- Connect Virtually - Wear Mask, Stay Home, Stay safe
- VMWare, PowerCLI, DevOps, Kubernetes
- Microsoft Azure, PowerShell, Ansible, Terraform

#header_text h1#site_heading a, #header_text h1#site_heading{ } @media (min-width: 650px) { #header_text h1#site_heading a, #header_text h1#site_heading{ } } Virtual Geek
#header_text h2#site_subheading a, #header_text h2#site_subheading{ } @media (min-width: 650px) { #header_text h2#site_subheading a, #header_text h2#site_subheading{ } } tales from real it system administrators world and non-production environment.
Working With Azure Key Vault Using Azure PowerShell and AzureCLI
This is second part of Create key vault and secrets with access policies in Microsoft Azure , In the this article I will use Powershell and Azure CLI to create and configure Azure Key Vault resource service. Azure Key Vault is a cloud service that provides a secure store for secrets. You can securely store keys, passwords, certificates, and other secrets. In the first example In the first example I am using Microsoft Powershell Az module to deploy and configure Key vault.
Connect-AzAccount The 'Connect-AzAccount' command was found in the module 'Az.Accounts', but the module could not be loaded Powershell Azure Az module Install-Package cannot convert value 2.0.0-preview to type system.version
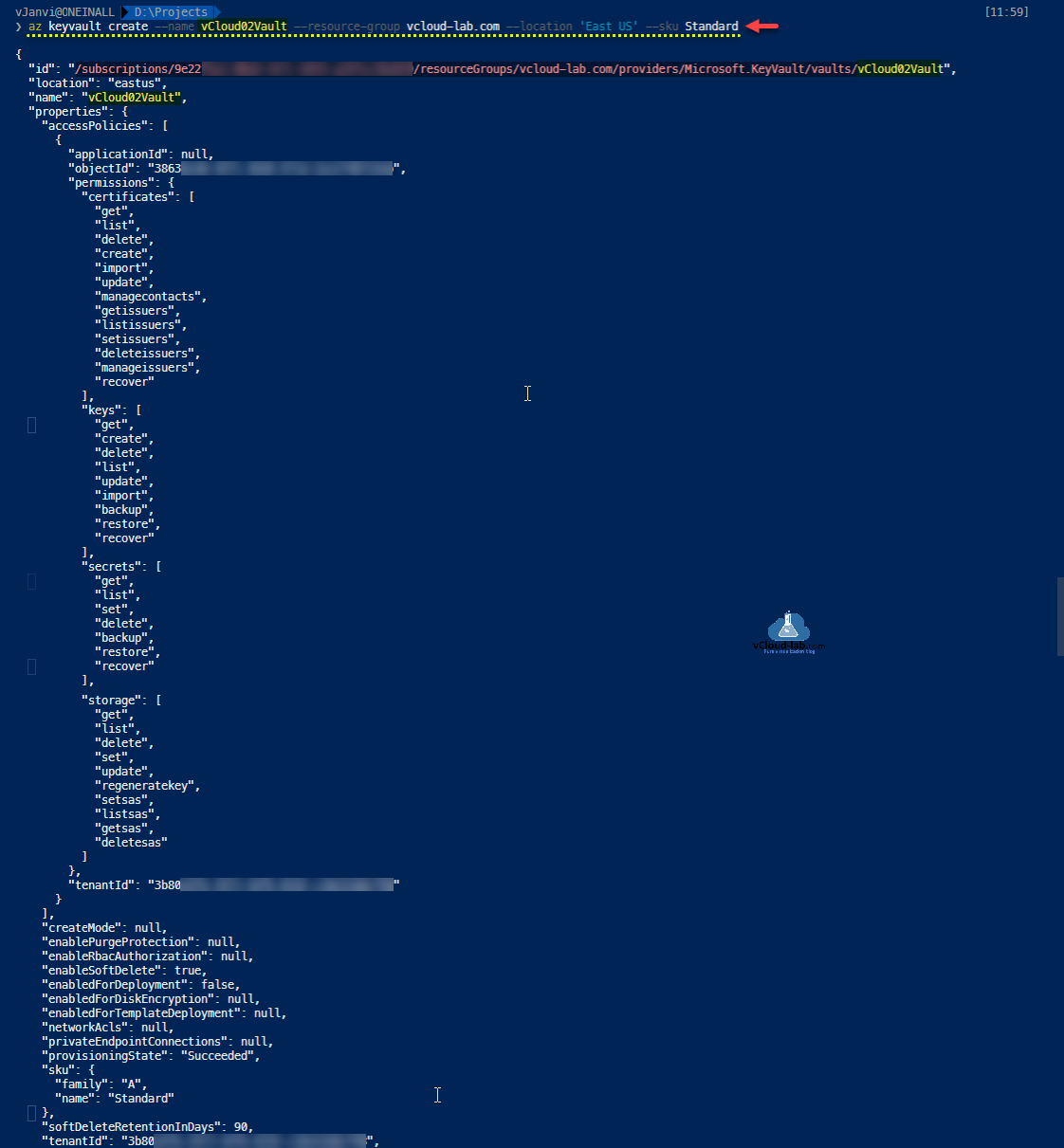
PowerShell Az module example First cmdlet connects to azure using az module and creates a new key vault resource. Download this script here or available on github.com .

