
An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
https://www.nist.gov/itl/smallbusinesscyber/nist-cybersecurity-fundamentals-presentation

Small Business Cybersecurity Corner
Nist cybersecurity fundamentals presentation.
Download the Slides
Managing a small business is always challenging but keeping up with cybersecurity threats can be overwhelming. How do you learn about the latest threats? How do you educate your staff about best practices? NIST has prepared a training presentation (draft) that you can use to self-teach and help your team learn at the same time. Please download the slides so you can use them at your convenience.
Each slide includes speaker’s notes – so you will be able to understand and share the material and find links to resources to learn more. You can go through the materials as quickly or slowly as you need, knowing that the recommendations come from the Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST).
The material is in sections: Cybersecurity Basics; Cybersecurity Threats; Risk Management; Cybersecurity Framework; and Small Business Cybersecurity Resources. You and your team will become familiar with common threats like phishing and ransomware, understand steps you can take every day to prevent falling victim and steps to take to recover should trouble strike.
We welcome your feedback on this draft presentation and will incorporate improvements in the future.
Cybersecurity Guide
Mastering the basics: A comprehensive guide to cybersecurity 101 for the digital age
- Notable attacks
Current challenges
- Future of cybersec industry
Our dependence on the internet, corporate networks, and digital devices have far exceeded what was even imaginable only a few decades ago.
Governments, corporations big and small, and individuals the world over rely on interconnected digital systems and technology for every aspect of their commerce, finance, and communication.
The challenge of securing personal information, intellectual property, and critical data has increased in parallel to our use of and dependence on technology.
Motivated by politics, social activism, or greed, threat actors reach to every corner of the globe to intercept, exfiltrate, or disrupt the ever-increasing flow of data. Even wars today are fought in cyberspace.
Cybersecurity has become a pervasive need. A rapid increase in threats against data systems and breaches of sensitive information has created a deficit of individuals qualified to devise and execute sufficient security controls.
There exists in the workforce today a recognized need for technically-capable people to join the ranks of cybersecurity professionals.
This guide is intended to provide an introduction to the field of cybersecurity.
Beginning with a few of the relevant terms and expressions used in the industry, some important security principles, and providing a brief historical overview; the following will give those considering a career in this practice a bird’s-eye sketch of what to expect.
Related resources
- Malware analyst careers: Your ultimate playbook
- Cybersecurity in the food and agriculture industry
- What to do after you have been hacked
- Cybersecurity in the transportation industry
- Cybersecurity guide for small business
Cybersecurity terms, principles, and history
Basic terminology.
To understand the vast world of cybersecurity or any technical field for that matter, the learner must master the words and phrases unique to that specialty.
These terms and expressions will often have a related, but not entirely accurate meaning in general non-technical use.
Without a clear understanding of how security professionals use certain words and phrases, learning about this specialty can be very confusing.
Many words routinely used in security have such obscure origins that it is difficult to use them correctly without an understanding of their history.
As an example, the term pwn, or pwned, is commonly used by hackers. To understand how threat actors use pwn, it is helpful to know that this word likely comes from a common mistyping of “own” as a result of the proximity of the letter P to the letter O on a keyboard.
The following definitions explain some of the terms, abbreviations, and acronyms commonly used in the security field.
- Attack surface: The attack surface of a software-based system is the sum of the different locations (logical or physical) where a threat actor can try to enter or extract data. Reducing the attack surface as small as possible is a primary security measure.
- AV: Antivirus is a type of security software that scans for, detects, blocks, and eliminates malware. AV programs will run in the background, scanning for known malware signatures and behavior patterns that may indicate the presence of malware.
- Brute-force attack: A brute force attack is an attempt to decipher a username-password combination by trial and error. It is performed with software designed to try large samples of known username-password combinations. This method is an old attack method, but it’s still useful and popular with hackers.
- Cryptoworm: A form of malware that spreads like a worm and encrypts victims’ data.
- Data breach: A data breach refers to a security event where unauthorized users steal sensitive information from an organization’s IT systems. Often, stolen data is personally identifiable information (PII) or financial information, both of which are valuable on the dark web.
- EDR: Endpoint detection and response is a type of security tool that focuses on detecting and mitigating suspicious activity on devices and hosts. The value of EDR is the ability to detect advanced threats that may not have a recorded behavioral pattern or malware signature.
- Firewall: A firewall is a network security system that monitors and controls the network traffic based on specific security rules. A firewall usually establishes a barrier between a trusted internal network and an untrusted external network, such as the Internet.
- Honeypot: A honeypot is a piece of software code designed to detect, deflect, and counteract attempts at unauthorized use of information systems. A honeypot consists of data appearing to be a legitimate part of the site but is isolated and monitored. The data seems to contain information, or a resource of value, to attackers, who are then blocked.
- IPS: An intrusion prevention system (IPS) is a form of network security that works to detect and prevent identified threats. Intrusion prevention systems continuously monitor a network, looking for possible malicious incidents, then capturing and reporting information about them.
- Malware: Malware is malicious software that propagates via an email attachment or a link to a malicious website. It infects the endpoints when a user opens the attachment or clicks on the link.
- NIST: The National Institute of Standards and Technology (NIST) is a non-regulatory entity under the umbrella of the United States Department of Commerce. NIST Publication Series 800 provides a comprehensive listing of information security measures and controls based on extensive research.
- Phishing/Spearphishing: A malicious email that tricks users into surrendering their user credentials. The email may appear legitimate as if coming from a bank and ask the user to reset their password. Phishing attacks take advantage of mass email programs. In a spearphishing attack, an individually-crafted email targets a specific key executive or decision-maker.
- Ransomware: Ransomware is a class of malicious software that prevents the end-user from accessing a system or data. The most common form is crypto-ransomware. This type of ransomware makes data or files unreadable through encryption and requires a decryption key to restore access. Another form, locker ransomware, locks access rather than encrypting data. Attackers typically request a payment, often in the form of bitcoins, to decrypt files or restore access.
- Ransomware attack: During a ransomware campaign, hackers often use phishing and social engineering to get a computer user to click on an attachment or a link to a malicious website. Some types of ransomware attacks, however, don’t require user action because they exploit site or computer vulnerabilities to deliver the payload. Once a system is infected, the attack will launch an on-screen notification with the ransom demand.
- Risk management framework: A Risk Management Framework provides a disciplined and structured process that integrates information security and risk management tasks into the system development life cycle. Essential components of an RMF include identification, measurement and assessment, mitigation, reporting and monitoring, and governance.
- Security misconfigurations: Security misconfigurations result from the improper implementation of security controls on devices, networks, cloud applications, firewalls, and other systems. They can lead to data breaches, unauthorized access, and other security incidents. Misconfigurations can include anything from default admin credentials, open ports, and unpatched software, to unused web pages and unprotected files.
- SOC: A security operations center (SOC) is a central location where cybersecurity personnel carry out threat detection and incident response processes. They employ security technologies that make up an organization’s security operations.
- SQL injection: A SQL injection is a technique that inserts structured query language (SQL) code into a web application database. Web applications use SQL to communicate with their databases. Attackers can use SQL injections to perform actions such as retrieval or manipulation of the database data, spoofing user identity, and executing remote commands.
- Tor : Tor is free and open-source software used to enable anonymous communication. Its name is derived from an acronym for the original software project name “The Onion Router” and is sometimes referred to as such. Tor directs Internet traffic through a free, worldwide, overlay network consisting of more than seven thousand relays. It conceals a user’s location and usage from anyone conducting network surveillance or traffic analysis.
- VA: Vulnerability assessment is the process of identifying, classifying, and prioritizing vulnerabilities in digital business systems. Assessments can focus on internal, external, or host-based vulnerabilities.
- VM: Vulnerability management solutions identify, track, and prioritize internal and external cybersecurity vulnerabilities. They optimize cyberattack prevention activities such as patching, upgrades, and configuration fixes.
Principles of cybersecurity
An effective cybersecurity program must adhere to a set of sound security principles. How these principles are implemented within each organization will vary, but the basic principles remain consistent. While each individual principle may be articulated differently for any given organization, governing cybersecurity policies should include a close variant of the following four concepts.
Identifying and managing security risks
Organizational security-related risks are identified and managed under the direction of a chief information security officer . This leader identifies and documents the value of systems, applications, and information owned or controlled by the organization. As directed by the CISO:
- The required confidentiality, integrity, and availability of systems, applications, and information is determined and documented.
- Security risk management processes are embedded in risk management frameworks applicable to the organization and its mission.
- Security risks are to be identified, documented, managed and accepted both before systems and applications are authorized for use, and continuously throughout their operational life.
Implementing security controls to reduce security risks
Security controls must be developed, acquired, and applied to protect the organization’s systems, applications, and information. Methods by which enforcement and compliance can be monitored and reported must be devised. Security controls, or processes, used to reduce risk include:
- Systems and applications are to be designed, deployed, and maintained according to their value. This value calculation should include the system’s confidentiality, integrity, and availability requirements.
- Systems and applications must be delivered and supported by trusted suppliers and configured to reduce their attack surface.
- Systems and applications must be administered in a secure, accountable, and auditable manner.
- Security vulnerabilities in systems and applications are identified and mitigated promptly.
- Only trusted and currently supported operating systems, applications, and computer code can execute on systems.
- Information is encrypted at rest and in transit between different systems.
- Information communicated between different systems is controlled, inspectable, and auditable.
- Information, applications, and configuration settings are backed up in a secure and proven manner regularly.
- Only trusted and recently vetted personnel are granted access to systems, applications, and data repositories.
- Personnel are granted the minimum access to systems, applications, and data repositories required for their duties.
- Multiple methods are used to identify and authenticate personnel to systems, applications, and data repositories.
- Personnel are provided with ongoing cybersecurity awareness training.
- Physical access to systems, supporting infrastructure, and facilities will be restricted to authorized personnel.
Detecting and understanding cybersecurity events
Security events and anomalous activities must be detected and analyzed promptly. Tools and applications used to achieve these policies include:
- Intrusion Prevention System (IPS)
- Endpoint Detection and Response Systems (EDR)
Responding to and recovering from cybersecurity incidents
In today’s business environment, the likelihood of a cyberattack is relatively high. Being prepared to respond and recover is paramount. Policies around this capability should include:
- Cybersecurity incidents must be identified and reported both internally and externally to relevant bodies promptly.
- Cybersecurity incidents are to be contained, eradicated, and recovered from immediately.
- Business continuity and disaster recovery plans are to be enacted when required.
A brief history of cybersecurity
Cyber attacks span back through history to the 1970s. In 1971 Digital Equipment Corporation’s DEC PDP-10 mainframe computers working on the TENEX operating system started displaying the message, “I’m the creeper, catch me if you can!” Dubbed Creeper , this worm spread using the ARPANET , a forerunner to the Internet. It was created by Bob Thomas and was designed only to see if the concept was possible. Creeper laid the groundwork for viruses to come.
In response to the Creeper virus, Ray Tomlinson created Reaper. Reaper was the first antivirus software and was designed to move across the ARPANET and delete the self-replicating Creeper worm.
In September of 1983, the first cybersecurity patent was granted. Massachusetts Institute of Technology (MIT) was awarded this patent for a “ cryptographic communications system and method .” It introduced the Rivest-Shamir-Adleman (RSA) algorithm . RSA is one of the first public-key cryptosystems and is widely used for secure data transmission.
In 1986 the Computer Fraud and Abuse Act (CFAA) was enacted to address hacking. It has been amended several times over the years to cover a broad range of conduct. The CFAA prohibits intentionally accessing a computer without prior authorization but fails to define what that means.
Also in 1986, Lawrence Berkeley National Laboratory systems manager Clifford Stoll learned that someone was hacking into the lab’s computer system. This discovery was made when Stoll tried to correct a 75-cent accounting error. Using a honeypot, Stoll determined that the lead hacker is Markus Hess , who had been selling information exfiltrated from hacked computers to the KGB. Hess and his accomplices were arrested by German authorities and convicted of selling stolen data to the Soviet Union. They only received suspended jail sentences.
In 1988 a Cornell University graduate student named Robert Morris released several dozen lines of code, which replicated wildly and spread to thousands of computers worldwide. The Morris Worm crashed about 10 percent of the 60,000 computers then linked to the Internet. Morris became the first person convicted by a jury under the CFAA.
Cybersecurity systems, as we think of them today, really started to become popular in the early 1990s. Antivirus (AV) software was the first mass-produced cyber protection application on the cyber landscape. They appeared in the late 1980s, but the masses did not convert to the idea that they were necessary for several years.
These first antivirus systems, initially called AV scanners , were simple in functionality. They essentially scanned all the compiled code on a given system. They tested them against a database of known malicious signatures. The thinking was that as new viruses were discovered, these databases would be updated to watch for the new malware.
Researchers soon found out, however, that staying ahead of the bad guys was no easy task. The number of malware samples to check against grew from tens of thousands in the early 90s to millions of new samples each year twenty years later. It is estimated that by 2014 as many as 500,000 unique malware samples were being produced every day.
These early software applications were resource-intensive and tended to bog down their host system. They also frustrated users with too many false-positive results.
Secure Sockets Layer (SSL) internet protocol is the security protocol that allows people to do simple things like purchase items online securely. Netscape released SSL 1.0 in 1994. After improvements, SSL became the core of the language for safely using the web known as Hypertext Transfer Protocol (HTTP).
In 1999, Kevin Mitnick pleaded guilty to four counts of wire fraud, two counts of computer fraud, and one count of illegally intercepting a wire communication. As the self-proclaimed world’s most famous hacker, he was sentenced to 46 months in prison plus 22 months for violating the terms of his supervised release sentence for computer fraud.
In his 2002 book entitled, The Art of Deception , Mitnick asserts that he compromised computers only by using user names and passwords that he gained by social engineering. He maintains he did not use software programs or hacking tools for cracking passwords or otherwise exploiting computer or phone security.
In 1998, Microsoft Windows 98 was released, and this ushered in a whole new level of accessibility for the novice computer user. This increase in computer usage paved the way for software security systems to become common. Many new releases, updates, and patches soon followed. Security vendors discovered the vast market for security products intended for home users.
In 2003 the first universally known hacker group, Anonymous , emerged on the scene. This group can be defined as a decentralized online community acting anonymously in a semi-coordinated manner, usually toward loosely self-agreed goals.
Over the years, dozens of people have been arrested for involvement in Anonymous cyberattacks around the world. Support of the group’s actions and effectiveness vary widely. Advocates have called the group freedom fighters and digital Robin Hoods.
In contrast, critics have described them as a cyber lynch-mob or cyber terrorists. In 2012, Time Magazine called Anonymous one of the 100 most influential people in the world.
In recent years, however, Anonymous’s media exposure has declined, and they have largely vanished from the popular culture’s lexicon.
