- Search Menu
- Advance articles
- Featured Content
- Author Guidelines
- Open Access
- About The British Journal of Criminology
- About the Centre for Crime and Justice Studies
- Editorial Board
- Advertising and Corporate Services
- Journals Career Network
- Self-Archiving Policy
- Dispatch Dates
- Terms and Conditions
- Journals on Oxford Academic
- Books on Oxford Academic

Eamonn Carrabine

About the journal
The British Journal of Criminology: An International Review of Crime and Society is one of the world's top criminology journals. It publishes work of the highest quality from around the world and across all areas of criminology.
Latest articles

Featured articles
The Editor of The British Journal of Criminology selects one paper from each new issue for its high-quality contribution to the field of research. Browse articles which are available to read and download for free. This collection is updated regularly so check back to keep up-to-date with the latest advances in the field.
Browse online

BJC prize winning articles
The Editors of BJC have awarded the 2023 Radzinowicz Prize.
Congratulations to Jason Warr for their paper, " Whitening Black Men: Narrative Labour and the Scriptural Economics of Risk and Rehabilitation ".
Read more prize winning articles from the BJC online.

BJC Virtual Issues
Sustaining Futures: Remaking Criminology in an age of Global Injustice The Conference Organising Committee Reimagining Criminological Futures: New Criminologies in a Changing World Francesca Menichelli, Giulia Berlusconi BJC through the decades Past and present editors of BJC Read more Virtual issues from the BJC

High Impact Research
Keep up to date with the latest research your peers are reading and citing, with a collection of the most cited articles published in The British Journal of Criminology in recent years.
Read the collection

BJC Headline Hitting Research
Sexual violence as a sexual script in mainstream online pornography Fiona Vera-Gray, Clare McGlynn, Ibad Kureshi, Kate Butterby
Hate in the Machine: Anti-Black and Anti-Muslim Social Media Posts as Predictors of Offline Racially and Religiously Aggravated Crime Matthew Williams, Pete Burnap, Amir Javed, Han Liu, Sefa Ozalp
Read more headline hitting research from the BJC free online

Email alerts
Register to receive table of contents email alerts as soon as new issues of The British Journal of Criminology are published online.

Recommend to your library
Fill out our simple online form to recommend The British Journal of Criminology to your library.
Recommend now

Why submit to BJC ?
Find out why you should submit your research to this top criminology journal.
Related Titles
- Recommend to your Library
Affiliations
- Online ISSN 1464-3529
- Print ISSN 0007-0955
- Copyright © 2024 Centre for Crime and Justice Studies (formerly ISTD)
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.

Journal of Quantitative Criminology
- Spans a broad range of disciplines along with criminology including statistics, sociology, geography, political science, economics, and engineering.
- Publishes original research, brief methodological critiques, and papers exploring new directions for study.
- Relevant to the criminological community in its broad scope and in-depth analysis.
- Focuses on the application of quantitative techniques at all complexity levels.
- John MacDonald,
- Greg Ridgeway
- Alex Knorre

Latest issue
Volume 40, Issue 2
Latest articles
The significance of duration weighted neighborhood effects for violent behavior and explanation of ethnoracial differences.
- Paul E. Bellair
- Thomas L. McNulty
- Daniel L. Carlson
Detecting Bias in Traffic Searches: Examining False Searches of Innocent Drivers
- Margaret A. Meyer
- Richard Gonzalez
Do Commercial Place Managers Explain Crime Across Places? Yes and NO(PE)
- Riley Tucker
- Daniel T. O’Brien
Causal Effect of Small Businesses on Street Theft: Evidence from a Natural Experiment of the Beijing Cleanup Campaign
- Yanji Zhang
Incremental Propensity Score Effects for Criminology: An Application Assessing the Relationship Between Homelessness, Behavioral Health Problems, and Recidivism
- Leah A. Jacobs
- Alec McClean
- Alex Fixler
Journal information
- Current Contents/Social & Behavioral Sciences
- Current Index to Statistics
- Google Scholar
- Japanese Science and Technology Agency (JST)
- Norwegian Register for Scientific Journals and Series
- OCLC WorldCat Discovery Service
- Social Science Citation Index
- TD Net Discovery Service
- UGC-CARE List (India)
Rights and permissions
Editorial policies
© Springer Science+Business Media, LLC, part of Springer Nature
- Find a journal
- Publish with us
- Track your research

- USF Research
- USF Libraries
Digital Commons @ USF > College of Behavioral and Community Sciences > Criminology > Theses and Dissertations
Criminology Theses and Dissertations
Theses/dissertations from 2023 2023.
Efficacy of Online Social Movements for Sparking Change: The Case of the Missing Murdered and Indigenous Women Movement (#MMIW) , Kacy A. Bleeker
An Examination of Racial Disparities in Arrest Across Florida Counties, 1998-2018: A Test of the Racial Threat and Political Representation Hypotheses , Xavier D. Burch
The Invisible Victims of Commercial Sexual Exploitation: Boys and Their Barriers to Access to Services , Amanda L. Connella
Damned & Damned: Examining Vexatious Litigation and the Vexatious Litigant Statute in Florida Courts , Sarah L. Harper
The Contributions of Mental Health Issues, Traumatic Brain Injury, and Adverse Childhood Experiences to Recidivism Among Rural Jail Incarcerees , Lauren N. Miley
Assessing the Relationship Between True Crime Documentary and Podcast Consumption, Fear of Crime, and Protective Behaviors , Lauren A. Tremblay
Police Officers’ Perceptions of Gunshot Detection Technology , Courtney L. Weber
Theses/Dissertations from 2022 2022
A Macro Social Examination of the Relationship Between Disabilities and Crime Using Neighborhood and County Level Data , Natasha A. Baloch
Racial Differences in Perceptions of Sanction Severity , Sarah L. Franklin
Juvenile Homicide Offenders: A Life-Course Perspective , Norair Khachatryan
Exploring the Effectiveness of a Life-Skills Program in a Florida Prison Through a Social Bond and General Strain Theory Perspective , Danielle M. Thomas
Theses/Dissertations from 2021 2021
Clean Water for All: Examining Safe Drinking Water Act Violations of Water Systems and Community Characteristics , Junghwan Bae
Morality and Offender Decision-Making: Testing the Empirical Relationship and Examining Methodological Implications , Jacquelyn Burckley
The Ring of Gyges 2.0: How Anonymity Providing Behaviors Affect Willingness to Participate in Online Deviance , Cassandra E. Dodge
A Macro Analysis of Illegal Hunting and Fishing Across Texas Counties: Using an Economic Structural Approach , Leo J. Genco Jr.
Self-Protection in Cyberspace: Assessing the Processual Relationship Between Thoughtfully Reflective Decision Making, Protection Motivation Theory, Cyber Hygiene, and Victimization , C. Jordan Howell
Racial Threat Theory: A Test of the Economic Threat Hypothesis , Carl L. Reeds
Online Perceptions of Panamanian Prisons and Incarcerated persons: An analysis of YouTube user comments , Mahaleth J. Sotelo
Theses/Dissertations from 2020 2020
Toxic Colonialism and Green Victimization of Native Americans: An Examination of the Genocidal Impacts of Uranium Mining , Averi R. Fegadel
Cross-National Incarceration Rates as Behavior of Law , Christopher J. Marier
The Effects of Perceived Motivations and Mental Distress on the Likelihood of Reporting and Engaging in Self-Protective Measures Among Victims of Stalking , Daniela Oramas Mora
Mental Health and In-Prison Experiences: Examining Socioeconomic and Sex Differences in the Effect of Mental Illness on Institutional Misconduct and Disciplinary Segregation , Rachel E. Severson
Theses/Dissertations from 2019 2019
Dating Application Facilitated Victimization: An Examination of Lifestyle-Routine Activities, Self-Control, and Self-Efficacy , Vanessa Centelles
Social Constructionism and Cultivation Theory in Development of the Juvenile “Super-Predator” , Elizabeth R. Jackson-Cruz
Bystander Intervention, Victimization, and Routine Activities Theory: An Examination of Feminist Routine Activities Theory in Cyber Space , Jennifer A. Leili
Sexual Assault and Robbery Disclosure: An Examination of Black’s Theory of the Behavior of Law , Caitlyn N. Muniz
Mass Shootings and Gun Sales: A Study on the Influence of Red and Blue Power , Maria Jose Rozo Osuna
A Multi-dimensional Macrolevel Study of Drug Enforcement Strategies, Heroin Prices, and Heroin Consumption Rates , Alexander G. Toth
Theses/Dissertations from 2018 2018
The Impact of a Religious/Spiritual Turning Point on Desistance: A Lifecourse Assessment of Racial/Ethnic Differences , Rhissa Briones Robinson
Political Decisions on Police Expenditures: Examining the Potential Relationship Between Political Structure, Police Expenditures and the Volume of Crime Across US States , Xavier D. Burch
Identifying the Personal and Perceived Organizational Characteristics Associated with Job Satisfaction Among Juvenile Probation Staff , Julie M. Krupa
The Role of Organizational Justice in Predicting Attitudes Toward Body-Worn Cameras in Police Officers , Nathaniel L. Lawshe
Yet Another Ferguson Effect: An Exploratory Content Analysis of News Stories on Police Brutality and Deadly Force Before and After the Killing of Michael Brown , Carl Root
The Role of Race/Ethnicity and Risk Assessment on Juvenile Case Outcomes , Tayler N. Shreve
Theses/Dissertations from 2017 2017
Intimate Partner Violence and the Capacity and Desire for Self-Control , Krista Taralynne Brewer
School Shootings in the United States from 1997 to 2012: A Content Analysis of Media Coverage , Victoria N. Iannuzzi
Chronic Runaway Youth: A Gender-Based Analysis , Michelle N. Jeanis
A Test of Wikström’s Situational Action Theory Using Self-Report Data on Intimate Partner Violence , Lauren Nicole Miley
An Exploratory Study of Macro-Social Correlates of Online Property Crime , Hyojong Song
Female Incarceration and Prison Social Order: An Examination of Gender Differences in Prison Misconduct and In-Prison Punishments , Elisa L. Toman
Adverse Childhood Experiences and Their Role as Mitigators for Youthful and Non-Youthful Offenders in Capital Sentencing Cases , Jessica R. Trapassi
Theses/Dissertations from 2016 2016
Disinhibition, Violence Exposure, and Delinquency: A Test of How Self-Control Affects the Impact of Exposure to Violence , Wyatt Brown
The Guilty But Mentally Ill Verdict: Assessing the Impact of Informing Jurors of Verdict Consequences , Erin Elizabeth Cotrone
The Relationship between Psychopathic Personality Traits and Lying , Jason A. Dobrow
Delving into the Heart of Victimization Risk: Examining the Interactive Relationship between Demographic Factors and Context , Amy Sheena Eggers
A Power Conflict Approach to Animal Cruelty: Examining How Economic Power Influences the Creation of Animal Cruelty Laws , Leonard J. Genco
The Role of Gender in Self-Control and Intimate Partner Violence , Laura Marie Gulledge
The Restrictive Deterrent Effect of Warning Banners in a Compromised Computer System , Christian Jordan-Michael Howell
Tactics of Sexual Control and Negative Health Outcomes , Anna Elizabeth Kleppe
The Applicability of Criminology to Terrorism Studies: An Exploratory Study of ISIS Supporters in the United States , Amanda Marie Sharp Parker
The Path to Violent Behavior: The Harmful Aftermath of Childhood Trauma , Nicholas Michael Perez
The Effects of Racial Bias on Perceptions of Intimate Partner Violence Scenarios , Batya Yisraela Rubenstein
Theses/Dissertations from 2015 2015
Reel or Reality? The Portrayal of Prostitution in Major Motion Pictures , Raleigh Blasdell
Psychopathy and Perception of Vulnerability , Barbara Joyce Dinkins
Effect of Empathy on Death Penalty Support in Relation to the Racial Divide and Gender Gap , Brian Godcharles
Exploring the Interactive Effects of Social Learning Theory and Psychopathy on Serious Juvenile Delinquency , Brandy Barenna Henderson
Tampa Electric Company's Big Bend Utility Plant in Hillsborough County, Florida: A Case Study , Lynne M. Hodalski-Champagne
Thirty Year Follow-Up of Juvenile Homicide Offenders , Norair Khachatryan
Organized Crime in Insurance Fraud: An Empirical Analysis of Staged Automobile Accident Rings , Chris Longino
The Role of Social Support in the Disclosure and Recovery Process of Rape Victims , Jessica Nicole Mitchell
Evaluating the Social Control of Banking Crimes: An Examination of Anti-Money Laundering Deficiencies and Industry Success , Erin M. Mulligan
Elite Deviance, Organized Crime, and Homicide: A Cross-National Quantitative Analysis , Carol L.s. Trent
An Evaluation of the Utah First District Mental Health Court: Gauging the Efficacy of Diverting Offenders Suffering With Serious Mental Illness , Stephen Guy VanGeem
Rape, Race, and Capital Punishment in North Carolina: A Qualitative Approach to Examining an Enduring Cultural Legacy , Douglas Wholl
Theses/Dissertations from 2014 2014
The Tattoo: A Mark of Subversion, Deviance, or Mainstream Self-Expression? , Jocelyn Camacho
Juvenile and Adult Involvement in Double Parricide and Familicide in the U.S.: An Empirical Analysis of 20 Years of Data , Averi Rebekah Fegadel
Predicting Successful Drug Court Graduation: Exploring Demographic and Psychosocial Factors among Medication-Assisted Drug Court Treatment Clients , Autumn Michelle Frei
Experimentally Evaluating Statistical Patterns of Offending Typology For Burglary: A Replication Study , Lance Edwin Gilmore
Developmental Trajectories of Physical Aggression and Nonaggressive Rule-Breaking among At-risk Males and Females during Late Childhood and Early Adolescence , Eugena Givens
Predicting Fear of Crime using a Multilevel and Multi-Model Approach: A Study in Hillsborough County , Jonathan Maskaly
Public Knowledge and Sentiments about Elite Deviance , Cedric Michel
The Influence of Community Context on Social Control: A Multi-Level Examination of the Relationship between Race/Ethnicity, Drug Offending, and Juvenile Court Outcomes , Jennifer Peck
Theses/Dissertations from 2013 2013
Assessing the Relationship Between Hotspots of Lead and Hotspots of Crime , Kimberly L. Barrett
A Life-Course Approach to Sexual Offending: Examining the Continuity of Juvenile Sexual Offending into Adulthood and Subsequent Patterns of Recidivism , Maude Beaudry-Cyr
Examining the link between self-control and misconduct in a multi-agency sample of police supervisors: A test of two theories , Christopher Matthew Donner
The Impact of Hyperfemininity on Explicit and Implicit Blame Assignment and Police Reporting of Alcohol Facilitated Rape in a Sample of College Women , Sarah Ehlke
Rurality and Intimate Partner Homicide: Exploring the Relationship between Place, Social Structure, and Femicide in North Carolina , Amelia Kirkland
Self-Control, Attitudinal Beliefs, and White-Collar Crime Intentions , Melissa Anne Lugo
Zero Tolerance for Marginal Populations: Examining Neoliberal Social Controls in American Schools , Brian Gregory Sellers
State-Corporate Crime in the Democratic Republic of Congo , Veronica Jane Winters
Theses/Dissertations from 2012 2012
The Walls Are Closing In: Comparing Property Crime Victimization Risk In Gated And Non-Gated Communities , Nicholas Branic
What Propels Sexual Homicide Offenders? Testing an Integrated Theory of Social Learning and Routine Activities Theories , Heng Choon Chan
A Deadly Way of Doing Business: A Case Study of Corporate Crime in the Coal Mining Industry , Charles Nickolas Stickeler
Deconstructing the "Power and Control Motive": Developing and Assessing the Measurability of Internal Power , Shelly Marie Wagers
Theses/Dissertations from 2011 2011
Assessing racial differences in offending trajectories: A life-course view of the race-crime relationship , Michael S. Caudy
Mental Health Courts Effectiveness in Reducing Recidivism and Improving Clinical Outcomes: A Meta-Analysis , Brittany Cross
General Strain Theory and Juvenile Delinquency: A Cross-Cultural Study , Wen-Hsu Lin
General Strain Theory, Race, and Delinquency , Jennifer Peck
Developmental Trajectories of Self-Control: Assessing the Stability Hypothesis , James Vance Ray
Explaining the "Female Victim Effect" in Capital Sentencing Decisions: A Case for Sex-Specific Models of Capital Sentencing Research , Tara N. Richards
A Multilevel Model of Police Corruption: Anomie, Decoupling, and Moral Disengagement , Ruth Zschoche
Theses/Dissertations from 2010 2010
The Emotional Guardianship of Foreign-Born and Native-Born Hispanic Youth and Its Effect on Violent Victimization , Amy Sheena Eggers
The Influence of Narcissism and Self-Control on Reactive Aggression , Melissa L. Harrison
Is There an "Innocent Female Victim" Effect in Capital Punishment Sentencing? , Amelia Lane Kirkland
An Analysis of the Influence of Sampling Methods on Estimation of Drug Use Prevalence and Patterns Among Arrestees in the United States: Implications for Research and Policy , Janine Kremling
A Pathway to Child Sex Trafficking in Prostitution: The Impact of Strain and Risk-Inflating Responses , Joan A. Reid
Victimization Among Individuals With Low Self-Control: Effects on Fear Versus Perceived Risk of Crime , Casey Williams
Theses/Dissertations from 2009 2009
Domestic Violence Within Law Enforcement Families: The Link Between Traditional Police Subculture and Domestic Violence Among Police , Lindsey Blumenstein
Rape Attitudes and Beliefs: A Replication Study , Rhissa Emily Briones
Reel Images: Representations of Adult Male Prisons by the Film Industry , Melissa E. Fenwick
Advanced Search
- Email Notifications and RSS
- All Collections
- USF Faculty Publications
- Open Access Journals
- Conferences and Events
- Theses and Dissertations
- Textbooks Collection
Useful Links
- Rights Information
- SelectedWorks
- Submit Research
Home | About | Help | My Account | Accessibility Statement | Language and Diversity Statements
Privacy Copyright

