This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.

List Azure role assignments using Azure PowerShell
- 6 contributors
Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To determine what resources users, groups, service principals, or managed identities have access to, you list their role assignments. This article describes how to list role assignments using Azure PowerShell.
We recommend that you use the Azure Az PowerShell module to interact with Azure. See Install Azure PowerShell to get started. To learn how to migrate to the Az PowerShell module, see Migrate Azure PowerShell from AzureRM to Az .
If your organization has outsourced management functions to a service provider who uses Azure Lighthouse , role assignments authorized by that service provider won't be shown here. Similarly, users in the service provider tenant won't see role assignments for users in a customer's tenant, regardless of the role they've been assigned.
Prerequisites
- PowerShell in Azure Cloud Shell or Azure PowerShell
List role assignments for the current subscription
The easiest way to get a list of all the role assignments in the current subscription (including inherited role assignments from root and management groups) is to use Get-AzRoleAssignment without any parameters.
List role assignments for a subscription
To list all role assignments at a subscription scope, use Get-AzRoleAssignment . To get the subscription ID, you can find it on the Subscriptions blade in the Azure portal or you can use Get-AzSubscription .
List role assignments for a user
To list all the roles that are assigned to a specified user, use Get-AzRoleAssignment .
To list all the roles that are assigned to a specified user and the roles that are assigned to the groups to which the user belongs, use Get-AzRoleAssignment .
List role assignments for a resource group
To list all role assignments at a resource group scope, use Get-AzRoleAssignment .
List role assignments for a management group
To list all role assignments at a management group scope, use Get-AzRoleAssignment . To get the management group ID, you can find it on the Management groups blade in the Azure portal or you can use Get-AzManagementGroup .
List role assignments for a resource
To list role assignments for a specific resource, use Get-AzRoleAssignment and the -Scope parameter. The scope will be different depending on the resource. To get the scope, you can run Get-AzRoleAssignment without any parameters to list all of the role assignments and then find the scope you want to list.
This following example shows how to list the role assignments for a storage account. Note that this command also lists role assignments at higher scopes, such as resource groups and subscriptions, that apply to this storage account.
If you want to just list role assignments that are assigned directly on a resource, you can use the Where-Object command to filter the list.
List role assignments for classic service administrator and co-administrators
To list role assignments for the classic subscription administrator and co-administrators, use Get-AzRoleAssignment .
List role assignments for a managed identity
Get the object ID of the system-assigned or user-assigned managed identity.
To get the object ID of a user-assigned managed identity, you can use Get-AzADServicePrincipal .
To list the role assignments, use Get-AzRoleAssignment .
- Assign Azure roles using Azure PowerShell
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources

Manage Azure Role Assignments Like a Pro with PowerShell
Today’s blog post is a little bit different. I have a couple of examples of how you can use PowerShell snippets and simple commandlets to get or set role assignmnets in your Azure Subscriptions.
PowerShell examples for managing Azure Role assignments
List all role assignments in a subscription, get all role assignments for a specific resource group, get all role assignments for a specific user, add a role assignment to a user, remove a role assignment for a user, remove all role assignments for a specific user, list all built-in roles, list all custom roles, create a custom role, update a custom role, delete a custom role, list all users or groups assigned to a specific role, list all permissions granted by a specific role, list all resource groups that a user has access to, create a role assignment for a service principal, powershell script to manage azure role assignments.
And now there is a script that combines some of these examples into one usable function:
I hope this was useful. Let me know if you liked the format of this blog and if you want me to include more of these examples.
Vukasin Terzic
Recent Update
- Writing your first Azure Terraform Configuration
- Transition from ARM Templates to Terraform with AI
- Getting started with Terraform for Azure
- Terraform Configuration Essentials: File Types, State Management, and Provider Selection
- Dynamically Managing Azure NSG Rules with PowerShell
Trending Tags
Retrieve azure resource group cost with powershell api.
The Future Of Azure Governance: Trends and Predictions
Further Reading
In my previous blog posts, I wrote about how simple PowerShell scripts can help speed up daily tasks for Azure administrators, and how you can convert them to your own API. One of these tasks is...
Azure Cost Optimization: 30 Ways to Save Money and Increase Efficiency
As organizations continue to migrate their applications and workloads to the cloud, managing and controlling cloud costs has become an increasingly critical issue. While Azure provides a robust s...
