From Covert Hiding to Visual Editing: Robust Generative Video Steganography
Traditional video steganography methods are based on modifying the covert space for embedding, whereas we propose an innovative approach that embeds secret message within semantic feature for steganography during the video editing process. Although existing traditional video steganography methods display a certain level of security and embedding capacity, they lack adequate robustness against common distortions in online social networks (OSNs). In this paper, we introduce an end-to-end robust generative video steganography network (RoGVS), which achieves visual editing by modifying semantic feature of videos to embed secret message. We employ face-swapping scenario to showcase the visual editing effects. We first design a secret message embedding module to adaptively hide secret message into the semantic feature of videos. Extensive experiments display that the proposed RoGVS method applied to facial video datasets demonstrate its superiority over existing video and image steganography techniques in terms of both robustness and capacity.
Index Terms — Generative video steganography, Robust steganography, Semantic modification

1 Introduction
Steganography is the science and technology of embedding secret message into natural digital carriers, such as image, video, text, etc. Generally, the natural digital carriers are called “cover” and the digital media with secret message are called “stego”. Conventional image steganography methods [ 49 , 12 , 31 ] primarily modify high-frequency components to embed secret message. They commonly utilize methodologies such as pixel value manipulation or integrating secret message into the cover image before inputting it into an encoder for steganographic purposes.

In the past few years, as the rise of short video software applications like TikTok, YouTube, Snapchat, etc., video has become a suitable carrier for steganography. Traditional video steganographic methods, utilizing direct pixel value manipulation [ 32 ] , coding mapping [ 34 ] , or adaptive distortion function [ 36 ] , exploit video data redundancy for information hiding. Nevertheless, while successful in security and embedding capacity, these methods on modifying covert space can be erased by common post-processing operations easily. So they are vulnerable to mitigate diverse distortions that may occur in lossy channel transmission.

Visual editing on videos can be seen as the process of modifying the semantic information of objects within them. Instead of hiding secret message in covert space, we embed secret message within semantic feature of videos for visual edition. The advanced semantic feature is less susceptible to distortions, making this method inherently robust. In order to improve the robustness of video steganography, we propose an end-to-end robust generative video steganography network (RoGVS), which consists of four modules, containing information encoding module, secret message embedding model, attacking layer, and secret message extraction module. For evaluation, we use face-swapping technology as an example to show the effectiveness of our method, while it can be easily extended to other applications. Comprehensive experiments have showcased that our method surpasses state-of-the-art techniques, attaining commendable robustness and generalization capabilities.
The main contributions of our work are as follows: 1) We are the first to explore a novel generative video steganography method, which modifies semantic feature to embed secret message during visual editing instead of modify the covert space. This framework exhibits strong extensibility, serving as a new topic for the future development of the steganography field. 2) The proposed method is robust against common distortions in social network platform and the secret message can be extracted with high accuracy. 3) Our method achieves better security for anti-steganalysis than other state-of-the-art methods, which can effectively evade the detection of steganalysis system.
2 Related Work
Image Steganography. Conventional image steganography methods primarily modify high-frequency components to embed secret message. The LSB substitution method [ 80 ] operates under the assumption that human eyes cannot perceive changes in the least significant bit of pixel values. HiDDeN [ 12 ] introduces an end-to-end trainable framework through an encoder-decoder architecture. SteganoGAN [ 31 ] employs dense encoders to enhance payload capacity. Wei et al [ 16 ] propose an advanced generative steganography network that can generate realistic stego images without using cover images. However, alterations in high-frequency components can be obliterated by common post-processing operations, such as JPEG compression or Gaussian Blur.
Video Steganography. Early video steganography usually modifies RGB or YUV color spaces for embedding secret message. Dong et al [ 33 ] observed that altering intra-frame modes in HEVC significantly affected video coding efficiency, while modifications to multilevel recursive coding units had minimal distortion impact. PWRN [ 35 ] employs a super-resolution CNN, the Wide Residual-Net filter (PWRN), to replace HEVC’s loop filter. Recently, He et al [ 36 ] devised an adaptive distortion function using enhanced Rate Distortion Optimization (RDO) and Syndrome-Trellis Code (STC) to minimize embedding distortion. However, these methods are struggle to handle various distortions that may arise in lossy channel transmission.
Visual Editing. Visual editing can encompass color correction on a single image, deletion, addition, or alteration of objects within the image, or even merging two photos to create an entirely new scene. In videos, visual editing might involve adding effects to specific frames, removing elements from the video to alter the scene, replacing one person’s face with another [ 26 ] , also called face-swapping.
3 Proposed Approach
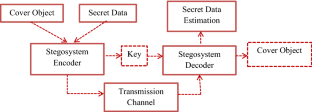
Our method aims to embed secret message 𝑴 𝑴 \bm{M} bold_italic_M using semantic feature extracted from reference image 𝑰 R subscript 𝑰 𝑅 \bm{I}_{R} bold_italic_I start_POSTSUBSCRIPT italic_R end_POSTSUBSCRIPT into cover video 𝑽 C subscript 𝑽 𝐶 \bm{V}_{C} bold_italic_V start_POSTSUBSCRIPT italic_C end_POSTSUBSCRIPT , generating stego video 𝑽 C ′ superscript subscript 𝑽 𝐶 ′ \bm{V}_{C}^{{}^{\prime}} bold_italic_V start_POSTSUBSCRIPT italic_C end_POSTSUBSCRIPT start_POSTSUPERSCRIPT start_FLOATSUPERSCRIPT ′ end_FLOATSUPERSCRIPT end_POSTSUPERSCRIPT . As illustrated in Fig. 2 , our approach comprises four modules: Information Encoding Module, Secret Message Embedding Module, Attacking Layer, Secret Message Extraction Module.
3.1 Information Encoding Module
The information encoding module consists of three parts: The first is identity extractor ( 𝑬 i d ) subscript 𝑬 𝑖 𝑑 \left(\bm{E}_{id}\right) ( bold_italic_E start_POSTSUBSCRIPT italic_i italic_d end_POSTSUBSCRIPT ) which utilizes a facial recognition network to extract identity feature tailored for the reference image ( 𝑰 R ) subscript 𝑰 𝑅 \left(\bm{I}_{R}\right) ( bold_italic_I start_POSTSUBSCRIPT italic_R end_POSTSUBSCRIPT ) . The second is video feature extractor ( 𝑬 ϕ ) subscript 𝑬 italic-ϕ \left(\bm{E}_{\phi}\right) ( bold_italic_E start_POSTSUBSCRIPT italic_ϕ end_POSTSUBSCRIPT ) . It acquires the latent representation of cover video 𝑽 C subscript 𝑽 𝐶 \bm{V}_{C} bold_italic_V start_POSTSUBSCRIPT italic_C end_POSTSUBSCRIPT with v 𝑣 v italic_v frames, employing an encoder [ 26 ] for video feature extraction. The third is secret message encoder ( 𝑬 m ) subscript 𝑬 𝑚 \left(\bm{E}_{m}\right) ( bold_italic_E start_POSTSUBSCRIPT italic_m end_POSTSUBSCRIPT ) which is a one-layer dense Multi-layer Perceptron (MLP). The above three parts are formulated as follows:
where 𝑰 C i subscript superscript 𝑰 𝑖 𝐶 \bm{I}^{i}_{C} bold_italic_I start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT start_POSTSUBSCRIPT italic_C end_POSTSUBSCRIPT is the i 𝑖 i italic_i -th frame of the cover video. 𝑭 C i subscript superscript 𝑭 𝑖 𝐶 \bm{F}^{i}_{C} bold_italic_F start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT start_POSTSUBSCRIPT italic_C end_POSTSUBSCRIPT represents the latent feature representation of i 𝑖 i italic_i -th frame. 𝑭 i d subscript 𝑭 𝑖 𝑑 \bm{F}_{id} bold_italic_F start_POSTSUBSCRIPT italic_i italic_d end_POSTSUBSCRIPT is the identity feature of the reference image. 𝑴 𝑴 \bm{M} bold_italic_M is the secret message. 𝑾 𝒎 subscript 𝑾 𝒎 \bm{W_{m}} bold_italic_W start_POSTSUBSCRIPT bold_italic_m end_POSTSUBSCRIPT and 𝒃 m subscript 𝒃 𝑚 \bm{b}_{m} bold_italic_b start_POSTSUBSCRIPT italic_m end_POSTSUBSCRIPT represents the learnable weights and biases.
3.2 Secret Message Embedding and Extraction Module
This module aims to embed the secret message during face swapping. The key problem is how to implement face swapping under the guidance of secret message. To our understanding, the latent features of the cover video encompass both identity and attribute feature. Face swapping essentially involves replacing the cover video’s identity with that of the reference image. Consequently, we embed the secret message into the identity feature of the reference image, formulated as follows:
where λ 𝜆 \lambda italic_λ is a hyper-parameter adjusting the influence of secret message on identity feature.