The late 2000s brought a whole new level of cyber-attacks. Bad actors had developed an appetite for stolen credit cards. The years 2005 to 2007 were plagued with in ever-increasing frequency of data breaches.
To stem the flow of stolen data, governments around the world began to implement regulatory solutions. In the US regulation required that authorities be notified when a breach was discovered and that funds be set aside to compensate victims.
The increased regulation of the 2000s proved to be too little, too late. The sophistication of hackers spiked as the profits seemed limitless.
Even nation-sanctioned bad actors with access to enormous funding could be observed battling for cyber-turf and waring over such prizes as online betting or gaming sites.
This decade saw the appearance and rise of Endpoint Protection and Response systems (EPR) . The systems replaced the legacy AV systems by including the same basic functionality but are radically improved and enhanced.
Instead of relying on a static signature to identify viruses, EPR scan for malware families. Malware samples follow a progression or mutation and so they can effectively be recognized as belonging to certain families even when no known malware signatures are detected.
Notable cybersecurity attacks
Each year brings with it a new spate of cyberattacks. Some reported by the victims in compliance with ever-stiffening government regulations and some uncovered by Security analysts . Largely because of their news value, the size of reported high-profile attacks is undoubtedly trending upward.
Some attacks catch the publics’ attention because of the name recognition of the victim. In contrast, others swindle large segments of the general population. Below are a few of the more notable cyberattacks over the last decade-plus.
Adobe released information in October 2013 about the massive hacking of its IT infrastructure . Personal information of 2.9 million accounts was stolen.
Exfiltrated information included logins, passwords, names, and credit card numbers with expiration dates.
Another file discovered on the Internet later brought the number of accounts affected by the attack to 150 million. To access this information, the hackers took advantage of a security breach related to security practices around passwords.
Adult Friend Finder
In 2015, this dating site was attacked for the first time.
The information revealed included pseudonyms, dates of birth, postal codes, IP addresses, and sexual preferences of 4 million accounts.
This stolen data was made public on a forum only accessible on Tor. Malicious actors obtained these files; however, no banking data had been hijacked.
The following year, Adult Friend Finder faced a new attack, even more severe than the first one. This time more than 400 million files were exposed.
The stolen information was less sensitive, but in total, 20 years of personal information were taken.
This marketing analytics firm left an unsecured database online that publicly exposed sensitive information for about 123 million U.S. households .
The information included 248 fields of data for each home, ranging from addresses and income to ethnicity and personal interests.
Details included contact information, mortgage ownership, financial histories, and whether a household contained a pet enthusiast. Names were not included.
Equifax, an American credit company, revealed, six weeks after the fact, that it had suffered a cyberattack over the course of several months.
Detected in July of 2017, it contained personal data such as names, birthdates, social security numbers, and driver’s license numbers.
It also exposed 200,000 credit card numbers. Victims included 143 million American, Canadian, and British customers.
ILOVEYOU Virus
ILOVEYOU , sometimes referred to as Love Bug or Love Letter for you, is a computer worm that infected over ten million personal computers on and after May 2000.
It started circulating as an email message with the subject line “ILOVEYOU” and the attachment “LOVE-LETTER-FOR-YOU.
Personally identifiable information from up to 500 million guests at the Marriott-owned Starwood hotel group was compromised, beginning in 2014.
The rift was first detected in September 2018.
Data exfiltrated includes payment information, names, mailing addresses, phone numbers, email addresses, passport numbers, and even details about the Starwood Preferred Guest (SPG) account.
NotPeta Malware
Petya is a class of encrypting ransomware that was first discovered in 2016. The malware targets Microsoft Windows-based systems.
It infects the master boot record and executes a payload that encrypts a hard drive’s file system table and prevents Windows from booting. It subsequently demands that the user make a payment in Bitcoin to regain access to the system.
Variants of Petya were first seen in March 2016, which propagated via infected email attachments. In June 2017, a new variant of Petya was used for a global cyberattack targeting Ukraine.
The new variant spreads via the EternalBlue exploit, which was used earlier in the year by the WannaCry ransomware.
Kaspersky Lab referred to this latest version as NotPetya to distinguish it from the 2016 variants, due to these differences in operation. Although it claims to be ransomware, this variant was modified so that it is unable to revert its own changes and release the hard drive.
Sony’s PlayStation Network (PSN) was attacked in April 2011. This attack leaked the personal data of 77 million users. The banking information of tens of thousands of players was compromised.
After the intrusion discovery, PSN, as well as Sony Online Entertainment and Qriocity, were closed for one month. Unfortunately, in November 2014, a subsidiary, Sony Pictures Entertainment, was attacked by malware .
The “Guardians of Peace” stole 100 terabytes of data, including large quantities of confidential information such as film scripts, compromising emails, and personal data of 47,000 employees.
Target, the second-largest U.S. discount retail chain, was the victim of a massive cyberattack in December 2013.
Data was hijacked between November 27 and December 15 of that year. The information taken included bank card records of 40 million customers and personal data of another 70 million customers.
In March of 2007, TJX Companies (parent of TJ Maxx) confirmed with the Securities and Exchange Commission that it had been attacked.
A network intrusion carried out on its systems resulted in the loss of 45.7 million consumer records, making it the most significant such breach on record at that time.
WannaCry Ransomware Attack
The WannaCry ransomware attack was a May 2017 worldwide cyber-event.
This attack employed the WannaCry ransomware cryptoworm which targeted devices running the Microsoft Windows operating system. It encrypted data and demanded ransom payments.
It propagated through EternalBlue; an exploit developed by the United States National Security Agency (NSA) for older Windows systems. EternalBlue was stolen and leaked by a group called The Shadow Brokers a few months before the attack.
In 2014, Yahoo announced it had suffered a cyberattack that affected 500 million user accounts , constituting the most extensive hacking of individual data directed against a single company to that date.
Names, dates of birth, telephone numbers, and passwords were taken. It is now thought that as many as 3 billion user accounts may have been affected by this attack.
Attribution
In what many security researchers view as a victory, albeit a small one, the security industry has made substantial improvements in the ability to assign attribution for cyberattacks.
While attribution, per se, is still challenging to achieve, vast knowledge about the various current attack techniques , how they are deployed, and who uses them has been accumulated. This understanding allows researchers to make highly accurate educated guesses about the origins of an attack.
Knowing that security professionals are much better at attribution, the adversaries adapt. It is becoming more common for nation-state hackers and cybercriminals to try and imitate each other in an attempt to foil attribution efforts.
They also learn from each other to increase their capabilities. Primarily, however, their objectives remain different. Cybercriminals are generally more interested in money, while nation-state hackers are interested in stealing intellectual property and causing disruption.
While activism was once a prominent motivation for hackers, that has significantly subsided. Political and social cause activists use the Internet and modern communication tools to their great advantage but are less often seen interrupting services or exfiltrating data.
Today, we have reached the point at which cybercrime is so sophisticated that it seems nearly impossible to prevent. Scrutiny is placed on how an enterprise responds once breached – essentially a not “if” but “when” paradigm. Corporate leaders vie for the most talented chief information security officers .
These CISOs are focused mainly on organizational resiliency so they can appropriately manage events surrounding what is considered to be the inevitable data breach.
Organizations that would not have previously believed they needed a CISO are now hiring search firms to locate the best and the brightest. While the demand is high, they often require advanced infosec related degrees.
Across the board, security professionals are asked to increase their level of education, gain new skills, and hone their craft in response to the increased capabilities of their adversaries. Organizations, large and small, have accepted the fact that significant resources must be allocated to cyber defense. Security departments are enjoying a larger share of the enterprise’s budget. They can, therefore, spend more to hire people with the desired education and certifications.
At one time, some employers were known to hire real-world hackers and convert them from the “dark side” to work for the good guys.
In recent years, however, college degrees have become near mandatory for penetration testers , and the demand for security professionals with offensive security skills is growing every year.
The storied cybersecurity skills gap is mostly being solved by increased security budgets. While this challenge presents itself as an overwhelming shortage of people with the right cybersecurity skills, it is being solved by attracting talented, educated, and experienced IT professionals from other specialties.
Active defensive strategies
Cybercriminals, nation-state hackers, and hacktivists are all finding new and innovative ways to compromise digital assets. Some of the more prolific examples include:
- Using PowerPoint slides to run malicious code
- Using Microsoft Word documents to run malicious code
- Installing trojans that can use computer resources to mine cryptocurrency
- Using email spam to trick users
Many security organizations are becoming more inclined to employ defensive cybersecurity strategies.
Contrary to what some may imagine, active defensive strategies do not include attacking adversaries. Active defensive strategies are that category of strategies that include a proactive element, rather than just waiting to be attacked.
The use of pentesters or ethical hackers is an example of an active defensive strategy. These proactive activities are used to test static defenses and allow them to be fine-tuned.
Deception-based cybersecurity systems and processes are the best examples of active defense. A honeypot is the most basic of deception-based security.
In more sophisticated schemes, security professionals will put decoy data and what appears to be attack points all over their systems.
This strategy gives the security team the opportunity to monitor these decoy points and record the behavior of an adversary. Once the bait has been taken, the security analyst can choose to simply shut down the attack or to use forensic analysis to monitor the threat actor further. Since only decoy systems and data are at risk, much can be learned from the attack and then employed to protect the real data systems.
These deception-based security systems can also be used to test the organization’s playbook for automated and manual responses. These can then be updated to improve their effectiveness.
Future of the cybersecurity industry
Historically security has been treated as an after-thought or, at best, a side-track. Growing cybersecurity concerns have made it essential to clarify that security controls are a vital aspect of continuous delivery.
To adapt to a philosophy that asserts that the entire development team is responsible for security, the role of DevSecOps was born.
DevSecOps stands for Development, Security, and Operations. Related to DevOps or SecOps, it is an idea that joins two previously separate functions into a consolidated framework.
DevSecOps teams are accountable for producing conditions for continuous secure application development. Being a newer concept than DevOps, DevSecOps underscores the importance of IT security processes and security automation in the software development lifecycle.
Conventional DevOps processes do not include security. Development without an eye toward security means that many application development ventures that practice DevOps may have no security team. Or, they may test apps only after deploying them.
This approach may cause significant delays in development and is not fit for agile DevOps practices with security included.
Going forward, security professionals need to be fully embedded in the application development process. Security professionals must learn DevOps skills, and DevOps teams must make room for these security experts.
Artificial intelligence
While quickly becoming an overused, and little-understood, buzzword, machine learning, and its subordinate technology of artificial intelligence, hold great promise for cybersecurity.
The ability to accurately predict future attack behavior based on historical data and identify vulnerabilities will greatly increase our defensive capabilities.
Tech writer Kayla Matthews addresses the promising use of machine learning in cybersecurity.
In her article, “ Using Machine Learning to Evaluate Cybersecurity Risk”, she acknowledges that machine learning or artificial intelligence is no replacement for human intelligence .
“Machine learning analyzes current and past data to identify possible weak points in a business’s cybersecurity perimeter. By pinpointing these risks, it aids information security in recognizing and resolving points of liability. This strategy also utilizes past and present information to find trends that are predictive of future occurrences. By reviewing data logs, AI finds suspicious activities and flags them as likely dangers, which cybersecurity professionals can then quarantine and investigate further.”
It is critical that security software developers continually upgrade their skill sets. As cyber-attacks become evermore advanced, those charged with protecting digital assets must stay one step ahead.
Governments enforce stringent regulations to protect their citizens’ privacy — regulations like the E.U. General Data Protection Regulation (GDPR) and the new California Consumer Privacy Act are raising the bar for compliance.
Cyberspace has become a digital battleground for nation-states and hacktivists. The cybersecurity industry is continually innovating. It uses advanced machine learning (ML) and AI-driven approaches to analyze network behavior and prevent adversaries from prevailing. It’s an exciting time for the industry, and looking back helps us predict where it’s going.
The prognosis for cybersecurity professionals is good – better than good. Excellent.
The other side of that coin, however, is that it is expected that threats and breaches will also increase. Most industry analysts agree that while we are not yet winning the war, we are making great strides toward shutting down all but the financially well-backed and highly educated threat actors.
Gone are the days where a credible threat is likely to be launched from the proverbial teenaged hacker working from his parent’s dingy basement.
The good guys will win. It undoubtedly doesn’t seem that way to a CISO in the throes of defending his or her systems against an aggressive cyberattack or to a CEO facing the prospect of announcing a historic data breach, but it is nevertheless true.
In the end, enterprises take whatever steps are necessary and realign whatever priorities are needed to survive, and even thrive.
The desire to be on the right side of this struggle for control in cyberspace has attracted some of the most capable minds in government, business, or academia.
Just as with physical threats, attacks, and wars, however, there will always be another threat actor scheming to exploit a perceived vulnerability for their benefit.
This condition provides thoroughly satisfying career opportunities for those with a desire to master the relevant technologies and learn the appropriate skills.
Frequently asked questions
Cybersecurity refers to the practice of protecting computer systems, networks, and data from theft, damage, or unauthorized access. In today’s digital age, with increasing threats and sophisticated cyber-attacks, it’s crucial to safeguard personal, corporate, and government information.
While both terms are often used interchangeably, information security is a broader concept that encompasses the protection of all information, regardless of its format. Cybersecurity specifically focuses on digital data and the systems that store, process, or transmit it.
Some prevalent cyber threats include malware (like viruses and ransomware), phishing attacks, denial-of-service attacks, and man-in-the-middle attacks. Regularly updating software and being cautious of suspicious emails can help mitigate these risks.
Start by using strong, unique passwords for all accounts and enable two-factor authentication where possible. Regularly update software, use a reputable antivirus program, and avoid clicking on suspicious links or downloading files from untrusted sources.
Encryption scrambles data into a code to prevent unauthorized access. It’s vital for protecting sensitive information, especially during transmission over the internet.
Phishing scams often appear as legitimate emails or messages urging you to click on a link or provide personal information. Be wary of unsolicited communications, especially those with generic greetings, spelling errors, or suspicious URLs.
- The Classroom
- Cybersecurity Bootcamp
- Career Support
Start Your Cybersecurity Training Today!
Are you ready to gain hands-on experience with the digital marketing industry's top tools, techniques, and technologies?
By clicking "Apply Now", I consent to be contacted by or on behalf of Nexus at University of Michigan, including by email, calls, and text messages, (including by autodialer or prerecorded messages) about my educational interests. I understand consent to be contacted is not required to enroll. Msg. and data rates may apply.
Contact (734)-707-9985 for more information. I also agree to the Terms of Use and Privacy Policy .
- Introduction To Cybersecurity
Introduction to Cybersecurity: What Beginners Need to Know
On the Internet, information is widespread—and business operators, alike, risk data theft. Every year, technology becomes more complicated—and so do cyber attacks. The world of digital crime is expansive—and it isn’t exclusive to any particular Internet-accessible platform. Desktops, smartphones, and tablets may each carry a degree of digital defense—but each has inherent ‘weak points’ to which hackers have become attuned.
Fortunately, some digital security tools and services run parallel to their ill-intended tech counterparts. Even though our digital landscape’s complexity obscures advanced threats, most can leverage network-based assaults with digital disaster prevention tools.

