, Erin. 2019. Kim Kardashian mom-shamed over photo of North staring at a phone: “Give her a book.” Yahoo! Entertainment . Retrieved April 11, 2021 from https://www.yahoo.com/entertainment/kim-kardashian-mom-shamed-north-west-phone-book-151126429.html .
Sutton, Jeannette, Leysia Palen, and Irina Shklovski. 2008. Backchannels on the Front Lines: Emergent Uses of Social Media in the 2007 Southern California Wildfires . 9.
Litt, Eden. 2012. Knock, knock. Who’s there? The imagined audience. Journal of Broadcasting & Electronic Media 56 (3): 330–345.
Litt, Eden, and Eszter Hargittai. 2016. The imagined audience on social network sites. Social Media + Society 2 (1): 2056305116633482.
Li, N., and G. Chen. 2010. Sharing location in online social networks. IEEE Network 24 (5): 20–25.
Stutzman, Fred, and Jacob Kramer-Duffield. 2010. Friends only: Examining a privacy-enhancing behavior in Facebook. In Proceedings of the 28th international conference on Human factors in computing systems – CHI ’10 , ACM Press, 1553.
Jung, Yumi, and Emilee Rader. 2016. The imagined audience and privacy concern on Facebook: Differences between producers and consumers. Social Media + Society 2 (2): 2056305116644615.
Vitak, Jessica. 2015. Balancing Audience and Privacy Tensions on Social Network Sites . 20.
Oolo, Egle, and Andra Siibak. 2013. Performing for one’s imagined audience: Social steganography and other privacy strategies of Estonian teens on networked publics. Institute of Journalism and Communication, University of Tartu, Tartu, Estonia 7: 1.
Stutzman, Fred, and Woodrow Hartzog. 2012. Boundary Regulation in Social Media . 10.
Pounders, Kathrynn, Christine M. Kowalczyk, and Kirsten Stowers. 2016. Insight into the motivation of selfie postings: Impression management and self-esteem. European Journal of Marketing 50 (9/10): 1879–1892.
Krämer, Nicole C., and Stephan Winter. 2008. Impression Management 2.0: The relationship of self-esteem, extraversion, self-efficacy, and self-presentation within social networking sites. Journal of Media Psychology 20 (3): 106–116.
Duguay, Stefanie. 2016. “He has a way gayer Facebook than I do”: Investigating sexual identity disclosure and context collapse on a social networking site. New Media & Society 18 (6): 891–907.
Tang, Karen P., Jialiu Lin, Jason I. Hong, Daniel P. Siewiorek, and Norman Sadeh. 2010. Rethinking location sharing: Exploring the implications of social-driven vs. purpose-driven location sharing. In Proceedings of the 12th ACM International Conference on Ubiquitous Computing , ACM, 85–94.
Back, Mitja D., Juliane M. Stopfer, Simine Vazire, et al. 2010. Facebook profiles reflect actual personality, not self-idealization. Psychological Science 21 (3): 372–374.
Choi, Tae Rang, and Yongjun Sung. 2018. Instagram versus Snapchat: Self-expression and privacy concern on social media. Telematics and Informatics 35 (8): 2289–2298.
Lindqvist, Janne, Justin Cranshaw, Jason Wiese, Jason Hong, and John Zimmerman. 2011. I’m the mayor of my house: Examining why people use foursquare – a social-driven location sharing application. In Proceedings of the 2011 Annual Conference on Human Factors in Computing Systems – CHI ’11 , ACM Press, 2409.
Page, Xinru, Bart P. Knijnenburg, and Alfred Kobsa. 2013. What a tangled web we weave: Lying backfires in location-sharing social media. In Proceedings of the 2013 Conference on Computer Supported Cooperative Work – CSCW ’13 , ACM Press, 273.
Hogg, Tad, and D Wilkinson. 2008. Multiple Relationship Types in Online Communities and Social Networks . 6.
Page, Xinru, Reza Ghaiumy Anaraky, Bart P. Knijnenburg, and Pamela J. Wisniewski. 2019. Pragmatic tool vs. relational hindrance: Exploring why some social media users avoid privacy features. In Proceedings of the ACM on Human-Computer Interaction 3, CSCW: 1–23.
