Using Power Automate to get the list of users an app has been shared with?
Have you ever wanted to get the list of users a canvas app has been shared with?
Of course you could go to the maker portal and look at it there:
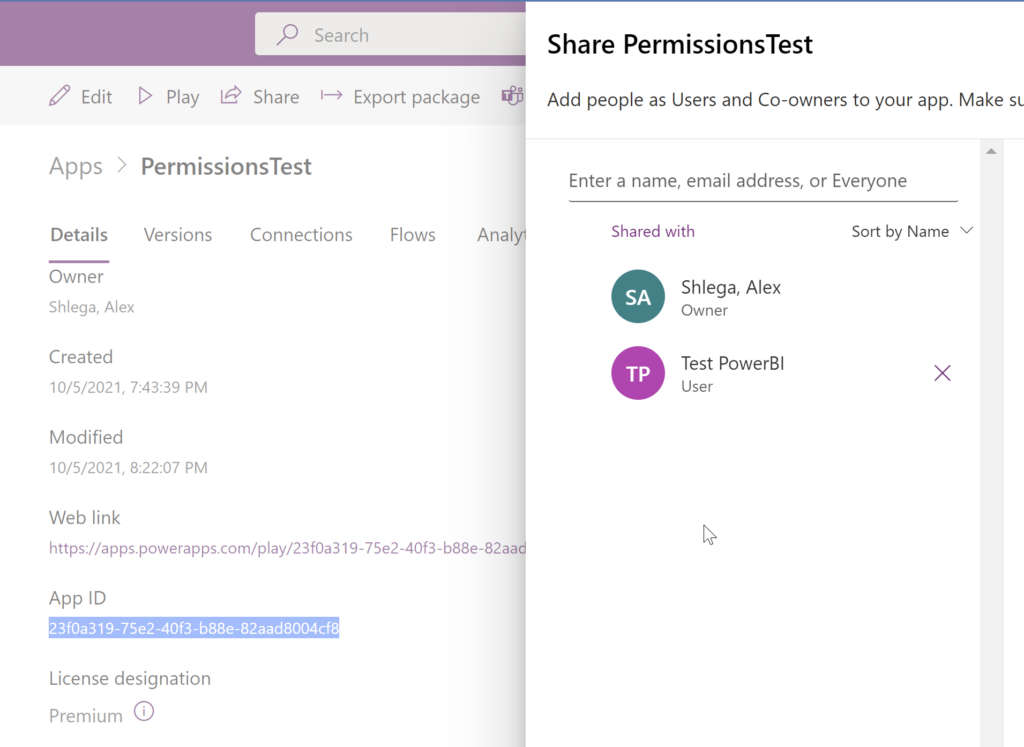
But you can also do it in your flows easily (assuming you have permissions).
There is Power Apps for Admins Connector:
https://docs.microsoft.com/en-us/connectors/powerappsforadmins/
And it offers “Get App Role Assignments as Admin” action which will give you the list of users for any given app in any given environment.
Here is an example:
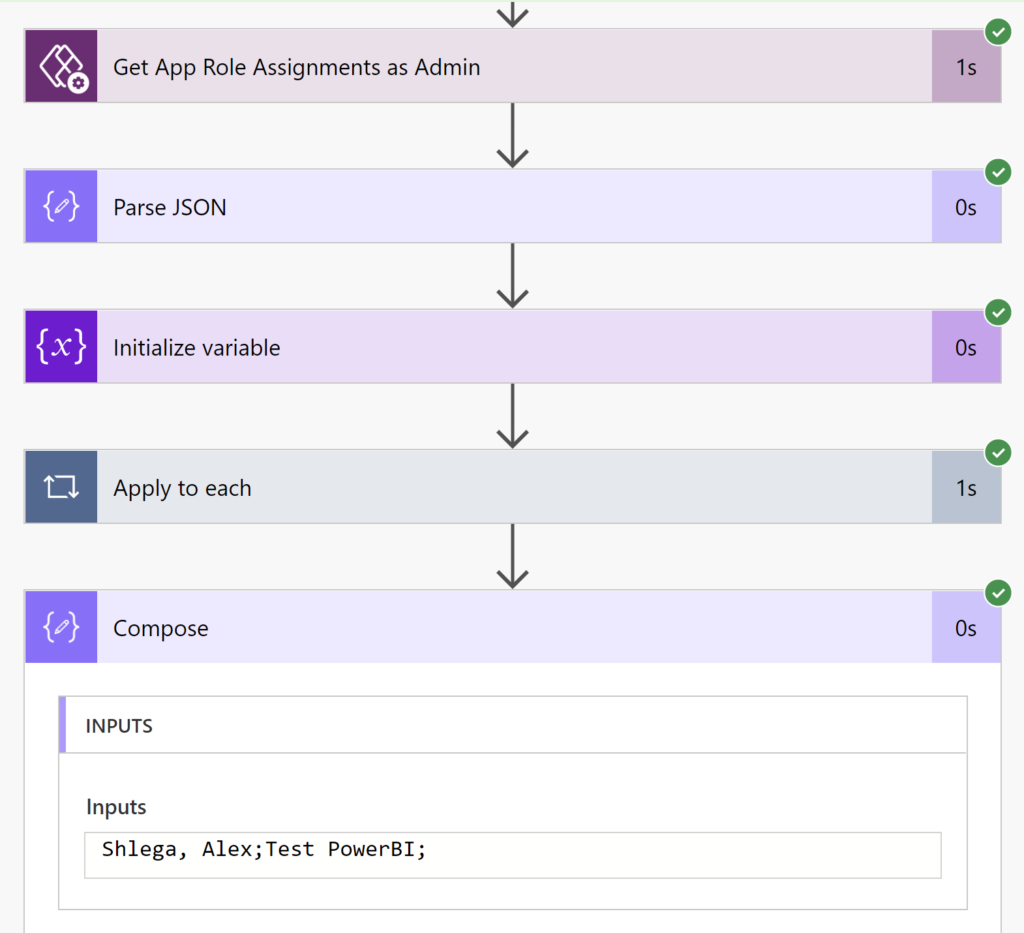
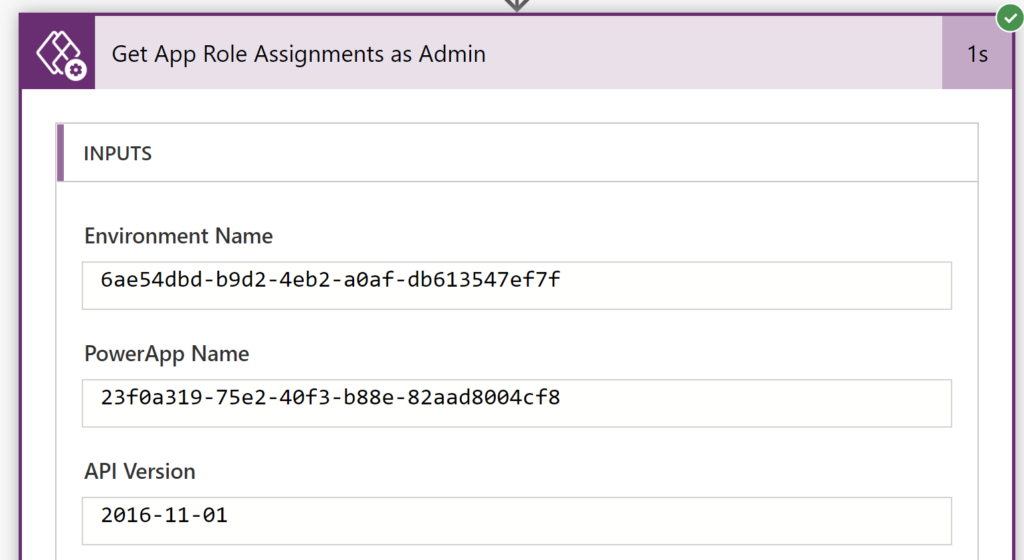
As you can see, the output of this flow matches the original screenshot. You just need to pass environment ID and application ID to the action
And, from there, you need to parse json and format the output the way you want it to be formatted.
So how/why would we use it? In reality, this could probably help with monitoring/notifications. Which is where a lot of this functionality would already be available out of the box in the CoE toolkit:
https://docs.microsoft.com/en-us/power-platform/guidance/coe/starter-kit
But, if you don’t want to deal with the CoE toolkit rollout yet, you might implement your own flow for now using Power Apps for Admins Connector. And if you are wondering whether there is a similar connector for Power Automate flows – the answer is yes, here is another link: https://docs.microsoft.com/en-us/connectors/microsoftflowforadmins/

Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Good Workaround!
Full IGA using Azure AD – Getting app role assignments using PowerShell
In this post I will quickly demo how to use PowerShell to get app role assignments for all application using the Microsoft Graph.
You should have followed my previous post in order to have created an application, added some appRoles to the manifest and granted access to the Graph.
Let’s recap the important parts:
1 – Create an enterprise application in Azure AD