Before we dive into these common threats, let’s dive into the cornerstones of digital security. Because today’s digital threats don’t exclusively exist on hardware, so ascertaining risk requires a different approach—one which prioritizes controlled network security over all else.
Defining Modern Cybersecurity: Network-Based Safety
When the term ‘ cybersecurity ’ comes to mind—we tend to assume it encompasses all facets of modern technology. This is understandable, as it’s technically accurate. Digital safety tools have become incredibly flexible—having been adopted by numerous industries of numerous designs.
The driving factor behind this technicality, then, is a little easier to understand:
Most devices—including navigation apps, game apps, and social media, are always connected to the Internet . Likewise, so are desktops. Whether you’re perusing a store or listening to music—chances are, you’re engaging in this encompassing environment that necessitates cybersecurity’s modern definitions.
Cybersecurity jobs, today, handle the digital defense of information sent and received between digital devices; in essence, network defense. It involves information storage protection, the identification of intrusions, the response to cyber attacks, and—in worst-case scenarios—the recovery of valuable, often personal, information that’s been stolen. Understandably, cybersecurity’s scope is pretty big—and the salary for cybersecurity professionals is sizable, too. Cybersecurity’s niche’ approach to digital safety immediately raises a question, however:
What encompasses cybersecurity itself?
Network Security
Whereas cybersecurity primarily focuses on data transfer and storage, network security is a bit broader. As per its name, network security involves the defense, maintenance, and recovery of networks in general. It encompasses cybersecurity as a defensive umbrella of sorts, protecting all network users from all digital threats—even if a given cyber attacker has intentions other than data exploitation.
To protect the integrity, safety, and sustainability of a network’s users, network security professionals tend to focus on connection privacy. This preference is synonymous with the practice of cybersecurity, resulting in the two terms often used interchangeably.
This said, the vehicles of network security services also encompass anti-virus software, malware detection tools, firewall upgrades, virtual private networks (VPNs), and other security programs. So, even though network security and cybersecurity pros often cover similar bases, they deviate at intersections wherein things like data storage and data tracking need overlap.
Of course, these intersections also tend to be serviced by additional security providers—each arriving from their own, specialized avenues of digital risk management. While these additional cyber crime defenders conduct vital services, however, they’re not as far-reaching as network security is—or even cybersecurity, for that matter.

