Daniel's Tech Blog
Cloud Computing, Cloud Native & Kubernetes

Assigning RBAC permissions with Azure Resource Manager templates
Recently, I updated my AKS ARM template supporting the latest AKS feature set and important RBAC role assignments for the AKS cluster.
After having a hard time, I managed to get the RBAC role assignment working.
When you now think what should be so complicated? Check out my tweet on Twitter getting the background information.
-> https://twitter.com/neumanndaniel/status/1294272253211947008
It is not as easy as it sounds. Just using the Microsoft.Authorization resource provider as in the ARM template reference only works on resource group level and above like subscriptions.
-> https://docs.microsoft.com/en-us/azure/templates/microsoft.authorization/roleassignments
Here starts our journey of todays blog post. I walk you through my findings and provide you with the necessary guidance doing the RBAC role assignment with ARM templates in the correct way. So, at least I can spare you some time when this topic arises.
Let us start from the beginning why you can use the Microsoft.Authorization resource provider only on resource group level and above like subscriptions.
When using the RP Microsoft.Authorization we specifically using the resource type roleAssignments.
As you can deploy ARM templates only on MG (management group), subscription and RG (resource group) level, tenant level is also possible, the RP targets the resource at the deployment level. This excludes resources and their sub resources for instance a Virtual Network and its subnets.
Let us take a look at two ARM templates with an RBAC role assignment on subscription and RG level.
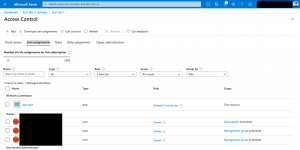
As seen above the template assigns a user object Network Contributor permission on the subscription level.
The Azure CLI command explicitly targets the subscription for the deployment.
Similar looks the template targeting the resource group.
Using the following ARM template assigning the Network Contributor permissions on a VNET subnet will not work.
We get an error message that the assignment scope does not match the scope of the deployment.
So, how you going to do an RBAC role assignment on a resource or sub resource?
Via a sub resource deployment. Each RP has a providers resource type roleAssignments which we can leverage in a sub resource deployment assigning the RBAC role to resources like a VNET or sub resources like a VNET subnet.
The template assumes that the target resource lives in the same RG that the deployment targets. If this is not the case, you must use a nested / linked template where you can specify the resource group.
One important part in the RBAC role assignment via sub resource deployments plays the dependency between the name and the type.
The segment length must be the same.
Not the name defines the segment length it is the type and the /providers/ does not count towards the length.
From the given example someone might think the segment length is five, but as I mentioned that /providers/ does not count the actual segment length is four.
Looking at the name this is true for our name.
I hope you got some useful insights into RBAC role assignments via Azure Resource Manager templates that can spare you some time in the foreseeable future.
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Azure custom permissions on subnet
We have a VNET that is coupled to an Express route, on which we will give our users access to specific subnets.
These subnets are created for each resource group, and the idea is to have these users only able to add machines in their subnet. To allow users to add machines to a subnet I gave them the following permissions:
- Read on Virtual Network
- Contributor on their subnet
However this allowed the users to select all subnets on the virtual network. It simply throws an error when you try to deploy a machine on a subnet you lack contributor on.
I tried creating custom roles, but if I am to create one that only disallows reading as such:
I get the error:
I assume this is because the actions value can not be empty. I'm not sure what I should/could safely add in the actions, and at this point it's starting to look like I'm putting together something complex for what should be quite simple.
So how should I set up/create roles to allow for a user to see and utilize only a single subnet within a larger VNET?
- permissions
- What is it your trying to achieve here, it seems overly complicated. If you only want users to be able to create VM's in specific subnets it sounds like you already achieved that. If you want users not to be able to see what machines are in other subnets then I don't think this is the right method. Even if you do manage to prevent this in the portal, the machines on different subnets can still communicate, users can still gather this data through network tools. If you want to complete separate your teams, then you need separate VNets. – Sam Cogan Oct 26, 2016 at 10:53
- @Sam I want people to be able to see only the subnets they are allowed to create machines in. We already have network security groups in place to prevent communication between subnets. the main problem is that users are presented with a large list of subnets, while they only have access to one. – Reaces Oct 26, 2016 at 11:00
- How many subnets are you talking about? If it's a small number it would be easier to create them as separate VNet's if your not going to allow communication between them anyway – Sam Cogan Oct 26, 2016 at 11:01
- @Sam Creating the subnets is scripted, and the idea is to allow different divisions to be in control of creating their own resource groups with subnet ranges defined by the scripting, currently there are 30, and probably more incoming. – Reaces Oct 26, 2016 at 11:04
We can not put restrictions on a specific subnet. I had the same issue.
The custom rules can only be applied on 1) Resource Groups 2) Resource (vnet is a resource and not subnets, subnets are the outcome of a resource) 3) Subscription
As explained, subnets are not resources and you will not be able to restrict which subnets can and cannot be used, via RBAC/Custom roles feature.
You might have to look into Azure Blueprints or Azure policies for that.
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged permissions powershell azure ..
- The Overflow Blog
- The Good, the Bad, and the Disruptive: Let us know where you stand in the...
- How to train your dream machine
- Featured on Meta
- Our Partnership with OpenAI
- What deliverables would you like to see out of a working group?
Hot Network Questions
- Polarizing paper "almost good enough", but no revision offered
- How do photons have temperature?
- How can my blue and black deck return enchantments from the graveyard?
- Logic behind Stradella Accordion Octaves?
- Older fantasy book series about a boy who trains with a demon to become a wizard
- Why "guilty" or "not guilty"and not "guilty" or "innocent"?
- Extrusion of a parametric surface with different face and boundary colours
- Which duplo digit is 6 or 9?
- How to name a TikZ path?
- Is it an offense to photograph a seahorse?
- A silly entry: different sizes for "True" or "False" boxes in a test
- My other Mac mini's clipboard history has my laptop's clipboard history and it's freaking me out
- I am a US citizen, my wife is Belgian. We intend to spend 6+ months in Italy. Do I need a visa?
- Could ghosts be an airborne species of octopus?
- How to know if you've caught a pokemon in the catching screen in Pokemon Go
- What are the minimum system requirements to run GW-BASIC?
- Why do cryogenic fuels want an extra pressure tank?
- Reasons for implementing op-amps which are not unity-gain stable
- Are one in four victims of intimate partner homicides in Australia male?
- In what situation would universal full-body protective clothing be preferable to living in sealed habitats?
- How long does malware last "in the wild"?
- Does FIDE allow viewing how many IM/GM norms a player has?
- What is the significance behind the Molecule Man's quirk of consistently asking visitors for food?
- BoM says of itself it is comparable to the Bible and contains the fulness of the everlasting gospel. Why is not Mormon doctrine taught in the BoM?
Creating AKS cluster with Managed Identity to give it access to a subnet
I configured an AKS cluster to use a system-assigned managed identity to access to other Azure resources
I want to use that managed identity (the service principal created inside AKS cluster section code) to give it roles like this Network Contributor over a subnet:
But the output I got after terraform apply is:
It seems the service principal is being created does not have enough privileges to perform a role assignment over the subnet, or maybe I have wrong the scope attribute. I am passing there, the aks subnet id.
What am I doing wrong?
UPDATE: Checking the way Managed Identities has role assigneds, looks like we can only assign it roles related with Subscriptions, Resource Groups, Storage services, SQL services, and KeyVault.