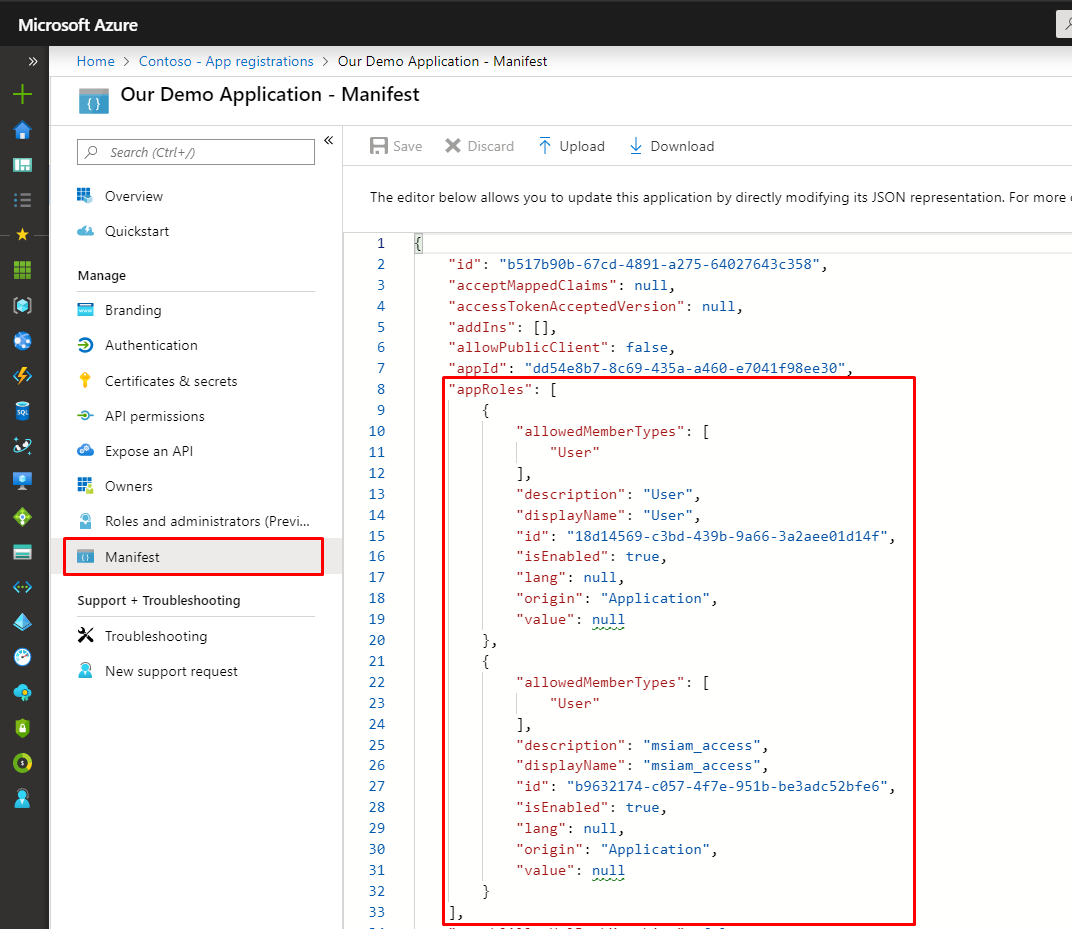
2 – Go to “app registrations”, find the app and add appRoles to the manifest
The following are provided by default, disable those and add some custom ones. See the below example roles.
3 – Go back to enterprise applications and assign users some roles
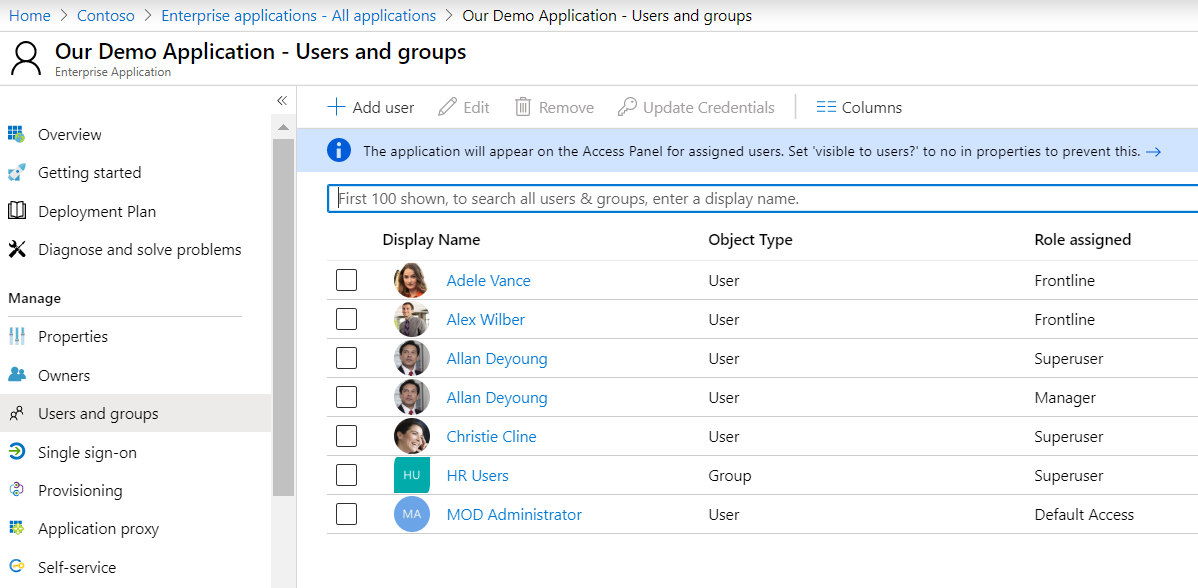
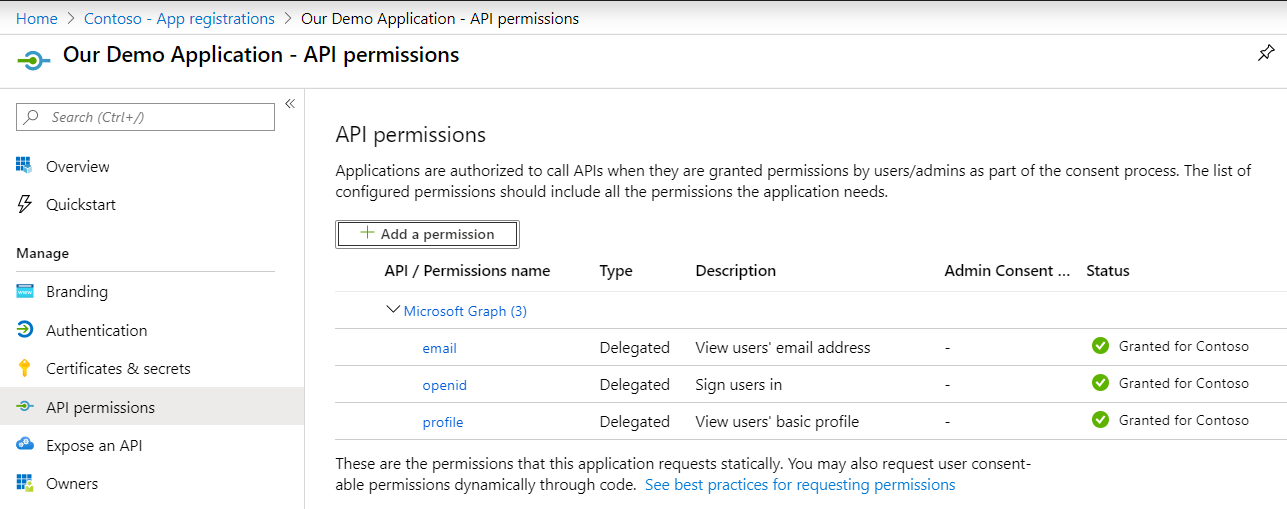
4 – Grant access to the required Graph resources
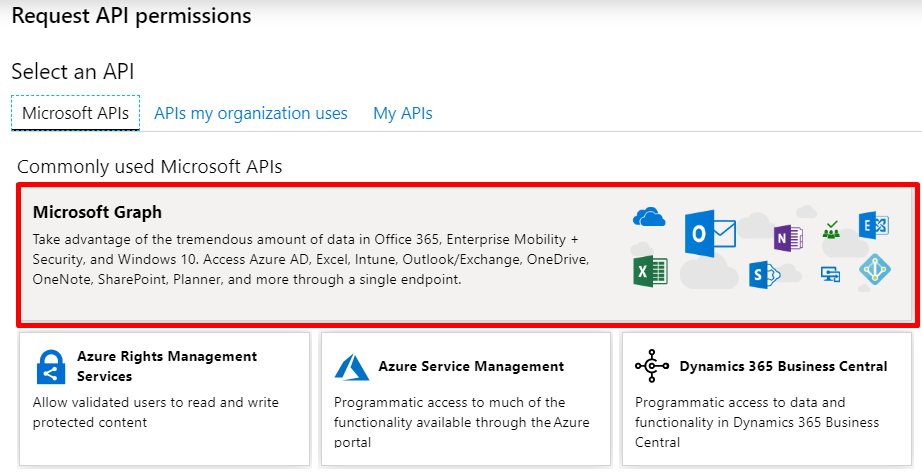
Go to app registrations, find the application and go to “API permissions”. Click “Add a permission”:
Select the Microsoft Graph:
Choose Application permissions, as we are doing things without a user context:
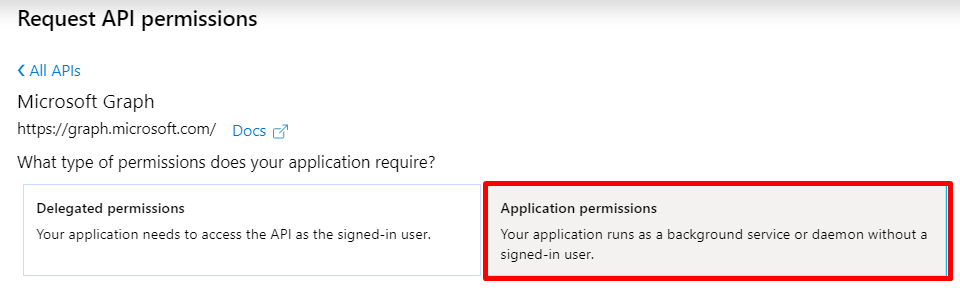
Add “User.Read.All” and “Group.Read.All” and click save.
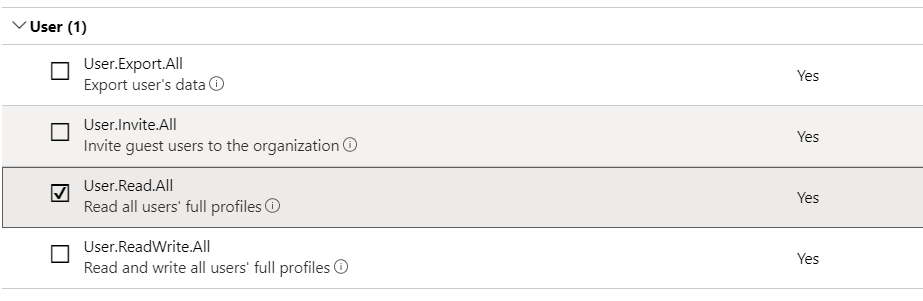
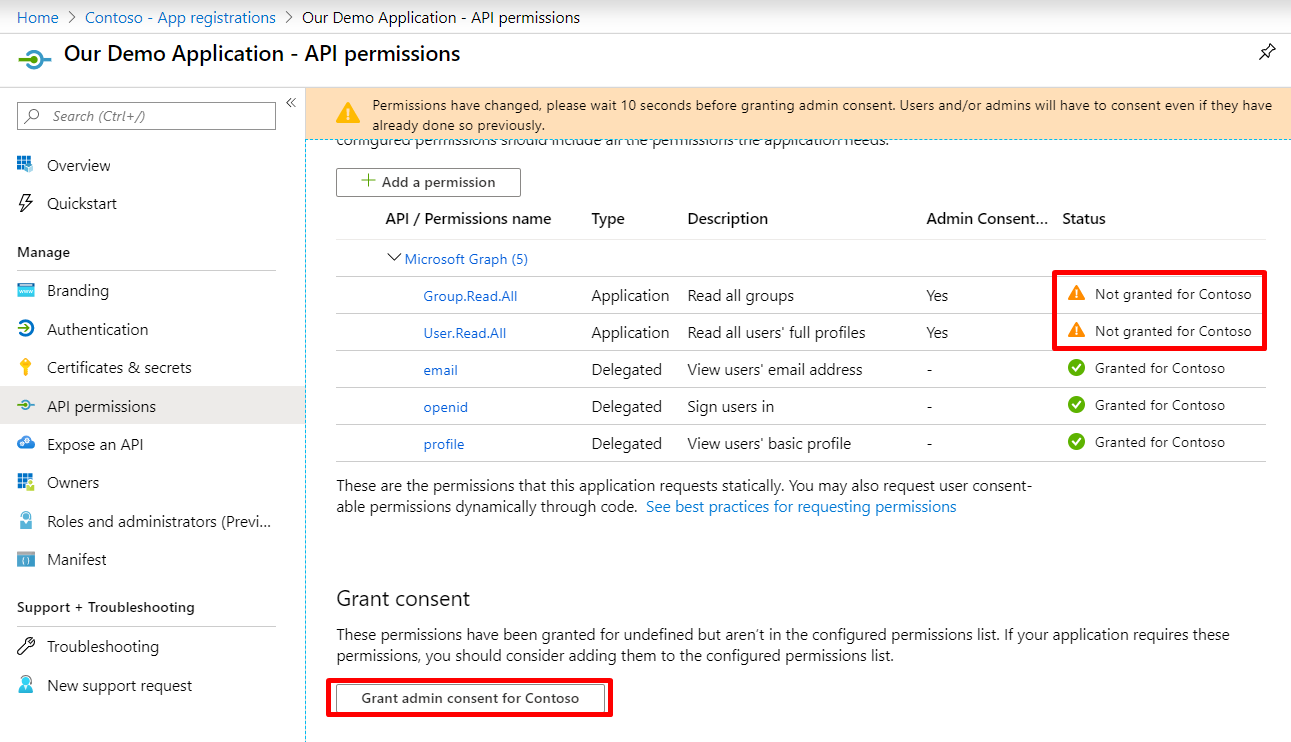
You will see that the added permissions now have “Not granted for <Organization>” as status. Click “Grant admin consent for <Organization>” in order to enable these new permissions:
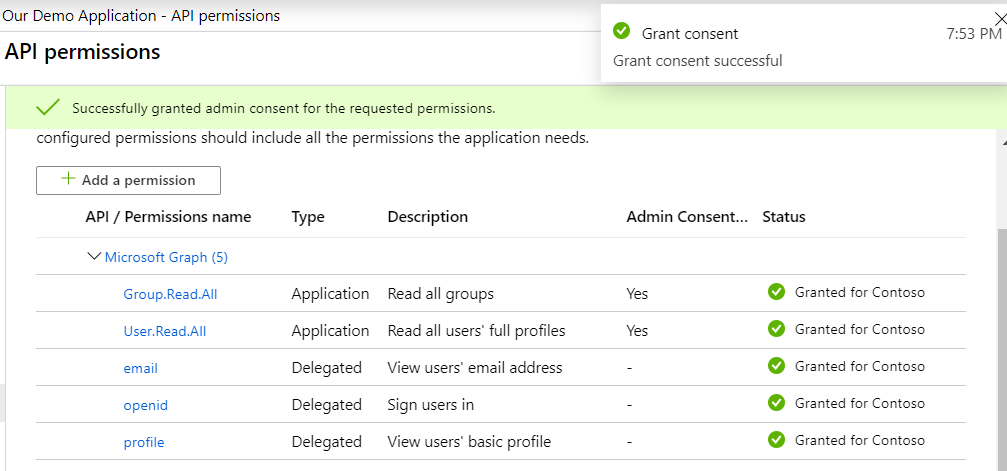
This is what it should look like:
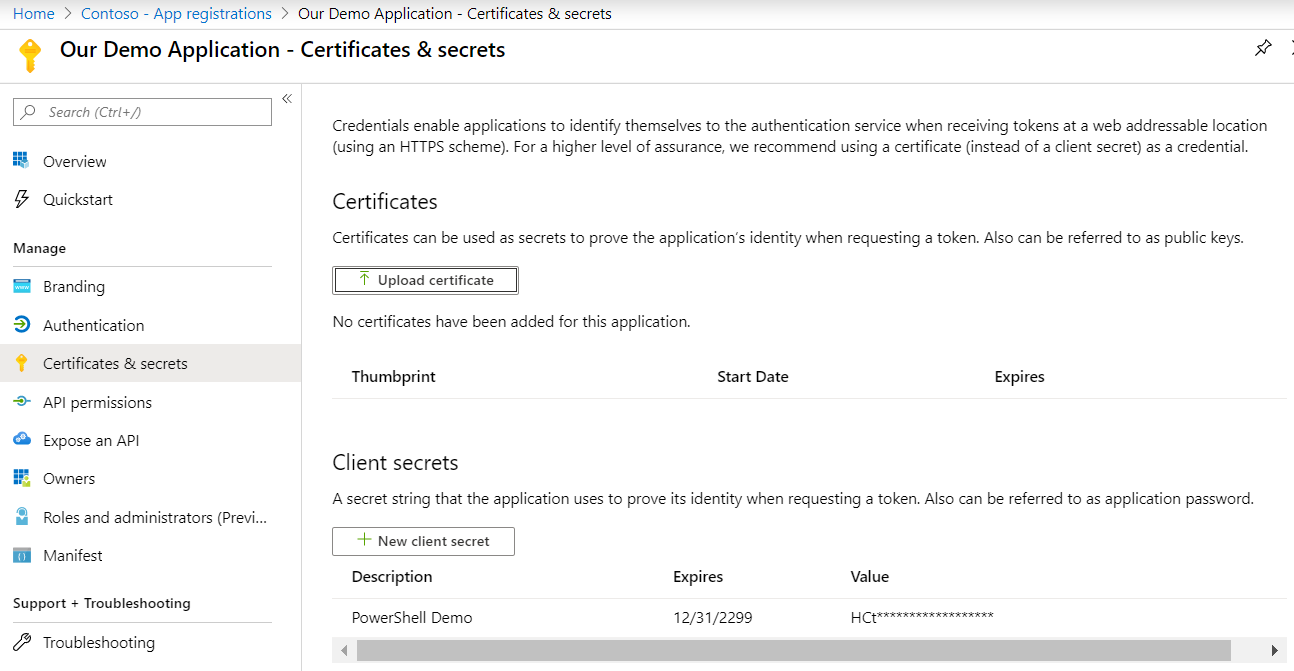
5 – Request data with PowerShell
First, generate a secret under app registrations in Azure AD. This is the $secret variable in the below PowerShells.
Go the enterprise application and copy the “Application ID” – this is the $clientid variable in the below PowerShells.
Copy “Object ID” – this is the $servicePrincipalId variable in the below PowerShells.
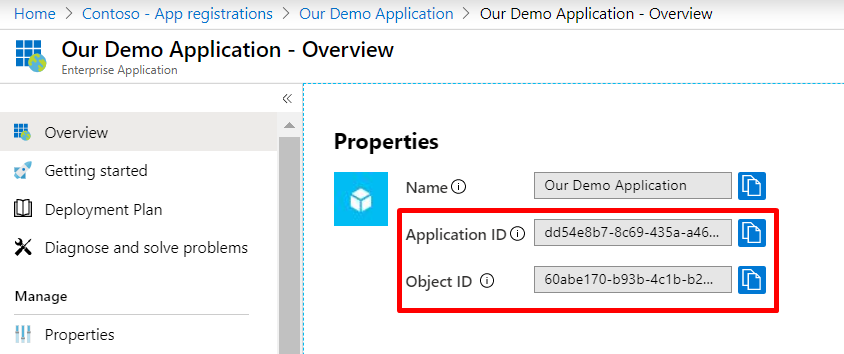
The $tenant variable can be either any custom domain registered in the tenant, the default domain or the tenant id (you can find it here) found on the app registrations page on your application.
The first example PowerShell will return a simple grid view with a multi valued column containing the roles of each assigned object. The script will not dig into the group members.
And here is an example for you that also digs into the different assigned groups and fetches all transitive members of those:
That’s it, I have now gone through three ways of getting the application role assignments from Azure AD into your application:
- SCIM provisioning
- At sign in (OAuth ID Token or SAML Claim)
- Fetching by Graph calls
The next posts will focus on how to actually manage application role assignments, dynamically assigning, using Entitlement Management to allow both internal and invited users to request access and other means. Stay tuned!
Share this:
- Full IGA using Azure AD
Published by Marius Solbakken
View all posts by Marius Solbakken
One thought on “ Full IGA using Azure AD – Getting app role assignments using PowerShell ”
- Pingback: Full IGA using Azure AD – Entitlement Management – Good Workaround!
Leave a comment Cancel reply

