

A Brief History of National ID Cards

“ID card adoption is more likely following economic or political shocks”

National ID cards can provoke diverse reactions. In some countries, identity cards are seen as uncontroversial,even boring, documents. In others, the cards can arouse heated controversy. In short, what is striking about national ID cards is how debate over their merits has varied over space and time. In this blog, we trace out this evolution of ID cards worldwide.
One precursor to national ID cards emerged in 19th century France. Napoleon sought to streamline the central government in France after the revolutionary period between 1789 and 1799. As he clarified property rights and created new bureaucratic offices, he also introduced a system of internal ID documents for workers in 1803-1804.
Although the French passcards were intended for workers, the Napoleonic reforms prompted other countries to implement more comprehensive ID systems. Starting in 1839, Sultan Mahmud II, impressed by the success of the Napoleonic reforms for building state capabilities, introduced national ID cards to the Ottoman empire in 1844. Hence, early identity cards were adopted to consolidate state institutions. Yet few countries would adopt national ID cards until the shock of World War II.
Origins of Contemporary ID Systems
World War II initiated the contemporary era of ID cards. In 1938, lawmakers in the United Kingdom passed the National Registry Act, which mandated that all residents possess identity cards. The German government also instituted an ID system that year (although these cards contained information about residents’ religion for discriminatory purposes). In 1940, the Vichy government in France instituted an ID system as well, as in Greece and Poland. These systems largely endure to this day, except in the United Kingdom, where courts repealed mandatory IDs in 1952. Analysts have noted that civil law countries are more likely to maintain ID statutes than common law countries (such as the UK). With only a handful of exceptions, no common law country in the world has accepted a peacetime identification system. [1]
In the decades following WWII, ID card adoption was rapid in Asia, as newly independent governments sought to expand state authority. The Hong Kong government introduced an identity card in 1949 to strengthen its sovereignty and quell immigration from mainland China. Taiwan also introduced ID cards in 1949 for similar reasons, and, in the 1960s, South Korea and Singapore followed suit in the context of economic transformation.
ID systems would continue to expand in the twenty years between 1985 and 2005, revealing several trends:
First, the events of 9/11 renewed debate over ID cards. Despite long-standing opposition to identity cards in the UK, the British government passed the (since repealed) Identity Cards Act in 2006, and the Canadian government considered similar legislation. Although a national ID card system was never pursued in the US, lawmakers passed the REAL ID Act (2005), which created security standards for state identity documents.
Second, European unification intensified the adoption of ID card systems in member states. Indeed, by 2014, most European Union countries were using ID cards, which were intended to facilitate travel and communications in the EU.
Third, ID cards have come to include increasingly sophisticated biometrics, which enhance the security of ID systems. In 1999 South Africa introduced electronic ID cards. In the 2000s, Indonesia and others launched ID systems containing iris and fingerprint information.
Overall, ID card policy depends on each country’s institutional specificities, but some trends are common across countries. National ID systems are often implemented in times of heightened security risk. Governments also tend to implement ID systems to consolidate state institutions or during periods of economic transformation. In sum, ID card adoption is more likely following economic or political shocks, which give governments the incentive and legitimacy to create identity systems.
[1] Whitley, E. A., & Hosein, G. (2009). Global challenges for identity policies . Palgrave Macmillan.
This blog is part of a series we will be publishing in the lead up to an international conference on November 19-21. The conference is free and open to the public. For details visit the conference website.
Philippine e-Legal Forum
Philippine laws and legal system (pnl-law blog).

Cases on the National Identification (ID) System
The recent talks on reviving the plan to implement a national identification (ID) system brings two cases back into the spotlight. In the first case, Ople vs. Torres , the Supreme Court struck down Administrative Order 308 which seeks to implement the “National Computerized Identification Reference System.†In the second case, Kilusang Mayo Uno vs. Director-General of NEDA , the SC upheld the validity of Executive Order 420 which adopts a unified multi-purpose ID system for government agencies. Let’s discuss each case, in the hope of giving our readers a brief overview how the new proposals are different from these cases.
Ople vs. Torres (G.R. No. 127685, 23 July 1998, penned by Chief Justice Reynaldo Puno)
In 1996, President Fidel Ramos issued Administrative Order No. 308, entitled “Adoption of a National Computerized Identification Reference System,” the pertinent portions of which reads:
ADOPTION OF A NATIONAL COMPUTERIZED IDENTIFICATION REFERENCE SYSTEM WHEREAS, there is a need to provide Filipino citizens and foreign residents with the facility to conveniently transact business with basic service and social security providers and other government instrumentalities; WHEREAS, this will require a computerized system to properly and efficiently identify persons seeking basic services on social security and reduce, if not totally eradicate, fraudulent transactions and misrepresentations; WHEREAS, a concerted and collaborative effort among the various basic services and social security providing agencies and other government instrumentalities is required to achieve such a system; NOW, THEREFORE, I, FIDEL V. RAMOS, President of the Republic of the Philippines, by virtue of the powers vested in me by law, do hereby direct the following: SECTION 1. Establishment of a National Computerized Identification Reference System. A decentralized Identification Reference System among the key basic services and social security providers is hereby established. xxx SEC. 4. Linkage Among Agencies. The Population Reference Number (PRN) generated by the NSO shall serve as the common reference number to establish a linkage among concerned agencies. The IACC Secretariat shall coordinate with the different Social Security and Services Agencies to establish the standards in the use of Biometrics Technology and in computer application designs of their respective systems.
A.O. 308 involves a subject that is not appropriate to be covered by an administrative order and usurps the power of Congress to legislate
Congress is vested with the power to enact laws, while the President executes the laws. The President’s administrative power is concerned with the work of applying policies and enforcing orders as determined by proper governmental organs. An “administrative order” refers to “[a]cts of the President which relate to particular aspects of governmental operation in pursuance of his duties as administrative head shall be promulgated in administrative orders.” An administrative order is an ordinance issued by the President which relates to specific aspects in the administrative operation of government. It must be in harmony with the law and should be for the sole purpose of implementing the law and carrying out the legislative policy.
A.O. No. 308 establishes for the first time a National Computerized Identification Reference System. It does not simply implement the Administrative Code of 1987. This administrative order redefines the parameters of some basic rights of the citizenry vis-a-vis the State, as well as the line that separates the administrative power of the President to make rules and the legislative power of Congress. It deals with a subject that should be covered by law.
A.O. violates the right to privacy
In striking down A.O. 308, the SC emphasized that the Court is not per se against the use of computers to accumulate, store, process, retrieve and transmit data to improve our bureaucracy. The SC also emphasized that the right to privacy does not bar all incursions into the right to individual privacy. This right merely requires that the law be narrowly focused and a compelling interest justify such intrusions. Intrusions into the right must be accompanied by proper safeguards and well-defined standards to prevent unconstitutional invasions.
The right to privacy is a constitutional right, granted recognition independently of its identification with liberty. It is recognized and enshrined in several provisions of our Constitution, specifically in Sections 1, 2, 3 (1), 6, 8 and 17 of the Bill of Rights . Zones of privacy are also recognized and protected in our laws, including certain provisions of the Civil Code and the Revised Penal Code, as well as in special laws (e.g., Anti-Wiretapping Law, the Secrecy of Bank Deposit Act and the Intellectual Property Code).
The right to privacy is a fundamental right guaranteed by the Constitution. Thefore, it is the burden of government to show that A.O. 308 is justified by some compelling state interest and that it is narrowly drawn. The government failed to discharge this burden.
A.O. 308 is predicated on two considerations: (1) the need to provide our citizens and foreigners with the facility to conveniently transact business with basic service and social security providers and other government instrumentalities and (2) the need to reduce, if not totally eradicate, fraudulent transactions and misrepresentations by persons seeking basic services. While it is debatable whether these interests are compelling enough to warrant the issuance of A.O. 308, it is not arguable that the broadness, the vagueness, the overbreadth of A.O. 308, if implemented, will put our people’s right to privacy in clear and present danger.
The heart of A.O. 308 lies in its Section 4 which provides for a Population Reference Number (PRN) as a “common reference number to establish a linkage among concerned agencies” through the use of “Biometrics Technology” and “computer application designs.” Biometry or biometrics is “the science of the application of statistical methods to biological facts; a mathematical analysis of biological data.” The methods or forms of biological encoding include finger-scanning and retinal scanning, as well as the method known as the “artificial nose” and the thermogram. A.O. 308 does not state what specific biological characteristics and what particular biometrics technology shall be used.
Moreover, A.O. 308 does not state whether encoding of data is limited to biological information alone for identification purposes. The Solicitor General’s claim that the adoption of the Identification Reference System will contribute to the “generation of population data for development planning” is an admission that the PRN will not be used solely for identification but for the generation of other data with remote relation to the avowed purposes of A.O. 308. The computer linkage gives other government agencies access to the information, but there are no controls to guard against leakage of information. When the access code of the control programs of the particular computer system is broken, an intruder, without fear of sanction or penalty, can make use of the data for whatever purpose, or worse, manipulate the data stored within the system.
A.O. 308 falls short of assuring that personal information which will be gathered about our people will only be processed for unequivocally specified purposes. The lack of proper safeguards in this regard of A.O. 308 may interfere with the individual’s liberty of abode and travel by enabling authorities to track down his movement; it may also enable unscrupulous persons to access confidential information and circumvent the right against self-incrimination; it may pave the way for “fishing expeditions” by government authorities and evade the right against unreasonable searches and seizures. The possibilities of abuse and misuse of the PRN, biometrics and computer technology are accentuated when we consider that the individual lacks control over what can be read or placed on his ID, much less verify the correctness of the data encoded. They threaten the very abuses that the Bill of Rights seeks to prevent.
- Recent Posts

