Cyber Insight

What is Data Diddling and How It Threatens Your Cyber Security?
June 28, 2023

I’ve spent years working in cyber security, and although we’re constantly fighting new threats, there’s one that I find particularly insidious – data diddling. It’s a sneaky technique where hackers manipulate data without being detected, leaving your personal information – and your money – vulnerable. The worst part? You may not even know it’s happened until it’s too late. So, what is data diddling exactly, and how can you protect yourself? Let’s dive in.
What is data diddling in cyber security?
- Manipulating financial records: One of the most common types of data diddling is financial fraud. Criminals use data diddling techniques to modify financial records to conceal their activities and avoid detection.
- Changing customer records: Hackers use data diddling techniques to change customer records to gain access to sensitive information. For example, they might change the email address associated with a customer account to gain access to their email and steal personal data.
- Deleting or modifying critical data: Malicious actors might delete or modify critical data to disrupt business operations or blackmail an organization. For example, they might delete a critical file system or modify database records.
Data diddling can have serious consequences for individuals and businesses alike. Organizations must implement robust cybersecurity measures to prevent data diddling attacks. This may include employing advanced data monitoring and analysis tools, restricting access to critical systems, and regularly testing their cybersecurity policies and procedures.
???? Pro Tips:
1. Develop a thorough understanding of data diddling techniques in cyber security, and ensure that your team is well-informed of these malicious practices. 2. Regularly review and update your security measures, particularly when it comes to data handling and access controls. 3. Be vigilant for signs of data diddling, such as unexpected changes to data records or anomalies in user behaviour. 4. Educate all stakeholders, including employees and customers, on how to protect their data from potential diddling attacks. 5. Have a robust incident response plan in place in the event that data diddling does occur, including clear guidelines on how to report and address any suspicious activity.
Overview of Data Diddling in Cyber Security
In the world of cybercrime, data diddling is a technique that is frequently employed to manipulate electronic data. This occurs when a user intentionally enters incorrect data into a computer system, or other device. Data diddling is usually utilized when individuals and businesses are seeking to conceal a portion of their earnings to avoid tax.
The process of data diddling involves data manipulation, often through the use of sophisticated software, to modify values, transaction dates, and other critical information. Data diddling is a significant cybersecurity risk as it can lead to financial loss, non-compliance penalties, and reputation damage.
Types of Cybercrime Using Data Diddling
There are various types of cybercrime that employ data diddling as a technique. These include:
- Phishing attacks: This is when cybercriminals obtain sensitive data such as login credentials, credit card details, or bank account information by masquerading as a trustworthy entity. Phishing attacks often use emails that contain links to fake websites, login pages, or attachments carrying malware. Data diddling could be used to manipulate the details on these fake sites and, in turn, deceive users into providing sensitive information.
- Payroll Fraud: This type of cybercrime occurs when an employee or an outsider manipulates payroll data to divert funds from the organization. Data diddling is often employed to misrepresent hours worked, change tax withholdings, or modify employee names or bank account details.
- Tax Evasion: As mentioned earlier, tax evasion is a common type of cybercrime that utilizes data diddling. Cybercriminals may manipulate earnings, underreport sales, or overstate expenses to reduce the amount of tax they owe.
Consequences of Data Diddling in Cyber Security
Data diddling can lead to a wide range of cybersecurity risks, including:
- Financial loss: Cybercriminals can manipulate data to divert funds or steal sensitive financial information. This could result in serious financial consequences for the organization or individual affected.
- Non-compliance penalties: Organizations that manipulate data risk penalties and fines from regulatory authorities. This could result in significant legal fees, financial penalties and negative publicity.
- Reputational damage: Organizations whose data has been manipulated can suffer damage to their reputation. Data diddling can result in a loss of customer trust, decreased sales, and negative media coverage.
- Security breaches: Data diddling can be used to introduce malware or other forms of cyber-attacks into computer systems and networks. These attacks could result in significant damage to the organization, including stolen data or network-wide shutdowns.
How to Detect Data Diddling in Cyber Security
Detecting data diddling in a computing system can be difficult. However, there are several methods that organizations and individuals can use to identify suspicious activity:
- Regular audits: Conducting routine audits of systems can help identify suspicious activity or unusual patterns of data manipulation.
- Log analysis: Analyzing logs of system activity and user behavior can help organizations identify anomalies in data or system usage.
- Data validation: Ensuring that data entered into computer systems is consistent and accurate can help mitigate data diddling. One way to validate data is to employ biometric authentication methods such as fingerprints, facial recognition, or voice recognition.
Preventive Measures of Cybercrime Using Data Diddling
Organizations and individuals can employ various preventive measures to avoid falling victim to cyberattacks using data diddling. These include:
- Employee training: Organizations can ensure employees are properly trained to identify and prevent cybercrime, including data diddling. Educating employees on how to recognize phishing attacks and how to maintain best practices when handling sensitive data is critical to preventing cybercrime.
- Antivirus and firewall protection: Installing antivirus and firewall software can protect against malware and other forms of cyberattack that could be introduced through data diddling.
- Regular backups: Conducting regular backups of critical data mitigates the impact of any attacks that could occur, and can help organizations return to normal operations quickly.
- Strict access control: Restricting access to sensitive systems and data and using multifactor authentication can minimize the risk of an attack.
Real-Life Examples of Data Diddling Cyber Attacks
There have been several high-profile cases of data diddling in the recent past. One of the most notorious cases occurred in 2014 when Sony Pictures Entertainment fell victim to a cyberattack that resulted in the exposure of sensitive data. Hackers employed data diddling to manipulate sensitive data such as personal employee information, internal emails, and movies that had yet to be released. The attack resulted in widespread damage to Sony’s reputation and incurred significant financial losses.
Another example occurred in 2018 when Marriott International Inc. experienced a data breach that resulted in the exposure of approximately 500 million guests’ data, including passport details and credit card information. The hackers employed data diddling to manipulate the data to conceal their tracks and evade detection, resulting in significant legal penalties and damage to Marriott’s reputation.
Legal Implications of Data Diddling in Cyber Security
Data diddling is a serious cybercrime, and those who engage in it face severe legal consequences. In the United States, under the Computer Fraud and Abuse Act (CFAA), data diddling crimes are punishable by fines, imprisonment, and damages. The various state laws in the US and international law–such as the EU General Data Protection Regulation (GDPR), have strict data protection and data privacy regulations that impose legal and financial penalties for data diddling. The legal implications of data diddling are severe, making it essential for organizations and individuals to take preventive and protective measures to minimize the associated risks.
In conclusion, data diddling is a common but dangerous technique used by cybercriminals to manipulate electronic data. It is critical that individuals and organizations employ preventive and protective measures against such crimes to avoid the associated damages. Identifying suspicious behavior, strict access control measures, regular backup, employee training, and antivirus protection are among the few measures that can help prevent cyberattacks using data diddling.
most recent

Cybersecurity Basics
What are the three approaches to security in cyber security: explained.

Services & Solutions
What is security solution and why it matters: ultimate guide.

Training & Certification
Is a masters in cybersecurity worth the investment.

What is the Cyber Security Strategy Objective? Protecting Against Breaches.

What is Dart in Cyber Security? A Powerful Tool for Threat Detection.

Decoding SLED: Is Public Sector Cybersecurity the Same?
PH +1 000 000 0000
24 M Drive East Hampton, NY 11937
© 2024 INFO
Preventing Data Diddling and Salami Attacks
Data diddling is the alteration of data prior to the computer systems processing the request, then after the execution of the application, the hacker changes the data information bank. Adding one cent to people’s accounts would be a good example of this type of hacking.
Salami attack
This fraudulent activity targets financial systems specifically. A bank employee inserts a program into the financial systems, which deducts a small amount of money from every customer's account no account holder will notice this unauthorised debit, but the bank employee will make monthly money.
A hacker "slices" away small sums of money from multiple accounts.
Real-world cases of data diddling
- Michael Largent, a 21-year-old from California, wrote a program that allowed him to take advantage of the practice of challenge deposits, which companies like Google and others use to validate a client's bank account.
- Verizon also cited that 85% of breaches in 2020 involved the human element, as phishing was present in 36% of breaches, up from 25% in 2019. Though not citing a specific number, Verizon noted business email compromises doubled in 2020 and were part of an increase in social engineering threats.
NDMC Billing Case
The NDMC Electric Billing Fraud Case that occurred in 1996 illustrates how computers can be manipulated to defraud people. In this case, the computer network was used for receiving and recording electric bill payments by the NDMC, New Delhi. Automated collection of monies, accountancy, records maintenance, and cash transfer into the bank was solely left to a private company with a computer expert working for them. They misused the system to manipulate data so that they could claim fewer payments and less cash being transferred into the bank.
Vladimir Levin and Citibank
The Citibank hack was the first significant cybercrime involving banks. In 1994, Russian computer programmer Vladimir Levin tricked Citibank's computers into transferring money to his account. He then used the money to buy goods and services in various locations around the world. Levin pleaded guilty in January 1998, admitting that he had hacked into Citibank's systems and obtained the customer information.

Although Levin did not steal any money directly, he did gain control of funds belonging to others. Citibank denied that anyone within the bank helped Levin carry out the crime. However, no one has ever claimed responsibility for Levin's actions.
According to published reports (Citigroup), Citibank's internal systems detected suspicious activity involving two wire transfer requests totaling $26,800 and $304,000. When bank personnel contacted the Federal Bureau of Investigation, they could trace the source of the funds to an account belonging to Michael R. Levin, a resident of New York City. Telephone records showed that Levin had used his home telephone number to make the fraudulent requests. In addition, investigators determined that Levin had transferred money out of the United States through Western Union offices in Moscow, Russia.
How to prevent data diddling attacks?
Financial institutions, along with the customers, have several counter-measure options available to help stop diddling data attacks:
- Users should regularly check their monthly transaction history and statement for suspicious activity. They can scan through these activities to detect unusual charges on their credit card. They should immediately report anything odd to their financial institution if they notice anything abnormal.
- To ensure that all applications don't contain unwanted or malicious codes, we must follow the OWASP (Open Web Applications Security Project) guidelines.
- If you receive an email attachment or message asking for your banking information or asking you to click on a link to change your password, mark the email as a phishing message and delete it. Phishing attacks, including whale phishing, spear phishing, email, and barrel phishing, continue to impact global organisations. Security teams continue to spend human capital and organisational financial resources to help prevent data diddling and other forms of data theft.
Leveraging a managed security provider to help combat data diddling
Managed security service providers offer services to help organisations with phishing attacks through the email channel. Data diddling attacks start with account takeover breaches from an email phishing campaign. MSSPs offer managed email security solutions, 24 x 7 incident response, and a Security center as-a-service to help give organisations resources and peace of mind when dealing with growing data diddling, ransomware, and email phishing attacks while maintaining compliance mandates.
MSSP's also provided security awareness services tohelp educate the end-user community on the various phishing attacks and how to identify hackers attempting data diddling attacks and data exfiltration.
Benefits of Managed Security Services Provider- LinearStack
LinearStack brings operational efficiencies with its security experts to help protect your data, respond to a cyber security incident, and protect your intellectual property. You are gaining peace of mind, lowering operational and infrastructure costs while maintaining a higher level of security and critical business drivers for hiring a managed security service provider.
Internal IT, SecOps, and DevOps focus on net-new tasks and projects and less on operational upkeep. Managed services provide the skills, services, and reliability. LinearStack can handle monitoring, security incident response, and system patch. The cost of an MSSP to handle these operational tasks will be less expensive.
Cyber essentials package for cybersecurity governance
Who is this for.
This package is designed for small and medium enterprises to help with cybersecurity governance to provide their security adaptive controls, incidents, and processes are functioning correctly. Cybersecurity carriers will audit clients before renewal to validate that all security controls and other requirements are working. Leveraging an MSSP like LinearStack will meet these requirements.
Our package covers all stages of cyber defence, from gap assessment, remediation, and road mapping to 24 x 7 threat detection and response. This service helps support vulnerability management, protection of e-commerce environments, and continuous compliance mandates and regulatory requirements.
Managed service services for the financial industry
Our Technology and Architecture Implementation services are designed for organisations that need security frameworks tailored to their existing IT infrastructure and organisational goals to help secure the next-generation retail customer experience.
Industry expertise
We live and breathe cyber security, which means we use the best software, know how to set it up for the best results, and learn how to run a robust program. You get access to the latest industry innovations and intelligence and a team of experts, so your team can sleep at night.
Specialist teams ready to respond
Seconds matter with security breaches, malware infection, and ransomware attacks. Our dedicated threat response teams are ready and alert, quickly identifying threats, searching through log data, making decisions, collaborating, and remediate incidents.
Founded in 2013 with a strong focus on world-class cyber security services, LinearStack was built from the ground up in Auckland, New Zealand. Our passion for making information security simple and accessible for all organisations is the fuel that fires our engine.
We’re a growing team of certified Cyber Defence Analysts, Threat Hunters, Incident Responders, CTI specialists, Malware analysts, security architectures, and engineers with two geo-redundant operations centers across the globe.
We’re 100% privately held, grown with a family mindset. When working with clients, we’re well integrated within their teams and act as an extension of their operations. Augmenting existing teams is a transition we manage smoothly, empowering our customers to prioritize cybersecurity strategy while we protect their business from cyber threats 24x7.
We believe maintaining thriving IT systems and assuring data protection are fundamental needs that all businesses deserve.
Want to know more about what we have to offer? We'd love to hear from you
Get in touch with us today:
Phone: 0800 008 795
Email: [email protected]
Website: https://linearstack.co.nz

Start Reading

How Effectively Managing Risk Bolsters Cyber Defenses

How to Achieve Strategic Cyber Risk Management With NIST CSF

A Deep Dive Into Phishing Scams

- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
- Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld
- Network World

The 15 biggest data breaches of the 21st century
Data breaches affecting millions of users are far too common. here are some of the biggest, baddest breaches in recent memory..

