- Fundamentals

Data Leakage
Learn how data can "leak" off a network and ways to prevent it.
Topic Overview
What is Data Leakage?
How does data leakage occur , what are the effects of data leaks , types of data leakage, how to prevent data leakage, the 2024 attack intelligence report.
New research from Rapid7 Labs analyzes 14 months of attacker behavior and marquee vulnerabilities.
Data leakage is the occurrence of an organization inadvertently exposing sensitive information – usually due to a mistake like overlooking a critical vulnerability – to the public internet or unsecure networks. This process increases the chances that data will be taken by malicious actors.
In a worst-case scenario, data “leaks” off of the originating secure network and into the hands of bad actors who will hold the sensitive data for ransom or leak it wider onto more visible platforms and websites.
Data Leaks vs. Data Breach: What's the Difference?
The National Institute of Standards and Technology (NIST) defines a breach as:
"The loss of control, compromise, unauthorized disclosure, unauthorized acquisition, or any similar occurrence where: a person other than an authorized user accesses or potentially accesses personally identifiable information; or an authorized user accesses personally identifiable information for anything other than the authorized purpose.”
Simply put, a data breach is when data is knowingly accessed in an unauthorized manner. A data leak is when an authorized user mistakenly exposes data to the internet or unauthorized networks, but it technically hasn’t been stolen – yet.
The difference between these two terms is small but important when taking actions to secure the data in question or when reporting on the incident later.
Data leakage occurs as a result of a number of mistakes or oversights – or something that no one in an organization would ever have thought of. Let’s take a look at a few ways data leakage can occur:
- Human error : Way back in 2012, we said that there were a staggering number of cases involving human error that were leading to unprecedented governmental challenges in securing critical infrastructures, intellectual property, economic data, employee records, and other sensitive information. 12 years later, this still holds true.
- Legacy or outdated data : Keeping archived data can have benefits, but more often this type of outdated information is becoming a significant vulnerability/liability to businesses around the world. However this legacy data is secured, eventually there will be a crack in its armor and that data will be exposed. Whether or not malicious actors pick up on the fact that this information is there for the taking or not is another question besides the critical one: Is it absolutely necessary to keep this old data around?
- Poor password hygiene : If IT and security organizations do not implement sophisticated identity and access management (IAM) solutions to consistently update – and generate – new passwords, then odds are it’s only a matter of time before something like a credential stuffing attack occurs and the bad actors are exfiltrating data.
- Vulnerabilities : It happens every day, everywhere: a vulnerability goes overlooked or undiscovered in the software development lifecycle (SDLC) and attackers are taking advantage in the blink of an eye. Depending on the size of a business or DevOps organization, with limited resources it simply may not be possible to catch everything.
The effects of data leaks can be disastrous. But, like with anything in security, so much of the process is about timing. If analysts are able to catch the cause of data leaks early, the overall business may be lucky enough to entirely avoid any negative fallout. Or it may be able to minimize the damage. Or it may have to deal with business- or reputation-altering repercussions.
Damage to Reputation
Waiting until something happens shouldn’t be the priority; it should be planning in case of the event. Damage to reputation is something that can and should be scoped prior to the occurrence of any significant future event. That way, a business and its IT and security organizations will have a playbook to follow in such a situation. This will help minimize lasting negative reputational impact.
Damage to Finances
Following on from possible large-scale reputational damage, there is a two-pronged effect when it comes to a business’ bottom line: potential ransomware payments to threat actors as well as customers taking their business elsewhere. Businesses could quickly find themselves bankrupt or extinct if they aren’t prepared for the consequences of unintended data leakage.
Damage to Operations
The amount of time it takes for an organization to return to normal operations will depend on the severity of the security event following a data leak and in-progress initiatives that may have to be fully halted in an “all hands on deck” type data security event. This can cause incredible disruption to a business and create an operational deficit from which it could be near-impossible to return.
Damage to Talent Acquisition
The current cybersecurity talent shortage and skills gap only seems to continue to exacerbate as more managed security service providers (MSSPs) are called upon to provide monitoring, detection, and response actions on behalf of clients. Hiring skilled in-house talent can already be a laborious enterprise. Following a breach that causes catastrophic reputational damage? Not likely.
While there are obviously certain data types that are of higher value to threat actors – personally identifiable information (PII), financial- and health-related, etc. – what are some of the main vectors by which data leakage occurs? We’ve covered some of the various functionalities, but let’s now group them by type.
Human Error
Whether it was initiated by an internal source or perhaps a supply chain partner, to be classified as human error in this sense the act/disclosure/exposure must be unintentional. The root cause of this data exposure or leak might have begun as a misconfiguration during the SDLC and turned into a gaping vulnerability through which high-value data was exposed.
The inciting incident could also be something much less technical. Leaving workstations unattended and accessible while working remotely and lost devices are two such examples of mishaps that occur every day and lead to unintended negative consequences.
Attacker-initiated
For the purposes of this page, we are mainly discussing data leakage in a scenario whereby an internal actor – employee, visitor, contractor, vendor, etc. – would unknowingly leave data unprotected or exposed to potential theft or ransom.
However, if an exposure is leveraged by attackers to more easily steal potentially sensitive data, then this type of leak would be attacker initiated. The responsibility for the exposure, though, still lies with the person or people who were initially tasked with securing the data. But if a door is left open, we can all reasonably assume there aren’t many attackers who wouldn’t throw it wide open and steal sensitive data.
It's entirely possible to effectively prevent sensitive enterprise-level data from being exposed and subsequently leaking onto the public internet or into the data stores of malicious actors.
Whether one of the following preventive options are used as a standalone solution or part of a larger product suite, each organization should keep their unique needs and goals in mind when researching which solution/product is best for their environment.
- Institute a data loss prevention (DLP) solution : DLP solutions typically focus on the endpoint, network, and cloud. This functionality specifically addresses the issues we’ve discussed at length here, such as vulnerabilities as a result of misconfiguration and accidental exposure.
- Leverage encryption : Data encryption protects data from unauthorized use or access by using a “key” to encrypt a message on one end of a transmission and using the same key to decrypt it on the other end. With this process, even if malicious actors are able to successfully exfiltrate data, there is a good chance it will be of no use to them if strong encryption protocols are used. Increasingly, machine learning and AI are being used to create more sophisticated encryption techniques.
- Shift left : Ensuring security processes are part of the SDLC – and thereby a true DevSecOps workflow – can vastly cut down on the amount of vulnerabilities that go out the door at the end of the build cycle. By integrating security checks into Infrastructure as Code (IaC) templates and other parts of the coding process, DevSecOps organizations reduce the chances of a critical data leak.
- Train employees and partners : Engaging employee workforces in security awareness training that covers topics like basic password and authentication best practices can go a long way toward warding off a leak if, for instance, a device is lost or passwords are reused over a long period of time.
Related Topics
Data loss prevention (dlp), data encryption, data security, network access control (nac).

Preventing and Detecting Data Leaks: The Complete Guide

- April 28, 2023
- Reading time: 5 min

Data leaks have become a growing concern for businesses, governments, and individuals in today’s hyper-connected digital world. In this article, we cover the proven strategies and best practices of data leakage prevention.
Understanding Data Leaks
Before diving into prevention and detection methods, it is crucial to understand what data leaks are, their potential impact, and the common causes behind them.
Definition and types of data leaks
A data leak occurs when sensitive, confidential, or protected information is inadvertently or intentionally disclosed to unauthorized individuals. Data leaks can take various forms, such as:
- Accidental sharing of sensitive information by employees
- Misconfiguration of cloud storage or databases, leading to public exposure
- Insider threats, where a malicious employee or contractor steals or discloses data
- Cyberattacks, where external threat actors breach a system and exfiltrate data
The impact of data leaks on organizations
Data leaks can have severe consequences for organizations, including:
- Financial losses due to fines, lawsuits, and remediation costs
- Reputational damage, leading to a loss of customers, partners, and investors
- Loss of intellectual property and trade secrets
- Legal and regulatory penalties for non-compliance with data protection laws
Common causes of data leaks
Understanding the root causes of data leaks is essential for implementing effective prevention measures. Some of the most common causes include:
- Human error : Employees can unintentionally share sensitive information through email or other communication channels, misplace devices containing sensitive data, or fall victim to social engineering attacks.
- Weak security controls: Inadequate access controls, unencrypted data, and outdated software can leave organizations vulnerable to data leaks. Lack of best security practices for tools such as GitHub can result in leaked secrets .
- Third-party risks: Vendors or partners with weak security practices can expose an organization’s data to leaks.
- Insider threats : Disgruntled or malicious employees may intentionally steal or disclose sensitive data.
- Cyberattacks: Advanced persistent threats (APTs), ransomware, and other cyber threats can lead to data leaks if an organization’s defenses are breached.
Implementing Strong Security Policies to Prevent Data Leaks
Developing and enforcing robust security policies are essential in creating a secure environment to prevent and detect data leaks. This section outlines the key components of an effective security policy.
Employee awareness and training
Human error is a leading cause of data leaks, making it vital to educate employees about the importance of data security. Implement a comprehensive training program that covers topics such as handling sensitive data, identifying phishing attacks, and following proper password hygiene. Regularly update and reinforce this training to keep employees informed about the latest threats and best practices.
Access controls and least privilege principle
Restrict access to sensitive data by implementing role-based access control (RBAC) and the principle of least privilege. This ensures that employees only have access to the information necessary to perform their job functions. Regularly review and update access permissions to maintain a secure environment.
Password management and multi-factor authentication (MFA)
Enforce strong password policies, requiring employees to use complex, unique passwords for each account. Encourage or mandate the use of password managers to help employees securely store and manage their credentials. Implement multi-factor authentication (MFA) for an additional layer of security, especially for remote access and privileged accounts.
Data Classification and Encryption: A Hidden Key to Data Leak Prevention
Proper data classification and encryption can significantly reduce the risk of data leaks by ensuring that sensitive information is adequately protected.
Identifying and classifying sensitive data
Begin by identifying the types of data your organization handles, such as personal information, financial records, intellectual property, and trade secrets. Once identified, classify the data based on its sensitivity and the potential impact if leaked. Establish clear guidelines and processes for handling each data classification level, and ensure that employees understand their responsibilities.
Implementing data encryption at rest and in transit
Encrypt sensitive data both at rest (e.g., stored on hard drives, servers, or cloud storage) and in transit (e.g., transmitted over networks or between systems). This ensures that even if unauthorized individuals gain access to the data, they cannot read or use it without the decryption keys. Use industry-standard encryption algorithms such as AES-256 for optimal protection.
Key management best practices
Proper key management is crucial for maintaining the effectiveness of encryption. Implement the following best practices for managing encryption keys:
- Store encryption keys separately from the encrypted data
- Limit access to encryption keys to a small group of trusted employees or systems
- Use hardware security modules (HSMs) or key management services (KMS) to protect and manage keys
- Regularly rotate encryption keys to minimize the impact of potential key compromises
- Implement procedures for securely generating, storing, and retiring encryption keys
Endpoint Security and Mobile Device Management for Preventing Data Leaks
Securing endpoints and managing mobile devices is critical for preventing unauthorized access to sensitive data and minimizing the risk of data leaks.
Antivirus and anti-malware software
Install reputable antivirus and anti-malware software on all endpoints, including servers, desktops, and laptops. Regularly update these programs to ensure they can effectively detect and mitigate the latest threats.
Patch management and software updates
Keep operating systems, applications, and firmware up-to-date by regularly applying security patches and updates. Implement a patch management process to track, test, and deploy updates in a timely manner, prioritizing critical security patches.
Implementing mobile device management (MDM) solutions
With the increasing use of mobile devices for work purposes, it’s essential to have a robust mobile device management (MDM) solution in place. MDM solutions help enforce security policies, remotely wipe lost or stolen devices, and monitor for potential threats. Additionally, consider implementing containerization or app sandboxing to separate personal and work-related data on mobile devices.
Incident Response and Data Leak Detection
Being prepared for data leaks and having a plan in place to respond to incidents can significantly minimize their impact.
Building an effective incident response team
Assemble a cross-functional incident response team that includes members from IT, legal, public relations, and other relevant departments. Develop a clear incident response plan that outlines roles, responsibilities, and procedures to follow in the event of a data leak.
Implementing data loss prevention (DLP) solutions
Deploy data leakage prevention (DLP) tools to monitor, detect, and block unauthorized access, transmission, or exfiltration of sensitive data. DLP solutions can be implemented at various points, including endpoints, networks, and cloud storage.
Regular auditing and penetration testing
Conduct regular security audits to identify and address vulnerabilities in your organization’s security posture. Additionally, perform penetration testing to simulate real-world attacks and assess the effectiveness of your security controls.
Data Leak Prevention and Detection
Preventing and detecting data leaks is a continuous process that requires vigilance and adaptation to the evolving threat landscape. By implementing strong security policies, data classification and encryption, network security, endpoint and mobile device management, incident response, and adhering to legal and regulatory requirements, organizations can significantly reduce their risk of data leaks and minimize the impact of potential incidents. Stay proactive and up-to-date with the latest best practices to ensure the safety of your organization’s sensitive information.
Detect Leaks with Flare
Flare monitors the clear & dark web so you can find data leaks immediately, before threat actors do. Our comprehensive Threat Exposure Management (TEM) capabilities protect your organization’s sensitive information.
Sign up for Flare’s free trial to see how we can detect leaks for your organization.

“What used to take about 1500 hours to complete can now be done in 1 week. Flare allows me to empower junior analysts to do dark web investigations that were previously impossible, hence liberating bandwidth. “
Senior Security Specialist at a MSSP
“Other solutions would present us with thousands of potential leaks which were impossible to work with for our small team, Flare was the only one that could successfully filter and prioritize data leaks with their 5-point scoring system.”
CTI Director at a Major North American Bank
“Flare enables us to react quickly when threats are publicized. It helps us protect our brand and financial resources from data breaches.”
CISO in a Major North American Bank
“We audited dozens of different solutions and Flare was the only one making CTI easy and understandable for all , with the right data.”
Senior Advisor at an IT Services Industry
Start your free trial today
Experience Flare for yourself and see why Flare is used by organization’s including federal law enforcement, Fortune 50, financial institutions, and software startups.
- Office: 1-833.685.3527
- Sales: 1- 833.486.3527
- Product Overview
- Flare Live Status
- Integrations
- By Use Case
- Dark Web Monitoring
- External Attack Surface Management
- Data Leak Monitoring
- Cyber Reconnaissance
- By Industry
- Financial Services
- Security Teams
- Customer Success Stories
- Company Overview
- Resource Center
- Webinars & Events
- Technical Blog
- Github Community
- Privacy Policy
- Terms of Service

- Security Operations
- Security Executives
- Threat Intelligence
- Advisory Board
- Threat Spotlight
- Partner Login
- Find a Partner
- Become a Partner
- Global Partner Program
- Technology Partners
- Find a Distributor
- Support Login
- Professional Services
- Work With Us
- Forcepoint Trust Hub
You are here

What is Data Leakage?

