Systematic Literature Review of Cloud Computing Research Between 2010 and 2023
- Conference paper
- First Online: 21 May 2024
- Cite this conference paper

- Shailaja Jha 10 &
- Devina Chaturvedi ORCID: orcid.org/0009-0004-1242-2099 11
Part of the book series: Lecture Notes in Business Information Processing ((LNBIP,volume 508))
Included in the following conference series:
- Workshop on e-Business
We present a meta-analysis of cloud computing research in information systems. The study includes 152 referenced journal articles published between January 2010 to June 2023. We take stock of the literature and the associated research themes, research frameworks, the employed research methodology, and the geographical distribution of the articles. This review provides holistic insights into trends in cloud computing research based on themes, frameworks, methodology, geographical focus, and future research directions. The results indicate that the extant literature tends to skew toward themes related to business issues, which is an indicator of the maturing and widespread use of cloud computing. This trend is evidenced in the more recent articles published between 2016 to 2023.
This is a preview of subscription content, log in via an institution to check access.

Access this chapter
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
The conference proceedings were primarily used to assess the year-on-year numerical trends in publications, and they have not been used for detailed analysis.
Abdalla Mikhaeil, C., James, T.L.: Examining the case of French hesitancy toward IDaaS solutions: technical and social contextual factors of the organizational IDaaS privacy calculus. Inform. Manage. 60 (4), 103779 (2023)
Google Scholar
Allen, B., et al.: Software as a service for data scientists. Commun. ACM 55 (2), 81–88 (2012)
Andrade-Rojas, M.G., Kathuria, A., Lee, H.-H.: Multilevel synergy of IT operational integration: competition networks and operating performance. Prod. Oper. Manage. (forthcoming) (2024)
Andrade-Rojas, M.G., Saldanha, T., Kathuria, A., Khuntia, J., Boh, W.F.: How IT overcomes deficiencies for innovation in SMEs: closed innovation versus open innovation. Inform. Syst. Res. (forthcoming) (2024)
Anthes, G.: Security in the cloud. Commun. ACM 53 , 16–18 (2010)
Armbrust, M., et al.: A view of cloud computing. Commun. ACM 53 , 50–58 (2010)
August, T., Niculescu, M.F., Shin, H.: Cloud implications on software network structure and security risks. Inform. Syst. Res. 25 , 489–510 (2014)
Bandara, W., Furtmueller, E., Gorbacheva, E., Miskon, S., Beekhuyzen, J.: Achieving rigor in literature reviews: insights from qualitative data analysis and tool-support. Commun. Assoc. Inform. Syst. 37 (8), 154–204 (2015). http://aisel.aisnet.org/cais/vol37/iss1/8
Benlian, A.: Is traditional, open-source, or on-demand first choice? Developing an AHP-based framework for the comparison of different software models in office suites selection. Eur. J. Inform. Syst. 20 , 542–559 (2011)
Benlian, A., Kettinger, W.J., Sunyaev, A., Winkler, T.J.: Special section: the transformative value of cloud computing: a decoupling, platformization, and recombination theoretical framework. J. Manage. Inform. Syst. 35 , 719–739 (2018)
Benlian, A., Koufaris, M., Hess, T.: The role of SaaS service quality for continued SaaS use: Empirical insights from SaaS using firms (2010)
Bhattacherjee, A., Park, S.C.: Why end-users move to the cloud: a migration-theoretic analysis. Eur. J. Inform. Syst. 23, 357–372 (2014)
Chaturvedi, D., Kathuria, A., Andrade, M., Saldanha, T.: Navigating the Paradox of IT Novelty and Strategic Conformity: The Moderating Role of Industry Dynamism (2023)
Chen, F., Lu, A., Wu, H., Li, M.: Compensation and pricing strategies in cloud service SLAs: considering participants’ risk attitudes and consumer quality perception. Electron. Commerce Res. Appl. 56 , 101215 (2022)
Cheng, H.K., Li, Z., Naranjo, A.: Research note—cloud computing spot pricing dynamics: latency and limits to arbitrage. Inform. Syst. Res. 27 , 145–165 (2016)
Choudhary, V., Vithayathil, J.: The impact of cloud computing: should the IT department be organized as a cost center or a profit center? J. Manage. Inform. Syst. 30 , 67–100 (2013)
Choudhary, V., Zhang, Z.: Research note—patching the cloud: the impact of SaaS on patching strategy and the timing of software release. Inform. Syst. Res. 26 , 845–858 (2015)
Dasgupta, A., Karhade, P., Kathuria, A., Konsynski, B.: Holding space for voices that do not speak: design reform of rating systems for platforms in GREAT economies (2021)
Demirkan, H., Cheng, H.K., Bandyopadhyay, S.: Coordination strategies in an SaaS supply chain. J. Manage. Inform. Syst. 26 , 119–143 (2010)
Demirkan, H., Delen, D.: Leveraging the capabilities of service-oriented decision support systems: putting analytics and big data in cloud. Decis. Support Syst. 55 , 412–421 (2013)
Dierks, L., Seuken, S.: Cloud pricing: the spot market strikes back. Manage. Sci. 68 (1), 105–122 (2022)
Article Google Scholar
Ding, S., Xia, C., Wang, C., Desheng, Wu., Zhang, Y.: Multi-objective optimization based ranking prediction for cloud service recommendation. Decis. Support. Syst. 101 , 106–114 (2017)
Dong, L., Shu, W., Sun, D., Li, X., Zhang, L.: Pre-alarm system based on real-time monitoring and numerical simulation using internet of things and cloud computing for tailings dam in mines. IEEE Access 5 , 21080–21089 (2017)
Xin, Du., Tang, S., Zhihui, Lu., Gai, K., Jie, Wu., Hung, P.C.K.: Scientific workflows in IoT environments: a data placement strategy based on heterogeneous edge-cloud computing. ACM Trans. Manage. Inform. Syst. 13 (4), 1–26 (2022)
Ermakova, T., Fabian, B., Kornacka, M., Thiebes, S., Sunyaev, A.: Security and privacy requirements for cloud computing in healthcare: elicitation and prioritization from a patient perspective. ACM Trans. Manage. Inform. Syst. 11 (2), 1–29 (2020)
Garrison, G., Kim, S., Wakefield, R.L.: Success factors for deploying cloud computing. Commun. ACM 55 (9), 62–68 (2012)
Giessmann, A., Legner, C.: Designing business models for cloud platforms. Inf. Syst. J. 26 (5), 551–579 (2016). https://doi.org/10.1111/isj.12107
Gray, A.: Conflict of laws and the cloud. Comput. Law Secur. Rev. 29 (1), 58–65 (2013)
Hosseini, L., Tang, S., Mookerjee, V., Sriskandarajah, C.: A switch in time saves the dime: a model to reduce rental cost in cloud computing. Inform. Syst. Res. 31 (3), 753–775 (2020)
Huang, K.-W., Sundararajan, A.: Pricing digital goods: discontinuous costs and shared infrastructure. Inf. Syst. Res. 22 (4), 721–738 (2011)
Iosup, A., Ostermann, S., Yigitbasi, M.N., Prodan, R., Fahringer, T., Epema, D.H.J.: Performance analysis of cloud computing services for many-tasks scientific computing. IEEE Trans. Parallel Distrib. Syst. 22 , 931–945 (2011)
Iyer, B., Henderson, J.C.: Preparing for the future: understanding the seven capabilities cloud computing. MIS Q. Exec. 9 , 2 (2010)
Jha, S. and Kathuria, A. Size Matters for Cloud Capability and Performance (2022)
Jha, S., Kathuria, A.: How firm age and size influence value creation from cloud computing (2023)
Joe-Wong, C., Sen, S.: Harnessing the power of the cloud: revenue, fairness, and cloud neutrality. J. Manage. Inf. Syst. 35 , 813–836 (2018)
Joint, A., Baker, E.: Knowing the past to understand the present–issues in the contracting for cloud based services. Comput. Law Secur. Rev. 27 (4), 407–415 (2011)
Karhade, P., Kathuria, A.: Missing impact of ratings on platform participation in India: a call for research in GREAT domains. Commun. Assoc. Inf. Syst. 47 (1), 19 (2020)
Karhade, P., Kathuria, A., Dasgupta, A., Malik, O., Konsynski, B.R.: Decolonization of digital platforms: a research agenda for GREAT domains. In: Garimella, A., Karhade, P., Kathuria, A., Liu, X., Xu, J., Zhao, K. (eds.) The Role of e-Business during the Time of Grand Challenges. LNBIP, vol. 418, pp. 51–58. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-79454-5_5
Chapter Google Scholar
Karhade, P., Kathuria, A., Konsynski, B.: When choice matters: assortment and participation for performance on digital platforms (2021)
Kathuria, A., Karhade, P.P., Konsynski, B.R.: In the realm of hungry ghosts: multi-level theory for supplier participation on digital platforms. J. Manag. Inf. Syst. 37 (2), 396–430 (2020)
Kathuria, A., Mann, A., Khuntia, J., Saldanha, T.J.V., Kauffman, R.J.: A strategic value appropriation path for cloud computing. J. Manage. Inf. Syst. 35 (3), 740–775 (2018). https://doi.org/10.1080/07421222.2018.1481635
Kaur, J., Kaur, P.D.: CE-GMS: A cloud IoT-enabled grocery management system. Electron. Commer. Res. Appl. 28 , 63–72 (2018)
Kepes, B.: 30% of servers are sitting “Comatose” according to research. Forbes https://forbes.com/sites/benkepes/2015/06/03/30-of-servers-are-sitting-comatose-according-to-research (2015)
Khokhar, R.H., Fung, B.C.M., Iqbal, F., Alhadidi, D., Bentahar, J.: Privacy-preserving data mashup model for trading person-specific information. Electron. Commer. Res. Appl. 17 , 19–37 (2016)
Khuntia, J., Kathuria, A., Andrade-Rojas, M.G., Saldanha, T., Celly, N.: How foreign and domestic firms differ in leveraging IT-enabled supply chain information integration in BOP markets: the role of supplier and client business collaboration. J. Assoc. Inf. Syst. 22 (3), 6 (2021)
King, W.R., He, J.: Understanding the role and methods of meta-analysis in IS Research. Commun. Assoc. Inf. Syst. 16, 665–686 (2005)
Krancher, O., Luther, P., Jost, M.: Key affordances of Platform-as-a-Service: self-organization and continuous feedback. J. Manage. Inf. Syst. 35 , 776–812 (2018)
Kumar, C., Marston, S., Sen, R., Narisetty, A.: Greening the cloud: a load balancing mechanism to optimize cloud computing networks. J. Manage. Inf. Syst. 39 ,, 513–541 (2022)
Kung, L., Cegielski, C.G., Kung, H.-J.: An integrated environmental perspective on software as a service adoption in manufacturing and retail firms. J. Inf. Technol. 30 , 352–363 (2015)
Lansing, J., Benlian, A., Sunyaev, A.: Unblackboxing” decision makers’ interpretations of IS certifications in the context of cloud service certifications. J. Assoc. Inf. Syst. 19 (11), 1064–1096 (2018)
Lansing, J., Siegfried, N., Sunyaev, A., Benlian, A.: Strategic signaling through cloud service certifications: Comparing the relative importance of certifications’ assurances to companies and consumers. J. Strateg. Inf. Syst. 28 , 101579 (2019)
Lansing, J., Sunyaev, A.: Trust in cloud computing. ACM SIGMIS Database DATABASE Adv. Inform. Syst. 47 , 58–96 (2016)
Lee, J., Cho, D., Lim, G.: Design and validation of the bright internet. J. Assoc. Inform. Syst. 19 , 63–85 (2018)
Lee, M.H., Han, S.P., Park, S., Oh, W.: Positive demand spillover of popular app adoption: implications for platform owners’ management of complements. Inf. Syst. Res. 34 (3), 961–995 (2023)
Li, S., Chen, W., Chen, Y., Chen, C. and Zheng, Z.: Makespan-minimized computation offloading for smart toys in edge-cloud computing. Electron. Commerce Res. Appl. 37 , 100884 (2019)
Li, S., Cheng, H.K., Duan, Y., Yang, Y.-C.: A study of enterprise software licensing models. J. Manag. Inf. Syst. 34 (1), 177–205 (2017)