In today’s data-driven world, data breaches can affect hundreds of millions or even billions of people at a time. Digital transformation has increased the supply of data moving, and data breaches have scaled up with it as attackers exploit the data-dependencies of daily life. How large cyberattacks of the future might become remains speculation, but as this list of the biggest data breaches of the 21 st Century indicates, they have already reached enormous magnitudes.
For transparency, this list has been calculated by the number of users impacted, records exposed, or accounts affected. We have also made a distinction between incidents where data was actively stolen or reposted maliciously and those where an organization has inadvertently left data unprotected and exposed, but there has been no significant evidence of misuse. The latter have purposefully not been included in the list.
So, here it is – an up-to-date list of the 15 biggest data breaches in recent history, including details of those affected, who was responsible, and how the companies responded (as of July 2021).
Date: August 2013 Impact: 3 billion accounts
Securing the number one spot – almost seven years after the initial breach and four since the true number of records exposed was revealed – is the attack on Yahoo. The company first publicly announced the incident – which it said took place in 2013 – in December 2016. At the time, it was in the process of being acquired by Verizon and estimated that account information of more than a billion of its customers had been accessed by a hacking group. Less than a year later, Yahoo announced that the actual figure of user accounts exposed was 3 billion. Yahoo stated that the revised estimate did not represent a new “security issue” and that it was sending emails to all the “additional affected user accounts.”
Despite the attack, the deal with Verizon was completed, albeit at a reduced price. Verizon’s CISO Chandra McMahon said at the time: “Verizon is committed to the highest standards of accountability and transparency, and we proactively work to ensure the safety and security of our users and networks in an evolving landscape of online threats. Our investment in Yahoo is allowing that team to continue to take significant steps to enhance their security, as well as benefit from Verizon’s experience and resources.” After investigation, it was discovered that, while the attackers accessed account information such as security questions and answers, plaintext passwords, payment card and bank data were not stolen.
2. Aadhaar [tie with Alibaba]
Date: January 2018 Impact: 1.1 billion Indian citizens’ identity/biometric information exposed
In early 2018, news broke that malicious actors has infiltrated the world’s largest ID database, Aadhaar , exposing information on more than 1.1 billion Indian citizens including names, addresses, photos, phone numbers, and emails, as well as biometric data like fingerprints and iris scans. What’s more, since the database – established by the Unique Identification Authority of India (UIDAI) in 2009 – also held information about bank accounts connected with unique 12-digit numbers, it became a credit breach too. This was despite the UIDAI initially denying that the database held such data
The actors infiltrated the Aadhaar database through the website of Indane, a state-owned utility company connected to the government database through an application programming interface that allowed applications to retrieve data stored by other applications or software. Unfortunately, Indane’s API had no access controls, thus rendering its data vulnerable. Hackers sold access to the data for as little as $7 via a WhatsApp group. Despite warnings from security researchers and tech groups, it took Indian authorities until March 23, 2018, to take the vulnerable access point offline.
2. Alibaba [tie with Aadhaar]
Date: November 2019 Impact: 1.1 billion pieces of user data
Over an eight-month period, a developer working for an affiliate marketer scraped customer data, including usernames and mobile numbers, from the Alibaba Chinese shopping website, Taobao, using crawler software that he created. It appears the developer and his employer were collecting the information for their own use and did not sell it on the black market, although both were sentenced to three years in prison.
A Taobao spokesperson said in a statement : “Taobao devotes substantial resources to combat unauthorized scraping on our platform, as data privacy and security is of utmost importance. We have proactively discovered and addressed this unauthorized scraping. We will continue to work with law enforcement to defend and protect the interests of our users and partners.”
4. LinkedIn
Date: June 2021 Impact: 700 million users
Professional networking giant LinkedIn saw data associated with 700 million of its users posted on a dark web forum in June 2021, impacting more than 90% of its user base. A hacker going by the moniker of “God User” used data scraping techniques by exploiting the site’s (and others’) API before dumping a first information data set of around 500 million customers. They then followed up with a boast that they were selling the full 700 million customer database. While LinkedIn argued that as no sensitive, private personal data was exposed, the incident was a violation of its terms of service rather than a data breach, a scraped data sample posted by God User contained information including email addresses, phone numbers, geolocation records, genders and other social media details, which would give malicious actors plenty of data to craft convincing, follow-on social engineering attacks in the wake of the leak, as warned by the UK’s NCSC .
5. Sina Weibo
Date: March 2020 Impact: 538 million accounts
With over 600 million users, Sina Weibo is one of China’s largest social media platforms. In March 2020, the company announced that an attacker obtained part of its database, impacting 538 million Weibo users and their personal details including real names, site usernames, gender, location, and phone numbers. The attacker is reported to have then sold the database on the dark web for $250.
China’s Ministry of Industry and Information Technology (MIIT) ordered Weibo to enhance its data security measures to better protect personal information and to notify users and authorities when data security incidents occur. In a statement , Sina Weibo argued that an attacker had gathered publicly posted information by using a service meant to help users locate the Weibo accounts of friends by inputting their phone numbers and that no passwords were affected. However, it admitted that the exposed data could be used to associate accounts to passwords if passwords are reused on other accounts. The company said it strengthened its security strategy and reported the details to the appropriate authority.
6. Facebook
Date: April 2019 Impact: 533 million users
In April 2019, it was revealed that two datasets from Facebook apps had been exposed to the public internet. The information related to more than 530 million Facebook users and included phone numbers, account names, and Facebook IDs. However, two years later (April 2021) the data was posted for free, indicating new and real criminal intent surrounding the data. In fact, given the sheer number of phone numbers impacted and readily available on the dark web as a result of the incident, security researcher Troy Hunt added functionality to his HaveIBeenPwned (HIBP) breached credential checking site that would allow users to verify if their phone numbers had been included in the exposed dataset.
“I’d never planned to make phone numbers searchable,” Hunt wrote in blog post . “My position on this was that it didn’t make sense for a bunch of reasons. The Facebook data changed all that. There’s over 500 million phone numbers but only a few million email addresses so >99% of people were getting a miss when they should have gotten a hit.”
7. Marriott International (Starwood)
Date: September 2018 Impact: 500 million customers
Hotel Marriot International announced the exposure of sensitive details belonging to half a million Starwood guests following an attack on its systems in September 2018. In a statement published in November the same year, the hotel giant said: “On September 8, 2018, Marriott received an alert from an internal security tool regarding an attempt to access the Starwood guest reservation database. Marriott quickly engaged leading security experts to help determine what occurred.”
Marriott learned during the investigation that there had been unauthorized access to the Starwood network since 2014. “Marriott recently discovered that an unauthorized party had copied and encrypted information and took steps towards removing it. On November 19, 2018, Marriott was able to decrypt the information and determined that the contents were from the Starwood guest reservation database,” the statement added.
The data copied included guests’ names, mailing addresses, phone numbers, email addresses, passport numbers, Starwood Preferred Guest account information, dates of birth, gender, arrival and departure information, reservation dates, and communication preferences. For some, the information also included payment card numbers and expiration dates, though these were apparently encrypted.
Marriot carried out an investigation assisted by security experts following the breach and announced plans to phase out Starwood systems and accelerate security enhancements to its network. The company was eventually fined £18.4 million (reduced from £99 million) by UK data governing body the Information Commissioner’s Office (ICO) in 2020 for failing to keep customers’ personal data secure. An article by New York Times attributed the attack to a Chinese intelligence group seeking to gather data on US citizens.
Date: 2014 Impact: 500 million accounts
Making its second appearance in this list is Yahoo, which suffered an attack in 2014 separate to the one in 2013 cited above. On this occasion, state-sponsored actors stole data from 500 million accounts including names, email addresses, phone numbers, hashed passwords, and dates of birth. The company took initial remedial steps back in 2014, but it wasn’t until 2016 that Yahoo went public with the details after a stolen database went on sale on the black market.
9. Adult Friend Finder
Date: October 2016 Impact: 412.2 million accounts
The adult-oriented social networking service The FriendFinder Network had 20 years’ worth of user data across six databases stolen by cyber-thieves in October 2016. Given the sensitive nature of the services offered by the company – which include casual hookup and adult content websites like Adult Friend Finder, Penthouse.com, and Stripshow.com – the breach of data from more than 414 million accounts including names, email addresses, and passwords had the potential to be particularly damning for victims. What’s more, the vast majority of the exposed passwords were hashed via the notoriously weak algorithm SHA-1, with an estimated 99% of them cracked by the time LeakedSource.com published its analysis of the data set on November 14, 2016.
10. MySpace
Date: 2013 Impact: 360 million user accounts
Though it had long stopped being the powerhouse that it once was, social media site MySpace hit the headlines in 2016 after 360 million user accounts were leaked onto both LeakedSource.com and put up for sale on dark web market The Real Deal with an asking price of 6 bitcoin (around $3,000 at the time).
According to the company , lost data included email addresses, passwords and usernames for “a portion of accounts that were created prior to June 11, 2013, on the old Myspace platform. In order to protect our users, we have invalidated all user passwords for the affected accounts created prior to June 11, 2013, on the old Myspace platform. These users returning to Myspace will be prompted to authenticate their account and to reset their password by following instructions.”
It’s believed that the passwords were stored as SHA-1 hashes of the first 10 characters of the password converted to lowercase.
11. NetEase
Date: October 2015 Impact: 235 million user accounts
NetEase, a provider of mailbox services through the likes of 163.com and 126.com, reportedly suffered a breach in October 2015 when email addresses and plaintext passwords relating to 235 million accounts were being sold by dark web marketplace vendor DoubleFlag. NetEase has maintained that no data breach occurred and to this day HIBP states : “Whilst there is evidence that the data itself is legitimate (multiple HIBP subscribers confirmed a password they use is in the data), due to the difficulty of emphatically verifying the Chinese breach it has been flagged as “unverified.”
12. Court Ventures (Experian)
Date: October 2013 Impact: 200 million personal records
Experian subsidiary Court Ventures fell victim in 2013 when a Vietnamese man tricked it into giving him access to a database containing 200 million personal records by posing as a private investigator from Singapore. The details of Hieu Minh Ngo’s exploits only came to light following his arrest for selling personal information of US residents (including credit card numbers and Social Security numbers) to cybercriminals across the world, something he had been doing since 2007. In March 2014, he pleaded guilty to multiple charges including identity fraud in the US District Court for the District of New Hampshire. The DoJ stated at the time that Ngo had made a total of $2 million from selling personal data.
13. LinkedIn
Date: June 2012 Impact: 165 million users
With its second appearance on this list is LinkedIn, this time in reference to a breach it suffered in 2012 when it announced that 6.5 million unassociated passwords (unsalted SHA-1 hashes) had been stolen by attackers and posted onto a Russian hacker forum. However, it wasn’t until 2016 that the full extent of the incident was revealed. The same hacker selling MySpace’s data was found to be offering the email addresses and passwords of around 165 million LinkedIn users for just 5 bitcoins (around $2,000 at the time). LinkedIn acknowledged that it had been made aware of the breach, and said it had reset the passwords of affected accounts.
14. Dubsmash
Date: December 2018 Impact: 162 million user accounts
In December 2018, New York-based video messaging service Dubsmash had 162 million email addresses, usernames, PBKDF2 password hashes, and other personal data such as dates of birth stolen, all of which was then put up for sale on the Dream Market dark web market the following December. The information was being sold as part of a collected dump also including the likes of MyFitnessPal (more on that below), MyHeritage (92 million), ShareThis, Armor Games, and dating app CoffeeMeetsBagel.
Dubsmash acknowledged the breach and sale of information had occurred and provided advice around password changing. However, it failed to state how the attackers got in or confirm how many users were affected.
Date: October 2013 Impact: 153 million user records
In early October 2013, Adobe reported that hackers had stolen almost three million encrypted customer credit card records and login data for an undetermined number of user accounts. Days later, Adobe increased that estimate to include IDs and encrypted passwords for 38 million “active users.” Security blogger Brian Krebs then reported that a file posted just days earlier “appears to include more than 150 million username and hashed password pairs taken from Adobe.” Weeks of research showed that the hack had also exposed customer names, password, and debit and credit card information. An agreement in August 2015 called for Adobe to pay $1.1 million in legal fees and an undisclosed amount to users to settle claims of violating the Customer Records Act and unfair business practices. In November 2016, the amount paid to customers was reported to be $1 million.
Related content
The art of saying no is a powerful tool for the ciso in the era of ai, how to choose the right network security monitoring product, chrome patches fourth zero-day flaw this month, kroll cyber threat landscape report: ai assists attackers, from our editors straight to your inbox.

Michael Hill is the UK editor of CSO Online. He has spent the past five-plus years covering various aspects of the cybersecurity industry, with particular interest in the ever-evolving role of the human-related elements of information security. A keen storyteller with a passion for the publishing process, he enjoys working creatively to produce media that has the biggest possible impact on the audience.
More from this author
The biggest data breach fines, penalties, and settlements so far, if you don’t already have a generative ai security policy, there’s no time to lose, bigid unveils new data risk remediation guidance feature, generative ai could erode customer trust, half of business leaders say.

Dan Swinhoe is UK Editor of CSO Online. Previously he was Senior Staff Writer at IDG Connect.
Man-in-the-middle (MitM) attack definition and examples
How decision-making psychology can improve incident response, how stagecoach stops bec attacks with security training, email controls, most popular authors.

- Microsoft Security
Show me more
Windows recall — a ‘privacy nightmare’.

What is spear phishing? Examples, tactics, and techniques

Emerging ransomware groups on the rise: Who they are, how they operate

CSO Executive Sessions India with Pradipta Kumar Patro, Global CISO and Head IT Platform, KEC International

CSO Executive Sessions: The personality of cybersecurity leaders

CSO Executive Sessions: Geopolitical tensions in the South China Sea - why the private sector should care

Sponsored Links
- Tomorrow’s cybersecurity success starts with next-level innovation today. Join the discussion now to sharpen your focus on risk and resilience.

What Is Data Diddling and How Can You Prevent It?
As clinical administrators and physicians, you're probably aware of the recent surge in ransomware attacks. Yet, there's an equally pressing issue that may not be on everyone's radar: the significant risks posed by data diddling.
While external threats grab headlines, the potential damage caused by insiders or untrained members—intentionally or unintentionally—can be just as devastating, if not more so.
Let's explore how safeguarding against these internal risks is important for preserving the trust and integrity of practices. With insights from expert IT consulting in Sacramento , this blog covers everything you need to learn about data diddling, including the top vulnerabilities it exploits and prevention techniques.
Defining Data Diddling

Data diddling refers to altering or manipulating data, often to deceive others. This cybercrime can lead to conclusions or decisions based on false information that is difficult to detect.
Diddling activities differ primarily in method and intent from other cybercrimes:
- Data diddling or tampering involves unauthorized alteration by individuals with legitimate access to the system or data. Other forms of manipulation, such as hacking, often involve external actors gaining unauthorized access.
- The main intent behind data diddling is to commit fraud, hide fraudulent activities, or gain personal benefits. Other manipulation types have different intents, such as disrupting operations for sabotage or ransom.
Types of Data Diddling
Data diddling involves sneaky tricks to change or mess up information. Familiarity with these tricks helps you keep information intact and uncorrupted. Here are some typical data-diddling activities:
Input Data Diddling
This form of data diddling involves altering data before it enters a system or database. This activity occurs at various entry points, such as manual data entry or through forms.
Example: An employee enters false information before saving it in the electronic health record.
Processing Data Diddling
Processing data diddling means modifying data while it is being processed in the system. This can happen during the data transformation, calculation, or analysis.
Example: An insider changes billing data within a healthcare billing system to inflate charges.
Output Data Diddling
Output data diddling involves unauthorized data alteration during an application's output process. This attack occurs while generating reports, documents, or data exports.
Example: A healthcare provider modifies patient outcome data in performance reports to present a more favorable picture of their quality of care.
Impact of Data Diddling on Healthcare Practices
Messing with healthcare data can cause significant problems for medical centers. These actions can lead to severe consequences, like putting patients at risk, getting in legal trouble, and losing trust.
Let's explore how data diddling can affect healthcare practices:
- Inaccurate patient records lead to incorrect diagnoses or treatments.
- Fraudulent billing practices (e.g., unbundling services) result in legal liabilities and reputational damage.
- Violations of healthcare laws, such as the Health Insurance Portability and Accountability Act (HIPAA), result in penalties and sanctions.
- Compromised data integrity undermines the effectiveness of health management initiatives.
- Breaches of privacy, confidentiality, or ethical standards lead to low patient satisfaction.
Download Free Ebook : Protect Your Practice from Insider Threats
Top 9 Vulnerabilities Exploited by Data Diddling

In 2022, researchers found that cyberattacks are twice as likely to target small healthcare organizations . Despite this, many of these organizations believe they are not attractive targets for cybercriminals.
As a result, they fail to invest in cybersecurity measures, increasing their risk of cybercrime incidents such as data diddling. Such manipulation exploits the following vulnerabilities:
- Weak Access Controls: Lax authentication mechanisms may allow unauthorized individuals to access sensitive data, enabling them to manipulate it without detection.
- Insider Threats: Employees or insiders with malicious intent may use their knowledge of internal processes to engage in data-diddling activities.
- Lack of Data Encryption: Data transmitted or stored without encryption are susceptible to tampering by cyber attackers.
- Poor Data Checks: Inadequate data validation may fail data leak detection or miss data alterations. This weakness allows manipulated data to be processed or accepted as valid.
- Insecure Software: Attackers exploit flaws in software components and bypass security controls to manipulate data.
- Negligence: Failure to follow security protocols and other errors inadvertently expose data to manipulation. Training on how to prevent data leakage and maintain security practices can address these issues.
- Lack of Auditing: Inadequate monitoring and auditing limits the clinic’s visibility to access and usage activities. This flaw makes detecting and responding to unauthorized data manipulation difficult.
- Compliance Gaps: Failure to adhere to regulatory requirements for data security creates compliance gaps that leave data vulnerable to data diddling.
- Complex Systems: Interconnected systems introduce hidden vulnerabilities that attackers can exploit without detection.
Techniques for Preventing Data Diddling
In response to the recent cyberattacks, Senate Intelligence Committee Chair Mark Warner has introduced the Health Care Cybersecurity Improvement Act . The proposed law aims to aid providers during cash crunches caused by cyberattacks.
If the law is enacted, intermediaries must meet specific cybersecurity standards. While such a law may take two years to become effective, healthcare practices like yours can start taking preventive measures now. Some actionable steps include:
Access Control
Access control involves managing access to data by granting user permissions based on authorization level. This measure also complements data leakage prevention strategies.
- Protection Offered: Prevention tactics include encryption and user authentication mechanisms.
- Specialists: IT security specialists with expertise in access control and data leak prevention can support establishing effective control measures.
Data Validation
Data validation checks data to ensure it hasn't been changed or tampered with. Using a cloud hosting service can make this process more secure as it offers compliance features that help ensure the accuracy of your data.
- Protection Offered: Hosting services provide data loss prevention and regular security audits to protect against tampering.
- Specialists: Cloud security specialists assist organizations in implementing cloud services that align with the practice's compliance needs.
Audit Trails
Audit trails involve monitoring activities related to data access, modification, and usage. Collaborating with managed IT service providers (MSPs) can help organizations detect and respond to data diddling incidents.
- Protection Offered: Organizations detect suspicious behavior related to tampering by maintaining detailed audit trails.
- Specialists: MSP healthcare partners and compliance experts can guide the establishment of audit trails and monitoring systems.
ER Tech Pros: Defending Against Data Diddling

As you navigate the complexities of healthcare data security, taking proactive steps against data diddling is paramount. You must offer staff training and invest in prevention techniques, including access control, data validation, and audit trails.
By partnering with ER Tech Pros , you can guarantee that you are investing in top-notch cybersecurity solutions. Our customized approach ensures compliance with relevant industry standards like HIPAA and the NIST Cybersecurity Framework. You can be confident that your data is protected and will remain safeguarded against future threats.
Take the first step towards a more secure future with a FREE IT Assessment. Contact us today at (855) ER-TECH-1 or [email protected] to learn more about our IT service in Sacramento.
Search Articles

Cybersecurity: Is Your Data at Risk?

How the Right Cloud Phone System Can Transform Your Business

Risks and Solutions in AI Integration for Cybersecurity

Email Phishing Attacks: SLAM Method for HIPAA IT Management

Cybersecurity for Remote Workers: Securing Your Home Office

Best Practices for Healthcare Privacy in Mobile Apps

Navigating Remote Healthcare: The Vital Role of MSPs

Exploring the Benefits of Cloud Security in Hosting

Why Your Business Needs to Adopt MFA

Best Practices for Protecting Against Cloud Ransomware
Healthcare & tech articles.

ER Tech Pros is a managed service provider (MSP) that specializes in catering to the IT needs of businesses across the globe. We have offices in Sacramento and the Greater Fresno area.
We use our cutting-edge technology, extensive experience, and global team of technology experts to ensure your IT network is in its most secure and optimal state.
We focus on your IT so you can focus on growing your company.
8795 Folsom Blvd, Ste 205
Sacramento, CA 95826
1501 Howard Rd, Ste 2
Madera, CA 93637
(855) ER-TECH-1 / (855) 378-3241
Search this Site
Get Updates
Enter your email address below to receive tech tips and resources from ER Tech Pros.
Connect With Us
ERTech Pros | All Rights Reserved.
+ Clients Back
- Get Free Legal Answers
- Get Fee Estimates
- Deeds & Drafts
- Find Lawyers
- Get A Dedicated Legal Assistant
- Office Manager
- Display Boards
- Petitions & Pleadings Templates
- Case Diary & Office Manager
- Post News & Artilces
- Post Jobs & Internships
- Get A Dedicated Legal Secretary
+ Law Students
- Campus Ambassadors
- Find Jobs & Internships
- Post News & Articles
- Resource Sharing
+ Law Schools
- Post Admissions
- Post Opportunities
- Get Law School Rating
CRITICAL ANALYSIS ON DATA DIDDLING
Latest news.

Data diddling is an unauthorized altering of data before or during entry into computer system and changing it same after the processing is done. As the original information that is entered is changed either by the person typing the data, a virus that programmed to change the data, the programmer of the data base or the application, or anyone else is involved in the process of creating, recording, encoding, examining, checking, converting and transmitting data. It is said to be one of the simplest methods of computer related crime.
DATA DIDDLING
Data diddling can occur at various points along the chain of information entry, and it is often very subtle and virtually undetectable. It can be something as small as a time clerk substituting his own name or employee number for another employee's name or number. It can be combated by ensuring that all information is identical, whether it is a hard copy or the data within a digital system.
As it is said to be one of the easiest crimes to commit so it will be said as effortless task, it can have detrimental effects. For E.g., Electricity boards in India have victims of data diddling by computer criminals when private parties were computerizing their systems.
As Data diddling is also refers to changing of data before or during entry into the computer system. This kind of an attack involves altering the raw data just before a computer processes it and then changing it back after the processing is completed. The NDMC Electricity Billing Fraud Case that took place in 1996 is a typical example. The computer network was used for receipt and accounting of electricity bills by the NDMC, Delhi. Collection of money, computerized accounting, record maintenance and payment in the bank were exclusively left to a private contractor who was a computer professional. He misappropriated huge amount of funds by manipulating data files to show less receipts and bank remittances.
LAWS FOR DATA DIDDLING
- Section 66 [i] and 43(d) [ii] of the I.T. Act covers the offence of Data Diddling.
- Penalty: Not increasing 1 Crore
CASE REALTED TO CYBER CRIME
NDMC Electricity Billing Fraud Case: A private contractor who was to deal with receipt and accounting of electricity bills by the NDMC, Delhi. Collection of money, computerised, accounting record maintenance and remittance in his bank who misappropriated huge amounts of funds by manipulating data files to less receipt and bank remittance.
PREVENTIVE APPROCHES OF CYBER CRIMES
Prevention [iii] is better than cure. Its s always better to take certain precautions while using the internet. So always follow these preventive approaches-
- Be aware that your mobile device is vulnerable to viruses and hackers. Download applications from trusted sources.
- Use encryption for your most sensitive files such as tax returns or financial records, make regular back-ups of all your important data, and store it in another location
- Use of firewalls may be beneficial.
- Always use secure wireless network. Wi-Fi (wireless) networks at home are vulnerable to intrusion if they are not properly secured. Review and modify default settings. Public Wi-Fi, a.k.a. “Hot Spots”, is also vulnerable. Avoid conducting financial or corporate transactions on these networks.
- Always avoid sending any photograph online particularly to strangers and chat friends as there have been incidents of misuse of the photographs.
- Always keep a watch on the sites that your children are accessing to prevent any kind of harassment or depravation in children.
SUGGESTIONS
- Enable students to secretly report acts of harassment to teachers and school administrators and require students to be notified annually of the process by which they may report.
- Require teachers and other school staff who witness acts of harassment or receive student reports of bullying to notify school administrators in writing.
- Enable the parents or guardians of students to file written reports of suspected harassment.
- Require school administrators to investigate any written reports made under this section and to review.
News Updates

Allow Cookies!
By using our website, you agree to the use of cookies
Lawyers Network
Cities Serving
Law Schools Network
Law Students Network

- Comparative study
- Definition & Learning
Understanding Data diddling in ICS/OT perspective

What is Data diddling?
Data diddling is a form of cyber attack where an attacker manipulates data during its input, processing, transmission, or output to cause disruptions, steal information, or achieve other malicious objectives. This type of attack is particularly concerning in manufacturing and Industrial Control Systems (ICS) environments, where the integrity of data is critical for safe and efficient operations.
How can Data diddling affect Operational Technology / ICS / CPS environments?
One of the biggest challenges in an Operational Environment is the use of legacy protocols like Modbus. With legacy computers on ground, it becomes more easy to tamper such systems. The issue is more prominent in some critical infrastructure sites where replacing older systems is not practical.
In addition, a lot of information is stored unsecured within the OT environment – for e.g. many automation vendor do not save logfiles securely. Backup data are stored on local machines or on hard drives which could be accessed by multiple people who have access to the site.
Since availability is important in a production environment, there is little or no control implemented to validate data flow. However, “restricted data flow”, which is one of the foundational requirements as per IEC 62443 can be utilized to enhance security.
How can an data diddling impact manufacturing/ICS environment?
In manufacturing/ICS environments, data diddling can be used by attackers to:
- Manipulate Process Control : Attackers may tamper with data related to process control systems, causing machinery to malfunction or produce defective products.
- Sabotage Production : By altering production schedules or quality control data, attackers can disrupt production processes, leading to financial losses or safety hazards.
- Steal Intellectual Property : Manipulating design or production data can allow attackers to steal intellectual property or trade secrets, impacting the competitiveness of the organization.
- Cover Up Other Attacks : Attackers might manipulate data to cover up their tracks during other forms of cyber attacks, such as ransomware or espionage.
What are the key methods to mitigate this risk especially in an ICS/OT environment?
To mitigate the risk of data diddling, especially in ICS/OT environments, organizations can implement several key methods:
- Access Control : Limit access to critical systems and data to authorized personnel only. Implement strong authentication mechanisms and role-based access controls to prevent unauthorized manipulation of data.
- Data Integrity Checks : Implement data integrity checks at various stages of data processing to detect any unauthorized alterations. This includes checksums, digital signatures, and other cryptographic methods to verify the integrity of data.
- Network Segmentation : Segmenting the network into separate zones with controlled communication flows can prevent attackers from easily accessing and manipulating critical data.
- Anomaly Detection : Deploy anomaly detection systems that can identify unusual patterns or behaviors in data traffic, indicating potential data manipulation attempts.
- Regular Auditing and Monitoring : Conduct regular audits of system configurations, data logs, and user activities to detect any suspicious changes or unauthorized access. Continuous monitoring of network traffic and system activities can also help identify data diddling attempts in real-time.
- Employee Training and Awareness : Educate employees about the risks of data manipulation and the importance of following security protocols. Training programs should include guidance on recognizing phishing attempts, social engineering tactics, and other common attack vectors.
- Vendor Security : Ensure that third-party vendors and suppliers adhere to strict security standards and practices, especially if they have access to critical systems or data.
- Incident Response Plan : Develop and regularly test an incident response plan specifically tailored for data manipulation incidents. This plan should include procedures for containing the attack, restoring data integrity, and communicating with stakeholders.
By implementing these measures, organizations can significantly reduce the risk of data diddling attacks in manufacturing and ICS environments, safeguarding critical systems and data from manipulation and exploitation by malicious actors.
cybersecurityot_Adm
Related posts.