- Data Leakage Defined
Data leakage is the unauthorized transmission of data from within an organization to an external destination or recipient. The term can be used to describe data that is transferred electronically or physically. Data leakage threats usually occur via the web and email, but can also occur via mobile data storage devices such as optical media, USB keys, and laptops.
Barely a day goes by without a confidential data breach hitting the headlines. Data leakage, also known as low and slow data theft, is a huge problem for data security , and the damage caused to any organization, regardless of size or industry, can be serious. From declining revenue to a tarnished reputation or massive financial penalties to crippling lawsuits, this is a threat that any organization will want to protect themselves from.
Unify Cloud, Endpoint and BYOD Data Protection
- Types of Data Leakage
There are many different types of data leakage and it is important to understand that the problem can be initiated via an external or internal source. Protective measures need to address all areas to ensure that the most common data leakage threats are prevented.
The Accidental Breach
"Unauthorized" data leakage does not necessarily mean intended or malicious. The good news is that the majority of data leakage incidents are accidental. For example, an employee may unintentionally choose the wrong recipient when sending an email containing confidential data. Unfortunately, unintentional data leakage can still result in the same penalties and reputational damage as they do not mitigate legal responsibilities.
The Disgruntled or Ill-Intentioned Employee
When we think of data leakages, we think about data held on stolen or misplaced laptops or data that is leaked over email. However, the vast majority of data loss does not occur over an electronic medium; it occurs via printers, cameras, photocopiers, removable USB drives and even dumpster diving for discarded documents. While an employee may have signed an employment contract that effectively signifies trust between employer and employee, there is nothing to stop them from later leaking confidential information out of the building if they are disgruntled or promised a hefty payout by cybercriminals. This type of data leakage is often refered to as data exfiltration
Electronic Communications with Malicious Intent
Many organizations give employees access to the internet, email, and instant messaging as part of their role. The problem is that all of these mediums are capable of file transfer or accessing external sources over the internet. Malware is often used to target these mediums and with a high success rate. For example, a cybercriminal could quite easily spoof a legitimate business email account and request sensitive information to be sent to them. The user would unwittingly send the information, which could contain financial data or sensitive pricing information.
Phishing attacks are another cyber attack method with a high data leakage success rate. Simply by clicking on a link and visiting a web page that contains malicious code could allow an attacker to access a computer or network to retrieve the information they need.
- Data Leakage Prevention
The threat is real, and real threats need serious data leakage prevention. Data loss prevention (DLP) is a strategy that ensures end users do not send confidential or sensitive information outside of the enterprise network. These strategies may involve a combination of user and security policies and security tools.
DLP software solutions allow administrators to set business rules that classify confidential and sensitive information so that it cannot be disclosed maliciously or accidentally by unauthorized end users. Forcepoint's DLP solution allows you to discover and control all sensitive data easily and identify your riskiest users within seconds. Whether you need to apply controls to source code, engineering drawings, financial data or sensitive trade secrets, our solution gives you granular control over the data that matters without affecting productivity and progress.
Report Gartner®️: 2023 Market Guide for Data Loss Prevention
Report 2023 Radicati Data Loss Prevention Market Quadrant
Whitepaper The Practical Executive's Guide to Hospital Data Loss Prevention
In This Doc:
The forrester wave™: data security platforms, q1 2023, more from cyber edu.

What is Data Security Posture Management? DSPM Meaning

Cloud Data Protection Importance, Benefits and Solutions

What Is SASE Technology?
BreachSight
Vendor risk, trust exchange, product features, vendor risk assessments, security questionnaires.
- Security Ratings
Data Leaks Detection
- Integrations
AI Autofill
- Financial Services
eBooks, Reports, & more
8 data leak prevention strategies in 2024.

Edward Kost
Data leak prevention is a cybersecurity practice that involves implementing secure data practices to reduce accidental exposure. Effective data leak prevention plays a crucial role in a comprehensive data loss prevention strategy (DLP strategy ).
Data leaks are an easy attack vector for cybercriminals. Exposed data, such as leaked credentials, allows unauthorized access to an organization's systems. This direct access enables hackers to carry out a range of cyber attacks with less effort, such as:
- Ransomware and other types of malware injections
- Social engineering , including phishing
- Data exfiltration / data theft
What is a Data Leak?
A data leak is an overlooked exposure of sensitive data , either electronically or physically. Data leaks could occur internally or via physical devices such as external hard drives or laptops. If a cybercriminal locates a data leak, they can use the information to arm themselves for a data breach attack.
When sensitive data is stolen from either a data breach or a ransomware attack and published on the dark web, these events are also classified as data leaks.
The Difference Between Data Leaks and Data Breaches
A data leak is the accidental exposure of sensitive information. These events are not initiated by an external impetus. They're caused by vulnerabilities in the security controls protecting confidential data. Data leaks can also be caused by cybercriminals publishing stolen data on their official dark web noticeboards, also known as ransomware blogs.

A data breach , on the other hand, is the outcome of a planned cyberattack. These events are initiated by an external impetus. Before sensitive data can be detected and exfiltrated, cybercriminals must overcome a series of data security measures securing the cyber kill chain.

Learn how to prevent data breaches >
Data loss is another term commonly associated with data leaks. Data loss is the irreversible loss of sensitive data, either by accidental deletion or theft.
These events can be mitigated with Data Loss Prevention (DLP) strategies that prevent data transfer beyond specified boundaries. However, a DLP strategy alone will not prevent data leaks ; its focus is too narrow.
Data leak prevention efforts need to consider all of the processes that have a direct and indirect impact on sensitive data protection . This effort even stretches as far back as the coding practices that develop a solution .

Learn more about the differences between data leaks, data breaches, and data loss >
Why is Data Leakage Prevention Important?
Leaked data is a treasured find for a cybercriminal. These events significantly reduce the effort of cybercrime by removing all of the laborious stages preceding data compromised in the cyber kill chain .
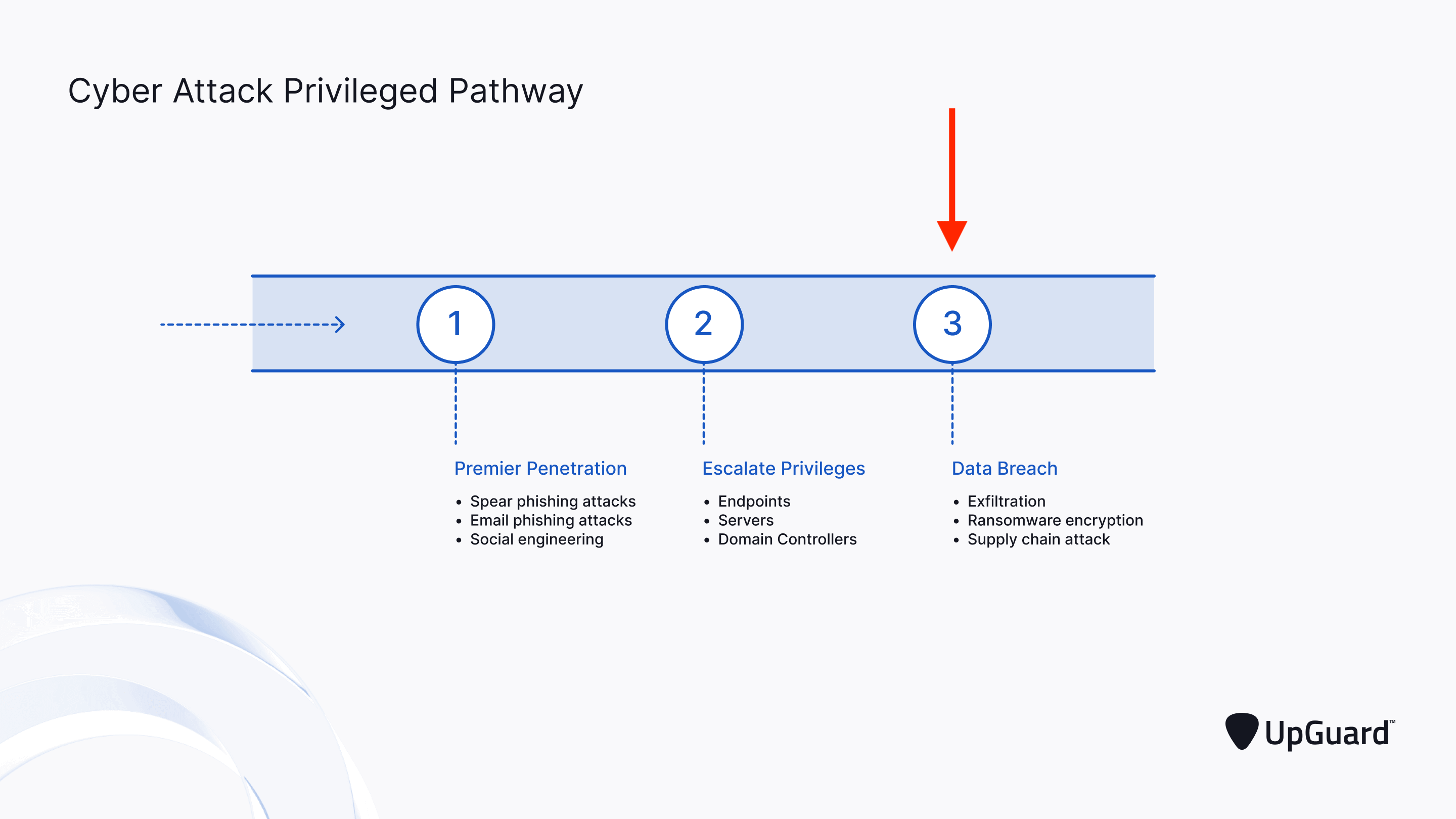
Because they make life so much easier for cybercriminals, data leak finds are becoming a primary focus in the world of cybercrime. Meeting this performance metric is relatively easy, given the growing prevalence of data leaks.
A 2021 UpGuard study revealed that half of analyzed Fortune 500 companies were leaking data useful for cybercriminal reconnaissance in their public documents.
Also, in 2021, UpGuard researchers discovered that at least 47 organizations were unknowingly leaking data through a misconfiguration in Microsoft's PowerApp solutions - an oversight resulting in the exposure of tens of millions of private records.
Many organizations unknowingly leak sensitive data sets, potentially exposing trade secrets, Personal Identifiable Information (PII), and even credit card data.
The normalization of data breach prevention efforts will likely positively impact all other cybersecurity sectors . The degree of sensitive data exposure is proportional to the success of data breaches and phishing attacks . Both events could, therefore, be reduced if data leaks are remediated before cybercriminals discover them.
What Causes Data Leaks?
Data leaks occur when sensitive data is accidentally exposed publicly, either physically or digitally. Common causes of data leaks include:
- Misconfigured software settings
- Social engineering
- Recycled or weak passwords
- Physical theft/loss of sensitive devices
- Software vulnerabilities
- Insider threats
Learn more about the common causes of data leaks >
Examples of Data Leaks
The holy grail of sensitive information exposure is Personally Identifiable Information (PII), including names, contact information, financial details, and other personal data. Other less potent forms of data leaks can be used for reconnaissance missions to uncover internal secrets.
There are four major categories of data leaks - customer information, company information, trade secrets, and analytics.
1. Customer Information
Some of the biggest data breaches included customer data leaks that involved Personal Identifiable information. Customer data is unique to each company. Customer confidential information could include any of the following:
- Customer names
- Phone number
- Email addresses
- Social Security numbers
- Payments histories
- Product browsing habits
- Credit Card numbers
2. Company Information
Leaked company information exposes sensitive internal activity. Such data leaks tend to be in the crosshairs of unscrupulous businesses pursuing the marketing plans of their competitors.
Company data leaks could include the following:
- Internal communications
- Performance metrics
- Marketing strategies
3. Trade Secrets
This is the most dangerous form of data leak to a business. Intellectual property theft destroys a business's growth potential, running it to the ground.
Trade secret leakage could include the following types of data:
- Upcoming product plans
- Software coding
- Proprietary technology information
4. Analytics
Large data sets feed analytics dashboards, and cybercriminals are drawn to any sizable pool of data. Analytics software is, therefore, an attack vector that needs to be monitored .
Analytics data leaks could include the following:
- Customer behavior data
- Psychographic data
- Modeled data
Common Host of Data Leak Dumps
There has been enough data breach intelligence analyzed to paint a picture of common cybercriminal behavior. Thanks to this data, we can now deploy security controls along each stage of the cyberattack lifecycle.
Data breach post-mortem analysis has also unveiled common cybercriminal behavior beyond a successful breach. After exploiting leaked data, the next stop for cybercriminals is usually dark web forums, where they either put it up for sale or publish it freely.
Such forums need to be continuously monitored in a data leak detection strategy.
Data leaks could still offer helpful reconnaissance information while in the process of being sold. Dark web marketplace listings often include a sample of compromised data to prove the authenticity of the event.
By cross-referencing the sample information against your third-party vendor list and a database of known breaches, such as Have I Been Pwnd , the source of the leak could be identified.
The following popular dark web forums should be monitored for data leaks:
- Crackingking
- evilzone.org
Learn how to reduce data leak false positives >
Ransomware Blog Data Leaks
Another common cause of data leaks is data dumps from ransomware attacks. Hackers publish data stolen from ransomware attacks on dark websites known as ransomware blogs (or ransomware sites). Ransomware blogs are like noticeboards for specific ransomware groups, hosting official updates as well as data dumps.
A data leak prevention strategy must accommodate for these types of leaks by implementing security measures beyond the final phase of the ransomware attack lifecycle - after the data dump phase (phase 8).
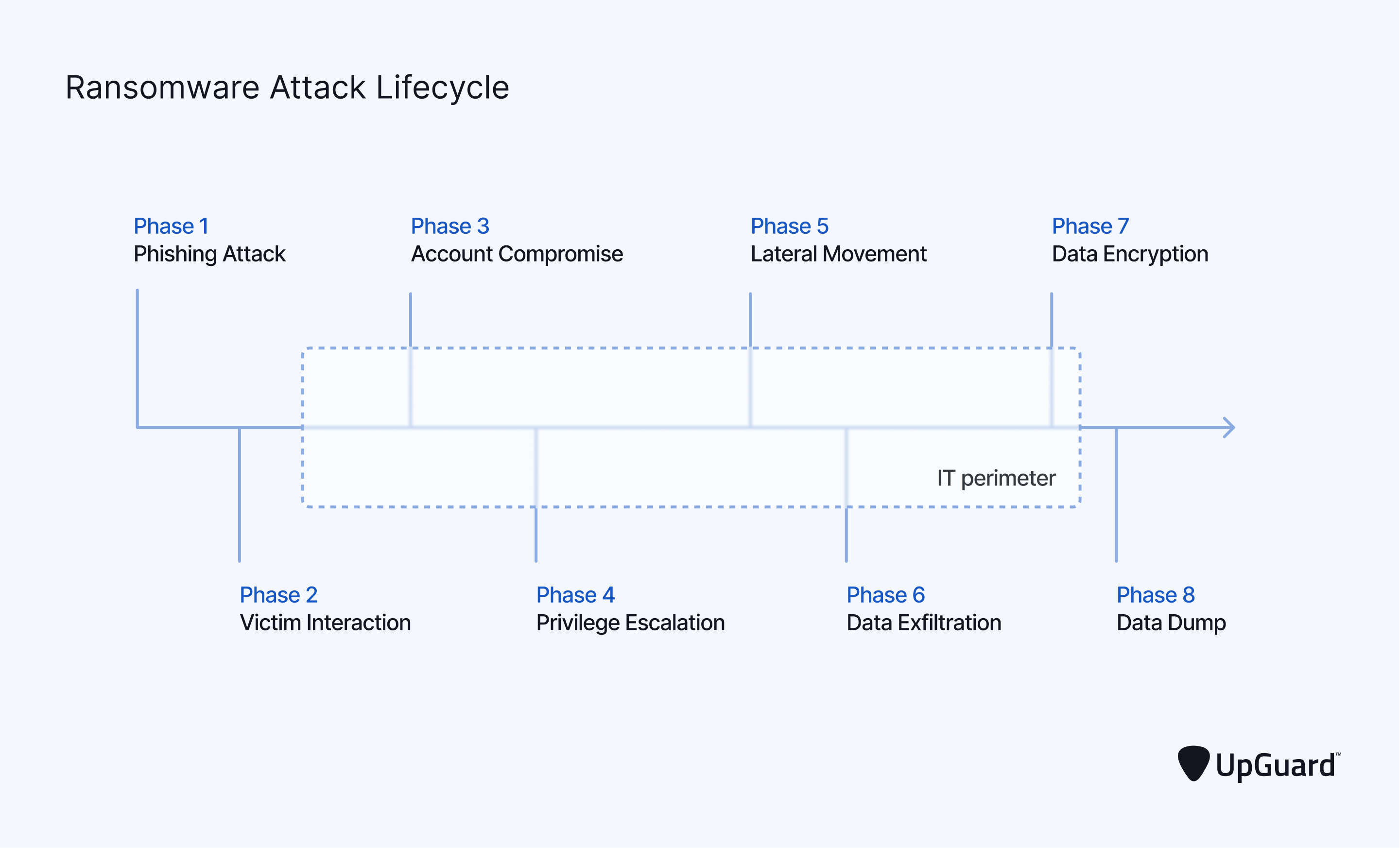
Learn how to reduce the impact of ransomware attacks >
A ransomware data leak security tool monitors popular ransomware blogs for critical data and internal confidential information (like employee credentials leaks). If ransomware leaks are left unaddressed, cybercriminals could use them to instantly gain access to a private network without the usual social engineering processes that preclude unauthorized access attempts.
Armed with internal credentials from a ransomware blog, cybercriminals could circumvent the perimeter penetration phases - the most difficult stages of a ransomware attack - leaving just the challenge of escalating permissions before a breach is achieved.

