Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.

What is LAN IPv6 address for a router?
My ISP offers IPv4 address. My router DIR 615 has IPv6 options. Under IPv6 settings there’s a text box to enter LAN IPv6 address.
What exactly is meant by the term LAN IPv6 address for a router? The routers inline help page is not much useful.
Is it something similar to internal private IP that we assign to router in IPv4 like 192.168.0.1 ? Who provides it, does the user assign one or is it provided by the ISP?

- 2 Typically you don't need tp set that unless your ISP does ipv6 or tunneling, In both cases, they would tell you what setting to use I think. Most users probably don't need an internal IPv6 network as well. – Journeyman Geek ♦ May 2, 2017 at 13:03
This setting controls the IPv6 address used on the LAN side of the router. You need an assigned IPv6 address space, which use can then use to use on your local LAN. For consumer connections this would have to be provided by your ISP (since you cannot request IPv6 address space from your RIR).
This is usually called "Routed /64, /52 or /48".
You are not supposed to use RFC1918 (192.168.x.x-like) addresses with IPv6. This is exactly what IPv6 solves, that every device on the internet can have a directly addressable IP. (technically you could, but the point is that you don't have to use NAT anymore)
Technically, the auto-assigned link-local FE80 address will work just as well. If you really want to use IPv6, but your ISP does not give you IPv6 space, use the link-local address.
- Thanks for the answer mtak. Does it mean that each device that will connect to router will have its own IPv6 address assigned by the router from the IPv6 address space given by ISP? In that case will each device on LAN side be connected to externally from over IPv6 Internet without port forwarding? – rajeev May 2, 2017 at 15:37
- Yes, indeed, welcome to IPv6 :) . You will need to make sure that your firewall is configured correctly, otherwise all hosts will be accessible from the internet on all ports. – mtak May 3, 2017 at 6:16
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged router lan ipv6 ..
- The Overflow Blog
- Supporting the world’s most-used database engine through 2050
- What language should beginning programmers choose?
Hot Network Questions
- Why use a special "Name" class (instead of just a string) for representing object names in C++?
- Conditions for Binomial Distribution
- What idiom could describe bureaucratic inefficiency?
- What would you call the ground floor if you were in a country where it is the first floor?
- Adding stacked bracket annotation above nodes in tikzpicture
- How to remove tyre dust caps
- My paper has been rejected for accusations of "gift authorship", what now?
- How to Write an Involuntary Secret Reveal
- Using DeleteDuplicates with choosing which item of the pair should be deleted
- How was the miraculous complement of two Harkonnen legions for the retaking of Arrakis explained?
- What security risks do you see with wrong OTPs appearing in application logs?
- What does "as a person in Bath who drinks the water" mean?
- Poisson equation and gravitational potential
- Is the supposedly fake prophecy of Mahdi that the Bene Gesserit implanted on Arrakis actually a real prophecy?
- Why did XML lose out to XHTML, then HTML 5, on the web?
- Why did I lose a point of rating in stalemate?
- Can copy-pasting a word definition from a dictionary site cause a copyright issue?
- A simple cross-number puzzle
- Homebrew Cleric Subclass: Spirit Domain. Is this balanced?
- Correct Choice of First Vowel in Words Such as "Regret" and "Return"
- Meaning of "too silver for a seam" in "A Bird, came down the Walk"
- What is the rationale for the change of syscall calling convention in new Linuxes?
- Coding challenge for mixing a string
- How to view operator norms on open-system representation of quantum channels
IPv6 Address Assignment Example
Lesson Contents
In this lesson we’ll take a look how you can create IPv6 prefixes and subnets so that you can configure your entire network with IPv6. We’ll start at the top where IANA (Internet Assigned Numbers Authority) is responsible for the global coordination of the IPv4 and IPv6 address space and move our way all the way to the bottom where we assign subnets and IPv6 addresses to our routers, switches and VLANs.
IPv6 Global Unicast Prefix Assignments
IANA “owns” the entire IPv6 address space and they assign certain prefixes to the RIRs (Regional Internet Registry). There are 5 RIRs at the moment:
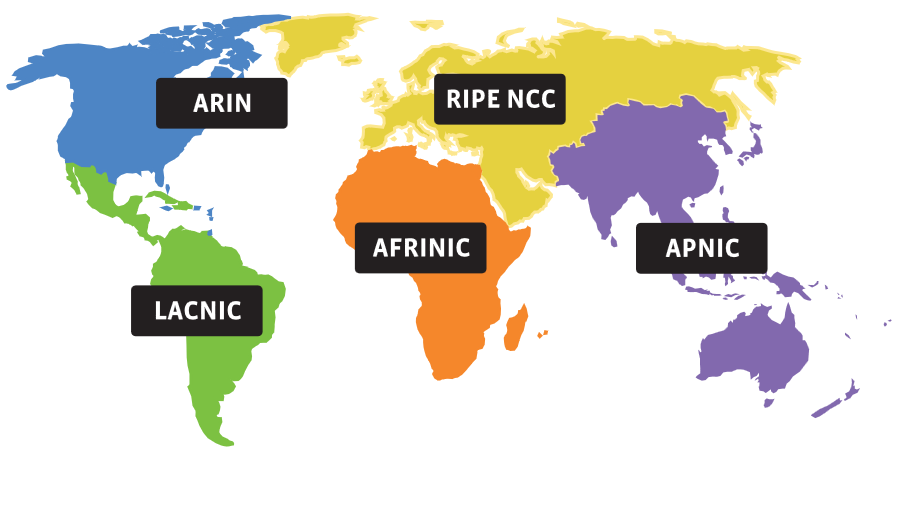
- AFRINIC : Africa
- APNIC : Asia/Pacific
- ARIN : North America
- LACNIC : Latin America and some Caribbean Islands
- RIPE NCC : Europe, Middle east and Central Asia
If you are interested, click here for an overview of all IPv6 prefix assignments by IANA.
When a large ISP (or large company) in North America wants IPv6 addresses then they will contact ARIN who will assign them an IPv6 prefix if they meet all requirements. The ISP can then assign prefixes to their customers.
Let’s take a look at some actual prefixes:
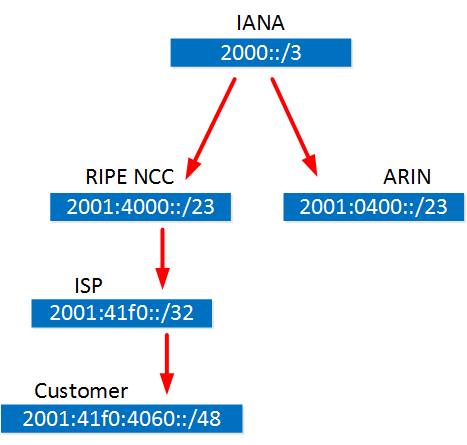
- IANA is using the 2000::/3 prefix for global unicast address space.
- According to this list, RIPE NCC received prefix 2001:4000::/23 from IANA.
- A large ISP called Ziggo in The Netherlands receives prefix 2001:41f0::/32 from RIPE NCC.
- The ISP assigns prefix 2001:41f0:4060::/48 to one of their customers.
Now it’s up to the customer what they want to do with their IPv6 prefix…
IPv6 Global Unicast Subnet Assignments
Our customer received prefix 2001:41f0:4060::/48 and they want to use it to configure IPv6 on their entire network. Where do we start? Take a look at the image below:
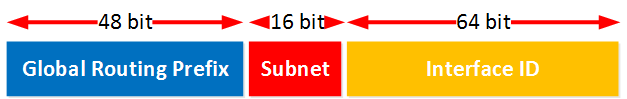
The 48-bit prefix that we received is typically called the global routing prefix or site prefix . The interface ID is normally 64 bit which means we have 16 bits left to create subnets .
If I want I can steal some more bits from the Interface ID to create even more subnets but there’s no need for this. Using 16 bits we can create 65.536 subnets …more than enough for most of us. Let’s see what we can do for our customer:
We're Sorry, Full Content Access is for Members Only...
If you like to keep on reading, Become a Member Now! Here is why:
- Learn any CCNA, CCNP and CCIE R&S Topic . Explained As Simple As Possible.
- Try for Just $1 . The Best Dollar You’ve Ever Spent on Your Cisco Career!
- Full Access to our 786 Lessons . More Lessons Added Every Week!
- Content created by Rene Molenaar (CCIE #41726)
1225 Sign Ups in the last 30 days

Forum Replies
Rene, just to be clear, they aren’t the same right? 2001:41f0:4060:10::/64 and 2001:41f0:4060:A::/64 ?
That’s right.
shouldn’t this be /64 ?
Yes that’s right, just fixed it. Thanks!
Why are these not the same
2001:41f0:4060:10::/64 and 2001:41f0:4060:A::/64 ?
45 more replies! Ask a question or join the discussion by visiting our Community Forum

- school Campus Bookshelves
- menu_book Bookshelves
- perm_media Learning Objects
- login Login
- how_to_reg Request Instructor Account
- hub Instructor Commons
- Download Page (PDF)
- Download Full Book (PDF)
- Periodic Table
- Physics Constants
- Scientific Calculator
- Reference & Cite
- Tools expand_more
- Readability
selected template will load here
This action is not available.

8.8: IPv6 Host Address Assignment
- Last updated
- Save as PDF
- Page ID 11173

- Peter Lars Dordal
- Loyola University of Chicago
IPv6 provides two competing ways for hosts to obtain their full IP addresses. One is DHCPv6 , based on IPv4’s DHCP ( 7.10 Dynamic Host Configuration Protocol (DHCP) ), in which the entire address is handed out by a DHCPv6 server. The other is StateLess Address AutoConfiguration , or SLAAC, in which the interface-identifier part of the address is generated locally, and the network prefix is obtained via prefix discovery. The original idea behind SLAAC was to support complete plug-and-play network setup: hosts on an isolated LAN could talk to one another out of the box, and if a router was introduced connecting the LAN to the Internet, then hosts would be able to determine unique, routable addresses from information available from the router.
In the early days of IPv6 development, in fact, DHCPv6 may have been intended only for address assignments to routers and servers, with SLAAC meant for “ordinary” hosts. In that era, it was still common for IPv4 addresses to be assigned “statically”, via per-host configuration files. RFC 4862 [ https://tools.ietf.org/html/rfc4862.html] states that SLAAC is to be used when “a site is not particularly concerned with the exact addresses hosts use, so long as they are unique and properly routable.”
SLAAC and DHCPv6 evolved to some degree in parallel. While SLAAC solves the autoconfiguration problem quite neatly, at this point DHCPv6 solves it just as effectively, and provides for greater administrative control. For this reason, SLAAC may end up less widely deployed. On the other hand, SLAAC gives hosts greater control over their IPv6 addresses, and so may end up offering hosts a greater degree of privacy by allowing endpoint management of the use of private and temporary addresses (below).