Lins, S., Schneider, S., Szefer, J., Ibraheem, S., Ali, A.: Designing monitoring systems for continuous certification of cloud services: deriving meta-requirements and design guidelines. Commun. Assoc. Inf. Syst. 44 (1), 460–510 (2019)
Liu, Y., Sheng, X., Marston, S.R.: The impact of client-side security restrictions on the competition of cloud computing services. Int. J. Electron. Comm. 19 (3), 90–117 (2015)
Ma, D., Seidmann, A.: Analyzing software as a service with per-transaction charges. Inf. Syst. Res. 26 , 360–378 (2015)
Malik, O., Jaiswal, A., Kathuria, A., Karhade, P.: Leveraging BI systems to overcome infobesity: a comparative analysis of incumbent and new entrant firms (2022)
Mani, D., Srikanth, K., Bharadwaj, A.: Efficacy of R&D work in offshore captive centers: an empirical study of task characteristics, coordination mechanisms, and performance. Inf. Syst. Res. 25 (4), 846–864 (2014)
Mann, A., Kathuria, A., Khuntia, J., Saldanha, T.: Cloud-integration and business flexibility: the mediating role of cloud functional capabilities (2016)
Marston, S., Li, Z., Bandyopadhyay, S., Zhang, J., Ghalsasi, A.: Cloud computing — the business perspective. Decis. Support. Syst. 51 (1), 176–189 (2011)
Mell, P.M., Grance, T.: The NIST definition of cloud computing. National Institute of Standards and Technology (2011)
Metz, C.: The epic story of dropboxs exodus from the amazon cloud empire (2016)
Mithas, R., Sambamurthy,: How information management capability influences firm performance. MIS Q. 35 (1), 237 (2011)
Mithas, T., Bardhan, G.: Information technology and firm profitability: mechanisms and empirical evidence. MIS Q. 36 (1), 205 (2012)
Muhic, M., Bengtsson, L., Holmström, J.: Barriers to continuance use of cloud computing: evidence from two case studies. Inf. Manage. 60 , 103792 (2023)
Mukherjee, A., Sundarraj, R.P., Dutta, K.: Time-preference-based on-spot bundled cloud-service provisioning. Decis. Support. Syst. 151 , 113607 (2021)
Müller, S.D., Holm, S.R., Søndergaard, J.: Benefits of cloud computing: literature review in a maturity model perspective. Commun. Assoc. Inform. Syst. 37 , 851–878 (2015)
Ojala, A.: Business models and opportunity creation: how IT entrepreneurs create and develop business models under uncertainty. Inf. Syst. J. 26 , 451–476 (2015)
Oliveira, T., Thomas, M., Espadanal, M.: Assessing the determinants of cloud computing adoption: An analysis of the manufacturing and services sectors. Inf. Manage. 51 , 497–510 (2014)
Owens, D. Securing elasticity in the cloud. Communications of the ACM , 53, 6 (2010/06 2010), 46–51 (2010)
Pang, M.-S., Tanriverdi, H.: Strategic roles of IT modernization and cloud migration in reducing cybersecurity risks of organizations: the case of U.S. federal government. J. Strat. Inf. Syst. 31 , 101707 (2022)
Park, J., Han, K., Lee, B.: Green cloud? An empirical analysis of cloud computing and energy efficiency. Manage. Sci. 69 , 1639–1664 (2023)
Parno, B., Howell, J., Gentry, C., Raykova, M.: Pinocchio. Commun. ACM 59 , 103–112 (2016)
Pye, J., Rai, A., Dong, J.Q.: Business value of information technology capabilities: an institutional governance perspective. Inf. Syst. Res. 35 , 28–44 (2023)
Ramakrishnan, T., Kathuria, A., Khuntia, J., Konsynski, B.: IoT value creation through supply chain analytics capability (2022)
Retana, G., Forman, C., Narasimhan, S., Niculescu, M.F., Wu, D.J.: Technical support, knowledge transfer, and service demand: evidence from the cloud. SSRN Electron. J. (2012)
Rodrigues, J., Ruivo, P., Oliveira, T.: Mediation role of business value and strategy in firm performance of organizations using software-as-a-service enterprise applications. Inf. Manag. 58 (1), 103289 (2021)
Saldanha, T.J., Andrade-Rojas, M.G., Kathuria, A., Khuntia, J., Krishnan, M.: How the locus of uncertainty shapes the influence of CEO long-term compensation on IT capital investments. MIS Q. (2023)
Sambhara, C., Rai, A., Xu, S.X.: Configuring the enterprise systems portfolio: the role of information risk. Inf. Syst. Res. 33 (2), 446–463 (2022)
Sarker, S., Chatterjee, S., Xiao, X., Elbanna, A.: The sociotechnical axis of cohesion for the IS discipline: its historical legacy and its continued relevance. MIS Q. 43 (3), 695–720 (2019)
Schlagwein, D., Thorogood, A., Willcocks, L.P.: How commonwealth bank of Australia gained benefits using a standards-based, multi-provider cloud model. MIS Q. Exec. 13 (4), 209–222 (2014)
Schneider, S., Sunyaev, A.: Determinant factors of cloud-sourcing decisions: reflecting on the IT outsourcing literature in the era of cloud computing. J. Inf. Technol. 31 (1), 1–31 (2016). https://doi.org/10.1057/jit.2014.25
Schneider, S., Wollersheim, J., Krcmar, H., Sunyaev, A.: How do Requirements evolve over Time? A case study investigating the role of context and experiences in the evolution of enterprise software requirements. J. Inf. Technol. 33 (2), 151–170 (2018)
Schniederjans, D.G., Hales, D.N.: Cloud computing and its impact on economic and environmental performance: a transaction cost economics perspective. Decis. Support. Syst. 86 , 73–82 (2016)
Schreieck, M., Wiesche, M., Krcmar, H.: Capabilities for value co-creation and value capture in emergent platform ecosystems: a longitudinal case study of SAP’s cloud platform. J. Inf. Technol. 36 (4), 365–390 (2021)
Shiau, W.-L., Chau, P.Y.K.: Understanding behavioral intention to use a cloud computing classroom: a multiple model comparison approach. Inf. Manag. 53 (3), 355–365 (2016)
Singh, V.K., Shivendu, S., Dutta, K.: Spot instance similarity and substitution effect in cloud spot market. Decis. Support. Syst. 159 , 113815 (2022)
Soh, F., Setia, P.: The impact of dominant IT infrastructure in multi-establishment firms: the moderating role of environmental dynamism. J. Assoc. Inf. Syst. 23 (6), 1603–1633 (2022)
Son, I., Lee, D., Lee, J.-N., Chang, Y.B.: Market perception on cloud computing initiatives in organizations: an extended resource-based view. Inf. Manag. 51 (6), 653–669 (2014)
Srinivasan, S.: Is security realistic in cloud computing? J. Int. Technol. Inf. Manag. 22 (4), 3 (2013). https://doi.org/10.58729/1941-6679.1020
Article MathSciNet Google Scholar
Sun, T., Shi, L., Viswanathan, S., Zheleva, E.: Motivating effective mobile app adoptions: evidence from a large-scale randomized field experiment. Inf. Syst. Res. 30 (2), 523–539 (2019)
Templier, M., Paré, G.: Transparency in literature reviews: an assessment of reporting practices across review types and genres in top IS journals. Eur. J. Inf. Syst. 27 (5), 503–550 (2017). https://doi.org/10.1080/0960085X.2017.1398880
Trenz, M., Huntgeburth, J., Veit, D.: Uncertainty in cloud service relationships: uncovering the differential effect of three social influence processes on potential and current users. Inf. Manage. 55, 971–983 (2018)
van de Weerd, I., Mangula, I.S., Brinkkemper, S.: Adoption of software as a service in Indonesia: examining the influence of organizational factors. Inf. Manage. 53 (7), 915–928 (2016)
Venkatesh, V., Bala, H., Sambamurthy, V.: Implementation of an information and communication technology in a developing country: a multimethod longitudinal study in a Bank in India. Inf. Syst. Res. 27 (3), 558–579 (2016)
Venkatesh, V., Sykes, T.A.: Digital divide initiative success in developing countries: a longitudinal field study in a Village in India. Inf. Syst. Res. 24 (2), 239–260 (2013)
Venters, W., Whitley, E.A.: A critical review of cloud computing: researching desires and realities. J. Inf. Technol. 27 (3), 179–197 (2012)
Wang, N., Huigang Liang, Yu., Jia, S.G., Xue, Y., Wang, Z.: Cloud computing research in the IS discipline: a citation/co-citation analysis. Decis. Support. Syst. 86 , 35–47 (2016)
Wang, X., Wang, X.: Multimedia data delivery based on IoT clouds. Commun. ACM 64 (8), 80–86 (2021)
Winkler, T.J., Benlian, A., Piper, M., Hirsch, H.: Bayer healthcare delivers a dose of reality for cloud payoff mantras in multinationals. MIS Q. Exec. 13 , 4 (2014)
Winkler, T.J., Brown, C.V.: Horizontal allocation of decision rights for on-premise applications and Software-as-a-Service. J. Manage. Inf. Syst. 30 (3), 13–48 (2013)
Wright, R.T., Roberts, N., Wilson, D.: The role of context in IT assimilation: a multi-method study of a SaaS platform in the US nonprofit sector. Eur. J. Inf. Syst. 26 (5), 509–539 (2017). https://doi.org/10.1057/s41303-017-0053-2
Wulf, F., Lindner, T., Strahringer, S., Westner, M.: IaaS, PaaS, or SaaS? The why of cloud computing delivery model selection: vignettes on the post-adoption of cloud computing. In: The Proceedings of Proceedings of the 54th Hawaii International Conference on System Sciences, pp. 6285–6294 (2021)
Xiong, Hu., Wang, Yi., Li, W., Chen, C.-M.: Flexible, efficient, and secure access delegation in cloud computing. ACM Trans. Manage. Inf. Syst. 10 (1), 1–20 (2019)
Yang, H., Tate, M.: A descriptive literature review and classification of cloud computing research. Commun. Assoc. Inf. Syst. 31 (1), 2 (2012)
Yaraghi, N., Du, A.Y., Sharman, R., Gopal, R.D., Ramesh, R.: Health Information exchange as a multisided platform: adoption, usage, and practice involvement in service co-production. Inf. Syst. Res. 26 (1), 1–18 (2015)
Yuan, S., Sanjukta Das, R., Ramesh, C.Q.: Service agreement trifecta: backup resources, price and penalty in the availability-aware cloud. Inf. Syst. Res. 29 (4), 947–964 (2018)
Zhang, G., Ravishankar, M.N.: Exploring vendor capabilities in the cloud environment: a case study of Alibaba cloud computing. Inf. Manage. 56 , 343–355 (2019)
Zhang, X., Yue, W.: Integration of on-premises and cloud-based software: the product bundling perspective. J. Assoc. Inform. Syst. 21 , 1507–1551 (2020)
Zorrilla, M., García-Saiz, D.: A service oriented architecture to provide data mining services for non-expert data miners. Decis. Support. Syst.. Support. Syst. 55 (1), 399–411 (2013). https://doi.org/10.1016/j.dss.2012.05.045
Download references
Author information
Authors and affiliations.
SP Jain Institute of Management and Research, Mumbai, India
Shailaja Jha
Indian School of Business, Hyderabad, India
Devina Chaturvedi
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Devina Chaturvedi .
Editor information
Editors and affiliations.
#6104, Indian School of Business, Hyderabad, Telangana, India
Abhishek Kathuria
Chinese University of Hong Kong, Sha Tin District, Hong Kong
Prasanna P. Karhade
University of North Carolina at Charlotte, Charlotte, NC, USA
Indian School of Business, Hyderabad, Telangana, India
Rights and permissions
Reprints and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper.
Jha, S., Chaturvedi, D. (2024). Systematic Literature Review of Cloud Computing Research Between 2010 and 2023. In: Kathuria, A., Karhade, P.P., Zhao, K., Chaturvedi, D. (eds) Digital Transformation in the Viral Age. WeB 2022. Lecture Notes in Business Information Processing, vol 508. Springer, Cham. https://doi.org/10.1007/978-3-031-60003-6_5
Download citation
DOI : https://doi.org/10.1007/978-3-031-60003-6_5
Published : 21 May 2024
Publisher Name : Springer, Cham
Print ISBN : 978-3-031-60002-9
Online ISBN : 978-3-031-60003-6
eBook Packages : Computer Science Computer Science (R0)
Share this paper
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research
Advances, Systems and Applications