- Already have a WordPress.com account? Log in now.
- Subscribe Subscribed
- Copy shortlink
- Report this content
- View post in Reader
- Manage subscriptions
- Collapse this bar

Power Apps for Admins
Power Apps Management Connector for Administrators
Get-AdminAppRoleAssignment
Summary : Get App Role Assignments as Admin
Description : Returns permissions for a PowerApp.
PowerAppsforAdmins.Get-AdminAppRoleAssignment (string environment, string app, [Optional]string api-version, [advanced][Optional]integer $top)
Parameters:
Type: Get-AdminAppRoleAssignmentResponse
Set-AdminAppOwner
Summary : Set App Owner
Description : Updates a PowerApp's owner role, and specifies the old owner's new role.
PowerAppsforAdmins.Set-AdminAppOwner (string environment, string app, [Optional]string api-version, [Optional]string Content-Type, [Optional]Set-AdminAppOwnerParameterBody body)
Get-AdminApps
Summary : Get Apps as Admin
Description : Returns a list of apps.
PowerAppsforAdmins.Get-AdminApps (string environment, [Optional]string api-version, [advanced][Optional]integer $top, [Optional]string $skiptoken)
Type: ResourceArray[PowerApp]
Get-AdminApp
Summary : Get App as Admin
Description : Returns a PowerApp.
PowerAppsforAdmins.Get-AdminApp (string environment, string app, [Optional]string api-version)
Type: PowerApp
Remove-AdminApp
Summary : Remove App as Admin
Description : Deletes a PowerApp.
PowerAppsforAdmins.Remove-AdminApp (string environment, string app, [Optional]string api-version)
Edit-AdminAppRoleAssignment
Summary : Edit App Role Assignment as Admin
Description : Sets permissions for a PowerApp.
PowerAppsforAdmins.Edit-AdminAppRoleAssignment (string environment, string app, [Optional]string api-version, [Optional]string $filter, [Optional]Edit-AdminAppRoleAssignmentParameterBody body)
Type: Edit-AdminAppRoleAssignmentResponse
Get-AdminConnections
Summary : Get Connections as Admin
Description : Returns a list of Connections.
PowerAppsforAdmins.Get-AdminConnections (string environment, [Optional]string api-version, [advanced][Optional]integer $top)
Type: Get-AdminConnectionsResponse
Remove-AdminConnection
Summary : Remove Connection as Admin
Description : Deletes a Connection.
PowerAppsforAdmins.Remove-AdminConnection (string environment, string connectorName, string connectionName, [Optional]string api-version)
Get-AdminConnectionRoleAssignment
Summary : Get Connection Role Assignments as Admin
Description : Returns all permissions for a Connection.
PowerAppsforAdmins.Get-AdminConnectionRoleAssignment (string environment, string connectorName, string connectionName, [Optional]string api-version, [advanced][Optional]integer $top)
Type: Get-AdminConnectionRoleAssignmentResponse
Edit-AdminConnectionRoleAssignment
Summary : Edit Connection Role Assignment as Admin
Description : Sets permissions for a Connection.
PowerAppsforAdmins.Edit-AdminConnectionRoleAssignment (string environment, string connector, string connection, [Optional]string api-version, [Optional]string Content-Type, [Optional]Edit-AdminConnectionRoleAssignmentParameterBody body)
Get-AdminConnectors
Summary : Get Custom Connectors as Admin
Description : Returns a list of custom Connectors.
PowerAppsforAdmins.Get-AdminConnectors (string environment, [Optional]string api-version, [advanced][Optional]integer $top)
Type: Get-AdminConnectorsResponse
Get-AdminConnectorRoleAssignment
Summary : Get Connector Role Assignments as Admin
Description : Returns permissions for a custom Connector.
PowerAppsforAdmins.Get-AdminConnectorRoleAssignment (string environment, string connectorName, [Optional]string api-version, [advanced][Optional]integer $top)
Type: Get-AdminConnectorRoleAssignmentResponse
Edit-AdminConnectorRoleAssignment
Summary : Edit Connector Role Assignment as Admin
Description : Sets permissions for a Connector.
PowerAppsforAdmins.Edit-AdminConnectorRoleAssignment (string environment, string connectorName, [Optional]string api-version, [Optional]string Content-Type, [Optional]Edit-AdminConnectorRoleAssignmentParameterBody body)
ConnectionReference
Description :
Properties:
Edit-AdminAppRoleAssignmentParameterBody
Description : properties
Description : principal
Edit-AdminAppRoleAssignmentResponse
Description : App Role Assignment properties object.
Description : App Role Assignment principal object.
ResourceResponsesItem
Edit-adminconnectionroleassignmentparameterbody, edit-adminconnectorroleassignmentparameterbody, get-adminapproleassignmentresponse.
Description : PowerApp Role Assignment properties object.
Description : PowerApp Role Assignment principal object.
Get-AdminConnectionRoleAssignmentResponse
Description : Connection Role Assignment properties.
Description : Connection Role Assignment principal object.
Get-AdminConnectionsResponse
Description : Connection properties.
StatusesItem
Description : Connection status error.
ConnectionParameters
Description : Connection property parameters object.
Description : Connection creator principal object.
Environment
Description : Connection Environment object.
TestLinksItem
Get-adminconnectorroleassignmentresponse.
Description : Connector Role Assignment principal object.
Get-AdminConnectorsResponse
Description : Connector connection parameters.
Description : metadata
Description : contact
Description : license
ApiDefinitions
Description : Connector api definitions.
Description : Connector creator's principal object.
Description : Connector last modified by principal object.
Description : Connector Environment.
Description : PowerApp properties object.
CreatedByClientVersion
Description : PowerApp property createdByClientVersion object.
MinClientVersion
Description : PowerApp property minClientVersion object.
Description : PowerApp owner principal object.
Description : PowerApp createdBy principal object.
LastModifiedBy
Description : PowerApp lastModifiedBy object.
Description : PowerApp appUri object.
DocumentUri
Description : PowerApp appUri documentUri object.
UserAppMetadata
Description : PowerApp property userAppMetadata object.
Description : PowerApp Environment property object.
Description : tags
ResourceArray[PowerApp]
Set-adminappownerparameterbody.
No Ads, No Fluff, Just Power Apps Stuff
- Power Apps Standards
- Power Automate Standards
- Power Apps Functions
- Collections Cookbook
- Free Power Apps Icons
Designing A Role-Based User Interface In Power Apps
- Posted by - Matthew Devaney
- on - August 9, 2020
- 36 Comments

