A Comprehensive Survey on Computer Forensics: State-of-the-Art, Tools, Techniques, Challenges, and Future Directions
Ieee account.
- Change Username/Password
- Update Address

Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Accessibility Links
- Skip to content
- Skip to search IOPscience
- Skip to Journals list
- Accessibility help
- Accessibility Help
Click here to close this panel.
Purpose-led Publishing is a coalition of three not-for-profit publishers in the field of physical sciences: AIP Publishing, the American Physical Society and IOP Publishing.
Together, as publishers that will always put purpose above profit, we have defined a set of industry standards that underpin high-quality, ethical scholarly communications.
We are proudly declaring that science is our only shareholder.
Research on Computer Forensics Technology Based on Data Recovery
Ruibo Duan 1 and Xiong Zhang 2
Published under licence by IOP Publishing Ltd Journal of Physics: Conference Series , Volume 1648 , Information technology Citation Ruibo Duan and Xiong Zhang 2020 J. Phys.: Conf. Ser. 1648 032025 DOI 10.1088/1742-6596/1648/3/032025
Article metrics
780 Total downloads
Share this article
Author e-mails.
Author affiliations
1 Yunnan College of Foreign Affairs & Foreign Language, China, 651700
2 Songming County Public Security Bureau, China, 651700
Buy this article in print
With the rapid development of information technology, fundamental changes have taken place in the way people work. However, computer crime has also become the main type of cases in the Internet era. Therefore, computer forensics technology has become an important research content of computer crime evidence collection. Firstly, this paper analyzes the relationship between computer forensics and data recovery. Then, this paper analyzes the steps of computer forensics. Finally, this paper analyzes the application of anti-forensics technology and computer forensics technology.
Export citation and abstract BibTeX RIS
Content from this work may be used under the terms of the Creative Commons Attribution 3.0 licence . Any further distribution of this work must maintain attribution to the author(s) and the title of the work, journal citation and DOI.
cyber forensics Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
Digital Forensics and Cyber Forensics Investigation: Security Challenges, Limitations, Open Issues, and Future Direction
Performance of cryptographic hash function used in digital forensic tools.
Cryptographic hash functions are which transform any long message to fixed-length data. It seeks to ensure the confidentiality of the data through the cryptographic hash. The digital forensic tool is a method for extracting information from various storage devices, such as hard drives, memory. SHA-1 and SHA-2 methods are both widely used in forensic image archives. The hash method is usually used during evidence processing, the checking of forensic images (duplicate evidence), then at the completion of the analysis again to ensure data integrity and forensic evaluation of evidence. There was a vulnerability called a collision in the hashing algorithm in which two independent messages had the same hash values. While SHA-3 is secure than its former counterparts, the processors for general purposes are being slow and are not yet so popular. This task proposes a basic yet successful framework to meet the needs of cyber forensics, combining hash functions with other cryptographic concepts, for instance, SALT, such as modified secured hash algorithm (MSHA). A salt applies to the hashing mechanism to make it exclusive, expand its complexity and reduce user attacks like hash tables without increasing user requirements.
Forensic Investigation for Cyber Space: Importance of Cyber Forensics in Business and Global Economy
Review paper on introduction to cyber forensics.
Abstract: Cyber Forensics is termed as scientific methods or applications in association with the judiciary or court of laws. The aim behind these methods is to unveil the digital evidence to be utilized in court for solving crime cases. This sort of technology wasn’t practiced before therefore most criminals tend to urge away with their criminal acts without valid proof to incriminate or prosecute them. During that time the oaths, confessions, testimonies from witnesses were the sole determining factors of evidence Crimes committed within electronic or digital domains, particularly within cyberspace, have become common. Criminals are using technology to commit their offenses and make new challenges for law enforcement agents, attorneys, judges, military, and security professionals. Digital forensics has become a vital instrument in identifying and solving computer-based and computerassisted crime. This paper provides a quick introduction to cyber forensics. During this paper we present a typical model for both Incident Response and Computer Forensics processes which mixes their advantages in an exceedingly flexible way: It allows for a management oriented approach in digital investigations while retaining the chance of a rigorous forensics investigation. Keywords: cyber forensics, digital forensic science, computer forensics, evidence, judicial system.
