

Writing a Proper Essay on Cyber-Security in Banking Sector
The banking industry is very important for all people who deal with money. Banking systems throughout the globe regulate the monetary stability in a concrete country. Great unions regulate huge regions. Once a bank crashes, a country may live through a default, which means economic catastrophe. As the result, it involves other spheres and destabilizes normal life in general. One of the reasons that lead to problems is poor cybersecurity . This article concentrates on 6 good ways that help to improve cybersecurity in the banking sector.
Nowadays, cyber-attacks have increased many a time. This is a huge threat to every citizen of the Earth because privacy is violated. The threat becomes even more troublesome and dangerous when it involves cyber-attacks on banks. If you want to write an essay on the topic, but if seems too complicated for you, you can address professionals. Simply type write my essay for me by EssayHub in the search bar and find your essay helper!
Cybercriminals get directly into the pockets of citizens. This becomes possible due to multiple attacks of hackers on banks. The banking sector is of huge importance for the stability of people’s well-being. A hacker attack, which ruins the banking industry, leads to a dangerous destabilization of the economy of the country. Accordingly, it triggers lots of factors that affect other spheres of human activity. Such danger negatively affects business, education, culture, and so on. Attacks from hackers in the banking sector must be prevented and stopped. There are six measures, which can help to overcome this threatening situation.
1. The threat should be taken seriously.
Some banks strongly believe that they will never be robbed thanks to dependable safeguards and firewalls. They think that they are simply invisible. This makes them less cautious and actually irresponsible. They understand that their protective measures are weak when it’s too late. A solution is to fully realize all threats and accept the possibility of being attacked. Afterward, banks should implement new equipment to prevent dangers. No matter how good the equipment is, it should be constantly improved to stop new attempts, which become better each time.
2. Good analysis is required.
Banking protection systems compile data on various issues. This gives an opportunity to enhance every point to ensure safety, as well as other branches. One may simply say “Here is a problem and I have information about how to fix and improve it”. Unfortunately, tons of information isn’t analyzed properly. Regulators commonly don’t collect security data. As the result, there is no possibility to define the potential threats. It’s needed to change this function and gather all possible data. Thus, it will become much easier to foresee possible cyber assault.
3. All third-parties vendors must be verified.
They commonly give data on technology services. Nonetheless, the practice shows that they may open this data to other people, which sufficiently increases the risks. Other people may turn it to their advantage and steal money. Currently, this is a critical issue because there is no permission to verify third parties. The government should realize the risks and allow checking distributors of information in order to secure their own safety. Thus, the safety of banks will be enhanced as well.
4. Secure mobile operations.
Today, people actively use their cell phones for greater speed and comfort. It goes beyond all doubts that mobile banking is among them. Banks support this kind of access. People don’t have to stand in long queues while their turn comes. Banks thrive as well because they can make much more operations, which results in their prosperity at a great tempo. In the meanwhile, they don’t give enough heed to the security of mobile banking. It also requires modern equipment and advanced safeguards. Otherwise, clients become vulnerable to hacker attacks. Besides, banks are under a threat too.
5. Regulators should hire more IT specialists.
Currently, small and medium-sized banks aren’t protected properly. Commonly, they are considered to be units that are at low risk of attacks. IT specialists only make general analyses. This is a fatal mistake. Such banks are attacked on a constant basis. This inevitably leads to problems with bigger institutions. They become weaker. Banks should involve more experts to dig deeper into the slightest details.
6. The information on threats is supposed to be shared faster and with all the details.
People share information about potential hazards, but this process is way too slow and lacks details, which are crucial on such occasions. Once there appears suspicion, banks or clients don’t always have an immediate possibility to report the case. Sometimes, banks simply hide this data because they are afraid that their reputation will be shaken off. It’s much better to allow clients to share this vital information. This helps to prevent thousands of attacks annually.
The matter of banking security is important and it should be ensured in all possible ways and at any cost. There are at least six available variants. Unfortunately, some of them are disallowed. For example, banks hide or don’t compile data on cyber threats or the government doesn’t allow verifying third parties. Once these issues are solved, the danger of cyber-attacks will be significantly decreased”.
References:
- Anand, Priya. “6 ways the banking industry could improve on cybersecurity”. Marketwatch.com, https://www.marketwatch.com/story/6-ways-the-banking-industry-could-improve-on-cybersecurity-2015-07-02. 2015, 2 July.
- “How the Banking Industry is Fighting Cyber Crime”. Careersincybersecurity.com, https://careersincybersecurity.com/banking-industry-fighting-cyber-crime/. 2019
- Barnes, Samantha “HOW WILL BANKS ADDRESS GAPS IN CYBERSECURITY?” Internationalbanker.com, https://internationalbanker.com/technology/2017-will-banks-address-gaps-cybersecurity/. 2017, March 2.

For enquiries call:
+1-469-442-0620

Cybersecurity in Banking: Importance, Threats, Challenges
Home Blog Security Cybersecurity in Banking: Importance, Threats, Challenges
As we transition to a digital economy, cybersecurity in banking is becoming a serious concern. Utilizing methods and procedures created to safeguard the data is essential for a successful digital revolution. The effectiveness of cybersecurity in banks influences the safety of our Personally Identifiable Information (PII), whether it be an unintentional breach or a well-planned cyberattack.
The stakes are high in the banking and financial industry since substantial financial sums are at risk and the potential for significant economic upheaval if banks and other financial systems are compromised. With an exponential increase in financial cybersecurity, there is high demand for the profession of cybersecurity. Take a look at the best Security certifications .
What is Cybersecurity in Banking?
The arrangement of technologies, protocols, and methods referred to as "cybersecurity" is meant to guard against attacks, damage, malware, viruses, hacking, data theft, and unauthorized access to networks, devices, programs, and data.
Protecting the user's assets is the primary goal of cybersecurity in banking. As more people become cashless, additional acts or transactions go online. People conduct transactions using digital payment methods like debit and credit cards, which must be protected by cybersecurity.
.jpg&w=3840&q=75)
Current State of Cybersecurity in Banks
The market for IT security in banking has maintained its rapid growth in 2024. Since financial institutions are primary attack targets, investments in protection continue to scale. The market value reached $38.72 billion in 2021 , and projections see a compound growth rate of 22.4% and a value of $195.5 billion by 2029.
Between June 2018 and March 2022, Indian banks reported 248 successful data breaches by hackers and criminals; the government notified Parliament on Aug 2, 2022.
The Indian government has reported 11,60,000 cyber-attacks in 2022. It is estimated to be three times more than in 2019. India has been the target of serious cyberattacks, such as the phishing attempt that nearly resulted in a $171 million fraudulent transaction in 2016 against the Union Bank of India.
Another instance of a cyberattack involving online banking was Union Bank of India, resulting in a substantial loss. One of the officials fell for the phishing email and clicked on a dubious link, which allowed the malware to hack the system. The attackers entered the system using fake RBI IDs.
Banks have been mandated to strengthen their IT risk governance framework, which includes a mandate for their Chief Information Security Officer to play a proactive role in addition to the Board and the Board's IT committee playing a proactive role in ensuring compliance with the necessary standards.
Reasons Why Cybersecurity is Important in Banking
The banking industry has prioritized cybersecurity highly. Building credibility and trust is the cornerstone of banking, so it becomes much more essential. Here are five factors that demonstrate the significance of cybersecurity in the banking industry and why you should care:
- Everyone looks to be entirely cashless and using digital payment methods like debit and credit cards. In this case, ensuring that the required cybersecurity safeguards are in place to protect your privacy and data is critical.
- After data breaches, it could be difficult to trust financial institutions. That's a significant issue for banks. Data breaches caused by a shoddy cybersecurity solution may easily lead to their consumer base moving their business elsewhere.
- The majority of the time, when a bank's data is compromised, you lose time and money. Recovery from the same can be unpleasant and time-consuming. It would entail canceling cards, reviewing statements, and keeping a watchful lookout for issues.
- Inappropriate use of your private information might be very harmful. Your data is sensitive and could expose a lot of information that could be exploited against you, even if the cards are revoked and fraud is swiftly dealt with.
- Banks need to be more cautious than most other firms. That is the price for banks to retain the kind of valuable personal data they do. If the bank's information is not safeguarded against risks from cybercrime, it could be compromised.
.jpg&w=3840&q=75)
Top Cybersecurity Threats Faced by Banks
Cybercrimes have increased frequently over the past several years to the point where it is thought that they are one of the most significant hazards to the financial sector. Hackers have improved their technology and expertise, making it difficult for any banking sector to thwart the attack consistently. The following are some dangers to banks' cybersecurity:
1. Phishing Attacks
One of the most frequent problems with cybersecurity in the banking sector is phishing assaults. They can be used to enter a financial institution's network and conduct a more severe attack like APT, which can have a disastrous effect on those organizations ( Advanced Persistent Threat ). In an APT, a user who is not permitted can access the system and use it while going unnoticed for a long time. Significant financial, data and reputational losses may result from this. According to the survey , phishing assaults on financial institutions peaked in the first quarter of 2021.
The term "Trojan" is used to designate several dangerous tactics hackers use to cheat their way into secure data. Until it is installed on a computer, a Banker Trojan looks like trustworthy software. However, it is a malicious computer application created to access private data processed or kept by online banking systems. This kind of computer program has a backdoor that enables access to a computer from the outside.
Around the globe, there were roughly 54,000 installation packages for mobile banking trojans in the first quarter of 2022. There has been an increase of more than 53% compared to last year's quarter. After declining for the first three quarters of 2021, the number of trojan packages targeting mobile banking increased in the fourth quarter.
3. Ransomware
A cyber threat known as ransomware encrypts important data and prevents owners from accessing it until they pay a high cost or ransom. Since 90% of banking institutions have faced ransomware in the past year, it poses a severe threat to them.
In addition to posing a threat to financial cybersecurity, ransomware also affects cryptocurrency. Due to their decentralized structure, cryptocurrencies allow fraudsters to break into trading systems and steal money.
4. Spoofing
Hackers use a clone site in this type of cyberattack. By posing as a financial website, they;
- Design a layout that resembles the original one in both appearance and functionality.
- Establish a domain with a modest modification in spelling or domain extension.
The user can access this duplicate website via a third-party messaging service, such as text or email. Hackers can access a user's login information when the person is not paying attention. Seamless multi-factor authentication can solve a lot of these issues.
The Reserve Bank of India (RBI) reported bank frauds of 604 billion Indian rupees in 2022. From more than 1.3 trillion rupees in 2021, this was a decline.
Applications of Cybersecurity in Banking
Cybersecurity threats are constantly evolving, and the banking sector must take action to protect itself. Hackers adapt when new defenses threaten more recent attacks by developing tools and strategies to compromise security. The financial cybersecurity system is only as strong as its weakest link. It is critical to have a selection of cybersecurity tools and approaches available to protect your data and systems. Here are a few crucial cybersecurity tools:
1. Network Security Surveillance
Network monitoring is known as continuously scanning a network for signs of dangerous or intrusive behavior. It is frequently utilized with other security solutions like firewalls, antivirus software, and IDS ( Intrusion Detection System ). The software allows for either manual or automatic network security monitoring .
2. Software Security
Application security safeguards applications that are essential to business operations. It has features like an application allowing listing and code signing and could help you synchronize your security policies with file-sharing permissions and multi-factor authentication. The use of AI in cybersecurity will inevitably improve software security.
3. Risk Management
Financial cybersecurity includes risk management, data integrity, security awareness training, and risk analysis . Essential elements of risk management include risk evaluation and the prevention of harm from those risks. Data security also addresses the security of sensitive information.
4. Protecting Critical Systems
Wide-area network connections help avoid attacks on massive systems. It upholds the rigid safety standards set by the industry for users to follow when taking cybersecurity steps to protect their devices. It continuously monitors all programs and performs security checks on users, servers, and the network.
How to Make Banking Institutions Cyber Secure?
Security ratings are a great approach to indicate that you're concerned about the organization's cybersecurity. Still, you must also demonstrate that you're following industry and regulatory best practices for IT security and making long-term decisions based on that knowledge. A cybersecurity framework may be beneficial. You can go for Ethical Hacking training to enhance your knowledge further.
Top Cybersecurity Framework for Banks
A cybersecurity framework provides a common language and set of standards for security leaders across countries and industries to understand their security postures and those of their vendors. With a framework, it becomes easier to define the processes and procedures your organization must take to assess, monitor, and mitigate cybersecurity risk.
Let us take a look at some common financial cybersecurity frameworks:
1. NIST Cybersecurity Framework
The former president's executive order, Improving Critical Infrastructure Cybersecurity, asked for increased cooperation between the public and private sectors for recognizing, analyzing, and managing cyber risk. In response, the NIST Cybersecurity Framework was created. NIST has emerged as the gold standard for evaluating cybersecurity maturity, detecting security weaknesses, and adhering to cybersecurity legislation even when compliance is optional. To achieve NIST compliance , organizations can follow the guidelines outlined in the NIST Cybersecurity Framework and undergo rigorous assessments to ensure they meet the necessary standards.
2. The Bank of England's CBEST Vulnerability Testing Framework
CBEST vulnerability testing methodology was developed by the UK Financial Authorities in collaboration with CREST (the Council for Registered Ethical Security Testers) and Digital Shadows. It is an intelligence-led testing framework. CBEST's official debut took place on June 10, 2013.
CBEST leverages intelligence from reputable commercial and government sources to find possible attackers for a specific financial institution. Then, it imitates these potential attackers' methods to see how successfully they can breach the institution's Defenses. This enables a company to identify the weak points in its system and create and implement corrective action plans.
3. Cybersecurity and Privacy Framework for Privately Held Information Systems (the CIPHER Framework)
Computer systems that organizations, both public and private, control and that hold personal data gathered from their clients are referred to as PHISs (Privately Held Information Systems).
CIPHER framework addresses electronic systems, digital information kinds, and methods for data sharing, processing, and upkeep (not paper documents).
The CIPHER methodological framework's primary goal is to suggest procedures and best practices for protecting privately held information systems online (PHIS). The following are the main features of CIPHER methodological framework:
- Technology independence (versatility) refers to the ability to be used by any organization functioning in any field, even as existing technologies deteriorate or are replaced by newer ones.
- PHIS owners, developers, and citizens are the three primary users who focus on this user-centric approach.
- Practicality - outlines possible precautions and controls to improve or verify whether the organization is safeguarding data from online dangers.
- It is simple to use and doesn't require specialized knowledge from businesses or individuals.
Challenges in Implementing Cybersecurity in Banking
Some contributing elements have presented a significant challenge to digital cybersecurity in banking. The following are some of these:
- Lack of Knowledge: The general public's understanding of cybersecurity has been relatively low, and few businesses have significantly invested in raising that awareness.
- Budgets That are Too Small and Poor Management: Due to the low priority given to cybersecurity, it frequently receives short budgetary shrift. Cybersecurity continues to receive little attention from top management, and programs that assist it are accorded low priority. They might have underestimated how serious these risks are, which is why.
- Identities and Access are Poorly Managed: The core component of cybersecurity has always been identity and access management, especially now when hackers are in control and might access a business network with just one compromised login. Although there has been a little progress in this area, much work still needs to be done.
- Increase in Ransomware: Recent computer attacks have brought our attention to the growing threat of ransomware. Cybercriminals are beginning to employ various techniques to avoid being identified by endpoint protection code that concentrates on executable files.
- Smartphones and Apps: The majority of banking organizations now conduct business primarily through mobile devices. Every day the base grows, making it the best option for exploiters. Due to increased mobile phone transactions, mobile phones have become a desirable target for hackers.
- Social Media: Hackers have increased their exploitation as a result of social media adoption. Customers that are less knowledgeable expose their data to the public, which the attackers abuse.
Cybersecurity in the Banking Sector as a Career: Outlook
Compared to many other occupations, the cybersecurity field offers more job stability. For instance, the BLS predicts a 33% increase in employment for information security experts between 2020 and 2030. Information security in banking has also exponentially increased, and there is a high job demand for protecting against cyber threats to the banking industry. The following skills are required for cybersecurity in the banking industry:
1. Problem Solving Skills
In your day-to-day work as a cybersecurity specialist, problem-solving will be crucial. People working in the field must come up with innovative solutions to tackle and solve difficult information security concerns in a range of current and new technologies as well as digital surroundings.
2. Technical Skills
As the name suggests, cybersecurity focuses on technology. You will probably be assigned with duties including diagnosing, maintaining, and updating information security systems, putting in place continuous network monitoring, and offering real-time security solutions. To carry out a cybersecurity professional's daily duties, one must be digitally competent.
3. Communication Skills
Since you'll be collaborating closely with people in various departments and jobs as a cybersecurity professional, it's crucial that you can clearly express your discoveries, worries, and solutions to others. Speaking clearly and concisely about cybersecurity strategy and policy is crucial, as is being able to explain technical concepts to people with varying degrees of technical knowledge.
Looking to boost your ITIL knowledge? Join our unique online ITIL Foundation course ! Gain valuable insights and skills to excel in the IT industry. Enroll now and enhance your career prospects. Don't miss out!
Every organization is concerned about cyber security. It is crucial for banks to have the proper cyber security solutions and procedures in place, especially for institutions that store a lot of personal data and transaction lists. Banking cyber security is an issue that cannot be bargained with. Hackers are more likely to target the banking sector as digitalization advances.
KnowledgeHut is a platform that provides hundreds of courses in Data Science, Machine Learning, DevOps, Cybersecurity, Full Stack Development, and People and Process Certifications. With KnowledgeHut top Cybersecurity certifications , you can increase your knowledge about cybersecurity in the banking industry and get the proper training.
Frequently Asked Questions (FAQs)
The goal of cybersecurity in the banking sector is to protect consumer assets. The bank should also take action to thwart the hackers. The number of financial-related acts is growing as more individuals work.
Through fraudulent transactions, cyberattacks can result in significant financial losses for the customer and the banks. Attackers who steal sensitive data from a banking institution may sell it. Data that has been stolen is later misused.
Antivirus software is typically used on bank computers, firewalls, fraud detection, and website encryption, which encrypts data so that only the intended receiver can read it. Your financial institution likely implements these security precautions if you bank online.