Fono, D., and K. Raynes-Goldie. 2006. Hyperfriends and beyond: Friendship and social norms on Live Journal. Internet Research Annual .
Zinoviev, Dmitry, and Vy Duong. 2009. Toward understanding friendship in online social networks. arXiv:0902.4658 [cs] .
Smith, Hilary, Yvonne Rogers, and Mark Brady. 2003. Managing one’s social network: Does age make a difference. In Proceedings of the Interact 2003, IOS Press, 551–558.
Ehrlich, Kate, and N. Shami. 2010. Microblogging inside and outside the workplace. Proceedings of the International AAAI Conference on Web and Social Media 4: 1.
Page, Xinru, Alfred Kobsa, and Bart P. Knijnenburg. 2012. Don’t disturb my circles! Boundary preservation is at the center of location-sharing concerns. In Proceedings of the Sixth International AAAI Conference on Weblogs and Social Media , 266–273.
Iachello, Giovanni, and Jason Hong. 2007. End-user privacy in human-computer interaction. Foundations and Trends in Human-Computer Interaction 1 (1): 1–137.
Article MATH Google Scholar
Bentley, Frank R., and Crysta J. Metcalf. 2008. Location and activity sharing in everyday mobile communication. In Proceeding of the Twenty-Sixth Annual CHI Conference Extended Abstracts on Human Factors in Computing Systems – CHI ’08 , ACM Press, 2453.
Tsai, Janice Y., Patrick Gage Kelley, Lorrie Faith Cranor, and Norman Sadeh. Location-Sharing Technologies: Privacy Risks and Controls . 34.
Friedland, Gerald, and Robin Sommer. 2010. Cybercasing the Joint: On the Privacy Implications of Geo-Tagging . 6.
Stefanidis, Anthony, Andrew Crooks, and Jacek Radzikowski. 2011. Harvesting ambient geospatial information from social media feeds.
Awad, Naveen Farag, and M.S. Krishnan. 2006. The personalization privacy paradox: An empirical evaluation of information transparency and the willingness to be profiled online for personalization. MIS Quarterly 30 (1): 13–28.
Chen, Xi, and Shuo Shi. 2009. A literature review of privacy research on social network sites. In 2009 International Conference on Multimedia Information Networking and Security , IEEE, 93–97.
Gerber, Nina, Paul Gerber, and Melanie Volkamer. 2018. Explaining the privacy paradox: A systematic review of literature investigating privacy attitude and behavior. Computers & Security 77: 226–261.
Houghton, David J., and Adam N. Joinson. 2010. Privacy, social network sites, and social relations. Journal of Technology in Human Services 28 (1–2): 74–94.
Pavlou, Paul A. 2011. State of the information privacy literature: Where are we now and where should we go. MIS Quarterly 35 (4): 977–988.
Xu, Feng, Katina Michael, and Xi Chen. 2013. Factors affecting privacy disclosure on social network sites: An integrated model. Electronic Commerce Research 13 (2): 151–168.
Xu, Heng, Rachida Parks, Chao-Hsien Chu, and Xiaolong Luke Zhang. 2010. Information disclosure and online social networks: From the case of Facebook news feed controversy to a theoretical understanding. AMCIS , Citeseer, 503.
Dinev, Tamara, Massimo Bellotto, Paul Hart, Vincenzo Russo, Ilaria Serra, and Christian Colautti. 2006. Privacy calculus model in e-commerce – a study of Italy and the United States. European Journal of Information Systems 15 (4): 389–402.
Selten, Reinhard. 1990. Bounded rationality. Journal of Institutional and Theoretical Economics (JITE)/Zeitschrift für die gesamte Staatswissenschaft 146 (4): 649–658.
Knijnenburg, Bart P., Elaine M. Raybourn, David Cherry, Daricia Wilkinson, Saadhika Sivakumar, and Henry Sloan. 2017. Death to the privacy calculus? In Proceedings of the 2017 Networked Privacy Workshop at CSCW , Social Science Research Network.
Dienlin, Tobias, and Sabine Trepte. Is the privacy paradox a relic of the past? An in-depth analysis of privacy attitudes and privacy behaviors. European Journal of Social Psychology 45 (3): 285–297.
