This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.

Assign Azure resource roles in Privileged Identity Management
- 19 contributors
With Microsoft Entra Privileged Identity Management (PIM), you can manage the built-in Azure resource roles, and custom roles, including (but not limited to):
- User Access Administrator
- Contributor
- Security Admin
- Security Manager
Users or members of a group assigned to the Owner or User Access Administrator subscription roles, and Microsoft Entra Global administrators that enable subscription management in Microsoft Entra ID have Resource administrator permissions by default. These administrators can assign roles, configure role settings, and review access using Privileged Identity Management for Azure resources. A user can't manage Privileged Identity Management for Resources without Resource administrator permissions. View the list of Azure built-in roles .
Privileged Identity Management support both built-in and custom Azure roles. For more information on Azure custom roles, see Azure custom roles .
Role assignment conditions
You can use the Azure attribute-based access control (Azure ABAC) to add conditions on eligible role assignments using Microsoft Entra PIM for Azure resources. With Microsoft Entra PIM, your end users must activate an eligible role assignment to get permission to perform certain actions. Using conditions in Microsoft Entra PIM enables you not only to limit a user's role permissions to a resource using fine-grained conditions, but also to use Microsoft Entra PIM to secure the role assignment with a time-bound setting, approval workflow, audit trail, and so on.
When a role is assigned, the assignment:
- Can't be assigned for a duration of less than five minutes
- Can't be removed within five minutes of it being assigned
Currently, the following built-in roles can have conditions added:
- Storage Blob Data Contributor
- Storage Blob Data Owner
- Storage Blob Data Reader
For more information, see What is Azure attribute-based access control (Azure ABAC) .
Assign a role
Follow these steps to make a user eligible for an Azure resource role.
Sign in to the Microsoft Entra admin center as at least a User Access Administrator .
Browse to Identity governance > Privileged Identity Management > Azure resources .
Select the resource type you want to manage. Start at either the Management group dropdown or the Subscriptions dropdown, and then further select Resource groups or Resources as needed. Click the Select button for the resource you want to manage to open its overview page.

Under Manage , select Roles to see the list of roles for Azure resources.
Select Add assignments to open the Add assignments pane.

Select a Role you want to assign.
Select No member selected link to open the Select a member or group pane.

Select a member or group you want to assign to the role and then choose Select .

On the Settings tab, in the Assignment type list, select Eligible or Active .

Microsoft Entra PIM for Azure resources provides two distinct assignment types:
Eligible assignments require the member to activate the role before using it. Administrator may require role member to perform certain actions before role activation, which might include performing a multi-factor authentication (MFA) check, providing a business justification, or requesting approval from designated approvers.
Active assignments don't require the member to activate the role before usage. Members assigned as active have the privileges assigned ready to use. This type of assignment is also available to customers that don't use Microsoft Entra PIM.
To specify a specific assignment duration, change the start and end dates and times.
If the role has been defined with actions that permit assignments to that role with conditions, then you can select Add condition to add a condition based on the principal user and resource attributes that are part of the assignment.

Conditions can be entered in the expression builder.

When finished, select Assign .
After the new role assignment is created, a status notification is displayed.

Assign a role using ARM API
Privileged Identity Management supports Azure Resource Manager (ARM) API commands to manage Azure resource roles, as documented in the PIM ARM API reference . For the permissions required to use the PIM API, see Understand the Privileged Identity Management APIs .
The following example is a sample HTTP request to create an eligible assignment for an Azure role.
Request body
Status code: 201
Update or remove an existing role assignment
Follow these steps to update or remove an existing role assignment.
Open Microsoft Entra Privileged Identity Management .
Select Azure resources .

Under Manage , select Roles to list the roles for Azure resources. The following screenshot lists the roles of an Azure Storage account. Select the role that you want to update or remove.

Find the role assignment on the Eligible roles or Active roles tabs.

To add or update a condition to refine Azure resource access, select Add or View/Edit in the Condition column for the role assignment. Currently, the Storage Blob Data Owner, Storage Blob Data Reader, and Storage Blob Data Contributor roles in Microsoft Entra PIM are the only roles that can have conditions added.
Select Add expression or Delete to update the expression. You can also select Add condition to add a new condition to your role.

For information about extending a role assignment, see Extend or renew Azure resource roles in Privileged Identity Management .
- Configure Azure resource role settings in Privileged Identity Management
- Assign Microsoft Entra roles in Privileged Identity Management
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources
Cloud Build
Microsoft azure, 365 and all things tech.
difference between eligible and active azure PIM
How to configure azure ad roles in privileged identity management (pim).
Privileged Identity Management (PIM) is a service in Azure Active Directory (Azure AD) that enables you to manage, control, and monitor access to important resources in your organisation.
Privileged Identity Management provides time based and approval based role activation to mitigate the risks of excessive, unnecessary, or misused access permissions on resources that you care about. Here are some of the key features of Privileged Identity Management:
- Provide just-in-time privileged access to Azure AD and Azure resources
- Assign time-bound access to resources using start and end dates
- Require approval to activate privileged roles
- Enforce multi-factor authentication to activate any role
- Use justification to understand why users activate
- Get notifications when privileged roles are activated
- Conduct access reviews to ensure users still need roles
- Download audit history for internal or external audit
Privileged Identity Management licence requirements
- Azure AD Premium P2 or Enterprise Mobility + Security (EMS) E5
Ensure that your directory has at least as many Azure AD Premium P2 licenses as you have employees that will be performing the following tasks:
- Users assigned as eligible to Azure AD or Azure roles managed using PIM
- Users who are assigned as eligible members or owners of privileged access groups
- Users able to approve or reject activation requests in PIM
- Users assigned to an access review
- Users who perform access reviews
Azure AD Premium P2 licenses are not required for the following tasks:
- No licenses are required for users who set up PIM, configure policies, receive alerts, and set up access reviews.
It can become confusing when working out the number of Azure AD P2 licences required so Microsoft have provided examples at the following link: Azure PIM Example Licence Scenari os In this blog post I will go through the process of configuring Azure AD Roles in Privileged Identity Management (PIM). I will grant a user named Joe Bloggs eligible assignment for one of my Azure admin roles.
As mentioned above, to use PIM you must have an Azure AD P2 or Enterprise Mobility + Security (EMS) E5 licence. I currently have access to an E3 license which grants me access to an Azure AD P1 licence which is obviously not sufficient.
If you already have access to Azure AD P2, skip to the next section by scrolling down to section Configuring Azure Privileged Identity Management (PIM)
- Firstly, I will sign up to a free 90 day Enterprise Mobility + Security (EMS) E5 trial account. As you can see from the screenshot below my licence assignment is currently Azure AD Premium P1.

and if I attempt to access PIM, I receive the message below

Microsoft offer trials for a number of their products including Azure AD P2 which will allow you to test Azure PIM. I’ll start with activating a free trial which can be ready within minutes as you’ll find out shortly.
2. Access Azure AD, click Licenses , click All products and click the + Try / Buy button as highlighted below

3. Enterprise Mobility + Security E5 includes Azure AD P2 and Microsoft offer a 90 day trial so I selected this option. I’ll be going through further demo’s at a later date which require Enterprise Mobility + Security E5 so this licence will be useful.

4. Click Free Trial under the licence you wish to activate. In my case I clicked Free trial under Enterprise Mobility + Security E5

5. Click Activate

6. Wait for the product to activate which should take seconds

7. After activation my licence status still shows as Azure AD P1

8. Log out of the portal and back in and the correct version is now displayed

That’s the free trial sorted
Configuring Azure AD Roles – Azure Privileged Identity Management (PIM)
- Log into the Azure Portal (portal.azure.com)
- Search PIM and select Azure AD Privileged Identity Management

3. Click Azure AD roles

4. Click Assignments

5. I don’t have any assignments at the moment, click +Add Assignments

6. Select a role and member

For the purpose of this demo, I have selected the role Global Administrator and selected an existing user named Joe Bloggs from my directory. Click Next

7. For the purpose of this demo, I will select Eligible and leave the default at permanently eligible. Eligible A role assignment that requires a user to perform one or more actions to use the role. If a user has been made eligible for a role, that means they can activate the role when they need to perform privileged tasks. There’s no difference in the access given to someone with a permanent versus an eligible role assignment. An eligible administrator can activate the role when they need it, and then their permissions expire at a set time, until the next time the role is activated. The only difference is that some people don’t need that access all the time. So in my case, Joe Bloggs will be eligible which means he will request access each time he requires access to the Global Administrator role (Default limit for 8 hours and his permissions will be removed until he activates again). Permanently eligible which means he will be allowed to continue to activate the role when he needs to perform privileged tasks. A permanently eligible end date can be configured, for example, users can activate access for 8 hours at a time for up to 1 year instead of being able to activate the role continuously without an end date. I’ll cover more on this as we move on.
Active: This is a role assignment that doesn’t require a user to perform any action to use the role. Users assigned as active have the privileges assigned to the role at all times but can be setup so access is removed at a certain date.

