- Shell Scripting
- Docker in Linux
- Kubernetes in Linux
- Linux interview question
- Linux/Unix Tutorial

Getting Started with Linux
What is linux operating system.
- LINUX Full Form
- Linux History
- Difference between Linux and Windows
- What are Linux Distributions ?
- Difference between Unix and Linux
- Why Linux is Better?
Installation with Linux
- How to Install Arch Linux in VirtualBox?
- Fedora Linux Operating System
- How to install Ubuntu on VirtualBox?
- How to Install Linux Mint?
- How to Install Kali Linux on Windows?
- How to Install Linux on Windows PowerShell Subsystem?
- How to Find openSUSE Linux Version?
- How to Install CentOS
- Linux Commands
- Essential Unix Commands
- How to Find a File in Linux | Find Command
- Linux File System
- Linux File Hierarchy Structure
- Linux Directory Structure
- Linux Kernel
- Kernel in Operating System
- How Linux Kernel Boots?
- Difference between Operating System and Kernel
- Linux Kernel Module Programming: Hello World Program
- Linux Loadable Kernel Module
- Loadable Kernel Module - Linux Device Driver Development
- Linux Networking Tools
- Network configuration and troubleshooting commands in Linux
- How to configure network interfaces in CentOS?
- Command-Line Tools and Utilities For Network Management in Linux
- Linux - Network Monitoring Tools
Linux Process
- Processes in Linux/Unix
- Process Management in Linux
- Getting System and Process Information Using C Programming and Shell in Linux
- Process states and Transitions in a UNIX Process
Linux Firewall
- LINUX Firewall
- iptables command in Linux with Examples
- How to setup firewall in Linux?
Shell Scripting & Bash Scripting
- Introduction to Linux Shell and Shell Scripting
- What is Terminal, Console, Shell and Kernel?
- How to Create a Shell Script in linux
- Shell Scripting - Different types of Variables
- Bash Scripting - Introduction to Bash and Bash Scripting
- Bash Script - Define Bash Variables and its types
- Shell Scripting - Shell Variables
- Bash Script - Difference between Bash Script and Shell Script
- Shell Scripting - Difference between Korn Shell and Bash shell
- Shell Scripting - Interactive and Non-Interactive Shell
- Shell Script to Show the Difference Between echo “$SHELL” and echo ‘$SHELL’
Linux Administrator System
- What is Linux System Administration?
- Beginner's Guide to Linux System Administration
- How to Monitor System Usage, Outages and Troubleshoot Linux Servers
- Linux - Systemd and its Components
- Boot Process with Systemd in Linux
- How to Control Systemd Services on Remote Linux Server
- How to Start, Stop and Restart Services in Linux Using systemctl Command
The Linux Operating System is a type of operating system that is similar to Unix, and it is built upon the Linux Kernel. The Linux Kernel is like the brain of the operating system because it manages how the computer interacts with its hardware and resources. It makes sure everything works smoothly and efficiently. But the Linux Kernel alone is not enough to make a complete operating system. To create a full and functional system, the Linux Kernel is combined with a collection of software packages and utilities, which are together called Linux distributions. These distributions make the Linux Operating System ready for users to run their applications and perform tasks on their computers securely and effectively. Linux distributions come in different flavors, each tailored to suit the specific needs and preferences of users.
What is Linux
Linux is a powerful and flexible family of operating systems that are free to use and share. It was created by a person named Linus Torvalds in 1991. What’s cool is that anyone can see how the system works because its source code is open for everyone to explore and modify. This openness encourages people from all over the world to work together and make Linux better and better. Since its beginning, Linux has grown into a stable and safe system used in many different things, like computers, smartphones, and big supercomputers. It’s known for being efficient, meaning it can do a lot of tasks quickly, and it’s also cost-effective, which means it doesn’t cost a lot to use. Lots of people love Linux, and they’re part of a big community where they share ideas and help each other out. As technology keeps moving forward, Linux will keep evolving and staying important in the world of computers.
Linux Distribution
Linux distribution is an operating system that is made up of a collection of software based on Linux kernel or you can say distribution contains the Linux kernel and supporting libraries and software. And you can get Linux based operating system by downloading one of the Linux distributions and these distributions are available for different types of devices like embedded devices, personal computers, etc. Around 600 + Linux Distributions are available and some of the popular Linux distributions are:
Architecture of Linux
Linux architecture has the following components:
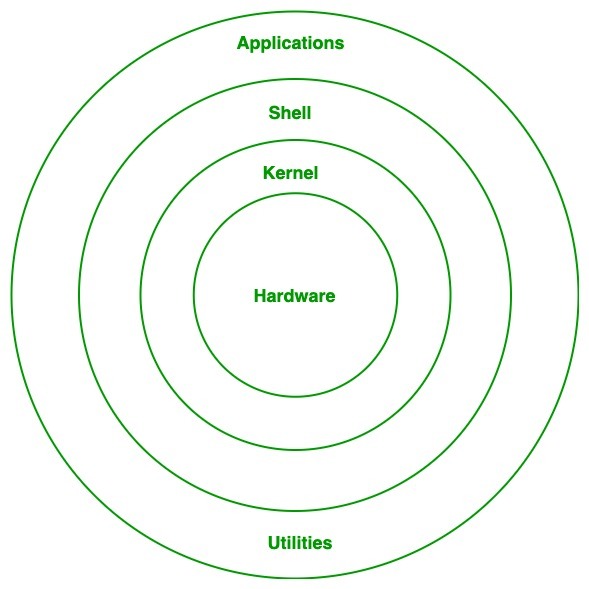
Linux Architecture
- Monolithic Kernel
- Hybrid kernels
- Exo kernels
- Micro kernels
- System Library: Linux uses system libraries, also known as shared libraries, to implement various functionalities of the operating system. These libraries contain pre-written code that applications can use to perform specific tasks. By using these libraries, developers can save time and effort, as they don’t need to write the same code repeatedly. System libraries act as an interface between applications and the kernel, providing a standardized and efficient way for applications to interact with the underlying system.
- Shell: The shell is the user interface of the Linux Operating System. It allows users to interact with the system by entering commands, which the shell interprets and executes. The shell serves as a bridge between the user and the kernel, forwarding the user’s requests to the kernel for processing. It provides a convenient way for users to perform various tasks, such as running programs, managing files, and configuring the system.
- Hardware Layer: The hardware layer encompasses all the physical components of the computer, such as RAM (Random Access Memory), HDD (Hard Disk Drive), CPU (Central Processing Unit), and input/output devices. This layer is responsible for interacting with the Linux Operating System and providing the necessary resources for the system and applications to function properly. The Linux kernel and system libraries enable communication and control over these hardware components, ensuring that they work harmoniously together.
- System Utility: System utilities are essential tools and programs provided by the Linux Operating System to manage and configure various aspects of the system. These utilities perform tasks such as installing software, configuring network settings, monitoring system performance, managing users and permissions, and much more. System utilities simplify system administration tasks, making it easier for users to maintain their Linux systems efficiently.
Advantages of Linux
- The main advantage of Linux is it is an open-source operating system. This means the source code is easily available for everyone and you are allowed to contribute, modify and distribute the code to anyone without any permissions.
- In terms of security, Linux is more secure than any other operating system. It does not mean that Linux is 100 percent secure, it has some malware for it but is less vulnerable than any other operating system. So, it does not require any anti-virus software.
- The software updates in Linux are easy and frequent.
- Various Linux distributions are available so that you can use them according to your requirements or according to your taste.
- Linux is freely available to use on the internet.
- It has large community support.
- It provides high stability. It rarely slows down or freezes and there is no need to reboot it after a short time.
- It maintains the privacy of the user.
- The performance of the Linux system is much higher than other operating systems. It allows a large number of people to work at the same time and it handles them efficiently.
- It is network friendly.
- The flexibility of Linux is high. There is no need to install a complete Linux suite; you are allowed to install only the required components.
- Linux is compatible with a large number of file formats.
- It is fast and easy to install from the web. It can also install it on any hardware even on your old computer system.
- It performs all tasks properly even if it has limited space on the hard disk.
Disadvantages of Linux
- It is not very user-friendly. So, it may be confusing for beginners.
- It has small peripheral hardware drivers as compared to windows.
Frequently Asked Questions in Linux Operating System
What is linux operating system.
Linux is an open-source operating system developed by Linus Torvalds in 1991. It provides a customizable and secure alternative to proprietary systems. With its stable performance, Linux is widely used across devices, from personal computers to servers and smartphones. The collaborative efforts of its developer community continue to drive innovation, making Linux a dominant force in the world of computing.
Is There Any Difference between Linux and Ubuntu?
The answer is YES. The main difference between Linux and Ubuntu is Linux is the family of open-source operating systems which is based on Linux kernel, whereas Ubuntu is a free open-source operating system and the Linux distribution which is based on Debian. Or in other words, Linux is the core system and Ubuntu is the distribution of Linux. Linux is developed by Linus Torvalds and released in 1991 and Ubuntu is developed by Canonical Ltd. and released in 2004.
How do I install software on Linux Operating System?
To install software on Linux, we can use package managers specific to your Linux distribution. For example, In Ubuntu, you can use the “apt” package manager, while on Fedora, you can use “dnf.” You can simply open a terminal and use the package manager to search for and install software. For example , To install the text editor “nano” on Ubuntu, you can use the command sudo apt install nano
Can we dual-boot Linux with another operating system?
Yes, we can dual-boot Linux with another operating system, such as Windows. During the installation of Linux, we can allocate a separate partition for Linux, and a boot manager (like GRUB) allows us to choose which operating system to boot when starting our computer.
How can I update my Linux distribution?
We can update our Linux distribution using the package manager of our specific distribution. For instance, on Ubuntu, we can run the following commands to update the package list and upgrade the installed packages: sudo apt update sudo apt upgrade
What are the essential Linux commands for beginners?
Some essential Linux commands for beginners include: ls : List files and directories cd : Change directory mkdir : Create a new directory rm : Remove files or directories cp : Copy files and directories mv : Move or rename files and directories cat : Display file content grep : Search for text in files sudo : Execute commands with administrative privileges
How do I access the command-line interface in Linux Operating System?
To access the command-line interface in Linux , we can open a terminal window. In most Linux distributions, we can press Ctrl + Alt + T to open the terminal. The terminal allows us to execute commands directly, providing more advanced control over our system.
In this article, we discussed Linux Operating System which is a powerful and flexible open-source operating system based on the Linux Kernel. With a collaborative global community, it offers security, frequent updates, and diverse distributions tailored to user needs. Its architecture, comprising the kernel, system libraries, shell, hardware layer, and utilities, ensures efficient functionality. While Linux boasts high performance, stability, and compatibility, challenges include user-friendliness for beginners and a limited number of peripheral hardware drivers. Despite this, Linux remains a significant player in computing, poised for continued evolution and relevance.

Please Login to comment...
Similar reads, improve your coding skills with practice.
What kind of Experience do you want to share?
Register For AI_dev Europe | 19-20 June - Paris, France REGISTER NOW
Case studies
See why critical open source projects choose the linux foundation.
The Linux Foundation is home to over 800 open source projects. The case studies here detail why projects benefit from being hosted at the Linux Foundation, and other studies here showcase how our projects support collaborative innovation around the world.
Let’s Encrypt Makes the Internet More Secure and Privacy Respecting
As the world’s largest certificate authority, Let’s Encrypt is a nonprofit project that makes the internet more secure and privacy-respecting for everyone who uses it. And they did it in just a little more than five years.
InfluxData Doubles Down on Developer and Customer Happiness With Kubernetes Deployment Model
The Kubernetes-powered cloud abstraction layer has made it possible to write a multi-tenant application that allows customers the flexibility to control their usage and costs in a way they couldn’t by provisioning their own infrastructure.
Disney uses Pytorch in Their Genome Project
Pytorch is used in an initiative to deeply annotate all Disney content and make it accessible at very granular levels to creatives. Miquel Farré is a senior technology manager at Disney, taking the lead on projects at the intersection of video technology, machine learning and web applications. In this talk, he speaks about the Genome project and talks more about this initiative.
The Linux Foundation Builds the Global Foundation for Open Source Enterprise Blockchain Technologies
The role of Hyperledger Foundation is to ensure the health and transparency of the community and all its projects, including managing the development cycle, software licensing, security audits, and provenance tracking for every line of code.
