
IAM CASE STUDIES
Fortify your data's protection with powerful iam solutions.
- IAM Case Studies
Download Access Management Case Studies PDF

ENECO – Eneco is leading the way in digitalization by utilizing OneWelcome’s advanced CIAM solution.
Philippines healthcare organization grows with cloud access management solutions using the onewelcome identity platform., rgf staffing – rgf’s goals for an efficient and secure access platform for their clients and flex workers to collaborate made possible with iam., baloise iam – empowers belgium-based company baloise to launch new company initiatives., tvm insurance – insurance company innovates claims handling processes with onewelcome identity platform., quick links.
Request a Call Back
Request A Demo
Request A Quote
SSL Support Desk
Follow us on
Digital Certificates
Authentication
Access Management
Email Security & Digital Signing
IOT & Connected Devices
Verified Mark Certificates TryVMC
Code & Document Security

Explore More: Find Exactly What You're Looking For with Acmetek's Search
Download this case study now.
"We have updated our PRIVACY POLICY and encourage you to read it by clicking here. Acmetek uses cookies, web beacons and log files to automatically gather, analyze, and store non-personal information about website visitors. This information is used to improve Acmetek’s services and your experience. To learn how to limit/opt-out these cookies within your browsers privacy control click here. "

The New Equation
Executive leadership hub - What’s important to the C-suite?

Tech Effect

Shared success benefits
Loading Results
No Match Found
Security at scale: The value drivers of PwC’s identity management transformation
/content/dam/pwc/us/en/library/case-studies/assets/pwc-cs-logo.svg
Professional services
Enabling an IAM transformation to strengthen security and improve operations
Cybersecurity and trust<br>Cloud and digital
A global transformation based on technology and trust
As an organization respected worldwide for experience in combining technology, business transformation and trust, PwC understands the importance of modern, secure solutions for managing large-scale enterprises. When evaluating our own complex identity and access management (IAM) system, we saw an opportunity to model that principle.
From a consistent, mobile-first single sign-on (SSO) experience across platforms and devices to reduced time for client delivery and employee onboarding, our IAM transformation was designed to improve user experiences, standardize global operations, strengthen security and reduce technical debt. In pivoting to a streamlined, scalable cloud solution, we laid the foundation for our own growth and developed a successful approach to digital transformation on a global scale that could benefit our clients in more ways than one. Not only does the modern solution streamline access to PwC platforms for engagement-related work, it also enhances our ability to guide clients through their own transformations.
By 2016, PwC’s network of member firms in more than 150 countries encompassed over 13 IAM platforms, 4,600 administrators and 90 Active Directory forests worldwide — a construct of directories that store user and group data and provide authentication services.
Faced with a fast-growing, mobile-first workforce, a digitization movement in the market and an evolving cyber-threat landscape, we performed a significant data transformation — moving from traditional on-premises legacy directories to a cloud-first, centrally managed identity solution. The new platform integrated IAM with security functions, including cloud governance, data privacy and controls , building greater trust among employees and customers alike.
Getting to cloud faster with a modular approach
The primary challenge was to consolidate a web of directories, users and platforms into a cloud-based IAM system that would be secure, nondisruptive and seamless to use. This was complex because the specific business and IT needs involved differed by region and application, and there was a lack of overarching authentication standards across the network of member firms.
Rather than build a whole solution first and migrate all applications at once, we adopted a modular approach. The team worked in phases, prioritizing functions based on the applications that required them, then migrating those applications in batches. This phased “migration factory” eliminated the need to wait for all functionality to be built prior to implementation, which saved time and provided greater flexibility to respond to challenges.
Establishing a collective vision
The first step to a data modernization of this scale was a yearlong series of cross-disciplinary workshops held across the North America, Europe and Asia-Pacific regions. The goal was to establish a collective vision among executives from PwC’s global member firms — no small feat considering the nuances we had to consider. Not only did we need to account for different business and IT team preferences and use cases across regions, but also matters of data residency and privacy requirements. That included the growing problem of cross-border data transfer, which has threatened to disrupt market strategies worldwide.
Drawing on the global feedback received in the workshops, we fine-tuned an enterprise solution to address the needs of our employees and internal users, as well as our customers . With the buy-in of our global membership secured, we began the intricate process of migrating IAM capabilities to the cloud.
Crafting a scalable, security-first solution
Given our extensive cloud knowledge, PwC was well-positioned to construct a robust and scalable cloud solution. But even with our wealth of experience, the complexity of migrating a company of our size to an entirely new platform presented a unique learning opportunity. Our global IAM system expanded over the years into its current state: a complicated web of disparate Active Directories, users and platforms — typically seen as a result of mergers and acquisitions in other companies, but in this case, of organic global growth across the firm.
To meet the complexity of our global use cases — while allowing for the size and scope our IAM platform would need to accommodate — we prioritized strength and flexibility. The resulting solution now handles the traffic of roughly 350,000 internal users and up to two million external users logging in multiple times a day, 24/7, with capacity to grow.
Laying the groundwork for a zero-trust future
As a result of this transformation, we’re standardizing controls and unlocking operational efficiencies across the global organization. Better capabilities to manage user access like SSO help improve security workflows and vulnerability management along with employee and client productivity, self-service features for processes like password resets can reduce time-consuming administrative labor and automated attestation of user access enables more scalability. The migration lays the groundwork for progress toward our zero-trust initiatives, including advanced security capabilities like multifactor authentication and password-less access.
A key factor to our success was keeping our business, IT and security teams in close collaboration throughout the implementation — and that wealth of first-hand experience has paid off. Having gained a deeper understanding of the challenges and benefits of undertaking such a significant, disruptive project, PwC can be a better strategic advisor in guiding clients through their own IAM leading practices and cloud transformation journeys.
minutes to register new users, down from 4-8 hours
growth in login activity during the first two years following the launch
internal and ~2M external users migrated
Modern standards and applications that improve operations, safeguard the business and provide a quick and easy login experience.
“There was no playbook for this. We had to create one. We worked together to build a global solution and successfully delivered on our design and security principles — authentications that take place on a single platform for more visibility, control and forensic capability as we secure the PwC network.”
James Shira Global and US Chief Information & Technology Officer, PwC US
“It’s about building trust — making sure that our customers, stakeholders and employees trust that their data is protected and that every digital interaction is secure.”
Avinash Rajeev Principal, Cyber, Risk and Regulatory, PwC US
Integrate cyber into your strategy
Align security with your business objectives.
Explore PwC's case study library
Share this case study.
PwC’s IAM transformation strengthened security and improved operations across the organization. Learn more about how we crafted a scalable, security-first solution.
{{filterContent.facetedTitle}}
{{item.publishDate}}
{{item.title}}
{{item.text}}
Avinash Rajeev
Principal, Cyber, Risk and Regulatory, PwC US

Thank you for your interest in PwC
We have received your information. Should you need to refer back to this submission in the future, please use reference number "refID" .
Required fields are marked with an asterisk( * )
Please correct the errors and send your information again.
By submitting your email address, you acknowledge that you have read the Privacy Statement and that you consent to our processing data in accordance with the Privacy Statement (including international transfers). If you change your mind at any time about wishing to receive the information from us, you can send us an email message using the Contact Us page.
© 2017 - 2024 PwC. All rights reserved. PwC refers to the PwC network and/or one or more of its member firms, each of which is a separate legal entity. Please see www.pwc.com/structure for further details.
- Data Privacy Framework
- Cookie info
- Terms and conditions
- Site provider
- Your Privacy Choices
A Systematic Review of Identity and Access Management Requirements in Enterprises and Potential Contributions of Self-Sovereign Identity
- Research Paper
- Open access
- Published: 12 September 2023
Cite this article
You have full access to this open access article

- Jana Glöckler 1 ,
- Johannes Sedlmeir ORCID: orcid.org/0000-0003-2631-8749 2 , 3 ,
- Muriel Frank ORCID: orcid.org/0000-0003-2294-6465 3 &
- Gilbert Fridgen ORCID: orcid.org/0000-0001-7037-4807 3
3731 Accesses
2 Altmetric
Explore all metrics
A Publisher Correction to this article was published on 12 December 2023
This article has been updated
Digital identity and access management (IAM) poses significant challenges for companies. Cyberattacks and resulting data breaches frequently have their root cause in enterprises’ IAM systems. During the COVID-19 pandemic, issues with the remote authentication of employees working from home highlighted the need for better IAM solutions. Using a design science research approach, the paper reviews the requirements for IAM systems from an enterprise perspective and identifies the potential benefits of self-sovereign identity (SSI) – an emerging, passwordless paradigm in identity management that provides end users with cryptographic attestations stored in digital wallet apps. To do so, this paper first conducts a systematic literature review followed by an interview study and categorizes IAM system requirements according to security and compliance, operability, technology, and user aspects. In a second step, it presents an SSI-based prototype for IAM, whose suitability for addressing IAM challenges was assessed by twelve domain experts. The results suggest that the SSI-based authentication of employees can address requirements in each of the four IAM requirement categories. SSI can specifically improve manageability and usability aspects and help implement acknowledged best practices such as the principle of least privilege. Nonetheless, the findings also reveal that SSI is not a silver bullet for all of the challenges that today’s complex IAM systems face.
Similar content being viewed by others

Blockchain for healthcare data management: opportunities, challenges, and future recommendations
Putting AI ethics to work: are the tools fit for purpose?

