Got any suggestions?
We want to hear from you! Send us a message and help improve Slidesgo
Top searches
Trending searches


solar eclipse
25 templates

16 templates

autism awareness
28 templates

12 templates

35 templates

7 templates
3D Presentation templates
Life in 3d looks better. make your presentations have 3d elements with these templates for google slides and powerpoint. what are you waiting for to go three-dimensional.

3D Characters Consulting Toolkit
Let these cute 3D characters guide your audience through a perfect plan for your client’s company. Thanks to the illustrative resources we have included (SWOT analysis, charts, diagrams, maps, infographics, strategy maps, growth matrixes…) and the help of your new little friends, the project’s success is ensured. The design and...
Premium template
Unlock this template and gain unlimited access
3D Acid Y2K Aesthetics Marketing Plan
The Internet is all about it: Y2K this, Y2K that… but what does that even mean? Let me give you a hint: shiny aesthetics, chains, old computers, oversaturated pictures, graffitis… those are the aesthetics that were trending in the first years of this new century, and they have made a...

Social Media Collaboration
Download the Social Media Collaboration presentation for PowerPoint or Google Slides. How do you use social media platforms to achieve your business goals? If you need a thorough and professional tool to plan and keep track of your social media strategy, this fully customizable template is your ultimate solution. It...

Genetic Therapy for Down Syndrome Breakthrough
Download the Genetic Therapy for Down Syndrome Breakthrough presentation for PowerPoint or Google Slides.Treating diseases involves a lot of prior research and clinical trials. But whenever there’s a new discovery, a revolutionary finding that opens the door to new treatments, vaccines or ways to prevent illnesses, it’s great news. Should...
Icons Infographics
Download the Icons Infographics template for PowerPoint or Google Slides and discover the power of infographics. An infographic resource gives you the ability to showcase your content in a more visual way, which will make it easier for your audience to understand your topic. Slidesgo infographics like this set here...

Fructose Malabsorption Syndrome
Download the Fructose Malabsorption Syndrome presentation for PowerPoint or Google Slides. Taking care of yourself and of those around you is key! By learning about various illnesses and how they are spread, people can get a better understanding of them and make informed decisions about eating, exercise, and seeking medical...

Ionizing Radiation and Health Effects
Download the Ionizing Radiation and Health Effects presentation for PowerPoint or Google Slides. Healthcare goes beyond curing patients and combating illnesses. Raising awareness about diseases, informing people about prevention methods, discussing some good practices, or even talking about a balanced diet—there are many topics related to medicine that you could...
3D Infographics
Download the 3D Infographics template for PowerPoint or Google Slides and discover the power of infographics. An infographic resource gives you the ability to showcase your content in a more visual way, which will make it easier for your audience to understand your topic. Slidesgo infographics like this set here...
3D Gradient Style Advertising Agency
Your agency is the most popular one in all dimensions known and yet to be known. That's because your services offered have no equal... and the presentations you use are unrivaled too! Present your company profile and be ahead of the competition with slides that make use of three-dimensional shapes...

Candlelight Concert Project Proposal
Download the Candlelight Concert Project Proposal presentation for PowerPoint or Google Slides. A well-crafted proposal can be the key factor in determining the success of your project. It's an opportunity to showcase your ideas, objectives, and plans in a clear and concise manner, and to convince others to invest their...

3D Printing Prosthesis Pitch Deck
Present your innovative 3D printing prosthesis idea with this modern and professional pitch deck. This template comes with all the slides you need, including an introduction slide, a timeline, a results slide, and more. With custom diagrams and 3D models, you can show the audience the impact that 3D printing...

Brutalist Style Planner for College
College is the first step to get higher degrees, so you must take it seriously. For example, download our template and start planning classes, exams and other things you need. It's for teachers and students alike, since its multiple layouts are completely customizable. The dark colored backgrounds contrast with the...

World Health Day Medical Newsletter
Download the World Health Day Medical Newsletter presentation for PowerPoint or Google Slides. Attention all marketers! Are you looking for a way to make your newsletters more creative and eye-catching for your target audience? This amazing template is perfect for creating the perfect newsletter that will capture your audience's attention...
Technical Drawing Printable Sheets: building 3D geometric shapes in Middle School
We are sure that your technical drawing classes are full of creativity and precision. We wanted to contribute to your work by designing this wonderful template in gradient shades of purple so you can give your lesson on building 3D geometric shapes to your middle school students. Download this presentation...