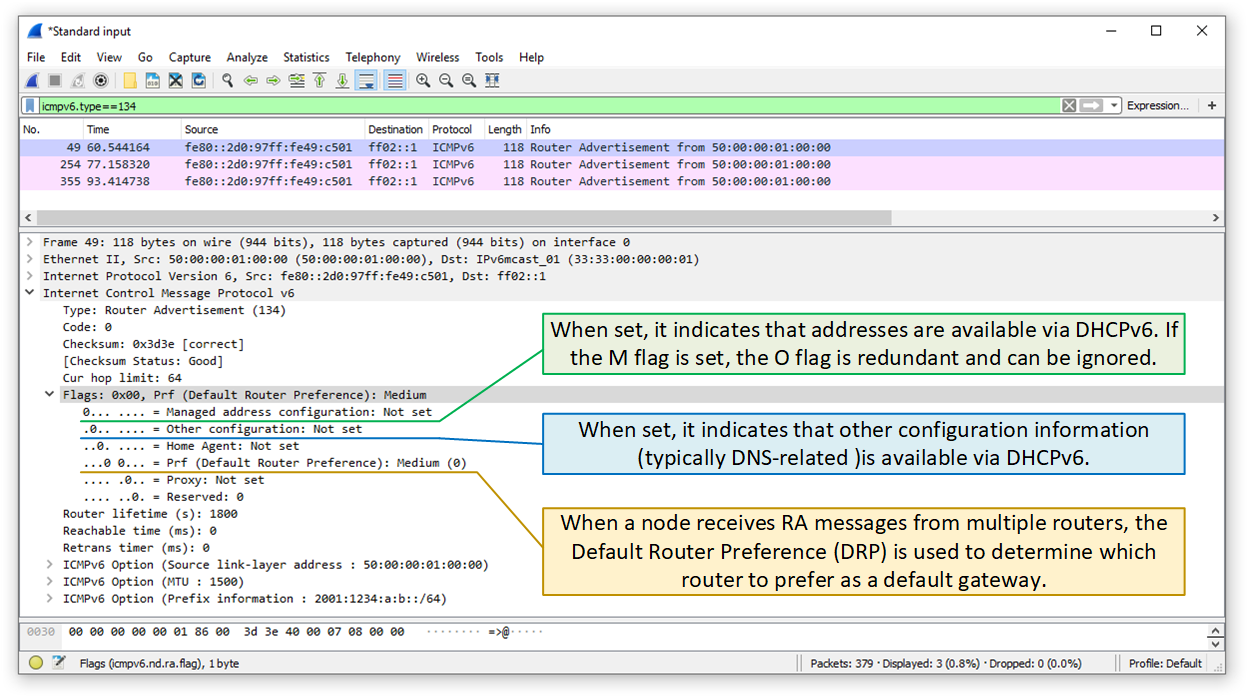
When a host first begins the Neighbor Discovery process, it receives a Router Advertisement packet. In this packet are two special bits: the M (managed) bit and the O (other configuration) bit. The M bit is set to indicate that DHCPv6 is available on the network for address assignment. The O bit is set to indicate that DHCPv6 is able to provide additional configuration information ( eg the name of the DNS server) to hosts that are using SLAAC to obtain their addresses. In addition, each individual prefix in the RA packet has an A bit, which when set indicates that the associated prefix may be used with SLAAC.
8.7.1 Duplicate Address Detection
Whenever an IPv6 host obtains a unicast address – a link-local address, an address created via SLAAC, an address received via DHCPv6 or a manually configured address – it goes through a duplicate-address detection (DAD) process. The host sends one or more Neighbor Solicitation messages (that is, like an ARP query), as in 8.6 Neighbor Discovery , asking if any other host has this address. If anyone answers, then the address is a duplicate. As with IPv4 ACD ( 7.9.1 ARP Finer Points ), but not as with the original IPv4 self-ARP, the source-IP-address field of this NS message is set to a special “unspecified” value; this allows other hosts to recognize it as a DAD query.
Because this NS process may take some time, and because addresses are in fact almost always unique, RFC 4429 [ https://tools.ietf.org/html/rfc4429.html] defines an optimistic DAD mechanism. This allows limited use of an address before the DAD process completes; in the meantime, the address is marked as “optimistic”.
Outside the optimistic-DAD interval, a host is not allowed to use an IPv6 address if the DAD process has failed. RFC 4862 [ https://tools.ietf.org/html/rfc4862.html] in fact goes further: if a host with an established address receives a DAD query for that address, indicating that some other host wants to use that address, then the original host should discontinue use of the address.
If the DAD process fails for an address based on an EUI-64 identifier, then some other node has the same Ethernet address and you have bigger problems than just finding a working IPv6 address. If the DAD process fails for an address constructed with the RFC 7217 [ https://tools.ietf.org/html/rfc7217.html] mechanism, 8.2.1 Interface identifiers , the host is able to generate a new interface identifier and try again. A counter for the number of DAD attempts is included in the hash that calculates the interface identifier; incrementing this counter results in an entirely new identifier.
While DAD works quite well on Ethernet-like networks with true LAN-layer multicast, it may be inefficient on, say, MANETs ( 3.7.8 MANETs ), as distant hosts may receive the DAD Neighbor Solicitation message only after some delay, or even not at all. Work continues on the development of improvements to DAD for such networks.
8.7.2 Stateless Autoconfiguration (SLAAC)
To obtain an address via SLAAC, defined in RFC 4862 [ https://tools.ietf.org/html/rfc4862.html] , the first step for a host is to generate its link-local address (above, 8.2.2 Link-local addresses ), appending the standard 64-bit link-local prefix fe80::/64 to its interface identifier ( 8.2.1 Interface identifiers ). The latter is likely derived from the host’s LAN address using either EUI-64 or the RFC 7217 [ https://tools.ietf.org/html/rfc7217.html] mechanism; the important point is that it is available without network involvement.
The host must then ensure that its newly configured link-local address is in fact unique; it uses DAD (above) to verify this. Assuming no duplicate is found, then at this point the host can talk to any other hosts on the same LAN, eg to figure out where the printers are.
The next step is to see if there is a router available. The host may send a Router Solicitation (RS) message to the all-routers multicast address. A router – if present – should answer with a Router Advertisement (RA) message that also contains a Prefix Information option; that is, a list of IPv6 network-address prefixes ( 8.6.2 Prefix Discovery ).
As mentioned earlier, the RA message will mark with a flag those prefixes eligible for use with SLAAC; if no prefixes are so marked, then SLAAC should not be used. All prefixes will also be marked with a lifetime, indicating how long the host may continue to use the prefix. Once the prefix expires, the host must obtain a new one via a new RA message.
The host chooses an appropriate prefix, stores the prefix-lifetime information, and appends the prefix to the front of its interface identifier to create what should now be a routable address. The address so formed must now be verified through the DAD mechanism above.
In the era of EUI-64 interface identifiers, it would in principle have been possible for the receiver of a packet to extract the sender’s LAN address from the interface-identifier portion of the sender’s SLAAC-generated IPv6 address. This in turn would allow bypassing the Neighbor Solicitation process to look up the sender’s LAN address. This was never actually permitted, however, even before the privacy options below, as there is no way to be certain that a received address was in fact generated via SLAAC. With RFC 7217 [ https://tools.ietf.org/html/rfc7217.html] -based interface identifiers, LAN-address extraction is no longer even potentially an option.
A host using SLAAC may receive multiple network prefixes, and thus generate for itself multiple addresses. RFC 6724 [ https://tools.ietf.org/html/rfc6724.html] defines a process for a host to determine, when it wishes to connect to destination address D, which of its own multiple addresses to use. For example, if D is a unique-local address, not globally visible, then the host will likely want to choose a source address that is also unique-local. RFC 6724 [ https://tools.ietf.org/html/rfc6724.html] also includes mechanisms to allow a host with a permanent public address (possibly corresponding to a DNS entry, but just as possibly formed directly from an interface identifier) to prefer alternative “temporary” or “privacy” addresses for outbound connections. Finally, RFC 6724 [ https://tools.ietf.org/html/rfc6724.html] also defines the sorting order for multiple addresses representing the same destination; see 8.11 Using IPv6 and IPv4 Together .
At the end of the SLAAC process, the host knows its IPv6 address (or set of addresses) and its default router. In IPv4, these would have been learned through DHCP along with the identity of the host’s DNS server; one concern with SLAAC is that it originally did not provide a way for a host to find its DNS server. One strategy is to fall back on DHCPv6 for this. However, RFC 6106 [ https://tools.ietf.org/html/rfc6106.html] now defines a process by which IPv6 routers can include DNS-server information in the RA packets they send to hosts as part of the SLAAC process; this completes the final step of autoconfiguration.
How to get DNS names for SLAAC-configured IPv6 hosts into the DNS servers is an entirely separate issue. One approach is simply not to give DNS names to such hosts. In the NAT-router model for IPv4 autoconfiguration, hosts on the inward side of the NAT router similarly do not have DNS names (although they are also not reachable directly, while SLAAC IPv6 hosts would be reachable). If DNS names are needed for hosts, then a site might choose DHCPv6 for address assignment instead of SLAAC. It is also possible to figure out the addresses SLAAC would use (by identifying the host-identifier bits) and then creating DNS entries for these hosts. Finally, hosts can also use Dynamic DNS ( RFC 2136 [ https://tools.ietf.org/html/rfc2136.html] ) to update their own DNS records.
8.7.2.1 SLAAC privacy
A portable host that always uses SLAAC as it moves from network to network and always bases its SLAAC addresses on the EUI-64 interface identifier (or on any other static interface identifier) will be easy to track: its interface identifier will never change. This is one reason why the obfuscation mechanism of RFC 7217 [ https://tools.ietf.org/html/rfc7217.html] interface identifiers ( 8.2.1 Interface identifiers ) includes the network prefix in the hash: connecting to a new network will then result in a new interface identifier.
Well before RFC 7217 [ https://tools.ietf.org/html/rfc7217.html] , however, RFC 4941 [ https://tools.ietf.org/html/rfc4941.html] introduced a set of privacy extensions to SLAAC: optional mechanisms for the generation of alternative interface identifiers, based as with RFC 7217 on pseudorandom generation using the original LAN-address-based interface identifier as a “seed” value.
RFC 4941 goes further, however, in that it supports regular changes to the interface identifier, to increase the difficulty of tracking a host over time even if it does not change its network prefix. One first selects a 128-bit secure-hash function F(), eg MD5 ( 22.6 Secure Hashes ). New temporary interface IDs (IIDs) can then be calculated as follows
\[(IID_{new},seed_{new}) = F(seed_{old}, IID_{old})\]
where the left-hand pair represents the two 64-bit halves of the 128-bit return value of F() and the arguments to F() are concatenated together. (The seventh bit of IID new must also be set to 0; cf 8.2.1 Interface identifiers where this bit is set to 1.) This process is privacy-safe even if the initial IID is based on EUI-64.
The probability of two hosts accidentally choosing the same interface identifier in this manner is vanishingly small; the Neighbor Solicitation mechanism with DAD must, however, still be used to verify that the address is in fact unique within the host’s LAN.
The privacy addresses above are to be used only for connections initiated by the client; to the extent that the host accepts incoming connections and so needs a “fixed” IPv6 address, the address based on the original EUI-64/RFC-7217 interface identifier should still be available. As a result, the RFC 7217 mechanism is still important for privacy even if the RFC 4941 mechanism is fully operational.
RFC 4941 stated that privacy addresses were to be disabled by default, largely because of concerns about frequently changing IP addresses. These concerns have abated with experience and so privacy addresses are often now automatically enabled. Typical address lifetimes range from a few hours to 24 hours. Once an address has “expired” it generally remains available but deprecated for a few temporary-address cycles longer.