The Future of Nursing Informatics in a Digitally-Enabled World
Avoid common mistakes on your manuscript.
1 Introduction
Employees’ simple and reliable access to digital resources and software applications is one of the essential prerequisites for many organizations’ operation (Smith and McKeen 2011 ). In practice, however, it is difficult for IT managers and users to set up, maintain, and use this access, and it comes at a high cost (Casassa Mont et al. 2003 ; Sinclair and Smith 2008 ; Windley 2005 ), especially when businesses grow and their technology environment becomes increasingly heterogeneous (Bradford et al. 2014 ). Complexity is also a driver for security incidents like data breaches that can result in unexpected remediation costs and damage to company reputation (Enterprise Management Associates, Inc. 2020 ), customer churn (Ponemon Institute 2019 ), and severe fines for violating data protection regulation (LogMeIn 2019 ; Schlackl et al. 2022 ). The situation was further aggravated during the COVID-19 pandemic with an estimated 70% of employees working from home (Sadler and Hancock 2020 ) and a corresponding increase of cyber-attacks; mainly phishing (Naidoo 2020 ). Several studies found that employees feel more tired, unmotivated, and distracted when working from home (e.g., Velocity Smart Technology 2021 ). As a result, mistakes and a lack of vigilance appear more frequently (Irwin 2021 ), and the likelihood of employees giving away their passwords in a phishing attempt increases (Sadler and Hancock 2020 ).
Besides offering better password management for employees, identity and access management (IAM) systems provide enterprises with tools to support them in handling and monitoring a growing number of identities beyond employees, such as external partners, customers, and – driven by the growing relevance of the Internet of Things (IOT) – smart devices (Haber 2020 ). 77 % of enterprises aim to increase their budget for IAM to mitigate cybersecurity risks (Globenewswire 2020 ). In contrast, only 38% of companies used dedicated IAM software in 2017 (IDG Business Media GmbH 2017 ), illustrating the considerable challenges and costs involved with setting up and maintaining these systems. Consequently, enterprises also take complementary approaches, such as raising the awareness of cybersecurity among employees and deploying anti-virus software (Deloitte 2020 ), or look into new approaches, for instance, zero-trust architectures (Puchta et al. 2019 ; Buck et al. 2021 ).
At the same time, the threat of being subject to cybersecurity incidents for companies is increasing. In 2019, the global cost of data breaches alone was $ 2.1 trillion, and it is expected to rise further to $ 5 trillion in 2024, according to Juniper Research ( 2019 ). More conservative estimates still suggest that data breaches account for a significant share of the total annual costs of cybercrime of $ 1 trillion (Dyble 2020 ). 43 % of data breaches involve attacks on web applications, of which more than 80 % can be traced back to brute force attacks on employees’ passwords or the use of lost or stolen credentials (Verizon 2020 ). Consequently, every third data breach can be linked directly to password management. Taking into account that data breaches are only one of the potential consequences of poorly implemented IAM, the need to improve related solutions seems to be widely recognized by researchers and practitioners (Smith and McKeen 2011 ; Puchta et al. 2019 ). However, there has been surprisingly little holistic academic research on the requirements of IAM systems, which we deem essential to designing and evaluating new solutions. Consequently, this study seeks to identify and categorize enterprise requirements for employee IAM solutions, leading to our first research question (RQ):
RQ1: What are the requirements of IAM in enterprises?
One of the most prominent new paradigms for digital identity management and in particular authentication is decentralized digital identity management or self-sovereign identity (SSI) (Gartner Inc. 2020 ; Sedlmeir et al. 2022 ; Soltani et al. 2021 ). SSI is not specifically targeting IAM but rather end users’, organizations’, and smart devices’ digital identity management in general. It provides users with digital wallet apps on their mobile phones and empowers them to self-manage digital representations of identity documents such as passports, qualifications, access authorizations, or membership cards (Sartor et al. 2022 ; Richter et al. 2023 ). This paradigm, which is often associated with blockchain technology (Mühle et al. 2018 ; Sedlmeir et al. 2022 ), has received increasing support from industry consortia and governments in recent years (Kubach and Sellung 2021 ; Schmidt et al. 2021 ). Despite these developments, there is still a lack of research in the academic literature on how SSI can improve digital identity management in organizations in general and in IAM in particular. While some research has started investigating different technical aspects of SSI in the context of established IAM standards (Yildiz et al. 2021 ; Di Francesco Maesa et al. 2023 ), this study is to the best of our knowledge the first to holistically investigate the extent to which the SSI paradigm in IAM is suitable for meeting IAM system requirements (see RQ1). Our second research question, therefore, is as follows:
RQ2: How can SSI help address the requirements of IAM in enterprises?
To explore the requirements of IAM systems and potential improvements through SSI, we choose a design science research (DSR) approach (Hevner et al. 2004 ; Peffers et al. 2007 ). DSR uses scientific methods to design new artifacts or modify existing ones to solve relevant practical problems (Venable and Baskerville 2012 ; Johannesson and Perjons 2014 ) and is, therefore, suitable for identifying the challenges of today’s IAM in enterprises and designing corresponding solutions. Our study finds that both technical considerations and the role of enterprise IT management and employees as end users are essential for deploying IAM solutions in practice. We first identify four categories of requirements for IAM and use them to discuss how SSI can contribute to creating more secure and manageable IAM solutions.
The remainder of this paper is as follows: Sect. 2 introduces the theoretical background and salient research on identity and access management and SSI. We then describe our DSR approach (Sect. 3 ), which we use to identify and analyze IAM requirements (Sect. 4 ). Section 5 presents our SSI-based IAM prototype, followed by its evaluation by experts (Sect. 6 ) that sheds light on the potential benefits of SSI-based IAM. We also discuss limitations that point to avenues for future research and conclude with Sect. 7 .
2 Related Research
2.1 identity and access management.
IAM encompasses both “identity management” and “access management” (Thakur and Gaikwad 2015 ), i.e., it involves the management of identities as well as the processes associated with authentication and authorization processes in organizations. Identities can be claimed by human and non-human entities (Windley 2005 ). In an enterprise context, the human entities of employees, suppliers, partners, and customers can be distinguished (Mezler-Andelberg 2008 ). Non-human entities cover organizations, machines, or software applications (Windley 2005 ).
Authentication is the process of proving control of an identity but does not yet grant access rights (Haber and Rolls 2020 ). Such proofs of identity involve credentials, sometimes called authenticators, which can be divided into three categories: “what you know” (e.g., a password), “what you have” (e.g., a physical key), and “who you are” (e.g., represented by a fingerprint) (O’Gorman 2003 ). These credentials can be used also in combination in so called multi-factor authentication (MFA) to increase the level of assurance and, thus, security (Windley 2005 ). The form of authentication that a system admits generally depends on the type of access and the associated risks (Mezler-Andelberg 2008 ). In 2019, the use of MFA by companies reached around 57% worldwide, a significant increase from the previous year (LogMeIn 2019 ). However, MFA not only increases security, it can also increase cost and complexity for organizations and negatively impact user experience (Windley 2005 ; Yubico and 451 Research 2021 ; Acemyan et al. 2018 ).
Once a user is authenticated, access is granted or denied during authorization (Haber and Rolls 2020 ). An access control list (ACL) of authorized users, i.e., to implement read and write permissions, can be attached to resources (Ferraiolo et al. 2007 ). By configuring and maintaining such a list, it is easy to keep an overview of which user has which kind of access to the respective resource. However, at the same time it is often difficult to determine to which resources an individual user has access (Ferraiolo et al. 2007 ), especially in an enterprise with thousands of software applications, some of which are hosted by third parties. As the number of users and resources increases, the costs of managing ACLs hence increase substantially, making the approach inappropriate for larger organizations (Oh and Park 2003 ). Moreover, while adding permissions is easy, revoking permissions for a particular user is difficult with ACLs (Ferraiolo et al. 2007 ). Consequently, more common access control models used in enterprises are discretionary access control (DAC), role-based access control (RBAC), and attribute-based access control (ABAC).
DAC allows a resource’s owner to decide who is granted access, and entities that have access can in turn delegate, i.e., pass on, this permission (Ferraiolo et al. 2007 ). In contrast, RBAC assigns roles to specific access rights (Benantar 2006 ; Mezler-Andelberg 2008 ). Users can then be assigned one or multiple roles and receive the associated permissions (Ferraiolo et al. 2007 ). RBAC is the access control model most used by enterprises (IDG Business Media GmbH 2017 ); yet it causes considerable problems. For instance, when employees change jobs, access rights and roles need to be adjusted, which represents a major administrative burden and cost factor for companies (Kern and Walhorn 2005 ; Li and Karp 2007 ; Fuchs and Pernul 2013 ; Oh and Park 2003 ; Zhao and Johnson 2010 ). ABAC aims to address these challenges by granting or denying access based on users’ and resources’ attributes and environmental conditions. Since attributes can be specified and combined more flexibly than roles, ABAC enables particularly fine-grained access control (Hu et al. 2015 ). If a change of access rights is necessary, the underlying rules can remain untouched and the modification of a single attribute associated with a user is sufficient (Hu et al. 2015 ).
Regardless of the choice of access control model, there are generally acknowledged principles that should be applied in IAM systems. The principle of least privilege states that users should only possess the minimum rights necessary for their tasks (Ferraiolo et al. 2007 ). If a user has significantly more rights than necessary, they could cause excessive damage to the system in the event of an attack or misuse (Benantar 2006 ). Access rights should, therefore, be chosen carefully and reviewed from time to time. A similar guideline is the principle of least knowledge , which specifies that users but also IAM system administrators should only see the resources associated with their task (Alsmadi 2019 ). Moreover, to mitigate fraud, separation of duties can be used to ensure that not all steps of a critical operation can be performed by a single user (Ferraiolo et al. 2007 ).
IAM remains a major challenge for organizations, as attempts to improve the security of their employees’ passwords often prove ineffective. When employees are forced to reset their passwords on a regular basis, 49% of employees change only a single digit or character in their old passwords (Jacobson 2020 ). Employees who find password policies and management onerous also tend to experience security fatigue, making enterprise IT systems even more vulnerable (Cram et al. 2021 ).
2.2 Self-Sovereign Identity and Digital Wallets
SSI can be considered a paradigm that extends the use of asymmetric cryptography and, in particular, digital signatures beyond the identity management of web servers and makes it accessible to end users via digital wallets (Sedlmeir et al. 2022 ). Certificate-based identity management has been a backbone of cybersecurity for decades (Lioy et al. 2006 ), and SSI aims to apply this approach to identity management for end users, smart devices, and organizations (Preukschat and Reed 2021 ). It is seen as an answer to the security, usability, and efficiency challenges of logging in with usernames and passwords (Bonneau et al. 2012 ), and as an alternative to the privacy issues and lock-in effects related to the data silos of federated identity providers that offer a convenient single sign-on experience (Kubach et al. 2020 ; Ehrlich et al. 2021 ; Sedlmeir et al. 2022 ).
Certificate-based digital identity management for end users was already widely discussed in the computer science literature as early as the 2000 s (e.g. Backes et al. 2005 ; Lioy et al. 2006 ; Jøsang and Pope 2005 ; Ahn et al. 2009 ), but did not gain broad awareness or acceptance in practice until recently (Kubach et al. 2020 ). Potential reasons for the renewed interest in using this paradigm for end users’ identity management may be traced back to the increasing availability and capabilities of mobile phones (Sedlmeir et al. 2022 ). Moreover, it seems that the collaborative spirit in public and private ecosystems in the context of a broad enthusiasm for blockchain technologies, and the corresponding cryptographic key management, may have promoted the interest in identity management through digital wallets (Mühle et al. 2018 ; Jørgensen and Beck 2022 ). Although blockchain technology is not required for SSI (Chadwick 2020 ; Schlatt et al. 2022a ), the technologies are strongly connected (Mühle et al. 2018 ; Čučko and Turkanović 2021 ), and many SSI frameworks leverage a blockchain for their underlying public key infrastructure (PKI) (Schmidt et al. 2021 ). In the context of SSI, also a new standard – verifiable credential (VC) – has emerged (Sporny et al. 2021 ). VCs aim to replace identity documents based on paper or “plastic cards” (Richter et al. 2023 ) by means of digital attestations and can be thought of as an extension and generalization of traditional, digitally signed documents, such as X.509 certificates that build the identity layer for web servers and JSON Web Tokens that are frequently used in enterprise applications leveraging federated identity management based on protocols like OpenID Connect (OIDC) (Babel and Sedlmeir 2023 ; Kuperberg and Klemens 2022 ).
SSI comprises three important roles: Issuers, holders, and verifiers (Soltani et al. 2021 ). An issuer digitally signs VC that contain claims about their subject’s attributes and sends them to the holder (Sporny et al. 2021 ). Holders request VC from issuers and store them in their digital wallets that often take the form of mobile apps for end users. Since holders store their VC locally, they have control over data disclosure (Sartor et al. 2022 ). They can then use their VC according to their preferences to create machine-verifiable proofs about claims concerning their identity in a verifiable presentation (VP) when interacting with a verifier (Sporny et al. 2021 ; Feulner et al. 2022 ). As digital information tends to leave unique traces, an important principle of SSI is that it is possible to reveal only certain parts (“selective disclosure”) or only properties derived from it (“predicates”), such as a proof of legal age (Feulner et al. 2022 ), and to allow the cryptographic verification of the VP’s authenticity despite hiding the unique value of the digital signature or the binding public key from the verifier (Babel and Sedlmeir 2023 ). These privacy-enhancing features are typically based on cryptographic zero-knowledge proof (ZKP) (Backes et al. 2005 ; Camenisch and Lysyanskaya 2001 ; Hardman 2020 ; Di Francesco et al. 2023 ). A ZKP gives evidence about the correctness of a statement (e.g., the result of a computation) without transferring any knowledge beyond the statement under consideration (Goldwasser et al. 1989 ).
A VP can involve one or several VC, and the corresponding proof is automatically checked by the verifier upon receipt (Preukschat and Reed 2021 ; Feulner et al. 2022 ). Due to the forgery-proofness of digital signatures, there is no need for communication between the issuer and the verifier. However, verifiers will in general only trust a verifiable credential (VC) used in a VP if they trust the corresponding issuer. Communication between parties takes place via end-to-end encrypted messaging between software components, so-called agents (Preukschat and Reed 2021 ; Schlatt et al. 2022b ). Agents sometimes integrate a client for a blockchain that is used to store issuers’ public signing keys, standards, and revocation information (Schlatt et al. 2022a ). The latter is required as VC reside in the holder’s wallet, so they can no longer be removed reliably after issuance (Ruff 2018 ). Revocation is often implemented via revocation registries. For the identity management of servers, there is no big issue with publicly available revocation information; however, from an end user’s perspective, this approach poses privacy challenges (Babel and Sedlmeir 2023 ). For this purpose, some SSI implementations hide credentials’ unique identifiers in VPs, proving only set membership or non-membership in the public revocation registry by using a ZKP (Hardman 2020 ; Schlatt et al. 2022a ).
Several businesses and organizations have already started to provide software solutions based on SSI. In particular, companies such as esatus, Evernym (recently acquired by Avast), or Trinsic, as well as public-private initiatives like IDunion that involve many public and private sector stakeholders, implement digital wallet apps for end users that already offer a decent level of standardization and interoperability (Sartor et al. 2022 ). The EU has also passed a law that mandates member states to provide their citizens with digital wallets and to enforce their use for login with digital service providers in the course of the revision of the electronic identification, authentication and trust services (eIDAS) regulation (European Commission 2021 ; Schwalm et al. 2022 ). The range of SSI use cases and potential benefits covers, for instance, passwordless digital authentication and digital proofs of attributes or permissions through digital ID cards, driver’s licenses, credit cards, or COVID-19 vaccination certificates (Sedlmeir et al. 2022 ). In domains such as access control for web applications (Braun et al. 2023 ), managing know your customer (KYC) processes (Schlatt et al. 2022a ), digital diplomas (Grech et al. 2021 ), and event tickets (Feulner et al. 2022 ), researchers have already studied the improvements that SSI can provide for individuals’ authentication and authorization processes. On the other hand, businesses such as esatus, IdRamp, MATTR, or Workday advocate the potential benefits of an SSI-based flexible and passwordless digital identity management for enterprise IAM and offer corresponding software solutions. Kuperberg and Klemens ( 2022 ) recently surveyed the compatibility of and technical bridges between technical components and protocols associated with legacy IAM and SSI, and Belchior et al. ( 2020 ) proposed and implemented an SSI-based identity management across organizations.
3 Research Approach
To determine how SSI can improve enterprise IAM, we follow a DSR approach (Hevner et al. 2004 ; Peffers et al. 2007 ). DSR had long a tradition in software engineering before it found its way into the field of information systems (Peffers et al. 2007 ), combining elements from engineering (Eekels and Roozenburg 1991 ) and behavioral sciences (Hevner et al. 2004 ). In general, DSR involves the development of an artifact, such as methods, products, processes, or services, to address a general problem, and an evaluation of the solution’s fitness to solve the problem (Venable and Baskerville 2012 ). DSR therefore aligns with the goals of information systems research, which also employs build-and-evaluate processes to study the interaction of technical and social systems and find solutions to practical challenges (Lee 2001 ).
Commonly, DSR encompasses three different phases: first, the relevance cycle that identifies the practical problem that needs to be solved and the corresponding requirements for research (Hevner et al. 2004 ; Hevner 2007 ; Peffers et al. 2007 ). The next phase, also known as the design phase, is concerned with building and evaluating the design artifact (Hevner 2007 ). This is followed by a rigor cycle to ensure that artifacts are useful contributions to research and not routine designs (Hevner et al. 2004 ; Gregor and Hevner 2013 ). Since it can be challenging to balance the need for practical contributions in a changing technological environment with generalizing and theory building (Baskerville et al. 2018 ), an expansion of the knowledge base or the implementation of a novel IT artifact that provides solutions to practical problems can already be an appropriate contribution to research (Beck et al. 2013 ; Gregor and Hevner 2013 ; Baskerville et al. 2018 ). In the following, we will further elaborate on our research design and the involved methods. Figure 1 displays our DSR approach and the involved methods that we will describe in more detail below.
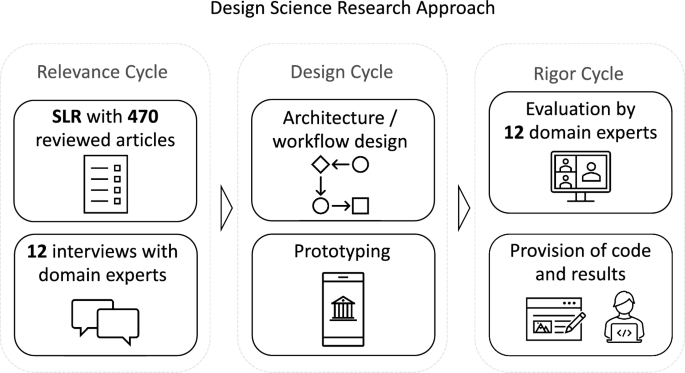
Phases of the design science research approach
In the relevance phase, we first conducted a systematic literature review (SLR) to identify IAM requirements in enterprises (Levy and Ellis 2006 ). Next, we coded all publications using Saldaña ( 2015 )’s approach and clustered the requirements using a distance metric derived from related sub-requirements. This generated an initial structured collection of IAM requirements that served as design objectives for the artifact (Peffers et al. 2007 ). To increase relevance, we then conducted interviews with twelve domain experts with the goal of (1) completing the perspective on IAM requirements and (2) refining the categorization. After examining the state of the art of research on SSI in an enterprise context, we took the results as input for a design cycle in which we conceptualized and instantiated a prototype for SSI-based IAM (Sect. 5 ). In a subsequent rigor cycle (Hevner et al. 2004 ), we again used expert interviews to assess whether the implementation sufficiently addresses the previously defined opportunities or problems (Hevner 2007 ). Furthermore, we present new knowledge generated in our DSR in the form of structured requirements and our prototype to the scientific community (Peffers et al. 2007 ) and demonstrate how SSI can contribute to improving IAM in enterprises. This involves both the dissemination of this manuscript and the disclosure of our demonstrator’s source code. Footnote 1
4 Analysis of IAM Requirements
4.1 systematic literature review.
To identify and structure the requirements associated with IAM systems in enterprises (see RQ1), we rely on a SLR consisting of three steps: inputs, processing, and outputs (Levy and Ellis 2006 ). We then use the results of this analysis as input for the design of our artifact as part of the DSR (as described in Sect. 3 ). In general, literature reviews support the proposed research question and provide a solid foundation for the research endeavor (Levy and Ellis 2006 ). The first step is to identify the relevant literature to ensure a certain level of quality of the literature (Levy and Ellis 2006 ; Kitchenham et al. 2009 ). This can be achieved through various techniques, such as applying inclusion and exclusion criteria and documenting the search process (Kitchenham et al. 2009 ). Next, the processing step involves either analyzing, synthesizing, applying, or evaluating the identified literature. The final step is to present the results in a comprehensive and understandable way. We will elaborate more on these steps below.
4.1.1 Procedure
Following Levy and Ellis ( 2006 ), we selected the articles for the SLR using a keyword search, followed by forward and backward searches. To determine a suitable search string that is broad enough to cover existing work on IAM in enterprises but at the same time has a sufficiently high density of relevant hits, we performed a keyword search in several databases with many synonyms for IAM, combined with synonyms for enterprises using the logical operator “AND”. We screened the first pages of results and focused on works with many citations or where the abstract matched our research topic. Due to the large number of potentially relevant articles we found in the initial search, we decided to limit our focus to enterprise IAM for employees. The final search string we used for the SLR was
(“Identity Management” OR “Access Management” OR “Access Control”) AND Employe* AND (Busines* OR Compan* OR Enterpris* OR Organi*)
Table 1 features the databases we searched with this search string and the corresponding numbers of hits. We considered 10 hits as a page. Since many databases still yielded far too many initial hits, we decided to end the search once 20 hits in a row no longer yielded a relevant article after abstract and full-text screening. The decreasing trend of the number of relevant hits per page (see Table 1 ), as well as the limited number of works that the subsequent backward search (9 new articles) and forward search (no new articles) added, indicate that we were able to cover the field comprehensively with these heuristics. In the course of the search, we screened a total of 5,569 articles. After applying inclusion and exclusion criteria (Kitchenham et al. 2009 ), 40 articles remained for in-depth full-text analysis (see Table 1 in Appendix A.1; available online via http://link.springer.com ). Inclusion criteria included selecting articles or book chapters that address enterprise IAM requirements or improvements for IAM approaches; exclusion criteria, on the other hand, applied to articles written in a language other than English or German and articles with IAM requirements for consumers or other stakeholders. In addition, articles to which the authors did not have access were not considered. These were 45 articles in the keyword search, 164 in the backward search, and 25 in the forward search.
Among these 40 articles, Puchta et al.’s ( 2019 ) study is the only one that systematically structures requirements for IAM systems, using a literature review and expert interviews. The authors identify five current challenges for IAM. These are integration of identities beyond the employee level, heterogeneity, data quality and management, the transition from role-based to attribute-based approaches, and privacy. Puchta et al. ( 2019 ) also discuss how visual analytics can address the first three challenges to varying degrees. In contrast, our focus is not only on incremental improvements but on the suitability of an alternative, SSI-based solution for enterprise IAM. Consequently, for identifying comprehensive design objectives of a novel approach, we intend to cover not only current challenges of IAM but also general requirements. We will also see that SSI can contribute to the last two challenges of Puchta et al.’s ( 2019 ) study, thus complementing their research.
After screening papers of interest in accordance with RQ1, we continued with the processing step, which included the analysis and evaluation of the works to be reviewed. As proposed by Levy and Ellis ( 2006 ), we identified key IAM requirements germane to the research question and categorized thematically similar ones into groups. For generating categories, we used coding (Saldaña 2015 ). The coding was performed iteratively in MAXQDA by one researcher alone, which is a common procedure for less extensive research projects (Saldaña 2015 ). To ensure validity, the researcher shared her coding scheme captured in the codebook – a compilation of codes and brief examples – with the other researchers in the team to achieve group consensus (Harry et al. 2005 ; Saldaña 2015 ). The first cycle consisted of two steps: (1) the initial coding in which the relevant data were divided into smaller parts (Strauss and Corbin 1998 ) and (2) subcoding in which the obtained codes were further subdivided and refined (Saldaña 2015 ). For books, we only coded the relevant sections. During the first cycle, we identified 24 categories corresponding to 280 (sub-)codes. Figure 1 in Appendix A.2 illustrates how often the 24 categories appeared in the 40 articles.
In a second cycle, we relied on pattern coding to identify and group thematically similar codes together (Onwuegbuzie et al. 2016 ). We performed pattern coding using the unweighted average linkage method in MAXQDA, as it allows to merge the clusters with the highest similarity step by step (Forina et al. 2002 ). Our computer-assisted, statistical analysis may also allow for more rigorous analysis than human-based merging (Bringer et al. 2004 ). Structuring the codes from the SLR resulted in eight different requirement clusters that define our design objectives. Figure 2 in Appendix A.3 depicts how often codes from these clusters appeared in the articles overall, while Tables 2, 3, and 4 in Appendix A.4 present the number of overlapping subcodes, used to generate the distance matrix for pattern coding. Figure 3 in Appendix A.4 illustrates the corresponding distances between categories. The colors indicate which of the categories form a cluster. One theme (“control”) is missing in the distance matrix because the topic has insufficient links with other codes to calculate a meaningful distance matrix. Therefore, we have kept it as a separate cluster.
4.1.2 Results of the Literature Review
In the following, as part of the final step of the SLR (Levy and Ellis 2006 ), we present all eight clusters we identified in descending order according to the aggregate frequency of the codes they comprise:
Cluster 1 – Security, Compliance, Integrity, & Auditability: The first cluster consists of requirements associated with security risk avoidance, technical measures to increase security, as well as with auditing and monitoring. Security threats, for instance, should be minimized as far as possible or, if feasible, prevented altogether (Walter et al. 2004 ). Frequently, passwords are a root cause for security problems, so the usage of MFA that requires further credentials like biometric data or a physical token is increasing (Theofanos et al. 2016 ; Keszthelyi and Michelberger 2012 ). The continuous adaptation of security mechanisms is essential, as the methods used to break into a system are also constantly evolving (D’Costa-Alphonso and Lane 2010 ). To reduce risks, audits can be conducted (Damon and Coetzee 2018 ), for instance, to determine overprivileged users (Bradford et al. 2014 ). Monitoring employees’ activities is not only important from a security perspective but also with regard to ensuring integrity and compliance (Haber 2020 ). For instance, organizations today have to comply with several regulations that mandate the record-keeping and reporting of IAM-related information (e.g. Damon and Coetzee 2018 ; Hummer et al. 2018 ; Zhao and Johnson 2010 ), such as the Sarbances-Oxley Act.
Cluster 2 – Manageability, Efficiency, Automation & Cost: The large number of identities, databases, and applications that today’s IAM systems need to handle contribute significantly to obfuscating and ultimately inhibiting a holistic picture of users’ permissions, complicating manageability (Puchta et al. 2019 ; Pöhn and Hommel 2020 ; Osmanoglu 2014 ; D’Costa-Alphonso and Lane 2010 ). Consequently, it is important to track employees’ authorizations and activities to some extent to prevent fraud and facilitate audits (Smith and McKeen 2011 ; Osmanoglu 2014 ). Automating related processes, such as access reviews, certifications, and password resets, can help reduce the manual effort and increase efficiency (Osmanoglu 2014 ; Bradford et al. 2014 ) and reducing costs, for instance, for IT help desks (Osmanoglu 2014 ; Theofanos et al. 2016 ; Windley 2005 ). Other cost factors include modifications to role assignments and access lists – frequent processes that considerably increase the management workload (Kern and Walhorn 2005 ; Li and Karp 2007 ).
Cluster 3 – Standardization, Interoperability & Simplicity: Many companies face an organic growth of their digital resources and related IAM tools, without considering standards or interoperability (Bradford et al. 2014 ; Windley 2005 ). In addition, there are often differences in processes depending on the location or department (Osmanoglu 2014 ). The prevailing complexity from the company’s point of view is often underestimated and can lead to substantial problems, especially when introducing new IAM systems (Royer 2013 ). The use of and adherence to established standards can help mitigate these challenges with interoperability and integration as well as simplify IAM systems (Small 2006 ; Windley 2005 ). Furthermore, standards can help create a more consistent user experience and make it easier to realize a higher degree of automation (Damon and Coetzee 2013 ; Osmanoglu 2014 ; Sinclair and Smith 2008 ; Windley 2005 ). Complexity, on the other hand, can negatively impact manageability, security, and efficiency (D’Costa-Alphonso and Lane 2010 ) and imply high costs (Small 2006 ; Sinclair and Smith 2008 ).
Cluster 4 – Privacy & Trust: Employees’ personal data must be protected and proper use should be ensured by using data only to the required extent (Windley 2005 ). Users need to be able to trust identity and service providers as well as devices not to disclose unnecessary information (Bertino and Takahashi 2011 ; Walter et al. 2004 ). Concerns about data being accessed and correlated, sold, or misused in some other ways are frequently present (Casassa Mont et al. 2003 ). Privacy-enhancing mechanisms are also important to comply with data protection regulations (Bertino et al. 2001 ), for instance, the EU GDPR (Puchta et al. 2019 ). Owing to the presence of tradeoffs between privacy and accountability, the extent to which data is kept private may depend on the resource that is to be protected (Windley 2005 ).
Cluster 5 – Flexibility: Flexibility refers to the ability to adapt to the introduction of new IT solutions or security threats that need to be dealt with (Casassa Mont et al. 2003 ; Keszthelyi and Michelberger 2012 ). Furthermore, it also includes the capability of an implementation to grow with an increasing number of applications or users (Fairchild and Ribbers 2011 ).
Cluster 6 – Availability: Beyond a few critical special cases, access to systems and data should not depend on employees’ location or device, allowing tasks to be completed at all times (Walter et al. 2004 ) and from different places. This requirement has become apparent particularly in lockdowns and home office periods during the COVID-19 pandemic (Guggenberger et al. 2021 ). This means that every employee on site, as well as employees accessing them remotely, should have the necessary access to resources in a timely manner (Damon and Coetzee 2013 , 2018 ; Zhao and Johnson 2010 ).
Cluster 7 – Control: Employees and users in general often feel that they have limited control over their identity data. While no attributes of their identity should be shared with a service provider without explicit consent (Hoepman et al. 2008 ), it is unclear how users are able to technically enforce this. Once their data is stored on different, unrelated sites or platforms (silos), they can no longer influence what is shared with whom. Hence, they call for more transparency and selective disclosure that allows only the minimum necessary information to be shared on request (Casassa Mont et al. 2003 ; Smith 2008 ).
Cluster 8 – Portability: Portability requirements apply to identities and accounts (Pöhn and Hommel 2020 ; Smith and McKeen 2011 ). Their usage should not be restricted to a single device or system (Hoepman et al. 2008 ; Smith and McKeen 2011 ). A lack of portability can be used by IAM service providers as part of their business strategy to increase the cost of switching. This aggravates the negative implications of lock-in effects for enterprises regarding their IAM system (Graef et al. 2013 ).
4.2 Refinement and Interview-Based Evaluation
We conducted semi-structured interviews with a total of twelve experts to complement and review the identified IAM requirements. The research team approached participants individually because of their expertise in the field of IAM or SSI. Of those who agreed to be interviewed, four work or have worked directly in the field of IAM, and four other experts have a background in IT management. In addition, eight of the twelve experts are working or have worked on novel forms of digital identity management, for example, based on blockchain and SSI. We include more details on the experts’ areas of expertise in Table 5 in Appendix B.1. To minimize response bias, we assured all respondents that their participation was voluntary and offered to anonymize their statements (Podsakoff et al. 2003 ). In addition, all interviews were conducted by the same researcher to ensure consistency in data collection (Brod et al. 2009 ).
Each interview followed a guideline in a semi-structured format (see Table 6 in Appendix B.2). In the beginning, questions focused on the experts’ general interest in IAM and their personal experience in this field. In the second, exploratory part of the interview, we asked the experts to report on what requirements and challenges they can identify in the use of IAM systems in companies, and where they currently see the greatest need to catch up. For instance, we asked “what benefits do you see for an organization by implementing an IAM system?” and “what are the possible drawbacks of such a system?”. In the last part of the interview, to avoid bias, we then discussed the design objectives we derived in Sect. 4.1 .
We transcribed and coded the interviews as we did for our literature review. In the first cycle, we performed a structural coding to break down the data into segments (Saldaña 2015 ). We chose the segments based on our interview guidelines, resulting in 10 codes. Following Saldaña ( 2015 )’s recommendation to use other first cycle methods as the next step (Saldaña 2015 ), we continued with an initial coding as a starting point for further analysis. In a second cycle, we then used axial coding to define the dimensions of a category, as categories are linked to subcategories (Saldaña 2015 ; Charmaz 2014 ; Strauss and Corbin 1998 ). At the end of this cycle, we had a total of 213 codes. We present the results according to the structure defined in the structural coding.
4.2.1 Open Collection of IAM Challenges
To compare the experts’ assessments of IAM system requirements with the result of our SLR, a researcher with knowledge in the field of IAM first coded the experts’ responses along the original 24 categories we derived from the literature review. We illustrate the frequency of appearances in Figure 4 (Appendix B.4). The in-depth analysis of the interviews reveals that the experts most frequently addressed topics from the cluster “Security, Compliance, Integrity, & Auditability” . From their perspective, organizations need IAM to better control access to resources from both a security and a governance perspective, addressing auditing and risk issues (Experts 1, 4, 5 & 12). They also mentioned that monitoring user rights is often a compliance issue, especially for insurance companies and banks:
“They [A/N: banks and insurance companies] are already required by their compliance frameworks, whether it’s COBIT or the Basel standards and anything else that’s out there, to clarify who has which authorization, and they have to fully delineate that.” (Expert 8)
The experts also see a substantial risk of security breaches when IAM systems are poorly implemented, as the following statement indicates:
“So if it’s poorly implemented [...], then under certain circumstances [...] you have the problem that the identity can be stolen [...].” (Expert 6)
Overall, the experts still see a great need to catch up in terms of the implementation of IAM systems, especially among medium-sized companies. During the interviews, some of them mentioned that enterprises’ IT departments often lack incentives to implement such a complex system, and the benefits are often not yet fully recognized, especially if IT is not part of the business model (Experts 9 & 10).
The second cluster most frequently addressed by experts was “Manageability, Efficiency, Automation & Cost” . The experts agree that IAM systems offer considerable advantages for overseeing systems and employees and their authorizations (Experts 1, 2, 6 & 10). When the size of a company reaches a certain threshold, they consider an IAM system indispensable (Experts 10 & 12). However, the experts note that managing an IAM system also involves increased effort, including costs (Experts 2, 3, 6, 9, and 10). With regard to efficiency, the experts contended that authorizations should be assigned as efficiently and quickly as possible to new employees to achieve first-day readiness. On the other hand, they also emphasized the importance of being able to revoke authorizations quickly (Expert 8). Some of the interview participants emphasized how a high degree of automation in IAM systems can help prevent unwanted access:
“It helps [...] to have strict identity and access management [...] so that [...] I can automate things and then no users [...] that have been retired for ten years have access to any systems.” (Expert 1)
As there are usually many different systems in large companies (Bradford et al. 2014 ), the effort required to maintain the IAM system increases and IAM staff can lose the global perspective (Experts 1, 6 & 10). When each system has its own independent process and assigns permissions individually, there is no longer a single comprehensive history of permission granting and revoking processes (Expert 10). Expert 8 noted that IAM systems can assist with these issues by mapping the organizational structure and managing employees’ permissions and roles.
Topics from the cluster “Standardization, Interoperability & Simplicity” were third-most mentioned. The experts see particular challenges when integrating a new IAM solution into existing systems. One of the experts pointed out:
“It’s [...] always difficult when you want to migrate from one system to another, and there’s kind of a [system] landscape already in place.” (Expert 1)
One expert also mentioned that businesses often avoid implementing IAM systems because they fear the corresponding complexity. The following statement addresses the potential hassle due to overlaps with other systems:
“Our whole structure is not designed for that at all. [...] We have the file server where all kinds of data converge, and to separate that [...], [everything] would have to be completely redone.” (Expert 4)
The experts also see room for improvement in terms of standardization and usability; for instance, to prevent the need for several roles across different systems (Expert 12). According to the experts, the heterogeneity and the number of isolated solutions affect not only security but also have substantial implications, as the following statement reasons:
“For the individual user, I would say, it [A/N: the implementation of an IAM] is certainly associated with certain fears because it of course makes it quite transparent who has access to what, and things that work in a shadow IT environment, like when users somehow book an app service or a cloud service themselves [...], are no longer that simple [...].” (Expert 1)
Besides these three clusters, the experts also referred to each of the clusters “Privacy & Trust” and “Flexibility” . Overall, the distribution of the experts’ responses is quite similar to the findings of the SLR, indicating that our findings are consistent. However, comparing the individual categories that they named, we notice some differences compared to related work (cf. Figures 1, 2, and 4 in the Appendix). The topic of security, which was one of the most mentioned in our SLR, was also mentioned several times by the experts, but not quite as frequently. A potential reason is that the security requirement is so obvious that the experts did not consider it worth discussing as much. The topic of manageability, by contrast, was mentioned considerably more often in interviews than in the literature, indicating that this is where current IAM solutions cause substantial difficulties for IT departments.
4.2.2 Refinement of the Clustering
After the initial discussion of requirements for IAM, we confronted the experts with the requirements we had identified in Sect. 4.1 through our SLR. For the most part, the experts agreed with the requirements and also found the scope and structure comprehensive and useful. In the following, we will present their remaining suggestions for improvement, which included merging and splitting some clusters and adding new topics. In addition, we will present the final structuring of our IAM requirements (see Fig. 2 ).
When asked what changes they thought were needed, the expert frequently suggested merging the “Privacy & Trust” and “Control” clusters, as indicated in the following statement:
“Privacy protection is always divided into two parts: On the one hand, there is the protection of privacy as ensured by governance frameworks [...] but on the other hand, there is also the issue of self-data protection. Do I have a way of exercising control over it?” (Expert 8)
Moreover, the experts suggested combining “Standardization, Interoperability & Simplicity” and “Portability” (Experts 6 & 8). One expert suggested that “Manageability, Efficiency, Automation & Cost” and “Availability” should either be merged or more clearly separated:
“In a way, automation [and] efficiency also means availability.” (Expert 6)
When asked about which topics need to be rearranged or removed from clusters, the experts mainly discussed the role of “Simplicity” in Cluster 3. In particular, they expressed concerns about the relationship between simplicity and the other two subcategories, “standardization” and “interoperability.” The following statement reflects their doubts:
“Whether, for example, standardization, interoperability, and simplicity, i.e., Cluster 3, fit together so well, I don’t know. [...] Standardization is a topic that does not necessarily have anything to do with simplicity.” (Expert 2)
When we asked the experts whether or not they see any topics that should be added to the clusters, they came up with several ideas. One of the experts, for instance, brought up future readiness, which describes the extent to which the requirements leave room for potential adjustments in the future. The following statement reflects his thoughts:
“For us what is always important is [...] the adoption somehow happening, [...] and is it future proof, so I can somehow adapt it in the future for things, but maybe that is also covered with [the cluster] flexibility.” (Expert 10)
Another expert suggested adding “effectiveness” to Cluster 2 (Manageability, Efficiency, Automation & Cost) but had to admit that it is probably already covered by manageability and automation (Expert 8). Finally, one expert recommended attaching concise labels to each cluster (Expert 7).
Drawing on the experts’ suggestions on the composition of the clusters, we made some adjustments: We combined “Privacy & Trust” with “Control”, we combined “Standardization, Interoperability & Simplicity” with “Portability”, and we added “Availability” to “Manageability, Efficiency, Automation & Cost”. Furthermore, based on the discussion above, we decided to split the category “Simplicity” from Cluster 3 (“Standardization, Interoperability & Simplicity”) and combine it with the new cluster “Control, Privacy & Trust”, as these all relate closely to the user perspective. As proposed by Expert 8, we added the aspect of “Effectiveness” to the second new cluster. We also added “Flexibility” to this cluster, as it concerns the design of the system. To make the newly formed clusters easier to understand and put the topics within the clusters into the right context, we gave them concise labels following Expert 7’s recommendation. Ultimately, our changes led to the following four clusters: “Security & Compliance”, “Operability”, “Technology”, and “User”. We illustrate the final structuring of IAM requirements in Fig. 2 .
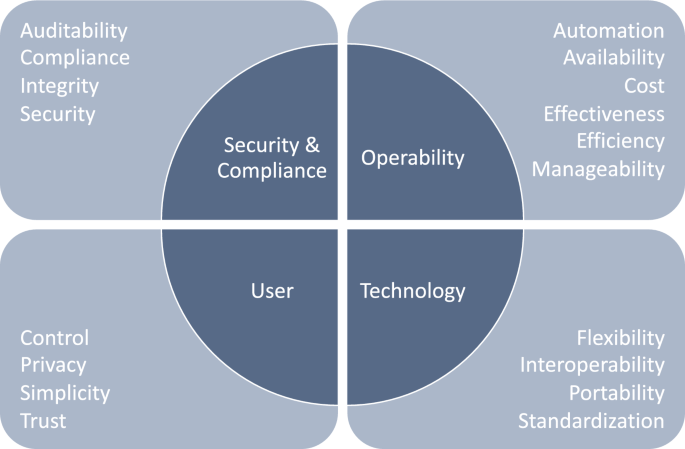
Requirements for an enterprise IAM system: consolidated results after the SLR and the evaluation with experts
5 Prototype
In this section, we present the SSI-based prototype that we developed based on the requirements identified in Sect. 4 . Our prototype allows an employee VC to be issued, used, and revoked as part of a simulated intranet login. There are three parties involved in the process: The human resources (HR) department, which issues and revokes VC, the employee, who receives and holds the VC and uses it to prove authorization for logging in, and the intranet login manager or gateway that ensures that only authorized users gain access. Both the HR department and the intranet login operate “institutional agents”, i.e., independent instances of the Hyperledger Aries Cloud Agent in Python (ACA-Py) , as a microservice. ACA-Py is suitable for non-mobile environments and can be used to build decentralized identity applications (Linux Foundation 2020 ). It implements a RESTful API that allows an admin to manage cryptographic keys and VC in an SQLite database, integrates client functionalities to communicate with a public permissioned Hyperledger Indy blockchain, and provides an endpoint for standardized and encrypted peer-to-peer messaging (Schlatt et al. 2022b ). As this messaging is often asynchronous (e.g., because a user’s confirmation is required to continue a credential issuance or VP process), ACA-Py also provides webhooks to notify an application’s controller about corresponding events.