3D Printing Day
3D is coming! 3D? December 3rd or 3D which refers to three-dimensional objects? Well, it's both! In a very appropriate way, December 3rd (3D) has been chosen as International 3D Printing Day and we at Slidesgo want to join the party. And what we bring to the party is not...

3D Radiography to Find Diseases
Radiography has existed since decades and has allowed many diseases to be prevented and cured, and for that is Wilhem Röntgen to be thanked. He was the one to first discover X-Rays, the science behind radiographies. However, his work doesn’t stop there, scientists of today have developed new techniques that...
3D Printing Processes
Did you get a new key holder? Oh, are you talking about this? I made it by myself. What? Yes, we bought a 3D printer and you can make literally anything! But, wait a minute, how does a 3D printer work? We know that you are an expert in this...
- Page 1 of 31
New! Make quick presentations with AI
Slidesgo AI presentation maker puts the power of design and creativity in your hands, so you can effortlessly craft stunning slideshows in minutes.
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
- Data Concealment Methods
- Knapsack Encryption Algorithm in Cryptography
- Message Authentication Codes
- Simplified Data Encryption Standard Key Generation
- Schnorr Digital Signature
- Winternitz One Time Signature Scheme
- Merkle-Damgard Scheme in Cryptography
- Simplified Data Encryption Standard | Set 2
- Vernam Cipher in Cryptography
- Voice Biometric Technique in Network Security
- RSA Algorithm using Multiple Precision Arithmetic Library
- Onion Routing
- Chaumian Blinding
- Advanced Encryption Standard (AES)
- Digital Certificate Creation
- DjVu Compression in Computer Network
- Key Management in Cryptography
- Privacy Enhanced Mail (PEM) and it's Working
- What is p-box in Cryptography?
3D passwords-Advanced Authentication Systems
The increase in the usage of computer systems has given rise to many security concerns. One of the major security concern is authentication , which is the process of validating who you are to whom you claimed to be.
Current authentication systems suffer from various weaknesses. People usually use textual passwords; however they do not follow their requirements.The issue is that users intend to use meaningful words from the dictionary, which eventually are easier to break and vulnerable to attack.
A major drawback of the textual password is its conflicting requirements- the selection of a password that is easy to remember(for the user), and at the same time, hard to guess(to prevent unauthorized access to private data).
As a solution, many biometric authentications have been proposed. These include:
However, users usually tend to resist biometrics because:
- because of their effect on privacy and their intrusiveness.
- moreover, biometrics cannot be revoked.
3D password is a multi factor authentication scheme, that is, it is a security approach that requires the user to provide more than 1 identity factor before accessing their data.
Some factors include:
- what a user KNOWS: that is their password.
- what a user HAS: that is a smart card/hard token.
- what a user IS: that is a retinal scan/ finger print.
To be authenticated into a secure system, we present a 3-D virtual environment where the user navigates and interacts with various objects. The sequence of actions and interactions towards the objects inside the environment.Then the user’s password is constructed. The password can combine most existing authentication schemes, i.e., graphical and textual passwords and various biometrics into a virtual 3D environment.
The design of the 3D virtual environment and the type of objects selected determine the 3D password key space.
Advantages:
- easy to remember and is highly secure.
- easy to customise.
- difficult to share.
- 3D graphical password has no limit.
Disadvantages:
- difficult to use for the blind people.
- requires complex computer technology.
Please Login to comment...
Similar reads.
- cryptography
- How to Use Bard for Creative Writing
- How To Get A Free Domain Name [2024]
- 10 Best Crypto Portfolio Tracker Apps in 2024
- 10 Best Free Blockchain Learning apps for Android in 2024
- 30 OOPs Interview Questions and Answers (2024)
Improve your Coding Skills with Practice
What kind of Experience do you want to share?

3D Password
Apr 11, 2018
440 likes | 783 Views
password can combine most existing authentication schemes such as textual passwords, graphical passwords, and various types of biometrics into a 3D virtual environment. The choice of what authentication schemes will be part of the user's 3D password reflects the user's preferences and requirements.
Share Presentation
- authentication schemes
- 3d password
- 4d password
- preferred 3d password
- multi factor authentication scheme