What is OTCC – Operational Technology Cybersecurity Controls, Saudi Arabia
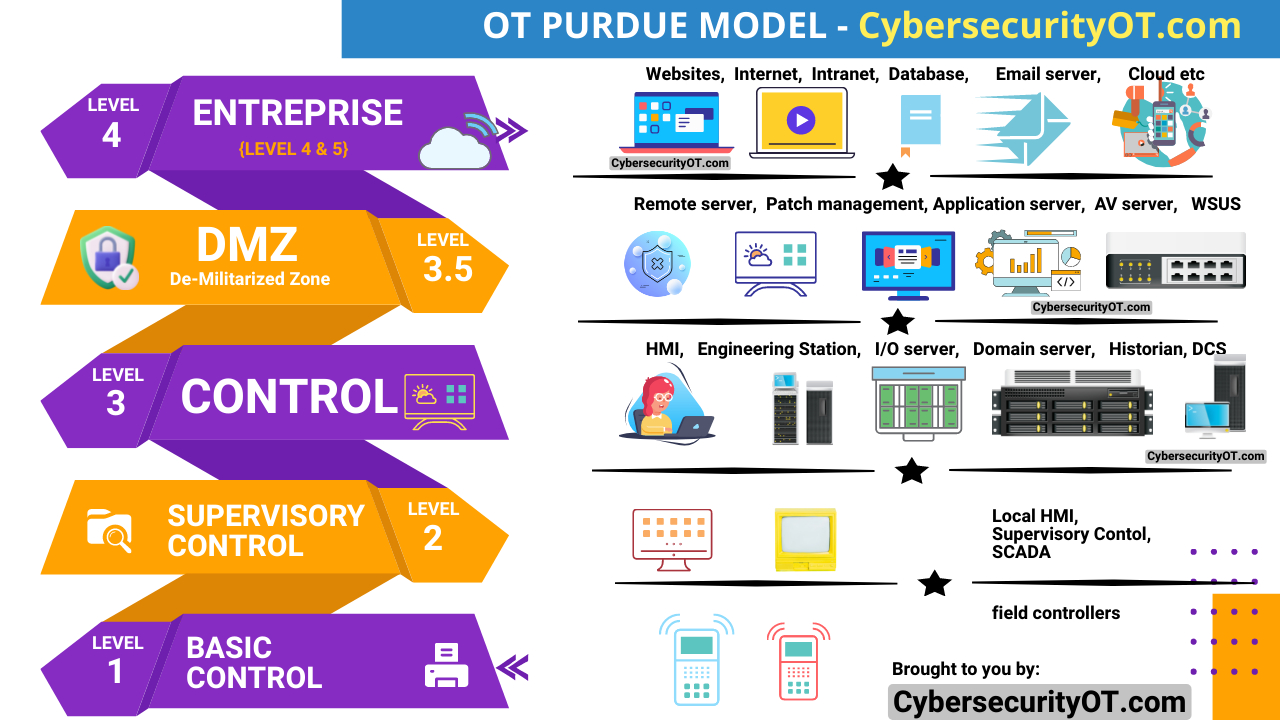

The Purdue Model of Cybersecurity for Operational Technology

What are Zones & Conduits? What are the key elements in implementing them in an architecture?

What are the 7 foundational requirements as per IEC 62443?

Data Diddling vs Man-In-The Middle cyberattacks

What is an Advanced Persistent Threat?

Meet ICSpector – Microsoft’s Open Source Tool for OT Security

Challenges in Implementing AI in OT Security
Vulnerability Assessment for an Operational Technology Environment (High Level)

IEC 61508 standard, Functional Safety & OT Cybersecurity?

- NIST 800-82
- Submit Your Content
Welcome, Login to your account.
Welcome, Create your new account
Recover your password.
A password will be e-mailed to you.

Data diddling

Data diddling is a form of computer fraud involving the intentional falsification of numbers in data entry . It often involves the inflation or understatement of income or expenses to benefit a company or individual when completing tax or other financial documents. This act is performed manually by someone in a data entry position, or remotely by hacking or using malware . Data diddling is a form of cyber crime , and is punishable by large fines or imprisonment.
Unlike other fraud, data diddling specifically refers to the misrepresentation of information during entry, and not after. The phrase is comprised of the term data , which is digital information, and the verb diddle , which means to falsify or exploit.
Related information
- How to protect yourself while on the Internet.
- How to hack someone or something.
- See our computer crime definition for more information and a list of computer crimes.
Business terms , Security terms
Security and Privacy in Big Data Environment
- Reference work entry
- First Online: 01 January 2019
- pp 1487–1495
- Cite this reference work entry

- Shekha Chenthara 3 ,
- Hua Wang 3 &
- Khandakar Ahmed 3
322 Accesses
1 Citations
With the Big Data been increasingly used nowadays across multiple domains, viz., science, engineering, commercial fields, and so on, it has become an interest of research as there is growing concern over Big Data security and privacy of individuals involved. This entry delineates a study regarding issues, benefits, and challenges of security and privacy of Big Data in the cloud and will discuss research challenges and directions concerning data confidentiality, privacy, and trustworthiness in the context of Big Data. Key research issues discussed in this paper include enormous benefits and challenges regarding security and privacy in Big Data and some techniques to enforce security in Big Data stores.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Durable hardcover edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
Abbas A, Khan SU (2014) A review on the state-of-the-art privacy-preserving approaches in the e-health clouds. IEEE J Biomed Health Inform 18:1431–1441
Article Google Scholar
AbuKhousa E, Mohamed N, Al-Jaroodi J (2012) E-health cloud: opportunities and challenges. Futur Internet 4:621–645
Ahmed M, Ullah ASB (2017) False data injection attacks in healthcare. In Australasian Conference on Data Mining. Springer Singapore, Singapore, pp 192--202
Google Scholar
Alguliyev R, Imamverdiyev Y (2014) Big data: big promises for information security. In: Proceedings of IEEE 8th international conference on application of information and communication technologies, pp 1–4
Alshehri S, Raj RK (2013) Secure access control for health information sharing systems. In: Proceedings of IEEE international conference on healthcare informatics, pp 277–286
Azmi Z (2015) Opportunities and security challenges of big data. In: Current and emerging trends in cyber operations. Palgrave Macmillan UK, London, pp 181–197
Chapter Google Scholar
Balamurugan B, Shivitha NG, Monisha V, Saranya V (2015) Survey of access control models for cloud based real-time applications. In: Proceedings of the international conference on innovation information in computing technologies, 2015. IEEE, pp 1–6
Barua M, Lu R, Shen X (2013) SPS: spersonal health information sharing with patient-centric access control in cloud computing. In: Proceedings of the IEEE global communications conference (GLOBECOM), 2013 IEEE. pp 647–652
Bertino E, Ghinita G, Kamra A (2011) Access control for databases: concepts and systems. Found Trends® Databases 3:1–148
MATH Google Scholar
Cheng K, Wang L, Shen Y, Wang H, Wang Y, Jiang X, Zhong H (2017) Secure k-NN query on encrypted cloud data with multiple keys. In: IEEE transactions on big data. IEEE. https://doi.org/10.1109/TBDATA.2017.2707552
Clemens S, Alekhya G, Sneha V, Ujwala S, Yazhini C (2017) Impact of electronic health records on long-term care facilities: systematic review. JMIR Med Inform 5:e35. https://doi.org/10.2196/medinform.7958
Cuzzocrea A (2014) Privacy and security of big data: current challenges and future research perspectives. In: Proceedings of the first international workshop on privacy and secuirty of big data. ACM, pp 45–47
Dwork C (2011) Differential privacy. In: Encyclopedia of cryptography and security. Springer-Verlag Berlin, Heidelberg, pp 338–340
Fang W, Wen XZ, Zheng Y, Zhou M (2017) A survey of big data security and privacy preserving. IETE Tech Rev 34:544–560
Gantz J, Reinsel D (2012) The digital universe in 2020: big data, bigger digital shadows, and biggest growth in the far east. IDC iView: IDC Analyze Futur 2007:1–16
Glavic B (2014) Big data provenance: challenges and implications for benchmarking. In: Specifying big data benchmarks. Springer Berlin Heidelberg. pp 72–80
Griebel L et al (2015) A scoping review of cloud computing in healthcare. BMC Med Inform Decis Mak 15:17. https://doi.org/10.1186/s12911-015-0145-7
Huang J, Peng M, Wang H, Cao J, Gao W, Zhang X (2017) A probabilistic method for emerging topic tracking in microblog stream. World Wide Web 20(2):325–350
Ibraimi L, Asim M, Petković M (2009) Secure management of personal health records by applying attribute-based encryption. In: Proceedings of 2009 6th international workshop on wearable micro and nano technologies for personalized health (pHealth). IEEE, pp 71–74
Jensen M (2013) Challenges of privacy protection in big data analytics. In: Proceedings of 2013 IEEE international congress on big data (BigData Congress). IEEE, pp 235–238
Jeong Y-S, Shin S-S (2016) An efficient authentication scheme to protect user privacy in seamless big data services. Wirel Pers Commun 86:7–19
Kabir ME, Wang H, Bertino E (2012) A role-involved purpose-based access control model. Inf Syst Front 14:809–822
Kadhiwala NJaB (2017) Big data security and privacy issues – a survey. In: Proceedings of the international conference on innovations in power and advanced computing technologies (i-PACT). pp 1–5. https://doi.org/10.1109/IPACT.2017.8245064
Katal A, Wazid M, Goudar R (2013) Big data: issues, challenges, tools and good practices. In: Proceedings of 2013 sixth international conference on contemporary computing (IC3). IEEE, pp 404–409
Khalil F, Wang H, Li J (2007) Integrating markov model with clustering for predicting web page accesses. In: Proceeding of the 13th Australasian world wide web conference, pp 63–74
Li N, Li T, Venkatasubramanian S (2007) t-closeness: privacy beyond k-anonymity and l-diversity. In: Proceeding of the IEEE 23rd international conference on data engineering (ICDE 2007). IEEE, pp 106–115
Li M, Sun X, Wang H, Zhang Y, Zhang J (2011) Privacy-aware access control with trust management in web service. World Wide Web 14:407–430
Li M, Yu S, Zheng Y, Ren K, Lou W (2013) Scalable and secure sharing of personal health records in cloud computing using attribute-based encryption. IEEE Trans Parallel Distrib Syst 24:131–143
Li P, Guo S, Miyazaki T, Xie M, Hu J, Zhuang W (2016) Privacy-preserving access to big data in the cloud. IEEE Cloud Comput 3:34–42
Machanavajjhala A, Kifer D, Gehrke J, Venkitasubramaniam M (2007) L-diversity: privacy beyond k-anonymity. ACM Trans Knowl Discov Data 1:3
Matturdi B, Xianwei Z, Shuai L, Fuhong L (2014) Big data security and privacy: a review. China Commun 11:135–145
McCune JC (1998) Data, data, everywhere. Manag Rev 87:10
Nabeel M, Shang N, Bertino E (2013) Privacy preserving policy-based content sharing in public clouds. IEEE Trans Knowl Data Eng 25:2602–2614
Narayan S, Gagné M, Safavi-Naini R (2010) Privacy preserving EHR system using attribute-based infrastructure. In: Proceedings of the 2010 ACM workshop on cloud computing security workshop. ACM, pp 47–52
Ruj S (2014) Attribute based access control in clouds: a survey. In: Proceedings of the 2014 international conference on signal processing and communications (SPCOM). IEEE, pp 1–6
Shang N, Nabeel M, Paci F, Bertino E (2010) A privacy-preserving approach to policy-based content dissemination. In: Proceedings of 2010 IEEE 26th international conference on data engineering (ICDE). IEEE, pp 944–955
Shen Y, Zhang T, Wang Y, Wang H, Jiang X (2017) MicroThings: a generic iot architecture for flexible data aggregation and scalable service cooperation. IEEE Commun Mag 55:86–93
Shu J, Jia X, Yang Kand Wang H (2018) Privacy-preserving task recommendation services for crowdsourcing. IEEE Trans Serv Comput 1(99):1–1
Sudarsan SD, Jetley RP, Ramaswamy S (2015) Security and privacy of big data. In: Big data. Springer India, New Delhi, pp 121–136
Sun X, Wang H, Li J, Pei J (2011a) Publishing anonymous survey rating data. Data Min Knowl Disc 23:379–406
Article MathSciNet MATH Google Scholar
Sun X, Wang H, Li J, Zhang Y (2011b) Injecting purpose and trust into data anonymisation. Comput Secur 30:332–345
Sweeney L (2002) K-anonymity: a model for protecting privacy. Int J Uncertainty Fuzziness Knowledge Based Syst 10:557–570
Types of Network Attacks against Confidentiality, Integrity and Avilability (2017) http://www.omnisecu.com/ccna-security/types-of-network-attacks.php . Accessed 23 Jan 2017
Ulusoy H, Kantarcioglu M, Pattuk E, Hamlen K (2014) Vigiles: fine-grained access control for mapreduce systems. In: Proceedings of 2014 IEEE international congress on big data (BigData Congress). IEEE, pp 40–47
Venkatram K, Geetha MA (2017) Review on big data & analytics – concepts, philosophy, process and applications. Cybern Inf Technol 17:3–27
MathSciNet Google Scholar
Vimalachandran P, Wang H, Zhang Y, Zhuo G, Kuang H (2017) Cryptographic access control in electronic health record systems: a security implication. In: Proceedings of the international conference on web information systems engineering. Springer, pp 540–549
Wang H, Cao J, Zhang Y (2002) Ticket-based service access scheme for mobile users. Aust Comput Sci Commun 24(1):285–292
Wang H, Cao J, Zhang Y (2005) A flexible payment scheme and its role-based access control. IEEE Trans Knowl Data Eng 17:425–436
Wang H, Zhang Y, Cao J (2009) Effective collaboration with information sharing in virtual universities. IEEE Trans Knowl Data Eng 21(6):840–853
Wang H, Jiang X, Kambourakis G (2015) Special issue on security, privacy and trust in network-based big data. Inf Sci Int J 318:48–50
Wu R, Ahn G-J, Hu H (2012) Secure sharing of electronic health records in clouds. In: Proceedings of 2012 8th international conference on collaborative computing: networking, applications and worksharing (CollaborateCom). IEEE, pp 711–718
Xu L, Shi W (2016) Security theories and practices for big data. In: Big data concepts, theories, and applications. Springer International Publishing, Cham, pp 157–192
Yi X, Miao Y, Bertino E, Willemson J (2013) Multiparty privacy protection for electronic health records. In: Proceedings of the global communications conference (GLOBECOM), 2013 IEEE. IEEE, pp 2730–2735
Zhang J, Tao X, Wang H (2014) Outlier detection from large distributed databases. World Wide Web 17:539–568
Zhang Y, Shen Y, Wang H, Yong J, Jiang X (2015) On secure wireless communications for IoT under eavesdropper collusion. IEEE Trans Autom Sci Eng 13(3):1281–1293. July 2016
Zhang J, Li H, Liu X, Luo Y, Chen F, Wang H, Chang L (2017) On efficient and robust anonymization for privacy protection on massive streaming categorical information. IEEE Trans Dependable Secure Comput 14(5):507–520
Download references
Author information
Authors and affiliations.
Institute for Sustainable Industries and Liveable Cities, VU Research, Victoria University, Melbourne, Australia
Shekha Chenthara, Hua Wang & Khandakar Ahmed
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Hua Wang .
Editor information
Editors and affiliations.
Institute of Computer Science, University of Tartu, Tartu, Estonia
Sherif Sakr
School of Information Technologies, Sydney University, Sydney, Australia
Albert Y. Zomaya
Section Editor information
Swinburne University of Technology, Melbourne, Victoria, Australia
Junjun Chen
Faculty of Engineering and Information Technologies, University of Technology Sydney https://www.uts.edu.au/staff/deepak.puthal
Deepak Puthal
Rights and permissions
Reprints and permissions
Copyright information
© 2019 Springer International Publishing AG, part of Springer Nature
About this entry
Cite this entry.
Chenthara, S., Wang, H., Ahmed, K. (2019). Security and Privacy in Big Data Environment. In: Sakr, S., Zomaya, A.Y. (eds) Encyclopedia of Big Data Technologies. Springer, Cham. https://doi.org/10.1007/978-3-319-77525-8_245
Download citation
DOI : https://doi.org/10.1007/978-3-319-77525-8_245
Published : 20 February 2019
Publisher Name : Springer, Cham
Print ISBN : 978-3-319-77524-1
Online ISBN : 978-3-319-77525-8
eBook Packages : Computer Science Reference Module Computer Science and Engineering
Share this entry
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research
- Project Management
- Application Development
- Collaboration
- Cloud Virtualization
- Enterprise Apps
- Infrastructure
- News & Trends
- Case Studies
- Books for CIOs

What’s Worse Than Stolen Data? Altered Data

What’s Worse Than Stolen Data? Altered Data

Cyber-criminals are not only stealing data and accessing organizations’ data inappropriately—they’re altering it. Here’s a look at the 2016 security landscape.

Organizations will start to realize that cyber-criminals are not only accessing their data inappropriately, they are tampering with it.

When data is unknowingly manipulated, company decisions will be made based on false data. That can lead to devastating consequences because that can taint mixed compounds, control systems and manufacturing processes.