Continuing with Active Assignment, this options provides a user with permanent access or up to a date set by the administrator. See screenshot below. In this case, the user will have access to the role assigned permanently or by a set expiry date. A further text box appears as shown below requesting a justification on why the admin is granting the user with an active assignment.

8. For the purpose of this demo, I have selected eligible. Click Assign when ready

9. Now that Joe Bloggs has been granted an eligible assignment, I will log in as Joe Bloggs and demonstrate what Joe Bloggs will see.
10. When logging in as Joe Bloggs, I am prompted to enable MFA.

11. MFA configured, I can now move on to logging in as Joe Bloggs. Now that I am logged in, Joe Bloggs is still a basic user without global admin permissions, which is normal. He can’t create accounts within Azure AD or perform any other administrative tasks which require elevated permissions. Access is disabled.

12. Joe Bloggs will need to activate his eligible assignment within PIM. Whilst still logged in as Joe Bloggs, I search for PIM and click Azure AD Privileged Identity Management

13. Click My roles

14. The eligible assignment is displayed with an Activate link as shown below. Click Activate

If the user skipped MFA at the initial logon stage, as shown in the screenshot below, the user will be prompted to authorise via MFA which is enforced by a default enabled setting within PIM. I’ll explain where this option is found shortly. If you wish to disable the below 14 day reminder, you can have a read of the following link later – Disable Skip MFA prompt

15. After clicking activate, Joe Bloggs receives the below prompt

Duration: maximum of 8 hours access. After the 8 hours, Joe Bloggs access will be revoked and he will have to activate his assignment again. Joe Bloggs was allowed permanent eligibility which allows him to activate his eligible assignment when required.
Custom activation: If Joe Bloggs requires admin access in the future, he could select the option Custom activation start time and select a date and time he would like his 8 hours access to begin. In the example below, I have configured the time for a time in the past.

16. When ready, click activate
17. Activation has been scheduled

If I check access from my account, i’ll find that Joes Bloggs has been granted access without any further action required from me Location: Access PIM > Click Azure AD Roles > Pending Access
From here you could also cancel Joe Bloggs access by clicking the Cancel link

That’s the default settings but what if you wish to increase the default 8 hour access limit? Or you would like for the request to go to a team of approvers for review before Joe Bloggs is granted access? or you require 8 hours access for the Global Administrator role but 10 hours access for the Exchange Administrator role. Let’s move onto where these settings are configured.
Configuring Azure AD Privileged Identity Management Azure AD role settings
- Click Azure AD Privileged Identity Management

2. Click Azure AD roles

3. Click Settings

4. Here you can apply different configuration settings based on roles. For the purpose of this demo, I will be configuring the Global Administrator role.

5. After clicking the Global Administrator Role, you’ll find the below settings. Review and click Edit

6. The first windows displays a number of settings including the default 8 hour access. You can extend this to 24 hours if required
Azure MFA is enabled by default, which enforces MFA while activating the assignment.
Require justification: requests a reason why the user requires access
Require ticket information: you may have a process where the user requiring access needs to input a ticket or change number
Require approval to activate: this feature is an important one. Setting approvers adds an additional check before a users assignment is activated. The request goes into a pending approval list after the user activates the assignment which allows a approver to review access and deny or approve access accordingly. Note: each approver will need to be assigned an Azure AD P2 licence

To allow me to demo the approval process, I have enabled require approval to activate and added a single user as an approver.

Before I move on and demo the approval process, clicking the assignments button moves us onto the next screen below. You may wish to leave the defaults or set an expiry. For example, you could configure the below policy so that users will be eligible to elevate their account into the role assigned for one year instead of being eligible forever. The same applies for the active role.

Finally, the next screen is where you can configure email notifications
7. When ready, click the update button. Note the below fields which can be useful.

We can now move on and test the approval process.
Azure AD PIM Approval demo
- I granted Joe Bloggs an eligible assignment earlier. The new settings I configured above will apply to Joe on his next eligible assignment activation.
- I log in as Joe Bloggs
- Click Azure PIM
- Click My Roles
- Click Activate

6. Type in justification details and click activate

7. After clicking activate, Joe Bloggs is not granted access immediately. His request is pending approval as shown below

8. The admin allocated as a approver earlier must review the request and decide whether to approve or deny access. Back over to my account where I will review Joe Bloggs access. I will also receive an email to notify me that there is a request pending.
Access PIM > Azure AD Roles > Approve requests
9. Here is the pending request where I can review each case.

Note: Clicking approve or deny opens the window below allowing you review the details fully without having to expand the tabs above. A justification needs to be provided.

10. And Joes Bloggs access is approved. He will be granted access for 8 hours and does not need to take any further action to activate the role.

A complete audit of all actions carried out in PIM Azure AD Roles can also be located at: PIM > Azure AD Roles > Audit

Using Azure Active Directory (Azure AD) Privileged Identity Management (PIM), you can also improve the protection of your Azure resources and as you can see below Privileged access groups which was in preview at the time of writing this post.

Azure PIM also offers Access Reviews. Access to privileged Azure resource roles for employees changes over time. To reduce the risk associated with stale role assignments, you should regularly review access. You can use Azure Active Directory (Azure AD) Privileged Identity Management (PIM) to create access reviews for privileged Azure resource roles. You can also configure recurring access reviews that occur automatically. I will cover these topics in a further post. Note: Azure AD P2 licences are required within your directory for users assigned to an access review and users who perform access reviews.
Feedback welcome, please comment below. It would also be great to hear about your experience using Azure PIM.