DHCPv6 also provides an option for temporary address assignments, again to improve privacy, but one of the potential advantages of SLAAC is that this process is entirely under the control of the end system.
Regularly ( eg every few hours, or less) changing the host portion of an IPv6 address should make external tracking of a host more difficult, at least if tracking via web-browser cookies is also somehow prevented. However, for a residential “site” with only a handful of hosts, a considerable degree of tracking may be obtained simply by observing the common 64-bit prefix.
For a general discussion of privacy issues related to IPv6 addressing, see RFC 7721 [ https://tools.ietf.org/html/rfc7721.html] .
8.7.3 DHCPv6
The job of a DHCPv6 server is to tell an inquiring host its network prefix(es) and also supply a 64-bit host-identifier, very similar to an IPv4 DHCPv4 server. Hosts begin the process by sending a DHCPv6 request to the All_DHCP_Relay_Agents_and_Servers multicast IPv6 address ff02::1:2 (versus the broadcast address for IPv4). As with DHCPv4, the job of a relay agent is to tag a DHCPv6 request with the correct current subnet, and then to forward it to the actual DCHPv6 server. This allows the DHCPv6 server to be on a different subnet from the requester. Note that the use of multicast does nothing to diminish the need for relay agents. In fact, the All_DHCP_Relay_Agents_and_Servers multicast address scope is limited to the current LAN; relay agents then forward to the actual DHCPv6 server using the site -scoped address All_DHCP_Servers.
Hosts using SLAAC to obtain their address can still use a special Information-Request form of DHCPv6 to obtain their DNS server and any other “static” DHCPv6 information.
Clients may ask for temporary addresses. These are identified as such in the “Identity Association” field of the DHCPv6 request. They are handled much like “permanent” address requests, except that the client may ask for a new temporary address only a short time later. When the client does so, a different temporary address will be returned; a repeated request for a permanent address, on the other hand, would usually return the same address as before.
When the DHCPv6 server returns a temporary address, it may of course keep a log of this address. The absence of such a log is one reason SLAAC may provide a greater degree of privacy. SLAAC also places control of the cryptographic mechanisms for temporary-address creation in the hands of the end user.
A DHCPv6 response contains a list (perhaps of length 1) of IPv6 addresses. Each separate address has an expiration date. The client must send a new request before the expiration of any address it is actually using.
In DHCPv4, the host portion of addresses typically comes from “address pools” representing small ranges of integers such as 64-254; these values are generally allocated consecutively. A DHCPv6 server, on the other hand, should take advantage of the enormous range (2 64 ) of possible host portions by allocating values more sparsely, through the use of pseudorandomness. This is to make it very difficult for an outsider who knows one of a site’s host addresses to guess the addresses of other hosts, cf 8.2.1 Interface identifiers .
The Internet Draft draft-ietf-dhc-stable-privacy-addresses [tools.ietf.org/id/draft-ietf...resses-00.txt] proposes the following mechanism by which a DHCPv6 server may generate the interface-identifier bits for the addresses it hands out; F() is a secure-hash function and its arguments are concatenated together:
\[F(prefix, client_DUID, IAID, DAD_counter, secret_key)\]
The prefix, DAD_counter and secret_key arguments are as in 8.7.2.1 SLAAC privacy . The client_DUID is the string by which the client identifies itself to the DHCPv6 server; it may be based on the Ethernet address though other options are possible. The IAID, or Identity Association identifier, is a client-provided name for this request; different names are used when requesting temporary versus permanent addresses.
Some older DHCPv6 servers may still allocate interface identifiers in serial order; such obsolete servers might make the SLAAC approach more attractive.
PacketMania
Technology | Knowledge | Sharing
IPv6 Dynamic Address Allocation Mechanism Illustrated
IPv6 supports multiple addresses, making address assignments more flexible and convenient. Unlike IPv4, which relied solely on the DHCP protocol for address assignment, IPv6 incorporates a native Stateless Address AutoConfiguration SLAAC) protocol. SLAAC can either work alone to provide IPv6 addresses to hosts, or it can work with DHCPv6 to generate new assignment schemes. Here is a comprehensive analysis of the dynamic address allocation mechanism for IPv6.
Who the hell knew how much address space we needed? — Vint Cerf (American Internet pioneer and one of "the fathers of the Internet")
IPv6 Address Overview
Address formats.

The interface identifier can be generated in several ways:
- Static manual setting
- Converted from the interface's MAC address using the modified EUI-64 format
- Obtained from a DHCPv6 server
- Automatically established randomly or cryptographically
IETF recommends a canonical textual representation format for ease of writing. It includes leading zeros suppression and compression of consecutive all-zero fields. With the network prefix length at the end, the above address can be shortened to 2001:db8:130f :: 7000: 0 :140b/ 64 .
Address Types
RFC 4291 defines three types of addresses:
- Unicast: A network address corresponds to a single network node, point-to-point connection.
- Anycast: The target address corresponds to a group of receiving nodes, but only the "nearest" one receives.
- Multicast: The target address corresponds to a group of nodes that can receive replicated messages.
Note that there are no broadcast addresses in IPv6, their function being superseded by multicast addresses. Anycast addresses are syntactically indistinguishable from unicast addresses and have very limited applications. A typical application for anycast is to set up a DNS root server to allow hosts to look up domain names in close proximity. For unicast and multicast addresses, they can be identified by different network prefixes:

- All Nodes Addresses on the local link — ff02::1
- All Routers Addresses on the local link — ff02::2
- Solicited-Node Address on local link — ff02::1:ffxx:xxxx
Dynamic Allocation Schemes
Ndp protocol.
IPv6 dynamic address assignment depends on Neighbor Discovery Protocol (NDP). NDP acts at the data link layer and is responsible for discovering other nodes and corresponding IPv6 addresses on the link and determining available routes and maintaining information reachability to other active nodes. It provides the IPv6 network with the equivalent of the Address Resolution Protocol (ARP) and ICMP router discovery and redirection protocols in IPv4 networks. However, NDP adds many improvements and new features. NDP defines five ICMPv6 message types:
- Router Solicitation (RS)
- Router Advertisement (RA)
- Neighbor Solicitation (NS)
- Neighbor Advertisement (NA)
The first two message types here, RS and RA, are the keys to implementing dynamic IPv6 address assignment. The host sends an RS message to the multicast address ff02::2 of all routers in the local network segment to request routing information. When the router receives the RS from the network node, it sends an immediate RA in response. The message format of the RA is as follows
It defines two special bits, M and O, with the following meaning:
- M — "Managed address configuration" flag, set to 1 when the address is obtained from DHCPv6.
- O — "Other configuration" flag, set to 1 to indicate that other configuration information is available via DHCPv6
The RA message ends with the Options section, which originally had three possible options: Source Link-Layer Address, MTU, and Prefix Information. Later, RFC 8106 (which replaced RFC 6106) added the Recursive DNS Server (RDNSS) and DNS Search List (DNSSL) options. The Prefix Information option directly provide hosts with on-link prefixes and prefixes for Address Autoconfiguration, and it has the following format
Here the Prefix Length and the Prefix jointly determine the network prefix of the IPv6 address. In addition, the Prefix Information option also defines two special bits, L and A:
- L — on-link flag. When set, indicates that this prefix can be used for on-link determination.
- A — autonomous address-configuration flag. When set, indicates that this prefix can be used for SLAAC.
Similar to the IPv4 subnet mask feature, the purpose of the "on-link" determination is to allow the host to determine which networks an interface can access. By default, the host only considers the network where the link-local address is located as "on-link". If the "on-link" status of a destination address cannot be determined, the host forwards the IPv6 datagram to the default gateway (or default router) by default. When the host receives an RA message, if the "on-link" flag for a prefix information option is set to 1 and the Valid Lifetime is also a non-zero value, the host creates a new prefix network entry for it in the prefix list. All unexpired prefix network entries are "on-link".
Message Sequence
After understanding the NDP protocol and the information conveyed by the RA messages, let's see how they guide the network nodes to achieve dynamic address assignment.
Routers in the network periodically send RA messages to the multicast addresses (ff02::1) of all nodes in the local subnet. However, to avoid latency, the host sends one or more RS messages to all routers in the local subnet as soon as it has finished booting. The protocol requires the routers to respond to the RA messages within 0.5 seconds. Then, based on the values of the M/O/A bits in the received RA messages, the host decides how to dynamically configure the unique local and global unicast addresses of the interface and how to obtain other configuration information. With certain combinations of bit fetch values, the host needs to run DHCPv6 client software to connect to the server to obtain address assignment and/or other configuration information. The entire process is shown in the following message sequence diagram.
Note: Unlike the IPv4 DHCP protocol, DHCPv6 clients use UDP port 546 and servers use UDP port 547.
Next explain in detail three dynamic allocation schemes determined by the combination of the M/O/A-bit values:
SLAAC + Stateless DHCPv6
Stateful dhcpv6.
SLAAC is the simplest automatic IPv6 address assignment scheme and does not require any server. It works by sending an RS message request after the host starts up and the router sends back RA messages to all nodes in the local network segment. If the RA message contains the following configuration
- M-bit and O-bit all clear in the message header
- L-bit and A-bit all set in Prefix Information option
Then the host receives this RA message and performs the following operations to implement SLAAC:
- Combine the network prefix with the local interface identifier to generate a unique local address or global unicast address.
- Install the default gateway (or default route) to point to the router address (source address of the RA message).
- Set this interface as the "on-link" corresponding to the network prefix, which is also the next-hop interface of the default gateway above.
- If the RDNSS and/or DNSSL options are included, install the name servers and domain name suffixes.
This way, the host gets one or more IPv6 unique local addresses or global unicast addresses, plus the default gateway and domain name service information to complete various Internet connections.
The following is an example of the SLAAC configuration on a Cisco Catalyst 9300 Multilayer Access Switch:
The Layer 3 interface of the Cisco Multilayer Switch provides routing functionality. As you can see, when IPv6 is activated on the Layer 3 interface in VLAN 10, its default address auto-assignment scheme is SLAAC. the control bits of RA messages from this interface are all set according to the SLAAC scheme, and the network prefixes for each IPv6 address it configures are automatically added to the RA prefix information options list. Of course, the network administrator can also exclude certain network prefixes with a separate interface configuration command. The last two lines of the example configuration command specify RDNSS and DNSSL, which are also added to the RA message options.
If a host connects to a port in VLAN 10, it immediately gets a global unicast address with the network prefix of 2001:ABCD:1000::/64, and its default gateway address is set to 2001:ABCD:1000::1. Open a browser and enter a URL, and it will send a message to the specified domain name server 2001:4860:4860::8888 (Google's public name server address) to obtain the IPv6 address of the destination URL to establish a connection.
SLAAC automatic address assignment is fast and easy, providing a plug-and-play IPv6 deployment solution for small and medium-sized network deployments. However, if a network node needs access to additional configuration information, such as NTP/SNTP server, TFTP server, and SIP server addresses, or if its functionality relies on certain Vendor-specific Information Options, it must choose SLAAC + stateless DHCPv6 scheme.
This scenario still uses SLAAC automatic address assignment, but the router instructs the host to connect to a DHCPv6 server for additional configuration information. At this point, the RA message sent back by the router has
- M-bit clear and O-bit set in the message header
After receiving this RA message, the host performs the following actions:
- Install a default gateway (or default route) pointing to the router address (source address of the RA message).