Vitesh Sharma
Vitesh Sharma, a distinguished Cyber Security expert with a wealth of experience exceeding 6 years in the Telecom & Networking Industry. Armed with a CCIE and CISA certification, Vitesh possesses expertise in MPLS, Wi-Fi Planning & Designing, High Availability, QoS, IPv6, and IP KPIs. With a robust background in evaluating and optimizing MPLS security for telecom giants, Vitesh has been instrumental in driving large service provider engagements, emphasizing planning, designing, assessment, and optimization. His experience spans prestigious organizations like Barclays, Protiviti, EY, PwC India, Tata Consultancy Services, and more. With a unique blend of technical prowess and management acumen, Vitesh remains at the forefront of ensuring secure and efficient networking solutions, solidifying his position as a notable figure in the cybersecurity landscape.
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates
- Leading in the Post-COVID World
- Leadership Development
- Top C-Suite Interviews
- Women in Leadership
- Career and Learning
- Corporate Governance
- Culture & Lifestyle
- Legal Services
- Future Series
- Accelerator Series
- Emerging Ideas
- Design Thinking
- Business Model
- Latest News
- Digital Transformation
- Artificial Intelligence
- Blockchain & Crypto
- Big Data & Analytics
- Computer & Software
- Internet of Things
- Business Mobility & E-Commerce
- Industry 4.0 & Manufacturing
- Product and Service Reviews
- Home Improvement
- Strategic Spotlight
- People Management
- Remote Work
- Organisational Change
- Crisis Management
- Global Business
- Luxury Strategy
- Personal Finance
- Social Media
- Business Process
- Transportation & Business Fleet
- Succession Planning
- Climate Change & Green Business
- Social Impact
- Health & Wellness
- Top Executive Education with Best ROI
- Interviews with Directors and Faculties
- Executive Education Calendar
- Programme Highlights
- Success Stories
- Industry Insights
- Programme Directory
- Executive Education Q&As
- The Hamilton Mann Conversation: Digital For Good
- Fernanda Arreola – Inclusive Innovation: Rendering Change Accessible
- Simon L. Dolan – A Future Shaper
- Hervé LEGENVRE – EIPM Research on Technology and Collaboration
- Mapping the Future of Business with Jacques Bughin
- Adrian Furnham – On Your Head
- Kamil Mizgier On Navigating Risk Frontiers
- Delivering Innovation – Accenture Research
- The Better Boards Podcast Series
- Best Partners for Business Growth
- David De Cremer on Management
- Success through the Lorange Network
- A Special Report on AI and Humans by AiTH, NUS Business School
- Surdak on Technology
- Female Leadership In Our Time
- Europe’s recovery is possible. This is how…
- Editors’ Pick
- Business Events Calendar
- Events Partnership
- Travel & Leisure
- Our Mission
- Top Executive Education
- Advertising
- Guidelines for Authors
- Past Covers
- Privacy Policy
- Terms and Conditions

- IoT & Cyber Security
Cybersecurity in Banking Industry: Importance, Challenges, and Use-Cases

Cybersecurity is not a recent term in the financial industry. Banking institutions have been using it to protect their systems, data, and transactions to avoid fraud and identity thefts.
According to Statista, by 2026 , the global cybersecurity market size is forecast to grow to 345.4 billion U.S. dollars . Similarly, India crossed over 500 million dollars in 2020 , which would rise to 800 million dollars by 2022 .
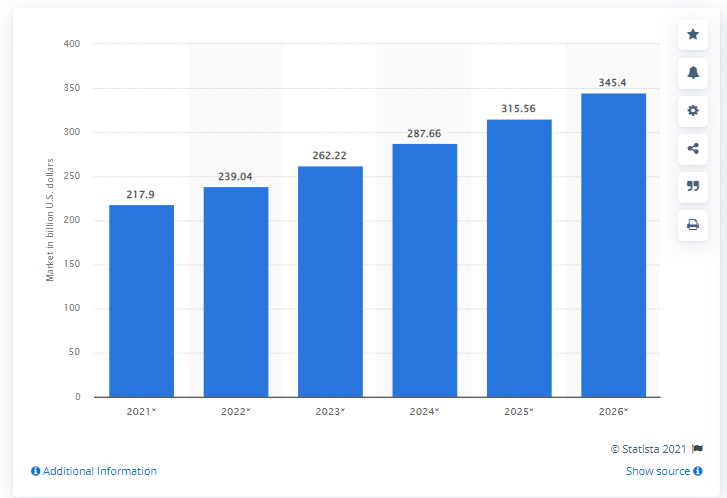
This means that Cybersecurity in the banking industry is a relatively not new concept, but it will increase exponentially in the future.
However, Did you ever think about it? :
- Why is it so important?
- What are the challenges of Cybersecurity in the banking industry?
- And what are the use-cases of it?
Not yet? Don’t worry; you will learn about them in this article. Let’s first start with the importance of Cybersecurity in the banking industry.
Cybersecurity in Banking Industry: Importance
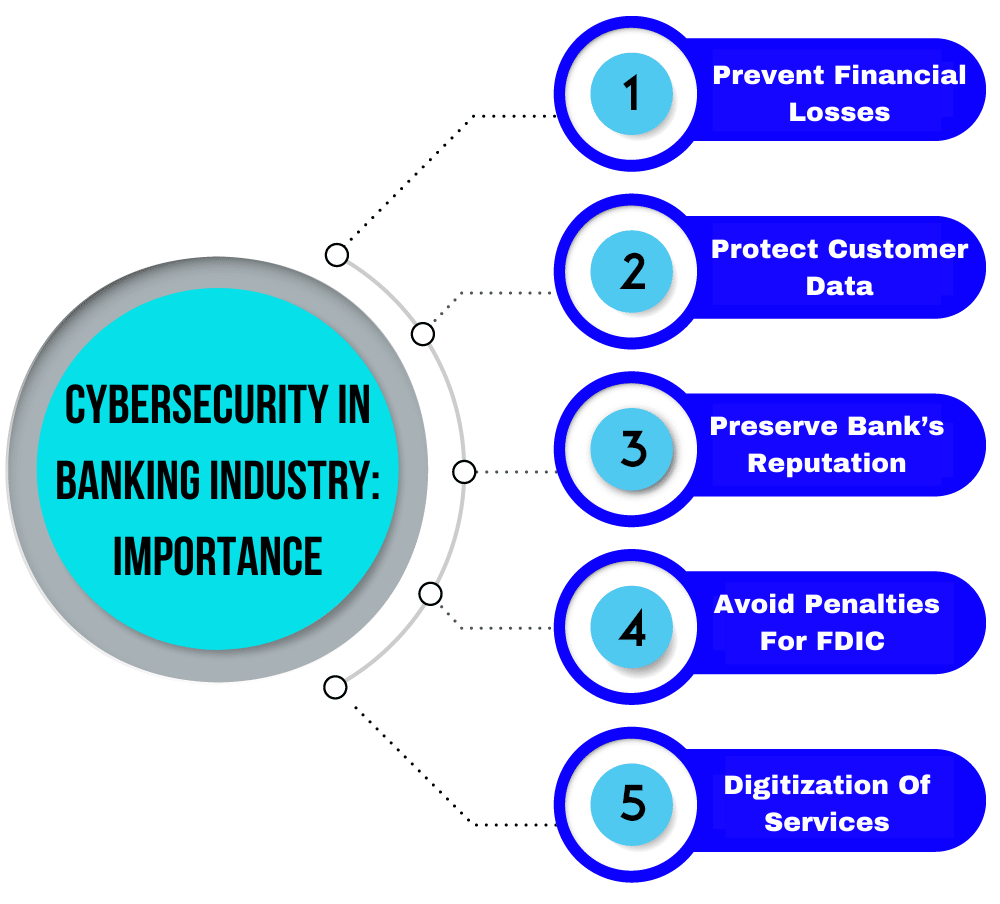
1. Prevent Financial Losses
The banking industry holds the data of millions of people, and this data can help hackers in many ways. For example, if someone hacks your bank account using your ID info, they can steal all your money in seconds, not to mention that it is almost impossible to recover stolen money.
In such cases, banks are left with three options:
- They can compensate money
- Freeze the account in which fraud has occurred
- Close down the entire branch where fraud has happened.
But banks do not prefer two out of all these three options. Compensating money can be costly, and freezing accounts may result in a loss of customers.
With the help of Cybersecurity in the banking industry, banks can minimize these losses and protect their accounts from fraud. Technology like biometric authentication and Artificial Intelligence (AI) can help credit institutions save money.

Furthermore, it will protect customers’ accounts and increase customers’ trust in the banking industry.
2. Protect Customer Data
The banking industry is expanding daily, and with that expansion comes a great deal of responsibility. Financial authorities now need to prioritize the security of their customers’ data and transactions since it can be used for multiple purposes:
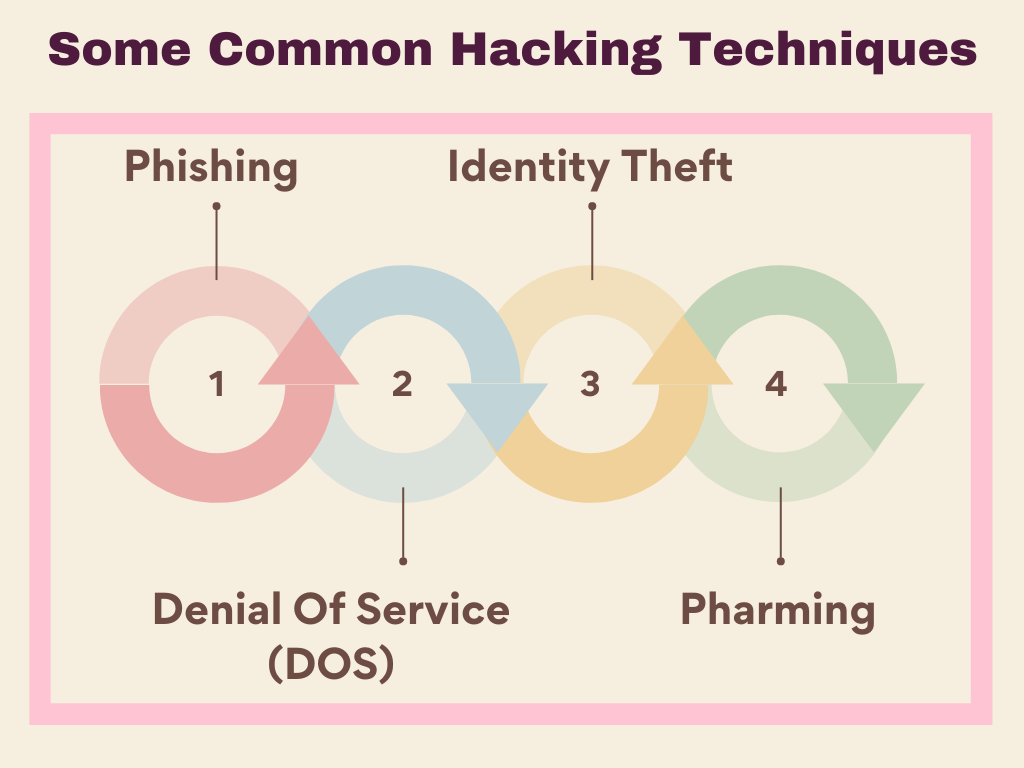
• Phishing : This technique uses fake emails like official emails, but they contain links to malware. Hackers use this technique to steal customers’ sensitive data like passwords, credit card numbers, etc.
• Identity Theft: This refers to changing a person’s personal information without their consent and then using it for harmful purposes.
• Denial Of Service (DOS): A DOS attack works by sending traffic from unrelated sources towards a server on which an organization’s website is hosted. It causes the server to overload and shut down, resulting in the organization losing its site temporarily.
• Pharming: This technique is used by fraudsters to redirect users from an authentic website to a fake website. Hackers use it to steal the information required for online transactions. Therefore, this technique puts customers’ data at risk and financial security.
Moreover, all these techniques share one thing: They use sensitive personal information for personal and financial gains. In addition to this, if hackers get access to these techniques, they can misuse them for other purposes as well. That is why Cybersecurity in the banking industry is so important.
Some big organizations have already started using it. For example, Citigroup has introduced biometric authentication for all its US customers.
3. Preserve Bank’s Reputation
Banks must follow strict regulations, so it takes them quite some time to adopt new technology. However, with the increased number of cyberattacks, they are now more open to Cybersecurity.
The increase in cyberattacks has also hurt the reputation of banks. According to a study by Kaspersky Lab, out of 1000 consumers surveyed in the UK, Germany, India, and USA, 94% of consumers said they would switch banks if their data got into the wrong hands.
The study also revealed that 60% of consumers take their time when choosing a bank because they are afraid of becoming a victim of a cyberattack.
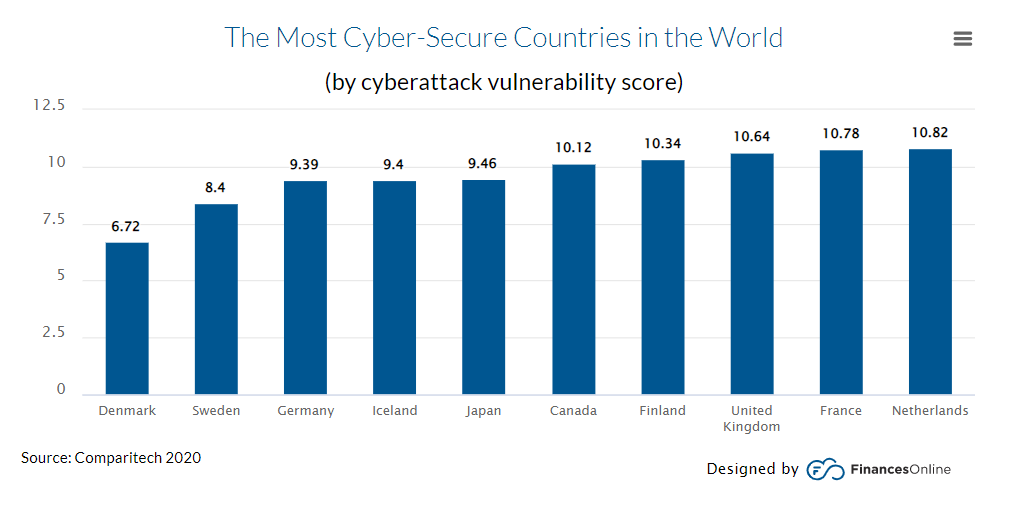
Therefore, banks need to restore their reputation by introducing new technology like AI, data encryption, etc., for better security. Furthermore, according to Comparitech’s 2020 report, the most cyber-safe countries in the world are Denmark (6.72), Sweden (8.40), Germany (9.39), Ireland (9.40), and Japan (9.46) based on cyberattack vulnerability scores.
4. Avoid Penalties For FDIC Non-Compliance
The next most considerable importance of Cybersecurity in the banking industry is avoiding penalties from FDIC. If a bank does not follow the Federal Deposit Insurance Corporation (FDIC) regulations, it can impose hefty fines and even shut down that particular bank.