The two ACA-Py agents for the HR department and the intranet login never communicate with each other in our prototype and do not use a shared directory. The employee runs an SSI wallet app on a smartphone that can generate and use cryptographic keys, receive and manage VC, and interact with verifiers in VPs (Schlatt et al. 2022a ; Sartor et al. 2022 ). The wallet app can be thought of as having a subset of the ACA-Py’s functionalities. As such, the wallet also requires client capabilities for the Hyperledger Indy blockchain, so a user must currently choose the same blockchain that the other two agents are connected to within their digital wallet app. No other customizations of the mobile wallet were required for our prototype. We chose the esatus wallet, but there are other, compatible digital wallet apps such as Trinsic ’s or Lissi ’s that we could have used equivalently. We also built a web interface to run the demo using Django .
5.1 Connection Establishment
Establishing an initial connection between two agents is necessary for them to exchange information over a secure, end-to-end encrypted channel (Mühle et al. 2018 ). In this scenario, the employee’s wallet app requires a connection with the HR department’s agent (issuer) and with the intranet login manager’s agent (verifier). The procedures to establish these connections are almost identical: in both cases, the institutional agent creates a personalized invitation link that resolves to an endpoint of the agent that serves the agent organization’s name and public key for encrypted and authenticated messaging. Employees can either scan a quick response (QR) code that represents this link with their wallet app, or they can access it via a deep link that directly opens the payload in their digital wallet. As we illustrate in Fig. 3 , the HR department can also personalize the invitation with an icon. To date, the QR code needs to be delivered through a trustworthy communication channel, like a personalized email or the company’s authentic website, secured by traditional website certificates: Manipulating the QR code by inserting another endpoint that serves another public key but the same organization name and icon would enable man-in-the-middle attacks (Babel and Sedlmeir 2023 ). This topic has been extensively discussed in the context of the German ID wallet (Lissi 2021 ; Schellinger et al. 2022 ). The corresponding vulnerability is currently being addressed by verifying that the connection’s service endpoint corresponds to the referenced public key and organization name, either via using existing public key certificates for web servers or via a lookup on the permissioned Hyperledger Indy blockchain (Lissi 2021 ; Schellinger et al. 2022 ).
If the employee then scans the QR code, the employee’s wallet creates a cryptographic key pair for this connection and asks the user whether he or she would like to accept the invitation. By accepting the invitation, the wallet sends a response to the HR department’s or intranet login manager’s agent respectively, i.e., to the service endpoint specified in the invitation, encrypted with the agent’s public key referenced in the connection invitation. After a standardized initial message and key exchange, there is now an active connection between the two parties. The wallet sends messages directly to the agent; in the opposite direction, the wallet app provider runs a so-called mediation service that collects messages and provides them to the wallet when it is online. Fundamentally, such a mediator agent could be provided by any party and does not need to be trusted concerning confidentiality owing to end-to-end encryption. Yet, switching to a custom mediation agent is not yet supported by the wallet, and implementations of mediation agents usually rely on the push notification services of Apple and Google to avoid periodic polling.
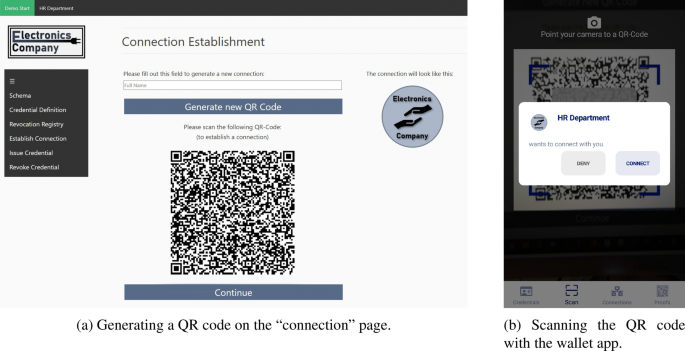
Establishing a connection between the HR department and the employee
5.2 Credential Issuance
To issue VC representing attested attributes to employees, the HR department has to make some preparations to bootstrap their agent for issuance. The agent first needs to register its endpoint and public key on the Hyperledger Indy blockchain. After that, it may have to publish a new schema. The schema contains, among other things, the type of attributes that are to be issued to the employee, i.e., it can be regarded a template or standard for a VC type in a specific context. In our prototype, the schema references the attributes “employee name”, “company name”, “division”, and “job title”. After publishing the schema or deciding to use an existing one, an issuer-specific credential definition must be derived from it. This determines the issuer’s signing public key (more precisely, one key for each attribute) that is referred to in later proofs. If the agent is to revoke VC, it must also create and upload a revocation registry, which refers to a specific credential definition, to the Hyperledger Indy blockchain, and publish tails files – a list of public random numbers that the wallet needs for later ZKPs of non-revocation yet is too large to be uploaded to a blockchain (Babel and Sedlmeir 2023 ) – to a public repository, for which we chose GitHub.
Once the HR department has bootstrapped a credential definition and revocation registry, it can issue VC to employees. To do so, the process is initiated by the HR department which uses a web interface to define which values the attributes should have for the respective employee. We illustrate the form to enter the values in Figure 5 in Appendix C.1. In practice, HR departments would likely automate this by retrieving the attributes from an existing employee database. Next, the HR department’s agent creates a credential offer with these attributes and sends it to the respective employee via an existing connection. The mediation agent associated with employees’ wallets then pushes a notification on the smartphone, and employees can view and accept or reject the offer. If they accept the VC offer and respond with their binding public key to be included in the VC, the HR department agent creates and signs the VC and sends it to the employee’s wallet app, where the VC is stored. Now the employee is ready to use the VC for future VPs.
5.3 Credential Usage for a Verifiable Presentation
If employees want to log in to the intranet with their mobile wallet, they need a credential issued by the HR department and an active connection with the intranet login manager. The view of the login page differs depending on whether users are new or returning: By using a session key to recognize a user’s repeated logins, the intranet login manager can use a previously set-up communication channel instead of initializing a new connection through a QR code or deep link. We present both views in Figure 6 in Appendix C.2. After establishing a new connection or clicking the login button in the case of an existing one, employees automatically receive a proof request on their mobile wallet. The proof request asks for selected attributes from their employee VC. A proof request contains a random challenge (“noce”) to prevent replay attacks and “restrictions”, i.e., the VC must follow a specific schema or be issued by an issuer from a specific trusted list. Employees’ digital wallets automatically create a drop-down list of VC that include the required attribute and that satisfy the corresponding restriction for every attribute requested and preselect one. In our case, the only choice is the VC that the HR department has previously issued. We illustrate the corresponding view in the wallet app in Figure 7 in Appendix C.3. Employees can change the selection of VC (if applicable) and give consent to answer the request. Their wallet then queries the current state of the revocation registry on the Hyperledger Indy blockchain and uses it to create a cryptographic proof. This proof corresponds to a ZKP that – simplified – asserts that:
One of the issuers specified in the proof request’s restrictions digitally signed the VC used to generate the proof.
The user knows the private key associated with the (undisclosed) binding public key referenced in the VC.
The attributes requested have the values revealed in the proof.
The VC is not expired and not revoked.
Through the ZKP, as opposed to certificates based on conventional digital signatures that are used for authentication in some organizations, no additional information like the full VC including the value of the signature or the public binding key, is given to the verifier (Babel and Sedlmeir 2023 ). Moreover, it is possible to reveal attributes selectively, and verifiers cannot correlate them beyond the equality of the revealed attributes in repeated VPs that use the same VC (Hardman 2020 ). The wallet also supports predicates, e.g., it proves that the VC’s expiration date (as UNIX timestamp) is larger than a specific timestamp (e.g., the current time) specified in the verifier’s proof request, without disclosing the potentially correlated expiration dates themselves. Likewise, the ZKP proves set membership of the VC’s revocation ID in the revocation registry without revealing the revocation ID. The digital wallet then sends the cryptographic proof to the intranet login’s agent, which checks the status of the revocation registry and cryptographically verifies the proof accordingly. Afterward, the agent sends the proof verification result to the intranet controller – the core backend of an application that implements the overall process logic and potentially coordinates additional microservices, including databases – via a webhook. Only if the proof is valid, the employee can access the web application (intranet) based on the value of the revealed attributes. The sequence diagram for the verifiable presentation is depicted in Figure 8 in Appendix C.4.
5.4 Credential Revocation
If an employee retires, resigns, or changes the department in the organization (or other attributes), it may be necessary to revoke a VC to ensure access is no longer granted or to revoke and re-issue when attributes need to be updated. For this, an employee in the HR department can select the VC to be revoked. Automation would also be conceivable, for example, by revoking and re-issuing the VC after changes in the personnel database. The HR department’s agent performs the revocation itself by creating an update for the revocation registry on the blockchain and publishing it there. To do this, it must authenticate with the same cryptographic key that was used for creating the revocation registry in the bootstrapping process. If the employee wants to use a revoked VC, it is recognized as invalid: The state of the revocation registry no longer allows the creation of a ZKP of non-revocation for a current timestamp, making it impossible to log in to the intranet. For the purpose of the demo, the agent immediately publishes the update to the revocation registry, so that the VC is effectively revoked after a few seconds. In a real-life enterprise context, it would be more practical to publish aggregate changes to the revocation registry state on the blockchain in larger intervals, e.g., once a day: Writing data to distributed ledgers is costly in general owing to redundancy, and Hyperledger Indy in particular has considerable performance limitations when it comes to write throughput (Sedlmeir et al. 2021 ).
6 Discussion
6.1 prototype evaluation.
To evaluate the potential contributions of SSI to improve enterprise IAM solutions, we presented our prototype to the same twelve experts who had already evaluated the IAM requirements in Sect. 4.2 . The researcher introduced the prototype to the participants and walked them through its features and functionalities. To illustrate this, the experts were presented with the case of Alice, a new hire, who receives a VC from the HR department. The VC is stored in a digital wallet on her cell phone and is used to create a VP when she wants to log in to the company’s intranet. The login backend ensures that only authorized users have access. The interviewer explained all the roles (issuer, holder, and verifier) and also demonstrated how revocation works (for more details see Sect. 5 ). Participants were then asked to evaluate first the strengths and weaknesses of the prototype and then those of SSI-based solutions in general in a semi-structured way. We included the interview guideline in Table 6 in Appendix B.2. All interviews were recorded and transcribed with the consent of the participants. Again, one researcher coded the interviews along the coding dimensions identified in Sect. 4.2 (Saldaña 2015 ). Table 7 in Appendix B.3 displays an excerpt from the codebook with codes, subcodes, and brief explanations. Figure 4 in Appendix B.4 illustrates how often codes from the clusters were mentioned in these interviews.
Throughout the interviews, the experts agreed that our prototype suggests that SSI integrates very well with existing IAM systems. They, for instance, mentioned its strong similarity with OIDC-based solutions (Kuperberg and Klemens 2022 ), and that verifiable attributes retrieved from the VP can be used as part of a JSON web token for OAuth-based protocols. The following statement stresses these findings:
“[One] can make a gradual transition without hurting anyone, [...]. Otherwise, you would have to throw away all the investments you may have made, and of course no one in a large company makes that decision.” (Expert 10)
The experts, however, also noted that some of the technical wording in the frontend and wallet might be difficult for users to understand. Users who are not yet familiar with SSI may feel insecure because of the unfamiliar workflow and terminology, as the following statement suggests:
“I would like it to be a bit more user friendly, [...] [because] I wouldn’t understand anything at first, although I think I’m already halfway living in today’s time. Everything is very, I would say, technically formulated.” (Expert 4)
This perspective is also in line with the results of first user experience studies (Sartor et al. 2022 ; Guggenberger et al. 2023 ; Khayretdinova et al. 2022 ) that indicate usability challenges but also promising solution approaches. Other experts pointed out that it is important to delete also sessions to make revocation effective. In line with this, one of the experts suggested the following procedure:
“And when the credential is revoked, you can flag that right there [A/N] in the user database] and just delete the session. Then the session is basically sent there and the website realizes, oh, this one doesn’t exist anymore, and then you’re automatically redirected back to the login and can’t get in.” (Expert 6)
However, when the selective disclosure capabilities of SSI-based authentication prevent a direct mapping of a session to an employee and their VC, it may be necessary to delete all sessions periodically (e.g., once a day) or a subset of potentially matching sessions when revoking a VC.
Expert 11 suggested that a less similar layout for the two pages (issuance and verification) could help to visually make clear the separation of the HR department page and the intranet pages in the architecture for the end user. Expert 12 noted that if the credential contains only the four attributes “employee name”, “company”, “department” and “job title”, it may happen that two employees have the same name. He, therefore, suggested that a unique employee identifier be added as an attribute to overcome this problem, which also resonates with enterprises’ current management of employees in databases. We subsequently incorporated these changes into our prototype.
6.2 Benefits and Challenges of SSI-Based Solutions for IAM
In the following, we highlight the experts’ opinions on the hurdles and benefits of SSI-based solutions for IAM. The experts identified many benefits of SSI in terms of integration with existing IAM systems. They emphasized that SSI-based IAM solutions offer fine-granular access control and support the use of ABAC through the verifiable disclosure of identity attributes in VPs. Particularly the positive contribution of revocation to security was emphasized:
“And then if they [A/N: employees] resign or leave or are fired, then blocking them in the systems [...] is also faster. I think the technology stack [A/N: SSI], even if it still has weaknesses [...] is strong. With the revocation of keys, the technology stack generally resolves this tension between usability and security quite well.” (Expert 7)
The experts also highlighted the benefits of SSI-based solutions in terms of speed, as the following statement reflects:
“On the one hand, you can integrate your new employees into the systems much faster, or rather you grant them access to the systems more quickly. And then when they resign or leave or are laid off, they’re also locked out of the systems faster.” (Expert 7)
However, one of the experts mentioned that providers of conventional IAM services are not yet showing much interest in the technology. This perception is supported by Glaude and Kudra ( 2021 ), who hypothesize that maintaining the existing complex and often non-interoperable landscapes is in the interest of IAM software providers as they want to secure their business models.
During the interviews, experts also discussed how SSI balances privacy and auditability features. They agreed that security is enhanced by passwordless authentication and native two-factor authentication, as VC are stored only on employees’ mobile phones and unlocking the digital wallet for a VP requires a valid PIN or biometric unlock. Some of the experts pointed to benefits of SSI in terms of usability and user-friendliness:
“The fact that you don’t have to come up with a different password for each system, or any password at all, but have the password in your wallet that you need to unlock your smartphone, or the biometric feature, makes it convenient.” (Expert 3)
In addition to increased usability, the experts considered improved privacy and control over information disclosure the main benefit for the user, especially as identity attributes only need to be stored in employees’ digital wallets. One of the experts stated:
“What I think is an advantage [...] is that I actually have full transparency in this wallet at all times [...] about who has somehow already queried my credentials then perhaps I could also somehow consolidate the whole thing at once and in principle say [...] I somehow don’t want to use them anymore [...].” (Expert 1)
In summary, the experts see several positive contributions that SSI can provide for IAM in all four clusters (please see Table 8 in Appendix B.5 for additional direct quotes from the experts indicating that they see potential improvements that SSI can provide for IAM systems in all four sets of requirements that we identified in Sect. 4 ). Nonetheless, the experts also pointed out some issues that need to be addressed in the future in order for such a solution to become established. These include, for example, the network connection that is required for checking (non-)revocation, standards that are still evolving, and the lack of availability of credential chaining, which is still a limitation for large-scale adoption from a technical point of view (Schlatt et al. 2022b ; Babel and Sedlmeir 2023 ). Notably, the lack of maturity that is hard to deny after having implemented the prototype was not criticized by the majority of experts, as they consider a gradual introduction of SSI in IAM possible.
6.3 Limitations and Future Work
As with any research endeavor, our study comes with limitations that point to avenues for future research. First, we limited our literature review to employees in the enterprise context only. However, the perspectives and requirements of customers, suppliers, and partners could be also considered to further explore the potential benefits of SSI in an enterprise context. Another perspective we did not consider relates to the ongoing trend of IOT. First research in this domain has already appeared (Bartolomeu et al. 2019 ), but implementing SSI wallets on embedded devices is still an underexplored topic beyond working groups in SSI-related foundations like Sovrin and Trust over IP.
The second limitation concerns the prototype. Even though we have tried to develop an application that is as close to reality as possible, some of the processes involved that promise to improve IAM have not yet been implemented in practice. One example is the automatic issuance of a credential based on identity information stored in the companies’ existing employee management system, or the distribution of a credential offer and the ensuing issuance to an employee who is not on-site, e.g., via e-mail.
Lastly, it is worth mentioning that our research focused on the authentication of employees, providing machine-verifiable attributes for ABAC, and managing the issuance and revocation of VC and the verification of VPs. Yet, some of the challenges of IAM systems as pointed out by Puchta et al. ( 2019 ), such as detecting entities with an unusual number of entitlements, might constitute a separate issue that can be addressed through complementary approaches like visual or automated data analytics. Future research could therefore investigate the additional adaptations that IAM software needs to monitor activities and manage access policies to resources based on verifiable attributes.
Another fruitful avenue for future work is a comparative analysis of our prototype with existing solutions such as Keycloak, as this would improve our understanding of which technology can best meet the IAM requirements and also identify more narrowly the potential for improvement of existing solutions.
Enterprise IAM is only one of many proposed applications of SSI. We believe that shedding light on where SSI can reduce complexities, increase security, and save costs is an interesting area for more interdisciplinary research, particularly in combination with other novel paradigms for enterprises’ IT security like zero trust (Buck et al. 2021 ) and the integration of smart devices. For example, researchers could study how the introduction of passwordless authentication affects technology adoption and user security behavior. With regard to the latter, they could investigate whether digital wallets mitigate security-related stress – a phenomenon that employees often experience when complex security measures are involved (Frank and Kohn 2021 ).
7 Conclusion
The goal of this study was to identify IAM requirements in enterprises and investigate the extent to which SSI is able to address and fulfill these requirements. Using a SLR refined by twelve domain experts, we were able to cluster IAM requirements into four categories: “Security & Compliance” covering the subcategories security, compliance, integrity, and auditability, “Operability” covering the subcategories manageability, efficiency, effectiveness, automation, cost, and availability, “Technology” covering the subcategories standardization, interoperability, flexibility, and portability, and “User” covering the subcategories simplicity, privacy, trust, and control. Building on these requirement categories and the new paradigm of decentralized identity management called SSI, we developed a prototype and had it evaluated by the twelve domain experts. Our prototype and the evaluation process suggest that integrating SSI into IAM systems can offer advantages in each of the four requirements categories. We conclude that SSI can indeed help improve IAM systems. These improvements encompass, for example, the possibility of selective disclosure, the fast onboarding and off-boarding of employees (revocation), consideration of the principle of least privilege, and the possibility of a higher degree of automation to improve efficiency and manageability.
Change history
12 december 2023.
A Correction to this paper has been published: https://doi.org/10.1007/s12599-023-00838-3
The code is available at https://github.com/JSedlmeir92/SSI-IAM .
Acemyan CZ, Kortum P, Xiong J, Wallach DS (2018) 2FA might be secure, but it’s not usable: a summative usability assessment of Google’s two-factor authentication (2FA) methods. Proc Human Factors Ergon Soc Annu Meeting SAGE 62:1141–1145. https://doi.org/10.1177/1541931218621262
Article Google Scholar
Ahn GJ, Ko M, Shehab M (2009) Privacy-enhanced user-centric identity management. In: Proceedings of the international conference on communications, IEEE, https://doi.org/10.1109/ICC.2009.5199363
Alsmadi I (2019) Identity management. In: The NICE cyber security framework, Springer, Heidelberg, chap 12, pp 313–329
Babel M, Sedlmeir J (2023) Bringing data minimization to digital wallets at scale with general-purpose zero-knowledge proofs. arXiv:2301.00823 . Accessed 9 Aug 2023
Backes M, Camenisch J, Sommer D (2005) Anonymous yet accountable access control. In: Proceedings of the ACM workshop on privacy in the electronic society, ACM, pp 40–46, https://doi.org/10.1145/1102199.1102208
Bartolomeu PC, Vieira E, Hosseini SM, Ferreira J (2019) Self-sovereign identity: use-cases, technologies, and challenges for industrial IoT. In: Proceedings of the 24th international conference on emerging technologies and factory automation, IEEE, pp 1173–1180, https://doi.org/10.1109/ETFA.2019.8869262
Baskerville R, Baiyere A, Gregor S, Hevner A, Rossi M (2018) Design science research contributions: finding a balance between artifact and theory. J AIS 19:358–376. https://doi.org/10.17705/1jais.00495
Beck R, Weber S, Gregory RW (2013) Theory-generating design science research. Inf Syst Front 15:637–651. https://doi.org/10.1007/s10796-012-9342-4
Belchior R, Putz B, Pernul G, Correia M, Vasconcelos A, Guerreiro S (2020) SSIBAC: self-sovereign identity based access control. In: Proceedings of the 19th international conference on trust, security and privacy in computing and communications, IEEE, pp 1935–1943, https://doi.org/10.1109/TrustCom50675.2020.00264
Benantar M (2006) Access control systems: security, identity management and trust models. Springer, Heidelberg
Google Scholar
Bertino E, Takahashi K (2011) Identity management: concepts, technologies, and systems. Artech House, London
Bertino E, Bonatti PA, Ferrari E (2001) TRBAC: a temporal role-based access control model. ACM Transact Inf Syst Secur (TISSEC) 4:191–233. https://doi.org/10.1145/501978.501979
Bonneau J, Herley C, Van Oorschot PC, Stajano F (2012) The quest to replace passwords: a framework for comparative evaluation of web authentication schemes. In: Symposium on security and privacy, IEEE, pp 553–567, https://doi.org/10.1109/SP.2012.44
Bradford M, Earp JB, Grabski S (2014) Centralized end-to-end identity and access management and ERP systems: a multi-case analysis using the technology organization environment framework. Int J Account Inf Syst 15:149–165. https://doi.org/10.1016/j.accinf.2014.01.003
Braun CHJ, Papanchev V, Käfer T (2023) SISSI: an architecture for semantic interoperable self-sovereign identity-based access control on the web. In: Proceedings of the ACM web conference 2023, pp 3011–3021. https://doi.org/10.1145/3543507.3583409
Bringer JD, Johnston LH, Brackenridge CH (2004) Maximizing transparency in a doctoral thesis 1: the complexities of writing about the use of QSR*NVIVO within a grounded theory study. Qual Res 4:247–265. https://doi.org/10.1177/1468794104044434
Brod M, Tesler LE, Christensen TL (2009) Qualitative research and content validity: developing best practices based on science and experience. Qual Life Res 18:1263–1278. https://doi.org/10.1007/s11136-009-9540-9
Buck C, Olenberger C, Schweizer A, Völter F, Eymann T (2021) Never trust, always verify: a multivocal literature review on current knowledge and research gaps of zero-trust. Comput Secur 110(102):436. https://doi.org/10.1016/j.cose.2021.102436
Camenisch J, Lysyanskaya A (2001) An efficient system for non-transferable anonymous credentials with optional anonymity revocation. In: Proceedings of the international conference on the theory and applications of cryptographic techniques, Springer, Heidelberg, pp 93–118, https://doi.org/10.1007/3-540-44987-6_7
Casassa Mont M, Bramhall P, Pato J (2003) On adaptive identity management: the next generation of identity management technologies. https://www.hpl.hp.com/techreports/2003/HPL-2003-149.pdf . Accessed 9 Aug 2023
Chadwick DW (2020) Why I do NOT need DIDs or a DLT for VCs and SSI. https://verifiablecredentials.info/contact-us . Accessed 9 Aug 2023
Charmaz K (2014) Constructing grounded theory. Sage, Thousand Oaks
Cram WA, Proudfoot JG, D’Arcy J (2021) When enough is enough: investigating the antecedents and consequences of information security fatigue. Inf Syst J 31:521–549. https://doi.org/10.1111/isj.12319
Čučko Š, Turkanović M (2021) Decentralized and self-sovereign identity: systematic mapping study. IEEE Access 9:139,009-139,027. https://doi.org/10.1109/ACCESS.2021.3117588
Damon F, Coetzee M (2013) Towards a generic identity and access assurance model by component analysis – a conceptual review. In: Proceedings of the first international conference on enterprise systems, IEEE, https://doi.org/10.1109/ES.2013.6690086
Damon F, Coetzee M (2018) The design of an identity and access management assurance dashboard model. In: Proceedings of the international conference on research and practical issues of enterprise information systems, Springer, Heidelberg, pp 123–133, https://doi.org/10.1007/978-3-319-99040-8_10
D’Costa-Alphonso MM, Lane M (2010) The adoption of single sign-on and multifactor authentication in organisations: a critical evaluation using TOE framework. Issues Inform Sci Inf Technol 7:161–189. https://doi.org/10.28945/1199
Deloitte (2020) Impact of COVID-19 on cybersecurity. https://www2.deloitte.com/ch/en/pages/risk/articles/impact-covid-cybersecurity.html . Accessed 9 Aug 2023
Di Francesco Maesa D, Lisi A, Mori P, Ricci L, Boschi G (2023) Self sovereign and blockchain based access control: supporting attributes privacy with zero knowledge. J Netw Comput Appl 212(103):577. https://doi.org/10.1016/j.jnca.2022.103577
Dyble J (2020) McAfee: cybercrime costs the global economy $600bn annually. https://technologymagazine.com/data-and-data-analytics/mcafee-cybercrime-costs-global-economy-dollar600bn-annually ,. Accessed 9 Aug 2023
Eekels J, Roozenburg NF (1991) A methodological comparison of the structures of scientific research and engineering design: their similarities and differences. Design Stud 12:197–203. https://doi.org/10.1016/0142-694X(91)90031-Q
Ehrlich T, Richter D, Meisel M, Anke J (2021) Self-Sovereign identity als Grundlage für universell einsetzbare digitale Identitäten. HMD Prax Wirtschaftsinform 58:247–270. https://doi.org/10.1365/s40702-021-00711-5
Enterprise Management Associates, Inc (2020) Contextual awareness: advancing identity and access management to the next level of security effectiveness. https://www.enzoic.com/wp-content/uploads/EMA-Contextual-Awareness-Report-03.2020-ENZOIC-SUMMARY.pdf . Accessed 9 Aug 2023
European Commission (2021) Commission proposes a trusted and secure digital identity for all Europeans. https://ec.europa.eu/commission/presscorner/detail/en/IP_21_2663 . Accessed 9 Aug 2023
Fairchild A, Ribbers P (2011) Privacy-enhancing identity management in business. In: Camenisch J, Leenes R, Sommer D (eds) Digital Privacy. Springer, Heidelberg, pp 107–129. https://doi.org/10.1007/978-3-642-19050-6_7
Chapter Google Scholar
Ferraiolo DF, Chandramouli R, Kuhn DR (2007) Role-based access control, 2nd edn. Artech House, London
Feulner S, Sedlmeir J, Schlatt V, Urbach N (2022) Exploring the use of self-sovereign identity for event ticketing systems. Electron Market 32:1759–1777. https://doi.org/10.1007/s12525-022-00573-9
Forina M, Armanino C, Raggio V (2002) Clustering with dendrograms on interpretation variables. Analytica Chimica Acta 454:13–19. https://doi.org/10.1016/S0003-2670(01)01517-3
Frank M, Kohn V (2021) How to mitigate security-related stress: the role of psychological capital. In: Proceedings of the 55th Hawaii international conference on system sciences, pp 4538–4547. https://doi.org/10.24251/HICSS.2021.550
Fuchs L, Pernul G (2013) Qualitätssicherung im Identity-und Access Management. HMD Prax Wirtschaftsinform 50:88–97
Gartner Inc (2020) Hype cycle for identity and access management technologies. https://www.gartner.com/en/documents/4004062 . Accessed 9 Aug 2023
Glaude M, Kudra A (2021) SSI for identity & access management (IAM). https://northernblock.io/ssi-for-identity-access-management-iam/ . Accessed 9 Aug 2023
Globenewswire (2020) New ESG & JumpCloud study uncovers IT’s biggest identity and security challenges due to COVID-19. https://www.globenewswire.com/news-release/2020/10/02/2102941/0/en/New-ESG-JumpCloud-Study-Uncovers-IT-s-Biggest-Identity-and-Security-Challenges-Due-to-COVID-19.html . Accessed 9 Aug 2023
Goldwasser S, Micali S, Rackoff C (1989) The knowledge complexity of interactive proof systems. SIAM J Comput 18:186–208. https://doi.org/10.1137/0218012
Graef I, Verschakelen J, Valcke P (2013) Putting the right to data portability into a competition law perspective. Law J High School Econ Annu Rev pp 53–63
Grech A, Sood I, Ariño L (2021) Blockchain, self-sovereign identity and digital credentials: promise versus praxis in education. Front Blockchain 4:7. https://doi.org/10.3389/fbloc.2021.616779
Gregor S, Hevner AR (2013) Positioning and presenting design science research for maximum impact. MIS Q 37:337–355. https://doi.org/10.25300/misq/2013/37.2.01
Guggenberger T, Lockl J, Röglinger M, Schlatt V, Sedlmeir J, Stoetzer JC, Urbach N, Völter F (2021) Emerging digital technologies to combat future crises: learnings from COVID-19 to be prepared for the future. Int J Innov Technol Manag 18:2140,002. https://doi.org/10.1142/S0219877021400022
Guggenberger T, Neubauer L, Stramm J, Völter F, Zwede T (2023) Accept me as I am or see me go: a qualitative analysis of user acceptance of self-sovereign identity applications. In: Proceedings of the 56th Hawaii international conference on system sciences, pp 6560–6569. https://hdl.handle.net/10125/103427
Haber MJ (2020) Privileged access management. In: Privileged attack vectors, Springer, Heidelberg, pp 151–171, https://doi.org/10.1007/978-1-4842-5914-6_11
Haber MJ, Rolls D (2020) Identity attack vectors: implementing an effective identity and access management solution. Apress, New York
Book Google Scholar
Hardman D (2020) No paradox here: ZKPs deliver savvy trust. https://www.evernym.com/blog/no-paradox-here-zkps-deliver-savvy-trust/ . Accessed 9 Aug 2023
Harry B, Sturges KM, Klingner JK (2005) Mapping the process: an exemplar of process and challenge in grounded theory analysis. Edu Res 34:3–13. https://doi.org/10.3102/0013189X034002003
Hevner AR (2007) A three cycle view of design science research. Scand J Inf Syst 19, http://aisel.aisnet.org/sjis/vol19/iss2/4
Hevner AR, March ST, Park J, Ram S (2004) Design science in information systems research. MIS Q 28:75–105. https://doi.org/10.2307/25148625
Hoepman JH, Joosten R, Siljee J (2008) Comparing identity management frameworks in a business context. In: IFIP summer school on the future of identity in the information society, Springer, Heidelberg, pp 184–196, https://doi.org/10.1007/978-3-642-03315-5_14
Hu VC, Kuhn DR, Ferraiolo DF, Voas J (2015) Attribute-based access control. Comput 48:85–88. https://doi.org/10.1109/MC.2015.33
Hummer M, Groll S, Kunz M, Fuchs L, Pernul G (2018) Measuring identity and access management performance – an expert survey on possible performance indicators. In: Proceedings of the international conference on information systems security and privacy, pp 233–240, https://doi.org/10.5220/0006557702330240
IDG Business Media GmbH (2017) Studie Identity- & Access-Management 2017. https://www.airlock.com/fileadmin/content/07_Airlock-PDFs/Studie_Identity-_und_Access_Management_2017.pdf . Accessed 9 Aug 2023
Irwin L (2021) The cyber security risks of working from home. https://www.itgovernance.co.uk/blog/the-cyber-security-risks-of-working-from-home . Accessed 9 Aug 2023
Jacobson K (2020) 8 scary statistics about the password reuse problem. https://securityboulevard.com/2020/04/8-scary-statistics-about-the-password-reuse-problem/ . Accessed 9 Aug 2023
Johannesson P, Perjons E (2014) An introduction to design science, vol 10. Springer, Heidelberg
Jørgensen KP, Beck R (2022) Universal wallets. Bus Inf Syst Eng pp 115–125, https://doi.org/10.1007/s12599-021-00736-6
Jøsang A, Pope S (2005) User centric identity management. In: Proceedings of the AUSCERT Asia Pacific information technology security conference, Citeseer, pp 77–89. https://citeseerx.ist.psu.edu/document?repid=rep1 &type=pdf &doi=6bf895c183de4673085f556b2d89043a95a21759
Juniper Research (2019) Business losses to cybercrime data breaches to exceed $5 trillion by 2024. https://www.juniperresearch.com/press/business-losses-cybercrime-data-breaches . Accessed 9 Aug 2023
Kern A, Walhorn C (2005) Rule support for role-based access control. In: Proceedings of the tenth symposium on access control models and technologies, ACM, pp 130–138. https://doi.org/10.1145/1063979.1064002
Keszthelyi A, Michelberger P (2012) From the IT authorisation to the role- and identity management. In: 4th international symposium on logistics and industrial informatics, IEEE, pp 173–178. https://doi.org/10.1109/LINDI.2012.6319483
Khayretdinova A, Kubach M, Sellung R, Roßnagel H (2022) Conducting a usability evaluation of decentralized identity management solutions. In: Selbstbestimmung, Privatheit und Datenschutz: Gestaltungsoptionen für einen europäischen Weg, Springer, Heidelberg, pp 389–406, https://doi.org/10.1007/978-3-658-33306-5_19
Kitchenham B, Pearl Brereton O, Budgen D, Turner M, Bailey J, Linkman S (2009) Systematic literature reviews in software engineering - a systematic literature review. Inf Softw Technol 51:7–15. https://doi.org/10.1016/j.infsof.2008.09.009
Kubach M, Sellung R (2021) On the market for self-sovereign identity: structure and stakeholders. In: Open Identity Summit, pp 143–154. https://dl.gi.de/handle/20.500.12116/36488
Kubach M, Schunck CH, Sellung R, Roßnagel H (2020) Self-sovereign and decentralized identity as the future of identity management? Open Identity Summit, pp 35–47, https://doi.org/10.18420/ois2020_03
Kuperberg M, Klemens R (2022) Integration of self-sovereign identity into conventional software using established IAM protocols: a survey. In: Open Identity Summit, pp 51–60. https://doi.org/10.18420/OID2022_04
Lee AS (2001) Editor’s comments. MIS Q 25:iii–vii, https://www.jstor.org/stable/3250954
Levy Y, Ellis TJ (2006) A systems approach to conduct an effective literature review in support of information systems research. Inform Sci J 9:181–212. https://doi.org/10.28945/479
Li J, Karp AH (2007) Access control for the services oriented architecture. In: Proceedings of the workshop on secure web services, ACM, pp 9–17. https://doi.org/10.1145/1314418.1314421
Linux Foundation (2020) Hyperledger Aries Cloud Agent – Python. https://github.com/hyperledger/aries-cloudagent-python . Accessed 9 Aug 2023
Lioy A, Marian M, Moltchanova N, Pala M (2006) PKI past, present and future. Int J Inf Secur 5:18–29. https://doi.org/10.1007/s10207-005-0077-9
Lissi (2021) Diskussion über die Sicherheit von Wallets für digitale Identitäten. https://lissi-id.medium.com/diskussion-%C3%BCber-die-sicherheit-von-wallets-f%C3%BCr-digitalen-identit%C3%A4ten-d1c6218fef66 . Accessed 9 Aug 2023
LogMeIn (2019) Der dritte jährliche globale Passwort-Sicherheitsreport. https://www.lastpass.com/de/business/articles/password-benchmark-report . Accessed 9 Aug 2023
Mezler-Andelberg C (2008) Identity Management - eine Einführung: Grundlagen, Technik, wirtschaftlicher Nutzen. Dpunkt, Heidelberg
Mühle A, Grüner A, Gayvoronskaya T, Meinel C (2018) A survey on essential components of a self-sovereign identity. Comput Sci Rev 30:80–86. https://doi.org/10.1016/j.cosrev.2018.10.002
Naidoo R (2020) A multi-level influence model of COVID-19 themed cybercrime. Europ J Inf Syst 29:306–321. https://doi.org/10.1080/0960085X.2020.1771222
O’Gorman L (2003) Comparing passwords, tokens, and biometrics for user authentication. Proc IEEE 91:2021–2040. https://doi.org/10.1109/JPROC.2003.819611
Oh S, Park S (2003) Task-role-based access control model. Inf Syst 28:533–562. https://doi.org/10.1016/S0306-4379(02)00029-7
Onwuegbuzie AJ, Frels RK, Hwang E (2016) Mapping Saldaña’s coding methods onto the literature review process. J Edu Issues 2:130–150
Osmanoglu E (2014) Identity and access management: business performance through connected intelligence. Elsevier, Amsterdam
Peffers K, Tuunanen T, Rothenberger MA, Chatterjee S (2007) A design science research methodology for information systems research. J Manag Inf Syst 24:45–77. https://doi.org/10.2753/mis0742-1222240302
Podsakoff PM, MacKenzie SB, Lee JY, Podsakoff NP (2003) Common method biases in behavioral research: a critical review of the literature and recommended remedies. J Appl Psychol 88:879–903. https://doi.org/10.1037/0021-9010.88.5.879
Pöhn D, Hommel W (2020) An overview of limitations and approaches in identity management. In: Proceedings of the 15th international conference on availability, reliability and security, https://doi.org/10.1145/3407023.3407026
Ponemon Institute (2019) Cost of a data breach report. https://www.ibm.com/downloads/cas/RDEQK07R . Accessed 9 Aug 2023
Preukschat A, Reed D (2021) Self-sovereign identity: decentralized digital identity and verifiable credentials. Manning, Shelter Island, NY
Puchta A, Böhm F, Pernul G (2019) Contributing to current challenges in identity and access management with visual analytics. In: IFIP annual conference on data and applications security and privacy, Springer, Heidelberg, pp 221–239, https://doi.org/10.1007/978-3-030-22479-0_12
Richter D, Praas CR, Anke J (2023) Beyond paper and plastic: a meta-model for credential use and governance. In: Proceedings of the 31st European conference on information systems. https://aisel.aisnet.org/ecis2023_rp/371/ . Accessed 9 Aug 2023
Royer D (2013) EIdM: concepts, technologies, and application fields. In: Enterprise Identity Management, Springer, Heidelberg, pp 27–56, https://doi.org/10.1007/978-3-642-35040-5_3
Ruff T (2018) The three models of digital identity relationships. https://medium.com/evernym/the-three-models-of-digital-identity-relationships-ca0727cb5186 . Accessed 9 Aug 2023
Sadler T, Hancock J (2020) A Stanford deception expert and cybersecurity CEO explain why people fall for online scams. https://www.fastcompany.com/90542273/a-stanford-deception-expert-explains-why-people-fall-for-online-scams . Accessed 9 Aug 2023
Saldaña J (2015) The coding manual for qualitative researchers. Sage, Thousand Oaks
Sartor S, Sedlmeir J, Rieger A, Roth T (2022) Love at first sight? A user experience study of self-sovereign identity wallets. In: Proceedings of the 30th European conference on information systems, AIS. https://aisel.aisnet.org/ecis2022_rp/46/ . Accessed 9 Aug 2023
Schellinger B, Sedlmeir J, Willburger L, Strüker J, Urbach N (2022) Mythbusting self-sovereign identity (SSI): discussion paper on user-centric identities. https://www.fim-rc.de/Paperbibliothek/Veroeffentlicht/1426/wi-1426.pdf . Accessed 9 Aug 2023
Schlackl F, Link N, Hoehle H (2022) Antecedents and consequences of data breaches: a systematic review. Inf Manag 59(103):638. https://doi.org/10.1016/j.im.2022.103638
Schlatt V, Sedlmeir J, Feulner S, Urbach N (2022) Designing a framework for digital KYC processes built on blockchain-based self-sovereign identity. Inf Manag 59(103):553. https://doi.org/10.1016/j.im.2021.103553
Schlatt V, Sedlmeir J, Traue J, Völter F (2022) Harmonizing sensitive data exchange and double-spending prevention through blockchain and digital wallets: the case of e-prescription management. Distrib Ledger Technol Res Pract 2. https://doi.org/10.1145/3571509
Schmidt K, Mühle A, Grüner A, Meinel C (2021) Clear the fog: Towards a taxonomy of self-sovereign identity ecosystem members. In: Proceedings of the 18th international conference on privacy, security and trust, IEEE, https://doi.org/10.1109/PST52912.2021.9647797
Schwalm S, Albrecht D, Alamillo I (2022) eIDAS 2.0: challenges, perspectives and proposals to avoid contradictions between eIDAS 2.0 and SSI. In: Open Identity Summit, pp 63–74. https://doi.org/10.18420/OID2022_05
Sedlmeir J, Ross P, Luckow A, Lockl J, Miehle D, Fridgen G (2021) The DLPS: a new framework for benchmarking blockchains. In: Proceedings of the 54th Hawaii international conference on system sciences, pp 6855–6864. https://doi.org/10.24251/hicss.2021.822
Sedlmeir J, Barbereau T, Huber J, Weigl L, Roth T (2022) Transition pathways towards design principles of self-sovereign identity. In: Proceedings of the 43rd international conference on information systems, AIS. https://aisel.aisnet.org/icis2022/is_implement/is_implement/4/ . Accessed 9 Aug 2023
Sinclair S, Smith SW (2008) Preventative directions for insider threat mitigation via access control. In: Stolfo SJ, Bellovin SM, Keromytis AD, Hershkop S, Smith SW, Sinclair S (eds) Insider Attack and Cyber Security. Springer, Heidelberg, pp 165–194. https://doi.org/10.1007/978-0-387-77322-3_10
Small M (2006) Unify and simplify: Re-thinking identity management. Netw Secur 2006:11–14. https://doi.org/10.1016/S1353-4858(06)70411-1
Smith D (2008) The challenge of federated identity management. Netw Secur 2008:7–9. https://doi.org/10.1016/S1353-4858(08)70051-5
Smith HA, McKeen JD (2011) The identity management challenge. Commun AIS 28, https://doi.org/10.17705/1CAIS.02811
Soltani R, Nguyen UT, An A (2021) A survey of self-sovereign identity ecosystem. Secur Commun Netw 2021:1–26. https://doi.org/10.1155/2021/8873429
Sporny M, Longley D, Chadwick D (2021) Verifiable credentials data model 1.1: expressing verifiable information on the Web. https://www.w3.org/TR/vc-data-model/ . Accessed 9 Aug 2023
Strauss A, Corbin J (1998) Basics of qualitative research: techniques and procedures for developing grounded theory. Sage, Thousand Oaks
Thakur MA, Gaikwad R (2015) User identity and access management trends in IT infrastructure – an overview. In: Proceedings of the international conference on pervasive computing, IEEE, https://doi.org/10.1109/PERVASIVE.2015.7086972
Theofanos M, Garfinkel S, Choong YY (2016) Secure and usable enterprise authentication: lessons from the field. IEEE Secur Priv 14:14–21. https://doi.org/10.1109/MSP.2016.96
Velocity Smart Technology (2021) Velocity smart market research report 2021. https://www.velocity-smart.com/en-gb/velocity-smart-technology-market-research-report-2021 . Accessed 9 Aug 2023
Venable J, Baskerville R (2012) Eating our own cooking: toward a more rigorous design science of research methods. Electron J Bus Res Method 10:141–153
Verizon (2020) 2020 Data breach investigations report. https://enterprise.verizon.com/resources/reports/2020-data-breach-investigations-report.pdf ,. Accessed 9 Aug 2023
Walter T, Bussard L, Robinson P, Roudier Y (2004) Security and trust issues in ubiquitous environments – the business-to-employee dimension. In: International symposium on applications and the internet workshops, IEEE, pp 696–701, https://doi.org/10.1109/SAINTW.2004.1268723
Windley PJ (2005) Digital Identity: unmasking identity management architecture (IMA). O’Reilly, Sebastopol
Yildiz H, Ritter C, Nguyen LT, Frech B, Martinez MM, Küpper A (2021) Connecting self-sovereign identity with federated and user-centric identities via SAML integration. In: Symposium on computers and communications, IEEE, https://doi.org/10.1109/ISCC53001.2021.9631453
Yubico, 451 Research (2021) Work-from-home policies driving MFA adoption, but still work to be done. https://resources.yubico.com/53ZDUYE6/at/kxjzxgg79h94js67jt8mnv/451_Advisory_BW_Yubico_v2.pdf . Accessed 9 Aug 2023
Zhao X, Johnson ME (2010) Managing information access in data-rich enterprises with escalation and incentives. Int J Electron Commer 15:79–112. https://doi.org/10.2753/JEC1086-4415150104
Download references
Acknowledgements
This research was funded in part by the Luxembourg National Research Fund (FNR) through the FiReSPArX (grant reference 14783405) and PABLO (grant reference 16326754) projects and by PayPal, grant reference “P17/IS/13342933/PayPal-FNR/Chair in DFS/Gilbert Fridgen” (PEARL). We also gratefully acknowledge the support of the Bavarian Ministry of Economic Affairs, Regional Development and Energy in form of their funding of the project “Fraunhofer Blockchain Center (20-3066-2-6-14)” that made this paper possible. We further thank the editor and the anonymous reviewers for their highly valuable and constructive feedback.
Open Access funding enabled and organized by Projekt DEAL.
Author information
Authors and affiliations.
University of Bayreuth, Bayreuth, Germany
Jana Glöckler
Branch Business and Information Systems Engineering of Fraunhofer FIT, Bayreuth, Germany
Johannes Sedlmeir
Interdisciplinary Centre for Security, Reliability and Trust, University of Luxembourg, Luxembourg, Luxembourg
Johannes Sedlmeir, Muriel Frank & Gilbert Fridgen
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Johannes Sedlmeir .
Additional information
Accepted after 2 revisions by Oscar Pastor.
Article was approved to be OA with the fees covered by Fraunhofer-Institut für Angewandte Informationstechnik FIT (1050)
Supplementary Information
Below is the link to the electronic supplementary material.
Supplementary file1 (PDF 2683 kb)
Rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Glöckler, J., Sedlmeir, J., Frank, M. et al. A Systematic Review of Identity and Access Management Requirements in Enterprises and Potential Contributions of Self-Sovereign Identity. Bus Inf Syst Eng (2023). https://doi.org/10.1007/s12599-023-00830-x
Download citation
Received : 26 September 2022
Accepted : 11 July 2023
Published : 12 September 2023
DOI : https://doi.org/10.1007/s12599-023-00830-x
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Authentication
- Digital wallet
- Verifiable credential
- Find a journal
- Publish with us
- Track your research
Managed IT Services
Spend more time innovating and less time maintaining IT. Our suite of Managed IT Services options ensures the right fit for your organization.
- Fully Managed IT Services
- Co-Managed IT Services
- Managed Cybersecurity