- Start the DHCPv6 client and connect to the DHCPv6 server to request additional configuration information .
- Save the additional configuration information replied by the DHCPv6 server .
As you can see, SLAAC + stateless DHCPv6 is not different from SLAAC in terms of address assignment. DHCPv6 only provides additional configuration information and does not assign IPv6 addresses. So the DHCPv6 server does not track the address assignment status of network nodes, which is what "stateless" means.
The corresponding configuration commands on the Catalyst 9300 switch are as follows.
The difference with the SLAAC example is that the VLAN 10 interface configuration command ipv6 nd other-config-flag explicitly specifies to set the O-bit of the RA message. Its next command, ipv6 dhcp server vlan-10-clients , activates the DHCPv6 server response feature of the interface, corresponding to the server's pool name of vlan-10-clients . The DHCPv6 server is configured above the interface configuration, starting at ipv6 dhcp pool vlan-10-clients , and contains the DNS server address, DNS domain name, and SNTP server address.
If you are using a separate DHCPv6 server located on a network segment, you can remove the ipv6 dhcp server command and enable the ipv6 dhcp relay destination command on the next line of the example to specify the address to forward DHCPv6 requests to the external server.
Many large enterprises use DHCP to manage the IPv4 addresses of their devices, so deploying DHCPv6 to centrally assign and manage IPv6 addresses is a natural preference. This is where Stateful DHCPv6 comes into play. This scenario also requires RA messages sent by the router but does not rely solely on network prefixes for automatic address assignment. The control bits of the RA messages are configured to
- M-bit set in the message header, O-bit does not matter
- L-bit and A-bit can be set or clear as desired in Prefix Information option
Upon receiving this RA message, the host performs the following actions:
- Generate a unique local address or a global unicast address if there is a Prefix Information option with the A-bit set.
- If there is a Prefix Information option with the L-bit set, set this interface to "on-link" with the corresponding network prefix.
- If the RDNSS and/or DNSSL options are included, install the name servers and domain suffixes.
- Start the DHCPv6 client and connect to the server to request addresses and other configuration information .
- Set the address assigned by the DHCPv6 server to this interface .
- Save additional configuration information from the DHCPv6 server response .
An example of the Stateful DHCPv6 configuration command on a Catalyst 9300 switch is as follows.
Compared to SLAAC + Stateless DHCPv6 , the interface configuration here removes the ipv6 nd other-config-flag and replaces it with the ipv6 nd managed-config-flag command. This corresponds to setting the M-bit of the RA message header. The DHCPv6 server configuration adds two address prefix commands to set the network prefix. Also, the ipv6 nd prefix 2001:ABCD:1:1::/64 no-advertise configured for the interface specifies that the router does not include the 2001:ABCD:1:1::/64 prefix information option into the RA. So, this example host interface will not generate SLAAC addresses, but only two addresses from DHPCv6: a unique local address with the network prefix FD09:9:5:90::/64, and a global unicast address with the network prefix 2001:9:5:90::/64. The interface identifier for each of these two addresses is also specified by DHPCv6.
How to distinguish the source of dynamically assigned addresses for host interfaces? The method is simple. One thing to remember is that DHPCv6 does not send the network prefix length to the requestor, so the network prefix length of the addresses received from DHPCv6 is 128, while the network prefix length of the addresses generated by SLAAC will not be 128. See the following example of the wired0 interface on a Linux host:
We can immediately determine that the interface is using Stateful DHCPv6 address assignment, but also generates the SLAAC address with the same network prefix 2001:20::/64 received.
- 2001:20::53c7:1364:a4d8:fd91/128 — DHCPv6 address, random interface identifer
- 2001:20::a2ec:f9ff:fe6c:d930/64 — SLAAC addeess, interface identifer is MAC in EUI-64 format
- fe80::a2ec:f9ff:fe6c:d930/64 — Link-local address, interface identifer is MAC in EUI-64 format
Note: DHPCv6 server also does not provide any IPv6 default gateway information. The host needs to be informed of the dynamic default gateway from the RA message.
Summary and Comparison
The following table shows the control bit combinations of RA messages concerning different address allocation and other configuration acquisition methods.
Summarize three dynamic allocation schemes:
Note: Since IPv6 network interfaces can have multiple addresses (a link-local address, plus one or more unique local addresses and/or global unicast addresses), it becomes important how the source address is selected when establishing an external connection. RFC 6724 gives detailed IPv6 source address selection rules. In the development of embedded systems, the control plane and the data plane connected to the same remote device are often implemented by different functional components. For example, the control plane directly calls a Linux userspace socket to establish the connection, and the IPv6 source address used for the connection is selected by the TCP/IP stack, while the data plane directly implements data encapsulation processing and transmission in kernel space. In this case, the IPv6 source address selected by the control plane has to be synchronized to the data plane in time, otherwise, the user data might not be delivered to the same destination.
Troubleshooting Guide
The common IPv6 dynamic address assignment debugging and troubleshooting commands on Cisco routers and switches are listed in the following table.
The following console NDP protocol debug log shows that the router received an RS message from host FE80::5850:6D61:1FB:EF3A and responded with an RA message to the multicast address FF02::1 of all nodes in this network:
And the next log shows an example of Stateless DHCPv6 observed after entering the debug ipv6 dhcp debug command. Host FE80::5850:6D61:1FB:EF3A sends an INFORMATION-REQUEST message to the DHCPv6 server, which selects the source address FE80::C801:B9FF:FEF0:8 and sends a response message.
The following debug log of Stateful DHCPv6 shows the complete process of two message exchanges (SOLICIT/ADVERTISE, REQUEST/REPLY) on lines 1, 15, 16, and 26.
For complex cases where it is difficult to identify whether the problem is with the host, router, or DHCPv6 server, we recommend using the free open-source network packet analysis software Wireshark to capture packets of the entire process for analysis. While analyzing packets with Wireshark, you can apply the keyword filtering function.
We can either run Wireshark directly on the host side, or we can use the Switched Port Analyzer (SPAN) provided with the switch. Running on the network side, SPAN can collectively redirect packets from a given port to the monitor port running Wireshark for capturing. Cisco Catalyst 9300 Series switches also directly integrate with Wireshark software to intercept and analyze filtered packets online, making it very easy to use.
Sample packet capture files for three allocation scheme are available here for download and study: slaac.pcap , stateless-dhcpv6.pcap , stateful-dhcpv6.pcap
IPv6 Product Certification Test
Accurate and effective testing of IPv6 products is key to ensuring high interoperability, security, and reliability of IPv6 infrastructure deployments. The IPv6 Ready logo is an IPv6 testing and certification program created by the IPv6 Forum . Its goals are to define IPv6 conformance and interoperability test specifications, provide a self-testing toolset, establish Global IPv6 Test Centers and provide product validation services, and finally, issue IPv6 Ready logo.
In May 2020, IPv6 Ready Logo Program published new version 5.0 test specifications :
- IPv6 Core Protocols Test Specification (Conformance)
- IPv6 Core Protocols Interoperability Test Specification (Interoperability)
Along with these two new test specifications, the project team also affirmed two permanent changes:
- Testing must be done in an IPv6-only environment, without any IPv4 being used for the device to function.
- The device under test must have IPv6 on and enabled on all IP interfaces by default.
Not surprisingly, the new version 5.0 core protocols test specification has a section dedicated to defining SLAAC test cases to validate this core IPv6 protocol.
IPv6 Core Protocol RFC List
In the list below, the RFCs shown in bold are directly covered by the IPv6 Ready Version 5.0 Core Protocol Test Specification:
- RFC 4191 Default Router Preferences and More-Specific Routes
- RFC 4193 Unique Local IPv6 Unicast Addresses
- RFC 4291 IP Version 6 Addressing Architecture
- RFC 4443 Internet Control Message Protocol (ICMPv6) for the Internet Protocol Version 6 (IPv6) Specification
- RFC 4861 Neighbor Discovery for IP version 6 (IPv6)
- RFC 4862 IPv6 Stateless Address Autoconfiguration
- RFC 4941 Privacy Extensions for Stateless Address Autoconfiguration in IPv6
- RFC 5095 Deprecation of Type 0 Routing Headers in IPv6
- RFC 6724 Default Address Selection for Internet Protocol Version 6 (IPv6)
- RFC 6980 Security Implications of IPv6 Fragmentation with IPv6 Neighbor Discovery
- RFC 7217 A Method for Generating Semantically Opaque Interface Identifiers with IPv6 Stateless Address Autoconfiguration (SLAAC)
- RFC 8064 Recommendation on Stable IPv6 Interface Identifiers
- RFC 8106 IPv6 Router Advertisement Options for DNS Configuration
- RFC 8200 Internet Protocol, Version 6 (IPv6) Specification
- RFC 8201 Path MTU Discovery for IP version 6
- RFC 8415 Dynamic Host Configuration Protocol for IPv6 (DHCPv6)
- Gitalk Comments
- Utterances Comments
- Disqus Comments
The Cisco Learning Network
Ipv6 – basic configuration –address assignment slaac/dhcpv6, feb 13, 2020 • knowledge, information.
This post was first publish on my website. ( http://www.allinrouting.com )
This is the second post of my series on IPv6 addressing and routing:
IPv6 – The beginning – Addressing plans and adresses configuration
IPv6 – Basic configuration –address assignment SLAAC/DHCPv6
IPv6 – Routing – OSPFv3
IPv6 – Routing – EIGRPv6
Following my previous post, we need to finish the basic configuration of our network.
Here is again our network diagram with the IPv6 addresses.
Site 1 configuration:
Here is the config for the interco between R1 and SW1.
R1(config)#int Ethernet0/2 R1(config-if)#ipv6 add 2001:db8:10:2::/124 %Ethernet0/2: Warning: 2001:DB8:10:2::/124 is a Subnet Router Anycast SW1(config-if)#ipv6 add 2001:db8:10::0/124 %Ethernet0/0: Warning: 2001:DB8:10::/124 is a Subnet Router Anycast
One thing that you have to be careful with is that if you configure 2 IPv6 addresses under an interface, the second doesn’t replace the first one like in IPv4, it add another IPv6 under the interface.
R1(config-if)#ipv6 add 2001:db8:99:1::1/124 R1(config-if)#ipv6 add 2001:db8:99:1::2/124 R1#sh ipv6 int brie Ethernet1/3 [up/up] FE80::A8BB:CCFF:FE00:331 2001:DB8:99:1::1 2001:DB8:99:1::2
Let’s move on and configure the vlan interfaces on SW1.
SW1(config)#int vlan 10 SW1(config-if)#ipv6 add 2001:db8:10:10::1/64 SW1(config-if)#int vlan 11 SW1(config-if)#ipv6 add 2001:db8:10:10::1/64 SW1(config-if)#int vlan 12 SW1(config-if)#ipv6 add 2001:db8:10:11::1/64
That was easy, interface vlan are currently down so we will now activate the host.
Vlan10 [down/down] FE80::A8BB:CCFF:FE80:600 2001:DB8:10:10::1 Vlan11 [down/down] FE80::A8BB:CCFF:FE80:600 2001:DB8:10:11::1 Vlan12 [down/down] FE80::A8BB:CCFF:FE80:600 2001:DB8:10:12::1
End host ip address assignment – SLAAC:
I’m using routers as end host.