How Fledge, UC Davis and Opus One Create World-Class Wine in Safer Conditions
Learn how IIoT works with the wine industry, in this case study that outlines how Fledge is being used by UC Davis and Opus One to create a multi-node wireless sensor network for UC Davis Teaching and Research Winery, and Opus One’s facility. The system successfully measures the CO2 levels in a winery to ultimately reduce costs and create safer conditions for the wine and the workers.
Open Retail Initiative: Technology Collaboration to Drive Innovation in Retail
Loss detection in real time for self-checkout at point of sale for grocery or convenience stores. Using EdgeX Foundry to combine POS, RFID, Weight Scale and Computer Vision data all in a single pane of glass and use it to alert associates in real time. This demo showcases how to take advantage of data from sensors currently available in stores to create a better solution compared to using a single sensor (i.e. weight scale).

Paving the Way to Battle Climate Change: How Two Utilities Embraced Open Source to Speed Modernization of the Electric Grid
A case study of how two large European distribution and transmission systems operators, the Netherlands’ Alliander and France’s RTE, adopted and contributed to three significant LF Energy projects, SEAPATH, CoMPAS, and OpenSTEF so that their electrical substations can become more modular, interoperable, and scalable, and alleviate the challenges associated with less predictable renewable energy sources.
Dolby Labs is Using PyTorch to Develop Deep Learning for Audio
Hear how Dolby Labs is using PyTorch to develop deep learning for audio, and learn about the challenges that audio AI presents and the breakthroughs and applications they’ve built at Dolby to push the field forward.

The FINOS Legend Studio Pilot: an Open Source Success Story in Financial Services
“Legend is an impressive technology with great potential for improving industry efficiency. We see tremendous potential for synergies between Legend and our own Morphir project, also open-sourced through FINOS, just last month. These contributions together validate the FINOS model of bringing industry competitors together to solve industry challenges.”

Why the T-Mobile Data Science and Analytics Team migrated to a Data Lakehouse on Delta Lake
This architecture allows a relatively simple infrastructure that will expose data at the speed of business. It allows the reading and writing of data without blocking and scales out linearly. Business partners can easily adopt advanced analytics and derive new insights, which promote innovation across disparate workstreams and solidify the decentralized approach to analytics taken by T-Mobile.
Amazon Ads Uses PyTorch and AWS Inferentia to Scale Models for Ads Processing
Our DL models, developed in PyTorch and deployed on Inferentia, sped up our ads analysis while cutting costs. Starting with our first explorations in DL, programming in PyTorch felt natural. Its user-friendly features helped smooth the course from our early experiments to the deployment of our multimodal ensembles. PyTorch lets us prototype and build models quickly, which is vital as our advertising service evolves and expands.
Tesla is Using PyTorch to Develop Full Self-Driving Capabilities for Its Vehicles, Including AutoPilot and Smart Summon
Hear from Andrej Karpathy on how Tesla is using PyTorch to develop full self-driving capabilities for its vehicles, including AutoPilot and Smart Summon.
With an eye toward standardization and security for its media brands, Verizon Media turned to cloud native
Moving services into containers and using Kubernetes as an acquisition platform “helped us to reduce duplication, standardize the way we build and deploy code, and increased our cluster utilization too. Security is now from the ground up. The developers don’t need to worry; by default, everything is secured.”
With Kubernetes, the U.S. Department of Defense is enabling DevSecOps on F-16s and battleships
Releases, which once took as long as 3 to 8 months, now can be achieved in one week. An authority to operate (ATO) for a cloud enclave can be obtained within one week, plus “we have a continuous ATO on the platform stack. Anytime it’s going to pass the gates, the software is automatically accredited. So you can push software multiple times a day.”
How Walmart brought unprecedented transparency to the food supply chain with Hyperledger Fabric
Walmart can now trace the origin of over 25 products from 5 different suppliers using a system powered by Hyperledger Fabric. The company plans to roll out the system to more products and categories in the near future.
Change Healthcare: 50 million transactions a day using Hyperledger Fabric
Implementing Hyperledger Fabric took just a couple of months. Since January 2018, the test network demonstrated the ability to process up to 50 million transactions a day—with throughput up to 550 transactions a second.

OpenJS In Action: How Wix Applied Multi-threading to Node.js and Cut Thousands of SSR Pods and Money
In Wix, as part of our sites’ Server-Side-Rendering architecture, we build and maintain the heavily used Server-Side-Rendering-Execution platform (aka SSRE). SSRE is a Node.js based multipurpose code execution platform, that’s used for executing React.js code written by front-end developers all across the company. Most often, these pieces of JS code perform CPU-intensive operations that simulate activities related to site rendering in the browser.
OpenJS in Action: There’s Open Source in Your Credit Card with Neo Financial
The Neo Financial web banking portal provides seamless mobile-first interactions for users. The backend of the portal is built entirely using JavaScript and Node.js and powers all of the app’s microservices and transaction processing.
Stay Connected with the Linux Foundation
Linux Case Study
- Linux is a popular open-source operating system.
- It was initially created by Linus Torvalds in 1991. At the time, Torvalds was a computer science student at the University of Helsinki, Finland and began working on the Linux project as a personal endeavor. The name Linux is a combination of his first name, Linus, and Unix, the operating system that inspired his projects.
- Linux is considered one of the most stable, secure and reliable operating systems and is widely used in servers, supercomputers and enterprise environments.
- Today, Linux is one of the most widely used operating systems in the world, with an estimated 2.76% of all desktop computers and more than 90% of the world’s top supercomputers running on Linux, and approx. 71.85% of all mobile devices run on Android, which is, you guessed it, Linux-based.
- Nitrux (best for begginers)
- Zorin OS (best for Windows user)
- Pop!_OS (best for gaming)
- Kodachi (best for privacy and security)
- Rescatux (best for repair and rescue)
How does Linux Work?
- Kernel: This is actually a component of the “Linux” system as a whole. The kernel, which controls the CPU, memory, and peripherals, serves as the brain of the system. The operating system’s kernel is at the most fundamental level.
- Desktop Environment: The user actually engages in interaction at this point. There are numerous desktop environments available (GNOME, Cinnamon, Mate, Pantheon, Enlightenment, KDE, Xfce, etc.). Every desktop environment has pre-installed programmes (file managers, configuration tools, web browsers, games, etc.).
- Shell: Linux uses a command-line interface called a shell, which allows users to interact with the operating system by typing commands. The shell interprets these commands and communicates them to the kernel for execution.
Why Use Linux?
There are several reasons why one might choose to use linux:
- Open-source: Linux is open-source software, meaning that the source code is freely available for anyone to use, modify, and distribute. This allows for a large and active community of developers to contribute to the development and maintenance of the operating system.
- Customizability: Linux is highly customizable, means users can easily install and configure different software packages to suit their needs.
- Stability and security: Linux is known for its stability and security, as it is less prone to crashes and viruses than other operating systems.
- Cost-effective: Linux is free to download and use, making it a cost- effective option for individuals and businesses.
Events leading to the creation of Linux
The emergence of Linux, one of the world’s most widely used open-source operating systems, can be traced to several important events and the work of a few people. Below is a summary of the major events that led to the emergence of Linux.
- Unix development: Linux was heavily influenced by the Unix operating system developed by Bell Labs in the late 1960s and early 1970s. Unix was developed as a multi-user, multi-tasking operating system and has been widely used in science and research.
- Minix is born: In the early 1980s, computer science professor Andrew S. Tanenbaum created a small Unix-like operating system called Minix. Minix was developed as an educational tool and the source code was made available to students.
- Linux is born: In 1991, a 21-year-old student named Linus Torvalds began working on a new operating system, he named it Linux. Linus was inspired by his Minix and used its source code as a starting point for his own projects. He also drew heavily on Unix design principles.
- Release of Linux 0.01: In September 1991, Linus released the first version of his Linux called Linux 0.01. It was a command-line operating system and was freely distributed on the Internet.
- Linux community development: In the years that followed, Linux quickly gained popularity among programmers and enthusiasts. A community of developers began to form around Linux, contributing to the development of the operating system by writing code, filing bug reports, and providing feedback.
- Enterprise Adoption: In the late 1990s and early 2000s, the open- source nature of Linux made it more flexible, cost-effective, and more secure than proprietary operating systems such as Windows, making it a popular choice for enterprises and businesses. started being hired by companies. This increased acceptance led to the development of commercial support and services for Linux.
- Linux Distribution Growth: As Linux became more popular, various groups of developers began creating their own versions of the operating system, called distributions (distro). Some of the most popular distributions are Red Hat, Debian, and Ubuntu. These distros contain the Linux kernel and a number of packages of easy-to-use tools and software that make using Linux easy for both developers and end users.
- Linux in the Consumer Market: Linux has also entered the consumer market with the advent of Linux-based mobile devices, smart TVs, and other consumer electronics.
Development of Linux
The Linux ecosystem is a constantly evolving and expanding platform, so there is a lot of development going on. Notable recent developments include:
- Linux 5.11 kernel release. It includes new features such as AMD Zen 3 processor support, memory management system improvements, and new hardware support.
- Continued development of various Linux distributions. Ubuntu 21.04 released in April 2021. It features an updated Gnome desktop environment, improved ZFS file system support, and new security features.
- Development of new open-source software and tools for Linux. For example, the release of version 6.0 of Ansible automation tools brings new features such as support for Windows Subsystem for Linux 2 (WSL2) and improved support for Kubernetes.
- The rise of containerization and orchestration technologies such as Docker and Kubernetes. They are becoming more and more common in deploying and managing Linux-based applications.
- Linux is growing in popularity in the cloud computing space, with many major cloud providers offering Linux-based virtual machines and managed services.
- ecurity Enhancements: Linux developers have been actively working on improving security measures. Features like secure boot, kernel lockdown, and improved access controls have been introduced to enhance the overall security posture of Linux-based systems. Efforts have also been made to address vulnerabilities and mitigate potential threats through regular security updates.
- Artificial Intelligence and Machine Learning: Linux has become a popular platform for AI and machine learning applications. Frameworks like TensorFlow, PyTorch, and scikit-learn are widely used for developing and deploying machine learning models on Linux systems. There has been a focus on optimizing these frameworks and providing better support for hardware acceleration.
Linux Files
- In Linux system, everything is a file and if it is not a file, it is a process. A file doesn't include only text files, images and compiled programs but also include partitions, hardware device drivers and directories. Linux consider everything as as file.
- Regular files: It contain programs, executable files and text files.
- Directory files (d) : It is shown in blue color. It contain list of files.
- Block file (b)
- Character device file (c)
- Named pipe file (p)
- Symbolic link file (l)
- Socket file (s)
Absolute and Relative Pathnames
- A path is a unique location of a file or a folder in a file system of an OS. A path to a file is combination of / and alpha-numeric characters.
Absolute Pathname
- An absolute path is defined as the specifying the location of a file or directory from the root directory (/).
- Start at the root directory (/) and work down.
- Write a slash (/) after every directory name (last one is optional)
- For example: $cat abc.sql Note: we don't have to write '$' its already written in terminal. 'cat' command is used for displaying content of a file, in this case abc.sql. The above command only work when there is a file 'abc.sql' in the current directory. $cat /home/database/abc.sql In the above example, if the first character of a pathname is /, the file’s location must be determined with respect to root.
- An absolute path is defined as specifying the location of a file or directory from the root directory(/). In other words,we can say that an absolute path is a complete path from start of actual file system from / directory.
Relative path
- Relative path is defined as the path related to the present working directly(pwd).
- It starts at your current directory and never starts with a /.
Using . and .. in Relative Path-names
- Linux offers a shortcut in the relative pathname that uses either the current or parent directory as reference and specifies the path relative to it.
- . (a single dot) - this represents the current directory.
- .. (two dots) - this represents the parent directory.
- If we are currently in directory /home/kt/abc and now you use .. as an argument to cd to move to the parent directory /home/kt as : $pwd /home/kt/abc $cd .. *** moves one level up *** $pwd /home/kt Note: Now when / is used with .. has a different meaning, instead of moving down a level, it moves one level up. $pwd /home/kt/abc $cd ../.. *** moves two level up *** $pwd /home
Example of Absolute and Relative Path
Suppose you are currently located in home/kt and you want to change your directory to home/kt/abc. Let's see both the absolute and relative path concepts to do this:
1. Changing directory with relative path concept:
2. Changing directory with absolute path concept:
Commands to navigate your Linux file system
- This command displays the present working directory , letting you know where you are now.