As organizations become more comfortable with the “as-a-service” model and aggregate valuable data on the cloud, that data will become a lucrative target for cyber-criminals and cyber-espionage. A deeper appreciation of third risk party is needed.

As cyber-attack tools and services become more commoditized, the cost of attacking an organization will drop dramatically. Result: more attacks whose primary focus is not financial gain.

Unsophisticated cyber-vigilantes have joined sophisticated collectives such as Anonymous. Financial gain is no longer their main goal, so enterprises must broaden their understanding to include what, why, where, and how they are being targeted.

Attacks on Industrial Control Systems (ICS) that control chemical, electrical, water and transport have increased 17-fold during the last three years. Automated sensors are exacerbating these issues. A critical breach of an ICS is extremely likely.

The high-tech industry has been awash in venture capital, and foolish investments have been made. As organizations’ security programs mature, they will realize that claims of preventing advanced threats are fantasies.

Expect a shakeout in the security industry as organizations’ understanding of advanced threats mature and increasingly drive their security investment decisions.

Get the Free Newsletter!
Subscribe to Daily Tech Insider for top news, trends, and analysis.
Latest Articles
Storage vulnerabilities: the neglected cybersecurity frontier, 7 principles of quality management, domo vs tableau: which is the better bi solution, related articles, ngfw vs utm: differences & use cases, top next-generation firewall (ngfw) software, perimeter 81 vs nordlayer: network security comparison.
CIO Insight offers thought leadership and best practices in the IT security and management industry while providing expert recommendations on software solutions for IT leaders. It is the trusted resource for security professionals who need to maintain regulatory compliance for their teams and organizations. CIO Insight is an ideal website for IT decision makers, systems integrators and administrators, and IT managers to stay informed about emerging technologies, software developments and trends in the IT security and management industry.
Advertisers
Advertise with TechnologyAdvice on CIO Insight and our other IT-focused platforms.
- IT Management
- IT Strategy
- Privacy Policy
- California – Do Not Sell My Information
Property of TechnologyAdvice. © 2022 TechnologyAdvice. All Rights Reserved Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.
- Case Studies
Cyber Crime Awareness Society
Harbinger of war against cyber crime
data diddling

Techniques used in Cyber crimes
Techniques used in Cyber crimes- Cyber Criminals make use of various tools & techniques. Many
- Case Studies (3)
- Cyber Crime News (53)
- Cyber Laws (37)
- Definitions (17)
- Trending Frauds (15)
- Tutorials (20)
- Uncategorized (1)
Landmark Cyber Law cases in India
- Post author By ashwin
- Post date March 1, 2021

By:-Muskan Sharma
Introduction
Cyber Law, as the name suggests, deals with statutory provisions that regulate Cyberspace. With the advent of digitalization and AI (Artificial Intelligence), there is a significant rise in Cyber Crimes being registered. Around 44, 546 cases were registered under the Cyber Crime head in 2019 as compared to 27, 248 cases in 2018. Therefore, a spike of 63.5% was observed in Cyber Crimes [1] .
The legislative framework concerning Cyber Law in India comprises the Information Technology Act, 2000 (hereinafter referred to as the “ IT Act ”) and the Rules made thereunder. The IT Act is the parent legislation that provides for various forms of Cyber Crimes, punishments to be inflicted thereby, compliances for intermediaries, and so on.
Learn more about Cyber Laws Courses with Enhelion’s Online Law Course !
However, the IT Act is not exhaustive of the Cyber Law regime that exists in India. There are some judgments that have evolved the Cyber Law regime in India to a great extent. To fully understand the scope of the Cyber Law regime, it is pertinent to refer to the following landmark Cyber Law cases in India:
- Shreya Singhal v. UOI [2]
In the instant case, the validity of Section 66A of the IT Act was challenged before the Supreme Court.
Facts: Two women were arrested under Section 66A of the IT Act after they posted allegedly offensive and objectionable comments on Facebook concerning the complete shutdown of Mumbai after the demise of a political leader. Section 66A of the IT Act provides punishment if any person using a computer resource or communication, such information which is offensive, false, or causes annoyance, inconvenience, danger, insult, hatred, injury, or ill will.
The women, in response to the arrest, filed a petition challenging the constitutionality of Section 66A of the IT Act on the ground that it is violative of the freedom of speech and expression.
Decision: The Supreme Court based its decision on three concepts namely: discussion, advocacy, and incitement. It observed that mere discussion or even advocacy of a cause, no matter how unpopular, is at the heart of the freedom of speech and expression. It was found that Section 66A was capable of restricting all forms of communication and it contained no distinction between mere advocacy or discussion on a particular cause which is offensive to some and incitement by such words leading to a causal connection to public disorder, security, health, and so on.
Learn more about Cyber Laws with Enhelion’s Online Law firm certified Course!
In response to the question of whether Section 66A attempts to protect individuals from defamation, the Court said that Section 66A condemns offensive statements that may be annoying to an individual but not affecting his reputation.
However, the Court also noted that Section 66A of the IT Act is not violative of Article 14 of the Indian Constitution because there existed an intelligible difference between information communicated through the internet and through other forms of speech. Also, the Apex Court did not even address the challenge of procedural unreasonableness because it is unconstitutional on substantive grounds.
- Shamsher Singh Verma v. State of Haryana [3]
In this case, the accused preferred an appeal before the Supreme Court after the High Court rejected the application of the accused to exhibit the Compact Disc filed in defence and to get it proved from the Forensic Science Laboratory.
The Supreme Court held that a Compact Disc is also a document. It further observed that it is not necessary to obtain admission or denial concerning a document under Section 294 (1) of CrPC personally from the accused, the complainant, or the witness.
- Syed Asifuddin and Ors. v. State of Andhra Pradesh and Anr. [4]
Facts: The subscriber purchased a Reliance handset and Reliance mobile services together under the Dhirubhai Ambani Pioneer Scheme. The subscriber was attracted by better tariff plans of other service providers and hence, wanted to shift to other service providers. The petitioners (staff members of TATA Indicom) hacked the Electronic Serial Number (hereinafter referred to as “ESN”). The Mobile Identification Number (MIN) of Reliance handsets were irreversibly integrated with ESN, the reprogramming of ESN made the device would be validated by Petitioner’s service provider and not by Reliance Infocomm.
Questions before the Court: i) Whether a telephone handset is a “Computer” under Section 2(1)(i) of the IT Act?
- ii) Whether manipulation of ESN programmed into a mobile handset amounts to an alteration of source code under Section 65 of the IT Act?
Decision: (i) Section 2(1)(i) of the IT Act provides that a “computer” means any electronic, magnetic, optical, or other high-speed data processing device or system which performs logical, arithmetic, and memory functions by manipulations of electronic, magnetic, or optical impulses, and includes all input, output, processing, storage, computer software or communication facilities which are connected or related to the computer in a computer system or computer network. Hence, a telephone handset is covered under the ambit of “computer” as defined under Section 2(1)(i) of the IT Act.
(ii) Alteration of ESN makes exclusively used handsets usable by other service providers like TATA Indicomm. Therefore, alteration of ESN is an offence under Section 65 of the IT Act because every service provider has to maintain its own SID code and give its customers a specific number to each instrument used to avail the services provided. Therefore, the offence registered against the petitioners cannot be quashed with regard to Section 65 of the IT Act.
- Shankar v. State Rep [5]
Facts: The petitioner approached the Court under Section 482, CrPC to quash the charge sheet filed against him. The petitioner secured unauthorized access to the protected system of the Legal Advisor of Directorate of Vigilance and Anti-Corruption (DVAC) and was charged under Sections 66, 70, and 72 of the IT Act.
Decision: The Court observed that the charge sheet filed against the petitioner cannot be quashed with respect to the law concerning non-granting of sanction of prosecution under Section 72 of the IT Act.
- Christian Louboutin SAS v. Nakul Bajaj & Ors . [6]
Facts: The Complainant, a Luxury shoes manufacturer filed a suit seeking an injunction against an e-commerce portal www.darveys.com for indulging in a Trademark violation with the seller of spurious goods.
The question before the Court was whether the defendant’s use of the plaintiff’s mark, logos, and image are protected under Section 79 of the IT Act.
Decision: The Court observed that the defendant is more than an intermediary on the ground that the website has full control over the products being sold via its platform. It first identifies and then promotes third parties to sell their products. The Court further said that active participation by an e-commerce platform would exempt it from the rights provided to intermediaries under Section 79 of the IT Act.
- Avnish Bajaj v. State (NCT) of Delhi [7]
Facts: Avnish Bajaj, the CEO of Bazee.com was arrested under Section 67 of the IT Act for the broadcasting of cyber pornography. Someone else had sold copies of a CD containing pornographic material through the bazee.com website.
Decision: The Court noted that Mr. Bajaj was nowhere involved in the broadcasting of pornographic material. Also, the pornographic material could not be viewed on the Bazee.com website. But Bazee.com receives a commission from the sales and earns revenue for advertisements carried on via its web pages.
The Court further observed that the evidence collected indicates that the offence of cyber pornography cannot be attributed to Bazee.com but to some other person. The Court granted bail to Mr. Bajaj subject to the furnishing of 2 sureties Rs. 1 lakh each. However, the burden lies on the accused that he was merely the service provider and does not provide content.
- State of Tamil Nadu v. Suhas Katti [8]
The instant case is a landmark case in the Cyber Law regime for its efficient handling made the conviction possible within 7 months from the date of filing the FIR.
Facts: The accused was a family friend of the victim and wanted to marry her but she married another man which resulted in a Divorce. After her divorce, the accused persuaded her again and on her reluctance to marrying him, he took the course of harassment through the Internet. The accused opened a false e-mail account in the name of the victim and posted defamatory, obscene, and annoying information about the victim.
A charge-sheet was filed against the accused person under Section 67 of the IT Act and Section 469 and 509 of the Indian Penal Code, 1860.
Decision: The Additional Chief Metropolitan Magistrate, Egmore convicted the accused person under Section 469 and 509 of the Indian Penal Code, 1860 and Section 67 of the IT Act. The accused was subjected to the Rigorous Imprisonment of 2 years along with a fine of Rs. 500 under Section 469 of the IPC, Simple Imprisonment of 1 year along with a fine of Rs. 500 under Section 509 of the IPC, and Rigorous Imprisonment of 2 years along with a fine of Rs. 4,000 under Section 67 of the IT Act.
- CBI v. Arif Azim (Sony Sambandh case)
A website called www.sony-sambandh.com enabled NRIs to send Sony products to their Indian friends and relatives after online payment for the same.
In May 2002, someone logged into the website under the name of Barbara Campa and ordered a Sony Colour TV set along with a cordless telephone for one Arif Azim in Noida. She paid through her credit card and the said order was delivered to Arif Azim. However, the credit card agency informed the company that it was an unauthorized payment as the real owner denied any such purchase.
A complaint was therefore lodged with CBI and further, a case under Sections 418, 419, and 420 of the Indian Penal Code, 1860 was registered. The investigations concluded that Arif Azim while working at a call center in Noida, got access to the credit card details of Barbara Campa which he misused.
The Court convicted Arif Azim but being a young boy and a first-time convict, the Court’s approach was lenient towards him. The Court released the convicted person on probation for 1 year. This was one among the landmark cases of Cyber Law because it displayed that the Indian Penal Code, 1860 can be an effective legislation to rely on when the IT Act is not exhaustive.
- Pune Citibank Mphasis Call Center Fraud
Facts: In 2005, US $ 3,50,000 were dishonestly transferred from the Citibank accounts of four US customers through the internet to few bogus accounts. The employees gained the confidence of the customer and obtained their PINs under the impression that they would be a helping hand to those customers to deal with difficult situations. They were not decoding encrypted software or breathing through firewalls, instead, they identified loopholes in the MphasiS system.
Decision: The Court observed that the accused in this case are the ex-employees of the MphasiS call center. The employees there are checked whenever they enter or exit. Therefore, it is clear that the employees must have memorized the numbers. The service that was used to transfer the funds was SWIFT i.e. society for worldwide interbank financial telecommunication. The crime was committed using unauthorized access to the electronic accounts of the customers. Therefore this case falls within the domain of ‘cyber crimes”. The IT Act is broad enough to accommodate these aspects of crimes and any offense under the IPC with the use of electronic documents can be put at the same level as the crimes with written documents.
The court held that section 43(a) of the IT Act, 2000 is applicable because of the presence of the nature of unauthorized access that is involved to commit transactions. The accused were also charged under section 66 of the IT Act, 2000 and section 420 i.e. cheating, 465,467 and 471 of The Indian Penal Code, 1860.
- SMC Pneumatics (India) Pvt. Ltd. vs. Jogesh Kwatra [9]
Facts: In this case, Defendant Jogesh Kwatra was an employee of the plaintiff’s company. He started sending derogatory, defamatory, vulgar, abusive, and filthy emails to his employers and to different subsidiaries of the said company all over the world to defame the company and its Managing Director Mr. R K Malhotra. In the investigations, it was found that the email originated from a Cyber Cafe in New Delhi. The Cybercafé attendant identified the defendant during the enquiry. On 11 May 2011, Defendant was terminated of the services by the plaintiff.
Decision: The plaintiffs are not entitled to relief of perpetual injunction as prayed because the court did not qualify as certified evidence under section 65B of the Indian Evidence Act. Due to the absence of direct evidence that it was the defendant who was sending these emails, the court was not in a position to accept even the strongest evidence. The court also restrained the defendant from publishing, transmitting any information in the Cyberspace which is derogatory or abusive of the plaintiffs.
The Cyber Law regime is governed by the IT Act and the Rules made thereunder. Also, one may take recourse to the provisions of the Indian Penal Code, 1860 when the IT Act is unable to provide for any specific type of offence or if it does not contain exhaustive provisions with respect to an offence.
However, the Cyber Law regime is still not competent enough to deal with all sorts of Cyber Crimes that exist at this moment. With the country moving towards the ‘Digital India’ movement, the Cyber Crimes are evolving constantly and new kinds of Cyber Crimes enter the Cyber Law regime each day. The Cyber Law regime in India is weaker than what exists in other nations.
Hence, the Cyber Law regime in India needs extensive reforms to deal with the huge spike of Cyber Crimes each year.
[1] “Crime in India – 2019” Snapshots (States/UTs), NCRB, available at: https://ncrb.gov.in/sites/default/files/CII%202019%20SNAPSHOTS%20STATES.pdf (Last visited on 25 th Feb; 2021)
[2] (2013) 12 SCC 73
[3] 2015 SCC OnLine SC 1242
[4] 2005 CriLJ 4314
[5] Crl. O.P. No. 6628 of 2010
[6] (2018) 253 DLT 728
[7] (2008) 150 DLT 769
[8] CC No. 4680 of 2004
[9] CM APPL. No. 33474 of 2016
- Tags artificial intelligence courses online , aviation law courses india , best online law courses , business law course , civil courts , civil law law courses online , civil system in india , competition law , corporate law courses online , covaxin , covid vaccine , diploma courses , diploma in criminal law , drafting , fashion law online course , how to study law at home , indian law institute online courses , innovation , Intellectual Property , international law courses , international law degree online , international law schools , introduction to law course , invention , knowledge , labour law course distance learning , law , law certificate courses , law certificate programs online , law classes , law classes online , law college courses , law courses in india , law firms , law schools , lawyers , learn at home , legal aid , legal courses , online law courses , online law courses in india , pfizer , pleading , space law courses , sports law , sports law courses , study criminal law online , study later , study law at home , study law by correspondence , study law degree online , study law degree online australia , study law distance education , study law distance learning , study law online , study law online free , study law online uk , study legal studies online , teach law online , technology law courses , trademark
Data Modeling in Action: Case Studies from Real-World Projects