PRIMARY RESEARCH PAPERS
These primary criminology research papers are written by some of the most up and coming criminologists in their fields. It should be noted that although these criminology papers are not anonymously peer reviewed, like those in our articles section of the journal, primary research papers are reviewed and edited by the General Editor and members of the Editorial Board to ensure they meet the high standards of the Internet Journal of Criminology.
To download the articles please click on the the title of the articles below.
Dr. Charles Scott’s Role as an Expert Witness in the Nikolas Cruz Sentencing Trial by Professor Dina Lenore Cirigliano
On Valentine’s Day of the year 2018, a nineteen-year-old man by the name of Nikolas Cruz entered his alma mater, the Marjory Stoneman Douglas High School, located in the Miami suburb of Parkland, Florida. With “an AR-15-style semiautomatic rifle” (Laughland, et at, 2018) in hand, Cruz gunned down thirty-four people and traumatizing all within the building. Authorities stated that Cruz was equipped with three-hundred-thirty rounds of ammo when he crossed the threshold of the school and had carved swastikas onto the magazines. At the end of his rampage, seventeen were wounded and seventeen were deceased on account of this mass murderer’s actions.
Richard von Krafft-Ebing’s Psychopathia Sexualis & Jacob Appel’s The Mask of Sanity By Professor Dina Lenore Cirigliano
In the year 1886, a medical doctor who was “recognized as an authority on deviant sexual behavior and its medico-legal aspects” (Kupferschmidt, 1987) published Psychopathia Sexualis. This expert was Richard von Krafft-Ebbing, a University of Heidelberg graduate who practiced psychiatry within asylums across Germany. One-hundred-thirty-one years later in the year 2017, a Bronx-born lawyer/bioethicist/physician who specializes in emergency psychiatry published Mask of Sanity. This professional is Jacob Appel, professor of psychiatry and medical education at the Mount Sinai School of Medicine in New York. While Krafft-Ebing’s Psychopathia Sexualis is a German-printed, non-fictional piece classified as a medico-legal reference, and Appel’s Mask of Sanity is an American novel of the fiction genre, both pieces are scribed by authorities in their field and both publications address individuals who suffer from pervasive mental disorders steeped in criminality.
Are Non-Scientists Qualified To Be Blood Spatter Analysis Professionals?
By Dina Cirigliano, Plaza College, Forest Hills, New York
While blood spatter analysis has indeed developed and expanded with the passage of time, there have been notable setbacks in the field as of late. These setbacks come in the form of questionable credentials of those permitted to offer expert testimony regarding blood spatter in courts of law. Particularly in the last half decade, blood spatter analysis has come under the inspection of some watchful eyes, as the qualifications of supposed experts are more and more often being viewed as subpar. The purpose of this paper is to establish whether or not non-medical doctor and non-scientific researcher blood spatter analysis professionals deserve the scrutiny they have been facing for the past five years.
Advances in Forensic Science: Deoxyribonucleic Acid Breakthroughs in the Last Five Years
Deoxyribonucleic acid (DNA) has come a long way since its discovery by Swiss chemist, Dr. Friedrich Miescher, in the year 1869. It has subsequently been recognized as presenting in three-dimensional, double helix form, has been utilized to exonerate the accused but not-guilty, and has been applied as irrefutable scientific evidence to convict offenders in criminal court, regardless of their lack of admission of guilt. Scientific discovery is a continuum of knowledge to be acquired with each passing year, especially within the field of genetics. The purpose of this paper is to explore what the last five years of DNA research has brought forth.
From 1860 Miescher to 1986 Jeffreys: A Times Past View of Forensic DNA Analysis
B y Dina Lenore Ciriligiano, Plaza College, Forest Hills, New York
The purpose of this piece is to highlight the major events throughout the short history of DNA, specifically 1) the first discovery of its existence, 2) Watson and Crick’s discovery of its three-dimensional double helix form and more, 3) Dr. Alec Jeffreys’ and the first conviction in a criminal case using DNA as scientific evidence, and 4) the recognition of identical twin DNA and the doubt it brings forth.
From Galton to the First Repository: Fingerprint Analysis During the Pre-AFIS Period By Dina Cirigliano, Plaza College, Forest Hills, New York
At the present time, fingerprints are utilized to confirm or refute an individual’s identity within the confines of criminal justice systems throughout the world. Today, fingerprints are used to identify individuals who were present at crime scenes even after fleeing, to link one crime scene to another by comparing prints from both locations, often connecting them to the very same individual, to differentiate inmates housed in correctional facilities, to track the criminal record of repeat offenders, and to even ;put a name to the face of many a John and Jane Doe in the custody of the Office of the Chief Medical Examiner (OCME). All of this comparing, tracking, differentiating, and linking is done with advanced computer technologies whose system houses an infinite repository of fingerprints and identities the individuals to whom each print belongs. However, this high-tech database known as the Automated Fingerprint Identification System (AFIS) did not come into existence until the year 1980 (Crime Scene Forensics, 2018). Prior to that, anything regarding fingerprint analysis and sharing was done the old-fashioned way. The purpose of this paper is to highlight the establishment of fingerprint usage during the pre-AFIS period, specifically 1) Sir Francis Galton’s concepts of minutiae, 2) Sir Edward Henry’s pattern classification, 3) the William West conundrum, 4) the Thomas Jennings case, and 5) the growth of the Federal Bureau of Investigation’s fingerprint repository.
The Last Five Years In Blood Spatter
By Professor Dina L. Cirigliano / Plaza College / Forest Hills, New York
Blood spatter analysis by forensic science experts began one-hundred-twenty-eight years ago and is therefore, by no means, a new specialization. The maturity of this concentration of forensic science has increased over time. That is quite evident with the professionals’ ability to establish categories of blood spatter as passive stains (droplets, flows, and pools), transfer stains (wipes, swipes, footprints, shoeprints, handprints, glove prints, and body drag marks), and impact stains (cast-off and arterial gush), their ability to identify the bloodshed event (sharp-force injury, blunt-force injury, or gunshot injury), their ability to determine the trajectory of a projectile, their ability to establish the locations and positions of victims and offenders, their ability to bring forth chemiluminescence with a mere spray of aerosol Luminol, and their ability to to recreate crime scenes by utilizing simulation software. While blood spatter analysis has indeed developed and expanded with the passage of time, there have been notable setbacks in the field as of late. These setbacks come in the form of questionable credentials of those permitted to offer expert testimony regarding blood spatter in courts of law. Particularly in the last half decade, blood spatter analysis has come under the inspection of some watchful eyes, as the qualifications of supposed experts are more and more often being viewed as subpar. The purpose of this paper is to establish whether or not non-medical doctor and non-scientific researcher blood spatter analysis professionals deserve the scrutiny they have been facing for the past five years.
Innovations in Forensic Fingerprint Analysis Over the Last Half-Decade By Dina Cirigliano, Plaza College, Forest Hills, New York
The study of fingerprints has come a long way from its meagre beginnings in 1892, when Galton introduced the world’s first fingerprint analysis publication. So much had happened in the field since then that by the year 1980, the database known as the Automated Fingerprint Identification System (AFIS) was not only founded, but up and running, so that print sharing between law enforcement agencies could occur seamlessly. Today, forty-three years after the establishment of AFIS, fingerprint research is still at the forefront of forensic scientists’ focus. The purpose of this piece is to highlight advances in fingerprint science in the last five years, particularly 1) how and when fingerprints develop on the bulbs of human fingers, 2) the role of INTERPOL in fighting international crime, 3) the recognition of irregularly rare fingerprints, and 4) the ability to estimate the sex of an offender or victim based on the ridge density of the fingerprints left behind at the crime scene.
Blood Spatter: The History of Analysis
Blood spatter analysis is, at the present time, a well-established subcategory within the field of forensic science. In today’s world of innovative technologies and highly-sophisticated equipment, attorneys can rely on the testimony of blood spatter experts in the form of forensic scientists, to make or break their cases. However, this was not always so. Blood splatter analysis was not always in existence, let alone as evolved as it is at the current time. The purpose of this piece is to highlight the major milestones throughout blood splatter analysis’ historical timeline, specifically 1) its origin with Dr. Eduard Piotrowski, 2) its breakthrough into the American legal system as accepted scientific proof presented during trial, 3) its popularity among researchers enacting the establishment of the International Association of Bloodstain Pattern Analysts, 4) its introduction of Fred Carter’s blood simulation software, and 5) its use of detection Luminol to reveal weaponry used along with the locations of the victim and offender.
EXAMINING AN ECCENTRIC NECROPHILE
By Dina Lenore Cirigliano. Plaza College.
As far back as historical documentation goes, necrophilia has always been a macabre constant. In earlier times, Herodotus (who lived from 484 BC - 425 BC), documented in his record writings that bodies of remarkably stunning women were no longer embalmed immediately after their deaths in Ancient Egypt, to deter a repetition of a situation where it was exposed that an embalmer had intercourse with the corpse of a freshly deceased woman. Hundreds of years later, the Babylonian Talmud (3rd–5th centuries AD), records a chosen maiden killing herself to avoid marrying King Herod of Judea, as she had no desire to be with him. It continues to state that following her suicide, the king had her corpse conserved in thick honey for seven years so that he may have sex with her body at a later date. Later still, Gilles de Rais, a knight, lord, leader in the French army, and companion-in-arms to Joan of Arc, was “noted to have sexually violated the dead bodies of his victims” until his death in October 1440. Continuing onward in time, notable criminologist Herschel Prins, proved that up until the 19th century, if an engaged woman in passed away in Central Europe prior to her marriage, the male betrothed to her may copulate with her body. Again, necrophilia has plagued every era throughout history and will continue to do so throughout the future, as paraphilias are neither preventable nor curable. They are, in fact, “innate, driven by some complex interactions between androgenization of the brain and neurohormonal changes”.
EVOLUTION OF AUTHORIZED DEATH DEVICES: PROGRESSION OF SANCTIONED KILLING MACHINES, TRENDS THEY YIELD, AND WHAT THESE DRIFTS INDICATE ABOUT THE NLAC LASER AS THE FUTURE OF CAPITAL PUNISHMENT IMPLEMENTATION
By Dina Lenore Cirigliano, Plaza College
This article illustrates the progression in the sophistication of death devices with regard to both materials utilized and apparatus design, from times in ancient history through modern days. The article will illustrate the fact that when examining the development of death penalty constituents and contraptions, as the means by which the convicted are condemned to death become increasingly technologically savvy, they also become decreasingly gruesome and less time-consumingly torturous. With the passage of time and the rise of innovative methods of execution comes a change from primitive, bloody, lengthy agony to state-of-the-art, minimally-gory, swift humaneness. This alteration shows a definite surge in moral and ethical responsibility. If this trend is to continue, the questions for corrections professionals are as follows:
1. What will the capital punishment device of the future be? 2. In what ways will the future death apparatus continue the ongoing movement toward innovative technology, morality, ethics, and humaneness and away from bloody displays and drawn-out suffering?
THE EXPERIENCE AND TREATMENT OF WOMEN PRISONERS AS VICTIMS OF VIOLENCE
By Rezia Begum, Loughborough University
This research was undertaken for my PhD thesis. The aim of the research was to gain access to women’s prison in the UK in order to undertake qualitative research into two specific issues: women prisoners’ experience of domestic violence; and what treatment or management programmes are in place to deal with this issue, both whilst women are in prison and upon their release.
‘It’s Life But Not As We Know It’. An Impact Study Looking At Youth Offending Practitioners Interactions With Their Service Users By Antony Peter Gadsby, Nottingham Trent Universtity, UK
In recent years, studies that aim to understand the experiences of youth justice practice have tended to focus on the practice as a whole using quantitative methods and statistics to explain the trends in offending behaviours rather that the impact this has on the practitioners themselves (Burnett & Appleton, 2004). There has also been a tendency to concentrate solely on the offending behaviour rather than the individual’s behaviour, which is portrayed mainly in negative ways, resulting in even less emphasis on the impacts and implications for practitioner and client relationship. For this very reason, a single participant case study utilising Interpretive Phenomenological Analysis, aimed to look into the experience of a practitioner within a youth offending team, to understand the psychological impacts both positive and negative that may occur, in work related situations. The study’s main aim was to extract rich idiographic data, in order to give the researcher a clear and richer understanding of their experiences and coping mechanisms needed to efficiently manage their daily activities. The participant Trevor (pseudonym) was a white male with extensive experience working with young people, also with a youth working background. A youth offending office such as the one in the study was a very busy environment, and unexpected events occurred frequently from the initial observations during part 1 of the interview. Due to the nature of the work, the interview with Trevor had to be conducted in 2 parts to facilitate the study. There was a main theme in the interview, whereby time constraints and adhering to procedures affected the way relationships were built up. Other emerging themes from the semi-structured interview reflected on a reactive practice, whereby immediate action was required, uncertainty in daily planning of duties, resulting in what Trevor described as ‘fire fighting’. However, where policies and procedures are in place, in inter- agency organisations such as youth offending teams, the mix of historical, professional and cultural traditions (Eadie & Canton, 2002) may unfortunately do little to alter these working practices for the foreseeable future, but measures may be introduced to ease these working practices.
Field Observations of Australian Private Investigators Conducting Fraud Investigations
By Michael King, Brisbane North Institute of Technical and Further Education, Australia
It has been over a decade since the last study was conducted investigating the nature and role of the private investigation profession. To fill this gap, this study uses semi-structured interviews and field observation of private investigators working within the metropolitan area of Brisbane, Queensland, Australia to obtain data to further this field. This study focuses on the investigative methods used by private investigators to conduct their investigations and examines the ethical and legal issues arising from their work. Despite some advances in training and licensing, the industry is still prone to investigators adopting questionable ethical practices such as deception to solve cases. The objective of this paper is to provide a greater insight into this little understood profession.
Police interviewing of criminal suspects: A historical perspective
By Karl Roberts, Macquarie University, Australia
This paper provides an historical overview of the development of police suspect interviewing. The paper highlights how different approaches developed based upon the prevailing needs of the time, from early approaches involving torture and threats, simple question and answer approaches, through to methods incorporating knowledge from the behavioural sciences such as persuasive interviewing. The paper highlights some of the problems associated with these approaches in particular risks of unreliable information and potential miscarriages of justice and discusses more recent ethically oriented interview approaches developed to minimise some of these risks. The paper stresses the importance of sensitivity to the rights and needs of suspects even when carrying out interviews under pressured conditions.
Youth Offenders and Functional Literacy By Edward Thomas, Middlesex University, UK
One of the key findings of the Department of Communities and Local Government’s Report into the 2011 riots found that a significant causal issue amongst those persons convicted of criminal offences during the riots of August 2011, was their lack of ‘Functional Literacy’. This article looks at longitudinal study of convicted youth offenders from 1995 and 2006. It sets out to establish that there has been sufficient academic writing from Rutter (1975) to Goodman & Ruggeiro (2010) coupled with the findings of successive Government Reports, including The Moser Report 1999, that have gone virtually unheeded by Governments of all political persuasions. These findings have been left to gather dust during periods of financial growth as well as recession for over more than thirty years. Why should the Department of Communities and Local Government’s Report fare any better?
Portsmouth Community Safety Survey 2012
By Nick Sandford-Smith & Tom Ellis, Institute of Criminal Justice Studies, Portsmouth University, UK
This is a summary report of the key findings from the 5th Portsmouth Community Safety Survey (PCSS). Previous surveys were carried out in 2001, 2004, 2007and 2009 by Ipsos MORI. This 2012 survey has been carried out by second year research students in the Institute of Criminal Justice Studies (ICJS). It was designed to gather opinions from Portsmouth residents on: quality of life; perceptions and experience of crime and anti-social behaviour; and fear of crime in relation to particular areas of Portsmouth. This summary report was commissioned by Portsmouth City Council to inform the Safer Portsmouth Partnership Strategic Assessment (SPPSA) and the Safer Portsmouth Partnership Plan (SPPP). Both of these documents identify the community safety priorities for the partner agencies involved and provide the evidence on which the allocation of relevant resources and the commissioning of associated services within Portsmouth are based.
Sentenced to Work: From Retribution to Rehabilitation
By Keith Price, Anthony Pierson and Susan Coleman, all at West Texas A&M University, USA.
Inmate work has been an important feature of prison systems in the United States from the colonial period until today (Fox, 1972), and work has been seen as a method to accomplish several correctional objectives (Hawkins, 1976). Prison labor was initiated for disciplinary reasons and retribution in the seventeenth and eighteenth centuries, extended and expanded for financial profit with the development of the industrial prison in the nineteenth, and maintained for its alleged therapeutic and educational value as a part of rehabilitation in the twentieth and twenty-first centuries (Conley, 2001).
In Pursuit of the Beast:
Undergraduate Attitudes Towards Sex Offenders and Implications for Society, Rehabilitation and British Psychology Education By Craig A. Harper, University of Lincoln, UK
Positive attitudes toward sex offenders can lead to favourable treatment outcomes and with psychology students being among the most likely graduates to move into offender rehabilitation, it is important to investigate the attitudes of this group. Students from British psychology and non-psychology courses read vignettes depicting an adult and a juvenile committing a contact sexual offence on a child, and completed modified versions of the attitudes towards sex offenders [ATS] questionnaire. The adult offender was viewed significantly more punitively than the juvenile offender, but no significant differences were found between subgroups of participants. It was concluded that undergraduate psychology degrees do not go far enough to address some of the stigmatised views held by the general population towards sex offenders. Implications for media reporting, recidivism and psychology education are discussed.
Criminal Attitudes of Ex-Prisoners: The Role of Personality, Criminal Friends and Recidivism By Daniel Boduszek, University of Ulster and Dublin Business School, Christopher G. McLaughlin, University of Ulster and Philip E. Hyland, University of Ulster and Dublin Business School, Ireland
Previous research suggests that those who enter prison with a low level of criminal attitudes tend to acquire more deviant attitudes during their sentence due to persistent contact with criminal others, and moreover, presence of criminal personality may be sufficient to develop criminal attitudes. The aim of this paper is to determine which of the independent variables: age, education level, marital status, number of children, location, recidivism, association with criminal friends, and personality traits could be used to explain why ex-prisoners hold criminal attitudes.
Policing in the Pacific: Why the Wontok Sysytem of the Solomons Encourages Corruption
By Jason Paul Sargent, JP. SJP. B Policing. Grad Dip Psych. FSA. MAIPIO, Kathleen Lumley College & Adelaide University, Australia
Jason Sargent spent 4 months serving in the Solomon Islands in 2003 as part of the (RAMSI) Royal Assistance Mission to the Solomon Islands, when he was a uniformed member of the Australian Federal Police in the Protective Service section. This paper will examine how policing in the Solomon Islands will always face the reality of corruption due to the tribal system known as the Wontok system of family association and protection.
Multi-ethnic Comparisons of the Predictors of Delinquency Among Urban Adolescents
By Tia E. Kim, Ph.D., The Pennsylvania State University, USA and Michiko Otsuki-Clutter, Ph.D., University of South Florida, USA
The purpose of the present study was to examine the roles of parental and peer influences on adolescent delinquency in a multiethnic sample of European American, Asian American, and Latino youth. The study utilized survey data on parental monitoring, peer delinquency, and delinquency on 187 high school students (10-12th grade). Overall, we found that when controlling for ethnicity and other demographic variables, both parental monitoring and peer delinquency independently predicted participants’ delinquency. In addition, peer delinquency functioned as a mediator between parental monitoring and delinquency. Findings from our study also show that correlates of delinquency differ among European American, Asian American, and Latino adolescents. Our findings suggest that prevention and intervention programs should acknowledge ethnic differences and should gauge whether steps can be taken to tailor programming to specific ethnic grou
A Global Crime: Why Transnational Sex Trafficking Networks are Succeeding in the 21st Century
By Peter Mameli, Associate Professor, Department of Public Management, John Jay College of Criminal Justice, U.S.A.
This article explores the relationship between increasing environmental complexity born of globalization processes and transnational criminal activity. In particular, the phenomenon of transnational sex trafficking is spotlighted for review. Initially, this review sketches the parameters of the problem and the main actors involved. Next, an analysis of how transnational criminals function examines why changes in organizational form have unleashed operational capabilities that public sector entities in law enforcement are finding difficult to overcome. The study closes suggesting productive paths forward to combat this growing scourge.
From the USA to the ROK, CSI is Getting Airplay :
An Exploratory Study of the Presence and Popularity of American Criminal Justice Dramas in Northeast Asia
By Ben Brown, Criminal Justice Department, The University of Texas at Brownsville, U.S.A.
Considerable research has focused on media presentations of crime and the criminal justice system in the United States, but little attention has been afforded to the popularity of American criminal justice dramas in foreign nations. This study utilizes a mixed methodological strategy to examine the availability and viewing of American criminal justice dramas (television programs and movies) in South Korea. An analysis of daily programming on several networks available in South Korea shows that American criminal justice television dramas such as CSI and American movies about crime and justice such as The Fugitive are frequently broadcast. An analysis of data obtained from a survey of South Korean college students shows that more than half the students watched an American criminal justice dramatic television program at least once and that more than one out of ten of the students watched American criminal justice dramatic programs on a regular basis. The implications of the data for future research are discussed.
The Women of Stormfront: An Examination of White Nationalist Discussion Threads on the Internet
By Tammy Castle, Ph.D, James Madison University and Meagan Chevalier, B.A, George Mason University, USA
Although a plethora of literature exists on hate or extremist group activity, the role of racist women remains an unexplored area. The current study sought to explore one method of communication for racist women, the Internet. The researchers conducted a content analysis on 227 discussion threads provided on one of the oldest extremist websites on the Internet, Stormfront. The purpose of this study was to investigate the content of the discussion threads described as ‘For Stormfront Ladies Only.’ Of primary interest to the researchers was whether the content discussed by women in this ‘White Nationalist’ cyber community supported the assertion by some scholars that the role of women in racist activities is undergoing a transformation and the implications of this study in that regard are discussed.
Criminal Justice Department Chairs' Attitudes Towards Homosexuals and Curricular Issues
By Alexis J. Miller, Ph.D., Associate Professor of Criminal Justice, and Danielle McDonald, Ph.D. Assistant Professor of Criminal Justice, Northern Kentucky University, USA
Criminal justice students have stronger negative attitudes toward homosexuals than do other social science students (Cannon 2005; Miller 2001; & Olivero and Murataya’s 2001). The current research surveys criminal justice department chairs’ attitudes toward homosexuals and the number and nature of courses in their departments that deal with gay and lesbian issues. Results show that male chairs and chairs that are older and white tend to have more negative feelings towards homosexuals. Furthermore, while chairs’ believe that some gay and lesbian issues are also criminal justice issues, courses covering issues facing homosexual in the criminal justice system are lacking.
Betting Shops and Crime: Is There a Relationship?
By Professor Mark Griffiths, International Gaming Research Unit, Nottingham Trent University, U
Gambling and its link with criminal activity is an area of growing research interest. Studies from various regions worldwide have suggested an association between criminal activity and easily accessible gambling, yet, despite growth in the commercial gambling industry, relatively little is known about the nature, extent or impact of gambling-related crime. Such information is critical in the current UK climate as some gambling establishments (particularly betting shops) are prevented from getting operating licenses on the basis of police objections that they are likely to become ‘crime hotspots’. Therefore, this paper briefly overviews to what extent betting shops cause, facilitate, or attract crime. It is concluded that only two types of betting shops can realistically be associated with crime arising from problem gamblers who use their premises and with criminal behaviour occurring within or in the immediate environment of the premises itself. Although a few studies have shown associations between gambling and crime there is no empirical evidence showing that gambling venues (including betting shops) cause crime. Most of the empirical evidence concerning the relationship between crime and gambling concerns the criminal consequences of problem gambling (including those ‘addicted’ to gambling). In order to be a cause of crime, betting shops must be both a necessary and sufficient condition for the crimes in question to occur. This paper finds that they are neither.
Public Perceptions of the Police: Effects of Police Investigation and Police Resources
By Andreas Cebulla, Research Director at the National Centre for Social Research and Mike Stephens, Senior Lecturer in Criminology and Social Policy at Loughborough University, UK
Since the 1980s, successive UK governments have sought to increase efficiency in, and effectiveness of, policing through what has been described as “cycles of reform” (Reiner, 2000, p. 204). The reforms typically involved exerting greater central control over regional police forces. Many of the early initiatives met with resistance from within the police and, as a result, were not fully implemented (McLaughlin and Murji, 1995). By the late 1990s and early 2000s, however, more effective and direct control over police performance was finally established. This took the form of a centralisation of police management, which resulted in the introduction of more uniform measures of monitoring police performance, including the regular recording of crime and crime detection rates among police forces. Performance targets were set and the public’s satisfaction with the work of the police in their local area became one of several performance indicators. Performance targets and measures to generate greater cost efficiency in service provision, however, can have unexpected, sometimes perverse side effects. Two of these are focus of this paper. First, it explores how shifts in the police’s focus on specific types of crime in response to the introduction of performance targets affected the public’s reporting of crime. Second, it asks whether, in the light of efforts to achieve efficiency savings in the police, public spending on police forces has had any bearing on the public’s perception of the quality of local policing.
Socio-Cultural Determinants of Criminal and Anti-Social Behaviour of Agaba Groups in Calabar Metropolis, Nigeria By Moses U. Ikoh, PhD, Graduate School, University of Calabar, Calabar, Nigeria and Prof. Joseph O. Charles, PhD, Department of Sociology, University of Calabar, Calabar, Nigeria.
This paper explored the involvement and arrest of street boys (popularly called Agaba boys) in 19 criminal and anti-social behaviours. Using the General Strain Theory (GST) to guide discussion, the study administered questionnaires on 80 Agaba members drawn purposively from four groups in Calabar Metropolis. It equally held Focus Group Discussions (FGDs) with group leaders. Chi square statistical tool and multiple regressions were used in analysis. The results revealed differences in the four groups’ involvements in the 19 criminal and anti-social behaviours that were tested. Socio-economic activities found in their residential areas were the major determinants of type of criminal and anti-social activities they specialized in. The study argues that socio-demographic backgrounds that the boys found themselves exerted significant effect on their subsequent behaviours. It suggests the creation of a Public Private Partnership (PPP) initiative that would deliberately create employments which require low and manual skills that could help in taking most of the boys from the streets.
Perception of Smuggling Among the Yoruba People of Oke-Ogun of South Western Nigeria
By Oladeji, Matthew Olaniyi, Senior Principal Lecturer, The Polytechnic Ibadan, Oyo State, Nigeria
Smuggling, defined by Nigerian law as criminal, is rampant in Oke-ogun area of Southwestern Nigeria. Consequently, a research project was conducted among the people of the area to determine; how the people perceive smuggling. Also, to see the relationship that exists between the smugglers and the border town dwellers as well as between the smugglers and the law enforcement agents. Furthermore, it was meant to investigate the relationship between the level of education and perception of smuggling by the people of the area. The major instruments used were structured questionnaire, key informant method and in-depth interview. The study established that most residents did not see anything bad in smuggling as they profit from smuggling activities; and most of the services they provide are not without rewards. A positive relationship also exists between levels of education and perception of smuggling among the people of the study area.
Spinach, Iron and Popeye: Ironic lessons from biochemistry and history on the importance of healthy eating, healthy scepticism and adequate citation By Dr Mike Sutton, Reader in Criminology, Nottingham Trent University, UK
To inform knowledge in research methods and dissemination ethics for the natural and social sciences, this article reinforces the importance of citation to support all assertions of fact. New findings are presented for the history of biochemistry, nutrition, psychology, medicine, and the social sciences. Bio-chemistry papers and scientific news reports from the 1930’s seriously undermine a long standing truism that in the 1920s and 30s, bio-chemists, nutrition experts, public health policy makers, and E. Segar the creator of the newspaper comic strip Popeye were misled either by a decimal place error in 19th Century published research, or else by erroneous interpretation of 19th Century scientific findings, to exaggerate the iron content of spinach tenfold. Further, the failure to study original sources is evidenced in a multitude of completely erroneous publications claiming that these apocryphal errors caused Segar to choose spinach for Popeye’s super human strength. In fact, Segar chose and promoted spinach for its vitamin A content alone.
Relationship between Psycho-demographic Factors and Civil Servants’ Attitudes to Corruption in Osun State, Nigeria By Adebayo O. Adejumo, Department of Psychology, University of Ibadan, Nigeria and a member of Nigeria’s National Health Research Ethics Committee
This paper examines the relationship between psycho-demographic factors and attitude to corruption (ATC). The cross-sectional survey included 600 local government civil servants following multi-stage sampling. A 58-item self report validated questionnaire was used for data gathering. There was significant relationship between; personality, fraudulent intent, N-Ach and ATC. Fear of crime had an inverse relationship with ATC, personality was shown to be the most potent predictor of ATC and there was significant relationship between age and ATC. This study provides insight to the role of these psychological factors and age as fundamental to improving public servants’ ATC, especially in Nigeria. Utilisation of these findings could be useful in staff recruitment and reduction of corruption in private and public administration in other settings.
Male Inmate Perspective on Reducing Recidivism Rates Through Post-Incarceration Resources By Misty Malott and Ali Fromander, Department of Human Development and Family Studies, Univeristy of Wisconsin, USA
Most people who are incarcerated come from the community and ultimately will return to the community (Andress, Wildes, Rechtine, and Moritsugu, 2004). What are some unmet needs post-incarceration that could be addressed to reduce their risk of reoffending? This nonrandom pilot study investigates inmate perspectives regarding perceived access to resources post-incarceration that could reduce their recidivism, by surveying 102 male inmates at three Midwestern jails. It was hypothesized that male inmates would agree that accessible resources, treatment, and/or support services, post-incarceration would help reduce their recidivism. Major findings supported the hypothesis. The survey data was statistically analyzed using frequencies, means, and a reliability analysis. Implications for practitioners and future researchers were addressed.
Crime and gambling: A brief overview of gambling fraud on the Internet
By Dr. Mark Griffiths (BSc, PhD, PGDipHE, CPsychol), Professor of Gambling Studies and Director of the International Gaming Research Unit at Nottingham Trent University, UK
Although there is an association between crime and gambling there is relatively little information and research on the topic. One area that appears to have become more prevalent over the last five years is that of fraudulent gambling activities on the Internet. This paper briefly outlines how many frauds and scams have moved into technological media such as the Internet and overviews a number of these including: (i) lottery scams, (ii) fake gambling site scams, (iii) betting software scams, (iv) gambling ‘bonus’ scams, (v) ‘twofer’ scams, and (vi) prize scams. It is concluded that gambling fraud on the Internet is a growth area because many gamblers themselves want to get a huge reward from a small outlay (just as the fraudsters do). As long as there are people who are prepared to risk money on chance events, there will be those out there who will want to fraudulently take their money from them. Given the complete lack of empirical data on these fraudulent practices, there is a need for research to be initiated in this newly emerging area of criminological concern.
A Physicist, a Philosopher and a Politician: What penologists can learn from Einstein, Kant and Churchill
By Dr. Curtis R. Blakely, Assistant Professor in the Justice Systems Department at Truman State University, and Alice Walkley, Justice Systems major at Truman State University, USA
For the past three decades scholars, politicians and prison officials within the United States have collectively ignored offender rehabilitation as a legitimate penal pursuit. This has stifled the development and use of treatment initiatives. The absence of a treatment objective signifies a state of ideological imbalance. Prison specialization is offered as a potential solution to restore this balance while helping to break the criminogenic cycle. In looking at the feasibility of prison specialization, attention is given to three great thinkers, Albert Einstein, Immanuel Kant, and Winston Churchill. Both Einstein and Kant suggested that creative and innovative thinking can produce immensely rewarding results regardless of the field under consideration. Likewise, Churchill specifically lobbied for the creation of a specialized prison system.
Bias Motivation in Crime: A Theoretical Examination
By Erica Hutton, Criminal Justice PhD Program, Capella University, USA
This paper assesses the social problem of racially motivated crime that occurs within our communities. Racially motivated crime is also known as bias motivation and this type of offense is personal in nature, pertaining to one’s race, ethnicity or nationality, religion, disability, or sexual orientation. There are various categories of bias that influence an individual to participate in the execution of a hate crime. The Labeling Perspective and the Constructionist Perspective are examined to assess a theoretical interpretation of this complex social problem. There is substantial controversy in regards to what exactly constitutes a hate crime and how this discrimination of one another effects members of our communities, affecting behavior as well as shaping social norms, violations, and deviant behavior correlated to the occurrence of bias acts of criminal activity.
Cameras in the Courtroom: A Comprehensive Examination
This paper will examine the utilization of cameras within the courtroom and will discuss the historical context of broadcasting court proceedings as well as the current legal regulations pertaining to the use of cameras in and outside of the court. The strengths and weaknesses of utilizing cameras in court are explored. A section is devoted to the discussion of the diverse implications associated with utilizing cameras in court proceedings as well as the precarious influences correlating to the members thereof. An assessment of the behavioral and theoretical perspectives will be considered in regards to the sociological, psychological and criminological aspects of the community, citizens, and members of the criminal justice system.
Pakistan: Far-Right Islamist Militants and a Resurgence in the Illicit Opiates Trade
By James Windle, Midlands Centre for Criminology and Criminal Justice, Loughborough University, UK
Between the mid-1970s and late-1990s, Pakistan was a major source of illicit opium and heroin to the global market. By 2001, development and law enforcement activities where successful in creating a business environment in which Pakistani opium poppy farmers could not compete with their Afghan counterparts, resulting in Pakistan being declared ‘opium free’ by the UN Office of Drugs and Crime. Since 2003, there has been a gradual increase in illicit opium production in Pakistan, however, the state has been able to eradicate as much as 77 percent of all crops; this was not the case in 2008, mainly due to the redeployment of resources from counter-narcotics to counter-militancy operations. This paper posits that the current high levels of violent conflict between the state and far-right Islamist militants could act as an impetus to an increase in illicit opium production in Pakistan’s North West Frontier Province and Federally Administered Tribal Areas.
Family Structure and Juvenile Delinquency: Correctional Centre Betamba, Centre Province of Cameroon
By Ilongo Fritz Ngale, Institute of Education, National University of Lesotho, Lesotho-Southern Africa
The relationship between family structure and juvenile delinquency was explored in a purposive probability sample of 120 adolescents of the Betamba children’s correctional center using a questionnaire. The use of quantitative statistical analysis revealed the following significant relationships: (1) Juvenile delinquents mostly come from homes in which the parents are married; (2) The moral education of juvenile delinquents is undertaken more by others than their biological parents; (3) Most delinquent children come from the lowest socio-economic stratum of society; (4) About two-thirds of the juvenile delinquents come from homes where 7 persons and above live under the same roof; (5) Most parents of our respondents have low paid jobs which keep them for long periods away from their children. A growing number of parents need additional socio-economic support, development of vital skills of responsible parenting, in order to adequately manage periods of rapid social change and simultaneous multidimensional challenges.
Moral Remediation, Multi-Systemic Therapy and Effective Interventions for Serious Juvenile Offenders
By David Sortino, Sonoma County Probation Department, Director of the Center for Moral Development, Values and Character Education, USA
Our juvenile hall population is at an all time high, 2.2 million inmates at an average cost of about $35,000 per inmate (OJJDP, 2006). In fact, we lead the world in incarcerated juvenile offenders and the juvenile system is fast becoming a breeding ground for adult prisons. In Washington State alone, 73% of adult inmates served time in a juvenile detention facility (OJJDP, 2005). This paper describes how a “Moral Remediation” program could be employed as an adjunct to the most successful intervention programs as defined by a recent study in the Office of Juvenile Justice and Delinquency Prevention Bulletin (April, 2000). The Bulletin defined 200 intervention programs and the methods they used to lower the recidivism rates of serious juvenile offenders in non-institutionalized and institutionalized facilities.
Identity Crisis? Negotiating Blackness in the British Police Service: a Regional Perspective
By Barbara Perry, University of Ontario Institute of Technology, USA and Catherine John-Baptiste, Nottingham Trent University, UK
Our paper will address preliminary findings from a pilot study in which we will interview a sample of black police personnel from Nottingham, UK. Our goal in this project is to uncover the mechanisms by which police officers as well as other police staff negotiate their black identities in the context of their roles within law enforcement – an entity that clearly been historically characterized by systemic racism.
How Prolific Thieves Sell Stolen Goods
By Mike Sutton, Nottingham Trent University, UK
Aiming to reduce acquisitive crimes and associated offending, Nottinghamshire Constabulary is considering adopting the Market Reduction Approach (MRA) to tackle stolen goods markets in order to reduce theft. As a first step, this report provides a review of findings from a study of local stolen goods markets in Nottingham and Mansfield. The study examined the ways that local stolen goods markets operate and their influence upon local theft levels and criminal careers. Funding for the study was provided by Nottinghamshire County Council’s Communities Department. The findings in this report come from in-depth interviews conducted in the summer of 2006 with 20 offenders under supervision by Mansfield and Nottingham’s prolific offender units. Some interviewees admitted that they were active offenders. Others were making a concerted effort to remain out of trouble. Most had recently completed a spell in custody.
Differences at the Border: Views of Crime, Criminals, Punishment, and Treatment Among Canadian and U.S. College Students By Eric G. Lambert, Kasey A. Tucker and David N. Baker, University of Toldeo, USA
Crime is universal; views about crime and how to control it vary widely in different cultural and political climates. This study examined cross-cultural views of crime, criminals, punishment and treatment for offenders. Specifically, this study compared Canadian and U.S. college students and their perceptions of these issues to determine whether cultural differences exist and to what degree. Both the independent t-test and ordered ordinal regression indicated that U.S. students tended to be more punitive than their Canadian counterparts on a majority of the indicators. This attitude may be due to the fact that U.S. students were more likely to perceive a higher crime rate.
Handling Stolen Goods: Findings from the 2003 Offending Crime and Justice Survey
By Mike Sutton, Nottingham Trent University, England, Sarah Hodgkinson, Leicester University, England and Mike Levi, Cardiff University, Wales
This paper presents findings from a systematic analysis of stolen goods markets, based upon scholarly research and criminological theory, with a toolkit for implementing Sutton’s MRA. The MRA has been implemented in several UK police forces including Kent, Thames Valley, The Metropolitan Police. Derbyshire, Manchester and West Mercia. Other forces use MRA techniques, while Nottinghamshire and Cheshire currently seek to build it into routine policing. Independent academic evaluators, commissioned by the Home Office to evaluate the MRA in 3 police force areas: Kent; Greater Manchester and West Mercia, found MRA theory to be sound, referring positively to police using this report as ‘The Sutton Bible’. This Primary Research Paper presents important analysis.
Counter-Terrorism and Democracy Transition in Russia
By Anna Tabolina, Far Eastern State University, Vladivostok, Russian Federation
The purpose of this essay is to open up East and West dialogues by critically discussing the measures that Russia is undertaking in order to tackle terrorism and to discuss how this impacts upon the provision of security in a nation recently undergoing such relatively rapid change.
Targeted Intervention Effects on Antisocial Behaviour
By Dr Boaz Shulruf, Faculty of Education, University of Auckland, New Zealand
The current study reports on an evaluation of a school-based intervention aimed at altering at-risk primary students’ self-perception and social awareness as an avenue to mainstream citizenship rather than delinquency and criminal activity. Fourteen students participated in a pilot intervention programme operated once weekly over four months. Programme activities were focused on raising awareness of antisocial behaviours and awareness of personal life quality. The evaluation applied a mixed-methods approach using both quantitative and qualitative data. Evidence for improvement in children’s self-perception was identified as well as effective methods facilitating such changes. Implications of the findings for further intervention programmes and evaluations are discussed.
The relationship between community attitudes and recent racial vilification laws in Victoria Australia: A comparison of a legal and extra-legal classification model. By Kristine Muraca and Terence P Bartholomew, School of Applied Sciences, Forensic Psychology Program, School of Psychology, Deakin University, Melbourne, Australia
This study assessed the level of consistency between the elements prescribed in Victoria, Australia’s Racial and Religious Tolerance Act (2001) and the criteria utilised by a sample of the general population in that state. A random sample of 197 adult Victorians was asked to provide their opinions about a hypothetical vignette where seemingly racist comments were made. Based on existing research and theory, it was anticipated that participants’ classifications of conduct as racial vilification would be better predicted by factors not included in the legislation, than legislatively-defined considerations. Results indicate that the legal model, which included the elements of ‘incitement’ and ‘basis of race’, was a significant predictor of classifications of racial vilification. However, the proposed ‘extra-legal’ model, which included ‘race of the target’, ‘race of the perpetrator’, ‘intention’, and ‘perceived seriousness’, also emerged as a significant predictor of respondent classifications. Although the legal model did in fact emerge as a more effective predictor, a hybrid model including the legally prescribed elements as well as ‘perceived seriousness’ had the greatest predictive ability. It is concluded that the public, as potential jurors, show a preference for grounded ‘act-based’ factors when determining whether a behaviour constitutes racial vilification or not, and that the tenets of Victoria’s Racial and Religious Tolerance Act (2001) largely reflect these intuitive criteria.
The Effect of Initial Meeting Context and Video-Mediation on Jury Perceptions of an Eyewitness
By Chris Fullwood, Amy Marie Judd, and Mandy Finn, School of Applied Sciences, University of Wolverhampton, UK
Video-mediated testimony in the courtroom has become more widespread since introduced as a method to aid vulnerable witnesses. Despite many benefits, research indicates that individuals are perceived more negatively over video links in comparison to face-to-face contact. Studies have also shown that an initial face-to-face meeting can improve subsequent person perceptions across video. The current study compared participant perceptions of an eyewitness in three conditions: face-to-face testimony, video testimony and video testimony with an initial face-to-face introduction. Results suggest that although impressions of the eyewitness were more negative when the testimony was given via video (compared with face-to-face), this did not impact upon the jury’s decision to convict the accused. Furthermore, the initial face-to-face meeting did not significantly improve the jury’s perceptions of the eyewitness. Video-mediated impressions may be more negative due to social distance and the attenuation of visual cues.
“If They Are Dead, Tell Us!” A Criminological Study of the “Disappearances” in Kashmir
By Teresa Crew, Postgraduate Student, University of Wales, Bangor
Cradled in the lap of majestic mountains of the Himalayas, Kashmir is one of the most beautiful places on earth. This paradise is now hell for many Kashmiris due to the prolonged war between India and Pakistan since the end of the British Empire and subsequent partition of the Indian Subcontinent. This paper focuses on the enforced disappearances in Kashmir. The aim of this study is to further develop the study into the victims of State harm. In order to do this, Kauzlarich et al's 'Victimology of State Crime' is utilised, and their general propositions of State crime are tested with reference to the disappeared in Kashmir. This study holds with Kauzlarich et al's assertion that State crime victimology is a different phenomenon from that of street crime as victims are doubly victimised by the state - once during the actual harm inflicted and then again by the criminal justice process. Whilst the majority of Kauzlarich's propositions were consistent with the situation in Kashmir, the concept of secondary victimisation was underdeveloped throughout the original Kauzlarich et al paper. This concept, in relation to Kashmir, is developed in this paper.
The Public Discourse on Corruption in Greece
By Effi Lambropoulou, Panteion University of Social and Political Sciences, Greece.
Perceptions of corruption have significant impact on a country’s awareness of the issue and thereby on the success of any prevention measures. This paper provides a brief overview and summary of preliminary findings from an on-going study funded by the European Commission to examine issues of corruption in 8 EU countries. The study examines the perceptions of political and administrative decision-makers in the various countries, of the representatives of various institutions and authorities, as well as of citizens and media in the European societies. Overall, the project attempts to investigate the difference between institutionalised prevention policies, how they are perceived in daily practice and how effective they are.
Honour-Related Violence (HRV) in Scotland: A Cross- And Multi-Agency Intervention Involvement Survey. by Dr. Roxanne Khan, University of Central Lancashire, UK
This paper documents the results of a small-scale pilot study, which represents the first step towards further research in this overlooked area of violence against women and represents a first step towards responding to widespread calls for multi-disciplinary research to be conducted in this area. ‘Honour’ killings and ‘honour’ related violence is a neglected area in criminology. Such killings and acts of violence are assaults committed against women both by female and male family or community members, for what is considered ‘immoral behaviour,’ that might include women choosing their own marriage partner, allegations of premarital or extramarital sex, being a victim of sexual abuse or rape and even talking innocently with a man who is not a relative. This paper highlights the lack of provision for females facing this specific type of family violence and problems faced by agencies who attempt to help them. This Primary Research Paper provides insights that will remind/inform readers that because this form of violence is shrouded by notions of ‘honour’, there are girls and women living in the UK who are outwardly living calmly in what are effectively dangerous and violent family- and community-governed environments.
Are Reality TV Crime Shows Continuing to Perpetuate Crime Myths?
By Elizabeth Monk-Turner, Homer Martinez, Jason Holbrook & Nathan Harvey, Department of Sociology and Criminal Justice, Old Dominion University, USA
This article examines the portrayal of gender and race in the USA reality television program COPS. Fifty one police officers apprehending sixty perpetrators were content analyzed into four categories including race (of both officer and perpetrator), gender (of both officer and perpetrator), US Uniform Crime Report (UCR) type offense (type I or type II), as well as the specific type of crime depicted. The vast majority of police officers shown on COPS were white male (92%) and the majority of offenders were nonwhite males (62%). Black men were most likely to be shown engaging in a crime of burglary or theft or crimes involving drugs. Hispanic men were most likely to be involved in UCR Part I offenses; however, they were in a distinct minority on these episodes. On the other hand, the most likely scenario for white offenders is to be shown committing an alcohol related offense or causing, or being part of, a domestic disturbance. Few white women were included on the show. One was a police officer and among the other five, one was looking for a lost child and the others were picked up for a variety of relatively minor violations (driving under the influence, drug possession, stolen bike, animal disturbance). No minority women were shown on COPS during this period of evaluation - as either an officer or perpetrator of a crime. The authors argue that media images depicted in COPS are at odds with UCR official crime statistics and reinforce stereotypes and myths about the nature of crime in the United States.
Culture, Violence and Rape Adjudication: Reflections on the Zuma Rape Trial and Judgment
B y Sarah H. Krieg, Ph.D. fellow, Humboldt-Universität zu Berlin, Germany
This paper offers contextualised reflections on the role of cultural arguments during the rape trial of South Africa's former Deputy President, Jacob Gedleyihlekisa Zuma. In conjunction with an analysis of International and South African Law on violence against women, it establishes and applies a gender and culture sensitive framework with which rape adjudication and other criminal law judgments can be examined.
Anti-social Behaviour: Concerns of Minority and Marginalised Londoners
B y Andrew Millie, Lecturer in Criminology and Social Policy, Loughborough University
In the UK there is currently a lot of political and media attention on what has become known as anti-social behaviour (ASB). Concerns about ASB appear to be higher in deprived and/or urban areas. In particular, people living in London are more likely to suffer from ASB. There is undoubtedly real ASB in London; however, this article argues that people will have different expectations of urban living and use of public spaces, resulting in contested notions or tolerances of what is acceptable or anti-social behaviour. This has implications for people’s acceptance of difference or ‘otherness’. With this in mind, evidence is drawn from 10 focus groups with minority and marginalised Londoners. The article argues that our beliefs and expectations of urban living need to be challenged as this is what urban living is all about. Similarly, we should take on board the focus group participants’ assertion that all can be anti-social - rather than focusing on certain groups that ‘don’t fit in’ and entrenching their social exclusion.
Police Administrators in Indiana: A Descriptive Study of Attitudes, Perceptions, and Stressors
By Billy Long, Ph.D., Indiana University Southeast, and Officer Courtney Yerington, Owensboro Police Department.
Surveys were sent to 308 police chiefs and sheriffs in Indiana in the USA - resulting in 229 being returned for a response rate of 74%. The survey device measured six areas of policing: 1) demographics of police executives; 2) departmental characteristics; 3) stressors (external); 4) stressors (internal/work-related); 5) police executive attitudes toward the current use of police resources; and 6) police executive perceptions of the efficacy of current police strategies and tactics. Results showed that Indiana police departments and sheriff’s offices are mostly small departments with little turnover and are rarely accredited by the Commission on Accreditation for Law Enforcement Agencies (CALEA). Civilian Review Boards and Early Warning Systems are rarely used to address police misconduct. Indiana departments are overwhelmingly white and male and attempts to increase diversity have failed. Police executive stressors were highest in the area of perceiving courts as too lenient, the criminal justice system as ineffective and media reports about police as overly hostile. Similarly, they indicate significant sources of stress in the areas of financial resources for the department, poor equipment, and dealing with complaints about their officers. Chiefs and sheriffs indicate strong support for the use of police resources for tracking sex offenders and enforcing drug laws. Problem areas were identified in that police executives are not familiar with research on policing. These misunderstandings result in stress on the part of police executives. Areas of misunderstanding include the effectiveness of random patrol and enforcing anti-marijuana laws. Policy implications are discussed.
Race, Diversity and Criminal Justice in Canada: A view from the UK
By David Denney, Department of Health and Social Care, Royal Holloway, University of London, UK, Tom Ellis, Institute of Criminal Justice Studies, University of Portsmouth, UK, and Ravinder Barn, Department of Health and Social Care, Royal Holloway, University of London, UK
This article examines the way in which those employed in the Canadian criminal justice system perceive race and diversity, and how such perceptions could affect professional practice. By drawing on research carried out under the Canadian High Commission Institutional Research Program, the paper has a number of purposes. Firstly, to explore the possibility that disparities in the outcomes of courtroom proceedings could be related to the perceptions and practices of those who play a key part in the sentencing process. Secondly, to examine the nature of current anti-racist criminal justice practices in one province of Canada. Thirdly, the paper also makes recommendations for the development of future antiracist training. Finally, the paper discusses the implications of the findings with respect to developments in the British criminal justice system.
Black and Asian Police Officers and Support Staff: Prejudice, Identity, Agency and Social Cohesion
By Mike Sutton, Nottingham Trent University, Barbara Perry, University of Ontario Institute of Technology, Catherine John-Baptiste, Nottingham Trent University and Glen Williams, National Black Police Association
This primary research paper presents a review of research that finds that the British Government’s new social cohesion agenda does hold promise for racial and ethnic prejudice reduction – but that social cohesion policies and practice must include at their core policies to reduce institutional racism in British police services. Analysis of the literature reveals that considerably more research is required to examine the precise nature and dynamics of institutional racism within the police services. There is a need to understand how racism against Black and minority ethnic (BME) police employees, and police racism against BME communities, influences social cohesion. That this is important, given the British government’s current social cohesion policy agenda, is patently clear. Considerably more research is about to be undertaken in this area by the authors of this paper and the results will be published in the academic press, disseminated at conferences and presented in training programmes.
Reasons for Supporting and Opposing Capital Punishment in the USA: A Preliminary Study
By Eric G. Lambert, and Alan Clarke (both at Utah Valley State College) and Janet Lambert
The death penalty is a controversial subject in our society. Research has explored why people support or oppose capital punishment. Most the literature to date looks at the reasons provided one at a time. In this study, a multivariate analysis was conducted to see which reasons best explain the observed variation of support and opposition for capital punishment. It was found that emotional retribution, emotional opposition, morality, and law and order, were the only reasons which had statistically significant effects on the degree of death penalty support among college students at a Midwestern university. Other variables, such as fear of crime, religious measures, other punishment ideologies, and personal characteristics (which earlier studies found statistically significant using bivariate analysis) were not statistically significant in this study. The results suggest the need for greater attention to and more study of death penalty attitudes using multivariate analysis.
Just Deserts: University Students' Inclination to Nullify the Law
By Morris Jenkins and Bradene Moore, both at University of Toledo, USA Professors Jenkins and Moore present findings from a groundbreaking small-scale exploratory study of circumstances that might influence juror’s decisions not to follow the law in their determination of a trial verdict.