Example ↓
- The tree command displays filesystem information in a similar manner to a graphical interface. This can be handy for new Linux users who are more used to the hierarchical filesystem display in other operating systems.
- This command moves you to the specified directory, changing your present working directory location.
- For example, to use an absolute path to move to the /etc/ssh directory, type the following command: $cd /etc/ssh By using the absolute path, it doesn't matter where in the filesystem you currently are.
- Single dot, or .
- Double dot, or ..
- Tilde, or ~
- The single dot represents the present working directory, or where you are right now. Say you're in your home directory and you want to copy the sshd_config file from /etc/ssh. You can specify it with just a dot because you're copying the file to your current directory. The command looks like this: $sudo cp /etc/ssh/sshd_config .
- Double dots represent the parent directory, or the directory immediately above the current one in the filesystem. If there's a subdirectory namedRockin theMusicdirectory, thenMusicis the parent directory ofRock. As another example, consider where log files are stored: /var/log. In that case, var is the parent directory of log (and the filesystem root / is the parent of var). So, to move from the current Rock directory to the Music directory above it, type: $cd ..
- Similarly, the tilde character ~ represents the current, logged-on user's home directory. To copy the sshd_config file from /etc/ssh to your home directory (no matter where in the filesystem I'm presently located), type: $cp /etc/ssh/sshd_config ~
Home directory
- The directory in which you find yourself when you first login is called your home directory.
- You can go in your home directory anytime using the following command − $cd ~
- Here ~ indicates the home directory. Suppose you have to go in any other user's home directory, use the following command − $cd ~username
- To go in your last directory, you can use the following command − $cd -
- Listing Directories: To list the files in a directory, you can use the following syntax - $ls dirname
- Creating Directories, directories are created by the following command - $mkdir mydir Creates the directory mydir in the currect directory.
- Here is another example - $mkdir /tmp/test-dir This command creates the directory test-dir in the /tmp directory. The mkdir command produces no output if it successfully creates the requested directory.
- If you give more than one directory on the command line, mkdir creates each of the directories. For example, − $mkdir docs pub Creates the directories docs and pub under the current directory.
Creating Parent Directories
- Sometimes when you want to create a directory, its parent directory or directories might not exitst. In this case, mkdir issues an error message as follows- $mkdir /tmp/amrood/test mkdir: Failed to make directory "/tmp/amrood/test"; No such file or directory
- In such cases, you can specify the -p option to the mkdir command. It creates all the necessay directories for you. For example - $mkdir -p /tmp/amrood/test
- Removing Directories: Directories can be deleted using the rmdir command as follows - $rmdir dirname Note − To remove a directory, make sure it is empty which means there should not be any file or sub-directory inside this directory.
- You can remove multiple directories at a time as follows - $rmdir dirname1 dirname2 dirname3 The above command removes the directories dirname1, dirname2, and dirname3, if they are empty. The rmdir command produces no output if it is successful.
- Renaming Directores: The mv (move) command can also be used to rename a directory. The syntax is as follows - $mv olddir newdir $mv mydir yourdir
- If we enter the command to show a listing of the current working directories/files and use the -a option to list all the files and the -l option to provide the long listing, we will receive the following result pravin@Pravins-MacBook-Air BCA % ls -la total 64 drwxr-xr-x@ 10 pravin staff 320 Apr 18 19:01 . drwxrwxrwx@ 8 pravin staff 256 Feb 15 09:46 .. -rw-r--r--@ 1 pravin staff 8196 Jun 4 10:58 .DS_Store drwxr-xr-x 15 pravin staff 480 Jun 5 12:29 .git -rw-r--r-- 1 pravin staff 8 Feb 18 12:13 .gitignore drwxr-xr-x 3 pravin staff 96 Apr 18 19:01 .vscode -rw-r--r--@ 1 pravin staff 8661 May 28 09:15 index.html drwxr-xr-x 9 pravin staff 288 May 21 10:34 public -rw-r--r-- 1 pravin staff 674 Apr 17 06:09 readme.md drwxr-xr-x 6 pravin staff 192 Apr 27 16:18 resources
Creating files
- You can use vi editor to create ordinary files on any Unix system. You simply need to give the following command:
- The above command will open a file with the given filename. Now, press the key i to come into the edit mode. Once you are in the edit mode, you can start writing your content in the file as in the following program :
- Press esc to come out of the edit mode
- Press two keys Shift + Z together to come out of the file completely.
- You will now have a file with filename in the current directory.
Editing files
- You can edit an existing file using the vi editor.
- Once the file in opened, you can come in the edit mode by pressing the key i and then you can proceed by editingg the file.
Display content of a file
- Use cat command to see the content of a file. Following is the simple content of the above created file:
Copying files
- To make a copy of a file use the cp command. The basic syntax of the command is:
- Following is the example to create a copy of the existing file filename.
- You wil find one more file copyfile in your current directory. This file will exactly be the same as the original file filename.
Renaming files
- We same command for files as we have used for folders.
- To change the name of a file, use the mv command. Following is the basic syntax:
Deleting files
- To delete an existing file, use the rm command. Following is the basic syntax:
- You can remove multiple files at a time with the command given below −
Standard Unix Streams
Under normal circumstances, every Unix program has three streams (files) opened for it when it starts up
- stdin: This is referred to as the standard input and the associated file descriptor is 0. This is also represented as STDIN. The Unix program will read the default input from STDIN.
- stdout: This is referred to as the standard output and the associated file descriptor is 1. This is also represented as STDOUT. The Unix program will write the default output at STDOUT.
- stderr: This is referred to as the standard error and the associated file descriptor is 2. This is also represented as STDERR. The Unix program will write all the error messages at STDERR.
We will discuss in detail about file permission and access modes in Unix. File ownership is an important component of Unix that provides a secure method for storing files. Every file in Unix has the following attributes −
- Owner permissions: The owner's permissions determine what actions the owner of the file can perform on the file.
- Group permissions: The group's permissions determine what actions a user, who is a member of the group that a file belongs to, can perform on the file.
- Other (world) permissions: The permissions for others indicate what action all other users can perform on the file.
The Permission Indicators
- While using ls -l command, it displays various information related to file permission as follows:
- Here, the first column represents different access modes, i.e., the permission associated with a file or a directory.
- The first three characters (2-4) represent the permissions for the file's owner. For example, -rwxr-xr-- represents that the owner has read (r), write (w) and execute (x) permission.
- The second group of three characters (5-7) consists of the permissions for the group to which the file belongs. For example, -rwxr-xr-- represents that the group has read (r) and execute (x) permission, but no write permission.
- The last group of three characters (8-10) represents the permissions for everyone else. For example,-rwxr-xr--represents that there isread (r) only permission.
File Access Modes
The permissions of a file are the first line of defense in the security of a Unix system. The basic building blocks of Unix permissions are the read, write, and execute permissions, which have been described below :
- Read : Grants the capability to read, i.e., view the contents of the file.
- Write : Grants the capability to modify, or remove the content of the file.
- Execute : User with execute permissions can run a file as a program.
Directory Access Modes
Directory access modes are listed and organized in the same manner as any other file. There are a few differences that need to be mentioned:
- Read : Access to a directory means that the user can read the contents. The user can look at the filenames inside the directory.
- Write : Access means that the user can add or delete files from the directory.
- Execute : Executing a directory doesn't really make sense, so think of this as a traverse permission. A user must have execute access to the bin directory in order to execute the ls or the cd command.
Changing Permissions
To change the file or the directory permissions, you use the chmod (change mode) command. There are two ways to use chmod — the symbolic mode and the absolute mode.
Using chmod in Symbolic Mode
The easiest way for a beginner to modify file or directory permissions is to use the symbolic mode. With symbolic permissions you can add, delete, or specify the permission set you want by using the operators in the following table.
Here's an example using testfile. Running ls -l on the testfile shows that the file's permissions are as follows
Then each example chmod command from the preceding table is run on the testfile, followed by ls –l, so you can see the permission changes
Here's how you can combine these commands on a single line
Using chmod with Absolute Permissions
The second way to modify permissions with the chmod command is to use a number to specify each set of permissions for the file.
Each permission is assigned a value, as the following table shows, and the total of each set of permissions provides a number for that set.
Here's an example using the testfile. Running ls -1 on the testfile shows that the file's permissions are as follows:
Changing Ownership
The chown command changes the ownership of a file. The basic syntax is as follows:
The value of the user can be either the name of a user on the system or the user id (uid) of a user on the system. The following example will help you understand the concept
Changes the owner of the given file to the user amrood. NOTE − The super user, root, has the unrestricted capability to change the ownership of any file but normal users can change the ownership of only those files that they own.
Changing Group Ownership
The chgrp command changes the group ownership of a file. The basic syntax is as follows
The value of group can be the name of a group on the system or the group ID (GID) of a group on the system. Following example helps you understand the concept:
Changes the group of the given file to special group.
SUID and SGID File Permission
Often when a command is executed, it will have to be executed with special privileges in order to accomplish its task. As an example, when you change your password with the passwd command, your new password is stored in the file /etc/shadow . As a regular user, you do not have read or write access to this file for security reasons, but when you change your password, you need to have the write permission to this file. This means that the passwd program has to give you additional permissions so that you can write to the file /etc/shadow . Additional permissions are given to programs via a mechanism known as the Set User ID (SUID) and Set Group ID (SGID) bits. When you execute a program that has the SUID bit enabled, you inherit the permissions of that program's owner. Programs that do not have the SUID bit set are run with the permissions of the user who started the program. This is the case with SGID as well. Normally, programs execute with your group permissions, but instead your group will be changed just for this program to the group owner of the program. The SUID and SGID bits will appear as the letter "s" if the permission is available. The SUID "s" bit will be located in the permission bits where the owners’ execute permission normally resides. For example, the command
- The owner of the sticky directory
- The owner of the file being removed
- The super user, root
- A Shell provides you with an interface to the Unix system. It gathers input from you and executes programs based on that input. When a program finishes executing, it displays that program's output.
- Shell is an environment in which we can run our commands, programs, and shell scripts. There are different flavors of a shell, just as there are different flavors of operating systems. Each flavor of shell has its own set of recognized commands and functions.
Shell Prompt
- The prompt, $ which is called the command prompt , issued by the shell. While the prompt is displayed, you can type a command.
- Shell reads your input after you press Enter . It determines the command you want executed by looking at the first word of your input. A word is an unbroken set of characters. Spaces and tabs separate words.
- Following is a simple example of data command, which displays the current date and time-
Shell Types
- Bourne shell: If you are using a Bourne-type shell, the $ character is the default prompt.
- C shell: If you are using a C-type shell, the % character is the default prompt.
- Bourne shell
- Bourne again shell
- POSIX shell
- TENEX/TOPS C shell
- The original Unix shell was written in the mid-1970s by Stephen R. Bourne while he was at the AT & T Bell labs in New Jersey.
- Bourne shell was the first shell to appear on Unix systems, thus it is referred to as "the shell".
- We are going to cover most of the shell concepts that are based on the Borne shell.
Shell scripts
- Comments are preceded by # sign. # this is a comment
- Comments provide information about the script, such as its purpose, author, and date. The comment lines are not executed by the shell and are purely for human readability.
Example scripts
- Scripts have .sh extension.
- Before you add anything else to your script, you need to alert the system that a shell script is being started. This is done using the shebang construct. For example: #!/bin/sh
- This tells the system that the commands that follow are to be executed by the Bourne shell. It's called a shebang because the # symbol is called a hash, and ! symbol is called a bang.
- To create a script containing these commands, you put the shebang line first and then add the commands: #!/bin/bash pwd ls
Shell comments
- You can put your comments in your script as follows:
Extended Shell Scripts
- Shell scripts have several required constructs that tell the shell environment what to do and when to do it.
- The shell is a real programming language, complete with variables, control structures, and so forth. No matter how complicated a script gets, it is still just a list of commands executed sequentially.
- The following script uses the read command which takes the input from the keyboard and assigns it as the value of the variable PERSON and finally prints it on STDOUT.
- Here is a sample run of the script:
String programs in Linux
- String concatenation is the process of appending a string to the end of another string. This can be done with shell scripting using two methods: using the += operator, or simply writing strings one after the other. The examples below show some shell scripts that can be used to concatenate strings.
Example 1: In this example, we will concatenate two strings using += operator. The input strings will be stored in two variables, a and b . Code ↓
Example 2: In this example, we have two variables a and b, and we stored a string in each variable. We want to concatenate them one after the other. The result of concatenation will be stored in the variable c. Code ↓
Problem solution: Here, we will create a shell script program to create two variables and then print values of variables on the console screen. Program/Source code: The source code to create a Linux shell script program to create and print the value of variables is given below. The given program is compiled and executed successfully on Ubuntu 20.04.