Custom PowerShell API for Azure Naming Policy
To continue our PowerShell API series, we have another example of a highly useful API that you can integrate into your environment. Choosing names for Azure resources can be a challenging task. ...

PowerShell Basics: Query Azure Role Based Access Control Assignments
The scenario: what role based access control does somebody have, azure deny assignments.

A great way to learn PowerShell is to set up a scenario in the Azure portal, then try different PowerShell commands to see if you can get the same results. In this article, we'll use Azure Role Based Access control, as it's both visible in the Azure Portal and we have some PowerShell commands for it.
If you're taking over an existing Azure environment, or if you organization has been running Azure for a while without enforced consistency of your Role Based Access Control, you might want to explore your existing RBAC assignments at scale or query the permissions for a specific user. RBAC assignments display in the Access control (IAM) blade of Azure resources, resource groups, subscriptions. Because you can assign a role to a user (or group) on an individual resource, their roles and permissions across your Azure environment may vary, and it's time consuming to check the IAM blade of everything.
Fortunately, we can use PowerShell commands and different display formats, to get the data we want. For the purposes of learning PowerShell, you can use the Azure portal to set up RBAC for different test users (and as part of group memberships) on your resources, resource groups and subscription, so you know what results the PowerShell commands should return.
To keep things simple, I'm running these commands in Cloud Shell inside the Azure Portal.
PowerShell: Get-AzRoleAssignment
Azure RBAC is supported by a number of PowerShell commands, but for this scenario our friend is “ Get-AzRoleAssignment “.
Looking at the structure of PowerShell, because this is a “ Get ” command, it's going to query Azure for some information and return the results to us. “ AzRoleAssignment ” is the base for this command. The command also has a “ New- ” variation, for adding a new assignment, and a “ Remove- ” variation for removing a role assignment.
Note: If you see older blogs or scripts using “Get-AzureRmRoleAssignment”, that was an earlier name for this command before the Az updates. You can often replace the AzureRm bit with just Az, but not in every case as some commands have been deprecated.
If you have multiple subscriptions, Cloud Shell will default to one of them, and your commands will query that subscription and it's associated resources. You can run “ Get-AzContext ” to see which subscription is selected, and run “ Set-AzContext -SubscriptionName “My other subscription”” to change to a different one. (Note I've placed the actual name of my other subscription in it's own set of brackets because it has spaces in it).
Let's start by just running this command and getting a list of all of the RBAC assignments:
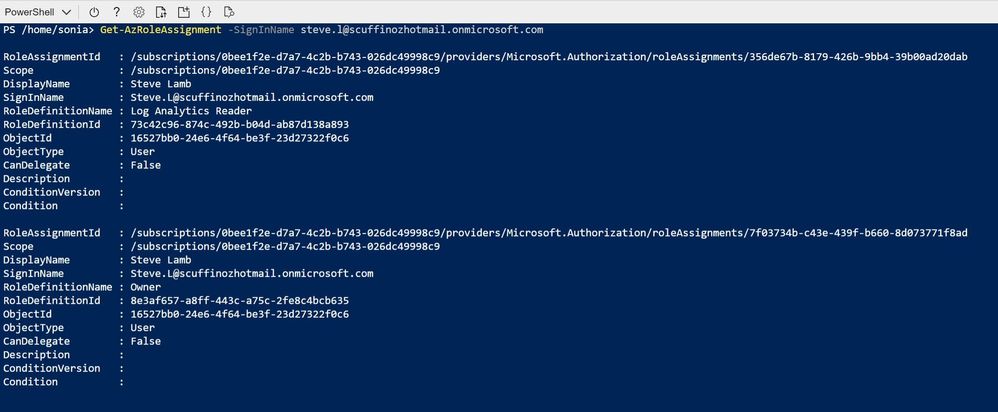
Next, let's narrow that down so we are only looking for role assignments for one particular user. The Get-AzRoleAssignment command has a range of different parameters we can add which will act as a filter. We'll use SignInName , which you can find in the user's details in Azure Active Directory , if you don't know the exact format (and replace my steve.l example name):
This gives us a long list of Steve's role assignments:
Now I want to play with the formatting to make it a little more readable onscreen.