Our extensive portfolio of government and education contract awards lets you compare and procure the products and services you need with confidence and ease.
- Higher Education
- State + Local Government

Get the latest Data Networks news and know-how, plus our views on what’s new and what’s next in enterprise IT.
- Testimonials
- Case Studies
- Recent Projects
- Events + Webcasts
- E-Rate Program
- Blog: IT Insights

We have built lasting relationships with leading hardware and software manufacturers to architect the best solutions and ensure your project success.
- Cisco Select
- Dell Platinum
- HPE/Aruba Gold
- Juniper/Mist Elite
- Microsoft Gold
- Palo Alto Innovator
- Pulse Secure Preferred
- Veeam Silver ProPartner
- VMware Advanced

We support organizations in the public-sector, healthcare, and commercial markets with effective, affordable solutions that simplify enterprise IT.
- K-12 Education

We deliver enterprise solutions that work. Our innovative solutions address every area of the enterprise and help you do more by taking complexity out of your way.
- Client Computing
- Data Center
- Microsoft Solutions
- Cloud Services
- Cybersecurity
- Professional Services
- Staffing & Support

Since 1983, we’ve been providing solutions focused on simplifying enterprise IT for our education, government, and mid-market commercial customers.
- News Release

Case Studies Identity & Access Management Solution with Azure AD

Identity & Access Management Solution with Azure AD
This Microsoft project modernized and simplified a secure identity and access management solution by leveraging SSO, MFA, conditional access, and more with Azure AD for a private Mid-Atlantic University.
What Data Networks Did for the University
- Planned a modern authentication solution leveraging existing investments and Microsoft’s Authenticator application.
- Integrated existing user, device, and group management solutions into the new, modern identity and access management solution.
- Reduced the volume of password reset requests by enabling a self-service password reset portal.
- Increased security by blocking legacy authentication solutions through Azure AD Conditional Access to prevent unsecured authentication protocols (POP, SMTP, IMAP, MAPI) that cannot enforce MFA.
- Implemented Microsoft’s Azure Directory Premium P2 and Identity & Access Management solution.
The challenge
The University had to keep IT infrastructure and security current with the demands of today’s students, staff, and faculty. IT administration was already taxed with the planning and implementation efforts to improve their internal systems, including:
- A new finance application to protect and manage financial aid
- A new student information system (SIS) to deliver better learning and development tracking for students
As the application footprint grew (both on-premises and in the cloud), so did the university’s attack surface. These growing security concerns caused the university to seek the support of Data Networks.
With their student body becoming increasingly mobile and with more educational content moving online, the university faced an uphill climb. The university’s IT leaders and staff were tasked with providing access to as many applications as possible while protecting the university and its students from unauthorized users, in addition to other key challenges:
- Deploying critical applications, such CampusNexus’ campus management system and student management system
- Maintaining an effective access management and identity solution
- Replacing multiple siloed solutions that were burdensome to manage and secure
- Deploying a comprehensive “single source of truth” identity management system to resolve conflicts with data sources and personnel
- Eliminating significant security vulnerabilities and replacing outdated security practices
- Handling a high volume in password reset requests
The solution
Data Networks created a multi-phased plan to deliver increased security and modern applications to the university’s students, faculty, and staff. The solution introduced new technologies while leveraging the university’s existing technology investments, delivering a security overhaul that improved the university’s service offerings while making the entire environment more secure.
Implementation of Microsoft Azure Active Directory Premium P2
This comprehensive security suite already owned by the university allowed for the creation of a single sign-on across all applications, whether on-premises or in the cloud. As a robust and refined cloud-based Identity and Access Management platform, Azure AD Premium P2 provided the university with advanced security features, including:
- Conditional Access
Multi-Factor Authentication (MFA)
- Single Sign-On (SSO) Self-Service Password Reset (SSPR)
- Privileged Identity Management (PIM)
Microsoft Applications
- Microsoft Azure Active Directory Premium P2
- Multi-Factor Authentication & risk-based MFA
Microsoft Azure AD Conditional Access
With the support of Data Networks’ Microsoft Engineers, the school was able to deploy the Microsoft Azure AD P2 application to its fullest.
By asking more of the user, multi-factor authentication (MFA) adds a crucial extra layer of security. As a result, the university encountered fewer help-desk costs, while enjoying the benefits of MFA’s enhanced protection.
Risk-based MFA
To maximize the experience for trusted users and stop infiltrators in their tracks, risk-based MFA intelligently analyzes users and decides when to request additional verification. With this capability in place, IT Admin can detect suspicious activity and challenge intruders before they can do any damage, while allowing frictionless access to legitimate users.
Today’s security administrators are faced with two competing priorities: protect the organization and its electronic assets, and enable users to be productive no matter their location. Organizations can no longer settle for passwords alone to block or allow access to their networks and applications. With Conditional Access, a component of Microsoft Azure Active Directory, the system analyzes various user signals like the user identity and location, the device they’re using, the application they’re accessing, and other risk factors. Based on these factors, the system can decide whether to allow access, require MFA, or deny access.
Knowledge Transfer
Data Networks’ final deliverable was to setup knowledge transfer sessions with their Senior Microsoft Engineers and the university’s IT staff. These sessions reviewed the setup and functionality of the new platforms, the Recent Activity page, remediation procedures, guest user access plans, Azure AD’s activity and risk reports, their Microsoft 365 Security Score, and Conditional Access policies.
Mission accomplished
By leveraging the advanced features of Azure Active Directory Premium P2 (part of the Microsoft 365 A5 suite), the university was able to both modernize and simplify their identity and access management solution. Users benefit from a simpler authentication process that works everywhere (single sign-on), and administrators benefit from easier security reporting, management, and automation. Dashboard reporting of authentication allows for IT Admins to quickly identify and remediate threats and determine that the university’s network is secure.
Click here to view the PDF version of the Foundational Security with Azure AD for Private Mid-Atlantic University case study .