I will configure the router’s interface in order for them to get an IPv6 address using SLAAC.
SLAAC (Stateless Address AutoConfiguration) : Clients self-address with no ready centralized tracking or management.
Here is the config used on the router interface for SLAAC.
PC12(config-if)#int Ethernet0/0 PC12(config-if)#ipv6 enable PC12(config-if)#ipv6 address autoconfig
And we get an IP address in the correct range !
I can also ping vlan 10 interface.
PC12#sh ipv6 int brie Ethernet0/0 [up/up] FE80::A8BB:CCFF:FE00:800 2001:DB8:10:10:A8BB:CCFF:FE00:800 PC12#ping ipv6 2001:DB8:10:10::1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 2001:DB8:10:10::1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/8/24 ms
End host ip address assignment – Stateful DHCPv6:
For Stateful DHCPv6 we need to configure a DHCP server on SW1. We will use it to assign address on host in vlan 11.
SW1(config)#ipv6 dhcp pool USER-VLAN11 SW1(config-dhcpv6)#address prefix 2001:db8:10:11::/64 lifetime infinite infinite SW1(config-dhcpv6)#dns-server 2001:4860:4860::8888 (That's google ipv6 public DNS)
Note that there is no option for default-router as in IPv4 DHCP.
SW1(config-dhcpv6)#? IPv6 DHCP configuration commands: address IPv6 address allocation default Set a command to its defaults dns-server DNS servers domain-name Domain name to complete unqualified host names exit Exit from DHCPv6 configuration mode import Import options information Information refresh option link-address Link-address to match nis NIS server options nisp NISP server options no Negate a command or set its defaults prefix-delegation IPv6 prefix delegation sip SIP server options sntp SNTP server options vendor-specific Configure Vendor-specific option
Now we will setup our end host to get an IP address from DHCP.
I enable IPv6 and choose the dhcp option.
PC14(config)#int eth 0/0 PC14(config-if)#ipv6 enabl PC14(config-if)#ipv6 add dhcp
But as per the log and debugs on, no address is assign:
*Jul 31 19:25:43.203: IPv6 DHCP: Sending SOLICIT to FF02::1:2 on Ethernet0/0 *Jul 31 19:25:43.203: IPv6-Fwd: Sending on Ethernet0/0 *Jul 31 19:26:15.051: IPv6-Sas: SAS on intf Ethernet0/0 picked source FE80::A8BB:CCFF:FE00:A00 for FF02::1:2 *Jul 31 19:26:15.051: IPv6 DHCP: Sending SOLICIT to FF02::1:2 on Ethernet0/0 *Jul 31 19:26:15.051: IPv6-Fwd: Sending on Ethernet0/0
The host is sending solicit message but gets nothing.
That’s because we also need to add a new command under the interface vlan 11 on SW1.
We need to specify the DHCP pool.
SW1(config)#int vlan 11 SW1(config-if)#ipv6 dhcp server USER-VLAN11
And now we get our address.
ul 31 19:31:05.363: IPv6 DHCP: Sending SOLICIT to FF02::1:2 on Ethernet0/0 *Jul 31 19:31:05.363: IPv6-Fwd: Sending on Ethernet0/0 *Jul 31 19:31:19.925: IPV6: source FE80::A8BB:CCFF:FE80:600 (Ethernet0/0) *Jul 31 19:31:19.925: dest FF02::1:FF00:A00 *Jul 31 19:31:19.925: traffic class 224, flow 0x0, len 72+14, prot 58, hops 255, forward to ulp *Jul 31 19:31:19.926: IPV6: source FE80::A8BB:CCFF:FE00:A00 (local) *Jul 31 19:31:19.926: dest FE80::A8BB:CCFF:FE80:600 (Ethernet0/0) *Jul 31 19:31:19.926: traffic class 224, flow 0x0, len 72+0, prot 58, hops 255, originating *Jul 31 19:31:19.927: IPv6-Fwd: Created tmp mtu cache entry for FE80::A8BB:CCFF:FE00:A00 FE80::A8BB:CCFF:FE80:600 00000000 *Jul 31 19:31:19.927: IPv6-Fwd: Sending on Ethernet0/0 *Jul 31 19:31:19.929: IPv6 DHCP: Received ADVERTISE from FE80::A8BB:CCFF:FE80:600 on Ethernet0/0 *Jul 31 19:31:19.929: IPv6 DHCP: Adding server FE80::A8BB:CCFF:FE80:600 *Jul 31 19:31:19.929: IPv6 DHCP: Sending REQUEST to FF02::1:2 on Ethernet0/0 *Jul 31 19:31:19.929: IPv6 DHCP: DHCPv6 address changes state from SOLICIT to REQUEST (ADDR_ADVERTISE_RECEIVED) on Ethernet0/0 *Jul 31 19:31:19.933: IPv6 DHCP: Received REPLY from FE80::A8BB:CCFF:FE80:600 on Ethernet0/0 *Jul 31 19:31:19.933: IPv6 DHCP: Processing options *Jul 31 19:31:19.933: IPv6 DHCP: Adding address 2001:DB8:10:11:3965:F165:3DDB:9226/128 to Ethernet0/0 *Jul 31 19:31:19.934: IPv6 DHCP: T1 set to expire in 43200 seconds *Jul 31 19:31:19.934: IPv6 DHCP: T2 set to expire in 69120 seconds *Jul 31 19:31:19.934: IPv6 DHCP: Configuring DNS server 2001:4860:4860::8888 *Jul 31 19:31:19.934: IPv6 DHCP: DHCPv6 address changes state from REQUEST to OPEN (ADDR_REPLY_RECEIVED) on Ethernet0/0 PC14#sh ipv6 int brie Ethernet0/0 [up/up] FE80::A8BB:CCFF:FE00:A00 2001:DB8:10:11:3965:F165:3DDB:9226
End host ip address assignment – stateless DHCPv6:
Last is stateless assignment, it’s a combination of SLAAC and statefull DHCPv6.
Address assignment comes from SLAAC and DNS and other option from DHCP.
We will use that for end host in vlan 12.
On SW1, we create a new DHCPv6 pool and we configure the interface vlan 12.
SW1(config)#ipv6 dhcp pool USER-VLAN12 SW1(config-dhcpv6)#dns-server 2001:4860:4860::8888 SW1(config-dhcpv6)#domain-name allinrouting.com SW1(config)#int vlan 12 SW1(config-if)#ipv6 dhcp server USER-VLAN12
See that no IPv6 prefix is configure in the DHCP pool.
Next we configure our end host and turn on debugging.
I get my IP address but from the debug I do not see that the DNS was received.
*Jul 31 19:51:33.823: [IPv6 Input]IPV6ADDR: intfid_algo '3' is not active on intf 3: unknown *Jul 31 19:51:33.823: [IPv6 Input]IPV6ADDR: intfid_algo '2' is active on intf 3: eui64 *Jul 31 19:51:33.823: [IPv6 Input]IPV6ADDR: Generating IntfID for 'eui64', prefix 2001:DB8:10:12::/64, address 2001:DB8:10:12:A8BB:CCFF:FE00:700: rc 0 *Jul 31 19:51:33.823: [IPv6 Input]IPV6ADDR: Preferring 2001:DB8:10:12:A8BB:CCFF:FE00:700 from Ethernet0/0 *Jul 31 19:51:33.824: [IPv6 Input]IPV6ADDR: Adding operating owner address configured on Ethernet0/0 *Jul 31 19:51:33.824: [IPv6 Input]IPV6ADDR: Notification: Address 2001:DB8:10:12:A8BB:CCFF:FE00:700 added to Ethernet0/0 *Jul 31 19:51:33.824: [IPv6 Input]IPV6ADDR: Ethernet0/0 - Join Mcast group: New refcnt for FF02::1:FF00:700 is 2 *Jul 31 19:51:34.829: [IPv6 ND]IPV6ADDR: Notification: Address 2001:DB8:10:12:A8BB:CCFF:FE00:700/64 is up on Ethernet0/0 PC11#sh ipv6 int brie Ethernet0/0 [up/up] FE80::A8BB:CCFF:FE00:700 2001:DB8:10:12:A8BB:CCFF:FE00:700
Again, another command needs to be added under the interface vlan 12 of SW1.
This is use to obtain autoconfiguration information other than addresses. If the flag is set, the attached hosts should use stateful autoconfiguration to obtain the other (nonaddress) information.
SW1(config)#int vlan 12 SW1(config-if)#ipv6 nd other-config-flag
And with this command we get DHCP option.
*Jul 31 19:56:04.091: IPv6 DHCP: Received REPLY from FE80::A8BB:CCFF:FE80:600 on Ethernet0/0 *Jul 31 19:56:04.091: IPv6 DHCP: detailed packet contents *Jul 31 19:56:04.091: src FE80::A8BB:CCFF:FE80:600 (Ethernet0/0) *Jul 31 19:56:04.091: dst FE80::A8BB:CCFF:FE00:700 (Ethernet0/0) *Jul 31 19:56:04.091: type REPLY(7), xid 16576445 *Jul 31 19:56:04.091: option SERVERID(2), len 10 *Jul 31 19:56:04.091: 00030001AABBCC000600 *Jul 31 19:56:04.091: option CLIENTID(1), len 10 *Jul 31 19:56:04.091: 00030001AABBCC000700 *Jul 31 19:56:04.091: option DNS-SERVERS(23), len 16 *Jul 31 19:56:04.091: 2001:4860:4860::8888 *Jul 31 19:56:04.091: option DOMAIN-LIST(24), len 18 *Jul 31 19:56:04.091: allinrouting.com *Jul 31 19:56:04.092: IPv6 DHCP: Adding server FE80::A8BB:CCFF:FE80:600 PC11# *Jul 31 19:56:04.092: IPv6 DHCP: Processing options *Jul 31 19:56:04.092: IPv6 DHCP: Configuring DNS server 2001:4860:4860::8888 *Jul 31 19:56:04.092: IPv6 DHCP: Configuring domain name allinrouting.com *Jul 31 19:56:04.092: IPv6 DHCP: DHCPv6 changes state from INFORMATION-REQUEST to IDLE (REPLY_RECEIVED) on Ethernet0/0
And DNS works.
PC11#sSH LOG Translating "LOG"...domain server (2001:4860:4860::8888) *Jul 31 19:58:32.941: IPv6-Sas: SAS picked source 2001:DB8:10:12:A8BB:CCFF:FE00:700 for 2001:4860:4860::8888 *Jul 31 19:58:32.941: IPv6-Fwd: No route to destination 2001:4860:4860::8888 (tableid=0)
On SW1, the DHCP pool reports 0 client. That makes sense because no IPv6 addresses are in lease.
DHCPv6 pool: USER-VLAN12 DNS server: 2001:4860:4860::8888 Domain name: allinrouting.com Active clients: 0
I will assign addresses to end host from site 2 and 3 the same way.
In the next post we will try to make all those stuff communicating together using dynamic routing protocols.
Thank you for reading.
Comments and reviews are appreciated.
Check out the other posts of this IPv6 series:
Article Details
Nothing here yet?
Log in to post to this feed.