INTERNET JOURNAL OF CRIMINOLOGY
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 23 June 2023
The relationship between criminology and criminal law: implications for developing Chinese criminology
- Honglan Shuai 1 &
- Jianhong Liu 2
Humanities and Social Sciences Communications volume 10 , Article number: 350 ( 2023 ) Cite this article
6167 Accesses
Metrics details
- Criminology
During the last four decades, Chinese criminology has grown steadily but modestly. One consensus is the lack of a clear understanding of the relationship between criminology and criminal law. This paper attempts to provide a critical review of the relationship between the two disciplines by first tracing the historical development of criminology in both China and Western countries. It then clarifies the distinctions and overlaps between criminology and criminal law and explains how this relationship has influenced the growth of criminology in China. It concludes by proposing implications for developing criminology in China, particularly discussing potential collaborations that could be forged between criminology and criminal law and how such partnerships can benefit both fields in China.
Similar content being viewed by others

Normative analysis of the paternity presumption in Article 1073 of the Civil Code of China
Joint liability and aggravation? An inspection of legislative and judicial practices in cases of the crime of the abduction, sale, and purchase of women and children in China
The logic of the slave patrol: the fantasy of black predatory violence and the use of force by the police, introduction.
Over the last four decades, criminology in China has evolved. However, a vast body of literature argued that its expansion has been relatively slow (Cao and Hebenton, 2018 ; Cao et al., 2014 ; He and Zhuo, 2016 ; Hebenton and Jou, 2010 ; Liu, 2021 ; Triplett, 2018 ). One problem is the lack of clarity about the link between criminology and criminal law. Contemporary scholarship in criminology and criminal law has grown into a vast field. Their overlaps and differences have created significant uncertainty about the relationship between the two. In China, many consider criminology a part of criminal law, while others consider it a social science field. As a result of this ambiguity, scholars in each field are largely unacquainted with the other’s subject matter.
Notwithstanding this ambiguity, this paper argues that progress in one field can benefit greatly from knowledge generated in another. Before providing concrete recommendations to strengthen the collaboration between and growth of Chinese criminology and criminal law, we start by revisiting the historical trajectory of Chinese criminology. We then proceed to provide a thorough analysis of the activities of the two fields before launching into explicating the intricate relationship between them. We do so by examining the relationship between criminology and criminal law both in China and Western democracies, summarising the significant influence of criminology on the development of criminal law with examples from the West and demonstrating the limited development of Chinese criminology. Relying on both the historical developmental paths and contemporary overlaps and distinctions between the two fields in the West and China, this paper concludes by providing three recommendations for the growth and development of criminology in China.
Relationship between criminology and criminal law in the West
The two ideas of “punishment” (criminal law) and “crime” (criminology) shared the exact intellectual genesis. The development of the former could be traced to Beccaria’s seminal work On Crimes and Punishments in the 18th century, which, as one part of the classical school, was also the origin of criminology (Walters and Bradley, 2019 ). However, during the subsequent century, human behaviour became a branch of natural science that could be researched using scientific approaches (see Mannheim, 1972 ; Wright, 2010 ). Under this influence, the positivist school gradually displaced the classical school of criminology. Modern criminology, as a scientific discipline, arose against this backdrop. What started as one unity under Beccaria’s paradigm of studying the causes and reactions to crime has evolved into two distinct developmental paths—criminology and criminal law.
The rise and development of classical and positivist criminology schools reveal the overlap and differences between criminology and criminal law in the West. On the one hand, criminology and criminal law are inextricably linked. First, they have connections in origin. By emphasising the rule of law and individual dignity, Beccaria, a noteworthy representative of the classical school of criminology, is known as the father of modern criminal law (Hostettler, 2011 ). The classical school of criminology is regarded as laying the groundwork for criminal law today. Second, both disciplines are involved in the study of crime. Criminal law regulates crimes that seriously danger society and should be punished according to the criminal code. These crimes are also the research subjects of criminology. In addition, some deviant behaviours that have minor danger to society or have not been provided in the criminal code may be explored in criminological research. Third, these two disciplines have ideals and values in common. Criminal law aims to realise the rule of law by identifying and punishing criminal and criminal behaviour. Criminology, based on the observation of crime phenomenon, explores the regularity of crime, particularly causes of crime, to prevent and control crime. They both serve to achieve crime control, maintain social order and protect public security. Fourth, as criminology and criminal law evolved, studies on topics in one discipline touched upon those in the other. For example, criminologists have been studying domestic violence, which criminal laws often did not address during the early era. However, as society develops and criminal law improves, domestic violence is criminalised and becomes an important topic discussed by scholars in criminal law.
On the other hand, criminology is distinguished from criminal law in perspectives like orientation, research methods, procedure, and so on. Criminal law concentrates on the legal norms of crime and the idea of legal dogmatic through applying interpretative, logical and inference methods. In contrast, criminology studies individual criminals or offenders using scientific or empirical methods (qualitative and quantitative research methods), such as surveys, interviews, experiments, content analysis and so on (Laufer, 2017 ; Mannheim, 1972 ). Procedurally, criminology is active; researchers actively discover social problems, observe crime phenomena, analyse data, draw conclusions, and make suggestions to governments or policymakers. However, criminal law procedure is passive: it cannot be initiated until a crime is reported, a criminal is arrested, or a criminal lawsuit is filed. For example, criminal law might not deal with minor theft if victims do not report it, while criminologists should still research it through a victimisation survey or report. Essentially, criminal law is a discipline focusing on criminals’ responsibilities and punishments, while criminology studies the nature and causes of crime and crime prevention at individual and social levels. Criminal law academics see criminals and non-criminals as equal. In contrast, criminologists see distinctions between criminals and non-criminals and argue that criminals should be treated rather than punished, given that crime is a disease (White et al., 2017 ).
The connection and distinctions between criminology and criminal law have aided the enormous advancement of both disciplines, as each may benefit significantly from the knowledge created in the other. As an example, this paper will look at the significant impact of criminology on criminal law in the West.
Great influence of criminology on criminal law in Western societies
The field of criminology, along with the broader academic trend of interdisciplinary growth and application of empirical research approaches, has dramatically influenced the development of criminal law in Western countries.
Criminological contributions towards theoretical innovation in criminal law
For many years, criminology has been regarded as an interdisciplinary science or an integrated discipline encompassing sociology, psychology, biology, economics, political science, etc. The scientific paradigms, interpretation tools and methodologies utilised in other social science disciplines constitute the bedrock for conducting research in criminological studies. In contrast, as a normative discipline, criminal law tends to rely on explanatory, logical and reasoning methods as its primary research methods; it concludes conviction and sentencing within the scope of existing legal norms or regulations (Zheng and Yang, 2014 ). Criminology has inspired researchers in criminal law to look at their field from a more scientific and objective perspective. For example, from a criminological perspective, American law professor Herbert Leslie Packer (1925–72) proposed two criminal justice systems models: the crime control and due process models (Packer, 1964 ). The former emphasises protecting victims’ rights and maintaining social stability through repressing criminal behaviours with as few restrictions on the authorities’ power of fact-finding as possible; the latter aims to protect defendants’ rights by restricting administrative power and requires police and prosecutors to observe the principle of presumption of innocence when investigating, examining, and interrogating suspects or defendants (Packer, 1964 ).
Application of empirical methods in criminal law
As a scientific discipline, criminology is mainly realised through empirical research methods. However, the general wisdom in criminal law is that punishment is a philosophical issue, not an empirical one (Von Hirsch, 1976 ). Despite this, empirical research is not new in criminal law (Ho and Kramer, 2013 ), and criminal justice academics have long benefited from social scientific research on crime causes and crime rates, or, put, from criminological research (Weisberg, 2013 ).
Since the 1900s, empirical research methods have been applied in dealing with crimes (Kritzer, 2009 ). Many European countries and nearly half of US states routinely publish statistics on crime and criminal cases (Goebel, 1912 ; MacDonald, 1910 ). As an essential forerunner of the legal realist movement, American legal scholar Roscoe Pound ( 1910 ) emphasised the significance of the social sciences in law in his well-known publication “Law in Books and Law in Action”. In addition, the American Institute of Criminal Law and Criminology was established in 1909 to advance the scientific study of crime, criminal law, and procedure (Rundell, 1912 ). During this period, empirical legal researchers focused on studying criminal justice systems, such as comparing cases with private attorneys and paid public defenders (Wood, 1916 ) and examining the behaviour of magistrates in misdemeanour trials (Everson, 1919 ).
During the 1920s and 1930s, the focus shifted to crime surveys. One notable example was the Cleveland Crime Survey, which included prosecution, police administration, criminal courts, and corrections (Pound et al., 1922 ). It is believed that most empirical legal work during this period was exclusively carried out by scholars in the United States (Kritzer, 2009 ). Starting in the mid-1960s, the law and society movement (Friedman, 1986 ) and the law and economics movement thrived, promoting the broader use of empirical methods among legal scholars (Kalven and Zeisel, 1966 ). Footnote 1 Empirical legal studies (ELS) developed more influentially around 2000 (Weisberg, 2013 ). The Journal of Empirical Legal Studies (JELS) and the Society for Empirical Legal Studies (SELS) were founded in 2004, and the first annual Conference on Empirical Legal Studies (CELS) was held in 2006.
Transformed idea of punishment in criminal law
The rehabilitation idea of criminology has deeply influenced the punishment idea of criminal law. Criminal law scholars commonly regard punishment as efforts based on revenge and deterrence, with their justification being retribution or retributive justice. In comparison, criminologists are more inclined to advocate consequentialism, a forward-looking rational approach to achieve rehabilitation or neutralisation (Koppel et al., 2018 ). Over time, the rehabilitation idea of criminology has gradually been adopted by the legal systems of Western countries. For example, the European Convention on Human Rights provides clear and detailed laws and regulations regarding rehabilitation measures, such as safeguarding and regulating the use and disposal of any criminal records (Ovey, 2014 ). The Rehabilitation of Offenders Act 1974 (c.53) passed by the British Parliament is an example. In addition, the United States Code has emphasised that “imprisonment is not an appropriate means of promoting correction and rehabilitation.” Footnote 2 Furthermore, Massachusetts’ juvenile justice system has successfully applied rehabilitation instead of punishment (Macallair, 1993 ). All the above legal provisions demonstrate the spirit of humanitarianism and rehabilitation within criminal legal systems.
Also, most criminal law scholars hold the view that there is no significant difference between criminals and non-criminals, while criminologists posit a distinction between criminals and non-criminals (White et al., 2017 ). Thus, another topic concerning punishment is ensuring fair treatment for criminals who commit similar crimes. When modern criminal law emerged, minors and adults, or first offenders and recidivists, were treated equally and subjected to the same penalties (Richards, 2011 ). For example, no separate category of juvenile offender could be found in Western legal systems before the mid-19th century, and in Australia, six-year-old children were incarcerated in prisons (Cunneen and White, 2011 ). However, this ideal of absolute equality in criminal law was criticised because the ultimate result was inequality (Li, 2010 ). In criminological research, offenders have been studied according to gender, age, occupation, education, and other demographic characteristics. Criminologists have researched specific subjects, like juvenile delinquency (see Agnew, 2001 ; Shaw and McKay, 1942 ), white-collar crime (see Nelken, 1994 ; Sutherland, 1945 ), and so on, based on those subjects’ distinctive features. Thus, the equality idea of traditional criminal law has been dramatically influenced by criminology. For example, most countries now have specific procedures for treating juveniles in their legal systems, such as juvenile detention centres and courts, and matters involving children are commonly treated as civil rather than criminal cases (Richards, 2011 ). Therefore, criminological theories provide a reference for the more scientific and equal provisioning of criminal law.
Establishment of criminal policies and criminal legislation
Another influence of criminology on criminal law can be understood from the criminal policy perspective. The term criminal policy (German: Kriminalpolitik) was coined by the German legal scholar von Feuerbach (1775–1833) in his 1801 Textbook of Criminal Law Generally Applied in Germany, describing how governments established crime prevention policies through scientific methods. In 1898, another legal scholar and criminologist, Franz von Liszt (1851–1919), further proposed that goal-oriented social policy was the best and the most effective criminal policy (Gallo and Kim, 2016 ). Both von Feuerbach and von Liszt emphasised the significant role of scientific methods in criminal policy research and that of criminal policy in legislation. The research methods applied by criminal policy researchers are similar to those commonly used in the social sciences for programme evaluation (Babbie, 2015 ), given that criminal policy comprises a broad convergence of criminal law, criminology, criminal sociology, criminal psychology, and political science.
As suggested by Zaffaroni and Oliveira ( 2013 , p. 331), criminal policy is not only considered “a science of observation” (criminology) but also “the art of organising the fight against crime” (criminal law and criminal justice). To accurately explain responses to crime, criminal policy researchers should pay attention to the police and judicial statistics to verify the effects of law implementations (Zaffaroni and Oliveira, 2013 ). This observation does not constitute criminal policy per se but calls attention to the absence of legitimate criminal policy. According to Hans-Heinrich and Weigend ( 1996 ), recent fundamental advances in criminal policy can be attributed to criminology. Also, as art, criminal policy is created to drive society toward resisting crime by employing specific means to achieve previously established objectives (Ancel, 1981 ). It prepares effective strategies for reacting to crime, laying the foundation for criminal law and criminal justice (Zaffaroni and Oliveira, 2013 ). This paper will take the American “get tough” criminal policy as an example.
After the Civil Rights Movement in the 1960s, urban race riots in the United States led to sharp increases in the rate of violent crime. In 1970, the violent crime rate was about 364 per 100,000, compared with 161 per 100,000 in 1960 (Latzer, 2016 ). Attempts to rehabilitate criminals and use indeterminate sentencing during such times with rising crime rates proved ineffective (Martinson et al., 1974 ). Then, the political orientation began to shift. The Republicans called for a toppling of the soft policy favouring offenders’ rights over victims’ rights and advocated “enforcing law and order” and “fighting violence on the streets” (Gest, 2003 , p. 5). Thus, the get-tough criminal policy was established, marking a policy shift from rehabilitation orientation to punishment orientation (Mears, 2010 ). Correspondingly, the Supreme Court began favouring punishing offenders more severely (Goodstein and Hepburn, 1985 ). For instance, victims were protected in rape cases instead of being blamed.
Effective criminal justice (by criminal justice evaluation research)
Criminological research has played an essential role in evaluating the deterrence effect, which almost all criminal law systems in the world regard as their “primary and essential postulate” (Morris, 1966 , p. 631). As early as 1959, scholars suggested conducting controlled experiments in law to make criminal justice policy less discriminatory and less influenced by factors like race, sex, class, etc. (Zeisel et al., 1959 ). This suggestion later pushed Chief Justice Burger’s Advisory Committee on Experimentation in the Law to legalise controlled experiments in criminal law (Federal Judicial Centre, 1981 ). However, numerous obstacles, such as ethical objections and lack of funding, led to slow progress in this area in the United States and United Kingdom (Farrington, 1983 ) until the early 1960s, when controlled experiments thrived in a few correctional agencies and private justice research centres (see, for example, Empey and Erickson, 1972 ; Empey and Lubeck, 1971 ; Keve, 1976 ). A famous experiment testing Release on Recognizance (ROR) as an alternative to money bail contributed to ROR finally being adopted by legislatures across the United States and several other countries (Sherman, 1992 ).
Since the 1980s, interest groups have called attention to the under-enforcement of laws against some violent crimes, such as domestic violence, and advocated increasing the severity of criminal justice responses. On May 27, 1984, the US National Institute of Justice announced that arrest was the most effective response to misdemeanour domestic violence, based on the results of a randomised clinical trial conducted with the Minneapolis Police Department, where arrest had been the most common police policy for those cases for two years (Sherman, 1992 ; Sherman and Cohn, 1989 ). Nevertheless, this policy was criticised for its minimal use of “science, caution, and delay” (Sherman, 1992 , p. 3) and experiments in six more cities (Atlanta, Charlotte, Colorado Springs, Metro-Dade [Miami], Omaha, and Milwaukee) were conducted later (Sherman, 1992 ). It was suggested that criminology had never achieved such an impact on criminal law until this Minneapolis case (Sherman and Cohn, 1989 ). In conclusion, criminology can empirically evaluate whether implementing criminal law is effective, strongly influencing the practices and policies of the corresponding authority.
These various influences from the field of criminology do not exist independently but have combined to promote the reform and progress of criminal law in Western countries.
Historical trajectory of criminology in China and its relationship with criminal law
Criminology and criminal law in China have a more complicated relationship than in the West. The unclear boundaries between these two largely impede the expansion of Chinese criminology. Accurate knowledge of this relationship requires a thorough review of the historical evolution of China’s criminology.