Some of the fines that FDIC imposes on banks for non-compliance are:
• Up to $1 million per violation.
• In severe cases, a year in prison may be imposed.
• Forced ratification of contracts violations in some cases.
And many others.
So, imagine what would happen if a bank’s security was compromised due to a hack? That is why banks should implement security measures to prevent such a situation. FinTech companies can provide cybersecurity solutions using blockchain technology to help banks improve their security standards.
Besides, some financial institutions hire blockchain developers to help them use this technology for their purposes. Accordingly, here are some examples of how blockchain can be used in financial institutions to improve cybersecurity:
- Using blockchain, financial institutions can store sensitive information about their clients in a decentralized database. It will help them stay compliant with regulations and avoid hefty fines imposed by FDIC.
- Banks can also use blockchain to share information about the customer without compromising their identity and security. It can be beneficial to prevent fraud and money laundering cases in the future.
- By integrating blockchain technology into their systems, banks can create a scalable and efficient system that will prevent security breaches like:
- Phishing attacks to access customers’ sensitive information.
- Man in the middle (MITM) attacks.
- DDoS Attack.
- Some experts say that as blockchain is decentralized, it is more secure than conventional databases because it is nearly impossible to hack. The encryption technology used in blockchain also makes it more secure than conventional systems.
- Blockchain protects sensitive information by splitting it into pieces and storing it on different nodes, decentralizing the whole system. This way, hackers will not find or misuse any information even if they manage to access a single block.
5. Digitization Of Services

Another importance of cyber security in banking is the digitization of services. As we know, more and more people prefer online bank account management to the old brick-and-mortar institutions. They can do everything from their computers or mobile phones that they could do at a physical branch.
For example:
• Direct deposit means customers don’t have to wait days to get their paychecks.
• Purchasing shares of a company is now as easy as buying vegetables at the local supermarket.
• Transferring money to another country has never been easier because all you need is an internet connection and bank account number or routing number.
As digitalization becomes more popular, banks spend vast chunks of their revenue upgrading their systems. But, these huge costs are not being returned to banks because people have already mastered the art of managing their bank accounts online.
This is why there’s a massive need for cyber security in the banking industry because, without it, all that investment will go down the drain.
So, you can see how critical cybersecurity is to banks and other financial institutions. It is now time to count down the banking industry’s challenges.
Cybersecurity in Banking Industry: Challenges
1. balancing security and convenience.
Although cybersecurity is essential to banks, they also need to provide convenience to their customers. If a bank’s security measures are too strict, many people may switch their accounts to a bank with less stringent regulations.
On the other hand, if the security provided by a bank is not convenient, then there will be huge costs because of the extra security measures. More money will need to be spent on additional personnel, software, and hardware for the bank’s security system.
Therefore, banks must come up with the right balance of convenience and security to survive in the long run.
2. Effectively Managing The Risk Of Breaches
Another challenge faced by banks is to manage the risk of breaches effectively. They may have the most secure system in place, but hackers can still find ways to compromise these systems.
That is why banks must test their system regularly for vulnerabilities. They also need to continuously update their security systems with the latest technologies available to remain one step ahead of hackers.
3. Financial Impact Of Breaches
Not only does cybersecurity affect customers, but it also has a direct impact on the bank’s bottom line. When hackers successfully breach a bank’s system and gain access to sensitive information, there’s no telling what they’ll do with it.
This can be terrifying because it could result in lawsuits against the bank or even government regulations that change its operation. These changes will affect a bank’s profit margins because additional costs will be deducted from their revenue.
4. Constant Evolution Of Threats And Vulnerabilities
Another cybersecurity challenge faced by banks is the constant evolution of threats and vulnerabilities. Hackers are constantly updating their techniques to get around new security measures.
Therefore, banks may need to continuously update their cyber security protocols to stay ahead of hackers every step of the way. Also, it requires a lot of time and money because banks need to hire more personnel, spend vast amounts on software, and buy new hardware for their security systems.
5. Efficient Protection Against Advanced Threats
In addition to the constant evolution of threats and vulnerabilities, banks also need to focus on efficient protection against advanced threats. Furthermore, hackers are becoming more sophisticated by the day, which means that a bank’s security system will struggle to keep up.
This is especially problematic because the more time hackers have to unleash their attack, the higher the chances of successfully breaching a bank’s system. This means that banks need to invest in new technologies for defense against these advanced threats to ensure cyber security.
These were some of the cybersecurity challenges faced by banks. If you are interested in learning about use cases for Cybersecurity in Banking, you can keep reading this blog.
5 Use Cases for Cybersecurity in Banking
1. fraud monitoring and prevention.
When customers use their bank accounts, they must provide personal information for verification purposes. Hackers can abuse this information by transferring money to their accounts or creating unauthorized transactions.
Banks will need to incorporate more advanced technologies like machine learning algorithms to prevent fraud. These tools can learn how customers use their bank accounts and detect “suspicious” transactions.
2. Identify Compromised Devices
These days, many credit card fraud cases can be traced back to hacked personal computers or mobile phones. Hackers will seek out any device with access to a person’s bank account and then try to hijack it to run their transactions.
Since this can be difficult to detect, banks will need “threat intelligence” tools that will allow them to keep track of any suspicious behavior on the account holder’s end.
3. Payment Security
Sending bank customers bogus emails that look to come from their banks is one of the most prevalent ways hackers obtain information. These emails will ask the bank customers to verify their information by clicking on a link or providing their security credentials.
This way, hackers can gain access to a person’s bank account because they now have all the personal and financial information they need. Banks will need “phishing protection tools” to keep track of these fraudulent emails to protect their customers.
4. Data Retrieval
Before a bank customer can withdraw or transfer money, they must provide the proper data such as account numbers and PINs. Banks must always be on guard for stolen credentials because these can give hackers direct access to the targeted person’s bank account.
Banks can protect their customers by requiring additional security measures before money can be withdrawn or transferred. For example, they can ask for verification codes sent through text messages generated every time a transaction is made.
5. Data Protection Tools
One of the most fundamental reasons we need to focus on cyber security is that hackers can use stolen customer credentials to access sensitive company data. If a hacker manages to infiltrate a bank’s system, they can steal any information in the server, including personal and financial data.
This is very dangerous because it can lead to identity theft or fraud—Banks must-have tools in place that will keep hackers out of their data storage.
As you can see, banks will need top-of-the-line technology to protect their customers and company data from hackers. If they don’t focus on cyber security, they can expect significant losses in the future due to stolen records or leaked customer information.
This article should have given you some examples or use cases for cybersecurity in banking. Why is it important to banks and other financial institutions? What challenges will banks face when they incorporate cybersecurity into their business model?
Although, if you are searching for banking software development companies in India that can help you with your banking needs or any other financial software development? Feel free to contact PixelCrayons; we will provide you with the best cost-effective solution per your requirement.
RELATED ARTICLES MORE FROM AUTHOR

Emerging Technology Trends in Real Estate: Transforming the Market in 2024

What is AES Encryption and How Does It Work?

5 Unknown Risks of AI Personal Assistants

How AI Liberates the Transition to a Skill-Based Organisation

Navigating the World of Hidden Apps on Android: A Deep Dive into Privacy and Security

Privacy Matters: How to Maintain Anonymity and Security When Using Escort Sites
Leave a reply cancel reply.
Save my name, email, and website in this browser for the next time I comment.
Free Online Event for Digital Publishing and News Media Professionals!
Ai & big data expo north america, responsible business europe 2024 (london, june 11-12), international hrd summit 2024, curious2024 – future insight™ conference, global ev & mobility technology forum, 2024 world battery & energy storage industry expo (wbe), reuters events: sustainable transport 2024 (3-4 september, amsterdam), leading people and teams, online mba – stephen m. ross school of business, meet our mba alumni – university of bath, v-entrepreneurs talk 2024: the ritchie story, 2024 learning impact conference, meet us in london – university of st.gallen (hsg), mba experience event – ghent campus – vlerick business school, hr day 2024 – vlerick business school, featured articles.

Unlocking the Power of AI Leadership: A Dialogue with Professor David De Cremer

How Top-Performing Firms Needed to Reorganise Seven Times for Digital

How to Put Curiosity to Work in Your Organisation

Leading the Gen AI Revolution: Building Workers’ Trust to Reinvent Work in Europe

Aligning Organisational Ecosystems to be Fit for Purpose

Generative AI Update for 2024

Longevity for Sustainability: Adding Value That Lasts

Magnetic Loyalty: Crafting Effective Loyalty Programmes that Attract and Retain Customers

A New Business Leadership Paradigm to Understand Signals and Timing: When to ENTER a Business and When to EXIT
Future series.

What Does EVhype Teach Us, and How Can We Consider the Lessons in AI’s Development?

Embracing AI: The Next Frontier in Elderly Housing

The Dawn of the Value Economy Era

Models to Scale ESG Metrics and Data
Strategy & management.

How To Build a Strong Brand Identity for Your SaaS MVP

Bluemina: A Leading Force in Citizenship and Residency Solutions Launching a Virtual Office for Clients Anytime Anywhere!

How to Build a Highly Successful Email Marketing Funnel for Conversions

German Stock Index Hits Record

Gender Pay Disparities Persist Among Independent Contractors
Upcoming events, privacy overview.
Cybersecurity hazards and financial system vulnerability: a synthesis of literature
- Original Article
- Published: 18 August 2020
- Volume 22 , pages 239–309, ( 2020 )
Cite this article

- Md. Hamid Uddin ORCID: orcid.org/0000-0003-3025-0206 1 , 2 ,
- Md. Hakim Ali 2 &
- Mohammad Kabir Hassan 3
2683 Accesses
25 Citations
1 Altmetric
Explore all metrics
In this paper, we provide a systematic review of the growing body of literature exploring the issues related to pervasive effects of cybersecurity risk on the financial system. As the cybersecurity risk has appeared as a significant threat to the financial sector, researchers and analysts are trying to understand this problem from different perspectives. There are plenty of documents providing conceptual discussions, technical analysis, and survey results, but empirical studies based on real data are yet limited. Besides, the international and national regulatory bodies suggest guidelines to help banks and financial institutions managing cyber risk exposure. In this paper, we synthesize relevant articles and policy documents on cybersecurity risk, focusing on the dimensions detrimental to the banking system’s vulnerability. Finally, we propose five new research avenues for consideration that may enhance our knowledge of cybersecurity risk and help practitioners develop a better cyber risk management framework.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others