Due to strong coupling between identity and attribute features, direct extraction of attribute feature from the latent representation 𝑭 c i superscript subscript 𝑭 𝑐 𝑖 \bm{F}_{c}^{i} bold_italic_F start_POSTSUBSCRIPT italic_c end_POSTSUBSCRIPT start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT by 𝑬 ϕ subscript 𝑬 italic-ϕ \bm{E}_{\phi} bold_italic_E start_POSTSUBSCRIPT italic_ϕ end_POSTSUBSCRIPT is unfeasible. To ensure better attribute preservation, we design a Secret-ID block, consisting of the modified version of the residual block and AdaIN to inject 𝑭 i d i superscript subscript 𝑭 𝑖 𝑑 𝑖 \bm{F}_{id}^{i} bold_italic_F start_POSTSUBSCRIPT italic_i italic_d end_POSTSUBSCRIPT start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT into 𝑭 C i superscript subscript 𝑭 𝐶 𝑖 \bm{F}_{C}^{i} bold_italic_F start_POSTSUBSCRIPT italic_C end_POSTSUBSCRIPT start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT . The Secret-ID block is formulated as follows:
where μ ( 𝑭 C i ) 𝜇 subscript superscript 𝑭 𝑖 𝐶 \mu({\bm{F}^{i}_{C}}) italic_μ ( bold_italic_F start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT start_POSTSUBSCRIPT italic_C end_POSTSUBSCRIPT ) and σ ( 𝑭 C i ) 𝜎 subscript superscript 𝑭 𝑖 𝐶 \sigma({\bm{F}^{i}_{C}}) italic_σ ( bold_italic_F start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT start_POSTSUBSCRIPT italic_C end_POSTSUBSCRIPT ) represent the channel-wise mean and standard deviation of the input feature 𝑭 C i subscript superscript 𝑭 𝑖 𝐶 \bm{F}^{i}_{C} bold_italic_F start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT start_POSTSUBSCRIPT italic_C end_POSTSUBSCRIPT , respectively. Meanwhile, σ 𝑭 i d ′ subscript 𝜎 subscript superscript 𝑭 ′ 𝑖 𝑑 \sigma_{\bm{F}^{\prime}_{id}} italic_σ start_POSTSUBSCRIPT bold_italic_F start_POSTSUPERSCRIPT ′ end_POSTSUPERSCRIPT start_POSTSUBSCRIPT italic_i italic_d end_POSTSUBSCRIPT end_POSTSUBSCRIPT and μ 𝑭 i d ′ subscript 𝜇 subscript superscript 𝑭 ′ 𝑖 𝑑 \mu_{\bm{F}^{\prime}_{id}} italic_μ start_POSTSUBSCRIPT bold_italic_F start_POSTSUPERSCRIPT ′ end_POSTSUPERSCRIPT start_POSTSUBSCRIPT italic_i italic_d end_POSTSUBSCRIPT end_POSTSUBSCRIPT correspond to two variables derived from the secret-identity feature 𝑭 i d ′ subscript superscript 𝑭 ′ 𝑖 𝑑 \bm{F}^{\prime}_{id} bold_italic_F start_POSTSUPERSCRIPT ′ end_POSTSUPERSCRIPT start_POSTSUBSCRIPT italic_i italic_d end_POSTSUBSCRIPT .
After N Secret-ID blocks, the identity feature in 𝑭 C i superscript subscript 𝑭 𝐶 𝑖 \bm{F}_{C}^{i} bold_italic_F start_POSTSUBSCRIPT italic_C end_POSTSUBSCRIPT start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT is replaced by 𝑭 i d ′ subscript superscript 𝑭 ′ 𝑖 𝑑 \bm{F}^{\prime}_{id} bold_italic_F start_POSTSUPERSCRIPT ′ end_POSTSUPERSCRIPT start_POSTSUBSCRIPT italic_i italic_d end_POSTSUBSCRIPT and then we get 𝑭 S i subscript superscript 𝑭 𝑖 𝑆 \bm{F}^{i}_{S} bold_italic_F start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT start_POSTSUBSCRIPT italic_S end_POSTSUBSCRIPT . Subsequently, we use an video Decoder 𝑫 ϕ subscript 𝑫 italic-ϕ \bm{D}_{\phi} bold_italic_D start_POSTSUBSCRIPT italic_ϕ end_POSTSUBSCRIPT to recover the i 𝑖 i italic_i -th frame 𝑰 S i superscript subscript 𝑰 𝑆 𝑖 \bm{I}_{S}^{i} bold_italic_I start_POSTSUBSCRIPT italic_S end_POSTSUBSCRIPT start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT of the stego video from 𝑭 S i subscript superscript 𝑭 𝑖 𝑆 \bm{F}^{i}_{S} bold_italic_F start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT start_POSTSUBSCRIPT italic_S end_POSTSUBSCRIPT . The Decoder contains four upsample blocks, a ReflectionPad layer and a convolutional layer. Each upsample block consists of a upsample layer, a convolutional layer and a BatchNorm layer. The process to get 𝑰 S i subscript superscript 𝑰 𝑖 𝑆 \bm{I}^{i}_{S} bold_italic_I start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT start_POSTSUBSCRIPT italic_S end_POSTSUBSCRIPT can be expressed as 𝑰 S i = 𝑫 ϕ ( 𝑭 S i ) subscript superscript 𝑰 𝑖 𝑆 subscript 𝑫 italic-ϕ subscript superscript 𝑭 𝑖 𝑆 \bm{I}^{i}_{S}=\bm{D}_{\phi}(\bm{F}^{i}_{S}) bold_italic_I start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT start_POSTSUBSCRIPT italic_S end_POSTSUBSCRIPT = bold_italic_D start_POSTSUBSCRIPT italic_ϕ end_POSTSUBSCRIPT ( bold_italic_F start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT start_POSTSUBSCRIPT italic_S end_POSTSUBSCRIPT ) .
We design an extraction module to retrieve secret message 𝑴 ′ superscript 𝑴 ′ \bm{M}^{\prime} bold_italic_M start_POSTSUPERSCRIPT ′ end_POSTSUPERSCRIPT from the stego videos, featuring seven convolutional layers using ReLU activation. Ultimately, a sigmoid activation function and binarization are applied to extract the embedded secret message. This module’s formulation is as 𝑴 ′ = 𝑬 e x t ( 𝑽 S ) superscript 𝑴 ′ subscript 𝑬 𝑒 𝑥 𝑡 subscript 𝑽 𝑆 \bm{M}^{\prime}=\bm{E}_{ext}\left(\bm{V}_{S}\right) bold_italic_M start_POSTSUPERSCRIPT ′ end_POSTSUPERSCRIPT = bold_italic_E start_POSTSUBSCRIPT italic_e italic_x italic_t end_POSTSUBSCRIPT ( bold_italic_V start_POSTSUBSCRIPT italic_S end_POSTSUBSCRIPT ) .
3.3 Attacking Layer
To bolster the robustness of our method for face-swapping videos in real-world scenarios, we design a attacking layer. This module simulates prevalent distortions encountered across social network platforms.
JPEG Compression. JPEG compression involves a non-differentiable quantization step due to rounding. To mitigate this, we apply Shin et al.’s method [ 53 ] to approximate the near-zero quantization step using function Eq. ( 6 ):
where x 𝑥 x italic_x denotes pixels of the input image. We uniformly sample the JPEG quality from within the range of [50, 100].
Color Distortions. We consider two general color distortions: brightness and contrast. We perform a linear transformation on the pixels of each channel as the formula Eq. ( 7 ):
where 𝒑 ( 𝒙 ) 𝒑 𝒙 \bm{p(x)} bold_italic_p bold_( bold_italic_x bold_) and 𝒇 ( 𝒙 ) 𝒇 𝒙 \bm{f(x)} bold_italic_f bold_( bold_italic_x bold_) refers to the distorted and the original image. The parameters 𝒂 𝒂 \bm{a} bold_italic_a and 𝒄 𝒄 \bm{c} bold_italic_c regulate contrast and brightness, respectively.
Color Saturation. We perform random linear interpolation between RGB and gray images equivalent to simulate the distortion.
Additive Noise. We use Gaussian noise to simulate any other distortions that are not considered in the attacking layer. We employ a Gaussian noise model (sampling the standard deviation δ ∼ U [ 0 , 0.2 ] ) \delta\sim U[0,0.2]) italic_δ ∼ italic_U [ 0 , 0.2 ] ) to simulate imaging noise.
3.4 Loss Function
The proposed method ensures both high stego video quality and precise extraction of secret message. We achieve this by training the modules using the following losses.