- Twin-Notice Rule and Procedural Requirements in Employment Termination Proceedings - June 3, 2020
- When Travel Pass is Needed for Interzonal Travel during Community Quarantine - June 1, 2020
- Can Companies Compel Employees to Work during the General Community Quarantine (GCQ) and Impose Disciplinary Sanctions - May 29, 2020
- Special Court could Oversee Anti-Terror Law
- Primer on Separation of Powers, Inquiry in Aid of Legislation
- Constitutional Commissions (Article IX, Philippine Constitution): Full Text
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
This site uses Akismet to reduce spam. Learn how your comment data is processed .
AttyAtWork * VisitPinas * ChatTimeWithJulia RSS Entries and RSS Comments
Sign up to Newsletter
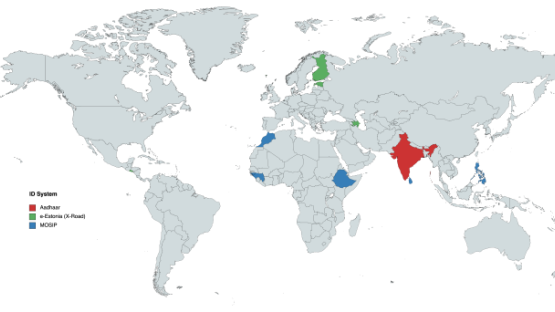
Digital National ID systems: Ways, shapes and forms
PI has put together an analysis of some of the most used Foundational ID systems worldwide.
Governments around the world are increasingly making registration in national digital ID systems mandatory for populations, justifying its need on a range of issues from facilitating access to services , to national security and fighting against corruption. This is an attempt to create a "foundational identity" for an individual, or "a single source of truth" about who someone is, according to a government agency. These identity systems are run by governments, sometimes by private companies, or by a combination of both.
ID systems are the gatekeepers to access an increasingly-wide range of goods and services, resulting in potential limitation of the exercise of a range of human rights. The ID system designer or manager not only has control over what people have access to, but may also make the use of the system mandatory.
While governments and other proponents of ID systems highlight their potential benefits, little attention and public debate has focused on the potential harm that come from the implementation of such systems, notably:
Exclusion - People can be excluded from accessing some public services as the result of not having an ID, because of discriminatory application, technical or logistical barriers or enrollment and verification not being possible. Sometimes the capture of biometric identifiers such as fingerprints is made mandatory to enroll in these systems, despite not everyone having "readable" fingerprints. We have seen governments going forward with such measures despite expecting up to 15% failure rates in fingerprint authentication due to a large chunk of the population being dependent on manual labour , which abrases people's hands and fingertips. Similarly, exclusion is likely to happen if someone ends up with an ID that they are not able to make use of (e.g. if gender markers assigned on ID is different from their self-identified gender )
Exploitation - People's data can be exploited through their use and processing within identity schemes. This is particularly the case when 'Unique identifier' is introduced. A 'unique identifier' is a unique number or code, for example an ID number, through which government and the private sector are able to connect together various data sets. The prevalence of this unique identifier across multiple government or private sector databases, implies the risk of providing a “360 degree view” of an individual. On top of this, it raises concerns of further data processing for purposes beyond initial legitimate purpose .
Surveillance - ID systems can be used as tools of surveillance within a broader surveillance infrastructure, often leading to disproportionate and unnecessary interference with our privacy and enabling violations of other human rights. Since 9/11, governments have sought to justify the imposition of ID systems, the indiscriminate tracing and tracking of individuals within countries and across borders in the name of national security.
These harms can occur at multiple points along the identity system - from the issuing of a document or credential and the information required to do so, through to how the data is stored and processed, down to the time when someone is requested or required to show their credentials for verification. Understanding this fact should lead governments to be cautious about new technological approaches for identification.
When despite these concerns, governments decide to go forward in implementing foundational ID systems, they are still left with the big question of how to technically and in practice roll out such systems. National ID schemes can take various forms: some have smartcards, some don't; some rely on biometrics, some don't; some are linked to citizenship, some aren't. Some link to birth registration, some don't. Some link to voter rolls, some don't. Some give everyone a unique number, some don't. Some have advanced security features, some are left for the deploying end to laminate.
Most used Foundational ID systems worldwide: an analysis
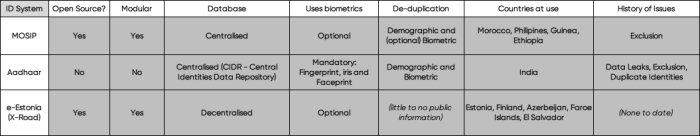
With this in mind, PI has put together this analysis of some of the most used Foundational ID systems worldwide. This analysis is based on publicly available information, collated into this one article for the purpose of making it easier for our readers to compare the characteristics of the commonly used identity systems. This is a developing piece and more systems will be added over time. A summary of our findings can be found on the table below. At the time of writing, the findings in this piece are based on our analysis of MOSIP, Adhaar and e-Estonia:

ID systems analysed: MOSIP
Id systems analysed: aadhaar, id systems analysed: e-estonia.

ID systems analysed: DNIe in Peru
What our analysis includes.
For each individual analysis we explore and present:
An overview of the ID system
This includes information about where and when it was developed and by whom. We also include a list of advocates, representatives and funders for each particular system, so decision-makers can have an idea of who the particular solution is being pushed by.
In this overview we also provide information about whether the system is open source or a proprietary . Open source systems are characterised by an underlying code that is made publicly available. This means anyone can inspect, modify and distribute the code, meaning it's developed in a decentralised way, relying on peer reviews and community production. It is important that government founded software is made open source and having an open source approach to the development of an ID system has several advantages:
- increased transparency as anyone can see how implementation is done in practice, the project becomes open to a large community of developers,
- testers and other contributors who can constantly provide feedback, contribute actively with new features, or fix bugs,
- on top of this open source solutions are often cheaper,
- more flexible and
- offer more longevity that proprietary alternatives because they are developed by communities rather than a single author or company.
Some might argue that making a codebase open source is a source of risk as motivated enough malicious attackers can take their time to look for vulnerabilities or ways to exploit the code. In reality, keeping the code away from the eyes of the public will not stop this either way, instead missing out on public scrutiny and community development.
From the foundational ID systems currently analysed two out of the three rely on open source software:
- MOSIP is fully open-source and all its code is publicly available .
- e-Estonia services rely on X-Road - an open source data exchange layer. On top of this, earlier this year the Estonian government decided to make all government software publicly available in this repository .
- Aadhaar relies on proprietary technology that belongs neither to the Indian government nor the UIDAI (Unique Identification Authority of India) which makes the system a "black box" in the sense that one cannot know of how operations are de facto being handled.
Insights into the infrastructure makeup
Authentication attributes and personal data need to be appropriately safeguarded. Encryption is the process through which data is encoded so that it remains inaccessible to unauthorised users. On top of storing and dealing with people's personal information such as name and date of birth, several foundational ID systems systems across the world increasingly rely on biometric data, which data protection frameworks largely recognise as sensitive, and therefore a special category of personal data.
The use of such sensitive and uniquely identifying personal data should mandate that the tightest security safeguards are in place. Encryption is crucial to keeping data safe from unwanted third parties and to provide users with a reliable authentication process, providing veracity when determining if an entity - user, server, or client app - is who it claims to be.
In any modern software the use of strong encryption should be assumed, and as such we will generally not discuss implementations unless we cannot find any information, or what is being used is wildly and obviously dangerous (such as using encryption protocols which are obsolete or no use of encryption at all).
Is user data stored in a centralised or decentralised way?
Electronic databases are the preferred option to store, reference, validate and authenticate identity data. These databases can exist as a central repository or as distributed systems depending on the country and the implemented solution.
Physical V Logical (de)centralisation
(De)centralisation can take two forms; distributing the database across several geographically dispersed physical computers (either through a process known as "sharding", where different parts of the database are held in different places, or with identically replicated databases spread over several computers), or through holding logically separate data in separate (preferably geographically dispersed) databases which use some form of API (Application Programming Interface) to interact with each other.
Whilst logical decentralisation is a design decision, physical decentralisation should be expected in any at-scale system to reduce (and attempt to eliminate) single points of failure, as well as potentially speeding up access by "moving" the database being interacted with physically closer to the user.
Insights into how de-duplication is handled
Identity de-duplication is a procedure used to attempt to 1:1 match a natural person to a unique "identity" within a system -- the ultimate goal being no cases where one person has two "identities", or where one "identity" is shared by more than one person.
Some systems may attempt de-duplication based purely on demographic data, while others will attempt to compare against biometric identifiers already stored by the database.
False Positives
In the particular case of Aadhaar for example, the UIDAI published a report with a proof of concept on biometric de-duplication. In this report, the UIDAI states that the occasional false positive is expected due to reasons such as:
- faulty biometric collection equipment.
- human error in assigning biometrics to the correct "unique" profile.
- one person enrols twice with a different name.
- two people may happen to have the same biometrics.
This proof of concept is based on a sample of 40,000 people where the UIDAI (Unique Identification Authority of India) is aiming for a false positive identification rate of 0.0025%, meaning 2.5 false positives for every 100,000 comparisons. In this context a false positive means a biometric system incorrectly matches an individual to someone else’s biometric identifiers. This may not seem like a lot but when scaling up the sample size to India's population of 1,380,000,000 it adds up to each person having over 17,000 false positives to resolve when using their biometrics for identification purposes.
In practice this means that solely based on biometrics an individual cannot prove to be one of 1,380,000,000 citizens. Rather they can only prove that they are one of the 17,000 people with that one biometric identifier, within the whole population. This shows that in reality we are dealing with a lot more than occasional false positives when doing biometric deduplication and that it is impossible to claim that all the IDs in UIDAI's CIDR (Central Identities Data Repository) are biometrically unique. You can find a breakdown of the simple maths used to get to these numbers on our research into Aadhaar.
Principles of engagement for each system
The technological choices in the design and deployment of digital ID systems can express a variety of political motives, which impact how societies operate at the deepest level. The design, deployment and governance of large socio-technical systems can establish a different public order and power entrenchment among social and political groups.
With this in mind, besides presenting information on the technical infrastructure makeup of each ID system, we will also delve into the engagement principles or governing principles published by developers, when existent. Such guidelines on external conditions and safeguards present what developers believe should be in place so that the risk of abuse and exploitation in the use of their tool is minimised.
Countries where the particular ID system is deployed or where there's evidence it will be deployed in the future
- India (2009)
- Morocco (2018)
- Philipines (2019)
- Guinea (2021)
- Ethiopia (2020)
- Sri Lanka (to sign soon)
e-Estonia (X-Road):
- Estonia (2001)
- Finland (2017)
- Azerbeijan (2018)
- Faroe Islands (2016)
- El Salvador (2017)
Reported examples of abuse in countries where the researched ID system is in use
In our research PI found reported example of abuses in all systems we analysed, despite the fact that some of them proclaim to be 'safe', 'inclusive' and 'privacy friendly'.
For instance, Aadhaar in India has had countless reports of abuse over the years including massive data leaks, exclusion from access to benefits and even issues around de-duplication. This list by itself contains almost 40 isolated cases of breaches between February 2017 and May 2018. The data leaked are not limited to Aadhaar numbers and demographic information. In some of the cases sensitive data such as data on pregnancy , people's religion and caste and even bank details were leaked alongside Aadhaar numbers. The Indian government has also made enrolment in Aadhaar a mandatory requirement to access a myriad of social protection schemes. This measure creates thick barriers in accessibility for a lot of people and has led to cuts in accessing food rations which has been linked to several deaths by starvation across the country. On top of this, the Indian government and the Unique Identification Authority of India (UIDAI), have ignored privacy concerns as well as sample test results of its pilot project that showed that there could be up to 17,000 false positives each time an Indian citizen engages in an identification process. This systematic fail has led to cases where one person somehow ends up getting two different "unique" Aadhaar numbers .
MOSIP is being deployed in Morocco and there have been concerns regarding exclusion through language. Morocco’s General Directorate of National Security announced a new generation of identity cards in 2020, but according to a draft law the card would only be in Arabic - one of the two official languages of the country - and French - a foreign non-constitutional language, leaving Tamazight - the second official language - out. This goes directly against regulations aimed at gradually including Tamazight in Morocco’s public life and encouraging the usage of Tamazight, alongside Arabic, in administrative documents, including national identity cards.
Regarding countries where e-Estonia or X-Road based ID systems have been implemented there haven't been any similar reports of abuse to this day.
Methodology
The information presented about each of the systems was all collected from publicly available sources. As stated above, some of the analysed systems will be open-source meaning they have increased levels of transparency, including public access to the source code being used. This allows for anyone to confirm any technological statements made about the said system, which we must stress is an invaluable feature . On the opposite end, there are "black box" systems for which our research was based on documentation made publicly available by the ID system designer or owner. In these cases it becomes impossible for the public to verify that the system behaves as described in the documentation, and hence the public's knowledge is trust-based and limited to whatever information is picked as fit for public consumption.
Identities under our control
Related content.