Output ↓
Explanation: Here, we created two variables country, year. which are initialized with "India", 2021 respectively. After that, we printed the value of variables on the console screen using echo command.
Problem solution: Here, we will create a shell script program to add two integer numbers and then print the sum of numbers on the console screen. Program/Source code: The source code to create a Linux shell script program to add two numbers is given below.
Now, we will save the shell script program with "add_two_num.sh" name.
Explanation: In the above program, we created two variables num1, num2 that are initialized with 10 and 20 respectively. Here, we used the expr command to add two values of variables and then print the sum of two numbers on the console screen.
Problem solution: Here, we will create a shell script program to swap to numbers and then print both variables after swapping on the console screen. Program/Source code: The source code to create a Linux shell script program to swap two numbers is given below.
Previous Year Question
Q- explain various file handling commands in linux with example., explain the working of logical and relational operators in linux..
- Logical and relational operatos in Linux are primarily used within shell scripting and command-line operations. These operators allow you to perform logical and relational comparisons on values or expressions to determine the truth or falsehood of a condition. They are commonly used in conditional statements, loops, and decision making processes.
Logical Operators
- AND (&&): Represents the logical AND operation. It returns true if both operands are true, otherwise, it return fale.
- OR (||): Represents the logical OR operation. It returns true if either of the operands is true; otherwise, it returns false.
- NOT (!): Represents the logical NOT operation. It reverses the logical state of its operand. If a condition is true, the NOT operator makes it false, and vice versa.
These operators are typically used to combine multiple conditions or expressions and evaluate the result based on their logical relationship. Example ↓
Relational Operators
- Equal to (==): Checks if two values or expressions are equal.
- Not equal to (!=): Checks if two values or expressions are not equal.
- Greater than (>): Checks if the left operand is greater than the right operand.
- Less than (<): Checks if the left operand is less than the right operand.
- Greater than or equal to (>=): Checks if the left operand is greater than or equal to the right operand.
- Less than or equal to (<=): Checks if the left operand is less than or equal to the right operand.
These operators are primarily used for comparing values or variables and returning a true or false result based on the comparison. Example ↓
Q- What are the file permissions in LINUX and how you can change the permission for a particular file?
Reference ↓
- www.techradar.com (Linux distribution name)
Your submission was sent successfully! Close
You have successfully unsubscribed! Close
Thank you for signing up for our newsletter! In these regular emails you will find the latest updates about Ubuntu and upcoming events where you can meet our team. e.preventDefault()"> Close
Engage pages
Ubuntu case studies, whitepapers and webinars.
Unlocking the Potential: Navigating the AI Journey
27 Aug 2024, Sydney
Innovating the Public Sector with AI: Canonical and NVIDIA Cocktail Reception
In-person networking on June 26th, 2024, Washington D.C.
How automotive companies drive innovation with Ubuntu
Accelerate your automotive development with Ubuntu
Congestion control in the era of high parallelism data centres
Understanding the networking challenges posed by HPC, Machine Learning and Big Data workloads and the avenues that could be explored to solve them.
AI on the edge: solving enterprise challenges with embedded machine learning
Join our panel discussing AI on the edge: challenges, benefits, key considerations and use cases
Discover real-time kernel on Ubuntu 24.04 LTS and Raspberry Pi
Join our webinar on Thursday June 20th at 6pm CET / 9 am PT
Data science tools on Ubuntu: how can you quickly get started?
Learn how Data Science Stack will accelerate your learning curve
OneUptime takes back its servers and saves $352,500 a year with Canonical infrastructure solutions
Migrating to bare metal infrastructure using Canonical’s open-source technologies slashed OneUptime’s cloud costs by over 76%
Canonical deploys infrastructure solutions and managed IT services for critical space mission operations
Canonical Infrastructure enables efficient, automated, and fast deployment of systems across more missions
Security and compliance for IoT device deployments
Download our datasheet and learn more about what Ubuntu Pro for Devices can do for you
(Asia Pacific) Best practices for scheduling security patching automations
Best practices for scheduling security patching automations, from vmware to the future.
Gain another decade of stability with an open source cloud infrastructure
Start your Data and AI journey with Canonical
Explore the rich data and ML open source ecosystem
Migrating from RHEL-based distributions to Ubuntu in the public cloud
A strategy guide for administrators, with a cheat sheet and an example migration
Building ROS snaps with content sharing
ROS Developer Guide - Part 4
Using the Snap Store to distribute ROS applications
ROS Developer Guide - Part 3
Vector databases for generative AI applications
GenAI and beyond: advanced applications of vector databases for Large Language Models (LLM)
Guide to Managed AI Infrastructure
Discover how managed AI infrastructure can accelerate deployments and increase security in our latest executive guide
Guide to deploying AI at the edge with open source
Drivers, challenges, use cases and best practices for edge AI
Secure your supply chain on Google Cloud with Ubuntu Pro
May 15, 2024 12PM ET / 5PM BST
Build and scale your AI projects
Start on Ubuntu, deploy from cloud to edge with Canonical and NVIDIA
Reference Architecture: Use MicroK8s with Charmed Kubeflow on NVIDIA EGX platform
從 vmware 遷移到基於ubuntu 的基礎設施.
確保無縫遷移-對OpenStack和MicroCloud等替代方案的實用見解
Telekom Networks Malawi redefines its infrastructure with Managed OpenStack
Learn how TNM took control of its infrastructure by consolidating its diverse systems onto Charmed OpenStack
Jantar com a Canonical
Transformando empresas através da Infraestrutura de Código Aberto
Guía de control de vulnerabilidad del código abierto
Dedicar menos tiempo al seguimiento de dependencias mientras se mejora la postura de seguridad con un enfoque integral
Pentera shatters misconceptions with seamless migration from CentOS to Ubuntu
Migrating from CentOS to Ubuntu proves easier than expected, and well worth the effort.
Sicredi setzt mit Charmed OpenStack auf Infrastructure as Code
Sicredi adota infraestrutura como código com o charmed openstack, sicredi adopta la infraestructura como código con charmed openstack, 2024년 트렌드에 대한 자동차 업계 리더의 가이드.
지평선 너머: 자동차를 형성하는 혁신적인 트렌드
Introduction to MicroCloud
Join us on April 16th to learn more about MicroCloud - a low-touch open source cloud for all
How to: Secure Embedded Device Management
How to manage your Ubuntu devices at scale with Landscape or Azure IoT Edge
AI on public cloud with open source
Learn why you should use open source tooling for your AI projects on the public cloud
Sicredi embraces the cloud with Canonical OpenStack
Learn how a leading Brazilian financial institution is staying ahead of fintech competition through an open source infrastructure transformation
MongoDB for modern data management
Enterprise use cases and MongoDB’s key features and benefits for modern data management
A deep dive into PostgreSQL replication and automatic failover techniques
Make your PostgreSQL unbreakable
Migrating enterprise Kafka workloads from RHEL to the Ubuntu Platform
A guide for your migration from RHEL
Case Study: Machine learning drives down operational costs in media & entertainment industry
Learn how Canonical Managed Kubeflow helped create a modernised AI strategy
Secure your AI workloads with Confidential VMs
Migrating from rhel-based distributions to ubuntu in microsoft azure.
A strategy guide for administrators, including a cheat sheet and an example migration on Microsoft Azure
Make better decisions with open source Big Data and AI solutions
How to build a smarter enterprise with a secure, integrated open source stack
Unlocking software-defined vehicles: a deep dive into automotive software
Join the expert discussion on March 20 at 9 AM PT, 4 PM GMT
Edge Computing Use Cases
Explore edge computing use cases across industries such as the automotive, telecom, retail, industrial, agriculture, and energy sectors in our latest whitepaper.
Managed AI infrastructure
Discover how managed AI infrastructure accelerates deployments and increases security in our webinar. Join us on March 6th at 3:15 pm CET.
Introduction to Apache Kafka
Learn all about Kafka from the experts - what it is and what it’s used for
Confidential Computing Demystified
Meet canonical at kubecon eu 2024.
Join us at booth E25
AI storage with Ceph
Discover how AI impacts your storage systems and what it means for your business
ARX Fit builds the world’s most effective and efficient fitness machines on Ubuntu Core
Learn how the world leader in Adaptive Resistance technology transformed the user experience for its exercise machines with an immutable OS and OTA updates
Screenly takes the next step in secure screen technology with Ubuntu Core
Learn how Ubuntu Core is enabling Screenly’s new business model, empowering the company to sell to leading, security conscious enterprises
Lightweight Machine Learning with MLflow
Learn more about when, why and how to choose MLflow
Webinar: Navigating the End of CentOS with Ubuntu on Microsoft Azure
Explore the post-CentOS era and learn why Ubuntu is the operating system of choice for the future
MongoDB® for enterprise data management
Understanding MongoDB’s key features, benefits and use cases for modern enterprise data management
Intelligent auto-scaling for Open RAN Network Slicing
Missed us on Lightreading? The unique expert discussion will be available again on February 15th!
A guide to Infrastructure Hardening
Best practices to improve the security posture of your Linux-based infrastructure deployments
Le autovetture autonome e il loro impatto sui trend di consumo
I cambiamenti delle abitudini legate al proprietà dei veicoli e le tendenze nel campo della mobilità
Charmed OpenStack integration with HPE Alletra Storage 9000
A comprehensive guide for integrating Charmed OpenStack, delivered by Canonical, with the HPE Alletra Storage 9000 array from Hewlett Packard Enterprise.
Charmed OpenStack integration with HPE Alletra Storage 6000
A comprehensive guide for integrating Charmed OpenStack, delivered by Canonical, with the HPE Alletra Storage 6000 array from Hewlett Packard Enterprise.
Charmed Kubernetes integration with HPE Alletra Storage 9000
A comprehensive guide for integrating Charmed Kubernetes, delivered by Canonical, with the HPE Alletra Storage 9000 array from Hewlett Packard Enterprise.
Charmed Kubernetes integration with HPE Alletra Storage 6000
A comprehensive guide for integrating Charmed Kubernetes, delivered by Canonical, with the HPE Alletra Storage 6000 array from Hewlett Packard Enterprise.
Building an online datahub with Spark
A guide to building your datahub on or off public clouds.
Secure your stack with Ubuntu
An enterprise-ready OS to manage CVEs, simplify patching and meet compliance needs
A guide to software-defined and multi-source IoT
Why you should choose your IoT software platform before hardware
Using PostgreSQL to power your AI applications
Learn what PostgreSQL has to offer for your AI projects
AI on Private Cloud: why is it relevant in the hyperscalers era?
Learn more about the key considerations of running your AI workloads on a private cloud. Join us on Feb 21 from 3pm CET to dive into this topic.
Simplifying MongoDB operations
Navigate the complexity of managing your database with Charmed MongoDB
The automotive leader’s guide to 2024 trends
在金融服務界應用開源軟體 — 打造穩固的起跑點.
Canonical 協助金融機構革新 IT 基礎架構
Exploring edge computing in automotive
From autonomous cars to factories: how data processing at the edge will transform automotive
Scale, accelerate, and reduce time-to-market throughout IoT development
Canonical bridges the gap between silicon vendors, ODMs and end customers
A CTO’s guide to real-time Linux
Understanding real-time systems, their use cases and inner workings
The Future of Telecom Edge Computing
January 30th, 2024, Paris, France
Jantar com Inteligência Artificial - descubra as novas tendências em Open Source no Azure
O roadshow de IA da Canonical está chegando ao Brasil
Enhanced edge computing for business applications with private mobile networks
Delivering performance, agility, and reliability to enterprises
Guida del CTO ai micro cloud
Scopri come creare una strategia di edge computing di successo grazie ai micro cloud
Guía para CTO sobre micronubes
Descubra cómo desarrollar una estrategia eficaz de procesos perimetrales con micronubes
Get started with Spark on MicroK8s
Deliver production-ready pipelines from your laptop
MLOps Toolkit Explained
From hardware to applications, discover the key factors to consider when building your machine learning toolkit
From VMware to OpenStack
Lower your TCO by 40% with your own open source cloud
What is OpenStack and why does it matter?
Learn how to build a cloud your way by joining us on 22nd Nov at 12 PM CET. Scroll down to register.