A successful app has many different types of users, each with their own needs. Employees, Managers and Administrators all require unique levels of access to maintain data privacy and should be able to perform tasks assigned to their role. I will show you how to design a role-based user interface in Power Apps that adapts to the person using the app.
Site Inspections App
The ‘Site Inspections App’ is used by the quality control department of a restaurant-chain to track the result of on-site audits. Inspectors should only be able to see their own records whereas the manager has the ability to view all records. An administrator also has the unique ability to delete a record if needed. We will build the ‘Site Inspections App’ to look like the image below. I have used a different color scheme for each role but my instructions do not include how to do this.
Make a new SharePoint list called ‘ App Users ‘ with two columns: User (Person column type) and Role (Choices column type) with the options Employee, Manager and Administrator . Any people in the User column will need to exist within your organization so you will need to choose different names than I do.
Open Power Apps and create a new Canvas App From Blank called Site Inspections App. When the user starts the app we need to determine their user details ( varUser ) and role ( varRole ). Put this code in the OnStart property of the app.
Now we will display the User’s name and role in the app.
Place a Person icon on the Title bar. Then insert a label beside it with the following code in the Text property:
Also add a Lock icon to the Title bar. The label beside it should have this code in the Text property:
Your name and role should now appear in the app. If you want to use the app as another person (example: Jennifer Houston) for testing purposes simply hard-code their email in the app’s OnStart property as shown below.
Then run the app’s OnStart property to see the changes take effect. Remember to remove the hard-coded employee email before publishing the app.

Filter Records Based On User Role
An employee should only be able to view their own records in the app whereas a manager or an administrator can see all records in the datasource. Build another SharePoint list called ‘Site Inspections’ with the following columns: LocationName (single-line text), OverallRating (number), InspectionDate (date), InspectedBy (person)
In Power Apps, create a new connection to the ‘Site Inspections’ SharePoint list. After that, insert a gallery onto the screen with ‘Site Inspections’ as the datasource. Format the gallery to display information as shown in the image below using labels, an edit icon and the rating control. Add a label above the gallery to act as a header row.
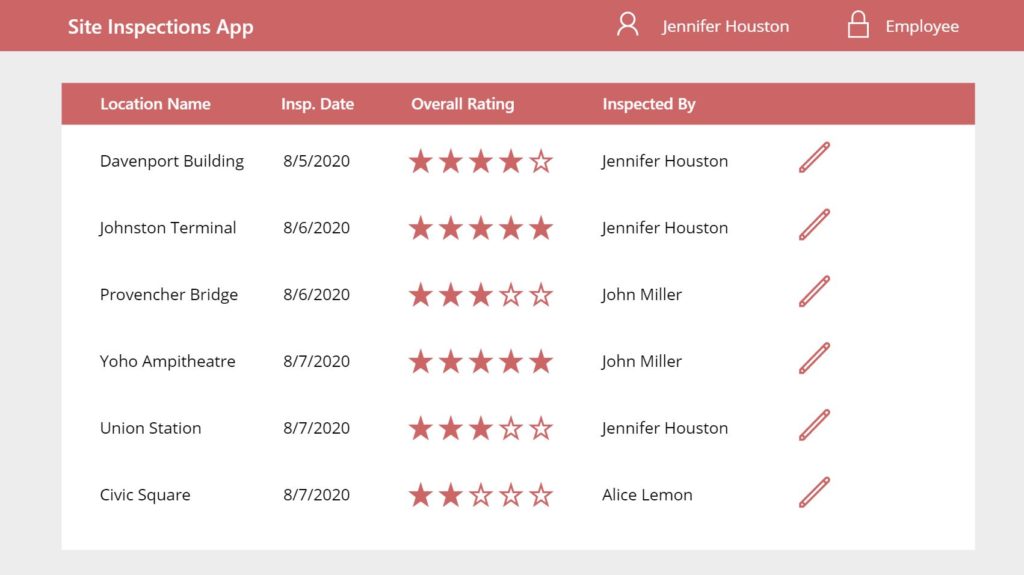
Jennifer Houston is has the role Employee so she should only see 3 records. Put this code in the Items property of the gallery.
Now she can only view her own records.
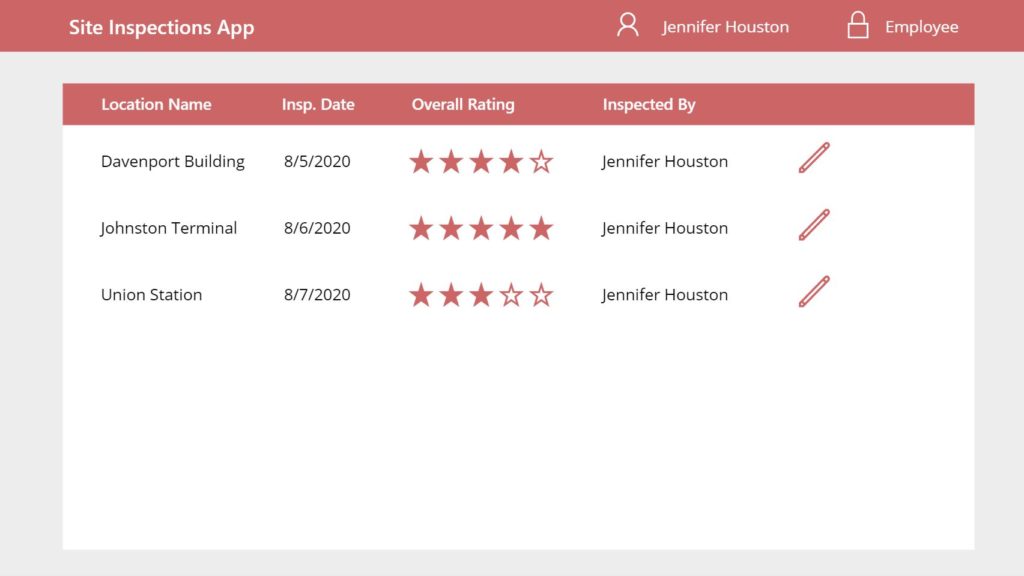
Whereas the Manager Sarah Green can see every record.
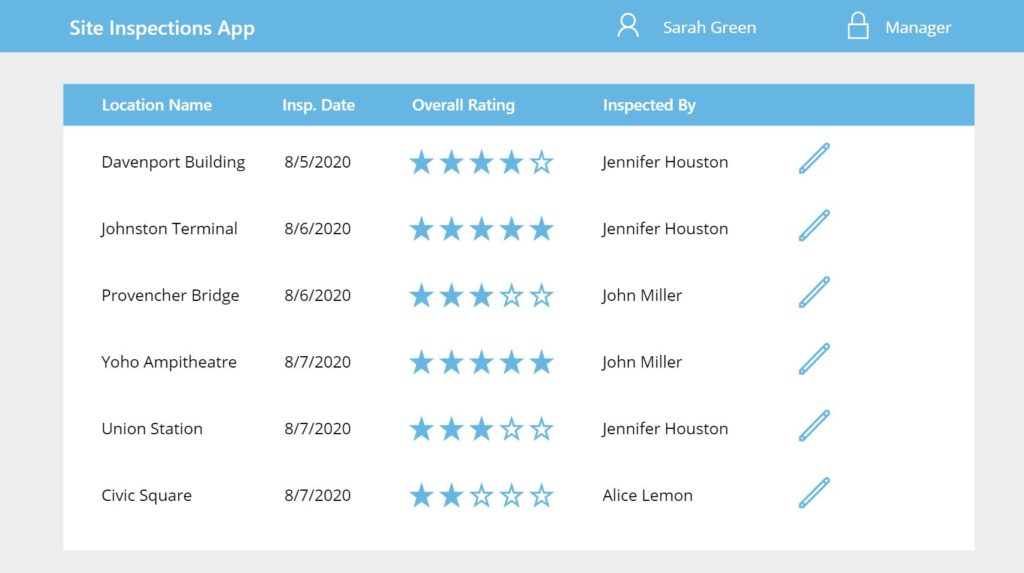
Give Different Abilities Based On User Role
An Administrator is the only role which has the ability to delete records from the datasource. Add a Delete icon to the gallery as shown in the picture below.
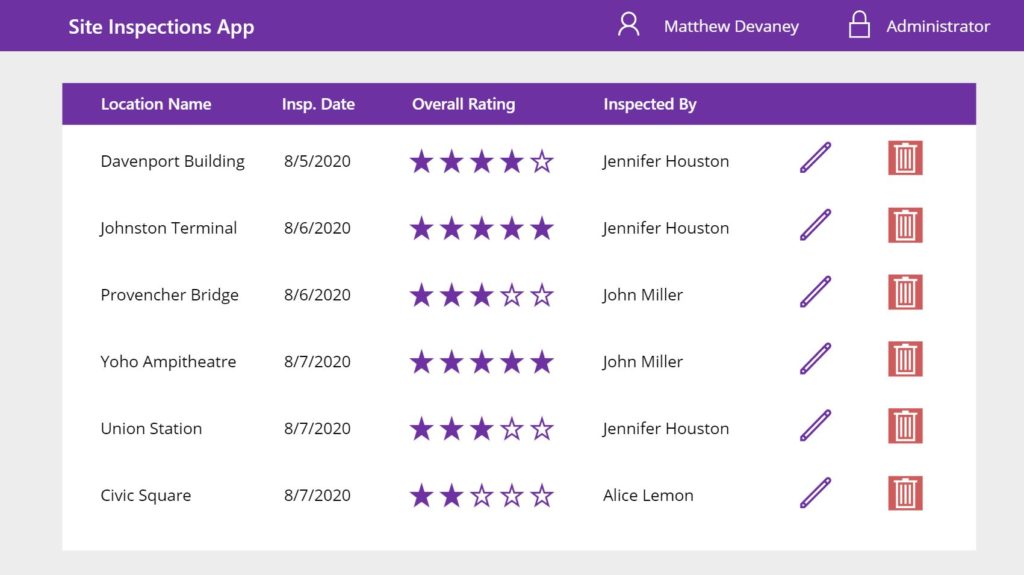
Then use this code in the Visible property of the Delete icon
The Delete icon will show for the administrator and disappear for employees and managers making it impossible to click.
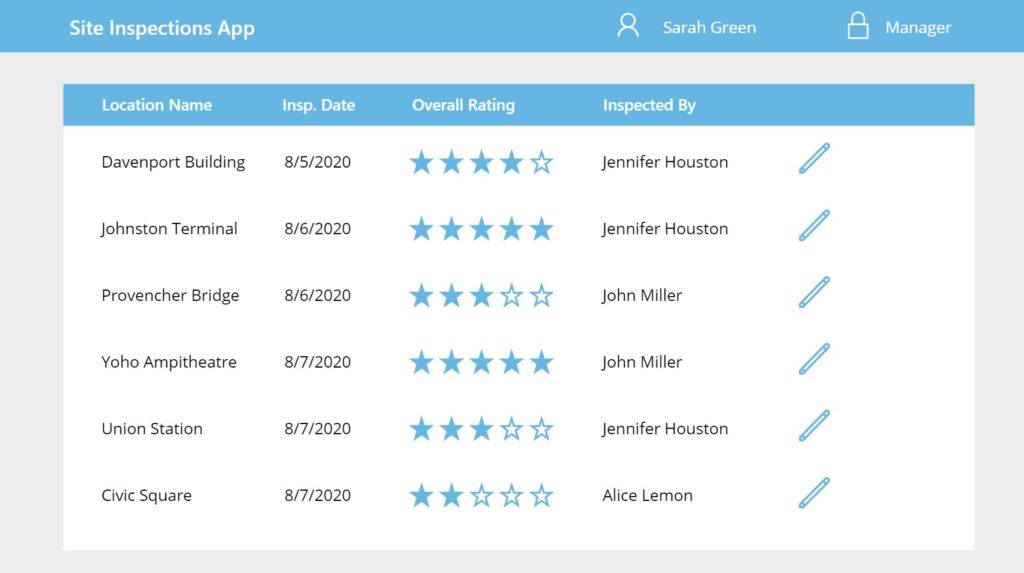
Did You Enjoy This Article? 😺
Subscribe to get new Power Apps articles sent to your inbox each week for FREE
Enter your email address
If you have any questions or feedback about designing a role-based user-interface in Power Apps please leave a message in the comments section below. You can post using your email address and are not required to create an account to join the discussion.
Matthew Devaney