Presentation Transcript
3D PASSWORD FOR SECURE AUTHENTICATION ASHA KUMARI MONA THAKUR NEHA THAKUR POOJA KUMARI SHALINI KUMARI
CONTENTS • Password • Advantages and disadvantages • Introduction • 3d password • Functionalities Required • Mathematical concept • Working • Attacks and counter measure • Applications • 4d password differentiator • Future work
PASSWORD:- • A password is a secret word used for user authentication to prove identity or access approval to gain access to a resource. • In modern times, username and passwords are commonly used by people during a login process that controls access to protected computer operating systems, mobiles phones, cable TV decoders, automated teller machines (ATMs), etc.
TYPES OF PASSWORD:- • Random password • Common password
RANDOM PASSWORD • Random password:-An easy to remember password, which is based on a pass-phrase that is important to you, the user. • This phrase can be a set of words taken from a book, a song, a quotation, a statement, or anything else that you always easily remember. • No one else should ever think about attributing it to you. • E.G: pass-phrase: “four score and seven years ago our fathers” • Password: “Fs&7yA0F”.
COMMON PASSWORD • Easy to remember password, which is based on a combination of two unrelated words with a mixed case of letters, numbers and symbols. • E.G: pass-words: “funny bone” • Password: “phnyb0ne”.
ADVANTAGES AND DISADVANTAGES • Can only be accessed by the owner of the site. • A password protected website. • Password may protect files, folders and documents. • Disadvantages:- • If you don’t have strong server security, someone can break into the database and read the password.
INTRODUCTION • Commonly used authentication schemes are textual passwords, graphical passwords and biometrics. • 3D password is a multifactor authentication scheme. • To be authenticated, were 3D virtual environment. • Combines recognition, recall, token, and biometrics-based systems. • Users choice to select the type of authentication technique.
3D PASSWORD • It is a multi factor authentication scheme. • It is not only based on recall and recognition. • It is the combination of recall, recognition, biometrics as well as token-based authentication schemes. • It is also known as 3 dimensional virtual environment. • It contain any virtual object.
VIRTUAL OBJECTS ARE: • A computer with which user can type. • A fingerprint reader that requires the user’s fingerprint. • An ATM machine that requires a smart card and PIN. • A light that can be switched ON/OFF. • A television or radio where channels can be selected. • A car that can be driven. • A paper or a whiteboard that a user can write, sign, or draw on.
AUTHENTICATION SCHEMES • KNOWLEDGE BASED • Recall based • Recognition based • TOKEN BASED e.g. : smart card
BIOMETRIC BASED • Fingerprint ,palm prints ,hand geometry ,face recognition • GRAPHICAL PASSWORDS • Picture based.
FUNCTIONALITIES REQUIRED • New scheme should combine the existing authentication schemes • Freedom to select the type of authentication technique. • Should provide secrets that are easy to remember ,difficult to guess.
MATHEMATICAL CONCEPT • Time complexity • Space complexity
WORKING OF 3D PASSWORD • Representation of user actions in the 3D virtual environment (10,24,91) Action=Open the office door; (10,24,91) Action=Close the office door; (4,34,18) Action= Typing, “A”; (4,34,18) Action= Typing, “N”; (4,34,18) Action= Typing, “G”; (4,34,18) Action= Typing, “E”; (4,34,18) Action= Typing, “L”; (10,24,80) Action= Pick up the pen; (1,18,80) Action= Drawing, point=(330,130).
Virtual Computer where user typing a textual password as a part of user’s 3D Password
State diagram of a 3D Password application
ATTACKS AND COUNTER MEASURE • Time attacks. • Brute force attacks. • Well studied attacks. • Key logger. • Shoulder suffering attacks.
APPLICATION • Nuclear and military areas. • Air plans and jetfighters. • Critical server. • Other areas.
4D PASSWORD DIFFERENTIATOR • Flexibility: allow multifactor authentication. • Biometrics and textual passwords can be embedded in 4d password. • Strength: provides unlimited password possibilities. • Easy to remember: can be remembered in the form of short story. • Privacy: organizer can select authentication schemes that respect the user’s privacy.
FUTURE WORK • Use different password for different accounts. • Use 3d password. • The 3d password will protect against many brute force attacks. • A brute password cracker will simply attempt to guess your password. • Use longer password, harder to crack. • Brute force attack known as a dictionary attack.
CONCLUSION • Commonly used authentication schemes are vulnerable to attacks. • 3D Password is a multifactor authentication scheme. • User’s choice and decision to construct the desired and preferred 3D password.
- More by User

Password Protection
Password Protection. Passwords Basic Problem. What you know Passwords Secret key Where you are IP address What you are Biometrics What you have Secure tokens. How do you prove to someone that you are who you claim to be? Any system with access control must solve this problem.
468 views • 23 slides