Reading here
Before you can use the managed identity, it has to be configured. There are two steps:
Assign a role for the identity, associating it with the subscription that will be used to run Terraform. This step gives the identity permission to access Azure Resource Manager (ARM) resources.
Configure access control for one or more Azure resources. For example, if you use a key vault and a storage account, you will need to configure the vault and container separately.
Before you can create a resource with a managed identity and then assign an RBAC role, your account needs sufficient permissions. You need to be a member of the account Owner role, or have Contributor plus User Access Administrator roles.
Trying to proceed accordingly, I defined this section code:
The terraform workflow try to create the role …
but finally got the same AuthorizationFailed error this time over the subscription passed.
By the way, I have the owner role in the subscription I am working with.
When we create a managed identity, it creates a service principal to be used to assign roles to that managed identity behind the scenes
Azure AD creates an AD identity when you configure an Azure resource to use a system-assigned managed identity. The configuration process is described in more detail, below. Azure AD then creates a service principal to represent the resource for role-based access control (RBAC) and access control (IAM). The lifecycle of a system-assigned identity is tied to the resource it is enabled for: it is created when the resource is created and it is automatically removed when the resource is deleted.
From Microsoft Docs
To call this API, you must have access to the Microsoft.Authorization/roleAssignments/write operation. Of the built-in roles, only Owner and User Access Administrator are granted access to this operation
It means, the service principal created (in my case I had an existing one used to create the role - the client afd5bd09-c294-4597-9c90-e1ee293e5f3a shown in the error message - ), must have an Owner or User Administrator role. In my case my service principal did not have it.
So it was a matter to have acces to Microsoft.Authorization/roleAssignments/write operation. All that I did was to go to my subscription I am owner of, and assign the User Access Administrator role to the Service principal that terraform workflow was referencing and it works.
Could you clarify that you did indeed have to manually log into the portal and assign the permissions to get this to work?
I think I am in a similar boat, but I can’t log in and manually approve / assign these permissions. This is part of a pipeline where it all has to be 100% automatic.
Plz see How do I automatically create service principals or MSIs with Terraform for use in Azure Pipelines to manage AKS resources? - Stack Overflow
It seems this was possible per this feature request, but has since stopped working https://github.com/hashicorp/terraform-provider-azuread/issues/40#issuecomment-477076926
Any thoughts on how to implement this automatically again?
Hansen Cloud
All things Cloud, by Matt Hansen.