Identity Loss . The identity loss minimizes the variance between the identity features ( 𝑭 i d subscript 𝑭 𝑖 𝑑 \bm{F}_{id} bold_italic_F start_POSTSUBSCRIPT italic_i italic_d end_POSTSUBSCRIPT ) of the reference image and the i 𝑖 i italic_i -th frame ( 𝑭 ^ i d i superscript subscript ^ 𝑭 𝑖 𝑑 𝑖 \hat{\bm{F}}_{id}^{i} over^ start_ARG bold_italic_F end_ARG start_POSTSUBSCRIPT italic_i italic_d end_POSTSUBSCRIPT start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT ) in the stego video, reducing alterations caused by secret message. Cosine similarity is used to measure this loss by the formula Eq ( 8 ).
Attribute Loss. We use the weak feature matching loss [ 26 ] to constrain attribute difference before and after embedding secret message. The loss function is defined as follows:
where 𝑫 j subscript 𝑫 𝑗 \bm{D}_{j} bold_italic_D start_POSTSUBSCRIPT italic_j end_POSTSUBSCRIPT refers to the feature extractor of Discriminator D for the j-th layer, N j subscript 𝑁 𝑗 N_{j} italic_N start_POSTSUBSCRIPT italic_j end_POSTSUBSCRIPT is the number of elements in the j-th layer, and H 𝐻 H italic_H is the total number of layers. Additionally, h ℎ h italic_h represents the starting layer for computing the weak feature matching loss.
Adversarial Loss. To enhance performance, we use multi-scale Discriminator with gradient penalty. We adopt the Hinge version of adversarial loss defined as follows:
where 𝑫 𝑫 \bm{D} bold_italic_D denotes the Discriminator, x 𝑥 x italic_x and z 𝑧 z italic_z in our method is respectively 𝑰 R subscript 𝑰 𝑅 \bm{I}_{R} bold_italic_I start_POSTSUBSCRIPT italic_R end_POSTSUBSCRIPT and 𝑰 S i superscript subscript 𝑰 𝑆 𝑖 \bm{I}_{S}^{i} bold_italic_I start_POSTSUBSCRIPT italic_S end_POSTSUBSCRIPT start_POSTSUPERSCRIPT italic_i end_POSTSUPERSCRIPT
Secret Loss. To address this, we use the Binary Cross-Entropy loss (BCE) as defined in Eq. ( 11 ).
Total loss. The total loss is defined as follows:
4 Experiments
4.1 experimental setups.
Datasets. We use Vggface2 [ 61 ] for training and FFHQ [ 15 ] for validation. We crop and resize facial areas to a fixed 224 × \times × 224 resolution for input images. To analyze quality and performance, we randomly select 100 videos from DeepFake MNIST+ [ 65 ] to evaluate the performance.
Implementation Details. We train the model to encode a binary message of length m 𝑚 m italic_m = 9 or 18 bits in a frame. During training, we employ Adam optimizer with a learning rate of 4 × 10 − 4 4 superscript 10 4 4\times 10^{-4} 4 × 10 start_POSTSUPERSCRIPT - 4 end_POSTSUPERSCRIPT and a batch size of 4. We set α 1 = 10 subscript 𝛼 1 10 \alpha_{1}=10 italic_α start_POSTSUBSCRIPT 1 end_POSTSUBSCRIPT = 10 , α 2 = 10 subscript 𝛼 2 10 \alpha_{2}=10 italic_α start_POSTSUBSCRIPT 2 end_POSTSUBSCRIPT = 10 , α 3 = 15 subscript 𝛼 3 15 \alpha_{3}=15 italic_α start_POSTSUBSCRIPT 3 end_POSTSUBSCRIPT = 15 , and α 4 = 10 − 5 subscript 𝛼 4 superscript 10 5 \alpha_{4}=10^{-5} italic_α start_POSTSUBSCRIPT 4 end_POSTSUBSCRIPT = 10 start_POSTSUPERSCRIPT - 5 end_POSTSUPERSCRIPT . The networks train for 1 million steps, integrating the Attacking Layer after the initial 800k steps for stability. We use an NVIDIA GeForce RTX 3090 GPU for our experiments.

Evaluation Metrics. We employ Bits Per Frame (BPF), quantifying the bits number of secret message per frame in the stego video. To assess robustness, we evaluate secret message extraction accuracy under various scenarios. For security assessment, we use three steganalysis methods [ 62 , 63 , 64 ] to demonstrate our method’s anti-detection capability.
Baselines. To ensure fair comparison in our experiments, we align HiDDeN and LSB to this capacity. Detailed methods of HiDDeN and LSB are available in the supplementary materials. Additionally, due to its PU-based design, PWRN has a limited capacity of 15 BPF when resizing input images to 224 × 224 224 224 224\times 224 224 × 224 .
4.2 Performance Analysis
We compare the performance of our RoGVS with image-level steganography including HiDDeN [ 12 ] and LSB [ 80 ] and video-level steganography including PWRN [ 35 ] .
Video Quality Assessment. Fig 4 shows qualitative results on the integrity of generated video frames. We perform tests within and across datasets, each containing 16 test samples. The generated faces effectively change individual identities while retaining attributes like expressions and poses. More findings are available in the supplementary materials. Fig 3 illustrates the visual effects of certain intermittent frames within the stego videos.
Comparisons on Extraction Accuracy & Robustness. We conduct extensive experiments with multiple types of distortions. Detailed distortion implementations are provided in the supplement.
The quantitative comparison results in terms of accuracy are reported in Table 1 . The results show that our method can successfully extract secret message with high accuracy even after severe distortions. LSB [ 80 ] struggles even with PNG (quantization) and HiDDeN [ 12 ] , though trained with a distortion module, can not generalize well to video-level distortions. PWRN [ 35 ] demonstrates robustness across numerous distortions, yet its performance remains constrained under operations such as motion blur or contrast adjustment. The proposed RoGVS method shows superior robustness to these distortions while maintaining high extraction accuracy. Security Analysis. We use three video steganalysis tools to evaluate the security of our method. The detection performance of these three steganalysis schemes is presented in Table 4 . Table 4 demonstrates that our method exhibits slightly superior security compared to the three counterparts.
4.3 Ablation Study
Embedding Position of Secret Message. In our generation network with 9 Secret-ID blocks, we explore different positions for embedding the secret message. We divide the secret message into two 9-bit segments and allocate their positions. In detail, Setting (a): 1st-4th blocks and 5th-9th blocks. Setting (b): 1st-2nd blocks and 3rd-4th blocks. Setting (c): 5th-6th blocks and 7th-8th blocks. They are in comparison of the standard setting of RoGVS: 1st-3rd blocks and 4th-6th blocks.
Table 2 displays the performance for these four setups. Both Settings b and c show a considerable decrease compared to Settings a and d, suggesting that adding more Secret-ID blocks improves performance. Notably, Setting c outperforms Setting b, indicating the higher influence of subsequent blocks on the generated image.
Ablation on Attacking Layer, λ 𝜆 \lambda italic_λ & Discriminator. Fig 5 shows even without the module, our method demonstrates considerable robustness, surpassing the three comparative methods. The addition of attacking layer improves accuracy by an average of 6%.

Table 3 presents the impact of λ 𝜆 \lambda italic_λ on the extraction accuracy. More ablation results on λ 𝜆 \lambda italic_λ and the discriminator are displayed in the supplement.
5 Conclusions
We propose a robust generative video steganography method based on visual editing, which modifies semantic feature to embed secret message. We use face-swapping scenario as an example to show the effectiveness of our RoGVS. The results showcase that our method can generate high-quality visually edited stego videos. What’s more, RoGVS outperforms existing video and image steganography methods in robustness and capacity.
- [1] Authors, “The frobnicatable foo filter,” ACM MM 2013 submission ID 324. Supplied as additional material acmmm13.pdf .
- [2] Authors, “Frobnication tutorial,” 2012, Supplied as additional material tr.pdf .
- [3] J. W. Cooley and J. W. Tukey, “An algorithm for the machine computation of complex Fourier series,” Math. Comp. , vol. 19, pp. 297–301, Apr. 1965.
- [4] S. Haykin, “Adaptive filter theory,” Information and System Science. Prentice Hall, 4th edition, 2002.
- [5] Dennis R. Morgan, “Dos and don’ts of technical writing,” IEEE Potentials , vol. 24, no. 3, pp. 22–25, Aug. 2005.
- [6] Vojtěch Holub and Jessica Fridrich, “Designing steganographic distortion using directional filters,” in 2012 IEEE International workshop on information forensics and security (WIFS) . IEEE, 2012, pp. 234–239.
- [7] Vojtěch Holub, Jessica Fridrich, and Tomáš Denemark, “Universal distortion function for steganography in an arbitrary domain,” EURASIP Journal on Information Security , vol. 2014, pp. 1–13, 2014.
- [8] Bin Li, Ming Wang, Jiwu Huang, and Xiaolong Li, “A new cost function for spatial image steganography,” in 2014 IEEE International conference on image processing (ICIP) . IEEE, 2014, pp. 4206–4210.