- Search by keyword
- Search by citation
Page 1 of 14
Topic and knowledge-enhanced modeling for edge-enabled IoT user identity linkage across social networks
The Internet of Things (IoT) devices spawn growing diverse social platforms and online data at the network edge, propelling the development of cross-platform applications. To integrate cross-platform data, use...
- View Full Text
Privacy-preserving sports data fusion and prediction with smart devices in distributed environment
With the rapid advancement of sports analytics and fan engagement technologies, the volume and diversity of physique data generated by smart devices across various distributed sports platforms have grown signi...
Quantum support vector machine for forecasting house energy consumption: a comparative study with deep learning models
The Smart Grid operates autonomously, facilitating the smooth integration of diverse power generation sources into the grid, thereby ensuring a continuous, reliable, and high-quality supply of electricity to e...
Enhancing multimedia management: cloud-based movie type recognition with hybrid deep learning architecture
Film and movie genres play a pivotal role in captivating relevant audiences across interactive multimedia platforms. With a focus on entertainment, streaming providers are increasingly prioritizing the automat...
MTG_CD: Multi-scale learnable transformation graph for fault classification and diagnosis in microservices
The rapid advancement of microservice architecture in the cloud has led to the necessity of effectively detecting, classifying, and diagnosing run failures in microservice applications. Due to the high dynamic...
Recognizing online video genres using ensemble deep convolutional learning for digital media service management
It's evident that streaming services increasingly seek to automate the generation of film genres, a factor profoundly shaping a film's structure and target audience. Integrating a hybrid convolutional network ...
A bizarre synthesized cascaded optimized predictor (BizSCOP) model for enhancing security in cloud systems
Due to growing network data dissemination in cloud, the elasticity, pay as you go options, globally accessible facilities, and security of networks have become increasingly important in today's world. Cloud se...
STAM-LSGRU: a spatiotemporal radar echo extrapolation algorithm with edge computing for short-term forecasting
With the advent of Mobile Edge Computing (MEC), shifting data processing from cloud centers to the network edge presents an advanced computational paradigm for addressing latency-sensitive applications. Specif...
Constrained optimal grouping of cloud application components
Cloud applications are built from a set of components often deployed as containers, which can be deployed individually on separate Virtual Machines (VMs) or grouped on a smaller set of VMs. Additionally, the a...
Students health physique information sharing in publicly collaborative services over edge-cloud networks
Data privacy is playing a vital role while facing the digital life aspects. Today, the world is being extensively inter-connected through the internet of things (IoT) technologies. This huge interconnectivity ...
Efficient and secure privacy protection scheme and consensus mechanism in MEC enabled e-commerce consortium blockchain
The application of blockchain technology to the field of e-commerce has solved many dilemmas, such as low transparency of transactions, hidden risks of data security and high payment costs. Mobile edge computi...
A mobile edge computing-focused transferable sensitive data identification method based on product quantization
Sensitive data identification represents the initial and crucial step in safeguarding sensitive information. With the ongoing evolution of the industrial internet, including its interconnectivity across variou...
Blockchain-based 6G task offloading and cooperative computing resource allocation study
In the upcoming era of 6G, the accelerated development of the Internet of Everything and high-speed communication is poised to provide people with an efficient and intelligent life experience. However, the exp...
Deep Reinforcement Learning techniques for dynamic task offloading in the 5G edge-cloud continuum
The integration of new Internet of Things (IoT) applications and services heavily relies on task offloading to external devices due to the constrained computing and battery resources of IoT devices. Up to now,...
Enhancing patient healthcare with mobile edge computing and 5G: challenges and solutions for secure online health tools
Patient-focused healthcare applications are important to patients because they offer a range of advantages that add value and improve the overall healthcare experience. The 5G networks, along with Mobile Edge ...
Online dynamic multi-user computation offloading and resource allocation for HAP-assisted MEC: an energy efficient approach
Nowadays, the paradigm of mobile computing is evolving from a centralized cloud model towards Mobile Edge Computing (MEC). In regions without ground communication infrastructure, incorporating aerial edge comp...
Enhancing lung cancer diagnosis with data fusion and mobile edge computing using DenseNet and CNN
The recent advancements in automated lung cancer diagnosis through the application of Convolutional Neural Networks (CNN) on Computed Tomography (CT) scans have marked a significant leap in medical imaging and...
Cross-chain asset trading scheme for notaries based on edge cloud storage
Blockchain has penetrated in various fields, such as finance, healthcare, supply chain, and intelligent transportation, but the value exchange between different blockchains limits their expansion. Cross-chain ...
An overview of QoS-aware load balancing techniques in SDN-based IoT networks
Increasing and heterogeneous service demands have led to traffic increase, and load imbalance challenges among network entities in the Internet of Things (IoT) environments. It can affect Quality of Service (Q...
MSCO: Mobility-aware Secure Computation Offloading in blockchain-enabled Fog computing environments
Fog computing has evolved as a promising computing paradigm to support the execution of latency-sensitive Internet of Things (IoT) applications. The mobile devices connected to the fog environment are resource...
Correction to: Edge intelligence‑assisted animation design with large models: a survey
The original article was published in Journal of Cloud Computing 2024 13 :48
Provably secure data selective sharing scheme with cloud-based decentralized trust management systems
The smart collection and sharing of data is an important part of cloud-based systems, since huge amounts of data are being created all the time. This feature allows users to distribute data to particular recip...
Stacked-CNN-BiLSTM-COVID: an effective stacked ensemble deep learning framework for sentiment analysis of Arabic COVID-19 tweets
Social networks are popular for advertising, idea sharing, and opinion formation. Due to COVID-19, coronavirus information disseminated on social media affects people’s lives directly. Individuals sometimes ma...
Traffic prediction for diverse edge IoT data using graph network
More researchers are proposing artificial intelligence algorithms for Internet of Things (IoT) devices and applying them to themes such as smart cities and smart transportation. In recent years, relevant resea...
Predicting UPDRS in Parkinson’s disease using ensembles of self-organizing map and neuro-fuzzy
Parkinson's Disease (PD) is a complex, degenerative disease that affects nerve cells that are responsible for body movement. Artificial Intelligence (AI) algorithms are widely used to diagnose and track the pr...
A cloud-edge computing architecture for monitoring protective equipment
The proper use of protective equipment is very important to avoid fatalities. One sector in which this has a great impact is that of construction sites, where a large number of workers die each year. In this s...
A cloud-edge collaborative task scheduling method based on model segmentation
With the continuous development and combined application of cloud computing and artificial intelligence, some new methods have emerged to reduce task execution time for training neural network models in a clou...
Analysis and prediction of virtual machine boot time on virtualized computing environments
Starting a virtual machine (VM) is a common operation in cloud computing platforms. In order to achieve better management of resource provisioning, a cloud platform needs to accurately estimate the VM boot tim...
IoT workload offloading efficient intelligent transport system in federated ACNN integrated cooperated edge-cloud networks
Intelligent transport systems (ITS) provide various cooperative edge cloud services for roadside vehicular applications. These applications offer additional diversity, including ticket validation across transp...
Intelligent code search aids edge software development
The growth of multimedia applications poses new challenges to software facilities in edge computing. Developers must effectively develop edge computing software to accommodate the rapid expansion of multimedia...
Correction to: Advanced series decomposition with a gated recurrent unit and graph convolutional neural network for non‑stationary data patterns
The original article was published in Journal of Cloud Computing 2024 13 :20
PMNet: a multi-branch and multi-scale semantic segmentation approach to water extraction from high-resolution remote sensing images with edge-cloud computing
In the field of remote sensing image interpretation, automatically extracting water body information from high-resolution images is a key task. However, facing the complex multi-scale features in high-resoluti...
Correction: FLM-ICR: a federated learning model for classification of internet of vehicle terminals using connection records
The original article was published in Journal of Cloud Computing 2024 13 :57
CG-PBFT: an efficient PBFT algorithm based on credit grouping
Because of its excellent properties of fault tolerance, efficiency and availability, the practical Byzantine fault tolerance (PBFT) algorithm has become the mainstream consensus algorithm in blockchain. Howeve...
Time-aware outlier detection in health physique monitoring in edge-aided sport education decision-makings
The increasing popularity of various intelligent sensor and mobile communication technologies has enabled quick health physique sensing, monitoring, collection and analyses of students, which significantly pro...
Accurate and fast congestion feedback in MEC-enabled RDMA datacenters
Mobile edge computing (MEC) is a novel computing paradigm that pushes computation and storage resources to the edge of the network. The interconnection of edge servers forms small-scale data centers, enabling ...
Optimus: association-based dynamic system call filtering for container attack surface reduction
While container adoption has witnessed significant growth in facilitating the operation of large-scale applications, this increased attention has also attracted adversaries who exploit numerous vulnerabilities...
A secure cross-domain authentication scheme based on threshold signature for MEC
The widespread adoption of fifth-generation mobile networks has spurred the rapid advancement of mobile edge computing (MEC). By decentralizing computing and storage resources to the network edge, MEC signific...
Edge intelligence empowered delivery route planning for handling changes in uncertain supply chain environment
Traditional delivery route planning faces challenges in reducing logistics costs and improving customer satisfaction with growing customer demand and complex road traffic, especially in uncertain supply chain ...
Security issues of news data dissemination in internet environment
With the rise of artificial intelligence and the development of social media, people's communication is more convenient and convenient. However, in the Internet environment, the untrue dissemination of news da...
Short-term forecasting of surface solar incident radiation on edge intelligence based on AttUNet
Solar energy has emerged as a key industry in the field of renewable energy due to its universality, harmlessness, and sustainability. Accurate prediction of solar radiation is crucial for optimizing the econo...
Edge computing-oriented smart agricultural supply chain mechanism with auction and fuzzy neural networks
Powered by data-driven technologies, precision agriculture offers immense productivity and sustainability benefits. However, fragmentation across farmlands necessitates distributed transparent automation. We d...