Subscribe to new tech posts. We will never send you spam email or forward your details to third parties.
This will close in 0 seconds
Privacy Overview
Lab 11 - Assign Azure resource roles in Privileged Identity Management
Note - This lab requires an Azure Pass. Please see lab 00 for directions.
Lab scenario
Microsoft Entra Privileged Identity Management (PIM) can manage the built-in Azure resource roles, as well as custom roles, including (but not limited to):
- User Access Administrator
- Contributor
- Security Admin
- Security Manager
You need to make a user eligible for an Azure resource role.
Estimated time: 10 minutes
Exercise 1 - pim with azure resources, task 1 - assign azure resource roles.
Sign in to https://entra.microsoft.com using a Global Administrator account.
Search for and then select Privileged Identity Management.
In the Privileged Identity Management page, in the left navigation, select Azure resources.
On the top menu, select Discover resources .
In the Azure resources – Discovery page, select your subscription.
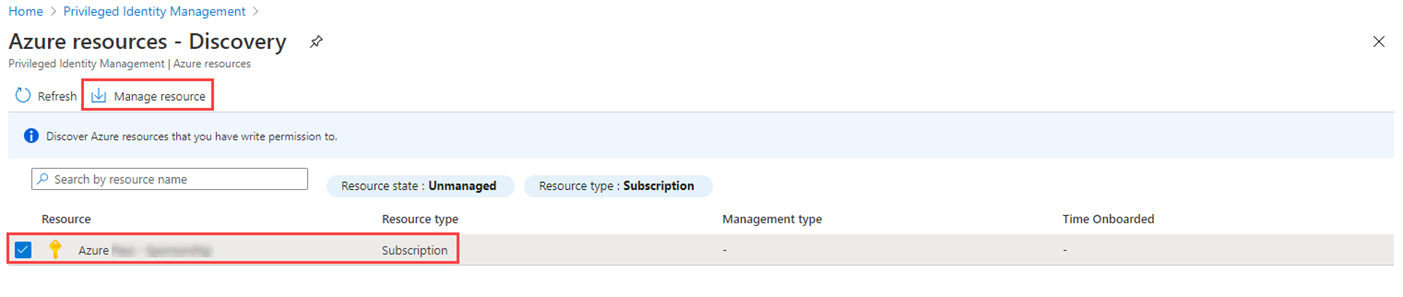
In the Overview page, review the information.
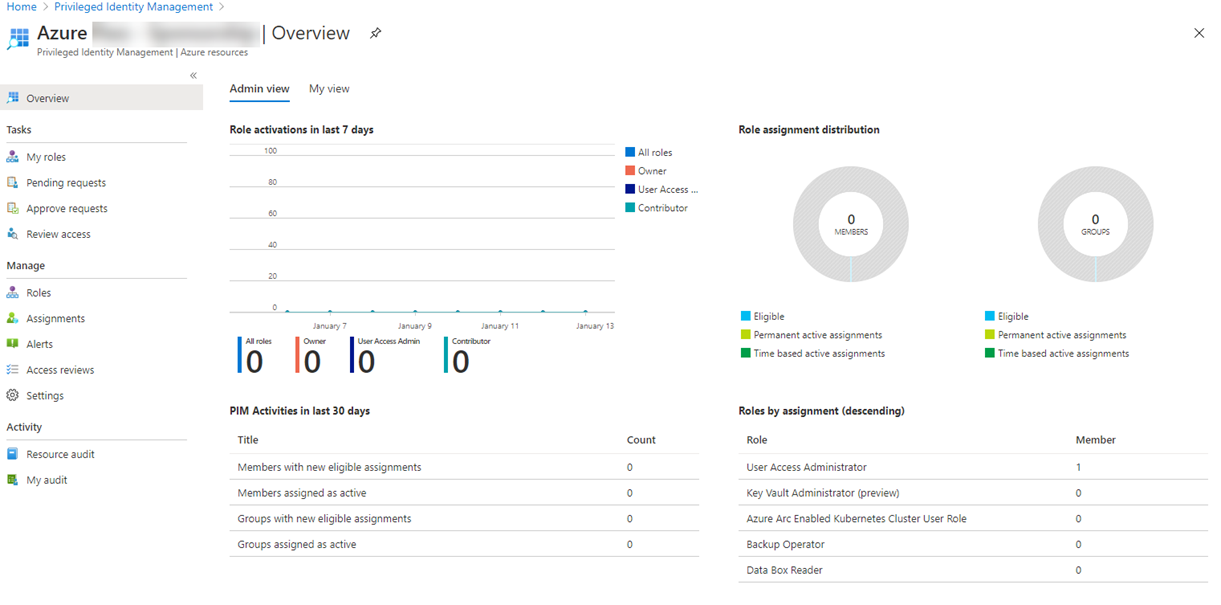
In the left navigation menu, under Manage , select Roles to see the list of roles for Azure resources.
On the top menu, select + Add assignments .
In the Add assignments page, select the Select role menu and then select API Management Service Contributor.
Under Select member(s), select No member selected .
In the Select Miriam Graham from your organization that will be assigned the role. Then chose Select .
Select Next .
On the Settings tab, under Assignment type , select Eligible .
Eligible assignments require the member of the role to perform an action to use the role. Actions might include performing a multi-factor authentication (MFA) check, providing a business justification, or requesting approval from designated approvers.
Active assignments do not require the member to perform any action to use the role. Members assigned as active have the privileges always assigned to the role.
Specify an assignment duration by changing the start and end dates and times.
When finished, select Assign .
After the new role assignment is created, a status notification is displayed.
Task 2 - Update or remove an existing resource role assignment
Follow these steps to update or remove an existing role assignment.
Open Microsoft Entra Privileged Identity Management .
Select Azure resources .
Select the subscription you want to manage to open its overview page.
Under Manage , select Assignments .
On the Eligible assignments tab, in the Action column, review the available options.
Select Remove .
In the Remove dialog box, review the information and then select Yes .
Assigning groups to Azure AD roles and Privileged access groups, a first look!
On August 13th 2020, Alex Simons (Microsoft Identity PM) announced that assigning groups to Azure AD roles in now in public preview . This feature is one of the most requested features to be found in the Azure AD feedback forum .
I have been following this feature request for a while now, and up until recently Microsoft stated that implementing Azure AD role assignment for Azure AD groups wasn’t the issue, the issue was more related to who is able to manage those groups. For example, if enabled how can we circumvent that someone with the “User Administrator” role (capable of adding users to groups) is capable of adding someone to the group used to assign Global Administrator rights. When implemented incorrectly, this new “feature” could then introduce a new security risk in your environment.