449 views • 14 slides

Password Managers
Password Managers. Software that can create and remember different passwords for different sites . Today’s Agenda:. Do your passwords measure up? What makes for a good password? Reconciling security and complexity with usability. Comparison of popular password manager applications.
447 views • 28 slides

Password Management:
Password Management:. Creating and managing passwords to be as secure as possible. Table of contents. The scale of consumer cyber crime What is a password and facts about password security and its importance Tiered password system - review and categorize your existing passwords
1.49k views • 53 slides

PASSWORD. Reading the Classics. PASSWORD Vocab #1: Game 1. Cravat Depredation Visage Cupreous Pumice . PASSWORD Vocab #1: Game 2. Irrevocably Pennant Asperity Fetid insignia. PASSWORD Vocab #1: Game 3. Insignia pumice Visage asperity Irrevocably .
511 views • 5 slides

Economics Vocabulary. PASSWORD. Natural resources. Raw materials from nature used to produce goods. Can be renewable (has no limit, like the sun’s energy) or non-renewable (limited supply, as in oil). . HUMAN CAPITAL.
358 views • 20 slides

Password Management
Password Management. Password Protection. Virtually all multiuser systems require that a user provide not only a name or identifier (ID) but also a password. The password serves to authenticate the ID of the individual logging on to the system.
4.82k views • 19 slides


3D PASSWORD
3D PASSWORD. Prepared By Gauswami Hetal G.R.NO.707. Topic of overview. Introduction Authentication schemes Functionalities required 3D password selection and input Virtual environment design guidelines Applications Security analysis Advantages & disadvantages. Introduction.
8.31k views • 15 slides
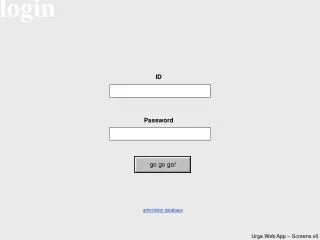
login. go go go!. ID. Password. administer database. welcome. NEW CUSTOMER. We have a new customer! >>>. FIND EXISTING CUSTOMER. By surname By enquiry date By tour start date By e-mail. Select…. Select…. Select…. Select…. REPORTS. Take a gander at some reports. customer details.
269 views • 11 slides

Password Managers. What is a Password Manager?. A tool that stores logon names, passwords, PINs other items related to Web and program logons. This data is stored in an encrypted file and is accessed with a "master" password.
434 views • 24 slides

Password cracking
Password cracking. Patrick Sparrow, Matt Prestifillipo, Bill Kazmierski. Overview. Who uses password crackers? List of programs needed Gain access to password list Password Salting Installing John the Ripper How to use PwDump2 and John the Ripper How to make a strong password.
293 views • 10 slides

Password Security
Password Security. Everything (well… a lot, anyway) you didn’t know, or want to, but really actually need to. Quote of the Day:. Treat your password like your toothbrush. Don't let anybody else use it, and get a new one every six months.”
564 views • 21 slides
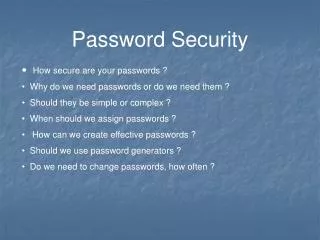
Password Security. How secure are your passwords ? Why do we need passwords or do we need them ? Should they be simple or complex ? When should we assign passwords ? How can we create effective passwords ? Should we use password generators ?
5.46k views • 19 slides

CLASP Project Update. C5 Meeting, 16 June 2000. Denise Heagerty, IT/IS. Password?. Password?. Password?. Password?. Password?. Password?. Password?. Outline. CLASP purpose and phase 1 Goals Service survey results Kerberos feasibility results Integration with GRID applications
491 views • 19 slides

Forget Password
Forget Password. Double Click on Odin Diet 9.1.0.5. Double Click Here. Click on File & Click on Login. Click on Forgot Password. Click Here. Enter your Client Code and Email id {Register with our BackOffice} & click on Submit. 123456. [email protected].
273 views • 7 slides

Free Password Locker | Password Manager - AKick
Save your personal account with free password locker https://goo.gl/QtfXdp .If you forget your personal password or old password. So don't worry.! Here you can save your bank account password or you can recover your password with help of AKick password safeguard.
228 views • 7 slides