The resulting compressed ransomware lifecycle, which makes data breaches easier and faster to accomplish, highlights the critical need for ransomware leak security measures in security policies.
Request a free demo of UpGuard's ransomware data leak solution >
Addressing the Source of Data Leaks
The most effective and sustainable cybersecurity initiatives are those that assume a proactive approach to protection .
Data leak monitoring efforts are reduced if the vulnerabilities facilitating data leaks are addressed.
This is most efficiently achieved with an attack surface monitoring solution . Such a solution will discover the security vulnerabilities inside your ecosystem and those throughout your third-party vendor network.
Monitoring the third-party attack surface is crucial since over half of data breach events result from compromised third-party vendors.
Since most breaches stem from compromised third parties, it's safe to assume that your vendors aren't addressing data leaks in their cybersecurity practices.
Because of this, the scope of a data leak detection strategy should also extend to the third-party landscape.
Since data leaks commonly preceded data breaches, this effort will reduce third-party breaches and supply chain attacks and, therefore, most data breach events.
8 Tips to Protect Your Business from Data Leaks in 2024
The following data security practices could prevent data leaks and minimize the chances of data breaches .
1. Evaluate the Risk of Third Parties
Unfortunately, your vendors may not take cybersecurity as seriously as you do. It's important to keep evaluating the security posture of all vendors to ensure they're not at risk of suffering data leaks through critical security vulnerabilities.
Vendor risk assessments are a common method of identifying third-party security risks and ensuring compliance with regulatory standards, such as HIPAA , PCI-DSS , or GDPR . Risk questionnaires could be compiled from templates based on existing frameworks or custom-built for bespoke security queries.
Learn about UpGuard's custom questionnaire builder >
It can be difficult for security teams to keep up with the risk management demands of a rapidly expanding third-party network. To prevent overlooked vendor risks while scaling cloud data and cloud storage, vendor risk management can be easily scaled as a managed service.
2. Monitor all Network Access
The more corporate network traffic being monitored, the higher the chances of identifying suspicious activity. Cyber attacks are usually preceded by reconnaissance campaigns - cybercriminals need to identify the specific defenses that need circumventing during an attack.
Data leak prevention solutions empower organizations to identify and strengthen security vulnerabilities to prevent the possibility of reconnaissance campaigns.
Information security policies may need to be revised to enforce privileged access to highly sensitive data.
3. Identify All Sensitive Data
Data Loss Prevention (DLP) should be front of mind for organizations looking to enhance their data leak prevention strategies. Before DLP policies can be initiated, businesses need to identify all of the sensitive data that needs to be secured. This data then needs to be correctly classified in line with strict security policies.
Data classification categories could include Protective Health Information , financial data, and other sensitive data forms.
With correct sensitive data discovery and classification, a business can tailor the most efficient data leak prevention defenses for each data category.
4. Secure All Endpoints
An endpoint is any remote access point that communicates with a business network via end-users or autonomously. This includes Internet of Things (IoT) devices, desktop computers, and mobile devices.
With most organizations now adopting some form of a remote working model, endpoints have become dispersed (sometimes even internationally), making them harder to secure. Organizations must extend their coverage to cloud-based endpoint security.
Employees with iPhone access to their organizations' networks should ensure they use the Security Recommendations feature , which identifies if any of their saved credentials have been compromised in a data leak.
Firewalls and VPNs offer a base layer of endpoint security, but they're not enough on their own. Staff are often tricked into introducing malware into an ecosystem to bypass these security defenses.
Organizations need to train their staff to recognize the trickery of cyberattackers, particularly email phishing and social engineering attacks. Education is a very powerful data leakage prevention solution. Securing endpoints is a fundamental component of Data Loss Prevention (DLP).
5. Implement Data Loss Prevention (DLP) Software
Data loss prevention (DLP) is an overarching data protection strategy that should include data leak prevention as a core component. An effective DLP system combines processes and technology to ensure sensitive data is not lost, misused, or exposed to unauthorized users.
Below are the six components of a DLP program requiring DLP solutions:
1. Data identification: Many organizations leverage automation techniques, such as machine learning and artificial intelligence (AI), to streamline the data identification process.
2. Securing data in motion: Deploy DLP software at the network edge to detect sensitive data transfers violating data loss prevention policies.
3. Securing endpoints: Endpoint DLP agents can monitor user behavior in real-time and control data transfers between specified parties, e.g., through instant messaging apps.
4. Securing data at rest: DLP products can enforce access control , regulatory compliance requirements , encryption algorithms , and data storage policies to protect archived data.
5. Secure data in use: Comprehensive DLP tools can monitor and flag unauthorized user behavior, e.g., unauthorized privilege escalation on an app.
6. Data leak detection: If data leak prevention strategies fall through, fast remediation is crucial to avoiding a data breach. Effective data leak detection tools can scan the open and deep web for data exposures, including S3 buckets and GitHub repositories, enabling faster removal of potential breach vectors.
6. Encrypt All Data
Cybercriminals may find it difficult to exploit data leaks if the data is encrypted. There are two main categories of data encryption - Symmetric-Key Encryption and Public-Key Encryption.
While encrypted data may stump amateur hackers, capable cyber attackers could decrypt the data without a decryption key. For this reason, data encryption shouldn't be the sole data leak prevention tactic but should be used alongside all the methods in this list.
Learn how tech companies can detect data leaks >
7. Evaluate All Permissions
Your confidential data could currently be accessed by users that don't require it. As an initial response, all permissions should be evaluated to ensure access isn't being granted to authorized parties.
Once this has been verified, all critical data should be categorized into different levels of sensitivity to control access to different pools of data . Only trustworthy staff with essential requirements should have access to highly sensitive data.
This privileged access assignment process may also identify malicious insiders facilitating sensitive data exfiltration.
Learn more about Privileged Access Managemet >
8. Monitor the Security Posture of All Vendors
Sending risk assessments will prompt vendors to strengthen their cybersecurity efforts, but without a monitoring solution, remediation efforts cannot be confirmed.
Security scoring is a highly efficient way of evaluating a vendor's susceptibility to data breaches. These monitoring solutions display all vendors in the third-party network alongside their security rating, giving organizations instant transparency into the health status of their entire vendor network.
The UpGuard platform assigns all vendors a security score based on an analysis of 70+ critical vectors.

Learn more about UpGuard's security rating feature >
Watch the video below for an overview of UpGuard's data leak detection features.
Reviewed by

Kaushik Sen
Ready to see upguard in action, ready to save time and streamline your trust management process, join 27,000+ cybersecurity newsletter subscribers, whitepaper: data leak detection.
Related posts
What are security ratings cyber performance scoring explained.

Why is Cybersecurity Important?
What is typosquatting (and how to prevent it), how to secure your nginx deployment: 10 tips.

Top 10 Ways To Harden Nginx For Windows
What is an open port definition & free checking tools.
- UpGuard Vendor Risk
- UpGuard BreachSight
- Product Video
- Release notes
- SecurityScorecard
- All comparisons
- Security Reports
- Instant Security Score
- Third-Party Risk Management
- Attack Surface Management
- Cybersecurity
Home > Learning Center > Data Loss Prevention (DLP)
Article's content

Looking for a way to protect personal data?
See how imperva can help, data loss prevention (dlp), what is dlp.
Data Loss Prevention (DLP) is the practice of detecting and preventing data breaches, exfiltration, or unwanted destruction of sensitive data . Organizations use DLP to protect and secure their data and comply with regulations.
The DLP term refers to defending organizations against both data loss and data leakage prevention. Data loss refers to an event in which important data is lost to the enterprise, such as in a ransomware attack . Data loss prevention focuses on preventing illicit transfer of data outside organizational boundaries.
Blog: Top Four Reasons for Data Loss from Databases (and what to do about it).
Organizations typically use DLP to:
- Protect Personally Identifiable Information (PII) and comply with relevant regulations
- Protect Intellectual Property critical for the organization
- Achieve data visibility in large organizations
- Secure mobile workforce and enforce security in Bring Your Own Device (BYOD) environments
- Secure data on remote cloud systems
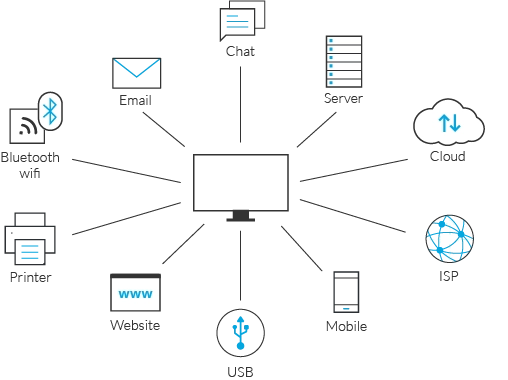
DLP: Preventing data loss from various sources
Causes of Data Leaks
Three common causes of data leaks are:
- Insider threats — a malicious insider, or an attacker who has compromised a privileged user account, abuses their permissions and attempts to move data outside the organization.
- Extrusion by attackers — many cyber attacks have sensitive data as their target. Attackers penetrate the security perimeter using techniques like phishing , malware or code injection, and gain access to sensitive data.
- Unintentional or negligent data exposure — many data leaks occur as a result of employees who lose sensitive data in public, provide open Internet access to data, or fail to restrict access per organizational policies.
Blog: Analysis of 100 Data Breaches: Part 2, What are the root causes of breaches?

Evolving Legislative and Compliance Landscape: Your Data Security Roadmap
Register Now
Data Leakage Prevention
You can use standard security tools to defend against data loss and leakage. For example, an Intrusion Detection System (IDS) can alert about attacker attempts to access to sensitive data. Antivirus software can prevent attackers from compromising sensitive systems. A firewall can block access from any unauthorized party to systems storing sensitive data.
If you are part of a large organization, you might turn to designated DLP tools or solutions to safeguard your data. You can also use tooling in the Security Operations Center (SOC) to assist with DLP. For example, you can use a Security Information and Event (SIEM) system to detect and correlate events which might constitute a data leak.
See how Imperva File Security can help you with DLP.
Components of a Data Loss Solution
- Securing data in motion — technology installed at the network edge can analyze traffic to detect sensitive data sent in violation of security policies.
- Securing endpoints — endpoint-based agents can control information transfer between users, groups of users, and external parties. Some endpoint-based systems can block attempted communications in real time and provide user feedback.
- Securing data at rest — access control, encryption and data retention policies can protect archived organizational data.
- Securing data in use — some DLP systems can monitor and flag unauthorized activities that users may intentionally or unintentionally perform in their interactions with data.
- Data identification — it is crucial to determine if data needs to be protected or not. Data can be defined as sensitive either done manually by applying rules and metadata, or automatically via techniques like machine learning.
- Data leak detection — DLP solutions and other security systems like IDS, IPS, and SIEM, identify data transfers that are anomalous or suspicious. These solutions also alert security staff of a possible data leak.
DLP Solutions and File Security Solutions
File Security Solutions , such as Imperva File Firewall, are an important part of a DLP strategy. Such solutions safeguard data at rest and data in use, and detect leaks of file-based data.
Imperva File Firewall helps prevent data leaks by:
- Monitoring access to all sensitive files and recording granular usage data such as user, department, file accessed, file type and operation response time.
- Alerting on, and automatically blocking, file actions that violate security policies.
- Detecting abnormal or suspicious user behavior using machine learning, to detect insider threats.
- Mitigating Ransomware attacks by detecting and blocking typical file access patterns.
- Auditing and reporting on all file operations for compliance and investigation purposes.
Latest Blogs

Lynne Murray
Apr 25, 2024 4 min read

Brian Robertson
Apr 19, 2024 3 min read

- Industry Perspective
Apr 2, 2024 3 min read

Mar 11, 2024 4 min read

Feb 28, 2024 5 min read

, Paul Steen
Feb 26, 2024 5 min read

, Shiri Margel
Dec 1, 2023 5 min read
Latest Articles
- Data Security
149.3k Views
131.6k Views
117.6k Views
112.7k Views
86.6k Views
84.1k Views
83.2k Views
74.5k Views
2024 Bad Bot Report
Bad bots now represent almost one-third of all internet traffic
The State of API Security in 2024
Learn about the current API threat landscape and the key security insights for 2024
Protect Against Business Logic Abuse
Identify key capabilities to prevent attacks targeting your business logic
The State of Security Within eCommerce in 2022
Learn how automated threats and API attacks on retailers are increasing
Prevoty is now part of the Imperva Runtime Protection
Protection against zero-day attacks
No tuning, highly-accurate out-of-the-box
Effective against OWASP top 10 vulnerabilities
An Imperva security specialist will contact you shortly.
Top 3 US Retailer

What is data loss prevention (DLP)?
Discover how to identify and help prevent risky or inappropriate sharing, transfer, or use of sensitive data on-premises and across apps and devices.
- Explore Microsoft Purview Data Loss Prevention

Data loss prevention defined
Data loss prevention is a security solution that identifies and helps prevent unsafe or inappropriate sharing, transfer, or use of sensitive data. It can help your organization monitor and protect sensitive information across on-premises systems, cloud-based locations, and endpoint devices. It also helps you achieve compliance with regulations such as the Health Insurance Portability and Accountability Act (HIPAA) and General Data Protection Regulation (GDPR). When it comes to security data, following information protection and governance best practices is critical Information protection places controls (for example, encryption) around sensitive data, while information governance determines its lifecycle (how long an organization retains the data). Together, they help your organization understand, safeguard, and govern its data.
Know your data. Understand your data landscape; identify and classify important data across your hybrid environment.
Protect your data. Apply protective actions like encryption, access restrictions, and visual markings.
Prevent data loss. Help people in your organization to avoid accidental oversharing of sensitive information.
Govern your data. Retain, delete, and store data and records in a compliant manner.
How does DLP work?
Data loss prevention is a combination of people, processes, and technology that works to detect and prevent the leakage of sensitive data. A DLP solution uses things like antivirus software, AI, and machine learning to detect suspicious activities by comparing content to your organization’s DLP policy, which defines how your organization labels, shares, and protects data without exposing it to unauthorized users.
Types of data threats
Data threats are actions that can affect the integrity, confidentiality, or availability of your organization’s data, while a data leak exposes your sensitive data to untrustworthy environments.

Cyberattack
A cyberattack is a deliberate, malicious attempt to gain unauthorized access to computer systems (business and personal) and steal, modify, or destroy data. Examples of cyberattacks include distributed denial-of-service (DDoS) attacks , spyware, and ransomware. Cloud security, identity and access management, and risk management are a few ways to protect your network.

Malware , or malicious software—including worms, viruses, and spyware—is often disguised as a trusted email attachment or program (for example, an encrypted document or file folder). Once opened, it allows unauthorized users into your environment who can then disrupt your entire IT network.

Insider risks
Insiders are people who have information about your data, computer systems, and security practices, such as employees, vendors, contractors, and partners. Misusing authorized access to negatively impact the organization is one example of an insider risk .

Unintentional exposure
Unintentional exposure occurs when employees unknowingly allow access to unauthorized users or viruses. Identity and access management tools help organizations control what users can and can’t access, and helps keep your organization’s important resources—like apps, files, and data—secure.

Phishing is the act of sending fraudulent emails on behalf of reputable companies or other trustworthy sources. The intention of a phishing attack is to steal or damage sensitive data by tricking people into revealing personal information such as passwords and credit card numbers. They can target a single person, a team, a department, or an entire company.

Ransomware is a type of malware that threatens to destroy or block access to critical data or systems until a ransom is paid. Human-operated ransomware that targets organizations can be difficult to prevent and reverse because the attackers use their collective intelligence to gain access to an organization’s network.
Why is DLP important?
A DLP solution is essential to your risk reduction strategy, especially when it comes to securing endpoints like mobile devices, desktop computers, and servers.
Information security (InfoSec) refers to the security procedures that protect sensitive information from misuse, unauthorized access, disruption, or destruction, including both physical and digital security. Key elements of InfoSec include the following:
Infrastructure and cloud security . Security for your hardware and software systems to help prevent unauthorized access and data leaks from your public cloud, private cloud, hybrid cloud, and multicloud environments.
Cryptography. Algorithm-based communication security to ensure that only the intended recipients of a message can decipher and view it.
Incident response . How your organization responds to, remediates, and manages the aftermath of a cyberattack, data breach, or another disruptive event.
Disaster recovery. A plan for re-establishing your technological systems after a natural disaster, cyberattack, or other disruptive events.
Benefits of a DLP solution
DLP benefits begin with the ability to classify and monitor your data and include improving your overall visibility and control.