Cybersecurity disclosure in the banking industry: a comparative study

A Survey of Cybersecurity Risk Management Frameworks

Cyber risk and cybersecurity: a systematic review of data availability
The systems should be designed to ensure a high degree of security and operational reliability. Also, the system should be strong enough to predict the likelihood of future cyber events and take auto protective measures in anticipation of a cyber breach.
It is because cybersecurity risk cannot be mitigated by mere application of upgraded hardware or software as no technology is perfect, and perpetrators can always break the system. Therefore, cybersecurity is now a boardroom issue. It means the corporate managers of financial institutions need to consider the amount of investment in cyber technology more rationally. Otherwise, it might adversely affect the financial performance and stability of banks.
The operational efficiency declines because of unavoidable cybersecurity hazards that often require the users to apply more complex passwords or two-stage authentication. Since complex passwords and multi-stage authorization processes are difficult to memorize, the chances of access denial to genuine users increase that has an implication of time and cost for the users.
The asymmetry of cyber knowledge (between criminals and innocent users) allows criminals to exploit the innocent users to breach the system, suggesting a positive association between faster and widespread use of cyber technology and security risk exposure (Willison and Warkentin 2013 ; Longstaff et al. 2020 ).
Bouveret ( 2018 ) proposed a broader framework of cyber risk assessment that captures the different dimension of cybersecurity hazards such as (i) security threat level, (ii) system vulnerability status, and (iii) financial consequences of a security breach.
The expert report suggests that the DDoS attack can be prevented by increasing bandwidth, creating redundancy in cyber infrastructure, configuring hardware, and deploying anti-DDoS hardware and software, using the DDoS protection appliance, move to a cloud-based DNS provider (Rubens 2018 ).
Without technological support, hybrid securities cannot be developed.
For example, General Data Protection Regulation 2016 (for EU), the UK Data Protection Act 2018, the Personal Data Protection Act 2010 of Malaysia.
Abraham, S., and P.J. Shrives. 2014. Improving the relevance of risk factor disclosure in corporate annual reports. The British accounting review 46 (1): 91–107.
Google Scholar
ACSS. 2016. Australia’s cyber security strategy. Commonwealth of Australia, Department of the Prime Minister and Cabinet. https://cybersecuritystrategy.homeaffairs.gov.au/ .
Ahmad, N., and P. Schreyer. 2016. Measuring GDP in a digitalised economy . Paris: OECD Publishing. https://doi.org/10.1787/18152031 .
Book Google Scholar
AIG. 2016. December. Is cyber risk systemic? New York: American International Group. https://www.aig.com/content/dam/aig/america-canada/us/documents/business/cyber/aig-cyber-risk-systemic-final.pdf .
Akhawe, D., A. Barth, P.E. Lam, J. Mitchell, and D. Song. 2010. Towards a formal foundation of web security. In 2010 23rd IEEE computer security foundations symposium , 290–304. IEEE.
Akhisar, İ., K.B. Tunay, and N. Tunay. 2015. The effects of innovations on bank performance: The case of electronic banking services. Procedia—Social and Behavioral Sciences 195: 369–375.
Aldasoro, I., L. Gambacorta, P. Giudici, and T. Leach. 2020a. Operational and cyber risks in the financial sector. BIS Working Paper No. 840 . Basel, Switzerland: Bank for International Settlements.
Aldasoro, I., L. Gambacorta, P. Giudici, and T. Leach. 2020b. The drivers of cyber risk. BIS Working Paper No. 865 . Basel, Switzerland: Bank for International Settlements.
Alex Johnson. 2018, May 9. Equifax breaks down just how bad last year’s data breach was. NBC News. https://www.nbcnews.com/news/us-news/equifax-breaks-down-just-how-bad-last-year-s-data-n872496 .
Allen, F., and D. Gale. 2004. Competition and financial stability. Journal of Money, Credit and Banking 36 (3): 453–480.
Almansi, A.A. 2018. Financial sector’s cybersecurity: Regulations and supervision . Washington, United States of America: World Bank Group.
Almansi, A.A., Y.C. Lee, and J. Lincoln. 2017. Financial sector’s cybersecurity: A regulatory digest. World Bank . Washington: Financial Sector Advisory Center.
Ames, M., T. Schuermann, and H.S. Scott. 2015. Bank capital for operational risk: A tale of fragility and instability. Journal of Risk Management in Financial Institutions 8 (3): 227–243.
Antonescua, M., and R. Birău. 2015. Financial and non-financial implications of cybercrimes in emerging countries. Procedia Economics and Finance 32: 618–621.
Arner, D.W., J. Barberis, and R.P. Buckley. 2016. FinTech, RegTech, and the reconceptualization of financial regulation. Northwestern Journal of International Law & Business 37 (3).
Aseef, N., P. Davis, M. Mittal, K. Sedky, and A. Tolba. 2005. Cyber-criminal activity and analysis . Washington Education: White paper.
Ashford, W. 2019, July 31. Financial services top cyber attack target. Computer Weekly . https://www.computerweekly.com .
Aziz, A.S., M.A. Salama, A.E. Hassanien, and S.E.O. Hanaf. 2012. Artificial immune system inspired intrusion detection system using genetic algorithm. Informatica 36: 347–357.
Banker, R.D., R.J. Kauffman, and R.C. Morey. 1990. Measuring gains in operational efficiency from information technology: A study of the Positran deployment at Hardee’s Inc. Journal of Management Information Systems 7 (2): 29–54.
Barrett, M., E. Davidson, J. Prabhu, and S.L. Vargo. 2015. Service innovation in the digital age: Key contributions and future directions. MIS quarterly 39 (1): 135–154.
Barthelemy, J. 2001. The hidden costs of IT outsourcing: Lessons from 50 IT-outsourcing efforts show that unforeseen costs can undercut anticipated benefits. Understanding the issues can lead to better outsourcing decisions. MIT Sloan Management Review 42 (3): 60–72.
BDO. 2017. Cyber security in banking industry . India: BDO.
Beccalli, E. 2007. Does IT investment improve bank performance? Evidence from Europe. Journal of Banking & Finance 31 (7): 2205–2230.
Beitollahi, H., and G. Deconinck. 2012. Analyzing well-known countermeasures against distributed denial of service attacks. Computer Communications 35 (11): 1312–1332.
Benaroch, M., A. Chernobai, and J. Goldstein. 2012. An internal control perspective on the market value consequences of IT operational risk events. International Journal of Accounting Information Systems 13: 357–381.
Berger, A.N., and R.D. Young. 1997. Problem loans and cost efficiency in commercial banks. Journal of Banking & Finance 21 (6): 849–870.
Berkman, H., J. Jona, G. Lee, and N. Soderstrom. 2018. Cybersecurity awareness and market valuations. Journal of Accounting and Public Policy 37 (6): 508–526.
Bernik, I. 2014. Cybercrime: The cost of investments into protection. Journal of Criminal Justice and Security 16 (2): 105–116.
Biener, C., M. Eling, and J.H. Wirfs. 2015. Insurability of cyber risk: An empirical analysis. The Geneva Papers on Risk and Insurance-Issues and Practice 40 (1): 131–158.
BIS. 2004. Consolidated KYC risk management. Basel Committee on Banking Supervision. https://www.bis.org/publ/bcbs110.pdf .
BIS. 2013. The road to a more resilient banking sector. BIS. https://www.bis.org/publ/arpdf/ar2013e.htm .
BIS. 2016, June. Bank for international settlements. www.bis.org . https://www.bis.org/cpmi/publ/d146.pdf .
Boer, M., and J. Vazquez. 2017. Cyber security & financial stability: How cyber-attacks could materially impact the global financial system . Washington: The Institute of International Finance.
Böhme, R. 2010. Security Metrics and Security Investment Models. In Advances in information and computer security , ed. I. Echizen, N. Kunihiro, and R. Sasaki, 10–24. Berlin: Springer.
Böhme, R. 2012, February. Security audits revisited. in International conference on financial cryptography and data security , 129–147. Berlin: Springer.
Boin, A., and A. McConnell. 2007. Preparing for critical infrastructure breakdowns: The limits of crisis management and the need for resilience. Journal of Contingencies and Crisis Management 15 (1): 50–59.
Bouveret, A. 2018. Cyber risk for the financial sector: A framework for quantitative assessment. IMF Working Paper No. WP/18/143 . International Monetary Fund.
Bouveret, A. 2019a. Cyber risk for the financial services sector. Journal of Financial Transformation 49.
Bouveret, A. 2019b. Estimation of losses due to cyber risk for financial institutions. Journal of Operational Risk , Forthcoming.
Brechbuhl, H., R. Bruce, S. Dynes, and M.E. Johnson. 2010. Protecting critical information infrastructure: Developing cybersecurity policy. Information Technology for Development 16 (1): 83–91.
Brown, C.S. 2015. Investigating and prosecuting cyber crime: Forensic dependencies and barriers to justice. International Journal of Cyber Criminology 9 (01): 55–119. https://doi.org/10.5281/zenodo.22387 .
Article Google Scholar
Burden, K., and C. Palmer. 2003. Internet crime: Cyber crime—A new breed of criminal? Computer Law & Security Review 19 (3): 222–227.
Cabinet Decision. 2015. Cybersecurity strategy. The Government of Japan. https://www.nisc.go.jp/eng/pdf/cs-strategy-en.pdf .
Carey, M., and R.M. Stulz. 2008. The risks of financial institutions. Journal of Contingencies and Crisis Management 16 (1): 65–66. https://doi.org/10.1111/j.1468-5973.2008.00532_2.x .
CarlColwill, 2009. Human factors in information security: The insider threat—Who can you trust these days? Information Security Technical Report 14 (4): 186–196.
Caron, F. 2015. Cyber risk management in financial market infrastructures: Elements for a holistic and risk - based approach to cyber security. Belgium: National Bank of Belgium. https://lirias.kuleuven.be/1834699?limo=0 .
Carter, W.A., and D.E. Zheng. 2015. The evolution of cybersecurity requirements for the U.S. financial industry . USA: Center for Strategic and International Studies.
Caruana, J. 2009, February. Lessons of the financial crisis for future regulation of financial institutions and markets and for liquidity management . Washington, DC: IMF.
Casu, B., A. Ferrari, C. Girardone, and J.O. Wilson. 2016. Integration, productivity and technological spillovers: Evidence for eurozone banking industries. European Journal of Operational Research 255 (3): 971–983.
Cavusoglu, H., S. Raghunathan, and W. Yue. 2008. Decision-theoretic and game-theoretic approaches to IT security investment. Journal of Management Information Systems 25 (2): 281–304.
Cebula, J.J., and L.R. Young. 2010. A taxonomy of operational cyber. Carnegie-Mellon Univ Pittsburgh PA Software Engineering Inst.
Cetorelli, N., B. Hirtle, D. Morgan, S. Peristiani, and A.J. Santos. 2007. Trends in financial market concentration and their implications for market stability. Federal Reserve Bank of New York Policy Review 33–51.
Chauhan, Y., and S.B. Kumar. 2018. Do investors value the nonfinancial disclosure in emerging markets? Emerging Markets Review 37: 32–46.
Cherdantseva, Y., P. Burnap, A. Blyth, P. Eden, K. Jones, H. Soulsby, and K. Stoddart. 2016. A review of cyber security risk assessment methods for SCADA systems. Computers & Security 56: 1–27.
Choo, K.-K.R. 2011. The cyber threat landscape: Challenges and future research directions. Computers & Security 33 (8): 719–731.
Choo, K.-K.R., R.G. Smith, and R. McCusker. 2007. Future directions in technology-enabled crime: 2007–09 . Canberra: Australian Institute of Criminology.
Chowdhury, A. 2003. Information technology and productivity payoff in the banking industry: Evidence from the emerging markets. Journal of International Development 15 (6): 693–708.
Clare Sullivan, E.B. 2017. “In the public interest”: The privacy implications of international business-to-business sharing of cyber-threat intelligence. Computer Law & Security Review 33: 14–29.
Committee on Payments and Market Infrastructures. 2016. Guidance on cyber resilience for financial market infrastructures. Bank for International Settlements. https://www.bis.org/cpmi/publ/d146.pdf .
Crisanto, J.C., and J. Prenio. 2017, August. Regulatory approaches to enhance banks’ cyber - security frameworks. Bank for International Settlements. https://www.bis.org/fsi/publ/insights2.pdf .
Das, S., A. Mukhopadhyay, and M. Anand. 2012. Stock market response to information security breach: A study using firm and attack characteristics. Journal of Information Privacy and Security 8 (4): 27–55.
Deloitte. 2014. Transforming cybersecurity in the Financial Services Industry. Deloitte. https://www2.deloitte.com/content/dam/Deloitte/za/Documents/risk/ZA_Transforming_Cybersecurity_05122014.pdf .
Demirgüç-Kunt, A., L. Klapper, D. Singer, S. Ansar, and J. Hess. 2018. The global findex database 2017: Measuring financial inclusion and the Fintech revolution. The World Bank.
Derek Young, J.L. 2016. A framework for incorporating insurance in critical infrastructure cyber risk strategies. International Journal of Critical Infrastructure Protection 14: 43–57.
Diamond, D.W., and P.H. Dybvig. 1983. Bank runs, deposit insurance, and liquidity. Journal of Political Economy 91 (3): 401–419.
Diamond, D.W., and P.H. Dybvig. 1986. Banking theory, deposit insurance, and bank regulation. The Journal of Business 59 (1): 55–68.
Donge, Z., F. Luo, and G. Liang. 2018. Blockchain: A secure, decentralized, trusted cyber infrastructure solution for future energy systems. Journal of Modern Power Systems and Clean Energy 1–10.
Duffie, D., and J. Younger. 2019. Cyber runs. Hutchins Center Working Paper #51 . Washington, DC: The Hutchins Center on Fiscal & Monetary Policy, Brookings Institution.
Dufwenberg, M., and M.A. Dufwenberg. 2018. Lies in disguise—A theoretical analysis of cheating. Journal of Economic Theory 175: 248–264.
Duncan, N.B. 1995. Capturing flexibility of information technology infrastructure: A study of resource characteristics and their measure. Journal of Management Information Systems 12 (2): 37–57.
Duran, R.E., & P. Griffin. 2019. Smart contracts: Will Fintech be the catalyst for the next global financial crisis? Journal of Financial Regulation and Compliance (in press)
Dutta, A., and K. McCrohan. 2002. Management’s role in information security in a cyber economy. California Management Review . https://doi.org/10.2307/41166154 .
Eling, M., and M. Lehmann. 2018. The impact of digitalization on the insurance value chain and the insurability of risks. The Geneva Papers on Risk and Insurance-Issues and Practice 43 (3): 359–396.
Eling, M., and J. Wirfs. 2019. What are the actual costs of cyber risk events? European Journal of Operational Research 272 (3): 1109–1119.
Embrechts, P., H. Furrer, and R. Kauffman. 2003. Quantifying regulatory capital for operational risk. Derivatives Use, Trading and Regulation 9 (3): 217–233.
EU. 2018, May. The Directive on security of network and information systems (NIS Directive). https://ec.europa.eu/digital-single-market/en/network-and-information-security-nis-directive .
Euromoney. 2017, August 1. Technology investments drive up banks’ costs. Euromoney Magazine . London.
Fed. 2017, September. Federal reserve policy on payment system risk. Washington: Federal Reserve System.
Federal Office for Information Security. 2017. The state of IT security in Germany 2017. FOIS.
Fitch. 2017, April. Cybersecurity an increasing focus for financial institutions. https://www.fitchratings.com/site/pr/1022468 .
Francis, L., and V.R. Prevosto. 2010. Data and disaster: The role of data in the financial crisis. In casualty actuarial society e-forum, 62. New York: Springer.
Garg, A., J. Curtis, and H. Halper. 2003. The financial impact of IT security breaches: What do investors think? Information Systems Security 12 (1): 22–33.
Gatzlaff, K.M., and K.A. McCullough. 2010. The effect of data breaches on shareholder wealth. Risk Management and Insurance Review 13 (1): 61–83.
Gelenbe, E., and G. Loukas. 2007. A self-aware approach to denial of service defence. Computer Networks 51: 1299–1314.
Germano, J.H. 2014. Cybersecurity partnerships: A new era of public-private collaboration . New York: New York University School of Law.
Geyres, S., and M. Orozco. 2016. Think banking cybersecurity is just a technology issue? Think again. Accenture strategy. https://www.accenture.com/t20160419t004021__w__/us-en/_acnmedia/pdf-13/accenture-strategy-cybersecurity-in-banking.pdf .
Gladstone, R. 2016, March 15. Bangladesh Bank chief resigns after cyber theft of $81 million. The New York Times .
Glaessner, T., T. Kellermann, and V. McNevin. 2002. Electronic security: Risk mitigation in financial transactions — Public policy issues. The World Bank.
Goel, S., and H.A. Shawky. 2009. Estimating the market impact of security breach announcements on firm values. Information & Management 46 (7): 404–410.
Goldman, D. 2012, September 28. Major banks hit with biggest cyberattacks in history. CNN Business . Altanta.
Gommans, L., J. Vollbrecht, B.G.-D. Bruijn, and C.D. Laat. 2015. The service provider group framework a framework for arranging trust and power to facilitate authorization of network services. Future Generation Computer Systems 45: 176–192.
Goodman, S.E., and R. Ramer. 2007. Identify and mitigate the risks of global IT outsourcing. Journal of Global Information Technology Management 10 (4): 1–6.
Gopalakrishnan, R., and M. Mogato. 2016, May 19. Bangladesh Bank official’s computer was hacked to carry out $81 million heist: Diplomat. Reuters: Business News . Thomson Reuters.
Gordon, L.A., and M.P. Loeb. 2002a. The economics of information security investment. ACM Transactions on Information and Systems Security 5 (4): 438–457.
Gordon, L.A., and M.P. Loeb. 2002b. Return on information security investments, myths vs realities. Strategic Finance 84 (5): 26–31.
Gordon, L.A., M.P. Loeb, W. Lucyshyn, and T. Sohail. 2006. The impact of the Sarbanes-Oxley Act on the corporate disclosures of information security activities. Journal of Accounting and Public Policy 25 (5): 503–530.
Gracie, A. 2015. Cyber resilience: A financial stability perspective. Cyber defence and network security conference. London. https://www.bankofengland.co.uk/speech/2015/cyber-resilience-a-financial-stability-perspective .
Granåsen, M., and D. Andersson. 2016. Measuring team effectiveness in cyber-defense exercises: A cross-disciplinary case study. Cognition, Technology & Work 18 (1): 121–143.
Gupta, U.G., and A. Gupta. 2007. Outsourcing the is function: Is it necessary for your organization? Information Systems Management 9 (3): 44–47.
Gutu, L.M. 2014. The impact of Internet technology on the Romanian banks performance. In Proceedings of international academic conferences (No. 0702397). International Institute of Social and Economic Sciences.
Hall, C., R.J. Anderson, R. Clayton, E. Ouzounis, and P. Trimintzios. 2013. Resilience of the internet interconnection ecosystem. Economics of Information Security and Privacy III: 119–148.
Heeks, R. 2002. Information systems and developing countries: Failure, success, and local improvisations. The Information Society 18: 101–112.
Hemphill, T.A., and P. Longstreet. 2016. Financial data breaches in the U.S. retail economy: Restoring. Technology in Society 44: 30–38.
Herath, T., and H.R. Rao. 2009. Encouraging information security behaviors in organizations: Role of penalties, pressures and perceived effectiveness. Decision Support System 47 (02): 154–165.
HKMA. 2016. Enhanced competency framework on cybersecurity. Hong Kong: Hong Kong Monetary Authority. https://www.hkma.gov.hk/media/eng/doc/key-information/guidelines-and-circular/2016/20161219e1.pdf .
Ho, S.J., and S.K. Mallick. 2010. The impact of information technology on the banking industry. Journal of the Operational Research Society 61 (2): 211–221.
Holt, T.J., and E. Lampke. 2010. Exploring stolen data markets online: Products and market forces. Criminal Justice Studies 23 (1): 33–50.
Hon, W.K., and C. Millard. 2018. Banking in the cloud: Part 1—Banks’ use of cloud services. Computer Law & Security Review 34: 4–24.
Horne, R. 2014. The cyber threat to banking. PWC. https://www.bba.org.uk/wp-content/uploads/2014/06/BBAJ2110_Cyber_report_May_2014_WEB.pdf .
Hovav, A., and J. D’Arcy. 2004. The impact of virus attack announcements on the market value of firms. Information Systems Security 13 (3): 32–40.
Hsu, A.W.-H., H. Pourjalali, and Y.-J. Song. 2018. Fair value disclosures and crash risk. Journal of Contemporary Accounting & Economics 14 (3): 358–372.
Humayun, M., N. J. Mahmood Niazi, M. Alshayeb, and S. Mahmood. 2020. Cyber security threats and vulnerabilities: A systematic mapping study. Arabian Journal for Science and Engineering 1–19.
Hyytinen, A., and T. Takalo. 2002. Enhancing bank transparency: A re-assessment. Review of Finance 6 (3): 429–445.
IDSA. 2012. India’s cyber security challenge. New Delhi: Institute for Defence Studies and Analyses. https://idsa.in/system/files/book/book_indiacybersecurity.pdf .
IOSC. 2016. Cyber security in securities markets — An international perspective. International Organization of Securities Commissions. https://www.iosco.org/library/pubdocs/pdf/IOSCOPD528.pdf .
Ismail, N. 2018. The financial impact of data breaches is just the beginning . www.information-age.com . https://www.information-age.com/data-breaches-financial-impact-123470254/ .
ITU. 2012a. Cyberwellness profile hong kong. Hong Kong: ITU. https://www.itu.int/dms_pub/itu-d/opb/str/D-STR-SECU-2015-PDF-E.pdf .
ITU. 2012b. Cyberwellness profile poland. Poland: ITU. https://www.itu.int/en/ITU-D/Cybersecurity/Documents/Country_Profiles/Poland.pdf .
ITU. 2013. Cyberwellness profile Hungary. Hungary: ITU. https://www.itu.int/en/ITU-D/Cybersecurity/Documents/Country_Profiles/Hungary.pdf .
ITU Slovakia. 2012. Cyberwellness profile slovakia. ITU. https://www.itu.int/en/ITU-D/Cybersecurity/Documents/Country_Profiles/Slovakia.pdf .
Javaid, M.A. 2013. Cyber security: Challenges ahead. Available SSRN 2339594 . http://nexusacademicpublishers.com/uploads/portals/Cyber_Security_Challenged_Ahead.pdf .
Jayawardhena, C., and P. Foley. 2000. Changes in the banking sector—The case of Internet banking in the UK. Internet Research 10 (1): 19–31.
Johnson, K.N. 2015. Managing cyber risk. Georgia Law Review 50 (2): 548–592.
Jordan, J.S., J. Peek, and E.S. Rosengren. 2000. The market reaction to the disclosure of supervisory actions: Implications for bank transparency. Journal of Financial Intermediation 9 (3): 298–319.
Juma’h, A.H., and Y. Alnsour. 2020. The effect of data breaches on company performance. International Journal of Accounting & Information Management 28 (2): 275–301.
Kamiya, S., KangJun-Koo, K. Jungmin, A. Milidonis, and R. M. Stulz. 2020. Risk management, firm reputation, and the impact of successful cyberattacks on target firms. Journal of Financial Economics
Kark, K., A. Shaikh, and C. Brown. 2017, November 28. Technology budgets: From value preservation to value creation. Deloitte Insight. London.
Kauffman, R.J., J. Liu, and D. Ma. 2015. Technology investment decision-making under uncertainty. Information Technology and Management 16 (2): 153–172.
Kayworth, T., and D. Whitten. 2012. Effective information security requires a balance of social and technology factors. MIS Quarterly Executive 9(3).
Kesswani, N., and S. Kumar. 2015. Maintaining cyber security: Implications, cost and returns. Proceedings of the 2015 ACM SIGMIS Conference on Computers and People Research. New York: Association for Computer Machinery, 161–164.
Khoury, S., and E. Rolland. 2006. Conceptual model for explaining the IT investment paradox in the banking sector. International Journal of Technology, Policy and Management 6 (3): 309–326.
King, R.G., and R. Levine. 1993. Finance, entrepreneurship, and growth. Journal of Monetary Economics 3 (32): 513–542.
Ko, M., and C. Dorantes. 2006. The impact of information security breaches on financial performance of the breached firms: An empirical investigation. Journal of Information Technology Management 17 (2): 13–22.
Koette, M., and T. Poghosyan. 2009. The identification of technology regimes in banking: Implications for the market power-fragility nexus. Journal of Banking & Finance 33 (8): 1413–1422.
Kopp, E., L. Kaffenberger, and C. Wilson. 2017. Cyber risk, market failures, and financial stability, working paper. International Monetary Fund (WP/17/185).
Kox, H. L. 2013. Cybersecurity in the perspective of Internet traffic growth. Working paper. CPB Netherlands Bureau for Economic Policy Analysis. https://mpra.ub.uni-muenchen.de/47994/ .
Kröger, W. 2008. Critical infrastructures at risk: A need for a new conceptual approach and extended analytical tools. Reliability Engineering & System Safety 93 (12): 1781–1787.
Kunreuther, H., and G. Heal. 2003. Interdependent security. Journal of Risk and Uncertainty 26 (2–3): 231–249.
Kwast, M.L., and J.T. Rose. 1982. Pricing, operating efficiency, and profitability among large commercial banks. Journal of Banking & Finance 6 (2): 233–254.
Lagazio, M., N. Sherif, and A.M. Cushman. 2014. A multi-level approach to understanding the impact of cyber crime on the financial sector. Computers & Security 45: 58–74.
Lages, L.F. 2016. VCW-value creation wheel: Innovation, technology, business, and society. Journal of Business Research 69: 4849–4855.
Langton, J. 2018, June 4. Data breaches credit negative for BMO and CIBC: Moody’s . www.investmentexecutive.com : https://www.investmentexecutive.com/news/industry-news/data-breaches-credit-negative-for-bmo-and-cibc-moodys/ .
Lee, D., and S. Mithas. 2014. IT investments, alignment and firm performance: Evidence from an emerging economy. ICIS Conference Proceedings. Association for Information Systems. https://aisel.aisnet.org/icis2014/proceedings/ISStrategy/29/ .
Lever, K.E., and K. Kifayat. 2020. Identifying and mitigating security risks for secure and robust NGI networks. Sustainable Cities and Society 59: 102098.
Levine, R.G. 1993. Finance and growth: Schumpeter might be right. The Quarterly Journal of Economics 108 (3): 717–737.
Lewis, J.A. 2002. Assessing the risks of cyber terrorism, cyber war and other cyber threats . Washington, DC: Center for Strategic & International Studies.
Lewis, J., and S. Baker. 2013. The economic impact of cybercrime and cyber espionage. McAfee.
Li, H., W.G. No, and T. Wang. 2018. SEC’s cybersecurity disclosure guidance and disclosed cybersecurity risk factors. International Journal of Accounting Information Systems 30: 40–55.
Linsley, P.M., and P.J. Shrives. 2005. Transparency and the disclosure of risk information in the banking sector. Journal of Financial Regulation and Compliance 13 (3): 205–214.