Kokolakis, Spyros. 2017. Privacy attitudes and privacy behaviour: A review of current research on the privacy paradox phenomenon. Computers & Security 64: 122–134.
Palen, Leysia, and Paul Dourish. 2003. Unpacking “Privacy” for a networked world. NEW HORIZONS 5: 8.
Petronio, Sandra. 1991. Communication boundary management: A theoretical model of managing disclosure of private information between marital couples. Communication Theory 1 (4): 311–335.
Nissenbaum, Helen. 2010. Privacy in Context . Stanford University Press.
Wisniewski, Pamela, Heather Lipford, and David Wilson. 2012. Fighting for my space: Coping mechanisms for SNS boundary regulation. In Proceedings of the 2012 ACM annual conference on Human Factors in Computing Systems – CHI ’12 , ACM Press, 609.
Petronio, S. 2010. Communication Privacy Management Theory: What Do We Know About Family Privacy Regulation? Journal of Family Theory & Review 2 (3): 175–196.
Clemens, Chris, David Atkin, and Archana Krishnan. 2015. The influence of biological and personality traits on gratifications obtained through online dating websites. Computers in Human Behavior 49: 120–129.
Vitak, Jessica, and Nicole B. Ellison. 2013. ‘There’s a network out there you might as well tap’: Exploring the benefits of and barriers to exchanging informational and support-based resources on Facebook. New Media & Society 15 (2): 243–259.
Fogel, Joshua, and Elham Nehmad. 2009. Internet social network communities: Risk taking, trust, and privacy concerns. Computers in Human Behavior 25 (1): 153–160.
Agger, Ben. 2015. Oversharing: Presentations of Self in the Internet Age . Routledge.
Book Google Scholar
Krämer, Nicole C., and Nina Haferkamp. 2011. Online self-presentation: Balancing privacy concerns and impression construction on social networking sites. In Privacy Online: Perspectives on Privacy and Self-Disclosure in the Social Web , ed. S. Trepte and L. Reinecke, 127–141. Berlin: Springer.
The University of Central Florida, Wisniewski Pamela, A.K.M. Najmul Islam, et al. 2016. Framing and measuring multi-dimensional interpersonal privacy preferences of social networking site users. Communications of the Association for Information Systems 38: 235–258.
Pamela Wisniewski, A.K.M. Najmul Islam, Bart P. Knijnenburg, and Sameer Patil. 2015. Give social network users the privacy they want. In Proceedings of the 18th ACM Conference on Computer Supported Cooperative Work & Social Computing , ACM, 1427–1441.
Bouvier, Gwen. 2015. What is a discourse approach to Twitter, Facebook, YouTube and other social media: Connecting with other academic fields? Journal of Multicultural Discourses 10 (2): 149–162.
Altman, Irwin. 1975. The Environment and Social Behavior: Privacy, Personal Space, Territory, and Crowding . Monterey, CA: Brooks/Cole Publishing Company.
Paasonen, Susanna, Ben Light, and Kylie Jarrett. 2019. The dick pic: Harassment, curation, and desire. Social Media + Society 5 (2): 2056305119826126.
Karr-Wisniewski, Pamela, David Wilson, and Heather Richter-Lipford. 2011. A new social order: Mechanisms for social network site boundary regulation. In Americas Conference on Information Systems, AMCIS .
Page, Xinru, Pamela Wisniewski, Bart P. Knijnenburg, and Moses Namara. 2018. Social media’s have-nots: An era of social disenfranchisement. Internet Research 28: 5.
Sleeper, Manya, Rebecca Balebako, Sauvik Das, Amber Lynn McConahy, Jason Wiese, and Lorrie Faith Cranor. 2013. The post that wasn’t: Exploring self-censorship on Facebook. In Proceedings of the 2013 Conference on Computer Supported Cooperative Work , ACM, 793–802.
Das, Sauvik, and Adam Kramer. 2013. Self-censorship on Facebook. Proceedings of the International AAAI Conference on Web and Social Media 7: 1.
Lampinen, Airi, Vilma Lehtinen, Asko Lehmuskallio, and Sakari Tamminen. 2011. We’re in it together: Interpersonal management of disclosure in social network services. In Proceedings of the 2011 Annual Conference on Human Factors in Computing Systems – CHI ’11 , ACM Press, 3217.