PI joins civil society in concerns over Mexico’s World Bank funded digital ID scheme
Mexico's proposed new CUID biometric ID card, funded by the a $225 million loan from the World Bank, has been criticised by civil society organisations.

Afghanistan: What Now After Two Decades of Building Data-Intensive Systems?
Over the last 20 years, vast data-intensive systems were deployed in Afghanistan by national and foreign actors. As we highlight some of these systems we present our concerns as to what will happen to them.

Covid-19 vaccination certificates: WHO sets minimum demands, governments must do even better
We analysed the WHO's guidance on "Digital Documentation of COVID-19 Certificates: Vaccination Status" (DDCC:VS). Here is our take on it and what we will keep an eye out for as countries deploy their own digital Covid-19 vaccination certificates.

IPANDETEC publish a report on the development of digital identities in Central America
ID4D Practitioner's Guide
- Full Document
- Visit Self-paced Guide

Principles on Identification for Sustainable Development (Second Edition)
- French (2021)
- Portuguese (2021)
- Spanish (2021)
- Visit Webpage

ID4D Global Dataset 2021: Volume 3 - Trends in Identification for Development

- ID4D Global Dataset 2021 : Volume 2 - Digital Identification Progress & Gaps

ID4D Global Dataset 2021: Volumne 1 - ID Coverage Estimates Report

ID Diagnostic - Lebanon

Lebanon Digital ID Use Cases

Closing the Gender Gap in ID Ownership in Ethiopia: Findings and Recommendations

- ID4D : Diagnostic of ID Systems in Cameroon

ID4D Diagnostic in Sao Tome e Principe

- ID4D Federated Ecosystems for Digital ID (English)

A Digital Stack for Transforming Service Delivery : ID, Payments, and Data Sharing

National Digital Identity and Government Data Sharing in Singapore : A Case Study of Singpass and APEX

Engaging Civil Society Organizations for Successful ID Systems: Guidance Note

Digital ID Systems as an Enabler of Effective Covid-19 Vaccination (English)

ID and COVID-19 : Overview of Country Examples in Safety Protocols and Practices

Strategic Communications for Identification Systems : Guidance Note (English)
Using Biometrics to Deliver Cash Payments to Women : Early Results From an Impact Evaluation in Pakistan - Evidence Note

Global ID Coverage, Barriers, and Use by the Numbers: An In-Depth Look at the 2017 ID4D-Findex Survey

ID Systems and SOGI Inclusive Design

Barriers to the Inclusion of Women and Marginalized Groups in Nigeria’s ID System : Findings and Solutions from an In-Depth Qualitative Study

Understanding the Gender Gap in ID : Key Research Findings and Policy Lessons from Nigeria - Evidence Note (English)

ID Enrollment Strategies: Practical Lessons From Around The Globe

People’s Perspectives on ID and Civil Registration in Rwanda : Research Report

Creating Disability Inclusive ID Systems

Privacy by Design: Current Practices in Estonia, India and Austria
- View Webinar

Open Source for Global Public Goods

Understanding Cost Drivers of Identification Systems
- Cost Model Tool
- Guidance Note

Digital ID and the Data Protection Challenge: Practitioner's Note

Identity Authentication and Verification Fees: Overview of Current Practices

Understanding People's Perspectives on Identification: A Qualitative Research Toolkit

G20 Digital Identity Onboarding

The Role of Digital Identification in Agriculture: Emerging Applications

The Role of Digital Identification for Healthcare: The Emerging Use Cases

Identification in the Context of Forced Displacement

The Role of Identification in Ending Child Marriage: Identification for Development

Incentives for Improving Birth Registration Coverage: A Review of the Literature

Private Sector Economic Impacts from Identification Systems

Public Sector Savings and Revenue from Identification Systems

Technology Landscape for Digital Identification

Argentina ID Case Study: The Evolution of Identification

Moldova Mobile ID Case Study

South Africa ID Case Study

Study of Options for Mutual Recognition of National IDs in the East African Community

The State of Identification Systems in Africa: A Synthesis of Country Assessments

The State of Identification Systems in Africa: Country Briefs

Identification for Development: Africa Business Plan

Digital Identity: Public and Private Sector Cooperation

ID Enabling Environment Assessment (IDEEA)

Guidelines for ID4D Diagnostics
- Country Diagnostics

The Catalog of Technical Standards for Digital Identification Systems

Achieving Universal Access to ID: Gender-based Legal Barriers Against Women and Good Practice Reforms
To read this content please select one of the options below:
Please note you do not have access to teaching notes, risking identity: a case study of jamaica’s short-lived national id system.
Journal of Information, Communication and Ethics in Society
ISSN : 1477-996X
Article publication date: 2 July 2020
Issue publication date: 4 August 2020
This paper aims to expose the challenges facing the attempt by Jamaica to introduce a new digital ID system without adequate regard to public consultation and the rights of citizens.
Design/methodology/approach
The method used is critical text analysis and policy analysis, providing background and relevant factors leading up to the legislative changes under review. Extensive literature sources were consulted and the relevant sections of the Jamaican constitution referenced and analysed.
The case study may have national peculiarities not applicable in other jurisdictions. Its introduction acknowledges that the Jamaican Government may amend and re-submit the legislation, absent the flawed clauses. The paper however will remain valid given its detailed analysis and exposure of risks associated with biometric data collection, face recognition technology and data storage flaws.
Practical implications
It will be a practical example of the risks associated with flawed biometric data collection and the role of Courts in reviewing such legislation. Referrals to the Courts can be used as a remedy, as occurred not only in Jamaica but also in many other jurisdictions, including India and Kenya.
Social implications
The paper foregrounds the rights of citizens to be consulted on the collection and storage of their sensitive biometric data. The social implications and risks of violating the constitutional rights of citizens were made evident, and can be an example to other jurisdictions.
Originality/value
The paper is the first of its kind to provide detailed data and analysis on an outright rejection by the Courts of a country's ID legislation on grounds that it violated the constitution and rights of citizens. It shows the ethical and social challenges in proposing and implementing legislation without adequate public consultation on such sensitive matters as biometric data. It also exposes some of the challenges of artificial intelligence and face recognition technologies in ID data collection, including flaws related to race, gender and coding.
- AI and face recognition
- Biometric ID systems
- Citizen rights and digital data
- Ethics and ID data collection
- Jamaica Supreme Court NIDS rejection
- NIDS Jamaica
Dunn, H.S. (2020), "Risking identity: a case study of Jamaica’s short-lived national ID system", Journal of Information, Communication and Ethics in Society , Vol. 18 No. 3, pp. 329-338. https://doi.org/10.1108/JICES-04-2020-0040
Emerald Publishing Limited
Copyright © 2020, Emerald Publishing Limited
Related articles
We’re listening — tell us what you think, something didn’t work….
Report bugs here
All feedback is valuable
Please share your general feedback
Join us on our journey
Platform update page.
Visit emeraldpublishing.com/platformupdate to discover the latest news and updates

Questions & More Information
Answers to the most commonly asked questions here

Laura Camplisson has led on the Future Identity portfolio of content and events since the brand’s launch in 2021. Laura regularly contributes to articles, reports and blogs exploring the latest initiatives, technologies and concepts in the identity space. She is particularly excited about the potential for digital identity to enable greater inclusion and make everyday life more seamless.
View all posts
The state of digital identity in North America
- By Laura Camplisson
North America’s digital identity landscape
Identity systems across North America have not evolved for a digital world. Most online services still rely on physical documents such as passports and drivers licences – used by 80% of American adults – as a root of trust. Verifying that a credential is genuine and belongs to the individual you are interacting with is much more challenging when an interaction does not take place face-to-face.
And for individuals without any form of government issued ID – 11% of the population, and as many as 25% of minority populations – proving who you are to establish a digital identity, is almost impossible. Physical documents also display far more personal data than is necessary for most transactions. With data breaches on the rise, systems to better protect privacy are urgently needed.
Knowledge-based authentication methods such as social security or national ID numbers are also still widely used, despite their known vulnerability and extensive misuse. As more and more of our lives and interactions move online, identity systems across North America need to improve.
A national digital identity crisis
In 2020 the pandemic swept across North America, and millions went online to apply for unemployment, food, housing, and other public benefits. The need for digital identity became more apparent than ever, as many experienced difficulties verifying their identity and faced delays or were denied payments. Yet criminals successfully defrauded these same government programs of billions of dollars.
After the US CARES act was passed, $36 billion was lost to fraudulent claims. In Canada, reports of identity fraud skyrocketed 54% in 2020 , and one in three people experienced a benefit related phishing attempt. And in Mexico, a country facing one of the world’s worst COVID fatality tolls, there were widespread report s of online scammers extracting money for fake tests, prescriptions and even vaccine doses.
Legacy solutions simply cannot keep pace with the sophisticated techniques used by today’s cybercriminals. Digital identity is no longer just a nice-to-have for convenience. It has become a necessity for national security and citizen autonomy.
A fragmented landscape
Efforts to introduce a government-backed digital identity have not yet been successful, in either Canada, Mexico or the United States. A range of digital ID initiatives based on public-private partnerships have sprung up, but rules and requirements vary immensely between different federal, state, provincial, and local entities within the region.
From financial services, to travel, to healthcare, there are some extremely advanced digital identity initiatives underway within the region. New technologies such as big data and analytics, mobile, cloud computing and biometrics are changing the way citizens identify themselves online.
But some solutions provide stronger security than others, and interoperability between systems is limited. A lack of coordinated public infrastructure, entrenched private interests, and disparate legislation keep data held in siloes and limit consumer choice. Digital identity is not viewed as a necessity and as a result there are those who are left behind.
Collaboration between public and private sector stakeholders could help to spur the necessary standards and privacy protections to support innovation. Open access to information across verification and authentication systems will be critical to enabling more coordinated progress.
Time to make digital identity a reality
As consumers become accustomed to a world of instant and boundless connection, expectations are set which extend to products and services across all areas of life. Organisations everywhere are adapting their products and services for an increasingly digital world.
The reality is that handing over personally identifiable information online has become a requirement for accessing most products and services. Reports show that 8 in 10 Americans now feel they have little to no control over how their data is collected by the government or private companies.
The more data points exist about the average user online, the greater the need to ensure personal information is only shared and used with the direction and consent of consumers. As digital transformation accelerates so does the need for an identity framework centred around privacy. Digital identity today should be a national priority, to enable growth, inclusion, and trust in a changing world.
_________________________________________________________________________________
The conversation continues at Future Identity North America , May 12th 2022

- Future Identity Customer Europe 2024
- Future Identity Finance North America 2024
- Future Identity Festival 2024
- FID Fraud & FinCrime 2024
- Future Identity Customer North America 2024
- Future Identity Finance Europe 2025
- Join the community
- Digital reports
- On-demand sessions
- VC INNOVATIONS – Accelerated Marketing
Publication: South Africa ID Case Study
Original bundle.
License bundle
Collections.
Search form
Identity documents & solutions.
Trusted identity is a vital component of a well-functioning society.
That's why improving security, slashing ID fraud and identity theft, and creating an infrastructure of trust for new online access are high on every government's agenda, with a call for greater security features and the necessary legislation to implement them.
Many advanced countries are now demonstrating that, beyond the security benefits for both states and individuals, national ID cards with their derived digital IDs can provide citizens and businesses with real services and benefits without infringing upon new rules on data protection and civil liberties.
Secure national ID cards.