Traditional criminological thinking in China
It is believed that, rather than being entirely imported from the West, Chinese criminology has native roots (Cao et al., 2014 ; Hebenton and Jou, 2010 ), which Chinese criminologists have greatly neglected. During the traditional Chinese period, many philosophers investigated the crime phenomenon. They put forward numerous illuminating arguments about its causation, which, while not systematic enough to be theories, coincide with some influential criminological mindsets of the modern era (Cao et al., 2014 ). For example, Confucius (551–479 BC), the founder of the Confucian school, said that crime resulted from personal traits and social factors like rulers’ misconduct Footnote 3 and poverty (Confucius, 1999 ). Mencius (372–289 BC), a follower of Confucius, stated that humans were born with good morals and should be educated to maintain their goodness and prevent them from committing offences. He noted the significant link between the economy and crime, emphasising that people were more prone to lose their “goodness” if they did not have “a certain livelihood” (Mencius, 1995 , p. 351). Footnote 4 Xunzi (313–238 BC), another notable Confucian scholar, inherited and further expanded Confucius and Mencius’s ideas, claiming that everyone was born wicked and should be schooled to contain their evil traits (Cao et al., 2014 ). For Xunzi, this evil nature was the internal, but not the exclusive, cause of crime. External political, economic, or environmental factors could trigger an offence (Xunzi, 1999 ). Footnote 5 Unlike these Confucian thinkers, the Chinese Legalist school considered the utilitarian personality and rational choice factors affecting whether people committed crimes, which is remarkably consistent with the classical school of Western criminology founded by Beccaria and Bentham (Cao, 2004 ; Cao and Jou, 2007 ). Generally, “it is not an exaggeration to say that one can find some precursors of almost all contemporary criminological theories in Chinese classics” (Cao et al., 2014 , p. 12).
Despite their differing insights into crime, these Chinese classics, to some extent, explained crime aetiology and proposed implications for governance-oriented crime prevention. The Chinese government employed these classic criminological ideas to address various factors triggering crime conceptually and embedded these ideas into different criminal policies. Thus, criminological ideas were integrated into the criminal legal system in traditional China. These indigenous roots of criminological thinking then developed alongside the criminal justice and penal systems through different dynasties, providing a firm foundation for the later development of Chinese criminology.
Development of criminology in modern China
In modern China, criminology has developed as an independent field through four periods: the 1900s to 1949 [influenced by the West], 1949 to the late 1970s [stagnation stage], the early 1980s to the late 20th century [rapid development] (Zhao and Lan, 1998 ), and the beginning of the 21st century to the present [increasing attention to the criminology paradigm].
The 1900s to 1949
Since the 1900s, Chinese liberal elites have advocated the “social sciences” as an alternative conceptual toolbox (Freedman, 1962 , p. 106), mainly by introducing various Western scientific disciplines. As a scientific discipline, criminology arose in China primarily through translating and interpreting Western criminological classics. Criminology scholars at this time mainly conveyed their personal opinions on Western ideologies rather than conducting empirical research, except for a few sociology-trained scholars like Yan and Liu (Liu, 1946 ; Yan, 1934 ). Both carried out empirical studies on crime within Chinese contexts, focusing on the impact of social and economic inequality on crime. At the same time, criminology courses grew and were adopted by many law schools and legal departments in China. A significant portion of criminological publications written by Chinese criminologists took the form of lecture notes (Zhao and Lan, 1998 ).
1949 to the late 1970s
In the early days after the People’s Republic of China was established in 1949, many criminological studies appeared due to the intense class struggle and prosecution of counter-revolutionary crimes. Criminology was not yet acknowledged as an independent discipline but was included in mainstream criminal fields such as criminal law, prison law and crime investigation (Cao et al., 2014 ; Zhao and Lan, 1998 ). After the mid-1950s, under the influence of leftist ideology, legal nihilism and the former Soviet Union’s negative attitude towards criminology and sociology, the Chinese government believed the socialist system could eliminate crime and paid no attention to criminology. From 1966 to 1976, criminology and all other legal disciplines stagnated due to the rampant trend of ultra-leftism and the interference and destruction of the Cultural Revolution. It is suggested that criminology had no place in China within 30 years of the founding of the People’s Republic (Kang, 1999 ; Zhao and Lan, 1998 ).
The 1980s to the late 20th century
Chinese criminology resurfaced after the end of the Cultural Revolution in the late 1970s. Given the dramatically rising crime rate, especially the youth delinquency rate, which would account for more than 60 per cent of total crime after 1980 (Bakken, 2005 ), the Central Committee of the Communist Party of China (CPC) released the “Report on the CPC’s Attention to the Resolution of Youth Delinquency” in 1979, requesting that social science research departments and political and legal departments focus attention on the causes and regulation of juvenile delinquency (Kang, 1999 ; Zhao and Lan, 1998 ). Relevant scholars and judicial practitioners, therefore, comprehensively employed a variety of disciplines as well as scientific and technological tools to address this issue within Chinese contexts. Criminology in China has since proliferated, with numerous publications on the subject and increasing numbers of scholars and organisations in the field (for example, the establishment of the Chinese Society of Criminology in 1992 was a landmark) (Cao et al., 2014 ; Kang, 1999 ; Zhao and Lan, 1998 ). Also, various political and legal colleges began training master’s and doctoral students in criminology, laying a good foundation for the further development of criminology in China.
Although criminology in China developed rapidly during this period, it was not yet viewed as an independent discipline. Some considered it a branch of sociology (Comparative Criminology Editing Group, 1992 ; Hao, 1996 ), but most leading scholars regarded it as part of criminal law or criminal science (Chen, 1999 ; Chu, 1997 ). The fundamental justification for this was the influential idea of criminal science integration ( xing shi yi ti hua ) proposed by Chu Huaizhi (1997). Chu’s idea continued to be influential in the 21st century when the development of Chinese criminology reached a new stage.
The 21st century
The 21st century has witnessed a paradigm shift in criminology in China and the rest of the world. Internationally, criminological researchers have begun to pay attention to non-Western criminology, realising that Western criminological theories are not always supported in non-Western contexts (Wang et al., 2002 ; Zhang et al., 2007 ). Asian criminology has been deemed one of “the latest projects that seek to decolonise criminology from its Westerncentric bias”, with Jianhong Liu as its “most vocal advocate” (Moosavi, 2019 , pp. 257–258). In 2009, Liu proposed the Asian criminology paradigm as distinguished from the Western criminology paradigm, requiring that scholars “fully consider the diversity of Asia, particularly encouraging the in-depth study of particular Asian contexts, traditions, and theoretical or practice models, as well as topics that are particularly Asian” (Liu, 2009 , p. 8). The advancement of Asian criminology, to a certain extent, has promoted the progress of Chinese criminology, given that China has been a prominent region for Asian criminology research.
Simultaneously, in China, criminology scholars are keeping up with the international pace and putting forward a Chinese criminology paradigm (Li, 2005 ; Zhang, 2001 ; Zhang and Shan, 2005 ), emphasising the inheritance of traditional Chinese criminology ideas, the transformation from traditional speculation to empirical research, and the eventual creation of Chinese-style criminology. Although this innovation has not produced a systematic toolbox of theory and methodology like Asian criminology, it does mark that Chinese criminology has evolved into an independent field with Chinese characteristics rather than focusing on introducing, importing, and verifying Western criminology.
Regrettably, despite these vast breakthroughs, Chinese criminology still has not achieved official recognition as an independent academic discipline, retaining third-level or lower-level status in Chinese universities (as a subfield of criminal law or public security) since a decision by the National Planning Committee of Higher Education in the 1980s (Jin, 2007 ; Liu, 2019 ; Triplett, 2018 ; Zhang, 2007 ). To date, except for some political and law schools and police academies, many law schools paid no attention to criminology courses.
Criminology vs. criminal law: inextricably linked with no clear boundary
The trajectory of criminology in China reveals the unique relationship between Chinese criminology and criminal law: they are inextricably linked with no clear boundary. In traditional China, many criminological ideas were embedded in governance-oriented policies to deal with crime. After the introduction of Western criminology to modern China, more research was conducted on crime in the Chinese context, but criminology was still shackled to criminal law. Rather than using empirical sociological approaches, researchers were accustomed to employing criminal law thinking and methodologies to study crime problems. It was not until the 21st century that Chinese researchers began to realise the importance of the criminology paradigm, which has not yet led to independent disciplinary status. Criminology in China is still considered part of the discipline of criminal law.
Two reasons explain this. First, Chinese criminology was objectively born out of the historical traces of criminal law (Zhang, 2007 ). This idea was further strengthened by the criminal integration put forward in the late 1980s (Chu, 1997 ) and the idea proposed in the 21st century that criminology, criminal law, criminal policy, criminal procedure law and other criminal disciplines together constitute a substantial criminal discipline community (Wang and Zhao, 2007 ). These have influenced the discipline construction of Chinese criminology. Second, academic rationality has not yet relieved a long-standing stubborn bias toward criminal law research (Zhang, 2007 ). In China’s law schools, where the discipline of law is dominant, there is a collective attitude that criminology should be included in criminal law instead of being established independently (Pi, 2004 ).
Generally, the relationship between criminology and criminal law in China notably differs from that in the West, where criminology and criminal law grew into essential and independent disciplines with clear boundaries. In China, criminology has been a subfield of criminal law since the early 20th century. This subordination has inevitably led to the slow development of Chinese criminology.
Limited development of criminology in China
Although criminology in contemporary China has made significant advances (Hebenton and Jou, 2010 ; Triplett, 2018 ), its development remains slow compared to that in English-speaking countries. Cao and Hebenton ( 2018 , p. 2) summarised the growth of Chinese criminology as “continued expansion but still at a slower pace”. Several primary limitations explain the slow pace.
Limited theoretical and empirical research
Over the past 40 years, the number of criminological research papers published annually in China has increased but remained limited. From 1987 to 2009, 147 published empirical criminology articles were identified in China, with an annual average of six publications, about 60 per cent appearing after 2007 (Zhang and Lin, 2010 ). From 2007 to 2016, the total number of criminological research papers in China fluctuated by around 156 per year, based on the CNKI (China National Knowledge Infrastructure) database, and no significant growing trend was seen (Liu et al., 2017 ). From 2017 to 2021, China’s criminology research entered a stable development phase. According to the CNKI database, the overall number of Chinese criminology papers in 2021 is estimated to be 2011, which is almost the same as that in 2017 (2441), 2018 (2130), 2019 (2084) and 2020 (2061) (Zhang and Xing, 2022 ). The good news is that the number of high-quality papers, that is, those published in Peking University Core (Chinese Core collection of Peking University) and CSSCI (Chinese Social Sciences Citation Index) journals, Footnote 6 has increased, indicating that Chinese criminology has developed in-depth and achieved certain breakthroughs (Zhang and Xing, 2022 ). Despite this, there remains a large gap between criminology publications in China and those in the English-speaking world during the same period (Liu, 2021 ; Zhang and Xing, 2022 ), which might be owing to the long-standing limitations of criminological theoretical and empirical research in China.
With the further in-depth study of Chinese criminology, more Chinese scholars have become interested in Western criminological theories and committed to their localisation. However, with little knowledge of mature Western criminological theories and the latest research progress, they often propose arguments or hypotheses that have been extensively criticised or proved insignificant or copy the theories without localised verification (Liu, 2021 ). In addition, empirical studies have been lacking in China (Yao, 2021 ) due to several factors (Yan, 2007 ; Zhang and Lin, 2010 ). First, criminological researchers’ lack of statistical and evaluation training limits their capacity; this may result from the course setting of Chinese criminology, which will be discussed later. Second, access to data is often a significant obstacle to empirical research. Official primary source data are sometimes unreliable and insufficient for definitive empirical research. Although criminology research centres in China have contributed many data, they always focus on specific issues. It remains challenging for investigators to initiate criminological research to get alternative and complementary indicators (Cao et al., 2014 ; Liu and Yu, 2010 ). Third, although Chinese scholars have recognised the significance of the criminological paradigm, they have not yet fully grasped the theory or method (Zhang and Xing, 2022 ). They still have a long way to go to conduct scientific theoretical and empirical research and establish new criminological theories within Chinese contexts or a Chinese criminological paradigm (Liu, 2021 ).
Limited support from all tiers of society
In addition to the weaknesses of criminological research in China, external support is also lacking for Chinese criminology. Cao, Sun and Hebenton ( 2014 , p. 342) state that “gaining access and official support is central for any kind of collaborative endeavour.” In a unitary one-party socialist republic like China, crime is still a sensitive issue, and the government controls organisational development and access to research funding and data (Cao et al., 2014 ; Mei and Wang, 2007 ). The foundation for gaining such support is officially recognised as an academic discipline, which Chinese criminology has not achieved due to its linkage with criminal law. As a result, Chinese criminology obtains less support from diverse sectors of society, including official departments (research funds), academic platforms (organisations and journals), higher education institutions (setting of courses) and so on.
Research funds
In China, research funding is available at various levels of society, from the national to the private sector. Key projects are mainly managed by governmental organisations such as the Ministry of Education, the National Natural Science Foundation of China, the National Planning Office of Philosophy and Social Science and the Ministry of Justice. However, no criminology projects can be found within the catalogue of those supported by the National Social Science Fund of China (NSSFC), the Ministry of Education’s Humanities and Social Sciences Fund, or the National Rule of Law and Legal Theoretical Research (Liu, 2021 ). Provincial and municipal government departments fund local higher educational institutions’ researchers, scientists, and academics. Still, criminology is rarely seen on those discipline lists. Chinese colleges and universities in the lower-level sector offer a range of grants to their faculty. However, they refer to the subject catalogue of the up-level departments when deciding on the discipline list. As a result, young scholars who have finished their criminology education and are committed to contributing to Chinese criminology usually obtain sparse support and opportunities after acquiring positions in higher education institutions. One way to improve the situation might be to turn to funding provided by professional research centres, such as the Crime Research Centre of Peking University, established in 1987, and the Criminology Research Centre of the Tianjin Academy of Social Sciences, established in 1992. However, research centres provide less funding than the state government and provincial and municipal government departments.
Academic platform support
In addition to the lack of research funds, academic platform support is also lacking for Chinese criminology. Although professional organisations in criminology have been established since the late 20th century, most are government-approved organisations. For example, the Chinese Society of Criminology’s president is also a member of the Central Committee of the CPC, and its costs are paid by the National Prosecutors’ College (Cao, 2012 ; Triplett, 2018 ). These organisations are often influenced by political factors when conducting relevant research. High-quality academic journals are another type of academic platform required for developing criminology. A few professional criminology journals are published in China, such as Crime and Correction , Chinese Criminology Review , Footnote 7 China Prison Journal, Issues on Juvenile Crimes and Delinquency , Juvenile Delinquency Prevention Research , etc. However, they are not CSSCI or Peking University Core journals. To date, the Journal of the People’s Public Security University of China (Social Sciences Edition) is the only journal in the Peking University Core collection and CSSCI Extended journals that include a crime research column, and this column has been selected as a famous column by China’s Ministry of Education (Liu, 2021 ; Zhang and Xing, 2022 ).
Setting of criminology courses
In addition to financial and platform support, teaching criminology in Chinese higher education institutions is indispensable for popularising criminology knowledge and cultivating criminology talents. However, the current setting of criminology courses is somewhat inappropriate. On the one hand, existing university courses on criminology have been cut (Kang, 2012 ), possibly because there are few full-time teaching and research personnel in the field or because of the view “that criminology … produces no direct economic benefits and therefore is unlikely to attract any financial support from businesses or government” (Liu and Jiang, 2011 , p. 494). On the other hand, criminology courses are disregarded by most colleges and universities in China. Only the People’s Public Security University of China has established a criminology college and incorporated criminology into the first-level discipline system of public security (Ren, 2019 ).
Limited market for the products
Academia generally acknowledges the considerable role of government. It should be noted, however, that the market usually influences government decisions and actions. Therefore, this paper will examine the Chinese criminology market in depth. Theoretically, many bodies have strongly demanded criminology talents and products, such as the government, which administers crime prevention and control; security technology enterprises that safeguard individuals and groups; individuals concerned with personal protection, etc. Nevertheless, human resource departments of Chinese government institutions, enterprises and social organisations rarely include the major of criminology in their recruitment (Liu, 2021 ). Even political and legal personnel practising in the field (more than two million) have no rigid demand for criminology knowledge (Zhang and Xing, 2022 ).
Besides criminological talent, criminological products are seriously neglected in China (Liu, 2021 ). The reason might be that quite a range of crime countermeasures are not based on random sampling and scientific analysis, leading to so-called unreliable conclusions . Also, there is a lack of adequate scientific evaluation of the implementation effects of most crime prevention projects. Chinese policymakers, thus, have not paid much attention to criminology research or criminologists’ views, despite the normative shift in academic scholars’ understanding of the value of social science and statistics (Cao et al., 2014 ; Zhang and Lin, 2010 ). Furthermore, traditional criminological knowledge is less applicable with the emergence of new crimes in professional fields such as telecommunication, cyber, corporate, and other crimes with certain technical thresholds. All these factors have weakened the practical value of criminology products, making the criminology market an urgent problem that needs to be solved to develop Chinese criminology further.
In general, the unique relationship between Chinese criminology and criminal law, mainly the unclear borders between them, can largely explain the limited development of Chinese criminology. This provides some inspiration for the future development of Chinese criminology.
Implications for developing Chinese criminology
Based on the previous exposition of the relationship between Chinese criminology and criminal law and the limited development of Chinese criminology, this paper puts forward several implications for the development of Chinese criminology, including strengthening both disciplinary distinction and academic collaboration between criminology and criminal law in China and paying more attention to the cultivation of Western analytical thinking and empirical approaches.
Strengthening disciplinary distinction
The development of Chinese criminology is both an academic and a political issue. Scholars, practitioners, and policymakers must actively participate in negotiations and manoeuvres inside and outside institutions to direct the research from the top down (Bourdieu, 1988 ; Zhou, 2019 ). Unlike China, the West developed this discipline from the bottom up over time (Zhou, 2019 ). This difference in disciplinary development modes reveals that the development of Chinese criminology requires official top-down promotion, especially official recognition of independent disciplinary status.
Criminology has proven its independent disciplinary value in that its research subjects and theoretical systems are distinct from other disciplines, especially criminal law. It plays an irreplaceable role in identifying the causes of crime, preventing crime, and maintaining social stability. However, the field’s growth trajectories, social cognition, and talent cultivation differ between Chinese and Western criminology. Therefore, scholars have suggested that Chinese criminology should be active in an independent capacity at the forefront of the legal discipline system (Jin, 2007 ; Zhang, 2007 ), just as criminal law has been in China.
The formal establishment of Interdiscipline in China also provides an opportunity for Chinese criminology, given that criminology is fundamentally interdisciplinary. On December 30, 2020, the China Academic Degrees Committee of the State Council and the Ministry of Education issued the “Notice on Establishing the Category of ‘interdiscipline’ and the First-level Disciplines of ‘Integrated Circuit Science and Engineering’ and ‘National Security’”. Footnote 8 Before that, the National Natural Science Foundation of China established the Department of Interdisciplinary Science (see https://www.nsfc.gov.cn ). Then in September 2022, the fifth edition of the Professional Catalogue of Graduate Education Disciplines was published, which newly established seven interdisciplinary subjects and will be implemented in 2023. Footnote 9 These reforms aimed to establish a new interdisciplinary training mechanism and promote cultivating high-quality composite talents. The category of interdiscipline is now an option in project declarations, especially for provincial and municipal projects. Many colleges and universities have established interdisciplinary disciplines according to the need for talent development. For example, the China University of Political Science and Law has set up Criminal Psychology as an interdisciplinary subject. It is expected that criminology can be found as an independent or interdisciplinary discipline in higher education institutions.
Strengthening academic collaboration
In addition to the disciplinary distinction, academic collaboration is an essential and feasible route to promoting criminology and criminal law in modern China. Marvin Wolfgang raised the idea of collaboration between criminal law and criminology in 1974. He emphasised the intersection of criminology and criminal law with the concept of “disciplinary mix” in his publication “The Social Scientist in Court.” He argued that criminologists could be employed as expert witnesses in court, while criminal justice doctrines could be used to guide criminology research (Wolfgang, 1974). Agreeing with Wolfgang’s concept, Chinese scholars put forward several theories on disciplinary integration, such as the theory of criminal science integration raised by Chu Huaizhi ( 1997 ) and the theory of multidimensional criminal law raised by Liu Renwen ( 2003 ). They state that considering criminology is essential when understanding the knowledge and promoting the development of criminal law. This integration has produced Legal Sociology (or “law and society”), an interdisciplinary field within legal research. It reflects the integration of criminal law and criminology discipline. Given the much tardier development of criminology in China, academic collaboration appears to be more urgent. Scholars in criminal law need to acknowledge the outstanding contribution of criminology to the development of criminal law. At the same time, criminologists should also absorb valuable criminal law knowledge to promote criminology’s innovation and progress.
Significant role of Chinese criminology in criminal law
A shift in attitudes towards criminology has appeared among Chinese criminal law scholars. The prominent criminal law scholar Zhang Mingkai ( 2021a ) has recognised the critical role of criminological research in formulating criminal policy, improving criminal legislation and reforming the penalty system. He stated that criminal law could not exclude any knowledge and methods that assisted in achieving its goals and proposed an equal emphasis on factual science (criminology) and normative science (criminal law) (Zhang, 2021b ). Furthermore, scholars in the fields of criminal law and criminal procedure law have acknowledged metaphysical approaches as outdated (Bai, 2009 ; Chu, 1987 ; Zhao, 2005 ) and started to employ empirical techniques for legal research (Zhang, 2016 ), though most of the research carried out has been more like decoration than rigorous empirical research, given that the researchers were not professionally trained and criminal law was more involved with values than measurable indicators (Liu, 2007 ; Weisberg, 2013 ). Recently, opinions and arguments of various parties have been collected before criminal law amendments and judicial interpretations are issued. Among them, those of criminology scholars and researchers are deemed indispensable.
Additionally, Chinese criminology has proven its significant role in criminal law from different perspectives. From the legislation perspective, criminological research has helped guide criminal legislation and legal amendments in China, especially regarding criminalisation (or decriminalisation) and penalisation (or depenalisation), through evaluating the social effects of policy implementation. Specifically, 2011 saw pickpocketing, burglary and stealing with a lethal weapon being adopted as new types of theft crime by the Amendment (VIII) to the Criminal Law of the PRC (hereinafter “the Amendment VIII”) Footnote 10 (Article 39 of the Amendment VIII). It was criminological research that finally triggered the criminalisation of these behaviours. Revision and amendment to the Chinese criminal provisions involving the amount also required the statistical results of relevant criminological research as reference. As reported by Lu and Liu ( 2017 ), in China, theft cannot be filed as a crime until the amount in question meets the requirement, which is 300–600 yuan under the 1991 Notice, 500–2000 yuan under the 1997 Judicial Interpretation and 1000–3000 yuan under the 2013 Judicial Interpretation. From the punishment perspective, Chinese criminal law mandates different punishments for different offenders, consistent with criminological thinking regarding offender treatment. Footnote 11 For instance, based on the restorative justice theory advanced by the illustrious Australian criminologist John Braithwaite ( 1989 ; 2002 ), China established a juvenile delinquency protection system, a community correction system (Article 269 of the 2018 Chinese Criminal Procedure Law) and a criminal reconciliation system (Articles 288, 289, 290 of the 2018 Chinese Criminal Procedure Law). Footnote 12
From the theory perspective, two criminological theories are applied for crime prevention, especially on some specific crime types. One is the “situational crime prevention” theory, which stresses that a motivated offender, a suitable target, and the absence of a capable guardian must simultaneously occur in a crime (Cornish and Clarke, 2003 ; Smith and Clarke, 2012 ). It is imperative for crime prevention in China, which has taken many measures to prevent favourable situations or opportunities that facilitate the creation of criminal motives, such as criminal objectives (e.g., children, women, the disabled), means (e.g., the use of the internet), weapons (e.g., ammunition, firearms, explosives) and so on. The other is the “broken window” theory, which focuses on the physical and social environment of the community (Wilson and Kelling, 1982 ). According to this theory, a community with a disordered climate (e.g., graffiti walls, dirty roads) signals the offender that the community is not monitored, and crime could be committed there. Therefore, more and more Chinese cities and communities are required to maintain a clean and ordered physical environment, which will increase community coherence and contribute to crime prevention. Generally, growth in criminology has provided opportunities for reform and development of criminal law in China (Yuan, 2017 ).
Significant contribution of criminal law to the advancement of criminology in China
Criminal law has also undoubtedly contributed to the advancement of criminology in China. As Triplett argued, realising the full potential of Chinese criminology partially depends on progress in other areas, such as the Chinese rule of law itself (Triplett, 2018 ). For any research activity, meeting social demands and demonstrating research value are as essential as satisfying intellectual knowledge (Zheng and Yang, 2014 ). The successful development of criminal law in China has offered many new topics for criminology. For example, Bai ( 2001 ; 2003 ) believed that rules (principles) behind criminal law provisions were difficult to see but did exist. Therefore, he explored to what extent the weight of crimes explained the severity of penalties by sorting, quantifying, and analysing more than 400 crimes under Chinese criminal law, recognised as an empirical study of criminal norms (Bai, 2001 ; Bai, 2003 ). Attempts to examine criminal law from a criminological perspective and study the content of legal norms using empirical research methods will inevitably result in corresponding interdisciplinary results—more specifically, the progress of criminology. Therefore, collaboration is particularly essential for promoting the development of both fields. The story of criminology is inseparable from the support of criminal law while also driving progress and innovation in criminal law.
Facilitating the collaboration of criminal law and criminology through the interdisciplinary or transdisciplinary approach
Collaborative working between two or more disciplines often requires specific methods to synthesise broad perspectives, knowledge, and skills in an academic activity. The methods are usually acknowledged as interdisciplinary or transdisciplinary approaches, through which researchers can answer questions or address problems that are too complex or too big to be fully understood by a single discipline or profession (Klein and Newell, 1997 ). The interdisciplinary approach can be categorised as method crossing, theoretical introducing, problem pulling, and culture blending based on different perspectives. The first two approaches often combine methods or theories from diverse disciplines or transplants methods or theories from one field to another. The inter-influence between criminology and criminal law in China mentioned in the previous parts demonstrated the employment of these two approaches. Thus, this part focuses on the problem-pull approach, which might be the most effective approach for facilitating collaboration between disciplines, considering the other approaches involves narrowly, usually involving one aspect.
The problem-pull approach or perspective involves an interdisciplinary synthesis process centred on significant problems that emerge from reality. It has been applied in increasing multidisciplinary studies and has attracted much attention in China. For example, on April 06, 2023, the National Office for Philosophy and Social Sciences in China released the 2023 NSSFC Project Application Guide. Compared to the previous guides that provided topics within every single discipline, it added selected synthesis topics for the first time. Footnote 13 It encourages applicants to conduct interdisciplinary research, focusing on major theoretical and practical issues related to the overall development of the party and the country and the critical fundamental theoretical and frontier academic issues associated with the construction of philosophy and social sciences with Chinese characteristics. For example, one of the synthesis topics is “Research on the Modernisation of National Security System and Capabilities”, which involves the post-event governance of criminal law and the pre-event prevention of criminology. It proves that China has officially offered opportunities for interdisciplinary research, such as between criminology and criminal law, from the perspective of more significant issues.
As the fourth approach, cultural blending refers to the mutual penetration and integration of the cultural backgrounds on which different disciplines rely. On this task, the interaction between criminology and criminal law involves cultural conflicts between the West and China since criminology in China is introduced earlier primarily from the West. How to address the cultural conflicts and achieve the cultural blending between these two disciplines is another task that requires another paper to handle.
Cultivating western analytical thinking based on Chinese native roots
Strengthening the disciplinary distinction and academic collaboration between criminology and criminal law is recommended based on the different characteristics of their relationship in the West and China. However, Western experiences, especially the Western analytical thinking mode, should not be ignored in promoting Chinese criminology.
The thriving Chinese approach to crime has always regarded it as a normative or good governance issue that requires applying holistic thinking. In contrast, the Western approach considers the study of crime a scientific enterprise whose main features are analytical thinking and empirical research methods (Nisbett et al., 2001 ). Footnote 14 Differences between holistic and analytic thinking inevitably lead to different ways of reasoning about crime in China and the West. Specifically, rulers and scholars in China have been accustomed to interpreting crime causality from a relational and dynamic perspective, considering the combined effects of various changing factors. They believe specific issues should be addressed through specific analyses and that different principles apply to different people and circumstances. Thus, no general rules or patterns for addressing crime can be derived. However, Westerners tend to regard crime as having general or universal rules or patterns that can be used empirically to explain cause and effect. These rules or patterns do not change and apply to all contexts. Most other potentially relevant factors can be excluded as intervention or control variables. Therefore, modern criminology has been established as a scientific discipline in the West, comprising prominent theories and methods conducive to crime studies.
To a certain extent, the Chinese thinking mode has resulted in a lack of mature criminological theories and empirical research methods, which has hindered the establishment of scientific criminology in China. Thus, the further advancement of Chinese criminology requires official recognition of independent disciplinary status and cultivation of the Western analytical thinking mode based on China’s native roots.
Chinese criminology has grown slowly due to its complicated relationship with criminal law. Unlike in Western countries where criminology and criminal law are closely related but also distinguished, in China, criminology and criminal law have been closely related for decades with no clear disciplinary boundaries. Chinese criminology has not yet achieved officially recognised independent disciplinary status. Given the breadth and prosperity of Chinese criminal law, modern China must develop the criminology discipline. The possible implications include paying more attention to disciplinary distinction and academic collaboration between criminology and criminal law, and cultivating Western analytical thinking in China. The development of criminology in the pursuit of rehabilitative justice will offset the consequences resulting from extensive criminal law aiming at punishment, ultimately promoting the dual goals of “control of crime” and “rule of law” in modern China.
Data availability
Data sharing is not applicable to this article as no datasets were generated or analysed during the current study.
For example, the “American Jury Project”.
18 U.S. Code § 3582, “Imposition of a Sentence of Imprisonment” ( Legal Information Institute) . https://www.law.cornell.edu/uscode/text/18/3582 . Accessed 23 November 2022.
孔子在《论语·子张》中说到: “其身正, 不令而行。其身不正, 虽令不从。” “When a ruler” s personal conduct is correct, his government is effective without giving orders. If his personal conduct is not correct, even he may give orders, but they will not be followed”.
孟子在《梁惠王上》中指出:“若民, 则无恒产, 因无恒心。苟无恒心, 放辟邪侈, 无不为己。及陷于罪, 然后从而刑之, 是罔民也。” “If they have not a certain livelihood, they have not a fixed heart. And if they have not a fixed heart, there is nothing which they will not do in the way of self-abandonment, of moral deflection, of depravity, and of wild license. When they have thus been involved in crime, to follow them up and punish them:—this is to entrap the people”.
荀子在《荀子·劝学》中指出:“邪秽在身, 怨之所构。施薪若一, 火就燥也; 平地若一, 火就湿也。” “Evil and filthy things exist within themselves and constitute resentment. If you add firewood, the fire will be more vigorous; if you add earth, the fire will be extinguished”.
CSSCI (Chinese Social Sciences Citation Index) is an interdisciplinary citation index programme in China that developed by the Academy of Social Science Research Evaluation Center in Nanjing University of China. A Guide to the Core Journal of China developed by Peking University, often called Chinese core collection of Peking University, is the other database that covers high-quality Chinese academic journals of humanities and social sciences in China. Both have been utilised by Chinese universities and institutes as a basis to evaluate academic achievements and promotions.
According to Zhang and Xing ( 2022 ), Crime and Correction published 36 papers on criminology in 2021, and Chinese Criminology Review published 16 papers on criminology in 2021.
http://www.moe.gov.cn/srcsite/A22/yjss_xwgl/xwgl_xwsy/202101/t20210113_509633.html . Accessed 23 November 2022.
http://www.gov.cn/xinwen/2022-09/14/content_5709784.htm . Accessed 23 November 2022.
Amendment (VIII) to the Criminal Law of the People’s Republic of China [effective] (Laws U.S.C., 2011). http://en.pkulaw.cn/display.aspx?cgid=c3bca3c5ab0ed5c1bdfb&lib=law . Accessed 23 November 2022.
Criminal Law of the People’s Republic of China (2020 Amendment). https://www-pkulaw-com.libezproxy.um.edu.mo/en_law/39c1b78830b970eabdfb.html . Accessed 23 November 2022.
Chinese Criminal Procedural Law (2018). https://www.chinalawtranslate.com/en/criminal-procedure-law-2018/ . Accessed 23 November 2022.
The 2023 National Social Science Fund of China Project Application Announcement, retrieved on April 13, 2023, from http://www.nopss.gov.cn/n1/2023/0406/c431027-32658630.html .
As suggested by Nisbett, Peng, Choi and Norenzayan ( 2001 ), holistic thinking involves “an orientation to the context or field as a whole, including attention to relationships between a focal object and the field, and a preference for explaining and predicting events on the basis of such relationships”, while analytic thinking involves “a detachment of the object from its context, a tendency to focus on attributes of the object to assign it to categories, and a preference for using rules about the categories to explain and predict the object’s behaviour.”
Agnew R (2001) Juvenile delinquency. Roxbury, Los Angeles
Google Scholar
Ancel M (1981) The new social defense: a humanist criminal policy movement (la défense sociale nouvelle: un mouvement de politique criminelle humaniste). Cujas, Paris
Babbie ER (2015). The practice of social research. Nelson Education
Bai J (2001) The gradation of penalties: towards a quantitative analysis. Soc Sci China 6:114–125
Bai J (2003) A quantitative analysis of crimes. Soc Sci China 6:123–133
Bai J (2009) Guanxi criminology, 2nd edn. China Renmin University Press, Beijing
Bakken B (ed.) (2005) Crime, punishment, and policing in China. Rowman & Littlefield Publishers
Bourdieu P (1988) Homo academicus. Stanford University Press, Stanford, CA
Braithwaite J (1989) Crime, shame and reintegration. Cambridge University Press
Braithwaite J (2002) Restorative justice & responsive regulation. Oxford University Press
Cornish DB, Clarke RV (2003) Opportunities, precipitators and criminal decisions: a reply to Wortley’s critique of situational crime prevention. Crime Prevent Stud 16:41–96
Cao L (2004) Major criminological theories: concepts and measurement. Wadsworth Publishing Company, Belmont, CA
Cao L (2012) Recurrent flirtations of law and criminology in the USA. Issue Juvenile Crime Delinq 177:22–30
Cao L, Hebenton B (2018) Criminology in China: taking stock (again). Criminol 43(2):1–5
Cao L, Jou S (2007) Criminological theories and their empirical status. Qunzhong Press, Beijing
Cao L, Sun IY, Hebenton B (Eds.) (2014) The Routledge handbook of Chinese criminology. Routledge, Abingdon, Oxon
Chen X (1999) Criminology research from the perspective of criminal integration. China Legal Sci 6:113–121
ADS Google Scholar
Chu H (1987) One-half causal relationship. Chin J Law 3:27–30
Chu H (1997) Criminal science integration and relational criminal law. Peking University Press, Beijing
Comparative Criminology Editing Group (1992) Comparative criminology. Publishing House of People’s Public Security University of China, Beijing, (eds)
Confucius (1999) The Analects (trans: Bojun Yang & Waley Arthur). Foreign Languages Press
Cunneen C, White R (2011) Juvenile Justice: Youth and Crime in Australia. Oxford University Press
Empey LT, Erickson ML (1972) The Provo experiment: evaluating community control of delinquency. Lexington Books, Lexington, MA
Empey LT, Lubeck SG (1971) The Silverlake experiment: testing delinquency theory and community intervention. Aldine Publishing Company, Chicago
Everson G (1919) Human element in justice. J Am Inst Crim Law Criminol 10(1):90–99
Article Google Scholar
Farrington DP (1983) Randomized experiments on crime and justice. Crime Just 4:257–308
Federal Judicial Center (1981) Experimentation in the law. Advisory committee on experimentation in the law
Freedman M (1962) Sociology in and of China. Br J Sociol 13(2):106–116
Article MathSciNet Google Scholar
Friedman LM (1986) The law and society movement. Stanford Law Review. pp. 763–780
Gallo C, Kim ME (2016) Crime policy and welfare policy. Oxford Handbook Online. https://www.oxfordhandbooks.com/view/10.1093/oxfordhb/9780199935383.001.0001/oxfordhb-9780199935383-e-46 . Accessed 23 Nov 2022
Gest T (2003) Crime & politics: big government’s erratic campaign for law and order. Oxford University Press on Demand
Goebel Jr J (1912) Prevalence of crime in the United States and its extent compared with that in the leading European States. J Am Inst Crim Law Criminol 3(5):754–769
Goodstein L, Hepburn JR (1985) Determinate sentencing and imprisonment: a failure of reform. Anderson Publishing Company, Cincinnati, OH
Hans-Heinrich J, Weigend T (1996) Lehrbuch des Strafrechts, Allgemeiner Teil. Duncker & Humblot, Berlin
Hao H (1996) On the disciplinary nature and status of criminology. J People’s Public Secur Univ China (Social Sciences Edition) 6:56–61
He N, Zhuo Y (2016) Criminology’s new frontier in China: opportunities, possibilities and challenges. Crime Law Soc Change 66(5):439–446
Hebenton B, Jou S (2010) Criminology in and of China: Discipline and power. J Contemp Crim Just 26(1):7–19
Ho DE, Kramer L (2013) Introduction: the empirical revolution in law. Stanford Law Rev 65:1195–1202
Hostettler J (2011) Cesare Beccaria: the genius of “On Crimes and Punishments”. Waterside Press
Jin G (2007) Discussion on the construction and development direction of the discipline of criminology in China. J People’s Public Secur Univ China (Social Sciences Edition) 23(5):76–82
Kalven H, Zeisel H (1966) The American jury. Little, Brown, Boston, p. 498
Kang S (1999) The creation, development stage and characteristics of criminology in New China. J Henan Univ Econ Law 4:3–12
Kang S (2012) The function and development of New China criminological research. J People’s Public Secur Univ China 2:1–7
Keve PW (1976) Paul Lerman, “Community treatment and social control” (Book Review). Soc Serv Rev 50(2):342
Klein JT, Newell WH (1997). Advancing interdisciplinary studies. Handbook of the undergraduate curriculum: a comprehensive guide to purposes, structures, practices, and change, 393–415
Koppel S, Fondacaro M, Na C (2018) Cast into doubt: free will and the justification for punishment. Behav Sci Law 36(4):490–505
Kritzer HM (2009) Empirical legal studies before 1940: a bibliographic essay. J Empirical Legal Stud 6(4):925–968
Latzer B (2016) The rise and fall of violent crime in America. Encounter Books
Laufer W (2017) The criminology of criminal law. Routledge
Li J (2010) A brief discussion on the relationship between western criminology theory and criminal law. J Chongqing Univ Sci Technol (Social Sciences Edition) 15:57–58
ADS CAS Google Scholar
Li S (2005) A preliminary probe into the research paradigm of criminology in China. J Yunnan Univ (Law Edition) 18(6):51–54
CAS Google Scholar
Liu J (2007) The method of ‘Experience’ and law research. J SWUPL 9(3):33–39
Liu J (2009) Asian criminology–challenges, opportunities, and directions. Asian J Criminol 4(1):1–9
Liu J (2021) Research, discipline, and market: the approach for developing chinese criminology from an international perspective. Chin Criminol Rev 3:2–10
Liu R (2003) Advocate the “multidimensional criminal law”. Stud Law Bus 3:11–13. https://doi.org/10.16390/j.cnki.issn1672-0393.2003.03.004
Liu T (2019) From the periphery to center: criminology in law school undergraduate education. Legal Educ Res 26(31):274–294
Liu X, Jiang T (2011) People’s Republic of China: the state of criminology. In: Smith, CJ, Zhang SX, Barberet R (eds), Routledge Handbook of international criminology, Routledge, pp. 518–528
Liu X, Li W, Li L (2017) An analysis of criminological research in China—based on the CNKI Database (2007-2016). Crime Corr 9:14
Liu X, Yu Y (2010) Analysis of the status of Chinese criminology and its future development. J Shandong Police College 4:83–91
Liu Y (1946) Criminology syllabus. Dadong Shuju, Shanghai
Lu J, Liu C (2017) Research on the governance model of theft under the rule of law: based on analysis of the crime statistics. Modern Law Sci 3:93–111
Macallair D (1993) Reaffirming rehabilitation in juvenile justice. Youth Soc 25(1):104–125
MacDonald A (1910) Criminal statistics in Germany France and England. J Am Inst Crim Law Criminol 1(2):59–70
Mannheim H (ed.) (1972) Pioneers in criminology (No. 121). Patterson Smith Publishing Corporation
Martinson R, Lipton D, Wilks J (1974) Nothing works. Public Interest 35:22
Mears DP (2010) American criminal justice policy: an evaluation approach to increasing accountability and effectiveness. Cambridge University Press
Mei J, Wang M (2007) Social change, crime, and criminology in China. Crime Justice Int 23(97):14
MathSciNet Google Scholar
Mencius (1995) The works of Mencius. In: The Four Books (trans: James Legge), Hunan People’s Publishing House, Changsha
Moosavi L (2019) A friendly critique of ‘Asian Criminology’ and ‘Southern Criminology’. Br J Criminol 59(2):257–275
Morris N (1966) Impediments to penal reform. Univ Chicago Law Rev 33(4):627–656
Nelken D (ed.) (1994) White-collar crime. Dartmouth, Aldershot
Nisbett RE, Peng K, Choi I, Norenzayan A (2001) Culture and systems of thought: Holistic versus analytic cognition. Psychol Rev 108(2):291–310
Article CAS PubMed Google Scholar
Ovey C (2014) Ensuring respect of the rights of prisoners under the European Convention on Human Rights as part of their reintegration process. Registry of the European Court of Human Rights. [Online] https://rm.coe.int/16806f4555 . Accessed 7 May 2022
Packer HL (1964) Two models of the criminal process. Univ of Pennsylvania Law Rev 113:1
Pi Y (2004) Criminology vs criminal law: the end of criminal law discourse hegemony. J Shandong Police College 3:79–83
Pound R (1910) Law in books and law in action. Am Law Rev 44:12
Pound R, Frankfurter F, Fosdick RB (1922) Criminal justice in Cleveland: reports of the Cleveland Foundation Survey of the Administration of Criminal Justice in Cleveland, Ohio (Vol. 8). The Cleveland Foundation
Ren S (2019) Criminology professional development foundation and construction plan. Gong An Jiao Yu (Police Education) 11:59
Richards K (2011) What makes juvenile offenders different from adult offenders? Trend Issue Crime Crim Just 409:1–8
Rundell OS (1912) The time element in criminal prosecutions in Wisconsin (No. 512). The University of Wisconsin
Shaw CR, McKay HD (1942) Juvenile delinquency and urban areas. University of Chicago Press
Sherman LW (1992) Influence of criminology on criminal law: evaluating arrests for misdemeanor domestic violence. J Crim Law Criminol 83(1):1
Sherman LW, Cohn EG (1989) The impact of research on legal policy: the Minneapolis domestic violence experiment. Law Soc Rev 23(1):117
Smith MJ, Clarke RV (2012) Situational crime prevention: Classifying techniques using “good enough” theory. The Oxford Handbook of Crime Prevention. pp. 291–315
Sutherland EH (1945) Is “white collar crime” crime? Am Sociol Rev 10(2):132–139
Triplett RA (ed.) (2018) The handbook of the history and philosophy of criminology. John Wiley & Sons
von Feuerbach PJAR (1801) Textbook of criminal law generally applied in Germany (German: Lehrbuch des gemeinen in Deutschland geltenden peinlichen Rechts). G. F. Heyer
von Hirsch A (1976) Doing justice: the choice of punishments. Hill and Wang, New York
Walters R, Bradley T (2019) Introduction to criminological thought. Pearson Education
Wang GT, Qiao H, Hong S, Zhang J (2002) Adolescent social bond, self-control and deviant behavior in China. Int J Contemp Sociol 39:52–68
Wang M, Zhao B (2007) Building a harmonious society: a historical opportunity for the development of criminology in China—a review of criminology research in 2006. China Legal Sci 2:183–192
Weisberg R (2013) Empirical criminal law scholarship and the shift to institutions. Stanford Law Rev 65:1371–1401
White R, Haines F, & Asquith NL (2017) Crime & criminology (6th edition). Oxford University Press
Wilson JQ, Kelling GL (1982) Broken windows: the police and neighbourhood safety. Atlantic Month249(3):29–38
Wood WJ (1916) Necessity for public defender established by statistics. J Am Inst Crim Law Criminol 7(2):230–244
Wright R (2010) The moral animal: why we are, the way we are: the new science of evolutionary psychology. Vintage
Xunzi (1999) Xunzi (trans: John Knoblock). Hunan People’s Publishing House, Changsha
Yan J (1934) Crime in relation to social change in China. Am J Sociol 40(3):298–308
Yan L (2007) Discussing the routine to the research of criminology again. Legal Forum 22(2):19–27
Yao J (2021) Lombroso in China: an investigation into the history of criminology. Sci Law 1:112–122
Yuan X (2017) The possible contribution of criminology to the study of Chinese Criminal Law. Chin Criminol Rev 1:2–7
Zaffaroni ER, Oliveira E (2013) Criminology and criminal policy movements. Rowman & Littlefield
Zeisel H, Kalven H, Buchholz B (1959) Delay in the court. Little, Brown, Boston
Zhang D (2007) On the formation and development of Chinese criminology. Xin Xibu (New West) 1:249
Zhang J, Xing P (2022) Analysis of Chinese criminology literature in 2021. Crime Corr 2:7–13
Zhang L, Messner SF, Liu J (2007) A multilevel analysis of the risk of household burglary in the city of Tianjin, China. Br J Criminol 47(6):918–937
Zhang M (2021a) Concept usage and creation in criminal law. Stud Law Bus 38(1):3–22
Zhang M (2021b) The development direction of Chinese Criminal Law. Chinese Social Science Today (Law edition)
Zhang W (2016) Chinese school of legal empirical: a growing school. Guangming Daily
Zhang X (2001) The research paradigm of criminology. Chin J Law 5:3
Zhang X, Shan Y (2005) On the research paradigm of criminology. Law Rev 4:17–24
Zhang Y, Lin D (2010) Analysis on symptomatic and causes of lack of empirical research of criminology. J Henan Public Security Academy 4:25–29
Zhao G, Lan Q (1998) Chinese criminology in the twentieth century. Peking Univ Law J 1:90–104
Zhao T (2005) Empirical study on sentencing justice. Wuhan University Press
Zheng X, Yang X (2014) On the mutual relationship and complementarity between criminology and criminal law. Issue Juvenile Crime Delinq 3:19–28
Zhou X (2019) The academic specialization and academic community by comparing Chinese and American sociological disciplines. China Soc Sci Rev 4:18–20
Download references
Author information
Authors and affiliations.
School of Law, Jiangsu University, Zhenjiang, China
Honglan Shuai
Faculty of Law, University of Macau, Macau, China
Jianhong Liu
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Jianhong Liu .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Ethical approval
This article does not contain any studies with human participants performed by any of the authors.
Informed consent
Additional information.
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Shuai, H., Liu, J. The relationship between criminology and criminal law: implications for developing Chinese criminology. Humanit Soc Sci Commun 10 , 350 (2023). https://doi.org/10.1057/s41599-023-01851-3
Download citation
Received : 24 November 2022
Accepted : 13 June 2023
Published : 23 June 2023
DOI : https://doi.org/10.1057/s41599-023-01851-3
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Criminology Research Paper