I can format the output of this PowerShell command a few different ways, including as a list or as a table. The output above show sme all of the information that is returned by the query though, so I can use that to further refine the display:
I'm using the ‘pipe' character of | (which is Shift + on my keyboard), then the short version of the “ format-list ” command, then I'm listing just the properties I want to be displayed (DisplayName, RoleDefinitionName and Scope). The pipe tells the first command to send it's output to the second command.

For more formatting command examples, visit Using Format Commands to Change Output View .
Hmm, that could still be a pretty long list if Steve had more role assignments. Let's try a table view instead with “ format-table ” or FT for short:
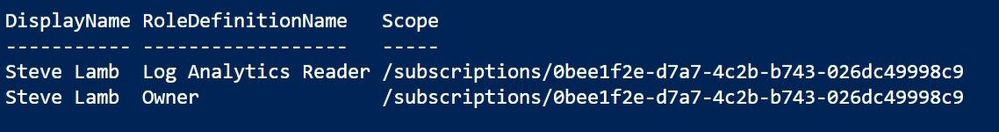
That's better! So, Steve has a pretty high level of access at the top level of my subscription (Owner) plus a Log Analytics Reader role assignment which isn't needed – I can go and tidy that up. But if I run that same command for a different user, I'm seeing a different scope:

Sonia's account is showing the scope as the SCuffSubsMG, not the subscription ID. That's because her Owner access to the current subscription is determined by a role assignment that has been added at the management group level, and as this subscription belongs to that management group, the role assignment is inherited too.
There's one more important thing we need to include – what if our user is a member of a group that has been assigned a role? Our commands so far won't include that. We need to add “ -ExpandPrincipalGroups “.
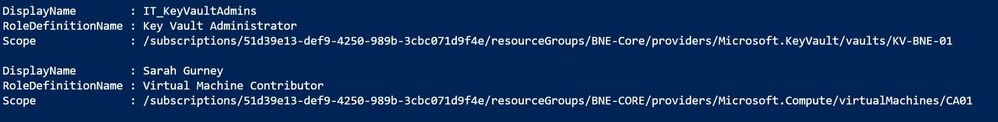
Now I can see that as well as being listed as an individual with the Virtual Machine Contributor role to VM CA01, Sarah is also a member of the IT_KeyVaultAdmins group, who have Key Vault Administrator access to the KV-BNE-01 key vault.
There's one type of Azure role assignment that won't display with Get-AzRoleAssignment, and that's an Azure deny assignment . You can't manually assign someone a deny assignment – they are created and used by Azure to protect system-managed resources. Azure Blueprints and Azure managed apps are the only way that they can be created.
You can query where they are being used in your subscription, by using the Get-AzDenyAssignment command.
Now you've learnt about the capabilities and structure of this command, go and explore with different command parameters. If you get stuck, visit List Azure role assignments using PowerShell or Remove Azure role assignments for more inspiration.
Get-AzRoleAssignment has the full command syntax, parameters, inputs and outputs.
And many of the basic PowerShell concepts we've explored here, like Get/Set/Remove and output formatting, are applicable to a ton of other PowerShell commands too. You're now on your way to understanding and exploring more of PowerShell, especially for scenarios where you can't easily retrieve the same information in the Azure portal.
This article was originally published by Microsoft's SQL Server Blog . You can find the original article here .
Related Posts
- What's the difference between Azure AD Graph, Azure Resource Graph and Microsoft Graph?
- Using Azure Automation with Multiple Tenants
- Unlocking Azure Secrets: Using Identities for Key Vault Access
- Tracking the Source of ADFS Account Lockouts
- Threat matrix for storage
Search code, repositories, users, issues, pull requests...
Provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications

Export role assignments for all Azure subscriptions
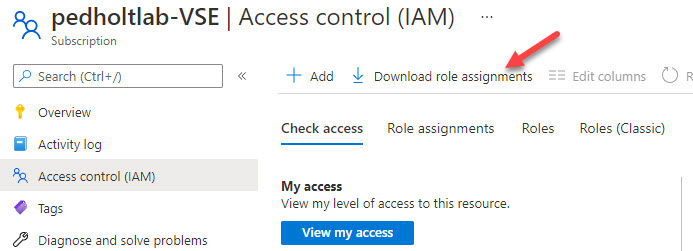
Microsoft has done it straightforward to get an overview of Azure role assignments for a subscription. They have added the Download role assignments button in the Azure portal under Subscriptions. When I’m working with customers that have many subscriptions, I’ll like to get an overview of all the subscriptions at once. Therefore I use PowerShell the export role assignments for all Azure subscriptions at once.