Assigning groups to Azure AD roles requires an Azure AD Premium P1 license at minimum, for the Privileged Identity Functionality an Azure AD Premium P2 license is needed.
Disclaimer: This post reflects the status of assigning groups to Azure AD roles as of August 20, 2020. Functionality may change, even right after this post has been published.
So, let’s walk through on what was announced and see..
So, up until now when you wanted to assign a user an Azure AD role, you had to include the user account directly in the role. Verifying which account has what privileges is therefore hard, especially if you don’t have Azure AD Privileged Identity Management (PIM) licensed.
For a more in depth overview of what Azure AD Privileged Identity Management (PIM) is, please see another blogpost I wrote on this subject here: Lessons learned while implementing Azure AD Privileged Identity Management (PIM)
Changed behaviour while adding members to Azure AD Roles
On the topic of PIM, I also noticed some changed functionality when adding users when you have PIM enabled in your environment. If you don’t have PIM enabled you can assign a user to a role, but if you have PIM enabled there is another experience where when you want to assign an Azure AD role you are actually redirected to the Privileged Identity Management blade, where you can directly create an Eligible (must be activated) or Active (always active) assignment.
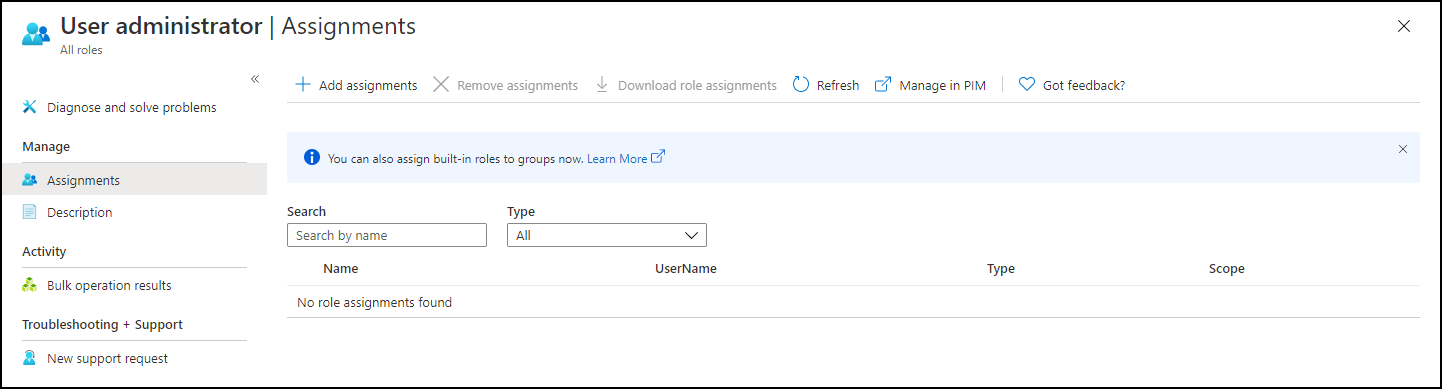
Adding users to Azure AD roles via Group membership
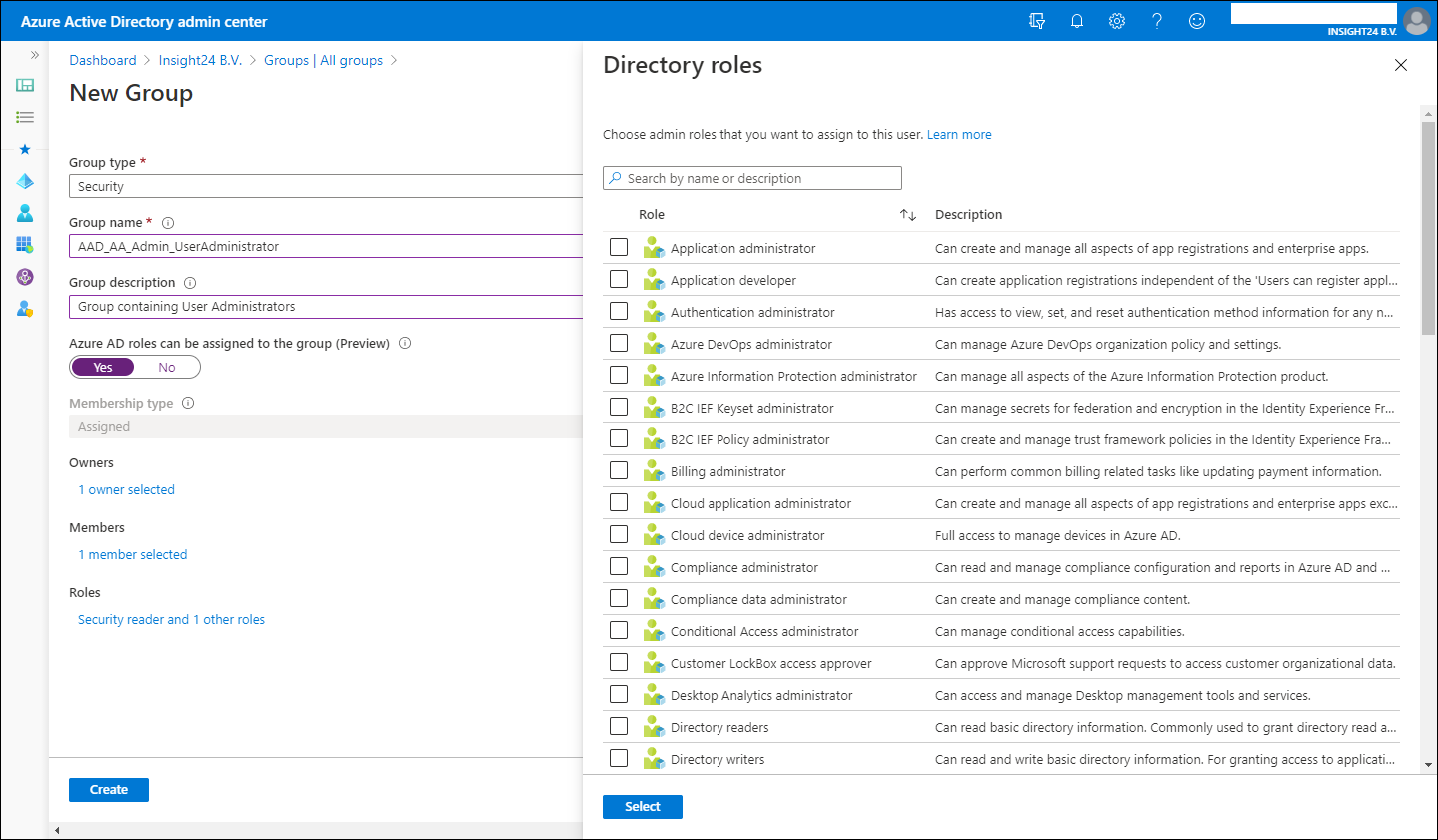
In order to add users to Azure AD roles via Group membership you first have to create a new group, so it’s not possible to repurpose an existing group for this.
New groups have the option to set the “Azure AD roles can be assigned to the group (Preview)” option which can be set to either “No” or “Yes”. When you switch this setting to ‘Yes’ the group’s eligibility for role assignment is permanent. Besides that you can only have a membership type of Assigned, so using Dynamic Groups is not supported, and within the wizard you can only add users as member and not groups (group nesting). Interestingly, you can assign multiple Azure AD roles to the group.
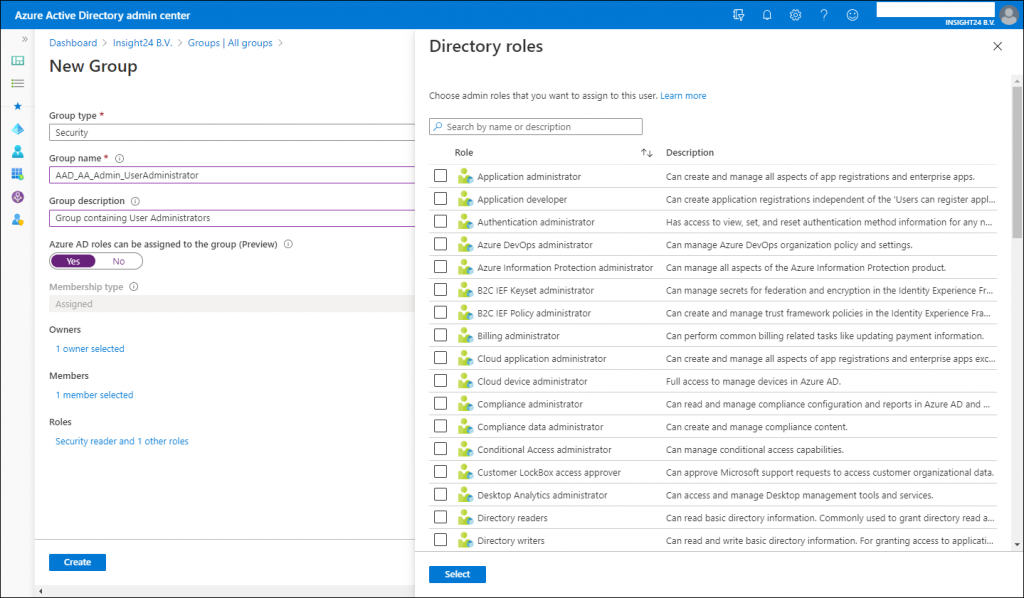
If you want to create the Group with the “Azure AD roles can be assigned to the group (Preview)” option enabled you will get an extra confirmation screen:
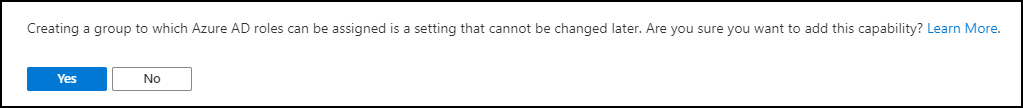
The option “Azure AD roles can be assigned to the group (Preview)” is only visible if you are member of either the Global Administrator or Privileged Role Administrator role.
Privileged access groups
Once a group with the option to enable Azure AD role assignments is created and you have PIM enabled, a new option becomes available called “Privileged access (Preview)”.
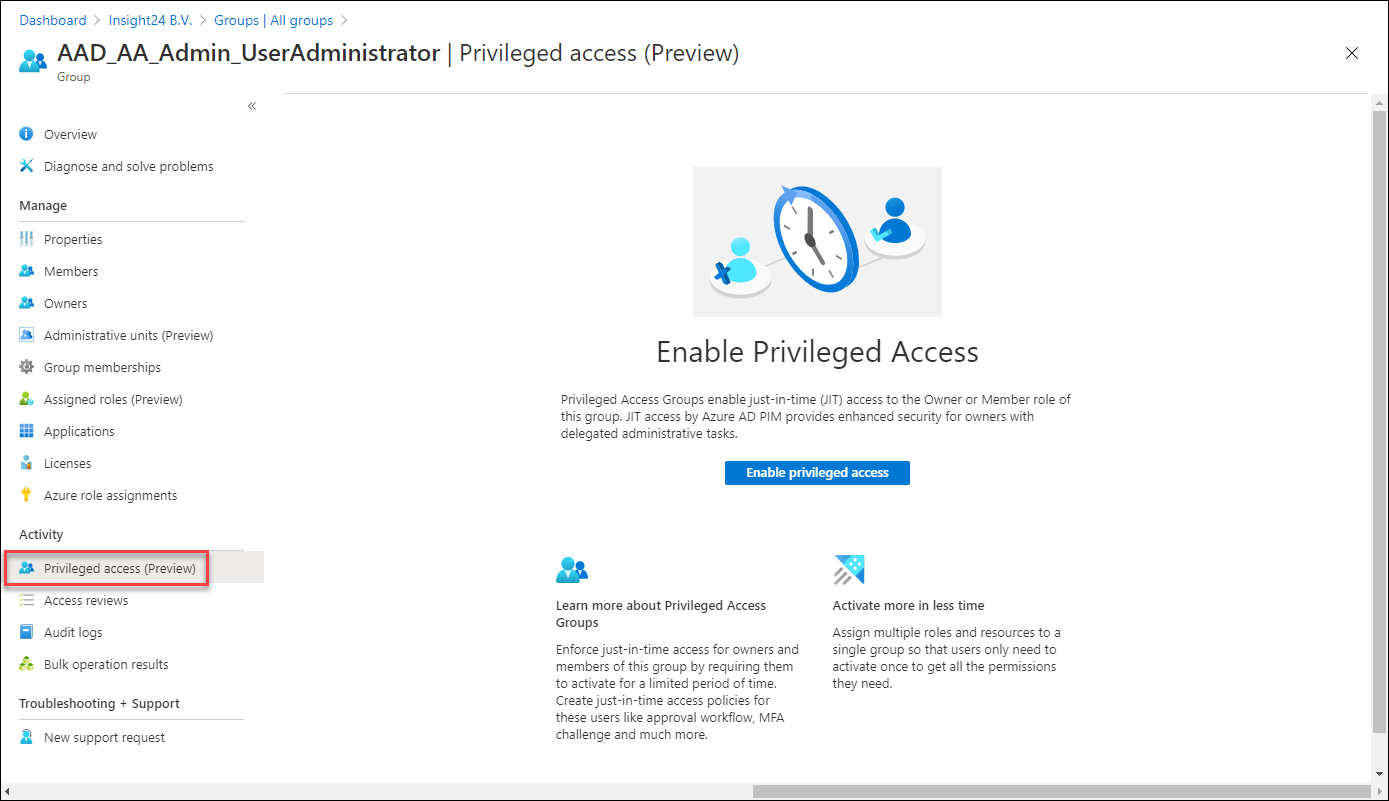
Enabling this option gives us the following options:
Define Eligible or Active assignments to the group
On the group you can assign members or owners using the capabilities provided by PIM. So for example, while adding our user as a member of the group permanently earlier in this article, I now have the option to make the membership Eligible. Also notice that this assignment type is time bound, with a maximum of 1 year.
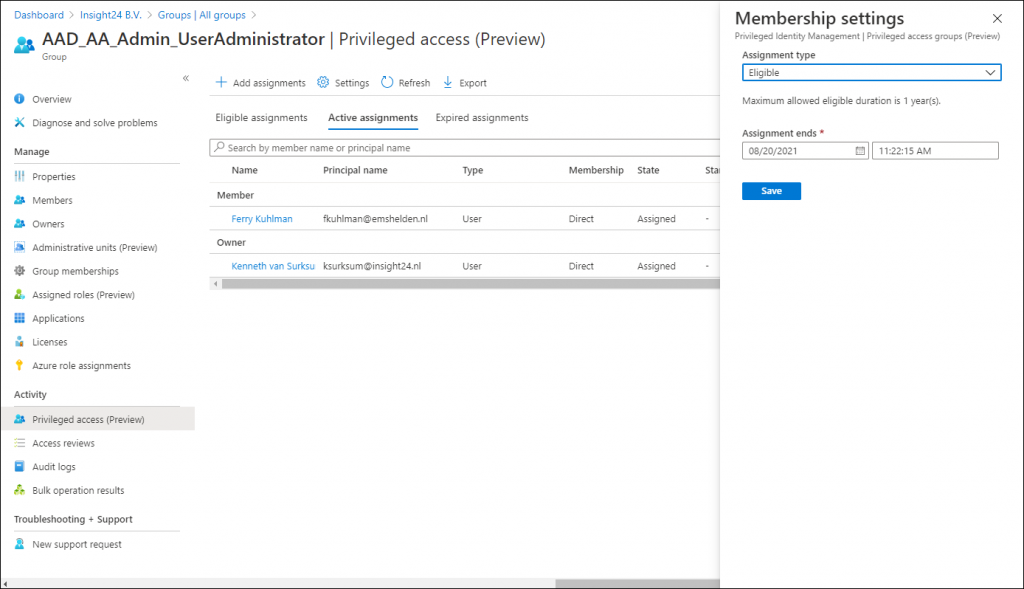