Product Launch MicroCloud: Live Stream
Enroll now to join us on November 14th, 4:30 pm UK time
Jantar com Inteligência Artificial - descubra as novas tendências em São Paulo
Maximizing security and compliance in the us public sector with ubuntu pro.
Solving compliance complexity with Ubuntu Pro
Sign up for the Canonical Data Fabric beta program
Join the beta program to get early access to tomorrow’s tech today and to help shape Canonical’s data products as they get introduced to the world
Telco edge cloud automation at scale
How to automate your cloud-native edge cloud deployment, maintenance and operations
Lunch with Canonical: Trasformazione Digitale e scalabilita nell’open-source
Join us at our exclusive launch event in Milan on 9th November, 2023
Charmed OpenStack 促成的私有雲變革 - 角川集團子公司
【案例分享】建構開源基礎設施所帶來的轉變
Ubuntu를 이용한 디지털 사이니지와 키오스크
비즈니스를 위한 스마트 디스플레이를 만드는 쉽고 안전하며 신뢰할 수 있는 방법
MongoDB® Toolkit
A guide to streamline MongoDB database operations including security and support
MicroVision powers autonomous driving
Learn how MicroVision, a pioneer in scanning technology, migrated from a legacy virtualisation platform to a Charmed OpenStack private cloud
Enterprise Data Management: Big Data
A guide to Implementing big data solutions with open source
Meet us at GITEX 2023
October 16th to 20th, 2023
Still running Ubuntu 18.04? What you need to know
Discover how existing Ubuntu 18.04 users can swiftly and effortlessly safeguard their system’s security using Ubuntu Pro.
PostgreSQL for Oracle database users
Compare two of the most advanced database management systems
MicroCloud Launch Event: Munich
Join us at our in-person launch event in Munich on 21st November
Lancement de MicroCloud: Paris
Rejoignez-nous pour le lancement en exclusivité, à Paris le 16 novembre.
MicroCloud Launch Event: London
Join us at our in-person launch event in London on 14th November
Meet Us at India Mobile Congress 2023
October 27th to 29th, 2023
Canonical no Dell Technologies Forum - Brasil
19 de Setembro — Encontre nosso time em São Paulo, aprofunde seu conhecimento em open source e ainda ganhe prêmios!
VMware migration to Ubuntu-based infrastructure
Practical insights into VMware alternatives such as OpenStack and MicroCloud to ensure a seamless migration
A guide to open source vulnerability management
Spend less time tracking dependencies while improving your security posture with a comprehensive approach
Software-defined storage for enterprises
A guide to utilizing Ceph for your enterprise cloud storage needs
Accelerate banking transformation with secure open source
A guide for banking leaders
Build your LLM factory with NVIDIA and Canonical
Hands-on workshop at World AI Summit, Amsterdam
Canonical Tech Summit – Edge/IoT
Bangalore – 05 October
Canonical Tech Summit – Data Fabric
Canonical tech summit - cloud, canonical tech summit – bangalore.
Choose your track
Dive into open source technologies with Canonical
New Mexico State University Physical Science Laboratory drives agile and compliant federal research with Ubuntu
Learn why New Mexico State University Physical Science Laboratory chose Ubuntu to replace CentOS and enable FIPS compliance in line with new DoD regulations
Open source AI in banking
Insights, use cases and best practices for effective AI deployment at scale
Cloud Cost Optimization Best Practices
Discover proven techniques to reduce TCO in public, private, and hybrid multi-cloud environments
Back to school: Ubuntu Desktop in education
Join us live to learn more about the role of Ubuntu in Education
How to ensure business continuity with IT infrastructure support
Learn how the power of professional support can help you minimise downtime and quickly restore your systems.
Canonical Partner Executive Summit – Dallas
Increase your sales with Canonical, the publisher of Ubuntu
Canonical Partner Executive Summit – Bangalore
How ubuntu enables your compliance with fedramp, fisma, fips, and disa-stig.
Complying with the Government security standards
IoT용 도커(Docker) 컨테이너
學習如何選擇機器學習運營化工具,確保AI計畫的生產部署及維運
Demystifying generative AI: how to roll it out in your enterprise
A round table with machine learning experts from Dell, NVIDIA and Canonical
UAB accelerates research with Canonical and Dell
Learn how University of Alabama at Birmingham further accelerates research by transforming its approach to compute and storage resource management through Kubernetes.
L’Istituto Nazionale Italiano di Geofisica e Vulcanologia mette a prova di disastri naturali le sue capacità di monitoraggio grazie a Charmed OpenStack
Run ai at scale.
Build Your Performant ML Stack with NVIDIA DGX and Kubeflow
Garantizar la seguridad y el tiempo de actividad al parchear vulnerabilidades en Linux
Aprenda a crear una estrategia práctica para la aplicación de parches de seguridad en Linux
Patches de segurança do Linux: práticas recomendadas para mitigação de riscos e do tempo de atividade
Aprenda a criar uma estratégia acionável para patches de segurança no Linux
Código aberto seguro para serviços financeiros
Construção de uma base para a adoção eficaz e segura
Código abierto seguro para servicios financieros
Cómo sentar las bases para una adopción eficaz y segura
How real-time Linux accelerates industrial transformation
An overview of real-time use cases and technologies with Canonical and Intel
Get bug and security fixes and operational support for your PostgreSQL deployments
One-month free trial
Secure your open source Redis software
Secure all the components and extensions of your Redis deployments
Get an Ubuntu Pro upgrade with 1 month free trial
Reduce your open source vulnerability from 98 days to just 1 day
Código aberto em serviços financeiros – comece com uma base sólida
Introducción a las redes lte y 5g privadas de código abierto, charmed spark.
Reference Architecture Guide for Charmed Spark 3 Release 1
El código abierto en los servicios financieros: comenzar con una base sólida
Hpe telco validated design with canonical microcloud.
Next-generation compute solutions to power hybrid environments wherever it lives — from the edge to the cloud
Introduction to high-performance computing
Understand what is HPC, its architectures, tooling, deployment, and more in our latest ebook
How to build a cloud in under an hour?
Join our online workshop and build your own cloud
Ubuntu or macOS: a guide for enterprise developers and IT administrators
Overcome the telco dilemma: reduce 5g infrastructure costs with open source, o linux é seguro.
A segurança do sistema operacional é o limite superior da segurança do seu aplicativo
¿Linux es seguro?
La seguridad del sistema operativo es el nivel máximo de seguridad de su aplicación
Improving telecom security in 2023
Best practices to keep open source telco infrastructure secure
Docker security and FIPS compliance from air gap to cloud
FIPS-enabled Ubuntu containers anywhere
Open source MLOps on AWS
Quickly set up your AI/ML infrastructure with Kubefow on AWS
Kubeflow vs MLFlow
Learn the main differences between the MLOps tools of choice: Kubeflow and MLFlow
Data Backups
A strategic guide to improve your database security with backups
Meet us at OSM Hackfest
12-16 June, 2023 in Barcelona, Spain
從 VMWare 轉換至 OpenStack
採用開源以降低基礎設施之成本並提升效率
Secure your customers’ open source ecosystems with Ubuntu Pro
Open-source software adoption is on the rise, but securing open source long-term is a challenge for most organizations who use it.
Meet us at Data Edge - Australia
May 25, 2023 in HYATT REGENCY, SYDNEY
University of Tasmania unlocks real-time space tracking with AI/ML supercomputing
Learn how Tasmania University is modernising its space-tracking data processing with the Firmus Supercloud, built on Canonical’s open infrastructure stack
임베디드 리눅스: 욕토(Yocto) 또는 우분투(Ubuntu) 코어
CTO를 위한 비교 안내
Canonical Partner Executive Summit - Paris
Augmentez vos ventes avec Canonical, l’éditeur d’Ubuntu
Spark Security for Big Data Operations
Best practices and practical steps to spark security
Telco cloud implementation
How to build carrier-grade infrastructure using enterprise open source solutions
Migrating from VMware to Open Source
Artificial intelligence in retail: use cases, tools & business benefits.
AI’s impact on operational efficiency, CX personalisation, and the rise of omnichannel
An introduction to confidential computing
Improve the security of your public cloud workloads
Italy’s National Institute of Geophysics and Volcanology disaster-proofs its monitoring capabilities with Charmed OpenStack
Ubuntu 18.04 lts end of standard support.
Get options and recommendations
Solution brief: Charmed Kubeflow delivered on NVIDIA DGX systems
Canonical and NVIDIA: working together to help enterprises benefit from AI/ML
HPE Telco Validated Design with Canonical Anbox Cloud Appliance
Generate and monetise new offerings for stream mobile apps with HPE and Canonical Anbox
Driving open source together with Canonical and Intel
Canonical and Intel collaborate on strategy, engineering, and support to deliver an exceptional experience to our shared customers, from cloud to edge, using open source software
What’s new in Ubuntu Desktop 23.04 Roundtable discussion
Join us at 4pm GMT on May the 4th
Introduzione ad OpenStack
Introducción a openstack, une introduction à openstack, phoenix systems’new standard for secure cloud services.
Learn how the company built a hyper-secure OpenStack cloud using IBM LinuxONE, Ubuntu, and Canonical automation solutions
Define a Data Migration Strategy
Join us on the 18th of April to learn how to successfully plan and execute your data migration
We appreciate your feedback
Now you can download the assets from our presentation.
Ubuntu at Infosys
Fill out the evaluation form and download the assets from our presentation.
Cloud storage cost optimization
Learn how you can reduce your storage costs with cloud-adjacent storage
Case Study: from hypervisors to LXD
Learn how Wyoming Department of Transportation keeps drivers safe and informed by pivoting from hypervisors to LXD!
Docker containers for IoT
What are the limitations of Docker containers for IoT and Canonicals alternative for you to securely distribute and manage applications at the edge.
Avoid kubernetes security risks with hardening best practices
Watch on-demand
Canonical Executive Summit - London
The power of open source event in London
OpenStack vs Kubernetes
Which one to pick? That is the question!
KADOKAWA Connected becomes a catalyst for change with Charmed OpenStack
Embracing open source infrastructure
What’s new with MAAS 3.3?
Hear about the latest bare metal provisioning features

Migrating from VMware to Ubuntu-based infrastructure
Discover how you can assist your customers to seamlessly migrate from VMware to Ubuntu-based infrastructure.
How Canonical and NVIDIA can help operationalise your AI models quickly
Life sciences: deep learning helps image analysis for drug discovery
Intelligent auto-scaling in 5G RAN based on MicroK8s with Ubuntu real-time kernel on Intel® technology
Cue.01: linux beta: faq.
Please read the FAQ carefully before your exam
Embedded Ubuntu for devices
Setting new standards in the embedded world
Go Low-Ops and stay in control with Software Operators
Lower your overhead with an open-source framework
Kubernetes & cloud native operations survey
Fill out the survey to win the Mystery Box Raspberry Pi Raffle!
Talk to us about your open source initiatives at Fintech Meetup
March 19-22, 2023 in Las Vegas, NV
Cloud cost management: how to cut your cloud costs by 2/3rd?
Discover proven techniques to manage your cloud costs for public, hybrid, private or multi-cloud environments
A guide to MLOps
Learn how to choose your MLOps tooling; take your AI projects to production.
Secure Access To Linux VMs: SSH Security Guide
Practical linux identity management guide, focused on helping you secure SSH access to Linux VMs
Deploying ROS Applications With Snaps
A Developer Guide
2022 雲端定價報告
瞭解雲端定價對雲端基礎架構選擇的影響
The automotive leader’s guide to 2023 trends
The year of software-defined everything
How to migrate from VMware to Ubuntu-based infrastructure
What to expect and how to prepare for a seamless migration
Securing the cloud with Canonical Kubernetes and Kubescape
Join us for the webinar on Feb 8th at 12:30pm GMT. More details below.
HPE Telco Validated Design with Canonical OpenStack
A virtualization technology solution to allow multiple and isolated applications to run on a single OS on top of the HPE ProLiant server family.
Un guide commercial pour l’hybride/multi-cloud
Une extension rentable de l’infrastructure du cloud public
Chiselled Ubuntu images for containers
Smaller container images can save on storage costs, improve the security and even minimise the carbon footprint of our apps.
Adopting a secure enterprise Linux desktop
How to empower developers and data scientists and get trusted manageability for IT with Ubuntu Pro Desktop
Introduction to Machine Learning Operations (MLOps)
Automate your machine learning workflows with an MLOps solution. A hands-on demo with Kubeflow.