Once Key vault is created in azure, generate a secret on it with encrypted password string, next configure Access policy to provide access on key vault secret to Azure AD user principal .

I have already create a new user account vaultviewer on Azure Active directory for testing Creating a new user in Azure AD using oneliner PowerShell and Azure CLI . Next get and store the key vault information in variable to know ResourceID which I will use when assinging role ( Key Vault Reader ) to user principal on the keyvault. (In my case user principal name is vaultviewer )

Logout of Azure powershell account with Disconnect-AzAccount and login with the user (in my case vaultviewer ), Get the key vault secret and convert the secure string to readable plain text password with below commands.

AzureCLI example
Login to the AzureCLI, All the Az command generate output in JSON format.
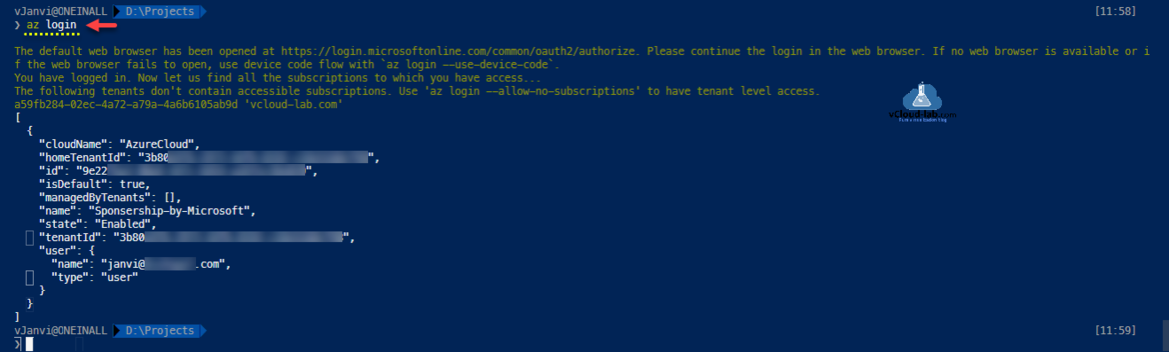
Create a new Azure Key Vault resource, note down the resource ID I will use it later in the command.
Once key vault is created, setup a new secret and set attribute content type (description) on to it.

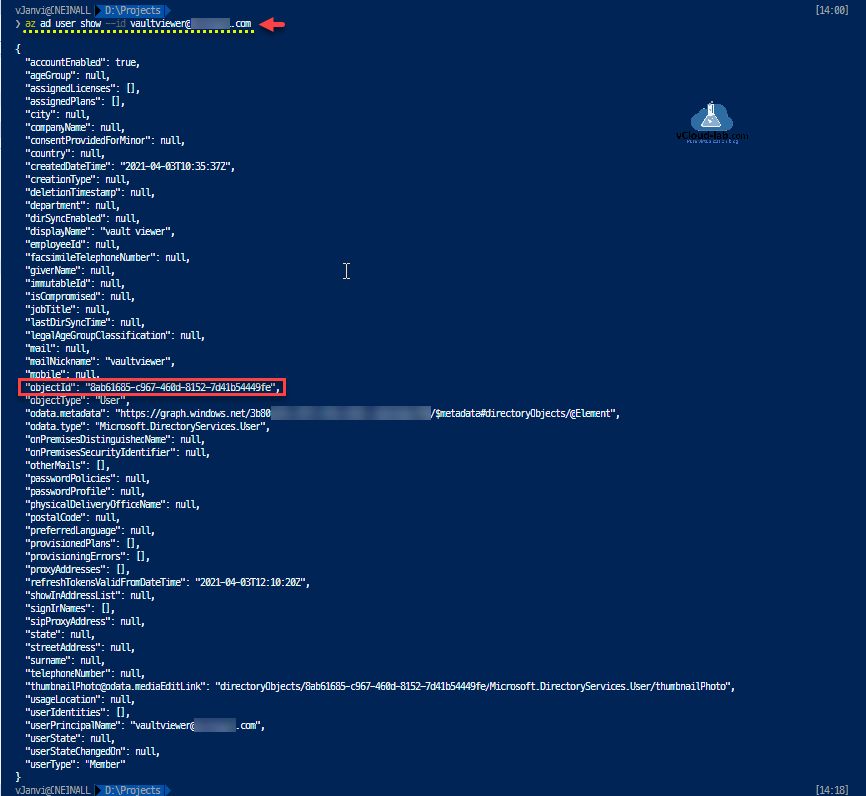
Next get the complete information of AzureAD user whom i will provide Key vault access policy and role, Grab ObjectId from the list.