Script parameters
There are 2 parameters in the script, $OutputPath and $SelectCurrentSubscription . None of them are mandatory.
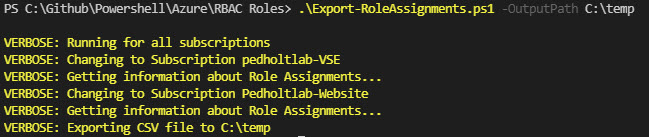
$OutputPath: If defined, a CSV file will be exported to the chosen location. Example: .\Export-RoleAssignments.ps1 -OutputPath C:\temp
$SelectCurrentSubscription: Will only export role assignments from the subscription that are selected. Example: .\Export-RoleAssignments.ps1 -SelectCurrentSubscription
Run Get-Azcontext to view which subscription is selected.
Script Output
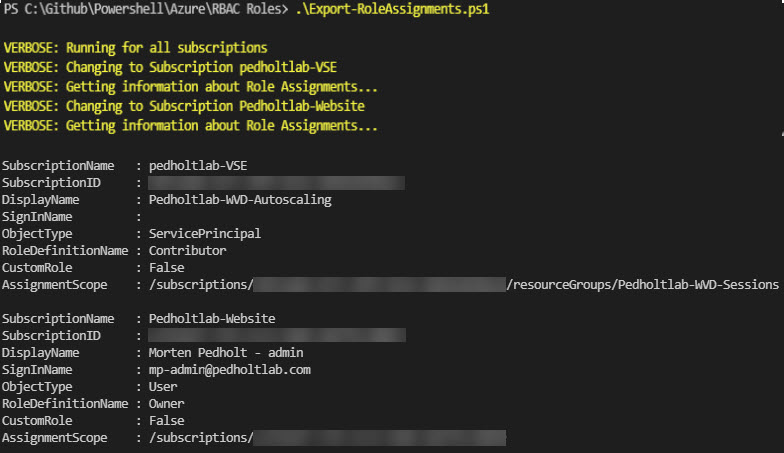
Besides getting an overview of the overall role assignments in an Azure subscription, I also like to know if a role is a Custom or Built-in role. The script will check each assignment if CustomRole is True or False.
Output Example in Powershell Console
Output Example to CSV File
The PowerShell Script
The Powershell script will be available on my account Github . Go there for the latest updates (article script will not be synced with the GitHub version).
3 thoughts on “ Export role assignments for all Azure subscriptions ”
Can you edit the script that when roles assigned to groups the group members are also exported in that csv?
getting the following error on azuread part:
PS C:\scripts> .\azure.ps1 -OutPutPath C:\temp VERBOSE: Running for all subscriptions in tenant VERBOSE: Changing to Subscription Access to Azure Active Directory VERBOSE: Getting information about Role Assignments… WARNING: We have migrated the API calls for this cmdlet from Azure Active Directory Graph to Microsoft Graph. Visit https://go.microsoft.com/fwlink/?linkid=2181475 for any permission issues. Get-AzRoleAssignment : Operation returned an invalid status code ‘BadRequest’ At C:\scripts\azure.ps1:39 char:14 + $roles = Get-AzRoleAssignment | Select-Object RoleDefinitionName, … + ~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : CloseError: (:) [Get-AzRoleAssignment], ErrorResponseException + FullyQualifiedErrorId : Microsoft.Azure.Commands.Resources.GetAzureRoleAssignmentCommand
You have to edit the script for it to work again. You will have to change the API call to Microsoft Graph. Maybe I will do it at some point.
Leave a Reply Cancel reply
Your email address will not be published.
New-AzRoleAssignment
In this Azure PowerShell article, we will discuss the syntax and usage of the New-AzRoleAssignment Azure PowerShell cmdlet with examples.
Table of Contents
Wrapping Up
New-AzRoleAssignment is a very good PowerShell command that you can use to assign an RBAC role to a specific principal for a specified scope. Let’s discuss the Syntax of the New-AzRoleAssignment Azure PowerShell cmdlet.