- [9] Mahdi Ahmadi, Alireza Norouzi, Nader Karimi, Shadrokh Samavi, and Ali Emami, “Redmark: Framework for residual diffusion watermarking based on deep networks,” Expert Systems with Applications , vol. 146, pp. 113157, 2020.
- [10] Junpeng Jing, Xin Deng, Mai Xu, Jianyi Wang, and Zhenyu Guan, “Hinet: deep image hiding by invertible network,” in Proceedings of the IEEE/CVF international conference on computer vision , 2021, pp. 4733–4742.
- [11] Shao-Ping Lu, Rong Wang, Tao Zhong, and Paul L Rosin, “Large-capacity image steganography based on invertible neural networks,” in Proceedings of the IEEE/CVF conference on computer vision and pattern recognition , 2021, pp. 10816–10825.
- [12] Jiren Zhu, Russell Kaplan, Justin Johnson, and Li Fei-Fei, “Hidden: Hiding data with deep networks,” in Proceedings of the European conference on computer vision (ECCV) , 2018, pp. 657–672.
- [13] Andrew Brock, Jeff Donahue, and Karen Simonyan, “Large scale gan training for high fidelity natural image synthesis,” arXiv preprint arXiv:1809.11096 , 2018.
- [14] Tero Karras, Timo Aila, Samuli Laine, and Jaakko Lehtinen, “Progressive growing of gans for improved quality, stability, and variation,” arXiv preprint arXiv:1710.10196 , 2017.
- [15] Tero Karras, Samuli Laine, and Timo Aila, “A style-based generator architecture for generative adversarial networks,” in Proceedings of the IEEE/CVF conference on computer vision and pattern recognition , 2019, pp. 4401–4410.
- [16] Ping Wei, Sheng Li, Xinpeng Zhang, Ge Luo, Zhenxing Qian, and Qing Zhou, “Generative steganography network,” in Proceedings of the 30th ACM International Conference on Multimedia , 2022, pp. 1621–1629.
- [17] Han Zhang, Ian Goodfellow, Dimitris Metaxas, and Augustus Odena, “Self-attention generative adversarial networks,” in International conference on machine learning . PMLR, 2019, pp. 7354–7363.
- [18] Donghui Hu, Liang Wang, Wenjie Jiang, Shuli Zheng, and Bin Li, “A novel image steganography method via deep convolutional generative adversarial networks,” IEEE access , vol. 6, pp. 38303–38314, 2018.
- [19] Zhuo Zhang, Guangyuan Fu, Rongrong Ni, Jia Liu, and Xiaoyuan Yang, “A generative method for steganography by cover synthesis with auxiliary semantics,” Tsinghua Science and Technology , vol. 25, no. 4, pp. 516–527, 2020.
- [20] Zhuo Zhang, Jia Liu, Yan Ke, Yu Lei, Jun Li, Minqing Zhang, and Xiaoyuan Yang, “Generative steganography by sampling,” IEEE access , vol. 7, pp. 118586–118597, 2019.
- [21] Zhian Liu, Maomao Li, Yong Zhang, Cairong Wang, Qi Zhang, Jue Wang, and Yongwei Nie, “Fine-grained face swapping via regional gan inversion,” in Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition , 2023, pp. 8578–8587.
- [22] Yi-Ting Cheng, Virginia Tzeng, Yu Liang, Chuan-Chang Wang, Bing-Yu Chen, Yung-Yu Chuang, and Ming Ouhyoung, “3d-model-based face replacement in video,” in SIGGRAPH’09: Posters , pp. 1–1. 2009.
- [23] Justus Thies, Michael Zollhofer, Marc Stamminger, Christian Theobalt, and Matthias Nießner, “Face2face: Real-time face capture and reenactment of rgb videos,” in Proceedings of the IEEE conference on computer vision and pattern recognition , 2016, pp. 2387–2395.
- [24] Yuval Nirkin, Yosi Keller, and Tal Hassner, “Fsgan: Subject agnostic face swapping and reenactment,” in Proceedings of the IEEE/CVF international conference on computer vision , 2019, pp. 7184–7193.
- [25] Lingzhi Li, Jianmin Bao, Hao Yang, Dong Chen, and Fang Wen, “Faceshifter: Towards high fidelity and occlusion aware face swapping,” arXiv preprint arXiv:1912.13457 , 2019.
- [26] Renwang Chen, Xuanhong Chen, Bingbing Ni, and Yanhao Ge, “Simswap: An efficient framework for high fidelity face swapping,” in Proceedings of the 28th ACM International Conference on Multimedia , 2020, pp. 2003–2011.
- [27] Zhili Zhou, Xiaohua Dong, Ruohan Meng, Meimin Wang, Hongyang Yan, Keping Yu, and Kim-Kwang Raymond Choo, “Generative steganography via auto-generation of semantic object contours,” IEEE Transactions on Information Forensics and Security , 2023.
- [28] Zichi Wang, Guorui Feng, Hanzhou Wu, and Xinpeng Zhang, “Data hiding during image processing using capsule networks,” Neurocomputing , vol. 537, pp. 49–60, 2023.
- [29] Shilpa Gupta, Geeta Gujral, and Neha Aggarwal, “Enhanced least significant bit algorithm for image steganography,” IJCEM International Journal of Computational Engineering & Management , vol. 15, no. 4, pp. 40–42, 2012.
- [30] Amritpal Singh and Harpal Singh, “An improved lsb based image steganography technique for rgb images,” in 2015 IEEE International Conference on electrical, computer and communication technologies (ICECCT) . IEEE, 2015, pp. 1–4.
- [31] Kevin Alex Zhang, Alfredo Cuesta-Infante, Lei Xu, and Kalyan Veeramachaneni, “Steganogan: High capacity image steganography with gans,” arXiv preprint arXiv:1901.03892 , 2019.
- [32] Ozdemir Cetin and A Turan Ozcerit, “A new steganography algorithm based on color histograms for data embedding into raw video streams,” computers & security , vol. 28, no. 7, pp. 670–682, 2009.
- [33] Yi Dong, Tanfeng Sun, and Xinghao Jiang, “A high capacity hevc steganographic algorithm using intra prediction modes in multi-sized prediction blocks,” in Digital Forensics and Watermarking: 17th International Workshop, IWDW 2018, Jeju Island, Korea, October 22-24, 2018, Proceedings 17 . Springer, 2019, pp. 233–247.
- [34] Jindou Liu, Zhaohong Li, Xinghao Jiang, and Zhenzhen Zhang, “A high-performance cnn-applied hevc steganography based on diamond-coded pu partition modes,” IEEE Transactions on Multimedia , vol. 24, pp. 2084–2097, 2021.
- [35] Zhonghao Li, Xinghao Jiang, Yi Dong, Laijin Meng, and Tanfeng Sun, “An anti-steganalysis hevc video steganography with high performance based on cnn and pu partition modes,” IEEE Transactions on Dependable and Secure Computing , vol. 20, no. 1, pp. 606–619, 2022.
- [36] Songhan He, Dawen Xu, Lin Yang, and Weipeng Liang, “Adaptive hevc video steganography with high performance based on attention-net and pu partition modes,” IEEE Transactions on Multimedia , 2023.
- [37] Jiankang Deng, Jia Guo, Niannan Xue, and Stefanos Zafeiriou, “Arcface: Additive angular margin loss for deep face recognition,” in Proceedings of the IEEE/CVF conference on computer vision and pattern recognition , 2019, pp. 4690–4699.
- [38] Max Jaderberg, Karen Simonyan, Andrew Zisserman, et al., “Spatial transformer networks,” Advances in neural information processing systems , vol. 28, 2015.
- [39] Nuur Alifah Roslan, Nur Izura Udzir, Ramlan Mahmod, and Adnan Gutub, “Systematic literature review and analysis for arabic text steganography method practically,” Egyptian Informatics Journal , 2022.
- [40] Nadia A Karim, Suhad A Ali, and Majid Jabbar Jawad, “A coverless image steganography based on robust image wavelet hashing,” TELKOMNIKA (Telecommunication Computing Electronics and Control) , vol. 20, no. 6, pp. 1317–1325, 2022.
- [41] Sheng Li, Zichi Wang, Xiudong Zhang, and Xinpeng Zhang, “Robust image steganography against general downsampling operations with lossless secret recovery,” IEEE Transactions on Dependable and Secure Computing , 2023.
- [42] Mahmoud M Mahmoud and Huwaida T Elshoush, “Enhancing lsb using binary message size encoding for high capacity, transparent and secure audio steganography–an innovative approach,” IEEE Access , vol. 10, pp. 29954–29971, 2022.
- [43] Omer Farooq Ahmed Adeeb and Seyed Jahanshah Kabudian, “Arabic text steganography based on deep learning methods,” IEEE Access , vol. 10, pp. 94403–94416, 2022.
- [44] M Hassan Shirali-Shahreza and Mohammad Shirali-Shahreza, “Text steganography in chat,” in 2007 3rd IEEE/IFIP International Conference in Central Asia on Internet . IEEE, 2007, pp. 1–5.