Related Articles
- Number of Views 616
- Number of Views 915
- Number of Views 937
Trending Articles
- Cisco Packet Tracer: Software de Simulación para Redes
- 200-301 CCNA Study Materials
- Packet Tracer Labs
If you encounter a technical issue on the site, please open a support case .
Communities: Chinese | Japanese | Korean
Cisco.com © Copyright 2024 Cisco, Inc. All Rights Reserved. Privacy Statement Terms & Conditions Cookie Policy Trademarks
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.

How should I configure properly my LAN to use IPv6 for communication on LAN and WAN?
I would like to use IPv6 on my LAN and would like to be able to go out to the WAN as well. My network is a classic IPv4 environment. It works well.
My ISP provides Global Unicast IPv6 address on the WAN interface of my router ( pfsense 2.5.2 ). I can ping google's IPv6 address from my router:
Behind the router the same thing does not work . I cannot ping google's IPv6 address. I need help to configure the LAN side properly.
May I ask your assistance please ?
EDIT: I had a call with my ISP and confirmed that ping might not work from my LAN. Maybe the the contact was not the right person to answer all my question because he answered that he does not know why but ping should not work but everything else should. Weird.
- local-area-network
- wide-area-network
- 1 Did you forget to enable prefix delegation? I think pfSense has it off by default. – Michael Hampton Sep 2, 2021 at 12:58
- I forgot really. It is now enabled. Thx. Problem is not solved yet though. I am still working on it. – supi007 Sep 2, 2021 at 15:01
2 Answers 2
Finally I have found the answer. Let's see what I have:
- pfSense is being used as a router/firewall on my LAN.
- I got Global Unicast IPv6 address from my ISP on my WAN interface. (GUIPv6 is routable on Internet.)
- pfSense need to be configured properly to get Global Unicast IPv6 address from the ISP on the LAN interface.
- Interfaces --> WAN --> DHCP6 Client Configuration --> DHCPv6 Prefix Delegation size="60" --> Save
- Interfaces --> LAN --> General Configuration --> IPv6 Configuration Type="Track Interface"
- Interfaces --> LAN --> Track IPv6 Interface --> IPv6 Interface="WAN"
- Interfaces --> LAN --> Track IPv6 Interface --> IPv6 Prefix ID="0" --> Save
- Services --> DHCPv6 Server & RA --> Router Advertisements --> Router mode="Managed" --> Save
- Services --> DHCPv6 Server & RA --> DHCPv6 Server --> "Enable DHCPv6 server on interface LAN"
- Range from="::1000"
- Range to="::2000" -- > Save
Abovementioned steps set up pfSense to be able to dynamically assigns GUIPv6 addresses on LAN.
Well, you need to have routable network from your provider for that. If there is no routable network, what router should route then?
- What do you mean "routable network" ? My ISP routes the IPv6 traffic. At least I think they do because ping works between my pfsense's interface and google's interface. – supi007 Sep 2, 2021 at 7:19
- routable network is an opposite of 'directly connected'. You provider must have something like 2a00:1450:4006:80d::0/64 via 2a00:1450:4006:80e::feab dev te10/11/12 in their routing table. (where 2a00:1450:4006:80e::feab is your router IP, and 2a00:1450:4006:80d::0/64 is your routable IPv6 network). If you have IP addresses allocated to you with provider IP (gateway) been in the same network, than you can't route it. – George Shuklin Sep 2, 2021 at 7:26
- Fine. You say I need to add a Unique Local IPv6 address to my LAN interface and need to add a record to the route table that points to the Global Unicast address? Is it working like IPv4 routing ? – supi007 Sep 2, 2021 at 7:40
- I have found an article about the IPv6 NAT: docs.netgate.com/pfsense/en/latest/nat/npt.html Is this the right way to solve my issue ? Could anybody confirm that ? – supi007 Sep 2, 2021 at 8:43
- 1 Forget NAT with IPv6. Ask your provider for a suitably sized network, and bear in mind that the smallest subnet you should ever deploy outside a PtP-link is a /64. My home ISP hands me a /48. – vidarlo Sep 2, 2021 at 12:45
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged networking ipv6 local-area-network wide-area-network unicast ..
- The Overflow Blog
- Supporting the world’s most-used database engine through 2050
- What language should beginning programmers choose?
Hot Network Questions
- How to force generation of Image thumbnails?
- Homebrew Cleric Subclass: Spirit Domain. Is this balanced?
- Please help check why my opamp calculation has a different answer from my lecturer's
- Why use a special "Name" class (instead of just a string) for representing object names in C++?
- How to solve this kernel-panic on a Debian 12 system?
- Correct Choice of First Vowel in Words Such as "Regret" and "Return"
- No output from PCM5102 I2S DAC
- Is there such a thing as a "physical" fractal?
- Homemade salad dressing with raw garlic not safe?
- 2,6,?,30,-270 number sequence
- How was the miraculous complement of two Harkonnen legions for the retaking of Arrakis explained?
- Can copy-pasting a word definition from a dictionary site cause a copyright issue?
- Enumerate all matches of a regex
- What idiom could describe bureaucratic inefficiency?
- Adding stacked bracket annotation above nodes in tikzpicture
- Cannot upgrade from Ubuntu 23.10 or 22.04 to Ubuntu 24.04
- Why is the metallicity of dwarf galaxies low?
- Old metal window stuck open and metal strap/band fell out; what to do?
- Is it an independent and additional offence to have a fake passenger (e.g., a mannequin) to try to avoid HOV violation detection?
- "on a farm" vs "on the farm"
- How do normal species and a religious-fanatic species tolerate each other?
- How does one research mathematics in a more inclusive manner?
- How are Gimli's athletic abilities in the books?
- What is the rationale for the change of syscall calling convention in new Linuxes?
Each IPv6 node on the network needs a globally unique address to communicate outside its local segment. But where a node get such an address from? There are a few options:
- Manual assignment - Every node can be configured with an IPv6 address manually by an administrator. It is not a scalable approach and is prone to human error.
- DHCPv6 (The Dynamic Host Configuration Protocol version 6) - The most widely adopted protocol for dynamically assigning addresses to hosts. Requires a DHCP server on the network and additional configuration.
- SLAAC (Stateless Address Autoconfiguration) - It was designed to be a simpler and more straight-forward approach to IPv6 auto-addressing. In its current implementation as defined in RFC 4862 , SLAAC does not provide DNS server addresses to hosts and that is why it is not widely adopted at the moment.
In this lesson, we are going to learn how SLAAC works and what are the pros and cons of using it in comparison to DHCPv6.
What is SLAAC?
SLAAC stands for Stateless Address Autoconfiguration and the name pretty much explains what it does. It is a mechanism that enables each host on the network to auto-configure a unique IPv6 address without any device keeping track of which address is assigned to which node.
Stateless and Stateful in the context of address assignment mean the following:
- A stateful address assignment involves a server or other device that keeps track of the state of each assignment. It tracks the address pool availability and resolves duplicated address conflicts. It also logs every assignment and keeps track of the expiration times.
- Stateless address assignment means that no server keeps track of what addresses have been assigned and what addresses are still available for an assignment. Also in the stateless assignment scenario, nodes are responsible to resolve any duplicated address conflicts following the logic: Generate an IPv6 address, run the Duplicate Address Detection (DAD), if the address happens to be in use, generate another one and run DAD again, etc.
How does SLAAC work?
To fully understand how the IPv6 auto-addressing work, let's follow the steps an IPv6 node takes from the moment it gets connect to the network to the moment it has a unique global unicast address.
Step 1: The node configures itself with a link-local address
When an IPv6 node is connected to an IPv6 enabled network, the first thing it typically does is to auto-configure itself with a link-local address. The purpose of this local address is to enable the node to communicate at Layer 3 with other IPv6 devices in the local segment. The most widely adopted way of auto-configuring a link-local address is by combining the link-local prefix FE80::/64 and the EUI-64 interface identifier, generated from the interface's MAC address.
Figure 1 shows a step by step example of how a local address is generated from MAC address 7007.1234.5678.
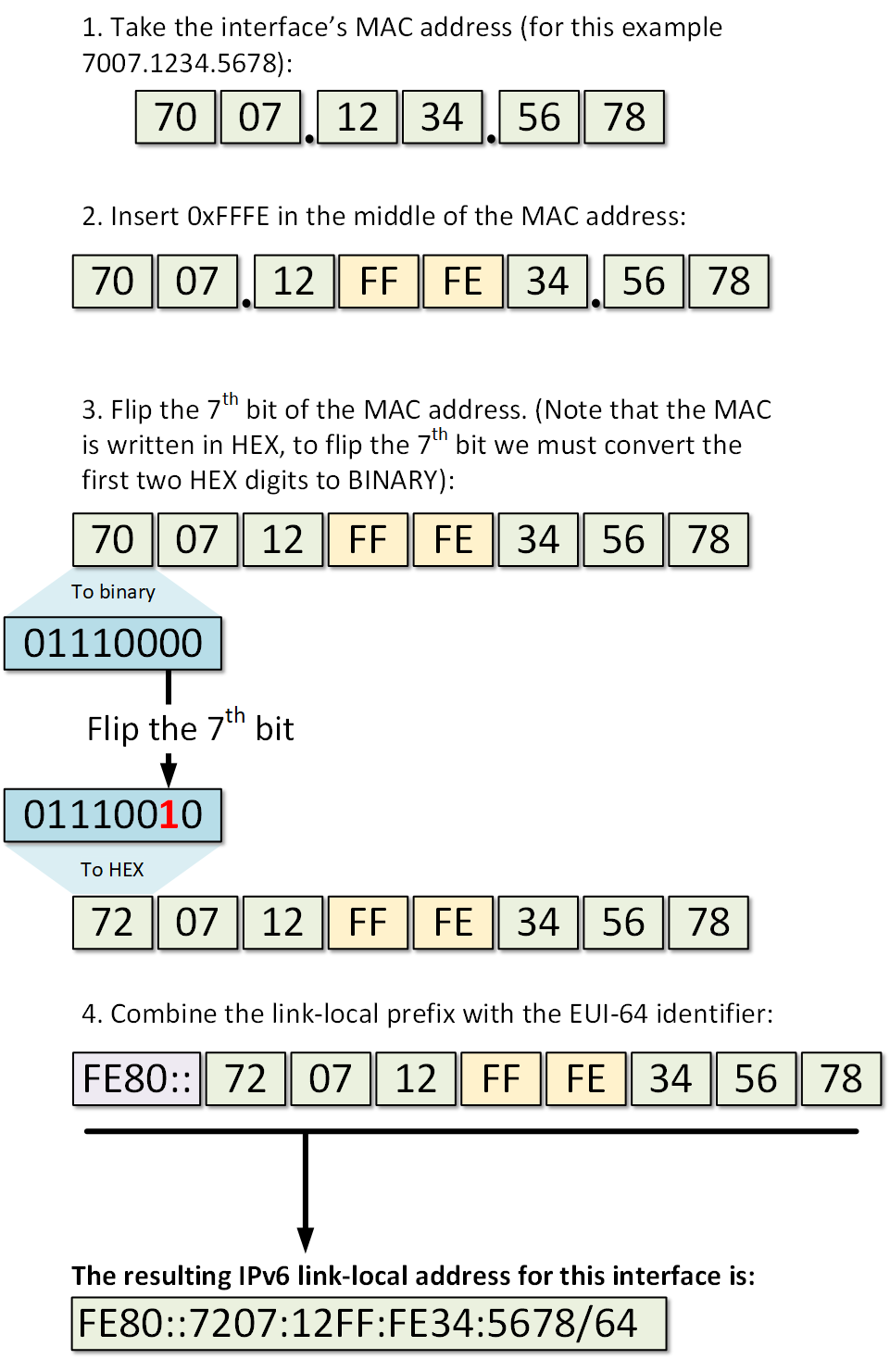
Once the above steps are completed, the node has a fully functional EUI-64 format link-local address as shown below:
Step 2: The node performs Duplicate Address Detection (DAD)
After the IPv6 host has its link-local address auto-configured, it has to make sure that the address is actually unique in the local segment. Even though the chances that another node has the same exact address are very slim. It has to perform a process called Duplicate Address Detection (DAD).