Artificial Intelligence and Machine Learning advisory
Start your AI/ML journey now with Canonical
Financial services industry leaders’ guide to secure open source
Adapt. Innovate. Transform.
A Guide to Database Cloud Migration
Best practices to migrate your data to the cloud
Ein Cloud-Migrations-Leitfaden für Unternehmen
Cto’s guide to microcloud.
Learn how to build a successful edge computing strategy with MicroClouds
Autonomous cars and their impact on consumer trends
Changing vehicle ownership habits and mobility trends
A stronger approach to Azure cloud security with Ubuntu
Building a foundation for security-sensitive workloads
Embedded Linux: Yocto or Ubuntu Core
A comparison guide for CTOs
混合雲基礎設施現代化教戰手冊
獻給所有首席技術長(CTO)的運用範例和策略指引
Apache Kafka architecture: authentication options
An examination of authentication options for Apache Kafka
Ein Hybrid-/Multi-Cloud-Leitfaden für Unternehmen
Die Umstellung auf die Cloud wird von einer Reihe von Vorteilen der Cloud-Infrastruktur im Vergleich zu traditionellen Datenzentren vorangetrieben
Kubernetes Operators 指南
完整了解軟體營運師框架(operator frameworks)的功能與優勢
Increase efficiency of your operations with Kafka
Ace your Kafka commands with this cheat sheet
Linux security patches: best practices for risk-mitigation and uptime
Learn how to build an actionable strategy for security patching in Linux.
Hybrid cloud strategy: a modernisation playbook for CTOs
Best practices to modernise your cloud infrastructure and drive hybrid cloud adoption
Confidential computing for financial services
Protect your sensitive data and enable new business models
More infrastructure and open source support for your customers
Together with Canonical, Dell can take advantage of this momentum and propose the most cost-effective, performant, consistent and secure pure upstream open source stack.
Adopt open source securely from bare metal to cloud
Join us on December 1 at 9 AM PT, 5 PM GMT
Lift and Shift, or Rebuild: choosing your cloud migration strategy
Learn how you can digitally transform your company by migrating to the cloud
Ubuntu auf einem neuen Level: Amazon WorkSpaces
Erfahren Sie mehr über das erste vollständig gemanagte Ubuntu VDI auf AWS WorkPlaces und relevante Use Cases
Introduction to cloud-native storage
Understand what is needed from a storage system to support containerised workloads in private clouds
Cloud cost optimisation best practices
Optimised ubuntu on next-gen intel socs accelerates iot adoption.
11am CEST, Nov 28, 2022
Artificial Intelligence in Retail: new use cases for brick and mortar & e-commerce
Join us on November 29 at 9 AM PT, 5 PM GMT
Security and real-time Linux in a shifting automotive world
Bridge the gap between the traditional automotive industry approaches and the best software practices
Secure Kubernetes at the Edge
How strict confinement enables a secure IoT landscape
Cloud Pricing Report 2022
Understand the impact of cloud pricing on cloud infrastructure choices
Compliant managed services in Microsoft Azure
Get the best from managed service providers while ensuring governance
Meet our team at FST Government Australia
8 November 2023, Canberra, Australia
From VMware to Open Source
How to prepare for a seamless migration to the world’s largest infrastructure and applications ecosystem?
Introduction to Ubuntu Pro, the most comprehensive subscription for open-source software security
Learn how your enterprise can benefit from using Ubuntu Pro
Firmus 利用以再生能源電力網供電之超高效率資料中心
重新定義雲端服務永續性
Hyperparameter tuning with MLOps platform
Watch the webinar on-demand
How to reduce your IoT costs with Ubuntu Core
October 26, 6:00 PM Europe/Paris
Introduction to micro clouds
An on-demand edge computing solution
Magma Deployment - The Charming Way
A Canonical and TCS eBook
Canonical Anbox Cloud Workload on Ampere Altra
Solution Brief
Canonical & Ubuntu at Arm DevSummit 2022
Join us virtually on October 26-27, 2022
Gestisci la disruption: come adattare la tua strategia IT ai mercati in costante evoluzione
Leggi il nostro whitepaper per scoprire di più sul moderno panorama aziendale in continua evoluzione – cloud e SaaS, metodo agile ed outsourcing – ed invididuare una strategia per sopravvivere nel mercato
De VMWare vers Charmed OpenStack
Réduisez les coûts et augmentez l’efficacité de votre infrastructure grâce à l’adoption de logiciels open source
Solution brief: Kubernetes by Canonical delivered on NVIDIA DGX systems
Android-based cloud gaming solution with nvidia gpus and anbox cloud, a practical guide to iot lifecycle management.
Best practices to plan, implement and operate IoT projects
Exploring cloud-native and open-source data solutions in transport and logistics
The key to building a customer-centric organisation
Building an autonomous Open RAN ecosystem with Open Source MANO
Manage your telco infrastructure with OpenRAN service orchestration
GSI Executive Summit 2022
Open Source for Enterprises: from infrastructure to cloud applications
Go-to-market strategy with MassRobotics
Robot Makers webinar, Chapter 3, Oct 5th 2022, 5:00pm CEST
Microsoft and Canonical announce native .NET availability in Ubuntu 22.04 hosts and containers
Install the ASP .NET, .NET SDK and .NET runtime with a single command on Ubuntu 22.04
HPE Telco validated design with Canonical Kubernetes
Telco infrastructure solutions from HPE and Canonical provide leading, carrier-grade infrastructure to enable choice, flexibility, agility, and a lower total cost of ownership (TCO).
Managing OpenStack like a public cloud
A guide to kubernetes operators.
Understand software operator frameworks, their capabilities and benefits.
[Webinar] CentOS to Ubuntu Migration with AWS
Join us on September 1, 8am PT as Canonical and AWS discuss CentOS retirement and migration journey to Ubuntu.
Together with Canonical, HPE can take advantage of this momentum and propose the most cost-effective, performant, consistent and secure pure upstream open source stack.
物聯網的五大挑戰與解決之道
以五大關鍵問題搭配自我檢核表,協助您成功推展 IoT 專案
How to bridge the IT/OT divide in Industry 4.0
A developer’s guide to operators.
Get best practices to develop software operators on a solid foundation
Meet our team at AWS Summit in Canberra
31 August 2022. Canberra, Australia
Is Linux secure?
Don’t miss the updates of the Summer 2023 Edition!
Kubernetes operators explained
Learn about the operator pattern and dive into its capabilities and benefits.
Get a Guest Pass for Image’22 and meet us in Houston, TX
George R. Brown Convention Center, 28 Aug - 1 Sept 2022
IoT DevOps webinar
How to scale software development to the edge
Canonical’s Response on NCSC Requirements
Introduction to open source mano (osm).
Accelerate telco workload migration to NFV with OSM
What’s new in MAAS 3.2?
A cto’s guide to software-defined vehicles.
Tackle hardware and software complexity in automotive
A technical introduction to Ubuntu Core 22
Gain a technical understanding of the new features in Ubuntu Core, the OS optimised for IoT and embedded devices
Implementing FIPS with maximum security configurations
Minimise the amount of time your systems are vulnerable after a patch is published, to be safe when an exploit becomes active
Public, private and managed clouds
Building hassle-free cloud operations
Top 5 IoT challenges and how to solve them
A guide and checklist with questions to advance your IoT project and drive success
An introduction to OpenStack
Guía de nubes híbridas o multicloud para empresas.
Una extensión rentable de la infraestructura en la nube pública
Ubuntu Pro no Microsoft Azure
Explore recursos como segurança estendida, conformidade certificada e proteção para Ubuntu Pro no Azure.
Cutting the cost and complexity of cloud
GSIs can deploy and manage the most innovative and easy to use technology on the market without sacrificing security, stability, or incurring unnecessary costs.
Introduction to cybersecurity with Ubuntu Pro on Azure Government
Join us on June 27 at 9 AM PDT, 12 PM EDT
4 ways to accelerate time to market for IoT devices
A guide for manufacturers looking to speed up innovation at lower costs
A guide to software operators for metal, cloud and Kubernetes
Intro to ubuntu core 22.
Join us on July 27th at 6:00pm BST
[Roundtable] Energy Companies on the Move: From CentOS to Ubuntu
Join us on June 28, at 10 AM CDT
What’s new in Charmed Ceph and Quincy in the Ubuntu 22.04 LTS release?
Canonical at hpe discover 2022.
June 28–30 — Meet the Canonical team in Las Vegas
[Partner Webinar] Raising the bar on cybersecurity with Ubuntu for AWS GovCloud
Register now!
Introduction to confidential computing on public clouds with Ubuntu
Open-source supply chain on azure i microsoft oss series.
Webinar Schedule: 18th May, 1:30PM EEST
[Webinar] Security of telecom infra
Part I: Intro to telco grade Kubernetes, on-demand webinar
Omnichannel Enablement for enhanced customer experience in Retail
August 16 at 10 AM PDT, 1 PM EDT
[Webinar] Interview with Akara Robotics CEO
Robot Makers, Chapter 2, June 2 at 5:00 PM CET
Getting started with Ubuntu Pro on Azure
Thank you for choosing Ubuntu Pro on Azure!
Cross platform data science workflows using Ubuntu WSL
Learn about the benefits of a mixed ecosystem approach for day to day DataScience workflows.
Open infrastructure for data science
Charmed OpenStack with NVIDIA vGPU Software
Active Directory integration features in Ubuntu 22.04
Demo and Live Q&A
Ubuntu WSL for Data Scientists
Balancing accessibility against performance in a Windows-centric workplace.
Canonical at Dell Technologies World 2022
May 2–5 — Meet the Canonical team in Las Vegas
Meet our Public Sector team at AWS Summit
May 23 - 25 at Walter E. Washington Convention Center, Washington, DC
Getting started with Ubuntu Pro on AWS
Thank you for choosing Ubuntu Pro on AWS!
The collection of Charmed Operators
A win-win for users and developers
Seeking satisfaction: Customer-centric digital transformation in logistics
Guide on how to make your customers happy using open source technologies and digital transformation for logistics leaders
Firmus builds a supercloud with Canonical
Cloud sustainability redefined with ultra-efficient data centre powered by grid connected renewable energy
Umony transforms communications compliance
Learn how Anbox Cloud enables Umony to deliver its software through an app on any phone, web browser, or desktop
DISA STIG auditing and remediation in air-gapped environment
Compliance with DoD Security Technical Implementation Guide (STIG) is an essential requirement for all DoD agencies or any organisation that is part of the DoD information network (DoDIN). Auditing and hardening systems at scale is often a complicated task, especially in air-gapped environments.
OpenStack Yoga: What’s new?
Learn about the latest release of OpenStack
Introduction to MLOps: Six proven techniques to amplify AI maturity
Learn how to leverage MLOps to amplify AI and data science productivity and maturity through six proven techniques from the pros.
Ubuntu Pro: Maggiore supporto e sicurezza per le VM su Azure
Live webinar: 31 Marzo alle 11 CET
Webinar: Guía de operaciones para Kubeflow
Mar 31 2022 at 6:00 pm CET
[Webinar] Yocto or Ubuntu Core for your embedded Linux project?
Register for the webinar: March 29 2022, 5:00 PM CET
Build on MicroK8s, the lightweight Kubernetes
Easier deployments. Better customer experiences.
Reduce complexity & increase storage efficiency with multi-protocol Ceph
Public cloud vs private cloud: building an innovative cloud strategy, open ran infrastructure: turbo charge your hardware with epa.
Maximise hardware utilisation by using metal-as-a-service (MAAS) to build your bare metal cloud
Win-win for software vendors and IT admins
OpenStack made easy for GSIs
Easily build a modern, scalable, repeatable and affordable cloud infrastructure.
Managed IT Services: Overcoming CIOs biggest challenges
How to build a strategic IT model that drives innovation while cutting down operational costs
Architecting Price-Performance Private Cloud
Learn how GSIs can build the most cost-efficient private cloud infrastructure using open source technologies
Embracing the Enterprise Open Source Mandate
85% of enterprises have an open source mandate, preference or are exploring
Webinar: IoT Project Lifecycle
What are the typical steps when deploying IoT edge devices?
Introduction to Bare Metal Cloud
Build your own bare metal cloud in a box with Kubernetes
A guide to Linux for embedded applications
Why is Linux the OS of choice for embedded systems?
Roboat, more than a self-driving boat
Robot Makers, Chapter 1
Financial Services CTO’s guide to unlocking success in digital transformations using cloud-native infrastructure
Enterprise kubernetes case studies.