It’s also interesting to notice that if you want to update an Active Assignment you will not be allowed to Permanently assign an Active role by default. And that assigning an Active role has a maximum allowed assignment duration of 6 months. Once the group is enabled for Privileged Access and you want to add a member, then you don’t have the option “Permanently assigned” available. Also notice that providing a justification is mandatory.
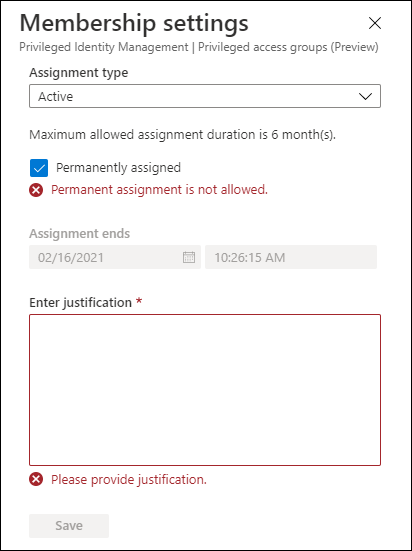
The default options described above are configurable though, trough the settings, so you are able to configure these depending on your requirements.
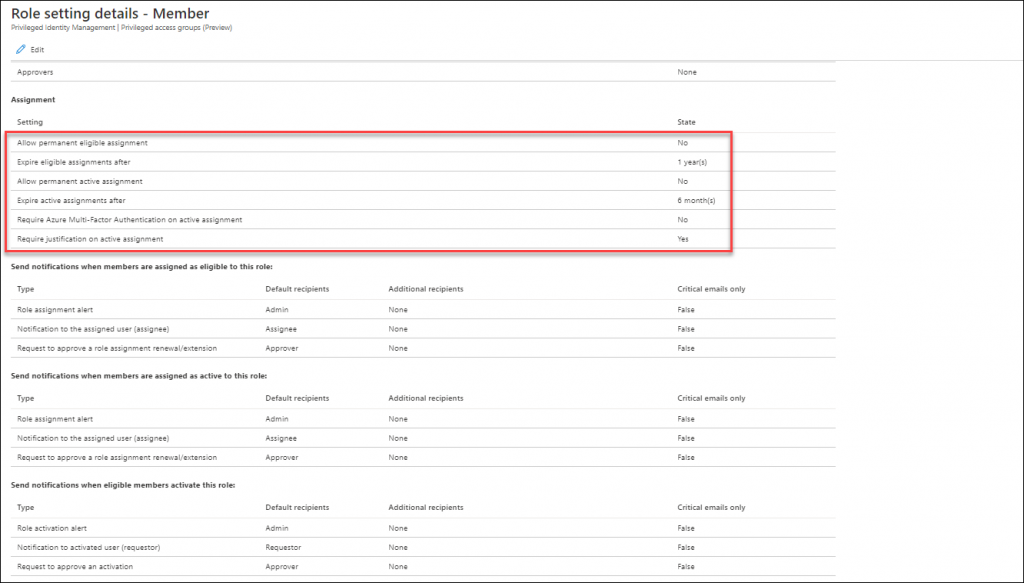
Activating your Azure AD role while using Privileged access groups
It’s interesting to see that once a user is set to Eligible for the privileged access group, that the Azure AD role doesn’t show up under Eligible Assignments when the user browses to My Roles in PIM. In order to active the Azure AD role in this scenario, the user must go to Privileged access groups (Preview) and active the role from there.
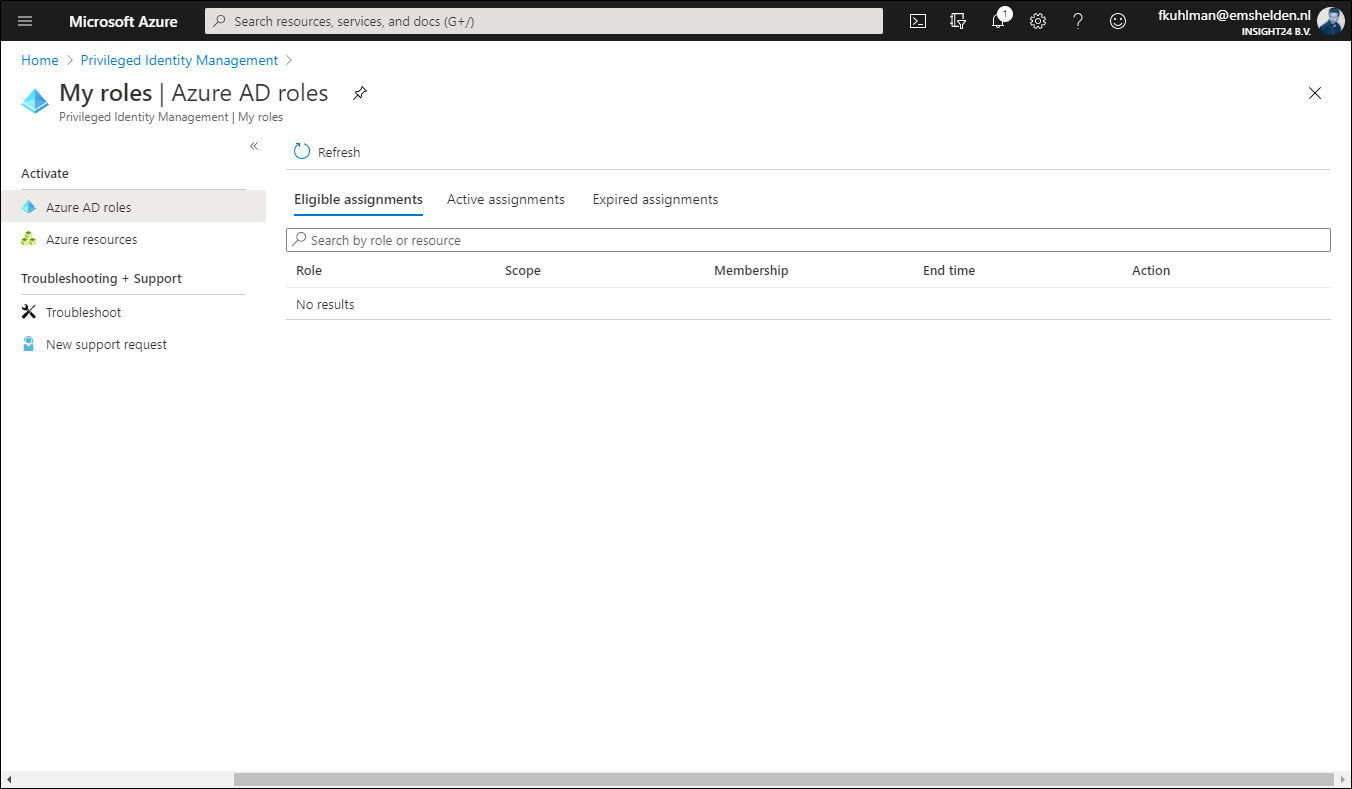
Once the role is activated via the group, it will show up under Active assignments, and what’s interesting to see is that at this time it’s still displayed as being permanent. But I expect that to be fixed while the functionality is still in preview.
Within the PIM settings of the group you can also specify that any Activation request for the group must be approved. This works similar to approval in PIM as we already know it. You define that approval is mandatory and specify who can approve. This can either be a user or a group.
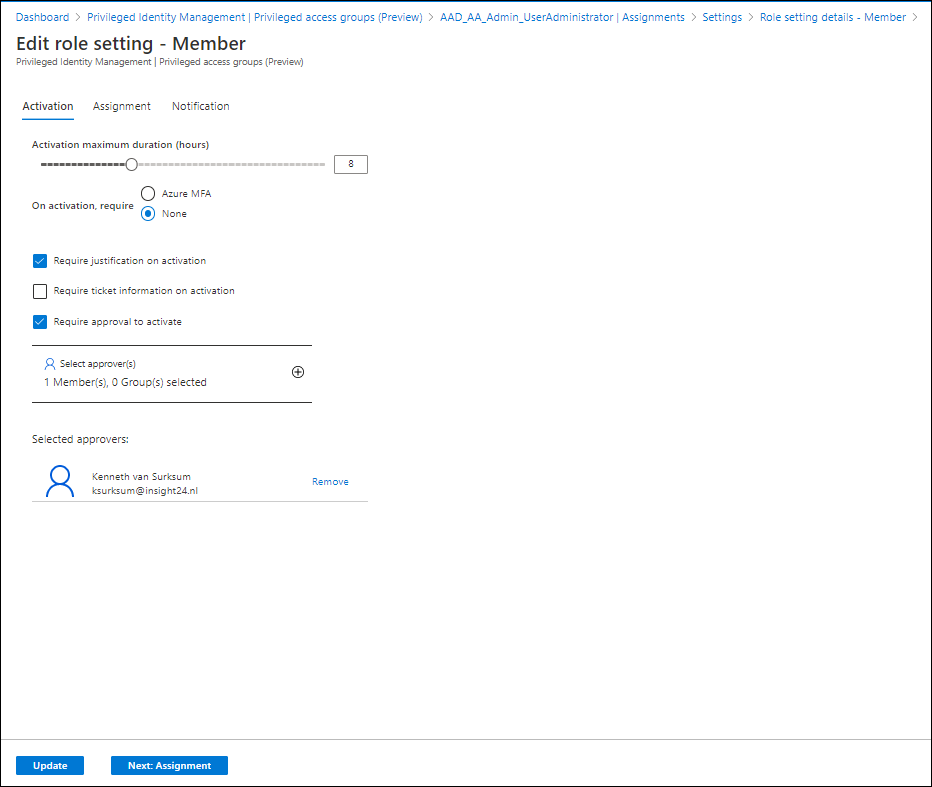
If the user now requests to activate the privileged access group, he will receive the message that the request is pending for approval
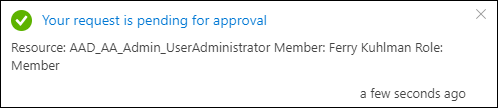
The approver doesn’t see the request under Privileged Identity Management | Approve requests but has to go to Privileged Identity Management | Privileged access groups (Preview) and select the group, from there the Approve Requests functionality is providing the ability to approve the request.
I hope this walkthrough gave you an idea on the new possibilities as announced in the public preview. And there is much more to cover actually when it comes to PIM, like more in depth information about auditing and access reviews.
Microsoft has addressed its own concerns by only allowing Global Administrators and Privileged Role Administrators to create the groups enabled for Azure AD role assignment. And having this functionality combined with Privileged Identity Management (PIM) makes the solution even better. Another reason to buy an Azure AD Premium P2 license for your administrative accounts at least.
A winning feature is that by using Privileged access with Azure AD Groups is that you can enable multiple Azure AD roles at once, this could save you creation of a custom role in some cases when using PIM.
While there are still some little fixes which must be applied, for now this looks like a welcome addition for any Azure AD tenant using Premium functionality.
Assigning groups to Azure AD roles is now in public preview!
Use cloud groups to manage role assignments in Azure Active Directory (preview)
Management capabilities for privileged access Azure AD groups (preview)
2 thoughts on “ Assigning groups to Azure AD roles and Privileged access groups, a first look! ”
- Pingback: Active Directory Identity Governance – Privileged Identity Management - JanBakker.tech
make the Security Admin Role a member Privilege Role Admin in Privilege Identity Management in Azure AD is this possible??
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Privacy Overview
Emilyvanputten.com