Because of this, professionals of cyber threat reduction can be considered in an umbrella ‘hierarchy,’ of sorts: Network security, in most cases, extends in some way, shape or form, to each of these spheres—existing as the ‘top’ umbrella. Subsequently, cybersecurity defines a userbase’s primary concern with data protection. It ‘covers,’ or concerns, three other spheres of cybersecurity framework management: information security, operational security, and application security.
Information Security
Most, if not all, commercial workplaces utilize networks to synchronize every facet of day-to-day operations. They handle user logins, schedule management tools, project software, telecommunications, and more—necessitating the employment of those capable of holding it all together:
An information technology security team.
Their continuous monitoring keeps a network’s traveling information secure, assuring only authorized users can access its services. It’s important to note their difference from cybersecurity professionals, however, as their goals can easily be confused. Cybersecurity pertains to the protection of valuable data—such as social security numbers, business transaction logs, and stored infrastructure data. Information security, meanwhile, protects digital traffic.
Even though valuable data can indeed be parsed from this traffic—resulting in yet another service overlap—information security professionals are the direct responders. This area of work covers disaster recovery planning: processes enacted via rigorous risk assessments, practiced response strategies, and concrete plans for long-term defense.
Operational Security
Also referred to as OPSEC , operational security is commonly held in high regard for its modular design as a risk management process. It encourages company management teams to view their commercial operations from an external point of view—to identify potential lapses in overall security. While companies often succeed in managing public relations, risk-free, data thieves may still glean sub-textual information throughout. In this scenario, the risk of data theft becomes much higher—as parsed data compiled into actionable information, externally, eludes the standard security protocols behind a business’s walls.

OPSEC can be categorized into five distinct steps:
One: Identify Potentially Exposed Data
Operations security takes great care in exploring every scenario in which a cyber attacker might extract meaningful data. Typically, this step includes the analysis of product searches, financial statements, intellectual property, and public employee information.
Two: Identify Potential Threats
For every identified data source deemed sensitive, operational security teams take a closer look at potential threats. While third-party providers are commonly analyzed first due to their proximity, insider threats are also considered. Negligent or otherwise disgruntled employees may indeed pose a threat to a business’s data integrity—whether intentionally or accidentally.
Three: Analyze Risk Severity
Because data value varies widely, it’s in a business’s best interest to identify the degree of damage potential exploits might cause. By ranking vulnerabilities based upon attack likelihood chances, a team can even determine the likelihood of different cyber attacks.
Four: Locate Security Weaknesses
Operational management teams are also highly capable of information security operators. By assessing current safeguards and identifying any system loopholes, they can spot weaknesses well before being exploited. This information can also be compared with insights ascertained from the previous three steps—to get clearer outlooks on a threat-to-threat basis.
Five: Plan Countermeasures
Once more, preventative methods are of top concern for those who practice digital security. This last OPSEC step serves to mitigate risks before risk elimination is an unavoidable approach. Step Five typically involves updating hardware, initiating new digital policies for data protection, and training employees in the latest security measures.
Application Security
Even though commercial networks operate on custom-tailored software platforms, application-specific threats still exist. Application security is the initiation of protective measures on the application level. This includes both software and hardware security to minimize exploitation threats, which often spawn from outdated firmware and aged platforms.
Application security teams prevent app code from being hijacked, implementing several firewall-centric security measures alongside software modifications and encryption. Because many of today’s applications are cloud-based, network access persists as a potential threat. Fortunately, many application security workers are experts at eliminating vulnerabilities on the app-to-network level.
By and large, security on the app level benefits every sphere of a company’s digital defense framework. Most app security implementations revolve around software authentication, intensive logging, and constant authorization inspections in unison—to be ever-reliable. Cybersecurity management varies on a network-to-network basis. Still, virtual runtimes are a stable cornerstone upon which reliable, adequate security measures can grow—especially when backed by general data protection regulation updates.
Advanced Persistent Cybersecurity Threats
Over the years, renowned entities like the National Institute of Standards and Technology or NIST have greatly enhanced economic security across industries. Meanwhile, the three primary elements of information security—the ICA or Integrity, Confidentiality, and Availability triad—keep the public informed about the world’s most recent, highly dangerous digital attacks.
Despite the public’s general awareness of spyware and adware, the potential threat posed by malicious scripts, bots, and malicious UI modifications tends to be overlooked. In recent years, phishing and ransomware have proven a rare prevalence inherent in digital elusivity. Occasionally spotted, their accurate identification similarly verifies tricks of the trade having inherited our tools—freshly sharpened for digital exception exploitation against the grind of today’s strongest firewalls.
So it seems, cyber criminals have adopted, and have capably learned, the ins and outs of today’s leading information systems: innovations otherwise mastered by their respective creators and management teams.
The targets remain clearly defined, and no deviation from them has yet to be seen. Entities with extensive data collections—commercial properties—are ever a bullseye. But now, it seems, a common purpose of eroding digital defenses may very well have devastating impacts. Commercial data stockpiles aren’t highly appraised by thieves for their operational DNA—but for their customers’ digital footprints.
Identifying a Cyber Attack
Understanding a malicious digital object’s mode of operation dramatically increases one’s security—both online and offline. These nefarious tools do pose extensive threats, undoubtedly, but their digital footprint patterns have given us valuable knowledge to avoid them, or even eliminate them if they’re encountered. One should never stop being cautious, however, as they’re elusive by design.
Behind the Term: Hacking
We hear the word ‘hack’ quite a lot. One might assume, reasonably, that hacking is an action taken to sidestep usual barriers to entry—whatever they may be. This is correct. When it comes to digital environments, hacking is a broad-stroke term used to describe the practice of compromising digital devices. Not all hacking is malicious, as system developers frequently employ hacks to test system security. Still, a majority of hacks are conducted as illicit activities.
Hacking defines direct attempts to breach platform security protocols via implemented scripts. It also, however, can be passive—such as the creation, and careful placement, of dangerous malware. Let’s take a closer look at today’s most common digital attacks through this lens—wherein each malicious activity below, regardless of their respective tools, falls into the hacking category.
Malware is often referred to, yet its intricacies tend to surprise people. Most simply consider malware to be a benign, albeit, more inconvenient version of adware. While the two are similar, malware can be far more dangerous if it isn’t identified, quarantined, and removed.
Malware’s namesake, ‘malicious software,’ is a blanket term that encompasses various viruses and trojans. The tools implement digit-based code attacks to disarm or bypass a system’s security architecture. Malware’s pre-scripted destinations, of course, are directories known for storing vital operating system components.
Malware is identified by the way it spreads: Viruses and trojans, while both ‘malware,’ engage a target system in different ways. A virus contains a small string of computer code—one which is placed within a file typically presented as a benign download. The code is designed to self-replicate across an operating system, ‘hopping’ from program host to program host. Upon finding a program flexible enough for control, the virus takes control—forcing it to perform malicious actions against the system’s users. Sometimes, this manifests as simple inconveniences—such as programs that continuously launch, toggle themselves as startup processes, or can’t be removed from background processes.
Sometimes, however, the malware’s host is a target linked to external financial accounts, valuable file information, or registry keys.
Trojans are popular tools of cyber attacks, too. Often hidden within downloadable programs, trojans technically can’t self-replicate—initially, at least. Instead, they must be launched by a user first. Once launched, however, trojans can spread throughout a system far quicker than viruses—sweeping many locations for information, system tools, and connections to valuable, external accounts.
Much like malware, phishing involves deceiving users into approaching an online service. However, unique to phishing is its focus not on breaking into a user’s system but tracking them for valuable information. Phishers typically come into contact with users via email – as the process spawns from direct deceit. Phishers pretend they’re people they’re not—specifically those who, hypothetically, would serve as a notable authority figure.
Phishers commonly masquerade as banking institution officials, insurance agents, and account service people. Via fraudulent contact information and email design mimicry, a phisher ultimately wants the recipient to click a link of some sort. Typically, the cyber attacker urges them to access the link as a way to reach one of their accounts or get in touch with another representative.
As one might guess, these malicious links can launch code strings when clicked—immediately jeopardizing the victim’s digital security. Most phishers have malware as their link-based weapon of choice. This said, advanced phishers have been known to launch far more complex, exceedingly dangerous scripts.
Also, in the realm of direct-communication cyber attacks is the use of ransomware. Ransomware, as per its name, is malware hinged upon a monetary demand—or a ransom. While some cyber attacks are motivated, driven, and executed to steal data for sale, ransomware usage is far more direct.
Ransomware is grounded in the use of encryption software. Usually smuggled into the victim’s computer similarly as phishing scripts, this type of malware serves to ‘lockdown’ the victim’s digital assets—rather than pursue them for theft. While this information can indeed be vital information such as one’s financial account details, it tends to be usable for blackmail.
Specifically, ransomware cybercriminals target corporate secrets, product designs, or any information which might damage the business’s reputation. The ransom is announced soon after—wherein the attacker demands direct funds for the safe return of the victim’s inaccessible, and stolen information assets.
Social Engineering
Sometimes, digital applications aren’t needed to exploit valuable information. Social engineering has become quite popular among the online world’s exploitative use—rendering even some of the most secure user-based platforms defenseless. It requires no tools as a means of online communication—as it revolves around psychological tricks, and very little more.
Social engineering attacks occur when a perpetrator begins investigating their intended victim for background information and information about the individual’s current digital security habits. After doing this, the attacker initializes contact—often through email. With the information parsed earlier, the attacker can effectively pretend to be a trusted and sometimes even authoritative figure.
Most social engineering attacks pursue valuable information via spoken word. Even the mere verbalization about a potential digital security weak point-can lead the attacker to the information they need—accessibility credentials for valuable accounts.