How To Validate A Power Apps Form Before Submission

- Power Platform Admin
Share A Model-Driven App With An Entra Security Group

Share Canvas App With A Microsoft 365 Group In Power Apps

Power Apps: Download File From Dataverse File Column

The Complete Dataverse Access Teams Setup Guide
How To Show File Type Icons In A Power Apps Gallery
Learning a lot from you. Thank you for the great article.
Awesome work Matt. Loved your blog articles always.
I know that you are aware of the following information but for other users, I placing my comments here.
As Power App runs on the user context and if user knows the SP site URL, the user can view/manipulate entire data as we are not trimming the security on SharePoint list.
Here are few recommendations:
- Hide SharePoint lists from user visibility in the SharePoint site.
- Create a Quicklinks web part with all the links to the lists used in the App and place it on the home page. Set the Quicklinks web part audience targeted to Administrator.
- If you want the Power App to be hosted in the SharePoint site, create another SharePoint site and host the app instead of hosting the app in the same site which contains the SharePoint lists.
If this does not help, we definitely need to trim the security on SharePoint list items level, which will degrade the performance of the SharePoint list and Power App. Alternatively, we can use CDS for record level security (it is premium).
These SharePoint list data security recommendations are amazing Krishna. Thank you so much for taking the time to share them!
Your observation is correct: my article only focuses on hiding records to enhance the user experience. Everyone should be paying careful attention to the methods proposed in your comments and enacting them to keep organizational data safe-and-secure 🙂
10/10 as always Matt!
You can also extend this by having a data source where the user can configure the roles different people are allowed to have – so that if people move on / join the company, you don’t need to edit hard values in the app itself, instead you can just refer to the dynamic configuration 🙂
I’ve even hidden entire sections of functionality behind the user-role check, like reporting using embedded Power BI tiles. It adds an extra layer of usability without having to maintain several similar apps. Thanks for sharing for the community! <3
This is so great! Thank you! Will the role validation work with Groups selected in the SharePoint list?
I am not getting the values for varuser and varRole in my app
Venkataramana,
Please click the three dots beside the app object in the left menu of Studio and try to run the OnStart property of the app.
Grear article, very easy to follow.
@odata . type’ :”#Microsoft.Azure.Connectors.SharePoint.SPListExpandedUser”, Claims:”i:0#.f|membership|”& varLoggedInUser . Email , – where did you get that part from?
I most likely learned it from Shane Young at some point: https://www.youtube.com/watch?v=gsk14D-CYRE
I’m not able to display varUser.DisplayName and varRole.Value values in a Label. I manually ran Onstart and see the variables have the correct value in the Variables section. I set the label property Text to “varUser.DisplayName” but it just shows the string “varUser.DisplayName” instead of the value stored in the variable.
I hate to say it but that sounds like a Power Apps bug. Have you tried changing the publisher version in advanced settings? Sometimes when Power Apps does weird stuff like this its because a bug was introduced.
You can use this code its working fine.
Set( varLoggedInUser , User());
Set(varDet,LookUp(‘App User’,User.Email=”priyesh@ companyname .com”));
With( { wUserRecord:varDet }, Set( varUser, wUserRecord.User ); Set( varRole, wUserRecord.Role.Value );
Does this tutorial also refer to Dataverse instead of Sharepoint ? Is there another Tutorial how to perform the tasks with Dataverse ? Would be really great 😊
It refers to SharePoint. I don’t have any plans to write a copy of this article for Dataverse right now but the basic concepts are right here in the article.
Thank you for this amazing article Matthew! I am still a beginner to PowerApps. And such simple solutions really help me stay motivated. I tried the solution in this blog post to access data based on a region. However, a user having 2 regions can only see 1. The table is something like this: User Region A FRANCE B USA C GERMANY D SPAIN D PORTUGAL
User D only sees SPAIN details. Is there any step that I missed? Would really appreciate your help with this! Many thanks!
My example only allows one role per employee. You would need to change the SharePoint list to accept multiple values in the Role column.
Then use this code to set user roles: Set(varRole, wUserRecord.Role.Value)
And check if the user has any roles with: If(IsEmpty(varRole), true_code, false_code)
It’s a start but you need to do more work after that…
Can I pull the employee, manager and administrator records from SharePoint list instead of O-365? as I have a scenario wherein users are not in Azure AD. Pls advise.
Yes, you can do that.
The above worked for me, however when I list multiple If functions in the formula it is unable to filter the information. So, I was trying to have it as
IF(varRole=“Marketing”, IF(VarRole=“Accounting”,If(varRole=“Human Resources”, and so on…
and then the filter function is listed after it. When I tested it out it wouldn’t populate the data in the Gallery. Then when I tested it out with only having one IF function it worked and I was able to see the data for let’s say only Marketing.
Is there a way to fix this issue?
This is great! But what if the image and the username controls are in a component and shared on several screens? How can I make it work?
Thanks for all of these great posts! This was a great help for a side-project of mine. I am having an issue. I am having an issue with not being able to get the Role variable to work. I cannot get it to display nor work in Visible control formulas, and everything matches your example, minus my variables are customizes for my situation, as are the column names and values in my SP list. I even gave changing all the variables to match the example, just in case I was missing a typo somewhere.
Any thoughts of what might be a problem I should check?
Hi Matt, thank you for your amazing work. I’ve been trying to use If( varRole =”Reviewer”, Filter( ‘SharePointList’ , Reviewer . DisplayName = varUser . DisplayName ), ‘ SharePointList ‘ ) But somehow my App does not recognise the Person type column “Reviewer”. In fact it throws me an error. Is there anything else I can try?
Thank you in Advance. Bruno
If you created it in SharePoint while the app was open, refresh the datasource to make it available for use.
man, thank u very much for this post! I have been reading your blog for like 1 month, and i have learned a lot. Amazing work! Nice solutions!
You’re welcome. I’m glad you liked it.
Awesome work Matt and I want display user roles form office365 group only dynamically so how can i do that
Is it possible somehow to check the role through Office365User object in the power app(without using a separate sharepoint list)?
Yes, you could refer to the user job title, although it’s not the same as a role. I would not recommend this path.
The other way to do it is referring to the Security Roles Dataverse table. However, it’s premium.
wondering if you solved that since i also donot want to mention emails in the SharePoint list but use like a Sharepoint group or security group
Hello Matt,
I’m trying to build a power app based off what you’ve done. But when I’m trying to find the user with a matching email, I’m getting an error ” Invalid use of ‘.’ ” where I’m looking up the User.Email and the Role.Value. Am I missing something?
How did you get your gallery to display the data like that? I’ve had nothing but issues trying to get the same look.
what about using security roles iin power platform for achieving the same. I have not yet been able to understand how to use that.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Get-Admin Power App Connection Role Assignment
Returns the connection role assignments for a user or a connection. Owner role assignments can't be deleted without deleting the connection resource.
Description
The Get-AdminPowerAppConnectionRoleAssignment cmdlet returns all roles assignments for an connection or all connection roles assignments for a user (across all of their connections). A connection's role assignments determine which users have access to the connection for using or building apps and flows and with which permission level (CanUse, CanUseAndShare) . Use Get-Help Get-AdminPowerAppConnectionRoleAssignment -Examples for more detail.
Returns all connection role assignments for the calling user.
Returns all role assignments for the connection with name 3b4b9592607147258a4f2fb33517e97ain environment with name ee1eef10-ba55-440b-a009-ce379f86e20c for the connector named shared_sharepointonline.
Returns all role assignments for the user, or group with an object of 3c2f7648-ad60-4871-91cb-b77d7ef3c239 for the connection with name 3b4b9592607147258a4f2fb33517e97ain environment with name ee1eef10-ba55-440b-a009-ce379f86e20c for the connector named shared_sharepointonline .
-ApiVersion
The api version to call with.
-ConnectionName
The connection identifier.
-ConnectorName
The connection's connector identifier.
-EnvironmentName
The connections's environment ID.
-PrincipalObjectId
The objectId of a user or group, if specified, this function will only return role assignments for that user or group.
Additional resources
Software Engineering
- ASP.NET Core
- Elasticsearch
- Entity Framework
Implement app roles authorization with Azure AD and ASP.NET Core
This post shows how to implement Azure AD App roles and applied to users or groups in Azure AD. The roles are used in an ASP.NET Core Razor page application as well as a ASP.NET Core API. The roles from the access token and the id token are used to authorize the identity which is authenticated.
Code: App roles
Create an Azure App registration for Web APP
In this example, a web application will implement authentication and will use a second ASP.NET Core application which implements the user API. Two Azure AD App registrations are created for this, one for each application.
The ASP.NET Core Razor page application is a client which can be authenticated, as well as the identity using the application. It has a trusted back end which can keep a secret. The Azure AD App registration uses a standard web application with a client secret. You could also use a certificate instead of a secret to authenticate the client.
App roles are added to the App registration for the UI client. These roles are used in the UI application which are returned in a user data profile request or in the id token, depending how your client implemented the OIDC standard.
Three roles were added to the Azure AD App registration using the App roles | preview blade.

The roles could also be added directly in the manifest json file.
The API permissions are setup to include the scope created in the API Azure AD App registration. The standard OIDC scopes are added to the registration. All scopes are delegated scopes.