Many countries are now upgrading their national documents and rolling out government-issued IDs in the form of credit cards.
These new ID documents include high -security printing features to deter fraud.
Polycarbonate as a material of choice
Polycarbonate is an increasingly popular choice for many ID programs worldwide, as it significantly enhances the level of ID document security.
We explain in detail what sets polycarbonate apart from other materials and why its layered structure is also ideally suited to deploying security features in our web dossier.
A digital identity for each citizen
These N a tional ID programs are also the opportunity to create a secure digital identity for each cardholder.
These secure electronic identity cards, called eID cards or simply eIDs, open the gate to secure and trusted online services.
The most common applications for these smart cards are smart to travel documents, electronic IDs, electronic signatures, municipal cards, key cards used to access secure areas or business infrastructures, social security cards, etc.
As the leading provider of secure, tailor-made ID solutions, Thales can help governments improve security and deploy electronic applications to offer better public services and cut administration costs.
Our expertise in numerous government ids worldwide can also help accelerate the dynamics of your national digital framework of trust.
Thales Gemalto's eID card solutions increase citizen protection, contribute to better control of immigration, and offer an effective means of ID checking, such as biometric authentication , using security that is always one step ahead.
Thales offers a variety of secure eID cards with a range of professional solutions for a complete solution, including ID verification software and smart ID scanners , which can be delivered as individual systems or using a managed service option.

Welcoming the Wallet
What the new European Digital Identity Framework means for citizens, governments and businesses
ID cards and eID initiatives: a wealth of best practices to share
Thales is contributing to 40 national eID programs:
- in Europe ( Belgium , Czech Republic , Italy, Finland, Norway , Sweden , Portugal , Luxembourg),
- in the Middle East ( Jordan , Kuwait Civil ID , Qatar , Oman , Bahrain , and Saudi Arabia ),
- in Africa ( Algeria , Cameroon , South Africa ),
- in Asia and Latin America, with Mongolia , Uruguay and Jamaica to name a few.
The military CAC card used by the United States Department of Defense personnel is an exciting example of a large deployment of an identification card with a robust online authentication mechanism.
National ID card and electronic ID: Benefits and trends
T he idea of a National ID card valid for physical and digital domains has become a reality for millions.
In some countries, citizens of public and private organizations are starting to reap benefits .
We investigated in our recent report what are these so-called digital dividends .
The past ten years have been filled with incremental tech developments serving as a foundation for a much smarter citizen ID future.
Want to know more about trends?
Our web dossier on ID facts and trendsdetail five major national ID trends you may want to discover.
Understand why biometrics is intimately linked with identity. See how countries are implementing biometric authentication and creating a state-of-the-art ID program.
Residence Permits
Thales Gemalto eResidence Permit offers the most complete, versatile electronic European Residence Permit (eERP) solution tailored to customer needs.
The eResidence Permit enables governments to realize significant cost savings and reduce fraud and illegal immigration.
Thales has supplied its Residence Permit solutions to numerous countries, including the first generation of chipless products and now the second generation of smart card-based solutions.

Position paper: Improving security for the EU eResidence Permit
Discover our recommendations for enhancing eRP security
Multi-application national ID cards
Thales Gemalto MultiApp ID is a Global Platform smart card solution for eID, eDriving License, eRegistration Certificate, and eHealthcare.
It is a Public Key Java Card designed to meet the most advanced security requirements of long-term multi-application programs such as the ones launched by governments and health insurance initiatives.
MultiApp ID supports RSA up to 4096 bits and Elliptic Curves up to 521 bits in particular and has been Common Criteria EAL 5+ certified .
Thales Gemalto MultiApp is the leading secure, open, and standard-compliant operating platform for electronic document issuance. It supports many identity applications that deploy a raft of citizen-centric government programs.
An innovative turnkey solution to federate eID programs
With contributions to more than 100 eGovernment programs to date, Thales has played a front-line role in making the new paradigm of secure multi-service electronic ID cards a reality.
Drawing on its extensive experience, the company has devised an innovative turnkey solution to federate eID programs across multiple government agencies, bringing together the best of smart card technology, software solutions, and multi-service apps.
Mobilize our financial and PPP experts.
Secure and robust identity management systems are becoming increasingly technically complex and involve significant investments .
The good news?
Many convincing business models can be built around Identity Management projects, and Public-Private Partnership (PPP) is an effective instrument for the delivery of services.
Thales' experience in Public-Private Partnership financing models - such as BOO or BOT - also translates into a significant reduction in your Total Cost of Ownership.
And it works.

Trusted Digital Identity for Everyone Everything Everyday

The identity card program in Belgium
The keystone of e-Government

Swedish ePassport and eID programs
A Gemalto contribution to the efficiency of Swedish Public Services

Republic of South Africa’s Smart ID Program
Meeting the vision of the Department of Home Affairs and the security needs of the country
Related whitepapers

Legal Identity Statement Paper 2023
Thales is committed to the evolution of Digital Identity Systems based on the notion of Unique Legal Identity also known as Foundational Identity. With this statement paper, we wish to share our vision, raise awareness among governments and support them in transition to digitalisation of their identity and economy.

Webinar ABI Research /Thales - Mobile ID in the 21st Century
Demand for government-issued mobile identities continues to accelerate at a considerable pace. A focus on service enablement and access via digitization is now considered of fundamental market importance as governments aggressively look toward the mobile form factor in order to execute on their digitisation strategies. With the tipping point within the mobile identities market now fast approaching, it’s critical that ecosystem players, governments, and service providers alike understand what lies ahead.

National ID cards: 2016-2021 facts and trends 5 reasons for Electronic National ID Cards eIDAS 2 regulation National register Professional services Voter authentication Identity Management System
Digital Identity Services > Trends > Mobile ID > Digital ID Wallet > Mobile Software Security > Self-service kiosks
Citizen enrollment and voter registration > Biometric voter registration Secure document issuance solutions > Document management system Mobile eVerification > Biometric tablet Professional services Voter authentication
Case studies Get Inspired Documents on Document readers Digital Identity & Security articles
Get in touch with us
For more information regarding our services and solutions contact one of our sales representatives. We have agents worldwide that are available to help with your digital security needs. Fill out our contact form and one of our representatives will be in touch to discuss how we can assist you.
Please note we do not sell any products nor offer support directly to end users. If you have questions regarding one of our products provided by e.g. your bank or government, then please contact them for advice first.

Singapore revolutionises national ID
Password-less future become everyday reality.
- Call for Change
- When Tech Meets Human Ingenuity
- A Valuable Difference
- Related Capabilities
Call for change
Singapore is known for punching above its weight in the global economy – a bustling financial hub that consistently ranks high in measures of economic productivity, public services and living standards.
Its success credits to the country's digital transformation efforts pursued for years. And a holistic "Smart Nation" approach that is tech-powered across all facets of the Singaporean society, from finance to education to transportation.
Amongst the most notable projects is the National Digital Identity (NDI) initiative— Users of their flagship service, Singpass, can conduct transactions with hundreds of government agencies and businesses on the cloud, without inconvenient paperwork, in-person visits and even passwords.
Ease of access helped the service see substantial growth in its early years, with total annual transactions rising from 4.5 million in its first year to 57 million in the first 10 years. The programme became known as the go-to secure gateway to hundreds of e-services offered by government.
The bigger ambition for the Singapore government, however, was to make Singpass a key enabler of the digital economy. But to expand the popular service into a universal trust framework, Singapore officials knew that managing infrastructure as well as identifying and mitigating potential security concerns was critical.

When tech meets human ingenuity
The Government’s Technology Agency, GovTech, engaged Accenture as one of the partners to support Singpass’ growth plans and improve resiliency.
Realizing that a simple "lift and shift" to replicate the on-premise architecture in the cloud wouldn't suffice, the team opted for a carefully managed migration with a new microservices architecture for service reliability, small-scale user testing and a user onboarding program that took place in waves.
One of the first moves was innovation on the security front, starting with the introduction of Two-Factor Authentication (2FA) to better protect user data. This also allowed users to perform government digital transactions involving sensitive information—such as filing taxes and viewing CPF statements—more secure.
To support the digitalisation of the economy, Singpass services were extended to the private sector. Financial institutions began integrating their digital services and allowing customers to do away with the need to submit supporting documents, such as NRIC scans or proof of address – ensuring greater ease and faster transaction times for services such as opening new bank accounts and applying for credit cards.
Another opportunity that presented itself was going mobile. GovTech launched the Singpass app in 2018, enabling users to log in to government’s digital services using fingerprint, face recognition or a 6-digit passcode. The app now serves as a secure mode of 2FA, with less reliance on SMS or hard tokens.
The early push to expand access to Singpass proved especially valuable as the COVID-19 pandemic unfolded. NDI’s infrastructure was used to develop SafeEntry for seamless registration for contact tracing purposes, allowing users to check in to thousands of establishments they visited through a mobile app.

Singpass on Cloud
How Singapore’s GovTech manages a surging userbase
A valuable difference
The NDI initiative has grown significantly since its launch. The Singpass app tripled its user base to become one of the most downloaded apps in Singapore in 2020, while kiosks for residents without mobile devices saw more than 19,000 logins in a year.
The business community continues to leverage Singpass’s suite of Application Programming Interfaces (APIs) to improve customer acquisition and business processes. For example, a human resource software company has integrated Singpass's face verification for HR portal logins, and a charity crowdfunding platform uses Singpass to verify beneficiaries, reducing paperwork by at least 40%.
The success of the Singpass story has helped propel Singapore along its “Smart Nation” journey with digital identity authentication, an important enabler of service delivery. As Singapore continues to explore and embrace innovation, it serves as an example to other countries seeking to harness technology to improve residents' lives and livelihoods.