Data modeling is the art of creating a representation of a complex system, which helps organizations make informed decisions. The practical value of data modeling becomes most evident when it is used to solve real-world problems.
In this article, we present case studies from real-world projects that illustrate the power of data modeling. From detecting fraud in financial transactions to predicting equipment failures in manufacturing plants, these stories will show you how data modeling can make a difference in the success of your projects. So buckle up and get ready to learn how data modeling can transform your business operations.
Case Study 1: Financial Institution Data Modeling
In the realm of data modeling, a financial institution is an excellent place to start when it comes to developing a comprehensive approach. In this case study, we'll dive into the details of how a financial institution created an effective data modeling strategy.
The primary objective for this financial institution was to modernize its existing data management systems. This entailed identifying key areas that required improvement, such as data structure, integration, and management. The next step was to develop a data modeling strategy that could streamline processes and minimize errors.
The strategy was built around the use of a data modeling tool that could automate much of the process of creating data models. The tool had the ability to automatically generate code based on the data models, which cut down on development time and helped to ensure consistency across the organization.
The financial institution also made sure to involve key stakeholders from across the company in the modeling process. This allowed the team to identify and address potential issues and ensure that the final data models fully met the needs of all stakeholders.
Additionally, the institution recognized the need to keep the data models up to date as the needs of the business changed. To accomplish this, they established a process for ongoing maintenance of the models. This involved regular reviews of the models and adjustments as needed.
Overall, the financial institution's data modeling strategy was a success. It helped them to modernize their data management systems, streamline processes and minimize errors. By involving key stakeholders and implementing ongoing maintenance processes, they were able to create a comprehensive data modeling approach that meets all their needs.
Case Study 2: E-Commerce Data Modeling
In this case study, we examine a hypothetical e-commerce company and its data modeling needs. The company, which sells various products online, has a constantly growing volume of data that needs to be managed effectively.
To address this issue, the company decides to implement a data warehouse that will serve as a central repository for all its data. The warehouse will consist of several tables, including:
- Product Table: containing all the products being sold by the company, including their name, description, price, and category.
- Customer Table: containing all the customers who have made purchases, including their name, address, and contact information.
- Order Table: containing all the orders placed, including the customer who placed the order, the product(s) ordered, and the order status.
Other tables will contain data related to inventory, shipping, payments, and promotions.
One of the key challenges facing the e-commerce company is ensuring that its data is accurate and up-to-date. To address this issue, the company plans to use several data validation and verification techniques, including:
- Regular data scrubbing: removing any duplicate data or incorrect entries.
- Data mining: analyzing the data to identify patterns or trends.
- Automated data quality checks: using software to perform regular checks and alert staff if any anomalies are detected.
By implementing a robust data modeling strategy, the e-commerce company will be able to effectively manage its growing volume of data and make better-informed decisions based on accurate, up-to-date information.
Case Study 3: Healthcare Data Modeling
Healthcare data model ing is a crucial aspect of healthcare management. It involves creating database structures that accurately represent healthcare data to facilitate data analysis, decision making, and the management of patient care. The following are some details about Case Study 3: Healthcare Data Modeling:
- The healthcare industry is data-intensive, which makes the need for an efficient data modeling process an essential requirement.
- In this case study, the focus was to develop a data model that captures patient information, hospital procedures, and necessary medical personnel data.
- The team of data modelers collaborated with different healthcare stakeholders to gather diverse healthcare-related information.
- They utilized entities relevant to the medical field to create the data model, such as patients, physicians, procedures, diagnoses, and medications.
- The resultant data model offered an all-encompassing view of the healthcare system, improving physicians' and patients' connectivity.
- The data model's success led to more efficient operations, optimization of healthcare outcomes, improved patient care, and an overall positive impact on the healthcare system.
- Furthermore, the data model's flexibility enabled easy data migration to different health information systems to support healthcare interoperability.
- Healthcare data modeling not only facilitates medical procedures but also contributes to strategic decision-making in the industry's administration and planning.
In conclusion, healthcare data modeling has proven to be an essential component of healthcare management. Its seamless integration in healthcare systems, such as in Case Study 3, has undoubtedly contributed to more smooth operations, better communication, medical decision-making, and improved healthcare outcomes.
Case Study 4: Manufacturing Data Modeling
Manufacturing data modeling is a technique used by manufacturing companies to improve their operations. A case study of a manufacturing company's data modeling project can be very informative.
The case study may include information about the company's goals, challenges, and the approach taken to improve the manufacturing process. It may also include details about the data modeling tools and techniques used, such as entity-relationship modeling and process modeling.
The manufacturing data model may be used to identify inefficiencies in the manufacturing process, such as bottlenecks and supplier delays. By analyzing this data, the company may be able to make changes to its operations and reduce costs.
One possible example of a manufacturing data modeling project might involve the analysis of the production line process. The data model could capture the different processes involved in assembling products, and identify where adjustments could be made to improve efficiency and reduce waste.
Ultimately, a successful manufacturing data modeling project can lead to improved productivity, better product quality, and ultimately, cost savings for the company.
Case Study 5: Education Data Modeling
In Case Study 5, we explore data modeling in the realm of education. Here are some key points about this particular case study:
- Data modeling for education involves organizing and analyzing data related to student performance, teacher effectiveness, and institutional program effectiveness.
- In this case study, we will look at a project that involved creating a data model for a higher education institution in order to improve student outcomes and retention rates.
- The project involved collecting and integrating data from a variety of sources, including student records, course evaluations, and surveys of both students and faculty.
- After the data was collected and organized, the team used various modeling techniques to identify patterns and correlations within the data.
- One key finding of the project was that certain courses and instructors were consistently associated with higher student retention rates.
- The team was able to use this information to make recommendations to the institution about which programs and instructors were most effective at retaining students.
- Overall, the project highlights the importance of data modeling in education, as it can help institutions improve student outcomes and identify areas for improvement.
Final thoughts
This article outlines several case studies showcasing the practical application of data modeling in real-world projects. The first case study explores how a healthcare organization used data modeling to implement a new electronic health records system, resulting in improved efficiency and patient care. The second case study highlights how a financial services company utilized data modeling to streamline their data management and reduce errors.
The third case study illustrates how a retail company used data modeling to improve their supply chain management and inventory forecasting, leading to increased sales.
Overall, these case studies demonstrate the value and effectiveness of data modeling in solving complex business problems.
Interested?
Leave your email and we'll send you occasional, honest promo material and more relevant content.
Full Guide on Cyber Crimes in India
Continued......
Online gambling
There are millions of websites; all hosted on servers abroad, that offer online gambling. In fact, it is believed that many of these websites are actually fronts for money laundering. Cases of hawala transactions and money laundering over the Internet have been reported. Whether these sites have any relationship with drug trafficking is yet to be explored. Recent Indian case about cyber lotto was very interesting. A man called Kola Mohan invented the story of winning the Euro Lottery. He himself created a website and an email address on the Internet with the address '[email protected].' Whenever accessed, the site would name him as the beneficiary of the 12.5 million pound.After confirmation a telgu newspaper published this as a news. He collected huge sums from the public as well as from some banks for mobilization of the deposits in foreign currency. However, the fraud came to light when a cheque discounted by him with the Andhra Bank for Rs 1.73 million bounced. Mohan had pledged with Andhra Bank the copy of a bond certificate purportedly issued by Midland Bank, Sheffields, London stating that a term deposit of 12.5 million was held in his name.
Intellectual Property crimes
These include software piracy, copyright infringement, trademarks violations, theft of computer source code etc. In other words this is also referred to as cybersquatting. Satyam Vs. Siffy is the most widely known case. Bharti Cellular Ltd. filed a case in the Delhi High Court that some cyber squatters had registered domain names such as barticellular.com and bhartimobile.com with Network solutions under different fictitious names. The court directed Network Solutions not to transfer the domain names in question to any third party and the matter is sub-judice. Similar issues had risen before various High Courts earlier. Yahoo had sued one Akash Arora for use of the domain name �Yahooindia.Com� deceptively similar to its �Yahoo.com�. As this case was governed by the Trade Marks Act, 1958, the additional defence taken against Yahoo�s legal action for the interim order was that the Trade Marks Act was applicable only to goods.
Email spoofing
A spoofed email is one that appears to originate from one source but actually has been sent from another source. E.g. Gauri has an e-mail address [email protected]. Her enemy, Prasad spoofs her e-mail and sends obscene messages to all her acquaintances. Since the e-mails appear to have originated from Gauri, her friends could take offence and relationships could be spoiled for life.
Email spoofing can also cause monetary damage. In an American case, a teenager made millions of dollars by spreading false information about certain companies whose shares he had short sold. This misinformation was spread by sending spoofed emails, purportedly from news agencies like Reuters, to share brokers and investors who were informed that the companies were doing very badly. Even after the truth came out the values of the shares did not go back to the earlier levels and thousands of investors lost a lot of money.
Recently, a branch of the Global Trust Bank experienced a run on the bank. Numerous customers decided to withdraw all their money and close their accounts. It was revealed that someone had sent out spoofed emails to many of the bank�s customers stating that the bank was in very bad shape financially and could close operations at any time. Unfortunately this information proved to be true in the next few days.
But the best example of the email spoofing can be given by the Gujarat Ambuja Executive�s case. Where he pretended to be a girl and cheated the Abu dhabi based NRI for crores by blackmailing tactics.
Counterfeit currency notes, postage and revenue stamps, mark sheets etc can be forged using sophisticated computers, printers and scanners.
Outside many colleges across India, one finds touts soliciting the sale of fake mark sheets or even certificates. These are made using computers, and high quality scanners and printers. In fact, this has becoming a booming business involving thousands of Rupees being given to student gangs in exchange for these bogus but authentic looking certificates.Some of the students are caught but this is very rare phenomenon.
Cyber Defamation:
This occurs when defamation takes place with the help of computers and / or the Internet. E.g. someone publishes defamatory matter about someone on a website or sends e-mails containing defamatory information to all of that person�s friends.
India�s first case of cyber defamation was reported when a company�s employee started sending derogatory, defamatory and obscene e-mails about its Managing Director. The e-mails were anonymous and frequent, and were sent to many of their business associates to tarnish the image and goodwill of the company.
The company was able to identify the employee with the help of a private computer expert and moved the Delhi High Court. The court granted an ad-interim injunction and restrained the employee from sending, publishing and transmitting e-mails, which are defamatory or derogatory to the plaintiffs.
Cyber stalking
The Oxford dictionary defines stalking as �pursuing stealthily�. Cyber stalking involves following a person�s movements across the Internet by posting messages (sometimes threatening) on the bulletin boards frequented by the victim, entering the chat-rooms frequented by the victim, constantly bombarding the victim with emails etc.
Ritu Kohli has the dubious distinction of being the first lady to register the cyber stalking case. A friend of her husband gave her telephonic number in the general chat room. The general chatting facility is provided by some websites like MIRC and ICQ. Where person can easily chat without disclosing his true identity. The friend of husband also encouraged this chatters to speak in slang language to Ms. Kohli.
Now, let us examine some of the acts wherein the computer is the target for an unlawful act. It may be noted that in these activities the computer may also be a tool. This kind of activity usually involves sophisticated crimes usually out of the purview of conventional criminal law. Some examples are:
Unauthorized access to computer systems or networks
This activity is commonly referred to as hacking. The Indian law has, however, given a different connotation to the term hacking, so we will not use the term �unauthorized access� interchangeably with the term �hacking�. However, as per Indian law, unauthorized access does occur, if hacking has taken place.
An active hackers� group, led by one �Dr. Nuker�, who claims to be the founder of Pakistan Hackerz Club, reportedly hacked the websites of the Indian Parliament, Ahmedabad Telephone Exchange, Engineering Export Promotion Council, and United Nations (India).
Theft of information contained in electronic form
This includes information stored in computer hard disks, removable storage media etc.
Email bombing
Email bombing refers to sending a large number of emails to the victim resulting in the victim�s email account (in case of an individual) or mail servers (in case of a company or an email service provider) crashing.
In one case, a foreigner who had been residing in Simla, India for almost thirty years wanted to avail of a scheme introduced by the Simla Housing Board to buy land at lower rates. When he made an application it was rejected on the grounds that the scheme was available only for citizens of India. He decided to take his revenge. Consequently he sent thousands of mails to the Simla Housing Board and repeatedly kept sending e-mails till their servers crashed.
This kind of an attack involves altering raw data just before it is processed by a computer and then changing it back after the processing is completed. Electricity Boards in India have been victims to data diddling programs inserted when private parties were computerizing their systems.
The NDMC Electricity Billing Fraud Case that took place in 1996 is a typical example. The computer network was used for receipt and accounting of electricity bills by the NDMC, Delhi. Collection of money, computerized accounting, record maintenance and remittance in he bank were exclusively left to a private contractor who was a computer professional. He misappropriated huge amount of funds by manipulating data files to show less receipt and bank remittance.
Salami attacks
These attacks are used for the commission of financial crimes. The key here is to make the alteration so insignificant that in a single case it would go completely unnoticed. E.g. a bank employee inserts a program, into the bank�s servers, that deducts a small amount of money (say Rs. 5 a month) from the account of every customer. No account holder will probably notice this unauthorized debit, but the bank employee will make a sizeable amount of money every month.
To cite an example, an employee of a bank in USA was dismissed from his job. Disgruntled at having been supposedly mistreated by his employers the man first introduced a logic bomb into the bank�s systems. Logic bombs are programmes, which get activated on the occurrence of a particular predefined event.
The logic bomb was programmed to take ten cents from all the accounts in the bank and put them into the account of the person whose name was alphabetically the last in the bank�s rosters. Then he went and opened an account in the name of Ziegler. The amount being withdrawn from each of the accounts in the bank was so insignificant that neither any of the account holders nor the bank officials noticed the fault.
It was brought to their notice when a person by the name of Zygler opened his account in that bank. He was surprised to find a sizeable amount of money being transferred into his account every Saturday. Being an honest person, he reported the �mistake� to the bank authorities and the entire scheme was revealed.
Denial of Service attack
This involves flooding a computer resource with more requests than it can handle. This causes the resource (e.g. a web server) to crash thereby denying authorized users the service offered by the resource. Another variation to a typical denial of service attack is known as a Distributed Denial of Service (DDoS) attack wherein the perpetrators are many and are geographically widespread.
It is very difficult to control such attacks. The attack is initiated by sending excessive demands to the victim�s computer(s), exceeding the limit that the victim�s servers can support and making the servers crash. Denial-of-service attacks have had an impressive history having, in the past, brought down websites like Amazon, CNN, Yahoo and eBay!
Virus / worm attacks
Viruses are programs that attach themselves to a computer or a file and then circulate themselves to other files and to other computers on a network. They usually affect the data on a computer, either by altering or deleting it. Worms, unlike viruses do not need the host to attach themselves to. They merely make functional copies of themselves and do this repeatedly till they eat up all the available space on a computer�s memory. The VBS_LOVELETTER virus (better known as the Love Bug or the ILOVEYOU virus) was reportedly written by a Filipino undergraduate.
In May 2000, this deadly virus became the world�s most prevalent virus. It struck one in every five personal computers in the world. When the virus was brought under check the true magnitude of the losses was incomprehensible. Losses incurred during this virus attack were pegged at US $ 10 billion.
VBS_LOVELETTER utilized the addresses in Microsoft Outlook and e-mailed itself to those addresses. The e-mail which was sent out had "ILOVEYOU" in its subject line. The attachment file was named "LOVE-LETTER-FOR-YOU.TXT.vbs". People wary of opening e-mail attachments were conquered by the subject line and those who had some knowledge of viruses, did not notice the tiny .vbs extension and believed the file to be a text file. The message in the e-mail was "kindly check the attached LOVELETTER coming from me".
In addition, the Love Bug also uses the Internet Relay Chat (IRC) for its propagation. It e-mails itself to users in the same channel as the infected user.
VBS_LOVELETTER first selects certain files and then inserts its own code in lieu of the original data contained in the file. This way it creates ever-increasing versions of itself.
Probably the world�s most famous worm was the Internet worm let loose on the Internet by Robert Morris sometime in 1988. The Internet was, then, still in its developing years and this worm, which affected thousands of computers, almost brought its development to a complete halt. It took a team of experts almost three days to get rid of the worm and in the meantime many of the computers had to be disconnected from the network.
Logic bombs
These are event dependent programs. This implies that these programs are created to do something only when a certain event (known as a trigger event) occurs. E.g. even some viruses may be termed logic bombs because they lie dormant all through the year and become active only on a particular date (like the Chernobyl virus).
Trojan attacks
A Trojan as this program is aptly called, is an unauthorized program which functions from inside what seems to be an authorized program, thereby concealing what it is actually doing.
There are many simple ways of installing a Trojan in someone�s computer. To cite an example, two friends Rahul and Mukesh (names changed), had a heated argument over one girl, Radha (name changed) whom they both liked. When the girl, asked to choose, chose Mukesh over Rahul, Rahul decided to get even. On the 14th of February, he sent Mukesh a spoofed e-card, which appeared to have come from Radha�s mail account. The e-card actually contained a Trojan. As soon as Mukesh opened the card, the Trojan was installed on his computer. Rahul now had complete control over Mukesh�s computer and proceeded to harass him thoroughly.
Internet time theft
This connotes the usage by an unauthorized person of the Internet hours paid for by another person. In May 2000, the economic offences wing, IPR section crime branch of Delhi police registered its first case involving theft of Internet hours. In this case, the accused, Mukesh Gupta an engineer with Nicom System (p) Ltd. was sent to the residence of the complainant to activate his Internet connection. However, the accused used Col. Bajwa�s login name and password from various places causing wrongful loss of 100 hours to Col. Bajwa. Delhi police arrested the accused for theft of Internet time.
On further inquiry in the case, it was found that Krishan Kumar, son of an ex army officer, working as senior executive in M/s Highpoint Tours & Travels had used Col Bajwa�s login and passwords as many as 207 times from his residence and twice from his office. He confessed that Shashi Nagpal, from whom he had purchased a computer, gave the login and password to him. The police could not believe that time could be stolen. They were not aware of the concept of time-theft at all. Colonel Bajwa�s report was rejected. He decided to approach The Times of India, New Delhi. They, in turn carried a report about the inadequacy of the New Delhi Police in handling cyber crimes. The Commissioner of Police, Delhi then took the case into his own hands and the police under his directions raided and arrested Krishan Kumar under sections 379, 411, 34 of IPC and section 25 of the Indian Telegraph Act. In another case, the Economic Offences Wing of Delhi Police arrested a computer engineer who got hold of the password of an Internet user, accessed the computer and stole 107 hours of Internet time from the other person�s account. He was booked for the crime by a Delhi court during May 2000.
Web jacking
This occurs when someone forcefully takes control of a website (by cracking the password and later changing it). The actual owner of the website does not have any more control over what appears on that website. In a recent incident reported in the USA the owner of a hobby website for children received an e-mail informing her that a group of hackers had gained control over her website. They demanded a ransom of 1 million dollars from her. The owner, a schoolteacher, did not take the threat seriously. She felt that it was just a scare tactic and ignored the e-mail.
It was three days later that she came to know, following many telephone calls from all over the country, that the hackers had web jacked her website. Subsequently, they had altered a portion of the website which was entitled �How to have fun with goldfish�. In all the places where it had been mentioned, they had replaced the word �goldfish� with the word �piranhas�.
Piranhas are tiny but extremely dangerous flesh-eating fish. Many children had visited the popular website and had believed what the contents of the website suggested. These unfortunate children followed the instructions, tried to play with piranhas, which they bought from pet shops, and were very seriously injured!
Theft of computer system
This type of offence involves the theft of a computer, some part(s) of a computer or a peripheral attached to the computer.
Physically damaging a computer system
This crime is committed by physically damaging a computer or its peripherals.
� 2004,Indiaforensic Foundation, All rights reserved
Case Study Research Method in Psychology
Saul Mcleod, PhD
Editor-in-Chief for Simply Psychology
BSc (Hons) Psychology, MRes, PhD, University of Manchester
Saul Mcleod, PhD., is a qualified psychology teacher with over 18 years of experience in further and higher education. He has been published in peer-reviewed journals, including the Journal of Clinical Psychology.
Learn about our Editorial Process
Olivia Guy-Evans, MSc
Associate Editor for Simply Psychology
BSc (Hons) Psychology, MSc Psychology of Education
Olivia Guy-Evans is a writer and associate editor for Simply Psychology. She has previously worked in healthcare and educational sectors.
On This Page:
Case studies are in-depth investigations of a person, group, event, or community. Typically, data is gathered from various sources using several methods (e.g., observations & interviews).
The case study research method originated in clinical medicine (the case history, i.e., the patient’s personal history). In psychology, case studies are often confined to the study of a particular individual.
The information is mainly biographical and relates to events in the individual’s past (i.e., retrospective), as well as to significant events that are currently occurring in his or her everyday life.
The case study is not a research method, but researchers select methods of data collection and analysis that will generate material suitable for case studies.
Freud (1909a, 1909b) conducted very detailed investigations into the private lives of his patients in an attempt to both understand and help them overcome their illnesses.
This makes it clear that the case study is a method that should only be used by a psychologist, therapist, or psychiatrist, i.e., someone with a professional qualification.
There is an ethical issue of competence. Only someone qualified to diagnose and treat a person can conduct a formal case study relating to atypical (i.e., abnormal) behavior or atypical development.
Famous Case Studies
- Anna O – One of the most famous case studies, documenting psychoanalyst Josef Breuer’s treatment of “Anna O” (real name Bertha Pappenheim) for hysteria in the late 1800s using early psychoanalytic theory.
- Little Hans – A child psychoanalysis case study published by Sigmund Freud in 1909 analyzing his five-year-old patient Herbert Graf’s house phobia as related to the Oedipus complex.
- Bruce/Brenda – Gender identity case of the boy (Bruce) whose botched circumcision led psychologist John Money to advise gender reassignment and raise him as a girl (Brenda) in the 1960s.
- Genie Wiley – Linguistics/psychological development case of the victim of extreme isolation abuse who was studied in 1970s California for effects of early language deprivation on acquiring speech later in life.
- Phineas Gage – One of the most famous neuropsychology case studies analyzes personality changes in railroad worker Phineas Gage after an 1848 brain injury involving a tamping iron piercing his skull.
Clinical Case Studies
- Studying the effectiveness of psychotherapy approaches with an individual patient
- Assessing and treating mental illnesses like depression, anxiety disorders, PTSD
- Neuropsychological cases investigating brain injuries or disorders
Child Psychology Case Studies
- Studying psychological development from birth through adolescence
- Cases of learning disabilities, autism spectrum disorders, ADHD
- Effects of trauma, abuse, deprivation on development
Types of Case Studies
- Explanatory case studies : Used to explore causation in order to find underlying principles. Helpful for doing qualitative analysis to explain presumed causal links.
- Exploratory case studies : Used to explore situations where an intervention being evaluated has no clear set of outcomes. It helps define questions and hypotheses for future research.
- Descriptive case studies : Describe an intervention or phenomenon and the real-life context in which it occurred. It is helpful for illustrating certain topics within an evaluation.
- Multiple-case studies : Used to explore differences between cases and replicate findings across cases. Helpful for comparing and contrasting specific cases.
- Intrinsic : Used to gain a better understanding of a particular case. Helpful for capturing the complexity of a single case.
- Collective : Used to explore a general phenomenon using multiple case studies. Helpful for jointly studying a group of cases in order to inquire into the phenomenon.
Where Do You Find Data for a Case Study?
There are several places to find data for a case study. The key is to gather data from multiple sources to get a complete picture of the case and corroborate facts or findings through triangulation of evidence. Most of this information is likely qualitative (i.e., verbal description rather than measurement), but the psychologist might also collect numerical data.
1. Primary sources
- Interviews – Interviewing key people related to the case to get their perspectives and insights. The interview is an extremely effective procedure for obtaining information about an individual, and it may be used to collect comments from the person’s friends, parents, employer, workmates, and others who have a good knowledge of the person, as well as to obtain facts from the person him or herself.
- Observations – Observing behaviors, interactions, processes, etc., related to the case as they unfold in real-time.
- Documents & Records – Reviewing private documents, diaries, public records, correspondence, meeting minutes, etc., relevant to the case.
2. Secondary sources
- News/Media – News coverage of events related to the case study.
- Academic articles – Journal articles, dissertations etc. that discuss the case.
- Government reports – Official data and records related to the case context.
- Books/films – Books, documentaries or films discussing the case.
3. Archival records
Searching historical archives, museum collections and databases to find relevant documents, visual/audio records related to the case history and context.
Public archives like newspapers, organizational records, photographic collections could all include potentially relevant pieces of information to shed light on attitudes, cultural perspectives, common practices and historical contexts related to psychology.
4. Organizational records
Organizational records offer the advantage of often having large datasets collected over time that can reveal or confirm psychological insights.
Of course, privacy and ethical concerns regarding confidential data must be navigated carefully.
However, with proper protocols, organizational records can provide invaluable context and empirical depth to qualitative case studies exploring the intersection of psychology and organizations.
- Organizational/industrial psychology research : Organizational records like employee surveys, turnover/retention data, policies, incident reports etc. may provide insight into topics like job satisfaction, workplace culture and dynamics, leadership issues, employee behaviors etc.
- Clinical psychology : Therapists/hospitals may grant access to anonymized medical records to study aspects like assessments, diagnoses, treatment plans etc. This could shed light on clinical practices.
- School psychology : Studies could utilize anonymized student records like test scores, grades, disciplinary issues, and counseling referrals to study child development, learning barriers, effectiveness of support programs, and more.
How do I Write a Case Study in Psychology?
Follow specified case study guidelines provided by a journal or your psychology tutor. General components of clinical case studies include: background, symptoms, assessments, diagnosis, treatment, and outcomes. Interpreting the information means the researcher decides what to include or leave out. A good case study should always clarify which information is the factual description and which is an inference or the researcher’s opinion.
1. Introduction
- Provide background on the case context and why it is of interest, presenting background information like demographics, relevant history, and presenting problem.
- Compare briefly to similar published cases if applicable. Clearly state the focus/importance of the case.
2. Case Presentation
- Describe the presenting problem in detail, including symptoms, duration,and impact on daily life.
- Include client demographics like age and gender, information about social relationships, and mental health history.
- Describe all physical, emotional, and/or sensory symptoms reported by the client.
- Use patient quotes to describe the initial complaint verbatim. Follow with full-sentence summaries of relevant history details gathered, including key components that led to a working diagnosis.
- Summarize clinical exam results, namely orthopedic/neurological tests, imaging, lab tests, etc. Note actual results rather than subjective conclusions. Provide images if clearly reproducible/anonymized.
- Clearly state the working diagnosis or clinical impression before transitioning to management.
3. Management and Outcome
- Indicate the total duration of care and number of treatments given over what timeframe. Use specific names/descriptions for any therapies/interventions applied.
- Present the results of the intervention,including any quantitative or qualitative data collected.
- For outcomes, utilize visual analog scales for pain, medication usage logs, etc., if possible. Include patient self-reports of improvement/worsening of symptoms. Note the reason for discharge/end of care.
4. Discussion
- Analyze the case, exploring contributing factors, limitations of the study, and connections to existing research.
- Analyze the effectiveness of the intervention,considering factors like participant adherence, limitations of the study, and potential alternative explanations for the results.
- Identify any questions raised in the case analysis and relate insights to established theories and current research if applicable. Avoid definitive claims about physiological explanations.
- Offer clinical implications, and suggest future research directions.
5. Additional Items
- Thank specific assistants for writing support only. No patient acknowledgments.
- References should directly support any key claims or quotes included.
- Use tables/figures/images only if substantially informative. Include permissions and legends/explanatory notes.
- Provides detailed (rich qualitative) information.
- Provides insight for further research.
- Permitting investigation of otherwise impractical (or unethical) situations.
Case studies allow a researcher to investigate a topic in far more detail than might be possible if they were trying to deal with a large number of research participants (nomothetic approach) with the aim of ‘averaging’.
Because of their in-depth, multi-sided approach, case studies often shed light on aspects of human thinking and behavior that would be unethical or impractical to study in other ways.
Research that only looks into the measurable aspects of human behavior is not likely to give us insights into the subjective dimension of experience, which is important to psychoanalytic and humanistic psychologists.
Case studies are often used in exploratory research. They can help us generate new ideas (that might be tested by other methods). They are an important way of illustrating theories and can help show how different aspects of a person’s life are related to each other.
The method is, therefore, important for psychologists who adopt a holistic point of view (i.e., humanistic psychologists ).
Limitations
- Lacking scientific rigor and providing little basis for generalization of results to the wider population.
- Researchers’ own subjective feelings may influence the case study (researcher bias).
- Difficult to replicate.
- Time-consuming and expensive.
- The volume of data, together with the time restrictions in place, impacted the depth of analysis that was possible within the available resources.
Because a case study deals with only one person/event/group, we can never be sure if the case study investigated is representative of the wider body of “similar” instances. This means the conclusions drawn from a particular case may not be transferable to other settings.
Because case studies are based on the analysis of qualitative (i.e., descriptive) data , a lot depends on the psychologist’s interpretation of the information she has acquired.
This means that there is a lot of scope for Anna O , and it could be that the subjective opinions of the psychologist intrude in the assessment of what the data means.
For example, Freud has been criticized for producing case studies in which the information was sometimes distorted to fit particular behavioral theories (e.g., Little Hans ).
This is also true of Money’s interpretation of the Bruce/Brenda case study (Diamond, 1997) when he ignored evidence that went against his theory.
Breuer, J., & Freud, S. (1895). Studies on hysteria . Standard Edition 2: London.
Curtiss, S. (1981). Genie: The case of a modern wild child .
Diamond, M., & Sigmundson, K. (1997). Sex Reassignment at Birth: Long-term Review and Clinical Implications. Archives of Pediatrics & Adolescent Medicine , 151(3), 298-304
Freud, S. (1909a). Analysis of a phobia of a five year old boy. In The Pelican Freud Library (1977), Vol 8, Case Histories 1, pages 169-306
Freud, S. (1909b). Bemerkungen über einen Fall von Zwangsneurose (Der “Rattenmann”). Jb. psychoanal. psychopathol. Forsch ., I, p. 357-421; GW, VII, p. 379-463; Notes upon a case of obsessional neurosis, SE , 10: 151-318.
Harlow J. M. (1848). Passage of an iron rod through the head. Boston Medical and Surgical Journal, 39 , 389–393.
Harlow, J. M. (1868). Recovery from the Passage of an Iron Bar through the Head . Publications of the Massachusetts Medical Society. 2 (3), 327-347.
Money, J., & Ehrhardt, A. A. (1972). Man & Woman, Boy & Girl : The Differentiation and Dimorphism of Gender Identity from Conception to Maturity. Baltimore, Maryland: Johns Hopkins University Press.
Money, J., & Tucker, P. (1975). Sexual signatures: On being a man or a woman.
Further Information
- Case Study Approach
- Case Study Method
- Enhancing the Quality of Case Studies in Health Services Research
- “We do things together” A case study of “couplehood” in dementia
- Using mixed methods for evaluating an integrative approach to cancer care: a case study
Related Articles
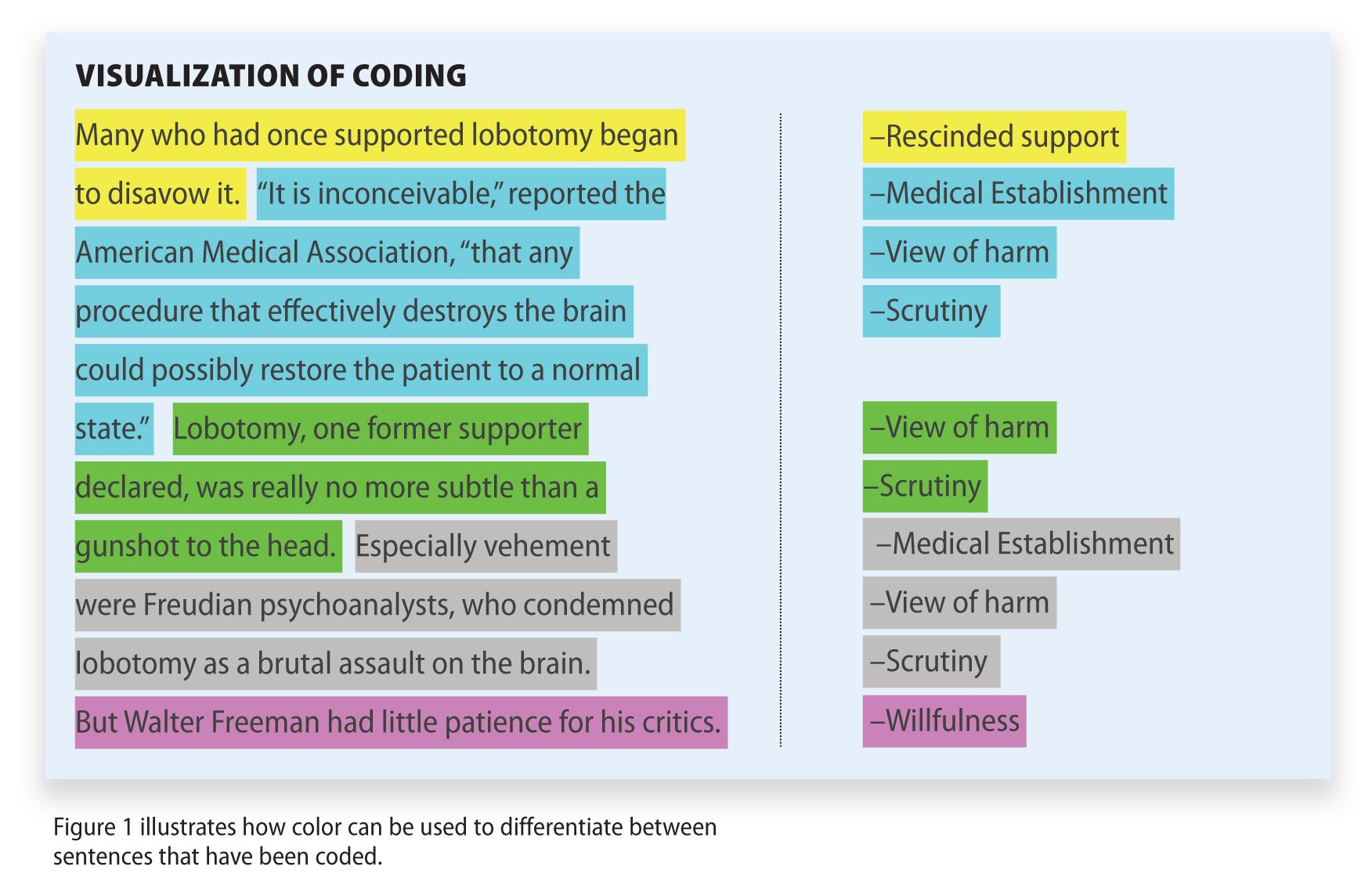
Research Methodology
Qualitative Data Coding