Game-Theoretic Decision Support for Cyber Forensic Investigations
The use of anti-forensic techniques is a very common practice that stealthy adversaries may deploy to minimise their traces and make the investigation of an incident harder by evading detection and attribution. In this paper, we study the interaction between a cyber forensic Investigator and a strategic Attacker using a game-theoretic framework. This is based on a Bayesian game of incomplete information played on a multi-host cyber forensics investigation graph of actions traversed by both players. The edges of the graph represent players’ actions across different hosts in a network. In alignment with the concept of Bayesian games, we define two Attacker types to represent their ability of deploying anti-forensic techniques to conceal their activities. In this way, our model allows the Investigator to identify the optimal investigating policy taking into consideration the cost and impact of the available actions, while coping with the uncertainty of the Attacker’s type and strategic decisions. To evaluate our model, we construct a realistic case study based on threat reports and data extracted from the MITRE ATT&CK STIX repository, Common Vulnerability Scoring System (CVSS), and interviews with cyber-security practitioners. We use the case study to compare the performance of the proposed method against two other investigative methods and three different types of Attackers.
Cyber forensics and risk management
Cyber forensics, forensic accounting and the use of e-discovery and cyber forensics, operational technology, industrial control systems, and cyber forensics, cyber forensics, export citation format, share document.
Implications of Forensic Investigation in Dark Web
- Conference paper
- First Online: 27 September 2023
- Cite this conference paper

- Ngaira Mandela 13 ,
- Amir Aboubakar Shaker Mahmoud 13 &
- Animesh Agrawal 13
Part of the book series: Communications in Computer and Information Science ((CCIS,volume 1893))
Included in the following conference series:
- International Conference on Communication, Networks and Computing
225 Accesses
2 Citations
1 Altmetric
The dark web has become a critical area of concern for law enforcement agencies and cybersecurity experts due to its association with illegal activities such as drug trafficking, money laundering, and cybercrime. Dark web forensics involves the collection, analysis, and preservation of digital evidence from the dark web, which presents several challenges such as anonymity, encryption, and the use of cryptocurrencies. This paper presents a comprehensive review of the current state of research on dark web forensics, with an emphasis on the methods, tools, and challenges associated with this field. The continuous improvement of darknet forensics technology has important practical significance for law enforcement agencies to combat darknet crimes.
This is a preview of subscription content, log in via an institution to check access.

Access this chapter
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
Similar content being viewed by others

An Analysis of the Dark Web Challenges to Digital Policing
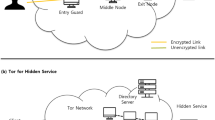
Forensic investigation of the dark web on the Tor network: pathway toward the surface web

The Dark Web and Digital Policing
Akhgar, B., et al.: Dark web investigation. Security Informatics and Law Enforcement (2021, Preprint). https://doi.org/10.1007/978-3-030-55343-2
Al-Khaleel, A., Bani-Salameh, D., Al-Saleh, M.I.: On the memory artifacts of the tor browser bundle. In: The International Conference on Computing Technology and Information Management (ICCTIM), p. 41. Society of Digital Information and Wireless Communication (2014)
Google Scholar
Alotaibi, M., et al.: Computer forensics: dark net forensic framework and tools used for digital evidence detection. Int. J. Commun. Netw. Inf. Secur. (IJCNIS) 11 (3), 424–431 (2022). https://doi.org/10.17762/ijcnis.v11i3.4407
Arshad, M.R., Hussain, M., Tahir, H., Qadir, S., Memon, F.I.A., Javed, Y.: Forensic analysis of tor browser on Windows 10 and Android 10 operating systems. IEEE Access 9 , 141273–141294 (2021)
Article Google Scholar
Ashburn, M.: Understanding the dark web and how IT can aid your investigation, authentic8 (2021). https://www.authentic8.com/blog/understanding-dark-web-and-how-it-can-aid-your-investigation . Accessed 3 Oct 2022