This sample criminology research paper features: 6300 words (approx. 21 pages), an outline, and a bibliography with 49 sources. Browse other research paper examples for more inspiration. If you need a thorough research paper written according to all the academic standards, you can always turn to our experienced writers for help. This is how your paper can get an A! Feel free to contact our writing service for professional assistance. We offer high-quality assignments for reasonable rates.
Introduction
Criminology and measuring crime, time and space, social class, criminology and explaining crime, criminology and preventing crime.
- Bibliography
Criminology is the scientific study of crime as a social phenomena. Edwin Sutherland (1947) noted in an early analysis that criminology investigates the processes of producing laws, breaking laws, and responding to the breaking of laws.
Academic Writing, Editing, Proofreading, And Problem Solving Services
Get 10% off with 24start discount code.
These processes are three aspects of a somewhat unified sequence of interactions. Certain acts which are regarded as undesirable are defined by the political society as crimes. In spite of this definition, some people persist in the behavior and thus commit crimes; the political society reacts by punishment or other treatment or by prevention. This sequence of interactions is the object-matter of criminology. (P. 1)
Consequently, criminology can be split into three subfields: the study of lawmaking, the study of lawbreaking, and the study of responses to lawbreaking. Because lawmaking and responses to lawbreaking are discussed in other research papers, we shall concentrate on the second branch, lawbreaking.
More Criminology Research Papers:
- Cultural Criminology Research Paper
- Geographic Criminology Research Paper
- Green Criminology Research Paper
- Historical Criminology Research Paper
- Marxist Criminology Research Paper
- Postmodern Criminology Research Paper
- Age and Crime Research Paper
- Alcohol and Crime Research Paper
- Class and Crime Research Paper
- Education and Crime Research Paper
- Gender and Crime Research Paper
- Intelligence and Crime Research Paper
- Literature and Crime Research Paper
- Mass Media and Crime Research Paper
- Modernization and Crime Research Paper
- Race and Crime Research Paper
- Religion and Crime Research Paper
- School Crime Research Paper
- Unemployment and Crime Research Paper
Regarding crime, sociologists have investigated numerous avenues of inquiry. They have endeavored to identify crime patterns, i.e., the manner in which criminal conduct is spread over time, place, and social structure. They have attempted to explain crime by identifying the factors that not only distinguish criminals from noncriminals but also account for its occurrence. In addition, they have investigated how crime might be averted. We shall discuss each of these inquiries in turn. Prior to discussing the distribution of crime, however, we must analyze its measurement.
How do we know what we know? is a fundamental question of any intellectual field. The empirical nature of criminology necessitates the use of the scientific method to observe and record crime. To quantify the nature and scope of crime phenomena, researchers employ a range of methodologies. The majority of criminologists’ scientific approaches are quantitative, aiming to count the number and kind of crimes and their connections. Researchers utilize two key types of quantitative data: secondary data derived from official sources and primary data derived from self-reports of criminal activity and victimization.
Official statistics extracted from police records are the most important source of information used to measure the nature and scope of crime. The Federal Bureau of Investigation has sponsored a statewide endeavor to develop a statistical description of crime in the United States since 1930. Today, more than 17,000 police agencies engage annually in the Uniform Crime Report data collecting and reporting program (UCR). The UCR provides information regarding crimes that are known to law enforcement and offenses that have been cleared by law enforcement, typically through arrest. Criminologists sometimes utilize UCR data to calculate a crime rate based on offenses reported to the police or arrests made by the police. A crime rate is superior to a crime count since the rate takes population into account. For example, UCR data for 2003 in the United States indicate a total of 16,503 homicides known to police, a fairly high amount.
However, given the magnitude of the nation’s population—nearly 280 million people—the murder rate in 2003 was among the lowest in the preceding four decades, at 5.7 murders per 100,000 people (Federal Bureau of Investigation 2004). The UCR provides crime statistics broken down by area, community type, and locality. Information identifying the age, color, and gender of criminals is restricted to crimes that have been cleared by police and for which an arrest has been made.
Until recently, the UCR classed major offenses as “Index” or Part I offenses, and less serious offenses as Part II offenses. Index crimes include the following eight offenses: murder and non-negligent manslaughter, forceful rape, robbery, serious assault, burglary, larceny-theft, auto theft, and arson. Traditionally, criminologists, politicians, and the media have depended on index crime data to follow changes in major crime through time and geography. Index data are a composite that conceal substantial variances in the frequency of each infraction. For instance, larceny-theft accounts for more than 60 percent of all Part I offenses (Federal Bureau of Investigation 2004). Consequently, fluctuations in more severe crimes, like as murder and rape, may be obscured by the vast volume of property crimes, such as larceny. Researchers in the field of criminal justice are aware of this and often separate index crimes into two categories: violent crimes and property crimes.
The FBI is now implementing the National Incident Based Reporting System, a new data collection tool (NIBRS). The NIBRS is intended to build upon the UCR by providing police with more information about criminal events, including the nature of the crimes and the characteristics of the perpetrators. This strategy is novel in two ways. First, the NIBRS analyzes occurrences as its core analytical unit. Second, it extends on the UCR by providing more information regarding the nature and types of individual offenses in each crime episode, such as the victim(s) and offender(s) involved, the type and amount of property stolen, and the characteristics of those arrested.
Even though the UCR and NIBRS include a wealth of information, official records pose a number of challenges. A huge portion of every crime gets unreported to the police, which is perhaps the most serious issue. Unreported crimes are referred to as “dark figures” since their nature and scope are unknown. Another problem of official records is that they are compiled, documented, and reported by non-researchers, making them secondary data. According to Thorsten Sellin (1931), each layer of administration in the gathering of official crime data raises the possibility of distortion, bias, or inaccuracy, hence diminishing the data’s usefulness. The data collected from police records have also been challenged for being political artifacts that reflect the operational logics and goals of law enforcement agencies. In addition, the UCR data collecting rules apply a judgment rule known as the hierarchy rule of classification, which sacrifices data regarding criminal episodes involving many crimes. Frequently, when a crime is committed, multiple laws are broken. However, the hierarchy rule dictates that only the most serious offense is reported to the FBI. The rule produces systematic downward bias in UCR data. A final shortcoming is that government records provide inadequate information about the correlates of crime, such as the relationship between victims and offenders, the racial and sexual mix of offenders and victims, and the drug use of offenders. The NIBRS aims to improve official records in light of the last two concerns, notably the hierarchy rule and the limited correlations between crime.
In large part as a result of concerns about the veracity of official data, academics have invented alternative ways for gathering data on crime. The majority of them are self-report questionnaires. The benefit of survey approach is that researchers directly obtain primary data from individuals in criminal activity. This gives researchers greater control over data collecting and facilitates testing of hypotheses. Typically, self-report questionnaires are available in two formats. One form requires people to disclose their own criminal behavior. The second sort of survey questions individuals about their victimization experiences.
A self-report survey of offending asks a sample of persons if and how frequently they have committed any of a variety of offenses during a certain time period. Thornberry and Krohn (2000) attribute the emergence of self-report methodology to Sutherland’s (1940) observation that respectable middle-class individuals are likely to commit crimes but are unlikely to be recorded in police files. Porterfield’s 1946 work was the first to utilize the self-report method in studies of criminal and delinquent conduct, maybe prompted by Sutherland’s observation. His work established the usefulness of self-reports for criminal and delinquent studies. Short and Nye’s (1958) research is primarily responsible for establishing self-reports as a methodological cornerstone of criminology. Throughout the years, criminologists have devoted significant efforts to enhancing the self-report method by creating strategies that increase the validity and reliability of self-reported crime and delinquency (Hindelang, Hirschi, and Weis 1981).
Self-report investigations of criminal behavior can be distinguished by their substantive focus and sample design. Using schools as sampling points is a frequent method for surveying teenagers. Monitoring the Future, an annual study addressing drug use undertaken with a nationally representative sample of 8th, 10th, and 12th graders, is one of the most renowned instances (Johnston, O’Malley, and Bachman, 1996). Other methods of surveying criminal or delinquent behavior include random samples of the broader population. Nationwide Youth Survey (NYS) is one of the most comprehensive national assessments of delinquency (Elliott 1983). The New York State uses a national probability sampling design to survey approximately 1,700 11- to 17-year-olds about their involvement in delinquency as well as a number of attitudinal and experiential issues. Similar to numerous other self-report surveys, the NYS supplies criminologists with data for addressing etiological questions. In addition, New York State utilizes a panel design, allowing researchers to track children through adulthood.
The other sort of self-report questionnaire is the victimization questionnaire. In this study, researchers ask a sample of individuals if and how frequently they had been victims of specific criminal crimes during a specific time period. The most well-known victimization survey is the 1973 National Crime Victimization Survey (NCVS). This is a twice-yearly, national household survey. In contrast to self-report surveys of offending, which were motivated by the empirical restrictions associated with the police focus on crimes of the lower classes, the NCVS was motivated by the failure of individuals to report crimes to the police. Each year, around 85,000 families and more than 150,000 responders participate, giving the most accurate estimate of real crime in the United States. Unlike the UCR, the NCVS includes information about crimes committed against individuals, regardless of whether the crimes were reported to authorities. Questions address crimes suffered by individuals and their home, whether the offenses were reported to police, as well as victim, household, and perpetrator characteristics in personal crimes. In addition, respondents are asked about their perspectives on the criminal justice system and their motivations for reporting or not reporting crimes. Generally speaking, victimization surveys are limited to the more common and readily identifiable memories. Although it appears that respondents are generally accurate when reporting their experiences as offenders and victims, there is evidence that underreporting is a danger to the validity of self-report studies of both offending (Hindelang et al., 1981) and victimization (Hindelang et al., 1981). (Murphy and Dodge 1981). As a result of embarrassment or a desire to protect their privacy, some respondents may choose not to discuss their criminal past. In addition, respondents do not always recall the infractions they committed or those committed against them, and they may recall offenses as being more recent or more remote than they actually were.
Crime statistics are crucial to the criminological endeavour. They contribute to the establishment of the fundamental social facts of crime, which comprise the objects of explanation and give evidence for the evaluation of explanations. Unfortunately, crime figures are among the most unreliable and challenging of any social phenomenon statistics. It is impossible to correctly estimate the level of crime in any specific location or time period. As stated previously, many crimes go unreported, while others are identified but not reported to police or researchers, and yet others are reported but not legally documented. Thus, any record of crimes can at most be regarded an index of the actual crimes committed. This fact has prompted both caution regarding crime data sources and more research to validate and enhance empiricism in the sector. Comparing the “behavior” of crime indexes across several data sources is a popular solution. Figure 1 displays how victimization data compare to government figures since 1973. Although it is a violation of individuals and property. They dismiss crimes done on behalf of corporations, such as deceptive advertising and price-fixing, as well as “victimless” crimes, such as drug usage and gambling.
Figure 1
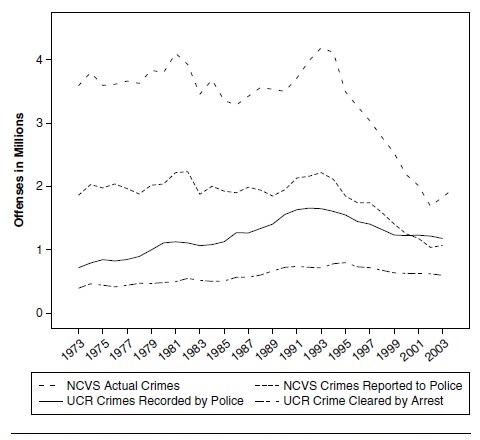
Both types of self-report surveys offer advantages over official crime statistics and are an essential source of crime data. They have access to a wide range of violations, ranging from significant crimes to minor infractions that are unlikely to be reported to police. In addition, by measuring the personal and societal traits of offenders and/or victims, they can supply a wealth of information for evaluating crime theories. Both sorts of self-reports are subject to the same constraints inherent to the self-report method. The fundamental limitations of self-report surveys stem from the size of the sample and the precision of assessment. A survey’s sample size is determined by guaranteeing representative participation and obtaining cooperation throughout the survey questionnaire. Both data sources produce indices that react similarly (growing and declining) across this time frame.
Criminology and Patterns of Crime
Criminologists document crime patterns in order to comprehend the nature and scope of crime. While the general public views many crimes as random acts, criminological research demonstrates that crime is not dispersed randomly among individuals or groups. The focus of criminological research on crime patterns is the relationship between criminal conduct and dimensions of time, place, and social structure. Crime tends to be a “intrastatus” activity, which is a crucial understanding in tracking criminal tendencies. In a significant number of crimes, the statuses used to identify offenders also describe the victims. Criminology has paid considerable attention to a number of contextual and structural factors that explain the fundamental crime patterns. These include the spatial and temporal distribution of crime, as well as the age, gender, race, and social status of the participants.
Criminologists have always been fascinated by the social factors that influence criminal behavior. Social context is characterized by the temporal and spatial characteristics that are connected with criminal behavior. At least three time metrics have been of interest to criminologists: annual patterns, seasonal patterns, and daily patterns. According to historical studies of crime in the United States, significant crime grew in the decades preceding the American Civil Conflict and continued to rise after the war. From roughly 1880 until the 1930s, reported crime generally declined, with the exception of the years before and during World War I. Since then, major crime has generally increased modestly, with a sharper rise commencing in the late 1960s (Gurr 1981). It reached its highest point in 1981 and again in 1991, but then plummeted in the middle and late 1990s and has been slowly dropping ever since (see Figure 2).
Figure 2
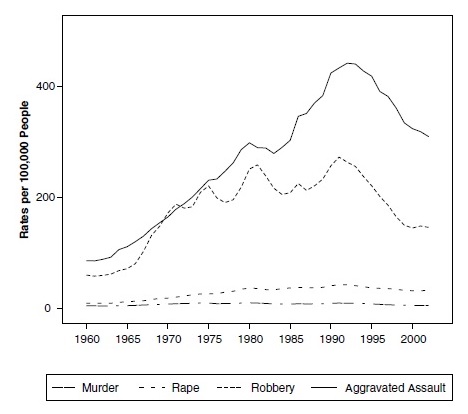
In addition to annual shifts, which reflect historical oscillations, criminologists have identified additional units of time in which crime fluctuates. For instance, crimes tend to increase towards the beginning of the month, when most people receive their paychecks. Most crimes occur over the summer, when youths are out of school and people spend extended periods of time outside and away from their homes. Murders are more likely to occur in the evening, when more people are at leisure, whereas domestic burglaries are more likely to occur during the day, when more people are at work or school and less able to monitor their houses.
Additionally, criminologists have attempted to document the spatial patterns of crime. Researchers have found that the rate of severe crime tends to increase as the population of a community grows. In general, urban areas have a greater crime rate than their suburban and rural counterparts. Consistently, victimization and self-report statistics indicate that crime is concentrated in major metropolitan areas (Sutherland, Cressey, and Luckenbill 1992:176–78). In the United States, however, the extent to which the urban crime rate exceeds the rural crime rate fluctuates over time. As improved communication and transportation have diminished the disparities between urban and rural areas, there is reason to believe that the disparities in crime rates have also decreased, with rural and suburban crime rates increasing more rapidly than urban crime rates. In local communities, crime is typically concentrated in areas characterized by social disadvantage. High-crime neighborhoods typically have higher-than-average percentages of poverty, rental and abandoned properties, single-parent households, and population mobility, all of which impede the organization of the community to prevent crime.
Youth engage in criminal activities. Researchers have found that age is the most accurate predictor of criminal behavior. The correlation between age and criminality is nonlinear. Criminal activity grows with age into adolescence, reaches its peak in late adolescence or early adulthood, and then drops rather rapidly with age before declining more slowly until death. Some have argued (Gottfredson and Hirschi, 1986) that the association between age and crime is constant, regardless of sex, race, and socioeconomic status, as well as across time and space (see Figure 3).
Figure 3
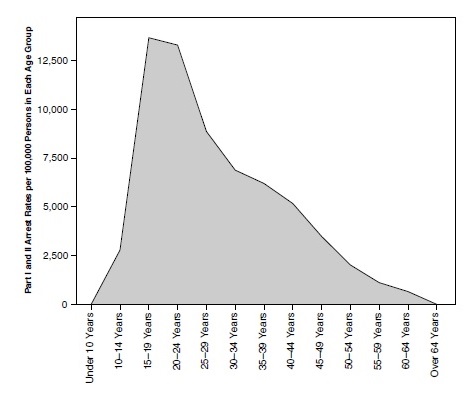
Criminologists use the term “distance” to characterize the cessation of criminal action as age increases beyond the peak offending ages of late adolescence or early adulthood (Laub and Sampson 1993). Although the majority of offenders “age out” of crime by early adulthood, a small proportion continue to commit crimes throughout their lives. This observation has spurred attention in the significance of age in differentiating between various sorts of offenders. Research on the effects of age at first offense and the trajectory of crime over the life cycle reveals the existence of several types of criminal careers that vary in terms of commencement, duration, and intensity. Individuals who engage in criminal activity at a young age and those who have contact with the judicial system at a younger age are more likely to become chronic offenders or “life-course persisters.” Laub and Sampson (1993) shown that even among first-time and chronic offenders, recidivism can be avoided. According to research in this field, the most prevalent type of criminal career is “adolescent limited,” meaning that criminal behavior is typically confined to adolescence and early adulthood, after which desistance occurs swiftly.
Men have a higher crime rate than women. Frequently, comparisons of sex-specific criminal conduct are given as a frequency or rate ratio of male to female offenses. Although the disparity in the sex ratio of offenders varies by kind of offense, it is largest for more serious offenses. In the United States, the ratio of male to female murder arrests in any given year is approximately eight male arrests to one female arrest. In contrast, the ratio of male to female arrests for theft, one of the least serious offenses, is two males for every female. Self-report data suggest that males are more likely to be involved in criminal activity than females, however these data tend to reveal less disparity in the sex ratio of criminal offending than official data, particularly for less severe offences (Triplett and Myers 1995). Some criminologists claim that the disparity between arrest statistics and self-reports is due to the chivalrous stance taken by criminal justice officials when ladies are the target of law enforcement (Steffensmeier 1993).
The official statistics portray an arresting picture of criminal behavior by race. African Americans are significantly more likely than whites to be arrested, despite the fact that whites account for the vast bulk of arrests. African Americans are responsible for over 40 percent of arrests for major violent crimes and over 25 percent of arrests for significant property offenses, although constituting just 13 percent of the United States’ population (Federal Bureau of Investigation 2004). In contrast, Whites are arrested disproportionately for specific Part II offenses, such as alcohol and driving under the influence offenses. The racial discrepancy in arrests for serious crimes has decreased in recent years, but African Americans have a considerably greater chance of arrest than whites (see Figure 4).
Figure 4
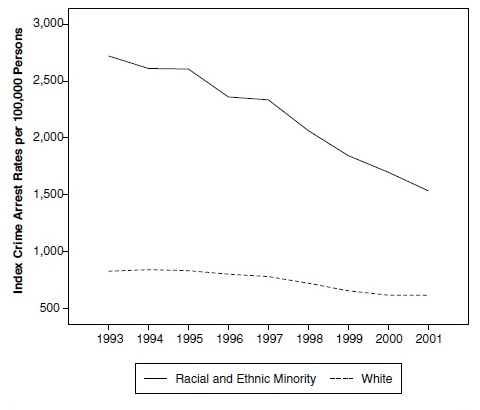
Some criminologists have proposed that racial prejudice in criminal justice may account for a significant portion of the reported racial discrepancy in official statistics (Tonry 1995). Others have argued that the judicial system and its agents are reasonably objective when processing defendants, implying that racial disparities in official crime figures reflect true racial inequalities in criminal behavior (Wilbanks 1987). Using self-report and victimization data, criminologists have attempted to settle this disagreement by examining race-specific involvement in criminal conduct. Self-report studies of delinquency among African American and white kids imply that racial disparities are significantly smaller than indicated by arrest statistics (Elliott and Ageton 1980).
Criminologists have long assumed a negative link between social class and crime: people at the bottom of the social hierarchy are more likely to be involved in criminal activity than those at the top. According to official statistics, lower-class status correlates with more criminal activity. Those convicted of a crime and sentenced to prison are more likely to be indigent, unemployed, or underemployed.
In spite of this evidence, criminologists have contended that the association between class and crime is less certain than indicated by official statistics. Sutherland was the first criminologist to examine the relationship between class and crime (1940). He noticed that white-collar crimes, or crimes perpetrated by respectable and high-status individuals in the course of their employment, are prevalent while being typically overlooked in official crime statistics. Sutherland’s discovery has led to numerous criticisms of people who believe a negative association between socioeconomic status and criminal behavior.
Conclusions regarding the relationship between class and crime may reflect the information source used. Self-report studies indicate that adolescents from all socioeconomic levels engage in delinquent behavior (Tittle, Villamez, and Smith 1978). However, these studies have been critiqued for failing to precisely define class status and for conflating delinquency with serious criminality (Braithwaite, 1979). (Farnworth,Thornberry, Krohn, and Lizotte 1994).
In conclusion, criminologists have committed significant effort in documenting crime patterns. These patterns are useful for evaluating and planning social responses to crime by policymakers. Correlating crime across dimensions of social context (time and geography) and social structure (age, sex, race, and social class) yields empirical facts that theory must explain.
Throughout the past two centuries, numerous criminology schools have flourished. A school of criminology is a body of thinking that combines a theory of crime causation with control methods required by the theory. In Europe during the eighteenth century, Cesare Beccaria and Jeremy Bentham established the classical school as one of the first criminology schools. According to the classical school, crime is a reasonable technique of maximizing one’s self-interest. Individuals are perceived as hedonistic, seeking pleasure and avoiding pain, and rational, calculating the pleasures and pains of possible behaviors and selecting those that promise the most pleasure with the least pain. Individuals will opt to commit a crime if they determine that it delivers the most joy and the least pain relative to other actions. To control crime, the state need merely persuade individuals that committing a crime would result in more pain than pleasure, which can be achieved by raising the severity of punishments. When individuals discover that criminal behavior is less enjoyable, they will pursue more fulfilling activities. During the nineteenth century, the positive school of criminology emerged largely due to the contributions of Cesare Lombroso and his followers. The positive school, which is grounded in the physical sciences, views crime as the result of personal faults or diseases. It asserts that the physical constitution influences behavior and that flaws in biological structure or processes result in criminal conduct. The positive school maintains that punishment is ineffective in reducing crime because criminals do not weigh the pleasures and pains of different actions and choose the one that maximizes pleasure. Instead, it asserts that the only rational approach to controlling crime is to identify and influence its causes. Given that crime is the result of a human defect or disorder, it follows that the most effective method of crime control is to treat the defect or condition in question. This school fell out of favor at the beginning of the twentieth century as the sociological school, which views crime as a product of the social environment, gained popularity. Over the course of the twentieth century, the sociological school has matured and grown to dominate scientific efforts to explain crime.
The sociological school predominantly emerged in the United States. Sociologists have conducted the majority of systematic studies of crime and criminals since the late nineteenth century, when criminology was recognized as a topic of study by the expanding sociology departments of universities. A 1901 survey found that criminology and penology were among the first courses taught under the label of sociology in American colleges (Tolman 1902–1903), and the first issue of the American Journal of Sociology included papers and book reviews on criminology. At the same time, though, American sociologists were impressed by a number of the positive school’s claims. Not until approximately 1915, after the publication of Charles Goring’s The English Convict (1913), was a strong environmentalist perspective developed. This pattern likely caused John Gillin (1914) to make his observation,
The longer the study of crime has continued in this country, the greater has grown the number of causes of crime which may be described as social. This is the aspect in the development of American criminology which has given to that study in this country the title of “The American School.” (P. 53)
The core thesis of the sociological school is that criminal behavior is the outcome of the same conditions and processes as other forms of social behavior. There are two types of analyses of these factors and processes in relation to crime. First, criminologists have attempted to establish a link between variances in crime rates and differences in social organization. Several socioeconomic circumstances, including social and economic inequality, political and economic ideology, and culture and normative conflict, have been studied in relation to differences in the crime rates of societies and units of society. In an early sociological study, Clifford Shaw (1929) utilized the Chicago School’s ecological method, which strongly drew on Durkheim’s analogy of society as an organism, to comprehend the metropolitan distribution of delinquency. He noticed that delinquency was concentrated in specific regions of the city and attributed this to social disarray. He viewed delinquency as a pathology endemic to urban slums, not the individuals who resided there. These regions had high mobility, heterogeneity, and conflict, factors that fostered social disorganization, a condition in which traditional means of social control are ineffective and individuals are free to engage in criminal conduct. In particular, Robert Merton’s (1938) anomie theory was significantly influenced by Durkheim’s functionalist concepts regarding the causes and implications of change in social solidarity. In a seminal remark, Albert Cohen (1955) asserted that differences in the access of social classes to legitimate means of obtaining success correlate with differences in their rates of delinquency. In American society, lower-class children are encouraged to seek the same goals as middle-class children and are evaluated using the same criteria. However, they lack the cultural and economic capital required to effectively compete with children from middle-class families. As a result, many children from disadvantaged backgrounds suffer failure, and in response, they may develop and participate in delinquent subcultures. These two arguments—that high rates of crime can be explained in terms of a breakdown of social organization and that high rates can be explained in terms of a conflict between culturally induced aspirations and structurally limited opportunities—have figured prominently in much macro-level contemporary theory.
Second, criminologists have worked to uncover the mechanisms that lead to the criminalization of persons. In general, their investigations link criminality to socialization differences. One view, advanced by Travis Hirschi (1969) under the umbrella of control theory, holds that criminality is the outcome of a breakdown in socialization. According to this perspective, criminal behavior is a manifestation of inherent instincts. When a person’s connection to society is weak, it is doubtful that he or she will absorb the values and conventions of society or be attentive to the needs and desires of others. The individual lacks control and is therefore free to participate in criminal activity. Edwin Sutherland (1947) and Ronald Akers (1998) expand the notion that criminality results from social learning. According to this viewpoint, criminal behavior is not a manifestation of inherent instincts. Rather, a person learns to engage in illegal behavior similarly to how they learn to engage in noncriminal behavior. The content of education, not the method itself, determines whether a person becomes a criminal. These arguments, namely, that criminality results from a breakdown in socialization and that criminality is a product of socialization, continue to dominate micro-level thinking about crime.
In recent decades, criminologists have pursued alternative methods of analysis. In the 1960s and 1970s, some criminologists began to rethink the key assumptions and themes that had been used to organize criminology. They noticed that criminality is not an inherent quality of a given conduct and that the breach of a criminal statute does not invariably result in the capture and punishment of the offender. Instead, an act is criminal because legislators have made it so, and those who violate the law are selectively captured and punished (Becker 1963). This moves the focus from the criminal to the mechanisms of defining and responding to disruptive behavior (Quinney 1964; Turk 1969). Consequently, criminologists have increasingly focused on patterns of selective law enforcement, asking what types of offenses and offenders are most likely to be treated as crimes and criminals and why? In the course of demystifying the legal system, criminologists also considered the consequences of being labeled and treated as a criminal, arguing that stigmatization reduces a person’s legitimate opportunities for success and alters his or her identity, thereby promoting chronic criminality (Kitsuse 1962; Lemert 1972:62–92).
Throughout the 1980s and 1990s, a number of criminologists attempted to develop comprehensive theories of crime. Traditionally, criminologists have evaluated hypotheses by pitting at least two against one another in a “theory competition” (Akers and Sellers 2004:267). Recognizing that there is nothing to be gained from such rivalry, criminologists have increasingly sought to develop more effective explanatory models by combining aspects of two or more distinct theories of crime. John Braithwaite (1989) incorporated elements of control theory, social learning theory, and labeling theory into his theory of reintegrative shaming, and Charles Tittle (1995) incorporated elements of control theory, social learning theory, strain theory, and Marxist theory into his control balance theory of deviance. Despite the significance of integration initiatives, caution must be exercised in this endeavor. As Akers (1989:24) correctly highlighted, if ideas are combined without respect for their incompatibilities, “theoretical mush” can arise.
Over the years, three crime prevention strategies have been utilized: punitive, defensive, and interventionist. Punitive tactics are predicated on the premise that criminality and crime rates can be lowered by instilling in individuals a strong fear of being penalized for committing crimes. It is believed that inflicting great suffering on criminals both reforms those who are punished (specific deterrence) and discourages others from committing crimes (general deterrence). Much of the legislation that aims to significantly reduce crime is merely an effort to improve the severity or certainty of punishment (Beckett and Sasson 2004). Methods of defense are based on the premise that crime can be decreased by making it difficult for individuals to commit crimes. These solutions include lighting streets, securing doors, and putting valuables in safes (Felson 2002:144–64). The confinement of criminals inside bars so that they cannot victimize strangers is another example of defensive measures. The premise of interventionist tactics is that punishment and defense are insufficient. Rather, it is assumed that criminality and crime rates can be efficiently lowered by identifying and altering the factors that produce them. Methods based on the premise that offenders lack basic interpersonal skills aim to develop their competence in empathy, problem solving, impulse control, and anger management, whereas methods based on the premise that offenders have learned criminal behavior aim to teach them lawful forms of behavior (Cullen 2002). Generally speaking, interventionist tactics think that high crime rates are a result of economic, political, and social organization and that it is folly to leave this structure intact and try to reduce crime rates by punishing or defending against criminals produced by it. Instead, the objective is to reform the economic, political, or social system in order to lower crime rates (Currie 1998).
There is substantial evidence that intervention is or may be the most effective method of reducing crime (Cullen 2002; MacKenzie 2000). As more is discovered about crime, interventionist approaches will have a stronger foundation. If consistently followed, these regulations would safeguard society against crime in three ways.
First, they would ensure the segregation of those whose recurrent involvement in major crime has shown their threat. Although segregation would not change these criminals, it will safeguard society by incapacitating them and demonstrating disapproval of significant lawbreaking. Currently, we are unable to dramatically alter the societal conditions that produce some chronic offenders or their behavior. We can only protect ourselves against this small group of dangerous individuals.
Second, interventionist policies would integrate into law-abiding society a greater number of citizens, including the majority of those who have committed a crime but have not proven to be dangerous. It is generally accepted that social control is derived from the benefits of lawful behavior rather than direct fear of punishment. The effective deterrent is not the dread of legal penalties per se, but rather the fear of status loss (Grasmick and Bursik 1990). However, fear is not what stops criminal action. Rather, a law-abiding citizen is someone who believes that certain actions, such as stealing from a neighbor or attacking a coworker, are inconceivable. In order for crime prevention strategies to be effective, more people must have a stake in adhering to the rules that prohibit criminal behavior.
Thirdly, interventionist policies would identify the social circumstances from which criminal activity is most likely to emanate and make it possible to abolish those circumstances. Instead of eliminating the economic, political, and social attitudes, conditions, and injustices that cause crime, political leaders have decided to rely on fear of punishment (Currie 1998). Punishment appears to be less expensive, but this is not the case. In addition, the emphasis on punishment detracts from the necessity of creating the environment required for household tranquility. If attitudes of shared respect for certain values could be fostered, punitive legislation relating to these values would be unneeded. If, for instance, all members of a community had an equal stake in the concept of private property, it would no longer be necessary to coerce individuals into upholding property rights.
In short, crime would be decreased by absorbing those criminals who can be absorbed, isolating those who cannot be absorbed for defense, and reducing the conditions that are most conducive to crime and hence necessitate the need to absorb some criminals and isolate others. As much as punishment would, the vigorous execution of such rules would demonstrate society disapproval of criminal behavior. Rather than punishment, approval and disapproval of criminals deter crime among the majority of citizens, including the majority of the poor and disadvantaged, from whom the vast majority of criminals originate.
Our knowledge of crime is elementary. Certainly, we have a sense of how crime is distributed along a variety of structural, temporal, and spatial dimensions; we have a sense of the principal variables that affect the occurrence of crime and development of criminality, as well as the general ways in which these variables operate to produce crime and criminality; and we have a sense of the types of methods that appear to be effective in controlling crime. However, more effort must be done before a solid comprehension of crime can be attained.
When we consider criminology in the twenty-first century, we observe that the field is evolving in multiple directions. There are persistent efforts to develop and enhance the methodological tools for documenting crime, testing theories of crime, and evaluating initiatives to combat crime. There are also ongoing efforts to create integrated theories of crime, theories that incorporate not just sociological, but also biological and psychological, factors. Integrated theory is advancing criminology down a path that may eventually identify it as an interdisciplinary field of study as opposed to a sociological specialty. These two streams, one methodological and one theoretical, will become more linked. The analytical state of the art, for instance, enables a broader and more rigorous range of theory-testing initiatives, which promotes the development of theory. Lastly, there are ongoing initiatives to employ criminological knowledge to improve social welfare by reducing rates of first and repeat offenses in a manner that is fair to offenders, victims, and the broader community. These trends are not exclusive to the criminological enterprise. In fact, they reflect sociological tendencies in which sociologists attempt to refine methods, develop unified theories, and apply research to educate public policy and enrich community life.
Bibliography:
- Akers, Ronald L. 1989. “A Social Behaviorist’s Perspective on Integration of Theories of Crime and Deviance.” Pp. 23–36 in Theoretical Integration in the Study of Deviance and Crime, edited by S. Messner, M. Krohn, and A. Liska. Albany: State University of New York Press.
- Akers, Ronald L. 1998. Social Learning and Social Structure. Boston, MA: Northeastern University Press.
- Akers, Ronald L. and Christine S. Sellers. 2004. Criminological Theories. 4th ed. Los Angeles, CA: Roxbury.
- Becker, Howard S. 1963. The Outsiders. New York: Free Press.
- Beckett, Katherine and Theodore Sasson. 2004. The Politics of Injustice. 2d ed. Thousand Oaks, CA: Sage.
- Braithwaite, John. 1979. Inequality, Crime and Public Policy. London, England: Routledge.
- Braithwaite, John. 1989. Crime, Shame, and Reintegration. Cambridge, England: Cambridge University Press.
- Cohen, Albert K. 1955. Delinquent Boys. Glencoe, IL: Free Press.
- Cullen, Francis T. 2002. “Rehabilitation and Treatment Programs.” Pp. 253–89 in Crime: Public Policies for Crime Control, edited by J. Wilson and J. Petersilia. Oakland, CA: ICS Press.
- Currie, Elliott. 1998. Crime and Punishment in America. New York: Henry Holt.
- Elliott, Delbert S. 1983. National Youth Survey. Boulder, CO: Behavioral Research Institute.
- Elliott, Delbert S. and Suzanne S. Ageton. 1980. “Reconciling Race and Class Differences in Self-Reported and Official Estimates of Delinquency.” American Sociological Review 45:95–110.
- Farnworth, Margaret, Terence P. Thornberry, Marvin D. Krohn, and Alan J. Lizotte. 1994. “Measurement in the Study of Class and Delinquency: Integrating Theory and Research.” Journal of Research in Crime and Delinquency 31:32–61.
- Federal Bureau of Investigation. 2003. Age-Specific Arrest Rates and Race-Specific Arrest Rates for Selected Offenses 1993–2001. Washington, DC: U.S. Department of Justice.
- Federal Bureau of Investigation. 2004. Crime in the United States, 2003. Washington, DC: U.S. Department of Justice.
- Federal Bureau of Investigation. 2005. State and National Level Crime Trend Estimates. Washington, DC: Federal Bureau of Investigation [producer]; Washington, DC: Bureau of Justice Statistics [distributor]. Retrieved December 1, 2005 (http://bjsdata.ojp.usdoj.gov/dataonline/Search/Crime/Stat/ StatebyState.cfm).
- Felson, Marcus. 2002. Crime and Everyday Life. 3d ed. Thousand Oaks, CA: Sage.
- Gillin, John L. 1914. “Social Factors Affecting the Volume of Crime.” Pp. 53–67 in Physical Bases of Crime: A Symposium, edited by the American Academy of Medicine. Easton, PA: American Academy of Medicine Press.
- Goring, Charles. 1913. The English Convict. London, England: HMSO.
- Gottfredson, Michael and Travis Hirschi. 1986. “The True Value of Lambda Would Appear to Be Zero: An Essay on Career Criminals, Criminal Careers, Selective Incapacitation, Cohort Studies, and Related Topics.” Criminology 24:213–34.
- Grasmick, Harold G. and Robert J. Bursik Jr. 1990. “Conscience, Significant Others, and Rational Choice: Extending the Deterrence Model.” Law and Society Review 24:837–61.
- Gurr, Ted R. 1981. “Historical Trends in Violent Crime: A Critical Review of the Evidence.” Crime and Justice 3:295–353.
- Hindelang, Michael J., Travis Hirschi, and Joseph G. Weis. 1981. Measuring Delinquency. Beverly Hills, CA: Sage.
- Hirschi, Travis. 1969. Causes of Delinquency. Berkeley: University of California Press.
- Johnston, Lloyd D., Patrick M. O’Malley, and Jerald G. Bachman. 1996. National Survey Results on Drug Use from the Monitoring the Future Study, 1975–1995. Rockville, MD: U.S. Department of Health and Human Services.
- Kitsuse, John I. 1962. “Societal Reactions to Deviant Behavior: Problems of Theory and Method.” Social Problems 9:247–56.
- Laub, John and Robert J. Sampson. 1993. “Turning Points in the Life Course.” Criminology 31:301–25.
- Lemert, Edwin M. 1972. Human Deviance, Social Problems, and Social Control. 2d ed. Englewood Cliffs, NJ: Prentice Hall.
- MacKenzie, Doris Layton. 2000. “Evidence-Based Corrections: Identifying What Works.” Crime and Delinquency 46:457–71.
- Maston, Kathy and Patsy Klaus. 2005. Four Measures of Serious Violent Crime. Washington, DC: U.S. Department of Justice, Bureau of Justice Statistics. Retrieved September 5, 2005 (http://www.ojp.usdoj.gov/bjs/glance/tables/4meastab.htm).
- Merton, Robert K. 1938. “Social Structure and Anomie.” American Sociological Review 3:672–82.
- Murphy, L. R. and R. W. Dodge. 1981. “The Baltimore Recall Study.” Pp. 16–21 in The National Crime Survey: Working Papers, 1, Current and Historical Perspectives, edited by R. G. Lenhen and W. G. Skogan. Washington, DC: U.S. Government Printing Office.
- Porterfield, Austin L. 1946. Youth in Trouble. Fort Worth, TX: Leo Potishman.
- Quinney, Richard. 1964. “Crime in Political Perspective.” American Behavioral Scientist 8:19–22.
- Sellin, Thorsten. 1931. “The Basis of a Crime Index.” Journal of Criminal Law and Criminology 22:335–56.
- Shaw, Clifford R. 1929. Delinquency Areas. Chicago, IL: University of Chicago Press.
- Short, James F., Jr. and F. Ivan Nye. 1958. “Extent of Unrecorded Juvenile Delinquency: Tentative Conclusions.” Journal of Criminal Law and Criminology 49:296–302.
- Steffensmeier, Darrell. 1993. “National Trends in Female Arrests, 1960–1990: Assessment and Recommendations for Research.” Journal of Quantitative Criminology 9:413–41.
- Sutherland, Edwin H. 1940. “White Collar Criminality.” American Sociological Review 5:1–12.
- Sutherland, Edwin H. 1947. Principles of Criminology. 4th ed. Philadelphia, PA: Lippincott.
- Sutherland, Edwin H., Donald R. Cressey, and David F. Luckenbill. 1992. Principles of Criminology. 11th ed. Dix Hills, NY: General Hall.
- Thornberry, Terence P. and Marvin D. Krohn. 2000. “The SelfReport Method for Measuring Delinquency and Crime.” Pp. 38–84 in Measurement and Analysis of Crime and Justice, 4, Criminal Justice 2000, edited by D. Duffee. Washington, DC: National Institute of Justice.
- Tittle, Charles R. 1995. Control Balance. Boulder, CO: Westview Press.
- Tittle, Charles R., Wayne J. Villamez, and Douglas A. Smith. 1978. “The Myth of Social Class and Criminality: An Assessment of the Empirical Evidence.” American Sociological Review 43:643–56.
- Tolman, Frank L. 1902–1903. “The Study of Sociology in Institutions of Learning in the United States.” American Journal of Sociology 7:797–838; 8:85–121, 251–72, 531–58.
- Tonry, Michael. 1995. Malign Neglect. New York: Oxford University Press.
- Triplett, Ruth and Laura B. Myers. 1995. “Evaluating Contextual Patterns of Delinquency: Gender-Based Differences.” Justice Quarterly 12:59–84.
- Turk, Austin T. 1969. Criminality and the Legal Order. Chicago, IL: Rand McNally.
- Wilbanks, William. 1987. The Myth of a Racist Criminal Justice System. Monterey, CA: Brooks/Cole.
- Crime and Criminology Research Paper
- Criminology of Place Research Paper
- Identification in Life Course Criminology Research Paper
- Longitudinal Studies in Criminology Research Paper
ORDER HIGH QUALITY CUSTOM PAPER