- [45] B Delina, “Information hiding: A new approach in text steganography,” in Proceedings of the International Conference on Applied Computer and Applied Computational Science, World Scientific and Engineering Academy and Society (WSEAS 2008) , 2008, pp. 689–695.
- [46] Fatiha Djebbar, Beghdad Ayad, Habib Hamam, and Karim Abed-Meraim, “A view on latest audio steganography techniques,” in 2011 International Conference on Innovations in Information Technology . IEEE, 2011, pp. 409–414.
- [47] Kaliappan Gopalan, “Audio steganography using bit modification,” in 2003 International Conference on Multimedia and Expo. ICME’03. Proceedings (Cat. No. 03TH8698) . IEEE, 2003, vol. 1, pp. I–629.
- [48] Fatiha Djebbar, Beghdad Ayad, Karim Abed Meraim, and Habib Hamam, “Comparative study of digital audio steganography techniques,” EURASIP Journal on Audio, Speech, and Music Processing , vol. 2012, no. 1, pp. 1–16, 2012.
- [49] Zhengxin You, Qichao Ying, Sheng Li, Zhenxing Qian, and Xinpeng Zhang, “Image generation network for covert transmission in online social network,” in Proceedings of the 30th ACM International Conference on Multimedia , 2022, pp. 2834–2842.
- [50] Ting-Chun Wang, Ming-Yu Liu, Jun-Yan Zhu, Andrew Tao, Jan Kautz, and Bryan Catanzaro, “High-resolution image synthesis and semantic manipulation with conditional gans,” in Proceedings of the IEEE conference on computer vision and pattern recognition , 2018, pp. 8798–8807.
- [51] Anish Athalye, Logan Engstrom, Andrew Ilyas, and Kevin Kwok, “Synthesizing robust adversarial examples,” in International conference on machine learning . PMLR, 2018, pp. 284–293.
- [52] Danying Hu, Daniel DeTone, and Tomasz Malisiewicz, “Deep charuco: Dark charuco marker pose estimation,” in Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition , 2019, pp. 8436–8444.
- [53] Richard Shin and Dawn Song, “Jpeg-resistant adversarial images,” in NIPS 2017 Workshop on Machine Learning and Computer Security , 2017, vol. 1, p. 8.
- [54] Matthew Tancik, Ben Mildenhall, and Ren Ng, “Stegastamp: Invisible hyperlinks in physical photographs,” in Proceedings of the IEEE/CVF conference on computer vision and pattern recognition , 2020, pp. 2117–2126.
- [55] Kaiming He, Xiangyu Zhang, Shaoqing Ren, and Jian Sun, “Deep residual learning for image recognition,” in Proceedings of the IEEE conference on computer vision and pattern recognition , 2016, pp. 770–778.
- [56] Xun Huang and Serge Belongie, “Arbitrary style transfer in real-time with adaptive instance normalization,” in Proceedings of the IEEE international conference on computer vision , 2017, pp. 1501–1510.
- [57] Ming-Yu Liu, Xun Huang, Arun Mallya, Tero Karras, Timo Aila, Jaakko Lehtinen, and Jan Kautz, “Few-shot unsupervised image-to-image translation,” in Proceedings of the IEEE/CVF international conference on computer vision , 2019, pp. 10551–10560.
- [58] Taesung Park, Ming-Yu Liu, Ting-Chun Wang, and Jun-Yan Zhu, “Semantic image synthesis with spatially-adaptive normalization,” in Proceedings of the IEEE/CVF conference on computer vision and pattern recognition , 2019, pp. 2337–2346.
- [59] Jonas Adler and Sebastian Lunz, “Banach wasserstein gan,” Advances in neural information processing systems , vol. 31, 2018.
- [60] Ishaan Gulrajani, Faruk Ahmed, Martin Arjovsky, Vincent Dumoulin, and Aaron C Courville, “Improved training of wasserstein gans,” Advances in neural information processing systems , vol. 30, 2017.
- [61] Qiong Cao, Li Shen, Weidi Xie, Omkar M Parkhi, and Andrew Zisserman, “Vggface2: A dataset for recognising faces across pose and age,” in 2018 13th IEEE international conference on automatic face & gesture recognition (FG 2018) . IEEE, 2018, pp. 67–74.
- [62] Liming Zhai, Lina Wang, and Yanzhen Ren, “Universal detection of video steganography in multiple domains based on the consistency of motion vectors,” IEEE transactions on information forensics and security , vol. 15, pp. 1762–1777, 2019.
- [63] Zhonghao Li, Laijing Meng, Shutong Xu, Zhaohong Li, Yunqing Shi, and Yuanchang Liang, “A hevc video steganalysis algorithm based on pu partition modes.,” Computers, Materials & Continua , vol. 59, no. 2, 2019.
- [64] Q Sheng, RD Wang, ML Huang, Q Li, and D Xu, “A prediction mode steganalysis detection algorithm for hevc,” J Optoelectron-laser , vol. 28, no. 4, pp. 433–440, 2017.
- [65] Jiajun Huang, Xueyu Wang, Bo Du, Pei Du, and Chang Xu, “Deepfake mnist+: a deepfake facial animation dataset,” in Proceedings of the IEEE/CVF International Conference on Computer Vision , 2021, pp. 1973–1982.
- [66] Xiyao Liu, Ziping Ma, Junxing Ma, Jian Zhang, Gerald Schaefer, and Hui Fang, “Image disentanglement autoencoder for steganography without embedding,” in Proceedings of the IEEE/CVF conference on computer vision and pattern recognition , 2022, pp. 2303–2312.
- [67] Robert Engelmore and Anthony Morgan, Eds., Blackboard Systems , Addison-Wesley, Reading, Mass., 1986.
- [68] William J. Clancey, “Communication, Simulation, and Intelligent Agents: Implications of Personal Intelligent Machines for Medical Education,” in Proceedings of the Eighth International Joint Conference on Artificial Intelligence (IJCAI-83) , Menlo Park, Calif, 1983, pp. 556–560, IJCAI Organization.
- [69] William J. Clancey, “Classification Problem Solving,” in Proceedings of the Fourth National Conference on Artificial Intelligence , Menlo Park, Calif., 1984, pp. 45–54, AAAI Press.
- [70] Arthur L. Robinson, “New ways to make microcircuits smaller,” Science , vol. 208, no. 4447, pp. 1019–1022, 1980.
- [71] Arthur L. Robinson, “New Ways to Make Microcircuits Smaller—Duplicate Entry,” Science , vol. 208, pp. 1019–1026, 1980.
- [72] Diane Warner Hasling, William J. Clancey, and Glenn Rennels, “Strategic explanations for a diagnostic consultation system,” International Journal of Man-Machine Studies , vol. 20, no. 1, pp. 3–19, 1984.
- [73] Diane Warner Hasling, William J. Clancey, Glenn R. Rennels, and Thomas Test, “Strategic Explanations in Consultation—Duplicate,” The International Journal of Man-Machine Studies , vol. 20, no. 1, pp. 3–19, 1983.
- [74] James Rice, “Poligon: A System for Parallel Problem Solving,” Technical Report KSL-86-19, Dept. of Computer Science, Stanford Univ., 1986.
- [75] William J. Clancey, Transfer of Rule-Based Expertise through a Tutorial Dialogue , Ph.D. diss., Dept. of Computer Science, Stanford Univ., Stanford, Calif., 1979.
- [76] William J. Clancey, “The Engineering of Qualitative Models,” Forthcoming, 2021.
- [77] Mathieu Bouville, “Crime and punishment in scientific research,” 2008.
- [78] NASA, “Pluto: The ’other’ red planet,” \url https://www.nasa.gov/nh/pluto-the-other-red-planet, 2015, Accessed: 2018-12-06.
- [79] Andreas Rossler, Davide Cozzolino, Luisa Verdoliva, Christian Riess, Justus Thies, and Matthias Nießner, “Faceforensics++: Learning to detect manipulated facial images,” in Proceedings of the IEEE/CVF international conference on computer vision , 2019, pp. 1–11.
- [80] Chi-Kwong Chan and Lee-Ming Cheng, “Hiding data in images by simple lsb substitution,” Pattern recognition , vol. 37, no. 3, pp. 469–474, 2004.
- [81] Yu Wang, Yun Cao, Xianfeng Zhao, Zhoujun Xu, and Meineng Zhu, “Maintaining rate-distortion optimization for ipm-based video steganography by constructing isolated channels in hevc,” in Proceedings of the 6th ACM workshop on information hiding and multimedia security , 2018, pp. 97–107.
- [82] Haiwei Wu, Jiantao Zhou, Jinyu Tian, and Jun Liu, “Robust image forgery detection over online social network shared images,” in Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition , 2022, pp. 13440–13449.
- [83] Shichao Dong, Jin Wang, Renhe Ji, and et al., “Implicit identity leakage: The stumbling block to improving deepfake detection generalization,” in CVPR , 2023.