Chetry, A., Sharma, U.: Dark web Activity on Tor—Investigation challenges and retrieval of memory artifacts. In: Gupta, D., Khanna, A., Bhattacharyya, S., Hassanien, A.E., Anand, S., Jaiswal, A. (eds.) International Conference on Innovative Computing and Communications. AISC, vol. 1165, pp. 953–964. Springer, Singapore (2021). https://doi.org/10.1007/978-981-15-5113-0_80
Darcie, W., Boggs, R.J., Sammons, J., Fenger, T.: Online anonymity: forensic analysis of the tor browser bundle. Forensic Science International (2014)
Dayalamurthy, D.: Forensic memory dump analysis and recovery of the artefacts of using tor bundle browser–the need (2013)
Goswami, G., Pandit, D., Patel, A.: Dark web intelligence: everything that you need to know: India (2022). https://heritagecyberworld.com . https://heritagecyberworld.com/blog-dark-web-intelligence-everything-that-you-need-to-know . Accessed 3 Oct 2022
Hawkins, B.: Under the ocean of the Internet-the deep web. SANS Institute InfoSec Reading Room, pp. 1–19 (2016)
Huang, M.J.C., Wan, Y.L., Chiang, C.P., Wang, S.J.: Tor browser forensics in exploring invisible evidence. In: 2018 IEEE International Conference on Systems, Man, and Cybernetics (SMC), pp. 3909–3914. IEEE (2018)
Jadoon, A.K., Iqbal, W., Amjad, M.F., Afzal, H., Bangash, Y.A.: Forensic analysis of Tor browser: a case study for privacy and anonymity on the web. Forensic Sci. Int. 299 , 59–73 (2019)
Keller, K.: The Tor browser: a forensic investigation study. Doctoral dissertation, Utica College (2016)
Kulm, A.: A Framework for Identifying Host-based Artifacts in Dark Web Investigations (2020)
Leng, T., Yu, A.: A framework of darknet forensics. In: 2021 3rd International Conference on Advanced Information Science and System (AISS 2021), pp. 1–6 (2021)
Moronwi, J.: Digital investigator, Digital Investigator (2021). https://digitalinvestigator.blogspot.com/ . Accessed 2 Oct 2022
Muir, M., Leimich, P., Buchanan, W.J.: A forensic audit of the Tor Browser Bundle. Digit. Invest. 29 , 118–128 (2019). https://doi.org/10.1016/j.diin.2019.03.009
Rathod, D.: (PDF) darknet forensics - Researchgate, Darknet Forensics (2017). https://www.researchgate.net/publication/321698383_Darknet_Forensics . Accessed 3 Oct 2022
Sandvik, R.A.: Forensic analysis of the tor browser bundle on OS X, Linux, and windows. Technical report, pp. 1–13 (2013)
Warren, A.: Tor browser artifacts in Windows 10. SANS Institute InfoSec Read, Room (2017)
Download references
Author information
Authors and affiliations.
National Forensic Sciences University, Gandhinagar, India
Ngaira Mandela, Amir Aboubakar Shaker Mahmoud & Animesh Agrawal
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Ngaira Mandela .
Editor information
Editors and affiliations.
ITM University, Gwalior, India
Ranjeet Singh Tomar
IIIT-Allahabad, Allahabad, Uttar Pradesh, India
Shekhar Verma
IIIT Lucknow, Lucknow, India
Brijesh Kumar Chaurasia
IIIT-Allahabad, Allahabad, India
Vrijendra Singh
Deakin University, Burwood, VIC, Australia
Jemal H. Abawajy
ITM University, Gwalior, Madhya Pradesh, India
Shyam Akashe
National Chung Cheng University, Chiayi, Taiwan
Pao-Ann Hsiung
Aarhus University, Herning, Denmark
Ramjee Prasad
Rights and permissions
Reprints and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper.
Mandela, N., Mahmoud, A.A.S., Agrawal, A. (2023). Implications of Forensic Investigation in Dark Web. In: Tomar, R.S., et al. Communication, Networks and Computing. CNC 2022. Communications in Computer and Information Science, vol 1893. Springer, Cham. https://doi.org/10.1007/978-3-031-43140-1_10
Download citation
DOI : https://doi.org/10.1007/978-3-031-43140-1_10
Published : 27 September 2023
Publisher Name : Springer, Cham
Print ISBN : 978-3-031-43139-5
Online ISBN : 978-3-031-43140-1
eBook Packages : Computer Science Computer Science (R0)
Share this paper
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research

IMAGES
VIDEO
COMMENTS
The proposed research survey focuses on identifying the current state-of-the-art digital forensics concepts in existing research, sheds light on research gaps, presents a detailed introduction of different computer forensic domains and forensic toolkits used for computer forensics in the current era.