AIoT-driven multi-source sensor emission monitoring and forecasting using multi-source sensor integration with reduced noise series decomposition
The integration of multi-source sensors based AIoT (Artificial Intelligence of Things) technologies into air quality measurement and forecasting is becoming increasingly critical in the fields of sustainable a...
An integrated SDN framework for early detection of DDoS attacks in cloud computing
Cloud computing is a rapidly advancing technology with numerous benefits, such as increased availability, scalability, and flexibility. Relocating computing infrastructure to a network simplifies hardware and ...
An optimized neural network with AdaHessian for cryptojacking attack prediction for Securing Crypto Exchange Operations of MEC applications
Bitcoin exchange security is crucial because of MEC's widespread use. Cryptojacking has compromised MEC app security and bitcoin exchange ecosystem functionality. This paper propose a cutting-edge neural netwo...
Privacy-preserving federated learning based on partial low-quality data
Traditional machine learning requires collecting data from participants for training, which may lead to malicious acquisition of privacy in participants’ data. Federated learning provides a method to protect p...
A secure data interaction method based on edge computing
Deep learning achieves an outstanding success in the edge scene due to the appearance of lightweight neural network. However, a number of works show that these networks are vulnerable for adversarial examples,...
TCP Stratos for stratosphere based computing platforms
Stratosphere computing platforms (SCPs) benefit from free cooling but face challenges necessitating transmission control protocol (TCP) re-design. The redesign should be considered due to stratospheric gravity...
Optimizing the resource allocation in cyber physical energy systems based on cloud storage and IoT infrastructure
Given the prohibited operating zones, losses, and valve point effects in power systems, energy optimization analysis in such systems includes numerous non-convex and non-smooth parameters, such as economic dis...
SRA-E-ABCO: terminal task offloading for cloud-edge-end environments
The rapid development of the Internet technology along with the emergence of intelligent applications has put forward higher requirements for task offloading. In Cloud-Edge-End (CEE) environments, offloading c...
- Editorial Board
- Sign up for article alerts and news from this journal
Annual Journal Metrics
2022 Citation Impact 4.0 - 2-year Impact Factor 4.4 - 5-year Impact Factor 1.711 - SNIP (Source Normalized Impact per Paper) 0.976 - SJR (SCImago Journal Rank)
2023 Speed 10 days submission to first editorial decision for all manuscripts (Median) 116 days submission to accept (Median)
2023 Usage 733,672 downloads 49 Altmetric mentions
- More about our metrics
- ISSN: 2192-113X (electronic)
Benefit from our free funding service

We offer a free open access support service to make it easier for you to discover and apply for article-processing charge (APC) funding.
Learn more here
Accepted papers
We have 40 papers accepted tentatively for socc 2023. paper title, content, and even the acceptance decision may change during the shepherding process. the detailed program is coming up soon., plexus: optimizing join approximation for geo-distributed data analytics, - joel wolfrath, abhishek chandra (university of minnesota), carbon containers: a system-level facility for managing application-level carbon emissions, - john thiede (university of massachusetts - amherst); noman bashir (university of massachusetts amherst); david irwin (university of massachusetts, amherst), prashant shenoy, golgi: performance-aware, resource-efficient function scheduling for serverless computing, - suyi li, wei wang (hong kong university of science and technology); jun yang, guangzhen chen, daohe lu (webank), lifting the fog of uncertainties: dynamic resource orchestration for the containerized cloud, - yuqiu zhang, tongkun zhang, gengrui zhang, hans-arno jacobsen (university of toronto), oblivious paxos: privacy-preserving consensus over secret-shares, - fadhil i. kurnia, arun venkataramani (university of massachusetts amherst), maximizing vms' io performance on overcommitted cpus with fairness, - tong xing, cong xiong (the university of edinburgh); chuan ye, qi wei, javier picorel (huawei); antonio barbalace (the university of edinburgh), not all resources are visible: exploiting fragmented shadow resources in shared-state scheduler architecture, - xinkai wang, hao he, yuancheng li, chao li, xiaofeng hou, jing wang, quan chen, jingwen leng, minyi guo (shanghai jiao tong university); leibo wang (huawei technologies co., ltd.), polis: efficient federated learning via scalable client clustering, - jiachen liu, fan lai (university of michigan); yinwei dai (princeton university); aditya akella (ut austin and google); harsha v. madhyastha (university of southern california); mosharaf chowdhury (university of michigan), dissecting overheads of service mesh sidecars, - xiangfeng zhu (university of washington); guozhen she (duke university); bowen xue (university of washington); yu zhang, yongsu zhang, xuan kelvin zou, xiongchun duan, peng he (bytedance inc.); arvind krishnamurthy (university of washington); matthew lentz (duke university and vmware research); danyang zhuo (duke university); ratul mahajan (university of washington, amazon), oneadapt: fast adaptation for deep learning applications via backpropagation, - kuntai du, yuhan liu, yitian hao (university of chicago); qizheng zhang (stanford university); haodong wang (the university of chicago); yuyang huang (university of chicago); ganesh ananthanarayanan (microsoft); junchen jiang (university of chicago), parrotfish: parametric regression for optimizing serverless functions, - arshia moghimi (university of british columbia); joe hattori (the university of tokyo); alexander li (university of british columbia); mehdi ben chikha (national institute of applied sciences and technology (insat)); mohammad shahrad (university of british columbia), a comparison of end-to-end decision forest inference pipelines, - hong guan, saif masood, mahidhar reddy dwarampudi, venkatesh gunda (arizona state university); hong min (ibm t. j. watson research center); lei yu (rensselaer polytechnic institut); soham nag, jia zou (arizona state university), enabling multi-tenancy on ssds with accurate io interference modeling, - lokesh n. jaliminche (university of california, santa cruz); chandranil (nil) chakraborttii (trinity college, hartford, usa); changho choi (samsung semiconductor, inc, usa); heiner litz (university of california, santa cruz), kvsev: a secure in-memory key-value store with secure encrypted virtualization, - junseung you, kyeongryong lee (seoul national university); hyungon moon (unist (ulsan national institute of science and technology)); yeongpil cho (hanyang university); yunheung paek (seoul national university), building gpu tees using cpu secure enclaves with gevisor, - xiaolong wu, dave (jing) tian (purdue university); chung hwan kim (university of texas at dallas), maximizing the utilization of gpus used by cloud gaming through adaptive co-location with combo, - binghao chen, han zhao, weihao cui, yifu he, shulai zhang, quan chen, zijun li, minyi guo (shanghai jiao tong university), asyfunc: a high-performance and resource-efficient serverless inference system via asymmetric functions, - qiangyu pei, yongjie yuan, haichuan hu (school of computer science and technology, huazhong university of science and technology); qiong chen (huawei); fangming liu (peng cheng laboratory & huazhong university of science and technology), fledge: simplifying topology extension in federated learning, - harshit daga (georgia institute of technology); jaemin shin (kaist); dhruv garg (georgia institute of technology); ada gavrilovska (georgia tech); myungjin lee, ramana rao kompella (cisco systems), tmc: near-optimal resource allocation for tiered-memory systems, - yuanjiang ni (alibaba group); pankaj mehra (elephance memory, inc.); ethan miller (pure storage / university of california, santa cruz); heiner litz (university of california, santa cruz), user disengagement-oriented target enforcement for multi-tenant database systems, - ning li (dept. of computer science and engineering, university of texas at arlington, usa); hong jiang (ut arlington); hao che (department of computer science and engineering, the university of texas at arlington); zhijun wang (university of texas at arlington); minh q. nguyen (faculty of it, ho chi minh city university of transport, vietnam); stoddard rosenkrantz (the university of texas at arlington), anticipatory resource allocation for ml training clusters, - tapan chugh (university of washington); srikanth kandula (microsoft); arvind krishnamurthy (university of washington); ratul mahajan (university of washington, amazon); ishai menache (microsoft), 𝜇conadapter: reinforcement learning-based fast concurrency adaptation for microservices in the cloud, - jianshu liu (louisiana state university); shungeng zhang (augusta university); qingyang wang (louisiana state university), filescale: fast and elastic metadata management for distributed file systems, - gang liao (university of maryland); daniel abadi (university of maryland, college park), helios: hardware-assisted high-performance security extension for cloud networking, - myoungsung you (kaist); jaehyun nam (dankook university); minjae seo, seungwon shin (kaist), latenseer: causal modeling of end-to-end latency distribution by harnessing distributed tracing, - yazhuo zhang (emory university); rebecca isaacs (amazon web services); yao yue (pelican foundation); juncheng yang (carnegie mellon university); lei zhang (princeton university); ymir vigfusson (emory university), cryonics: trustworthy function-as-a-service using snapshot-based enclaves, - seong-joong kim (the affiliated institute of etri, kaist); myoungsung you (kaist); byung joon kim (the affiliated institute of etri); seungwon shin (kaist), cameo: a causal transfer learning approach for performance optimization of configurable computer systems, - md shahriar iqbal (university of south carolina); ziyuan zhong (columbia university); iftakhar ahmad (university of south carolina); baishakhi ray (columbia university); pooyan jamshidi (university of south carolina), yama: providing performance isolation for black-box offloads, - tao ji, divyanshu saxena (the university of texas at austin); brent stephens (university of utah); aditya akella (ut austin and google), chitu: accelerating serverless workflows with asynchronous state replication pipeline, - zhengyu lei (institute of computing technology, chinese academy of sciences; university of chinese academy of sciences); xiao shi (institute of computing technology, chinese academy of sciences; nanjing institute of inforsuperbahn); cunchi lv, xiaobing yu, xiaofang zhao (institute of computing technology, chinese academy of sciences; university of chinese academy of sciences), towards gpu memory efficiency for distributed training at scale, - runxiang cheng (university of illinois urbana-champaign); chris cai, selman yilmaz, rahul mitra, malay bag, mrinmoy ghosh (meta platforms, inc.); tianyin xu (university of illinois urbana-champaign), gödel: unified large-scale resource management and scheduling at bytedance, - wu xiang (bytedance); yakun li (bytedance); yuquan ren (bytedance); fan jiang, chaohui xin, varun gupta, chao xiang (bytedance); xinyi song (bytedance); meng liu, bing li, kaiyang shao, chen xu, wei shao (bytedance); yuqi fu (george mason university); wilson wang, cong xu (bytedance); wei xu (bytedance); caixue lin, rui shi (bytedance); yuming liang (bytedance), disaggregating ml input data processing at scale, - andrew audibert, yang chen (google); dan-ovidiu graur, ana klimovic (eth zurich); jiri simsa, chandramohan a. thekkath (google), how does it function characterizing long-term trends in production serverless workloads, - artjom joosen, ahmed hassan, luke darlow, martin asenov, wang jianfeng, rajkarn singh (huawei); adam barker (huawei / university of st andrews), function as a function, - tom kuchler, michael giardino, timothy roscoe, ana klimovic (eth zurich), metaverse as a service: megascale social 3d on the cloud, - andreas haeberlen, linh thi xuan phan (roblox / university of pennsylvania); morgan mcguire (roblox), the gap between serverless research and real-world systems, - qingyuan liu, dong du, yubin xia (shanghai jiao tong university); ping zhang (huawei cloud); haibo chen (shanghai jiao tong university), is machine learning necessary for cloud resource usage forecasting, - georgia christofidi, konstantinos papaioannou, thaleia dimitra doudali (imdea software institute), sustainable supercomputing for ai: experiences from gpu power capping at hpc scale, - dan zhao (mit); siddharth samsi, joseph mcdonald (mit lincoln laboratory); baolin li (northeastern university); michael jones, david bestor (mit lincoln laboratory); devesh tiwari (northeastern university); vijay gadepally (mit lincoln laboratory), work-in progress, multivariate anomaly detection with domain clustering, - frederic boesel, livio schläpfer (ibm research zurich research lab); h. pozidis (ibm research gmbh, switzerland); mitch gusat (ibm research zurich research lab), online profiling and adaptation of quality sensitivity for internet video, - yihua cheng (university of chicago); hui zhang (conviva); junchen jiang (university of chicago).
IEEE Conferences
- Symposium on Distributed Computing Continuum (DCC)
- Call for Papers
- Organizing Committee
IEEE CLOUD 2023
IEEE INTERNATIONAL CONFERENCE ON CLOUD COMPUTING
Hybrid event
Chicago, Illinois USA
Hyatt Regency Chicago
July 2-8, 2023