- Previous Article
Many central banks are currently exploring the possibility of issuing retail central bank digital currency (CBDC). While the primary objective varies between jurisdictions, many central banks consider improved cross-border payments as a potential benefit and previous work has shown that CBDC can help overcome some of the frictions in cross-border payments. CBDC is a safe and liquid asset reducing the number of financial intermediaries and the settlement risk. Designing CBDC systems for cross-border payments is not fundamentally different from tailoring other payment systems. However, the roles and responsibilities might be slightly different in a CBDC system, and the central bank may play a more pivotal role given CBDC’s nature as public money as opposed to commercial bank money. This note draws lessons from ongoing experimentation and research to identify design and policy considerations when developing retail CBDC systems so it may be compatible for cross-border payments. The note focuses on retail CBDC—a CBDC primarily targeting households and non-financial firms—and leaves wholesale CBDC considerations for future work, although many of the discussions are applicable to wholesale CBDC and other forms of money as well.
- 1. Introduction
Many central banks are currently exploring the possibility of issuing retail central bank digital currency (CBDC). While the primary objective varies between jurisdictions, many central banks consider improved cross-border payments as a potential benefit 1 and previous work has shown that CBDC can help overcome some of the frictions in cross-border payments. 2 CBDC is a safe and liquid asset reducing the number of financial intermediaries and the settlement risk. In addition, the introduction of CBDC offers a window—a clean slate—to build cross-border payment functionality from the start, thus more efficiently. Past experiences suggest that making legacy payment systems interoperable across borders has been difficult once systems are up and running and have initially been designed for domestic purposes ( FSB 2020b ). Furthermore, CBDC, as a new means for cross-border payments, is commonly meant to coexist with and complement existing options, and can thus increase payment diversity and stimulate resilience, competition, and efficiency. Effects are potentially macro-critical, as faster, cheaper, and more inclusive payments could facilitate international commerce and remittance transfers. In turn, central banks could also see greater CBDC use domestically ( Tan 2023 ).
Designing CBDC systems for cross-border payments is not fundamentally different from tailoring other payment systems. In fact, many of the same challenges, opportunities, and implications highlighted in this paper apply generally. That said, the roles and responsibilities might be slightly different in a CBDC system, and the central bank may play a more pivotal role given CBDC’s nature as public money as opposed to commercial bank money. In a CBDC setting, end users would directly hold a central bank liability, just as when they hold cash, and the central bank is likely to have a large role in establishing and operating the infrastructure and scheme. 3
This paper draws lessons from ongoing experimentation and research to identify design and policy considerations when developing retail CBDC systems so it may be compatible for cross-border payments. The paper focuses on retail CBDC—a CBDC primarily targeting households and non-financial firms—and leaves wholesale CBDC considerations for future work, although many of the discussions are applicable to wholesale CBDC and other forms of money as well. 4 Many central banks are currently exploring retail CBDCs for domestic purposes, while many of the cross-border CBDC experiments to date have focused on wholesale transactions (see BIS, IMF, and World Bank 2021 and 2022). Project Icebreaker was, however, a first cross-border payment experiment using retail CBDCs ( BISIH and others 2023c ; see also Annex IV). The project used a communication hub to interlink the CBDC test systems of the central banks of Israel, Norway, and Sweden. This paper refers to lessons drawn from the Icebreaker project, as well as existing non-CBDC arrangements like Project Nexus ( BISIH 2021 ). Nexus is a blueprint for how to connect multiple national payment systems into a cross-border network that enables international retail payments in seconds. It overcomes the limitations of bilateral interlinking by standardizing how instant payment systems (IPSs) connect. Moreover, this paper also draws on lessons in publications issued under the “G20 Roadmap for Enhancing Cross-Border Payments” (see FSB 2020a ).
The paper provides an analytical framework by viewing cross-border CBDC payments through the lens of five interrelated elements: access, communication, currency conversion, compliance, and settlement. For each element, the paper identifies key CBDC design choices, many of which can be tackled in the initial preparation phases. 5
By making early decisions, central banks can diminish risks of having to redesign or adjust their domestic CBDC system at a later stage. Thus, the overarching key message is to factor in cross-border implications at an early stage, and that clear objectives on cross-border use can help make early design choices even if the CBDC is initially only used domestically. In addition, international cooperation is important: information sharing, consistent messaging standards and regulatory approaches, and common infrastructure can all facilitate CBDC interoperability. Such international cooperation can be more impactful if achieved at a global level to avoid fragmentation and walled gardens.
Other key messages from our work are as follows:
Assessing access policies and roles and responsibilities is paramount : Central banks should carefully evaluate access policies for end users and intermediaries. Wide access could reduce the cost associated with foreign exchange provision but might cause macrofinancial risks such as capital flow volatility or currency substitution.
The adoption of international standards for payment initiation, data, and messaging helps : Even in a CBDC environment, these standards, such as ISO 20022, will continue playing a role. 6
Having instant settlement and 24/7 availability helps mitigate some risks : By providing instant payments and 24/7 availability, settlement and liquidity risks can decrease.
Programmability can deliver efficiency gains : Experiments suggest that programmability could lower settlement risks by allowing synchronous payment versus payment (PvP).
Compliance with international regulatory frameworks should be factored in : These include technologies to ensure privacy and enhance regulatory compliance such as for anti-money laundering/combating the financing of terrorism (AML/CFT).
Flexible or modular technical designs can help : Solutions that can “plug into” different arrangements can more easily adapt to the likely continuous evolution of the future cross-border CBDC payments landscape.
The remainder of the paper is structured as follows. Section 2 presents a basic framework and Section 3 discusses design considerations and policy implications, including boxes summarizing key design considerations. Section 4 concludes.
- 2. A Framework to View CBDC Design through the Lens of Cross-Border Payments
Suppose Alice needs to send money to Bob who lives in a different country. One option for Alice is to send cash to Bob via mail. For the transfer to go through, certain requirements must be met. First, Alice needs access to banknotes. Second, Alice needs Bob’s postal address. Third, there needs to be a reliable postal service to deliver the envelope. Since Alice and Bob live in different countries, several postal services might be involved unless Alice uses a multinational delivery service. Fourth, Alice and Bob must ensure they comply with all rules and regulations, which may be difficult in the case of sending cash in an envelope. Fifth, they must agree on who owns the money at what stage and when the ownership is transferred.
Most cross-border payments are not made by sending money in an envelope; instead, they are made in a digital form. Currently, there are many different types of models including correspondent banking, closed loops, and aggregators (see Box 1 ). In addition, more formal arrangements between payment systems exist, such as the interlinking of payment systems and common platforms (see Box 2 ).
The models and arrangements underlying digital payments can nevertheless be understood through the envelope analogy. In every model, the question of access arises. Who can access what money and what rules govern that access? While Alice and Bob can easily access any country’s banknotes, having a bank account to hold a foreign currency is more sophisticated in the digital world. This typically gives rise to the need for a currency conversion for each payment. Addressing is also important in the digital world. In the envelope case, Alice needs the physical address where Bob lives. In the digital world, she often needs to know what bank Bob uses, the identifying number of that bank, and Bob’s account number. Also digital payments typically need an intermediary, like postal services in the envelope case. For example, multiple financial intermediaries are used in the correspondent banking model, as not all banks typically operate in all countries. Sometimes, fewer financial intermediaries are needed. For example, in a closed loop, a monetary transfer operator might be active in multiple countries and offer transfer services.
To ensure compliance with regulatory requirements in the digital world, payment service providers (PSPs) must conduct various checks (discussed in more details later) to facilitate payments. 7 These will be easier to undertake with CBDC than in the simple example of sending cash in an envelope. It is also essential to determine the ownership of the funds being transferred and the way the transfer occurs in the digital realm. When it comes to cross-border payments, multiple transactions take place within the payment chain, all of which must be settled and have the change of ownership agreed upon.
As demonstrated by the Alice and Bob example, cross-border payments involve multiple distinct elements. In this paper, we therefore analyze cross-border CBDC payments in terms of five key elements: access, communication, currency conversion, compliance, and settlement. These elements, as outlined in Figure 1 , form the fundamental components of a cross-border payment. Access refers to who is permitted to hold and transact a given currency and any potential restrictions on that access. Communication is the way in which the payer, payee, intermediaries, devices, and systems communicate and link up during a payment. Currency conversion refers to how and by whom one currency is exchanged for another. 8 Any cross-border transaction must adhere to applicable legal and regulatory requirements. Accordingly, responsibilities and requirements for compliance constitute an element. Compliance is very broad and could cover many aspects, and the legal considerations are many, especially as international standards and domestic legal and regulatory frameworks are still evolving. In this paper, recognizing broad scope and depth of compliance issues, we will focus on technical aspects as well as high-level policy considerations related to AML/CFT, privacy, anonymity, and capital flow management measures (CFMs), and we leave in-depth legal considerations and broader CBDC compliance issues for future work. Lastly, settlement is an element that encompasses how the transfer of funds between the parties involved is completed. By viewing cross-border CBDC payments through the lens of these five elements, the paper will identify relevant design choices that need cross-border consideration. 9
The elements are interconnected; for instance, access policies determine the need for currency conversion and who is qualified to offer foreign exchange services. Access policies also determine the need for financial intermediaries and, ultimately, how settlement is achieved. The necessary compliance checks will depend on who is involved in the payment chain, determined by access and the model utilized for currency conversion. Central banks must recognize this interconnectedness in their CBDC exploration and design.
The Alice and Bob example and the elements also highlight that many CBDC systems would have several actors—end users, PSPs, operators, the central bank—and the responsibilities of these actors can differ between different systems. We identify three main categories of responsibilities: first, technical services , such as providing the underlying infrastructure, an interface of payment device, digital wallet, or messaging; second, customer relationships , such as onboarding and addressing customer complaints and questions; and third, financial functions , such as financial intermediation and foreign exchange provision. We return to these functions and responsibilities throughout the paper.

The Core Elements of a Cross-Border Payment
Citation: Fintech Notes 2024, 002; 10.5089/9798400272035.063.A001
- Download Figure
- Download figure as PowerPoint slide
Prevailing Models for Cross-Border Payments
There are three prevailing models for processing cross-border payments: correspondent banking, closed loops, and aggregators. Hybrid forms are also possible, for example a closed-loop system utilizing correspondent banking relationships to maintain its liquidity and manage risks.
> Correspondent banking is one of the most common methods to facilitate cross-border payments. It involves two or more banks, typically located in different countries, establishing relationships to facilitate cross-border transactions. In this relationship, one bank acts as a correspondent bank and provides services to another bank, the respondent bank, sometimes with the use of intermediary banks. The respondent bank uses the correspondent bank’s services to facilitate cross-border payments for its customers.
> A closed-loop system operates within a specific network, usually owned by a single company, such that the payer and the payee interact with the same entity—exemplified by Western Union, PayPal, Wise, and Revolut. The payment is processed within the network, allowing quick and secure transfer of funds between accounts. The closed-loop system can facilitate cross-border payments because it has a local presence in multiple countries or has agreements with banks or financial institutions in the countries where the payment is being sent or received.
> Cross-border payments via aggregators refer to the process of PSPs using a third party, the aggregator, to process cross-border payments—exemplified by VISA, MasterCard, and Wse Platform. These payment aggregators establish a global network and do not communicate directly with end users but with PSPs, who interact with the end users. The aggregators typically use a correspondent banking network to gain access, but can also participate directly in local financial market infrastructures (FMIs).
In addition to these prevailing models, other models and arrangements do exist; see CPMI (2018) for more on cross-border retail payments. See also Annex I for how the above models are viewed through the five elements. The three models described above can be used also for processing cross-border retail CBDC payments, although some refinements of the models would occur. See Annex II for an example of the process for inbound diaspora remittances using the eNaira.
Interlinking and Common Platforms
Interlinking can be defined as a set of contractual agreements, technical links and standards, and operational components between systems. There are two interlinking models at the highest categorization: bilateral links and hub-and-spoke (see Figure 2 ). The key difference is that a bilateral link model rests on each payment system establishing an interlinking arrangement with each of the other payment systems, while the hub-and-spoke is characterized by having only one technical counterpart—the hub. The hub-and-spoke model can be further divided into two categories: the “airport model” and the “communicator model.” The key difference is that the hub in the airport model is a separate currency payment system itself, while the hub in the communicator model is not a payment system but rather a technical infrastructure that facilitates communication between systems. 10

Stylized Interlinking Models
An alternative to interlinking separate payment systems is to use a common platform. Again, we can think of two main classifications. First, we can consider having a limited-purpose common platform only for cross-border payments so that domestic payments are facilitated in domestic payment systems, while only cross-border payments are facilitated on a common platform. Second, we can consider a single common platform facilitating both domestic and cross-border payments. 11
3. CBDC Design Considerations and Policy Implications through the Lens of the Elements
This section discusses design and policy implications of cross-border CBDC through the lens of the elements. For each element—access, communication, currency conversion, compliance, and settlement—we look at different cross-border CBDC arrangement options to identify the main trade-offs and core design questions for cross-border consideration in domestic CBDC design. 12 At the end of each element subsection, we provide a small box covering some of the key design considerations where cross-border attention is needed. There are certain options and elements that are more policy-related, while others are more technical in nature. Although not comprehensive, the objective is to pinpoint the primary CBDC design areas where cross-border attention is required, while acknowledging that there may be additional options within these elements.
Element 1: Access
Central banks need to determine access policies for end users, financial intermediaries, and foreign exchange providers. Access policies—who has access to what currency and under what rules—impact both the domestic CBDC system and the possible models for cross-border payments. Key design options regard access by non-residents and foreign financial institutions as well as any restrictions to holdings or transactions. Access policies come with policy trade-offs that each jurisdiction needs to consider. For example, while wider access might increase risk sharing and currency diversification, risks associated with currency substitution in other jurisdictions would also increase.
- End User Access
Most central banks consider a CBDC mainly accessible to residents of the issuing jurisdiction. However, central banks recognize the possibility for non-resident citizens to gain access since they often have a strong presence in the payments market of their origin—remittances being one use case. 13 In addition, some non-resident foreigners can need to access the CBDC—tourism being one use case. 14 Hence, when a non-resident foreigner visits the country, they might want to exchange their home money for the CBDC to make payments in the local currency. Some jurisdictions consider supporting non-resident access on the same basis as residents—subject to certain requirements (see, for example, Bank of England and HM Treasury 2023 ). Any access to a CBDC will require someone to serve the end user with onboarding, customer service, technical interface, and other functions needed. Hence, actual adoption by non-residents might be limited if PSPs do not find it profitable or satisfactory from a regulatory viewpoint to serve these market segments. In addition, jurisdictions will have to consider potential regulatory implications such as privacy laws and KYC requirements, among others, by allowing for non-resident access.
If users can directly hold and transact a foreign CBDC, the cross-border CBDC transaction would not necessarily need a currency conversion but could mimic domestic payments, apart from potential differences in compliance checks; we return to compliance issues in element 4. If users cannot access the foreign CBDC directly, there is a need for a currency conversion and a financial intermediary to facilitate the transaction. The need for a financial intermediary highlights the importance of a model that ensures everyone with access to the CBDC also gains access to cheap cross-border, cross-currency functionality; we return to this in the third element on currency conversion.
While widespread adoption of a CBDC outside of the issuing jurisdiction could ease the complexity of the actual cross-border payment by limiting the need for currency conversion, there would be various macrofinancial implications ( IMF 2020 ). Such macrofinancial implications include currency substitution, capital flow volatility, and faster transmission of shocks. There is an international coordination problem related to the currency substitution risk as the risk would be materializing in countries other than the jurisdiction issuing the CBDC. Hence, a jurisdiction needs to consider negative spillover effects on its neighboring countries in addition to managing destabilizing effects in their own jurisdictions due to, for example, large capital inflows. Principle 7 from the Public Policy Principles for Retail CBDC by the G7 covers this issue and stresses that “CBDCs should be designed to avoid risks of harm to the international monetary and financial system, including the monetary sovereignty and financial stability of other countries” ( G7 2021 ). 15 To combat these risks, mitigation measures such as limits on holdings and transactions could be implemented. 16 These design options will be further explored in the Restrictions on Holdings and Transactions section.
- Access by Financial Intermediaries and Foreign Exchange Providers
When the end users make cross-border payments without direct access to both CBDCs, a financial intermediary and a foreign exchange provider will be needed. For example, say Alice resides in country A with access to its domestic CBDC, and she wishes to send money to Bob living in country B. Alice does not have access to CBDC-B, and Bob cannot access CBDC-A. Hence, if Alice wishes to send CBDCs to Bob, there needs to be a currency conversion (see element 3 on currency conversion for further details). 17 Therefore, there will be a need for a financial intermediary and a foreign exchange provider. To offer cross-currency financial intermediation or foreign exchange services, direct or indirect access to both currencies is needed.
Direct access refers to models where a domestic or foreign entity directly holds and participates in the CBDC system, while an indirect model refers to a situation where a foreign entity gains access via a domestic entity. In the case a foreign entity can have direct access, the entity would be under the supervision of its home government—hence under foreign supervision from the CBDC issuer’s perspective. This is uncommon today, but examples do exist. For example, the Swiss real-time gross settlement (RTGS) system allows foreign banks to participate via remote access if they meet the same level of standards regarding supervision, anti-money laundering and counter-terrorism financing, and communications infrastructure as domestic participants are subject to.
A foreign entity (typically a financial institution) without direct access to the CBDC can gain indirect access via a correspondent banking arrangement. A foreign entity can use a nostro account with a domestic entity to hold and transact the CBDC on its behalf. 18 However, this model would defeat some of the benefits of CBDC. Indirect holdings of CBDC through a correspondent bank would constitute a claim on a private entity. They would not be a direct liability of the central bank and not fall under the definition of a CBDC. Hence, such model would have credit risk. 19
As mentioned above, a narrower access policy for end users increases the need for financial intermediaries and foreign exchange providers in a cross-border setting. This implies that domestic or foreign entities may need access to hold and transact an ample amount of CBDC unless the central bank plays an active role in acting as an intermediary, or even a foreign exchange provider if willing to take currency risk (see element 3 for more on intermediation and foreign exchange provision). While access to foreign service providers has the potential to increase competition and market depth, those benefits must be balanced with potentially increased supervisory complexity. Similar trade-offs arise regarding access to central bank RTGS systems and reserves.
It is, however, important not to replicate existing challenges observed with correspondent banking (for example, long transaction chains and lack of commercial incentives may leave certain corridors unserved or underserved). In addition, a growing concentration of cross-border flows can potentially exacerbate financial fragilities in countries significantly affected by correspondent banking relationship withdrawal, as it can have consequences such as higher costs and reduced scope of service ( IMF 2022 ). Such flows, including remittances, are important for financial stability and support economic growth and development ( IMF 2017 ). The use of CBDC and interlinking of systems, as well as greater diversity of intermediaries and foreign exchange providers, can reduce transaction chains (BIS, IMF, and World Bank 2022; CPMI 2022b ) and dependencies on correspondent banks. In principle, anyone able to hold multiple currencies and willing to take on currency risk can act as a foreign exchange provider. Thus, a reduction in the number of intermediaries in the transaction chain is beneficial, but increasing the pool of intermediaries and foreign exchange providers to choose from is also important.
- Restrictions on Holdings and Transactions
In addition to determining who has access, there are options regarding restrictions on holdings and transactions. Limits can be motivated from both domestic and cross-border objectives, and from international standards, and can thus create trade-offs. To limit CBDC use by foreign (or domestic) users, restrictions can be applied. One alternative is to limit the maximum amount allowed to hold. Another alternative is to limit the size of any transaction to ensure low-value payments. Yet another alternative is to limit the number of transactions allowed within a certain timeframe. These alternatives are not unique to CBDC, and the policy trade-offs are largely similar for other forms of money as well.
From a domestic perspective, limits might be warranted to reduce disintermediation risk in the short term (see also Das and others 2023 ). Yet, limits could reduce digital financial inclusion if set too low as CBDC might be the only digital alternative for those financially excluded (see Lannquist and Tan 2023 , for more on CBDC and financial inclusion). Too low limits could also affect the usability of a CBDC and hinder uptake and adoption.
From a cross-border perspective, limiting the amount of CBDC individuals or institutions can hold could reduce risks in the international monetary and financial system. If residents and non-residents can use CBDC for cross-border payments, capital flow volatility could increase. Additionally, if non-residents can use a foreign CBDC for domestic payments, it could lead to currency substitution in the country where the non-residents reside. Limiting holdings and transactions could mitigate these risks. However, the jurisdiction responsible for implementing such limits does not gain from it as the currency substitution is a risk in the foreign jurisdiction. That said, jurisdictions should mitigate negative spillovers and avoid risks of harm to the international monetary and financial system, including the monetary sovereignty and financial stability of other countries.
One possible approach to mitigate these negative consequences would be to set different limits for residents and non-residents. It would lift some of the negative consequences, such as financial inclusion and privacy concerns due to low limits on holdings and transactions by residents, while addressing the concerns regarding capital flow volatility and currency substitution. On the other hand, different limits for residents and non-residents can be viewed as discriminatory treatment. In addition, non-resident’s access could be subject to (bilateral) agreements between central banks, further mitigating and balancing these risks. Limits for non-residents can also be conditional on their whereabouts. That is, limits can be different depending on if they are in CBDC issuing jurisdiction or abroad; such that tourists experience less stringent restrictions while visiting but more stringent restrictions when returning home. Risks with currency substitution arise when non-residents can use the CBDC outside of the issuing country, rather than from when given access temporarily when visiting the issuing country. Moreover, even if a CBDC can be used outside of the issuing country, the actual usage would still depend on the local demand. Thus, jurisdiction-specific assessment needs to be made.
Limits can, however, create complexity. Setting and enforcing limits would require the development of rules, regulations, and monitoring systems. This could create additional costs and administrative burdens for central banks and financial institutions, and potentially reduce the efficiency of the system. In addition, technical complexities would arise in ensuring that payments are still processed even when limits are hit.
One alternative to solve problems with limits is to use “waterfall models.” Suppose an incoming payment will bring the wallet balance over the limit. One possible way to address this problem would be for any payment taking CBDC holdings above a certain limit to be accepted but trigger an automatic transfer of the excess funds from the CBDC wallet to another asset. This asset could be an account with a commercial bank. Hence, each wallet holder would have to designate a “waterfall” account. See Annex III for more details on restrictions, and element 3 for more on foreign exchange liquidity management.
Key Design Considerations: Access
Wide access to non-residents is not needed to facilitate cross-border payments as long as intermediaries exist with access to both currencies. While wide access can remove some frictions, there are macrofinancial risks, such as currency substitution in other countries. Thus, non-residents’ access should be carefully analyzed and negative spillover effects should be avoided. That said, with mainly domestic access, currency conversion will be needed, and a key design question regards who should be the foreign exchange provider and how the foreign exchange provider gains access to the currencies. Some central banks might be willing and able to act as foreign exchange providers, but this would entail taking currency risk. Hence, many central banks might want to leave this role to the private sector, at least for well-served payment corridors with sufficient competition, and for some central banks, the mandate could prevent them from taking such role. Any limits and restrictions must be designed to allow for cross-border CBDC transactions by intermediation, and financial intermediaries and foreign exchange providers need to be able to transact large volumes of CBDC, although their holdings can be limited via waterfall accounts. Key design considerations where cross-border attention is needed include the following:
▸ Non-resident access
▸ Domestic and foreign financial intermediary and foreign exchange provider access
▸ Holding and transaction restrictions
▸ Waterfall accounts
Element 2: Communication
When access is established, the payer, payee, and potential intermediaries need to communicate. The section focuses on two main parts of communication: payment initiation and messaging, and infrastructure and connectivity. Payment messages are essential for payments, but they also pose several challenges in a cross-border setting that must be addressed to ensure secure, efficient, and compliant transactions. Challenges in a cross-border setting include lack of standardization, incomplete or incorrect information, limited transparency, lack of security, and regulatory differences. In addition to messaging, key design options regard responsibility for technical intermediation, payment initiation standards, and what infrastructure to use for communication, as this could impact competition.
- Payment Initiation and Messaging
The first instance of technical communication occurs when the payment is initiated. For example, when the payer in country A wishes to send money to a payee in country B, they need to communicate with each other. The payer needs to know the “address” of the payee. Today, for standard credit transfers, the payer typically addresses the payee via IBAN and BIC codes.
Many central banks are investigating the use of proxies, sometimes called aliases, such as phone numbers, nicknames, and email addresses, for addressing CBDC payments domestically. Cross-border addressing would be significantly more straightforward if the same proxies used domestically could be used also for cross-border payments, since they are more familiar to the users. Indeed, this is addressed in the Nexus project when connecting fast payment systems, such that Nexus allows the payer to use the proxy format used in the system of the payee. 20 In the Nexus blueprint, each system shares the service-level description—describing, among other things, the account number format and proxy format—so the payer PSP can retrieve this information.
The address book with proxies would likely need to be made available to foreign PSPs to validate the address and perform compliance checks. Initiating a cross-border CBDC payment with only a phone number would probably not meet most countries’ regulatory requirements. Hence, central banks should consider using proxies for simplified addressing for the end user and options for making the full address book available to foreign PSPs for compliance checks (such as those required for AML/CFT purposes). Furthermore, the authentication of users via digital ID systems is envisioned for many CBDC systems. Having standardized digital ID frameworks across jurisdictions would certainly be beneficial in facilitating more efficient communication and messaging across borders and systems. 21
In the case of person-to-business payments, there are additional complexities. For example, suppose a consumer is buying something online or in-store from a merchant abroad using her phone’s CBDC application, and that the local payment initiation method uses Near-Field Communication (NFC) or QR codes. 22 To offer a seamless experience, the consumer’s phone must be able to read and understand the message being transmitted via NFC or QR codes from the foreign merchant. Following international standards would not only facilitate cross-border interoperability but can also facilitate interoperability with domestic non-CBDC systems. If different standards are used, it increases the burden on PSPs to facilitate technical intermediation, which could hinder competition and market entry by smaller service providers. Coordination on international standards is, however, challenging but beneficial to limit the technical burden on intermediaries. Thus, international cooperation is needed.
When communicating across borders, a common “language” is achieved by standardizing data and messages. Currently, lack of standardization in payment messages creates friction since countries and financial institutions may use different formats, codes, and languages. Limited transparency can make it difficult for senders and recipients to understand the true cost and timing of the transaction, while a lack of security can compromise the confidentiality and integrity of the payment message, leading to unauthorized access, alteration, or theft of funds.
To address these problems, the G20 Roadmap has been actively promoting the adoption of ISO 20022, which is a priority theme on the updated G20 Roadmap (see Action 8 in FSB 2023 ). However, harmonizing ISO 20022 implementation for cross-border payments can be challenging and requires a coordinated effort among financial institutions, regulators, and standard-setting organizations to overcome the challenges associated with varying market practices, diverse payment systems, legacy systems, integration, cost, and security. Central banks are advised to follow the ongoing work within the CPMI for guidance on harmonizing the implementation of ISO 20022 (see CPMI 2023 ). These recommendations also apply to CBDC system design, and central banks should use ISO 20022.
- Communication Infrastructure and Connectivity
When the payer has the information needed to make the payment, there must be communication between the two CBDC systems to execute the payment. This communication can be done in several ways. It can be left to the PSPs to establish the necessary messaging infrastructure (for example, via the SWIFT network) and execute the payment. An alternative is for the systems to interlink and, for example, use Application Programming Interfaces (APIs) to facilitate communication ( CPMI 2022b ). In the case of interlinking via APIs, the central bank would need to ensure that such functionality is possible in the CBDC infrastructure. In addition, there can be a mix of the two approaches.
Linking systems can be done in several architectural ways (as described in Box 2 ), and some provide better scalability than others. Bilateral links have potential scalability problems due to many different links and communication channels need to be established. However, by adopting standardized data, messaging, and APIs, the scalability problem is mitigated. The hub-and-spoke model can make it easier to communicate and connect since there is only one technical counterpart—the hub. 23 For example, Project Nexus uses standardized gateways, while Project Icebreaker uses a central routing hub (see Annex IV for more information on Project Icebreaker). 24 These models are highly scalable—from a technical point of view—as they standardize the connection and communication in a hub-and-spoke fashion so that each system only has one technical counterpart. Lastly, a common platform can facilitate all communication within the platform, and thus be very efficient. While common platforms and hub-and-spoke interlinking can be scalable and efficient from a technical point of view, they can face other challenges such as governance (BIS, IMF, and World Bank 2022).
By providing communication standards and channels within the arrangement, competition can be enhanced. If each PSP is responsible for establishing communication between systems, it might put smaller entities at a disadvantage and thus limit competition. Efforts to improve competition and expand the set of actors offering payment services should lower costs and provide more choices for end users.
While choices of interlinking model arrangements and common platforms come at a later stage, central banks should consider if communication should be an integrated part of the core infrastructure or if that communication should be left to PSPs to establish. Central banks could, from the outset, consider options for a future national gateway for communication and follow international work on, for example, APIs.
In addition to the infrastructure, there is also a connectivity aspect. Cross-border CBDC arrangements can build on synchronous communication and processing, requiring both the payer and payee wallets to be online at the same time. Synchronous communication and processing mean that when a message or request is sent, there is an immediate response. Hence, the choice of having centralized versus decentralized architectures becomes important. For example, Project Icebreaker uses smart contracts, Hashed Time Lock Contract (HTLC), to facilitate PvP settlement in two separate currencies and decentralized systems (see element 5 and Annex IV for how Icebreaker implemented the HTLC protocol).
HTLC is one approach often used in distributed ledger technology-based systems to achieve coordinated payments in separate ledgers—where the completion of all transfers comprising the transaction either succeed together or fail together—without the use of a third-party coordinator. The basic idea of the HTLC protocol is to place the money in technical escrow until all necessary conditions are met. In traditional systems, such coordination between different ledgers is often achieved through a “two-phase commit” protocol involving a coordinator. 25 For optimal and fast execution of the HTLC protocol, and many similar protocols, synchronous communication and processing is used and all wallets involved in the payment must be online and actively participating or be represented by an online agent. This is not a problem for the payer’s wallet, as the payer typically must actively initiate and approve the payment.
However, the payee or intermediary might not be online, especially if their wallets are autonomous (unhosted). 26 Hence, in CBDC systems with autonomous wallets, it may be that the protocol must be asynchronous, leading to potentially significantly slower execution. Alternatively, the payee must sign up for a service that can act on his behalf in receiving cross-border payments synchronously. In a fully centralized system, this is not an issue as “wallets” cannot be autonomous. These trade-offs and alternative approaches should be taken into consideration in the CBDC design, especially since many central banks are considering enabling domestic offline payments (BIS, IMF, and World Bank 2022).
- Key Design Considerations: Communication
Payment initiation is critical, and international coordination regarding standards is important to offer a seamless cross-border experience. Likewise, adopting and harmonizing the implementation of ISO 20022 emerges as a must to ease cross-border payments. Many of these standards already exist since they are not CBDC specific. By adopting standards such as ISO 20022, central banks will not only ease cross-border payments but can also ease domestic interoperability between payment systems. Standardized digital ID frameworks should also be considered. The choices of centralized versus decentralized architectures and hosted versus non-hosted wallets in decentralized systems will impact whether the payee’s wallet is required to be online and need to be carefully analyzed. While not necessarily impacting the domestic CBDC design initially, central banks should consider if cross-border communication should be an integrated part of the core infrastructure, such as facilitating APIs, or if that communication should be left to PSPs to establish. Centralizing functions could be important to ensure better competition so to reduce the cost for end users, and it would remove the need to rely on PSPs to provide the infrastructure. Key design considerations where cross-border attention is needed include the following:
▸ Payment initiation (proxies, QR code, NFC)
▸ Data and messaging standards
▸ Digital ID frameworks
▸ Centralized or private communication solutions
▸ Centralized versus decentralized architectures
▸ Hosted versus unhosted wallets in decentralized architectures
Element 3: Currency Conversion
There are different models for how one currency is exchanged for another. The key options regard whom to offer foreign exchange services, how the end user is matched with the foreign exchange provider, and how foreign exchange providers manage liquidity. As highlighted in the framework, design elements cannot be viewed in isolation from other elements since they are interconnected. The choice of currency conversion model is closely linked to the access policies and settlement model. Thus, currency conversion options must be viewed in tandem with the other elements. For example, the need for currency conversion is determined by access policies, and access policies determine the potential entity that can provide any foreign exchange service and thus increase competition for lower fees.
- Foreign Exchange Provision
Conceptually, we can think of three basic models for currency conversion in a retail cross-border payment: (1) using a foreign exchange provider, (2) using a separate foreign exchange provider and a financial intermediary, and (3) using the same PSP as a foreign exchange provider and financial intermediary (see Figure 3 ). 27 While the figure shows all payment legs to be CBDC, all of them do not have to be. For example, in model 2, the foreign exchange trade between the intermediary and the foreign exchange provider could be done using commercial bank money, and in model 3, it could be that the payer sends CBDC to the intermediary and the foreign exchange provider, but the payee receives a non-CBDC asset. That said, we focus on cases where all legs are using CBDC to fully understand the implications.
The first model implies that the payer exchanges CBDC-A with the foreign exchange provider for CBDC-B before sending CBDC-B to the payee. Note that this rests on the payer having access and the possibility to hold and transact both CBDC-A and CBDC-B. We assume the payee cannot hold CBDC-A.
If the payer cannot hold and transact CBDC-B, a financial intermediary is needed. Model 2 is an example of this. In this model, the payer transfers CBDC-A to a financial intermediary that uses a third-party foreign exchange provider to exchange the CBDC-A for CBDC-B before sending it to the payee. This model assumes that the financial intermediary can hold and transact both CBDC-A and CBDC-B.
As the third model, we can think of one PSP taking the role of both financial intermediary and foreign exchange provider. The payer pays CBDC-A to the foreign exchange provider, who pays CBDC-B to the payee. All models rest on the foreign exchange provider being able to hold and transact both CBDC-A and CBDC-B.
All three models include a foreign exchange provision role, and two of the models include an intermediary role. With this comes counterparty risk unless there is some form of conditionality to the payment making it so that all legs happen, or none do. The more actors involved in a transfer, the greater the risk. We return to this issue in the PvP section in the settlement element.