Want to learn more about 4 success stories across 4 different markets?
Build Your Digital Signage Solution with Ubuntu Frame — The Developer Guide
Test, package and ship your embedded GUI for IoT
[Webinar] FIPS Enabled Ubuntu Pro on AWS
DevSecOps, RMF, ATO, Compliance as Code, FedRAMP & GovCloud
Deliver your software with Kubernetes
MicroK8s for streamlined application container deployment
Introduction to SmartNIC DPUs for the data centre
One-stop shopping for private clouds.
Now enterprises can easily and economically move forward in their cloud journeys.
Comparación de la plataforma Kubernetes: Red Hat OpenShift, SUSE Rancher y Canonical Kubernetes
¿Cómo elegir la distribución de Kubernetes ideal para su negocio?
Ubuntu on WSL
An FAQ for Data Scientists and Developers
How to enable FIPS on Ubuntu in air-gapped environments
Watch on-demand below
Reduce your storage costs with cloud adjacent storage
Private cloud vs managed cloud, report gratuito sui prezzi del cloud 2021.
Ottieni il report per confrontare i prezzi del cloud tra le principali piattaforme cloud pubbliche e private, tra cui AWS, Azure, Google, VMWare e OpenStack
Guida aziendale al multi-cloud
Canonical at mwc 2022, a business guide to cloud migration, confronto tra piattaforme kubernetes: red hat openshift, suse rancher e canonical kubernetes.
Come scegliere la giusta distribuzione Kubernetes per il vostro business
Screenly innovates IoT fleet management for secure digital signage
How to run workloads on bare metal kubernetes with maas.
Easy and automated bare metal Kubernetes provisioning
Model-driven observability with Prometheus, Alertmanager, Grafana and Loki
Leveraging Juju to remove toil out of best-of-breed open-source observability
Embedded Kubernetes for secure IoT Edge
MicroK8s on Ubuntu Core
Bare metal provisioning: What’s new in MAAS 3.1?
The latest and greatest news about bare metal provisioning with MAAS
Evaluating Microsoft SQL Server Options for Azure
This white paper provides an in-depth examination of the most popular approaches to running SQL Server on Azure, including SQL Server on Ubuntu Pro for Azure.
Migrating to Ubuntu LTS: six facts for CentOS users
Considering migrating to Ubuntu from other Linux platforms, such as CentOS?
How to increase developer productivity with Ubuntu Desktop
A guide for CTOs, IT managers and sysadmins
NFV Orchestration For Open Source Telco
Integrating And Managing Open Source Network Functions
Ubuntu Pro em Azure
Explore recursos como segurança estendida, conformidade certificada e proteção para Ubuntu Pro em Azure.
Docker & ROS: When all you have is a hammer, everything looks like a nail
Key Docker limitations for ROS and the snap alternative
Ubunto Pro en Azure
Explora características como seguridad extendida, cumplimiento certificado y refuerzo para Ubuntu Pro en Azure.
Introducing SQL Server on Ubuntu Pro for Azure Part 2
In this talk will deep dive on the anatomy of the performance features of SQL Server on Ubuntu Pro and setting up AD.
Building cost-efficient open source cloud operations
Nayatel builds public cloud service with charmed openstack.
Learn how Nayatel partnered with Canonical to build Pakistan’s first cost-effective enterprise-grade public cloud
Ceph for Enterprise
The best open-source enterprise storage solution
Introducing SQL Server on Ubuntu Pro for Azure Part 1
In this talk we will introduce SQL Server on Ubuntu Pro for Azure and deep dive on patching regimes and high availability clustering for SQL Server on Ubuntu Pro.
MicroK8s on IBM Z — minimal footprint meets zero downtime
A low-ops, minimal production Kubernetes on Ubuntu for your IBM Z / LinuxONE system.
Maximising private cloud ROI in Financial Institutions
The Case for Open Source over VMware
開發者選擇Ubuntu的六大理由
最流行的linux os 操作系統,選擇Ubuntu的六大理由
Ceph in the modern data center
Manage exponential data growth with Canonical Charmed Ceph and Dell PowerEdge Servers
Telecom infrastructure the open source way
Automated, secure and cloud native telco
Cybersecurity and Compliance with Ubuntu
Join the live webinar
Atresmedia domina il mercato spagnolo dei media OTT con l’architettura di microservizi Charmed Kubernetes
Come l’azienda ha ottenuto un’alta disponibilità e una produttività senza precedenti
Secure AI models deployment at the edge with OpenVINO on Ubuntu containers
Watch Intel and Canonical’s on-demand webinar
SmartDrone fast-tracks drone infrastructure revolution with Ubuntu Core
Ubuntu 16.04 lts verso la manutenzione estesa della sicurezza.
Sei aspetti da considerare nella pianificazione della migrazione
OpenStack Upgrades with Minimal Downtime
Guide to building a cost-effective private cloud.
Learn how to build the most cost-efficient private cloud infrastructure using open-source technologies
7 approaches to accelerating Apache Kafka on K8s
In this white paper, we will review seven techniques that can help to reduce latency in high volume, low criticality Kafka solutions running on Kubernetes.
Canonical & Ubuntu at Nvidia GTC 2021
Join us on November 8-11!
嵌入式Linux:自製或外購?
兩難的選擇:商業支援VS自研
Enterprise Kubernetes use cases: 4 real-world stories
Edge kubernetes: what’s brewing, driving robotics innovation.
Canonical & Ubuntu at ROS World 2021
Workstations on the AI Journey – Deploying Your Model – Part 4
In the fourth and final part of this webinar series, Canonical and Dell will talk about inference engines deployment.
Managed IT Services
Beat disruption: how to adapt your it strategy for changing markets.
Read our whitepaper to learn more about the fast changing modern business landscape - cloud & SaaS, agile, and outsourcing - and learn about a strategy to help navigate through the jungle.
Canonical & Ubuntu at ARM Dev Summit 2021
Join us virtually on October 19-21, 2021
Building graphical applications in embedded devices
Join us for a webinar introducing Ubuntu Frame on November 3rd at 5pm BST and 12pm ET
It’s like a jungle out there
Learn strategies to help you navigate the fast changing modern business landscape - cloud and SaaS, agile and outsourcing
Self-healing Kubernetes at the edge: MicroK8s, Raspberry Pis and Portainer
Atresmedia domine le marché des média en espagne avec l’architecture de microservices charmed kubernetes, finserv open source infrastructure powers hybrid cloud strategy.
An overview of how to simplify the deployment and management of an OpenStack cloud.
How to manage risks with the top 1% Managed Service Providers
Join our webinar to learn more about Canonical’s MSP Alliance security verification, and how the top 1% managed service providers help minimise your security risks and optimise your clouds.
Kubernetes platform comparison: Red Hat OpenShift, SUSE Rancher and Canonical Kubernetes
How to choose the right Kubernetes distribution for your business
Containers-as-a-service: Deploy faster with Canonical and Portainer
Helping developers reach new heights.
Canonical & Ubuntu at PX4 Developer Summit
Running enterprise-grade edge applications with EdgeX on Ubuntu Core
Watch our on-demand webinar
Applied AI for fraud prevention and detection
How open source AI/ML solutions can assist banks
Atresmedia dominates the OTT services market with Charmed Kubernetes
How the company accessed high availability and unprecedented productivity
Cloud pricing report 2021
Get the report to compare cloud pricing across leading public and private cloud platforms, including AWS, Azure, Google, VMWare and OpenStack
SBI Group sblocca l’automazione dell’infrastruttura con un cloud OpenStack sicuro e on-premises
A business guide to cybersecurity, handlungsoptionen nach dem endof-life der suse openstack cloud, atresmedia domina el mercado de servicios ott.
Con la arquitectura de microservicios Charmed Kubernetes
KAUST selects Canonical’s OpenStack cloud
New OpenStack and Kubernetes deployments improve computing performance for researchers, easing management pains for IT staff
Das Wellcome Sanger Institute ermöglicht weltweite Zusammenarbeit in der Genomforschung mit von Canonical unterstütztem Ceph-Speicher
A technical introduction to the snap store proxy, che cos’è il mec il telco edge., enterprise mlops in hybrid-cloud scenarios: best practices.
Learn about architectural best practices that have recently emerged
OpenStack public cloud implementation
Reduce total cost of ownership with local public cloud infrastructure
ROS Support
Security maintenance and enterprise support for your ROS environment
SUSE OpenStack Cloud end-of-life
A preparation guide
Guida CIO alle operazioni multi-cloud
Come scegliere un’architettura cloud conveniente
Kubernetes e Ubuntu in Italia
Un’esplorazione tecnica delle ultime tecnologie di infrastruttura
Private cloud for Financial Services
Comparing Red Hat OpenStack Platform and Canonical’s Charmed OpenStack
Canonical at MWC 2021
Open source private 5g and lte networks.
Use-cases, tools and technologies
Kubernetes at the edge: easy as Pi
Suse openstack cloud wird eingestellt..
Sind Sie vorbereitet?
Building and orchestrating network functions
Accelerate migration towards NFV with Open Source MANO
Simplifying Kubernetes across the Clouds
MicroK8s on NVIDIA Tech Stack
Data Lab Architectures
A field practitioner guide to building and accelerating data lab initiatives
A business guide to multi-cloud
Utilising a multi-cloud strategy serves as a cost-effective extension to the public cloud infrastructure
A business guide to hybrid cloud
A cost-effective extension to the public cloud infrastructure
Migrare ad Ubuntu LTS: 6 fatti per gli utenti CentOS
State pensando di migrare a Ubuntu da altre piattaforme Linux, come CentOS?
Meno di 6 mesi a Ubuntu 16.04 ESM: 6 cose da preparare
Questo articolo spiega come funziona il periodo ESM e fornisce una guida a sei considerazioni chiave per la pianificazione di un percorso di migrazione da Ubuntu 16.04 LTS.
ROS Kinetic End-Of-Life
Keep your robots secure with ROS ESM
Infrastruttura multi-cloud in Italia
L’evento, della durata di 2 ore, si terrà il 12 maggio 2021 su BrightTalk. Dai live talk dei nostri speaker alle sessioni di Q&A.
Workstations on the AI Journey - Choosing Your Algorithm - Part 2
Take a deep dive into how workstations enable the AI journey in part 2 of our series
Unleashing Z by HP Workstation Power with Ubuntu
Explore key solutions for AI, Machine Learning, and Data Science Workflows
What’s new in Ubuntu Server 21.04?
Introducing native integration with Microsoft SQL Server
The Value of Open Source in 2021
Explore the latest open source market trends and dive into OpenStack, Kubernetes and Edge solutions from Dell and Canonical.
Elkhart Lake
Embedded silicon from Intel focusing on IoT features for the next generation of edge devices.
Telecom AI: a guide for data teams
Optimising AI for production in the telco space
Workstations on the AI Journey – Part 1
Take a deep dive into how workstations enable the AI journey in this four-part webinar series
Model-driven Audit Trail Logs infrastructure for Telco VNFs
Live webinar on April 15th
Securing open source from cloud to edge
Get the full Ubuntu security story and see how our teams are securing Ubuntu systems across cloud, device and edge environments.
ESM garantisce la sicurezza dei sistemi Interana anche durante l’aggiornamento
Caso di studio - Interana
Migrar a Ubuntu LTS: seis factores a tener en cuenta para los usuarios de CentOS
¿Está considerando migrar a Ubuntu desde otras plataformas Linux, como CentOS?
From Yocto & Buildroot to Ubuntu Core 20
The path to enterprise-grade embedded Linux
Costruire infrastrutture multi-cloud con Ubuntu e Kubernetes
Kubeflow operations guide.
Automating day-0 to day-2 with Kubernetes operators
SUSE OpenStack Cloud arrive en fin de vie
Preparez pour votre migration d’OpenStack
What’s next for CentOS users?
Live Q&A with Ubuntu’s technical experts
A technical introduction to Ubuntu Core 20
Full-disk encryption, secure boot, device recovery and more
- Skip to content
- Skip to search
- Skip to footer
Support & Downloads
- Worldwide - English
- Arabic - عربي
- Brazil - Português
- Canada - Français
- China - 简体中文
- China - 繁體中文 (臺灣)
- Germany - Deutsch
- Italy - Italiano
- Japan - 日本語
- Korea - 한국어
- Latin America - Español
- Netherlands - Nederlands">Netherlands - Nederlands
- Helpful Links
- Licensing Support
- Technology Support
- Support for Cisco Acquisitions
- Support Tools
- Cisco Community

To open or view a case, you need a service contract
Get instant updates on your TAC Case and more
Contact TAC by Phone
800-553-2447 US/Canada
866-606-1866 US/Canada
- Returns Portal
Products by Category
- Unified Communications
- Networking Software (IOS & NX-OS)
- Collaboration Endpoints and Phones
Status Tools
The Cisco Security portal provides actionable intelligence for security threats and vulnerabilities in Cisco products and services and third-party products.