What Is a Focus Group?
Cross-Cultural Research Methodology In Psychology

What Is Internal Validity In Research?

Research Methodology , Statistics
What Is Face Validity In Research? Importance & How To Measure

Criterion Validity: Definition & Examples
- SUGGESTED TOPICS
- The Magazine
- Newsletters
- Managing Yourself
- Managing Teams
- Work-life Balance
- The Big Idea
- Data & Visuals
- Reading Lists
- Case Selections
- HBR Learning
- Topic Feeds
- Account Settings
- Email Preferences
How One Company Added Carbon Estimates to Its Customer Invoices
- Robert S. Kaplan
- Timmy Melotte

A four-step playbook to help businesses increase transparency and reduce emissions.
Soprema is an international building materials supplier, producing millions of square meters of waterproofing, insulating, and roofing products each year. In 2022, Pierre-Etienne Bindschedler, the company’s president and third-generation owner, committed to reporting the carbon footprint of each product on every customer invoice, and to help customers reduce the embedded GHG emissions in the products they purchased. Paper co-author Melotte, an experienced operations director, was selected to lead a pilot project to measure and subsequently lower the carbon embedded in its products. Melotte decided to follow the E-Liability Pilot Playbook, which divides a pilot project into four stages: Project Design, Data Collection; Data Analysis, and Action. This article describes how the pilot, which focused on the company’s bitumen waterproofing systems, unfolded at Soprema. The company estimates a potential carbon footprint reduction of 34% from the project.
In 2022, Pierre-Etienne Bindschedler, the president and third-generation owner of Soprema, set a goal to develop sustainable solutions for customers. Soprema is a multi-product, family-owned business in the middle of the building materials value chain and produces millions of square meters of waterproofing, insulating, and roofing products each year. Bindschedler wanted to report the carbon footprint of each product on every customer invoice, and to help customers reduce the embedded GHG emissions in the products they purchased.
- Robert S. Kaplan is a senior fellow and the Marvin Bower Professor of Leadership Development emeritus at Harvard Business School. He coauthored the McKinsey Award–winning HBR article “ Accounting for Climate Change ” (November–December 2021).
- TM Timmy Melotte is an Operational Excellence Director for Soprema International, a building materials supplier based in Limburg, Belgium
Partner Center