- Deploying Cyber Applications on Your Security Data Lake •
- Live Webinar | Mastering Cybersecurity Leadership: Effective Strategies for Boardroom Communication •
Access Management , Identity & Access Management , Security Operations
Case Study: Improving ID and Access Management
- Credit Eligible
- Get Permission
What are some of the moves that organizations can make to improve their identity and access management ? Veda Sankepally, an IT security manager at managed care company Molina Healthcare, describes critical steps in this case study interview.
A few years ago, Molina Healthcare was using a homegrown solution to onboard and offboard users daily in batches from the company's HR system into Active Directory, she says.
But the company was growing quickly, so the mostly manual process of provisioning and de-provisioning access to Molina's systems was time-consuming, Sankepally says in an interview with Information Security Media Group.
"With the increasing demands, we couldn't complete all the business processes involved, and there was a lack of standards," she says. "Our onboarding process was taking 10 to 20 days."
As a result, the company made a move to standardize and automate its ID and access management platform, choosing to implement technology from SailPoint Technologies, she says. "Today we have more than 15,000 active identities supporting 15 different states with different lines of business ... including caregivers on the ground."
For onboarding users, the company now has a "near real-time integration" with its cloud-based HR system that has automated the onboarding and offboarding process, she says.
"From that foundation, we introduced the next step; we built a platform for application provisioning and de-provisioning," she says. "As we are onboarding more applications, we can utilize that to do faster integration. First we focused on our crown jewels - our main applications. And then we brought in more applications."
The next phase involved access governance to build in regulatory compliance, she says. "We worked side by side with the compliance team to make sure all policies and procedures are being documented," she says.
In the interview (see audio link below photo), Sankepally also discusses:
- The end-user perspective of Molina Healthcare's ID and access management system and processes;
- Other steps the organization has taken to improve its ID and access management;
- Advice to other organizations struggling with ID and access management challenges.
Sankepally is an IT security manager and senior IAM architect at Molina Healthcare, a managed care company based in Long Beach, California, that provides health insurance to individuals through government programs such as Medicaid and Medicare. With over 18 years of experience in identity management, Sankepally has been leading major identity and access management projects, working with a broad number of client companies in various industries. Previously, she was a senior architect for IAM at a consulting company and later a technical lead for identity management initiatives at Southern California Edison.
- Access Management
- Customer Identity & Access Management (CIAM)
- Identity & Access Management
- Security Operations
You might also be interested in …

Identity Security: Why It Matters and Why Now

OnDemand | How Frictionless User Experience Makes Your Security Stronger
OnDemand Panel Discussion | Practical Viewpoints: Global IT Security Compliance in 2022

Identity & Access Management Master Compendium

The Next-Gen Machine Identity Management Report 2021

CAC-in-the-Cloud

The 3 Tenets of Enabling a Remote Government Workforce

The Future at Okta: IGA and PAM—The Identity Solution for Higher Education

Blueprint for Identity Security Success
Around the network.

La gestion des risques Cyber dans le Nucléaire
Web Trackers Persist in Healthcare Despite Privacy Risks

The Challenges in Keeping Medical Device Software Updated

Enterprise Technology Management: No Asset Management Silos

Healthcare Identity Security: What to Expect from Your Solution

Correlating Cyber Investments With Business Outcomes

Why Many Healthcare Sector Entities End Up Paying Ransoms

Major Areas of Cybersecurity Focus for Medical Device Makers

The Future of Security Awareness

Regulating AI: 'It's Going to Be a Madhouse'
Please fill out the following fields (all fields required):, subscription preferences:.
Was added to your briefcase
Request to Republish Content
Email this Content
Just to prove you are a human, please solve the equation:
Join the ISMG Community
Register with an ismg account, already have an ismg account.
Sign in now
Need help registering? Contact support
Thank you for registering with ISMG
Complete your profile and stay up to date
Need help registering?
Contact Support
Sign in to ISMG
Sign in with your ismg account, don't have one of these accounts.
Create an ISMG account now
Forgot Your Password?
Enter your email address to reset your password, forgot your password message:.
Our website uses cookies. Cookies enable us to provide the best experience possible and help us understand how visitors use our website. By browsing bankinfosecurity.com, you agree to our use of cookies.
You are using an outdated browser. Please upgrade your browser or activate Google Chrome Frame to improve your experience.
Identity and Access Management by Ertem Osmanoglu
Get full access to Identity and Access Management and 60K+ other titles, with a free 10-day trial of O'Reilly.
There are also live events, courses curated by job role, and more.
Implementation
Nicholas Gazos
A global organization struggles to effectively implement tools and technologies to support identity and access management, with a particular emphasis on the access certification process, to periodically validate user access appropriateness. Continued issues arise throughout the organization’s remediation efforts, highlighting key lessons learned that can be extrapolated in the areas of communication, planning, roles and responsibilities, technology selection and implementation, among others.
Access Review and Certification Implementation; recertification; IAM; identity and access management; IAM governance; program implementation
XYZ Finance Corporation, a leading financial services ...
Get Identity and Access Management now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.
Don’t leave empty-handed
Get Mark Richards’s Software Architecture Patterns ebook to better understand how to design components—and how they should interact.
It’s yours, free.

Check it out now on O’Reilly
Dive in for free with a 10-day trial of the O’Reilly learning platform—then explore all the other resources our members count on to build skills and solve problems every day.


- Identity Recharge
- IAM Expert Overlay Services
- Cyber Insurance Readiness
- CyberArk SailPoint Integration
- BeyondTrust SailPoint Integration
- SailPoint IdentityIQ vs IdentityNow Evaluation
- Endpoint Privilege Management
- IAM Services for Higher Education
- IAM Services for Healthcare
- Interim IAM Director
- SaaS Deployment & Support Subscription
- Identity Governance & Administration
- Privileged Access Management
- Customer Identity Access Management
- Access Management
- IAM Managed Services
- Cloud Infrastructure Entitlement Management
- FREE WORKSHOP: IAM Essentials
- FREE WORKSHOP: PAM Essentials
- FREE WORKSHOP: SailPoint Solutions
- FREE WORKSHOP: Saviynt Solutions
- FREE WORKSHOP: Oracle Identity Manager (OIM) Migration
- FREE WORKSHOP: Zero Trust
- About Integral Partners & Xalient
- Leadership Team
Learn how we’ve helped customers in every industry, SMBs to Fortune 500 enterprises, overcome their complex IAM challenges
BIOTECHNOLOGY
Getting Biogen on Track for PAM Maturity
Biogen, one the world’s leading pharmaceutical firms, was struggling with an underutilized legacy PAM solution in operation for several years and aligning with Good Practices (GxP) for the Biotechnology industry. We worked with Biogen to implement BeyondTrust, become GxP certified, and increase the scale and scope of their PAM program while establishing the basis for even greater PAM capabilities in the future.
⦿ Implemented the BeyondTrust PAM solution ⦿ Defined PAM policies using automated workflows ⦿ Biogen now working within GxP guidelines
Read the Case Study

Vertical Manufacturing
IAM Technology Access Management Deployment Application Onboarding
Solution Deploy Global IDaaS Solution MFA SSO
MANUFACTURING
Global IDaaS Project Brings Okta Cloud Identity to Avery Dennison
Integral Partners was selected by Avery Dennison to facilitate global deployment of a leading IDaaS (Identity-as-a-Service) solution to provide the its users with multi-factor authentication and single sign on.
⦿ 10-week global rollout ⦿ 95% adoption rate ⦿ Secured key cloud applications ⦿ Ongoing application onboarding process to maximize ROI
HIGHER EDUCATION
IAM Video Case Study: Building Modern IAM Program at Southern New Hampshire University
The 2nd largest sailpoint implementation ever with 1.5 million identities .
The Senior Director of IAM at Southern New Hampshire University discusses how Integral helped them build a strategy, implement SailPoint’s IdentityNow platform, and support the program with Managed Services. The complex environment included 4 authoritative sources, dual student information systems, and over 1.5 million identities!
⦿ Updating their Student Information System (SIS) from Colleague to Banner Cloud ⦿ A consolidated system of record for contractors using SailPoint’s NERM ⦿ The amazing role “Identity Mastering” played in dramatically reducing duplicates ⦿ Why they chose Integral to support their program through Managed Services
Watch the Video
IAM Video Case Study : Planning and Implementing a Modern IAM Program at Southern New Hampshire University

Case Study : Helping Laitram Build their IGA Program from the Ground Up

Case Study : Redefining the PAM Strategy and Implementing CyberArk Privileged Cloud at Boston Consulting Group

Case Study : Global Endpoint Management Made Easy at Elanco

Case Study : Reducing “Certification Fatigue” at PG&E with SailPoint AI

Case Study : Global IDaaS Project Brings Okta Cloud Identity to Avery Dennison

IAM Case Study : Creating Fail-Safe Compliance For ISO New England

IAM Case Study : Creating an IAM Strategy at Amgen

Case Study : Getting Biogen on Track for PAM Maturity
Committed to our customers’ success.
Integral Partners has helped customers across a broad range of industries overcome their complex IAM challenges—including SMBs and Fortune 500 enterprises in healthcare, financial services, telecommunications, manufacturing, education, government, and more. Some key benefits we’ve helped our customers achieve:
- Reducing risk and complexity
- Developing an efficient, effective RFP
- Passing audits with confidence
- Managing compliance
- Getting the most from existing solutions
- Streamlining processes and educating teams
- Having a comprehensive, actionable strategy and roadmap
- Aligning IGA strategy with overall business and IT strategy
Read more about the organizations we’ve worked with, and their challenges and results.
Identity Lifecycle Management For Hospitals
Tackling the persona problem, services/solutions:, end-to-end privileged access governance, connecting pam and iga solutions for full visibility, high compliance with high performance, implementing automation without losing the white glove service, roadmap for compliance and efficiency, addressing critical needs within an overarching plan, reducing risk and complexity, integrating a complex web of global identities, healthcare case study: deploying an integrated pam and iga solution, integrate cyberark and sailpoint to reduce audit pain, simplify user provisioning and create a single pane of glass to manage your privileged accounts and administrators., efficient and effective rfp, inception to delivery: four weeks to an iam rfp.
High Contrast
- Asia Pacific
- Latin America
- North America
- Afghanistan
- Bosnia and Herzegovina
- Cayman Islands
- Channel Islands
- Czech Republic
- Dominican Republic
- El Salvador
- Equatorial Guinea
- Hong Kong SAR, China
- Ireland (Republic of)
- Ivory Coast
- Macedonia (Republic of North)
- Netherlands
- New Zealand
- Philippines
- Puerto Rico
- Sao Tome & Principe
- Saudi Arabia
- South Africa
- Switzerland
- United Kingdom
- News releases
- RSM in the news

- AI, analytics and cloud services
- Audit and assurance
- Business operations and strategy
- Business tax
- Consulting services
- Family office services
- Financial management
- Global business services
- Managed services
- Mergers and acquisitions
- Private client
- Risk, fraud and cybersecurity
- See all services and capabilities
Strategic technology alliances
- Sage Intacct
- CorporateSight
- FamilySight
- PartnerSight
Featured topics
- 2024 economy and business opportunity
- Generative AI
- Middle market economics
- Environmental, social and governance
- Supply chain
Real Economy publications
- The Real Economy
- The Real Economy Industry Outlooks
- RSM US Middle Market Business Index
- The Real Economy Blog
- Construction
- Consumer goods
- Financial services
- Food and beverage
- Health care
- Life sciences
- Manufacturing
- Nonprofit and education
- Private equity
- Professional services
- Real estate
- Technology companies
- See all industry insights
- Business strategy and operations
- Family office
- Private client services
- Financial reporting resources
- Tax regulatory resources
Platform user insights and resources
- RSM Technology Blog
- Diversity and inclusion
- Middle market focus
- Our global approach
- Our strategy
- RSM alumni connection
- RSM Impact report
- RSM Classic experience
- RSM US Alliance
Experience RSM
- Your career at RSM
- Student opportunities
- Experienced professionals
- Executive careers
- Life at RSM
- Rewards and benefits
Spotlight on culture
Work with us.
- Careers in assurance
- Careers in consulting
- Careers in operations
- Careers in tax
- Our team in India
- Our team in El Salvador
- Apply for open roles
Popular Searches
Asset Management
Health Care
Partnersite
Your Recently Viewed Pages
Lorem ipsum
Dolor sit amet
Consectetur adipising
The business case for identity and access management
Investing in iam capabilities to protect top- and bottom-line growth, identity and access management (iam) is critical to your business, especially in an evolving business landscape..
Most of the time, in order to take action on something, you first need access to it. This is especially true when it comes to business computing. The first step to taking action, either intended or malicious, is getting access to computing systems and data. This fundamental principle is at the core of why effective identity and access management (IAM) is so critical to your business. If you can’t control and manage who has access to what, then you’re operating your business at risk—and the consequences, as unfortunately many companies have discovered, can be catastrophic. Now more than ever it is imperative for businesses to have robust, scalable and sustainable IAM capabilities to meet the evolving and dynamic threats of today’s business computing environment.
Why identity and access management is a strategic investment priority
Simply put, access management refers to control over the increasing number of paths that users and nonhuman entities take to access your critical data. Every day, malicious actors, often part of organized hacker teams, are working to gain access to your most valuable computing assets. This is why MITRE, a leading cross-industry security research organization, emphasizes access control in its popular ATT&CK framework.
A majority of businesses utilize cloud (software as a service or SaaS) technology such as Workday, Zoom, Box, Google Workspace and Office 365 to enable their business operations day to day. SaaS technology has many advantages, including providing native access controls, but it leaves companies to figure out how to coordinate and manage access across a sprawling technology footprint. It becomes a daunting challenge to get control over who has access to what from where.
This is where leading access management providers (also known as identity providers or IDPs) come in. These vendors provide technology in the form of services that help companies gain control over the myriad access points across their enterprise system landscape. Yet with access being so critical to how your employees, contractors and business partners perform their jobs, the technology alone is not enough. It is equally important to consider the business processes, roles and permissions, compliance requirements and risk mitigation your IAM solution will provide. Even for small businesses, the scope of IAM can be complex, and implementing a robust solution can take considerable time and effort.
Getting IAM in place when first implementing your technology plan is well worth the investment, as the alternative can leave your business operating with expanding risks and costs from an increasing number of access silos. Without effective IAM, the risk of unauthorized access to your business systems—resulting in real business losses in the form of monetary loss, reputational damage and exfiltration of intellectual property—is unreasonably high.
In fact, Verizon’s 2021 Data Breach Investigations Report found that access abuse is an increasing root cause for breaches since 2015. This trend, paired with the increase in high-profile breaches, is driving companies to prioritize IAM as a strategic investment to protect their business.
Given the importance of IAM to your business operations, this critical security capability requires the right funding to be done properly, but it does not have to break the bank. For example, a trusted advisor can work with you and your stakeholders to develop a robust, risk-prioritized road map tailored to your funding and business objectives. Your road map can include consideration of different IDP vendors, prioritization of application integrations and services, and evaluation of operational efficiencies such as automation to drive down costs.
Summarizing the strategic importance of IAM
Controlling who has access to what within your company’s computing environment is essential. Improper planning and prioritization of the investment required to implement an IAM solution that will not only meet your company’s access security requirements today, but scale to meet tomorrow’s demands, will leave you with unreasonable risk. In addition, deferring IAM investment can potentially leave you facing staggering costs when you later have to address a larger user population, complex stovepipe access, and controls dispersed across a large, hybrid cloud landscape. A better approach is to plan for the future of your IAM needs now and build a scalable, future-ready and sustainable solution today.
In addition, enterprise-ready cloud services and new requirements for employees who work remotely from wherever they are have expanded the attack surface that administrators are expected to secure. Many organizations today are using zero-trust principles in their IAM strategy to address these challenges—not just authenticating users, but also checking that they meet the security policy at the point of access each time they log in.

Related insights
Subscribe to risk bulletin, our cybersecurity, risk and fraud professionals provide regular insights and regulatory compliance updates to help your organization manage risk. .

THE POWER OF BEING UNDERSTOOD
ASSURANCE | TAX | CONSULTING
- Technologies
- RSM US client portals
- Cybersecurity
RSM US LLP is a limited liability partnership and the U.S. member firm of RSM International, a global network of independent assurance, tax and consulting firms. The member firms of RSM International collaborate to provide services to global clients, but are separate and distinct legal entities that cannot obligate each other. Each member firm is responsible only for its own acts and omissions, and not those of any other party. Visit rsmus.com/about for more information regarding RSM US LLP and RSM International.
© 2024 RSM US LLP. All rights reserved.
- Terms of Use
- Do Not Sell or Share My Personal Information (California)
- Utility Menu
GA4 Tracking code
Identity & access management.
Harvard University Information Technology (HUIT)
- Privacy Information (6)
- HarvardKey Integration Services
- InCommon (6)
- HR Resources (3)
- Group Services
- Overview (7)
- Planning (2)

25% Improved Delivery with Automation Infused Identity and Access Management Platform
Provided end-to-end identity and access management services and improved overall experience for a leading financial organization in America.
The client was facing issues in its Identity and Access Management (IAM) architecture and processes leading to loss of time, effort, and compliance issues.
Key Challenges
- Lack of streamlined processes in handling IDM (Identity Management) users impacting business productivity
- Complex and improper configurations for various IDM processes resulting in increased number of defects
- Inadequate usage of IAM products leading to increased manual effort and risk
- Unsystematic approach in following proper standards leading to compliance issues
The Solution
Automate, improve, and quick access management
- Automated Oracle Identity Manager (OIM) processes, user access review requests, and Lightweight Directory Access Protocol (LDAP) requests
- Developed and implemented scripts for user access provisioning, monitoring, and OIM server tracking
- Implemented best practices and knowledge management via complete documentation and systematic framework
- Centralized the governance processes to manage relationships and mitigate issues, and identified opportunities for quality and performance improvement
- Provided L1, L2 platform support, 24X7 monitoring, and resolution of tickets
Enhance business efficiency with Infosys IDAM solution
25% reduction in tickets with regular tracking via ServiceNow along with efficient resolution
25% increase in qualitative delivery by implementing automation services in IDM platform
Increase in business productivity
Decrease in user access issues
Increase in compliance by following company standards and processes

Identity and Access Management Customer Success Stories
Explore our Customer Success Stories
Customer Success Stories
Learn how we can help you to alleviate IAM challenges, and make it easier to access and manage your apps without compromising on security with Thales Identity and Access Management Solutions.
Contextual logging in from within and outside the office was really important. With SafeNet Trusted Access, we enjoy great user experience with push authentication and SSO.
Security Officer
The most important factor for our organization was that SafeNet Trusted Access let us offer a convenient and simple user experience for our employees. [Thales] met this need, creating excellent value.
Secure anywhere access for council staffers offers work convenience, in addition to reduced travel costs and journey times, and has further positive environmental effects.
Stuart Batson
[SafeNet Authentication] cloud-based authentication solution met our goals to operate with no infrastructure costs and be highly automated.
With the solution, we could address critical risks while enabling secure remote access. We now have more than 5,000 users enrolled in the solution, and people love it.
Mohammed Sayeed
Law firm lifts the fog over cloud apps with safenet trusted access.


Customer Usage and Satisfaction Patterns - Report
SafeNet Trusted Access This paper summarizes the findings of a customer satisfaction survey conducted among Thales SafeNet Trusted Access customers by TechValidate in 2022. It provides insights into how Thales customers are using SafeNet Trusted Access, their security...
Meet the thousands of organizations that trust Thales to protect their user access:

SafeNet Trusted Access awarded Top Solution of Q1 2024 by Expert Insights
"SafeNet Trusted Access is an industry leading IAM solution, from a highly trusted brand, with functionality built up over more than three decades in the authentication space."

SafeNet Trusted Access a Leader in Single Sign-On (SSO) Solutions for Spring 2024
SafeNet Trusted Access fits into organizational IT environments smoothly. With no infrastructure needed, and delivered as SaaS, it can be deployed rapidly and flexibly.

Read our Success Stories
Thales and ip4sure link cybersecurity with optimal user experience - case study.

Thales SafeNet Trusted Access (STA) and Stream IT Consulting - Case Study

Thales SafeNet Trusted Access (STA) and Benchmark Electronics - Case Study

Thales SafeNet Trusted Access (STA) and Canopius Services Ltd. - Case Study

Thales SafeNet Trusted Access (STA) and Shoreline Var Communication Technology Services (CTS) - Case Study

Thales SafeNet Trusted Access (STA) and Crown Agents Bank - Case Study

Thales SafeNet Trusted Access (STA) and Paragon Exchange - Case Study

Thales SafeNet Trusted Access (STA) and Neuberger Gebäudeautomation GmbH - Case Study

Thanks to SafeNet Trusted Access, Itancia secures remote access to its Information Systems - Case Study

Thales's SafeNet Authentication Service Helps Prevent Employee Identity Theft at VUMC - Case Study

A Court of Auditors in Brazil Ensures Confidential Data Protection, Compliance, and Agility with Thales Technology

JAN© Accountants and Business Consultants extend their long-standing partnership with Thales by migrating to SafeNet Trusted Access - Case Study

US Healthcare Organization selected SafeNet Trusted Access to modernize their Authentication and Access Management

Thales Helps India’s Largest Car Manufacturer Secure Remote Access Of Its VPN Users

Singapore Charity Organization Addresses Cloud Access Management Solutions with SafeNet Trusted Access (STA)

India’s Largest Media Conglomerate Secures Remote Access With Thales’s Safenet Trusted Access

Healthcare Organization in Netherlands protects Office 365 with SafeNet Trusted Access

German Manufacturing Group selected SafeNet Trusted Access to move securely to the Cloud

Real Estate Development Company Ensures Secure Cloud Access with Thales's SafeNet Trusted Access

Healthcare Organization Addresses Cloud Access Management Solutions with SafeNet Trusted Access (STA)

Law Firm lifts the Fog over Cloud App Security with SafeNet Trusted Access

Industrial Company Triumphs with Flexible Access Security

Westcon Relies on SafeNet Trusted Access for Constant Uptime and Reduced Costs

A Global Bank modernizes its Authentication Framework with SafeNet IDPrime Virtual

SafeNet Authentication Service Solution offers Multi-factor Authentication in Compliance with IT Security Guidelines (G3)
Testimonial: itancia secures remote access with safenet trusted access.