Classify and monitor sensitive data
Knowing what data you have and how it’s used across your digital estate makes it easier for your organization to identify unauthorized access to data and protect it from misuse. Classification means applying rules for identifying sensitive data and maintaining a compliant data security strategy.


Detect and block suspicious activity
Customize your DLP solution to scan all data flowing through your network and block it from leaving the network by email , being copied to USB drives, or other means.

Automate data classification
Automated classification gathers information, such as when a document was created, where it’s stored, and how it’s shared, to improve the quality of data classification in your organization. A DLP solution uses this information to enforce your DLP policy, which helps prevent sensitive data from being shared with unauthorized users.

Maintain regulatory compliance
Every organization must adhere to data protection standards, laws, and regulations like HIPAA, the Sarbanes-Oxley (SOX) Act, and the Federal Information Security Management Act (FISMA). A DLP solution gives you the reporting capabilities you need to complete compliance audits, which may also include having a data-retention plan and training program for your employees.

Monitor data access and usage
To keep threats at bay, you need to monitor who has access to what and what they’re doing with that access. Prevent insider breaches and fraud by managing the digital identities of employees, vendors, contractors, and partners across your network, apps, and devices. Role-based access control is one example of providing access to only the people who need it to do their jobs.

Improve visibility and control
A DLP solution gives you visibility into the sensitive data within your organization and helps you see who might be sending it to unauthorized users. Once you determine the scope of actual and potential issues, further customizations can be made to analyze data and content to strengthen your cybersecurity measures and DLP efforts.
DLP adoption and deployment
When adopting a data loss prevention solution, it’s important to do thorough research and find a vendor whose solution is appropriate for your needs.
To deploy your DLP solution with minimal downtime and avoid costly mistakes, your organization can:
Document the deployment process. Ensure your organization has procedures to follow, reference material for new team members, and records for compliance audits.
Define your security requirements. Help protect your organization’s intellectual property and your employees’ and customers’ personal information.
Establish roles and responsibilities. Clarify who’s accountable, who needs to be consulted, and who needs to be informed regarding activities related to your DLP solution. For example, your IT team must take part in the deployment so that they understand the changes being made and are able to resolve issues. It’s also important to separate responsibilities so that those who create policies can’t implement them, and those who implement policies can’t create them. These checks and balances help thwart the misuse of policies and sensitive data.
DLP best practices
Follow these best practices to help ensure successful data loss prevention:
- Identify and classify sensitive data . To protect your data, you need to know what you’ve got. Use your DLP policy to identify sensitive data and label it accordingly.
- Use data encryption. Encrypt data that is at rest or in transit so unauthorized users won’t be able to view file content even if they gain access to its location.
- Secure your systems. A network is only as secure as its weakest entry point. Limit access to employees who need it to do their jobs.
- Implement DLP in phases. Know your business priorities and establish a pilot test. Allow your organization to grow into the solution and all it has to offer.
- Implement a patch management strategy. Test all patches for your infrastructure to ensure there are no vulnerabilities being introduced into your organization.
- Allocate roles. Establish roles and responsibilities to clarify who is accountable for data security.
- Automate. Manual DLP processes are limited in scope and can’t scale to meet the future needs of your organization.
- Use anomaly detection. Machine learning and behavioral analytics can be used to identify abnormal behavior that could result in a data leak.
- Educate stakeholders. A DLP policy isn’t enough to prevent intentional or accidental incidents; stakeholders and users must know their role in protecting your organization’s data.
- Establish metrics. Tracking metrics—like the number of incidents and time-to-response—will help determine the effectiveness of your DLP strategy.
DLP solutions
With data threats, it’s a matter of when they’ll happen, not if they’ll happen. Choosing a DLP solution for your organization requires research and planning, but it’s time and money well spent to protect the sensitive data, personal information, and reputation of your brand.
Understanding these options and how they work with your DLP solution can help jumpstart your journey to more secure data.
User behavior analytics. Make sense of the data you gather about your systems and the people using them. Flag suspicious behavior before it leads to a data leak or security breach.
Security education and awareness. Teach employees, executives, and IT teammates how to recognize and report a security incident and what to do if a device is lost or stolen.
Encryption. Maintain the confidentiality and integrity of your data by ensuring that only authorized users can access data while it’s at rest or in transit.
Data classification. Identify which data is sensitive and business critical, then manage and protect it across your environment—wherever it lives or travels.
Cloud access security broker (CASB) software. Enforce your security policy between enterprise users and cloud service providers to mitigate risk and maintain regulatory compliance.
Insider risk management software. Pinpoint which employees may be accidentally leaking data and uncover malicious insiders who are intentionally stealing sensitive information.
Get governance , protection, and compliance solutions for your organization with Microsoft Purview . Visit the Purview website to learn how to improve visibility, manage your data securely, and go beyond compliance while safeguarding your data across platforms, apps, and clouds.
Learn more about Microsoft Security
Information protection.
Help protect and govern your data with built-in, intelligent, unified, and extensible solutions.
Microsoft Purview Data Loss Prevention
Identify inappropriate sharing, transfer, or use of sensitive data on endpoints, apps, and services.
Microsoft Purview Information Protection
Understand, manage, and protect your sensitive and business-critical data.
Microsoft Purview Data Lifecycle Management
Use information governance to classify, retain, review, dispose of, and manage content.
Protect Your Data End-to-End
Explore how data protection requirements are changing and learn three steps to help modernize the way you protect your data.
Frequently asked questions
What are the main types of data loss prevention.
The main types of data loss prevention are:
- Network DLP – Preventing the loss of sensitive data from your computer network, including email, web applications, and protocols like FTP and HTTP.
- Cloud DLP – Classifying and protecting sensitive data in cloud computing environments, including public, private, hybrid, and multicloud environments.
- Endpoint management DLP – Monitoring servers, computers and laptops, cloud repositories, and mobile phones and devices where data is accessed and stored.
What are examples of data loss prevention?
Examples of DLP include:
Software. Control who accesses and shares data in your organization. Establish policy controls to detect and prevent unauthorized data transfers, sharing, or leaks.
Encryption. Plaintext is transformed into unreadable cipher-text (more simply, data is converted into code) to prevent unauthorized access.
Alerts. Network administrators are notified when a user takes actions that go against your DLP policy.
Reporting. Customized DLP reports may contain policy matches, incidents, and false positives. Reporting helps you identify the accuracy of your DLP policies and refine them as needed.
What is a data loss prevention policy?
A DLP policy defines how your organization shares and protects data without exposing it to unauthorized users. It helps you comply with government regulations, protect intellectual property, and improve visibility into your data.
How do you implement a DLP plan?
Start with these important tasks to implement a data loss prevention plan.
- Categorize your data so you can monitor how it’s used.
- Define roles and responsibilities in your organization so that only employees who need specific data are allowed to access it.
- Establish a training plan for employees to make them aware of what actions can result in data loss.
Why is DLP important for organizations?
A data breach can cost your organization millions of dollars, damage its reputation, and affect its revenue stream for years. A data loss prevention solution helps your organization:
- Protect intellectual property and personally identifiable information.
- Gain visibility into how people are interacting with data.
- Comply with digital privacy laws.
Follow Microsoft 365
- Chat with sales
Available M-F 6 AM to 6 PM PT.
Maximize security. Optimize value.
Protect people, defend data, solutions by industry.
- Support Log-in
- Digital Risk Portal
- Email Fraud Defense
- ET Intelligence
- Proofpoint Essentials
- Sendmail Support Log-in
- English (Americas)
- English (Europe, Middle East, Africa)
- English (Asia-Pacific)
What Is a Data Leak?
Table of contents, data leak vs. data breach: key differences, what causes data leaks, types of data at risk, what do cybercriminals look for in leaked data, how do cybercriminals use leaked data, how to prevent data leaks, common data leak scenarios, real-world examples of data leaks, how proofpoint can help.
A data leak unintentionally exposes sensitive, protected, or confidential information outside its intended environment. This happens for various reasons, such as internal human errors, software vulnerabilities, or poor data security measures. Data leaks can compromise personal details, financial records, trade secrets, or other proprietary data. Leaked information can be used to quickly cause future data breaches and have severe consequences for individuals and organizations alike, leading to reputational damage, financial losses, and legal implications.
The terms “data leak” and “ data breach ” are often used interchangeably, but a data leak does not require exploiting a vulnerability. A data leak can simply be the disclosure of data to a third party from poor security policies or storage misconfigurations. In most scenarios, a data leak is accidental, while a data breach is malicious and intentional.
Cybersecurity Education and Training Begins Here
Here’s how your free trial works:.
- Meet with our cybersecurity experts to assess your environment and identify your threat risk exposure
- Within 24 hours and minimal configuration, we’ll deploy our solutions for 30 days
- Experience our technology in action!
- Receive report outlining your security vulnerabilities to help you take immediate action against cybersecurity attacks
Fill out this form to request a meeting with our cybersecurity experts.
Thank you for your submission.
It might seem insignificant, but it’s important to understand the difference between a data leak and a data breach. Both can be costly and have critical consequences, but a data leak involves much more negligence than a data breach. Human error is a significant risk for organizations, and a data leak is typically the result of insider threats , often unintentional but just as damaging as a data breach.
Unforeseen risks or unknown software, hardware, or security infrastructure vulnerabilities cause data breaches. To succeed, an attacker finds and exploits the vulnerability, so administrators must continually update outdated software and install security patches or updates immediately.
A data leak results in a data breach but does not require exploiting an unknown vulnerability. Typically, human error is behind a data leak. An excellent example of a data leak is a misconfigured Amazon Web Services (AWS) S3 bucket. S3 buckets are cloud storage spaces used to upload files and data. They can be configured for public access or locked down so only authorized users can access data. It’s common for administrators to misconfigure access, thereby disclosing data to any third party. Misconfigured S3 buckets are so common that some sites scan for misconfigured S3 buckets and post them for anyone to review.
Data leaks can arise from a combination of technical misconfigurations, human errors, and weaknesses in organizational security policies. The causes of data leaks often overlap with those of data breaches, but they primarily revolve around the unintentional exposure of sensitive information. Some of the key factors contributing to data leaks include:
- Infrastructure misconfigurations: One of the most common causes of data leaks. Whether it’s a misconfigured cloud service like AWS S3 or an internal server, improper security settings can lead to unintended data exposure. This includes misconfigured firewalls that might inadvertently open ports and allow unauthorized access to data.
- Weak security policies: Data can be unknowingly disclosed without stringent security policies. Organizations need to have robust protocols that prevent unauthorized user access.
- Employee and vendor errors: Human error, whether unintentional or malicious, is a significant factor in data leaks. These errors range from mishandling sensitive data and not following established security procedures to vendors inadvertently exposing data they can access. Proper cybersecurity training for all personnel is crucial in mitigating this risk.
- System errors: Occasionally, unexpected system errors can lead to data leaks by defaulting to open access for unauthorized users. Once exposed, search engines can even index sensitive information, making it easily discoverable.
- Open-Source files and repositories: Developers sometimes inadvertently include sensitive data in public repositories, such as hard-coded credentials or access keys. Malicious actors can exploit these to gain unauthorized access to data.
- Unpatched infrastructure: If not timely addressed with security patches, vulnerabilities in software and systems can become gateways for unauthorized data access.
By addressing these vulnerabilities and instilling a culture of cybersecurity awareness, organizations can significantly reduce the risk of data leaks.
Organizations don’t want data disclosed to an unauthorized user, but some data is more sensitive than others. It might not mean much to disclose a product table to the public, but a table full of user social security numbers and identification documents could be a grave predicament that could permanently damage the organization’s reputation.
Examples of data disclosure after a leak include:
- Trade secrets or intellectual property stored in files or databases.
- Private proprietary source code.
- Credentials like usernames, passwords, and security questions.
- Business data like customer lists, sales data, and other business-related information.
- Current product and inventory status, including vendor pricing.
- Proprietary research used for product improvements, patents, and inventions.
- Sensitive customer data, including health and financial information.
- Employee data, including social security numbers, financial information, and credentials.
- Health information, such as medical records, insurance information, and prescription information.
- Emails, chat logs, and other forms of private communication.
Cybercriminals are constantly on the prowl for vulnerabilities and opportunities, with leaked data as a valuable asset for their malicious endeavors. But what exactly do they seek in leaked data, and once they have it, what do they do with it?
- Personal Identification Information (PII): This includes names, addresses, social security numbers, and more. Criminals can use the data for identity theft, impersonating individuals to commit fraud, obtain credit, or gain other financial benefits.
- Financial information: Credit card details, bank account numbers, and other financial data are used to make unauthorized transactions, siphon funds, or even be sold on the dark web.
- Login credentials: Usernames and passwords for various accounts can be exploited to gain unauthorized access. Cybercriminals use techniques like credential stuffing to access multiple sites, banking on the fact that many individuals reuse passwords across platforms.
- Health records: Medical information is highly valuable and can be used for insurance fraud, prescription fraud, or sold to interested parties.
- Trade secrets and intellectual property: For corporations, leaked data might contain proprietary information. Cybercriminals can sell this to competitors or use it for corporate espionage.
- Emails and personal communications: These can be used for blackmail or to stage further targeted attacks, such as spear-phishing campaigns.
- Operational data: Information about an organization’s operations, network configurations, or security practices can be used to facilitate more sophisticated cyber-attacks.
Depending on the type of data, threat actors can use leaked information for a myriad of malicious intentions. Here are some of the things that cybercriminals do with leaked data:
- Direct financial gain: By selling the data on the dark web or using it for fraudulent transactions.
- Carry out phishing attacks: Cybercriminals can use leaked data to craft convincing phishing emails that appear to be from legitimate sources but are intended to deceive people into giving away their personal information or downloading malware.
- Conduct ransomware attacks: Threat actors can use leaked data to launch ransomware attacks, where they encrypt the victim’s data and demand payment in exchange for the decryption key.
- Commit identity theft: Cybercriminals can steal people’s identities with leaked data, which they use to open bank accounts, apply for loans, or make fraudulent purchases.
- Facilitate other crimes: With stolen identities, criminals can commit a range of offline crimes, from fraud to false credit applications.
- Reputation damage: For high-profile entities or celebrities, leaked data can be used to tarnish their reputation.
As the digital landscape evolves, the motives and methods of today’s cybercriminals continuously change. As they develop new ways to exploit leaked data, individuals and organizations must remain vigilant and proactive in their cybersecurity measures.
Data protection strategies should always include employee education and training, but administrators can take additional steps to stop data leaks.
Here are a few ways you can prevent a data leak incident:
- Audit and classify data: It’s common for fast-growing businesses to lose track of data and its storage locations. It’s challenging to cover all your bases without knowing where data is located and discovering after the fact that applications and users have moved data. Classifying data also reveals employee permission misuse and potential data leaks from unnecessary access.
- Be proactive: A risk assessment and management help identify risks and provide administrators with mitigation strategies that typically require additional security measures, policies, and employee training.
- Evaluate third-party risk: Evaluate the security practices of third-party vendors and partners accessing your data. Make sure they use robust security measures to prevent data leaks.
- Implement access control: Limit and review access as appropriate for your organization. Consider using role-based access control to ensure that only authorized personnel can access sensitive data.
- Use encryption: Data encryption translates data into another code or form, and only those with access to a decryption key or password can read it. Data encryption can prevent cybercriminals from reading sensitive data in the event of data leakage.
- Implement data loss prevention (DLP) software: DLP software continuously monitors and analyzes your data to identify potential violations of security policies. Beyond identifying policy violations, the proper DLP solution can effectively stop them.
- Protect data based on value and sensitivity: Data leaks on unimportant data are not ideal but are far less damaging than sensitive data disclosure. After an audit and data discovery, focus on the most valuable data first. Data discovery software can help because it provides dependable and automated content analysis and tracks information across your network.
- Offer cybersecurity training: Education reduces the chance of human error from phishing or social engineering . It also helps employees know how to properly manage data and protect data.
- Monitoring: Deploying the right monitoring tools helps administrators identify anomalies faster and makes them more proactive in containing and eradicating a threat. Some tools also identify misconfigurations and potential data leak issues.
- Have a disaster recovery plan: Disaster recovery with backups will restore destroyed data. A recovery plan includes the people involved in data recovery and the many steps to communicate with affected customers and any news outlets.
To better design security infrastructure around sensitive data, it helps to know common scenarios where data leaks occur. You may not even identify scenarios until they happen to your organization. Here are a few ways an organization could be victim to a data leak:
- Employee brings files home from work: There’s a reason why larger corporations lock down USB drive access. Employees might think it’s harmless to take their work home and store data on their devices, but it can lead to a data leak should the device get lost or insecurely stored.
- Unencrypted data storage: Users and attackers could obtain unencrypted data from a permission error or accidental transfer to publicly accessible cloud storage. Data sent in instant messages or emails are also vulnerable if unencrypted.
- Password misuse: Employees who write down passwords or insecurely store them could disclose them accidentally to a third party. Strong passwords are key to preventing breaches and data loss, which is why it’s so important to educate your people on password awareness and best practices.
- Outdated software: Developers patch software with known vulnerabilities, but administrators must take the initiative to install them. Security patches should be installed immediately, or attackers could exploit vulnerable data storage systems.
- Software misconfigurations: When software is not configured properly to store files or data, it could openly disclose data without administrators being aware.
- Development server compromise: Development environments are often loosely protected, but developers replicate production data to the development server for access. That might seem harmless, but developers could potentially configure the server or the environment in a way that discloses data.
Awareness of general scenarios helps with data governance and risk management, but even large corporations fall victim to threats. Here are a few real-world examples of data leaks that impacted large organizations or government entities:
- The Texas Department of Insurance experienced an ongoing data leak not identified until 2022. The potentially accessible information included names, addresses, dates of birth, phone numbers, parts or all of social security numbers, and information about injuries and workers’ compensation claims.
- A misconfigured database at Pegasus Airlines exposed 23 million files containing personal data online. The database contained flight charts, navigation materials, and information about the flight crew. The incident resulted in a significant loss of customer trust and a fine from regulators.
- The Veterans Administration lost 26.5 million records with sensitive data, including social security numbers and date-of-birth, after an employee took data home.
- Idaho Power Company in Boise was victim to a data leak after they sold used hard drives containing sensitive files and confidential information on eBay.
- Loyola University computers disposed of hard drives containing sensitive student information without wiping them. The result was the disclosure of social security numbers and financial aid records.
- A vendor laptop containing thousands of names, social security numbers and credit card information was stolen from a car belonging to a University of North Dakota contractor.
- An error in Texas University’s software allowed unauthorized users to access names, courses, and grades for 12,000 students.
Identifying misconfigurations and gaps in data loss prevention (DLP) requires staff that can monitor and scan for these issues. Many organizations lack the personnel to properly plan for disasters and build infrastructure to secure data from unintentional data leaks. Proofpoint can take you from start to finish to design a data loss prevention plan and implement it. Our information protection experts help you classify data, automate data procedures, comply with regulatory requirements, and build infrastructure that supports effective data governance.
Proofpoint also offers comprehensive DLP solutions to prevent sensitive information from leaking outside your organization. Our DLP products enable you to identify and analyze sensitive data unique to your organization, detect data exfiltration transmissions, and automate regulatory compliance.
- Enterprise DLP is a people-centric solution that brings context across content, behavior, and threats together for a complete view of risk.
- Email DLP detects sensitive data and confidential information and keeps it from leaking outside your organization through email.
- Endpoint DLP provides integrated content awareness along with behavioral and threat awareness, giving you granular visibility into your users’ interactions with sensitive data.
These solutions help organizations simplify discovery and quickly evaluate data to respond to any issue. For more information, contact Proofpoint .
Related Resources
4 ways to prevent insider threat driven data leaks, 4 types of data leaks and their consequences, prevent insider-led data leaks without compromising user privacy, proofpoint wins best data leakage prevention (dlp) solution at the sc media awards europe 2021, subscribe to the proofpoint blog, ready to give proofpoint a try.
Start with a free Proofpoint trial.
What is a Data Leak? Causes and Prevention
- Learn How Fortinet's Security Fabric Protects Your Organization