Buchanan, Tom, Carina Paine, Adam N. Joinson, and Ulf-Dietrich Reips. 2007. Development of measures of online privacy concern and protection for use on the internet. Journal of the American Society for Information Science & Technology 58 (2): 157–165.
Malhotra, Naresh K., Sung S. Kim, and James Agarwal. 2004. Internet Users’ Information Privacy Concerns (IUIPC): The construct, the scale, and a causal model. Information Systems Research 15 (4): 336–355.
Westin, Alan. 1991. Harris-Equifax Consumer Privacy Survey . Atlanta, GA: Equifax Inc.
Page, Xinru, Reza Ghaiumy Anaraky, and Bart P. Knijnenburg. 2019. How communication style shapes relationship boundary regulation and social media adoption. In Proceedings of the 10th International Conference on Social Media and Society , 126–135.
Page, Xinru, Bart P. Knijnenburg, and Alfred Kobsa. 2013. FYI: Communication style preferences underlie differences in location-sharing adoption and usage. In Proceedings of the 2013 ACM International Joint Conference on Pervasive and Ubiquitous Computing , ACM, 153–162.
Page, Xinru Woo. 2014. Factors That Influence Adoption and Use of Location-Sharing Social Media . Irvine: University of California.
Solove, Daniel. 2008. Understanding Privacy . Cambridge, MA: Harvard University Press.
Knijnenburg, B.P., Alfred Kobsa, and Hongxia Jin. 2013. Dimensionality of information disclosure behavior. International Journal of Human-Computer Studies 71 (12): 1144–1162.
Wilkinson, Daricia, Paritosh Bahirat, Moses Namara, et al. 2019. Privacy at a glance: Exploring the effectiveness of screensavers to improve privacy awareness. In Proceedings of the ACM Conference on Human Factors in Computing Systems (CHI). Under Review , ACM.
Joinson, Adam N., Ulf-Dietrich Reips, Tom Buchanan, and Carina B. Paine Schofield. 2010. Privacy, trust, and self-disclosure online. Human–Computer Interaction 25 (1): 1–24.
Nissenbaum, Helen. 2004. Privacy as contextual integrity. Washington Law Review 79: 119–157.
Ramokapane, Kopo M., Gaurav Misra, Jose M. Such, and Sören Preibusch. 2021. Truth or dare: Understanding and predicting how users lie and provide untruthful data online.
Barkhuus, Louise. 2012. The mismeasurement of privacy: Using contextual integrity to reconsider privacy in HCI. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems , ACM, 367–376.
Cho, Hichang, Bart Knijnenburg, Alfred Kobsa, and Yao Li. 2018. Collective privacy management in social media: A cross-cultural validation. ACM Transactions on Computer-Human Interaction 25 (3): 17:1–17:33.
Hoy, Mariea Grubbs, and George Milne. 2010. Gender differences in privacy-related measures for young adult Facebook users. Journal of Interactive Advertising 10 (2): 28–45.
Li, Yao, Bart P. Knijnenburg, Alfred Kobsa, and M-H. Carolyn Nguyen. 2015. Cross-cultural privacy prediction. In Workshop “Privacy Personas and Segmentation”, 11th Symposium On Usable Privacy and Security (SOUPS) .
Sheehan, Kim Bartel. 1999. An investigation of gender differences in on-line privacy concerns and resultant behaviors. Journal of Interactive Marketing 13 (4): 24–38.
Wyatt, Sally M.E. 2003. Non-users also matter: The construction of users and non-users of the Internet. Now Users Matter: The Co-construction of Users and Technology : 67–79.
2018. Facebook and Instagram introduce time limit tool. BBC News . Retrieved February 10, 2021 from https://www.bbc.com/news/newsbeat-45030712 .
Andalibi, Nazanin. 2020. Disclosure, privacy, and stigma on social media: Examining non-disclosure of distressing experiences. ACM Transactions on Computer-Human Interaction (TOCHI) 27 (3): 1–43.
Gibbs, Martin, James Meese, Michael Arnold, Bjorn Nansen, and Marcus Carter. 2015. #Funeral and Instagram: Death, social media, and platform vernacular. Information, Communication & Society 18 (3): 255–268.