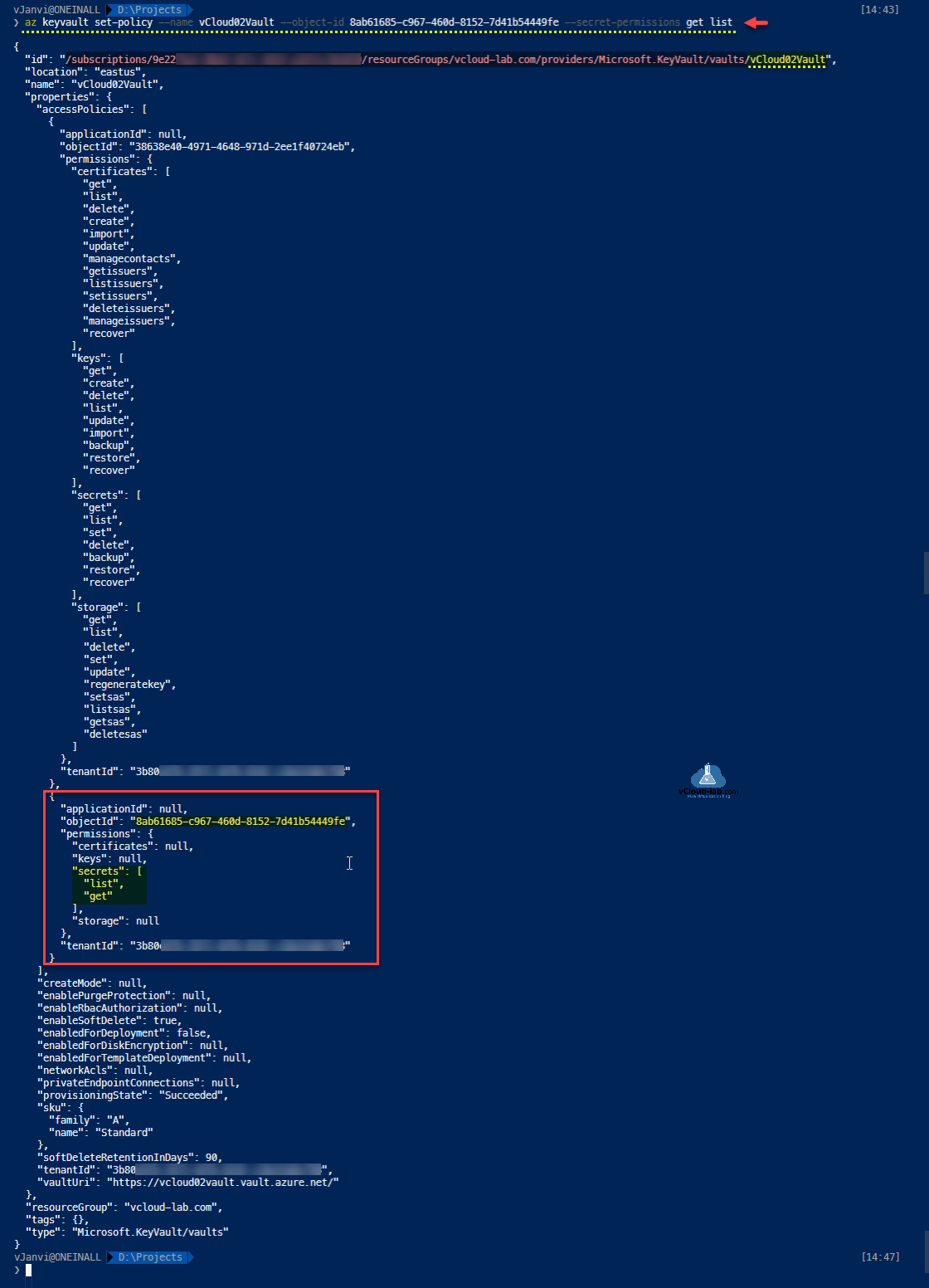
Using the User Object ID and Key vault resource ID (earlier shown in the command) set a secret access policy on the keyvault. In the Json output you can see the newly provided access.
After key vault access policy configuration, configure role ( key vault reader ) assignment access to the user on key vault ID got earlier.
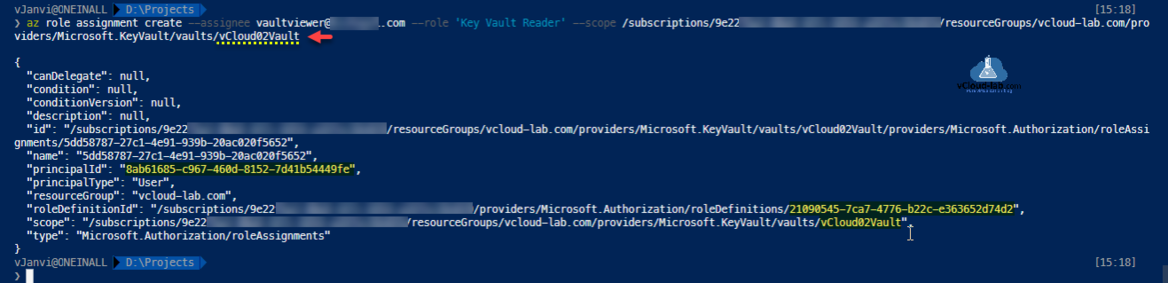
Re login to the azure with vaultviewer account to test if you can access and show/Retrieve secret value from the azure key vault.