Million users
Million personal and corporate Singpass transactions in a year.
Government agencies and private sector organisations on board.
Images credits: Government Technology Agency, all right reserved.
Related capabilities
Public service.
Smart Nation Singapore: A better life for Singaporeans with innovative, citizen-centric services.
- Mar 10, 2021
- 17 min read
Challenges and Solutions for the Development of an ID System in Post-conflict Areas
Somalia as a case study.
By Nur Dirie Hersi , PhD, Former Head of Somali National ID Program and ID4Africa Ambassador, and Hassan Omar Mahadallah , PhD, Senior Advisor of Somali National ID Program and ID4Africa Deputy Ambassador

Introduction
This study stems from a practical experience the authors have gained during their work to help establish a national identification (ID) system and its implementing institution in Somalia. The creation of the ID system was driven mainly by the need of the financial sector to abide by the universal principle of Know Your Customer (KYC) whereby, during business transactions, customers are required to prove their identity by presenting a legal, secure and verifiable personal ID. Unfortunately, in Somalia customers are not able to meet the KYC requirement since the country does not issue a legal, reliable and verifiable personal ID. As a result, the Somali financial sector, as well as other pertinent sectors, are paralyzed.
The challenges associated with the efforts to establish a national ID system and its implementing institutions are complex and often times entrenched. Accordingly, all our attempts to establish a legal national ID system in the traditional way are often met with financial, social, legal, and political challenges. Our experience is typical in many countries, especially in Africa. Many countries on the continent have never had an inclusive, legal, unified, secure and verifiable ID system. In this study, we refer to these countries as the ID Dark Zones .
Somalia is, for all intents and purposes, a quintessential ID Dark Zone . The country once had a fragmented and rudimentary paper-based family registry system. Even that, along with the memory of it, has been completely wiped out by a prolonged civil war that still rages on in some parts of the rural areas, where the overwhelming majority of the Somali population live. As such, it is fitting to use Somalia as a case study of the ID Dark Zones .
Objectives of the Study
The primary objective of this study is two-fold:
To present the challenges and potential solutions associated with the establishments of a national ID system in ID Dark Zones; and
To share the Somali experience and lessons learned with the ID4D global community, some of whose members would immensely benefit from it.
The following are some of the guiding queries of this study:
What are the factors inhibiting the institutionalization of a national ID system in the ID Dark Zones ?;
What are the implications of this “ ID-lessness ” for the national development plan?;
How can one navigate through the myriad of interests and conflicting views of different level decision makers to establish an ID system? and
How can an ID Dark Zone state overcome the financial, social, legal, and political resistance against the establishment of a National ID system?
Somalia: A Case Study
Using Somalia as a case study, the authors will attempt to provide answers to these pertinent questions. To do so, it is necessary to shed light on the challenges associated with the establishment of a national ID system in countries where there are no inclusive, legal, unified and verifiable system, and to sketch out a path to ID the population of these countries. We argue, and seek to systematically demonstrate, that these problems are directly related to the prevailing, social, financial, and political conditions in the so-called ID Dark Zones . In the latter, the establishment of the national ID system is inhibited by a culture of resistance to new technology, lack of transparency, business interests, political turf wars, lack of financial resources, poor public institution capacities, and rampant corruption—to name just a few.
Although the challenges associated with the process of instituting an ID system are complex and often times entrenched, a well thought-out foundational policy and legislation, coupled with a strong push and support from the International Non-governmental Organizations (INGOs), an strong support from the private sector and civil society participation, together with a sustained civic education can help overcome these impediments. But before delving deeper into these issues, a short background history of Somalia’s ID case may be in order.
Background History
Somalia has been embroiled in a prolonged civil war that decimated virtually all formal public institutions. The consequences of this long and arduous conflict varies from institution to institution. But in no other sector are the tribulations more pronounced than in the national ID system. The impact on civil/family registry system and the issuing office is particularly glaring. Because of the long duration of the war the already feeble, fragmented and under-resourced institution has virtually ceased to exist. A huge majority of the current population has never owned an identification document; worse yet, many have no memory of it. It is therefore incumbent on the minority of the people, like the two authors, who once owned such a document and still retain the memory of it, to lead the process of reinstituting the national ID system.
Historically, Somalia never had an inclusive, unified, secure, legal and verifiable ID system. Rather, the country has inherited from the colonial administration a modesty, fragmented, paper-based ID system with limited functionality. The whole ID ecosystem consisted of a family registry, birth certificate, an ID document, an authentication certificate, and their respective issuing offices. Each of these documents was designed for a specific purpose. Though rudimentary, the family registry served as the foundational and legal document from which all other identity documents were derived. Unfortunately, neither the family registry, nor the functional documents, were issued free of charge. Therefore, only the few urban dwellers, who were required to own these documents by other institutions, and who could afford them, were willing to pay for them.
In short, all post-colonial identity documents, including the family registry, were fragmented. For instance, each municipality issued its own family folder. It was, therefore, normal for an individual to abandon his/her family folder where it was issued and acquire a new one in the new place of residence. The functional documents were even more fragmented. The Labor Office issued ID cards to all the civilian public employees. Likewise, the various offices of the armed forces, the police and the municipal officers, issued their own IDs. The Traffic Office issued drivers licenses with limited uses—i.e., to operate motor vehicles. Worse yet, all these documents, along with the memory of them, have now faded away, making Somalia a quintessential ID Dark Zone.
The remainder of the paper will be devoted to this issue, its potential implications and solution. We start with the methodology we followed to introduce and describe the challenges associated with the creation of an ID system in ID Dark Zones . We conclude by presenting potential solutions.
Methodology
This study has less to contribute by way of theoretical constructs than empirical elucidation. Since we have started the National ID program in early 2017, our approach has been a hands-on one aimed mainly to design and implement an ID system that meets the multifaceted identity challenges faced by the country. Top among these challenges is the threat to the flow of financial remittance system (the so-called Hawalas ), the lifeline of the Somali people. Due to the lack of KYC compliance, some international banks are threatening to close the remittance accounts of the Hawalas , while many more have already done so. When we started the ID Program, our focus was fittingly on how to comply with international remittance standards, such as those of the Western Union and MoneyGram.
From early on, we realized that we could not go it alone, and that we needed substantial local and international support to bring the ID Program to fruition. Since our government could not fund the Program due to financial constraints, we have visited several countries and major ID solution providers which tackled similar situations. These included institutions such as Aadhaar of India, IRIS of Malaysia, and NADRA of Pakistan and presented our case to them. We forwarded technical presentations on the design, features and specifications of our desired system (i.e., ID numbers and cards). Since we have a similar social landscape as Pakistan, NADRA and the Government of Pakistan understood our needs very well and responded to our plea with a donation of US$ 10.3 million for software, hardware, stationary registration sites and mobile registration units, and staff training.
Our next step was to secure the buy-ins of all relevant local and international stakeholders. We started with the Somali Chamber of Commerce, followed by a consortium of local banks, money remittance firms, and telecommunication companies both in and outside of Somalia. Afterwards, we have arranged formal meetings with relevant International Non-Governmental Organization (INGOs), such as DfID, USAID, GIZ, the World Bank, as well as other INGOs, especially those involved in the Cash Transfer Program (CTP), who are bedeviled by identity duplications among aid recipients.
The World Bank responded positively to our request for assistance by providing us a wealth of technical support and advice on how to best setup a foundational ID system with all essential features. The Bank guided us to adapt the ten globally accepted principles on identification for sustainable development. In addition, the Bank agreed to partner with us in the development of the country’s ID ecosystem which elevated the status of our program.
After meeting with the non-political groups and organizations, and securing their full support, we scheduled a series of meetings with Somalia’s public officials, beginning with the Office of the President, Office of the Prime Minister, Ministry of Interior, Department of Immigration, Ministry of Labor, the National Election Commission, and members of the two chambers of the Parliament.
We have arranged a separate meeting with each one of those groups, where we presented the design, features and specification of the proposed (and by then revised) national ID system. We went over with them both the hardware and the software of the system. We explained the type of ID, type and method of data collection, storage system, vendor neutrality, system interoperability, data protection, data security, date migration and protection of personal privacy. During our presentations, we tried to stay clear of politics. Instead, we limited ourselves to the benefits and technical aspects of the ID Program. All went well with them.
At the end of each presentation and consultation with the stakeholders, the ID Program was unanimously endorsed. With the help of World Bank and Ministry of Interior, a national ID policy was drafted, submitted, and approved by the Council of Ministers of the Federal Government of Somalia. This was a huge step forward for the national ID program.
The remainder of the paper will be mainly devoted to the challenges we faced from the public realm. But before we do so, we need to draw a brief overview of the concept, “ ID Dark Zones ,” which is the organizing concept of the paper.
The ID Dark Zones : a Brief Overview of the Concept
The term “ ID Dark Zones ” refers to areas of the world, where there is no formally established, legal, secure, reliable, inclusive, and verifiable identification system. We include in this description countries where more than half of the population are unregistered and do not carry some form of legal identification document. A cursory look at the World Bank’s ID4D Dataset Dashboard reveals the countries that fall in this category. Somalia, where 77% of the population have no identification documents, tops the list. The countries that are included in the top list share some common social, economic and political features. We contend that the challenges against the establishment of an ID system and its implementing institutions stem from these social, economic and political features. Based on our practical experience, these features (outlined in the sections below) constitute some of the factors that fuel the resistance to the establishment of a legal, unified, secure, and verifiable ID system and its implementing institution in Somalia.
The Social Features
Socially, the countries in the ID Dark Zones are what Fred Riggs calls “ prismatic society .” [1] Riggs coined the term to describe a society in transition from a traditional to modern system of administration and governance. Such a society is characterized by persistent social cleavages, enduring loyalty to primordial societies and values, structural violence, widespread corruption in the civic sphere, and low trust in the modern state institutions--to name just a few. When taken together, these characteristics seriously undermine public administration and good governance in these states--and no less the establishment of the national ID system.
Economic Features
The countries in the ID Dark Zones are overwhelmingly low- or middle-income countries. They have a small urbanized society and a large rural population. In terms of the economy, they operate a dual-track system—one in the urban areas and the other in the rural. The urban economy is tenuously connected to the world markets. The Gross National Production (GNP) is dominated by a single natural commodity, such as fossil fuel, coffee, cocoa, cotton, livestock, etc. As the prices of these products fluctuate, so does the national cash flow. In terms of size, the local markets tend to be modest and economic transactions are less frequent--especially when the international commodity prices ebb. Due to the uncertainty of the international system, prices at the local market are also “indeterminate.”
The rural economies of the countries in the ID Dark Zones are more resilient, however, to the vicissitudes of world prices than their urban counterparts. In both cases, markets are small and the population has a low purchasing power. In fact, if we follow Riggs, there are no markets to speak of at the national level. This is why the countries in the ID Dark Zones are technologically and structurally marginalized in the world economy.
In the ID Dark Zones , the prices of goods and services are strongly influenced by non-market factors, such as social, political, and religious considerations. The prices of goods and services are not fixed, not even predictable from one market to another (even from a person to a person within the same market). Haggling, negotiations, even pleading with the seller, are some of the factors that determine the take-home prices of goods and services. Therefore, in the ID Dark Zones , instead of markets, Riggs speaks of the “bazaar” and the “canteen”.[2] In such settings, prices are “indeterminate,” fluctuating, and according to the character of the relationship between the buyer and seller, their relative power, prestige, social ties, skill in bargaining, value system, need for time, etc., as well as in relation to the supply and demand of the item exchanged—i.e., in response to both the arena and market.[3]
Political Features
The citizens of the countries in the ID Dark Zones espouse a divided loyalty—i.e., one to the “ civic public ” and the other to the “ primordial public ,” to use Ekeh’s now famous terms.[4] The dialectic between the two publics heavily influences public policy in the ID Dark Zones . In the latter, where most African states belong to, the primordial public holds more sway in the thinking of the societies than the civic one. Therefore, every political actor has to ingratiate himself/herself with the primordial public. However, the civic public also has its own attraction to society; it provides a wider political space where political actors can display their political acumen. This is the source of divided loyalty. In such a setting, those who hold political positions dwell in a bewildering socio-political conundrum.
The platform (or structures), whereby societies resolves conflict issues over social values, is what Riggs again refers to as the “Sala Bureaucracy.” The latter is characterized “…by the absence of political institutions capable of controlling the bureaucracy, since parties, interest groups, courts and parliament are too weak.”[5] As such, its officials run the bureaucracy by personal whims rather than by formal rules and operating procedures. In terms of service delivery, they give priority to what is appealing to their primordial society and desirable to politically relevant interests in the country, rather than what the people need.
The workers of the “Sala Bureaucracy” are hired on the basis of nepotism or tribal links. Family connections trump personal competencies. Consequently, “One department may become dominated by members of a particular ethnic group, who form a close-knit solidarity group.”[6] Since the top official of the institution is a member of the group, his/her kin folks insulate him/her from the critical eye of the higher-ups, the mass media and the general public. Thus, instead of supervising them, the top official becomes captive to them. He/she become dependent on his/her subordinates. Unfettered by civic rules--or morality, for that matter--they gain free hand at bilking the resources of the institution. Simply put, the Sala Bureaucracy leaves little or no space for public service.[7]
To the degree that these features of the prismatic society impinge on the national politics, they undermine the establishment of the national ID system and its implementing institution. In the following section, we will discuss the nature and character of the challenges associated with the ID Programs in the ID Dark Zones .
The ID System and Associated Challenges in the ID Dark Zones
It is hard to summarize in this paper the challenges that are associated with the establishment of an ID system and its implementing institution in the ID Dark Zones. For this reason, we limit ourselves to the most salient factors preventing the creation of an ID system in these countries. These include, but are not limited to:
Lack of an ID Culture. The Somali society is still moored in the old tradition. It is essentially a “primordial” society. Since the ID system belongs to the “civic” sphere, most Somalis hardly sense its usefulness. This is one of the main hinderances to the institution of a national ID system in Somalia.
Fear of the unknown. With the exception of a few returning expatriates, most Somalis never heard of a foundational ID or number, which breeds, say, drivers licenses, birth certificates, authentication papers, etc. Due to this lack of experience with the system, they tend to harbor a deep mistrust and suspicion about it.
Rudimentary Political Institutions. Somalia is a post-conflict state. The relationships and the respective spheres of power (ToR) of most public institutions are not well-defined. Consequently, political leaders (especially those who lead the sala bureaucracy) viciously compete for all valuable public programs, such as the national ID system. This political competition compounds the challenges associated with the establishment of Somalia’s ID Program.
Tug War. Due to a lack of well-defined institutional boundaries, issues of competences between institutions are settled by a tug of war. For instance, during our first meeting with the leadership of the Ministry of Interior, our interlocutors insisted that the national ID Program falls within the scope and function of the Ministry, and should, therefore, be housed in one of its specialized departments.
As we have canvassed the opinions of the local and international stakeholders, we found out that the private sector and the INGOs were more supportive of the Program than the public entities. The difference is a matter of institutional priority. The former understands the cross-sectoral roles of the ID system—i.e., the need to know your customer (KYC)), taxation, law enforcement, national security, service and delivery, to cite just a few. In the absence of a legal, unified, secure, reliable and verifiable national ID system, none of these core issues can be effectively addressed.
Unlike the private sector and the INGO community, our engagement with the public sector was less cooperative. One of the concerns that they have consistently expressed is their dislike of inclusivity of the Program—i.e., that every person in the country (citizen and non-citizen) will be eligible for a foundational number and ID card. We found out that our use of the word “national” in the name of the Program (i.e., National ID) is problematic, because It evokes as sense of exclusivity (for citizens only). Political leaders like to appear to be defending the “national interest,” irrespective of how one may define it.