Below is the syntax of the New-AzRoleAssignment PowerShell command.
Now, let’s discuss some examples of how to use the New-AzRoleAssignment PowerShell command.
You can execute the below Azure PowerShell command to grant a contributor role to the user “[email protected]” under the resource group “MyNewResGrp” scope, and the role assignment is available for delegation.
Below Azure PowerShell cmdlet can help you to grant owner access to the user “[email protected]” to the “TsInfoweb” website.
You may also like following the articles below
- Get-AzRoleAssignment
- Get-AzRoleDefinition
In this Azure PowerShell article, we discussed the syntax and usage of the New-AzRoleAssignment Azure PowerShell cmdlet with examples. Thanks for reading this article !!!

I am Rajkishore, and I have over 14 years of experience in Microsoft Azure and AWS, with good experience in Azure Functions, Storage, Virtual Machine, Logic Apps, PowerShell Commands, CLI Commands, Machine Learning, AI, Azure Cognitive Services, DevOps, etc. Not only that, I do have good real-time experience in designing and developing cloud-native data integrations on Azure or AWS, etc. I hope you will learn from these practical Azure tutorials. Read more .
Gain insights into your Azure role assignments on subscription level

List Azure role assignments and custom role definitions recursively with PowerShell and Azure CLI.
Jump to recipe
Azure Role-Based Access Control (RBAC)
Azure role-based access control (Azure RBAC) helps you manage who has access to Azure resources, what they can do with those resources, and what areas they have access to. Using RBAC in Azure for granular permissions makes it easy to assign permissions to users, groups, service principals, or managed identities. You can assign only the amount of access that users need to perform their jobs, thereby adhering to the principle of least privilege.
You have a ton of builtin roles to choose from, and you can also create your own custom roles if none of the builtin roles fit your use case.
I will not write a thesis on Azure RBAC, as you can find the necessary information on the Azure RBAC documentation page . I will, however, highlight a few shortcomings and how I worked around some of them.
List Azure role definitions
You can list role definitions in the portal , with Azure CLI , or PowerShell .
All these links read List all roles . That is a bit misleading, as they only list the roles in your current scope with any inherited from above (management groups). Any custom roles created in different subscriptions than the current one (or the one provided in scope parameter) will not be listed. A best practice is to create custom roles higher up in management groups so that they are inherited by all subscriptions below. This is not always done, and you might end up with custom roles in different subscriptions.
List Azure role assignments
You can list role assignments in the portal , with PowerShell , or with Azure CLI . There are different ways of listing role assignments, but no way to list all role assignments in your hierarchy recursively. You can list role assignments at a certain scope, with inherited assignments included. You can also find all role assignments for a specific user or group in Azure AD .
Shortcomings
As far as I can see, there are a few shortcomings. These are not critical, and there are other issues with the RBAC model, but I will not go into them here.
- There is no central listing of role assignments for all scopes
- There is no central listing of custom role definitions for all scopes
- Role assignments and role definitions are not linked in any way other than in backend. If you try to delete a custom role definition still in use, you get an error message. You have to find all role assignments using the custom role definition and delete them first.
- Role assignments and role definitions are not listed in Azure AD
Recently I was tasked with cleaning some clickOps’ed custom role definitions and converting them to Terraform. I needed to find all custom role definitions and all role assignments in all subscriptions in all management groups. I also needed to find all role assignments using the custom role definitions I was going to delete. Because of reasons I needed to create new role definitions, and could not import them into Terraform. Because of the shortcomings mentioned above, I had to write a script to list all role definitions and role assignments for all scopes.
I did not want to click through all of the subscriptions and management groups, so I wrote a script to do it for me.
Azure Governance Visualizer
At this point I would be remiss not to mention the Azure Governance Visualizer . It is a great tool created by Julian Hayward for visualizing your total Azure Governance. It lists all custom role definitions and every other detail you would need from your environment regarding RBAC and lot of other useful information. In this case it is too complex, and I wanted to focus on the RBAC part. Anyway, check it out if you need a great tool for visualizing your Azure Governance.
Log in with both Azure CLI and PowerShell
Recursively find all management groups and subscriptions, list all custom roles in all subscriptions, list all role assignments with relevant custom roles in all subscriptions, write everything to json files for documentation or investigation, prerequisites.