About IEEE Cloud 2023
The IEEE International Conference on Cloud Computing (CLOUD) has been a prime international forum for both researchers and industry practitioners to exchange the latest fundamental advances in the state of the art and practice of cloud computing, identify emerging research topics, and define the future of cloud computing. All topics regarding cloud computing align with the theme of CLOUD. In 2023, we will gather to strive to advance the largest international professional forum on cloud computing.
About IEEE SERVICES 2023
SERVICES 2023 is solely sponsored by the IEEE Computer Society under the auspice of the Technical Community on Services Computing (TCSVC). The scope of SERVICES 2023 covers all aspects of services computing and applications, current or emerging. Centered around services computing, SERVICES 2023 covers various systems and networking research pertaining to cloud, edge and Internet-of Things (IoT), as well as technologies for intelligent computing, learning, Big Data and blockchain applications, addressing critical issues such as knowledge network, high performance, security, privacy, dependability, trustworthiness, and cost-effectiveness. Particularly, the 2023 Congress will welcome papers on the aftermath and the impact of COVID-19 on services and the world infrastructure. In addition to co-located theme-topic conferences, the Congress will also include symposia and workshops supporting deep-dive discussions on emerging important topics, and complement the SERVICES 2023 program with industry and application presentations and panels. Authors are invited to prepare early and submit original papers to any of these conferences at www.easychair.org. All submitted manuscripts will be peer-reviewed by at least three reviewers. Accepted and presented papers will appear in the conference proceedings published by the IEEE Computer Society Press. SERVICES 2023 is the only premier professional event for the services computing field offered by IEEE.
Important Dates for 2023 (AOE)
December 1, 2022: EasyChair open for DRAFT submissions UPDATED: March 25, 2023: EasyChair closes for submissions (e.g., HARD submission deadline) UPDATED: May 8, 2023: Acceptance notification UPDATED: Camera-ready due: June 5, 2023 July 2-8, 2023: SERVICES Congress in Chicago
To contact CLOUD organizers, please send an email to [email protected]
About IEEE and IEEE Computer Society
IEEE is the world’s largest professional association advancing innovation and technological excellence for the benefit of humanity. IEEE and its members inspire a global community to innovate for a better tomorrow through its highly cited publications, conferences, technology standards, and professional and educational activities. IEEE is the trusted voice for engineering, computing and technology information around the globe.
With nearly 85,000 members, the IEEE Computer Society (CS) is the world’s leading organization of computing professionals. Founded in 1946, and the largest of the 38 societies of the Institute of Electrical and Electronics Engineers (IEEE), the CS is dedicated to advancing the theory and application of computer and information-processing technology.
About the Technical Community on Services Computing (TCSVC)
Founded in 2003, IEEE Computer Society's Technical Community on Services Computing (TCSVC) is a multidisciplinary group whose purpose is to advance and coordinate work in the field of Services Computing carried out throughout the IEEE in scientific, engineering, standard, literary and educational areas. IEEE TCSVC membership details are available at http://tab.computer.org/tcsvc/
The Fourteenth International Conference on Cloud Computing, GRIDs, and Virtualization
Cloud computing 2023, june 26, 2023 to june 30, 2023 - nice, saint-laurent-du-var, france.
Deadlines differ for special tracks. Please consult the conference home page for special tracks Call for Papers (if any).

CLOUD COMPUTING 2023 - The Fourteenth International Conference on Cloud Computing, GRIDs, and Virtualization
June 26, 2023 - June 30, 2023
Cloud computing is a normal evolution of distributed computing combined with Service-oriented architecture, leveraging most of the GRID features and Virtualization merits. The technology foundations for cloud computing led to a new approach of reusing what was achieved in GRID computing with support from virtualization.
CLOUD COMPUTING 2023 is intended as an event to prospect the applications supported by the new paradigm and validate the techniques and the mechanisms. A complementary target is to identify the open issues and the challenges to fix them, especially on security, privacy, and inter- and intra-clouds protocols.
We solicit both academic, research, and industrial contributions. We welcome technical papers presenting research and practical results, position papers addressing the pros and cons of specific proposals, such as those being discussed in the standard fora or in industry consortia, survey papers addressing the key problems and solutions on any of the above topics short papers on work in progress, and panel proposals.
Industrial presentations are not subject to the format and content constraints of regular submissions. We expect short and long presentations that express industrial position and status.
Tutorials on specific related topics and panels on challenging areas are encouraged.
The topics suggested by the conference can be discussed in term of concepts, state of the art, research, standards, implementations, running experiments, applications, and industrial case studies. Authors are invited to submit complete unpublished papers, which are not under review in any other conference or journal in the following, but not limited to, topic areas.
All topics and submission formats are open to both research and industry contributions.
CLOUD COMPUTING 2023 conference tracks:
TRENDS: New trends
Fog-computing; Mobile Edge Computing; Cloudlets; Hosted Cloud services (WebRTC, Containers, Cloud micro-services); Cloud computing and SDN/NFV; Cloud computing and 5G; Cloud computing and LTE Pro 4.5; Cloud computing ad Big Data; High performance computing (HPC) in the Cloud; Superfluid Clouds; Mobile Apps to the public Clouds; Vehicular Cloud networks; Cloud orchestration features; Converged edge systems; Cloud federation; Micro-cloud provider federation; Open-implementation Cloud infrastructures; Untrusted Cloud environments; Multiple Clouds and data centers; Power Constrained VMs; Cloud Green abstraction layer; Managing applications in the clouds (CloudOps)
CLOUD: Cloud computing
Cloud economics; Core cloud services; Cloud technologies; Cloud computing; On-demand computing models; Hardware-as-a-service; Software-as-a-service [SaaS applications]; Platform-as-service; Storage as a service in cloud; Data-as-a-Service; Service-oriented architecture (SOA); Cloud computing programming and application development; Scalability, discovery of services and data in Cloud computing infrastructures; Trust and clouds; Client-cloud computing challenges; Geographical constraints for deploying clouds
CLOUD: Challenging features
Privacy, security, ownership and reliability issues; Performance and QoS; Dynamic resource provisioning; Power-efficiency and Cloud computing; Load balancing; Application streaming; Cloud SLAs; Business models and pricing policies; Cloud service subscription models; Cloud standardized SLA; Cloud-related privacy; Cloud-related control; Managing applications in the clouds; Mobile clouds; Roaming services in Clouds; Agent-based cloud computing; Cloud brokering; Cloud contracts (machine readable); Cloud security; Security and assurance properties in cloud environments; Big Data Analytics in clouds; Cloud computing back-end solutions; Cloud applications portability; Cloud-native application design; Security by design for cloud services; Data privacy guarantee at run-time
CLOUD: Platforms, Infrastructures and Applications
Custom platforms; Large-scale compute infrastructures; Data centers; Processes intra- and inter-clouds; Content and service distribution in Cloud computing infrastructures; Multiple applications can run on one computer (virtualization a la VMWare); Grid computing (multiple computers can be used to run one application); Cloud-computing vendor governance and regulatory compliance; Enterprise clouds; Enterprise-centric cloud computing; Interaction between vertical clouds; Public, Private, and Hybrid clouds; Cloud computing testbeds
GRID: Grid networks, services and applications
GRID theory, frameworks, methodologies, architecture, ontology; GRID infrastructure and technologies; GRID middleware; GRID protocols and networking; GRID computing, utility computing, autonomic computing, metacomputing; Programmable GRID; Data GRID; Context ontology and management in GRIDs; Distributed decisions in GRID networks; GRID services and applications; Virtualization, modeling, and metadata in GRID; Resource management, scheduling, and scalability in GRID; GRID monitoring, control, and management; Traffic and load balancing in GRID; User profiles and priorities in GRID; Performance and security in GRID systems; Fault tolerance, resilience, survivability, robustness in GRID; QoS/SLA in GRID networks; GRID fora, standards, development, evolution; GRID case studies, validation testbeds, prototypes, and lessons learned
VIRTUALIZATION: Computing in virtualization-based environments
Principles of virtualization; Virtualization platforms; Thick and thin clients; Data centers and nano-centers; Open virtualization format; Orchestration of virtualization across data centers; Dynamic federation of compute capacity; Dynamic geo-balancing; Instant workload migration; Virtualization-aware storage; Virtualization-aware networking; Virtualization embedded-software-based smart mobile phones; Trusted platforms and embedded supervisors for security; Virtualization management operations /discovery, configuration, provisioning, performance, etc.; Energy optimization and saving for green datacenters; Virtualization supporting cloud computing; Applications as pre-packaged virtual machines; Licensing and support policies
INSTRUCTION FOR THE AUTHORS
Authors of selected papers will be invited to submit extended versions to one of the IARIA Journals .
Publisher: XPS (Xpert Publishing Services) Archived: ThinkMind TM Digital Library (free access) Prints available at Curran Associates, Inc. How to submit to appropriate indexes .
Only .pdf or .doc files will be accepted for paper submission. All received submissions will be acknowledged via an automated system.
Contribution types
- regular papers [in the proceedings, digital library]
- short papers (work in progress) [in the proceedings, digital library]
- ideas: two pages [in the proceedings, digital library]
- extended abstracts: two pages [in the proceedings, digital library]
- posters: two pages [in the proceedings, digital library]
- posters: slide only [slide-deck posted on www.iaria.org ]
- presentations: slide only [slide-deck posted on www.iaria.org ]
- demos: two pages [posted on www.iaria.org ]
Final author manuscripts will be 8.5" x 11", not exceeding 6 pages; max 4 extra pages allowed at additional cost. Helpful information for paper formatting can be found here . Latex templates are also available.
Slides-based contributions can use the corporate/university format and style.
Your paper should also comply with the additional editorial rules .
Once you receive the notification of contribution acceptance, you will be provided by the publisher an online author kit with all the steps an author needs to follow to submit the final version. The author kits URL will be included in the letter of acceptance.
We would recommend that you should not use too many extra pages, even if you can afford the extra fees. No more than 2 contributions per event are recommended, as each contribution must be separately registered and paid for. At least one author of each accepted paper must register to ensure that the paper will be included in the conference proceedings and in the digital library, or posted on the www.iaria.org (for slide-based contributions).
CONTRIBUTION TYPE
Regular Papers (up to 6-10 page article -6 pages covered the by regular registration; max 4 extra pages allowed at additional cost- ) (oral presentation) These contributions could be academic or industrial research, survey, white, implementation-oriented, architecture-oriented, white papers, etc. They will be included in the proceedings, posted in the free-access ThinkMind digital library and sent for indexing. Please submit the contributions following the instructions for the regular submissions using the "Submit a Paper" button and selecting the appropriate contribution type. 12-14 presentation slides are suggested.
Short papers (work in progress) (up to 4 pages long) (oral presentation) Work-in-progress contributions are welcome. These contributions represent partial achievements of longer-term projects. They could be academic or industrial research, survey, white, implementation-oriented, architecture-oriented, white papers, etc. Please submit the contributions following the instructions for the regular submissions using the "Submit a Paper" button and selecting the contribution type as work in progress. Contributors must follow the conference deadlines, describing early research and novel skeleton ideas in the areas of the conference topics. The work will be published in the conference proceedings, posted in the free-access ThinkMind digital library and sent for indexing. For more details, see the Work in Progress explanation page. 12-14 presentation slides are suggested.
Ideas contributions (2 pages long) (oral presentation) This category is dedicated to new ideas in their very early stage. Idea contributions are expression of yet to be developed approaches, with pros/cons, not yet consolidated. Ideas contributions are intended for a debate and audience feedback. Please submit the contributions following the instructions for the regular submissions using the "Submit a Paper" button and selecting the contribution type as Idea. Contributors must follow the conference deadlines, describing early research and novel skeleton ideas in the areas of the conference topics. The work will be published in the conference proceedings, posted in the free-access ThinkMind digital library and sent for indexing. For more details, see the Ideas explanation page. 12-14 presentation slides are suggested.
Extended abstracts (2 pages long) (oral presentation) Extended abstracts summarize a long potential publication with noticeable results. It is intended for sharing yet to be written, or further on intended for a journal publication. Please submit the contributions following the instructions for the regular submissions using the "Submit a Paper" button and selecting the contribution type as Extended abstract. Contributors must follow the conference deadlines, describing early research and novel skeleton ideas in the areas of the conference topics. The work will be published in the conference proceedings, posted in the free-access ThinkMind digital library and sent for indexing. 12-14 presentation slides are suggested.
Posters (paper-based, two pages long) (oral presentation) Posters are intended for ongoing research projects, concrete realizations, or industrial applications/projects presentations. The poster may be presented during sessions reserved for posters, or mixed with presentation of articles of similar topic. A two-page paper summarizes a presentation intended to be a POSTER. This allows an author to summarize a series of results and expose them via a big number of figures, graphics and tables. Please submit the contributions following the instructions for the regular submissions using the "Submit a Paper" button and selecting the contribution type as Poster Two Pages. Contributors must follow the conference deadlines, describing early research and novel skeleton ideas in the areas of the conference topics. The work will be published in the conference proceedings, posted in the free-access ThinkMind digital library and sent for indexing. 8-10 presentation slides are suggested. Also a big Poster is suitable, used for live discussions with the attendees, in addition to the oral presentation.
Posters (slide-based, only) (oral presentation) Posters are intended for ongoing research projects, concrete realizations, or industrial applications/projects presentations. The poster may be presented during sessions reserved for posters, or mixed with presentation of articles of similar topic. The slides must have comprehensive comments. This type of contribution only requires a 8-10 slide-deck. Please submit the contributions following the instructions for the regular submissions using the "Submit a Paper" button and selecting the contribution type as Poster (slide-only). The slide-deck will be posted, post-event, on www.iaria.org . 8-10 presentation slides are suggested. Also a big Poster is suitable, used for live discussions with the attendees, additionally to the oral presentation.
Presentations (slide-based, only) (oral presentation) These contributions represent technical marketing/industrial/business/positioning presentations. This type of contribution only requires a 12-14 slide-deck. Please submit the contributions following the submission instructions by using the "Submit a Paper" button and selecting the contribution type as Presentation (slide-only). The slide-deck will be posted, post-event, on www.iaria.org . 12-14 presentation slides are suggested.
Demos (two pages) [posted on www.iaria.org ] Demos represent special contributions where a tool, an implementation of an application, or a freshly implemented system is presented in its alfa/beta version. It might also be intended for thsoe new application to gather the attendee opinion. A two-page summary for a demo is intended to be. It would be scheduled in special time spots, to ensure a maximum attendance from the participants. Please submit the contributions following the submission instructions by using the "Submit a Paper" button and selecting the contribution type as Demos. The Demos paper will be posted, post-event, on www.iaria.org .
Tutorial proposals Tutorials provide overviews of current high interest topics. Proposals should be for 2-3 hour long. Proposals must contain the title, the summary of the content, and the biography of the presenter(s). The tutorial slide decks will be posted on the IARIA site. Please send your proposals to tutorial proposal
Panel proposals The organizers encourage scientists and industry leaders to organize dedicated panels dealing with controversial and challenging topics and paradigms. Panel moderators are asked to identify their guests and manage that their appropriate talk supports timely reach our deadlines. Moderators must specifically submit an official proposal, indicating their background, panelist names, their affiliation, the topic of the panel, as well as short biographies. The panel slide deck will be posted on the IARIA site. Please send your proposals to panel proposal