To end the confusion we have dropped the word “national” in the various components of the Program, and in its stead employed the word “federal”—hence, the Federal Identification and Registration Authority (FIRA).
Proposed Solutions
From our work in Somalia, we have discovered that to establish an ID System and its implementing institutions, the following resources are required:
Political Support from Top Government Leadership . In Somalia, as in other ID Dark Zones , the support of top political leaders for the institution of the ID system is essential. The main task of such an official is to champion the ID Program at all levels of government.
Local ID Movement Actors. In some cases and under certain conditions, the establishment of the ID system requires a wide public support. This may take the form of a popular campaign, public forums, networking, or simple petition writing.
Input and Support from Local ID Stakeholders. Building or starting a new public institution, such as the ID system, requires wide consultations with stakeholders and a vast civic education. Although this is time and resources consuming, it constitutes an important component of the process to create an ID system.
Support from the International Community. The support of international community (whether bilateral or multi-lateral) comes in two ways, either as a material or political support. Both are needed for the successful execution of the ID Program.
Strategic Implementation Approach
The production of foundational numbers and ID cards is essentially a technical undertaking. There are universal rules, processes and principles that apply in data collection, data storage, data security, and protection of personal privacy. If these are taken into account at the earliest stage of the ID Program, they would not encumber the enrollment, authentication and verification of applicants. Rather, they would elevate the status and credibility of the overall program.
Financial Sustainability
The ID Program must be financially sustainable. However, the foundational numbers and ID cards must be issued free of charge. The Program will raise funds from at least three sources:
Externalization of Cost. All private firms and corporations are required to comply with the principle of know your customer (KYC). Accordingly, they would be required to register all their customers, who do not already possess a legal, secure, reliable and verifiable ID card. Although this may not bring in any cash, it will certainly save substantial resources for the Program.
Collection of Fees. The ID Program may not charge fees for the initial registration, but it will certainly collect fees for duplication or lost IDs, use case application, downstream users, ID verification electronic callers, priority applicants, applicants from outside the country, etc.
Public Funds. Since the ID implementing agency (FIRA) is a public entity, it is entitled to public funds--i.e., annual budget. This is a very reliable revenue.
All proposed fees and charges of the implementing agency require prior approval by the Board and are subject to local economic considerations.
Concluding Remarks
This paper outlines the challenges and potential solutions associated with the establishment of an ID system and its implementing institution. It highlights the challenges that post-conflict countries, particularly those with a long history of disruption of governance and rule of law, will face in establishing a legal, unified, secure, reliable and verifiable ID system. It presents some key recommendation as well to address most of these challenges.
The main problem hindering the establishment of an ID system in the ID Dark Zones is primarily politics. In his seminal work, Africa: The Primacy of Politics , Herbert Spiro speaks about how politics dominates public life in Africa. When the national ID Program came to the public attention, all types of political interests came out of the woodworks--metaphorically speaking. All their demands were political in nature. None of them had an issue with:
The technical configuration of the ID or the design of the Program;
Its impact on the society, economy, politics, or even the National Development Plan (NDP);
Service delivery;
State-society relations;
Law and order; and
National security.
In short, with the exception of the business community, the INGOs and civil society organizations, no public entity was receptive to the ID Program. The following issues are some of the most salient factors affecting their decisions:
Loyalty to the Primordial Publics. As we have stated above, the Somali society is still tradition-bound. As a result, the average public official is torn up by a divided loyalty—i.e., one to the primordial public and the other civic public. In such context, politics is an apt tool to transfer resources from the center (state) to the peripheries. The ID Program is seen as a sources of transferrable cash.
Limited Civic Authority. The existing socio-political setting in the ID Dark Zones severely constrains the authority of the national leaders. In many cases, the authority of the national leaders is contested by the local community. Simply put, in the ID Dark Zones, one’s leader is another’s scoundrel. Hence, the lack of enforcement.
Political Corruption and Maladministration. In the ID Dark Zones , political corruption is prevalent. The platform or structures by which social values are divided (i.e., the sala bureaucracy) is laden with corruption. In some cases, a whole ministry is captured by one ethnic or tribal group. Resources are illegally funneled to the constituency of the bureaucratic leader.
Low Trust in Modern Public Institutions. Despite the deafening rhetoric to the contrary, many public officials in the ID Dark Zones are still beholden to their organic communities. Therefore they cannot acquire widespread public trust beyond their ethnic group or tribe.
Despite these great obstacles, it behooves on the ID Teams in the ID Dark Zones , to lead and establish an ID system and its implementing institution in their respective countries.
Recommendations
The ID Team must clearly distinguish between the foundational numbers and documents, which they issue, and the functional ones, which other agencies offer. The Team must explain that these are breading numbers and documents that facilitate the production and issuance of specialized numbers and documents. In addition, the Team must make it clear to the public that what they offer are foundational numbers and IDs, not functional ones.
Finally, the issuance of the foundational numbers and ID cards must not have any precondition—of course, apart from verification by a well-trained and duly appointed official. All residents in the country must be enrolled once their personal identity is verified.
There are at least three relevant reasons for this approach:
Inclusivity. It makes the process less political. Politics creeps in when resources are exclusively distributed to politically favored groups. However, when everyone is allowed to partake in the Program, there is going to be less room for politics. A corollary advantage of inclusivity is that is vastly improves governance and service delivery.
Avoidance of Turf Wars. Currently, there are many institutions that are issuing functional documents. They charge fees which they jealously guard. By staying clear from their sphere of power, they will interfere less with your foundational numbers and documents.
No Collection of Fees. The principal goal of the ID Team is to enroll all residents of the country. The collection of fees for enrollment precludes the indigent population. This is bound to have a serious implication for the legitimacy and usefulness of the foundational numbers and ID cards.
Fred W. Riggs coined the terms. See Administration in Developing Countries: The Theory of Prismatic Society , Houghton Mifflin (Boston, 1964), pp.
Fred W. Riggs coined the two terms to differential them from the traditional market. See “The Bazaar-Canteen Model: Economic Aspects of the Prismatic Society,” Philippine Sociological Review , Vol. 6, No. 3/4 (July-October, 1958), p. 12.
Ibid., p. 13.
The two terms are coined by Peter Ekeh. For a succinct discussion of this divided loyalty and its implications for good governance, see “Colonialism and the Two Publics: A Theoretical Statement,” Comparative Studies in Society and History , Vol. 17 (01), 1975, pp. 91-112.
Nelson Kasfir, “Prismatic Theory and African Administration,” World Politics , Vol. 21, No. 2 (Jan. 1969), p. 300.
Ibid., p. 301.
Ibid., p. 302.
Recent Posts
Dr. Atick in MIT's 10 Emerging Technologies that will Change the World (2001)
Trustworthy Digital Infrastructure for Identity Systems: The Global Imperative
Meeting the Identity Challenge to Feed Millions in Yemen
Commentaires
This site uses cookies to optimize functionality and give you the best possible experience. If you continue to navigate this website beyond this page, cookies will be placed on your browser. To learn more about cookies, click here .
- Publications
- Conferences & Events
- Professional Learning
- Science Standards
- Awards & Competitions
- Instructional Materials
- Free Resources
- American Rescue Plan
- For Preservice Teachers
NCCSTS Case Collection
- Partner Jobs in Education
- Interactive eBooks+
- Digital Catalog
- Regional Product Representatives
- e-Newsletters
- Bestselling Books
- Latest Books
- Popular Book Series
- Prospective Authors
- Web Seminars
- Exhibits & Sponsorship
- Conference Reviewers
- National Conference • Denver 24
- Leaders Institute 2024
- National Conference • New Orleans 24
- Submit a Proposal
- Latest Resources
- Professional Learning Units & Courses
- For Districts
- Online Course Providers
- Schools & Districts
- College Professors & Students
- The Standards
- Teachers and Admin
- eCYBERMISSION
- Toshiba/NSTA ExploraVision
- Junior Science & Humanities Symposium
- Teaching Awards
- Climate Change
- Earth & Space Science
- New Science Teachers
- Early Childhood
- Middle School
- High School
- Postsecondary
- Informal Education
- Journal Articles
- Lesson Plans
- e-newsletters
- Science & Children
- Science Scope
- The Science Teacher
- Journal of College Sci. Teaching
- Connected Science Learning
- NSTA Reports
- Next-Gen Navigator
- Science Update
- Teacher Tip Tuesday
- Trans. Sci. Learning
MyNSTA Community
- My Collections
Case Study Listserv
Permissions & Guidelines
Submit a Case Study
Resources & Publications
Enrich your students’ educational experience with case-based teaching
The NCCSTS Case Collection, created and curated by the National Center for Case Study Teaching in Science, on behalf of the University at Buffalo, contains over a thousand peer-reviewed case studies on a variety of topics in all areas of science.
Cases (only) are freely accessible; subscription is required for access to teaching notes and answer keys.
Subscribe Today
Browse Case Studies
Latest Case Studies