Get to know any significant issues, other than security vulnerability-related issues, that directly involve Cisco products and typically require an upgrade, workaround, or other customer action.
Check the current status of services and components for Cisco's cloud-based Webex, Security and IoT offerings.
The Cisco Support Assistant (formerly TAC Connect Bot) provides a self-service experience for common case inquiries and basic transactions without waiting in a queue.
Suite of tools to assist you in the day to day operations of your Collaboration infrastructure.
The Cisco CLI Analyzer (formerly ASA CLI Analyzer) is a smart SSH client with internal TAC tools and knowledge integrated. It is designed to help troubleshoot and check the overall health of your Cisco supported software.
My Notifications allows an user to subscribe and receive notifications for Cisco Security Advisories, End of Life Announcements, Field Notices, and Software & Bug updates for specific Cisco products and technologies.
More Support
- Partner Support
- Small Business Product Support
- Business Critical Services
- Customer Experience
- DevNet Developer Support
- Cisco Trust Portal
Cisco Communities
Generate and manage PAK-based and other device licenses, including demo licenses.
Track and manage Smart Software Licenses.
Generate and manage licenses from Enterprise Agreements.
Solve common licensing issues on your own.
Software and Downloads
Find software bugs based on product, release and keyword.
View Cisco suggestions for supported products.
Use the Cisco Software Checker to search for Cisco Security Advisories that apply to specific Cisco IOS, IOS XE, NX-OS and NX-OS in ACI Mode software releases.
Get the latest updates, patches and releases of Cisco Software.
- Español – América Latina
- Português – Brasil
- Tiếng Việt
- Android Studio
- Android Developers
Compose Preview Screenshot Testing
Screenshot testing is an effective way to verify how your UI looks to users. The Compose Preview Screenshot Testing tool combines the simplicity and features of composable previews with the productivity gains of running host-side screenshot tests. Compose Preview Screenshot Testing is designed to be as easy to use as composable previews.
A screenshot test is an automated test that takes a screenshot of a piece of UI and then compares it against a previously approved reference image. If the images don't match, the test fails and produces an HTML report to help you compare and find the differences.
With the Compose Preview Screenshot Testing tool, you can:
- Identify a number of existing or new composable previews you want to use for screenshot tests.
- Generate reference images from those composable previews.
- Generate an HTML report that identifies changes to those previews after you make code changes.
- Use @Preview parameters, such as uiMode or fontScale , and multi-previews to help you scale your tests.
- Modularize your tests with the new screenshotTest source set.
Requirements
To use Compose Preview Screenshot Testing, you need the following:
- Android Gradle 8.5.0-beta01 or higher.
- Kotlin 1.9.20 or higher.
To enable the tool, follow these steps:
- Add the com.android.compose.screenshot plugin, version 0.0.1-alpha01 to your project.
- Add the plugin to your version catalogs file: [versions] agp = "8.5.0-beta01" kotlin = "1.9.20" ... screenshot = "0.0.1-alpha01" [plugins] ... screenshot = { id = "com.android.compose.screenshot", version.ref = "screenshot"}
- In your module-level build.gradle.kts file, add the plugin in the plugins {} block: plugins { ... alias(libs.plugins.screenshot) }
- Enable the experimental property in your project's gradle.properties file. android.experimental.enableScreenshotTest=true
- Add it to your version catalogs: [libraries] androidx-compose-ui-tooling = { group = "androidx.compose.ui", name = "ui-tooling"}
- Add it to your module-level build.gradle.kts file: dependencies { screenshotTestImplementation(libs.androidx.compose.ui.tooling) }
Designate composable previews to use for screenshot tests
To designate the composable previews you want to use for screenshot tests, place the previews in a test class. The test class file must be located in the new screenshotTest source set, for example app/src/screenshotTest/kotlin/com/google/yourapp/ExamplePreviewScreenshots.kt ( {module}/src/screenshotTest/{kotlin|java}/com/your/package ).
You can add more composables and/or previews, including multi-previews, in this file or other files created in the same sourceset.
Generate reference images
After you set up a test class, you need to generate reference images for each preview. These reference images are used to identify changes later, after you make code changes. To generate reference images for your composable preview screenshot tests, run the following Gradle task:
- Linux and macOS: ./gradlew updateDebugScreenshotTest ( ./gradlew {:module:}update{Variant}ScreenshotTest )
- Windows: gradlew updateDebugScreenshotTest ( gradlew {:module:}update{Variant}ScreenshotTest )
After the task completes, find the reference images in app/src/debug/screenshotTest/reference ( {module}/src/{variant}/screenshotTest/reference ).
Generate a test report
Once the reference images exist, run the validate task to take a new screenshot and compare it with the reference image:
- Linux and macOS: ./gradlew validateDebugScreenshotTest ( ./gradlew {:module:}validate{Variant}ScreenshotTest )
- Windows: gradlew validateDebugScreenshotTest ( gradlew {:module:}validate{Variant}ScreenshotTest )
The verification task creates an HTML report at {module}/build/reports/screenshotTest/preview/{variant}/index.html .
Known issues
You can find the current list of known issues in the tool's Issue Tracker component . Report any other feedback and issues through the issue tracker .
Content and code samples on this page are subject to the licenses described in the Content License . Java and OpenJDK are trademarks or registered trademarks of Oracle and/or its affiliates.
Last updated 2024-05-17 UTC.

IMAGES
VIDEO
COMMENTS
•Only essential features inside the OS -editors, compilers etc are just applications •Processes are the units of scheduling and protection •Command interpreter (shell) just another process •All I/O looks like file operations •In UNIX, everything is a file 11. UNIX Case Study (I) 5
Linux Distribution. Linux distribution is an operating system that is made up of a collection of software based on Linux kernel or you can say distribution contains the Linux kernel and supporting libraries and software. And you can get Linux based operating system by downloading one of the Linux distributions and these distributions are available for different types of devices like embedded ...
Case Study on Linux Prof. Sujata Rizal 6 Open Source − Linux source code is freely available and it is community based development project. Multiple teams work in collaboration to enhance the capability of Linux operating system and it is continuously evolving.
Because Linux is an interesting representative of existing software systems, we chose to examine it as a case study. In particular, we studied the Linux kernel, which is respon- sible for process, memory, and hardware device manage- ment. The Linux kernel is itself a large system (approxi- mately 800 KLOC). Although there is some existing docu-
The case studies here detail why projects benefit from being hosted at the Linux Foundation, and other studies here showcase how our projects support collaborative innovation around the world. ... A case study of how two large European distribution and transmission systems operators, the Netherlands' Alliander and France's RTE, adopted and ...
The Linux operating system is a complete reimplementation of the POSIX interface initiated by Linus Torvalds [187]. Linux gained popularity throughout the 1990s, resulting in the promotion of Linux as a viable alternative to Windows, particularly for server systems (e.g., web servers). As Linux achieved acceptance, variety of efforts began to ...
Linux. Linux is a popular open-source operating system. It was initially created by Linus Torvalds in 1991. At the time, Torvalds was a computer science student at the University of Helsinki, Finland and began working on the Linux project as a personal endeavor. The name Linux is a combination of his first name, Linus, and Unix, the operating ...
The Linux kernel which forms the core of the Linux operating system is the result of one of the largest cooperative software projects ever attempted. The Linux ... CASE STUDY enterprises running Linux as their primary cloud platform, we can expect a dramatic increase in Linux deployments to support the move to the cloud.
An OS is a collection of system programs, tools and utilities that manage computer hardware and offer general services for client application software (Bassil, 2012). The operating system is the first program to do several tasks while focusing on the current task at hand. The first task is prompting the OS to boot the computer. Within minutes, the
When the Linux kernel creates a new task, it requests the necessary memory for the struct task struct object from its cache. The cache will fulfill the request using a struct task struct object that has already been allocated in a slab and is marked as free. In Linux, a slab may be in one of three possible states: 1. Full ...
Operating System Concepts with Java - 8 th Edition 21.4 Silberschatz, Galvin and Gagne ©2009 History Linux is a modern, free operating system based on UNIX standards. First developed as a small but self-contained kernel in 1991 by Linus Torvalds, with the major design goal of UNIX compatibility. Its history has been one of collaboration by many users from all around
Completely novel at the time: prior to this, everything was "inside" the OS. In Unix separation between essential things (kernel) and everything else Among other things: allows user wider choice without increasing size of core OS; allows easy replacement of functionality — resulted in over 100 subsystems including a dozen languages
2. Operating System Case Study: Linux Beginning of Linux -A famous professor Andrew Tanenbaum developed Minix, a simplified version of UNIX that runs on PC -Minix is for class teaching only. No intention for commercial use -In Sept 1991, Linus Torvalds, a second year student of Computer Science at the University of Helsinki,
The kernel is the heart of the operating system which provides a set of tools that are used by system calls. x The defining component of Linux is the Linux kernel, an operating system kernel first released on 5 October 1991 by Linus Torvalds. x A Linux-based system is a modular Unix-like operating system.
A technical introduction to Ubuntu Core 22. Gain a technical understanding of the new features in Ubuntu Core, the OS optimised for IoT and embedded devices. IoT, devices, ubuntu core, embedded linux, edge devices, webinar, Yocto, tutorial, security, developers, enablement, app development. webinar.
UNIT - V CASE STUDY. Linux System - Design Principles, Kernel Modules, Process Management, Scheduling, Memory Management, Input-Output Management, File System, Inter-process Communication; Mobile OS - iOS and Android - Architecture and SDK Framework, Media Layer, Services Layer, Core OS Layer, File System. ... The core Linux operating system ...
features of the OS with various user services. This paper presents a comparative study of six (i.e. Windows, Linux, Mac, UNIX, Android and iOS) operating systems. based on the OS features and ...
Since those early days, developers from large hardware companies to small emerging technology providers have contributed to Linux, building solutions that run on top of the open-source OS. Between 2005 and 2016, more than 14,000 individual developers from more than 1, companies contributed to the Linux kernel project.
Linux - Free download as Powerpoint Presentation (.ppt), PDF File (.pdf), Text File (.txt) or view presentation slides online. Linux originated from MINIX and was created by Linus Torvalds in 1991. It follows the design principles of Unix by being simple, powerful, and flexible. The Linux kernel provides interfaces for processes, memory, scheduling, signals, and I/O.
supercomputers, home appliances, personal computers to EnterpriseServers, the Linux operating system is everywhere. Case Study - LINUX 2.4 EVOLUTION OF LINUX By the beginning of the 90s home PCs were finally powerful enough to run UNIX. Linus Torvalds, a Computer Science student at the University of Helsinki, thought it
Unit 5: Case study on Linux 1. Explain evolution of UNIX. UNIX development was started in 1969 at Bell Laboratories in New Jersey. Bell Laboratories was (1964-1968) involved on the development of a multi-user, time- sharing operating system called Multics (Multiplexed Information and Computing System).
Check the current status of services and components for Cisco's cloud-based Webex, Security and IoT offerings. Cisco Support Assistant. The Cisco Support Assistant (formerly TAC Connect Bot) provides a self-service experience for common case inquiries and basic transactions without waiting in a queue.
With the Compose Preview Screenshot Testing tool, you can: Identify a number of existing or new composable previews you want to use for screenshot tests. Generate reference images from those composable previews. Generate an HTML report that identifies changes to those previews after you make code changes. Use @Preview parameters, such as uiMode ...
Despite advancement in surgical innovation, C1-C2 fixation remains challenging due to risks of screw malposition and vertebral artery (VA) injuries. Traditional image-based navigation, while useful, often demands that surgeons frequently shift their attention to external monitors, potentially causing distractions. In this article, we introduce a microscope-based augmented reality (AR ...
CASE STUDY ON LINUX. The Linux System An operating system is a program that acts as an interface between the user and the computer hardware and controls the execution of all kinds of programs. The Linux open source operating system, or Linux OS, is a freely distributable, cross-platform operating system based on UNIX.