Copyright (c) 2006-2024, IARIA
Cloud computing study 2023

- cloud computing
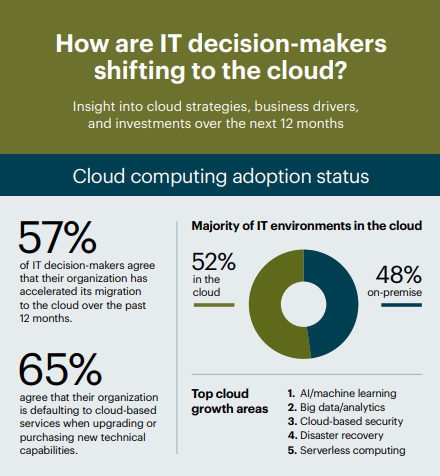
In its 10th year, Foundry’s 2023 Cloud Computing research was conducted to measure cloud computing trends among technology decision-makers, including adoption plans, spending, business drivers, challenges, and top cloud growth areas, such as AI. While cloud adoption is continuing at pace, there are signs that the frenzied activity that took place during and following the pandemic period is easing somewhat. This year’s study found that 57% of organizations have accelerated their cloud migration over the past 12 months, however this was 69% last year.
Organizations recognize the value of cloud computing, as half of IT decision-makers (ITDMs) state that cloud capabilities have helped their organization achieve sustainable revenue growth over the past 12 months. However, adoption and migration do not come without challenges that cloud providers must address. When asked about the biggest obstacles to implementing their cloud strategy, the top three stated by ITDMs are controlling cloud costs, data privacy and security challenges, and lack of cloud security skills/expertise.
Our study explores these challenges in more depth and also highlights what technology buyers need from their current and future cloud providers in order to successfully advance their cloud strategy.
Key takeaways for tech marketers:
- Cloud budgets continue to increase – IT decision-makers report that 31% of their overall IT budget will go towards cloud computing and two-thirds expect their cloud budget to increase in the next 12 months.
- Organizations are defaulting to cloud-based services when upgrading or purchasing new technical capabilities. It’s important to have a grasp on what business objectives are driving these cloud investments.
- IT decision-makers have plans for artificial intelligence and cloud computing, as the majority say AI/ML is the top cloud growth area this year and it is the number one cloud capability ITDMs plan to adopt.
- Due to an increase in cloud investments, organizations have added new cloud roles and functions. Understand their business needs and responsibilities when creating your messaging.
- Despite the benefits organizations see from the cloud, a variety of challenges still get in their way, mostly around cost control, security expertise and a skills gap. Provide solutions to your customers and prospects to combat these challenges.
View the sample slides below for further insights on the cloud computing research:

Click to enlarge
Additional cloud resources.
Cloud tech marketer’s guide

Based on Foundry’s cloud and buyer’s journey research, this guide explores key fundamentals of the purchase process that are necessary to know when marketing cloud services and solutions.
About the research
Foundry’s 2023 Cloud Computing Survey is the 10th year of this research and was conducted to measure cloud computing trends among technology decision-makers including: adoption plans, spending, business drivers, challenges, and top cloud growth areas, such as AI. The study was fielded throughout August 2023 and is based on the responses of 893 global IT decision-makers that are involved in the purchase process for cloud computing and their organization has, or plans to have, at least one application, or a portion of their infrastructure, in the cloud.

How to engage and market to AI-focused buyers

How to engage and market to security buyers

Security priorities: a look ahead
Related content.

Role & Influence of the Technology Decision-Maker white paper 2023
Insights to help tech vendors understand the decisions made around their products and services as they plan their strategies for the future and gain an advantage in this competitive landscape.
By Foundry • Research topic
Jun 15, 2023 • 10 mins

Cloud computing executive summary 2023
Insight into cloud computing trends There has been a massive shift to moving IT environments to the cloud over the past three years as organizations navigated a remote-first world due to the pandemic. According to…
Sep 14, 2023 • 1 mins

State of the CIO Study 2024
Foundry’s 23rd annual State of the CIO research details how the role of the CIO continues to evolve and elevate in today’s business climate and defines the CIO agenda for 2024.
Jan 24, 2024 • 5 mins
green cloud computing Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
Unconstrained Power Management Algorithm for Green Cloud Computing
Green cloud computing-oriented algorithmic approach-based virtual machine consolidation, green-cloud computing (g-cc) data center and its architecture toward efficient usage of energy, a new metaheuristic‐based method for solving the virtual machines migration problem in the green cloud computing, mapping and consolidation of vms using locust-inspired algorithms for green cloud computing, enabling rank-based distribution of microservices among containers for green cloud computing environment, an optimized vm placement approach to reduce energy consumption in green cloud computing, investigation study on secured data communication with blockchain and iot in green cloud computing, energy aware load balancing algorithm for upgraded effectiveness in green cloud computing, study on green cloud computing—a review, export citation format, share document.
For enquiries call:
+1-469-442-0620