Download references
Author information
Authors and affiliations.
Brigham Young University, Provo, UT, USA
Xinru Page & Sara Berrios
Department of Computer Science, Clemson University, Clemson, SC, USA
Daricia Wilkinson
Department of Computer Science, University of Central Florida, Orlando, FL, USA
Pamela J. Wisniewski
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Xinru Page .
Editor information
Editors and affiliations.
Clemson University, Clemson, SC, USA
Bart P. Knijnenburg
University of Central Florida, Orlando, FL, USA
Pamela Wisniewski
University of North Carolina at Charlotte, Charlotte, NC, USA
Heather Richter Lipford
School of Social and Behavioral Sciences, Arizona State University, Tempe, AZ, USA
Nicholas Proferes
Bridgewater Associates, Westport, CT, USA
Jennifer Romano
Rights and permissions
Open Access This chapter is licensed under the terms of the Creative Commons Attribution 4.0 International License ( http://creativecommons.org/licenses/by/4.0/ ), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license and indicate if changes were made.
The images or other third party material in this chapter are included in the chapter's Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the chapter's Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder.
Reprints and permissions
Copyright information
© 2022 The Author(s)
About this chapter
Page, X., Berrios, S., Wilkinson, D., Wisniewski, P.J. (2022). Social Media and Privacy. In: Knijnenburg, B.P., Page, X., Wisniewski, P., Lipford, H.R., Proferes, N., Romano, J. (eds) Modern Socio-Technical Perspectives on Privacy. Springer, Cham. https://doi.org/10.1007/978-3-030-82786-1_7
Download citation
DOI : https://doi.org/10.1007/978-3-030-82786-1_7
Published : 09 February 2022
Publisher Name : Springer, Cham
Print ISBN : 978-3-030-82785-4
Online ISBN : 978-3-030-82786-1
eBook Packages : Computer Science Computer Science (R0)
Share this chapter
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research
Social Media Issues Essay Examples and Topics
Social media and interpersonal relationships, social media and globalization: positive and negative effects essay.
- Words: 3161
Social Media: Negative and Positive Impacts
The effect of social media on today’s youth.
- Words: 2165
People’s Responsibility in the Social Media World and Its Effects on the Reputation
- Words: 1426
The Impact of Social Media on the Rise in Crime
Social media impacts in the “cyberbully” film.
- Words: 1179
The Effects of Social Media on Society
- Words: 1135
Social Media in Future: Twitter, Instagram and Tango
- Words: 1147
Adorno and Horkheimer ‘The Culture Industry’ Review
The role of social media.
- Words: 1590
Social Media’s Impact on Children
The social media effects on football clubs.
- Words: 1401
Impact of Electronic Environment on One’s Personal Security
Cyberbullying as a major problem in contemporary society.
- Words: 1107
Social Media Addiction in Society
Social networking threats for children, electronic crime: online predators on facebook.
- Words: 3984
Podcasts: Definition and Functions
Facebook addiction in the modern society, romania’s social media and technologies.
- Words: 1660
Social Media and Mental Health
- Words: 1165
Likecoholic: Social Media Addiction
Social media audit: the most effective social media channels.
- Words: 2877
Moral Panic Concept
- Words: 2072
Is Social Media Causing People to Lose Compassion?
Self-verification and self-enhancement on social media, fake trends on social media platforms: twitter, privacy in the age of social media, social media benefits: twitter, instagram, and google plus.
- Words: 1193
Intimacy and Media Technologies
Social media and the family, positives and negatives to having virtual communities, fake news in the age of social media.
- Words: 4188
Social Media Communication and Friendship
Intimacy and sexuality behaviors in social media.
- Words: 2529
Faux Friendship and Social Networking
- Words: 2976
Personal Information in Social Media Platforms
Social media appropriation for activism.
- Words: 3041
Impact of Digital Technologies on a Human Mind
Using social media as a reference checking method, the “how to fix social media” article by nicholas carr, developing technologies of humility, social media: past, present, and future, social media marketing and user satisfaction.
- Words: 1096
Applied Research in Action: Emergency Study
Travel agencies’ use of social media, the “johnny harris” youtube channel and perception.