- A user with Reader role on the management group level to list all management groups.
- A user with Reader role on the subscription level to list all subscriptions and their assignments/definitions.
- Azure PowerShell installed
- Azure CLI installed
The script can be found in all its glory in GitHub . I will explain the different sections below.
I did not want the script to force a login of both PowerShell and Azure CLI every time I ran it. Therefore I needed some logic to check for login status and login if necessary.
Since there could be several management groups in different levels, I need to recursively find the management groups to list all subscriptions.
This part is a simple loop through all subscriptions and list all custom role definitions. I could have used the PowerShell cmdlet Get-AzRoleDefinition , but I wanted to use the Azure CLI command az role definition list to get some more relevant information. The other actions done for each subscription are also done in the same foreach loop.
This part is a simple loop through all custom roles in the current subscription and list all assignments. Exports them if required with exportAssignments parameter.
This part is a simple conversion from PowerShell objects to json with ConvertTo-Json and dumpt to json file.
- Azure PowerShell
Some parameters are necessary in this script to make it dynamic.
- topLvlMgmtGroup - [String] Id of your top level management group to start recursive listing.
- customRolesOnly - [String] Set to true if exporting only custom roles. Defaults to true .
- excludeRegexPattern - [String] Any exclusion RegEx pattern to use. Remember escape chars!
- rolesFolder - [String] Folder where role definitions will be exported. Defaults to output .
- exportAssignments - [Switch] Whether to export assignments to file or not.
- subscription - [String] Subscription Id or name for when exporting in a single subscription.
Resulting json
Running the script results in some output to json files.
Role Definitions
It makes sense to only export custom role definitions, because the builtin ones are already pretty well documented.
For each custom role definition found, one file will be written. This is an example role and all guids are randomly generated.
Role Assignments
All role assignments will be exported if the relevant parameter is set.
Output to a single assignments.json:
I had some fun with this task, and maybe created an over engineered solution. Also I had the chance to practice my PowerShell-skills, which is a welcomed exercise!
Please let me know if you have a one-liner for this that I can use in the future 🙂

Get PIM Role Assignment Status For Azure AD Using Powershell
If you’re like me and you love to run reports to get valuable information for your tenant and settings, the get PIM role assignment status is the script for you. Recently I was running a report to audit user permissions in Azure AD and realized that my data was off by a bit. I knew some users were added to Privilege Identity Management (PIM) roles but they weren’t showing up in my report.
The reason they weren’t showing up is because I was using the Get-AzureADDirectoryRoleMember cmdlet and that only shows users with current or activated access. If a user was not elevated in PIM, they basically didn’t have access so it skewing my results.
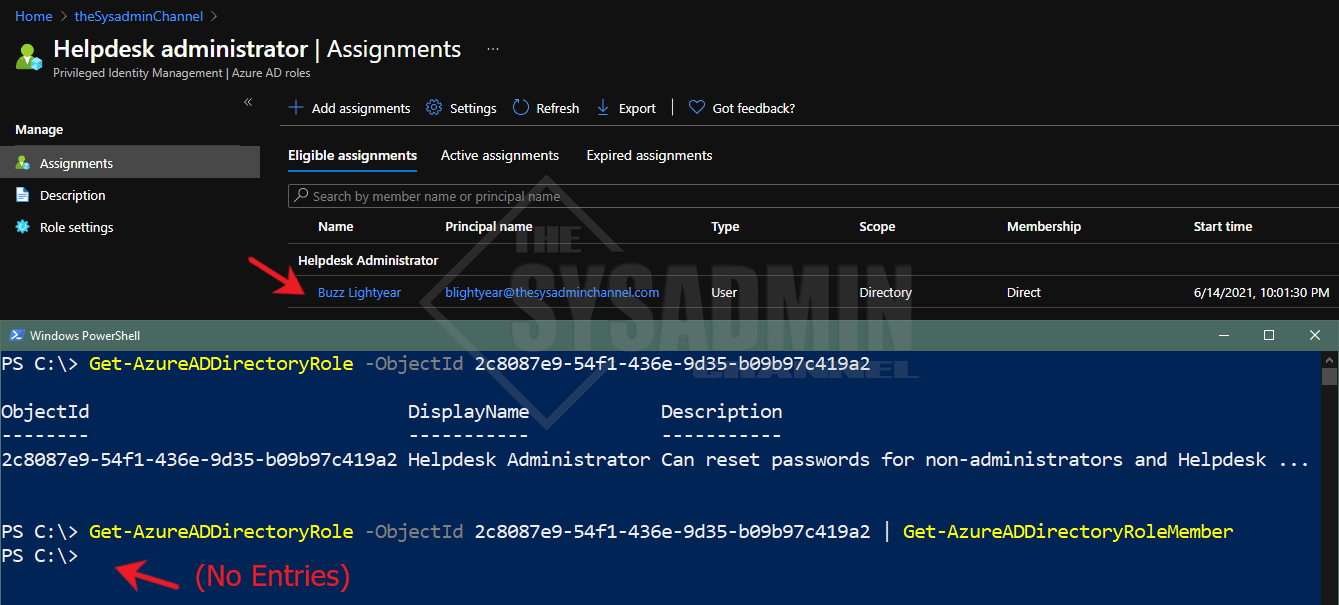
To give you a better idea of what I’m talking about, the above is a sample of the Helpdesk Administrators role. In the Azure AD GUI, the user is added as an eligible role, meaning he can elevate his just in time access. However in Powershell, since the role is not activated, it is not going to display.