Stylized Currency Conversion Models
An entity only serving the role of financial intermediary does not need to hold any liquidity and can avoid currency risk, contrary to foreign exchange providers. 28 A foreign exchange provider carries currency risk and needs to manage liquidity in two currencies. Hence, financial intermediaries need to be able to transact large volumes of CBDC on their accounts, and foreign exchange providers might need to be able to hold large volumes on their accounts. Thus, access policies and holding/transaction limits for entities serving as foreign exchange providers and financial intermediaries will be important factors to consider.
For any of these arrangements to work, the market for foreign exchange must be sufficiently liquid. Market liquidity can be improved by concentrating order flows or improving price transparency (see, for example, Foucault and others 2013 ). Liquidity can also benefit from centralized foreign exchange services offered by a hub-and-spoke model or common platforms. See, for example, Adrian and others (2022) for how the centralization of information and foreign exchange trading, as well as greater competition and on-platform services like multi-currency auctions, can contribute to improving market liquidity. Similarly, the Icebreaker project demonstrated how a central hub in a communicator model could serve as a foreign exchange marketplace connecting end users with foreign exchange providers, decoupling the foreign exchange provision and financial intermediation from wallet provision. At the foreign exchange marketplace, users can choose the best foreign exchange provider and financial intermediary, leading to competition which is difficult to achieve with traditional banking relationships.
While such models can lower barriers for market entry and increase competition in foreign exchange provision, a question remains on how to incentivize a wider range of PSPs to join the market, which could be less profitable for incumbents (see BISIH and others 2023c , for more on the trade-offs associated with the foreign exchange model tested in Project Icebreaker). Lack of participation by foreign exchange providers leads to less liquidity in the market, which would not attract sufficient demand from the users. Hence, a well-functioning two-sided market might not be fully established. On this point, central banks could play an important role in providing foreign exchange in underserved corridors, although this might not fall within the mandate of all central banks. Another potential issue with separate foreign exchange markets incorporated in cross-border arrangements is the risk of emergence of multiple exchange rates if the market is segmented and trades in CBDC are constrained. In addition, if multiple non-compatible platforms, or at least platforms with limited interoperability, emerge, there is a risk of segmentation of liquidity. Such segmentation can lead to less efficient price discovery. Moreover, managing liquidity across multiple platforms or dealing with varying regulatory environments adds complexity and operational risk.
- Foreign Exchange Liquidity Management
In addition to who provides foreign exchange, there is a question of how the foreign exchange providers manage their liquidity. In fact, some central banks are considering limits on transaction or holding, and such restrictions can impact foreign exchange providers’ liquidity. Most of these restrictions are considered to apply only to individuals, but restrictions could also be imposed on other participants in the CBDC ecosystem. As highlighted in the access element, any restrictions must be designed to not hinder financial intermediation and foreign exchange provision. If cross-border CBDC payments are to be instant, foreign exchange providers need to either hold large amounts of CBDC or be able to fund their accounts instantly. Funding CBDC accounts can be done automatically from a “reverse waterfall” account—where CBDC payments made are instantly funded from another form of money. 29 This other form of money can be a reserve account with the central bank or a commercial bank account. In the former case, where foreign exchange providers have reserve accounts, the pool of potential foreign exchange providers could shrink significantly if access to the central bank balance sheet is restrictive.
Suppose instead reverse waterfall accounts can be commercial bank accounts; in that case, commercial banks will serve as liquidity providers and need to be able to hold CBDC liquidity or be able to fund their accounts instantly. However, holding liquidity in CBDC should be superior to ensure speedy transactions and leverage safety benefits. Thus, expanding access to CBDC or central bank reserves can be beneficial to reduce risks.
In either case, any holding limits imposed on intermediaries and foreign exchange providers (or liquidity providers) need careful consideration, and the ability to fund CBDC accounts instantly 24/7 becomes an important design feature. Since many central bank RTGS systems are not operating 24/7, the ability to convert central bank reserves to CBDC outside of operating hours could be limited. Thus, allowing foreign exchange providers, or other liquidity providers in the ecosystem, to hold sufficient CBDC liquidity becomes important.
In addition, the cross-border arrangements themselves can provide facilities to help with liquidity. These facilities could, for example, be in the form of liquidity bridges managed by the central banks ( CPMI 2022c ) or Automated Market Makers (AMMs) ( BISIH and others 2023a ).
Central bank liquidity bridges refer to a mechanism through which central banks can provide liquidity to financial institutions, such as banks. These bridges are essentially arrangements, liquidity pools, which allow financial institutions to borrow from the central banks and are made available on a short-term basis. The funds in the liquidity pool can be used by these institutions to meet their immediate funding needs, such as to cover unexpected cross-border flows by depositors. For example, liquidity pledged at one central bank can be used as collateral in another central bank ( CPMI 2022c ). In liquidity bridges, foreign exchange providers can use a local CBDC as collateral to the local central bank and borrow a foreign CBDC from the counterparty central banks. This approach could reduce the cost of foreign exchange liquidity management and the risks of currency, credit, and settlement. The collateral can potentially be other financial assets, such as government bonds and commercial papers, depending on the terms set by the central banks. Thus, central banks need to consider how such liquidity and collateral arrangement could impact CBDC system design.
Another approach is to deploy AMMs. AMMs, typically decentralized, utilize algorithms and smart contracts to provide liquidity and determine asset prices. While primarily used for crypto assets, ongoing projects, like Project Mariana ( BISIH and others 2023a ), explore the application of AMMs in non-crypto settings. The basic idea behind AMMs is that when a user wants to make a trade, they simply deposit one asset into the pool and receive the other in exchange. AMMs offer advantages such as liquidity provision for illiquid assets by pooling assets from various providers and 24/7 operation due to their automated decentralized exchange protocol. However, challenges arise regarding user costs, particularly when the fund supply is limited. Central banks can potentially address these challenges by providing liquidity when it is scarce. Another challenge involves determining the price between different assets. AMMs employ mathematical formulas to set prices, but discrepancies with external prices may prevent traders from executing trades at fair market prices, leading to suboptimal outcomes. One solution is integrating realtime oracles, a third-party service, that provides accurate external price information, enabling the AMM to adjust its calculations accordingly. However, determining the relevant external price and update frequency is a non-trivial task. Other challenges and risks with AMMs include potential increase in operational complexity and cybersecurity risks, as well and scalability and network congestion.
Liquidity bridges and AMMs are decisions likely taken at a later stage when formal cross-border arrangements are to be determined. However, such arrangements might impact the optimal CBDC design. For example, since AMMs typically rest on smart contracts to provide a technical escrow, such functionality, or similar, would be important to consider in the CBDC design.
Key Design Considerations: Currency Conversion
Currency conversion is primarily about access. Most cross-border payments will likely involve a foreign exchange provider and intermediary. To this end, the access policies, restrictions, and limits for potential foreign exchange providers and intermediaries are critical. Central banks should consider efforts to expand the pool of potential PSPs taking such roles, and any competition-enhancing efforts available should be considered. Decoupling of PSP services might be a tool to enhance competition but can also discourage market entry in some cases. Establishing liquidity arrangements might be important to serve corridors with lower trade and remittance volumes. To this end, central banks should also consider their own role in providing liquidity or currency conversion, as well as escrow functionality. 24/7 CBDC funding ability is also important to facilitate more flexible liquidity management. Key design considerations where cross-border attention is needed include the following:
▸ PSP access and limits (see Access)
▸ PSP competition aspects
▸ Foreign exchange liquidity management
▸ Escrow functionality
▸ 24/7 CBDC funding ability
Element 4: Compliance
Any cross-border arrangement must comply with relevant legal and regulatory requirements. To this end, roles of and responsibilities for various actors in a CBDC ecosystem with respect to regulatory compliance become key design considerations. Compared to the current landscape, the roles and responsibilities of entities involved in compliance might not be straightforward in a CBDC setting, and especially international standards and domestic legal and regulatory frameworks are still evolving. In addition, design options such as those intended to enhance privacy may require even more thought. These design options will bear an impact in both the domestic setting and the cross-border setting, and policy trade-offs may arise.
- Financial Integrity
CBDC arrangements, whether domestic or cross-border, must adhere to AML/CFT standards and laws. The Financial Action Task Force (FATF) standards apply to CBDCs as it does to any other form of fiat currency. Jurisdictions issuing CBDCs need to assess and understand the risk associated with the CBDC being used for money laundering and terrorism financing and take measures to manage and mitigate these risks, including the application of AML/CFT preventive measures. Toward this end, thus, intermediaries in a CBDC ecosystem that are covered by the FATF standards 30 would need to be regulated and supervised for AML/CFT purposes. Compliance challenges that arise in a CBDC setting will be similar if not identical to those present in the current financial system, but it is important to analyze and understand if there may be novel and unprecedented risks emerging. Compliance implications are also likely to vary depending on the specific design choices adopted. When considering the impact of design choices on compliance, it is important to note that the CBDC ecosystem would be more complex in a retail than in a wholesale setting and, similarly, more complex in a cross-border versus domestic arrangement, particularly regarding financial integrity concerns. However, this does not necessarily imply that a CBDC system would be more complex than current systems as it will depend on design.
Additional compliance considerations are also likely to be raised by the introduction of new intermediaries or changes in the services and/or products provided by existing service providers (particularly those that historically have not been subject to AML/CFT rules and regulations). 31 Since a CBDC is issued by the central bank, the nature of customer accounts and the relationship between end users and PSPs may be different in a CBDC system compared to the current retail banking model. In addition, solutions such as many-to-one mapping of CBDC service providers to end users as presented in Project Sela ( BISIH and others 2023b ) can present new complexities as well and will require further research.
CBDC will face the same challenges as the current system when it comes to challenges with different regulatory frameworks and uneven application of AML/CFT rules and regulations across jurisdictions. CBDC alone would not solve the issue. Counterparties may still refuse to service countries with weak implementation of AML/CFT rules even if CBDCs were available. In the case the introduction of CBDC leads to a reduction in the number of intermediaries involved in cross-border payments, some risks and challenges associated to compliance checks could decrease. Long transaction chains often span multiple countries, each with its own regulatory framework and compliance standards, and they can lead to increased opacity and time delays.
The level of anonymity that would be permissible under the relevant standard is still unclear. Some central banks are considering allowing anonymous low-value transactions in a limited manner with their CBDCs domestically. Like cash, such models are vulnerable to misuse for illicit activities, such as money laundering and terrorism financing. The decision on whether and how to integrate features to allow for a degree of anonymity in transacting ultimately depends on the policy demands and priorities of the jurisdiction; however, regardless of a jurisdiction’s decision in this regard, the FATF standards still apply. The cross-border dimension poses additional challenges, as jurisdictions may have different approaches to anonymous or pseudonymous payments. The same challenge applies to privacy—an individual’s right to control the access and use of their information. Countries have different privacy policies and regulations, and difficulties will likely arise where countries wish to preserve the same privacy levels for cross-border payments as for domestic payments. To this end, the work in Project Aurora ( BISIH 2023a ) and Project Aurum 2.0 from the BIS Innovation Hub on privacy-enhancing technologies can play an important role.
- Capital Flow Management Measures
Some countries rely on CFMs to limit risks arising from sudden and volatile capital flows. The IMF’s Institutional View (IV) holds that CFMs can be potentially warranted in certain circumstances, but only if they do not substitute warranted macroeconomic adjustments ( IMF 2022 ).
CFMs come in various forms, including authorization requirements, taxes, fees, or quantity limits on capital inflows or outflows. Traditionally, CFMs are applied by commercial banks and other financial service providers. These intermediaries collect information on capital flows, such as ultimate beneficiary and transaction purposes. They then use this information to apply CFMs as required by law. A CBDC system used for cross-border payments must be designed such that these checkpoints exist, and technology might play a role in this. CFMs can be described as well-defined rules or instructions. These instructions can be coded as an algorithm in the design of CBDC, which would make the CFMs automatic. This paper follows He and others (2023) and refers to this type of CFMs as “smart CFMs.” The application of smart CFMs might require some streamlining of CFMs, if these are not particularly suitable for an algorithmic representation. In particular, a switch from discretionary CFMs to rule-based CFMs as much as is feasible might be necessary to reap the full benefits of digital application and automation. 32
As described by He and others (2023) , smart CFMs can be implemented broadly on three levels of the CBDC system. The first level is the one where end users interact to make payments—the technical interface. The second level is the core CBDC system operated by the central bank, while the third level would be for the central bank to coordinate with other central banks the implementation of CFMs on a cross-border platform that connects the CBDC rails, or payment systems, of different countries.
Using CFMs on the user interface can be effective for CFMs that only require basic information and do not need to be updated quickly. Private interface providers may not have the resources to implement or update CFMs quickly. Certain types of user interfaces, such as smart cards, may present difficulties in implementing CFMs that require more information as they need to be online to obtain stock information.
When the central bank implements CFMs directly within the CBDC architecture, it takes on the responsibility of both designing and enforcing the CFMs. This leads to a higher overall effectiveness for any type of CFMs, particularly for those that require a large amount of information and quick implementation. Additionally, the central bank is likely to have the majority of the required information. For example, if there is a database containing cross-border stock information, it will likely be housed within the central bank.
The ability of central banks to implement CFMs in multilateral platforms, such as the common platforms presented in Box 2 , depends on the platforms’ governance. The application of CFMs on the platform might not be allowed, and both the national legislation of the participating countries and the platform itself must have established roles, procedures, and responsibilities for their potential application. In addition, if the platform is operated by the private sector or a collection of central banks, changes and application are likely to be slow. However, flexible technical designs can be used to accommodate different CFMs across jurisdictions. For example, project mBridge has introduced the Lego-Bricks Approach that modularizes various rules and functions such as payment, foreign exchange, capital management, and AML/CFT. The participating central banks and monetary authorities of different jurisdictions can make flexible combinations of the modules according to their needs, such as to implement CFMs. 33
Key Design Considerations: Compliance
It is important to carefully analyze cross-border implications for compliance issues, and it is necessary to balance objectives, roles, and responsibilities. Compliance responsibility must be established, and efforts to harmonize and simplify compliance checks are also important for CBDC. Central banks should consider the potential implications of having different privacy and anonymity levels for domestic and cross-border payments since domestic choices might not be feasible in all cross-border arrangements. Utilizing new technologies to ensure privacy while enhancing compliance checks and CFMs is important consideration. Any central bank needs to ensure that the legal and policy frameworks are as robust and transparent as possible so to minimize legal risks. Key design considerations where cross-border attention is needed include the following:
▸ Roles and responsibilities in the ecosystem
▸ Anonymity and privacy measures
▸ Smart CFMs
Element 5: Settlement
As described in element 3, in the case of a cross-currency payment, there are two payments: one in currency A and the other in currency B. These two payments need to be settled. Settlement finality refers to the irrevocable and unconditional transfer of ownership of financial assets between parties in a financial transaction. In simpler terms, once a settlement is deemed final, the transaction is considered complete, and the parties involved can no longer reverse or cancel it. A core problem in a cross-currency payment is the settlement risk that arises due to the presence of two payments.
In addition to strong legal and regulatory frameworks, including the legal aspect of settlement finality, 34 two design choices play a crucial role in reducing settlement risk in cross-currency trades. First, 24/7 availability and instant settlement remove any settlement risk caused by timing and a mismatch of operating hours. Second, PvP settlement functions can reduce settlement risk by reducing the counterparty risk, often referred to as principal risk or Herstatt risk. Other measures, such as emergency liquidity assistance, can reduce counterparty default risk but go beyond the scope of this paper. The foreign exchange models presented earlier in Figure 3 can be used to exemplify the settlement risks. In models 1 and 2, the foreign exchange provider would only deliver CBDC-B if certain that the CBDC-A will be delivered. Likewise, the payer would only send CBDC-A to the foreign exchange provider or the intermediary if certain to receive the CBDC-B or certain that the intermediary will pay the money to the payee. In addition, CBDC has a unique benefit in removing the issuer default risk since the asset is a liability of a central bank rather than a private entity.
- Instant Settlement
Instant payments are processed and settled individually and continuously. This means that participants must maintain adequate balances to settle transactions at any time. In a CBDC setting, this is not a problem for the payer since they already hold the funds, and for the payee, instant settlement is a big benefit since they receive the funds directly without any delay.
In most foreign exchange transactions, trade execution and settlement are decoupled. This decoupling has the advantage that multilateral clearing and netting can be performed. The disadvantage is that there are long delays between trade execution and settlement. Instant settlement would imply that trade execution and settlement are one and the same. Hence, offering foreign exchange from currency A to currency B implies that the foreign exchange provider needs to hold liquidity in currency B at the trade moment. Hence, if foreign exchange providers are to offer CBDC foreign exchange services, they would need to forecast the CBDC liquidity need. Alternatively, the foreign exchange provider needs to be able to instantly secure the CBDC liquidity needed by, for example, utilizing an intraday credit offered by the central bank, or instant issuance of new CBDC. Most central banks consider a CBDC design with 24/7 availability and therefore need to consider any potential side effects related to liquidity management for foreign exchange providers and financial intermediaries in a cross-border setting.
Instant settlement and 24/7 availability come with challenges such as managing liquidity in real time and ensuring operational and cybersecurity in a 24/7 environment. Another issue that arises with instant settlement is how to prevent fraud. In many payment scenarios, the person making the payment can recall the payment in case of an error before it is settled. However, in the case of instant settlement, the payment is completed within seconds, and once completed, it cannot be canceled. Moreover, the recipient can withdraw the funds immediately. This creates a challenge in detecting and stopping fraudulent payments, particularly when the recipient is the bad actor. This issue is relevant for domestic payments, and it becomes even more complicated for cross-border payments. These trade-offs must be considered and studied during the design phase of a CBDC project.
- Payment versus Payment
Currently, most cross-border retail payments rely on trusted relationships. Payers typically have a longstanding relationship with their PSP and trust that the PSP will carry out the actions needed for the payee to receive the money. In the foreign exchange market between banks, trust is not always the only factor. Arrangements for PvP are available for the major currencies via the use of a common platform, such as CLS (see CPMI 2022a ). Based on the models presented in Figure 3 , we classify two forms of PvP: traditional PvP, where two actors exchange currencies, and coordinated (or one-directional) PvP, where there is an intermediary (see Figure 4 ).