Other Threats to Unsecured Platforms
The above-mentioned digital assaults don’t stand alone as the most dangerous cyber weapons an Internet attacker can wield—but they tend to be the most common. While high-capacity hacks, decryption tools, and complicated scripts capable of breaching high-security networks do exist, they tend to be rarer—as their usage requires both a high degree of digital knowledge and criminal know-how to avoid detection.
Cross-Site Scripting
Other ‘tricks of the hacker’s trade’ tend to revolve around cross-site scripting—wherein digital code is inserted into vulnerable user interfaces and web applications: JavaScript, CSS, and ActiveX being the most popular targets. This is called ‘CSS injection.’ It can be used to read HTML sources containing a sensitive date. Understandably, active XSS attacks can be used to track a user’s online activities—and even introduce entirely separate, malicious websites into the mix.
DNS Spoofing
The act of introducing fraudulent, and often dangerous, websites into safe environments is called DNS spoofing. It’s done by replacing a DNS server’s IP addresses with one’s own—thereby disguising it beneath a URL users are likely to click. The disguised website destination is often designed to resemble its real-world counterpart.
Soon after arriving, users are prompted to log into their accounts. If they do, their login credentials are saved and stored by the attacker: tools for eminent digital exploitation, soon.
The Best Practices in Cybersecurity
Our new digital defense inventories are packed with powerful security tools. Even simple mobile device security in the form of two-factor identification dramatically reduces the odds of successful attacks. Jobs with cybersecurity tools must always be informed of emergent hacking trends.
As for the other tools—those concerned for their online security have a few to choose from. More important than tools themselves, however, are the methods behind their employment.

Identity Management
Also called ‘ID Management,’ identity management involves the use of authorization. This practice ensures that the right people have access to the right parts of a system—and at precisely the right time. Because digital user rights and identification tests are contingent upon user specificity, they sometimes share a double purpose as data protection tools.
Mobile and Endpoint Security
Smartphone apps, mobile web services, and firmware have some extent of digital security—but smart devices still tend to be the first recipients of cutting-edge software security options. This isn’t necessarily because they’re unsecured—but because of their positioning within a given network.
Namely, system endpoints.
Whereas desktops can be USB hubs, mobile devices are merely self-sustaining by design. Because of this, they’re mostly digital doorways to entire network architectures. To keep these doorways shut—both for the device’s safety and network’s virtual integrity—tech teams often use monitoring and management toolkits.
They can conduct manual device patches, real-time monitoring services, automation scripting, and fundamentally transform simple mobile devices into full-fledged, handheld security suites.
End-User and Cloud Security
At times, security providers and a business’s end-users use the same tools to protect themselves. One of these tools is cloud-based security. Organizations can extend corporate security controls capable of rapidly detecting, responding to, and removing cyberterror objects.
Cloud security environments might be seamless in terms of accessibility—but their high-end encryption standards make them nearly impenetrable. Their mix of features is form-fitting to most jobs for cybersecurity, keeping workers secure regardless of their location.
Learning More About Network Security
To stay safe in the online world, a user must keep their industry knowledge up to date . You don’t necessarily need a cybersecurity degree, however. Information is widely available online—and plenty of cybersecurity experts offer cybersecurity certifications beyond the classroom.
Despite the Internet having risks, plenty of online users never encounter malicious hackers at all. Fortunately, today’s digital security tech—both hardware and software—is similarly advanced. Between platform-included security suites, encryption, firewalls VPNs, and the anti-tracking add-ons of today’s Internet browsers, being passively safe is undoubtedly possible.
It’s best not to take any chances, in any event, as perceivably minor digital threats can evolve—becoming full-fledged, multi-device, data-breaching digital weapons. Regardless of your daily Internet usage, career computing resources, or mobile device apps—preventative care is your biggest asset.
To nurture this asset, pursue new knowledge whenever you can—professionally or otherwise. You can take the first step with our Cybersecurity Professional Bootcamp . Gain hands-on experience with simulation training led by active industry experts and get one-on-one professional career coaching. In less than one year, you can become a well-rounded professional ready for your first day on the job.
Fill out the form below to schedule your first call or reach out to our admissions team at (734)-707-9985 to get started today!
View this post on Instagram A post shared by UMich Digital Skills (@um_nexusdigital)

To learn more about Nexus’ Cybersecurity Professional Bootcamp, give our Enrollment Advisors a call at (734) 707-9985 or fill out the form below.
Call Us and Get Started Today
By clicking "Request Info", I consent to be contacted by or on behalf of Nexus at University of Michigan, including by email, calls, and text messages, (including by autodialer or prerecorded messages) about my educational interests. I understand consent to be contacted is not required to enroll. Msg. and data rates may apply. Contact (734)-707-9985 for more information. I also agree to the Terms of Use and Privacy Policy .
By clicking "Request Info", I consent to be contacted by or on behalf of Nexus at University of Michigan, including by email, calls, and text messages, (including by autodialer or prerecorded messages) about my educational interests. I understand consent to be contacted is not required to enroll. Msg. and data rates may apply.

2401 Plymouth Road, Suite A/B, Ann Arbor, MI 48105
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Describe the basic concepts of cybersecurity
- Learning Path
Knowing the fundamentals of cybersecurity is a first step toward protecting against cyberthreats. In this learning path you will learn about cybersecurity concepts and ways to protect yourself and your business from cyberattacks.
Prerequisites
Achievement Code
Would you like to request an achievement code?
Modules in this learning path
Cyberattacks are impacting individuals and businesses at alarming rates. Being informed about the evolving threat landscape and common types of attacks are key to learning how to protect against attacks.
Cryptography is foundational to protecting the confidentiality, integrity, and availability of information; and defending against cyberattacks. Throughout this module, you'll learn about the different elements of cryptography and their application in cybsecurity.
Secure authentication and authorization are a cornerstone of protecting against cybersecurity threats. Learn about common identity-based attacks, different authentication methods, and ways to protect against unauthorized access.
Networks form the backbone of our digitally connected world. They also represent an entry point for cyberattacks. In this module, you'll learn about threats to network security and how to mitigate those threats.
Internet connected devices are everywhere, and users and organizations depend on them for pretty much every facet of daily life and business use. Throughout this module, you'll learn about device threats and mitigation techniques.
The proliferation of applications across the digital landscape presents an increased opportunity for cybercriminals. Throughout this module, you’ll learn about the threat landscape of application-based attacks and how to protect your applications.
Tutorial Playlist
Cyber security tutorial: a step-by-step guide, what is cybersecurity, cyber security for beginners, how to become a cybersecurity engineer, what is ethical hacking, what is penetration testing: a step-by-step guide, what is sql injection: how to prevent sql injection, how to become an ethical hacker, what is a firewall and why is it vital, the complete know-how on the md5 algorithm, a definitive guide to learn the sha 256 algorithm, what is a ransomware attack and how can you prevent it, 5 best programming languages for hacking in 2024, the most informative guide on what is an ip address.
18 Best Cyber Security Books and Ethical Hacking Books in 2024
Types of Cyber Attacks You Should Be Aware of in 2024
The Top Computer Hacks of All Time
Top 10 cybersecurity jobs in 2024: career and salary information, top cybersecurity interview questions and answers for 2024, what is a brute force attack and how to protect our data against it, the top 8 cybersecurity skills you must have, your guide to choose the best operating system between parrot os vs. kali linux, all you need to know about parrot security os, the best and easiest way to understand what is a vpn, what is nmap a comprehensive tutorial for network mapping, what is google dorking your way to becoming the best google hacker.
Cyber Security: Career Path | Skills | Salary | Certifications
The Value of Python in Ethical Hacking and a Password Cracking Tutorial
The best guide to understand what is tcp/ip model, what are keyloggers and its effect on our devices, best guide to understand the importance of what is subnetting, your guide to what is 5g and how it works, how to crack passwords and strengthen your credentials against brute-force, a look at ‘what is metasploitable’, a hacker’s playground based on ubuntu virtual machines, one-stop guide to understanding what is distance vector routing, best walkthrough for understanding the networking commands, best guide to understanding the operation of stop-and-wait protocol, the best guide to understanding the working and importance of go-back-n arq protocol, what are digital signatures: a thorough guide into cryptographic authentication, your one-stop guide ‘on how does the internet work’, an introduction to circuit switching and packet switching, one-stop guide to understanding what is network topology, a deep dive into cross-site scripting and its significance, the best walkthrough on what is dhcp and its working, a complete look at what a proxy is, along with the working of the proxy server, a detailed guide to understanding what identity and access management is, the best guide to understanding the working and effects of sliding window protocol, the best guide that you’ll ever need to understand typescript and express, express rest api, a definitive guide on how to create a strong password, ubuntu vs. debian: a look at beginner friendly linux distribution, your one-stop guide to learn command prompt hacks, best walkthrough to understand the difference between ipv4 and ipv6, what is kali nethunter a deep dive into the hackbox for android, a perfect guide that explains the differences between a hub and a switch, what is network security benefits, types of tools to protect your shared network, what is cidr and its importance in the networking domain, a thorough guide on application security: benefits, risks, and protection mechanisms, one-stop solution to learn about parity bit check, what is hdlc and understand the functioning of each part of an hdlc frame, what is dijkstra’s algorithm and implementing the algorithm through a complex example, what is checksum one-stop guide for all you need to know about checksum, an ultimate guide to cyber security for beginners.
Lesson 2 of 61 By Baivab Kumar Jena