Create an Azure App registration for Web API
The App registration used for the API implements NO authentication flows. This App registration exposes an API and defines roles for the API project authorization. An access_as_user scope is added to the Azure App registration which is a delegated scope type.

Three roles were added to the Azure AD App registration for the API. These roles are for the API and will be added to the access token if the identity has been assigned the roles in the enterprise application of the Azure AD directory. The roles could also be added directly in the manifest.

Apply roles in Azure AD enterprise applications
The new roles which were defined in the Azure AD App registration can now be used. This is setup in the Enterprise application blade of the Azure AD directory. In the Enterprise application list, select the App registration for the API. New users or groups can be added here, and the roles can then be assigned.

In the Add user/group a user or a group can be selected (! Groups can only be selected if you have the correct license) and the roles which were created in the Azure AD App registration can be applied.

If creating applications for tenants with lots of users, groups would be used.
Implement ASP.NET Core API
The API is implemented in ASP.NET Core . The startup class is used to setup the authorization of the access tokens. The Microsoft.Identity.Web Nuget package is used for this. This application configuration will match the configuration of the Azure AD App registration setup for the API. The AddMicrosoftIdentityWebApiAuthentication method is used for this.
ASP.NET Core adds namespaces per default to the claims which are extracted from the access token. We do not want this and so disable the default claim mapping. The roles and the name can should also be mapped, as the default setting does not match what Azure AD returns in the token.
Authorization is added for the API using the AddAuthorization method or it can be added global as a filter. The roles claims are mapped to policies which can then be enforced throughout the application. You could also do this directly using the roles property in the authorize attribute, but I prefer to use policies and separate the authorization. Only policies are used in the application.
A ValidateAccessTokenPolicy policy is implemented to do validation on the access token. The scp claim is validated for an access_as_user value as this is a user API for delegated access and not an application token. The azp claim is used to validate the client calling the API. The API is made specifically for the UI application and so we can validate that only access tokens created for the UI application can use this API. The azp claim is only sent in version 2 Azure App registrations. You must set this in the manifest.
The azpacr claim is also validated. Only authenticated clients can use this API. Any application which gets an access token for this API must use a secret as the value of “1” is controlled. This ensures that public clients cannot create access tokens for this API. If this was a value of “2”, only clients which used certificates to authenticate can acquire access tokens for this API.
It is good to validate the intended user, if possible.
Authorization can also be added globally as a filter in the AddControllers. This would be applied to this middleware.
The policies can then be applied in the API application as required. The access token used to access the API must fulfil all policies used on the API endpoint. If any single policy fails, the a 403 forbidden is returned.
Implement ASP.NET Core Razor Page APP
The ASP.NET Core Razor Page application uses an OIDC interactive flow to authenticate using Azure AD as the identity provider. Both the client application and the identity are authenticated. Microsoft.Identity.Web is used to implement the client code which uses Open ID connect. The AddMicrosoftIdentityWebAppAuthentication method is used in the Startup class in the ConfigureServices method. The downstream APIs are enabled as well as in memory cache. In memory cache is a bit of a problem with testing, as you need to delete the cookies in the browser manually after every test run. You can fix this by using a persistent cache. A filter is added so that an authenticated user is required.
The app.settings.json file contains the configurations for the Azure AD authentication of the application which uses the Microsoft.Identity.Web client. The ClientId from the Web APP App registration and the TenantId for the directory are added here. The ClientSecret also needs to be defined. This should be added to the user secrets in development or added to an Azure Key Vault if deploying to Azure. The ApiWithRoles configuration added the API scope and the URL for the API.
The GetDataFromApi method calls the APIs. The UI application can call any one of the APIs, user, student or admin, each which required a different role. The policies were applied to these APIs. If an error is returned, the exception is handled and returned as a list to demonstrate. The ITokenAcquisition interface is used to get the access token from cache or from the Azure AD identity provider and the access token is added to the Authorization header of the HTTP request as a Bearer token.
To demonstrate the application, the user has been assigned the user “web-api-with-roles-user” and the “web-api-with-roles-admin” roles but not the “web-api-with-roles-student” for the API access. The “web-app-with-roles-user” was assigned for the UI application.
After a successful authentication, the claims from Azure AD are added to the HttpContext.User. A single roles claim (“web-app-with-roles-user”) is added for the UI application. This is as we expected.

If the API is called, the access token can be extracted from the debugger and pasted to jwt.ms or jwt.io . The access token contains two roles, “web-api-with-roles-user”, “web-api-with-roles-admin” as was configured in the enterprise application for this user. The access token also has the scp claim with the access_as_user . The azp claim and the azpacr claims have the expected values. A secret was using to signin to the client UI application which we allow.
A breakpoint was added to Visual Studio in the API project and the claims from the access token can be inspected. We expect the same values like in the access token and without the ASP.NET Core extras.

The ASP.NET Core UI application displays the results of the three API calls. The user and the admin APIs return data and the student API returns a forbidden result. This is what was configured. Now if the user is assigned new roles, after a logout, login, the new claims will be included in the tokens.

This approach works well if you do not have many roles, groups or claims, or if you do not need to change the authorization without re-authentication. The size of the access_token is important, this should not become large. If you require lots of claims for the authorization rules, the claims should not be included in the access token and Microsoft Graph API could be used to access these, or you could implement your own policy management.
https://docs.microsoft.com/en-us/azure/architecture/multitenant-identity/app-roles
https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-enterprise-app-role-management
https://github.com/Azure-Samples/active-directory-aspnetcore-webapp-openidconnect-v2/tree/master/5-WebApp-AuthZ/5-1-Roles
https://docs.microsoft.com/en-us/azure/active-directory/develop/microsoft-identity-web
https://github.com/AzureAD/microsoft-identity-web
https://docs.microsoft.com/en-us/azure/active-directory/develop/id-tokens
https://docs.microsoft.com/en-us/azure/active-directory/develop/access-tokens
Restricting access to an Azure AD protected API using Azure AD Groups
https://docs.microsoft.com/en-us/aspnet/core/security/authorization/policies
Share this:
10 comments.
[…] Implement app roles authorization with Azure AD and ASP.NET Core – Damien Bowden […]
Thank you for the agreat post,
When WebAppWithRoles calls WebApiWithRoles returns an forbidden as result . Can you place explain how you configured web apps claims as azp, azpacr, roles”: [ “web-api-with-roles-user”, “web-api-with-roles-admin” ], and scp to the access token
Unable to run the application end-to-end…. Would appreciate some tips..
Sorry for the slow reply, just saw this now. The Azure App registrations need to be added from your tenants Azure App registration as well as the secrets
Nice tutorial.
Did you map users/groups in the SPA Enterprise App AND in the Api Enterprise App?
or did you only do it in the Api Enterpise App?
thanks, yes
It sounds like a problem from a maintenance point of view. Lets say you add the correct roles to the SPA for a user, but forgets one role on the API.
Then the user will be presented with some functionality, but when he tries to use it, he will get a 403 from the API.
I also asked this question in the msal library: https://github.com/AzureAD/microsoft-authentication-library-for-js/issues/4389
But not sure what the best strategy is to tackle this problem
I normally do this with security groups. The groups roles and APP are setup once at the start. The I restrict access to the Enterprise APP. Then you only need to assign or remove users from the security groups. But this is not black and white. You need too think about lifespan of the roles, where these belong and so on. No authz is ever the same. I would need to analyze this in more detail for your setup. Greetings Damien
[…] También revisa esto Implementar la autorización de roles de aplicaciones con Azure AD y ASP.NET Core | Ingeniería de S… […]
Can you kindly suggest changes to above required for App Role (application)
Leave a comment Cancel reply
This site uses Akismet to reduce spam. Learn how your comment data is processed .