Longstaff, T., C. Chittister, R. Pethia, and Y. Haimes. 2020. Are we forgetting the risks of information technology. Computer 33 (12): 43–51.
Low, P. 2017. Insuring against cyber-attacks. Computer Fraud & Security 2017: 18–20.
Macaulay, T. 2018. Critical infrastructure: Understanding its component parts, vulnerabilities, operating risks, and interdependencies , 1st ed. Boca Raton: Taylor and Francis Group.
Mandeville, T. 1998. An information economics perspective on innovation. International Journal of Social Economics 25 (2/3/4): 357–364.
Mayahi, A., and I. Humaid. 2016. Development of a comprehensive information security system for UAE e-Government. PhD thesis, Prifysgol Bangor University
McConnell, Patrick, and Keith Blacker. 2013. Systemic operational risk: Does it exist and if so, how do we regulate it? The Journal of Operational Risk 8 (1): 59–99.
McGraw, G. 2013. Cyber war is inevitable (unless we build security in). Journal of Strategic Studies 36 (1): 109–119. https://doi.org/10.1080/01402390.2012.742013 .
MCI. 2017. Public consultation paper on the draft cybersecurity bill. The Ministry of Communications and Information (MCI) and the Cyber Security Agency of Singapore. https://www.csa.gov.sg/~/media/csa/cybersecurity_bill/consult_document.pdf .
Ministry of Digital Affairs. 2017. National framework of cybersecurity policy of Republic of Poland for 2017-22 . Warsaw: Government of Poland.
Mohammed, A.-M., B. Idris, G. Saridakis, and V. Benson. 2020. Chapter 8—Information and communication technologies: A curse or blessing for SMEs? . New York: Academic Press.
Moore, T. 2010. The economics of cybersecurity: Principles and policy options. International Journal of Critical Infrastructure Protection 3 (3–4): 103–117.
Moore, T., S. Dynes, and F. Chang. 2015. Identifying how firms manage cybersecurity investment . Dallas: Southern Methodist University.
Morton, M., J. Werner, P. Kintis, K. Snow, M. Antonakakis, M. Polychronakis, and F. Monrose. 2018. Security risks in asynchronous web servers: When performance optimizations amplify the impact of data-oriented attacks. IEEE European Symposium on Security and Privacy , pp. 167–182.
Moumen, N., H.B. Othman, and K. Hussainey. 2015. The value relevance of risk disclosure in annual reports: Evidence from MENA emerging markets. Research in International Business and Finance 34: 177–204.
Mugarura, N., and E. Ssali. 2020. Intricacies of anti-money laundering and cyber-crimes regulation in a fluid global system. Journal of Money Laundering Control .
Mukhopadhyay, A., D.S. Samir Chatterjee, A. Mahanti, and A.S. Sadhukhan. 2013. Cyber-risk decision models: To insure IT or not? Decision Support Systems 56: 11–26.
NCG. 2016. 4 important cybersecurity focus areas for banks. Portland: Northcross Group. http://www.northcrossgroup.com .
NCSB. 2014. National cybersecurity strategy. Dhaka: ICT Ministry. https://sherloc.unodc.org/cld/lessons-learned/bgd/the_national_cybersecurity_strategy_of_bangladesh.html ?.
NCSC. 2018. The cyber threat to UK business. UK: The National Cyber Security Centre. https://www.ncsc.gov.uk/home .
Ngonzi, T.T. 2016. Theorizing ICT-based social innovation on development in the context of developing countries of Africa . Captown: University of Cape Town.
Ni, J., X. Lin, and X. Shen. 2019. Towards edge-assisted internet of things: From security and efficiency perspectives. IEEE Network 33 (2): 50–57.
OECD. 2015. Digital security risk management for economic and social prosperity: OECD recommendation and companion document . Paris: OECD Publishing.
OFR. 2017. Cybersecurity and financial stability: Risks and resilience. Office of Financial Research. https://www.financialresearch.gov/viewpoint-papers/files/OFRvp_17-01_Cybersecurity.pdf .
Page, J., M. Kaur, and E. Waters. 2017. Directors’ liability survey: Cyber attacks and data loss—A growing concern. Journal of Data Protection & Privacy 1 (2): 173–182.
Park, I., J. Lee, H.R. Rao, and S.J. Upadhyaya. 2006. Part 2: Emerging issues for secure knowledge management-results of a Delphi study. IEEE Transactions on Systems, Man, and Cybernetics-Part A: Systems and Humans 36 (3): 421–428.
Patterson, D., A. Brown, P. Broadwell, G. Candea, and J.C. Mike Chen. 2002. Recovery oriented computing (ROC): Motivation, definition, techniques, and case studies. UC Berkeley Computer Science.
Paul, J.A., and X. Wang. 2019. Socially optimal IT investment for cybersecurity. Decision Support Systems 122: 113069.
Pavlou, P.A., H. Liang, and Y. Xue. 2007. Understanding and mitigating uncertainty in online exchange relationships: A PrincipalAgent perspective. MIS Quarterly, 105–136.
Peeters, G. 2017. Strengthening the digital Achilles heel of the European Union: Make use of ethical hackers to find vulnerabilities in information systems? Master thesis .
Peng, C., M. Xu, S. Xu, and T. Hu. 2017. Modeling and predicting extreme cyber attack rates via marked point processes. Jornal of Applied Statistics 44 (14): 2534–2563.
Pirounias, S., D. Mermigas, and C. Patsakis. 2014. The relation between information security events and firm market value, empirical evidence on recent disclosures: An extension of the GLZ study. Journal of Information Security and Applications 19 (4–5): 257–271.
Power, M. 2005. The invention of operational risk. Review of International Political Economy 12 (4): 577–599.
PWC. 2014. Threats to the Financial Services sector. PWC. https://www.pwc.com/gx/en/financial-services/publications/assets/pwc-gecs-2014-threats-to-the-financial-services-sector.pdf .
PWC. 2015. Information security breaches survey. London: The UK Government. https://www.pwc.co.uk/assets/pdf/2015-isbs-technical-report-blue-digital.pdf .
Quinn, J.B., and M.N. Baily. 1994. Information technology: Increasing productivity in services. Academy of Management Perspectives 8 (3): 28–48.
Rackof, N., C. Wiseman, and W.A. Ullrich. 1985. Information systems for competitive advantage: implementation of a planning process. MIS Quarterly, 285-294.
Ralston, P., J. Graham, and J. Hieb. 2007. Cyber security risk assessment for SCADA and DCS networks. ISA Transactions 46: 583–594.
ReedSmith. 2017. China cybersecurity law. ReedSmith. https://www.reedsmith.com/en/perspectives/2017/01/chinas-cybersecurity-law .
Reuters. 2018, June 1. Bank of Chile trading down after hackers rob millions in cyberattack. Santiago. https://www.reuters.com/article/us-chile-banks-cyberattack/bank-of-chile-trading-down-after-hackers-rob-millions-in-cyberattack-idUSKBN1J72FC .
Rezek, T., T. Szatkowski, J. Świątkowska, J. Vyskoč, and M. Ziare. 2012. V4 cooperation in ensuring cyber security—Analysis and recommendations . Poland: The Kosciuszko Institute.
Ring, T. 2014. Threat intelligence: Why people don’t share. Computer Fraud & Security. 3: 5–9.
Risk.net. 2016, Jan 20. Top 10 operational risks for 2016 . www.risk.net . https://www.risk.net/risk-management/2441306/top-10-operational-risks-for-2016#risk1 .
Roth, A.V., and W.E. Jackson-III. 1995. Strategic determinants of service quality and performance: Evidence from the banking industry. Management Science 41 (11): 1720–1733.
Rubens, P. 2018, June 26. How to prevent DDoS attacks: 6 tips to keep your website safe. Nashville: eSecurity Planet, TechnologyAdvice. https://www.esecurityplanet.com/network-security/how-to-prevent-ddos-attacks.html .
Schwartz, M.J. 2013, March 21. South Korea Bank hacks: 7 key facts. Dark Reading. https://www.darkreading.com .
SCM. 2016. Guidelines on management of cyber risk. Securities Commission Malaysia. https://www.sc.com.my/api/documentms/download.ashx?id=9aaddb2e-aa13-409a-a47f-8d0124afd229 .
Scott, S.V., J.V. Reenen, and M. Zachariadis. 2017. The long-term effect of digital innovation on bank performance: An empirical study of SWIFT adoption in financial services. Research Policy 46 (5): 984–1004.
SecurityScoreboard. 2016. Financial industry cybersecurity report . New York: SecurityScoreboard.
Shackelford, S.J. 2012. Should your firm invest in cyber risk insurance? Business Horizons 55: 349–356.
Sharma, A., and P. Tandekar. 2018. Cyber security and business growth. IGI Global, 1208–1221.
Siegel, C.A., T.R. Sagalow, and P. Serritella. 2002. Cyber-risk management: Technical and insurance controls for enterprise-level security. Information Systems Security 11 (4): 33–49.
Skinner, D.J., and R.G. Sloan. 2002. Earnings surprises, growth expectations, and stock returns or don’t let an earnings torpedo sink your portfolio. Review of Accounting Studies 7: 289–312.
Smedinghoff, T.J. 2012. Solving the legal challenges of trustworthy online identity. Computer Law & Security Review 28: 532–541.
Solms, B.V. 2006. Information security—The fourth wave. Computers & Security 25 (3): 165–168.
Sommer, P., and I. Brown. 2011. “Future global shocks” reducing systemic cybersecurity risk . OECD/IFP: OECD.
Soomro, Z.A., M.H. Shah, and J. Ahmed. 2016. Information security management needs more holistic approach: A literature review. International Journal of Information Management 36 (2): 215–225.
Srinidhi, B., J. Yan, and G.K. Tayi. 2015. Allocation of resources to cyber-security: The effect of misalignment of interest between managers and investors. Decision Support Systems 75: 49–62.
State Bank of Pakistan. 2012. Guidelines on information technology security. The State Bank of Pakistan. http://www.sbp.org.pk/bsd/2004/Guidelines_on_IT_Security.pdf .
Stoneburner, G., A. Goguen, and A. Feringa. 2002. Risk management guide for information technology systems. Recommendations of the National Institute of Standards and Technology . Singapore: National Institute of Standards and Technology.
Teece, D.J. 2018. Profiting from innovation in the digital economy: Enabling technologies, standards, and licensing models in the wireless world. Research Policy 47 (8): 1367–1387.
Tendulkar, R. 2013. Cyber-crime, securities markets and systemic risk. CFA Digest 43 (4): 35–43.
Toivanen, H. 2015. Case study of why information security investment fail?. Master’s Thesis , 76. Jyväskylä: University of Jyväskylä.
Trautman, L.J., and K. Altenbaumer-Price. 2010. The board’s responsibility for information technology governance. John Marshall Journal of Computer and Information Law 28: 313.
Vagle, J. 2020. Cybersecurity and moral hazard. Stanford Technology Law Review 23: 71.
Veijalainen, J., V. Terziyan, and H. Tirri. 2006. Transaction management for m-commerce at a mobile terminal. Electronic Commerce Research and Applications 5: 229–245.
Watkins, B. 2014. The impact of cyber attacks on the private sector. Briefing Paper, Association for International Affair , 12.
Watters, P.A., S. McCombie, R. Layton, and J. Pieprzyk. 2012. Characterising and predicting cyber attacks using the cyber attacker model profile. Journal of Money Laundering Control 15 (4): 430–441.
Willison, R., and M. Warkentin. 2013. Beyond deterrence: An expanded view of employee computer abuse. MIS Quarterly 37 (1): 1–20.
Wright, D., S. Gutwirth, M. Friedewald, P.D. Hert, M. Langheinrich, and A. Moscibroda. 2009. Privacy, trust and policy-making: Challenges and responses. Computer Law & Security Review 25: 69–83.
Yang, S.J., S. Byers, J. Holsopple, B. Argauer, and D. Fava. 2008. Intrusion activity projection for cyber situational awareness. 2008 IEEE international conference on intelligence and security informatics , 167–172. Taiwan: IEEE.
Zephirin, M.G. 1994. Switching costs in the deposit market. The Economic Journal 104 (423): 455–461.
Download references
Acknowledgements
This paper is the first output of Taylor’s University’s flagship research project # TUFR/2017/004/05. Md Hamid Uddin led this project over the last three years. He recently moved to the University of Southampton - Malaysia Campus yet engaged with the project until completion of research outputs and obligations under the funding contract. Md Hakim Ali worked as the research scholar while Mohammad Kabir Hassan is an external collaborator who has intellectual contribution in developing this manuscript. The first version of this paper was presented at the Annual Financial Liquidity Conference 2018, Budapest, Hungary. We acknowledge the valuable suggestions received from Igor Lončarski (University of Ljubljana) and Seema Narayan (RMIT University Australia). We thank Mohammed Sawkat Hossain, who helped us at the beginning of literature searching. We appreciate the contribution of David Asirvatham Nor Shaipah Abdul Wahab and Vinitha Guptan at Taylor’s University and Sabur Mollah at Sheffield University in launching this project three years ago. We are grateful to David Asirvatham (leader of Data Analytics, Modeling and Visualization research program) and Centre for Research Management at Taylor’s University for extending full support in implementing the project.
Author information
Authors and affiliations.
University of Southampton, Malaysia Campus, No. 3, Persiaran Canselor 1, Kota Ilmu Educity, Iskandar, 79200, Nusajaya, Johor, Malaysia
Md. Hamid Uddin
Faculty of Business and Law, Taylor’s University, No 1, Jalan Taylor’s, 47500, Subang Jaya, Selangor, Malaysia
Md. Hamid Uddin & Md. Hakim Ali
Department of Economics and Finance, University of New Orleans, 438 Kirschman Hall, 2000 Lakeshore Drive, New Orleans, LA, 70148, USA
Mohammad Kabir Hassan
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Md. Hamid Uddin .
Ethics declarations
Conflict of interest.
On behalf of all authors, the corresponding author states that there is no conflict of interest.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This paper is the output of Taylor's University's flagship research project # TUFR/2017/004/05. Md Hamid Uddin led this project over the last three years. He recently moved to the University of Southampton – Malaysia Campus while maintaining engagement for this project until all outputs are published. Md Hakim Ali worked as the research scholar while M. Kabir Hassan is an external collaborator who has intellectual contribution in developing this manuscript. The first version of this paper was presented at the Annual Financial Liquidity Conference 2018, Budapest, Hungary. We acknowledge the valuable suggestions received from Igor Lončarski (University of Ljubljana) and Seema Narayan (RMIT University Australia). We thank Mohammed Sawkat Hossain, who helped us at the beginning of literature searching. We appreciate the contribution of David Asirvatham Nor Shaipah Abdul Wahab and Vinitha Guptan at Taylor's University and Sabur Mollah at Sheffield University in launching this project three years ago. We are grateful to David Asirvatham (leader of Data Analytics, Modeling & Visualization research program) and Centre for Research Management at Taylor's University for extending full support in implementing the project. All comments should be sent to Md Hamid Uddin at [email protected].
Appendix 1: literatures related to cyber security and operational costs
Appendix 2: literatures related to cybersecurity and institutional performance, appendix 3: literatures related to cybersecurity and operational risk, appendix 4: literatures related to cybersecurity disclosure and governance, appendix 5: cybersecurity guidelines in the global perspective, rights and permissions.
Reprints and permissions
About this article
Uddin, M.H., Ali, M.H. & Hassan, M.K. Cybersecurity hazards and financial system vulnerability: a synthesis of literature. Risk Manag 22 , 239–309 (2020). https://doi.org/10.1057/s41283-020-00063-2
Download citation
Published : 18 August 2020
Issue Date : December 2020
DOI : https://doi.org/10.1057/s41283-020-00063-2
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cybersecurity
- Banking stability
- Institutional performance
- Bank operational risks
- Find a journal
- Publish with us
- Track your research
Type above and press enter or press close to cancel.
Cybersecurity in digital banking: everything you need to know.
We live in an increasingly online world, and with the rise in digital banking, there’s also been a surge in attacks by cybercriminals. Financial institutions must thus invest heavily in their cybersecurity .
A cyberattack can have devastating consequences, and not just in terms of the data stolen. A bank can also lose credibility after a data breach. This is due to clients questioning their ability to keep their information and assets safe.
Now, more than ever, cybersecurity in digital banking is vital, as is having an awareness of what cyberattacks are and how to protect against them. So, let’s delve into the world of cybersecurity and examine everything you need to know about how cybercriminals operate.
Cybersecurity stats indicate a rise of data breaches and hacking. Click here to learn more!
What is Cybersecurity?
In today’s society, it’s difficult to imagine functioning without smartphones and computers, least of all without the internet. However, these devices are often filled with our private data and contain information on all of our accounts.
Our whole lives are thus contained in devices that fit in the palms of our hands. This is why taking the right steps to maintain privacy and prevent cybercriminals from gaining access to information is vital. If we don’t, the repercussions can be severe.
Enter cybersecurity. Cybersecurity revolves around protecting electronic systems and data. It acts as an umbrella term for a huge range of technologies and actions that shield information from the unwanted eyes of cybercriminals.
Enterprise digital transformation can help global corporations make that change. However, online spaces like digital banking also need extra cybersecurity measures in place to protect sensitive information.
Why Does the Digital Banking Sphere Need Cybersecurity?
Banks hold huge amounts of sensitive data belonging to clients. They also have the money to pay a ransom should data be leaked or stolen by cybercriminals. As they typically prioritize maintaining a good reputation, in many cases, agreeing to a ransom is seen as preferable to customer data being compromised.
That’s because data breaches can lead to several problems down the line, such as fraud against customers. Moreover, recovering data costs banks considerable sums in and of itself. This is why cybersecurity is so important.
Protecting client assets is the most fundamental purpose of cybersecurity in digital banking, especially in our increasingly cashless society, where more and more payments and transactions happen online.
If you own a credit or debit card, you’re at risk of cyberattacks. Therefore, your bank needs to ensure you’re protected by its cybersecurity practices.
What do Digital Banking Cyberattacks Look Like?
Banks are under constant threat from cyberattacks. These can take on several different forms, but all of them put sensitive data at risk.
Statistics show that in 2021, cybercrime was a top three most reported economic crime.
Let’s take a look at a few of the most common cyber-attack techniques.
Phishing is a form of cyberattack that attempts to gain sensitive information from victims. This is often banking details like their credit card digits, which cybercriminals then use to steal money.
This information is frequently obtained via email or phone call, although it can be discovered in many different ways. Online banking phishing scams are constantly evolving to trick customers.
Phishing, when done successfully, can look incredibly professional. This enables cybercriminals to fool a bank’s clients into thinking they’re being contacted by their actual bank. This persuades them to give away sensitive information.
This can have severe consequences, with cybercriminals convincing people to share details that can result in their money being taken or even their identity being stolen.
One of the most common phishing techniques is to create a sense of urgency. The victim is informed that they must act fast to prevent any number of bad things from happening. This causes people to be less diligent and act before they have time to think through what they’re doing.
Unencrypted data
Another common cyber threat is unencrypted data. Hackers can access unencrypted data easily. This can then cause serious problems for banks that have to deal with a data breach rather than preventing it from happening in the first place.
Data breaches are bad news for digital banks. They result in large amounts of money being put into recovering information and/or paying ransoms. Not to mention the loss of credibility that results from them.
Therefore, all digital banking data should be encrypted. This ensures that if data is stolen by a cybercriminal, it remains protected or at least harder to access. When data is properly encrypted – for example, by using an encryption algorithm like the advanced encryption standard – it becomes inaccessible even after a breach.
Third-party services
A bank might have excellent cybersecurity measures in place, but that doesn’t mean the vendors they collaborate with do.
Many banks use third-party services because these companies help them serve their customers more efficiently. However, banks can suffer badly if they partner with third-party vendors who have poor cybersecurity.
Cybercriminals often target these weaker, less protected third-party collaborators, causing damage to the bank as well.
For this reason, banks must select their partners with extreme care and caution. For example, by choosing the right enterprise eCommerce platforms, much of the danger can be averted.
The same is true if a bank is looking for the best personalization websites to improve the customer experience without sacrificing their security in the process.
Spoofing is a cyber threat that involves impersonating a bank’s website using a website similar to the original. This ‘spoof’ platform functions exactly like the legitimate one, tricking clients into entering their login details, which are then stolen and used by cybercriminals.
Here, users of the actual website are targeted, with URLs created that are similar to that of the real site. This is a popular cyberattack technique and one that has been and continues to be very dangerous for banks and their clients.
Strong cybersecurity, such as multi-factor authentication, can help to combat this. This creates a more secure system whereby your bank can ask for specific information that only the account holder will know during login. Such an approach ensures cybercriminals with stolen information can’t access your bank details in your place.
Why is this a Danger Now More than Ever?
As a result of COVID-19, far more people are opting to use digital banking and choosing to access their financial information online. This poses many of the same issues as hybrid working, with lots of companies introducing a bring your own device policy, for example.
Both offer greater flexibility and convenience than traditional approaches but also present increased security risks. Growing rates of cybercrime in turn propel demand for investment in cybersecurity.
Digitization, on the whole, has been dramatically fast-tracked by the pandemic. The rise in the adoption of certain technologies means, for instance, that companies are increasingly having to track essential SaaS metrics.
It’s no longer a question of merely preventing cyberattacks. This has become nearly impossible, especially for banks and other financial institutions. It’s about being prepared for when a cyberattack does happen and having a response already planned out.
A great way to do this, for instance, is by implementing a cloud-based contact center solution to make client reporting easier.
Banks must keep continually deploying new cybersecurity defenses to counteract the ever-evolving world of cybercrime and the rapidly developing threats they face.
How Do Banks Protect Themselves from Cyberattacks?
Banks typically have several tools in place to help them deal with cyberattacks. Below are three of the main methods they employ to protect their digital spaces from criminal actors.
Consumer awareness
One of the core ways criminals target banks is through their customers. They prey on the naivete and ignorance of those who don’t understand the dangers existing in the digital space and who they can trick into disclosing important information.
Bank clients need to be informed of what cyberattacks look like to prevent these scams from proving successful, which is why there’s lots of investment in educating people. This includes teaching them the dangers of revealing their credentials and how to respond if they suspect an attempted fraud is taking place.
Acting quickly is crucial to preventing damage.
The right applications
Banks also have a range of anti-malware and anti-virus applications on all their digital platforms.
Firewalls are a good start, but they won’t necessarily stop cyberattacks. If banks don’t employ the right applications, they can’t ensure their digital spaces will stay safe.
The right software can play a key role in preventing potentially damaging attacks from negatively impacting a bank’s digital system. Therefore, there’s usually heavy investment in various specialist cybersecurity measures.
A solid recovery plan
In this increasingly digitized world, cyberattacks are becoming nearly impossible to avoid. Therefore, banks need to have a good plan in place to deal with cybercrimes in the event they can’t be stopped. This minimizes how much data is lost and reduces disruption to online services.
A disaster recovery plan will ensure regular encrypted backups of data are stored in a secure cloud location. Digital banking systems will also be designed so they’re able to continue functioning with a reduced system in the event of a main system failure.
Having a plan ready in case of a cyberattack is a great way to minimize losses and limit any damage.
The right Managed Security Service provider should be a true partner. Learn more here!
The Takeaway
Cybersecurity is key to protecting data and preventing fraud from taking place in digital banking spaces. It’s no longer an option for online entities but a necessity.
Today, this is a priority for all those operating in the industry, as evidenced by the ever-increasing investment in solid security plans that protect both banks and their customers.
Author: Jessica Day is the Senior Director for Marketing Strategy at Dialpad , a modern business communications platform that takes every kind of conversation to the next level—turning conversations into opportunities. Jessica is an expert in collaborating with multifunctional teams to execute and optimize marketing efforts, for both company and client campaigns. Jessica has written for domains such as Plutio and ehotelier. Here is her LinkedIn .
- Cyber Security
- Digital Banking