Password Security. Overview. What are passwords, why are they used? Different types of attacks Bad password practices to avoid Good password practices How to create a secure password. What are passwords?. Secret combination of characters that only a user should know.
732 views • 22 slides

Password Cracking
Password Cracking. By Allison Ramondetta & Christine Giordano. Definition.
173 views • 9 slides

PASSWORD SECURITY
PASSWORD SECURITY. A Melbourne Athenaeum Library Cybersafety Information Guide. Image source: https://pixabay.com/en/password-keyword-codeword-solution-397657. Why use passwords?.
289 views • 11 slides

Microsoft 365 Life Hacks > Presentations > How to create an educational presentation
How to create an educational presentation
Using presentations can be an effective way to teach lessons and ensure that your audience can retain new facts. With visual aids, video and animated clips, and even interactive quizzes, you can use presentation software like Microsoft PowerPoint to dazzle your students.

The advantages of PowerPoint presentations in education
Students have different learning styles : some are visual learners, who retain images and videos more effectively than speech. Some take to audio and sound more easily. Others prefer to interact with their lessons—which usually refers to holding physical objects but can also be directly related to guessing answers and responding to questions.
Fortunately, PowerPoint’s versatility means that it can appeal to all of these diverse learning styles. You can embed multimedia elements such as videos, audio clips, and interactive graphics, creating a multi-sensory experience. PowerPoint can also be helpful when considering any visual impairments that your audience members may have so that you can present with different forms of media to cater to all learning styles.

Tell your story with captivating presentations
Powerpoint empowers you to develop well-designed content across all your devices
Before diving into PowerPoint, consider the following factors to help your audience retain as much information as possible:
- Define lesson objectives: Set a goal for what kind of lesson you want to impart to your audience. What do you want students to learn? You can answer this question by outlining your lesson objectives and clearly defining your goals, which will also guide the structure and content of your presentation.
- Organize your content: Divide your lesson into key points and organize them into a logical sequence that builds in complexity. Start with basic points or even a review of previous concepts before diving into more intricate or complicated aspects of your lesson. Each point should be presented on a separate slide to maintain clarity and focus.
- Use visuals effectively: Enhance your presentation with relevant visuals such as images, videos, audio clips, or interactive simulations to cater to different learning preferences and keep the presentation engaging. These can convey complex information more efficiently than text alone. At the same time, it can be easy to be carried away by inundating your audience with too many visual elements, so ensuring smooth flow and transitions is key.
- Encourage interaction: Foster active participation by including interactive elements like quizzes, polls, or discussion prompts to prompt student engagement. After you introduce a new concept in your lesson, these interactive elements can reinforce them and make them stick.
- Practice delivery: Public speaking isn’t always easy. One of the most effective ways to sound confident is to practice delivering your presentation before the day of your lesson. Familiarize yourself with the content and also the way that it’s presented: pacing, transitions, and interactive elements. This preparation will boost your confidence, ensure a smooth flow, and help you address any potential challenges during the actual presentation.
Staid lessons can be livened up thanks to the power of presentation! No matter what you’re teaching—the ABCs to a kindergarten class, or nuclear physics to a graduate department—you can check out more tips for effective presenting such as how to create compelling presentation designs , using the 10-20-30 rule for presenting, or discovering the history of PowerPoint .
Get started with Microsoft 365
It’s the Office you know, plus the tools to help you work better together, so you can get more done—anytime, anywhere.
Topics in this article
More articles like this one.

Five tips for choosing the right PowerPoint template
Choose an appropriate PowerPoint template to elevate your presentation’s storytelling. Consider time length, audience and other presentation elements when selecting a template.

How you can use AI to help you make the perfect presentation handouts
Learn how AI can help you organize and create handouts for your next presentation.

How to use AI to help improve your presentations
Your PowerPoint presentations are about to get a boost when you use AI to improve a PowerPoint presentation.

How to password protect your PowerPoint presentations
Learn how to password protect your PowerPoint presentations and secure your valuable files.

Everything you need to achieve more in less time
Get powerful productivity and security apps with Microsoft 365

Explore Other Categories
Suggestions or feedback?
MIT News | Massachusetts Institute of Technology
- Machine learning
- Social justice
- Black holes
- Classes and programs
Departments
- Aeronautics and Astronautics
- Brain and Cognitive Sciences
- Architecture
- Political Science
- Mechanical Engineering
Centers, Labs, & Programs
- Abdul Latif Jameel Poverty Action Lab (J-PAL)
- Picower Institute for Learning and Memory
- Lincoln Laboratory
- School of Architecture + Planning
- School of Engineering
- School of Humanities, Arts, and Social Sciences
- Sloan School of Management
- School of Science
- MIT Schwarzman College of Computing
- Q&A: Tips for viewing the 2024 solar eclipse
Q&A: Tips for viewing the 2024 solar eclipse
Press contact :.