- [84] Wenliang Zhao, Yongming Rao, Weikang Shi, and et al., “Diffswap: High-fidelity and controllable face swapping via 3d-aware masked diffusion,” in CVPR , 2023.
- [85] Zhendong Wang, Jianmin Bao, and et al., “Altfreezing for more general video face forgery detection,” in CVPR , 2023.
Universal Detection of Video Steganography in Multiple Domains Based on the Consistency of Motion Vectors
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.

A review of steganography techniques
- Article contents
- Figures & tables
- Supplementary Data
- Peer Review
- Reprints and Permissions
- Cite Icon Cite
- Search Site
Ali Mahmood Khalaf , Kamaljit Lakhtaria; A review of steganography techniques. AIP Conf. Proc. 16 February 2024; 3051 (1): 040005. https://doi.org/10.1063/5.0191705
Download citation file:
- Ris (Zotero)
- Reference Manager
Due to the importance, security, confidentiality, privacy, and progress of information at present due to the development in the field of information technology, sharing this information (text, image, audio, video) has become a critical problem due to the exposure of this information to penetration by attacking parties, and to solve the problem of penetration, many technologies have appeared to protect This information (text, image, audio, video) is cryptography algorithms and information steganography techniques. Steganography is a science that maintains the confidentiality of information (text, image, audio, video) between two communicating parties (the sender and the receiver), and it is a science that studies the invisible communication of information. In this paper, the researcher reviewed the most important techniques of previous studies for the last six years, such as LSB, PVD, DFT, DWT, DCT, Masking & Filtering, Distortion, and Statistical. In the science of hiding information, and analyzing it in terms of technical domain, invisibility, capacity, and complexity, all of these techniques can hide this information from hostile attacks. In this paper, the evaluation criteria for hiding the information (text, image, audio, video) were reviewed in terms of imperceptibility, robustness, capacity, and security. Also, the most important applications of hiding techniques (text, image, audio, video) were reviewed in this paper.
Sign in via your Institution
Citing articles via, publish with us - request a quote.

Sign up for alerts
- Online ISSN 1551-7616
- Print ISSN 0094-243X
- For Researchers
- For Librarians
- For Advertisers
- Our Publishing Partners
- Physics Today
- Conference Proceedings
- Special Topics
pubs.aip.org
- Privacy Policy
- Terms of Use
Connect with AIP Publishing
This feature is available to subscribers only.
Sign In or Create an Account
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
video-steganography
Here are 21 public repositories matching this topic..., zhanghong863 / feature-extractors-for-video-steganalysis.
To provide the stego community with C/C++ implementations of selected feature extractors mainly targeted at H.264 steganography.
- Updated Jun 2, 2021
Priyansh-15 / Steganography-Tools
A project named "STEGANOGRAPHY TOOLS " that provide 4 types of Steganography { Image, Text, Audio, Video } that hides User's Text message in the desired cover file using the tool and can send it to the receiver who can extract the Hidden message using the same tool .
- Updated Nov 25, 2023
anilsathyan7 / Deep-Video-Steganography-Hiding-Videos-in-Plain-Sight
- Updated Nov 20, 2020
itxKAE / Video-Steganography
School Assignment
- Updated Oct 31, 2020
Akshay-Arjun / Video-Steganography
AES 256 & RSA encrypted video steganography. SRU Hackathon 2022 - Cybersecurity Winners
- Updated Jan 6, 2024
Sanjipan / Steganography
A Advance Steganography Tool made with Python The Program Supports Hiding Secret Text data into an innocent looking cover file like : .mp4, .wav, .png, .jpeg, .txt through the use of Steganography Theory.
- Updated Feb 25, 2023
Kunal-Attri / Data-Security-using-Cryptography-and-Steganography
Improved way of securing data using combined Steganography and Cryptographic techniques
- Updated Jul 25, 2023

petermcneil / lodge
A video steganography tool; combining video files and subtitles
- Updated Jul 26, 2021
mightymoogle / StegoVideoDemo
Video Steganography / Watermarking Demo Tool
- Updated Jan 16, 2022
williamprout / NetworkVideoSteganography
Program that uses steganography and cryptography to hide a video file within another video file without noticeably effecting the appearance of the video. Networking component to securely send encoded files over a network.
- Updated Apr 6, 2022
Abanteeka / Steganography
A Advance Steganography Tool made with Python The Program Supports Hiding Secret Text data into an innocent looking cover file like : .mp4, .wav, .png, .jpeg, .txt through the use of Steganography Theory
koustubh1317 / Steganography-Tools
This project "STEGANOGRAPHY TOOLS" showcases algorithms to hide text message in four different cover file (Text, Image, Audio, Video) and transfer it to the receiver who can extract the hidden message from these files with the same tools.
- Updated Oct 27, 2022
- Jupyter Notebook
Prince326 / VideoSteganography-using-python3
- Updated Apr 9, 2020
DLarisa / Dissertation
Dissertation for master of Security and Applied Logic at FMI, UniBuc (Video Steganography - Topic)
- Updated Jul 11, 2023
olaitanade / stegaspy
Video steganography project for windows in wpf.
- Updated Dec 2, 2019
hrichharms / dct_coefficients_analysis
Explores both the relationships between discrete cosine transform (DCT) coefficients as well as the variation in DCT coefficients across popular video codecs with a focus on improving and optimizing DCT-based steganographic systems.
- Updated Jul 29, 2022
shrutityagi4102 / Information-Security-IA1
Video Steganography in Python for our Information Security Internal Assessment 1
- Updated Feb 23, 2023
HeeyaAmin / Steganography_Vid
I am thrilled to delve into the captivating realm of video steganography, driven by a fervent interest in concealing secret image data within cover videos. My project involves a meticulous process of selecting specific frames and applying the tried-and-true LSB techniques to seamlessly embed information.
- Updated Jun 9, 2023
createunique / STEGANOGRAPHY_HIDDEN_HARBOR
Explore a versatile Python repository enabling seamless steganography across Text, Image, Audio, GIF, and Video formats.
- Updated Apr 24, 2024
nishant-kumarr / Hidden_Layer
- Updated May 4, 2024
Improve this page
Add a description, image, and links to the video-steganography topic page so that developers can more easily learn about it.
Curate this topic
Add this topic to your repo
To associate your repository with the video-steganography topic, visit your repo's landing page and select "manage topics."
Advertisement
A survey on information hiding using video steganography
- Published: 09 February 2021
- Volume 54 , pages 5831–5895, ( 2021 )
Cite this article

- Mukesh Dalal ORCID: orcid.org/0000-0002-3473-6652 1 &
- Mamta Juneja 1
2122 Accesses
24 Citations
1 Altmetric
Explore all metrics
In the last few decades, information security has gained huge importance owing to the massive growth in digital communication; hence, driving steganography to the forefront for secure communication. Steganography is a practice of concealing information or message in covert communication which involves hiding the information in any multimedia file such as text, image, or video. Many contributions have been made in the domain of image steganography; however, due to the low embedding capacity and robustness of images; videos are gaining more attention of academic researchers. This paper aims to provide a qualitative as well as quantitative analysis of various video steganography techniques by highlighting their properties, challenges, pros, and cons. Moreover, different quality metrics for the evaluation of distinct steganography techniques have also been discussed. The paper also provides an overview of steganalysis attacks which are commonly employed to test the security of the steganography techniques. The experimental analysis of some of the prominent techniques using different quality metrics has also been done. This paper also presented a critical analysis driven from the literature and the experimental results. The primary objective of this paper is to help the beginners to understand the basic concepts of this research domain to initiate their research in this field. Further, the paper highlighted the real-life applications of video steganography and also suggested some future directions which require the attention of the research community.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others

Video steganography: recent advances and challenges
Compressed and raw video steganography techniques: a comprehensive survey and analysis.