Development of the NCCSTS Case Collection was originally funded by major grants to the University at Buffalo from the National Science Foundation , The Pew Charitable Trusts , and the U.S. Department of Education .

Mobilising National ID
In this case study we look at how MyID credential management has been deployed by a national government to issue and manage citizen digital identities across their mobile devices.
- Strong multi-factor authentication deployed for best practice security
- Citizen access via their mobile device into cloud and mobile based government services
- A futureproof solution designed to work with current and future versions of mobile operating systems

Trusted by Governments and Enterprises Worldwide
Where protecting systems and information really matters, you will find Intercede. Whether its citizen data, aerospace and defence systems, high-value financial transactions, intellectual property or air traffic control, we are proud that many leading organisations around the world choose Intercede solutions to protect themselves against data breach, comply with regulations and ensure business continuity.

Europe grapples with the best way to implement digital identity

As European nations push forward on implementing a secure digital identity wallet scheme, approaches and results vary. A blog from Spherical Cow Consulting dives into the EU Digital Identity Architecture Reference Framework (ARF), described as “an outline that provides the first blush of a framework for how digital wallets will work in the EU.” A case study from Poland explores how not to implement a national digital ID system. And Hungary is on the cusp of its digital identity launch.
EUDI Wallet ARF outlines integration points with external entities
The EUDI Wallet , says Spherical Cow principal Heather Flanagan, “needs to be able to do a variety of things. From the ability to perform electronic identification, store and manage qualified and non-qualified electronic attestations of attributes, and provide mutual authentication capabilities, this isn’t something you want to get wrong.”
Flanagan says the ARF outline includes guidance on security, privacy by design, and user control over personal data. “Having a presence in the EU and a reliance on government-issued credentials means playing in the digital wallet and verifiable credential landscape,” she writes. “The ARF puts the framework in a context that will help you comply with the appropriate legal and regulatory frameworks while providing a secure and user-friendly experience.”
The framework will also provide guidance on “various interfaces and integration points” for the EUDI Wallet with external entities such as member state infrastructures, identity cards and trusted registries.
Breakdown of Polish digital ID scheme discourages visual verification
Speaking about the Polish digital identity scheme Szymon Chadam , an IT and security consultant with SecuRing, breaks down the risks associated with improper identity verification. His case study , delivered to the Swiss cybersecurity conference Insomni’hack, covers scenarios such as health clinics, air travel, registering for telecom SIM cards, and banking. His research finds that 75 percent of high-risk organizations do not use what he defines as the strongest verification method – cryptographic verification method using QR codes, which Poland’s mCitizen ID system offers.
The big takeaways? Prioritize security. Test for effectiveness. And “never verify visually!”
Hungary begins biometric digital ID rollout
Beginning on May 18, citizens of Hungary can begin applying for a digital ID. Daily News Hungary reports that the National Digital Citizenship Programme’s mobile-based digital identity for Hungarians will offer digital versions of ID and government documents, a digital mailbox, document storage and electronic signature, and electronic payments. The system employs face biometrics by matching the users’ facial images against a government database.
Related Posts

Article Topics
biometrics | digital ID | digital wallets | EU Digital Identity Wallet | Europe | Hungary | Poland | SecuRing | Spherical Cow Consulting
Latest Biometrics News
Uk invests in 4 police vans with live facial recognition to cut knife crime.
The UK government has announced investments in live facial recognition and research and development for remote scanning technologies as it…
Passkeys continue march to mainstream with Visa, WhatsApp updates
Visa has unveiled new digital products and services based on biometrics and passkeys, as it aims to address rapid changes…
States should modernize identity verification to meet fraud challenge: Socure
U.S. state governments are facing major losses due to fraud, but the tools to improve the outcomes of digital interactions…
Digital identity protection tool backed by Australian bank sends alerts for fraud
The venture scaling arm of Australia’s biggest bank has launched a digital identity protection tool that will alert users to…
NADRA expands digital identity card services to post offices, trans people
The National Database and Registration Authority (NADRA) of Pakistan has expanded its digital identity services to enhance accessibility and inclusion,…
Nordic and Baltic countries need better cross-border digital identity matching: NOBID
Nordic and Baltic countries need better identity matching solutions to make cross-border digital identity a reality, concludes a new report…
Leave a Reply Cancel reply
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Continue Reading

Most Read This Week
- Cameroon hands 15-year biometric ID card contract to Augentic
- Bahrain to overhaul ID card system with Thales contract
- Australia outlines new budget for digital ID scheme
- Peru’s digital ID under magnifying glass after national identification registry hit by criticism
- Malawi on path to inclusion with digital ID project supported by EU, UNDP
- Biometric smart cards deployed to new markets for improved payment, access security
- Face biometrics secure payments, borders, public services, but good practice eludes some
- European digital ID project offers grants for more pilots
- Paris rolls out AI surveillance for Taylor Swift
- Malaysia greenlights Worldcoin token trading, setting up biometric crypto growth
- Daily Biometrics News
Featured Company
- More Biometrics Companies
Biometrics Insight, Opinion
- Deepfake fears motivate consumers to change behavior, but misconceptions linger
- Redefining online safety: The evolution of age verification laws
- Startup OVE reveals prototype for flexible biometric payment device
- Video injection attacks: What is that and the way forward?
- Biometrics Industry Interviews
Digital ID In-Depth
- Sri Lanka’s digital identity transformation seeks balance of speed and assurance
- Court orders changes to Tanzania’s data protection law
- Pakistan’s NFIS initiative leverages digital identity for financial inclusion
- Governance framework key to trust that enables data-driven policymaking
- Digital ID Biometrics
Biometrics White Papers
- Protect your business and customers from threat of account fraud
- A buyer’s guide to online identity verification
- Generative AI: How to protect your business in the golden age of fraud and disinformation
- Metrics that matter – How to evaluate identity verification technology
- Digital travel: definition and benefits
- More White Papers

Biometrics Events
- Future Identity Customer London, UK: May 21, 2024
- 2024 SIA GovSummit and Women in Biometrics Awards Washington, D.C.: May 21 - May 22, 2024
- ID4Africa 2024: The Annual General Meeting Cape Town, South Africa: May 21 - May 24, 2024
- EAB Lunch Talk: Implications of the forthcoming forensic sciences standard ISO/IEC 21043 for forensic biometrics Online: May 21, 2024
- Biometrics Institute Asia-Pacific Conference Sydney, Australia: May 22 - May 23, 2024
- More Biometrics Events
A .gov website belongs to an official government organization in the United States.
A lock ( ) or https:// means you've safely connected to the .gov website. Share sensitive information only on official, secure websites.
- Join the National ALS Registry
- Research Publications
Associations of self-reported occupational exposures and settings to ALS: a case–control study
Stephen A. Goutman [1], Jonathan Boss [2], Christopher Godwin [3], Bhramar Mukherjee [2], Eva L. Feldman [1], Stuart A. Batterman {3}
- Department of Neurology, University of Michigan, Ann Arbor, MI, USA.
- Department of Biostatistics, University of Michigan, Ann Arbor, MI, USA.
- Department of Environmental Health Sciences, University of Michigan, Ann Arbor, MI, USA.
International Archives of Occupational and Environmental Health
This research article aimed to identify occupational exposures associated with ALS using both survey and standard occupational classification coding procedures. Participants with ALS were recruited in Michigan through the University of Michigan Pranger ALS Clinic. Controls were recruited through the Michigan Institute for Clinical & Health Research. Through data gathered from recruitment surveys, the study found that occupational exposure to particulate matter, volatile organic compounds, metals, pesticides, and combustion and diesel exhaust and employment in “Production Occupations” was associated with an increased ALS risk in this cohort.
Link to Paper
Read the paper here !
National Amyotrophic Lateral Sclerosis (ALS) Registry
For everyone, public health.