DAD is a mechanism that involves a special type of address called solicited-node multicast . Upon configuring an IPv6 address, every node joins a multicast group identified by the address FF02::1:FFxx:xxxx where xx:xxxx are the last 6 hexadecimal values in the IPv6 unicast address. Therefore, for each configured unicast address, no matter if it is link-local or global, the host joins the respective auto-generated solicited-node multicast group.
In our example, the last 6 hexadecimal values of the link-local address are 34:5678 so the node joins the multicast group FF02::1:FF 34:5678 . As PC1 is running a Windows 10 operating system, we can verify that with the following command:
Having this logic in mind, we know that if another host has the same exact link-local address, it will also be listening for messages on the solicited-node multicast group auto-generated from this address - FF02::1:FF34:5678. In order for PC1 to check that, it sends an ICMPv6 message with a destination address set to this group, and the source address set to the IPv6 unspecified address. In the ICMPv6 portion of the packet, PC1 puts the whole address in the Target Address field. Figure 2 illustrates that process. PC1 then sends the packet on the network. Only nodes that are listening to this exact auto-generated multicast group will open the packet, all other nodes will discard it. If any node has an IPv6 address that has the same last 6 hex digits, will look in the ICMPv6 portion and check if the target address matches any of its own addresses. If there is a match, the host will reply back that this IPv6 address is already in use. If nobody replies back, PC1 will conclude that this address is unique and available to be used, and will assign it.
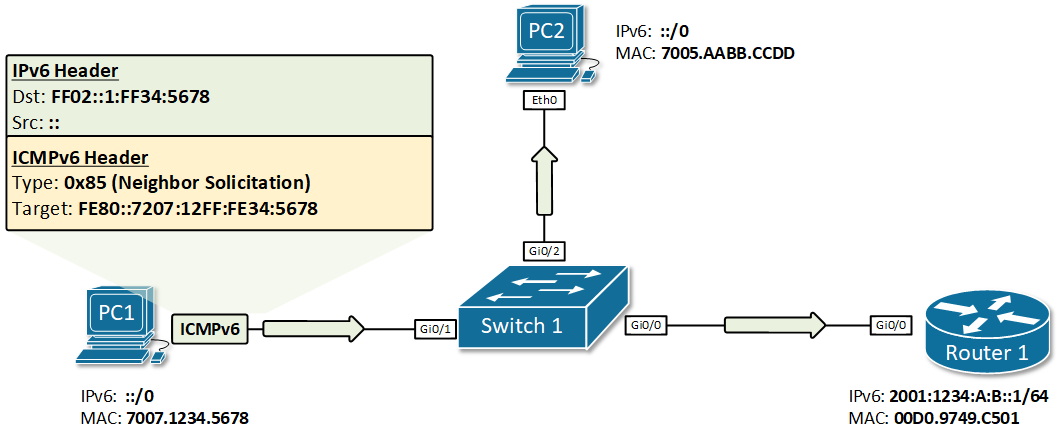
This process is called Duplicate Address Detection (DAD) and is done upon every new address assignment. In our example, PC1 sends the ICMPv6 Neighbor Solicitation message as shown in figure 2, and nobody replies back. PC1 will then know for sure that this link-local address is unique in this local segment.
Step 3: The node sends a Router Solicitation message
Step 1 and 2 in this example depict the process of generating and assigning a unique link-local address. This process is not exactly part of the Stateless Autoconfiguration feature but without a link-local address, PC1 won't be able to communicate at layer 3 with any other IPv6 node. Thus, it is a pre-requisite for the SLAAC to work and that's why we have included it in our example.
After PC1 has a link-local address, it can now start the process of auto-configuring a global unicast address using SLAAC. The first step of this process is to send an ICMPv6 message called Router Solicitation (RS) . The purpose of this message is to ' ask ' all IPv6 routers attached to this segment about the global unicast prefix that is used. The destination address is the all-routers multicast address FF02::2 and for source, PC1 uses its link-local address. Note that only routers are subscribed to multicast group FF02::2, which means that only Router 1 will process this message, and all other nodes on the local segment will discard it.
After Router 1 gets the Router Solicitation message, it responds back with an ICMPv6 message called Router Advertisement (RA). The RA message includes the global IPv6 prefix on the link and the prefix length. In our example, these would be the prefix 2001:1234:A:b:: and the prefix length of /64. For the source of this RA packet, Router 1 uses its own link-local address and destination is the all-nodes multicast address FF02::1. The process is illustrated in figure 3.
Step 4: The node configures its global unicast address
Once PC1 gets back the Router Advertisement from Router 1, it combines the prefix 2001:1234:A:B::/64 with its EUI-64 interface identifier (7207:12FF:FE34:5678) resulting in the global unicast address 2001:1234:A:B:7207:12FF:FE34:5678/64. Because the Router Advertisement came from Router 1, PC1 sets its IPv6 default gateway to the link-local address of R1.
Now PC1 has a global unicast address and a default gateway. But the SLAAC process is not completed. PC1 must know for sure this auto-generated address is unique in the local segment. Thus, PC1 performs the Duplicate Address Detection (DAD) process.
Step 5: The node performs Duplicate Address Detection (DAD)
We have already explained the DAD process in detail in step 2. When PC1 auto-generate its global unicast address, it immediately joins the auto-generated solicited-node multicast group FF02::1:FF34:5678. To be sure that nobody else is using this address, PC1 then sends an ICMPv6 message called Neighbor Solicitation to the solicited-node address FF02::1:FF34:5678 and waits to see if a node replies back. If no reply is received back, PC1 knows that this address is unique and can start using it for communication outside its local segment including on the Internet.
The problem with SLAAC
So far so good. We have seen how a node can auto-configure a globally unique IPv6 address and a default gateway.
However, SLAAC does not provide DNS information and without DNS, many services such as surfing the Internet are not possible.
There is a field in the Router Advertisement header, that is designed to solve this problem.
Router Advertisement Flags
As we said above, by default, SLAAC does not provide DNS. And without DNS, many services that require resolution from URL addresses to IP won't work. There is a field in the RA message that helps nodes understand where to get an IPv6 address and DNS information from.
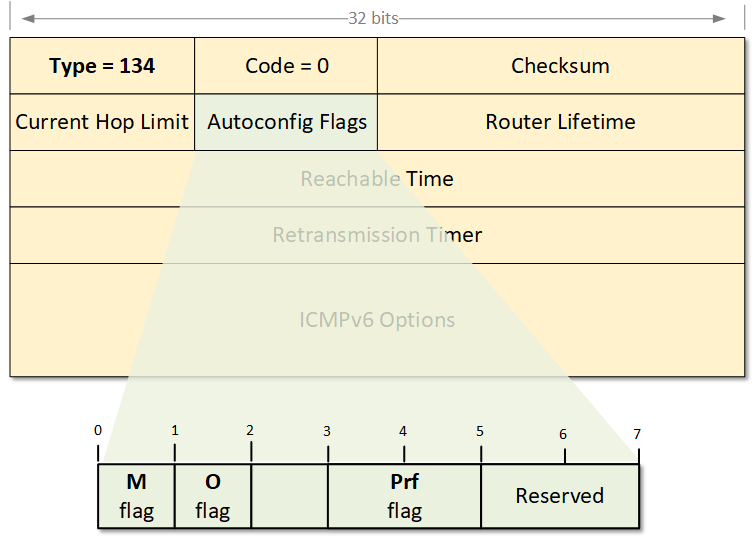
If the M-flag is set to 1, it indicates that addresses are available via DHCPv6. The router is basically telling the nodes to ask the DHCP server for addresses and DNS information. If the M flag is set, the O flag can be ignored because DHCPv6 will return all available information.
If the O-flag is set to 1, it indicates that DNS information is available via DHCPv6. The router is basically telling the nodes to auto-configure an address via SLAAC and ask the DHCP server for DNS information.
If neither M nor O flags are set, this indicates that no DHCPv6 server is available on the segment.
The Prf-flag (Default Router Preference) can be set to Low (1), Medium (0), or High(3). When a node receives Router Advertisement messages from multiple routers, the Default Router Preference (DRP) is used to determine which router to prefer as a default gateway.
Configuring SLAAC on Cisco routers
Typically, when IPv6 unicast-routing is enabled on a Cisco router, it starts to send RA messages via all interfaces that have a configured IPv6 global unicast address.
In our example, when interface GigabitEthernet 0/0 is configured with a global IPv6 unicast address, it immediately starts sending RA messages on the local segment.
Most parameters can be verified using the show ipv6 interface command
If there is a DHCPv6 server available on the segment, we can set the M-flag or the O-flag in the RA messages using the following options.
If you'd like to disable the SLAAC feature on this interface, you can use the suppress command under the interface ipv6 options
IPv6 Global Unicast Address Assignments
If the switch does not have the IPv6 address of a wireless client, the switch will not respond with NA and forward the NS packet to the wireless side. To resolve this, an NS Multicast Forwarding knob is provided. If this knob is enabled, the switch gets the NS packet for the IPv6 address that it does not have (cache miss) and forwards it to the wireless side. This packet reaches the intended wireless client and the client replies with NA.
This cache miss scenario occurs rarely, and only very few clients which do not implement complete IPv6 stack may not advertise their IPv6 address during NDP.
IPv6 clients configure IPv6 addresses and populate their router tables based on IPv6 router advertisement (RA) packets. The RA guard feature is similar to the RA guard feature of wired networks. RA guard increases the security of the IPv6 network by dropping the unwanted or rogue RA packets that come from wireless clients. If this feature is not configured, malicious IPv6 wireless clients announce themselves as the router for the network often with high priority, which would take higher precedence over legitimate IPv6 routers.
- Port on which the frame is received
- IPv6 source address
- Prefix list
The following configuration information created on the switch is available to RA-Guard to validate against the information found in the received RA frame:
- Trusted/Untrusted ports for receiving RA-guard messages
- Trusted/Untrusted IPv6 source addresses of RA-sender
- Trusted/Untrusted Prefix list and Prefix ranges
- Router Preference
RA guard occurs at the switch . You can configure the switch to drop RA messages at the switch . All IPv6 RA messages are dropped, which protects other wireless clients and upstream wired network from malicious IPv6 clients.