Custom “Virtual Network Operator” Role in Azure
*Edit* 6/9/20: At the time of writing this blog custom roles were not available in the Azure Portal. Since that feature now exists, I’ve added how to create this role through the portal to the end of this blog.
We all know that cloud environments are different than on premises. Development environments can be even more difficult, the right cross between giving freedom to produce business value and enough security and controls to maintain a good security posture. Recently I came across a scenario where the design was that the networking components (Virtual Network, S2S VPN, Peerings, Service Endpoints, UDRs, Subnets, etc.) were all under the control of a Networking team so that the Azure environment would be an extension of their local network. From a permissions standpoint though this caused some problems. The goal would be to empower developers to build whatever they need and just attach it to the vNet when connectivity was needed, with the caveat that they shouldn’t be able to modify any of the network settings or configurations in the shared vNet. This however, turned out not to be possible with default IAM roles.
In my testing, even though you’re not “modifying” anything per se in the vNet – when attaching a network interface card to a Subnet it does require write access. Reader access will give the user this error.

After looking through the default IAM roles, there aren’t any that do what I need them to do. Alas, a custom role is needed. For reference, please checkout this docs page for custom roles – https://docs.microsoft.com/en-us/azure/role-based-access-control/custom-roles .
First, I need to see what actions are available to pack into the custom role so I run the following command in Azure Powershell and get these results.
Get-AzProviderOperation “Microsoft.Network/virtualNetworks/*” | FT OperationName, Operation, Description -AutoSize