Thales helps prevent identity theft at VUMC

Real Estate Development Co. Ensures Secure Access with SafeNet Trusted Access

Try SafeNet Trusted Access for Yourself
Test drive our fully automated Identity-as-a-Service for 30 days, complete with mobile tokens and template-based integrations.
IDC Spotlight: It's Time to Modernize Multifactor Authentication
ISO GQL: A Defining Moment in the History of Database Innovation Learn More
- Neo4j Graph Database Self-managed, deploy anywhere
- Neo4j AuraDB Fully-managed graph database as a service
- Neo4j Graph Data Science Graph analytics and modeling platform
- Deployment Center Get started. Download, integrate, and deploy.
- GRAPH TOOLS
- Neo4j Developer Tools Tools to make graph application development easier
- Neo4j Workspace Import, explore, and query Neo4j
- Neo4j Bloom Easy graph visualization and exploration
- Cypher Query Language Declarative graph query language, created by Neo4j
- Neo4j GraphQL Library Low-code, open-source API library
- Generative AI Back your LLMs with a knowledge graph for better business AI
- Industries and Use Cases Fraud detection, knowledge graphs, financial services, and more
- Case Studies Customer success stories across industries
- Customers Companies, governments, and NGOs using Neo4j
- Developer Center Best practices, guides, tutorials, and downloads
- Developer Blog Deep dives into more technical Neo4j topics
- Community A global forum for online discussion
- DATA SCIENTISTS
- Graph Data Science Home Learn what Neo4j offers for data science
- Get Started With Graph Data Science Download or get started in Sandbox today
- Data Science Community A global forum for data-driven professionals
- Resource Library White papers, data sheets, and more
- Executive Insights Get to know Graph Technology
- Neo4j Blog Daily reads on general Neo4j topics
- FEATURED EVENTS
- GraphSummit Touring 20+ cities globally. Join us for free and hear from data and business trailblazers.
- Connections Free, online conference every quarter focusing on new themes every time
- QUICK LINKS
- Find a Partner
- Become a Partner
- Solution Partners
- OEM Partners
- Technology Partners
- Partner Portal Login
- Awards and Honors
- Graphs4Good
Neo4j Graph Database
Intro to the advantages of graph databases
Neo4j AuraDB
Fully-managed graph database as a service
Neo4j Graph Data Science
Graph Analytics and modeling platforms
Deployment Center
Get started. Download, integrate, and deploy.
- Neo4j Data Connectors Download Apache Kafka, Apache Spark, and BI tools
Generative AI
Back your LLMs with a Knowledge Graph for better business AI
Industries & Use Cases
Fraud detection, knowledge graphs, financial services, and more
All Use Cases
Developer Center
Best practices, guides, tutorials, and downloads
GraphAcademy
Free online courses and certifications. Join the 100K+ Neo4j experts.
Hear directly from data and business trailblazers
Touring 20+ cities globally | Free
Join our online conference. New themes every time.
Virtual | Every Quarter | Free
- Get Started Free
Warning: JavaScript is disabled on your browser. Parts of Neo4j.com will not work properly.
(Neo4j Blog)←[:BACK]
Top 10 Use Cases: Identity and Access Management
Jim webber , chief scientist, neo4j mar 15, 2021 4 mins read.

Use Case #9: Identity and Access Management
Why use graph technology for identity and access management.
- Which resources – company structures, products, services, agreements and end users – can a particular administrator manage? (Top-down)
- Given a particular resource, who can modify its access settings? (Bottom-up)
- Which resource can an end-user access?
Example: Telenor Norway
Neo4j’s fully managed cloud service
Free online courses & certifications. Join 100K+ Neo4j experts!
Developer Blog
Deep dives into more technical Neo4j topics
Jim Webber, Chief Scientist, Neo4j
Related Articles

- Manage Feature Requests
- How to become Salesforce Certified
- Salesforce Associate Certification
- Salesforce Administrator 201 Certification
- Salesforce Platform App Builder Certification
- Salesforce Administrator 301 Certification
- Salesforce Sales Cloud Certification
- Salesforce Service Cloud Certification
- Salesforce Experience Cloud Certification
- Salesforce Platform Developer 1 Certification
- Salesforce Javascript Developer I Certification
- Salesforce Platform Developer 2 Certification
- Salesforce Developer Certification
- Salesforce Sharing and Visibility Architect Certification
- Salesforce Data Architect Certification
- Salesforce Integration Architect Certification Information
- Salesforce Business Analyst Certification Guide
- Salesforce Marketing Cloud Email Specialist Certification
- Salesforce User Experience Designer Certification
- Salesforce AI Associate Certification
- Salesforce Field Service Consultant Certification Guide
- Salesforce Development Lifecycle and Deployment Architect
- Certification Courses
- Corporate Pricing
- User Testimonials
- Feature Requests
focusonforce.com

- FoF Slack Community
- Mobile Usage FAQs
- Moderate Comments
- Manage Credits
- Course Catalog
- Set a Goal!
- My Past Results
- Get the Book!
- Focus Merch
- Focus People
- Focus Videos
Identity and Access Management Architect Study Guide
Identity and access management architect - certification goal.
- May 18, 2024
- Your Target Date

Identity Management Concepts 6 Topics
- Describe common authentication patterns and understand the differences between each one.
- Describe the building blocks that are part of an identity solution (authentication, authorization, & accountability) and how you enable those building blocks using Salesforce features.
- Describe how trust is established between two systems.
- Given a scenario, recommend the appropriate method for provisioning users in Salesforce.
- Given a scenario, troubleshoot common points of failure that may be encountered in a single sign-on solution (SAML, OAuth, etc.)
- Knowledge Check
Accepting Third-Party Identity in Salesforce
Salesforce as an identity provider, access management best practices, salesforce identity, community (partner and customer), cancel reply.
You must be logged in to post a comment.
Privacy Overview
Google tag manager.
Google Tag Manager (GTM) is Google’s free tool for everyone to manage and deploy analytics and marketing tags as well as other code snippets using an intuitive web UI.
Master data management: The key to getting more from your data
Picture this: a sales representative at a multibillion-dollar organization has an upcoming meeting with a prospective client. She searches for the client in the organization’s customer relationship management software and finds several accounts with the same name. She struggles to learn more about the products and services the client is already buying, the customer contacts that have already been engaged, and the relationships the contact may have with other sales representatives within the organization. As a result, the sales representative spends several hours manually pulling together information to get organized for the upcoming meeting.
About the authors
This article is a collaborative effort by Aziz Shaikh, Holger Harreis , Jorge Machado , and Kayvaun Rowshankish , with Rachit Saxena and Rajat Jain, representing views from McKinsey Digital.
This scenario is an example of poor master data management (MDM), which commonly results in suboptimal customer and employee experience, higher costs, and lost revenue opportunities. MDM is a critical component of any organization’s data strategy (see sidebar “About master data management”). These capabilities can make or break an organization’s efficiency and reliability—particularly in complex organizations with multiple business units, where data silos can lead to inefficiencies and errors.
About master data management
Typically, organizations have four types of data: transaction, reference, derived, and master. Of these, master data provides the most relevant, foundational information about entities and their attributes, unique identifiers, hierarchies, and relationships within an organization. This information is shared across business functions and systems to support business processes and decision making.
In 2023, McKinsey surveyed more than 80 large global organizations 1 Companies surveyed earned more than $100 million in annual revenue. across several industries to learn more about how they organize, use, and mature their master data. McKinsey’s Master Data Management Survey indicated that organizations have four top objectives in maturing their MDM capabilities: improving customer experience and satisfaction, enhancing revenue growth by presenting better cross- and up-selling opportunities, increasing sales productivity, and streamlining reporting (Exhibit 1).
MDM plays an important role with modern data architecture concepts and creates value in five ways:
- MDM cleans, enriches, and standardizes data for key functions, such as customer or product data, before it is loaded into the data lake. In this way, MDM ensures that data is accurate, complete, and consistent across an organization.
- In the context of data products, MDM provides a hub for high-quality data across entities, which improves the effectiveness, consistency, and reliability of data products for improved decision making, accurate reporting and analysis, and compliance with local regulations and standards.
- MDM standardizes data across entities to provide a unified view across various systems.
- MDM can act as a system of reference that shares data with applications and other domains via web services, typically representational state transfer application programming interfaces (REST APIs).
- MDM and artificial intelligence (AI) can benefit from each other. For instance, MDM can leverage AI algorithms to identify duplicate records and merge them intelligently, which can enhance the performance and reliability of generative AI systems.
But many organizations have not fully harnessed the potential of MDM. This article builds on the insights from our MDM survey, describes the common challenges companies face when integrating MDM capabilities, and highlights areas in which MDM could be optimized to help businesses gain a competitive advantage.
Common issues organizations face when implementing MDM
Small and large organizations alike can benefit from implementing MDM models, yet collecting and aggregating quality data can be difficult because of funding constraints, insufficient technological support, and low-caliber data. Based on our survey results, following are some of the most prevalent challenges to implementing MDM.
Difficulty of making a business case
Demonstrating potential savings through reduced data errors, enhanced operational efficiency, and improved decision making can provide a clear return on investment for MDM initiatives. However, this return is inherently difficult to quantify, so positioning MDM as a priority ahead of projects with more visible, immediate benefits can be challenging. Consequently, despite MDM’s potential to enhance an organization, leaders may have a difficult time building a business case for augmenting their MDM and investing in associated architecture and technology capabilities.

Creating value beyond the hype
Let’s deliver on the promise of technology from strategy to scale.
Organizational silos
Types of master data domains.
A variety of categories can serve as master data domains, and each serves a specific purpose. The most common categories include the following:
Customer data. Customer data includes key details such as customer contact information, purchasing history, preferences, and demographic data. Organizations can leverage customer data to optimize marketing strategies, personalize customer experiences, and foster long-term relationships.
Client data. Client data typically includes client names, contact information, billing and shipping addresses, payment terms, key decision makers, and other client-specific identifiers. Business-to-business (B2B) organizations can manage client data to tailor their strategies, personalize communications, and optimize sales and marketing efforts to better serve their clients’ needs and preferences.
Product data. Product data includes attributes such as product names, descriptions, SKUs, pricing, and specifications. Product data typically spans across R&D, supply chain, and sales.
Supplier data. Supplier data includes attributes such as vendor names, contact details, payment terms, tax information, and vendor-specific codes. Accurate supplier data helps to establish a single, complete, and consistent definition of vendors across the organization.
Financial data. Financial data typically includes information about legal or management entities (a company code, for instance), a chart of accounts, cost and profit centers, and financial hierarchies.
Employee data. Employee data includes attributes such as employee names, contact information, job titles, employee IDs, department assignments, and payroll information.
Asset data. Asset data includes attributes such as asset name, type, purchase date, installation date, manufacturer details, financial and depreciation details, and maintenance and repair details. Organizations can improve their operational performance by maintaining consistent, accurate, and efficient management of assets across an organization.
According to the McKinsey Master Data Management Survey 2023, 83 percent of organizations consider client and product data to be the most dominant domains.
Eighty percent of organizations responding to our survey reported that some of their divisions operate in silos, each with its own data management requirements, practices, source systems, and consumption behaviors. For example, a sales team may maintain client data in a customer relationship management (CRM) system, while a marketing team may use a client data platform (CDP) to create customer profiles and inform ad campaigns. Silos can lead to inconsistencies and errors, increasing the difficulty of making decisions related to business, data, and technology (see sidebar “Types of master data domains”).
Treating MDM as a technology discipline only
Organizations typically think of MDM as a technology discipline rather than as a differentiator that can drive enterprise value. According to our survey, only 16 percent of MDM programs are funded as organization-wide strategic programs, leaving IT or tech functions to carry the financial responsibility (Exhibit 2). Sixty-two percent of respondents reported that their organizations had no well-defined process for integrating new and existing data sources, which may hinder the effectiveness of MDM.
While technology plays a crucial role, the success of MDM initiatives requires significant business influence and sponsorship to set the strategic direction, understand data dependencies, improve the quality of data, enhance business processes, and, ultimately, support the organization in achieving its goals. It’s important for the role of data owner to be played by a business stakeholder—specifically, the head of the business unit that uses the data most, such as the head of sales and marketing for the client data domain. That leader can provide guidance for defining data requirements and data quality rules that are aligned with the business’s goals.
Poor data quality
Poor-quality data cannot deliver analytics-based insights without substantial manual adjustment. According to the MDM survey, 82 percent of respondents spent one or more days per week resolving master data quality issues, and 66 percent used manual review to assess, monitor, and manage the quality of their master data. Consequently, large, multidivisional organizations may be unable to efficiently generate KPIs or other metrics, and sales representatives may be unable to quickly generate a consistent, holistic view of prospective clients. According to the MDM survey, the most prevalent issues in organizations’ data quality were incompleteness, inconsistency, and inaccuracy (Exhibit 3).
In addition to incompleteness, inconsistency, and accuracy, many companies also contend with issues of uniqueness, or duplicate information, across systems. Traditionally, organizations classify data assets based on the stakeholders they interact with, but this approach can lead to duplication of information. For example, a supplier to an organization can also be its customer. These circumstances have led to the design of a “party” data domain that generalizes the characteristics of a person or organization and establishes the connection between them and their distinctive roles to the company.
Master data quality issues can cause customer dissatisfaction, operational inefficiencies, and poor decision making. Furthermore, companies handling private or sensitive consumer information have stricter compliance requirements and data quality, security, and privacy standards. Without good data, implementing MDM processes will be difficult.
Complex data integration requirements
Organizations may find it difficult to integrate MDM into their existing systems. Compatibility issues, data migration challenges, and system upgrades can hinder successful MDM implementation, and minimizing integration latency is crucial to provide timely and accurate data to the MDM system. Organizations may have to significantly model, map, and transform data systems so they can work with newer and older technologies.
How to effectively implement and optimize MDM capabilities
To overcome these challenges and successfully implement and optimize MDM capabilities, organizations must clearly identify the value they hope to create based on their priority business use cases such as operational efficiency and customer insights, which lead to cost savings and revenue growth. Organizations should measure the impact and effectiveness of MDM implementation using metrics such as ROI, total cost of ownership, and performance baselines. Organizations should maintain a forward-looking approach to adopt modern tools and technologies; create a robust data governance model backed by performance KPIs; and plan for capability building among stakeholders to ensure a uniform adoption of MDM principles.

The data dividend: Fueling generative AI
Build a ‘golden record’ that contains the most up-to-date information.
An MDM “golden record” is a repository that holds the most accurate information available in the organization’s data ecosystem. For example, a golden record of client data is a single, trusted source of truth that can be used by marketing and sales representatives to analyze customer preferences, trends, and behaviors; improve customer segmentation; offer personalized products and services; and increase cross-sales, interactions, customer experiences, and retention.
To build a golden record that contains the most up-to-date information, organizations integrate data from every business unit into the golden record and update it as more accurate information becomes available. Integrating information can be done with the help of AI and machine learning (ML) technology. Alternatively, organizations may establish one existing system as the golden record for a specific data domain to maintain consistency, precision, and timeliness across the enterprise.
Four common master data management design approaches
Organizations typically use one of four master data management design approaches, depending on the complexity of their data:
Registry MDM. This model aggregates data from multiple sources to spot duplicates in information. It is a simple, inexpensive approach that large, global organizations with many data sources often find helpful.
Consolidation MDM. This approach periodically sorts and matches information from multiple source systems to create or update the master data record. Simple and inexpensive to set up, it is a good option for organizations seeking to analyze large sets of data.
Centralized MDM. This approach establishes a single master repository to create, update, and maintain data, and shares it back with the respective source systems. This model is good for banks, insurance companies, government agencies, and hospital networks that require strict compliance to maintain integrity and control over their data.
Coexistence MDM. This approach creates and updates data in source systems, giving businesses the flexibility and autonomy to manage data attributes at the division or business-unit level while maintaining consistent core client data. This model is especially good for large, complex enterprises with many segments and business-unit structures that are frequently integrating new clients into their databases.
Organizations typically start by deploying more rudimentary MDM models, such as registry or consolidation, then evolve to more mature approaches, such as centralized or coexistence. These more mature models are more flexible but also more complex. When choosing an MDM deployment approach, organizations should consider the following questions, among others:
- How should the organization centralize and streamline master data across different systems and locations to maximize accessibility and usability?
- What methodologies should be used to manage the complexity of data relationships and structures to improve efficiency and interoperability across systems?
- What strategies need to be implemented to enable real-time master data updates and guarantee instant access to the most current and accurate information?
- How should the organization maintain consistent, high-quality data across all departments to support data-driven decision making?
- What initiatives need to be implemented to empower business units to increase autonomy and maturity, fostering innovation and agility throughout the organization?
- Which systems must be seamlessly integrated with the MDM strategy to establish a cohesive and unified data ecosystem?
- How should MDM support and enhance current and future business processes to drive sustainable growth and competitive advantage?
- What proactive measures should be in place to address regulatory and compliance requirements, ensuring risk mitigation and adherence to industry best practices?
There are four common MDM design approaches that can be used to update the golden record within the business unit data (see sidebar “Four common master data management design approaches”). Deploying a modular architecture enables fit-for-purpose consumption and integration patterns with various systems to manage the golden record. For example, every mastered client record could be linked back to the source systems and mapped to a hierarchy to show association in the MDM system. Alternatively, client data could be mastered and assigned a unique client ID within the golden record to stitch together data from all systems and create a single portfolio of a client.
Establish a robust data governance model to maintain integrity and reliability of MDM capabilities
Only 29 percent of companies responding to our survey had full upstream and downstream MDM integrations with source systems and business applications, as well as all governance or stewardship roles, in place. Organizations should clearly identify the single source of truth for data and properly train employees on handling integration failures to avoid saving stale information.
Data governance models for MDM should be designed with clear roles and responsibilities, be managed by a governance council with representatives from different business units and IT, and be shepherded by someone who can serve as an MDM liaison among business, data, and technology stakeholders. The structure should be complemented by a clearly defined policy framework and a tailored, business-backed, and IT-supported operating model for master data domains. These data governance processes will allow upstream system owners and a data governance council to address data quality issues—for example, when the MDM identifies new or updated information as conflicting with other information based on the survivorship strategy.
Choose an MDM tool that enhances data quality and accelerates transformation
MDM tools are becoming more intuitive and user-friendly, and recent innovations in AI, ML, cloud technologies, and federated architectures have opened new possibilities for data mastering and processing. For example, AI-enabled tools use pretrained AI and ML models to automate data quality, data matching, and entity resolution tasks with a higher degree of accuracy and greater efficiency. According to the survey, 69 percent of organizations are already using AI as part of their overall data management capabilities; however, only 31 percent are using advanced AI-based techniques to enhance match-and-merge capabilities and to improve master data quality more broadly.
Organizations should choose data management tools that align with their priorities and make the transition seamless. It’s also important to consider the return on investment and the incremental value that each MDM tool can bring to the organization. When choosing an MDM tool, relevant business stakeholders should understand data processes and requirements, including the data elements that affect business operations and the priority use cases, and then help determine the technology capabilities and workflows that are required to integrate new systems.
For example, stakeholders should assess the maturity of their organization’s capabilities, including its data quality, matching, and entity resolution, to determine how easily new systems will be able to integrate with existing systems and technologies. It is also important to consider these systems’ scalability and flexibility to accommodate future growth and evolving data management needs. Moreover, AI and ML capabilities should be considered to help the MDM tool automate tasks to improve data quality.
Plan for capability building and change management
Organizations that implement technology without changing their processes and the way people work with master data may not fully reap the benefits of MDM.
Change management is crucial to ensure that employees understand and embrace the changes brought about by MDM implementation. It typically includes securing executive sponsorship to demonstrate the importance of MDM to the organization; engaging with business and technology stakeholders to communicate the vision; setting expectations for accountability and processes; and rolling out comprehensive training programs to educate employees on MDM and data principles, processes, and tools.
Start with a pilot implementation
Organizations can start integrating MDM tools by first piloting MDM in one domain to validate its design, governance model, and workflows in a controlled environment. Organizations can then easily identify any potential issues or challenges and make the necessary adjustments before scaling up the implementation to other master data domains or to the entire organization. Piloting these tools also allows organizations to gather feedback from users and stakeholders to understand the user experience, identify areas for improvement, and make necessary changes to optimize the MDM tool and workflows.
Implementing and optimizing MDM capabilities can seem daunting, especially for large organizations with multiple complex systems. But once successfully deployed across master data domains—using an optimal design approach, an efficient governance structure, and sufficient change management efforts—MDM can ensure that high-quality data is available for strategic decision making, leading to cost savings and revenue opportunities across an organization.
Aziz Shaikh and Jorge Machado are partners in McKinsey’s New York office, where Kayvaun Rowshankish is a senior partner, Rachit Saxena is a consultant, and Rajat Jain is an associate partner. Holger Harreis is a senior partner in the Düsseldorf office.
The authors wish to thank Vladimir Alekseev for his contributions to this article.
Explore a career with us
Related articles.