blogs 1 web, general
- Andrew Lock
- Anthony Giretti
- ASP.NET Core blog
- Benjamin Abt (de)
- Bryan Hogan
- Claudio Bernasconi
- code-maze.com
- Davide Bellone
- dotnetcore tutorials
- dotnetthoughts
- Fabian Gosebrink
- Filip WOJCIESZYN
- Gérald Barré
- Gunnar Peipman's
- haacked.com
- Isaac Abraham
- Isaac Levin
- Jürgen Gutsch
- Jeremy Likness
- João Antunes
- josef.codes
- joseph guadagno
- Jussi Roine
- khalid abuhakmeh
- Laurent Kempé
- mikesdotnetting
- Morning brew
- Niels Swimburger
- Ramani Sandeep
- Rockford Lhotka
- Scott Hanselman
- Shawn Wildermuth
- Steve Gordon
- thomas claudius huber
- Tobias Zimmergren
blogs 2 security
- Ackermann Yuriy
- Azure security podcast
- Bárbara Vieira
- Daniel Fett
- Daniel Miessler
- Dominick Baier
- Elie Bursztein
- futurae.com
- James Kettle
- John Patrick Dandison
- Justin Richer
- Kévin Chalet
- Kevin Dockx
- Matthijs Hoekstra
- Michal Špaček
- Microsoft Secure
- Mike Jones self-issued
- Nat Sakimura
- Philippe De Ryck
- research.kudelskisecurity
- Robert Broeckelmann
- Rory Braybrook
- Scott Brady
- Scott Helme
- securityguill
- sirdarckcat
- Stephen Haunts
- Steve Syfuhs
- Takahiko Kawasaki
- Tanya Janca
- Torsten Lodderstedt
blogs 3 Azure
- Alexandre Verkinderen
- Anthony Chu
- Azure DevOps
- Boris Wilhelms
- cloud-architekt.net
- cloudbrothers
- daniel chronlund
- Daniel Krzyczkowski
- Dominique St-Amand
- Eduard Keilholz
- francois leon
- Gareth Emslie
- Jan de Vries
- jeffrey appel
- Joonas Westlin
- Mahindra Morar
- Marius Solbakken
- Martin Lingstuyl
- Mickaël Derriey
- o365blog Dr Nestori Syynimaa
- olivier vaillancourt
- René Bremer
- Rick van den Bosch
- Sahil Malik
- Stephan van Rooij
- Stephane Eyskens
- Stian A. Strysse
- thomas maurer
- Thomas Naunheim
- Toon Vanhoutte
blogs 4 SSI DID
- hyperledger
- hyperledger aries-framework-dotnet
- identity.foundation
- identity.foundation blog
- idunion.org
- Kaliya-Identity Woman
- Kim Hamilton Duffy
- Kyle Den Hartog
- Markus Sabadello
- mattr.global
- Microsoft DID
- newsletter.identosphere.net
- Phillip J. Windley
- ssi-orbit-podcast
- Tomislav Markovski
- Andreas Helland
- Damien Guard
- Dan Wahlin's
- Data Farm Julie Lerman
- Dave Paquette
- Development With A Dot
- Elton Stoneman
- exceptionnotfound.net
- jeff handley
- Jeffrey T. Fritz
- Juan Carlos Sanchez's
- Maarten Balliauw
- Manfred Steyer (de)
- Manuel Meyer
- Mete Atamel
- Minko Gechev
- Nate Barbettini
- Nicholas Blumhardt
- Pawel Kadluczka
- Rui Figueiredo
- Stefan Prodan
- Stephen Cleary
- Alexander Beletsky
- Anders Janmyr
- Anže Vodovnik
- chsakell's Blog
- Florian Hopf
- fredrik normén
- Galdin Raphael
- Gernot Starke (de)
- Imran Baloch
- Jalpesh Vadgama DotNetJalps
- Jeffrey Palermo
- Jimmy Nilsson
- job tips for geeks
- Johnny Graber (de)
- Jon Galloway
- Kevin Jones
- Laurent Bugnion
- Linda Lawton
- Mick Taulty
- Muhammad Rehan Saeed
- PPEDV blog (de)
- Rashim's Blog
- Scott Addie
- scottgu .NET
- Shayne Boyer
- steven sanderson
- Taiseer Joudeh
- Thomas Ardal
- Thomas Levesque
- Tugberk Ugurlu
- .NET (Core, 5+ ) SDK
- Angular CLI
- bootstrap 4
- gitextensions
- IDP Azure AD
- IDP DuendeSoftware
- IDP keycloak
- IDP node-oidc-provider
- IDP OpenIddict
- lets encrypt
- protobuf-net
- randommer.io
- Search elasticsearch
- Search Solr
- Test achecker.ca
- Test DotTrace Profiler
- Test FakeItEasy
- Test Fiddler
- Test mkjwk.org JSON Web Key
- Test Ndepend
- Test Sysinternals Suite
- Test wireshark
- Test xunit.net
- Test zaproxy
- Visual Studio
- Visual Studio Code
- .NET Group Basel
- .NET Group Bern (de)
- .NET Group Luzern (de)
- .NET Group Zürich
- .NET User Group Geneva
- Angular Switzerland
- blackhat.com
- Brice's Entity Links
- Christian Mosers
- Code Project
- devcurry Suprotim Agarwal
- developer.chrome
- Fabrice Bellard
- fido alliance
- jeremy skinner
- Martin Fowler
- one unicorn
- OPC Foundation
- rob tiffany
- Simple Talk Red Gate
- thinktecture
- Thoughtworks Radar
- tutorialzine
- Web Fundamentals
- Entries feed
- Comments feed
- WordPress.com
- February 2024
- January 2024
- December 2023
- November 2023
- October 2023
- September 2023
- August 2023
- February 2023
- January 2023
- December 2022
- November 2022
- October 2022
- September 2022
- August 2022
- February 2022
- January 2022
- December 2021
- November 2021
- October 2021
- September 2021
- August 2021
- February 2021
- January 2021
- December 2020
- November 2020
- October 2020
- September 2020
- August 2020
- February 2020
- January 2020
- December 2019
- November 2019
- October 2019
- September 2019
- August 2019
- February 2019
- January 2019
- December 2018
- November 2018
- October 2018
- September 2018
- August 2018
- February 2018
- January 2018
- December 2017
- November 2017
- October 2017
- September 2017
- August 2017
- February 2017
- January 2017
- December 2016
- November 2016
- October 2016
- September 2016
- August 2016
- February 2016
- January 2016
- December 2015
- November 2015
- October 2015
- September 2015
- August 2015
- February 2015
- January 2015
- December 2014
- November 2014
- October 2014
- September 2014
- August 2014
- February 2014
- January 2014
- December 2013
- November 2013
- October 2013
- September 2013
- August 2013
- February 2013
- January 2013
- Already have a WordPress.com account? Log in now.
- Subscribe Subscribed
- Copy shortlink
- Report this content
- View post in Reader
- Manage subscriptions
- Collapse this bar
What's lurking in your Microsoft Graph app role assignments?
Gain insights for security and compliance reasons by reporting on all service principals in entra id (former azure ad) having microsoft graph app role assignments..
I’ve earlier blogged about Building a comprehensive report on admin role assignments in Powershell , this time we’ll look at app role assignments instead.
Application permissions, often called app role assignments in Entra ID (former Azure AD), are permission sets that an app, service principal or managed identity can be assigned in another resource app, and that app’s identity can then access and utilize the resource app’s API without a signed-in user present.
Service principals by default have no access to enumerate other objects in Entra ID (former Azure AD). An example, if a service principal used in automated workflows requires read access to all user objects in Entra ID, it will need to be assigned the app role User.Read.All application permission (app role) in Microsoft Graph, consented by an admin, to be able to query Graph for any or all users.
The Microsoft Graph API is covering endpoints for most of Entra ID and Microsoft 365 services, and it has a wide range of app roles for providing specific API access. And let’s not forget the old and deprecated Azure AD Graph API which has not yet been fully been sunset. It’s critical for compliance and security hygiene of the tenant to audit and monitor app role assignments for these resources especially. Do note that there are a lot of other APIs with their own sets of app roles in Entra ID, some examples below, but for this blog post I will focus on Microsoft Graph and Azure AD Graph.
Some app roles can be abused for privilege escalation all the way up to Global Admin , as Andy Robbins (co-creator of BloodHound) points out in this blog post . A Global Admin can do whatever it wants in Entra ID, and it can also elevate its access for all Azure subscriptions in the tenant with the flip of a switch . This just proves how critical it is to have full control on any high-privilege app roles.
With these things in mind, let’s look at how to extract all app role assignments for Microsoft Graph and Azure AD Graph, including other valuable information for each service principal, using Powershell and the Graph Powershell SDK v2 module.
Identify highly privileged app roles
Required scopes in graph powershell sdk, app roles and assignments.
- Owner organizations and sign-in activities
Compiling the report
Full script on github.
I wish there was a list of all Microsoft Graph app roles with tiering information, identifying how privileged each app role is. Since there are none I’ve added some of the app roles that I know are highly privileged - they will be specifically flagged as Tier 0 in the report. There are many other privileged app roles, but let’s start with these as abusing them can lead to Global Admin access. You can easily add other roles and other tiers, depending on what you want to report on.
Update 2023-08-17 @ 11:00 (CEST): Removed ‘Application.ReadWrite.OwnedBy’ from the list as this permission isn’t Tier 0 at all: “Allows the app to create other applications, and fully manage those applications (read, update, update application secrets and delete), without a signed-in user. It cannot update any apps that it is not an owner of.”
When connecting to Microsoft Graph with the Graph Powershell SDK v2 module, the following delegated scopes are required:
- Application.Read.All (to enumerate service principals)
- AuditLog.Read.All (to pull out service principal sign-in activity)
- CrossTenantInformation.ReadBasic.All (to query app owner tenant information for 3.party apps)
Other than that, no special privileges are necessary for the user account connecting to Microsoft Graph - only read-access is used.
Extracting data
Now let’s start extracting the data we need from Microsoft Graph to create the report.
First we are querying for Microsoft Graph and Azure AD Graph’s service principal objects in the tenant - by filtering on their well-known Application IDs ( 00000003-0000-0000-c000-000000000000 and 00000002-0000-0000-c000-000000000000 ). Once the service principals have been found, we are extracting all app roles and app role assignments, creating hashtable for quick lookups, and lastly joining the app role assignments for both service principals.
We can now process each of the app role assignments in $joinedAppRolesAssignedTo to create a report, while enriching the data set even further.
Service principals, owner organizations and sign-in activities
The app role assignments in $joinedAppRolesAssignedTo does not contain all the information we need about the assigned service principals. So we will query Graph for the service principal objects, the owner organizations for multi-tenant apps, and sign-in activities. To optimize the script we’re utilizing cache and only querying each object one time even tho it has multiple app role assignments.
Note that looking up the app owner organization (for multi-tenant apps) uses Invoke-MgGraphRequest with a URI since I haven’t found a cmdlet for this in Graph Powershell SDK yet.
Let’s pull the sign-in activities for the service principals. This gives us information about the most recent service principal sign-in and delegated (user) sign-in, which can help us identify stale apps. Note that this newly released reporting endpoint in Graph is still in beta, which is why we need to utilize the Get-MgBetaReportServicePrincipalSignInActivity cmdlet.
And finally we can generate a PSCustomObject with the data we need for the report.
This will generate a list of all the app role assignments for Microsoft Graph and Azure AD Graph, enriched with additional data for the assigned service principals and any configured tier. Here’s an example.
I like to explain how the Powershell scripts I publish works, and this blog post does just that. I have also published the full Powershell script on GitHub so you don’t have to copy/paste from this page, feel free to check it out.
Thanks for reading!
Be sure to provide any feedback on X (former Twitter) or LinkedIn .
- ← Previous Post
- Power Apps Community
- Welcome to the Community!
- News & Announcements
- Get Help with Power Apps
- Building Power Apps
- Microsoft Dataverse
- Power Apps Governance and Administering
- Power Apps Pro Dev & ISV
- Connector Development
- Power Query
- GCC, GCCH, DoD - Federal App Makers (FAM)
- Power Platform Integration - Better Together!
- Power Platform Integrations (Read Only)
- Power Platform and Dynamics 365 Integrations (Read Only)
- Community Blog
- Power Apps Community Blog
- Community Connections & How-To Videos
- Copilot Cookbook
- Community App Samples
- Webinars and Video Gallery
- Canvas Apps Components Samples
- Emergency Response Gallery
- 2021 MSBizAppsSummit Gallery
- 2020 MSBizAppsSummit Gallery
- 2019 MSBizAppsSummit Gallery
- Community Engagement
- Community Calls Conversations
- Hack Together: Power Platform AI Global Hack
- Experimental
- Error Handling
- Power Apps Experimental Features
- Community Support
- Community Accounts & Registration
- Using the Community
- Community Feedback
Set App owner action environment name null
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- All forum topics
- Previous Topic
- Mark as New
- Report Inappropriate Content
Solved! Go to Solution.
- General Questions
- Access to PowerApps usi…
View solution in original post
Helpful resources

Take a short Community User Survey | Help us make your experience better!
To ensure that we are providing the best possible experience for Community members, we want to hear from you! We value your feedback! As part of our commitment to enhancing your experience, we invite you to participate in a brief 15-question survey. Your insights will help us improve our services and better serve the community. 👉 Community User Survey Thank you for being an essential part of our community! Power Platform Engagement Team

Tuesday Tip | How to Get Community Support
It's time for another Tuesday Tip, your weekly connection with the most insightful tips and tricks that empower both newcomers and veterans in the Power Platform Community! Every Tuesday, we bring you a curated selection of the finest advice, distilled from the resources and tools in the Community. Whether you’re a seasoned member or just getting started, Tuesday Tips are the perfect compass guiding you across the dynamic landscape of the Power Platform Community. This Week: All About Community Support Whether you're a seasoned community veteran or just getting started, you may need a bit of help from time to time! If you need to share feedback with the Community Engagement team about the community or are looking for ways we can assist you with user groups, events, or something else, Community Support is the place to start. Community Support is part of every one of our communities, accessible to all our community members. Within each community's Community Support page, you'll find three distinct areas, each with a different focus to help you when you need support from us most. Power Apps: https://powerusers.microsoft.com/t5/Community-Support/ct-p/pa_community_support Power Automate: https://powerusers.microsoft.com/t5/Community-Support/ct-p/mpa_community_support Power Pages: https://powerusers.microsoft.com/t5/Community-Support/ct-p/mpp_community_support Copilot Studio: https://powerusers.microsoft.com/t5/Community-Support/ct-p/pva_community-support Community Support Form If you need more assistance, you can reach out to the Community Team via the Community support form. Choose the type of support you require and fill in the form accordingly. We will respond to you promptly. Thank you for being an active part of our community. Your contributions make a difference! Best Regards, The Community Management Team