Azure AD role-assignable groups
by Emily | Aug 7, 2020 | Azure AD , Privileged Identity Management

Group creation

Assigning Azure AD Roles

Group Perspective

A powershell script for activating an eligible role assignment in Azure AD
By Anatoly Mironov
Recently my role assignments in Azure AD were switched from permanent to eligible ones. This is part of PIM - Privileged Identity Management, you can read more about it on MS Docs:
- Start using Privileged Identity Management
To activate your eligible assignment you can use Azure Portal, Graph API, and PowerShell. The activation in the portal and Graph API is described on MS Docs:
- Activate my Azure AD roles in PIM
My roles within Privileged Identity Management in Azure Portal
I created a simple powershell script for activating my eligible roles quickier when I need it. There are two variants of this script:
- a generic one, that can be run by anyone
- a “shortcut” version that can be created for a specific account, a specific role, to make it even quicker.
A generic version
This version fetches the assignments you have, tenant id (resourcid), your account id (objectid, subjectid), and then it activates your desired role. Some parts can be made even more generic, but the key thing here is that you can adjust it and run for any account.
Shortcut version
This version assumes that you already know all the ids, by running the generic version or by looking it up in Azure. When you know those ids, you can skip many calls to Azure AD, which makes activation quicker and you can start working on your task rather than surfing around to activate your role in Azure.
Save it as a script and run it when you need it. Much quicker. One important note, though: Please be aware that it still can take time to fully activate (propagate) your role, especially SharePoint Administrator, often a couple of minutes. But instead of clicking around, run the script and go grab a cup of coffee, when you’re back, you are good to go.
Security Note. Automating role activations is not less secure. You still have to log in to Azure AD using MFA (I hope you have it) even when you run the script.
- administrator