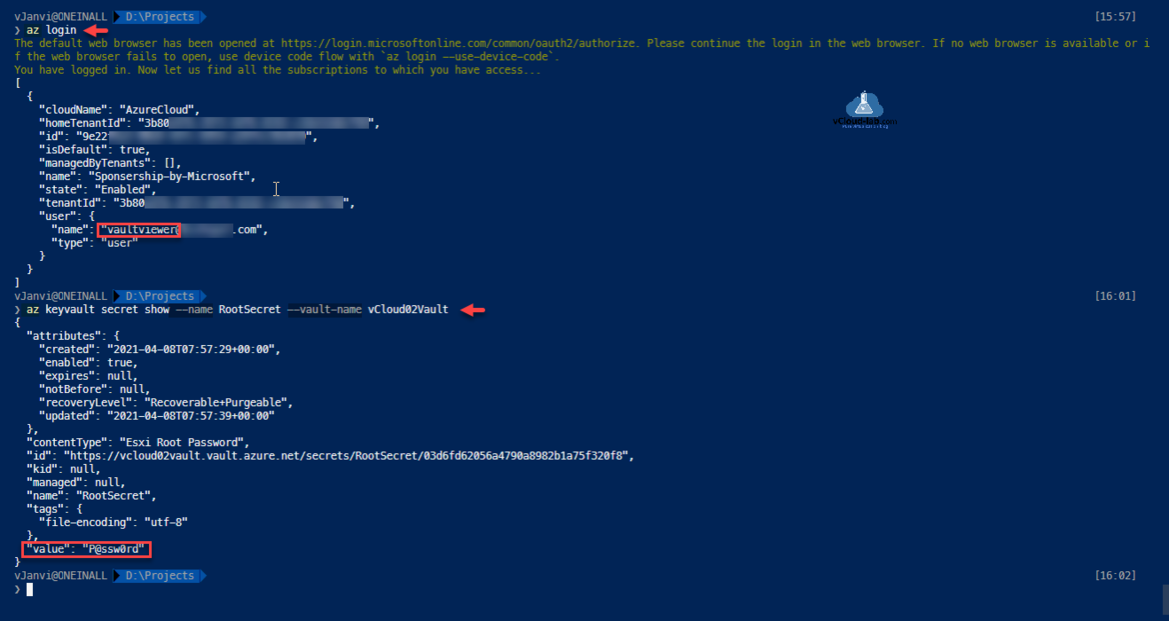
Download this script here or available on github.com .
Useful Articles CREATE NEW NSG (NETWORK SECURITY GROUP - VIRTUAL FIREWALL ACL) ON MICROSOFT AZURE POWERSHELL - EXPORT AZURE NSG (NETWORK SECURITY GROUP) RULES TO EXCEL MICROSOFT AZURE POWERSHELL: CREATING NEW NSG (NETWORK SECURITY GROUP) MICROSOFT AZURE POWERSHELL: CLONING (COPING) OR IMPORTING EXISTING NSG (NETWORK SECURITY GROUP) FROM EXCEL
Blog Search
1 1 5 4 2 2 2 6
Subscribe to our email newsletter & receive updates right in your inbox (550+ Users).
- May 2024 (3)
- April 2024 (5)
- November 2023 (1)
- September 2023 (6)
- July 2023 (15)
- June 2023 (5)
- May 2023 (9)
- April 2023 (4)
- March 2023 (7)
- February 2023 (1)
- January 2023 (1)
- December 2022 (10)
- November 2022 (15)
- October 2022 (15)
- September 2022 (14)
- March 2022 (8)
- December 2021 (9)
- November 2021 (6)
- October 2021 (12)
- September 2021 (10)
- August 2021 (8)
- July 2021 (9)
- June 2021 (9)
- May 2021 (11)
- April 2021 (8)
- March 2021 (13)
- February 2021 (9)
- January 2021 (5)
- November 2020 (7)
- October 2020 (3)
- September 2020 (4)
- August 2020 (7)
- July 2020 (8)
- June 2020 (10)
- May 2020 (10)
- April 2020 (5)
- March 2020 (4)
- February 2020 (3)
- January 2020 (3)
- December 2019 (11)
- November 2019 (2)
- October 2019 (3)
- June 2019 (1)
- May 2019 (5)
- April 2019 (11)
- March 2019 (5)
- February 2019 (2)
- December 2018 (1)
- September 2018 (4)
- July 2018 (3)
- June 2018 (7)
- May 2018 (12)
- April 2018 (9)
- March 2018 (13)
- February 2018 (4)
- January 2018 (10)
- December 2017 (11)
- November 2017 (10)
- October 2017 (11)
- September 2017 (7)
- August 2017 (10)
- July 2017 (12)
- June 2017 (4)
- May 2017 (3)
- February 2017 (1)
- January 2017 (3)
- December 2016 (7)
- November 2016 (8)
- October 2016 (13)
- September 2016 (7)
- August 2016 (9)
- July 2016 (11)
- June 2016 (17)
- May 2016 (7)
- Maas How to install Ansible AWX on Ubuntu using Kubernetes K8S March 9, 2024 02:13AM
- bazs VMware vCenter server vcsa Setting IP IPv6 configuration failed, IP configuration not allowed February 22, 2024 07:48PM
- nilanjan375 PowerShell HTML Server Racks Cabinet Live Diagram maker Demo February 22, 2024 12:36AM
- nilanjan375 PowerShell HTML Server Racks Cabinet Live Diagram maker Demo February 20, 2024 06:13PM
- debby Solved Visual studio Code make sure you configure your user.name and user.email in git February 19, 2024 07:51PM
Disclaimer: All the steps and scripts shown in my posts are tested on non-production servers first. All the scripts provided on my blogs are comes without any warranty, The entire risk and impacts arising out of the use or performance of the sample scripts and documentation remains with you. Author is not liable for any damages whatsoever arising out of the use of or inability to use the sample scripts or documentation. Warning: Everything I say and do in these blogs or videos are subject to mistake and criticism. please do everything in your power to correct me if I saying or doing something wrong, or inform me of what I could be doing better. I am a man made out of my environment, and you are the ones creating who I am. Please don't let me fall to stupidity or ignorance, I expect the absolute best in each and every one of you and I hope you expect the same of me. Thank you. Usage of cookies: In order to optimize the website and for continuous improvement vcloud-lab.com uses cookies. You agree to the usage of cookies when you continue using this site.