- Cloud Computing
Top 10 Cloud Computing Research Topics of 2024
Home Blog Cloud Computing Top 10 Cloud Computing Research Topics of 2024
Cloud computing is a fast-growing area in the technical landscape due to its recent developments. If we look ahead to 2024, there are new research topics in cloud computing that are getting more traction among researchers and practitioners. Cloud computing has ranged from new evolutions on security and privacy with the use of AI & ML usage in the Cloud computing for the new cloud-based applications for specific domains or industries. In this article, we will investigate some of the top cloud computing research topics for 2024 and explore what we get most out of it for researchers or cloud practitioners. To master a cloud computing field, we need to check these Cloud Computing online courses .
Why Cloud Computing is Important for Data-driven Business?
The Cloud computing is crucial for data-driven businesses because it provides scalable and cost-effective ways to store and process huge amounts of data. Cloud-based storage and analytical platform helps business to easily access their data whenever required irrespective of where it is located physically. This helps businesses to take good decisions about their products and marketing plans.
Cloud computing could help businesses to improve their security in terms of data, Cloud providers offer various features such as data encryption and access control to their customers so that they can protect the data as well as from unauthorized access.
Few benefits of Cloud computing are listed below:
- Scalability: With Cloud computing we get scalable applications which suits for large scale production systems for Businesses which store and process large sets of data.
- Cost-effectiveness : It is evident that Cloud computing is cost effective solution compared to the traditional on-premises data storage and analytical solutions due to its scaling capacity which leads to saving more IT costs.
- Security : Cloud providers offer various security features which includes data encryption and access control, that can help businesses to protect their data from unauthorized access.
- Reliability : Cloud providers ensure high reliability to their customers based on their SLA which is useful for the data-driven business to operate 24X7.
Top 10 Cloud Computing Research Topics
1. neural network based multi-objective evolutionary algorithm for dynamic workflow scheduling in cloud computing.
Cloud computing research topics are getting wider traction in the Cloud Computing field. These topics in the paper suggest a multi-objective evolutionary algorithm (NN-MOEA) based on neural networks for dynamic workflow scheduling in cloud computing. Due to the dynamic nature of cloud resources and the numerous competing objectives that need to be optimized, scheduling workflows in cloud computing is difficult. The NN-MOEA algorithm utilizes neural networks to optimize multiple objectives, such as planning, cost, and resource utilization. This research focuses on cloud computing and its potential to enhance the efficiency and effectiveness of businesses' cloud-based workflows.
The algorithm predicts workflow completion time using a feedforward neural network based on input and output data sizes and cloud resources. It generates a balanced schedule by taking into account conflicting objectives and projected execution time. It also includes an evolutionary algorithm for future improvement.
The proposed NN-MOEA algorithm has several benefits, such as the capacity to manage dynamic changes in cloud resources and the capacity to simultaneously optimize multiple objectives. The algorithm is also capable of handling a variety of workflows and is easily expandable to include additional goals. The algorithm's use of neural networks to forecast task execution times is a crucial component because it enables the algorithm to generate better schedules and more accurate predictions.
The paper concludes by presenting a novel multi-objective evolutionary algorithm-based neural network-based approach to dynamic workflow scheduling in cloud computing. In terms of optimizing multiple objectives, such as make span and cost, and achieving a better balance between them, these cloud computing dissertation topics on the proposed NN-MOEA algorithm exhibit encouraging results.
Key insights and Research Ideas:
Investigate the use of different neural network architectures for predicting the future positions of optimal solutions. Explore the use of different multi-objective evolutionary algorithms for solving dynamic workflow scheduling problems. Develop a cloud-based workflow scheduling platform that implements the proposed algorithm and makes it available to researchers and practitioners.
2. A systematic literature review on cloud computing security: threats and mitigation strategies
This is one of cloud computing security research topics in the cloud computing paradigm. The authors then provide a systematic literature review of studies that address security threats to cloud computing and mitigation techniques and were published between 2010 and 2020. They list and classify the risks and defense mechanisms covered in the literature, as well as the frequency and distribution of these subjects over time.
The paper suggests the data breaches, Insider threats and DDoS attack are most discussed threats to the security of cloud computing. Identity and access management, encryption, and intrusion detection and prevention systems are the mitigation techniques that are most frequently discussed. Authors depict the future trends of machine learning and artificial intelligence might help cloud computing to mitigate its risks.
The paper offers a thorough overview of security risks and mitigation techniques in cloud computing, and it emphasizes the need for more research and development in this field to address the constantly changing security issues with cloud computing. This research could help businesses to reduce the amount of spam that they receive in their cloud-based email systems.
Explore the use of blockchain technology to improve the security of cloud computing systems. Investigate the use of machine learning and artificial intelligence to detect and prevent cloud computing attacks. Develop new security tools and technologies for cloud computing environments.
3. Spam Identification in Cloud Computing Based on Text Filtering System
A text filtering system is suggested in the paper "Spam Identification in Cloud Computing Based on Text Filtering System" to help identify spam emails in cloud computing environments. Spam emails are a significant issue in cloud computing because they can use up computing resources and jeopardize the system's security.
To detect spam emails, the suggested system combines text filtering methods with machine learning algorithms. The email content is first pre-processed by the system, which eliminates stop words and stems the remaining words. The preprocessed text is then subjected to several filters, including a blacklist filter and a Bayesian filter, to identify spam emails.
In order to categorize emails as spam or non-spam based on their content, the system also employs machine learning algorithms like decision trees and random forests. The authors use a dataset of emails gathered from a cloud computing environment to train and test the system. They then assess its performance using metrics like precision, recall, and F1 score.
The findings demonstrate the effectiveness of the proposed system in detecting spam emails, achieving high precision and recall rates. By contrasting their system with other spam identification systems, the authors also show how accurate and effective it is.
The method presented in the paper for locating spam emails in cloud computing environments has the potential to improve the overall security and performance of cloud computing systems. This is one of the interesting clouds computing current research topics to explore and innovate. This is one of the good Cloud computing research topics to protect the Mail threats.
Create a stronger spam filtering system that can recognize spam emails even when they are made to avoid detection by more common spam filters. examine the application of artificial intelligence and machine learning to the evaluation of spam filtering system accuracy. Create a more effective spam filtering system that can handle a lot of emails quickly and accurately.
4. Blockchain data-based cloud data integrity protection mechanism
The "Blockchain data-based cloud data integrity protection mechanism" paper suggests a method for safeguarding the integrity of cloud data and which is one of the Cloud computing research topics. In order to store and process massive amounts of data, cloud computing has grown in popularity, but issues with data security and integrity still exist. For the proposed mechanism to guarantee the availability and integrity of cloud data, data redundancy and blockchain technology are combined.
A data redundancy layer, a blockchain layer, and a verification and recovery layer make up the mechanism. For availability in the event of server failure, the data redundancy layer replicates the cloud data across multiple cloud servers. The blockchain layer stores the metadata (such as access rights) and hash values of the cloud data and access control information
Using a dataset of cloud data, the authors assess the performance of the suggested mechanism and compare it to other cloud data protection mechanisms. The findings demonstrate that the suggested mechanism offers high levels of data availability and integrity and is superior to other mechanisms in terms of processing speed and storage space.
Overall, the paper offers a promising strategy for using blockchain technology to guarantee the availability and integrity of cloud data. The suggested mechanism may assist in addressing cloud computing's security issues and enhancing the dependability of cloud data processing and storage. This research could help businesses to protect the integrity of their cloud-based data from unauthorized access and manipulation.
Create a data integrity protection system based on blockchain that is capable of detecting and preventing data tampering in cloud computing environments. For enhancing the functionality and scalability of blockchain-based data integrity protection mechanisms, look into the use of various blockchain consensus algorithms. Create a data integrity protection system based on blockchain that is compatible with current cloud computing platforms. Create a safe and private data integrity protection system based on blockchain technology.
5. A survey on internet of things and cloud computing for healthcare
This article suggests how recent tech trends like the Internet of Things (IoT) and cloud computing could transform the healthcare industry. It is one of the Cloud computing research topics. These emerging technologies open exciting possibilities by enabling remote patient monitoring, personalized care, and efficient data management. This topic is one of the IoT and cloud computing research papers which aims to share a wider range of information.
The authors categorize the research into IoT-based systems, cloud-based systems, and integrated systems using both IoT and the cloud. They discussed the pros of real-time data collection, improved care coordination, automated diagnosis and treatment.
However, the authors also acknowledge concerns around data security, privacy, and the need for standardized protocols and platforms. Widespread adoption of these technologies faces challenges in ensuring they are implemented responsibly and ethically. To begin the journey KnowledgeHut’s Cloud Computing online course s are good starter for beginners so that they can cope with Cloud computing with IOT.
Overall, the paper provides a comprehensive overview of this rapidly developing field, highlighting opportunities to revolutionize how healthcare is delivered. New devices, systems and data analytics powered by IoT, and cloud computing could enable more proactive, preventative and affordable care in the future. But careful planning and governance will be crucial to maximize the value of these technologies while mitigating risks to patient safety, trust and autonomy. This research could help businesses to explore the potential of IoT and cloud computing to improve healthcare delivery.
Examine how IoT and cloud computing are affecting patient outcomes in various healthcare settings, including hospitals, clinics, and home care. Analyze how well various IoT devices and cloud computing platforms perform in-the-moment patient data collection, archival, and analysis. assessing the security and privacy risks connected to IoT devices and cloud computing in the healthcare industry and developing mitigation strategies.
6. Targeted influence maximization based on cloud computing over big data in social networks
Big data in cloud computing research papers are having huge visibility in the industry. The paper "Targeted Influence Maximization based on Cloud Computing over Big Data in Social Networks" proposes a targeted influence maximization algorithm to identify the most influential users in a social network. Influence maximization is the process of identifying a group of users in a social network who can have a significant impact or spread information.
A targeted influence maximization algorithm is suggested in the paper "Targeted Influence maximization based on Cloud Computing over Big Data in Social Networks" to find the most influential users in a social network. The process of finding a group of users in a social network who can make a significant impact or spread information is known as influence maximization.
Four steps make up the suggested algorithm: feature extraction, classification, influence maximization, and data preprocessing. The authors gather and preprocess social network data, such as user profiles and interaction data, during the data preprocessing stage. Using machine learning methods like text mining and sentiment analysis, they extract features from the data during the feature extraction stage. Overall, the paper offers a promising strategy for maximizing targeted influence using big data and Cloud computing research topics to look into. The suggested algorithm could assist companies and organizations in pinpointing their marketing or communication strategies to reach the most influential members of a social network.
Key insights and Research Ideas:
Develop a cloud-based targeted influence maximization algorithm that can effectively identify and influence a small number of users in a social network to achieve a desired outcome. Investigate the use of different cloud computing platforms to improve the performance and scalability of cloud-based targeted influence maximization algorithms. Develop a cloud-based targeted influence maximization algorithm that is compatible with existing social network platforms. Design a cloud-based targeted influence maximization algorithm that is secure and privacy-preserving.
7. Security and privacy protection in cloud computing: Discussions and challenges
Cloud computing current research topics are getting traction, this is of such topic which provides an overview of the challenges and discussions surrounding security and privacy protection in cloud computing. The authors highlight the importance of protecting sensitive data in the cloud, with the potential risks and threats to data privacy and security. The article explores various security and privacy issues that arise in cloud computing, including data breaches, insider threats, and regulatory compliance.
The article explores challenges associated with implementing these security measures and highlights the need for effective risk management strategies. Azure Solution Architect Certification course is suitable for a person who needs to work on Azure cloud as an architect who will do system design with keep security in mind.
Final take away of cloud computing thesis paper by an author points out by discussing some of the emerging trends in cloud security and privacy, including the use of artificial intelligence and machine learning to enhance security, and the emergence of new regulatory frameworks designed to protect data in the cloud and is one of the Cloud computing research topics to keep an eye in the security domain.
Develop a more comprehensive security and privacy framework for cloud computing. Explore the options with machine learning and artificial intelligence to enhance the security and privacy of cloud computing. Develop more robust security and privacy mechanisms for cloud computing. Design security and privacy policies for cloud computing that are fair and transparent. Educate cloud users about security and privacy risks and best practices.
8. Intelligent task prediction and computation offloading based on mobile-edge cloud computing
This Cloud Computing thesis paper "Intelligent Task Prediction and Computation Offloading Based on Mobile-Edge Cloud Computing" proposes a task prediction and computation offloading mechanism to improve the performance of mobile applications under the umbrella of cloud computing research ideas.
An algorithm for offloading computations and a task prediction model makes up the two main parts of the suggested mechanism. Based on the mobile application's usage patterns, the task prediction model employs machine learning techniques to forecast its upcoming tasks. This prediction is to decide whether to execute a specific task locally on the mobile device or offload the computation of it to the cloud.
Using a dataset of mobile application usage patterns, the authors assess the performance of the suggested mechanism and compare it to other computation offloading mechanisms. The findings demonstrate that the suggested mechanism performs better in terms of energy usage, response time, and network usage.
The authors also go over the difficulties in putting the suggested mechanism into practice, including the need for real-time task prediction and the trade-off between offloading computation and network usage. Additionally, they outline future research directions for mobile-edge cloud computing applications, including the use of edge caching and the integration of blockchain technology for security and privacy.
Overall, the paper offers a promising strategy for enhancing mobile application performance through mobile-edge cloud computing. The suggested mechanism might improve the user experience for mobile users while lowering the energy consumption and response time of mobile applications. These Cloud computing dissertation topic leads to many innovation ideas.
Develop an accurate task prediction model considering mobile device and cloud dynamics. Explore machine learning and AI for efficient computation offloading. Create a robust framework for diverse tasks and scenarios. Design a secure, privacy-preserving computation offloading mechanism. Assess computation offloading effectiveness in real-world mobile apps.
9. Cloud Computing and Security: The Security Mechanism and Pillars of ERPs on Cloud Technology
Enterprise resource planning (ERP) systems are one of the Cloud computing research topics in particular face security challenges with cloud computing, and the paper "Cloud Computing and Security: The Security Mechanism and Pillars of ERPs on Cloud Technology" discusses these challenges and suggests a security mechanism and pillars for protecting ERP systems on cloud technology.
The authors begin by going over the benefits of ERP systems and cloud computing as well as the security issues with cloud computing, like data breaches and insider threats. They then go on to present a security framework for cloud-based ERP systems that is built around four pillars: access control, data encryption, data backup and recovery, and security monitoring. The access control pillar restricts user access, while the data encryption pillar secures sensitive data. Data backup and recovery involve backing up lost or failed data. Security monitoring continuously monitors the ERP system for threats. The authors also discuss interoperability challenges and the need for standardization in securing ERP systems on the cloud. They propose future research directions, such as applying machine learning and artificial intelligence to security analytics.
Overall, the paper outlines a thorough strategy for safeguarding ERP systems using cloud computing and emphasizes the significance of addressing security issues related to this technology. Organizations can protect their ERP systems and make sure the Security as well as privacy of their data by implementing these security pillars and mechanisms.
Investigate the application of blockchain technology to enhance the security of cloud-based ERP systems. Look into the use of machine learning and artificial intelligence to identify and stop security threats in cloud-based ERP systems. Create fresh security measures that are intended only for cloud-based ERP systems. By more effectively managing access control and data encryption, cloud-based ERP systems can be made more secure. Inform ERP users about the security dangers that come with cloud-based ERP systems and how to avoid them.
10. Optimized data storage algorithm of IoT based on cloud computing in distributed system
The article proposes an optimized data storage algorithm for Internet of Things (IoT) devices which runs on cloud computing in a distributed system. In IoT apps, which normally generate huge amounts of data by various devices, the algorithm tries to increase the data storage and faster retrials of the same.
The algorithm proposed includes three main components: Data Processing, Data Storage, and Data Retrieval. The Data Processing module preprocesses IoT device data by filtering or compressing it. The Data Storage module distributes the preprocessed data across cloud servers using partitioning and stores it in a distributed database. The Data Retrieval module efficiently retrieves stored data in response to user queries, minimizing data transmission and enhancing query efficiency. The authors evaluated the algorithm's performance using an IoT dataset and compared it to other storage and retrieval algorithms. Results show that the proposed algorithm surpasses others in terms of storage effectiveness, query response time, and network usage.
They suggest future directions such as leveraging edge computing and blockchain technology for optimizing data storage and retrieval in IoT applications. In conclusion, the paper introduces a promising method to improve data archival and retrieval in distributed cloud based IoT applications, enhancing the effectiveness and scalability of IoT applications.
Create a data storage algorithm capable of storing and managing large amounts of IoT data efficiently. Examine the use of cloud computing to improve the performance and scalability of data storage algorithms for IoT. Create a secure and privacy-preserving data storage algorithm. Assess the performance and effectiveness of data storage algorithms for IoT in real-world applications.
How to Write a Perfect Research Paper?
- Choose a topic: Select the topic which is interesting to you so that you can share things with the viewer seamlessly with good content.
- Do your research: Read books, articles, and websites on your topic. Take notes and gather evidence to support your arguments.
- Write an outline: This will help you organize your thoughts and make sure your paper flows smoothly.
- Start your paper: Start with an introduction that grabs the reader's attention. Then, state your thesis statement and support it with evidence from your research. Finally, write a conclusion that summarizes your main points.
- Edit and proofread your paper. Make sure you check the grammatical errors and spelling mistakes.
Cloud computing is a rapidly evolving area with more interesting research topics being getting traction by researchers and practitioners. Cloud providers have their research to make sure their customer data is secured and take care of their security which includes encryption algorithms, improved access control and mitigating DDoS – Deniel of Service attack etc.,
With the improvements in AI & ML, a few features developed to improve the performance, efficiency, and security of cloud computing systems. Some of the research topics in this area include developing new algorithms for resource allocation, optimizing cloud workflows, and detecting and mitigating cyberattacks.
Cloud computing is being used in industries such as healthcare, finance, and manufacturing. Some of the research topics in this area include developing new cloud-based medical imaging applications, building cloud-based financial trading platforms, and designing cloud-based manufacturing systems.
Frequently Asked Questions (FAQs)
Data security and privacy problems, vendor lock-in, complex cloud management, a lack of standardization, and the risk of service provider disruptions are all current issues in cloud computing. Because data is housed on third-party servers, data security and privacy are key considerations. Vendor lock-in makes transferring providers harder and increases reliance on a single one. Managing many cloud services complicates things. Lack of standardization causes interoperability problems and restricts workload mobility between providers.
Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) are the cloud computing scenarios where industries focusing right now.
The six major components of cloud infrastructure are compute, storage, networking, security, management and monitoring, and database. These components enable cloud-based processing and execution, data storage and retrieval, communication between components, security measures, management and monitoring of the infrastructure, and database services.