RA Throttling
RA throttling allows the controller to enforce limits to RA packets headed toward the wireless network. By enabling RA throttling, routers that send many RA packets can be trimmed to a minimum frequency that will still maintain an IPv6 client connectivity. If a client sends an RS packet, an RA is sent back to the client. This RA is allowed through the controller and unicasted to the client. This process ensures that the new clients or roaming clients are not affected by the RA throttling.
Configuring IPv6 Unicast (CLI)
IPv6 unicasting must always be enabled on the switch and the controller. IPv6 unicast routing is disabled.
To enable the forwarding of IPv6 unicast datagrams, use the ipv6 unicast-routing command in global configuration mode. To disable the forwarding of IPv6 unicast datagrams, use the no form of this command.
1. configure terminal
2. ipv6 unicast routing
Configuring RA Guard Policy (CLI)
Configure RA Guard policy on the switch to add IPv6 client addresses and populate the router table based on IPv6 router advertisement packets.
2. ipv6 nd raguard policy raguard-router
3. trustedport
4. device-role router
5. exit
Applying RA Guard Policy (CLI)
Applying the RA Guard policy on the switch will block all the untrusted RA's.
2. interface tengigabitethernet 1/0/1
3. ipv6 nd raguard attach-policy raguard-router
4. exit
Configuring RA Throttle Policy (CLI)
Configure RA Throttle policy to allow the enforce the limits
2. ipv6 nd ra-throttler policy ra-throttler1
3. throttleperiod 500
4. max-through 10
5. allow-atleast 5 at-most 10
Applying RA Throttle Policy on VLAN (CLI)
Applying the RA Throttle policy on a VLAN. By enabling RA throttling, routers that send many RA packets can be trimmed to a minimum frequency that will still maintain an IPv6 client connectivity.
2. vlan configuration 1
3. ipv6 nd ra throttler attach-policy ra-throttler1
Configuring IPv6 Snooping (CLI)
IPv6 snooping must always be enabled on the switch and the controller.
Enable IPv6 on the client machine.
1. vlan configuration 1
2. ipv6 snooping
3. ipv6 nd suppress
Configuring IPv6 ND Suppress Policy (CLI)
The IPv6 neighbor discovery (ND) multicast suppress feature stops as many ND multicast neighbor solicit (NS) messages as possible by dropping them (and responding to solicitations on behalf of the targets) or converting them into unicast traffic. This feature runs on a layer 2 switch or a wireless controller and is used to reduce the amount of control traffic necessary for proper link operations.
When an address is inserted into the binding table, an address resolution request sent to a multicast address is intercepted, and the device either responds on behalf of the address owner or, at layer 2, converts the request into a unicast message and forwards it to its destination.
1. enable
2. configure terminal
3. ipv6 nd suppress policy
Configuring IPv6 Snooping on VLAN/PortChannel
Neighbor Discover (ND) suppress can be enabled or disabled on either the VLAN or a switchport.
1. vlan config901
2. ipv6 nd suppress
3. end
4. interface gi1/0/1
5. ipv6 nd suppress
6. end
Configuring IPv6 on Switch (CLI)
Use this configuration example to configure IPv6 on an interface.
Enable IPv6 on the client and IPv6 support on the wired infrastructure.
1. interface vlan 1
2. ip address fe80::1 link-local
3. ipv6 enable
4. end
Configuring DHCP Pool (CLI)
1. ipv6 dhcp pool Vlan21
2. address prefix 2001:DB8:0:1:FFFF:1234::/64 lifetime 300 10
3. dns-server 2001:100:0:1::1
4. domain-name example.com
5. end
Configuring Stateless Auto Address Configuration Without DHCP (CLI)
4. no ipv6 nd managed-config-flag
5. no ipv6 nd other-config-flag
Configuring Stateless Auto Address Configuration With DHCP (CLI)
5. ipv6 nd other-config-flag
Configuring Stateful DHCP Locally (CLI)
This interface configuration is for a Cisco IOS IPv6 router implementing stateful DHCPv6 on a local Switch
2. ipv6 unicast-routing
3. ipv6 dhcp pool IPv6_DHCPPOOL
4. address prefix 2001:DB8:0:1:FFFF:1234::/64
5. dns-server 2001:100:0:1::1
6. domain-name example.com
7. exit
8. interface vlan1
9. description IPv6-DHCP-Stateful
10. ipv6 address 2001:DB8:0:20::1/64
11. ip address 192.168.20.1 255.255.255.0
12. ipv6 nd prefix 2001:db8::/64 no-advertise
13. ipv6 nd managed-config-flag
14. ipv6 nd other-config-flag
15. ipv6 dhcp server IPv6_DHCPPOOL
Configuring Stateful DHCP Externally (CLI)
This interface configuration is for a Cisco IOS IPv6 router implementing stateful DHCPv6 on an external DHCP server.
6. interface vlan1
7. description IPv6-DHCP-Stateful
8. ipv6 address 2001:DB8:0:20::1/64
9. ip address 192.168.20.1 255.255.255.0
10. ipv6 nd prefix 2001:db8::/64 no-advertise
11. ipv6 nd managed-config-flag
12. ipv6 nd other-config-flag
13. ipv6 dhcp_relay destination 2001:DB8:0:20::2
Monitoring IPv6 Clients (GUI)
To view the IPv6 clients associated with the Switch
Verifying IPv6 Address Learning Configuration
This example displays the output of the show ipv6 dhcp pool command. This command displays the IPv6 service configuration on the switch . The vlan 21 configured pool detail displays 6 clients that are currently using addresses from the pool.
1. show ipv6 dhcp pool
Additional References
Related documents, error message decoder, technical assistance, feature information for ipv6 client address learning.

IMAGES
VIDEO
COMMENTS
1. This setting controls the IPv6 address used on the LAN side of the router. You need an assigned IPv6 address space, which use can then use to use on your local LAN. For consumer connections this would have to be provided by your ISP (since you cannot request IPv6 address space from your RIR). This is usually called "Routed /64, /52 or /48".
IPv6 Global Unicast Prefix Assignments. IANA "owns" the entire IPv6 address space and they assign certain prefixes to the RIRs (Regional Internet Registry). There are 5 RIRs at the moment: AFRINIC: Africa. APNIC: Asia/Pacific. ARIN: North America. LACNIC: Latin America and some Caribbean Islands.
An IPv6 address prefix, in the format ipv6-prefix / prefix-length, can be used to represent bit-wise contiguous blocks of the entire address space.The ipv6-prefix must be in the form documented in RFC 2373 where the address is specified in hexadecimal using 16-bit values between colons. The prefix length is a decimal value that indicates how many of the high-order contiguous bits of the ...
Key IPv6 addressing concepts. IPv6 addressing within a network has a few major differences from IPv4. With IPv4 certain address ranges are reserved for private networks (such as 10.0.0.0/8 or 192 ...
Devices request and receive specific IPv6 addresses from a DHCPv6 server, which maintains a record of assigned addresses and manages the overall address space. Pros: Centralized Control: Stateful DHCPv6 offers network administrators greater control over address assignments, ensuring a more structured and organized network.
The IPv6 prefix is part of the address that represents the left-most bits that have a fixed value and represent the network identifier. The IPv6 prefix is represented using the IPv6-prefix or prefix-length format just like an IPv4 address is represented in the classless interdomain routing (CIDR) notation.
This guide addresses: • How to successfully integrate IPv6 into a network that already has an existing IPv4 address space assigned • How to handle multiple IP address ranges in the network • When you should use a provider-independent IP space • How to set up the IPv6 subnets Who Should Read This Guide
8.7.1 Duplicate Address Detection. Whenever an IPv6 host obtains a unicast address - a link-local address, an address created via SLAAC, an address received via DHCPv6 or a manually configured address - it goes through a duplicate-address detection (DAD) process. The host sends one or more Neighbor Solicitation messages (that is, like an ARP query), as in 8.6 Neighbor Discovery, asking if ...
IPv6 supports multiple addresses, making address assignments more flexible and convenient. Unlike IPv4, which relied solely on the DHCP protocol for address assignment, IPv6 incorporates a native Stateless Address AutoConfiguration SLAAC) protocol. SLAAC can either work alone to provide IPv6 addresses to hosts, or it can work with DHCPv6 to generate new assignment schemes.
Decomposition of an IPv6 address into its binary form. An Internet Protocol version 6 address (IPv6 address) is a numeric label that is used to identify and locate a network interface of a computer or a network node participating in a computer network using IPv6. IP addresses are included in the packet header to indicate the source and the destination of each packet.
Automatic address configuration using APIPA, however, is usually used only on very small networks such as a home or office LAN that connects to the Internet using a DSL router. Address assignment on IPv6 networks is somewhat different. IPv6 addresses can be assigned to an interface by doing the following:
End host ip address assignment - Stateful DHCPv6: For Stateful DHCPv6 we need to configure a DHCP server on SW1. We will use it to assign address on host in vlan 11. SW1 (config)#ipv6 dhcp pool USER-VLAN11. SW1 (config-dhcpv6)#address prefix 2001:db8:10:11::/64 lifetime infinite infinite.
I would like to use IPv6 on my LAN and would like to be able to go out to the WAN as well. My network is a classic IPv4 environment. It works well. My ISP provides Global Unicast IPv6 address on the WAN interface of my router (pfsense 2.5.2). I can ping google's IPv6 address from my router:
SLAAC stands for Stateless Address Autoconfiguration and the name pretty much explains what it does. It is a mechanism that enables each host on the network to auto-configure a unique IPv6 address without any device keeping track of which address is assigned to which node. Stateless and Stateful in the context of address assignment mean the ...
Assigned a IPv6 unicast address in EUI-64 format. ipv6 ospf 1 area 1!--- Enables OSPFv3 on the interface and associates the interface looback10 to area 1. ... Ping Link-Local Address From Remote Network. When the router R1 tries to communicate with router R3 with the link local address, the router R1 returns with an ICMP time-out message that ...
This document describes policies for the allocation and assignment of globally unique Internet Protocol version 6 (IPv6) address space. [ RFC 4291] designates 2000::/3 to be global unicast address space that the Internet Assigned Numbers Authority (IANA) may allocate to the RIRs. In accordance with [ RFC 4291 ], IANA allocated initial ranges of ...
The link local address range for IPv6 is fe80::/10. See Wikipedia or RFC 4862 for details. In the Internet Protocol Version 6 (IPv6), the address block fe80::/10 has been reserved for link-local unicast addressing. For IPv6 there is an automatic mapping between MAC addresses and link local addresses. As Ethernet MAC addresses have 6 bytes and ...
The assignable Global Unicast Address space is defined in [ RFC3513] as the address block. defined by the prefix 2000::/3. [ RFC3513] was later obsoleted by [ RFC4291 ]. All address. space in this block not listed in the table below is reserved by IANA for future. allocation.
The most common method for IPv6 client address assignment is Stateless Address Auto-Configuration (SLAAC). SLAAC provides simple plug-and-play connectivity where clients self-assign an address based on the IPv6 prefix. ... RA guard increases the security of the IPv6 network by dropping the unwanted or rogue RA packets that come from wireless ...
1.Make sure there is a WAN interface that has IPv6 access available. (See Add IPv6 address on router's WAN interface .) 2. Go to LAN >> General Setup, and click on "IPv6" for the LAN subnet to enter IPv6 setting page. 3. In IPv6 Setup page, Enable IPv6. Set WAN Primary Interface to the WAN interface that has IPv6 service available.