© 2016 - 2020 vcloud-lab.com
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications You must be signed in to change notification settings
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement . We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
How do I add "key-vault-contributor" role to a resource group using azure Cli, I don't see it documented #8365
wamak9 commented Jan 28, 2019
Penberthy commented Feb 1, 2019
Sorry, something went wrong.
wamak9 commented Feb 6, 2019
Penberthy commented feb 8, 2019, wamak9 commented feb 11, 2019, penberthy commented feb 11, 2019.
yugangw-msft commented Mar 1, 2019
No branches or pull requests
Assigning Service Principals to Groups and Roles with the Azure CLI
The more I use Azure the more often I find myself needing to assign various managed identities / service principals to various groups and roles, and while that can be done in the Portal, it's cumbersome and I'd prefer to automate it.
So in this post I'll sharing a few Azure CLI commands that should prove useful whenever you're configuring Service Principals.
Getting a service principal's object id
Suppose you know the name of the service principal, but not the "object id", which is required for assigning it to groups and roles. You can use a filter with the az ad sp list command to find that service principal and then a query to pick out just the object id.
Note that you should avoid trying to use the query parameter to find the matching name, as that will likely not find it as it only applies to the first page of results .
Note that the object id is different from the app id. If you do need the app id for any reason you just need to change the query parameter:
Adding to a group
Suppose we want to add the service principal to a group. We need the group id to do that, and if we need to look it up, we can do so with the az ad group list command and using a filter .
Then the az ad group member add command allows us to add the object id of our service principal to the group.
Creating a role assignment
If we want to create a role assignment, then as well as knowing the user we're assigning the role to and the name of the role, we also need to provide a " scope " for that to apply to. This is typically a long / delimited path to an Azure resource. So for a KeyVault it might look like this:
You can of course construct this string yourself, but actually this is quite often just the "ID" of the resource as returned by the Azure CLI. So we could get the above value with the following command:
And now that we have the scope, we can simply use the az role assignment create to assign the role to our service principal, and we can pass the role name directly (in this example it's "Key Vault Administrator"):
Hope this proves useful to you.
Focus on cloud-native and Azure
Authenticate to Azure Resources with Azure Managed Identities

In this post, we will take a look at managed identities in general and system-assigned managed identity in particular. Managed identities can be used by your code to authenticate to Azure AD resources from Azure compute resources that support it, like virtual machines and containers.
But first, let’s look at the other option and why you should avoid it if you can: service principals.
Service Principals
If you have code that needs to authenticate to Azure AD-protected resources such as Azure Key Vault, you can always create a service principal. It’s the option that always works. It has some caveats that will be explained further in this post.
The easiest way to create a service principal is with the single Azure CLI command below:
The command results in the following output:
If the service principal needs access to, let’s say, Azure Key Vault, you could use the following command to grant that access:
The next step is to configure your application to use the service principal and its secret to obtain an Azure AD token (or credential) that can be passed to Azure Key Vault to retrieve secrets or keys. That means you need to find a secure way to store the service principal secret with your application, which is something you want to avoid.
In a Python app, you can use the ClientSecretCredential class and pass your Azure tenant id, the service principal appId (or client Id) and the secret. You can then use the secret with a SecretClient like in the snippet below.
Other languages and frameworks have similar libraries to reach the same result. For instance JavaScript and C# .
This is quite easy to do but again, where do you store the service principal’s secret securely?
The command az ad sp create-for-rbac also creates an App Registration (and Enterprise application) in Azure AD:

The secret (or password) for our service principal is partly displayed above. As you can see, it expires a year from now (blog post written on January 6th, 2023). You will need to update the secret and your application when that time comes, preferably before that. We all know what expiring secrets and certificates give us: an app that’s not working because we forgot to update the secret or certificate!
💡 Note that one year is the default. You can set the number of years with the --years parameter in az ad sp create-for-rbac .
💡 There will always be cases where managed identities are not supported such as connecting 3rd party systems to Azure. However, it should be clear that whenever managed identity is supported, use it to provide your app with the credentials it needs .
In what follows, we will explain managed identities in general, and system-assigned managed identity in particular. Another blog post will discuss user-assigned managed identity.

Managed Identities Explained
Azure Managed Identities allow you to authenticate to Azure resources without the need to store credentials or secrets in your code or configuration files.