Great, now I can see what is available. It looks like the actions that I need are the /subnet/join/action and /subnet/joinViaServiceEndpoint/Action. Based on the descriptions these two will essentially give “operator” role to the vnet. The assignee will be able to use the subnet(s) but not able to modify them.
Next, you can use one of the template references in the Microsoft Docs link ( https://docs.microsoft.com/en-us/azure/role-based-access-control/custom-roles-powershell#create-a-custom-role-with-json-template ) and modify the actions.
{ “Name”: “Custom – Network Operator Role”, “Id”: null, “IsCustom”: true, “Description”: “Allows for read access to Azure network and join actions for service endpoints and subnets.”, “Actions”: [ “Microsoft.Network/virtualNetworks/subnets/join/action”, “Microsoft.Network/virtualNetworks/subnets/joinViaServiceEndpoint/action”, “Microsoft.Network/virtualNetworks/read” ], “NotActions”: [], “AssignableScopes”: [ “/subscriptions/00000000-0000-0000-0000-000000000000”, “/subscriptions/11111111-1111-1111-1111-111111111111” ] }
After modifying the assignable subscription IDs, save that as a .json file and use it in the following command to import the custom role.
New-AzRoleDefinition -InputFile “C:\FileFolderLocationPath\CustomNetworkOperatorRole.json”
After a portal refresh you get the custom role available as an IAM role assignment.

There you go, after assigning this role the user was able to create VMs and attach them to the Virtual Network while still leaving control of the Network configuration to the Networking Team.
————————————————————————-
EDIT 6/9/20: Now that custom roles are available in the portal I’ve added how to create this role that way below.
Using the documentation on how to create custom IAM roles in the Azure portal you can clone any role, but I’m just going to use the “Network Contributor” role to clone.

I am going to just “start from scratch”, though you can easily use this page to modify the permissions set of a certain role that already exists. Additionally, if you have the JSON (like we generated before with powershell) you can just upload that here.

Now go ahead and add new permissions by going to the “Microsoft Network” Category and selecting the same permissions we wrote in the JSON and used with the powershell command above.

After adding those the next page will show you the permission that you’ve added, let’s double check those and make sure we have what we need.

Looks good, now we can set a scope where this role can be applied. I have this one scoped to the whole subscription, but you can use the interface to easily change that on this page.

Alright, that’s about it – let’s take a quick look at the summary pages. You can see that the portal actually generates the JSON, which is nice if you want to assign roles using Azure Policy or any other automation tooling.

Nice! Now we can see that users can use the four above actions which will allow them to interact with, and use a shared hub-style virtual network while now allowing full contributor access.
I hope I’ve made your day at least a little bit easier!
If you have any questions or suggestions for future blog posts feel free to comment below, or reach out to me via email, twitter, or LinkedIn.
Share this:
https://www.linkedin.com/in/matthansen0/
2 thoughts on “ Custom “Virtual Network Operator” Role in Azure ”
February 3, 2021 4:23 am
Just what i was looking for 🙂 What other permissions did you grant the devs so that they could spin up all the stuff they needed? I have the same requirement to restrict the networking stuff (also prevent them from creating VNGs and the like) Obviously they need to be able to spin up VMs, containers, databases & data lake etc… all the stuff devs like.
September 23, 2021 8:09 pm
Great explanation, ran into a similar issue today. Many thanks!
Leave a Reply Cancel reply
Discover more from hansen cloud.
Subscribe now to keep reading and get access to the full archive.
Type your email…
Continue reading
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
List Azure role assignments using the Azure portal
- 3 contributors
Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To determine what resources users, groups, service principals, or managed identities have access to, you list their role assignments. This article describes how to list role assignments using the Azure portal.
If your organization has outsourced management functions to a service provider who uses Azure Lighthouse , role assignments authorized by that service provider won't be shown here. Similarly, users in the service provider tenant won't see role assignments for users in a customer's tenant, regardless of the role they've been assigned.
Prerequisites
List role assignments for a user or group.
A quick way to see the roles assigned to a user or group in a subscription is to use the Azure role assignments pane.
In the Azure portal, select All services from the Azure portal menu.
Select Microsoft Entra ID and then select Users or Groups .
Click the user or group you want list the role assignments for.
Click Azure role assignments .
You see a list of roles assigned to the selected user or group at various scopes such as management group, subscription, resource group, or resource. This list includes all role assignments you have permission to read.