Data Leak Meaning and Examples
A data leak happens when an internal party or source exposes sensitive data, usually unintentionally or by accident. The results of a data leak can range from loss of information to malicious exploitation. Often, data leaks lead to data breaches .
How Do Data Leaks Happen?
- Weak infrastructure: An improperly configured network infrastructure can allow data to be leaked, causing loss or even misuse. For example, cybersecurity company Cognyte left a massive database unsecured, with no authentication or authorization required for access. As a result, more than 5 million records were exposed online.
- Human error: Recent statistics reveal that human error is the primary cause of data leaks and breaches. Human error can cause leaks of various degrees, from an email sent to the wrong people to massive leaks caused by stolen credentials. An example is the massive data loss (almost 23 terabytes) suffered by the city of Dallas due to employee negligence in 2021.
- System error: System errors can leave networks vulnerable. In 2019, a Facebook vulnerability that has since been fixed allowed scammers to scrape the personal data of over 530 million Facebook users across 106 countries, including their email addresses, phone numbers, locations, and other details. In 2021, the data was posted on a hacking forum.
- Third-party vulnerabilities: Third-party applications and vendors may need access to your system or network, but they can pose a risk. An example was the Marriott data leak in 2020 . Hackers took advantage of a third-party application to access over 5 million guest records.
- Malicious insiders: Leaks caused intentionally by malicious insiders are not as common as accidental leaks. In 2021, four lawyers at the Elliott Greenleaf law firm allegedly stole and deleted company files to help a competing law firm open a new office.
According to a recent report by the Identity Theft Resource Center (ITRC), in 2021, data compromises went up by almost 70% , which is almost 25% more than the previous all-time high record set in 2017.
The average yearly cost of data breaches is nearly $4.5 million in 2021 , so it is no wonder that more organizations are now implementing data protection measures to prevent data leakage, including the consequences associated with it, such as regulatory fines, lawsuits, and loss of customer trust.
Data Leak vs Data Breach: What Is the Difference?
While many use the terms "data leak" and "data breach" interchangeably, there is a difference between the two. A data leak often comes from within the organization either by accident or intent, while a data breach occurs when confidential or otherwise protected information is accessed, stolen, or used by outsiders without authorization.
Most often, data leaks are an accident, the result of mishandled information, while data breaches are carried out for malicious intent. For example, in a ransomware attack, confidential data is breached, encrypted, and then lost or exposed if the ransom isn’t paid.
A data breach also can be a tactic for espionage or to gain access to proprietary information including trade secrets and intellectual property. Some data breaches are done as a form of protest or hactivism to expose an organization and damage its reputation.
While a data leak may not result in a data breach, data leaks should be prevented to avoid loss or corruption of data.
4 Types of Data Leaks and Their Consequences
1. shadow it.
Employees contending with heavy workloads and very stringent deadlines may use workarounds and unapproved third-party applications and solutions to get things done. The resulting infrastructure is called “ shadow IT .” Some unsanctioned third-party applications and technology employees are likely to use may include:
- Cloud technology and storage
- Software-as-a-Service (SaaS) applications
- Web applications
Although employees using their own systems and devices can help with productivity, the risk is that shadow IT can lead to unauthorized access to data in the cloud, which can result in information leakage, changes to the data by unapproved users, and data corruption. Additionally, shadow IT creates blind spots for IT teams who may not become aware of the data leak until it is too late.
2. Legacy Tools
Despite technological advances, numerous organizations and their employees are still using certain legacy tools, such as external USB drives, desktop email applications, and public printers. While there is nothing inherently wrong with these tools, they can cause a leak. Imagine an employee losing a USB drive containing sensitive data in a public place. Or imagine private company documents being printed at home or a public printing center.
3. Privileged or Business Users
In 2018, Twitter urged its 330 million users to change and update their passwords after a bug exposed them. This was the result of a problem with the hashing process, which Twitter uses to encrypt its users’ passwords. The social networking site claimed it found and fixed the bug, but this is a good example of potential vulnerability exploits.
Twitter also suffered a potential breach in May 2020 , which could have affected businesses using its advertising and analytics platforms. An issue with its cache saw Twitter admit it was “possible” that some users’ email addresses, phone numbers, and the final four digits of their credit card numbers could have been accessed.
4. Phishing
Phishing continues to be a popular way to attack businesses—because it works. Phishing tactics can expose and allow exploitation of sensitive company data if an employee:
- Clicks on a malicious link in an email
- Shares credentials with others
- Falls for social engineering scams
The consequences can range from unauthorized data access to the installation of malware and other malicious files.
Six Common Causes of Data Leak
Because data leaks typically stem from internal issues, much can be done to identify vulnerabilities and apply preventative strategies. Additionally, staff members can be trained on best practices to reduce the threat of human error.
Here are some of the most common causes of data leaks:
1. Bad Infrastructure
Bad or weak infrastructures are made up of systems that are not configured properly or not maintained regularly. The wrong settings and permissions during initial configuration can lead to unauthorized access or insufficient security. Delays in maintenance, such as patching software or repairing and replacing bad components, can also lead to data exposure.
2. Social Engineering Scams
While social engineering scams may seem like an external attack, they are only successful if the target falls for them. Using emails and social media, criminals may seek to exploit unsuspecting employees to gain access to their organization’s network, system, or finances.
3. Poor Password Policies
Poor password policies, such as using the same credentials for multiple accounts and logins or not creating passwords that are complex enough, can lead to data leaks. Because malicious parties know that many people tend to reuse passwords for various accounts, once they successfully steal a user's password or convince them to reveal it, they will attempt to access as much data as possible.
4. Lost Devices
Lost or stolen laptops, USB storage devices, mobile phones, and other devices can result in major data leaks. Especially because more workers are now remotely accessing systems from various locations, these devices can become a doorway into an organization's network.
5. Software Vulnerabilities
Outdated software or software that has not been recently patched can put sensitive data at risk. Criminals may also create a vulnerability in open-source applications by writing it into the code.
6. Old Data
Most companies grow, expand, and evolve. Employees come and go, infrastructures are upgraded, and systems change, which may leave old data unprotected or exposed.
Four Ways Criminals Exploit Data Leaks
1. social engineering.
In social engineering scams, the perpetrator first attempts to gain and then exploit the user's trust. They usually send an email enticing the recipient to click on a link that installs malware or another malicious program on their computer. Or they may use phishing attacks to get them to reveal credentials, financial or personal information, or convince them to make an unauthorized transaction.
Doxxing is a form of bullying or harassment and entails acquiring and then publishing the information of a person or company without their permission. Once sensitive or personal information becomes public, it can be used to gain access to online accounts, bank accounts, or credit card accounts.
3. Surveillance and Intelligence
Data from a leak can be used to blackmail certain entities, shape public opinion, manipulate outcomes, and gain favor. It can be very damaging but effective, particularly in politics and business espionage.
4. Disruption
People who exploit data leaks may misuse information to disrupt the operations of target organizations, such as businesses or government bodies.
How To Fix a Data Leak: 3 Quick Steps
Prevention is better than cure, so whether you are trying to contain a data leak or preventing it from happening in the first place, here are some steps to take:
1. Validate Cloud Storage Configurations
Cloud storage can easily become the source of a leak, so make sure it is secure when you first set it up and then periodically as your organization expands and evolves. Establish that the system is working as intended.
2. Automate Process Controls
As your organization grows, it can be difficult to ensure consistency and security. Automation can help because computers can handle the workload better than humans. Documenting and standardizing process controls ensure security policies that safeguard cloud storage are enforced.
3. Monitor Third-party Risk
Allowing third parties to access your systems is often a necessary risk, but data leaks can be minimized through vigilant monitoring. This is particularly important because your company is responsible for data security compliance , even if a leak is caused by a third party.
Frequently Asked Questions about Data Leaks
1. what is a data leak, 2. how does a data leak happen, 3. how to fix a data leak.

Get A Cyber Threat Assessment Today
Get Insights into your Network Vulnerabilities with Cyber Security and Threat Assessment.
There are 2-ways to find the state of your network security - wait for a breach to happen or proactively carry out a security threat assessment. Sign up today to get a zero cost assessment done on your security landscape and network utilization.
Quick Links

Free Product Demo
Explore key features and capabilities, and experience user interfaces.
Resource Center
Download from a wide range of educational material and documents.

Free Trials
Test our products and solutions.
Contact Sales
Have a question? We're here to help.
Survey of Techniques on Data Leakage Protection and Methods to address the Insider threat
- Open access
- Published: 14 July 2022
- Volume 25 , pages 4289–4302, ( 2022 )
Cite this article
You have full access to this open access article

- Isabel Herrera Montano ORCID: orcid.org/0000-0003-0841-653X 1 ,
- José Javier García Aranda 2 ,
- Juan Ramos Diaz 2 ,
- Sergio Molina Cardín 2 ,
- Isabel de la Torre Díez 1 &
- Joel J. P. C. Rodrigues 3 , 4
6 Citations
3 Altmetric
Explore all metrics
Data leakage is a problem that companies and organizations face every day around the world. Mainly the data leak caused by the internal threat posed by authorized personnel to manipulate confidential information. The main objective of this work is to survey the literature to detect the existing techniques to protect against data leakage and to identify the methods used to address the insider threat. For this, a literature review of scientific databases was carried out in the period from 2011 to 2022, which resulted in 42 relevant papers. It was obtained that from 2017 to date, 60% of the studies found are concentrated and that 90% come from conferences and publications in journals. Significant advances were detected in protection systems against data leakage with the incorporation of new techniques and technologies, such as machine learning, blockchain, and digital rights management policies. In 40% of the relevant studies, significant interest was shown in avoiding internal threats. The most used techniques in the analyzed DLP tools were encryption and machine learning.
Similar content being viewed by others