There are two types of Managed Identities:
- system-assigned
- user-assigned
System-assigned Managed Identities are tied to a specific Azure resource, such as a virtual machine or Azure Container App. When you enable a system-assigned identity for a resource, Azure creates a corresponding identity in the Azure Active Directory (AD) for that resource, similar to what you have seen above. This identity can be used to authenticate to any service that supports Azure AD authentication. The lifecycle of a system-assigned identity is tied to the lifecycle of the Azure resource. When the resource is deleted, the corresponding identity is also deleted. Via a special token endpoint, your code can request an access token for the resource it wants to access.
User-assigned Managed Identities, on the other hand, are standalone identities that can be associated with one or more Azure resources. This allows you to use the same identity across multiple resources and manage the identity’s lifecycle independently from the resources it is associated with. In your code, you can request an access token via the same special token endpoint. You will have to specify the appId (client Id) of the user-managed identity when you request the token because multiple identities could be assigned to your Azure resource.
In summary, system-assigned Managed Identities are tied to a specific resource and are deleted when the resource is deleted, while user-assigned Managed Identities are standalone identities that can be associated with multiple resources and have a separate lifecycle.
System-assigned managed identity
Virtual machines support system and user-assigned managed identity and make it easy to demonstrate some of the internals.
Let’s create a Linux virtual machine and enable a system-assigned managed identity. You will need an Azure subscription and be logged on with the Azure CLI. I use a Linux virtual machine here to demonstrate how it works with bash. Remember that this also works on Windows VMs and many other Azure resources such as App Services, Container Apps, and more.
Run the code below. Adapt the variables for your environment.
After the creation of the resource group and virtual machine, the portal shows the system assigned managed identity in the virtual machine’s Identity section:

We can now run some code on the virtual machine to obtain an Azure AD token for this identity that allows access to a Key Vault. Key Vault is just an example here.
We will first need to create a Key Vault and a secret. After that we will grant the managed identity access to this Key Vault. Run these commands on your own machine, not the virtual machine you just created:
Now we can grant the system assigned managed identity access to Key Vault via Azure RBAC. Let’s look at the identity with the command below:
This returns the information below. Note that principalId was also visible in the portal as Object (principal) ID. Yes, not confusing at all… 🤷♂️
Now assign the Key Vault Secrets User role to this identity:
If you check the Key Vault in the portal, in IAM, you should see:

Now we can run some code on the VM to obtain an Azure AD token to read the secret from Key Vault. SSH into the virtual machine using its public IP address with ssh azureuser@IPADDRESS . Next, use the commands below:
It might look weird but by sending the curl request to that special IP address on the VM, you actually request an access token to access Key Vault resources (in this case, it could also be another type of resource). There’s more to know about this special IP address and the other services it provides. Check Microsoft Learn for more information.
The result of the curl command is JSON below (nicely formatted with jq):
Note that you did not need any secret to obtain the token. Great!
Now run the following code but first replace <YOUR VAULT NAME> with the short name of your Key Vault:
First, we set the vault URL to the full URL including https:// . Next, we retrieve the full JSON token response but use jq to only grab the access token. The -r option strips the " from the response. Next, we use the Azure Key Vault REST API to read the secret with the access token for authorization. The result should be TOPSECRET ! 😀
Instead of this raw curl code, which is great for understanding how it works under the hood, you can use Microsoft’s identity libraries for many popular languages. For example in Python:
If you are somewhat used to Python, you know you will need to install azure-identity and azure-keyvault-secrets with pip. The DefaultAzureCredential class used in the code automatically works with system managed identity in virtual machines but also other compute such as Azure Container Apps. The capabilities of this class are well explained in the docs: https://learn.microsoft.com/en-us/python/api/overview/azure/identity-readme?view=azure-python . The identity libraries for other languages work similarly.
What about Azure Arc-enabled servers?
Azure Arc-enabled servers also have a managed identity. It is used to update the properties of the Azure Arc resource in the portal. You can grant this identity access to other Azure resources such as Key Vault and then grab the token in a similar way. Similar but not quite identical. The code with curl looks like this (from the docs):
On an Azure Arc-enabled machine that runs on-premises or in other clouds, the special IP address 169.254.169.254 is not available. Instead, the token request is sent to http://localhost:40342 . The call is designed to fail and respond with a Www-Authenticate header that contains the path to a file on the machine (created dynamically). Only specific users and groups on the machine are allowed to read the contents of that file. This step was added for extra security so that not every process can read the contents of this file.
The second command retrieves the contents of the file and uses it for basic authentication purposes in the second curl request. It’s the second curl request that will return the access token.
Note that this works for both Linux and Windows Azure Arc-enabled systems. It is further explained here: https://learn.microsoft.com/en-us/azure/azure-arc/servers/managed-identity-authentication .
In contrast with managed identity on Azure compute, I am not aware of support for Azure Arc in the Microsoft identity libraries. To obtain a token with Python, check the following gist with some sample code: https://gist.github.com/gbaeke/343b14305e468aa433fe90441da0cabd .