To change the subscription, click the Subscriptions list.
List owners of a subscription
Users that have been assigned the Owner role for a subscription can manage everything in the subscription. Follow these steps to list the owners of a subscription.
In the Azure portal, click All services and then Subscriptions .
Click the subscription you want to list the owners of.
Click Access control (IAM) .
Click the Role assignments tab to view all the role assignments for this subscription.
Scroll to the Owners section to see all the users that have been assigned the Owner role for this subscription.

List or manage privileged administrator role assignments
On the Role assignments tab, you can list and see the count of privileged administrator role assignments at the current scope. For more information, see Privileged administrator roles .
In the Azure portal, click All services and then select the scope. For example, you can select Management groups , Subscriptions , Resource groups , or a resource.
Click the specific resource.
Click the Role assignments tab and then click the Privileged tab to list the privileged administrator role assignments at this scope.

To see the count of privileged administrator role assignments at this scope, see the Privileged card.
To manage privileged administrator role assignments, see the Privileged card and click View assignments .
On the Manage privileged role assignments page, you can add a condition to constrain the privileged role assignment or remove the role assignment. For more information, see Delegate Azure role assignment management to others with conditions .

List role assignments at a scope
Follow these steps:
Click the Role assignments tab to view all the role assignments at this scope.

On the Role assignments tab, you can see who has access at this scope. Notice that some roles are scoped to This resource while others are (Inherited) from another scope. Access is either assigned specifically to this resource or inherited from an assignment to the parent scope.

List role assignments for a user at a scope
To list access for a user, group, service principal, or managed identity, you list their role assignments. Follow these steps to list the role assignments for a single user, group, service principal, or managed identity at a particular scope.

On the Check access tab, click the Check access button.
In the Check access pane, click User, group, or service principal or Managed identity .
In the search box, enter a string to search the directory for display names, email addresses, or object identifiers.

Click the security principal to open the assignments pane.
On this pane, you can see the access for the selected security principal at this scope and inherited to this scope. Assignments at child scopes are not listed. You see the following assignments:
- Role assignments added with Azure RBAC.
- Deny assignments added using Azure Blueprints or Azure managed apps.
- Classic Service Administrator or Co-Administrator assignments for classic deployments.

List role assignments for a managed identity
You can list role assignments for system-assigned and user-assigned managed identities at a particular scope by using the Access control (IAM) blade as described earlier. This section describes how to list role assignments for just the managed identity.
System-assigned managed identity
In the Azure portal, open a system-assigned managed identity.
In the left menu, click Identity .

Under Permissions , click Azure role assignments .
You see a list of roles assigned to the selected system-assigned managed identity at various scopes such as management group, subscription, resource group, or resource. This list includes all role assignments you have permission to read.

To change the subscription, click the Subscription list.
User-assigned managed identity
In the Azure portal, open a user-assigned managed identity.
You see a list of roles assigned to the selected user-assigned managed identity at various scopes such as management group, subscription, resource group, or resource. This list includes all role assignments you have permission to read.

List number of role assignments
You can have up to 4000 role assignments in each subscription. This limit includes role assignments at the subscription, resource group, and resource scopes. To help you keep track of this limit, the Role assignments tab includes a chart that lists the number of role assignments for the current subscription.

If you are getting close to the maximum number and you try to add more role assignments, you'll see a warning in the Add role assignment pane. For ways that you can reduce the number of role assignments, see Troubleshoot Azure RBAC limits .