Securing Big Data: Current Challenges and Emerging Security Techniques

Cybersecurity, Data Privacy and Blockchain: A Review
Data breaches in healthcare: security mechanisms for attack mitigation
Avoid common mistakes on your manuscript.
1 Introduction
In terms of information security, insider threat refers to the risk posed by an organization’s employees, partners, or customers to the organization’s information [ 1 ]. Data leakage is the disclosure of information to unauthorized entities or individuals [ 2 ], commonly caused by an intentionally or unintentional threat to the insider [ 3 ], [ 4 ], [ 5 ]. Data leakage protection (DLP) systems or DLPS are designed primarily to monitor data flow in an organization and apply predefined measures on terminal devices or networks within the organization [ 2 ]. The measures range from logging activities, sending alerts to end users and administrators, to quarantining data or blocking it altogether. DLP tools can monitor data at rest and in motion to detect sensitive information [ 3 ], [ 6 ].
In both corporate and hospital environments, the security of classified information is vital, the cost to companies of the lack of DLP technologies is estimated at over $200 per employee per year, and the human factor accounts for 35% of the causes of security breaches, including malicious and unintentional activities of both employees and third parties [ 7 ]. Not all sectors are equally affected by the costs of data leakage, the most sensitive being the healthcare and banking sectors due to the large volume of personal data they both handle [ 8 ]. The Spanish report [ 9 ] shows several aspects that give rise to data leakage in the healthcare sector, with malicious insider threats and unintentional employee actions being evident. Motivated by all of the above, the main objective of this work is to survey the literature to detect existing techniques to protect data leakage, and to identify the methods used to address the insider threat.
Studies similar to this focus on reviewing the functions of DRM products popular in 2011 and available on the market, quantitatively evaluating the impact of the use of these products [ 10 ]; analyzing the existing digital forensics and incident management literature with the aim of contributing to the knowledge gaps in incident management in the cloud environment [ 11 ]; outline lines of research based on a systematic review focused on blockchain technology applied to eHealth [ 12 ]; examining the state of the art in security, privacy, and big data protection research [ 13 ]; in [ 14 ] a survey about sensitive data leakage prevention and anti-theft technologies for protecting the information security of e-government users; and in [ 15 ] study monitoring strategies for confidential documents based on virtual file system (VFS), in [ 16 ] a systematic review of the literature focused on management functions in information security is carried out. The recent studio [ 17 ] presents a review focused on the mobile agent model for data leakage prevention. The review only considered papers published in the journal “Communications and Network” and conference papers published between 2009 and 2019. Mobile agent-based distributed intrusion prevention and detection systems were analyzed in terms of their design, capabilities, and shortcomings. Other studies focus on reviewing blockchain strategies for secure and shareable computing, examining the state of blockchain security in the literature, from the point of view of information system security issues, classified into three levels: process level, data level, and infrastructure level [ 18 ], survey the literature to analyze how blockchain systems can overcome potential cybersecurity barriers to achieve intelligence in Industry 4.0 [ 19 ].
Research on data protection has increased with the introduction of telecommuting due to the pandemic and the need to move data to external devices and networks. Similar work has been found to exist in reviews related to data protection, but it is worth noting that there is no recent study focused on grouping the work developed in the last ten years on DLP tools, where special attention is given to the techniques used in DLP tools and methods to combat the insider threat. The main contributions of this article are the following: (1) it highlights the most used techniques in DLP tools, (2) it summarizes the methods found in the literature to face the insider threat, with the aim of promoting the transformation of protection against data leaks in this sense, to make it more secure, and (3) exposes the limitations, advances, and applications of DLPS, in order to encourage the development of new tools.
This paper addresses the following research questions:
RQ1. What techniques or technologies are used as DLP tools? It is solved in Sections 2 and 5, giving a presentation of the main tools found in Section 2 and an analysis of their frequency of use in relevant studies in Section 5. RQ2. How is the insider threat addressed in the DLP tools found in the literature? The answer to this question is presented in section 3, which summarizes how insider threat is addressed in the literature analyzed. RQ3. What are the highlights the most used techniques in DLP tools, limitations, advances, and applications of DLPS in different fields, in order to encourage the development of new tools, and 2) it exposes the methods found in the literature to face the insider threat, with the aim of promoting the transformation of data leakage protection in this sense, to make it more secure advances and applications of DLP systems? This question is answered in Section 5.3, where the main advances and applications of DLP systems in the period studied are presented.
The rest of the document is organized as follows: Sect. 2 describes the main techniques and technologies used in DLP. Section 3 presents the methods to address insider threats found in the literature and Sect. 4 describes the methodology followed for the literature review. Section 5 discusses the results obtained and the main limitations, advances, and applications of DLPS. Finally, this article is concluded, and future work is presented.
2 Techniques and Technologies in DLP
Several studies propose novel DLPS integrated by different techniques and technologies to try to ensure optimal protection of confidential information, this section gives an overview of the most used techniques and technologies in the papers relevant to this study.
2.1 Overview of techniques most commonly used in DLPS
2.1.1 inteligents documents.
This technique consists of encapsulating within the document both the data it contains and the security mechanisms to control the use of such data [ 20 ], [ 21 ]. The security mechanisms can be content deletion, content editing, content reading, or an authorized user to perform each operation. This technique makes it possible to record where, when, and by whom the content of the document is accessed [ 22 ]. It is a technique generally used in DRM systems and very useful in combination with DLPS.
2.1.2 Encryption
The most widely used technique in DLPS is cryptography, this is because it is the main basis of security and is based on the conversion of data from a readable format to an encrypted format. Any encryption algorithm is equivalent to a mutating substitution algorithm, the substitution unit being the concept of “block”, and the substitution table being something nonfixed (and therefore mutating). The robustness of the algorithm is given by the mutability, which prevents statistical attacks [ 3 ].
A widely used DLPS approach is exact file hash matching. This method is based on the verification of outbound traffic by comparing the hash values of the intercepted traffic and existing sensitive data [ 2 ]. If a match is detected between the values, a leak is detected by the system. This approach presents the problem that any modification of the original document may result in a completely different hash value, which would not allow the system to detect the confidential document [ 20 ].
2.1.4 Virtual file system (VFS)
A VSF is an abstraction layer on top of a real file system (RFS), that is, an intermediate layer between system calls and the RFS driver [ 15 ]. They also provide the ability to perform operations before and after reading, writing, etc. In exchange for this intermediate “translation” between the applications and the actual file system, some of the original RFS performance is lost.
2.1.5 Challenges or context-based keys
Challenges replace a stored key with a calculated key, eliminating the security problem in key storage and distribution [ 3 ], [ 21 ], [ 22 ], in turn, allowing the user to be identified through biometric data, the location of the computer by nearby Wi-Fi signals or GPS, among other benefits that this technique allows.
2.1.6 Minifilters
Minifilters are low-level applications that run in Windows kernel mode and perform value-added functions (backup, encryption, monitoring, etc.) on filesystem operations (read, write, metadata modification, etc.) [ 23 ], [ 24 ], [ 25 ].
2.1.7 Biometric information
This technique is widely used in DLPS to identify the user accessing the information and thus try to ensure that it is a legitimate user with permissions to access the information [ 26 ], [ 27 ], [ 28 ].
2.1.8 Hypervisor
Hypervisor-based memory introspection, the approach looks for the presence of sensitive raw data in memory on both client and server machines, transcending the dependency on pre-existing security perimeters. This solution presents a high computational cost as a hypervisor-based tool consists of deploying one or more virtual machines to monitor system calls, which consumes too much hardware resources, such as memory and processing [ 29 ].
2.2 DRM for document protection
Digital Rights Management (DRM) systems, this term refers to a set of policies, techniques and tools that guide the proper use of digital content. A DRM system is based on ensuring that only intended recipients can view sensitive files regardless of their location. Thus, ensuring data protection beyond the boundaries controlled by DLP systems, so that an organization is always in control of its information [ 30 ], [ 31 ].
The integration of DLPS and DRM policies ensures that vulnerabilities are minimized and that an organization can immediately deny access to any file, regardless of its location [ 6 ]. In [ 31 ], [ 32 ] and [ 33 ], the enterprise digital rights management (eDRM) system is presented, which provides persistent protection for documents using cryptographic methods and also includes features for document protection that are easy to use for the enterprise. In the study [ 34 ] the authors reveal the importance of DRM solutions to prevent unauthorized users, inside or outside the boundaries of the organization, from reading an accidentally sent document. As well as, their limitations towards certain types of documents, in addition to preventing the file from further propagation on the external network once filtered, nor an expert hacker from attempting to decrypt the file’s content. In [ 35 ] DRM systems are compared with the proposed DLPS (UC4Win). In [ 36 ] the authors reveal some of the problems faced by DRM systems as a document security solution, expose that they are difficult or inapplicable to the organization’s IT infrastructure and that they rely on certain plugins and these plugins may be used.
2.3 DLPS in the literature
Table 1 summarizes the contributions of the works found in the literature focused on the development and implementation of DLPS, as well as the techniques and technologies employed.
3 Methods to address the Insider threat
The main concern of recent times, in information security, is the internal threat posed by employees, partners, and collaborators of the organizations originating confidential information. One of the main measures adopted in the literature is the control of information use, which goes beyond access control [ 35 ] allowing to restrict operations that allow data leakage of confidential information and to regulate its use.
The authors of [ 54 ] highlight the importance of strengthening the security of the confidential document management system in the face of the threat of company employees to confidential information; to address this situation, they propose a security model for confidential documents with a distribution control strategy. The first is based on storing the content encrypted with a symmetric encryption algorithm, ensuring that only the authorized user is able to decrypt the content; access control information is stored that allows to know the degree of authority of the user to use such confidential information and records each operation that the user performs; in addition, a hash function is used to ensure the integrity of the content. To control the distribution of confidential information, a client-server strategy is used in which a client will not be able to distribute confidential documentation without permission from the server, in which the control policies defined by the administrator are used and a monitor is installed on the client’s computer that allows the server to control the operations performed by the user and prohibit unauthorized operations.
In the study [ 35 ] a DLPS based on usage control and dynamic data flow monitoring (UC4Win) is presented. This system can to monitor process calls to the Windows API in order to prevent or modify data flows that pose a threat of confidential information leakage.
In [ 55 ] a scheme based on mandatory kernel-level encryption on write operation and decryption on open operation is proposed through middleware to ensure that data remain encrypted in memory. In addition, usage control policies are established, such as read-only, save, export, write, backup, and impression rights. For access control, a method of mutual authentication and key agreement between client and server is proposed, using the SM2 algorithm for its management.
In [ 26 ] an approach is presented to control the use of confidential documentation, through the capture of biometric signals from users who interact with the object (document), correlating this information with the content accessed by users, without storing biometric information, but the correlation between the two. In this way, when a loss of information occurs, the organization will be able to know which user accessed the information, minimizing the risk of an attack on the biometric data.
The authors of [ 23 ] propose a DLPS based on widows file system mini-filters to control the use of classified documentation by controlling OS I/O operations. The proposed system will block I/O operations from any external storage device. In addition, a strategy is adopted to restrict the movement of classified information by adding the process that performs the read request on the path where the classified information is stored to a blacklist and blocking subsequent write attempts from that process.
The authors of [ 56 ] propose a Document Semantic Signature (DSS) approach to address the insider threat. To obtain the DSS, the content of a document is extracted and summarized, updating the DSS dynamically whenever the information is modified. The DLPS monitors the newly generated information by tracking its transfer or exfiltration by comparing the DSS of such information and the DSS of sensitive information. The study takes into account the possibility that an employee with access to confidential information can change the content using synonyms to evade the DLPS, which is based on keyword-based leak detection, and the proposed system addresses this problem. The system was tested with a public dataset achieving encouraging results.
In the study conducted by the authors of [ 57 ], a prototype of an anti-leakage system based on the enterprise cloud is presented. The system uses keyword-based content monitoring and filtering techniques. Once the keywords, which represent confidential information in a document to be sent, are detected, the user and the network administrator are alerted of the possible data leakage, and a trace is left in a log where the incidence is written.
In [ 27 ] it is proposed to use eye tracking technology for information protection. This technology allows obtaining user behavior information such as gaze location, gaze tracking, and points of interest. This technology in information security can be used to identify the user interacting with confidential information through biometric eye data, obtain metadata of the user performing operations of creating, sending, modifying, and receiving confidential information for use in cases of conflicts detected by the DLP system, in addition it can serve to improve the security and integrity of documents based on the information of which parts of the document are of greatest interest to the user.
The authors of the study [ 25 ] propose as a solution to the internal threat a free DLPS that is based on detecting confidential information at the exit of the USB ports by means of automatic learning and blocks the copy operation, for this purpose it integrates modules in the kernel space (minifilters). The system is developed for the Windows OS as it is the most widely distributed in business environments.
The study [ 1 ] focuses on the insider threat that can be intentionally caused by an employee, for this, they propose “Efficient DLP-Visor” which is a context-based DLPS. The system is a thin hypervisor that intercepts call in kernel space. The proposed DLPS makes it possible to detect data leaks even though the employee in question is the system administrator himself. Basically, the System works as follows: The administrator sets a File System path where sensitive information is stored, the DLPS logs any process that opens or reads a document from that path as critical, and any file written by that process is logged as sensitive, as well as any process that receives information from a critical process. DLPS tracks critical processes by capturing kernel mode calls and blocks the relevant operations of those processes.
In [ 3 ] and [ 21 ] a DLPS for the protection of confidential information is proposed. The proposed system allows access control, through the development of the encryption key, through the combination of a set of parameters; these parameters can be biometric identification of the user accessing the information, geographic location, electronic fingerprint of the device, date, and time, among others. Although this proposal does not specifically present usage control, it is robust due to the ability to require several parameters to generate the decryption key, thus ensuring that the content remains encrypted as long as the established criteria are not met, since the key is never stored.
It has also been seen in the results obtained that DRM tools are based on the control of copies of protected information and therefore gain value for the control of use and protection of information from the threat of collaborators and partners. The proposal of [ 33 ] and [ 32 ] allows the implementation of an information system independent of the servers containing the control policies that were necessary to access with conventional systems. It controls the use and access to the document through a license (document xml apart from the confidential information) containing the security rules and the configuration of the various security modules necessary for the management of the document. The rules are encrypted by means of public and private keys stored and known by the user.
The authors of [ 58 ] analyze three models of traditional document security management, exposing the limitations of each of them, and to try to overcome them they propose a system based on storage in the private enterprise cloud, with a system of authorization and encryption of documents in a virtual machine that encrypts all the document that is written in it, as well as light clients with a common terminal in the virtual machine that will guarantee that all written documents are encrypted and to decrypt them will have to be done through the same encryption system that will guarantee that the user leaves a trace of the operation carried out. External users will need an electronic certificate to decrypt the document.
In [ 36 ] the main problems of different solutions for information protection within an organization are identified, among which DLP and DRM solutions are described. A solution based on active documents and DRM is proposed that allows the control of document usage, mainly copy, paste, cut, delete, and print operations, inside and outside the organization of origin. The transfer channels considered in this work were removable storage, e-mails, and shared folders. This work does not implement the system, but proposes an idea on how to solve the problem of data leakage with active documents.
Given the persistent concern in organizations and enterprises regarding the internal threat to data leakage protection, it has attracted the interest of the research community in an attempt to circumvent it. The recent study conducted in [ 59 ], presents a system CITD for the detection of insider threats based on the behavior of workers according to their role and machine learning. The system was tested in three real organizations to reduce false positives that allow improvements in the tool.
4 Methodology
This paper utilizes the Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) method [ 60 ] in a literature review to analyze existing techniques and technologies for DLP focused on electronic document and classified information leakage. Three stages of PRISMA application are shown in this study: literature search; selection of relevant articles; and data extraction.
4.1 Literature search
For this research, the search was focused on articles related to the techniques and technologies used for DLP published in impact journals, conference articles, and book section, mainly in scientific databases such as Google Scholar, Science Direct, IEEE Xplore, Web of Science, Scopus and ACM Digital Library, from 2011 to April 2022, these databases cover relevant scientific information in multiple engineering fields, allowing access to articles published in scientific and academic journals, repositories, archives and other collections of scientific texts.

Search criteria in different databases
The following keywords were used for the literature search: “Security” AND (“DLP” OR (“Data AND (“Leak” OR “Loss”) AND (“Prevention OR Protection”). These terms are searched in Abstract/Title/Keywords from 2011 to 2022. Figure 1 shows the search strategy used in this research, the search criteria used are provided by the search engine of each of the scientific databases.
4.2 Study selection and relevant papers
Once the terms have been entered in the search engines of the databases, the articles to be analyzed are selected by reading the titles of the results obtained (in this case 158). Repeated entries in more than one database were eliminated (56 articles). Selection criteria were applied in the analysis of the abstracts of 102 articles to classify those that were completely analyzed, the selection criteria were as follows: (1) Studies of novel proposals of techniques and technologies for DLP. (2) Studies of analysis of techniques and technologies for DLP; 65 articles were obtained for complete analysis, then those studies aimed at systems for malware and rootkit protection, image cryptography and steganography were eliminated, as well as reviews of techniques and technologies since they are related works to this, but not relevant to the analysis. A total of 42 articles remained for analysis.
The procedure described is shown in in Fig. 2 the PRISMA diagram, where the paper selection process can be seen and how, out of a total of 158 papers found, a total of 42 papers papers were relevant for analysis in this paper.
PRISMA Methodology
5 Discussion of results
This section discusses the results, after applying the above methodology, classifying the relevant studies according to year and type of publication, analyzing the number of relevant publications for each year reviewed and their origin, to determine where the greatest dissemination of the topic in question is to be found. We analyze the use of the main techniques in DLPS, discuss their limitations, advances and applications according to the reviewed literature.
5.1 Classification according to year and type of publication
Figure 3 shows the frequency of publications by year of the relevant studies found during the period 2011–2022. It is observed that the year 2019 reaches the highest number of publications in this period. In general, the number of papers published per year ranges from 1 to 8 with a statistical mode of 3 and a mean of 4 approximately, which means that in the years 2011 and 2019 the mean was exceeded. We can appreciate that approximately 60% of the relevant articles for this study were found in the period between 2017 and 2022, which shows a significant interest in recent years in the security of sensitive digital information. Figure 4 shows the number of published papers according to their origin, it is observed that 60% of the relevant papers come from congresses and approximately 30% of them from journals, demonstrating the deep interest in the academic field for protection against data leakage.