How to unlock the full value of data? Manage it like a product

Realizing more value from data projects

Demystifying data mesh
- Open access
- Published: 09 May 2024
Evaluation of integrated community case management of the common childhood illness program in Gondar city, northwest Ethiopia: a case study evaluation design
- Mekides Geta 1 ,
- Geta Asrade Alemayehu 2 ,
- Wubshet Debebe Negash 2 ,
- Tadele Biresaw Belachew 2 ,
- Chalie Tadie Tsehay 2 &
- Getachew Teshale 2
BMC Pediatrics volume 24 , Article number: 310 ( 2024 ) Cite this article
127 Accesses
Metrics details
Integrated Community Case Management (ICCM) of common childhood illness is one of the global initiatives to reduce mortality among under-five children by two-thirds. It is also implemented in Ethiopia to improve community access and coverage of health services. However, as per our best knowledge the implementation status of integrated community case management in the study area is not well evaluated. Therefore, this study aimed to evaluate the implementation status of the integrated community case management program in Gondar City, Northwest Ethiopia.
A single case study design with mixed methods was employed to evaluate the process of integrated community case management for common childhood illness in Gondar town from March 17 to April 17, 2022. The availability, compliance, and acceptability dimensions of the program implementation were evaluated using 49 indicators. In this evaluation, 484 mothers or caregivers participated in exit interviews; 230 records were reviewed, 21 key informants were interviewed; and 42 observations were included. To identify the predictor variables associated with acceptability, we used a multivariable logistic regression analysis. Statistically significant variables were identified based on the adjusted odds ratio (AOR) with a 95% confidence interval (CI) and p-value. The qualitative data was recorded, transcribed, and translated into English, and thematic analysis was carried out.
The overall implementation of integrated community case management was 81.5%, of which availability (84.2%), compliance (83.1%), and acceptability (75.3%) contributed. Some drugs and medical equipment, like Cotrimoxazole, vitamin K, a timer, and a resuscitation bag, were stocked out. Health care providers complained that lack of refreshment training and continuous supportive supervision was the common challenges that led to a skill gap for effective program delivery. Educational status (primary AOR = 0.27, 95% CI:0.11–0.52), secondary AOR = 0.16, 95% CI:0.07–0.39), and college and above AOR = 0.08, 95% CI:0.07–0.39), prescribed drug availability (AOR = 2.17, 95% CI:1.14–4.10), travel time to the to the ICCM site (AOR = 3.8, 95% CI:1.99–7.35), and waiting time (AOR = 2.80, 95% CI:1.16–6.79) were factors associated with the acceptability of the program by caregivers.
Conclusion and recommendation
The overall implementation status of the integrated community case management program was judged as good. However, there were gaps observed in the assessment, classification, and treatment of diseases. Educational status, availability of the prescribed drugs, waiting time and travel time to integrated community case management sites were factors associated with the program acceptability. Continuous supportive supervision for health facilities, refreshment training for HEW’s to maximize compliance, construction clean water sources for HPs, and conducting longitudinal studies for the future are the forwarded recommendation.
Peer Review reports
Integrated Community Case Management (ICCM) is a critical public health strategy for expanding the coverage of quality child care services [ 1 , 2 ]. It mainly concentrated on curative care and also on the diagnosis, treatment, and referral of children who are ill with infectious diseases [ 3 , 4 ].
Based on the World Health Organization (WHO) and the United Nations Children’s Fund (UNICEF) recommendations, Ethiopia adopted and implemented a national policy supporting community-based treatment of common childhood illnesses like pneumonia, Diarrhea, uncomplicated malnutrition, malaria and other febrile illness and Amhara region was one the piloted regions in late 2010 [ 5 ]. The Ethiopian primary healthcare units, established at district levels include primary hospitals, health centers (HCs), and health posts (HPs). The HPs are run by Health Extension Workers (HEWs), and they have function of monitoring health programs and disease occurrence, providing health education, essential primary care services, and timely referrals to HCs [ 6 , 7 ]. The Health Extension Program (HEP) uses task shifting and community ownership to provide essential health services at the first level using the health development army and a network of woman volunteers. These groups are organized to promote health and prevent diseases through community participation and empowerment by identifying the salient local bottlenecks which hinder vital maternal, neonatal, and child health service utilization [ 8 , 9 ].
One of the key steps to enhance the clinical case of health extension staff is to encourage better growth and development among under-five children by health extension. Healthy family and neighborhood practices are also encouraged [ 10 , 11 ]. The program also combines immunization, community-based feeding, vitamin A and de-worming with multiple preventive measures [ 12 , 13 ]. Now a days rapidly scaling up of ICCM approach to efficiently manage the most common causes of morbidity and mortality of children under the age of five in an integrated manner at the community level is required [ 14 , 15 ].
Over 5.3 million children are died at a global level in 2018 and most causes (75%) are preventable or treatable diseases such as pneumonia, malaria and diarrhea [ 16 ]. About 99% of the global burden of mortality and morbidity of under-five children which exists in developing countries are due to common childhood diseases such as pneumonia, diarrhea, malaria and malnutrition [ 17 ].
In 2013, the mortality rate of under-five children in Sub-Saharan Africa decreased to 86 deaths per 1000 live birth and estimated to be 25 per 1000live births by 2030. However, it is a huge figure and the trends are not sufficient to reach the target [ 18 ]. About half of global under-five deaths occurred in sub-Saharan Africa. And from the top 26 nations burdened with 80% of the world’s under-five deaths, 19 are in sub-Saharan Africa [ 19 ].
To alleviate the burden, the Ethiopian government tries to deliver basic child care services at the community level by trained health extension workers. The program improves the health of the children not only in Ethiopia but also in some African nations. Despite its proven benefits, the program implementation had several challenges, in particular, non-adherence to the national guidelines among health care workers [ 20 ]. Addressing those challenges could further improve the program performance. Present treatment levels in sub-Saharan Africa are unacceptably poor; only 39% of children receive proper diarrhea treatment, 13% of children with suspected pneumonia receive antibiotics, 13% of children with fever receive a finger/heel stick to screen for malaria [ 21 ].
To improve the program performance, program gaps should be identified through scientific evaluations and stakeholder involvement. This evaluation not only identify gaps but also forward recommendations for the observed gaps. Furthermore, the implementation status of ICCM of common childhood illnesses has not been evaluated in the study area yet. Therefore, this work aimed to evaluate the implementation status of integrated community case management program implementation in Gondar town, northwest Ethiopia. The findings may be used by policy makers, healthcare providers, funders and researchers.
Method and material
Evaluation design and settings.
A single-case study design with concurrent mixed-methods evaluation was conducted in Gondar city, northwest Ethiopia, from March 17 to April 17, 2022. The evaluability assessment was done from December 15–30, 2021. Both qualitative and quantitative data were collected concurrently, analyzed separately, and integrated at the result interpretation phase.
The evaluation area, Gondar City, is located in northwest Ethiopia, 740 km from Addis Ababa, the capital city of the country. It has six sub-cities and thirty-six kebeles (25 urban and 11 rural). In 2019, the estimated total population of the town was 338,646, and 58,519 (17.3%) were under-five children. In the town there are eight public health centers and 14 health posts serving the population. All health posts provide ICCM service for more than 70,852 populations.
Evaluation approach and dimensions
Program stakeholders.
The evaluation followed a formative participatory approach by engaging the potential stakeholders in the program. Prior to the development of the proposal, an extensive discussion was held with the Gondar City Health Department to identify other key stakeholders in the program. Service providers at each health facility (HCs and HPs), caretakers of sick children, the Gondar City Health Office (GCHO), the Amhara Regional Health Bureau (ARHB), the Minister of Health (MoH), and NGOs (IFHP and Save the Children) were considered key stakeholders. During the Evaluability Assessment (EA), the stakeholders were involved in the development of evaluation questions, objectives, indicators, and judgment criteria of the evaluation.
Evaluation dimensions
The availability and acceptability dimensions from the access framework [ 22 ] and compliance dimension from the fidelity framework [ 23 ] were used to evaluate the implementation of ICCM.
Population and samplings
All under-five children and their caregivers attended at the HPs; program implementers (health extension workers, healthcare providers, healthcare managers, PHCU focal persons, MCH coordinators, and other stakeholders); and ICCM records and registries in the health posts of Gondar city administration were included in the evaluation. For quantitative data, the required sample size was proportionally allocated for each health post based on the number of cases served in the recent one month. But the qualitative sample size was determined by data saturation, and the samples were selected purposefully.
The data sources and sample size for the compliance dimension were all administrative records/reports and ICCM registration books (230 documents) in all health posts registered from December 1, 2021, to February 30, 2022 (three months retrospectively) included in the evaluation. The registries were assessed starting from the most recent registration number until the required sample size was obtained for each health post.
The sample size to measure the mothers’/caregivers’ acceptability towards ICCM was calculated by taking prevalence of caregivers’ satisfaction on ICCM program p = 74% from previously similar study [ 24 ] and considering standard error 4% at 95% CI and 10% non- responses, which gave 508. Except those who were seriously ill, all caregivers attending the ICCM sites during data collection were selected and interviewed consecutively.
The availability of required supplies, materials and human resources for the program were assessed in all 14HPs. The data collectors observed the health posts and collected required data by using a resources inventory checklist.
A total of 70 non-participatory patient-provider interactions were also observed. The observations were conducted per each health post and for health posts which have more than one health extension workers one of them were selected randomly. The observation findings were used to triangulate the findings obtained through other data collection techniques. Since people may act accordingly to the standards when they know they are observed for their activities, we discarded the first two observations from analysis. It is one of the strategies to minimize the Hawthorne effect of the study. Finally a total of 42 (3 in each HPs) observations were included in the analysis.
Twenty one key informants (14 HEWs, 3 PHCU focal person, 3 health center heads and one MCH coordinator) were interviewed. These key informants were selected since they are assumed to be best teachers in the program. Besides originally developed key informant interview questions, the data collectors probed them to get more detail and clear information.
Variables and measurement
The availability of resources, including trained healthcare workers, was examined using 17 indicators, with weighted score of 35%. Compliance was used to assess HEWs’ adherence to the ICCM treatment guidelines by observing patient-provider interactions and conducting document reviews. We used 18 indicators and a weighted value of 40%.
Mothers’ /caregivers’/ acceptance of ICCM service was examined using 14 indicators and had a weighted score of 25%. The indicators were developed with a five-point Likert scale (1: strongly disagree, 2: disagree, 3: neutral, 4: agree and 5: strongly agree). The cut off point for this categorization was calculated using the demarcation threshold formula: ( \(\frac{\text{t}\text{o}\text{t}\text{a}\text{l}\, \text{h}\text{i}\text{g}\text{h}\text{e}\text{s}\text{t}\, \text{s}\text{c}\text{o}\text{r}\text{e}-\,\text{t}\text{o}\text{t}\text{a}\text{l}\, \text{l}\text{o}\text{w}\text{e}\text{s}\text{t} \,\text{s}\text{c}\text{o}\text{r}\text{e}}{2}) +total lowest score\) ( 25 – 27 ). Those mothers/caregivers/ who scored above cut point (42) were considered as “satisfied”, otherwise “dissatisfied”. The indicators were adapted from the national ICCM and IMNCI implementation guideline and other related evaluations with the participation of stakeholders. Indicator weight was given by the stakeholders during EA. Indicators score was calculated using the formula \(\left(achieved \,in \%=\frac{indicator \,score \,x \,100}{indicator\, weight} \right)\) [ 26 , 28 ].
The independent variables for the acceptability dimension were socio-demographic and economic variables (age, educational status, marital status, occupation of caregiver, family size, income level, and mode of transport), availability of prescribed drugs, waiting time, travel time to ICCM site, home to home visit, consultation time, appointment, and source of information.
The overall implementation of ICCM was measured by using 49 indicators over the three dimensions: availability (17 indicators), compliance (18 indicators) and acceptability (14 indicators).
Program logic model
Based on the constructed program logic model and trained health care providers, mothers/caregivers received health information and counseling on child feeding; children were assessed, classified, and treated for disease, received follow-up; they were checked for vitamin A; and deworming and immunization status were the expected outputs of the program activities. Improved knowledge of HEWs on ICCM, increased health-seeking behavior, improved quality of health services, increased utilization of services, improved data quality and information use, and improved child health conditions are considered outcomes of the program. Reduction of under-five morbidity and mortality and improving quality of life in the society are the distant outcomes or impacts of the program (Fig. 1 ).
Integrated community case management of childhood illness program logic model in Gondar City in 2022
Data collection tools and procedure
Resource inventory and data extraction checklists were adapted from standard ICCM tool and check lists [ 29 ]. A structured interviewer administered questionnaire was adapted by referring different literatures [ 30 , 31 ] to measure the acceptability of ICCM. The key informant interview (KII) guide was also developed to explore the views of KIs. The interview questionnaire and guide were initially developed in English and translated into the local language (Amharic) and finally back to English to ensure consistency. All the interviews were done in the local language, Amharic.
Five trained clinical nurses and one BSC nurse were recruited from Gondar zuria and Wegera district as data collectors and supervisors, respectively. Two days training on the overall purpose of the evaluation and basic data collection procedures were provided prior to data collection. Then, both quantitative and qualitative data were gathered at the same time. The quantitative data were gathered from program documentation, charts of ICCM program visitors and, exit interview. Interviews with 21 KIIs and non-participatory observations of patient-provider interactions were used to acquire qualitative data. Key informant interviews were conducted to investigate the gaps and best practices in the implementation of the ICCM program.
A pretest was conducted to 26 mothers/caregivers/ at Maksegnit health post and appropriate modifications were made based on the pretest results. The data collectors were supervised and principal evaluator examined the completeness and consistency of the data on a daily basis.
Data management and analysis
For analysis, quantitative data were entered into epi-data version 4.6 and exported to Stata 14 software for analysis. Narration and tabular statistics were used to present descriptive statistics. Based on established judgment criteria, the total program implementation was examined and interpreted as a mix of the availability, compliance, and acceptability dimensions. To investigate the factors associated with ICCM acceptance, a binary logistic regression analysis was performed. During bivariable analysis, variables with p-values less than 0.25 were included in multivariable analysis. Finally, variables having a p-value less than 0.05 and an adjusted odds ratio (AOR) with a 95% confidence interval (CI) were judged statistically significant. Qualitative data were collected recorded, transcribed into Amharic, then translated into English and finally coded and thematically analyzed.
Judgment matrix analysis
The weighted values of availability, compliance, and acceptability dimensions were 35, 40, and 25 based on the stakeholder and investigator agreement on each indicator, respectively. The judgment parameters for each dimension and the overall implementation of the program were categorized as poor (< 60%), fair (60–74.9%), good (75-84.9%), and very good (85–100%).
Availability of resources
A total of 26 HEWs were assigned within the fourteen health posts, and 72.7% of them were trained on ICCM to manage common childhood illnesses in under-five children. However, the training was given before four years, and they didn’t get even refreshment training about ICCM. The KII responses also supported that the shortage of HEWs at the HPs was the problem in implementing the program properly.
I am the only HEW in this health post and I have not been trained on ICCM program. So, this may compromise the quality of service and client satisfaction.(25 years old HEW with two years’ experience)
All observed health posts had ICCM registration books, monthly report and referral formats, functional thermometer, weighting scale and MUAC tape meter. However, timer and resuscitation bag was not available in all HPs. Most of the key informant finding showed that, in all HPs there was no shortage of guideline, registration book and recording tool; however, there was no OTP card in some health posts.
“Guideline, ICCM registration book for 2–59 months of age, and other different recording and reporting formats and booklet charts are available since September/2016. However, OTP card is not available in most HPs.”. (A 30 years male health center director)
Only one-fifth (21%) of HPs had a clean water source for drinking and washing of equipment. Most of Key-informant interview findings showed that the availability of infrastructures like water was not available in most HPs. Poor linkage between HPs, HCs, town health department, and local Kebele administer were the reason for unavailability.
Since there is no water for hand washing, or drinking, we obligated to bring water from our home for daily consumptions. This increases the burden for us in our daily activity. (35 years old HEW)
Most medicines, such as anti-malaria drugs with RDT, Quartem, Albendazole, Amoxicillin, vitamin A capsules, ORS, and gloves, were available in all the health posts. Drugs like zinc, paracetamol, TTC eye ointment, and folic acid were available in some HPs. However, cotrimoxazole and vitamin K capsules were stocked-out in all health posts for the last six months. The key informant also revealed that: “Vitamin K was not available starting from the beginning of this program and Cotrimoxazole was not available for the past one year and they told us they would avail it soon but still not availed. Some essential ICCM drugs like anti malaria drugs, De-worming, Amoxicillin, vitamin A capsules, ORS and medical supplies were also not available in HCs regularly.”(28 years’ Female PHCU focal)
The overall availability of resources for ICCM implementation was 84.2% which was good based on our presetting judgment parameter (Table 1 ).
Health extension worker’s compliance
From the 42 patient-provider interactions, we found that 85.7%, 71.4%, 76.2%, and 95.2% of the children were checked for body temperature, weight, general danger signs, and immunization status respectively. Out of total (42) observation, 33(78.6%) of sick children were classified for their nutritional status. During observation time 29 (69.1%) of caregivers were counseled by HEWs on food, fluid and when to return back and 35 (83.3%) of children were appointed for next follow-up visit. Key informant interviews also affirmed that;
“Most of our health extension workers were trained on ICCM program guidelines but still there are problems on assessment classification and treatment of disease based on guidelines and standards this is mainly due to lack refreshment training on the program and lack of continuous supportive supervision from the respective body.” (27years’ Male health center head)
From 10 clients classified as having severe pneumonia cases, all of them were referred to a health center (with pre-referral treatment), and from those 57 pneumonia cases, 50 (87.7%) were treated at the HP with amoxicillin or cotrimoxazole. All children with severe diarrhea, very severe disease, and severe complicated malnutrition cases were referred to health centers with a pre-referral treatment for severe dehydration, very severe febrile disease, and severe complicated malnutrition, respectively. From those with some dehydration and no dehydration cases, (82.4%) and (86.8%) were treated at the HPs for some dehydration (ORS; plan B) and for no dehydration (ORS; plan A), respectively. Moreover, zinc sulfate was prescribed for 63 (90%) of under-five children with some dehydration or no dehydration. From 26 malaria cases and 32 severe uncomplicated malnutrition and moderate acute malnutrition cases, 20 (76.9%) and 25 (78.1%) were treated at the HPs, respectively. Of the total reviewed documents, 56 (93.3%), 66 (94.3%), 38 (84.4%), and 25 (78.1%) of them were given a follow-up date for pneumonia, diarrhea, malaria, and malnutrition, respectively.
Supportive supervision and performance review meetings were conducted only in 10 (71.4%) HPs, but all (100%) HPs sent timely reports to the next supervisory body.
Most of the key informants’ interview findings showed that supportive supervision was not conducted regularly and for all HPs.
I had mentored and supervised by supportive supervision teams who came to our health post at different times from health center, town health office and zonal health department. I received this integrated supervision from town health office irregularly, but every month from catchment health center and last integrated supportive supervision from HC was on January. The problem is the supervision was conducted for all programs.(32 years’ old and nine years experienced female HEW)
Moreover, the result showed that there was poor compliance of HEWs for the program mainly due to weak supportive supervision system of managerial and technical health workers. It was also supported by key informants as:
We conducted supportive supervision and performance review meeting at different time, but still there was not regular and not addressed all HPs. In addition to this the supervision and review meeting was conducted as integration of ICCM program with other services. The other problem is that most of the time we didn’t used checklist during supportive supervision. (Mid 30 years old male HC director)
Based on our observation and ICCM document review, 83.1% of the HEWs were complied with the ICCM guidelines and judged as fair (Table 2 ).
Acceptability of ICCM program
Sociodemographic and obstetric characteristics of participants.
A total of 484 study participants responded to the interviewer-administered questionnaire with a response rate of 95.3%. The mean age of study participants was 30.7 (SD ± 5.5) years. Of the total caregivers, the majority (38.6%) were categorized under the age group of 26–30 years. Among the total respondents, 89.3% were married, and regarding religion, the majorities (84.5%) were Orthodox Christian followers. Regarding educational status, over half of caregivers (52.1%) were illiterate (unable to read or write). Nearly two-thirds of the caregivers (62.6%) were housewives (Table 3 ).
All the caregivers came to the health post on foot, and most of them 418 (86.4%) arrived within one hour. The majority of 452 (93.4%) caregivers responded that the waiting time to get the service was less than 30 min. Caregivers who got the prescribed drugs at the health post were 409 (84.5%). Most of the respondents, 429 (88.6%) and 438 (90.5%), received counseling services on providing extra fluid and feeding for their sick child and were given a follow-up date.
Most 298 (61.6%) of the caregivers were satisfied with the convenience of the working hours of HPs, and more than three-fourths (80.8%) were satisfied with the counseling services they received. Most of the respondents, 366 (75.6%), were satisfied with the appropriateness of waiting time and 431 (89%) with the appropriateness of consultation time. The majority (448 (92.6%) of caregivers were satisfied with the way of communicating with HEWs, and 269 (55.6%) were satisfied with the knowledge and competence of HEWs. Nearly half of the caregivers (240, or 49.6%) were satisfied with the availability of drugs at health posts.
The overall acceptability of the ICCM program was 75.3%, which was judged as good. A low proportion of acceptability was measured on the cleanliness of the health posts, the appropriateness of the waiting area, and the competence and knowledge of the HEWs. On the other hand, high proportion of acceptability was measured on appropriateness of waiting time, way of communication with HEWs, and the availability of drugs (Table 4 ).
Factors associated with acceptability of ICCM program
In the final multivariable logistic regression analysis, educational status of caregivers, availability of prescribed drugs, time to arrive, and waiting time were factors significantly associated with the satisfaction of caregivers with the ICCM program.
Accordingly, the odds of caregivers with primary education, secondary education, and college and above were 73% (AOR = 0.27, 95% CI: 0.11–0.52), 84% (AOR = 0.16, 95% CI: 0.07–0.39), and 92% (AOR = 0.08, 95% CI: 0.07–0.40) less likely to accept the program as compared to mothers or caregivers who were not able to read and write, respectively. The odds of caregivers or mothers who received prescribed drugs were 2.17 times more likely to accept the program as compared to their counters (AOR = 2.17, 95% CI: 1.14–4.10). The odds of caregivers or mothers who waited for services for less than 30 min were 2.8 times more likely to accept the program as compared to those who waited for more than 30 min (AOR = 2.80, 95% CI: 1.16–6.79). Moreover, the odds of caregivers/mothers who traveled an hour or less for service were 3.8 times more likely to accept the ICCM program as compared to their counters (AOR = 3.82, 95% CI:1.99–7.35) (Table 5 ).
Overall ICCM program implementation and judgment
The implementation of the ICCM program in Gondar city administration was measured in terms of availability (84.2%), compliance (83.1%), and acceptability (75.3%) dimensions. In the availability dimension, amoxicillin, antimalarial drugs, albendazole, Vit. A, and ORS were available in all health posts, but only six HPs had Ready-to-Use Therapeutic Feedings, three HPs had ORT Corners, and none of the HPs had functional timers. In all health posts, the health extension workers asked the chief to complain, correctly assessed for pneumonia, diarrhea, malaria, and malnutrition, and sent reports based on the national schedule. However, only 70% of caretakers counseled about food, fluids, and when to return, 66% and 76% of the sick children were checked for anemia and other danger signs, respectively. The acceptability level of the program by caretakers and caretakers’/mothers’ educational status, waiting time to get the service and travel time ICCM sites were the factors affecting its acceptability. The overall ICCM program in Gondar city administration was 81.5% and judged as good (Fig. 2 ).
Overall ICCM program implementation and the evaluation dimensions in Gondar city administration, 2022
The implementation status of ICCM was judged by using three dimensions including availability, compliance and acceptability of the program. The judgment cut of points was determined during evaluability assessment (EA) along with the stakeholders. As a result, we found that the overall implementation status of ICCM program was good as per the presetting judgment parameter. Availability of resources for the program implementation, compliance of HEWs to the treatment guideline and acceptability of the program services by users were also judged as good as per the judgment parameter.
This evaluation showed that most medications, equipment and recording and reporting materials available. This finding was comparable with the standard ICCM treatment guide line [ 10 ]. On the other hand trained health care providers, some medications like Zink, Paracetamol and TTC eye ointment, folic acid and syringes were not found in some HPs. However the finding was higher than the study conducted in SNNPR on selected health posts [ 33 ] and a study conducted in Soro district, southern Ethiopia [ 24 ]. The possible reason might be due to low interruption of drugs at town health office or regional health department stores, regular supplies of essential drugs and good supply management and distribution of drug from health centers to health post.
The result of this evaluation showed that only one fourth of health posts had functional ORT Corner which was lower compared to the study conducted in SNNPR [ 34 ]. This might be due poor coverage of functional pipe water in the kebeles and the installation was not set at the beginning of health post construction as reported from one of ICCM program coordinator.
Compliance of HEWs to the treatment guidelines in this evaluation was higher than the study done in southern Ethiopia (65.6%) [ 24 ]. This might be due to availability of essential drugs educational level of HEWs and good utilization of ICCM guideline and chart booklet by HEWs. The observations showed most of the sick children were assessed for danger sign, weight, and temperature respectively. This finding is lower than the study conducted in Rwanda [ 35 ]. This difference might be due to lack of refreshment training and regular supportive supervision for HEWs. This also higher compared to the study done in three regions of Ethiopia indicates that 88%, 92% and 93% of children classified as per standard for Pneumonia, diarrhea and malaria respectively [ 36 ]. The reason for this difference may be due to the presence of medical equipment and supplies including RDT kit for malaria, and good educational level of HEWs.
Moreover most HPs received supportive supervision and performance review meeting was conducted and all of them send reports timely to next level. The finding of this evaluation was lower than the study conducted on implementation evaluation of ICCM program southern Ethiopia [ 24 ] and study done in three regions of Ethiopia (Amhara, Tigray and SNNPR) [ 37 ]. This difference might be due sample size variation.
The overall acceptability of the ICCM program was less than the presetting judgment parameter but slightly higher compared to the study in southern Ethiopia [ 24 ]. This might be due to presence of essential drugs for treating children, reasonable waiting and counseling time provided by HEWs, and smooth communication between HEWs and caregivers. In contrast, this was lower than similar studies conducted in Wakiso district, Uganda [ 38 ]. The reason for this might be due to contextual difference between the two countries, inappropriate waiting area to receive the service and poor cleanness of the HPs in our study area. Low acceptability of caregivers to ICCM service was observed in the appropriateness of waiting area, availability of drugs, cleanness of health post, and competence of HEWs while high level of caregiver’s acceptability was consultation time, counseling service they received, communication with HEWs, treatment given for their sick children and interest to return back for ICCM service.
Caregivers who achieved primary, secondary, and college and above were more likely accept the program services than those who were illiterate. This may more educated mothers know about their child health condition and expect quality service from healthcare providers which is more likely reduce the acceptability of the service. The finding is congruent with a study done on implementation evaluation of ICCM program in southern Ethiopia [ 24 ]. However, inconsistent with a study conducted in wakiso district in Uganda [ 38 ]. The possible reason for this might be due to contextual differences between the two countries. The ICCM program acceptability was high in caregivers who received all prescribed drugs than those did not. Caregivers those waited less than 30 min for service were more accepted ICCM services compared to those more than 30 minutes’ waiting time. This finding is similar compared with the study conducted on implementation evaluation of ICCM program in southern Ethiopia [ 24 ]. In contrary, the result was incongruent with a survey result conducted by Ethiopian public health institute in all regions and two administrative cities of Ethiopia [ 39 ]. This variation might be due to smaller sample size in our study the previous one. Moreover, caregivers who traveled to HPs less than 60 min were more likely accepted the program than who traveled more and the finding was similar with the study finding in Jimma zone [ 40 ].
Strengths and limitations
This evaluation used three evaluation dimensions, mixed method and different data sources that would enhance the reliability and credibility of the findings. However, the study might have limitations like social desirability bias, recall bias and Hawthorne effect.
The implementation of the ICCM program in Gondar city administration was measured in terms of availability (84.2%), compliance (83.1%), and acceptability (75.3%) dimensions. In the availability dimension, amoxicillin, antimalarial drugs, albendazole, Vit. A, and ORS were available in all health posts, but only six HPs had Ready-to-Use Therapeutic Feedings, three HPs had ORT Corners, and none of the HPs had functional timers.
This evaluation assessed the implementation status of the ICCM program, focusing mainly on availability, compliance, and acceptability dimensions. The overall implementation status of the program was judged as good. The availability dimension is compromised due to stock-outs of chloroquine syrup, cotrimoxazole, and vitamin K and the inaccessibility of clean water supply in some health posts. Educational statuses of caregivers, availability of prescribed drugs at the HPs, time to arrive to HPs, and waiting time to receive the service were the factors associated with the acceptability of the ICCM program.
Therefore, continuous supportive supervision for health facilities, and refreshment training for HEW’s to maximize compliance are recommended. Materials and supplies shall be delivered directly to the health centers or health posts to solve the transportation problem. HEWs shall document the assessment findings and the services provided using the registration format to identify their gaps, limitations, and better performances. The health facilities and local administrations should construct clean water sources for health facilities. Furthermore, we recommend for future researchers and program evaluators to conduct longitudinal studies to know the causal relationship of the program interventions and the outcomes.
Data availability
Data will be available upon reasonable request from the corresponding author.
Abbreviations
Ethiopian Demographic and Health Survey
Health Center/Health Facility
Health Extension Program
Health Extension Workers
Health Post
Health Sector Development Plan
Integrated Community Case Management of Common Childhood Illnesses
Information Communication and Education
Integrated Family Health Program
Integrated Management of Neonatal and Childhood Illness
Integrated Supportive Supervision
Maternal and Child Health
Mid Upper Arm Circumference
Non-Government Organization
Oral Rehydration Salts
Outpatient Therapeutic program
Primary health care unit
Rapid Diagnostics Test
Ready to Use Therapeutic Foods
Sever Acute Malnutrition
South Nation Nationalities People Region
United Nations International Child Emergency Fund
World Health Organization
Brenner JL, Barigye C, Maling S, Kabakyenga J, Nettel-Aguirre A, Buchner D, et al. Where there is no doctor: can volunteer community health workers in rural Uganda provide integrated community case management? Afr Health Sci. 2017;17(1):237–46.
Article PubMed PubMed Central Google Scholar
Mubiru D, Byabasheija R, Bwanika JB, Meier JE, Magumba G, Kaggwa FM, et al. Evaluation of integrated community case management in eight districts of Central Uganda. PLoS ONE. 2015;10(8):e0134767.
Samuel S, Arba A. Utilization of integrated community case management service and associated factors among mothers/caregivers who have sick eligible children in southern Ethiopia. Risk Manage Healthc Policy. 2021;14:431.
Article Google Scholar
Kavle JA, Pacqué M, Dalglish S, Mbombeshayi E, Anzolo J, Mirindi J, et al. Strengthening nutrition services within integrated community case management (iCCM) of childhood illnesses in the Democratic Republic of Congo: evidence to guide implementation. Matern Child Nutr. 2019;15:e12725.
Miller NP, Amouzou A, Tafesse M, Hazel E, Legesse H, Degefie T, et al. Integrated community case management of childhood illness in Ethiopia: implementation strength and quality of care. Am J Trop Med Hyg. 2014;91(2):424.
WHO. Annual report 2016: Partnership and policy engagement. World Health Organization, 2017.
Banteyerga H. Ethiopia’s health extension program: improving health through community involvement. MEDICC Rev. 2011;13:46–9.
Article PubMed Google Scholar
Wang H, Tesfaye R, Ramana NV, Chekagn G. CT. Ethiopia health extension program: an institutionalized community approach for universal health coverage. The World Bank; 2016.
Donnelly J. Ethiopia gears up for more major health reforms. Lancet. 2011;377(9781):1907–8.
Legesse H, Degefie T, Hiluf M, Sime K, Tesfaye C, Abebe H, et al. National scale-up of integrated community case management in rural Ethiopia: implementation and early lessons learned. Ethiop Med J. 2014;52(Suppl 3):15–26.
Google Scholar
Miller NP, Amouzou A, Hazel E, Legesse H, Degefie T, Tafesse M et al. Assessment of the impact of quality improvement interventions on the quality of sick child care provided by Health Extension workers in Ethiopia. J Global Health. 2016;6(2).
Oliver K, Young M, Oliphant N, Diaz T, Kim JJNYU. Review of systematic challenges to the scale-up of integrated community case management. Emerging lessons & recommendations from the catalytic initiative (CI/IHSS); 2012.
FMoH E. Health Sector Transformation Plan 2015: https://www.slideshare.net . Accessed 12 Jan 2022.
McGorman L, Marsh DR, Guenther T, Gilroy K, Barat LM, Hammamy D, et al. A health systems approach to integrated community case management of childhood illness: methods and tools. The American Journal of Tropical Medicine and Hygiene. 2012;87(5 Suppl):69.
Young M, Wolfheim C, Marsh DR, Hammamy D. World Health Organization/United Nations Children’s Fund joint statement on integrated community case management: an equity-focused strategy to improve access to essential treatment services for children. The American journal of tropical medicine and hygiene. 2012;87(5 Suppl):6.
Ezbakhe F, Pérez-Foguet A. Child mortality levels and trends. Demographic Research.2020;43:1263-96.
UNICEF, Ending child deaths from pneumonia and diarrhoea. 2016 report: Available at https://data.unicef.org. accessed 13 Jan 2022.
UNITED NATIONS, The Millinium Development Goals Report 2015: Available at https://www.un.org.Accessed 12 Jan 2022
Bent W, Beyene W, Adamu A. Factors Affecting Implementation of Integrated Community Case Management Of Childhood Illness In South West Shoa Zone, Central Ethiopia 2015.
Abdosh B. The quality of hospital services in eastern Ethiopia: Patient’s perspective.The Ethiopian Journal of Health Development. 2006;20(3).
Young M, Wolfheim C, Marsh DR, Hammamy DJTAjotm, hygiene. World Health Organization/United Nations Children’s Fund joint statement on integrated community case management: an equity-focused strategy to improve access to essential treatment services for children.2012;87(5_Suppl):6–10.
Obrist B, Iteba N, Lengeler C, Makemba A, Mshana C, Nathan R, et al. Access to health care in contexts of livelihood insecurity: a framework for analysis and action.PLoS medicine. 2007;4(10):e308.
Carroll C, Patterson M, Wood S, Booth A, Rick J, Balain S. A conceptual framework for implementation fidelity. Implementation science. 2007;2(1):1–9.
Dunalo S, Tadesse B, Abraham G. Implementation Evaluation of Integrated Community Case Management of Common Childhood Illness (ICCM) Program in Soro Woreda, Hadiya Zone Southern Ethiopia 2017 2017.
Asefa G, Atnafu A, Dellie E, Gebremedhin T, Aschalew AY, Tsehay CT. Health System Responsiveness for HIV/AIDS Treatment and Care Services in Shewarobit, North Shewa Zone, Ethiopia. Patient preference and adherence. 2021;15:581.
Gebremedhin T, Daka DW, Alemayehu YK, Yitbarek K, Debie A. Process evaluation of the community-based newborn care program implementation in Geze Gofa district,south Ethiopia: a case study evaluation design. BMC pregnancy and childbirth. 2019;19(1):1–13.
Pitaloka DS, Rizal A. Patient’s satisfaction in antenatal clinic hospital Universiti Kebangsaan Malaysia. Jurnal Kesihatan Masyarakat (Malaysia). 2006;12(1):1–10.
Teshale G, Debie A, Dellie E, Gebremedhin T. Evaluation of the outpatient therapeutic program for severe acute malnourished children aged 6–59 months implementation in Dehana District, Northern Ethiopia: a mixed-methods evaluation. BMC pediatrics. 2022;22(1):1–13.
Mason E. WHO’s strategy on Integrated Management of Childhood Illness. Bulletin of the World Health Organization. 2006;84(8):595.
Shaw B, Amouzou A, Miller NP, Tafesse M, Bryce J, Surkan PJ. Access to integrated community case management of childhood illnesses services in rural Ethiopia: a qualitative study of the perspectives and experiences of caregivers. Health policy and planning.2016;31(5):656 – 66.
Organization WH. Annual report 2016: Partnership and policy engagement. World Health Organization, 2017.
Berhanu D, Avan B. Community Based Newborn Care Baseline Survey Report Ethiopia,October 2014.
Save the children, Enhancing Ethiopia’s Health Extension Package in the Southern Nations and Nationalities People’s Region (SNNPR) Shebedino and Lanfero Woredas report.Hawassa;. 2012: Avalable at https://ethiopia.savethechildren.net
Kolbe AR, Muggah R, Hutson RA, James L, Puccio M, Trzcinski E, et al. Assessing Needs After the Quake: Preliminary Findings from a Randomized Survey of Port-au-Prince Households. University of Michigan/Small Arms Survey: Available at https://deepbluelibumichedu PDF. 2010.
Teferi E, Teno D, Ali I, Alemu H, Bulto T. Quality and use of IMNCI services at health center under-five clinics after introduction of integrated community-based case management (ICCM) in three regions of Ethiopia. Ethiopian Medical Journal. 2014;52(Suppl 3):91 – 8.
Last 10 Km project, Integrated Community Case Management (iCCM) Survey report in Amhara, SNNP, and Tigray Regions, 2017: Avaialable at https://l10k.jsi.com
Tumuhamye N, Rutebemberwa E, Kwesiga D, Bagonza J, Mukose A. Client satisfaction with integrated community case management program in Wakiso District, Uganda, October 2012: A cross sectional survey. Health scrip org. 2013;2013.
EPHI. Ethiopia service provision assessment plus survey 2014 report: available at http://repository.iifphc.org
Gintamo B. EY, Assefa Y. Implementation Evaluation of IMNCI Program at Public Health Centers of Soro District, Hadiya Zone, Southern Ethiopia,. 2017: Available at https://repository.ju.edu.et
Download references
Acknowledgements
We are very grateful to University of Gondar and Gondar town health office for its welcoming approaches. We would also like to thank all of the study participants of this evaluation for their information and commitment. Our appreciation also goes to the data collectors and supervisors for their unreserved contribution.
No funding is secured for this evaluation study.
Author information
Authors and affiliations.
Metema District Health office, Gondar, Ethiopia
Mekides Geta
Department of Health Systems and Policy, Institute of Public Health, College of Medicine and Health Sciences, University of Gondar, P.O. Box 196, Gondar, Ethiopia
Geta Asrade Alemayehu, Wubshet Debebe Negash, Tadele Biresaw Belachew, Chalie Tadie Tsehay & Getachew Teshale
You can also search for this author in PubMed Google Scholar
Contributions
All authors contributed to the preparation of the manuscript. M.G. conceived and designed the evaluation and performed the analysis then T.B.B., W.D.N., G.A.A., C.T.T. and G.T. revised the analysis. G.T. prepared the manuscript and all the authors revised and approved the final manuscript.
Corresponding author
Correspondence to Getachew Teshale .
Ethics declarations
Ethics approval and consent to participate.
Ethical approval was obtained from Institutional Review Board (IRB) of Institute of Public Health, College of Medicine and Health sciences, University of Gondar (Ref No/IPH/1482/2013). Informed consent was obtained from all subjects and/or their legal guardian(s).
Consent for publication
Not applicable.
Competing interests
All authors declared that they have no competing interest.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ . The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated in a credit line to the data.
Reprints and permissions
About this article
Cite this article.
Geta, M., Alemayehu, G.A., Negash, W.D. et al. Evaluation of integrated community case management of the common childhood illness program in Gondar city, northwest Ethiopia: a case study evaluation design. BMC Pediatr 24 , 310 (2024). https://doi.org/10.1186/s12887-024-04785-0
Download citation
Received : 20 February 2024
Accepted : 22 April 2024
Published : 09 May 2024
DOI : https://doi.org/10.1186/s12887-024-04785-0
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Integrated community case management
BMC Pediatrics
ISSN: 1471-2431
- Submission enquiries: [email protected]
- General enquiries: [email protected]
Artificial intelligence is being used in healthcare for everything from answering patient questions to assisting with surgeries and developing new pharmaceuticals.
According to Statista , the artificial intelligence (AI) healthcare market, which is valued at $11 billion in 2021, is projected to be worth $187 billion in 2030. That massive increase means we will likely continue to see considerable changes in how medical providers, hospitals, pharmaceutical and biotechnology companies, and others in the healthcare industry operate.
Better machine learning (ML) algorithms, more access to data, cheaper hardware, and the availability of 5G have contributed to the increasing application of AI in the healthcare industry, accelerating the pace of change. AI and ML technologies can sift through enormous volumes of health data—from health records and clinical studies to genetic information—and analyze it much faster than humans.
Healthcare organizations are using AI to improve the efficiency of all kinds of processes, from back-office tasks to patient care. The following are some examples of how AI might be used to benefit staff and patients:
- Administrative workflow: Healthcare workers spend a lot of time doing paperwork and other administrative tasks. AI and automation can help perform many of those mundane tasks, freeing up employee time for other activities and giving them more face-to-face time with patients. For example, generative AI can help clinicians with note-taking and content summarization that can help keep medical records as thoroughly as possible. AI might also help with accurate coding and sharing of information between departments and billing.
- Virtual nursing assistants: One study found that 64% of patients are comfortable with the use of AI for around-the-clock access to answers that support nurses provide. AI virtual nurse assistants—which are AI-powered chatbots, apps, or other interfaces—can be used to help answer questions about medications, forward reports to doctors or surgeons and help patients schedule a visit with a physician. These sorts of routine tasks can help take work off the hands of clinical staff, who can then spend more time directly on patient care, where human judgment and interaction matter most.
- Dosage error reduction: AI can be used to help identify errors in how a patient self-administers medication. One example comes from a study in Nature Medicine , which found that up to 70% of patients don’t take insulin as prescribed. An AI-powered tool that sits in the patient’s background (much like a wifi router) might be used to flag errors in how the patient administers an insulin pen or inhaler.
- Less invasive surgeries: AI-enabled robots might be used to work around sensitive organs and tissues to help reduce blood loss, infection risk and post-surgery pain.
- Fraud prevention: Fraud in the healthcare industry is enormous, at $380 billion/year, and raises the cost of consumers’ medical premiums and out-of-pocket expenses. Implementing AI can help recognize unusual or suspicious patterns in insurance claims, such as billing for costly services or procedures that are not performed, unbundling (which is billing for the individual steps of a procedure as though they were separate procedures), and performing unnecessary tests to take advantage of insurance payments.
A recent study found that 83% of patients report poor communication as the worst part of their experience, demonstrating a strong need for clearer communication between patients and providers. AI technologies like natural language processing (NLP), predictive analytics, and speech recognition might help healthcare providers have more effective communication with patients. AI might, for instance, deliver more specific information about a patient’s treatment options, allowing the healthcare provider to have more meaningful conversations with the patient for shared decision-making.
According to Harvard’s School of Public Health , although it’s early days for this use, using AI to make diagnoses may reduce treatment costs by up to 50% and improve health outcomes by 40%.
One use case example is out of the University of Hawaii , where a research team found that deploying deep learning AI technology can improve breast cancer risk prediction. More research is needed, but the lead researcher pointed out that an AI algorithm can be trained on a much larger set of images than a radiologist—as many as a million or more radiology images. Also, that algorithm can be replicated at no cost except for hardware.
An MIT group developed an ML algorithm to determine when a human expert is needed. In some instances, such as identifying cardiomegaly in chest X-rays, they found that a hybrid human-AI model produced the best results.
Another published study found that AI recognized skin cancer better than experienced doctors. US, German and French researchers used deep learning on more than 100,000 images to identify skin cancer. Comparing the results of AI to those of 58 international dermatologists, they found AI did better.
As health and fitness monitors become more popular and more people use apps that track and analyze details about their health. They can share these real-time data sets with their doctors to monitor health issues and provide alerts in case of problems.
AI solutions—such as big data applications, machine learning algorithms and deep learning algorithms—might also be used to help humans analyze large data sets to help clinical and other decision-making. AI might also be used to help detect and track infectious diseases, such as COVID-19, tuberculosis, and malaria.
One benefit the use of AI brings to health systems is making gathering and sharing information easier. AI can help providers keep track of patient data more efficiently.
One example is diabetes. According to the Centers for Disease Control and Prevention , 10% of the US population has diabetes. Patients can now use wearable and other monitoring devices that provide feedback about their glucose levels to themselves and their medical team. AI can help providers gather that information, store, and analyze it, and provide data-driven insights from vast numbers of people. Using this information can help healthcare professionals determine how to better treat and manage diseases.
Organizations are also starting to use AI to help improve drug safety. The company SELTA SQUARE, for example, is innovating the pharmacovigilance (PV) process , a legally mandated discipline for detecting and reporting adverse effects from drugs, then assessing, understanding, and preventing those effects. PV demands significant effort and diligence from pharma producers because it’s performed from the clinical trials phase all the way through the drug’s lifetime availability. Selta Square uses a combination of AI and automation to make the PV process faster and more accurate, which helps make medicines safer for people worldwide.
Sometimes, AI might reduce the need to test potential drug compounds physically, which is an enormous cost-savings. High-fidelity molecular simulations can run on computers without incurring the high costs of traditional discovery methods.
AI also has the potential to help humans predict toxicity, bioactivity, and other characteristics of molecules or create previously unknown drug molecules from scratch.
As AI becomes more important in healthcare delivery and more AI medical applications are developed, ethical, and regulatory governance must be established. Issues that raise concern include the possibility of bias, lack of transparency, privacy concerns regarding data used for training AI models, and safety and liability issues.
“AI governance is necessary, especially for clinical applications of the technology,” said Laura Craft, VP Analyst at Gartner . “However, because new AI techniques are largely new territory for most [health delivery organizations], there is a lack of common rules, processes, and guidelines for eager entrepreneurs to follow as they design their pilots.”
The World Health Organization (WHO) spent 18 months deliberating with leading experts in ethics, digital technology, law, and human rights and various Ministries of Health members to produce a report that is called Ethics & Governance of Artificial Intelligence for Health . This report identifies ethical challenges to using AI in healthcare, identifies risks, and outlines six consensus principles to ensure AI works for the public’s benefit:
- Protecting autonomy
- Promoting human safety and well-being
- Ensuring transparency
- Fostering accountability
- Ensuring equity
- Promoting tools that are responsive and sustainable
The WHO report also provides recommendations that ensure governing AI for healthcare both maximizes the technology’s promise and holds healthcare workers accountable and responsive to the communities and people they work with.
AI provides opportunities to help reduce human error, assist medical professionals and staff, and provide patient services 24/7. As AI tools continue to develop, there is potential to use AI even more in reading medical images, X-rays and scans, diagnosing medical problems and creating treatment plans.
AI applications continue to help streamline various tasks, from answering phones to analyzing population health trends (and likely, applications yet to be considered). For instance, future AI tools may automate or augment more of the work of clinicians and staff members. That will free up humans to spend more time on more effective and compassionate face-to-face professional care.
When patients need help, they don’t want to (or can’t) wait on hold. Healthcare facilities’ resources are finite, so help isn’t always available instantaneously or 24/7—and even slight delays can create frustration and feelings of isolation or cause certain conditions to worsen.
IBM® watsonx Assistant™ AI healthcare chatbots can help providers do two things: keep their time focused where it needs to be and empower patients who call in to get quick answers to simple questions.
IBM watsonx Assistant is built on deep learning, machine learning and natural language processing (NLP) models to understand questions, search for the best answers and complete transactions by using conversational AI.
Get email updates about AI advancements, strategies, how-tos, expert perspective and more.
See IBM watsonx Assistant in action and request a demo
Get our newsletters and topic updates that deliver the latest thought leadership and insights on emerging trends.
To read this content please select one of the options below:
Please note you do not have access to teaching notes, pushed over the limit: burnout as a consequence of unresolved stress.
Human Resource Management International Digest
ISSN : 0967-0734
Article publication date: 21 May 2024
This paper aims to review the latest management developments across the globe and pinpoint practical implications from cutting-edge research and case studies.
Design/methodology/approach
This briefing is prepared by an independent writer who adds their own impartial comments and places the articles in context.
This paper identified that when employees face burnout they self-regulate their behavior to cope. This can either lead to negative or positive outcomes.
Originality/value
The briefing saves busy executives, strategists and researchers hours of reading time by selecting only the very best, most pertinent information and presenting it in a condensed and easy-to-digest format.
- Self-regulation
(2024), "Pushed over the limit: Burnout as a consequence of unresolved stress", Human Resource Management International Digest , Vol. ahead-of-print No. ahead-of-print. https://doi.org/10.1108/HRMID-04-2024-0109
Emerald Publishing Limited
Copyright © 2024, Emerald Publishing Limited
Related articles
We’re listening — tell us what you think, something didn’t work….
Report bugs here
All feedback is valuable
Please share your general feedback
Join us on our journey
Platform update page.
Visit emeraldpublishing.com/platformupdate to discover the latest news and updates
Questions & More Information
Answers to the most commonly asked questions here