Join over 15,000 companies
Get Our Updates Sent Directly To Your Inbox.
Join our mailing list to receive monthly updates on the latest at Stefanini.

Build Your IT Support Offering Quickly
Our eBook “LiteSD – Choose Endlessly Scalable Success” reveals how to integrate LiteSD platform into your organization.
Ask SophieX
Cyber security analysis of internet banking in emerging countries: User and bank perspectives
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.

- TRP for UPSC Personality Test
- Interview Mentorship Programme – 2023
- Daily News & Analysis
- Daily Current Affairs Quiz
- Baba’s Explainer
- Dedicated TLP Portal
- 60 Day – Rapid Revision (RaRe) Series – 2024
- English Magazines
- Hindi Magazines
- Yojana & Kurukshetra Gist
- PT20 – Prelims Test Series
- Gurukul Foundation
- Gurukul Advanced – Launching Soon
- Prelims Exclusive Programme (PEP)
- Prelims Test Series (AIPTS)
- Integrated Learning Program (ILP) – 2025
- Connect to Conquer(C2C) 2024
- TLP Plus – 2024
- TLP Connect – 2024
- Public Administration FC – 2024
- Anthropology Foundation Course
- Anthropology Optional Test Series
- Sociology Foundation Course – 2024
- Sociology Test Series – 2023
- Geography Optional Foundation Course
- Geography Optional Test Series – Coming Soon!
- PSIR Foundation Course
- PSIR Test Series – Coming Soon
- ‘Mission ಸಂಕಲ್ಪ’ – Prelims Crash Course
- CTI (COMMERCIAL TAX INSPECTOR) Test Series & Video Classes
- Monthly Magazine
Cybersecurity & Banks
- September 24, 2021
UPSC Articles

SCIENCE & TECH/ GOVERNANCE
- GS-3: Cyber Security and its challenges
- GS-3: Government policies and interventions for development in various sectors and issues arising out of their design and implementation .
Cybersecurity & Banks
Context : With increasing emphasis being laid on digitisation for financial institutions, there has been a monumental increase in cybersecurity threats as well.
- Therefore, the need for stringent cybersecurity measures for digital banking is now more pressing than ever.
The threats
- Malware: Digital transactions are generally conducted on end-to-end user devices such as mobiles, computers, etc. If devices being used for access are infected with malware, then they end up posing a serious security risk to the bank’s cybersecurity network, whenever they connect with it.
- Third-party services: Numerous banks employ the services of third-party vendors, to be able to serve their customers in a better manner. However, if the vendors do not take active cybersecurity measures, then the bank can end up facing the repercussions.
- Spoofing: Cybercriminals try impersonating a bank’s URL with a website that is quite similar to the original one and has similar functions as well. Whenever a user enters his or her login to tensions into the fake website, the credentials are then stolen by the criminals.
- Phishing: Attempting to obtain sensitive information such as credit card details, etc. for fraudulent activities, by disguising oneself as an authentic, trustworthy entity via electronic communication
- Unencrypted data: It is imperative that whatever data that is stored on the computers, or servers of banks, needs to be encrypted fully, which ensures that even in the event of data being stolen, it cannot be used by cybercriminals.
The challenges
- Lack of awareness: There aren’t a lot of firms that end up investing in training and enhancing overall awareness related to cybersecurity amongst people.
- Increased use of social media: Many a time, customers who are not well-versed with cybersecurity measures, end up putting the data for anyone to see.
- Inadequate budget and lack of management: Cybersecurity is often neglected in budget allocations, where the firm does not realise the monumental impact that these threats can have.
The solutions
- Integrated security: In a sector as regulated as BFSI, integrated security is the future.
- Machine learning and big data analytics: These are essential for leveraging cyber resilience.
- Updated antivirus and anti-malware applications offer the best protection from attacks that can be potentially disastrous
- Endpoint protection: Financial institutions need to invest in technologies that can enhance the endpoint protection.
Connecting the dots:
- India needs a Cybersecurity Strategy
- Blockchain Technology: Advantages & Challenges
For a dedicated peer group, Motivation & Quick updates, Join our official telegram channel – https://t.me/IASbabaOfficialAccount
Subscribe to our YouTube Channel HERE to watch Explainer Videos, Strategy Sessions, Toppers Talks & many more…

Related Posts :
Federal reserve’s stance and india, digital india – financial inclusion.