Previous image Next image
On Monday, April 8, the United States will experience a total solar eclipse — a rare astronomical event where the moon passes directly between the sun and the Earth, blocking out the sun’s light almost completely. The last total solar eclipse in the contiguous U.S. was in 2017, and the next one won’t be until 2044.
If the weather cooperates, people across the United States — from northeastern Maine to southwestern Texas — will be able to observe the eclipse using protective eyewear. Those in the path of totality , where the moon entirely covers the sun, will have the best view, but 99% of people in the continental U.S. will be able to see a partial eclipse. Weather permitting, those on the MIT campus and the surrounding area will see 93 percent of the sun covered, with the partial eclipse starting at 2:15 p.m. and reaching its peak around 3:29 p.m. Gatherings are planned at the Kresge Oval and the MIT Museum , and a live NASA stream will be shown in the Building 55 atrium .
Brian Mernoff , manager of the CommLab in the Department of Aeronautics and Astronautics, is an accomplished astrophotographer and science educator. Mernoff is headed to Vermont with his family to experience the totality from the best possible angle — but has offered a few thoughts on how to enjoy the eclipse safely, wherever you are.
Q: What should viewers expect to see and experience with this solar eclipse?
A: When you’re watching TV (the sun) and your toddler, dog, or other large mammal (the moon) blocks your view, you no doubt move over a bit to try to get a partial or full view of the TV. This is exactly how the path of totality works for an eclipse. If you are exactly in line with the moon and sun, it will be completely blocked, but if you start moving away from this path, your view of the sun will start to increase until the moon is not in the way at all.
The closer you are to the path of totality, the more of the sun will be blocked. At MIT, about 93 percent of the sun will be blocked. Those in the area will notice that things around you will get slightly darker, just like when it starts to become overcast. Even so, the sun will remain very bright in the sky and solar glasses will be required to view the entirety of the eclipse. It really goes to show how incredibly bright the sun is!
Within the narrow path of totality, the moon will continue to move across the sun, reaching 100 percent coverage. For this short period of time, you can remove your glasses and see a black disk where the sun should be. Around the disk will be wispy white lines. This is the corona, the outermost part of the sun, which is normally outshone by the sun’s photosphere (surface). Around the edges of the black disk of the moon, right as totality begins and ends, you can also see bright spots around the edges, known as Bailey’s Beads, caused by sunlight shining between mountains and craters on the moon.
But that’s not all! Although you will be tempted to stare up at the sun throughout totality, do not forget to observe the world around you. During totality, it feels like twilight. There is a 360-degree sunset, the temperature changes rapidly, winds change, animals start making different sounds, and shadows start getting weird (look into “shadow bands” if you have a chance).
As soon as totality ends, and you start to see Baily’s Beads again, put your solar glasses back on as it will get very bright again very fast as the moon moves out of the way.
Q: What are the best options for viewing the eclipse safely and to greatest effect?
A: No matter where you are during the eclipse, make sure you have solar glasses. These glasses should be ISO-approved for solar viewing. Do not use glasses with scratches, holes, or other damage.
If you are unable to obtain solar glasses in time, you can safely view the eclipse using a home-made projection method , such as a pinhole camera or even projecting the image of the sun through a colander.
The best view of the eclipse will be from within the path of totality, but even if you are not within it, you should still go outside to experience the partial eclipse. Use the NASA Eclipse Explorer to find the start, maximum, and end times, and then find a nice spot outside — preferably with some shade — put on your glasses, and enjoy the show.
For a closer view of the sun, find a friend that has a telescope with the correct ISO-certified solar filter. This will let you see the photosphere (or chromosphere if it is an H-alpha scope) in a lot more detail. If you do not have access to a telescope, NASA plans to livestream a telescope view throughout the eclipse. [The livestream will be displayed publicly on a large screen in Building 55 at MIT, rain or shine.]
The only time you can look at or image the sun without a filter is during 100 percent totality. As soon as this period is done, glasses and filters must be put back on.
After the eclipse, keep your glasses and filters. You can use them to look at the sun on any day (it took me an embarrassing amount of time to realize that I could use the glasses at any time instead of lugging out a telescope). On a really clear day, you can sometimes see sunspots!
Q: How does eclipse photography work?
A: This year I plan to photograph the eclipse in two ways. The first is using a hydrogen-alpha telescope. This telescope filters out all light except for one wavelength that is given off by hydrogen. Because it blocks out most of the light from the sun’s surface, it allows you to see the turbulent upper atmosphere of the sun, including solar prominences that follow magnetic field lines.
Because this telescope does not allow for imaging during totality as too much light is blocked, I also plan to set up a regular camera with a wide-angle lens to capture the total eclipse with the surrounding environment as context. During the 2017 eclipse, I only captured close-ups of the sun using a regular solar filter and missed the opportunity to capture what was going on around me.
Will it work? That depends on if we get clear skies, and how many pictures of my 1.5-year-old need to be taken (as well as how much chasing needs to be done).
If you would like to take pictures of the eclipse, make sure you protect your camera sensor. The sun can easily damage lenses, sensors, and other components. Here are some examples of solar damaged cameras . The solution is simple, though. If using a camera phone, you can take pictures through an extra pair of solar glasses, or even tape them to the phone. For cameras with larger lenses, you can buy cardboard filters that slide over the front of your camera or even buy ISO-approved solar film and make your own.
Q: Any fun, unique, cool, or interesting science facts about this eclipse to share?
A: If you want to get even more involved with the eclipse, there are many citizen science projects that plan to collect as much data as possible throughout the eclipse.
NASA is planning to run several experiments during the eclipse , and researchers with MIT Haystack Observatory will also be using four different technologies to monitor changes in the upper atmosphere , both locally and across the continent.
If you are interested in learning more about the eclipse, here are two of my favorite videos, one on “ unexpected science from a 0.000001 megapixel home-made telescope ” and one on solar eclipse preparation .
Share this news article on:
Related links.
- Brian Mernoff
- AeroAstro Communication Lab
- Department of Aeronautics and Astronautics
Related Topics
- Space, astronomy and planetary science
- Aeronautical and astronautical engineering
- Earth and atmospheric sciences
- Photography
- Cambridge, Boston and region
- Science communications
Related Articles