Download role assignments
You can download role assignments at a scope in CSV or JSON formats. This can be helpful if you need to inspect the list in a spreadsheet or take an inventory when migrating a subscription.
When you download role assignments, you should keep in mind the following criteria:
- If you don't have permissions to read the directory, such as the Directory Readers role, the DisplayName, SignInName, and ObjectType columns will be blank.
- Role assignments whose security principal has been deleted are not included.
- Access granted to classic administrators are not included.
Follow these steps to download role assignments at a scope.
In the Azure portal, click All services and then select the scope where you want to download the role assignments. For example, you can select Management groups , Subscriptions , Resource groups , or a resource.
Click Download role assignments to open the Download role assignments pane.

Use the check boxes to select the role assignments you want to include in the downloaded file.
- Inherited - Include inherited role assignments for the current scope.
- At current scope - Include role assignments for the current scope.
- Children - Include role assignments at levels below the current scope. This check box is disabled for management group scope.
Select the file format, which can be comma-separated values (CSV) or JavaScript Object Notation (JSON).
Specify the file name.
Click Start to start the download.
The following show examples of the output for each file format.

Related content
- Assign Azure roles using the Azure portal
- Troubleshoot Azure RBAC
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources
Using azure role with subnet-component
In order to use Azure roles within a subnet, you need to manage Azure role assignments for a subnet within an Azure virtual network (VNet). The goal is to define a custom role that has specific permissions and then assign it to a principal (such as a user, group, or service principal) for the scope of a subnet.
To do this using Pulumi and Azure, we will use the following resources:
- azure-native.network.VirtualNetwork : to define a VNet in Azure.
- azure-native.network.Subnet : to create a subnet within the VNet.
- azure-native.authorization.RoleDefinition : to define a custom role with specific permissions.
- azure-native.authorization.RoleAssignment : to assign the role to a principal for the subnet's scope.
Here's a detailed breakdown of what each part of the code does:
- Import necessary packages and initialize a Pulumi program.
- Create a virtual network and a subnet within that VNet.
- Define a custom role that outlines the permissions we want to grant.
- Assign that role to a principal with the scope set to the subnet.
Here is the TypeScript program that demonstrates these steps:
In this program:
- We create a resource group my-resource-group which acts as a logical container for our network resources.
- A virtual network my-virtual-network and a subnet my-subnet are created with specified IP address ranges.
- We then define a custom role my-custom-role with specific actions (permissions) that we would like principals assigned this role to perform. The scope for the custom role is limited to our subnet by specifying its ARM ID.
- The role definition customRoleDefinition holds the actions and scopes, and is used in my-role-assignment to assign the role to the principalId .
Remember to replace "put-your-principal-id-here" with the actual principal ID you want to assign the custom role to. This principal ID represents the security principal (a user, group, managed identity, or application) in Azure Active Directory.
Exporting subnetId at the end of the program allows you to easily reference the subnet's ARM ID outside of Pulumi, such as in other deployment scripts or in the Azure portal.
To apply this Pulumi program, save the code in a index.ts file, and deploy it using the Pulumi CLI. This will create the resources and configure the role assignment as defined.
- TS TypeScript
- JS JavaScript
- TF Terraform
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement . We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Network Contributor role assignment fails with UserAssigned Identity and Azure subnet #405
bonddim commented Jul 5, 2023 • edited
zioproto commented Jul 5, 2023
Sorry, something went wrong.
bonddim commented Jul 6, 2023
lonegunmanb commented Jul 11, 2023 • edited
- 👍 1 reaction
Successfully merging a pull request may close this issue.