- DAILY CURRENT AFFAIRS IAS | UPSC Prelims and Mains Exam –24th May 2024
- UPSC Quiz – 2024 : IASbaba’s Daily Current Affairs Quiz 24th May 2024
- DAILY CURRENT AFFAIRS IAS | UPSC Prelims and Mains Exam –23rd May 2024
- UPSC Quiz – 2024 : IASbaba’s Daily Current Affairs Quiz 23rd May 2024
- DAILY CURRENT AFFAIRS IAS | UPSC Prelims and Mains Exam –22nd May 2024
- UPSC Quiz – 2024 : IASbaba’s Daily Current Affairs Quiz 22nd May 2024
- DAILY CURRENT AFFAIRS IAS | UPSC Prelims and Mains Exam –21st May 2024
- [MOCK TEST] Sameeksha 2024 – IASbaba’s All India Mock Test for UPSC Prelims 2024 on 2nd June (SUNDAY). Available in Offline & Online Mode (English & हिन्दी)
- UPSC Quiz – 2024 : IASbaba’s Daily Current Affairs Quiz 21st May 2024
- DAILY CURRENT AFFAIRS IAS | UPSC Prelims and Mains Exam –20th May 2024
Don’t lose out on any important Post and Update. Learn everyday with Experts!!
Email Address
Search now.....
Sign up to receive regular updates.
Sign Up Now !
Cyber Security Essay for Students and Children
Cyber security essay.
Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today’s world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software. This software protects the data. Cybersecurity is important because not only it helps to secure information but also our system from virus attack. After the U.S.A. and China, India has the highest number of internet users.

Cyber Threats
It can be further classified into 2 types. Cybercrime – against individuals, corporates, etc.and Cyberwarfare – against a state.
Cyber Crime
Use of cyberspace, i.e. computer, internet, cellphone, other technical devices, etc., to commit a crime by an individual or organized group is called cyber-crime. Cyber attackers use numerous software and codes in cyberspace to commit cybercrime. They exploit the weaknesses in the software and hardware design through the use of malware. Hacking is a common way of piercing the defenses of protected computer systems and interfering with their functioning. Identity theft is also common.
Cybercrimes may occur directly i.e, targeting the computers directly by spreading computer viruses. Other forms include DoS attack. It is an attempt to make a machine or network resource unavailable to its intended users. It suspends services of a host connected to the internet which may be temporary or permanent.
Malware is a software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It usually appears in the form of code, scripts, active content, and other software. ‘Malware’ refers to a variety of forms of hostile or intrusive software, for example, Trojan Horses, rootkits, worms, adware, etc.
Another way of committing cybercrime is independent of the Computer Network or Device. It includes Economic frauds. It is done to destabilize the economy of a country, attack on banking security and transaction system, extract money through fraud, acquisition of credit/debit card data, financial theft, etc.
Hinder the operations of a website or service through data alteration, data destruction. Others include using obscene content to humiliate girls and harm their reputation, Spreading pornography, threatening e-mail, assuming a fake identity, virtual impersonation. Nowadays misuse of social media in creating intolerance, instigating communal violence and inciting riots is happening a lot.
Get the huge list of more than 500 Essay Topics and Ideas
Cyber Warfare
Snowden revelations have shown that Cyberspace could become the theatre of warfare in the 21st century. Future wars will not be like traditional wars which are fought on land, water or air. when any state initiates the use of internet-based invisible force as an instrument of state policy to fight against another nation, it is called cyberwar’.
It includes hacking of vital information, important webpages, strategic controls, and intelligence. In December 2014 the cyberattack a six-month-long cyberattack on the German parliament for which the Sofacy Group is suspected. Another example 2008 cyberattack on US Military computers. Since these cyber-attacks, the issue of cyber warfare has assumed urgency in the global media.
Inexpensive Cybersecurity Measures
- The simplest thing you can do to up your security and rest easy at night knowing your data is safe is to change your passwords.
- You should use a password manager tool like LastPass, Dashlane, or Sticky Password to keep track of everything for you. These applications help you to use unique, secure passwords for every site you need while also keeping track of all of them for you.
- An easy way for an attacker to gain access to your network is to use old credentials that have fallen by the wayside. Hence delete unused accounts.
- Enabling two-factor authentication to add some extra security to your logins. An extra layer of security that makes it harder for an attacker to get into your accounts.
- Keep your Softwares up to date.
Today due to high internet penetration, cybersecurity is one of the biggest need of the world as cybersecurity threats are very dangerous to the country’s security. Not only the government but also the citizens should spread awareness among the people to always update your system and network security settings and to the use proper anti-virus so that your system and network security settings stay virus and malware-free.
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App


Essay on Cyber Security
Students are often asked to write an essay on Cyber Security in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Cyber Security
Understanding cyber security.
Cyber security is about protecting computers, servers, mobile devices, electronic systems, networks, and data from digital attacks. It’s a critical area as our daily life, economic vitality, and national security rely on a stable, safe, and resilient cyberspace.
The Importance of Cyber Security
Cyber security is important because it helps protect sensitive information, like our personal data and banking details, from being stolen by hackers. It also safeguards against harmful viruses that can damage our devices.
Types of Cyber Threats
Common threats include malware, phishing, and ransomware. Malware is harmful software, phishing tricks people into revealing sensitive information, and ransomware locks users out until they pay a ransom.
Cyber Security Practices
Good practices include using strong passwords, regularly updating software, and not clicking on suspicious links. These can help protect us from cyber threats.
Also check:
- Paragraph on Cyber Security
- Speech on Cyber Security
250 Words Essay on Cyber Security
Introduction to cyber security.
Cybersecurity, a term that has gained paramount importance in the digital age, refers to the practice of protecting internet-connected systems, including hardware, software, and data, from digital attacks. Its significance is amplified by the increasing reliance on technology, which, while offering numerous benefits, also opens up new avenues for potential threats.
The digital landscape is a double-edged sword. On one hand, it facilitates communication, commerce, and innovation. On the other, it provides a fertile ground for cybercriminals to exploit vulnerabilities. Cybersecurity thus becomes crucial in safeguarding sensitive information, preventing unauthorized access, and maintaining system integrity.
Challenges in Cyber Security
However, the complexity and sophistication of cyber threats are growing at an alarming pace. Cybercriminals are using advanced techniques, such as AI and machine learning, to bypass traditional security measures. This necessitates the development of more robust, adaptive cybersecurity strategies.
The Future of Cyber Security
The future of cybersecurity lies in proactive defense mechanisms. By leveraging technologies like AI, predictive analytics, and blockchain, we can anticipate and neutralize threats before they cause harm. Furthermore, fostering a culture of cybersecurity awareness is equally important to empower individuals and organizations against cyber threats.
In conclusion, cybersecurity is a vital aspect of our digital existence. Its importance, challenges, and future prospects underline the need for continuous research, development, and education in this field. As the digital landscape evolves, so too must our approach to cybersecurity.
500 Words Essay on Cyber Security
Cyber security, also known as information technology security, focuses on protecting computers, networks, programs, and data from unintended or unauthorized access, damage, or destruction. In the digital era, the importance of cyber security is growing exponentially due to the increasing reliance on computer systems, the internet, and wireless network standards such as Bluetooth and Wi-Fi, and due to the growth of smart devices like smartphones and televisions.
The significance of robust cyber security measures cannot be understated. Cyber attacks can lead to serious consequences like identity theft, extortion attempts, deletion of important data, and even the disruption of normal business operations. In more extreme cases, they can lead to the compromise of national security. Hence, cyber security is not just a concern for businesses or governments, but it is a potential threat to all internet users.
Cyber threats can be broadly divided into three categories: Cybercrime includes single actors or groups targeting systems for financial gain or to cause disruption; Cyber-attack often involves politically motivated information gathering; and Cyberterrorism is intended to undermine electronic systems to cause panic or fear. Examples of these threats are malware, phishing, ransomware, and social engineering.
Cyber Security Measures
In response to these threats, several cyber security measures are being employed. These include firewalls, intrusion detection systems, anti-virus software, and encryption. Furthermore, organizations are increasingly recognizing the importance of information assurance, where data integrity, confidentiality, and availability are assured.
As technology evolves, so does the complexity and sophistication of cyber threats. Hence, the future of cyber security lies in constant evolution and adaptation. Artificial Intelligence (AI) and Machine Learning (ML) are becoming integral in combating cyber threats. These technologies can learn and adapt to new threats, making them more efficient than traditional security measures.
In conclusion, cyber security is a crucial aspect of our digital lives, and its importance will only increase with time. To ensure a secure digital environment, individuals, organizations, and governments must understand the potential threats and employ robust security measures to counter them. The future of cyber security is promising, with the advent of AI and ML, but the road ahead is challenging, requiring constant vigilance and adaptation to new threats.
That’s it! I hope the essay helped you.
If you’re looking for more, here are essays on other interesting topics:
- Essay on Cyber Bullying
- Essay on Customer Service
- Essay on Tourism in Kerala
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

- Work & Careers
- Life & Arts
Become an FT subscriber
Try unlimited access Only $1 for 4 weeks
Then $75 per month. Complete digital access to quality FT journalism on any device. Cancel anytime during your trial.
- Global news & analysis
- Expert opinion
- Special features
- FirstFT newsletter
- Videos & Podcasts
- Android & iOS app
- FT Edit app
- 10 gift articles per month
Explore more offers.
Standard digital.
- FT Digital Edition
Premium Digital
Print + premium digital, ft professional, weekend print + standard digital, weekend print + premium digital.
Essential digital access to quality FT journalism on any device. Pay a year upfront and save 20%.
- Global news & analysis
- Exclusive FT analysis
- FT App on Android & iOS
- FirstFT: the day's biggest stories
- 20+ curated newsletters
- Follow topics & set alerts with myFT
- FT Videos & Podcasts
- 20 monthly gift articles to share
- Lex: FT's flagship investment column
- 15+ Premium newsletters by leading experts
- FT Digital Edition: our digitised print edition
- Weekday Print Edition
- Videos & Podcasts
- Premium newsletters
- 10 additional gift articles per month
- FT Weekend Print delivery
- Everything in Standard Digital
- Everything in Premium Digital
Complete digital access to quality FT journalism with expert analysis from industry leaders. Pay a year upfront and save 20%.
- 10 monthly gift articles to share
- Everything in Print
- Make and share highlights
- FT Workspace
- Markets data widget
- Subscription Manager
- Workflow integrations
- Occasional readers go free
- Volume discount
Terms & Conditions apply
Explore our full range of subscriptions.
Why the ft.
See why over a million readers pay to read the Financial Times.
International Edition

North Korean Hackers Exploit Facebook Messenger in Targeted Malware Campaign

The North Korea-linked Kimsuky hacking group has been attributed to a new social engineering attack that employs fictitious Facebook accounts to targets via Messenger and ultimately delivers malware.
"The threat actor created a Facebook account with a fake identity disguised as a public official working in the North Korean human rights field," South Korean cybersecurity company Genians said in a report published last week.
The multi-stage attack campaign, which impersonates a legitimate individual, is designed to target activists in the North Korean human rights and anti-North Korea sectors, it noted.
The approach is a departure from the typical email-based spear-phishing strategy in that it leverages the social media platform to approach targets through Facebook Messenger and trick them into opening seemingly private documents written by the persona.

The decoy documents, hosted on OneDrive, is a Microsoft Common Console document that masquerades as an essay or content related to a trilateral summit between Japan, South Korea, and the U.S. -- "My_Essay(prof).msc" or "NZZ_Interview_Kohei Yamamoto.msc" -- with the latter uploaded to the VirusTotal platform on April 5, 2024, from Japan.
This raises the possibility that the campaign may be oriented toward targeting specific people in Japan and South Korea .
The use of MSC files to pull off the attack is a sign that Kimsuky is utilizing uncommon document types to fly under the radar. In a further attempt to increase the likelihood of success of the infection, the document is disguised as an innocuous Word file using the word processor's icon.
Should a victim launch the MSC file and consent to opening it using Microsoft Management Console ( MMC ), they are displayed a console screen containing a Word document that, when launched, activates the attack sequence.
This involves running a command to establish a connection with an adversary-controlled server ("brandwizer.co[.]in") to display a document hosted on Google Drive ("Essay on Resolution of Korean Forced Labor Claims.docx"), while additional instructions are executed in the background to set up persistence as well as collect battery and process information.

The gathered information is then exfiltrated to the command-and-control (C2) server, which is also capable of harvesting IP addresses, User-Agent strings, and timestamp information from the HTTP requests, and delivering relevant payloads as necessary.
Genians said that some of the tactics, techniques, and procedures (TTPs) adopted in the campaign overlap with prior Kimsuky activity disseminating malware such as ReconShark , which was detailed by SentinelOne in May 2023.
"In the first quarter of this year, spear-phishing attacks were the most common method of APT attacks reported in South Korea," the company noted. "Although not commonly reported, covert attacks via social media are also occurring."
"Due to their one-on-one, personalized nature, they are not easily detected by security monitoring and are rarely reported externally, even if the victim is aware of them. Therefore, it is very important to detect these personalized threats at an early stage."

Cybersecurity Webinars
Discover the hidden tactics of cyber criminals.
Join us to explore how attackers are turning your tools against you and what you can do about it.
Mastering Data Security in the Age of Petabytes
Ever wondered how giants like McDonald's and the CIA secure petabytes of data? Find out in our exclusive webinar.

How to Investigate an OAuth Grant for Suspicious Activity or Overly Permissive Scopes