IMAGES
VIDEO
COMMENTS
The Identity and Access Management Report is based on the results of a comprehensive online survey of cybersecurity professionals, conducted in May of 2020 to gain deep insight into the latest trends, key challenges and solutions for identity and access management. The respondents range from technical executives to IT security practitioners ...
This 2020 Identity and Access Management Report has been produced by Cybersecurity Insiders, the 400,000 member information security community, to explore the latest trends, key challenges, gaps and solution preferences for Identity and Access Management (IAM). Many thanks to Simeio Solutions for supporting this unique research study.
A Netherlands-based transport insurance provider needed an Identity and Access Management (IAM) solution to modernize their claims handling processes. The objective was to eliminate paper-based accident statement forms and offer their clients a fully digital experience. Download Access Management. Case Studies PDF.
A global transformation based on technology and trust. As an organization respected worldwide for experience in combining technology, business transformation and trust, PwC understands the importance of modern, secure solutions for managing large-scale enterprises. When evaluating our own complex identity and access management (IAM) system, we ...
Digital identity and access management (IAM) poses significant challenges for companies. Cyberattacks and resulting data breaches frequently have their root cause in enterprises' IAM systems. During the COVID-19 pandemic, issues with the remote authentication of employees working from home highlighted the need for better IAM solutions. Using a design science research approach, the paper ...
Identity and access management (IAM) is more important today than ever. ... This case study shows how one company made it possible to modernize IAM even at this mega-scale and in a relatively ...
Case Study: Identity Management Identity Management for a Manufacturing Company with Over 2000 Employees. ... To address these challenges, our team recommended implementing JumpCloud, a unified device and identity access management platform, along with a Zero Trust framework. This was particularly important as the company had a significant ...
Maintaining an effective access management and identity solution. Replacing multiple siloed solutions that were burdensome to manage and secure. Deploying a comprehensive "single source of truth" identity management system to resolve conflicts with data sources and personnel. Eliminating significant security vulnerabilities and replacing ...
without compromising security. Identity and access management (IAM) is the task of accurately assigning and administering the required IT system access privileges and resource entitlements to employees within a business or organisation. WHO'S INVOLVED This project is funded by the CSCRC in collaboration with CSIRO's Data61 and National ...
This paper is a systematic review of Identity Access Man agement (IAM) in information security. Identity. and Access Administration (IAM) involves tools, proce dures, and policies for the ...
Case Study: Improving ID and Access Management. What are some of the moves that organizations can make to improve their identity and access management? Veda Sankepally, an IT security manager at ...
Case Study Identity and access management Today's enterprise architecture systems are challenged by the need to remain scalable, while managing increasingly complex infrastructure. Enterprise IT systems have become multi-location infrastructure systems, each with a wide variety of analytics and overlaid user-facing services. Central access ...
Identity Access Management Case Studies. IDMWORKS' identity experts have created a series of case studies to demonstrate the benefits of a custom IAM solution in order to deliver a centralized, modern approach to IAM. Our digital roadmaps range from Supply Chain Technology Enhancement to Health Care and Financial data Systems.
No. 1: Connect anywhere computing will further drive need for smarter access control. The transition to more remote, connected anywhere computing is placing greater demands on access management deployments. Access management platforms must become increasingly sophisticated to differentiate between valid users and malicious bots or fraudsters ...
Chapter 18 Case Study Implementation Nicholas Gazos A global organization struggles to effectively implement tools and technologies to support identity and access management, with a particular emphasis on the access … - Selection from Identity and Access Management [Book]
Case Study : Helping Laitram Build their IGA Program from the Ground Up Laitram worked with Integral Partners as a trusted advisor to learn best practices to help implement their Identity Governance and Administration program—improving identity access accuracy and security while transforming employee lifecycle management.
Identity and access management (IAM) is critical to your business, especially in an evolving business landscape. Most of the time, in order to take action on something, you first need access to it. This is especially true when it comes to business computing. The first step to taking action, either intended or malicious, is getting access to ...
Group Services. Forms (2) Case Study. Overview (7) Planning (2) 784 Memorial Drive. Cambridge, MA 02138. [email protected]. Home | About IAM | Get Started.
Automated Oracle Identity Manager (OIM) processes, user access review requests, and Lightweight Directory Access Protocol (LDAP) requests. Developed and implemented scripts for user access provisioning, monitoring, and OIM server tracking. Implemented best practices and knowledge management via complete documentation and systematic framework.
Case Studies UVA Enhances Security and Efficiency with Fischer Identity Discover how UVA modernized its Identity and Access Management (IAM) program with Fischer Identity, enhancing security, efficiency, and achieving top audit ratings in all assessment areas. Learn More UWCU Achieves IAM Excellence with Fischer Identity: A Regulatory Compliance Success Story […]
DeployID - Identity & Access Management (IAM) Case Study. The client was struggling to implement an Identity & Access Management (IAM) solution with extensive Access Request and Provisioning requirements to replace a heavily-customized, legacy IAM system.
Customer Success Stories. Learn how we can help you to alleviate IAM challenges, and make it easier to access and manage your apps without compromising on security with Thales Identity and Access Management Solutions. Contextual logging in from within and outside the office was really important. With SafeNet Trusted Access, we enjoy great user ...
Use Case #9: Identity and Access Management. Identity and access management (IAM) solutions store information about parties (e.g., administrators, business units, end-users) and resources (e.g., files, shares, network devices, products, agreements), along with the rules governing access to those resources. IAM solutions apply these rules to ...
An effective identity and policy orchestration framework must balance security and accessibility. Forcing users to adapt to a new authentication workflow or experience can reduce productivity and ...
Identity and Access Management Architect Study Guide Updated May 2024. Identity and Access Management Architect Study Guide. 0 out of 12 steps completed 0%. 6 Lessons. Time spent: 0h 0m.
1. MDM plays an important role with modern data architecture concepts and creates value in five ways: MDM cleans, enriches, and standardizes data for key functions, such as customer or product data, before it is loaded into the data lake. In this way, MDM ensures that data is accurate, complete, and consistent across an organization.
The case study included three scenarios: calculating the number of workers, selecting orders based on factory capacity and managing unexpected worker absences.,The developed simulator is approximately 97.2% accurate in assigning appropriate tasks to workstations using the mixed task assignment algorithm.
Background Integrated Community Case Management (ICCM) of common childhood illness is one of the global initiatives to reduce mortality among under-five children by two-thirds. It is also implemented in Ethiopia to improve community access and coverage of health services. However, as per our best knowledge the implementation status of integrated community case management in the study area is ...
A recent study found that 83% of patients report poor communication as the worst part of their experience, demonstrating a strong need for clearer communication between patients and providers. AI technologies like natural language processing (NLP), predictive analytics, and speech recognition might help healthcare providers have more effective communication with patients.
This paper aims to review the latest management developments across the globe and pinpoint practical implications from cutting-edge research and case studies.,This briefing is prepared by an independent writer who adds their own impartial comments and places the articles in context.,This paper identified that when employees face burnout they ...