IMAGES
VIDEO
COMMENTS
In this section, you remove a subnet delegation for an Azure service. Portal. PowerShell. Azure CLI. Sign-in to the Azure portal. In the search box at the top of the portal, enter Virtual network. Select Virtual networks in the search results. Select vnet-1. Select Subnets in Settings.
Bicep version Bicep CLI version 0.3.1 (d0f5c9b) Describe the bug I am not able to create a role assignment for the scope subnet. I want to assigned my servicePrincipal the role 'Network Contributer' as part of the AKS deployment. resourc...
Since Azure Resource Manager sometimes caches configurations and data to improve performance, it can sometimes take up to 30 minutes for changes to take effect when you assign roles or remove role assignments. Using Azure CLI, you can force a refresh of your role assignment changes by signing out and signing in.
Let us take a look at two ARM templates with an RBAC role assignment on subscription and RG level. As seen above the template assigns a user object Network Contributor permission on the subscription level. The Azure CLI command explicitly targets the subscription for the deployment. Similar looks the template targeting the resource group.
1. We can not put restrictions on a specific subnet. I had the same issue. The custom rules can only be applied on 1) Resource Groups 2) Resource (vnet is a resource and not subnets, subnets are the outcome of a resource) 3) Subscription. As explained, subnets are not resources and you will not be able to restrict which subnets can and cannot ...
1.Use Azure portal: Navigate to the vnet in the portal -> Access control (IAM) -> Role assignments -> search for the name of your service principal like below. 2.Use Azure CLI: az role assignment list --assignee SP_CLIENT_ID --scope VNET_ID. answered May 5, 2020 at 5:57.
Role assignments are the way you control access to Azure back end and infrastructure resources. If the built-in roles do not meet the specific needs of your organization, Azure Role Based Access Control (RBAC) allows account owners to create custom roles that an administrator can assign to Users/User groups. You can configure role assignments ...
For system-assigned managed identity, it's only supported to provide your own subnet and route table via Azure CLI because Azure CLI automatically adds the role assignment. If you're using an ARM template or other clients, you must use a user-assigned managed identity , assign permissions before cluster creation, and ensure the user-assigned ...
There are two steps: Assign a role for the identity, associating it with the subscription that will be used to run Terraform. This step gives the identity permission to access Azure Resource Manager (ARM) resources. Configure access control for one or more Azure resources. For example, if you use a key vault and a storage account, you will need ...
edited. I faced the same issue before, and I've solved my case. In my case, the root issue is due to too small range of subnet (192.168.1./26) which was specifed as --vnet-subnet-id of az aks create command. And the command just shows Could not create a role assignment for subnet.
Actual. Yesterday, on 26.06.2019 I was able to open UI (separate blade for management of single subnet) with subnet details, where on Users tab I could add/remove role assignments to the subnet.. This is still documented in the Change subnet settings section of Add, change, or delete a virtual network subnet.Quote:
On the Role tab, select a role that you want to use.. You can search for a role by name or by description. You can also filter roles by type and category. If you want to assign a privileged administrator role, select the Privileged administrator roles tab to select the role.. For best practices when using privileged administrator role assignments, see Best practices for Azure RBAC.
After modifying the assignable subscription IDs, save that as a .json file and use it in the following command to import the custom role. New-AzRoleDefinition -InputFile "C:\FileFolderLocationPath\CustomNetworkOperatorRole.json". After a portal refresh you get the custom role available as an IAM role assignment.
In the Azure portal, click All services and then select the scope. For example, you can select Management groups, Subscriptions, Resource groups, or a resource.. Click the specific resource. Click Access control (IAM).. Click the Role assignments tab to view all the role assignments at this scope.. On the Role assignments tab, you can see who has access at this scope.
In order to use Azure roles within a subnet, you need to manage Azure role assignments for a subnet within an Azure virtual network (VNet). The goal is to define a custom role that has specific permissions and then assign it to a principal (such as a user, group, or service principal) for the scope of a subnet. To do this using Pulumi and Azure ...
Hello all, the reason of could not create role assignment for subnet is because of the maxPods. The count has to be greater than 30. This is autogenerated. Please review and update as needed. Describe the bug. I'm unable to create a kubernetes cluster with the below az cli command, with the settings/inputs given. Command Name az aks create. Errors:
Module tries to assign role to non-existent SystemAssigned Identity. Steps to Reproduce. terraform apply. Important Factoids. No response. References. ... assignment fails if using UserAssigned Identity Network Contributor role assignment fails with UserAssigned Identity and Azure subnet Jul 5, 2023. Copy link Contributor.