Table of Contents
Cybersecurity is a popular topic, but do you know why it is essential? We are living in a digital era where data is everything. We must understand that private information is much more vulnerable than ever before. We often hear about data breaches and cases of identity theft that affect millions of consumers. Two years ago, WannaCry ransomware encrypted millions of computers. All companies and institutions are fighting to protect their data against hackers and cybercriminals, and you can also play a role in it. Cybersecurity is not involved only in organizations, but even personal computers, mobile phones, and tablets.
Before we begin learning this cyber security for beginners tutorial, let us first understand what exactly is cyber security and what is its significance. Cybersecurity is the technology and process that is designed to protect networks and devices from attacks, damage, or unauthorized access. Cybersecurity is essential for a country’s military, hospitals, large corporations, small businesses, and other organizations and individuals since data is now the cornerstone of any organization. If that data is exploited, then there are a lot of risks. Now, we have understood what cybersecurity is, let’s see what the CIA triad is and how it is related to cybersecurity.
The security of any organization starts with three principles: Confidentiality, Integrity, Availability. And next in this cyber security for beginners tutorial we will learn about the CIA Triad, which has served as the industry standard for computer security since the time of first mainframes.
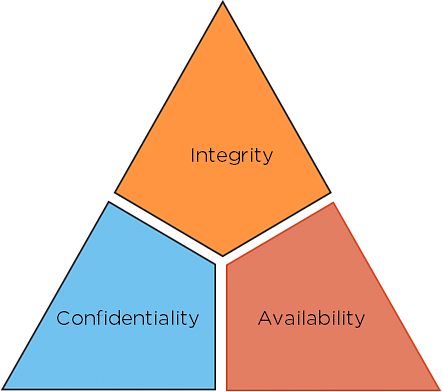
Fig: CIA triad
- Confidentiality: The principles of confidentiality assert that only authorized parties can access sensitive information and functions. Example: military secrets.
- Integrity: The principles of integrity assert that only authorized people and means can alter, add, or remove sensitive information and functions. Example: a user entering incorrect data into the database.
- Availability: The principles of availability assert that systems, functions, and data must be available on-demand according to agreed-upon parameters based on levels of service.
Next up in the cyber security for beginners tutorial, let’s look at the areas and speciality in cybersecurity to understand the space better.
Become a Certified Ethical Hacker!
Specialties in Cybersecurity
To pursue your career in cybersecurity , it is essential to know about the areas of specialization in it, and this cyber security for beginners tutorial will help you do just that. There are nine:
- Access control systems and methodology: This deals with protecting critical system resources from unauthorized modification.
- Telecommunications and network security: This focuses on communications, protocols, and network services, and the potential vulnerabilities associated with each.
- Security management practices: This area deals effectively with catastrophic systems failures, natural disasters, and other types of service interruptions.
- Security architecture and models: This focuses mostly on having security policies and procedures in place. This particular security domain involves policy planning for just about every type of security issue.
- Law, investigation, and ethics: This handles the legal issues associated with computer security.
- Application and system development security: This person covers things like database security models and the implementation of multilevel security for in-house applications.
- Cryptography : Designed to help you understand how and when to use encryption.
- Computer operations security: This covers all those things that happen while your computers are running.
- Physical security: This primarily addresses questions about physical access to your servers and workstations.
A cyber security bootcamp provides hands-on experience and theoretical insights, allowing individuals to uncover their specific interests and strengths. By focusing on these specialties, participants can enhance their skills and knowledge, preparing them for roles that demand expertise in specific aspects of cybersecurity.
Basic Terminologies
Next up, this cyber security for beginners tutorial will help you understand some of the terminologies you must be familiar with before learning anything about cybersecurity.
A network is a connection between two or more computers so that they can communicate with each other. For example:

Fig: Network Connection
2. Internet
Internet is a means of connecting a computer to any other computer anywhere in the world via dedicated routers and servers.
3. Internet Protocols
The data that is transferred or received cannot follow any path. There are a set of rules that are followed to control the flow of the internet. These rules are called internet protocol.
4. IP Address
An Internet Protocol address (IP address) is an address assigned to all devices that connect to a computer network and uses the Internet Protocol for communication. An IP address looks like this: 168.192.10.3

5. MAC Address
This is a unique identification number that every device has that connects to the internet. Traditional MAC addresses are 12-digit hexadecimal numbers. MAC address looks like this: D8-FC-93-C5-A5-EO.
6. Domain Name Server(DNS)
Consider DNS as the phonebook of the internet. All the IP addresses and the name of the links are saved in it. For example, you want to go to google.com. You type this on your web application. Then, this name goes to the DNS server, and the DNS server finds the IP address of google.com. Then, the DNS server returns it to your computer with the IP address.
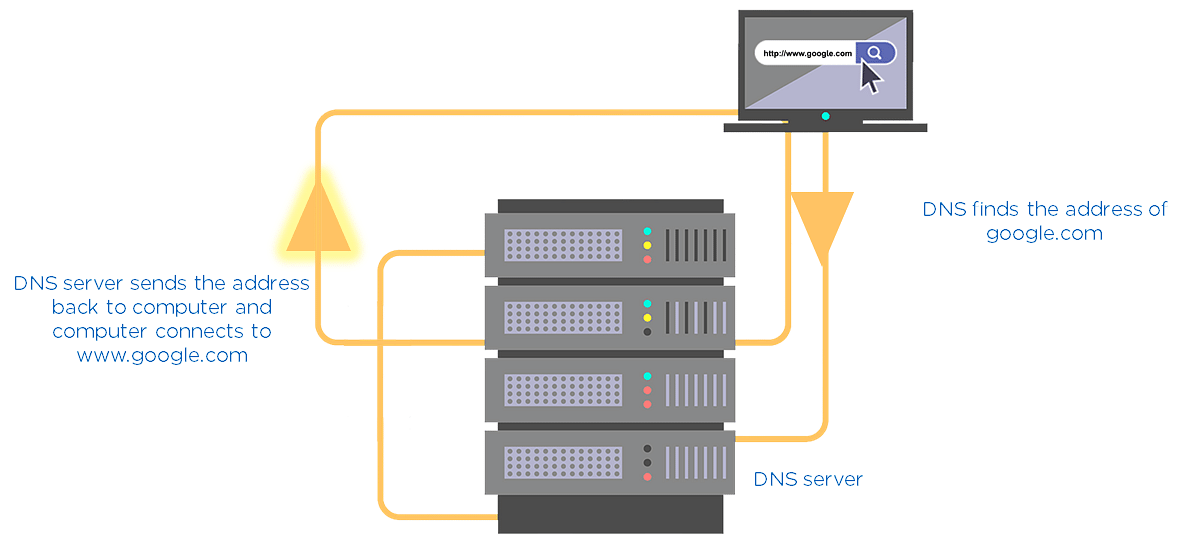
Fig: DNS Server Illustration
Develop Skills for Real Career Growth!
Dynamic host configuration protocol is a protocol that assigns an IP address to any device that wants to connect to the internet.
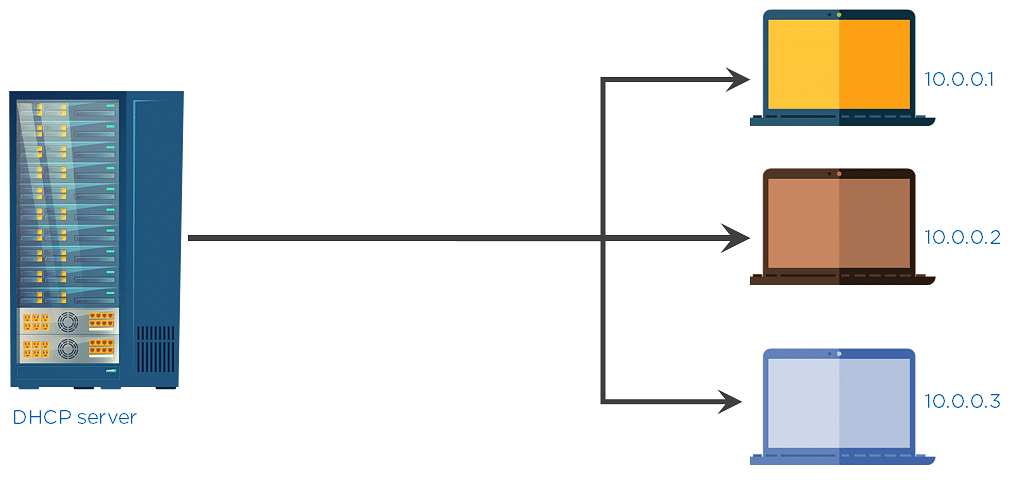
Fig: DHCP providing IP addresses
This is a device that routes the data that comes to it and then sends that data to the destination to ensure that it is on the appropriate path.
Bots are computer programs that control your computer without your knowledge. They automatically send emails, retrieve web pages, and change computer settings.
Upon completing this cyber security for beginners tutorial, build your network security skill-set with the Ethical Hacking Certification Training . Enroll today!
Common Types of Attacks
Before we get into the types of attacks, we should know why these attacks happen, and this cyber security for beginners tutorial will help you learn A-Z of both. There is always a motive behind every attack; the main reason for attacks is money. Hackers penetrate the system and then demand ransom from the victims. There are other reasons like a financial loss to the target, achieving a state’s military objective, damaging the reputation of the target, or political maneuvering.
There are mainly five types of attacks:
- Distributed denial of service(DDoS)
- Man in the middle
- Email attacks
- Password attacks
- Malware attack
In the next section of this cyber security for beginners tutorial, let’s look at all the attacks in detail:
1. Distributed Denial of Service
It is an attack used to restrict a user from accessing the resources by flooding the traffic that is used to access resources. A botnet controller controls all the bots that are under it. The attacker sends a command to the botnet controller that tells all bots to attack a server so that the server will be flooded. When a user wants to access a website, he will not be able to, as the traffic on the website will be at full capacity.
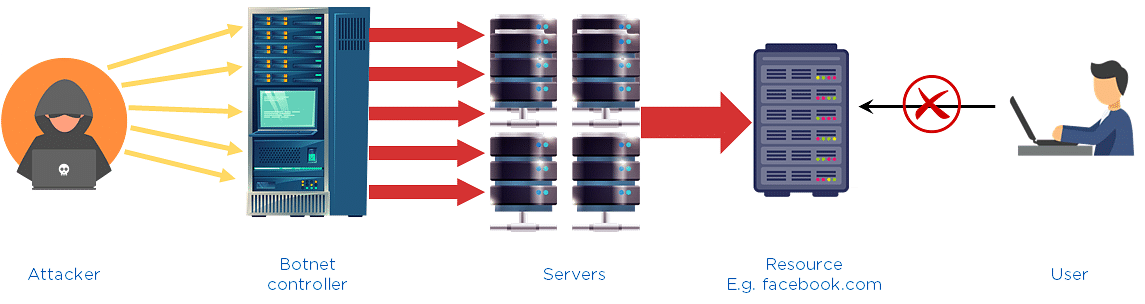
Fig: DDoS Illustration
2. Man in the Middle
Let’s look at an example to understand this better. Suppose you want to do an online transaction and you connect to your bank and make the payment.
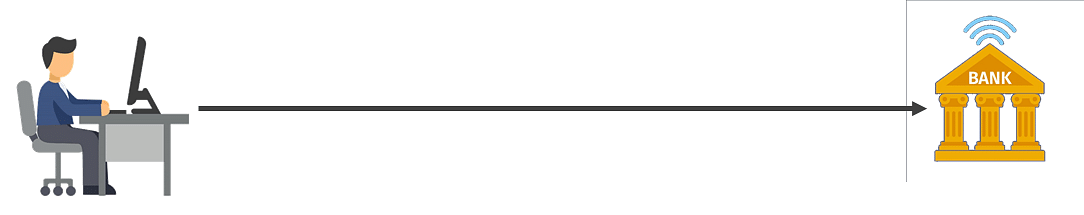
Fig: Man in the middle attack (1)
Now, while you are completing the transaction, you have to put in credit card details and the PIN. The attacker can spoof you and monitor your transaction. As soon as you put in your details, he will see them.