Frequency of papers published per year

Paper / Article source
5.2 Analysis of the use of the main techniques and technologies in DLPS
Figure 5 shows the most frequently used techniques in the literature. It can be seen that among the most used is cryptography with 40% of use and ML is present in 12% of the articles studied, being evident the progress of DLPS in the use of this technique for the classification of sensitive documentation. Others, such as hypervisor, biometric information capture, and intelligent documents, are present in 10% of the 42 relevant papers to this study. In the literature it has been seen that these techniques and technologies are widely used in combination with each other, For example, in systems where mini-filters and VFS or middleware are used, documents are often encrypted for storage in memory. Also, when active documents are used, hash algorithms are incorporated to guarantee the integrity of the information, as well as ML to classify the information according to the degree of confidentiality to apply security and access policies accordingly. In DLPS, these and other techniques used as a complement can undoubtedly guarantee maximum security to confidential information.
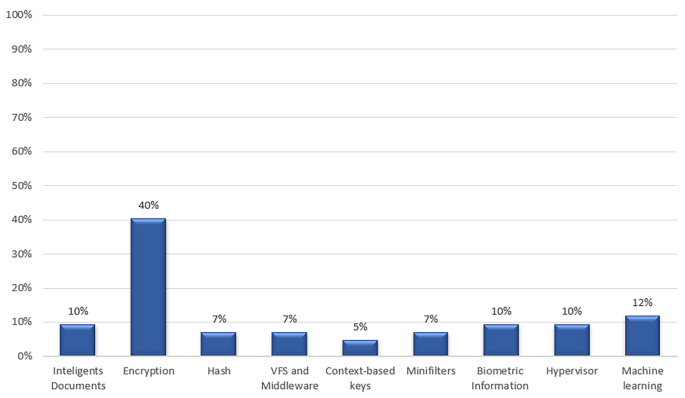
Percentage of use of the most frequent techniques and technologies
5.3 Limitations, advances, and applications
Limitations that have emerged over the years are the almost complete dependence on the quality of the security policies used and the precise definition of the data to be protected, as well as the necessary over-approaches in the dynamic monitoring of the data flow [ 35 ]. In [ 36 ] four challenges facing document security are identified, one of them being human negligence, DLPS are not able to overcome this challenge since as a means of security they rely on user, password and security policies to ensure the security of information, without taking into account that the user himself may be the one who provides the data leakage, they themselves are the tools to perform the security policy of any organization so a user and password is not enough. The tracking of unmarked documents [ 37 ] or not classified as confidential also represented a major limitation in the DLPS at the time.
Some of these problems have already been solved with the incorporation of new techniques and technologies to DLPS, such as ML for document classification, the recent study [ 61 ] proposes a multilayer framework for insider threat detection based on a hybrid method composed of two predictive models with an accuracy level higher than 97%, another application of ML in data protection are network intrusion detection systems, which can be seen in studies [ 62 ], [ 63 ], [ 64 ]. DRM systems for tracking sensitive information outside the organization, biometric information for user identification, and context-based keys to determine the date, place and time of information access. An important advance is the incorporation of blockchain to protect the DLPS logs where the information of detected anomalies is stored, storing these DLPS logs in the Hyperledger Fabric ledger in real time, thus preventing the manipulation of these logs by authorized users to try to eliminate evidence of data leakage [ 65 ].
In terms of DLPS applications, the studies reviewed focus on the security of sensitive information at the enterprise level and as such, most of the trends and developments lean in this area. However, the authors of [ 21 ] propose a DLP solution using context-based encryption to prevent information leakage in drones. In the poster [ 66 ] the authors propose a data leak detection tool for a health information system based on memory introspection. A recent study proposes a blockchain-based architecture that allows the secure transfer of electronic health records between different health care systems, verifying the integrity and consistency of requests and responses to electronic health records [ 67 ].
6 Conclusions
This research focuses on a literature survey where a total of 42 relevant studies were obtained. The survey allowed answering three research questions that met the objective proposed in this study. A deep interest in evading insider threat was detected in more than 40% of the analyzed studies. In addition, it is given that the DLPS with the highest incidence in this regard have access control and control of the use of confidential information by controlling the operations that allow data leakage (copy, opening, writing and reading), as well as policies of privacy. DRM for the case of partners and collaborators. These tools mainly use biometric information capture techniques, interception of calls in kernel space using hypervisor, VFS, middleware, and mini-filters. As well as security policies encapsulated in documents. In the analysis of the techniques and technologies that are the most used, We found the encryption technique with 40% use in the studies analyzed.
Significant progress is seen in DLP tools with the incorporation of techniques such as ML for the classification of sensitive information and detection of anomalous activity, in addition to blockchain for the protection of DLPS records. No article was found in the literature that provides the open access code of DLPS for reuse and improvement by other researchers. Few studies focused on data security in the healthcare sector and only one applying DLP on the Internet of Things (IoT) was found in the search results.That is why we propose as future lines of work to carry out studies on the security and protection of the electronic health record, as well as the development and implementation of a DLPS focused on the insider threat, based on the experience of the works found that meet the requirements of being lightweight, unobtrusive, where access to information does not depend on user data and saved passwords, with free access to the source code so that other researchers can adapt it to their needs and provide validations and improvements. To this end, we propose to carry out a study of the techniques and technologies that allow the development of virtual file systems, for the implementation of a secure file system as a DLP tool. As well as, the study of lightweight encryption and decryption algorithms suitable for the needs of a virtual file system. Another line of research that DLPS intends to adopt is its application to IoT, since this technology is advancing every day and most of them are high collectors of personal data.
Data Availability
Not required in the review article.
Kiperberg, M., Amit, G., Yeshooroon, A., Zaidenberg, N.J.: Efficient DLP-visor: An efficient hypervisor-based DLP. In: 2021 IEEE/ACM 21st International Symposium on Cluster, Cloud and Internet Computing (CCGrid). pp. 344–355. IEEE (2021)
Alneyadi, S., Sithirasenan, E., Muthukkumarasamy, V.: A survey on data leakage prevention systems. J. Netw. Comput. Appl. 62 , 137–152 (2016). https://doi.org/10.1016/j.jnca.2016.01.008
Article MATH Google Scholar
Holgado, P., García, A., García, J.J., Roncero, J., Villagrá, V.A., Jalain, H.: Context-based Encryption Applied to Data Leakage Prevention Solutions. In: Proceedings of the 14th International Joint Conference on e-Business and Telecommunications. pp. 566–571. SCITEPRESS - Science and Technology Publications (2017)
Morrow, B.: BYOD security challenges: Control and protect your most sensitive data. Network Security. 5–8 (2012). (2012). https://doi.org/10.1016/S1353-4858(12)70111-3
Barlette, Y., Jaouen, A., Baillette, P.: Bring Your Own Device (BYOD) as reversed IT adoption: Insights into managers’ coping strategies. Int. J. Inform. Manage. 56 , 102212 (2021). https://doi.org/10.1016/j.ijinfomgt.2020.102212
Article Google Scholar
Raj, S.R., Cherian, A., Abraham, A.: A Survey on Data Loss prevention Techniques. Int. J. Sci. Res. 2 , 2319–7064 (2013)
Google Scholar
Meizlik, D.: The ROI of Data Loss Prevention (DLP). (2008)
Brook, C.: DATAINSIDER Digital Guardian’s Blog, https://digitalguardian.com/blog/whats-cost-data-breach-2019
CCN-CERT: Ciberamenazas y Tendencias Edición 2017 CCN-CERT IA-16/17. In: Centro Criptológico Nacional de España. p. 86: (2017)
Zeng, W., Van Moorsel, A.: Quantitative Evaluation of Enterprise DRM Technology. Electronic Notes in Theoretical Computer Science. 275, 159–174 (2011). https://doi.org/10.1016/j.entcs.2011.09.011
Ab Rahman, N.H., Choo, K.-K.R.: A survey of information security incident handling in the cloud. Computers & Security. 49 , 45–69 (2015). https://doi.org/10.1016/j.cose.2014.11.006
Alonso, S.G., Arambarri, J., López-Coronado, M., de la Torre Díez, I.: Proposing New Blockchain Challenges in eHealth. J. Med. Syst. 43 , 64 (2019). https://doi.org/10.1007/s10916-019-1195-7
Georgiadis, G., Poels, G.: Enterprise architecture management as a solution for addressing general data protection regulation requirements in a big data context: a systematic mapping study. Springer, Berlin Heidelberg (2021)
Palazov, A.: Some Technologies for Information Security Protection in Weak-Controlled Computer Systems and Their Applicability for eGovernment Services Users. In: Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics). pp. 117–122 (2011)
Hu, C., Chen, F., Zheng, H.: Researches on the Security Protection and Inspection Method for Confidential Documents Based on Linux Operating System. In: Proceedings of the 3rd International Conference on Machine Learning and Soft Computing - ICMLSC 2019. pp. 249–252. ACM Press, New York, New York, USA (2019)
Soomro, Z.A., Shah, M.H., Ahmed, J.: Information security management needs more holistic approach: A literature review. Int. J. Inform. Manage. 36 , 215–225 (2016). https://doi.org/10.1016/j.ijinfomgt.2015.11.009
Kayode, A.B., Dayo, A.O., Uthman, A.A.: A Review on Distribution Model for Mobile Agent-Based Information Leakage Prevention. Commun. Netw. 13 , 68–78 (2021). https://doi.org/10.4236/cn.2021.132006
Leng, J., Zhou, M., Zhao, J.L., Huang, Y., Bian, Y.: Blockchain Security: A Survey of Techniques and Research Directions. IEEE Trans. Serv. Comput. 1–1 (2021). https://doi.org/10.1109/TSC.2020.3038641
Leng, J., Ye, S., Zhou, M., Zhao, J.L., Liu, Q., Guo, W., Cao, W., Fu, L.: Blockchain-Secured Smart Manufacturing in Industry 4.0: A Survey. IEEE Trans. Syst. Man Cybernetics: Syst. 51 , 237–252 (2021). https://doi.org/10.1109/TSMC.2020.3040789
Husham Ali, B., Jalal, A.A., Al-Obaydy Al-Obaydy, W.N.I.: Data loss prevention (DLP) by using MRSH-v2 algorithm. Int. J. Electr. Comput. Eng. (IJECE). 10 , 3615 (2020). https://doi.org/10.11591/ijece.v10i4.pp3615-3622
Garcia, A., Holgado, P., Garcia, J.J., Roncero, J., Villagrá, V., Jalain, H.: Sistema de cifrado basado en contexto aplicado a prevención de fuga de datos. In: Proceedings XIII Jornadas de Ingenieria Telematica - JITEL2017. pp. 93–100. Universitat Politècnica València, Valencia (2017)
Garcia Aranda, J.J.A.: EP 2 709 333 A1 EUROPEAN PATENT APPLICATION, (2014)
Buda, A., Colesa, A.: File System Minifilter Based Data Leakage Prevention System. In: 2018 17th RoEduNet Conference: Networking in Education and Research (RoEduNet). pp. 1–6. IEEE (2018)
Porízek*, D.: Transparent Encryption with Windows Minifilter Driver. (2019)
Thombre, S.: Freeware Solution for Preventing Data Leakage by Insider for Windows Framework. International Conference on Computational Performance Evaluation, ComPE 2020. 44–47 (2020). (2020). https://doi.org/10.1109/ComPE49325.2020.9200160
Alruban, A., Clarke, N., Li, F., Furnell, S.: Biometrically Linking Document Leakage to the Individuals Responsible. In: Furnell S., Mouratidis H., Pernul G. (eds) Trust, Privacy and Security in Digital Business. pp. 135–149 (2018)
Shokishalov, Z., Wang, H.: Applying Eye Tracking in Information Security. Procedia Comput. Sci. 150 , 347–351 (2019). https://doi.org/10.1016/j.procs.2019.02.062
Catuogno, L., Galdi, C., Riccio, D.: Off-line enterprise rights management leveraging biometric key binding and secure hardware. J. Ambient Intell. Humaniz. Comput. 10 , 2883–2894 (2019). https://doi.org/10.1007/s12652-018-1023-9
Vojnak, D.T., Eordevic, B.S., Timcenko, V.V., Strbac, S.M.: Performance Comparison of the type-2 hypervisor VirtualBox and VMWare Workstation. In: 2019 27th Telecommunications Forum (TELFOR). pp. 1–4. IEEE (2019)
Subramanya, S.R., Yi, B.K.: Digital rights management. IEEE Potentials. 25 , 31–34 (2006). https://doi.org/10.1109/MP.2006.1649008
Reddy, R.S.C., Gopu, S.R.: Enterprise Digital Rights Management for Document Protection. In: 2017 31st International Conference on Advanced Information Networking and Applications Workshops (WAINA). pp. 321–326. IEEE (2017)
Munier, M., Lalanne, V., Ricarde, M.: Self-protecting documents for cloud storage security. In: Proc. of the 11th IEEE Int. Conference on Trust, Security and Privacy in Computing and Communications, TrustCom-2012. pp. 1231–1238. IEEE (2012)
Munier, M.: A Secure Autonomous Document Architecture for Enterprise Digital Right Management. In: 2011 Seventh International Conference on Signal Image Technology & Internet-Based Systems. pp. 16–23. IEEE (2011)
Guri, M., Puzis, R., Choo, K.-K.R., Rubinshtein, S., Kedma, G., Elovici, Y.: Using malware for the greater good: Mitigating data leakage. J. Netw. Comput. Appl. 145 , 102405 (2019). https://doi.org/10.1016/j.jnca.2019.07.006
Wuchner, T., Pretschner, A.: Data Loss Prevention Based on Data-Driven Usage Control. In: 2012 IEEE 23rd International Symposium on Software Reliability Engineering. pp. 151–160. IEEE (2012)
Aaber, Z.S., Crowder, R.M., Fadhel, N.F., Wills, G.B.: Preventing document leakage through active document. In: 2014 World Congress on Internet Security, WorldCIS 2014. pp.53–58.Infonomics Society(2014)
Zhu, D.Y., Berkeley, U.C., Song, D., Wetherall, D.: TaintEraser: Protecting Sensitive Data Leaks Using Application-Level Taint Tracking. In: ACM SIGOPS Operating Systems Review. pp. 142–154 (2011)
Zhang, N., Jing, J., Liu, P.: CLOUD SHREDDER: Removing the Laptop On-road Data Disclosure Threat in the Cloud Computing Era. In: 2011IEEE 10th International Conference on Trust, Security and Privacy in Computing and Communications. pp. 1592–1599. IEEE (2011)
Omote, Y., Chubachi, Y., Shinagawa, T.: Hypervisor-based Background Encryption. In: 27th Annual ACM Symposium on Applied Computing. pp. 1829–1836 (2012)
Wang, J., Yu, M., Li, B., Qi, Z., Guan, H.: Hypervisor-based protection of sensitive files in a compromised system. In: 27th Annual ACM Symposium on Applied Computing. pp. 1765–1770 (2012)
Topaloglu, M., Ucar, E., Umut, I.: AWERProcedia Information Technology & Computer Science Architectural Design and Realization for Management of end Point. 03, 167–172 (2013)
Koutsourelis, D., Katsikas, S.K.: Designing and developing a free Data Loss Prevention system. In: Proceedings of the 18th Panhellenic Conference on Informatics - PCI ’14. pp. 1–5. ACM Press, New York, New York, USA (2014)
Allawi, M.A.A., Hadi, A., Awajan, A.: MLDED: Multi-layer Data Exfiltration Detection System. In: 2015 Fourth International Conference on Cyber Security, Cyber Warfare, and Digital Forensic (CyberSec). pp. 107–112. IEEE (2015)
Yin, J., Yang, J., Chen, Y.: The Design and Implementation of User Autonomous Encryption Cloud Storage System Based on Dokan. In: Proceedings of the 2016 International Conference on Computer Science and Electronic Technology. pp. 917–928. Atlantis Press, Paris, France (2016)
Burg, S., Channakeshava, P., Bringmann, O.: Linebased end-to-display encryption for secure documents. In: 2016 IEEE International Conference on Identity, Security and Behavior Analysis (ISBA). pp. 1–6. IEEE (2016)
Riccio, D., Galdi, C., Manzo, R.: Biometric/Cryptographic Keys Binding Based on Function Minimization. In: 2016 12th International Conference on Signal-Image Technology & Internet-Based Systems (SITIS). pp. 144–150. IEEE (2016)
Chang, S.-H., Mallissery, S., Hsieh, C.-H., Wu, Y.-S.: Hypervisor-Based Sensitive Data Leakage Detector. In: 2018 IEEE International Conference on Software Quality, Reliability and Security (QRS). pp. 155–162. IEEE (2018)
Anitha Ruth, J., Sirmathi, H., Meenakshi, A.: Secure data storage and intrusion detection in the cloud using MANN and dual encryption through various attacks. IET Inform. Secur. 13 , 321–329 (2019). https://doi.org/10.1049/iet-ifs.2018.5295
Divya, S.V., Shaji, R.S., Venkadesh, P., A COMBINED DATA STORAGE WITH ENCRYPTION, AND KEYWORD BASED DATA RETRIEVAL USING SCDS-TM MODEL IN CLOUD: Malaysian J. Comput. Sci. 32 , 163–185 (2019). https://doi.org/10.22452/mjcs.vol32no3.1
Dhanuja, B., Prabadevi, B., Bhavani Shankari, K., Sathiya, G.: E-REA Symmetric Key Cryptographic Technique. In: 2020 International Conference on Emerging Trends in Information Technology and Engineering (ic-ETITE). pp. 1–8. IEEE (2020)
Gupta, K., Kush, A.: A Forecasting-Based DLP Approach for Data Security. Presented at the (2021)
Fugkeaw, S., Worapaluk, K., Tuekla, A., Namkeatsakul, S.: Design and Development of a Dynamic and Efficient PII Data Loss Prevention System. In: Communications and Network. pp. 23–33 (2021)
Ahmad, S., Mehfuz, S., Beg, J.: Cloud security framework and key management services collectively for implementing DLP and IRM. Materials Today: Proceedings. (2022). https://doi.org/10.1016/j.matpr.2022.03.420
Zheng, S., Liu, J.: A global strategy for controlling document distribution in confidential document management system. In: 2011 IEEE 3rd International Conference on Communication Software and Networks. pp. 410–415. IEEE (2011)
Ma, Z.: CPSec DLP: Kernel-Level Content Protection Security System of Data Leakage Prevention. Chin. J. Electron. 26 , 827–836 (2017). https://doi.org/10.1049/cje.2017.05.002
Alhindi, H., Traore, I., Woungang, I.: Data Loss Prevention Using Document Semantic Signature. In: Lecture Notes on Data Engineering and Communications Technologies. pp. 75–99 (2019)
Chen, Z., Wang, J., Yang, Y., Yang, G., Wen, L., Chen, L.: Research on Key Technology of Enterprise Private Cloud Anti-Leakage. In: 2019 International Conference on Intelligent Computing, Automation and Systems (ICICAS). pp. 829–834. IEEE (2019)
Liu, N.: Cloud Technology in the Security Management of Enterprise Document. In: 2011 Second International Conference on Innovations in Bio-inspired Computing and Applications. pp. 267–269. IEEE (2011)
Erola, A., Agrafiotis, I., Goldsmith, M., Creese, S.: Insider-threat detection: Lessons from deploying the CITD tool in three multinational organisations. J. Inform. Secur. Appl. 67 , 103167 (2022). https://doi.org/10.1016/j.jisa.2022.103167
Moher, D., Liberati, A., Tetzlaff, J., Altman, D.G.: Preferred reporting items for systematic reviews and meta-analyses: the PRISMA statement. BMJ. 339 , b2535–b2535 (2009). https://doi.org/10.1136/bmj.b2535
Al-Mhiqani, M.N., Ahmad, R., Abidin, Z.Z., Abdulkareem, K.H., Mohammed, M.A., Gupta, D., Shankar, K.: A new intelligent multilayer framework for insider threat detection. Computers & Electrical Engineering. 97 , 107597 (2022). https://doi.org/10.1016/j.compeleceng.2021.107597
Awan, M.J., Masood, O.A., Mohammed, M.A., Yasin, A., Zain, A.M., Damaševičius, R., Abdulkareem, K.H.: Image-Based Malware Classification Using VGG19 Network and Spatial Convolutional Attention. Electronics. 10 , 2444 (2021). https://doi.org/10.3390/electronics10192444
Khalaf, B.A., Mostafa, S.A., Mustapha, A., Mohammed, M.A., Mahmoud, M.A., Al-Rimy, B.A.S., Abd Razak, S., Elhoseny, M., Marks, A.: An Adaptive Protection of Flooding Attacks Model for Complex Network Environments. Security and Communication Networks. 1–17 (2021). (2021). https://doi.org/10.1155/2021/5542919
Azizan, A.H., Mostafa, S.A., Mustapha, A., Foozy, C.F.M., Wahab, M.H.A., Mohammed, M.A., Khalaf, B.A.: A Machine Learning Approach for Improving the Performance of Network Intrusion Detection Systems. Annals of Emerging Technologies in Computing. 5 , 201–208 (2021). https://doi.org/10.33166/AETiC.2021.05.025
Lee, G., Son, M., Choi, N., Hong, S., Kim, H.: Blockchain based Removable Storage Device Log Management System. In: 2020 22nd International Conference on Advanced Communication Technology (ICACT). pp. 276–279. IEEE (2020)
Mallissery, S., Wu, M.-C., Bau, C.-A., Huang, G.-Z., Yang, C.-Y., Lin, W.-C., Wu, Y.-S.: POSTER: Data Leakage Detection for Health Information System based on Memory Introspection. In: Proceedings of the 15th ACM Asia Conference on Computer and Communications Security. pp. 898–900. ACM, New York, NY, USA (2020)
Ajayi, O., Abouali, M., Saadawi, T.: Blockchain architecture for secured inter-healthcare electronic health records exchange. Adv. Intell. Syst. Comput. 1263 AISC. 161–172 (2021). https://doi.org/10.1007/978-3-030-57796-4_16
Download references
Acknowledgements
This research has been carried out in a collaborative stay between the Telemedicine and e-Health group of the University of Valladolid and the Instituto da Telecomunicações da Delegação da Covilhã, Portugal. We thank Nokia Spain for the close collaboration to achieve successful results.
This research has been partially supported by the “Centro para el Desarrollo Tecnológico Industrial (CDTI)” of the Spanish Ministry of Science and Innovation in the framework of the project “Technologies for the security of digital relationships in a hyperconnected world (Secureworld)” number 18.IP.MJ. Authors: Mrs. Isabel Herrera Montano, Mr. José Javier García Aranda, Mr. Juan Ramos Diaz, Mr. Sergio Molina Cardín, Mrs. Isabel de la Torre Díez. It is also partially funded by the FCT/MCTES through national funds and, where appropriate, EU co-financed funds under project UIDB/50008/2020; and by the Brazilian National Council for Scientific and Technological Development - CNPq, through grant no. 313036/2020-9. Author: Prof. Joel J. P. C. Rodrigues. Open Access funding provided thanks to the CRUE-CSIC agreement with Springer Nature.
Author information
Authors and affiliations.
Department of Signal Theory and Communications and Telematics Engineering, University of Valladolid, Paseo de Belén, 15, 47011, Valladolid, Spain
Isabel Herrera Montano & Isabel de la Torre Díez
Department of Innovation, Nokia, Maria Tubau Street, 9, 28050, Madrid, Spain
José Javier García Aranda, Juan Ramos Diaz & Sergio Molina Cardín
College of Computer Science and Technology, China University of Petroleum (East China), 266555, Qingdao, China
Joel J. P. C. Rodrigues
Instituto de Telecomunicações, 6201-001, Covilhã, Portugal
You can also search for this author in PubMed Google Scholar
Contributions
All authors contributed to the conception and design of the study. The first draft of the manuscript was written by Isabel Herrera Montano and all authors commented on earlier versions of the manuscript. All authors read and approved the final manuscript.
Corresponding author
Correspondence to Isabel Herrera Montano .
Ethics declarations
Competing interests.
The authors have no relevant financial or non-financial interests to disclose.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Herrera Montano, I., García Aranda, J.J., Ramos Diaz, J. et al. Survey of Techniques on Data Leakage Protection and Methods to address the Insider threat. Cluster Comput 25 , 4289–4302 (2022). https://doi.org/10.1007/s10586-022-03668-2
Download citation
Received : 07 February 2022
Revised : 25 April 2022
Accepted : 21 June 2022
Published : 14 July 2022
Issue Date : December 2022
DOI : https://doi.org/10.1007/s10586-022-03668-2
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Data leak Protection
- Data leak Prevention
- Internal threat
- Classified Information Security
- Find a journal
- Publish with us
- Track your research

Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories

Data leakage detection ppt powerpoint presentation slides deck cpb
Our Data Leakage Detection Ppt Powerpoint Presentation Slides Deck Cpb are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.

- Add a user to your subscription for free
You must be logged in to download this presentation.
Do you want to remove this product from your favourites?
PowerPoint presentation slides
Presenting Data Leakage Detection Ppt Powerpoint Presentation Slides Deck Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Data Leakage Detection. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.

People who downloaded this PowerPoint presentation also viewed the following :
- Diagrams , Business , Strategy , Icons , Business Slides , Flat Designs , Circular Cycle Diagrams , Process Management
- Data Leakage Detection
Data leakage detection ppt powerpoint presentation slides deck cpb with all 2 slides:
Use our Data Leakage Detection Ppt Powerpoint Presentation Slides Deck Cpb to effectively help you save your valuable time. They are readymade to fit into any presentation structure.

Ratings and Reviews
by Damon Castro
November 10, 2021
by Curtis Herrera
by Daren Henry
by Duncan Berry
by Douglas Lane
April 13, 2021
by George Miller
by Clayton Sanders
by Dennis Stone

Can we help find anything?
No suggestions.
Suggested Searches
Popular Keyword
Search history, recommended search.
Select your province
*Based on your intended shipping destination/store pick-up location
Please confirm your selection. The page will be reloaded to display the corresponding prices.
We're here for you
Welcome to Samsung Support
Popular searches.
- Galaxy S9 - Insert a microSD Card or Remove it (SM-G960W)
- Which Canadian banks are supported on Samsung Pay?
- Can you wash tennis shoes or sneakers in your Samsung washer?
related search
- Live Translation
- Circle to Search
- How to find model number
- Samsung account
- Washer and Dryer
- Oven cleaning
- Refrigerator cleaning
Product Support
Select a model, how to find model code.
Need some help locating your model number? Select your product from the menus below and we'll show you where your number is.
It may be quicker to check for a solution here
Still can't find the answer you're looking for? Click next to e-mail us
How to enter the unlock code
Unlocking your Galaxy phone lets you use your device with a different provider and network. Disclaimer: When you purchase a Samsung phone from a carrier, your phone is locked to their network for a specified period of time according to the contract. You must contact your carrier to find out the conditions of your contract and obtain an unlock code.
Back up and restore your data
When you back up and restore your content using the storage options on your Galaxy device, you will be able to download the file again.
Update the phone number associated with your Samsung account
Please follow this process before updating to One UI 6.1 Your Samsung account holds a lot of important personal information, so it is protected with two-step verification. You'll receive a text message containing a code on your mobile device to confirm that it is you logging into the account. If your mobile number has changed, and you can't receive the text, you'll need to change the phone number on your account.
Find additional information
Setting up your galaxy device, warranty information, premium care service, screen replacement pricing, request repair service, buy authorized samsung parts, visual support, smartthings support, news & alerts, bespoke upgrade care, download manuals, sign language support, door to door repair service, samsung service: terms & conditions, windows information, samsung members community, maintenance mode, interactive tv simulator, protection & peace of mind, contact info, online support, call support.
1-800-SAMSUNG
Face to Face Support
Printers support.
The coding for Contact US > Call > View more function. And this text is only displayed on the editor page, please do not delet this component from Support Home. Thank you

IMAGES
VIDEO
COMMENTS
Data leakage prevention is one of the key topics which we have been talking in present. Due to the organizations moving towards big data, financial systems.. which resides in cyber space, there is an increasing number of frauds associated with the technology revolution in the cyberspace.This post highlights the threats and the counter measures, so we can protect the sensitive personal data.
What is Data Leakage? Data leakage is the occurrence of an organization inadvertently exposing sensitive information - usually due to a mistake like overlooking a critical vulnerability - to the public internet or unsecure networks. This process increases the chances that data will be taken by malicious actors.
A data leak occurs when sensitive, confidential, or protected information is inadvertently or intentionally disclosed to unauthorized individuals. Data leaks can take various forms, such as: Accidental sharing of sensitive information by employees. Misconfiguration of cloud storage or databases, leading to public exposure.
Data leakage refers to the unauthorized transfer of data from inside an organization to an external destination. It can involve all types of data, from non-sensitive and innocuous data to highly confidential information. The leakage may be intentional (as a result of malicious behavior) or unintentional (as a result of human error/lack of ...
Introducing our Data Leakage Icon With Digital Data And Lock Symbol set of slides. The topics discussed in these slides are Data Leakage, Icon Digital, Data Lock, Symbol. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience. Slide 1 of 2.
Companies that fail to protect their data are extremely prone to significant financial, legal, or reputational losses in the near future. Make use of our stunning Data Leakage slides, crafted to best fit with Microsoft PowerPoint and Google Slides presentations, to describe the transmission of the company's sensitive data to unauthorized parties.
Data Leakage Defined. Data leakage is the unauthorized transmission of data from within an organization to an external destination or recipient. The term can be used to describe data that is transferred electronically or physically. Data leakage threats usually occur via the web and email, but can also occur via mobile data storage devices such ...
Data leak prevention is a cybersecurity practice that involves implementing secure data practices to reduce accidental exposure. Effective data leak prevention plays a crucial role in a comprehensive data loss prevention strategy (DLP strategy).. Data leaks are an easy attack vector for cybercriminals. Exposed data, such as leaked credentials, allows unauthorized access to an organization's ...
What is DLP. Data Loss Prevention (DLP) is the practice of detecting and preventing data breaches, exfiltration, or unwanted destruction of sensitive data. Organizations use DLP to protect and secure their data and comply with regulations. The DLP term refers to defending organizations against both data loss and data leakage prevention.
Data loss prevention is a combination of people, processes, and technology that works to detect and prevent the leakage of sensitive data. A DLP solution uses things like antivirus software, AI, and machine learning to detect suspicious activities by comparing content to your organization's DLP policy, which defines how your organization labels, shares, and protects data without exposing it ...
We can help you with this by our ready-to-use Data Leakage PPT template, as it consists of all the information to understand the basic concept of data security and possible means of its leakage. Moreover, from visual elements to relevant content, everything is designed from scratch and proper research by our experts. Explore the Concept in Detail.
A data leak unintentionally exposes sensitive, protected, or confidential information outside its intended environment. This happens for various reasons, such as internal human errors, software vulnerabilities, or poor data security measures. Data leaks can compromise personal details, financial records, trade secrets, or other proprietary data ...
Slide 1 of 2. Data leakage icon with digital data and lock symbol. Slide 1 of 2. Data leakage ppt powerpoint presentation summary layouts cpb. Slide 1 of 2. Data leakage prevention policy ppt powerpoint presentation graphics cpb. Slide 1 of 6. Data Leakage Monotone Icon In Powerpoint Pptx Png And Editable Eps Format.
Lost or stolen laptops, USB storage devices, mobile phones, and other devices can result in major data leaks. Especially because more workers are now remotely accessing systems from various locations, these devices can become a doorway into an organization's network. 5. Software Vulnerabilities.
Data leakage is a problem that companies and organizations face every day around the world. Mainly the data leak caused by the internal threat posed by authorized personnel to manipulate confidential information. ... It is solved in Sections 2 and 5, giving a presentation of the main tools found in Section 2 and an analysis of their frequency ...
Presenting this set of slides with name Data Leakage Ppt Powerpoint Presentation Layouts Background Images Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Data Leakage to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent ...
Aug 2, 2014 • Download as PPTX, PDF •. 10 likes • 6,824 views. Mohit Pandey. somthing about data leakage detection. Engineering. 1 of 16. Download now. Data leakage detection - Download as a PDF or view online for free.
Presenting Data Leakage Detection Ppt Powerpoint Presentation Slides Deck Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content.
Back up and restore your data. When you back up and restore your content using the storage options on your Galaxy device, you will be able to download the file again. Read more . Update the phone number associated with your Samsung account . Please follow this process before updating to One UI 6.1