Vinoth Kumar P
Vinoth Kumar P is a Cloud DevOps Engineer at Amadeus Labs. He has over 7 years of experience in the IT industry, and is specialized in DevOps, GitOps, DevSecOps, MLOps, Chaos Engineering, Cloud and Cloud Native landscapes. He has published articles and blogs on recent tech trends and best practices on GitHub, Medium, and LinkedIn, and has delivered a DevSecOps 101 talk to Developers community , GitOps with Argo CD Webinar for DevOps Community. He has helped multiple enterprises with their cloud migration, cloud native design, CICD pipeline setup, and containerization journey.
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cloud Computing Batches & Dates
IEEE Account
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.

IMAGES
VIDEO
COMMENTS
New York. NY. United States. Conference: SoCC '23: ACM Symposium on Cloud Computing Santa Cruz CA USA 30 October 2023 - 1 November 2023. ISBN: 979-8-4007-0387-4. Published: 31 October 2023.
LAE-GAN: a novel cloud-based Low-light Attention Enhancement Generative Adversarial Network for unpaired text images. Minglong Xue. Yanyi He. Xin Feng. Research. Open Access. Published: 18 November 2023. Article: 160. This is part of 2 collections.
The Journal of Cloud Computing, Advances, Systems and Applications (JoCCASA) has been launched to offer a high quality journal geared entirely towards the research that will offer up future generations of Clouds. The journal publishes research that addresses the entire Cloud stack, and as relates Clouds to wider paradigms and topics.
We present a meta-analysis of cloud computing research in information systems. The study includes 152 referenced journal articles published between January 2010 to June 2023. We take stock of the literature and the associated research themes, research frameworks, the employed research methodology, and the geographical distribution of the articles.
The annual ACM Symposium on Cloud Computing (SoCC'23) brings together researchers, developers, users, and practitioners interested in cloud computing. ... Research Papers (12 pages + unlimited references): ... Author Response Period: August 14-18, 2023 Author Notification: September 1, 2023 Conference dates: October 30 - Nov 1, 2023 ...
Due to growing network data dissemination in cloud, the elasticity, pay as you go options, globally accessible facilities, and security of networks have become increasingly important in today's world. Cloud se... R. Julian Menezes, P. Jesu Jayarin and A. Chandra Sekar. Journal of Cloud Computing 2024 13 :101.
Profile Information. Communications Preferences. Profession and Education. Technical Interests. Need Help? US & Canada:+1 800 678 4333. Worldwide: +1 732 981 0060. Contact & Support. About IEEE Xplore.
Accepted papers. We have 40 papers accepted tentatively for SoCC 2023. Paper title, content, and even the acceptance decision may change during the shepherding process. The detailed program is coming up soon. Research. Plexus: Optimizing Join Approximation for Geo-Distributed Data Analytics - Joel Wolfrath, Abhishek Chandra (University of ...
This research investigates the crucial role of cloud computing services in web development for creating scalable applications. ... This paper presents a comprehensive analysis of the indispensability of cloud computing services in building scalable applications for the web. ... & Choudhury, T. (2023). Energy efficiency in cloud computing data ...
The conference is a prime international forum for researchers, academics, businesses, industry, and standard bodies to exchange the latest fundamental advances in the state of the art and practice of cloud computing, identify emerging research topics, and define the future of cloud computing. IEEE CLOUD 2023 invites original papers addressing ...
IC2E 2023 invites submissions of high-quality research papers describing fully-developed results and ongoing foundational and applied work related to all aspects of cloud engineering. The IC2E Program Committee will interpret "cloud engineering" very broadly - to include everything from engineering principles to practical experiences, and ...
About IEEE Cloud 2023. The IEEE International Conference on Cloud Computing (CLOUD) has been a prime international forum for both researchers and industry practitioners to exchange the latest fundamental advances in the state of the art and practice of cloud computing, identify emerging research topics, and define the future of cloud computing.
The paper further compares and reviews different layout model for the discovery of services, selection of services and composition of services in Cloud computing. Recent research trends in service composition are identified and then research about microservices are evaluated and shown in the form of table and graphs. Download Full-text.
CLOUD 2023 Chairs Message xix CLOUD 2023 Committees xx CLOUD Conference Papers Cloud & AI - I (CLD_CON1) xCloudServing: Automated ML Serving Across Clouds 1 Malgorzata Lazuka (IBM Research - Europe; ETH Zurich, Switzerland), Andreea Anghel (IBM Research - Europe, Switzerland), Parikshit Ram (IBM Research, USA), Haralampos Pozidis (IBM Research ...
7.1. Challenges. Via analysis and contrast, we observe that cloud computing security protection work has achieved satisfactory research results. However, many problems remain, which prompt the consideration of a variety of security factors and continuous improvements in defense technology and security strategies. 1.
CLOUD COMPUTING 2023 is intended as an event to prospect the applications supported by the new paradigm and validate the techniques and the mechanisms. A complementary target is to identify the open issues and the challenges to fix them, especially on security, privacy, and inter- and intra-clouds protocols. We solicit both academic, research ...
review is thought to inspire enterprises and managers that would like to use cloud computing in. terms of the scope, solution methods, factors, dimensions, and the results achieved in a holistic ...
We also explore the cybersecurity elements associated with cloud computing, focusing on intrusion detection and prevention and understanding how that can be applied in the cloud. Finally, we investigate the future research directions for cloud computing and expand this paper into further articles with experiments and results.
the cloud journey they're in. Cloud modernization is more than just a migration to the cloud; it's the process of optimizing costs, modernizing applications and security, and, when necessary, cloud native application replatforming. The benefits of cloud modernization Cloud modernization promotes efficiency, security and cost reduction ...
About the research. Foundry's 2023 Cloud Computing Survey is the 10th year of this research and was conducted to measure cloud computing trends among technology decision-makers including: adoption plans, spending, business drivers, challenges, and top cloud growth areas, such as AI. The study was fielded throughout August 2023 and is based on the responses of 893 global IT decision-makers ...
Find the latest published documents for green cloud computing, Related hot topics, top authors, the most cited documents, and related journals. ScienceGate; Advanced Search; Author Search ... The ScienceGate team tries to make research easier by managing and providing several unique services gathered in a web platform ©2024 ScienceGate All ...
4. Blockchain data-based cloud data integrity protection mechanism. The "Blockchain data-based cloud data integrity protection mechanism" paper suggests a method for safeguarding the integrity of cloud data and which is one of the Cloud computing research topics. In order to store and process massive amounts of data, cloud computing has grown ...
Read all the papers in 2023 IEEE 10th International Conference on Cyber Security and Cloud Computing (CSCloud)/2023 IEEE 9th International Conference on Edge Co IEEE Account. Change Username/Password; Update Address; Purchase Details. Payment Options; Order History ...
Download Citation | On Dec 4, 2023, Guang Yang and others published A Blockchain-based Online Trading Platform: TrustTrade | Find, read and cite all the research you need on ResearchGate