Stylized Models for Payment versus Payment (PvP)
In a retail CBDC setting, an intermediary is likely needed. Hence, a cross-border retail CBDC arrangement using PvP will probably have a “coordinated” setting, such as case 3 in Figure 3 . Note that case 1 in Figure 3 would have a traditional PvP function, while case 2 would have both a traditional and a coordinated part.
The choice of communication infrastructure will play a role in implementing PvP, regardless of it being traditional or coordinated PvP. In the case of a common platform, PvP is simple to facilitate, while PvP across systems is more complicated and often comes with some additional risk of failure. However, standardized communication and formal interlinking of systems reduce the risk. There are two main approaches for achieving PvP: third-party-based and peer-to-peer.
PvP can be implemented via the use of a trusted third party to facilitate the exchange of assets between two parties. The third party can take different forms, but the basic premise is that it acts as an intermediary that verifies the receipt of both assets and releases them to the respective parties. The third party can be an entity that acts as a central counterparty (CCP) so that the funds are paid to the entity, who in turn pays the final beneficiaries. The main role of such a CCP is to mitigate counterparty risk between market participants. In a typical transaction between two parties, each party is exposed to the credit and default risk of the other party. By using a CCP, both parties can reduce their counterparty risk, as the CCP becomes the counterparty to each trade.
An alternative to using a third party is to use peer-to-peer transactions which can be achieved in different ways. It is typically achieved via the use of “technical escrow” (or “smart contracts”). 35 Technical escrow uses technical locks, rather than third-party accounts, with some conditionality to unlock the money. This allows for peer-to-peer transactions. This exchange can be orchestrated by a technical “oracle” taking a role where the trusted oracle countersigns the transactions without actually holding any funds. 36 Instead of an oracle, atomic swaps can be used. A common alternative for atomic swaps is to use HTLC. HTLC can take different forms, but a traditional PvP can be seen in two stages: first, the payer locks a payment with hash of a secret, and the payee reciprocates with a mirrored payment. In the second stage, the payer reveals the secret to unlock the payee’s payment, initiating a chain reaction that allows both parties to access their respective funds. 37
The key difference between PvP by third party or peer-to-peer is the trust required between the parties. A third-party-based arrangement relies on a third-party entity to ensure that both parties receive their respective assets, which requires trust in the third-party entity. By contrast, peer-to-peer transactions do not require a third party to facilitate the exchange of assets but require trust in the technology implementation of the protocol.
For the CBDC design, ledger technology becomes an important factor to consider. While technology with innate smart contract functionality can facilitate certain protocols using trust in technology, the same protocol can be achieved with less advanced technology and even analog methods, implying that a trusted third party is needed.
Key Design Considerations: Settlement
Instant settlement and 24/7 availability, together with PvP functionalities, emerge as important to enhance cross-border payments since they reduce the settlement risk. Recent CBDC experiment and, more generally, cross-border experiments are all heavily focused on speed and utilizing smart contracts to facilitate PvP settlement. Hence, future cross-border arrangements might require programmability or alternative methods to follow such protocols, and this becomes an important design feature to consider. Key design considerations where cross-border attention is needed include the following:
▸ Instant settlement
▸ 24/7 availability
▸ Programmability
- 4. Conclusions
When designing retail CBDC systems, it is beneficial to factor in cross-border implications from the start. Even if cross-border payments are not considered to be available at the initial launch, avoiding unintended barriers for potential later stages is important. This importance was recognized in the G20 Roadmap, where Building block 19 consider “Factoring an international dimension into CBDC design” (BIS, IMF, World Bank 2021 and 2022). This paper further assists central bank in their efforts to factoring in an international dimension in their CBDC exploration.
While this paper has focused on retail CBDC, many of the lessons apply also to wholesale CBDC and other forms of money. A retail CBDC is intended to be available for household, providing them with direct access to central bank money. Instead, a wholesale CBDC is typically intended to only be available to banks and financial institutions. With a retail CBDC, households within a country transact directly and thus need fewer financial intermediaries. These are, however, likely to be needed in a cross-border payment, to convert currencies and expand access to foreign market. That said, using a retail CBDC for cross-border payments can reduce the total number of intermediaries needed, and can lower credit and settlement risks for users. If a retail CBDC is not available for cross-border payments, retail users could still benefit from cross-border wholesale CBDC arrangements. These can deliver more efficient interbank cross-border payments, which would ideally trickle down to faster and cheaper payments for end users.
Given that the future cross-border payments landscape is still unfolding and potentially fragmented, central banks should ensure their retail CBDC systems to be able to “plug in” to different forms of arrangements. Such flexible or modular design refers to an approach where systems are built using components that can be easily modified, replaced, or extended without requiring significant changes to the overall architecture.
A strong focus on international collaboration with other central banks is also important for central banks to consider. Establishing agreements, collaborations, and mechanisms to facilitate information sharing and policy coordination is paramount to the viability of these arrangements and their ability to facilitate and enhance cross-border payments. International organizations such as the International Monetary Fund, the World Bank, and the Bank for International Settlements play a significant role in fostering cooperation and providing capacity development and guidance. Such international cooperation can be more impactful if achieved at a global level to avoid fragmentation and walled gardens. Additionally, the priority actions agreed under the G20 Roadmap in the coming years will be important.
To factor in cross-border implications right from the start is not a trivial task. Central banks can establish a cross-border workstream in their CBDC exploration in an effort to consider cross-border implications. This paper has viewed cross-border payments through the lens of five elements, allowing us to identify and present some core design and policy options that central banks need to view from a cross-border perspective. However, this analysis is not comprehensive, and any technical and policy design considerations during the CBDC exploration should be viewed through the lens of cross-border payments. The questions listed in Box 3 provide additional guidance.
Guiding Baseline Questions When Factoring in Cross-Border Implications in the CBDC Design
1. What are the cross-border-related objectives?
2. What role should the central bank play in facilitating cross-border payments?
3. Do non-residents have access to the CBDC, and what are the rules and criteria for that access?
4. What are the rules and access criteria for financial intermediaries and foreign exchange providers?
Communication
5. What data and messaging standard(s) do the system support?
6. Are we following the guidance from CPMI on ISO 20022 implementation?
7. What standards are used for payment initiation (for example, proxies, QR code, NFC)?
8. What digital ID framework is necessary to ensure smooth and efficient cross-border transactions?
9. Is the system or the wallet providers responsible for identifying that it is a cross-border payment?
10. Should there be a national gateway for any formal interlinking with other systems?
Currency conversion
11. Who is providing foreign exchange and how are end users matched with the foreign exchange provider?
12. What is the role of the central bank in facilitating foreign exchange transactions and liquidity?
13. How will international AML/CFT standards be incorporated into the system’s compliance framework?
14. Who is responsible for AML/CFT compliance checks (including KYC)?
15. Who is responsible for CFM compliance checks?
16. Should AML/CFT compliance checks (including KYC) be automated and/or centralized?
17. Should “smart CFMs” be implemented, and at what level?
18. Should the system offer programmability options, for example, smart contracts, to facilitate PvP?
19. Should a centralized trusted oracle/CCP be part of the baseline CBDC ecosystem?
- Annex I. Traditional Arrangements through the Lens of the Five Elements
- Annex II. eNaira as a Payment Option for Inbound Remittances
The Central Bank of Nigeria (CBN) has introduced the eNaira as a payment option for inbound remittances. Hence, while the payment in the foreign currency might occur using other means than CBDC, the international money transfer operator (IMTO) can make the payment to the recipient using eNaira. As per the “Operational framework for eNaira payment option to recipients of diaspora remittances,” the following guidelines are provided: 38
1. IMTOs are to apply for a one-time “No Objection” to pay out in eNaira from the CBN.
2. The CBN shall provide account details where foreign currency from the IMTOs shall be received.
3. IMTOs are required to open Merchant Wallets through the CBN.
4. IMTOs are to prefund the CBN account mentioned in (2) above with foreign currency.
5. The CBN will subsequently fund the IMTO Merchant Wallet with eNaira equivalent of the foreign currency earlier prefunded by the IMTO.
6. Payment procedure shall be as follows:
a. Sender initiates diaspora transfer with IMTO of choice overseas providing details of beneficiary’s wallet,
b. IMTO logs into the eNaira web wallet portal, debits its eNaira Merchant wallet, and credits beneficiary with eNaira equivalent of foreign currency sent at origin using I&E window rate 39 , or
c. Alternatively, IMTO integrates with the eNaira portal from its platform via API provided by CBN and initiates transfer of eNaira equivalent of foreign currency sent at origin at the I&E window rate.
In other words, the payment process could be as follows. A payer residing in, for example, the USA sends US dollars to an IMTO. The IMTO deposits the dollar with the CBN in exchange for eNaira. The IMTO then transfers eNaira to the wallet of the recipient of the remittances. This process requires a CBDC design that allows for IMTOs to open CBDC wallets. In its most simple form, the process can be viewed as model 3 in Figure 3 but can also be viewed as model 2 if the IMTO purely acts as intermediary and do not take the currency risk itself.
- Annex III. Foreign Exchange Provider Restrictions
Some central banks are considering transaction or holding limits. Most of these restrictions are considered to apply to individuals but could also be imposed on other participants in the CBDC ecosystem. Some central banks might wish to restrict the amount of retail CBDC that entities can hold, and some central banks might want to limit holdings by financial institutions and other PSPs. While it is likely that foreign exchange providers will be commercial banks, efforts to allow for a more diverse group of foreign exchange providers might be beneficial from a competition standpoint. Hence, it is unclear who would take the role of foreign exchange provider, and potential limits can impact foreign exchange providers and the currency conversion mechanism in a cross-border arrangement.
One alternative to solve problems with limits is to use a “waterfall model.” Suppose the payer is sending CBDC-A to a foreign exchange provider wallet, but the wallet with the additional funds will be over the limit. To ensure seamless experience for end users, the foreign exchange wallet must be able to receive the funds. One possible way to address this problem would be for any payment taking CBDC holdings above a certain limit to be accepted but trigger an automatic transfer of the excess funds from the CBDC wallet to another asset. This asset could be a designated reserve account, a wholesale CBDC wallet, or an account with a commercial bank. Hence, each foreign exchange provider would have to designate a “waterfall” account. This model can also be used for handling limits for regular CBDC wallets held by individuals.
For the sending foreign exchange wallet, it is potentially more complicated. Since the foreign exchange provider is receiving CBDC-A in country A, the foreign exchange provider’s wallet in country B would need to send CBDC-B. Hence, the wallet would need to hold or source the funds. One alternative is for the wallet to instantly fund the wallet with the required amount of CBDC on a payment-by-payment basis. This model might, however, slow down the process since there would be an additional step in the payment chain. In addition, if set too low, the limits might cause a payment queue where one payment must wait for other payments to finalize.
An alternative model would be for the central bank to participate in each cross-border payment actively. Hence, instead of the payer sending CBDC to the foreign exchange provider and the foreign exchange provider sending CBDC to the payee, the instruction could be to redeem and issue CBDCs. That is, the payer could redeem its CBDC to the central bank who in turn issues reserves or a wholesale CBDC to the foreign exchange provider or the foreign exchange provider’s bank. Likewise, the foreign exchange provider could redeem a wholesale CBDC, or reserves, and request the central bank to issue CBDC directly to the payee. This model would be more complicated and likely significantly slower. In addition, if the foreign exchange provider is not eligible to hold reserves or a wholesale CBDC, the benefit of CBDC and central bank money would be lost from the perspective of the foreign exchange provider.
Yet another alternative is to do an overnight sweeping of accounts. This model would allow the foreign exchange provider to hold an unlimited amount of CBDC during the day but force the foreign exchange provider to convert the CBDC to reserves or a wholesale CBDC during monetary operations. This would not only remove potential problems for monetary policy implementation but would also create friction in the retail CBDC foreign exchange market during these operations.
Finally, foreign exchange wallets can have special rules, and any CBDC holdings in these wallets can be given the same status as a wholesale CBDC or even reserves. Such a model would, however, limit the pool of entities taking the role of foreign exchange provider to the current institutes participating in RTGS systems.
- Annex IV. Design Implications of the Icebreaker Protocol
The Icebreaker project is to date the only retail-focused, cross-border CBDC project, and we use this project as a case study to identify some important design options and considerations. Based on BIS and others (2023b), 40 the payment process in Icebreaker can be described in eight phases:
Phase 1: Payer enters currency and amount, and the payer wallet sends a quote request to the hub.
Phase 2: The hub retrieves the best available quote from its foreign exchange database and responds with the best quote and the identity of the associated foreign exchange provider.
Phase 3: If the payer accepts the quote, she proceeds by entering the payee’s payment address/alias and the payer wallet sends a payment request to the payee wallet.
Phase 4: The payee wallet validates its wallet address and generates a secret and sends the verification results and returns a hash value of the secret to the payer wallet. 41
Phase 5: The payer wallet creates a locked payment to the foreign exchange provider’s payer-currency wallet.
Phase 6: The foreign exchange provider’s payer-currency wallet sends the payment information and the hash value to the foreign exchange provider’s payee-currency wallet where it creates a locked payment in the payee currency to the payee wallet.
Phase 7: The payee wallet recognizes there is a locked incoming payment and presents the secret (generated in phase 4) to the smart contract locking the incoming payment, and the funds are released to the payee wallet only if the calculated hash value of the presented secret matches the hash value used to lock the payment.
Phase 8: The secret is now revealed to the foreign exchange provider’s payee-currency wallet and the secret is sent to the foreign exchange provider’s payer-currency wallet where it presents the secret to the smart contract to unlock the incoming payer currency payment.
The steps, especially in phases 1–3, might be slightly different from a user’s perspective depending on the use case. If the payer, for example, scans a QR code to initiate the payment, all the payment details such as amount, currency, and address would be entered at the same time. Regardless, using the above protocol, we can identify important design considerations for domestic CBDC systems.
The first step is payment initiation. Any domestic CBDC system needs to consider how cross-border payments would be initiated. This applies to both incoming and outgoing payments. For incoming payments, one relevant design feature is whether QR codes, NFC messages, and aliases are available to and compatible with foreign systems. For outgoing payments, the reverse question applies—are foreign systems “readable” by the domestic system directly, or is it up to the wallet provider to understand foreign systems and identify that a cross-border payment is to be initiated?
In an interlinking arrangement like Icebreaker, there is a question of whether each wallet or PSP communicates directly with the other systems (the hub in the Icebreaker case) or if the connection is centralized through a national gateway. The three systems connected in the Icebreaker project appear to have adopted different approaches, with Israel having a gateway, Sweden connecting via PSP nodes, and Norway directly to each non-hosted wallet.
While the project demonstrates that there is autonomy for central banks in how they design their systems, it also demonstrates that the design each system chooses will impact how those systems need to adopt to facilitate cross-border payments. A fundamental part of the Icebreaker model is the use of HTLC to facilitate coordinated PvP. BISIH and others (2023c) state that “[each CBDC] system must be able to implement HTLC-based conditional settlement.” It is important to clarify that for the protocol to operate correctly, it is sufficient for the foreign exchange provider to know and trust the status of the different HTLC states locally within each system and inform their foreign counterpart wallet of the status. At no point does the foreign wallet depend on the implementation details of how that status was reached. As a result, the HTLC functionality can be implemented in very different ways in different CBDC systems, depending on the underlying technology.
If a jurisdiction envisions that there might be scope for cross-border arrangements that utilize HTLC-like functions to facilitate PvP, they ought to consider technological implications. A system using distributed ledger technologies can leverage native capabilities, such as smart contracts, to provide the desired HTLC protocol. We can think of smart contracts as “technical escrow” where neither party can access the money while under the control of the smart contract.
A system without smart contract capabilities might instead use an escrow agent. This agent will have the same duties as the smart contract: release the money to the recipient if the conditions are satisfied, and release it back to the sender in case of a time-out. The agent must be a trusted third party. Hence, a jurisdiction does not need to adopt a technology that allows for smart contracts, but they may then need to establish a trusted escrow agent to achieve a payment protocol as in Icebreaker. The trade-off between having a trusted third party and utilizing technology to establish trust must be assessed.
Icebreaker assumes, for simplicity, that foreign exchange providers have the liquidity needed. A production version might have functionalities to “reserve” liquidity between phase 1 (payer asking for a quote) and phase 6 (locking of the payee currency payment). Such reservation of funds and other ill will intents might prompt illicit behavior of spamming the hub for quotes. This can easily be avoided by banning wallets that misbehave or by putting restrictions on how many requests can be sent. The design implication is whether any such restrictions are handled at the hub-connection level or on the wallet level.
Another potential spamming problem relates to the secret-generating phase. There are three main potential places for the payer to approve and commit to the payment. It could be done in phase 1 before sending the quote request. But the payer would then initiate a payment with no information regarding the foreign exchange rate. It could instead be done in phase 3, just before the payer sends the payment request to the payee. But this would still imply that the payee does not have all information. The payer does not have verification that the receiver of the money is correct or the hash value. The payer approval and commitment to the payment could instead be before phase 5 when the locked payment is created.
The problem with approving and committing late in the process is that the payer can spam other systems and wallets with payment requests, forcing them to generate address validation and hash value responses. Careful balancing of the approval process and rules regarding misbehavior will be needed to ensure that only genuine payments are initiated. It is also unclear if these decisions will be fully up to each CBDC systems, or if the cross-border arrangement will dictate the approval process.
Adrian , Tobias , and Tommaso Mancini-Griffoli . 2023 . “ The Rise of Payment and Contracting Platforms .” IMF Fintech Note 2023/005 , International Monetary Fund , Washington, DC .
- Search Google Scholar
- Export Citation
Adrian , Tobias , Federico Grinberg , Tommaso Mancini-Griffoli , Robert M. Townsend , and Nicolas Zhang . 2022 . “ A Multi-Currency Exchange and Contracting Platform .” IMF Working Paper 22/217 , International Monetary Fund , Washington, DC .
Bank of Canada and Monetary Authority of Singapore . 2019 . “ Jasper-Ubin design paper: enabling cross-border high value transfer using distributed ledger technologies .” Accenture, New York .
Bank of England and HM Treasury . 2023 . “ The digital pound: A new form of money for households and businesses .” Consultation Paper , Bank of England , London .
BIS Innovation Hub (BISIH) . 2021 . “ Nexus: a blueprint for instant cross-border payments .” Bank for International Settlements , Basel, Switzerland .
BIS Innovation Hub (BISIH) . 2023a . “ Project Aurora: The power of data, technology and collaboration to combat money laundering across institutions and border .” Bank for International Settlements , Basel, Switzerland .
BIS Innovation Hub (BISIH) . 2023b . “ Project mBridge Update Experimenting with a multi-CBDC platform for cross-border payments .” Bank for International Settlements , Basel, Switzerland .
BIS Innovation Hub (BISIH), Bank of France, and Swiss National Bank . 2021 . “ Project Jura – Cross-border settlement using wholesale CBDC .” Bank for International Settlements , Basel, Switzerland .
BIS Innovation Hub (BISIH), Bank of France, Monetary Authority of Singapore, and Swiss National Bank . 2023a . “ Project Mariana: Cross-border exchange of wholesale CBDCs using automated market-makers .” Interim Report , Bank for International Settlements , Basel, Switzerland .
BIS Innovation Hub (BISIH), Bank of Israel, and Hong Kong Monetary Authority . 2023b . “ Project Sela – An accessible and secure retail CBDC ecosystem .” Bank for International Settlements , Basel, Switzerland .
BIS Innovation Hub (BISIH), Bank of Israel, Norges Bank, and Sveriges Riksbank . 2023c . “ Project Icebreaker: breaking new paths in cross-border retail CBDC payments .” Bank for International Settlements , Basel, Switzerland .
BIS Innovation Hub (BISIH), Hong Kong Monetary Authority, Bank of Thailand, the Digital Currency Institute of the People’s Bank of China and the Central Bank of the United Arab Emirates . 2022a . “ Project mBridge: Connecting economies through CBDC .” Bank for International Settlements , Basel, Switzerland .
BIS Innovation Hub (BISIH), Reserve Bank of Australia, Central Bank of Malaysia, Monetary Authority of Singapore, and South African Reserve Bank . 2022b . “ Project Dunbar – International settlements using multi-CBDCs .” Bank for International Settlements , Basel, Switzerland .
Committee on Payments and Market Infrastructures (CPMI) . 2018 “ Cross-border retail payments .” Bank for International Settlements , Basel, Switzerland .
Committee on Payments and Market Infrastructures (CPMI) . 2020 . “ Enhancing cross-border payments: building blocks of a global roadmap .” Stage 2 Report to the G20 , Bank for International Settlements , Basel, Switzerland .
Committee on Payments and Market Infrastructures (CPMI) . 2022a . “ Facilitating increased adoption of payment versus payment (PvP) .” Consultative Report , Bank for International Settlements , Basel, Switzerland .
Committee on Payments and Market Infrastructures (CPMI) . 2022b . “ Interlinking payment systems and the role of application programming interfaces: a framework for cross-border payments .” Report to the G20 , Bank for International Settlements , Basel, Switzerland .
Committee on Payments and Market Infrastructures (CPMI) . 2022c . “ Liquidity bridges across central banks for cross-border payment .” Analysis and Framework , Bank for International Settlements , Basel, Switzerland .
Committee on Payments and Market Infrastructures (CPMI) . 2022d . “ Improving access to payment systems for cross-border payments: best practices for self-assessments .” Bank for International Settlements , Basel, Switzerland .
Committee on Payments and Market Infrastructures (CPMI) . 2023 . “ ISO 20022 harmonisation requirements for enhancing cross-border payments .” Consultative Report , Bank for International Settlements , Basel, Switzerland .
Committee on Payments and Market Infrastructures (CPMI) and the International Organization of Securities Commissions (IOSCO) . 2022 . “ Application of the Principles for Financial Market Infrastructures to stablecoin arrangements .” Bank for International Settlements , Basel, Switzerland .
Committee on Payments and Market Infrastructures and BIS Innovation Hub (BIS), International Monetary Fund (IMF), and World Bank . 2021 . “ Central bank digital currencies for cross-border payments .” Report to the G20 , Bank for International Settlements , Basel, Switzerland .
Committee on Payments and Market Infrastructures and BIS Innovation Hub (BIS), International Monetary Fund (IMF), and World Bank . 2022 . “ Options for access to and interoperability of CBDCs for cross-border payments .” Report to the G20 , Bank for International Settlements , Basel, Switzerland .
Das , Mitali , Tommaso Mancini Griffoli , Fumitaka Nakamura , Julia Otten , Gabriel Soderberg , Juan Sole , and Brandon Tan . 2023 . “ Implications of Central Bank Digital Currencies for Monetary Policy Transmission .” IMF Fintech Note 2023/010 , International Monetary Fund , Washington, DC .
European Central Bank (ECB) . 2024 . “ Sweden joins TIPS – Eurosystem instant payments platform also settles in kronor .” MIP News , February 27.
Financial Stability Board (FSB) . 2020a . “ Enhancing Cross-border Payments—Stage 1 Report to the G20 .” Financial Stability Board , Basel , Switzerland .
Financial Stability Board (FSB) . 2020b . “ Enhancing Cross-border Payments—Stage 1 report to the G20: Technical Background Report .” Financial Stability Board , Basel , Switzerland .
Financial Stability Board (FSB) . 2023 . “ G20 Roadmap for Enhancing Cross-border Payments: Priority actions for achieving the G20 targets .” Financial Stability Board , Basel , Switzerland .
Foucault , Thierry , Marco Pagano , and Ailsa Röell . 2013 . Market Liquidity: Theory, Evidence, and Policy . New York : Oxford University Press .
G7 . 2021 . “ Public Policy Principles for Retail Central Bank Digital Currencies (CBDCs) .” HM Treasury, London .
He , Dong , Annamaria Kokenyne , Tommaso Mancini Griffoli , Marcello Miccoli , Thorvardur Tjoervi Olafsson , Gabriel Soderberg , and Herve Tourpe . 2023 . “ Capital Flow Management Measures in the Digital Age (2): Design Choices for Central Bank Digital Currency .” IMF Fintech Note 2023/009 , International Monetary Fund , Washington, DC .
International Monetary Fund (IMF) . 2017 . “ Recent Trends in Correspondent Banking Relationships: Further Considerations .” Policy Paper , International Monetary Fund , Washington, DC .
International Monetary Fund (IMF) . 2020 . “ Digital Money across borders: macro-financial implications .” Policy Paper , International Monetary Fund , Washington, DC .
International Monetary Fund (IMF) . 2022 . “ Review of the institutional view on the liberalization and management of capital flows .” Policy Paper , International Monetary Fund , Washington, DC .
Kosse , Anneke , and Ilaria Mattei . 2023 . “ Making headway – Results of the 2022 BIS survey on central bank digital currencies and crypto .” BIS Papers No. 136 , Bank for International Settlements , Basel, Switzerland .
Lannquist , Ashley , and Brandon Tan . 2023 . “ Central Bank Digital Currency’s Role in Promoting Financial Inclusion .” IMF Fintech Note 2023/011 , International Monetary Fund , Washington, DC .
Mu , Changchun . 2023 . “ Theories and practice of exploring China’s e-CNY .” In Data, Digitalization, Decentialized Finance and Central Bank Digital Currencies: The Future of Banking and Money , edited by A. Dombret and P.S. Kenadjian . Boston : De Gruyter , 179 – 190 .
Soderberg , Gabriel , John Kiff , Herve Tourpe , Marianne Bechara , Stephanie Forte , Kathleen Kao , Ashley Lannquist , Tao Sun , and Akihiro Yoshinaga . 2023 . “ How Should Central Banks Explore Central Bank Digital Currency? A Dynamic Decision-Making Framework .” IMF Fintech Note 2023/008 , International Monetary Fund , Washington, DC .
Society for Worldwide Interbank Financial Telecommunication (SWIFT) . 2022 . “ Connecting digital islands: CBDCs .” Results Report: Phase 2 Experiments , Society for Worldwide Interbank Financial Telecommunication , La Hulpe, Belgium .
Tan , Brandon . 2023 . “ Central Bank Digital Currency Adoption: A Two-Sided Model ”, IMF Working paper 2023/127 , International Monetary Fund , Washington, DC .
Tourpe , Herve , Ashley Lannquist , and Gabriel Soderberg . 2023 . “ A Guide to Central Bank Digital Currency Product Development 5P Methodology and Research and Development .” IMF Fintech Note 2023/007 , International Monetary Fund , Washington, DC .
See Soderberg and others (2023) and Kosse and Mattei (2023) for central bank motivations for exploring CBDC.
See CPMI (2020) for challenges and frictions and BIS, IMF, and World Bank (2021 and 2022) for how CBDC can provide some benefits.
A CBDC system is a relationship of three components: the instrument, the infrastructure, and the scheme. The instrument refers to the liability issued by the central bank. The infrastructure is the software and hardware technology allowing the instrument to be transferred, and the scheme is the rules, standards, and practices clarifying processes and roles of ecosystem participants.
A wholesale CBDC is typically intended only for banks and financial institutions.
See Tourpe and others (2023) for the product development phases of a CBDC project.
ISO 20022 is an international financial messaging standard that provides a common language for communicating data between financial institutions.
A PSP is an entity that provides payment services. Payment service providers include, but are not limited to, banks and other deposit-taking institutions, as well as specialized entities such as money transfer operators and e-money issuers.
Many cross-border payments include a currency conversion. As such (at least) two currencies and two payments are involved. We define it to be a cross-border CBDC payment as long as at least one of the payments are made using CBDC. That is, a payment can, for example, be initiated using CBDC but be received as commercial bank money, e-money, or even cash (or reversed).
Cross-border payments can be viewed through additional elements, such as resilience, governance, and legal frameworks, but we leave these out of scope as they can be seen to “sit above” our five elements.
Examples of non-CBDC bilateral links are: Directo a Mexico , linking the US and Mexico; euroSIC , linking Switzerland and the Euro area; and the link between the PayNow system in Singapore and the PromptPay system in Thailand. In addition, there are wholesale CBDC experiments such as Jasper-Ubin ( Bank of Canada and Monetary Authority of Singapore 2019 ). For hub-and-spoke, the REPSS (COMESA) solution is an airport-style model, while Nexus ( BISIH 2021 ), Icebreaker ( BISIH and others 2023c ), and Swift (2022) are all examples of communicator models. See also CPMI (2022b) and BIS, IMF, and World Bank (2021 and 2022).
Wholesale CBDC experiments such as mBridge ( BISIH and others 2022a ; BISIH 2023b ), Jura ( BISIH and others 2021 ), and Dunbar ( BISIH and others 2022b ), are examples of using a limited-purpose common platform. TIPS is designed as a multicurrency platform—currently offering instant payments settlement in two currencies: the euro and the Swedish krona—would be more of an example of a single common platform ( ECB 2024 ). The framework presented by Adrian and Mancini-Griffoli (2023) and Adrian and others (2022) could be seen as either a limited-purpose or a single platform.
Thus, the focus is not on designing the cross-border arrangements themselves, but rather the implications for domestic design.
A non-resident citizen is an individual who is a citizen of the issuing jurisdiction but residing abroad.
A non-resident foreigner is an individual who is neither a resident nor a citizen of the issuing jurisdiction.
The People’s Bank of China has also introduced three principles for cross-border CBDC arrangements, which are “No disruption/Do no harm, Compliance, and Interoperability” ( Mu 2023 ).
In addition to policy measures, enhanced data frameworks can be important to better understand and mitigate risks. An international coordination effort is underway to establish a standard data reporting framework among central banks for digital money, as outlined in Recommendation 11 of the G-20 Data Gaps Initiative (DGI-3).
Both legs of the payment do not have to be CBDC. It could for example also be that one leg uses CBDC while the other uses commercial bank money.
A nostro account refers to an account that a bank holds in a foreign currency at another bank.
See BIS, IMF, and World Bank (2022) for more on access policies and CPMI (2022d) for best practices for self-assessments for improving access to payment systems for cross-border payments more generally. See also Project Dunbar (BISIH and others 2022) for an example of an indirect “sponsor” model.
The Nexus project is led by BISIH Singapore Centre, and in 2022, they built a working prototype to connect the test systems of three established instant payment systems (IPSs): The Eurozone’s TARGET Instant Payment Settlement (TIPS) system, operated by Bank of Italy on behalf of the Eurosystem, Malaysia’s Real-time Retail Payments Platform (RPP), operated by Payments Network Malaysia (PayNet), and Singapore’s Fast and Secure Transfers (FAST) payment system, operated by Banking Computer Services (BCS). The BISIH Singapore Centre is now collaborating with the central banks of Indonesia, Malaysia, the Philippines, Singapore, and Thailand as they work towards connecting their domestic payment systems. For more details about Nexus, see: https://www.bis.org/about/bisih/topics/fmis/nexus.htm
Related to information and identity sharing is the exploration of privacy-enhancing technologies by several central banks (see, for example, Project Aurora and Project Aurum 2.0, from the BIS Innovation Hub) demonstrating that the combination of identifiers and privacy-enhancing technologies can enable both efficient identification of all parties and ensure high levels of privacy.
NFC and QR codes are both technologies used for communication and information exchange. While NFC enables short-range wireless communication between devices in close proximity, QR codes are visual representations of information that can be scanned and interpreted by a camera-equipped device. NFC requires physical proximity and is often used for secure transactions and data exchange, while QR codes are versatile and widely used for a variety of purposes. NFC and QR codes can be used for both person-to-business and person-to-person payments.
In a bilateral link model, connecting three countries needs three links, connecting four needs six, and a network of five requires ten links. The number of links can be calculated using the formula n(n-1)/2, where n is the number of systems to connect. In the hub-and-spoke model, the number of links is simply equal to n. See Figure 2 for an illustration.
Project Icebreaker use a hub-and-spoke communicator-like model connecting the CBDC test systems of the central banks of Israel, Norway and Sweden, via a central API hub. The API hub acts as a router, so that each system communicates with the hub, and the hub routes the messages to the intended system. The hub has additional functionalities, such as a foreign exchange marketplace (see element 3 and Annex IV). Instead of a central routing hub, Nexus uses standardized gateways. The Nexus Gateway is software that manages communication between IPS to support proxy resolution, foreign exchange quote generation and payment processing between two countries. Each Gateway connects to its local (domestic) IPS infrastructure on one side and to Nexus Gateways in other countries on the other side ( BISIH 2021 ).
In these types of protocols, a coordinator sends a signal to all participants to commit to the transaction by updating its records, or to abort and roll back in the case of failure. See Bank of Canada and Monetary Authority of Singapore (2019) for more details on HTLC and similar protocols.
An autonomous, unhosted, wallet refer to when the end-user holds its credentials directly instead of having a PSP as a host.
These three models are intended to show a minimum set of combination to illustrate separate functions of intermediaries and foreign exchange providers. We could think of adding more intermediaries.
The intermediary can avoid currency risk if, for example, all legs of the payments are processed and settled instantly or on a payment vs. payment basis. See element 5 for more on instant settlement and payment vs payment. The intermediary may be expose to currency risk in the event of being in possession of the funds for an extended period of time.
See Annex III for further details on waterfall accounts and alternative models.
Namely any intermediary that qualifies as a financial institution, designated non-financial business or professional, or a virtual asset service provider, as defined in the FATF Glossary.
In-depth analysis of the financial integrity implications and corruption risks of retail CBDCs will be addressed in a future IMF publication as a part of the CBDC Handbook.
Other restrictions, such as for current payments (for example, payment for trade and services) could conceptually also be applied through “smart” integration via code in a similar way as for CFMs. However, Articles of Agreement of the IMF, Article VIII, Section 2(a), states that a member may not impose restrictions on the making of payments and transfers for current international transactions without the (prior) approval of the IMF.
Lessons from Project Mandala—a proof-of-concept run by BISIH Singapore Centre, the Reserve Bank of Australia, the Bank of Korea, the Central Bank of Malaysia, and the Monetary Authority of Singapore exploring the feasibility of encoding jurisdiction-specific policy and regulatory requirements into a common protocol for cross-border transactions—will also be important as the project advances.
As the legal certainty in the protection of settlement finality could differ across jurisdictions, there could be potential risk for retail cross-border payments if legal uncertainty remained. This also pertains to probabilistic finality in cases where distributed ledger technologies are used ( CPMI-IOSCO 2022 ).
Technical escrow refers here to a risk management tool in transactions that involves computer software to ensure that the funds can be released to the beneficiary if certain predefined conditions materialize. Such functionality is often called smart contracts, which are extensively mentioned in the blockchain discussion. However, it is worth noting that the concept of smart contracts has been introduced much earlier than the emergence of blockchain, and blockchain is not the only technology on which smart contracts can be deployed and executed.
Depending on the design of the oracle, it can be considered a third-party. The oracle can however be purely technical and an integrated part of the system without manual intervention.
See Annex IV for how Project Icebreaker implemented a coordinated PvP case using HTLC. It is also useful to note that the HTLC protocols can present the risk of non-atomicity due to operational events.
See https://www.cbn.gov.ng/Out/2023/TED/TEDFEMPUBFPC001003.pdf .
Investors and Exporters (I&E) window rates are the exchange rates at which investors and exporters can buy and sell foreign currencies at market-determined rates.
See also https://www.bis.org/about/bisih/topics/cbdc/icebreaker.htm for more information about Project Icebreaker.
The secret can be any set of information, for example a number or a phrase, while the hash value of a secret is an encryption of the secret that is easy to compute but it is impossible to compute the secret from the hash value.
Other IMF Content
- A Survey of Research on Retail Central Bank Digital Currency
- Exploring Multilateral Platforms for Cross-Border Payments
- Cross-Border Central Bank Digital Currencies, Bank Runs and Capital Flows Volatility
- Central Bank Digital Currency—Initial Considerations
- A Multi-Currency Exchange and Contracting Platform
- How Should Central Banks Explore Central Bank Digital Currency?
- Central Bank Digital Currencies in the Middle East and Central Asia
- Trust Bridges and Money Flows: A Digital Marketplace to Improve Cross-Border Payments
- IMF and World Bank Approach to Cross-Border Payments Technical Assistance
- Towards Central Bank Digital Currencies in Asia and the Pacific: Results of a Regional Survey
Other Publishers
Asian development bank.
- Central Bank Digital Currencies: A Potential Response to the Financial Inclusion Challenges of the Pacific
- Recent Central Bank Digital Currency Developments in Asia and Their Implications
- The Role of Central Bank Digital Currencies in Financial Inclusion: Asia-Pacific Financial Inclusion Forum 2022
- Local Currency Collateral for Cross-Border Financial Transactions: Policy Recommendations from the Cross-Border Settlement Infrastructure Forum
- Next Steps for ASEAN+3 Central Securities Depository and Real-Time Gross Settlement Linkages: A Progress Report of the Cross-Border Settlement Infrastructure Forum
- Concentration in Asia's Cross-Border Banking: Determinants and Impacts
- The Impact of Nonperforming Loans on Cross-Border Bank Lending: Implications for Emerging Market Economies
- Recent Technological Advances in Financial Market Infrastructure in ASEAN+3: Cross-Border Settlement Infrastructure Forum
- Strengthening Cross-Border Community Collaboration in the CAREC Region
- Cross-Sector Infrastructure Co-deployment: Closing Digital Connectivity Gaps through Collaboration and Sharing
Food and Agriculture Organization
- Crossing boundaries: Legal and policy arrangements for cross-border pastoralism
Inter-American Development Bank
- Digital Central Bank Money and the Unbundling of the Banking Function
- Remittances Payments through Central Banks: An Application to the Central American Countries Exchange Rates
- Impact of Cross-border Road Infrastructure on Trade and Investment in the Greater Mekong Subregion
- Central Bank Liquidity Management and "Unconventional" Monetary Policies
- Structured Finance In Latin America: A Look at Cross-Border Remittance Securitizations
- Risk across Borders: A Study of the Potential of Microinsurance Products to Help Migrants Cope with Cross Border Risks
- Program for Improving Central Bank Reporting and Procedures on Remittances: Barbados
- Cross-Border Mortgages
- Wholesale Payments Systems and Financial Discipline, Efficiency, and Liquidity
- Self-Sovereign Identity: The Future of Identity: Self-Sovereignity, Digital Wallets, and Blockchain
International Labour Organization
- Cross-border social dialogue and agreements: An emerging global industrial relations framework?
The World Bank
- Cross-Border Banking in Emdes: Trends, Scale, and Policy Implications
- The Retail Payment Costs and Savings in Albania
- Competitive implications of cross-border banking
- Digital Payment - A Dream or Reality for Vietnamese in Rural and Remote Areas?: World Bank Social Protection Payments Assessment for Vietnam
- Innovation in Electronic Payment Adoption: The Case of Small Retailers.
- Is the Financial Safety Net a Barrier to Cross-Border Banking?
- Challenges in Group Governance: The Governance of Cross-Border Bank Subsidiaries.
- Expanding bank outreach through retail partnerships: correspondent banking in Brazil
- Globalization and technology absorption in Europe and Central Asia: the role of trade, FDI, and cross-border knowledge flows
- Digitization of Agribusiness Payments in Africa: Building a Ramp for Farmers' Financial Inclusion and Participation in a Digital Economy
Table of Contents
- Front Matter
- Cross-Border Payments with Retail Central Bank Digital Currencies
- View raw image
- Download Powerpoint Slide
International Monetary Fund Copyright © 2010-2021. All Rights Reserved.
- [66.249.64.20|185.66.14.133]
- 185.66.14.133
Character limit 500 /500

COMMENTS
Criminology and Criminal Justice is a peer-reviewed journal that focuses on the broad field of criminology and criminal justice policy and practice. The journal publishes scholarly articles on all areas of criminology, crime and criminal justice. It includes theoretical pieces, as well as empirically-based analyses of policy and practice in areas that range from policing to sentencing ...
The Journal of Criminology is an international peer-reviewed journal in the field of criminology. Originally published under the title of the Australian and New Zealand Journal of Criminology, it expressly seeks to publish innovative theoretical, empirical and policy-oriented research from around the world, as well as maintaining a strong commitment to high quality research in the Australasian ...
Criminology is devoted to the study of crime and deviant behavior. Interdisciplinary in scope, the journal publishes articles that advance the theoretical and research agenda of criminology and criminal justice.
Predictive crime modelling can produce powerful statistical tools, but there are important considerations for researchers to take into account to avoid their findings being misused and doing more ...
Criminology is an interdisciplinary field of study. that focuses on crime and the responses to crime. Introduction. As the study of crime and society 's responses to it, criminology is an ...
The Journal of Research in Crime and Delinquency (JRCD), peer-reviewed and published bi-monthly, offers empirical articles and special issues to keep you up to date on contemporary issues and controversies in the study of crime and criminal-legal system responses.For more than sixty years, the journal has published work engaging a range of theoretical perspectives and methodological approaches ...
Featured articles. The Editor of The British Journal of Criminology selects one paper from each new issue for its high-quality contribution to the field of research.Browse articles which are available to read and download for free. This collection is updated regularly so check back to keep up-to-date with the latest advances in the field.
The contributions in this themed section developed from conversations that took place at an event hosted by the British Society of Criminology and Criminology & Criminal Justice in April 2019. The papers that follow respond to a 'think-piece' presented by Richard Sparks at that event, and engage with the subsequent debate about the future of funding for crime and justice research.
2009. Punishment and Inclusion: Race, Membership, and the Limits of American Liberalism. 2014. Punishment and the History of Political Philosophy: From Classical Republicanism to the Crisis of Modern Criminal Justice. 2016. Punishment in Paradise: Race, Slavery, Human Rights, and a Nineteenth-Century Brazilian Penal Colony.
Criminology. Chester L. Britt, in Encyclopedia of Social Measurement, 2005 Introduction. Criminology is a wide-ranging interdisciplinary field that encompasses the study of crime and the criminal justice system. Criminological research focuses on issues related to the causes and consequences of crime, delinquency, and victimization, as well as the operation of the criminal justice system, with ...
Spans a broad range of disciplines along with criminology including statistics, sociology, geography, political science, economics, and engineering. Publishes original research, brief methodological critiques, and papers exploring new directions for study. Relevant to the criminological community in its broad scope and in-depth analysis.
Theses/Dissertations from 2016. PDF. Disinhibition, Violence Exposure, and Delinquency: A Test of How Self-Control Affects the Impact of Exposure to Violence, Wyatt Brown. PDF. The Guilty But Mentally Ill Verdict: Assessing the Impact of Informing Jurors of Verdict Consequences, Erin Elizabeth Cotrone. PDF.
Introduction: Qualitative Research in Criminology. Michael Meuser & Gabi Löschper. Abstract: This paper begins with a brief overview of research traditions that paved the way for qual-. itative ...
PRIMARY RESEARCH PAPERS. These primary criminology research papers are written by some of the most up and coming criminologists in their fields. It should be noted that although these criminology papers are not anonymously peer reviewed, like those in our articles section of the journal, primary research papers are reviewed and edited by the ...
Taken together the 11 papers reviewed do demonstrate that the implicit and direct impact of crime is very widespread indeed. Keywords: criminality; divided societies; Islam; Introduction. ... Criminology and related social science disciplines rarely examine these broader aspects, yet a moments consideration reveals how much of societal ...
According to the CNKI database, the overall number of Chinese criminology papers in 2021 is estimated to be 2011, which is almost the same as that in 2017 (2441), 2018 (2130), 2019 (2084) and 2020 ...
named Victimology, a department of Criminology. Victimology deductively considers the relationship. between a harmed party and an guilty party by analysing the cau ses and the nature of the ...
Further information. CiteScore is a simple way of measuring the citation impact of sources, such as journals. Calculating the CiteScore is based on the number of citations to documents (articles, reviews, conference papers, book chapters, and data papers) by a journal over four years, divided by the number of the same document types indexed in Scopus and published in those same four years.
Dr. Tamar Berenblum is the research director of the The Federmann Cyber Security Center - Cyber Law Program, Faculty of Law, the Hebrew University of Jerusalem, Israel, and the co-chair of the European Society of Criminology (ESC) Working Group on Cybercrime. Tamar is also a Post-Doc Research Fellow at the Netherlands Institute for the Study of Crime and Law Enforcement (NSCR), Netherlands ...
The qualitative analysis of individual cases has a prominent place in the development of criminological theory, yet progression in the scientific study of crime has largely been viewed as a distinctly quantitative endeavor.
Criminology Research Paper. This sample criminology research paper features: 6300 words (approx. 21 pages), an outline, and a bibliography with 49 sources. Browse other research paper examples for more inspiration. If you need a thorough research paper written according to all the academic standards, you can always turn to our experienced ...
A common reason given by students for studying criminology is because it is thought to be an 'interesting' subject (Walters and Kremser, 2016).While some speculate that students may be influenced by the 'CSI effect', 'just as many are propelled into the field as a result of more altruistic and personal motivations' (Belknap and Potter, 2007: 16) and because they want to 'help ...
criminology students of Agoncillo College Inc. through the structured questionnaire. Sources of data There are two sources of data; the primary sources was taken from the answers to the survey questionnaire of the criminology students of ACI. The secondary source was taken from various reference materials such as books, journal article, station ...
Many central banks are currently exploring the possibility of issuing retail central bank digital currency (CBDC). While the primary objective varies between jurisdictions, many central banks consider improved cross-border payments as a potential benefit and previous work has shown that CBDC can help overcome some of the frictions in cross-border payments. CBDC is a safe and liquid asset ...