Fig: Man in the middle attack (2)
3. Password Attack
To crack a password or find a password, we use this technique. There are five types of password attacks:
- Dictionary attack: In this method, we handle every password that is possible through the dictionary.
- Brute force: This is a trial and error method used to decode the password or data. This attack takes the most amount of time.
- Keylogger: As the name suggests, a keylogger records all keystrokes on a keyboard. Most hackers use keyloggers to get passwords and account details.
- Shoulder surfing: The attackers observe the user’s keyboard by looking over the user’s shoulder.
- Rainbow table: There are rainbow tables that contain precomputed hash values. Attackers use this table to find the password of the user.
4. Email Attacks
First, let’s see how an email works. Suppose John is sending an email to Jack. The email first goes to the email server. Then it goes to the DNS server to find the IP address of the destination. From the source email server, the email goes to the destination server. From there, the email is sent to the IP address on which Jack is working. It is illustrated in the picture below.

Fig: How email works.
There are three types of email attacks.
Download these attachments only if you are sure that it is a legitimate email.
5. Malware Attack
- Malware: This is a malicious program or software that disrupts or damages the computer. There are three types of malware.
- Virus: A computer virus is a malicious code that replicates by copying itself to another program or document and changes how a computer works. The virus requires someone to knowingly or unknowingly spread the infection without the knowledge or permission of a user or system administrator. An example of a virus is the Melissa virus.
- Worms: These are standalone programs that run independently and infect systems. For example, W32.Alcra.F is a worm that propagates through network share devices.
Functions of Malware
- Overwhelming system resources: Malware, especially worms, can spread around and overwhelm a system or network. Some malware creates so many folders that no memory is left and slows a computer down.
- Creating a backdoor: Let’s look at an example: Microsoft sends updates every Sunday on all Windows platforms. How do these updates reach to your Windows OS? They create backdoors from where they can send updates. Similarly, hackers create backdoors from where they can continuously send viruses after getting into a system.
- Disabling security functions: Some malware can disable antivirus software, as well as security updates. This malware tends to last longer because there is no security to stop it. They tend to keep the system vulnerable to other malware.
- Creating botnets: Hackers make botnets by purely coding. A botmaster controls botnets, and they are usually used to crash websites. Botmaster tells all botnets to flood the website by accessing the website at the same time.
Sources of Malware
- Removable media: Removable media, like Pendrive, CDs, DVDs, and flash drives, may be used to send viruses to your system.
- Documents and executable files: Viruses can be hidden in document files with the .exe extension. As soon as you open them, the virus activates.
- Internet downloads: Download files only from trusted websites. If you download from untrusted websites, there may be chances that those files will contain viruses, and as soon as you open them, the hacker might get access to your system.
- Network connections: Be sure that your service provider is genuine. If the network is unsecured, then it can be accessed by anyone.
- Email attachments: Never open email attachments unless the sender can be trusted. These files may contain viruses to create backdoors.
- Malicious advertisements: Never click on ads that you don’t trust. They are created so that you can click on them, and hackers will receive details about you.
The kind of job you do is definitely something you wish to consider before you step foot in any field. In this section of the cyber security for beginners tutorial, we will learn about top roles in the cybersecurity field:
- Chief Information Security Officer: Manages the IT security division of an organization.
- Forensic Computer Analyst: Looks for evidence after the breach or attack on an organization.
- Information Security Analyst: Protects the computer systems and networks of an organization.
- Penetration Tester: Penetration testers are highly skilled security specialists that spend their days attempting to breach computer and network security systems.
- IT Security Engineer: Plan to carry security measures to monitor and protect data and systems from hackers and cyber attacks.
- Security Architect: Maintain the network security of an organization.
- Security Systems Administrator: Install, administer, maintain, and troubleshoot a computer, network, and data security systems are their responsibilities.
- IT Security Consultant: Protect the organization’s sensitive data.
What did you learn from this cyber security for beginners tutorial and how much do you know about security concepts? Take up this CISSP Practice Exam and test yourself.
Cyber Security Certifications
To start your career in the cybersecurity field, you must know the certifications that you need to clear to get into this field. Wondering what are they? This cyber security for beginners tutorial has got that covered for you too. The top three certifications are:

Check out the below video, to sum up this tutorial on cybersecurity -
There is substantial evidence that cybersecurity is in demand right now. This demand will continuously grow, and it is challenging to measure labor supply or demand in this field. The primary reason for growing this field is that technology is improving every day. It is good that the whole world is working together to reduce cyberattacks because of the economy and communication across the globe. cybersecurity is a complex subject that requires knowledge and expertise from multiple disciplines but not limited to computer science and information technology.
This cyber security for beginners tutorial covers everything you need to know about the fundamentals, basic terminologies, and certifications too. And if you think you’re ready for a challenging yet exciting field like cybersecurity, you must check out Simplilearn’s comprehensive Cybersecurity Training program , that covers everything from cyber security for beginners to advanced networking skills you need to build a successful career!
If you’re interested in learning more about cybersecurity, check out Simplilearn’s comprehensive Cybersecurity Training program.
Find our CEH (v12)- Certified Ethical Hacker Online Classroom training classes in top cities:
About the author.
Baivab Kumar Jena is a computer science engineering graduate, he is well versed in multiple coding languages such as C/C++, Java, and Python.
Recommended Resources
An Introduction to Cyber Security: A Beginner's Guide
Cyber Security Bootcamp: The Fast-Track to Becoming a Cyber Security Professional
How to Build an Enterprise Cyber Security Framework
- PMP, PMI, PMBOK, CAPM, PgMP, PfMP, ACP, PBA, RMP, SP, and OPM3 are registered marks of the Project Management Institute, Inc.

- Conferences
- Last updated April 30, 2020
- In AI Origins & Evolution
10 Popular Cybersecurity Presentations On Slideshare You Should Refer To

- Published on August 12, 2019
- by Ambika Choudhury

Securing networks and protecting data from breaching has become one of the crucial motives in an organisation. Cybercrime has eventually risen with the widespread use of emerging technologies and we have been witnessing data breaches and other hacks for a few years now. In this article, we list down 10 popular presentations on cybersecurity one must read on Slideshare.
(The list is in alphabetical order)
1| Artificial Intelligence And Cybersecurity
This presentation was published in March 2019 by Olivier Busolini, a cybersecurity professional who also works with AI in cybersecurity. This presentation includes a basic introduction to AI, an overview of AI technologies, an overview of machine learning underlying technologies, basics of deep learning, introduction to red and blue AI, emerging usages of blue AI, difficulties faced during developing AI solutions and tips for cybersecurity strategy.
2| Cyber Crime And Security
This powerpoint presentation was published by Lipsita Behera, a software developer and it has gathered more than 350,000 views till now. In this PPT, you can understand the basics of cybersecurity such as how cybersecurity emerged, know about cyber threat evolution, types of cybercrime, how to take preventive measures in order to control the threats, learn various security reasons as well as methods.
3| Cybersecurity
This presentation has got more than one lakh viewers and more than 700 clipping. Here, the author introduces the basics of cybersecurity and what is the actual need of cybersecurity, what are the major security problems, different viruses and worms and its solutions, brief introduction of hackers and measures to prevent hacking, what are malware and steps to stop malware, what are trojan horses and safety measures to avoid trojans, password cracking and securing password, cybersecurity strategy in India and much more.
4| Combating cybersecurity Using Artificial Intelligence
Combating Cybersecurity using Artificial Intelligence was published in January this year by Inderjeet Singh, Director – Strategic Accounts. This presentation discusses the threats with AI and machine learning. Here, you can learn about the advanced behavioural attacks, applications of emerging technologies in cybersecurity, various malicious activities, including the future of AI and machine learning in cybersecurity.
5| Cyber Crime And Security
This powerpoint presentation was published by Aeman Khan, an automation test engineer and it has crossed over 410,000 views till now. Here, the writer discusses the basics of cybersecurity such as its introduction, history, the various categories of cybercrime, its types, how cybersecurity threatens national security, advantages of cybercrime and other safety tips to cybercrimes including cyber law in India.
6| Cybersecurity
This ppt is published by Bijay Bhandari, an engineer and project manager by profession. It has been viewed for over 210,000 times where the author discusses how to take action against cybercrime. You will know about the basics of cybersecurity and cybercrime, what constitutes cyber crimes, protection measures for cybercrime, advantages of cybersecurity and various safety measures.
7| Cyber Crime
This presentation has been viewed for over 294,000 times and it includes a basic introduction to cybercrime. You will get to know about the variants of cybercrime such as phishing, vishing, cyberstalking, cost of cybercrime in India, cyber laws, various ACTs including the preventive measures for such activities.
8| Overview Of Artificial Intelligence In cybersecurity
This presentation, an overview of artificial intelligence in cybersecurity was published in June 2019 by Olivier Busolini, a cybersecurity professional. Here, he talks about artificial imitation augmented intelligence, basic types of AI and machine learning, difficulties to develop AI solutions, challenges in machine learning, AI in cybersecurity, key flaws of cybersecurity, AI risk framework, basic introduction to defensive AI, adversarial AI as well as offensive AI and much more.
9| Security Automation And Machine Learning
The security automation and machine learning ppt is published by Siemplify, a security platform in January this year and has got more than 100 viewers. It includes a basic introduction to cybersecurity and machine learning, types of machine learning techniques, security analysis for machine learning, threats on machine learning, machine learning for prevention, detection, incident response and SOC management.
10| The Role Of Big Data, AI And ML In Cyber Intelligence
The role of big data, AI and ML in cyber intelligence ppt was published by Aladdin Dandis, an information security manager who gives a brief introduction to cyber intelligence, raw threat data and threat intelligence, understanding AI and machine learning drivers, various kinds of cybersecurity options such as phishing, anti-malware, fraud detection, cyber intelligence framework and its challenges.
Access all our open Survey & Awards Nomination forms in one place
Ambika Choudhury