Assignment Types
At a time when security breaches seem to be an everyday occurrence, it’s become more and more important to protect resources with more than just a username and password. It’s even more important to protect resources from INTERNAL threats. By implementing Azure AD Privileged Identity Management, organizations can protect their resources with improved security features, and even keep an eye on what legitimate administrators are doing.
In this lesson, you’ll learn how to implement Azure AD Privileged Identity Management. We’ll start the lesson by touching on an overview of what Azure AD Privileged Identity Management is and what it offers. We will then work through the deployment of PIM and how it works with multi-factor authentication. As we work through some demos, you will learn how to enable PIM and how to navigate tasks in PIM.
We’ll then cover the activation of roles and the assignment of those roles, including permanent roles and just-in-time roles. We’ll also cover the concepts of updating and removing role assignments, reinforcing these concepts through demonstrations.
We’ll round out the lesson with supported management scenarios, configuring PIM management access, and how to process requests.
Learning Objectives
- Activate a PIM role
- Configure just-in-time resource access
- Configure permanent access to resources
- Configure PIM management access
- Configure time-bound resource access
- Create a Delegated Approver account
- Process pending approval requests
Intended Audience
- People who want to become Azure cloud architects
- People who are preparing to take Microsoft’s AZ-101 exam
Prerequisites
- Moderate knowledge of Azure Active Directory
To see the full range of Microsoft Azure Content, visit the Azure Training Library .
Tom is a 25+ year veteran of the IT industry, having worked in environments as large as 40k seats and as small as 50 seats. Throughout the course of a long an interesting career, he has built an in-depth skillset that spans numerous IT disciplines. Tom has designed and architected small, large, and global IT solutions. In addition to the Cloud Platform and Infrastructure MCSE certification, Tom also carries several other Microsoft certifications. His ability to see things from a strategic perspective allows Tom to architect solutions that closely align with business needs. In his spare time, Tom enjoys camping, fishing, and playing poker.
Azure Privileged Identity Management (PIM)
The Azure Active Directory connector supports Privileged Identity Management (PIM) as a service in Azure Active Directory. PIM enables you to manage, control, and monitor access to important resources in your organization.
These resources include resources in Azure Active Directory, Azure, and other Microsoft Online Services such as Microsoft 365 or Microsoft Intune.
PIM provides time-based and approval-based role activation to mitigate the risks of excessive, unnecessary, or misused access permissions on resources. It reduces the chance of a malicious actor getting access to the resource or an authorized user accidentally impacting a sensitive resource.
Supported Features
Aggregation of PIM Role Assignment objects for Azure and Azure Active Directory during entitlement aggregation of type "Groups"
Aggregation of PIM Role Assignment objects for Azure and Azure Active Directory during Account aggregation
Aggregation of Azure and Azure Active Directory PIM roles during Entitlement Aggregation
Provisioning of eligible role assignment on user for Azure or Azure Active Directory PIM role
Permissions
Azure Active Directory Roles
To communicate with the PIM Graph API for Azure Active Directory roles, you must have at least one of the following permissions:
RoleManagement.ReadWrite.Directory
RoleManagement.Read.Directory
Azure Resource Roles
The PIM API for Azure resource roles is developed on top of the Azure Resource Manager framework. You will need to give consent to Azure Resource Management but won’t need any Graph API permission. You must ensure that the user or the service principal communicating with the API has at least the Owner or User Access Administrator role on the resource.
© SailPoint Technologies, Inc. All Rights Reserved.
Votre plateforme d'emploi accessible et fiable pour tous en RDC
What is Microsoft Azure AD Privileged Identity Management (PIM)?

728x90 (Best VPN)
What is azure ad privileged identity management.
Privileged Identity Management (PIM) is a service in Azure Active Directory (Azure AD) that enables you to manage, control, and monitor access to important resources in your organization. These resources include resources in Azure AD, Azure, and other Microsoft Online Services such as Microsoft 365 or Microsoft Intune. The following video introduces you to important PIM concepts and features.
Reasons to use
Organizations want to minimize the number of people who have access to secure information or resources, because that reduces the chance of
- a malicious actor getting access
- an authorized user inadvertently impacting a sensitive resource
However, users still need to carry out privileged operations in Azure AD, Azure, Microsoft 365, or SaaS apps. Organizations can give users just-in-time privileged access to Azure and Azure AD resources and can oversee what those users are doing with their privileged access.
License requirements
Using this feature requires an Azure AD Premium P2 license. To find the right license for your requirements, see Compare generally available features of Azure AD .
For information about licenses for users, see License requirements to use Privileged Identity Management .
What does it do?
Privileged Identity Management provides time-based and approval-based role activation to mitigate the risks of excessive, unnecessary, or misused access permissions on resources that you care about. Here are some of the key features of Privileged Identity Management:
- Provide just-in-time privileged access to Azure AD and Azure resources
- Assign time-bound access to resources using start and end dates
- Require approval to activate privileged roles
- Enforce multi-factor authentication to activate any role
- Use justification to understand why users activate
- Get notifications when privileged roles are activated
- Conduct access reviews to ensure users still need roles
- Download audit history for internal or external audit
- Prevents removal of the last active Global Administrator and Privileged Role Administrator role assignments
What can I do with it?
Once you set up Privileged Identity Management, you’ll see Tasks , Manage , and Activity options in the left navigation menu. As an administrator, you’ll choose between options such as managing Azure AD roles , managing Azure resource roles, or privileged access groups. When you choose what you want to manage, you see the appropriate set of options for that option.

Who can do what?
For Azure AD roles in Privileged Identity Management, only a user who is in the Privileged Role Administrator or Global Administrator role can manage assignments for other administrators. Global Administrators, Security Administrators, Global Readers, and Security Readers can also view assignments to Azure AD roles in Privileged Identity Management.
For Azure resource roles in Privileged Identity Management, only a subscription administrator, a resource Owner, or a resource User Access administrator can manage assignments for other administrators. Users who are Privileged Role Administrators, Security Administrators, or Security Readers don’t by default have access to view assignments to Azure resource roles in Privileged Identity Management.
Terminology
To better understand Privileged Identity Management and its documentation, you should review the following terms.
Role assignment overview
The PIM role assignments give you a secure way to grant access to resources in your organization. This section describes the assignment process. It includes assign roles to members, activate assignments, approve or deny requests, extend and renew assignments.
PIM keeps you informed by sending you and other participants email notifications . These emails might also include links to relevant tasks, such activating, approve or deny a request.
The following screenshot shows an email message sent by PIM. The email informs Patti that Alex updated a role assignment for Emily.

The assignment process starts by assigning roles to members. To grant access to a resource, the administrator assigns roles to users, groups, service principals, or managed identities. The assignment includes the following data:
- The members or owners to assign the role.
- The scope of the assignment. The scope limits the assigned role to a particular set of resources.
- Eligible assignments require the member of the role to perform an action to use the role. Actions might include activation, or requesting approval from designated approvers.
- Active assignments don’t require the member to perform any action to use the role. Members assigned as active have the privileges assigned to the role.
- The duration of the assignment, using start and end dates or permanent. For eligible assignments, the members can activate or requesting approval during the start and end dates. For active assignments, the members can use the assign role during this period of time.
The following screenshot shows how administrator assigns a role to members.

For more information, check out the following articles: Assign Azure AD roles , Assign Azure resource roles , and Assign eligibility for a privileged access group
If users have been made eligible for a role, then they must activate the role assignment before using the role. To activate the role, users select specific activation duration within the maximum (configured by administrators), and the reason for the activation request.
The following screenshot shows how members activate their role to a limited time.