- Words: 1444
Major Issues Caused by Social Media (TikTok)
Montreal toheed society shifting to the new platform, social networks’ negative impact on relationships.
- Words: 1543
Social Media Platforms and Sports
Smartphone addiction in the united states.
- Words: 1112
Libel Law: Relation to Social Media
Self-profiling in digital media, the social dilemma: the documentary response, discussion: social media addiction, new horizons agency’s transformation into a social media platform.
- Words: 3129
Facts and Evidence in the E-Cigarettes Articles
Why is tiktok popular among teens, attracting the target audience through social media, how instagram claimed its users’ most intimate moments.
- Words: 3195
How Heavy Use of Social Media Is Linked to Mental Illness
- Words: 3365
Do Social Media Algorithms Lead to Harmful Social and Political Polarization?
Twitter accepts elon musk’s offer to buy company in $44 billion deal, “un condemns mali’s ban on french media” by bibbo, do social media algorithms lead to harmful social polarization, facebook and safety, security, and privacy issues, human consciousness: impact of social media, social media damages teenagers’ mental health, media literacy research: analysis of the issue, the testimony of frances haugen: facebook violations, social media as a component of mass communication, social media use and the risk of depression.
- Words: 1478
Instagram Addiction and Impact on Self-Esteem
- Words: 2800
Facebook Privacy Issue: Local, National, and Global Media Portrayals
Social media practice and offline presence, triggers behind electronic word-of-mouth, instagram addiction and self-esteem in kuwaiti high school students, impacts of instagram use on users’ well-being, tiktok users’ perception of intellectual property, instagram addiction and self-esteem in high school students, why the business class community opposes investigative journalism, how should the state deal with disinformation about covid-19 on social media, discussion on culture and news, modern internet and hate speech.
- Words: 1218
What Happens on Twitter Stays on Twitter
Social media and women’s mental health.
- Words: 2265
Surveillance Capitalism on Digital Platforms
Digital platforms: problem and solution, the digital self-harm among adolescents, conspiracy theories and prejudices in social media, social media promotes the pursuit of the thin ideal amongst teens, social media coverage in russia vs. global trends.
- Words: 3614
Social Media Risks to Patient Information
Social media profile matters for moderate voters, social media designers awareness training program.
- Words: 2242
Indigenous People Shown in Social Media
- Words: 1431
Social Media and Its Effects on Adolescents
Social media impact on political segregation.
- Words: 2453
The Cronkite News Homepage’s Improvement
The role of social media in businesses credibility, current formats of media and their traditional analogs, case activity: a plan for fair trade mojo, social media: impact on the retail business.
- Words: 1004
Media Bias Fact Check: Website Analysis
The problem of creating a false self in the social networks, cyberbullying and preventive strategies, reliability and validity analyses, social media and human rights memorandum, social media and social work practice.
- Words: 2340
The Influence of Social Media on Its Users’ Everyday Lives
- Words: 1388
Social Media and Credible Sources of Information
Bullying through social media: methods, bullying through social media: research proposal.
- Words: 1307
Free Speech and the Internet
Social media impact on wealth accumulation, how facebook invades privacy and security information, public opinion formed by celebrities in social media.
- Words: 1923
The Privacy Paradox in Contemporary Social Media
- Words: 2289

IMAGES
VIDEO
COMMENTS
(Busakorn Pongparnit) Amid public concerns over Cambridge Analytica's use of Facebook data and a subsequent movement to encourage users to abandon Facebook, there is a renewed focus on how social media companies collect personal information and make it available to marketers.. Pew Research Center has studied the spread and impact of social media since 2005, when just 5% of American adults ...
This essay will examine the privacy concerns associated with social media use. It will discuss how personal information is collected, used, and potentially misused by social media platforms and third parties. The piece will explore the implications of data breaches, targeted advertising, and the erosion of privacy boundaries.
This essay about privacy issues in social media discusses the complexities and risks associated with the vast amounts of personal data shared on platforms like Facebook, Twitter, and Instagram. It highlights the lack of transparency in how companies use this data, often hidden behind dense privacy policies, and the risks of data being shared ...
This argumentative essay will discuss the privacy issues that users may encounter on social media and argue that it is important to have a balance between privacy and online confidentiality to operate effectively in both the offline and online worlds. We will write a custom essay on your topic tailored to your instructions!