Digital Video Steganography: An Overview
Abbass AS, Soleit EA, Ghoniemy SA (2007) Blind video data hiding using integer wavelet transforms. Ubiquitous Comput Commun J 2(1):11–25
Google Scholar
Abdolmohammadi M, Toroghi RM, Bastanfard A (2019) Video steganography using 3D convolutional neural networks. Paper presented at Mediterranean conference on pattern recognition and artificial intelligence. pp. 149–161
Abu-El-Haija S, Kothari N, Lee J, Natsev P, Toderici G, Varadarajan B, Vijayanarasimhan S (2016) Youtube-8m: a large-scale video classification benchmark. arXiv Prepr. arXiv1609.08675
Ahmed EAE, Soliman HH, Mostafa HE (2014) Information hiding in video files using frequency domain. Int J Sci Res 3(6):2431–2437
Al-Frajat AK, Jalab HA, Kasirun ZM, Zaidan AA, Zaidan BB (2010) Hiding data in video file: an overview. J Appl Sci 10:1644–1649
Article Google Scholar
Aljahdali H, Townend P, Xu J (2013) Enhancing multi-tenancy security in the cloud IaaS model over public deployment. Paper presented at IEEE 7th International Symposium on in Service Oriented System Engineering (SOSE), 385–390
Aly HA (2011) Data hiding in motion vectors of compressed video based on their associated prediction error. IEEE Trans Inf Forensics Secur 6(1):14–18
Amirtharajan R, Rayappan JBB (2013) Steganography-time to time: a review. Res J Inform Technol 5:53–66
Asikuzzaman M, Pickering MR (2018) An overview of digital video watermarking. IEEE Trans Circuits Syst Video Technol 28(9):2131–2153
Babaguchi N, Cavallaro A, Chellappa R, Dufaux F, Wang L (2013) Guest editorial: special issue on intelligent video surveillance for public security and personal privacy. IEEE Trans Inf Forensics Secur 8(10):1559–1561
Balaji R, Naveen G (2011) Secure data transmission using video Steganography. Paper presented at IEEE International Conference in Electro/Information Technology (EIT). pp. 1–5
Balu S, Babu CNK, Amudha K (2018) Secure and efficient data transmission by video steganography in medical imaging system. Cluster Comput. 22(2):1–7
Bancroft FC, Clelland C (2001) DNA-based steganography. Google Patents, 2001
Bandyopadhyay SK, Bhattacharyya D, Ganguly D, Mukherjee S, Das P (2008) A tutorial review on steganography. Int Conf Contemp Comput 101:105–114
Bhattacharyya D, Bhaumik AK, Choi M, Kim TH (2010) Directed graph pattern synthesis in LSB technique on video steganography. Lect Notes Comput Sci 6059(1996):61–69
Bhautmage P, Jeyakumar A, Dahatonde A (2013) Advanced video steganography algorithm. Int J Eng Res Appl 3:1641–1644
Bo P, Jie Y (2018) A Reversible information hiding method based on HEVC. IFAC-PapersOnLine 51(17):238–243
Braun H, Lamothe E, Letort D (2018) Introduction: Les cultures ado, consommation et production. Publije, no. 1
Cao Y, Zhao X, Feng D, Sheng R (2011) Video steganography with perturbed motion estimation. In International workshop on information hiding. Springer, Berlin, Heidelberg, pp. 193–207
Cao Y, Zhao X, Feng D (2012) Video steganalysis exploiting motion vector reversion-based features. IEEE Signal Process Lett 19(1):35–38
Cao Y, Zhang H, Zhao X, Yu H (2015) Covert communication by compressed videos exploiting the uncertainty of motion estimation. IEEE Commun Lett 19(2):203–206
Cetin O, Ozcerit AT (2009) A new steganography algorithm based on color histograms for data embedding into raw video streams. Comput Secur 28(7):670–682
Chae JJ, Manjunath BS (1999) Data hiding in video. In: Proceedings of the 1999 International Conference on image processing. Vol. 1, pp. 311–315
Chandramouli R (2003) Steganography capacity: a steganalysis perspective. Proc SPIE. pp. 173–177
Chantrapornchai C, Churin K, Preechasuk J, Adulkasem S (2014) Video Steganography For Hiding Image With Wavelet Coefficients. Int J Multimed Ubiquitous Eng 9(6):385–396
Cheddad A, Condell J, Curran K, Mc Kevitt P (2010) Digital image steganography: survey and analysis of current methods. Signal Process 90(3):727–752
Article MATH Google Scholar
Chen S, Qu Z (2018) Novel quantum video steganography and authentication protocol with large payload. Int J Theor Phys 57(12):3689–3701
Choubey S, Bansal A (2014) Video steganography using neural network methods. Int J Res Advent Technol 2(2)
Cimpanu C (2016) Steganography is very popular with exploit kits all of a sudden [Online]. https://www.bleepingcomputer.com/news/security/steganography-is-very-popular-with-exploit-kits-all-of-a-sudden/ . Accessed 13 Dec 2017
Dalal M, Juneja M (2016) Overview of video steganography in compressed domain. Int J Comput Technol Appl 9(10):1–11
Dalal M, Juneja M (2018) Video steganalysis to obstruct criminal activities for digital forensics: a survey. Int J Electron Secur Digit Forensics 10(4):338–355
Dalal M, Juneja M (2018) Video steganography techniques in spatial domain-a survey. In: Proceedings of the international conference on computing and communication systems, Springer, Singapore. pp. 705–711
Dalal M, Juneja M (2019) A robust and imperceptible steganography technique for SD and HD videos. Multimed Tools Appl 78(5):5769–5789
Dalal M, Juneja M (2020) Evaluation of orthogonal and biorthogonal wavelets for video steganography. Inf Secur J A Glob Perspect 29(1):1–11
Darmstaedter V, Delaigle J-F, Quisquater J-J, Macq B (1998) Low cost spatial watermarking. Comput Graph 22(4):417–424
Dasgupta K, Mandal JK, Dutta P (2012) Hash based least significant bit technique for video steganography (HLSB). Int J Secur Priv Trust Manag 1(2):1–11
Dasgupta K, Mondal JK, Dutta P (2013) Optimized video steganography using Genetic Algorithm (GA). Procedia Technol 10:131–137
Easttom C (2017) System forensics, investigation, and response. Jones & Bartlett Learning, Burlington
Engineer arrested for attempted theft of trade secrets, Dark Reading (2017) [Online]. https://www.darkreading.com/vulnerabilities---threats/engineer-arrested-for-attempted-theft-of-trade-secrets/d/d-id/1328635 . Accessed 03 Feb 2019
Esen E, Alatan AA (2011) Robust video data hiding using forbidden zone data hiding and selective embedding. IEEE Trans Circuits Syst Video Technol 21(8):1130–1138
Fan M, Liu P, Wang H, Sun X (2016) Cross correlation feature mining for steganalysis of hash based least significant bit substitution video steganography. Telecommun Syst. 63:1–7
Faragallah OS (2013) Efficient video watermarking based on singular value decomposition in the discrete wavelet transform domain. AEU Int J Electron Commun 67(3):189–196
Ferreira AM (2015) An overview on hiding and detecting stego-data in video streams. [Online]. https://homepages.staff.os3.nl/~delaat/rp/2014-2015/p66/report.pdf . Accessed 12 Sep 2016
Firmansyah DM and, Ahmad T (2016) An improved neighbouring similarity method for video steganography. Paper presented at 4th international conference on cyber and IT service management, pp. 1–5
Forczmański P, Wekegrzyn M (2008) Virtual steganographic laboratory for digital images. Inf Syst Archit Technol Inf Syst Comput Commun Networks Wrocław Pol. pp. 163–174
Fridrich J, Goljan M (2002) Practical steganalysis of digital images: state of the art. Electronic Imaging 2002:1–13
Fridrich J, Goljan M, Soukal D (2003) Higher-order statistical steganalysis of palette images. Proc SPIE 5020:178–190
Fu P-W, Wu C-C, Cho Y-J (2017) What makes users share content on facebook? Compatibility among psychological incentive, social capital focus, and content type. Comput Human Behav 67:23–32
Furuta T, Noda H, Niimi M, Kawaguchi E (2003) Bit-plane decomposition steganography using wavelet compressed video. In: proceedings of the 2003 joint conference of the fourth international conference on information, communications and signal processing, 2003 and fourth pacific Rim conference on multimedia. Vol. 2. pp. 970–974
Galiano DR, Del Barrio AA, Botella G, Cuesta D (2020) Efficient embedding and retrieval of information for high-resolution videos coded with HEVC. Comput Electr Eng 81:106541
Gallagher S (2012) Steganography: how al-Qaeda hid secret documents in a porn video. [Online]. https://arstechnica.com/business/2012/05/steganography-how-al-qaeda-hid-secret-documents-in-a-porn-video/ . Accessed 01 Jul 2016
Gross MJ (2011) Exclusive: operation shady RAT: unprecedented cyber-espionage campaign and intellectual-property bonanza. Vanity Fair, vol. 2
Gujjunoori S, Amberker BB (2013) DCT based reversible data embedding for MPEG-4 video using HVS characteristics. J Inf Secur Appl 18(4):157–166
Gupta H, Chaturvedi DS (2013) Video data hiding through LSB substitution technique. Res Inven Int J Eng Sci 2(10):32–39
Gupta H, Chaturvedi S (2014) Video steganography through LSB based hybrid approach. Int J Comput Sci Netw Secur 14(3):99–106
H.264/AVC. [Online]. https://en.wikipedia.org/wiki/H.264/MPEG-4_AVC . Accessed 21 Nov 2016
Hanafy AA, Salama GI, Mohasseb YZ (2005) A secure covert communication model based on video steganography. In: Proceedings of the IEEE MILCOM Military Communication Conference. pp. 1–6, 2008
Hashemzadeh M (2018) Hiding information in videos using motion clues of feature points. Comput Electr Eng 68:14–25
He Y, Yang G, Zhu N (2012) A real-time dual watermarking algorithm of H. 264/AVC video stream for video-on-demand service. AEU International J Electron Commun 66(4):305–312
Holmes B (2015) Steganography: how Antonopoulos hid a US$100m transaction in a picture of kittens. [Online]. https://bravenewcoin.com/news/steganography-how-antonopoulos-hid-a-us12m-transaction-in-a-picture-of-kittens/ . Accessed 13 Dec 2017
Hu, SD KTU, “A novel video steganography based on non-uniform rectangular partition,” Proc. - 14th IEEE Int. Conf. Comput. Sci. Eng. CSE 2011 11th Int. Symp. Pervasive Syst. Algorithms, Networks, I-SPA 2011 10th IEEE Int. Conf. IUCC 2011 , pp. 57–61, 2011.