The great thing about this is that managed identity can work on servers not in Azure as long if you enable Azure Arc on them! 🎉
In this post, we looked at what managed identities are and zoomed in on system-assigned managed identity. Azure Managed Identities are a secure and convenient way to authenticate to Azure resources without having to store credentials in code or configuration files. Whenever you can, use managed identity instead of service principals. And as you have seen, it even works with compute that’s not in Azure, such as Azure Arc-enabled servers.
Stay tuned for the next post about user-assigned managed identity.
Share this:
Leave a reply cancel reply, discover more from baeke.info.
Subscribe now to keep reading and get access to the full archive.
Type your email…
Continue reading
- Español – América Latina
- Português – Brasil
- GKE Enterprise
- Documentation
- GKE on Azure
Create Azure role assignments
In this section, you grant permissions to GKE on Azure to access Azure APIs.
To save your service principal and subscription IDs to a shell variable, run the following command. Replace APPLICATION_NAME with a name for your application.
Assign permissions to the service principal. GKE on Azure requires permissions to provision required roles for the managed Azure resources at the subscription level.
To create a custom role with required subscription scoped permissions:
Create a new file named RoleAssignmentCreator.json .
Open RoleAssignmentCreator.json in an editor and add the following permissions:
Create the new custom role with the following command:
Assign the role to the service principal using the following command:
When assigning permissions, you can scope them either at the Azure subscription level, which applies to all resources within the subscription, or at the resource group level, which limits permissions to a specific resource group.
Subscription
Assign the Contributor, User Access Administrator, and Key Vault Administrator roles to your subscription:
Resource group
Create Role assignments scoped to the cluster resource group. Replace CLUSTER_RESOURCE_GROUP_NAME with the name of the resource group for your GKE on Azure.
If your Azure Virtual Network is in a different resource group, create Role assignments scoped to the virtual network resource group.
Replace the following:
- VNET_RESOURCE_GROUP_NAME : the name for the resource group for your GKE on Azure VNet
What's next
- Create a client certificate
Except as otherwise noted, the content of this page is licensed under the Creative Commons Attribution 4.0 License , and code samples are licensed under the Apache 2.0 License . For details, see the Google Developers Site Policies . Java is a registered trademark of Oracle and/or its affiliates.
Last updated 2024-06-03 UTC.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Create key vault, managed identity, and role assignment
- Code Sample
- 2 contributors
This template creates a key vault and managed identity, and a role assignment for the managed identity to access the key vault.
For more information about using Bicep to deploy key vaults, see Manage secrets by using Bicep , and for information about using Bicep to deploy role assignments, see Create Azure RBAC resources by using Bicep .
Deletion behavior
When a managed identity is deleted, any role assignments for that managed identity are not automatically deleted. If you try to deploy a new role assignment with the same role assignment ID, the deployment fails because the resource already exists and the principalId can't be modified.
To ensure that each deployment has a unique role assignment ID, you can use the guid() function with a seed value that is based in part on the managed identity's principal ID. However, because Azure Resource Manager requires each resource's name to be available at the beginning of the deployment, you can't use this approach in the same Bicep file that defines the managed identity. This sample uses a Bicep module to work around this issue.
Tags: Microsoft.KeyVault/vaults, Microsoft.ManagedIdentity/userAssignedIdentities, Microsoft.Resources/deployments, Microsoft.Authorization/roleAssignments
Azure Key Vault Secrets configuration provider for Microsoft.Extensions.Configuration
The Azure.Extensions.AspNetCore.Configuration.Secrets package allows storing configuration values using Azure Key Vault Secrets.
Getting started
Install the package.
Install the package with NuGet :
Prerequisites
You need an Azure subscription and Azure Key Vault to use this package.
To create a new Key Vault, you can use the Azure Portal , Azure PowerShell , or the Azure CLI . Here's an example using the Azure CLI:
Azure role-based access control
When using azure role-based access control , the identity you are authenticating has to have the "Key Vault Reader" and "Key Vault Secrets User" roles. The "Key Vault Reader" role allows the extension to list secrets while the "Key Vault Secrets User" allows retrieving their values.
Key concepts
Thread safety.
We guarantee that all client instance methods are thread-safe and independent of each other ( guideline ). This ensures that the recommendation of reusing client instances is always safe, even across threads.
Additional concepts
Client options | Accessing the response | Long-running operations | Handling failures | Diagnostics | Mocking | Client lifetime
To load initialize configuration from Azure Key Vault secrets call the AddAzureKeyVault on ConfigurationBuilder :
The Azure Identity library provides easy Azure Active Directory support for authentication.
Read more about configuration in ASP.NET Core .
Contributing
This project welcomes contributions and suggestions. Most contributions require you to agree to a Contributor License Agreement (CLA) declaring that you have the right to, and actually do, grant us the rights to use your contribution. For details, visit cla.microsoft.com .
This project has adopted the Microsoft Open Source Code of Conduct . For more information see the Code of Conduct FAQ or contact [email protected] with any additional questions or comments.


IMAGES
VIDEO
COMMENTS
Name Description Type Status; az keyvault role assignment create: Create a new role assignment for a user, group, or service principal. Core GA az keyvault role assignment delete
To create a role assignment using the Azure CLI, use the az role assignment command: az role assignment create --role {role-name-or-id} --assignee {assignee-upn}> --scope {scope} For full details, see Assign Azure roles using Azure CLI. To create a role assignment using Azure PowerShell, use the New-AzRoleAssignment cmdlet:
az keyvault role assignment: Manage role assignments. Core GA az keyvault role assignment create: Create a new role assignment for a user, group, or service principal. Core ... Examples. Create a key vault with network ACLs specified (use --network-acls to specify IP and VNet rules by using a JSON string).