Patching vs. Isolating Vulnerabilities

Securing SaaS Apps in the Era of Generative AI

GitHub Abuse Flaw Shows Why We Can't Shrug Off Abuse Vulnerabilities in Security
Sign up for free and start receiving your daily dose of cybersecurity news, insights and tips.
CYBER SECURITY
Cybersecurity in Healthcare: Protecting Patient Data in the Age of Medical Science Technology
The Silicon Review 24 May, 2024
In healthcare technology, the paramount concern is the protection of patient data. As medical science embraces technological advancements, the importance of cybersecurity cannot be overstated. Patient records, treatment plans, and sensitive medical information are all digitized, making them vulnerable to cyber threats.
The interconnected nature of healthcare systems, with electronic health records (EHRs) and medical devices linked to networks, presents numerous entry points for cyber-attacks. Malicious actors target these vulnerabilities to access valuable data, jeopardizing patient privacy and the integrity of medical services.
To counter these threats, healthcare institutions must implement robust cybersecurity measures. This includes encryption protocols to safeguard data both in transit and at rest, multi-factor authentication to prevent unauthorized access, and regular security audits to identify and address vulnerabilities.
Furthermore, staff training is essential to ensure awareness of cybersecurity best practices and protocols. Employees must be vigilant against phishing attempts, malware, and social engineering tactics that seek to exploit human error.
Collaboration between healthcare providers, technology vendors, and cybersecurity experts is imperative to develop comprehensive strategies for threat detection, incident response, and data breach prevention. Moreover, regulatory compliance with laws such as HIPAA (Health Insurance Portability and Accountability Act) is essential to uphold patient rights and confidentiality.
In the age of medical science and technology, the protection of patient data is not just a regulatory requirement but a moral imperative. By prioritizing cybersecurity, healthcare organizations can uphold the trust and integrity of their services while ensuring patient privacy measures and well-being of those they serve.
The Growing Importance of Cybersecurity in Healthcare
In the age of Medical Science Technology, commonly referred to as MedTech, the healthcare industry is witnessing an unprecedented surge in digitalization. This transformation brings forth immense benefits, revolutionizing patient care, diagnosis, treatment, and research. However, this digital evolution also introduces significant challenges, prominently among them being cybersecurity in safeguarding Medical Science data. Healthcare organizations need to handle various risks to safeguard patient information and maintain trust in the healthcare system.
Key Cybersecurity Challenges in Healthcare
In the healthcare sector, cyber threats pose significant challenges due to the sensitivity of patient data and critical infrastructure. Key challenges include ransomware attacks targeting hospitals, compromising patient records and disrupting services. Additionally, the proliferation of IoT devices in medical facilities increases the attack surface, amplifying vulnerabilities. Ensuring HIPAA compliance adds complexity to cybersecurity measures. In addition, staff training and awareness are crucial to mitigate human error.
Here are a few cybersecurity challenges healthcare faces today:
- Sophisticated Cyber-attacks: Healthcare institutions are increasingly becoming prime targets for sophisticated cyber-attacks due to the vast amounts of sensitive patient data they hold. These attacks often involve highly skilled hackers employing advanced techniques such as ransomware, phishing, and social engineering to breach systems and steal or manipulate data. The consequences of such attacks can be devastating, ranging from compromising patient privacy to disrupting critical medical services. Given the critical nature of medical data, healthcare organizations must continuously update their cybersecurity measures and invest in advanced threat detection systems to safeguard against evolving cyber threats, ensuring the integrity and confidentiality of medical science data.
- Legacy Systems: Many healthcare facilities still rely on outdated legacy systems that were not designed with modern cybersecurity threats in mind. These systems often lack essential security features and are more vulnerable to attacks, posing significant risks to the integrity and confidentiality of medical science data. Moreover, patching and updating these systems can be challenging due to compatibility issues and the need to ensure uninterrupted access to patient records and medical devices. Healthcare organizations must prioritize the modernization of their IT infrastructure, including the retirement or upgrading of legacy systems, to enhance cybersecurity resilience and protect critical medical data against evolving threats in the field of medical science.
- Interconnected Devices: The proliferation of interconnected medical devices and the Internet of Medical Things (IoMT) presents significant cybersecurity challenges for healthcare organizations. These devices, including patient monitors, infusion pumps, and imaging machines, often lack robust security controls, making them potential entry points for cyber-attacks. Moreover, the interconnected nature of these devices increases the attack surface and the complexity of managing security risks. Healthcare providers must implement strict access controls, encryption protocols, and continuous monitoring mechanisms to secure IoMT devices and prevent unauthorized access to sensitive patient data.
- Regulatory Compliance: Healthcare organizations must adhere to stringent regulatory requirements, such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States, to protect patient information and ensure data privacy and security. Achieving and maintaining regulatory compliance can be a complex and resource-intensive process, especially in the face of evolving cyber threats and regulatory frameworks. Non-compliance not only exposes healthcare providers to legal and financial penalties but also undermines patient trust and confidence in the integrity of their healthcare data. Therefore, healthcare organizations must prioritize compliance efforts by regularly conducting risk assessments, implementing appropriate security controls, and providing ongoing staff training on medical data protection and privacy laws.
Effective Cybersecurity Strategies in Healthcare
Effective cybersecurity strategies are essential for safeguarding healthcare systems, which handle sensitive patient data and are increasingly targeted by cyber threats. Here are some key strategies for ensuring cybersecurity in healthcare:
- Implementing Advanced Encryption: Advanced encryption is vital for safeguarding sensitive healthcare information. By encrypting data during transmission and storage, healthcare institutions prevent unauthorized access. Standards like AES not only offer robust defense against cyber threats such as breaches and compromising patient records but also incorporate effective ransomware prevention measures. End-to-end encryption for provider-patient communication boosts confidentiality. Regularly updating encryption methods and secure key management are crucial for staying ahead of evolving threats.
- Regular Software Updates and Patching: Regular software updates and patching are vital for healthcare system security. Vendors frequently release updates to fix vulnerabilities and boost security. Promptly applying these updates prevents exploitation by cybercriminals. Automated patch management systems streamline deployment across devices, reducing exposure to threats. Regular vulnerability assessments and penetration testing prioritize areas needing attention. Proactive updating enhances cybersecurity, safeguarding patient data from unauthorized access.
- Employee Training and Awareness: Employee training and awareness are crucial for healthcare cybersecurity. Human error is a top cause of breaches, so educating staff on best practices is vital. Topics should include spotting phishing emails, using strong passwords, and handling patient data securely. Regular simulated phishing exercises reinforce training and pinpoint areas for improvement. Awareness of cybersecurity consequences motivates staff to prioritize security. Fostering a culture of cybersecurity empowers employees to actively protect data and thwart threats.
- Multi-Factor Authentication (MFA): Multi-factor authentication strengthens security by requiring multiple forms of verification to access systems or data. In healthcare, where patient information protection is critical, MFA is highly beneficial. It typically combines a password with something the user has or is, like a smartphone or biometric data. This reduces the risk of unauthorized access, even with compromised credentials. Healthcare organizations should implement MFA for all systems containing sensitive data. Though it adds an extra step, the security benefits outweigh any inconvenience, especially in countering sophisticated cyber threats.
- Network Segmentation: Network segmentation divides a computer network into smaller sub-networks to boost security and control access to sensitive resources. In healthcare, where many devices are interconnected, it's crucial for isolating critical medical devices and patient data from threats. This limits attackers' movement in breaches, reducing the impact. Segmentation allows different security controls based on risk level, ensuring critical assets are best protected. Implementing it needs careful planning to balance security and efficiency. Regular policy reviews adapt to evolving threats and tech advancements.
- Incident Response Planning: Incident response planning is crucial for managing cybersecurity incidents in healthcare. A well-defined plan outlines steps for detection, containment, eradication, recovery, and analysis. Clear roles and responsibilities for response team members are essential, along with adequate training and resources. Testing the plan through exercises identifies gaps and enhances response capabilities. Communication protocols for notifying stakeholders, authorities, and affected individuals are vital. Proactive preparation minimizes the impact on patient care and reputation, ensuring compliance with data protection regulations.
The Role of Emerging Technologies
The role of emerging technologies in healthcare is rapidly transforming patient care, diagnosis, and management. Key technologies such as Artificial Intelligence (AI), Machine Learning (ML), Blockchain Technology, and Biometric Authentication are revolutionizing healthcare delivery in various ways:
- AI: AI enables machines to mimic human intelligence, allowing healthcare systems to analyze vast amounts of data efficiently. AI-powered tools aid in diagnosis, personalized treatment plans, predictive analytics, and administrative tasks, enhancing clinical decision-making and patient outcomes.
- ML: ML algorithms learn from data to make predictions and decisions without explicit programming. In healthcare, ML is applied in areas such as medical imaging analysis, drug discovery, patient risk stratification, and precision medicine, improving diagnostic accuracy and treatment effectiveness.
- Blockchain Technology: Blockchain offers a decentralized and secure way to record and share data across multiple parties. In healthcare, blockchain enhances data interoperability, ensures the integrity of medical records, facilitates secure sharing of patient information, and strengthens supply chain management and drug traceability.
- Biometric Authentication: Biometric authentication uses unique biological traits such as fingerprints, facial recognition, or iris scans to verify individual identities. In healthcare, biometric authentication enhances security and access control to electronic health records (EHRs), medical devices, and healthcare systems, reducing the risk of unauthorized access and identity theft.
These emerging technologies hold immense potential to revolutionize healthcare delivery, improve patient outcomes, enhance operational efficiency, and advance medical research and innovation. However, their successful integration requires careful consideration of regulatory compliance, privacy concerns, data security, and ethical implications to realize their full benefits in the healthcare ecosystem.
Put simply, the convergence of medical science and technology presents immense opportunities for innovation and advancement in healthcare. However, safeguarding patient data and ensuring the integrity and confidentiality of medical science systems require concerted efforts and investments in cybersecurity. By addressing key cybersecurity challenges, implementing effective strategies, and leveraging emerging technologies, healthcare organizations can navigate the complexities of the digital landscape and uphold the trust and security of the healthcare ecosystem.
What are the most common cyber securities threats facing healthcare organizations today?
Today, healthcare organizations face a range of cybersecurity threats: ransomware encrypts data for ransom, data breaches expose patient info, phishing scams trick employees, and insider threats jeopardize data integrity. With healthcare digitization, these risks grow, requiring strong security, training, and industry-wide collaboration to protect patient data and infrastructure.
How can healthcare providers ensure compliance with data protection regulations like HIPAA?
To comply with regulations like HIPAA, healthcare providers can: conduct risk assessments to spot and fix vulnerabilities, enforce strict access controls and encryption, train staff on HIPAA guidelines, use secure communication channels, audit systems for breaches, establish clear data handling policies, and promptly report breaches to maintain accountability and meet regulatory standards.
What role does encryption play in protecting patient data in medical science technology?
Encryption is vital in medical tech, scrambling data for confidentiality, integrity, and authenticity. It safeguards EHRs, diagnostic images, and communication channels, preventing unauthorized access and aiding HIPAA compliance. Advanced encryption and key management systems enhance security, preserving patient trust and confidentiality while improving care.
How can emerging technologies like AI and blockchain improve cyber security in healthcare?
AI and blockchain are transforming cybersecurity in healthcare. AI detects threats by analyzing data, automates security tasks, and enables predictive analytics to prevent breaches. Blockchain ensures data integrity, transparency, and secure exchange, with smart contracts enforcing regulations like HIPAA. Together, they offer real-time threat intelligence, improve incident response, and create a resilient ecosystem for secure patient data management.
What steps can healthcare organizations take to create a robust incident response plan?
A solid incident response plan in healthcare starts with risk assessment and protocols for detection. Assemble a response team, document procedures, and train regularly. In incidents, contain, recover, analyze, and communicate transparently with stakeholders. Regular reviews keep the plan adaptable to evolving threats, strengthening resilience against cyber-attacks.
MOST VIEWED ARTICLES
Segmentation strategies: enhancing customer outreach in email marketing, how to start a college essay about yourself, pitch perfect: the best soccer fields and facilities in the mls, how webflow development can revolutionize your marketing strategy, embracing digital transformation in manufacturing and inventory management, recommended news.
Bitcoin and Ethereum ETFs are predicted to be..
OpenAI inaugurated its first Tokyo operations..
PH launched the nat’l platform for &lsq..
Global Food & Beverage Industry leader Su..
Hyundai paused ads on X over brand safety iss..
Julius Baer appointed a new CEO for the Thail..
China Will No Longer Have Twitch: Reports Say..
New acquisition by Alibaba is expected to str..
ASG expanded by opening a London office
Alternus clean energy and acadia energy partnered to develop 200 mw microgrid projects, us science agency debuted startup matchmaking program in taiwan, dallas’ welker properties launched prophet homes, aims to raise $100m with new fund, joint eu-us-armenia high level meeting happened in support of armenia's resilience, you may also like, puma studio announced opening in la to create products and campaigns, efficiency redefined: driving the ford lease advantage, totalenergies expanded its natural gas production in texas, altice’s patrick drahi acquired sotheby’s auction house for $3.7 billion, mastercard and sap concur partnered to revolutionise expense management.
- Industry Newsletters
- Send Us Feedback
- Share your Ideas
- Middle East
- United Kingdom
- United States
© 2024 Silicon Review LLC. All Rights Reserved.
- PRIVACY POLICY
- PRINTS AND PERMISSIONS

COMMENTS
Cybercriminals get directly into the pockets of citizens. This becomes possible due to multiple attacks of hackers on banks. The banking sector is of huge importance for the stability of people's well-being. A hacker attack, which ruins the banking industry, leads to a dangerous destabilization of the economy of the country.
Cybersecurity in the Banking Sector as a Career: Outlook. Compared to many other occupations, the cybersecurity field offers more job stability. For instance, the BLS predicts a 33% increase in employment for information security experts between 2020 and 2030. Information security in banking has also exponentially increased, and there is a high ...
www.neu roquan tology .com. e ISSN 1303-5150. 405. A Review of Cyber Security Issues in Online Banking. and Online Transactions. Dr.Bhupali shah. Asst.Prof, Pratibha Institute of Business ...
into curre nt tre nds, p otential solutions, and best practices to enhance the security of online banking and financial. transactions in an increasingly digital world. V ol 9 Issue6 ...
Cybersecurity in Banking Industry: Importance. 1. Prevent Financial Losses. The banking industry holds the data of millions of people, and this data can help hackers in many ways. For example, if someone hacks your bank account using your ID info, they can steal all your money in seconds, not to mention that it is almost impossible to recover ...
In this paper, we provide a systematic review of the growing body of literature exploring the issues related to pervasive effects of cybersecurity risk on the financial system. As the cybersecurity risk has appeared as a significant threat to the financial sector, researchers and analysts are trying to understand this problem from different perspectives. There are plenty of documents providing ...
Abstract. With the rapid expansion of digital banking services and the increasing reliance on technology in the financial sector, the need for robust cybersecurity measures has never been more ...
emergence of open banking and the second PSD2 Payment Services Directive has the potential to transform the finance ecosystem, sparking debate around security capabilities of new players and the consequences of data breaches in those firms. Within banking institutions, there is a greater management focus on cyber security operations, and
For banks that store large amounts of personal data and transaction lists, cybersecurity solutions and procedures are critical. Nowadays, the importance of cybersecurity in banking cannot be ...
Friday, 1 April 2022 ∙ 7 minutes read. We live in an increasingly online world, and with the rise in digital banking, there's also been a surge in attacks by cybercriminals. Financial institutions must thus invest heavily in their cybersecurity. A cyberattack can have devastating consequences, and not just in terms of the data stolen.
The digital transformation of the banking industry has affected departments, strategies, processes, and sometimes entire business models (Benlian et al., 2014; Rodrigues et al., 2020).Banks face major internal challenges due to their inability to innovate more broadly (Tornjanski et al., 2015).Ben-Asher and Gonzalez (2015) observe that public Web servers that connect corporate networks to the ...
In summary, this essay offers useful insights on using modern machine learning algorithms to reduce cybersecurity threats and ensure the security of digital transactions within the banking industry. Keywords: ... Cybersecurity threats to the banking sector are evolving, and banks must take decisive action to safeguard their ...
Internet banking has become one of the fastest and easiest way of banking. The threat of cyber security attacks set a great challenge for the Internet banking and electronic commerce (E-commerce) industries. In this paper, we first analyse in detail the cyber security of Internet Banking in three emerging countries and then propose a novel model to reduce the cyber security risk to bridge the ...
cybersecurity needs to be steeped into the national consciousness through education, sustained messaging and increased cooperation among businesses and government. My research examines the vulnerabilities, and cites case studies, national policy and expert analysis. I will explore the ways forward, drawing from the national
PAGES. 5. WORDS. 1576. Cite. View Full Essay. Cybersecurity for Mistral Bank Mistral Bank is one of the global financial services company headquartered in the United States where it is the third-largest bank holding firm and fourth-largest in assets held by deposit and market capitalization respectively. Since its inception, the company has ...
SCIENCE & TECH/ GOVERNANCE GS-3: Cyber Security and its challenges GS-3: Government policies and interventions for development in various sectors and issues arising out of their design and implementation. Cybersecurity & Banks Context: With increasing emphasis being laid on digitisation for financial institutions, there has been a monumental increase in cybersecurity threats as well. Therefore,…
PDF | On Nov 7, 2019, Sara Al-Bassam and others published The Significance of Cybersecurity System in Helping Managing Risk in Banking and Financial Sector | Find, read and cite all the research ...
PAGES 2 WORDS 620. In an age where technological advancements have revolutionized how we communicate, transact, and store information, cybersecurity has emerged as a paramount concern for individuals, businesses, and governments alike. With the increasing dependency on digital systems and the internet, the vulnerabilities and threats associated ...
Cyber Security Essay. Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today's world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software.
Cyber security, also known as information technology security, focuses on protecting computers, networks, programs, and data from unintended or unauthorized access, damage, or destruction. In the digital era, the importance of cyber security is growing exponentially due to the increasing reliance on computer systems, the internet, and wireless ...
Recognizing fraudulent activity in the banking system is essential due to the significant risks involved. When fraudulent transactions are vastly outnumbered by non-fraudulent ones, dealing with imbalanced datasets can be difficult. This study aims to determine the best model for detecting fraud by comparing four commonly used machine learning algorithms: Support Vector Machine (SVM), XGBoost ...
Essay. Humanity Shouldn't Be Afraid to Say Hello to Aliens Some scientists worry that beaming signals into space could lead extraterrestrials to conquer Earth, as in the TV series '3 Body ...
Understanding networks properly will help us to better grasp how the economy actually works
Cybersecurity risk assessment in banking is the process of identifying, analyzing, and evaluating the cyber threats and vulnerabilities that may affect the confidentiality, integrity, and ...
The North Korea-linked Kimsuky hacking group has been attributed to a new social engineering attack that employs fictitious Facebook accounts to targets via Messenger and ultimately delivers malware. "The threat actor created a Facebook account with a fake identity disguised as a public official working in the North Korean human rights field," South Korean cybersecurity company Genians said in ...
Much like the internet, SS7 was built on the basis of trust, not security.That was reasonable when the protocol was introduced and only a few telecoms companies could access it. Today, many ...
Ab stract: Internet banking has become one of the fastest and easiest way of banking. The threat of cyber. security attacks set a great c hallenge for the I nternet banking and electronic c ...
Key Cybersecurity Challenges in Healthcare In the healthcare sector, cyber threats pose significant challenges due to the sensitivity of patient data and critical infrastructure. Key challenges include ransomware attacks targeting hospitals, compromising patient records and disrupting services.