[62] Computer forensics The proposed paper provides the researchers and readers valuable information about forensics, the current status of forensics, and anti-forensics techniques.
Explore the latest full-text research PDFs, articles, conference papers, preprints and more on COMPUTER FORENSICS. Find methods information, sources, references or conduct a literature review on ...
in Digital Forensics. 1.1.3 Challenges Computer forensics, even with its brief history, is proving to be an imperative science for law enforcement, and it is developing rapidly. Today however, computer forensics is still facing many challenges that force us to seek and develop new investigative analysis techniques.
Computer Forensic Tools & Techniques Catalogue is a comprehensive list of forensic tools developed by NIST. As stated on the website, "the primary goal of the tool catalogue is to provide an easily searchable catalogue of forensic tools and techniques". ... Although this paper is limited to tools developed from academic papers, other ...
Computer forensics is an emerging research area that applies computer investigation and analysis techniques to help detection of these crimes and gathering of digital evidence suitable for presentation in courts. This paper provides foundational concept of computer forensics, outlines various principles of computer forensics, discusses the ...
Since 2008, he is a Research Fellow in Citibank, Ireland (Citi). He obtained his PhD. in Computer Science in 2006 at the Institut National Polytechnique Grenoble (INPG), France. His research interest spans the area of Cybersecurity and Digital Forensics, Data Mining/Distributed Data Mining for Security, Fraud and Criminal Detection.
Today's Golden Age of computer forensics is quickly coming to an end. Without a clear strategy for enabling research efforts that build upon one another, forensic research will fall behind the market, tools will become increasingly obsolete, and law enforcement, military and other users of computer forensics products will be unable to rely on the results of forensic analysis.
PDF | On Apr 30, 2017, Matthew N. O. Sadiku and others published Digital Forensics | Find, read and cite all the research you need on ResearchGate
Forensics is the process of using scientific knowledge for collecting, analyzing, and presenting evidence to the courts. (The word forensics means "to bring to the court.". ) Forensics deals primarily with the recovery and analysis of latent evidence. Latent evidence can take many forms, from fingerprints left on a window to DNA evidence ...
In the first step we used Google Scholar with search terms AI digital forensics and Artificial Intelligence digital forensics to identify fitting papers. Then, we scrutinized the more than 10,000 results and derived search terms to narrow down the research (Schmid et al., 2022).Thus, we finally combined ("digital forensics" OR "digital forensic") with "AI" as well as "Artificial ...
Find the latest published documents for digital forensics, Related hot topics, top authors, the most cited documents, and related journals ... Despite a considerable number of approaches that have been proposed to protect computer systems, cyber-criminal activities are on the rise and forensic analysis of compromised machines and seized devices ...
Therefore, computer forensics technology has become an important research content of computer crime evidence collection. Firstly, this paper analyzes the relationship between computer forensics and data recovery. Then, this paper analyzes the steps of computer forensics. Finally, this paper analyzes the application of anti-forensics technology ...
33. Current Challenges of Digital Forensics in Cyber Security. Figure 1 shows some commonly used data for forensic tools including Bulk. Extraction, EVTXtract, and Scalpet. Fur ther, Bulk ...
Criminals are using technology to commit their offenses and make new challenges for law enforcement agents, attorneys, judges, military, and security professionals. Digital forensics has become a vital instrument in identifying and solving computer-based and computerassisted crime. This paper provides a quick introduction to cyber forensics.
Published by: The Mattingley Publishing Co., Inc. A Walkthrough of Digital Forensics and its Tools. Bhawna Narwal 1, Nimisha Goel 2. 1 ,2Department of IT, Indira Gandhi Delhi Technical University ...
This paper presents a comprehensive review of the current state of research on dark web forensics, with an emphasis on the methods, tools, and challenges associated with this field. The continuous improvement of darknet forensics technology has important practical significance for law enforcement agencies to combat darknet crimes.
Cyber Forensics and Cyber Crime: A m ultidimensional Study of Techniques. and issues. Mohammad Sameen. (2 nd Year, Faculty of Law, Aligarh Muslim University, Aligarh, UP) ABSTRACT. Crimes ...
This paper provided a review of challenges and existing studies of digital forensics in the IoT specifically digital evidence. Perumal et al. [5] 2015. This paper introduced a top-down forensic method for the IoT system in which the investigation process divided into three zones; internal, middle and external.