MIT Haystack scientists prepare a constellation of instruments to observe the solar eclipse’s effects
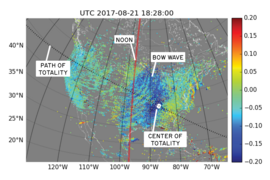
Solar eclipse caused bow waves in Earth's atmosphere
Q&A: Richard Binzel on tips for observing the 2017 solar eclipse
Previous item Next item
More MIT News

For Julie Greenberg, a career of research, mentoring, and advocacy
Read full story →
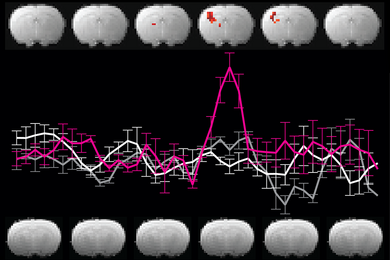
Reevaluating an approach to functional brain imaging
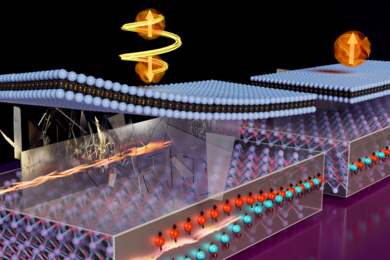
Propelling atomically layered magnets toward green computers

Researchers 3D print key components for a point-of-care mass spectrometer
Unlocking new science with devices that control electric power
- More news on MIT News homepage →
Massachusetts Institute of Technology 77 Massachusetts Avenue, Cambridge, MA, USA
- Map (opens in new window)
- Events (opens in new window)
- People (opens in new window)
- Careers (opens in new window)
- Accessibility
- Social Media Hub
- MIT on Facebook
- MIT on YouTube
- MIT on Instagram