PowerShell Az module example ... az keyvault create --name vCloud02Vault --resource-group vcloud-lab.com --location 'East US' --sku Standard ... After key vault access policy configuration, configure role (key vault reader) assignment access to the user on key vault ID got earlier.
Use az keyvault role assignment create command to assign a Managed HSM Crypto User role to user identified by user principal name [email protected] for a specific key named myrsakey. ... definition create command to a role from a file named my-custom-role-definition.json containing the JSON string for a role definition. See example above.
Now let's assign a role to a service principal. To do this we'll need a role definition Id and a service principal object Id. A role definition Id can be obtained from the Id property of one of the role definitions returned from GetRoleAssignments.. See the README for links and instructions on how to generate a new service principal and obtain it's object Id.
Azure role-based access control (Azure RBAC) is an authorization system built on Azure Resource Manager that provides centralized access management of Azure resources. Azure RBAC allows users to manage Key, Secrets, and Certificates permissions. It provides one place to manage all permissions across all key vaults.
Azure Key Vaults are essential components for storing sensitive information such as passwords, certificates, and secrets of any kind. Because the data stored in Key Vaults is sensitive, only authorized users or applications should be able to access them. At that point, we have two options to manage access control: traditional vault access policies and new role-based access control (RBAC).
The ARM template should assign the "Key Vault Secrets User" role to the Service Principle (on the new Key Vault) so that... The YAML pipeline (Service Principle) can gain access to the new secrets; Am I right in thinking that during creation of a Key Vault - the ARM template has full access to it, and can therefore assign these RBAC roles?
Step 1: Determine who needs access. You can assign a role to a user, group, service principal, or managed identity. To assign a role, you might need to specify the unique ID of the object. The ID has the format: 11111111-1111-1111-1111-111111111111. You can get the ID using the Azure portal or Azure CLI. User.
@Penberthy-- thanks for the info. az keyvault worked out but problem is, some of the teams cannot access the resource group at all because they are not contributors. but manually adding the azure ad group to the resource group with key-vault-contributor is working.teams can access the keyvault from the portal and through az cli.. Let me do some research and see if there is any documentation to ...
Adding to a group. Suppose we want to add the service principal to a group. We need the group id to do that, and if we need to look it up, we can do so with the az ad group list command and using a filter. --query "[].id" -o tsv. Then the az ad group member add command allows us to add the object id of our service principal to the group.
If you want Azure Key Vault to create a software-protected key for you, use the az key create command. Azure CLI. Copy. az keyvault key create --vault-name "ContosoKeyVault" --name "ContosoFirstKey" --protection software. If you have an existing key in a .pem file, you can upload it to Azure Key Vault.
To see the existing rotation policy for a key, use the following command: az keyvault key rotation-policy show \. --vault-name "kv-name" \. --name "key-name". To update the current rotation policy, you'll have options. Within the Azure Portal, enable the Enable auto rotation option, then set the rotation timespan.
Key Vault is just an example here. We will first need to create a Key Vault and a secret. After that we will grant the managed identity access to this Key Vault. ... az keyvault create--name $ KVNAME--resource-group $ RG # with full access, current user can create a secret. ... az role assignment create--assignee $ PRI _ ID \
Create Azure role assignments. In this section, you grant permissions to GKE on Azure to access Azure APIs. To save your service principal and subscription IDs to a shell variable, run the following command.
Azure KeyVault Administration client library for .NET. Azure Key Vault Managed HSM is a fully-managed, highly-available, single-tenant, standards-compliant cloud service that enables you to safeguard cryptographic keys for your cloud applications using FIPS 140-2 Level 3 validated HSMs. The Azure Key Vault administration library clients support ...
the HSM. Add your private key to the keyvault, which returns the URI you need for Step 4: $ az keyvault key import --hsm-name "KeylessHSM" --name "hsm-pub-keyless" --pem-file server.key. If the key server is running in an Azure VM in the same account, use Managed services for authorization: Enable managed services on the VM in the UI.
Create key vault, managed identity, and role assignment. Code Sample. 07/06/2022. 2 contributors. Browse code. This template creates a key vault and managed identity, and a role assignment for the managed identity to access the key vault. For more information about using Bicep to deploy key vaults, see Manage secrets by using Bicep, and for ...
To create a new Key Vault, you can use the Azure Portal, Azure PowerShell, or the Azure CLI. Here's an example using the Azure CLI: az keyvault create --name MyVault --resource-group MyResourceGroup --location westus az keyvault secret set --vault-name MyVault --name MySecret --value "hVFkk965BuUv" Azure role-based access control
If you are creating the Key vault with RBAC role from scratch then Please assign Key vault Administrator to your name for creating/ managing the secrets, certificates and keys. Steps: Go to your Key vault after its created and then click on Access Control (IAM): Then click on Add Role assignment and then add Key vault Administrator Role to your ...