Your company may already be a member. View our member list to find out, or create a new account .
Forgot Password?
Content Library
You can search our content library for case studies, research, industry insights, and more.
You can search our website for events, press releases, blog posts, and more.
With Principal Media on The Rise, ANA Report Seeks To Educate Marketers On Best Practices
Tactic Can Produce Cost Savings but Elevates Potential Conflicts of Interest between Marketers and Agencies
NEW YORK (May 14, 2024) – ANA’s latest report, “The Acceleration of Principal Media,” reveals a substantial knowledge gap among marketers regarding the use of principal media. The purpose of ANA’s report is to increase awareness and to help educate marketers on principal media, including its background, benefits, and challenges.
Principal-based media buying occurs when agencies buy inventory from media owners at bulk rates and then resell it to clients at a markup. Agencies become the owners or vendors of the media, rather than acting as independent agents for clients.
For some marketers, this practice can produce media cost savings of 10-15%. However, the report unveiled several notable findings, including:
- Only half of the survey respondents (48%) are very familiar with principal media. 39% are somewhat familiar and 13% are not familiar.
- About half (47%) of respondents have used principal media in the past year. Just over a third (35%) have not.
- Almost one-fifth (18%) don’t know if principal media has been part of their company’s media activity in the past year.
- About one-quarter (27%) of respondents noted principal media was part of an agency pitch.
In addition, the study found that 41% of respondents expect to use principal media over the next year. Of those respondents, the use of principal media is increasing for 24% and staying the same for 55%.
According to the report, agencies and holding companies have increased their use of principal media due to downward pressure on margins, deterioration of payment terms and an overall focus on “driving media costs down.”
Principal media may offer marketers reduced costs. However, there are multiple challenges marketers must navigate, including an overall determination as to whether such purchases are in their brand’s best interests. Multiple respondents confirmed they had concerns about agency conflicts of interest. Other issues cited include the loss of full audit rights, the quality of actual media inventory delivered and lack of visibility into agency profitability.
“Transparency and accountability are paramount in media transactions,” said Bob Liodice, CEO of the ANA. “This report gives marketers the insights they need to develop a deeper understanding of principal media, along with guidelines that protect their businesses.” A marketer on ANA’s board of directors recently remarked, “While principal media can indeed provide the benefit of cost savings, marketers pursue such deals with their eyes wide open.”
The new report lays out guidelines that marketers can use to assess the usefulness of principal media, including:
- Keep agency contracts up to date, with clear language that addresses principal media.
- Agencies should be required to provide a clear business case detailing why principal media is recommended and to ensure consistency with the marketer’s media strategy and buying guidelines.
- Ask for options that do not include the use of principal media.
- Develop a clear internal approval process for the use of principal media.
- Require that principal media be clearly identified on media flowcharts.
- Request the same proof of performance metrics and access to transaction data for both principal and agent-based media buys.
The report includes a quantitative survey of ANA client-side marketers fielded in February 2024, in addition to follow-up in-depth qualitative interviews. A copy of the full report can be accessed at https://ana.net/principalmedia .
MEDIA CONTACT
Marielena Santana [email protected]
ABOUT THE ANA
The mission of the ANA (Association of National Advertisers) is to drive growth for marketing professionals, brands and businesses, the industry, and humanity. The ANA serves the marketing needs of 20,000 brands by leveraging the 12-point ANA Growth Agenda, which has been endorsed by the Global CMO Growth Council. The ANA’s membership consists of U.S. and international companies, including client-side marketers, nonprofits, fundraisers, and marketing solutions providers (data science and technology companies, ad agencies, publishers, media companies, suppliers, and vendors). The ANA creates Marketing Growth Champions by serving, educating, and advocating for more than 50,000 industry members that collectively invest more than $400 billion in marketing and advertising annually.

IMAGES
VIDEO
COMMENTS
We reviewed the design and functioning of national ID programs in 42 low- and middle-income countries with populations over 15 million and GDP per capita under US$10,000 (as of 2013). Of the national ID programs we reviewed, 17 are in Sub-Saharan Africa, 8 are in the Middle East and North Africa, 6 are in Southeast Asia, 5 are in South Asia, 4 ...
Concerns over data security led to the end of a short-lived national identity card program in the U.K. in 2010. Conference co-chair Deborah Rose, SM '75, a visiting scholar at the FXB Center, urged audience members to take at-risk populations into consideration when planning national ID systems, and to make sure that that they "be used for ...
On the one hand, the global growth of national ID systems is strik-ing. Often, these ID systems are interoperable-most incorporate biome-trics 6 and some also add radio frequency identification (RFID).7 Large ... New IDs offer a concrete case study in the debates over globalization and the demise or persistence of the nation-state. And it is a ...
One precursor to national ID cards emerged in 19th century France. Napoleon sought to streamline the central government in France after the revolutionary period between 1789 and 1799. As he clarified property rights and created new bureaucratic offices, he also introduced a system of internal ID documents for workers in 1803-1804.
The recent talks on reviving the plan to implement a national identification (ID) system brings two cases back into the spotlight. In the first case, Ople vs. Torres, the Supreme Court struck down Administrative Order 308 which seeks to implement the “National Computerized Identification Reference System.†In the second case, Kilusang Mayo Uno vs. Director-General […]
IMPACT OF THE IMPLEMENTATION OF NATIONAL ID SYSTEM IN THE PHILIPPINES: CASE STUDY 3 by Billy Joel Gueta Jemuel Landerito Arrel Poblete Domingo Gaces Samontina, Jr Irish Jay Torres I. Background 1.1 Overview An identity document (also called a piece of identification or ID, or colloquially as papers) is any document which may be used to prove a ...
REAL ID's Case For A National ID. U.S. identification cards are getting a new look. Called the REAL ID, this update to the most common U.S. identity card will help reduce counterfeit and forged ...
Governments around the world are increasingly making registration in national digital ID systems mandatory for populations, justifying its need on a range of issues from facilitating access to services, to national security and fighting against corruption.This is an attempt to create a "foundational identity" for an individual, or "a single source of truth" about who someone is, according to a ...
South Africa ID Case Study. Full Document; Study of Options for Mutual Recognition of National IDs in the East African Community. The State of Identification Systems in Africa: A Synthesis of Country Assessments. Full Document; The State of Identification Systems in Africa: Country Briefs.
Biometric ID systems; Citizen rights and digital data; Ethics and ID data collection; Jamaica Supreme Court NIDS rejection; NIDS Jamaica; Citation. Dunn, H.S. (2020), "Risking identity: a case study of Jamaica's short-lived national ID system", Journal of Information, Communication and Ethics in Society, Vol. 18 No. 3, pp. 329-338.
A national digital identity crisis. In 2020 the pandemic swept across North America, and millions went online to apply for unemployment, food, housing, and other public benefits. The need for digital identity became more apparent than ever, as many experienced difficulties verifying their identity and faced delays or were denied payments.
07. Economic and Sector Work (ESW) Studies. South Africa's approach to identification offers valuable lessons for countries looking to increase the coverage, robustness, and use of their ID systems. Since the end of apartheid, South Africa's national identification system has been transformed from a tool of oppression to one for inclusion ...
A digital identity for each citizen. These National ID programs are also the opportunity to create a secure digital identity for each cardholder. These secure electronic identity cards, called eID cards or simply eIDs, open the gate to secure and trusted online services. The most common applications for these smart cards are smart to travel ...
Case Studies 23 Bolivia: Voter Registration 2009 23 ... Malawi: National Identification System 2017 25 Pakistan: National Identification System 2008-2014 28 Rwanda: New National Population Register 2007 31. ID4D.WRLDA.RG 2 About ID4D The World Bank Group's Identification for Development (ID4D) Initiative leverages global knowledge and
Amongst the most notable projects is the National Digital Identity (NDI) initiative— Users of their flagship service, Singpass, can conduct transactions with hundreds of government agencies and businesses on the cloud, without inconvenient paperwork, in-person visits and even passwords. Ease of access helped the service see substantial growth ...
Somalia as a Case StudyBy Nur Dirie Hersi, PhD, Former Head of Somali National ID Program and ID4Africa Ambassador, and Hassan Omar Mahadallah, PhD, Senior Advisor of Somali National ID Program and ID4Africa Deputy AmbassadorIntroductionThis study stems from a practical experience the authors have gained during their work to help establish a national identification (ID) system and its ...
A national identity system works against the interests of free people and a free society in several ways. ... or infrastructure. This option is the case with credit cards, other payment cards ...
With 189 member countries, staff from more than 170 countries, and offices in over 130 locations, the World Bank Group is a unique global partnership: five institutions working for sustainable solutions that reduce poverty and build shared prosperity in developing countries.
NID National Identification Document NPC National Planning Commission NPRS National Population Registration System NSA Namibia Statistics Agency ... This case study and the others also aim to assess how the enabling environment and the organizational capabilities, including their legal and institutional frameworks, supported these countries in ...
The NCCSTS Case Collection, created and curated by the National Center for Case Study Teaching in Science, on behalf of the University at Buffalo, contains over a thousand peer-reviewed case studies on a variety of topics in all areas of science. Cases (only) are freely accessible; subscription is required for access to teaching notes and ...
In this case study we look at how MyID credential management has been deployed by a national government to issue and manage citizen digital identities across their mobile devices. Strong multi-factor authentication deployed for best practice security; Citizen access via their mobile device into cloud and mobile based government services
(a case study of national identity card, ngwo local government area enugu state by nnamdi samuel uchenna (cst/t/2009/463) in partial fulfillment of the award of bachelor of science degree (b.sc) in the department of computer science and information technology faculty of natural sciences.
A case study of the implementation of an ID card programme in the UAE is presented to highlight some of the lessons learned which, if considered, are most likely to support the planning and execution of similar initiatives. This article provides some insight into the implementation of the national ID programme in the United Arab Emirates (UAE). The fundamental aim is to contribute to the ...
A case study from Poland explores how not to implement a national digital ID system. And Hungary is on the cusp of its digital identity launch. EUDI Wallet ARF outlines integration points with external entities. The EUDI Wallet, says Spherical Cow principal Heather Flanagan, "needs to be able to do a variety of things. From the ability to ...
The study utilized three statistical methods (z-score, straight section in a series, and Jenk's natural breaks) to identify reference counties in Ohio with normal case-population relationships to build a model to estimate case counts in target counties with unrecruited cases.
The Department of Energy's Vehicle Technologies Office has tasked the experts at Idaho National Laboratory to answer big questions surrounding this goal. Skip to content. Home . About . Research . ... Idaho National Laboratory seeks small hydropower utility for case study . May 9, 2024 . ... ID 83415 866-495-7440. Equal Opportunity Employer ...
Summary. This paper describes an alternative method to capture-recapture to estimate missing cases in Ohio's ALS Registry. The team used statistical modeling and spatial adjustments to identify counties in Ohio between 2016-2018 with normal case-population relationships and from it built a methodology of identifying missing cases per county.
Through data gathered from recruitment surveys, the study found that occupational exposure to particulate matter, volatile organic compounds, metals, pesticides, and combustion and diesel exhaust and employment in "Production Occupations" was associated with an increased ALS risk in this cohort.
Ethnopedagogy serves as an educational approach capable of reshaping societal dynamics by preserving cultural values, thereby reinforcing a multicultural national identity. This study explored the potential of ethnopedagogy in revitalizing local wisdom within early childhood character education in Indonesia. This case study was performed at Pertiwi Kindergarten in Puro Pakualaman, Yogyakarta ...
The mission of the ANA (Association of National Advertisers) is to drive growth for marketing professionals, brands and businesses, the industry, and humanity. ... Our member-exclusive online content portfolio of best practices, case studies, and research connects you to the knowledge and resources you need to become a smarter, more capable ...