IMAGES
VIDEO
COMMENTS
3D Presentation templates Life in 3D looks better. Make your presentations have 3D elements with these templates for Google Slides and PowerPoint. ... Download the Genetic Therapy for Down Syndrome Breakthrough presentation for PowerPoint or Google Slides.Treating diseases involves a lot of prior research and clinical trials. But whenever there ...
3d Password Ppt - Free download as Powerpoint Presentation (.ppt / .pptx), PDF File (.pdf), Text File (.txt) or view presentation slides online. 3d password
3d Password - Free download as Powerpoint Presentation (.ppt / .pptx), PDF File (.pdf), Text File (.txt) or view presentation slides online. This presentation will let you know what 3-D password is and how it actually works.
3D Password ppts - Free download as Powerpoint Presentation (.ppt / .pptx), PDF File (.pdf), Text File (.txt) or view presentation slides online. These are the complete PPTs of 3D password
Take your presentations to the next level with these 3D PowerPoint templates. Whether you're a business professional, a student, or a teacher, these templates will help you create an eye-catching presentation. With a range of customizable slides, you can easily manage your meetings and workshops, and make learning dynamic and attractive.
3D Password|3D Password Authentication|3D Password Powerpoint Presentation|ppt|Well Explain#3dpassword #codesclown #3dpasswordpowerpoint PowerPoint Presentat...
Presentation Transcript. Introduction • Commonly used authentication schemes are textual passwords, graphical passwords and biometrics. • 3D password is a multifactor authentication scheme. • To be authenticated, we require 3D virtual environment. • combines recognition, recall, token and biometrics based systems.
The password can combine most existing authentication schemes, i.e., graphical and textual passwords and various biometrics into a virtual 3D environment. The design of the 3D virtual environment and the type of objects selected determine the 3D password key space. Advantages: easy to remember and is highly secure. easy to customise. difficult ...
Multifactor authentication using 3D password has three. layers of authentication system. First is the normal. login-based layer and the second layer is Visual. authentication using QR code. Fig.7. ...
GitHub: Let's build from here · GitHub
3d Password Ppt - Free download as Powerpoint Presentation (.ppt / .pptx), PDF File (.pdf), Text File (.txt) or view presentation slides online. Scribd is the world's largest social reading and publishing site.
to 3D password scheme. They discuss on the time complexity, space complexity and the class problem related to the 3D password. [7] Sahana R. Gadagkar, Aditya Pawaskar, Mrs Ranjeeta B. Pandhare, in their paper discuss about the design of the 3D environment. They also discussed about the length of the 3D password based on the design of the system ...
Tell your story with captivating presentations. 2. Select a template with appropriate layout options. The layout plays a crucial role in determining how your content is delivered, read, and ultimately comprehended by your audience. When you assess presentation templates, ensure that the layout options align with the nature of your content.
If you're not sure how to organize your presentation handout, AI can help. You can copy and paste each slide into your favorite AI platform or give it a summary of your presentation. It's important that you give the AI tool as much context as possible about your presentation to get the best results. Once you've given the AI tool enough ...
3d-password PPT - Free download as Powerpoint Presentation (.ppt / .pptx), PDF File (.pdf) or view presentation slides online.
INTRODUCTION • Commonly used authentication schemes are textual passwords, graphical passwords and biometrics. • 3D password is a multifactor authentication scheme. • To be authenticated, were 3D virtual environment. • Combines recognition, recall, token, and biometrics-based systems. • Users choice to select the type of ...
The advantages of PowerPoint presentations in education. Students have different learning styles: some are visual learners, who retain images and videos more effectively than speech.Some take to audio and sound more easily. Others prefer to interact with their lessons—which usually refers to holding physical objects but can also be directly related to guessing answers and responding to ...
3D Password Ppt - Free download as Powerpoint Presentation (.ppt / .pptx), PDF File (.pdf), Text File (.txt) or view presentation slides online. presentation. presentation. ... Save Save 3D Password Ppt For Later. 0 ratings 0% found this document useful (0 votes) 89 views 13 pages. A Case Study On-3 Level Security Using 3D Password. Uploaded by
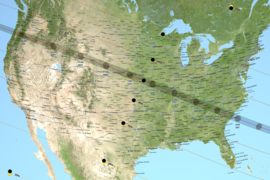
The path of totality and partial contours crossing the U.S. for the 2024 total solar eclipse occurring on April 8, 2024. On Monday, April 8, the United States will experience a total solar eclipse — a rare astronomical event where the moon passes directly between the sun and the Earth, blocking out the sun's light almost completely.
3d Password - Free download as Powerpoint Presentation (.ppt / .pptx), PDF File (.pdf), Text File (.txt) or view presentation slides online. The 3D password is a multi factor authentication scheme. The user login by navigating through a 3D environment. Collected user action and interaction in the virtual environment construct the password.