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
JavaScript appears to be disabled on this computer. Please click here to see any active alerts .
EPA Transcriptomic Assessment Product (ETAP) and Value of Information (VOI) Case Study
EPA’s Safer Chemicals Research aims to address the challenge of needing more chemical information to make informed, risk-based decisions. Less than a quarter of the tens of thousands of chemicals in commerce--as well as those found in the environment, various waste streams, and the human body--have traditional toxicity or epidemiological data that can inform human health risk assessments. To address the challenge, researchers developed the EPA Transcriptomic Assessment Product (ETAP). ETAP is a novel human health assessment approach targeting chemicals lacking traditional toxicity testing data. To accompany the ETAP, EPA also conducted a Value of Information (VOI) analysis to weigh the public health and economic trade-offs associated with the timeliness, uncertainty, and costs of the ETAP compared to traditional toxicity tests.
EPA Transcriptomic Assessment Product (ETAP)
Value of information (voi) analysis.
- Expected Results
A human health assessment or science assessment is typically the hazard identification and dose-response analysis that produces a reference value for the chemical. This, along with exposure information, is foundational for a risk assessment .
One reason for the limited number of human health assessments, and subsequent risk assessments, is traditional toxicity testing and human health assessments for a chemical are time and resource intensive--often taking eight or more years to complete. State agencies, the public, and various stakeholder organizations are in need of toxicity values for data poor chemicals in a shorter timeframe in order to take an informed action to protect human health.
The draft EPA Transcriptomic Assessment Product (ETAP) aims to help address chemicals lacking traditional toxicity testing data in a more timely way. The primary driver for this new assessment product is the lack of human health toxicity values for most chemicals under the EPA regulatory purview. The ETAP transcriptomic-based reference values can be developed and reported in a 6–9-month timeframe, providing key data to the Agency that may facilitate more timely regulatory decision-making. ETAP is currently undergoing a Board of Scientific Counselors (BOSC) and public comment review.
" Transcriptomics " is the study of messenger RNA molecules expressed in a cell or tissue, and it takes advantage of technology from the human genome project tha t allows for a comprehensive evaluation of changes in gene activity. Previous studies have demonstrated that doses of chemicals causing disruption of gene activity are highly correlated with doses causing toxicological responses in traditional animal toxicity tests. Costs associated with the RNA sequencing technology have fallen significantly, making it more accessible and enabling broad application to environmental issues.
Read the draft reports:
- Standard Methods for Development of ETAPs (pdf) (3.1 MB)
- Scientific Studies Supporting Development of Transcriptomic Points of Departure for EPA Transcriptomic Assessment Products (ETAPs) (pdf) (2.3 MB)
EPA developed a Value of Information (VOI) decision frameworks to evaluate the ETAP compared to toxicity testing in traditional human health assessments. VOI analysis was listed as a recommendation in the 2009 NAS report Science and Decisions to provide EPA a more objective decision framework in assessing the trade-offs of time, uncertainty, and cost for a variety of chemical exposure scenarios and decision contexts.
This socio-economic analysis compares the public health (i.e., societal health benefits) and economic trade-offs associated with the ETAP as compared to traditional toxicity testing and human health assessment.
The VOI results suggest a more timely new assessment product, like the ETAP, has significant public health and economic benefits compared with the traditional toxicity testing and human health assessment process.
Read the draft report:
- VOI Case Study Report (pdf) (3.1 MB)
- VOI Case Study Supplemental Material (pdf) (1.4 MB)
Results and Future Directions
The goal of the draft ETAP is to develop and operationalize a new process for timely human health assessment for chemicals that lack human health toxicity data. Once the chemical of interest is in the lab, an ETAP can be completed in less than a year. In the reports developed by the EPA for scientific peer review, a literature review and transcriptomic dose response analysis studies showed high concordance between transcriptomic and apical benchmark dose (BMD) values in traditional animal toxicity studies. The concordance was robust across species, sex, route of exposure, physical chemical properties, toxicokinetic half-life, and technology platform. The error associated with the concordance between the transcriptomic and apical BMD values was demonstrated to be approximately equivalent to the combined inter-study variability associated with the transcriptomic study and the two-year rodent bioassay.
In July 2023, EPA solicited public comment and held two separate ad hoc Board of Scientific Counselors (BOSC) panels met to review the ETAP and VOI materials. After these reviews, EPA will respond to comments, finalize and publish these reports.
- Board of Scientific Counselors (BOSC) EPA Transcriptomic Assessment Products (ETAP) Panel
- Board of Scientific Counselors (BOSC) Value of Information (VOI) Panel
- Standard Methods
- Value of Information Case Study
- Assessments
- Open access
- Published: 24 May 2024
Integration of case-based learning and three-dimensional printing for tetralogy of fallot instruction in clinical medical undergraduates: a randomized controlled trial
- Jian Zhao 1 na1 ,
- Xin Gong 1 na1 ,
- Jian Ding 1 ,
- Kepin Xiong 2 ,
- Kangle Zhuang 3 ,
- Rui Huang 1 ,
- Shu Li 4 &
- Huachun Miao 1
BMC Medical Education volume 24 , Article number: 571 ( 2024 ) Cite this article
65 Accesses
Metrics details
Case-based learning (CBL) methods have gained prominence in medical education, proving especially effective for preclinical training in undergraduate medical education. Tetralogy of Fallot (TOF) is a congenital heart disease characterized by four malformations, presenting a challenge in medical education due to the complexity of its anatomical pathology. Three-dimensional printing (3DP), generating physical replicas from data, offers a valuable tool for illustrating intricate anatomical structures and spatial relationships in the classroom. This study explores the integration of 3DP with CBL teaching for clinical medical undergraduates.
Sixty senior clinical medical undergraduates were randomly assigned to the CBL group and the CBL-3DP group. Computed tomography imaging data from a typical TOF case were exported, processed, and utilized to create four TOF models with a color 3D printer. The CBL group employed CBL teaching methods, while the CBL-3DP group combined CBL with 3D-printed models. Post-class exams and questionnaires assessed the teaching effectiveness of both groups.
The CBL-3DP group exhibited improved performance in post-class examinations, particularly in pathological anatomy and TOF imaging data analysis ( P < 0.05). Questionnaire responses from the CBL-3DP group indicated enhanced satisfaction with teaching mode, promotion of diagnostic skills, bolstering of self-assurance in managing TOF cases, and cultivation of critical thinking and clinical reasoning abilities ( P < 0.05). These findings underscore the potential of 3D printed models to augment the effectiveness of CBL, aiding students in mastering instructional content and bolstering their interest and self-confidence in learning.
The fusion of CBL with 3D printing models is feasible and effective in TOF instruction to clinical medical undergraduates, and worthy of popularization and application in medical education, especially for courses involving intricate anatomical components.
Peer Review reports
Tetralogy of Fallot (TOF) is the most common cyanotic congenital heart disease(CHD) [ 1 ]. Characterized by four structural anomalies: ventricular septal defect (VSD), pulmonary stenosis (PS), right ventricular hypertrophy (RVH), and overriding aorta (OA), TOF is a focal point and challenge in medical education. Understanding anatomical spatial structures is pivotal for learning and mastering TOF [ 2 ]. Given the constraints of course duration, medical school educators aim to provide students with a comprehensive and intuitive understanding of the disease within a limited timeframe [ 3 ].
The case-based learning (CBL) teaching model incorporates a case-based instructional approach that emphasizes typical clinical cases as a guide in student-centered and teacher-facilitated group discussions [ 4 ]. The CBL instructional methods have garnered widespread attention in medical education as they are particularly appropriate for preclinical training in undergraduate medical education [ 5 , 6 ]. The collection of case data, including medical records and examination results, is essential for case construction [ 7 ]. The anatomical and hemodynamic consequences of TOF can be determined using ultrasonography, computed tomography (CT), and magnetic resonance imaging techniques. However, understanding the anatomical structures from imaging data is a slow and challenging psychological reconstruction process for undergraduate medical students [ 8 ]. Three-dimensional (3D) visualization is valuable for depicting anatomical structures [ 9 ]. 3D printing (3DP), which creates physical replicas based on data, facilitates the demonstration of complex anatomical structures and spatial relationships in the classroom [ 10 ].
During the classroom session, 3D-printed models offer a convenient means for hands-on demonstration and communication, similar to facing a patient, enhancing the efficiency and specificity of intra-team communication and discussion [ 11 ]. In this study, we printed TOF models based on case imaging data, integrated them into CBL teaching, and assessed the effectiveness of classroom instruction.
Research participants
The study employed a prospective, randomized controlled design which received approval from the institutional ethics committee. Senior undergraduate students majoring in clinical medicine at Wannan Medical College were recruited for participation based on predefined inclusion criteria. The researchers implemented recruitment according to the recruitment criteria by contacting the class leaders of the target classes they had previously taught. Notably, these students were in their third year of medical education, with anticipation of progressing to clinical courses in the fourth year, encompassing Internal Medicine, Surgery, Obstetrics, Gynecology, and Pediatrics. Inclusion criteria for participants encompassed the following: (1) proficient communication and comprehension abilities, (2) consistent attendance without absenteeism or truancy, (3) absence of failing grades in prior examinations, and (4) capability to conscientiously fulfill assigned learning tasks. Exclusion criteria were (1) absence from lectures, (2) failure to complete pre-and post-tests, and (3) inadequate completion of questionnaires. For their participation in the study, Students were provided access to the e-book “Localized Anatomy,” authored by the investigators, as an incentive for their participation. Voluntary and anonymous participation was emphasized, with participants retaining the right to withdraw from the study at any time without providing a reason.
The study was conducted between May 1st, 2023, and June 30, 2023, from recruitment to completion of data collection. Drawing upon insights gained from a previous analogous investigation which yielded an effect size of 0.95 [ 10 ]. Sample size was computed, guided by a statistical consultant, with the aim of 0.85 power value, predicated on an effect size of 0.8 and a margin of error set at 0.05. A minimum of 30 participants per group was calculated using G*Power software (latest ver. 3.1.9.7; Heinrich-Heine-Universität Düsseldorf, Düsseldorf, Germany), resulting in the recruitment of a total of 60 undergraduate students. Each participant was assigned an identification number, with codes placed in boxes. Codes drawn from the boxes determined allocation to either the CBL group or the CBL-3DP group. Subsequently, participants were randomly assigned to either the CBL group, receiving instruction utilizing the CBL methodology, or the CBL-3DP group, which received instruction integrating both CBL and 3D Printed models.
Printing of TOF models
Figure 1 A shows the printing flowchart of the TOF models. A typical TOF case was collected from the Yijishan Hospital of Wannan Medical College. The CT angiography imaging data of the case was exported. Mimics Research 20.0 software (Mimics Innovation Suite version 20, Materialize, Belgium) was used for data processing. The cardiovascular module of the CT-Heart tool was employed to adjust the threshold range, independently obtain the cardiac chambers and vessels, post-process the chambers and vessels to generate a hollow blood pool, and merge it with the myocardial volume to construct a complete heart model. The file was imported into Magics 24.0 software (version 24.0; Materialize, Belgium) for correction using the Shell tool page. After repairs, the model entered the smoothing page, where tools such as triangular surface simplification, local smoothing, refinement and smoothing, subdivision of components, and mesh painting were utilized to achieve varying degrees of smoothness. Finally, optimized data were obtained and exported as stereolithography (STL) files. An experienced cardiothoracic surgeon validated the anatomical accuracy of the digital model.
The STL files were imported into a 3D printer (J401Pro; Sailner 3D Technology, China) for model printing. This printer can produce full-color medical models using different materials. The models were fabricated using two distinct materials: rigid and flexible. Both materials are suitable for the observational discussion of the teaching objectives outlined in our study. From the perspective of observing pathological changes in the TOF, there is no significant difference between the two materials.
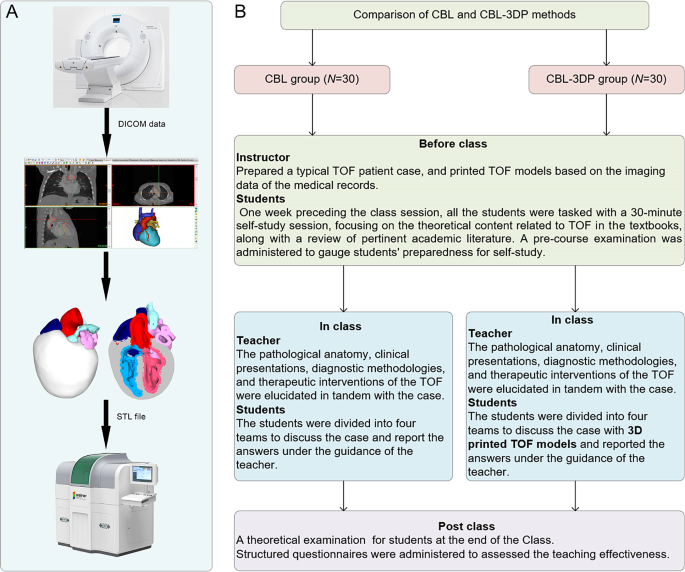
Experimental flow chart of this study. A TOF model printing flow chart. B The instructional framework
Teaching implementation
Figure 1 B illustrates the instructional framework employed in this study. One week preceding the class session, all the students were tasked with a 30-minute self-study session, focusing on the theoretical content related to TOF as outlined in the Pediatrics and Surgery textbooks, along with a review of pertinent academic literature. Both groups received co-supervision from two basic medicine lecturers boasting over a decade of teaching experience, alongside a senior cardiothoracic surgeon. Teaching conditions remained consistent across groups, encompassing uniform assessment criteria and adherence to predefined teaching time frames, all conducted in a Project-Based Learning (PBL) classroom at Wannan Medical College. Additionally, a pre-course examination was administered to gauge students’ preparedness for self-study.
In adherence to the curriculum guidelines, the teaching objectives aimed to empower students to master TOF’s clinical manifestations, diagnostic modalities, and differential diagnoses, while acquainting them with treatment principles and surgical methodologies. Additionally, the objectives sought to cultivate students’ clinical reasoning abilities and problem-solving skills. the duration of instruction for the TOF theory session was standardized to 25 min. The didactic content was integrated with the TOF case study to construct a coherent pedagogical structure.
During the instructional session, both groups underwent teaching utilizing the CBL methodology. Clinical manifestations and case details of TOF cases were presented to stimulate students’ interest and curiosity. Subsequently, the theory of TOF, including its etiology, pathogenesis, pathologic anatomy, clinical manifestations, diagnostic methods, and therapeutic interventions, was briefly elucidated. Emphasis was then placed on the case, wherein selected typical TOF cases were explained, guiding students in analysis and discussion. Students were organized into four teams under the instructors’ supervision, fostering cooperative learning and communication, thereby deepening their understanding of the disease through continuous inquiry and exploration (Fig. 2 L). In the routinely equipped PBL classroom with standard heart models (Fig. 2 J, K), all students had prior exposure to human anatomy and were familiar with these models. Both groups were provided with four standard heart models for reference, while the CBL-3DP group received additional four 3D-printed models depicting TOF anomalies, enriching their learning experience (Fig. 2 D, G). After the lesson, summarization, and feedback sessions were conducted to consolidate group discussions’ outcomes, evaluate teaching effectiveness, and assess learning outcomes.
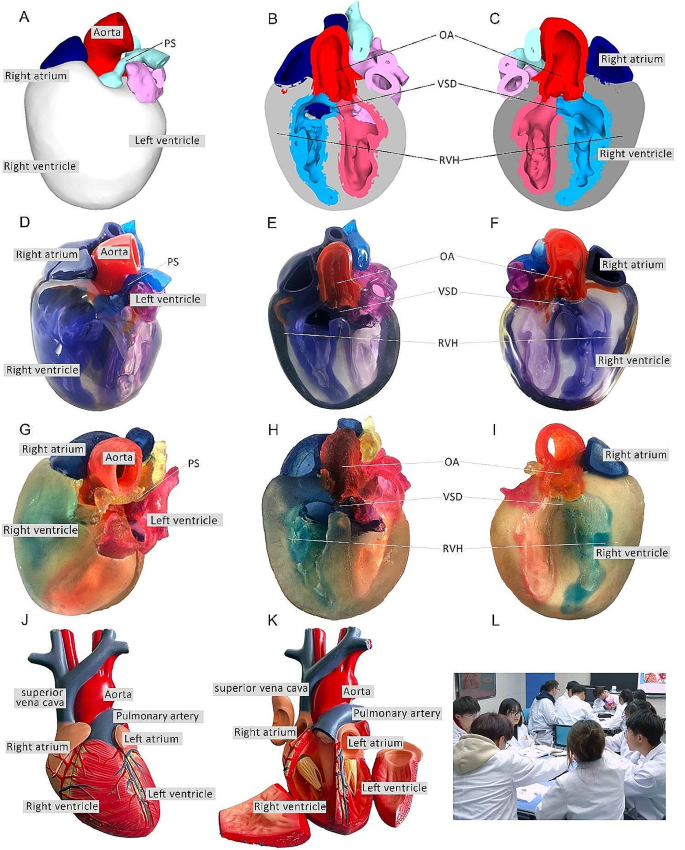
Heart models utilized in instructional sessions. A External perspective of 3D digital models. B, C Cross-sectional views following trans-septal sagittal dissection of the 3D digital model (PS: Pulmonary Stenosis; OA: Overriding Aorta; VSD: Ventricular Septal Defect; RVH: Right Ventricular Hypertrophy). D External depiction of rigid 3D printed model. E, F Sagittal sections of the rigid 3D printed model. G External portrayal of flexible 3D printed model. H, I Sagittal sections of the flexible 3D printed model. J, K The normal heart model employed in the instruction of the CBL group. L Ongoing classroom session
Teaching effectiveness assessment
Following the instructional session, participants from the two groups underwent a theoretical examination to assess their comprehension of the taught material. This assessment covered domains such as pathological anatomy, clinical manifestations, imaging data interpretation, diagnosis, and treatment relevant to TOF. Additionally, structured questionnaires were administered to evaluate the efficacy of the pedagogical approach employed. The questionnaire consisted of six questions designed to gauge participants’ understanding of the teaching content, enhancement of diagnostic skills, cultivation of critical thinking and clinical reasoning abilities, bolstering of confidence in managing TOF cases, satisfaction with the teaching mode, and satisfaction with the CBL methodology.
The questionnaire employed a 5-point Likert scale to gauge responses, with 5 indicating “strongly satisfied/agree,” 4 for “satisfied/agree,” 3 denoting “neutral,” 2 reflecting “dissatisfied/disagree,” and 1 indicating “strongly dissatisfied/disagree.” It comprised six questions, with the initial two probing participants’ knowledge acquisition, questions 3 and 4 exploring satisfaction regarding enhanced competence, and the final two assessing satisfaction with teaching methods and modes. Additionally, participants were encouraged to provide suggestions at the end of the questionnaire. To ensure the questionnaire’s validity, five esteemed lecturers in basic medical sciences with more than 10 years of experience verified its content and assessed its Content Validity Ratio and Content Validity Index to ensure alignment with the study’s objectives.
Statistical analysis
Statistical analyses were conducted utilizing GraphPad Prism 9.0 software. Aggregate score data for both groups were presented as mean ± standard deviation (x ± s). The gender comparisons were analyzed with the chi-square (χ2) test, while the other variables were compared using the Mann-Whitney U test. The threshold for determining statistical significance was set at P < 0.05.
Three-dimensional printing models
After configuring the structural colors of each component (Fig. 2 A, B, C), we printed four color TOF models using both rigid and flexible materials, resulting in four life-sized TOF models. Two color TOF models were created using rigid materials (Fig. 2 D, E, F). These models, exhibiting resistance to deformation, and with a firm texture, smooth and glossy surface, and good transparency, allowing visibility of the internal structures, were deemed conducive to teaching and observation. We also fabricated two color TOF models using flexible materials (Fig. 2 G, H, I), characterized by soft texture, opacity, and deformability, allowing for easy manipulation and cutting. It has potential utility beyond observational purposes. It can serve as a valuable tool for simulating surgical interventions and may be employed to create tomographic anatomical specimens. In this study, both material models were suitable for observation in the classroom. The participants were able to discern the four pathological changes characteristic of TOF from surface examination or cross-sectional analysis.
Baseline characteristics of the students
In total, 60 students were included in this study. The CBL group comprised 30 students (14 males and 16 females), with an average age of (21.20 ± 0.76) years. The CBL-3DP group consisted of 30 students (17 males and 13 females) with an average age of 20.96 years. All the students completed the study procedures. There were no significant differences in age, sex ratio, or pre-class exam scores between the two groups ( P > 0.05), indicating that the baseline scores between the two groups were comparable (Table 1 ).
Theoretical examination results
All students completed the research procedures as planned. The post-class theoretical examination encompassed assessment of pathological anatomy, clinical presentations, imaging data interpretation, diagnosis, and treatment pertinent to TOF. Notably, no statistically significant disparities were observed in the scores on clinical manifestations, diagnosis and treatment components between the cohorts, as delineated in Table 2 . Conversely, discernible distinctions were evident whereby the CBL-3DP group outperformed the CBL group notably in pathological anatomy, imaging data interpretation, and overall aggregate scores ( P < 0.05).
Results of the questionnaires
All the 60 participants submitted the questionnaire. Comparing the CBL and CBL-3DP groups, the scores from the CBL-3DP group showed significant improvements in many areas. This included satisfaction with the teaching mode, promotion of diagnostic skills, bolstering of self-assurance in managing TOF cases, and cultivation of critical thinking and clinical reasoning abilities (Fig. 3 B, C, D, E). All of which improved significantly ( P < 0.05 for the first aspects and P < 0.01 for the rest). However, the two groups were not comparable ( P > 0.05) in terms of understanding of the teaching content and Satisfaction with the CBL methodology (Fig. 3 A, F).
Upon completion of the questionnaires, participants were invited to proffer recommendations. Notably, in the CBL group, seven students expressed challenges in comprehending TOF and indicated a need for additional time for consolidation to enhance understanding. Conversely, within the CBL-3DP group, twelve students advocated for the augmentation of model repertoire and the expansion of disease-related data collection to bolster pedagogical efficacy across other didactic domains.
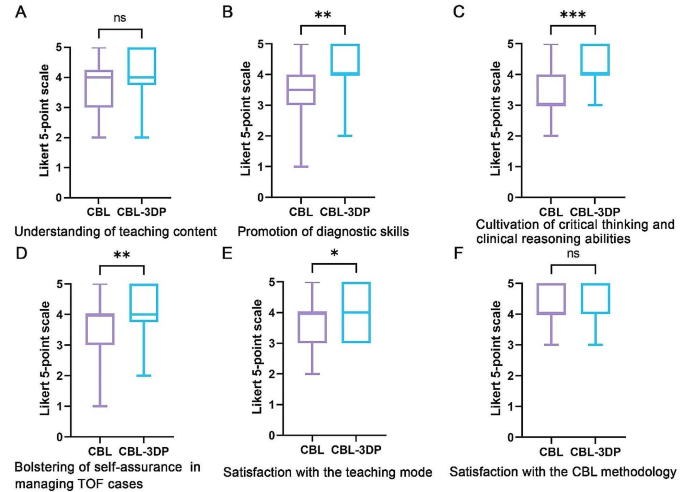
Five-point Likert scores of students’ attitudes in CBL ( n = 30) and CBL-3DP ( n = 30) groups. A Understanding of teaching content. B Promotion of diagnostic skills. C Cultivation of critical thinking and clinical reasoning abilities. D Bolstering of self-assurance in managing TOF cases. E Satisfaction with the teaching mode. F Satisfaction with the CBL methodology. ns No significant difference, * p < 0.05, ** p < 0.01, *** p < 0.001
TOF presents a significant challenge in clinical practice, necessitating a comprehensive understanding for effective diagnosis and treatment [ 12 ]. Traditional teaching methods in medical schools have relied on conventional resources such as textbooks, 2D illustrations, cadaver dissections, and radiographic materials to impart knowledge about complex conditions like TOF [ 13 ]. However, the limitations of these methods in fully engaging students and bridging the gap between theoretical knowledge and practical application have prompted a need for innovative instructional approaches.
CBL has emerged as a valuable tool in medical education, offering students opportunities to engage with authentic clinical cases through group discussions and inquiry-based learning [ 14 ]. By actively involving students in problem-solving and decision-making processes, CBL facilitates the application of theoretical knowledge to real-world scenarios, thus better-preparing students for future clinical practice [ 15 ]. Our investigation revealed that both groups of students exhibited comparable levels of satisfaction with the CBL methodology, devoid of discernible disparities.
CHD presents a formidable challenge due to the intricate nature of anatomical anomalies, the diverse spectrum of conditions, and individual variations [ 16 ]. Utilizing 3D-printed physical models, derived from patient imaging data, can significantly enhance comprehension of complex anatomical structures [ 17 ]. These models have proven invaluable in guiding surgical planning, providing training for junior or inexperienced pediatric residents, and educating healthcare professionals and parents of patients [ 18 ]. Studies indicate that as much as 50% of pediatric surgical decisions can be influenced by the insights gained from 3D printed models [ 19 ]. By providing tangible, anatomically accurate models, 3D printing offers a unique opportunity for people to visualize complex structures and enhance their understanding of anatomical intricacies. Our study utilized full-color, to-scale 3D printed models to illustrate the structural abnormalities associated with TOF, thereby enriching classroom sessions and facilitating a deeper comprehension of the condition.
Comparative analysis between the CBL-3DP group and the CBL group revealed significant improvements in post-test performance, particularly in pathological anatomy and imaging data interpretation. Additionally, questionnaire responses indicated higher levels of satisfaction and confidence among students in the CBL-3DP group, highlighting the positive impact of incorporating 3D printed models into the learning environment, improving the effectiveness of CBL classroom instruction. Despite the merits, our study has limitations. Primarily, participants were exclusively drawn from the same grade level within a single college, possibly engendering bias owing to shared learning backgrounds. Future research could further strengthen these findings by expanding the sample size and including long-term follow-up to assess the retention of knowledge and skills. Additionally, the influence of the 3D models depicting a normal heart on the learning process and its potential to introduce bias into the results warrants consideration, highlighting a need for scrutiny in subsequent studies.
As medical science continues to advance, the need for effective teaching methods becomes increasingly paramount. Our study underscores the potential of combining active learning approaches like CBL with innovative technologies such as 3D printing to enhance teaching effectiveness, improve knowledge acquisition, and foster students’ confidence and enthusiasm in pursuing clinical careers. Moving forward, further research and integration of such methodologies are essential for meeting the evolving demands of medical education, especially in areas involving complex anatomical understanding.
Conclusions
Integrating 3D-printed models with the CBL method is feasible and effective in TOF instruction. The demonstrated success of this method warrants broad implementation in medical education, particularly for complex anatomical topics.
Data availability
All data supporting the conclusions of this research are available upon reasonable request from the corresponding author.
Apitz C, Webb GD, Redington AN. Tetralogy of Fallot. Lancet. 2009;374:1462–71.
Article Google Scholar
Ghosh RM, Jolley MA, Mascio CE, Chen JM, Fuller S, Rome JJ, et al. Clinical 3D modeling to guide pediatric cardiothoracic surgery and intervention using 3D printed anatomic models, computer aided design and virtual reality. 3D Print Med. 2022;8:11.
Chakrabarti R, Wardle K, Wright T, Bennie T, Gishen F. Approaching an undergraduate medical curriculum map: challenges and expectations. BMC Med Educ. 2021;21:341.
Donkin R, Yule H, Fyfe T. Online case-based learning in medical education: a scoping review. BMC Med Educ. 2023;23:564.
Novack JP. Designing cases for case-based immunology teaching in large medical school classes. Front Immunol. 2020;11:995.
Chen HC, Van Den Broek WES, Ten Cate O. The case for use of entrustable professional activities in undergraduate medical education. Acad Med. 2015;90:431–6.
Wang M, Sun Z, Jia M, Wang Y, Wang H, Zhu X, et al. Intelligent virtual case learning system based on real medical records and natural language processing. BMC Med Inf Decis Mak. 2022;22:60.
Yoo S-J, Thabit O, Kim EK, Ide H, Yim D, Dragulescu A, et al. 3D printing in medicine of congenital heart diseases. 3D Print Med. 2015;2:3.
Yammine K, Violato C. A meta-analysis of the educational effectiveness of three-dimensional visualization technologies in teaching anatomy. Anat Sci Educ. 2015;8:525–38.
Miao H, Ding J, Gong X, Zhao J, Li H, Xiong K, et al. Application of 3D-printed pulmonary segment specimens in experimental teaching of sectional anatomy. BMC Surg. 2023;23:109.
Sun Z, Wong YH, Yeong CH. Patient-specific 3D-printed low-cost models in medical education and clinical practice. Micromachines (Basel). 2023;14:464.
Downing TE, Kim YY. Tetralogy of Fallot: general principles of management. Cardiol Clin. 2015;33:531–41. vii–viii.
Jia X, Zeng W, Zhang Q. Combined administration of problem- and lecture-based learning teaching models in medical education in China: a meta-analysis of randomized controlled trials. Med (Baltim). 2018;97:e11366.
McLean SF. Case-based learning and its application in medical and health-care fields: a review of worldwide literature. J Med Educ Curric Dev. 2016;3:JMECD.S20377.
Zeng N, Lu H, Li S, Yang Q, Liu F, Pan H, et al. Application of the combination of CBL teaching method and SEGUE framework to improve the doctor-patient communication skills of resident physicians in otolaryngology department. Bmc Med Educ. 2024;24:201.
Sun Z. Patient-specific 3D-printed models in pediatric congenital heart disease. Children. 2023;10:319.
Meyer-Szary J, Luis MS, Mikulski S, Patel A, Schulz F, Tretiakow D, et al. The role of 3D printing in planning complex medical procedures and training of medical professionals—cross-sectional multispecialty review. IJERPH. 2022;19:3331.
Sun Z, Wee C. 3D printed models in cardiovascular disease: an exciting future to deliver personalized medicine. Micromachines-basel. 2022;13:1575.
Valverde I, Gomez-Ciriza G, Hussain T, Suarez-Mejias C, Velasco-Forte MN, Byrne N, et al. Three-dimensional printed models for surgical planning of complex congenital heart defects: an international multicentre study. Eur J Cardio-thorac. 2017;52:1139–48.
Download references
Acknowledgements
We extend our sincere appreciation to the instructors and students whose invaluable participated in this study.
This paper received support from the Education Department of Anhui Province, China (Grant Numbers 2022jyxm1693, 2022jyxm1694, 2022xskc103, 2018jyxm1280).
Author information
Jian Zhao and Xin Gong are joint first authors.
Authors and Affiliations
Department of Human Anatomy, Wannan Medical College, No.22 West Wenchang Road, Wuhu, 241002, China
Jian Zhao, Xin Gong, Jian Ding, Rui Huang & Huachun Miao
Department of Cardio-Thoracic Surgery, Yijishan Hospital of Wannan Medical College, Wuhu, China
Kepin Xiong
Zhuhai Sailner 3D Technology Co., Ltd., Zhuhai, China
Kangle Zhuang
School of Basic Medical Sciences, Wannan Medical College, Wuhu, China
You can also search for this author in PubMed Google Scholar
Contributions
Jian Zhao and Huachun Miao designed the research. Jian Zhao, Xin Gong, Jian Ding, Kepin Xiong designed the tests and questionnaires. Kangle Zhuang processed the imaging data and printed the models. Xing Gong and Kepin Xiong implemented the teaching. Jian Zhao and Rui Huang collected the data and performed the statistical analysis. Jian Zhao and Huachun Miao prepared the manuscript. Shu Li and Huachun Miao revised the manuscript. Shu Li provided the Funding acquisition. All authors reviewed and approved the final manuscript.
Corresponding authors
Correspondence to Shu Li or Huachun Miao .
Ethics declarations
Ethics approval and consent to participate.
This investigation received ethical approval from the Ethical Committee of School of Basic Medical Sciences, Wannan Medical College (ECBMSWMC2022-1-12). All methodologies adhered strictly to established protocols and guidelines. Written informed consent was obtained from the study participants to take part in the study.
Consent for publication
Written informed consent was obtained from the individuals for the publication of any potentially identifiable images or data included in this article.
Competing interests
The authors declare no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Electronic supplementary material
Below is the link to the electronic supplementary material.
Supplementary Material 1
Supplementary material 2, supplementary material 3, rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ . The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated in a credit line to the data.
Reprints and permissions
About this article
Cite this article.
Zhao, J., Gong, X., Ding, J. et al. Integration of case-based learning and three-dimensional printing for tetralogy of fallot instruction in clinical medical undergraduates: a randomized controlled trial. BMC Med Educ 24 , 571 (2024). https://doi.org/10.1186/s12909-024-05583-z
Download citation
Received : 03 March 2024
Accepted : 21 May 2024
Published : 24 May 2024
DOI : https://doi.org/10.1186/s12909-024-05583-z
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Medical education
- Case-based learning
- 3D printing
- Tetralogy of fallot
- Medical undergraduates
BMC Medical Education
ISSN: 1472-6920
- Submission enquiries: [email protected]
- General enquiries: [email protected]