Community Roundup: A Look Back at Our Last 10 Tuesday Tips
As we continue to grow and learn together, it's important to reflect on the valuable insights we've shared. For today's #TuesdayTip, we're excited to take a moment to look back at the last 10 tips we've shared in case you missed any or want to revisit them. Thanks for your incredible support for this series--we're so glad it was able to help so many of you navigate your community experience! Getting Started in the Community An overview of everything you need to know about navigating the community on one page! Community Links: ○ Power Apps ○ Power Automate ○ Power Pages ○ Copilot Studio Community Ranks and YOU Have you ever wondered how your fellow community members ascend the ranks within our community? We explain everything about ranks and how to achieve points so you can climb up in the rankings! Community Links: ○ Power Apps ○ Power Automate ○ Power Pages ○ Copilot Studio Powering Up Your Community Profile Your Community User Profile is how the Community knows you--so it's essential that it works the way you need it to! From changing your username to updating contact information, this Knowledge Base Article is your best resource for powering up your profile. Community Links: ○ Power Apps ○ Power Automate ○ Power Pages ○ Copilot Studio Community Blogs--A Great Place to Start There's so much you'll discover in the Community Blogs, and we hope you'll check them out today! Community Links: ○ Power Apps ○ Power Automate ○ Power Pages ○ Copilot Studio Unlocking Community Achievements and Earning Badges Across the Communities, you'll see badges on users profile that recognize and reward their engagement and contributions. Check out some details on Community badges--and find out more in the detailed link at the end of the article! Community Links: ○ Power Apps ○ Power Automate ○ Power Pages ○ Copilot Studio Blogging in the Community Interested in blogging? Everything you need to know on writing blogs in our four communities! Get started blogging across the Power Platform communities today! Community Links: ○ Power Apps ○ Power Automate ○ Power Pages ○ Copilot Studio Subscriptions & Notifications We don't want you to miss a thing in the community! Read all about how to subscribe to sections of our forums and how to setup your notifications! Community Links: ○ Power Apps ○ Power Automate ○ Power Pages ○ Copilot Studio Getting Started with Private Messages & Macros Do you want to enhance your communication in the Community and streamline your interactions? One of the best ways to do this is to ensure you are using Private Messaging--and the ever-handy macros that are available to you as a Community member! Community Links: ○ Power Apps ○ Power Automate ○ Power Pages ○ Copilot Studio Community User Groups Learn everything about being part of, starting, or leading a User Group in the Power Platform Community. Community Links: ○ Power Apps ○ Power Automate ○ Power Pages ○ Copilot Studio Update Your Community Profile Today! Keep your community profile up to date which is essential for staying connected and engaged with the community. Community Links: ○ Power Apps ○ Power Automate ○ Power Pages ○ Copilot Studio Thank you for being an integral part of our journey. Here's to many more Tuesday Tips as we pave the way for a brighter, more connected future! As always, watch the News & Announcements for the next set of tips, coming soon!

Calling all User Group Leaders and Super Users! Mark Your Calendars for the next Community Ambassador Call on May 9th!
This month's Community Ambassador call is on May 9th at 9a & 3p PDT. Please keep an eye out in your private messages and Teams channels for your invitation. There are lots of exciting updates coming to the Community, and we have some exclusive opportunities to share with you! As always, we'll also review regular updates for User Groups, Super Users, and share general information about what's going on in the Community. Be sure to register & we hope to see all of you there!

April 2024 Community Newsletter
We're pleased to share the April Community Newsletter, where we highlight the latest news, product releases, upcoming events, and the amazing work of our outstanding Community members. If you're new to the Community, please make sure to follow the latest News & Announcements and check out the Community on LinkedIn as well! It's the best way to stay up-to-date with all the news from across Microsoft Power Platform and beyond. COMMUNITY HIGHLIGHTS Check out the most active community members of the last month! These hardworking members are posting regularly, answering questions, kudos, and providing top solutions in their communities. We are so thankful for each of you--keep up the great work! If you hope to see your name here next month, follow these awesome community members to see what they do! Power AppsPower AutomateCopilot StudioPower PagesWarrenBelzDeenujialexander2523ragavanrajanLaurensMManishSolankiMattJimisonLucas001AmikcapuanodanilostephenrobertOliverRodriguestimlAndrewJManikandanSFubarmmbr1606VishnuReddy1997theMacResolutionsVishalJhaveriVictorIvanidzejsrandhawahagrua33ikExpiscornovusFGuerrero1PowerAddictgulshankhuranaANBExpiscornovusprathyooSpongYeNived_Nambiardeeksha15795apangelesGochixgrantjenkinsvasu24Mfon LATEST NEWS Business Applications Launch Event - On Demand In case you missed the Business Applications Launch Event, you can now catch up on all the announcements and watch the entire event on-demand inside Charles Lamanna's latest cloud blog. This is your one stop shop for all the latest Copilot features across Power Platform and #Dynamics365, including first-hand looks at how companies such as Lenovo, Sonepar, Ford Motor Company, Omnicom and more are using these new capabilities in transformative ways. Click the image below to watch today! Power Platform Community Conference 2024 is here! It's time to look forward to the next installment of the Power Platform Community Conference, which takes place this year on 18-20th September 2024 at the MGM Grand in Las Vegas! Come and be inspired by Microsoft senior thought leaders and the engineers behind the #PowerPlatform, with Charles Lamanna, Sangya Singh, Ryan Cunningham, Kim Manis, Nirav Shah, Omar Aftab and Leon Welicki already confirmed to speak. You'll also be able to learn from industry experts and Microsoft MVPs who are dedicated to bridging the gap between humanity and technology. These include the likes of Lisa Crosbie, Victor Dantas, Kristine Kolodziejski, David Yack, Daniel Christian, Miguel Félix, and Mats Necker, with many more to be announced over the coming weeks. Click here to watch our brand-new sizzle reel for #PPCC24 or click the image below to find out more about registration. See you in Vegas! Power Up Program Announces New Video-Based Learning Hear from Principal Program Manager, Dimpi Gandhi, to discover the latest enhancements to the Microsoft #PowerUpProgram. These include a new accelerated video-based curriculum crafted with the expertise of Microsoft MVPs, Rory Neary and Charlie Phipps-Bennett. If you’d like to hear what’s coming next, click the image below to find out more! UPCOMING EVENTS Microsoft Build - Seattle and Online - 21-23rd May 2024 Taking place on 21-23rd May 2024 both online and in Seattle, this is the perfect event to learn more about low code development, creating copilots, cloud platforms, and so much more to help you unleash the power of AI. There's a serious wealth of talent speaking across the three days, including the likes of Satya Nadella, Amanda K. Silver, Scott Guthrie, Sarah Bird, Charles Lamanna, Miti J., Kevin Scott, Asha Sharma, Rajesh Jha, Arun Ulag, Clay Wesener, and many more. And don't worry if you can't make it to Seattle, the event will be online and totally free to join. Click the image below to register for #MSBuild today! European Collab Summit - Germany - 14-16th May 2024 The clock is counting down to the amazing European Collaboration Summit, which takes place in Germany May 14-16, 2024. #CollabSummit2024 is designed to provide cutting-edge insights and best practices into Power Platform, Microsoft 365, Teams, Viva, and so much more. There's a whole host of experts speakers across the three-day event, including the likes of Vesa Juvonen, Laurie Pottmeyer, Dan Holme, Mark Kashman, Dona Sarkar, Gavin Barron, Emily Mancini, Martina Grom, Ahmad Najjar, Liz Sundet, Nikki Chapple, Sara Fennah, Seb Matthews, Tobias Martin, Zoe Wilson, Fabian Williams, and many more. Click the image below to find out more about #ECS2024 and register today! Microsoft 365 & Power Platform Conference - Seattle - 3-7th June If you're looking to turbo boost your Power Platform skills this year, why not take a look at everything TechCon365 has to offer at the Seattle Convention Center on June 3-7, 2024. This amazing 3-day conference (with 2 optional days of workshops) offers over 130 sessions across multiple tracks, alongside 25 workshops presented by Power Platform, Microsoft 365, Microsoft Teams, Viva, Azure, Copilot and AI experts. There's a great array of speakers, including the likes of Nirav Shah, Naomi Moneypenny, Jason Himmelstein, Heather Cook, Karuana Gatimu, Mark Kashman, Michelle Gilbert, Taiki Y., Kristi K., Nate Chamberlain, Julie Koesmarno, Daniel Glenn, Sarah Haase, Marc Windle, Amit Vasu, Joanne C Klein, Agnes Molnar, and many more. Click the image below for more #Techcon365 intel and register today! For more events, click the image below to visit the Microsoft Community Days website.

Tuesday Tip | Update Your Community Profile Today!
It's time for another TUESDAY TIPS, your weekly connection with the most insightful tips and tricks that empower both newcomers and veterans in the Power Platform Community! Every Tuesday, we bring you a curated selection of the finest advice, distilled from the resources and tools in the Community. Whether you’re a seasoned member or just getting started, Tuesday Tips are the perfect compass guiding you across the dynamic landscape of the Power Platform Community. We're excited to announce that updating your community profile has never been easier! Keeping your profile up to date is essential for staying connected and engaged with the community. Check out the following Support Articles with these topics: Accessing Your Community ProfileRetrieving Your Profile URLUpdating Your Community Profile Time ZoneChanging Your Community Profile Picture (Avatar)Setting Your Date Display Preferences Click on your community link for more information: Power Apps, Power Automate, Power Pages, Copilot Studio Thank you for being an active part of our community. Your contributions make a difference! Best Regards, The Community Management Team
SharePoint in operator delegation warning


IMAGES
VIDEO
COMMENTS
Get Connections as Admin. Returns a list of Connections. Get Connector Role Assignments as Admin. Returns permissions for a custom Connector. Get Custom Connectors as Admin. Returns a list of custom Connectors. Get Power App Conditional Access. Gets a PowerApp's conditional access properties. Remove App as Admin.
And it offers "Get App Role Assignments as Admin" action which will give you the list of users for any given app in any given environment. Here is an example: As you can see, the output of this flow matches the original screenshot. You just need to pass environment ID and application ID to the action.
Let's recap the important parts: 1 - Create an enterprise application in Azure AD. 2 - Go to "app registrations", find the app and add appRoles to the manifest. The following are provided by default, disable those and add some custom ones. See the below example roles.
Get App Role Assignments as Admin. Set-AdminAppOwner (string environment, string app, [Optional]string api-version, [Optional]string Content-Type, [Optional]Set-AdminAppOwnerParameterBody body) Set App Owner.
Now we will display the User's name and role in the app. Place a Person icon on the Title bar. Then insert a label beside it with the following code in the Text property: varUser.DisplayName. Also add a Lock icon to the Title bar. The label beside it should have this code in the Text property: varRole.
A connection's role assignments determine which users have access to the connection for using or building apps and flows and with which permission level (CanUse, CanUseAndShare) . ... Get-Admin Power App Connection Role Assignment [[-ConnectionName] <String>] [-ConnectorName <String>] [-EnvironmentName <String>] [-PrincipalObjectId <String>] ...
This post shows how to implement Azure AD App roles and applied to users or groups in Azure AD. The roles are used in an ASP.NET Core Razor page application as well as a ASP.NET Core API. The roles from the access token and the id token are used to authorize the identity which is authenticated. Code: App roles.
Application permissions, often called app role assignments in Entra ID (former Azure AD), are permission sets that an app, service principal or managed identity can be assigned in another resource app, and that app's identity can then access and utilize the resource app's API without a signed-in user present. Service principals by default ...
# Get all service principals, and for each one, get all the app role assignments, # resolving the app role ID to it's display name. Output everything to a CSV. Get-AzureADServicePrincipal | % { # Build a hash table of the service principal's app roles. The 0-Guid is # used in an app role assignment to indicate that the principal is assigned ...
Edit Connector Role Assignment as Admin: Sets permissions for a Connector. Get App as Admin: Returns a PowerApp. Get App Role Assignments as Admin: Returns permissions for a PowerApp. Get Apps as Admin: Returns a list of apps. Get Connection Role Assignments as Admin: Returns all permissions for a Connection. Get Connections as Admin: Returns a ...