CyberArk Unveils CORA AI to Empower Enterprises with AI-Driven Identity Security

Cisco Unveils AI-Native Cybersecurity Innovations

Commvault’s Arlie Spearheads AI Democratisation in Cyber Resiliency

How Securonix is Building Cybersecurity for LLMs

AI Will Open a Pandora’s Box of Escalating Privacy and Security Woes: Splunk Report

Nearly 83% of Indian Firms Were Hit by Cyber Breaches in 2022

After WormGPT, FraudGPT Makes it Easier for Cybercriminals

Meta Needs You in Its Generative AI Gambit

Pride month is almost here, and so are the company’s seasonal initiatives for the LGBTQIA+ community.

Top Editorial Picks
Jivi’s Medical LLM Beats OpenAI at the Open Medical LLM Leaderboard Pritam Bordoloi
CtrlS Launches 13-MW, AI-ready Data Center in Hyderabad Shyam Nandan Upadhyay
Agnikul Cosmos Launches India’s Second Private Rocket, Agnibaan SOrTeD Shyam Nandan Upadhyay
UiPath Stock Plunges Nearly 30% as CEO Rob Enslin Abruptly Resigns Shyam Nandan Upadhyay
Subscribe to The Belamy: Our Weekly Newsletter
Biggest ai stories, delivered to your inbox every week..

"> "> Flagship Events

Join the forefront of data innovation at the Data Engineering Summit 2024, where industry leaders redefine technology’s future.
© Analytics India Magazine Pvt Ltd & AIM Media House LLC 2024
- Terms of use
- Privacy Policy

Cyber Security
Cyber attacks, cyber defence, quiz and certificate, cyber security tutorial.
Welcome to this introductory course in Cyber security.
This course serves as an excellent primer to the many different domains of Cyber security.
Learning by Reading
We have created 16 tutorial pages for you to learn the fundamentals of Cyber Security:
Basic Cyber Security
Learning by quiz test.
Test your Cyber Security skills with a quiz test.
Start Cyber Security Quiz
My Learning
Track your progress with the free "My Learning" program here at W3Schools.
Log in to your account, and start earning points!
This is an optional feature. You can study at W3Schools without using My Learning.

Kickstart your career
Get certified by completing the course

COLOR PICKER

Contact Sales
If you want to use W3Schools services as an educational institution, team or enterprise, send us an e-mail: [email protected]
Report Error
If you want to report an error, or if you want to make a suggestion, send us an e-mail: [email protected]
Top Tutorials
Top references, top examples, get certified.

COMMENTS
The material is in sections: Cybersecurity Basics; Cybersecurity Threats; Risk Management; Cybersecurity Framework; and Small Business Cybersecurity Resources. You and your team will become familiar with common threats like phishing and ransomware, understand steps you can take every day to prevent falling victim and steps to take to recover ...
Secure Sockets Layer (SSL) internet protocol is the security protocol that allows people to do simple things like purchase items online securely. Netscape released SSL 1.0 in 1994. After improvements, SSL became the core of the language for safely using the web known as Hypertext Transfer Protocol (HTTP).
Cyber security ppt. In this PowerPoint presentation, you can understand the basics of cybersecurity such as how cybersecurity emerged, know about cyber threat evolution, types of cybercrime, how to take preventive measures in order to control the threats, learn various security reasons as well as methods.
My role in cybersecurity! End-users are the last line of defense. As an end-user, you; Create and maintain password and passphrase. Manage your account and password. Secure your computer. Protect the data you are handling. Assess risky behavior online. Equip yourself with the knowledge of security guidelines, policies, and procedures.
Cybersecurity involves everyone and every entity — from you and your neighbors to organizations and companies to governments. It's considered a fundamental necessity, and in this introduction to cybersecurity course, you'll learn how to protect yourself and others from online attacks. This is a great starting point for anyone interested ...
34 likes • 46,071 views. Self-employed. The term cyber security is used to refer to the security offered through on-line services to protect your online information. With an increasing amount of people getting connected to Internet, the security threats that cause massive harm are increasing also. Read more. Education. 1 of 21. Download now ...
Presentation Cyber Security 2017 Challenges for Congresso Security Leaders, São Paulo. October 27th, 2016. Cyber Security 2017 Challenges. Cyber Security 2017 Challenges. Leandro Bennaton ... Basic powerpoint presentation on Cyber security Cyber security presentation.
Cybersecurity pertains to the protection of valuable data—such as social security numbers, business transaction logs, and stored infrastructure data. Information security, meanwhile, protects digital traffic. Even though valuable data can indeed be parsed from this traffic—resulting in yet another service overlap—information security ...
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. These attacks typically include business interruptions or the theft, tampering, or destruction of sensitive information. Ransomware attacks are on the rise and are predicted to cost victims more than $265 billion (USD) annually by 2031.
Earn a document to prove you've completed a course or path that you can share with your network. Learn the Cybersecurity fundamentals that will lay a foundation for securing your technology and personal life from dangerous cyber threats. Includes **Cyber Attacks**, **Social Engineering**, **Threat Actors**, **Third-Party Risks**, **Intelligence ...
The Definition of Security •Security: freedom from, or resilience against, potential harm (or other unwanted coercive change) from external forces (wikipedia) -in physical space •Cybersecurity: the protection of computer systems from theft or damage to their hardware, software or electronic data, as well as from disruption or
For over 20 years, Cisco Networking Academy has changed the lives of 15.1 million students in 180 countries by providing education, technical training, and career mentorship. Learn the basics of Cybersecurity and how you can protect networks and yourself online today. Start your training for a career in Cybersecurity today.
Modules in this learning path. Describe basic cybersecurity threats, attacks, and mitigations. Cyberattacks are impacting individuals and businesses at alarming rates. Being informed about the evolving threat landscape and common types of attacks are key to learning how to protect against attacks. Describe concepts of cryptography.
The security of any organization starts with three principles: Confidentiality, Integrity, Availability. And next in this cyber security for beginners tutorial we will learn about the CIA Triad, which has served as the industry standard for computer security since the time of first mainframes. Fig: CIA triad.
Module 1 • 2 hours to complete. This course focuses on building a foundation for the principles of Cyber Security and protections of data within computers, devices and networks. You will look at the concept of "thinking like a hacker" to learn techniques to defend from the types of attacks that are commonly conducted.
ITU-T X.1205 Definition. Cybersecurity is the collection of tools, policies, security concepts, security safeguards, guidelines, risk. management approaches, actions, training, best practices, assurance and technologies that can be used to. protect the cyber environment and organization and user's assets. Organization and user's assets include.
This presentation includes a basic introduction to AI, an overview of AI technologies, an overview of machine learning underlying technologies, basics of deep learning, introduction to red and blue AI, emerging usages of blue AI, difficulties faced during developing AI solutions and tips for cybersecurity strategy. 2| Cyber Crime And Security
CrowdStrike is providing explanations, examples and best practices on fundamental principles of a variety of cybersecurity topics. If you're looking for information on endpoint protection, cloud security, types of cyber attacks and more, you've come to the right place - welcome to Cybersecurity 101! a. b.
Cybersecurity fundamentals. To grasp the fundamentals of cybersecurity, we'll need to break down the CIA triad. The CIA triad refers to the three principles of cybersecurity: confidentiality, integrity, and availability. The CIA triad model serves as the basis for the development of most cybersecurity systems.
Cybersecurity Fundamentals | Understanding Cybersecurity Basics | Cybersecurity Course | Edureka - Download as a PDF or view online for free. Submit Search. Upload. ... cyber security presentation.pptx. cyber security presentation.pptx kishore golla ...
Cybersecurity aims to protect individuals' and organizations' systems, applications, computing devices, sensitive data and financial assets against computer viruses, sophisticated and costly ransomware attacks, and more. Cyberattacks have the power to disrupt, damage or destroy businesses, and the cost to victims keeps rising.
This means that cybersecurity risk at an enterprise level is not only a board discussion, but also a personal liability for board members. "Communication and reporting is more an art than a science," Olyaei says. "Security leaders must be able to educate, assure, empower and inform the board within the specific period of time allotted to ...
This course serves as an excellent primer to the many different domains of Cyber security. Learning by Reading. We have created 16 tutorial pages for you to learn the fundamentals of Cyber Security: Basic Cyber Security Cyber Crime . Money Making Threats . Dark Web . Networking Basics . Network Layer . Network Transport . Firewalls . Web ...