How NASA Tracked the Most Intense Solar Storm in Decades
May 2024 has already proven to be a particularly stormy month for our Sun. During the first full week of May, a barrage of large solar flares and coronal mass ejections (CMEs) launched clouds of charged particles and magnetic fields toward Earth, creating the strongest solar storm to reach Earth in two decades — and possibly one of the strongest displays of auroras on record in the past 500 years.
We’ll be studying this event for years. It will help us test the limits of our models and understanding of solar storms.

Teresa Nieves-Chinchilla
Acting Director of NASA’s Moon to Mars (M2M) Space Weather Analysis Office
“We’ll be studying this event for years,” said Teresa Nieves-Chinchilla, acting director of NASA’s Moon to Mars (M2M) Space Weather Analysis Office. “It will help us test the limits of our models and understanding of solar storms.”
The first signs of the solar storm started late on May 7 with two strong solar flares. From May 7 – 11, multiple strong solar flares and at least seven CMEs stormed toward Earth. Eight of the flares in this period were the most powerful type, known as X-class, with the strongest peaking with a rating of X5.8. (Since then, the same solar region has released many more large flares, including an X8.7 flare — the most powerful flare seen this solar cycle — on May 14.)
Traveling at speeds up to 3 million mph, the CMEs bunched up in waves that reached Earth starting May 10, creating a long-lasting geomagnetic storm that reached a rating of G5 — the highest level on the geomagnetic storm scale, and one that hasn’t been seen since 2003.
“The CMEs all arrived largely at once, and the conditions were just right to create a really historic storm,” said Elizabeth MacDonald, NASA heliophysics citizen science lead and a space scientist at NASA’s Goddard Space Flight Center in Greenbelt, Maryland.
When the storm reached Earth, it created brilliant auroras seen around the globe. Auroras were even visible at unusually low latitudes, including the southern U.S. and northern India. The strongest auroras were seen the night of May 10, and they continued to illuminate night skies throughout the weekend. Thousands of reports submitted to the NASA-funded Aurorasaurus citizen science site are helping scientists study the event to learn more about auroras.
“Cameras — even standard cell phone cameras — are much more sensitive to the colors of the aurora than they were in the past,” MacDonald said. “By collecting photos from around the world, we have a huge opportunity to learn more about auroras through citizen science.”

By one measure of geomagnetic storm strength, called the disturbance storm time index which dates back to 1957, this storm was similar to historic storms in 1958 and 2003. And with reports of auroras visible to as low as 26 degrees magnetic latitude, this recent storm may compete with some of the lowest-latitude aurora sightings on record over the past five centuries, though scientists are still assessing this ranking.
“It’s a little hard to gauge storms over time because our technology is always changing,” said Delores Knipp, a research professor in the Smead Aerospace Engineering Science Department and a senior research associate at the NCAR High Altitude Observatory, in Boulder, Colorado. “Aurora visibility is not the perfect measure, but it allows us to compare over centuries.”
MacDonald encourages people to continue submitting aurora reports to Aurorasaurus.org , noting that even non-sightings are valuable for helping scientists understand the extent of the event.
Leading up to the storm, the National Oceanic and Atmospheric Administration’s Space Weather Prediction Center, which is responsible for forecasting solar storm impacts, sent notifications to operators of power grids and commercial satellites to help them mitigate potential impacts.
Warnings helped many NASA missions brace for the storm, with some spacecraft preemptively powering down certain instruments or systems to avoid issues. NASA's ICESat-2 — which studies polar ice sheets — entered safe mode, likely because of increased drag due to the storm.
Looking Forward
Better data on how solar events influence Earth's upper atmosphere is crucial to understanding space weather's impact on satellites, crewed missions, and Earth- and space-based infrastructure. To date, only a few limited direct measurements exist in this region. But more are coming. Future missions, such as NASA’s Geospace Dynamics Constellation (GDC) and Dynamical Neutral Atmosphere-Ionosphere Coupling (DYNAMIC), will be able to see and measure exactly how Earth’s atmosphere responds to the energy influxes that occur during solar storms like this one. Such measurements will also be valuable as NASA sends astronauts to the Moon with the Artemis missions and, later, to Mars.

The solar region responsible for the recent stormy weather is now turning around the backside of the Sun, where its impacts can’t reach Earth. However, that doesn’t mean the storm is over. NASA’s Solar TErrestrial RElations Observatory (STEREO), currently located at about 12 degrees ahead of Earth in its orbit, will continue watching the active region an additional day after it is no longer visible from Earth.
“The active region is just starting to come into view of Mars,” said Jamie Favors, director for the NASA Space Weather Program at NASA Headquarters in Washington. “We’re already starting to capture some data at Mars, so this story only continues.”
By Mara Johnson-Groh NASA’s Goddard Space Flight Center, Greenbelt, Md.
Media Contact: Sarah Frazier NASA’s Goddard Space Flight Center, Greenbelt, Md.
Related Terms
- Citizen Science
- Goddard Space Flight Center
- Heliophysics
- Heliophysics Division
- ICESat-2 (Ice, Cloud and land Elevation Satellite-2)
- Science & Research
- Science Mission Directorate
- Skywatching
- Solar Dynamics Observatory (SDO)
- Solar Flares
- Space Weather
- STEREO (Solar TErrestrial RElations Observatory)
- The Solar System
- The Sun & Solar Physics
- Thermosphere
Explore More

Hubble Captures a Bright Spiral in the Queen’s Hair

Galaxies Actively Forming in Early Universe Caught Feeding on Cold Gas

NASA’s TESS Finds Intriguing World Sized Between Earth, Venus

IMAGES
VIDEO
COMMENTS
2. Technical assessment of the main regulations related to the case study; 3. Answer to the question: Why were the regulations insufficient to protect the data and what are the recommendations for an effective protection? 4. Recommendations for regulatory agencies, organizations, and entities. 3.1. Technical Criteria for Selection of the Case Study
Data diddling is a common technique used in cybercrimes that involve the manipulation of data with malicious intent. This technique involves intentionally changing, deleting, or inserting false data into an organization's computer systems or documents. It is often used by hackers, insiders, or malicious actors to steal sensitive information ...
Data diddling is one of the most difficult attacks to detect. Data diddling is the alteration of data prior to the computer systems processing the request, then after the execution of the application, the hacker changes the data information bank. Adding one cent to people's accounts would be a good example of this type of hacking.
Date: October 2015. Impact: 235 million user accounts. NetEase, a provider of mailbox services through the likes of 163.com and 126.com, reportedly suffered a breach in October 2015 when email ...
Processing data diddling means modifying data while it is being processed in the system. This can happen during the data transformation, calculation, or analysis. Example: An insider changes billing data within a healthcare billing system to inflate charges. Output Data Diddling. Output data diddling involves unauthorized data alteration during ...
As Data diddling is also refers to changing of data before or during entry into the computer system. This kind of an attack involves altering the raw data just before a computer processes it and then changing it back after the processing is completed. The NDMC Electricity Billing Fraud Case that took place in 1996 is a typical example.
Data Diddling - A study Dr.J.Star,M.L., Ph.D., Assistant Professor of Law, CDAGLC, Pattaraiperumbudur. ... The NDMC Electricity Billing Fraud Case that took place in 1996 is a typical example. The computer network was used for receipt and accounting of electricity bills by the NDMC, Delhi. Collection of money, computerized accounting, record ...
Data diddling. Data diddling is a type of cybercrime in which data is altered as it is entered into a computer system, [1] most often by a data entry clerk or a computer virus. [2] Computerized processing of the altered data results in a fraudulent benefit. In some cases, the altered data is changed back after processing to conceal the activity.
Data diddling is a form of cyber attack where an attacker manipulates data during its input, processing, transmission, or output to cause disruptions, steal information, or achieve other malicious objectives. This type of attack is particularly concerning in manufacturing and Industrial Control Systems (ICS) environments, where the integrity of ...
Data diddling. Data diddling is a form of computer fraud involving the intentional falsification of numbers in data entry. It often involves the inflation or understatement of income or expenses to benefit a company or individual when completing tax or other financial documents. This act is performed manually by someone in a data entry position ...
Salami attacks, data diddling attacks, trust relationship attacks, man in the middle attack, ... healthcare systems, energy industries, and other online database systems. In this study, we discuss one of the research applications related to Big Data in healthcare or EHD that explains how to enforce privacy and security of Big Data.
Consequences of Undetected Data Manipulation. When data is unknowingly manipulated, company decisions will be made based on false data. That can lead to devastating consequences because that can taint mixed compounds, control systems and manufacturing processes. Increasing Attacks on Application Service Providers.
The total average cost of insider threat incidents rose from $8.3 million in 2018 to $16.2 million in 2023 according to the 2023 Cost of Insider Threats Global Report by Ponemon Institute. Insider attacks can lead to various negative consequences, from penalties for non-compliance with cybersecurity requirements to the loss of customer trust.
Review Paper Vol.-7, Issue-2, Feb 2019 E-ISSN: 2347 -2693. Review Paper on Dynamic Mechanis ms of Data Leakage Detection and. Prevention. Shivakumara T 1*, Rajshekhar M Patil 2 M uneshwara M S 3 ...
Some Indian case studies 5. Summary . FORENSIC SCIENCE MODULE No. PAPER No.16: Digital Forensics 8: Classification of Computer Crimes 1. Learning Outcomes ... Data diddling Data diddling is the most obvious form of computer crime, which takes place by input manipulations. Data diddling comprises of altering the data, with malicious intentions,
9.7 Data Diddling 9.7.1 Indian Law 9.8 Steganography 9.9 Summary 9.10 Terminal Questions 9.11 Answers and Hints 9.12 References and Suggested Readings 9.1 INTRODUCTION Like the previous unit, this unit also discusses the the crimes which are committed on the cyberspace. These crimes are commonly called as the crimes
data diddling. Cyber Laws Definitions Laws Tutorials. Techniques used in Cyber crimes. Techniques used in Cyber crimes- Cyber Criminals make use of various tools & techniques. Many ... Case Studies (3) Cyber Crime News (53) Cyber Laws (37) Definitions (17) IPC (3) Laws (9) Trending Frauds (15) Tutorials (20) Uncategorized (1) Direct links. Careers;
Data Diddling Attack. ... We study quantum quenches to the one-dimensional Bose gas with attractive interactions in the case when the initial state is an ideal one-dimensional Bose condensate. We ...
In one case, a foreigner who had been residing in Simla, India for almost thirty years wanted to avail of a scheme introduced by the Simla Housing Board to buy land at lower rates. ... Data diddling. This kind of an attack involves altering raw data just before it is processed by a computer and then changing it back after the processing is ...
To fully understand the scope of the Cyber Law regime, it is pertinent to refer to the following landmark Cyber Law cases in India: Shreya Singhal v. UOI [2] In the instant case, the validity of Section 66A of the IT Act was challenged before the Supreme Court. Facts: Two women were arrested under Section 66A of the IT Act after they posted ...
Data modeling is the art of creating a representation of a complex system, which helps organizations make informed decisions. The practical value of data modeling becomes most evident when it is used to solve real-world problems. In this article, we present case studies from real-world projects that illustrate the power of data modeling.
Recent Indian case about cyber lotto was very interesting. A man called Kola Mohan invented the story of winning the Euro Lottery. ... Electricity Boards in India have been victims to data diddling programs inserted when private parties were computerizing their systems. The NDMC Electricity Billing Fraud Case that took place in 1996 is a ...
Case studies are in-depth investigations of a person, group, event, or community. Typically, data is gathered from various sources using several methods (e.g., observations & interviews). The case study research method originated in clinical medicine (the case history, i.e., the patient's personal history). In psychology, case studies are ...
Get access to the latest Data Diddling Attack prepared with CSEET course curated by Nikhil Ravi on Unacademy to prepare for the toughest competitive exam. Log in Join for free. Please Login To Continue Login. CSEET. Free courses. Data Diddling Attack. Lesson 7 of 25 • 0 upvotes • 5:05mins.
The company estimates a potential carbon footprint reduction of 34% from the project. In 2022, Pierre-Etienne Bindschedler, the president and third-generation owner of Soprema, set a goal to ...
The draft EPA Transcriptomic Assessment Product (ETAP) aims to help address chemicals lacking traditional toxicity testing data in a more timely way. The primary driver for this new assessment product is the lack of human health toxicity values for most chemicals under the EPA regulatory purview. The ETAP transcriptomic-based reference values ...
We randomly assigned patients with type 2 diabetes and chronic kidney disease (defined by an estimated glomerular filtration rate [eGFR] of 50 to 75 ml per minute per 1.73 m 2 of body-surface area ...
Background Case-based learning (CBL) methods have gained prominence in medical education, proving especially effective for preclinical training in undergraduate medical education. Tetralogy of Fallot (TOF) is a congenital heart disease characterized by four malformations, presenting a challenge in medical education due to the complexity of its anatomical pathology. Three-dimensional printing ...
On May 14, 2024, the Sun emitted a strong solar flare. This solar flare is the largest of Solar Cycle 25 and is classified as an X8.7 flare. NASA's Goddard Space Flight Center. Traveling at speeds up to 3 million mph, the CMEs bunched up in waves that reached Earth starting May 10, creating a long-lasting geomagnetic storm that reached a rating ...
This paper aims to report on Chinese college students' emotions in English as a foreign language (EFL) speaking classrooms, including the trajectory of their emotions, and their perceived impacts of these emotions on their performances in class. Through conducting a case study among 12 Chinese college students and qualitatively analyzing the ...