Therefore we are going to use the Get-AzureADMSPrivilegedRoleDefinition Azure AD cmdlet to display the list of roles available and the Get-AzureADMSPrivilegedRoleAssignment to filter for the user we’re specifying.
Requirements for this script to work
In order to make this work you’ll need the following:
- AzureADPreview Powershell module .
I want to emphasize the “preview” in the name of the module. Using just the regular AzureAD module is not not going to work so that’s something to keep in mind.
Script Parameters
Userprincipalname.
Specify the UserPrincipalName for the user you want to check roles for.
Specify the RoleName you want to filter for. This will display all PIM roles that are granted directly or through a group.
By default it will use the TenantId from your current session. If you’re connected to a multi-tenant, you can specify the tenant here.
By using this script you’ll be able to see all the people who have standing access as well as PIM eligible roles.
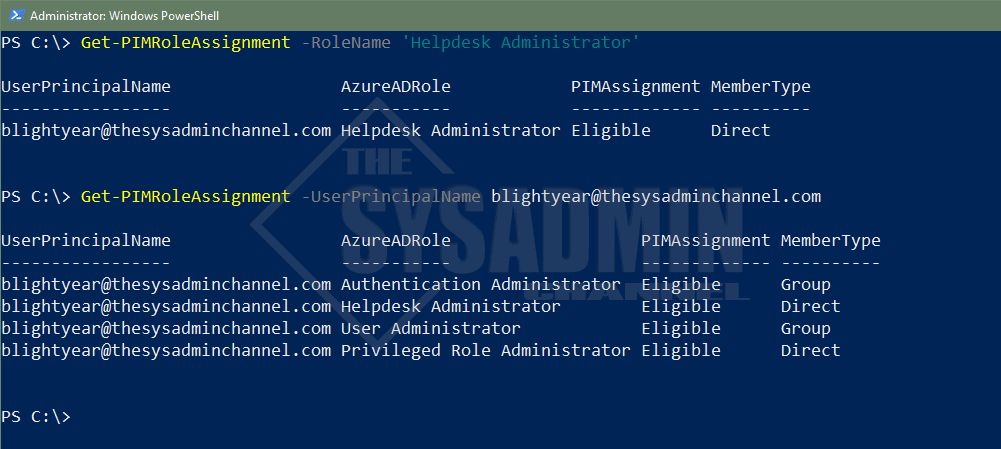
We can now see that the Helpdesk Administrator is now showing up in our output and in the Assignment column it is labeled as Eligible. We’ll also take note that we can see if the member type is added through a group or if it was added directly. This script will support that option.
Get PIM role assignment status for Azure AD using Powershell will now be in your arsenal of cool tips and tricks for your Syadmin role. If you’re interested in more scripts like this, be sure to check out our Powershell Gallery or Azure Content . Finally, be sure to check out our Youtube Channel for any video content.
Paul Contreras
Hi, my name is Paul and I am a Sysadmin who enjoys working on various technologies from Microsoft, VMWare, Cisco and many others. Join me as I document my trials and tribulations of the daily grind of System Administration.