If the role requires approval to activate, a notification will appear in the upper right corner of the user’s browser informing them the request is pending approval. If an approval isn’t required, the member can start using the role.
For more information, check out the following articles: Activate Azure AD roles , Activate my Azure resource roles , and Activate my privileged access group roles
Approve or deny
Delegated approvers receive email notifications when a role request is pending their approval. Approvers can view, approve or deny these pending requests in PIM. After the request has been approved, the member can start using the role. For example, if a user or a group was assigned with Contribution role to a resource group, they’ll be able to manage that particular resource group.
For more information, check out the following articles: Approve or deny requests for Azure AD roles , Approve or deny requests for Azure resource roles , and Approve activation requests for privileged access group
Extend and renew assignments
After administrators set up time-bound owner or member assignments, the first question you might ask is what happens if an assignment expires? In this new version, we provide two options for this scenario:
- Extend – When a role assignment nears expiration, the user can use Privileged Identity Management to request an extension for the role assignment
- Renew – When a role assignment has already expired, the user can use Privileged Identity Management to request a renewal for the role assignment
Both user-initiated actions require an approval from a Global Administrator or Privileged Role Administrator. Admins don’t need to be in the business of managing assignment expirations. You can just wait for the extension or renewal requests to arrive for simple approval or denial.
For more information, check out the following articles: Extend or renew Azure AD role assignments , Extend or renew Azure resource role assignments , and Extend or renew privileged access group assignments
Privileged Identity Management supports the following scenarios:
Privileged Role Administrator permissions
- Enable approval for specific roles
- Specify approver users or groups to approve requests
- View request and approval history for all privileged roles
Approver permissions
- View pending approvals (requests)
- Approve or reject requests for role elevation (single and bulk)
- Provide justification for my approval or rejection
Eligible role user permissions
- Request activation of a role that requires approval
- View the status of your request to activate
- Complete your task in Azure AD if activation was approved
Managing privileged access Azure AD groups (preview)
In Privileged Identity Management (PIM), you can now assign eligibility for membership or ownership of privileged access groups. Starting with this preview, you can assign Azure Active Directory (Azure AD) built-in roles to cloud groups and use PIM to manage group member and owner eligibility and activation. For more information about role-assignable groups in Azure AD, see Use Azure AD groups to manage role assignments .
To assign a privileged access group to a role for administrative access to Exchange, Security & Compliance Center, or SharePoint, use the Azure AD portal Roles and Administrators experience and not in the Privileged Access Groups experience to make the user or group eligible for activation into the group.
Different just-in-time policies for each group
Some organizations use tools like Azure AD business-to-business (B2B) collaboration to invite their partners as guests to their Azure AD organization. Instead of a single just-in-time policy for all assignments to a privileged role, you can create two different privileged access groups with their own policies. You can enforce less strict requirements for your trusted employees, and stricter requirements like approval workflow for your partners when they request activation into their assigned group.
Activate multiple role assignments in one request
With the privileged access groups preview, you can give workload-specific administrators quick access to multiple roles with a single just-in-time request. For example, your Tier 3 Office Admins might need just-in-time access to the Exchange Admin, Office Apps Admin, Teams Admin, and Search Admin roles to thoroughly investigate incidents daily. Before today it would require four consecutive requests, which are a process that takes some time. Instead, you can create a role assignable group called “Tier 3 Office Admins”, assign it to each of the four roles previously mentioned (or any Azure AD built-in roles) and enable it for Privileged Access in the group’s Activity section. Once enabled for privileged access, you can configure the just-in-time settings for members of the group and assign your admins and owners as eligible. When the admins elevate into the group, they’ll become members of all four Azure AD roles.
Invite guest users and assign Azure resource roles in Privileged Identity Management
Azure Active Directory (Azure AD) guest users are part of the business-to-business (B2B) collaboration capabilities within Azure AD so that you can manage external guest users and vendors as guests in Azure AD. For example, you can use these Privileged Identity Management features for Azure identity tasks with guests such as assigning access to specific Azure resources, specifying assignment duration and end date, or requiring two-step verification on active assignment or activation. For more information on how to invite a guest to your organization and manage their access, see Add B2B collaboration users in the Azure AD portal .
When would you invite guests?
Here are a couple examples of when you might invite guests to your organization:
- Allow an external self-employed vendor that only has an email account to access your Azure resources for a project.
- Allow an external partner in a large organization that uses on-premises Active Directory Federation Services to access your expense application.
- Allow support engineers not in your organization (such as Microsoft support) to temporarily access your Azure resource to troubleshoot issues.
How does collaboration using B2B guests work?
When you use B2B collaboration, you can invite an external user to your organization as a guest. The guest can be managed as a user in your organization, but a guest has to be authenticated in their home organization and not in your Azure AD organization. This means that if the guest no longer has access to their home organization, they also lose access to your organization. For example, if the guest leaves their organization, they automatically lose access to any resources you shared with them in Azure AD without you having to do anything. For more information about B2B collaboration, see What is guest user access in Azure Active Directory B2B? .

- License requirements to use Privileged Identity Management
- Securing privileged access for hybrid and cloud deployments in Azure AD
- Deploy Privileged Identity Management
Recommended content
Start using pim – azure active directory – microsoft entra.
Learn how to enable and get started using Azure AD Privileged Identity Management (PIM) in the Azure portal.
License requirements to use Privileged Identity Management – Azure Active Directory – Microsoft Entra
Describes the licensing requirements to use Azure AD Privileged Identity Management (PIM).
Plan a Privileged Identity Management deployment – Azure AD – Microsoft Entra
Learn how to deploy Privileged Identity Management (PIM) in your Azure AD organization.
Author: Editor
Share this:.
This website uses cookies to improve your experience. We'll assume you're ok with this, but you can opt-out if you wish. Read More

IMAGES
VIDEO
COMMENTS
On the Settings tab, in the Assignment type list, select Eligible or Active. Microsoft Entra PIM for Azure resources provides two distinct assignment types: Eligible assignments require the member to activate the role before using it. Administrator may require role member to perform certain actions before role activation, which might include ...
Here are some of the key features of Privileged Identity Management: Provide just-in-time privileged access to Azure AD and Azure resources. Assign time-bound access to resources using start and end dates. Require approval to activate privileged roles. Enforce multi-factor authentication to activate any role.
Assignment Details; Eligible assignments: The roles that a user is eligible to activate in Azure AD PIM. When a user is designated as eligible for a particular role, they can be assigned it when needed. But, the role is only actively assigned to them once they activate it. Active assignments: The roles that a user has currently activated in ...
Confirm the onboarding of the selected group (s) to Azure AD PIM by selecting OK when prompted. Return to the Azure AD PIM groups page to observe the newly onboarded group. To add a user as an eligible member to the group, select the group name, followed by Assignments in the group page. Select + Add assignment to initiate the configuration ...
You need to make a user eligible for an Azure resource role. Estimated time: 10 minutes Exercise 1 - PIM with Azure resources ... On the Settings tab, under Assignment type, select Eligible. Eligible assignments require the member of the role to perform an action to use the role. Actions might include performing a multi-factor authentication ...
On the group you can assign members or owners using the capabilities provided by PIM. So for example, while adding our user as a member of the group permanently earlier in this article, I now have the option to make the membership Eligible. Also notice that this assignment type is time bound, with a maximum of 1 year. Update assignment options
I am working with the Az and the Graph Powershell Module, getting information about role assignments in Entra ID and Azure Resource Manager. I found that there is two commands each I can use to query information about what user has which eligible role assignments. For Entra ID:
Click a member or group you want to assign to the role and then click Select. The Membership settings pane opens. In the Assignment type list, select Active and click ok. PIM for Azure resources provides two distinct assignment types: Active assignments don't require the member to perform any action to use the role. Members assigned as active ...
In the newly opened window, select under "Select role" the desired role that you want to assign to the group. Click on "Next". Set the desired assignment type (Eligible / Active) and optionally its duration. Then click on "Assign". Role Perspective Open the role you want to assign to (Azure Active Directory> Roles and administrators ...
To activate your eligible assignment you can use Azure Portal, Graph API, and PowerShell. The activation in the portal and Graph API is described on MS Docs: My roles within Privileged Identity Management in Azure Portal. I created a simple powershell script for activating my eligible roles quickier when I need it.
By implementing Azure AD Privileged Identity Management, organizations can protect their resources with improved security features, and even keep an eye on what legitimate administrators are doing. In this lesson, you'll learn how to implement Azure AD Privileged Identity Management.
Provisioning of eligible role assignment on user for Azure or Azure Active Directory PIM role. Operations. Group Objects . Entitlement Aggregation of type "Groups" The following group objects are aggregated as entitlements: Azure Eligible Roles, Azure Active Directory Eligible Roles, Azure Active Roles, and Azure Active Directory Active Roles. ...
Closed 9 months ago. Via PowerShell or API, is there a way to recursively or non-recursively list role assignments for azure resources at (a) given scope (s) and show whether the role assignment is Eligible or Active? The results need to be exportable to a csv file. azure. azure-rbac.
The type of the assignment. Eligible assignments require the member of the role to perform an action to use the role. Actions might include activation, or requesting approval from designated approvers. ... Starting with this preview, you can assign Azure Active Directory (Azure AD) built-in roles to cloud groups and use PIM to manage group ...