According to Cha (2011), security and privacy problems emanating from social media are classified into behavioral and technical issues. One of the problems associated with social media is the invasion of privacy. This has been attributed to technological advancements that have made invasion of privacy not only feasible, but also achievable.
Now that system, which ballooned into a $350 billion digital ad industry, is being dismantled. Driven by online privacy fears, Apple and Google have started revamping the rules around online data ...
Essential concerns that need to be addressed include the effect of social media on individual privacy, the accountability of social media businesses, and the requirement for greater regulation to safeguard user rights. We can make everyone's online experience safer and more secure by looking more closely at these issues. Last Words
Abstract. Most people's immediate concern about privacy in social media, and about the internet more generally, relates to data protection. People fear that information they post on various platforms is potentially abused by corporate entities, governments, or even criminals, in all sorts of nefarious ways. The main premise of this chapter is ...
In thinking about privacy, two emerging phenomena are of particular interest: on the one hand, technological architectures of social media push the boundaries of disclosure—both voluntary and involuntary—accompanied by privacy policy in the terms and conditions (T&C) 2 of use. In response, the question of informed consent has entered European law, to counterbalance a perceived disparity in ...
Social media users usually post private information as part of the process of knowing one another. Since social media is associated with having a large number of users unknown to the client, there is an increased risk of exposing personal details to cybercriminals. Social media is a threat to privacy. Social media has increased privacy concerns ...
This is why privacy can be viewed as the biggest ethical issue regarding digital media through, social privacy issues and data privacy issues. 2186 Words 9 Pages
Introduction. With 4.76 billion (59.4%) of the global population using social media (Petrosyan, Citation 2023) and over 46% of the world's population logging on to a Meta Footnote 1 product monthly (Meta, Citation 2022), social media is ubiquitous and habitual (Bartoli et al., Citation 2022; Geeling & Brown, Citation 2019).In 2022 alone, there were over 500 million downloads of the image ...
The social media privacy model. Social media privacy is based on interpersonal processes of mutual disclosure and communication (Altman, 1975; Petronio, 2002). Further, it can be considered a value that is co-developed by engaging in communication and that is expressed by a shared perception (Nissenbaum, 2010; Smith et al., 2011). On the basis ...
"We are totally exposed": Young people share concerns about social media's impact on privacy and mental health in global survey. Instagram, TikTok and other social media have become daily fixtures in the lives of children and young people around the world, with 59% of young people surveyed by Amnesty International now spending more than two hours of their average day on social media.
Section Highlights. Information disclosure privacy issues have been a dominant focus in online technologies and the primary focus for social media. It focuses on access to data and defining public vs. private disclosures.It emphasizes user control over who sees what. With so many people from different social circles able to access a user's social media content, the issues of context collapse ...
The growing online presence also created an unprecedented visibility opportunities, which immediately raised privacy concerns. With the increasing number of controversies surrounding the safety of personal information, the Internet has been termed by some "the final blow to privacy.". However, I argue that while it certainly changed the way ...
In our study, 78% of users reported experiencing specific privacy issues, shedding light on the prevalence and nature of challenges individuals face on social media platforms. These issues ...
Check our 100% free social media issues essay, research paper examples. Find inspiration and ideas Best topics Daily updates. Clear. Writing Help Login Writing Tools. ... The issue of security and privacy is one of the most pressing in the digital environment and the media. Common Sense Media and UNESCO promote the development and education of ...
In this paper it has been provided a brief overview of some attire to users' privacy. Classification has been made of these threats as: users' block, design pitfall and limitations, implicit flows of information, and clash of stimulus. Further also describe about the privacy and security issues associated with social network systems.
Over 30 years ago, Mason (Citation 1986) voiced ethical concerns over the protection of informational privacy, or "the ability of the individual to personally control information about one's self" (Stone et al., Citation 1983), calling it one of the four ethical issues of the information age.Since the 1980s, scholars have remained concerned about informational privacy, especially given ...
Data protection issues and loopholes in privacy controls can put user information at risk when using social media. Other social media privacy issues include the following. 1. Data mining for identity theft. Scammers do not need a great deal of information to steal someone's identity.