Is there a possibility we could get an updated version of this using Microsoft Graph or Graph API? I cannot find any suitable alternatives now that the azure cmdlets are depreciated.
Yes. I have the script already created, just need to create an article
Could you upload this script, please? This is wonderfull.
See my updated post for the Graph API version. https://thesysadminchannel.com/get-entra-id-pim-role-assignment-using-graph-api/
See my updated post for the Graph API script. https://thesysadminchannel.com/get-entra-id-pim-role-assignment-using-graph-api/
it was a great job but riles are changed and groups extract cannot work
What about a similar Script for Azure resource roles?
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *

COMMENTS
To list role assignments for a specific resource, use Get-AzRoleAssignment and the -Scope parameter. The scope will be different depending on the resource. To get the scope, you can run Get-AzRoleAssignment without any parameters to list all of the role assignments and then find the scope you want to list. Azure PowerShell.
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window.
Let's discuss some examples of implementation of the Get-AzRoleAssignment PowerShell command. Example-1: You can execute the Azure PowerShell cmdlet below to help you get the list of all the role assignments under my current subscription. Get-AzRoleAssignment. After executing the above PowerShell command, I got the below output.
Learn how to manage Azure Role assignments using PowerShell snippets and simple commandlets. Discover examples for listing all role assignments, adding and removing assignments for users or service principals, creating custom roles, and more. Plus, check out a script that combines some of these examples into a single function. Written by Vukasin Terzic.
Let's start by just running this command and getting a list of all of the RBAC assignments: Get-AzRoleAssignment. Next, let's narrow that down so we are only looking for role assignments for one particular user. The Get-AzRoleAssignment command has a range of different parameters we can add which will act as a filter.
How to get Azure Role Instance using Windows Azure Powershell commands. 0 Get Azure Resources details. 2 Azure Powershell command for getting resources in a Resource Group ... How to get list of all roles assignments using RBAC API. 2 Get all AppRole assignments in Azure Active Directory. 2 How to know the azure role assignment already exists ...
Get-AzRoleAssignmentSchedule SYNOPSIS SYNTAX List (Default) Get GetViaIdentity DESCRIPTION EXAMPLES Example 1: List all role assignment schedules for a resource Example 2: List all My role assignment schedules for a resource Example 3: List all role assignment schedules for a resource with filters Example 4: Get a role assignment schedule by ...
They have added the Download role assignments button in the Azure portal under Subscriptions. When I'm working with customers that have many subscriptions, I'll like to get an overview of all the subscriptions at once. Therefore I use PowerShell the export role assignments for all Azure subscriptions at once. Script parameters
Now, let's discuss some examples of how to use the New-AzRoleAssignment PowerShell command. Example-1: You can execute the below Azure PowerShell command to grant a contributor role to the user "[email protected]" under the resource group "MyNewResGrp" scope, and the role assignment is available for delegation.
List all custom roles in all subscriptions. This part is a simple loop through all subscriptions and list all custom role definitions. I could have used the PowerShell cmdlet Get-AzRoleDefinition, but I wanted to use the Azure CLI command az role definition list to get some more relevant information. The other actions done for each subscription are also done in the same foreach loop.
Get PIM Role Assignment Status For Azure AD Using Powershell. By using this script you'll be able to see all the people who have standing access as well as PIM eligible roles. This will check if a user is added to PIM or standing access. For updated help and examples refer to -Online version.
i am trying to get all objects from Access Control tab from Storage Account container using powershell. Using command: Get-AzRoleAssignment -ResourceGroupName 'devtest' -ResourceName 'sa-name' - ... You can list the RBAC on a specific container by listing all role assignments for the storage account and excluding all containers except for the ...
This command queries the user's currently active Entra ID roles, therefore including all statically assigned roles (in addition to roles currently enabled via PIM). The command already respects roles that come via role assignable groups. We add two additional properties to make the output more digestable.
Hello I am trying to get a list of all my role assignments after resource deployment in my CI/CD pipeline. However the displayName field is always empty in my response. I am using: Get-AzRoleAssig...
The AzurePowerShell@5 used the service principal from service connection to assign the role on the storage account. The Forbidden indicates the service principal permission is not enough. As you have done, you can fix it by assigning the role Storage Blob Data Contributor role to the service principal from the subscription scope.