Hussain M, Wahab AWA, Bin Idris YI, Ho ATS, Jung K-H (2018) Image steganography in spatial domain: a survey. Signal Process Image Commun 65:46–66
Idbeaa T, Samad SA, Husain H (2016) A secure and robust compressed domain video steganography for intra-and inter-frames using embedding-based byte differencing (EBBD) scheme. PLoS ONE 11(3):e0150732
Jiang B, Yang G, Chen W (2015) A CABAC based HEVC video steganography algorithm without bitrate increase. J Comput Inf Syst 11(6):2121–2130
Johnson NF, Jajodia S (1998) Exploring steganography: seeing the unseen. IEEE Comput 31(2):26–34
Johnson NF, Duric Z, Jajodia S (2001) Information hiding: steganography and watermarking-attacks and countermeasures: steganography and watermarking: attacks and countermeasures. Springer, Berlin
Book Google Scholar
Jue W, Min-qing Z, S. Juan-li S (2011) Video steganography using motion vector components. In: proceedings of the IEEE 3rd international conference on communication software and networks (ICCSN), pp. 500–503
Kamil S, Ayob M, Abdullah SNHS, Ahmad Z (2018) Optimized data hiding in complemented or non-complemented form in video steganography. Cyber Resilience Conf 2018:1–4
Kapoor V, Mirza A (2015) An enhanced LSB based video steganographic system for secure and efficient data transmission. Int J Comput Appl 121(10):38–42
Kaur R (2016) Kaur S (2016) XOR-EDGE based video steganography and testing against Chi-square steganalysis. Int J Image Graph Signal Process 8(9):31–39
Kaur M, Kaur A (2014) Improved security mechanism of text in video using steganographic technique. Int J Adv Res Comput Sci Softw Eng. vol. 2, no. 10
Kaur K, Kaur B (2018) DWT-LSB approach for video steganography using artificial neural network. Int. Adv. Res. J. Sci. Eng. Technol, IARJSET
Kelash HM, Wahab OFA, Elshakankiry OA, El-sayed HS (2014) Utilization of steganographic techniques in video sequences. Int J Comput Netw Technol 24(1):17–24
Kelley J (2001) Terrorist instructions hidden online, [Online]. http://usatoday30.usatoday.com/tech/news/2001-02-05-binladen-side.htm . Accessed 05 Jul 2016
Ker T, Andrew D, Bas, Bohme P, Cogranne R, Craver R, Filler S, Fridrich T, Pevny J (2013) Moving steganography and steganalysis from the laboratory into the real world. Proceedings of the first ACM workshop on Information hiding and multimedia security. pp. 45–58
Kessler GC (2004) Steganography: implications for the prosecutor and computer forensics examiner. American Prosecution Reasearch Institute
Khare R, Mishra R, Arya I (2014) Video steganography using LSB technique by neural network. Int Conf Comput Intell Commun Netw 2014:898–902
Khosla S, Kaur P (2014) Secure data hiding technique using video steganography and watermarking. Int J Comput Appl 95(20):7–12
Kolakalur A, Kagalidis I, Vuksanovic B, Iacsit M (2016) Wavelet based color video steganography. Int J Eng Technol 8(3):165
Konyar MZ, Akbulut O, Öztürk S (2020) Matrix encoding-based high-capacity and high-fidelity reversible data hiding in HEVC. Signal Image Video Process 14:1–9
Kopeytsev V (2020) Steganography in attacks on industrial enterprises, Kaspersky ICS CERT, [Online]. https://ics-cert.kaspersky.com/reports/2020/06/17/steganography-in-attacks-on-industrial-enterprises/ . Accessed 07 Jul 2020
Krenn R (2004) Steganography and steganalysis. Retrieved Sept 8:1–9
Kulkarni A, Goldman J, Nabholz B, Eyre W (2009) Detection of steganography-producing software artifacts on crime-related seized computers. J Digit Forensics Secur Law 4(2):5–26
Kumar P, Singh K (2018) An improved data-hiding approach using skin-tone detection for video steganography. Multimed Tools Appl 77(18):24247–24268
Le Gall D (1991) MPEG: a video compression standard for multimedia applications. Commun ACM 34(4):46–58
Lie W-N, Lin T-I, Lin C-W (2006) Enhancing video error resilience by using data-embedding techniques. IEEE Trans Circuits Syst Video Technol 16(2):300–308
Lin TJ, Chung KL, Chang PC, Huang YH, Liao HYM, Fang CY (2013) An improved DCT-based perturbation scheme for high capacity data hiding in H.264/AVC intra frames. J Syst Softw 86(3):604–614
Liu S, Xu D (2020) A robust steganography method for HEVC based on secret sharing. Cogn Syst Res 59:207–220
Liu B, Liu F, Lu B, Luo X (2006) Real-time steganography in compressed video. Paper presented at international workshop on multimedia content representation, classification and security, pp. 43–48
Liu B, Liu F, Ni D (2006) Adaptive compressed video steganography in the VLC-domain. Paper presented at 2006 IET international conference on wireless, mobile and multimedia networks. pp. 1–4
Liu B, Liu F, Yang C, Sun Y (2008) Secure steganography in compressed video bitstreams. Paper presented at 3rd international conference on ARES Availability, Reliability and Security. pp. 1382–1387
Liu Y, Hu M, Ma X, Zhao H (2015) A new robust data hiding method for H. 264/AVC without intra-frame distortion drift. Neurocomputing 151:1076–1085
Liu Y, Ju L, Hu M, Zhao H, Jia S, Jia Z (2016) A new data hiding method for H.264 based on secret sharing. Neurocomputing 188:113–119
Liu Y, Liu S, Zhao H, Liu S (2019) A new data hiding method for H. 265/HEVC video streams without intra-frame distortion drift. Multimed Tools Appl 78(6):6459–6486
Lu Y, Lu C, Qi M (2010) An effective video steganography method for biometric identification. Lect Notes Comput Sci 6059:469–479
Luo W, Huang F, Huang J (2010) Edge adaptive image steganography based on LSB matching revisited. IEEE Trans Inf forensics Secur 5(2):201–214
Luo T, Jiang G, Yu M, Xu H (2016) Asymmetric self-recovery oriented stereo image watermarking method for three dimensional video system. Multimed Syst 22(5):641–655
Luo T, Jiang G, Yu M, Xu H, Gao W (2017) Sparse recovery based reversible data hiding method using the human visual system. Multimed Tools Appl 77(15):1–24
Luo T, Zuo L, Jiang G, Gao W, Xu H, Jiang Q (2020) Security of MVD-based 3D video in 3D-HEVC using data hiding and encryption. J Real-Time Image Process 17(4):773–785
Ma X, Li Z, Tu H, Zhang B (2010) A data hiding algorithm for h.264/AVC video streams without intra-frame distortion drift. IEEE Trans Circuits Syst Video Technol 20(10):1320–1330
Mandal JK (2016) Handbook of research on natural computing for optimization problems. IGI Global, Pennsylvania
Manikandan G, Bala Krishnan R, Rajesh Kumar N, Sairam N, Raajan NR (2017) A steganographic approach for realizing medical data privacy in a distributed environment. Biomed Res 28(3)
Manisha S, Sharmila TS (2019) A two-level secure data hiding algorithm for video steganography. Multidimens Syst Signal Process 30(2):529–542
Mazurczyk W, Caviglione L (2015) Information hiding as a challenge for malware detection. arXiv Prepr. arXiv1504.04867
Mazurczyk W, Wendzel S, Zander S, Houmansadr A, Szczypiorski K (2016) Information hiding in communication networks: fundamentals, mechanisms, applications, and countermeasures, vol 7. Wiley, New Jersey
Mielikainen J (2006) LSB matching revisited. IEEE Signal Process Lett 13(5):285–287
Mollin RA (2000) An introduction to cryptography. CRC Press, Florida
MATH Google Scholar
Moon SK, Raut RD (2013) “Analysis of secured video steganography using computer forensics technique for enhance data security”, 2013 IEEE 2nd Int . Conf Image Inf Process IEEE ICIIP 2013:660–665
Mstafa RJ, Elleithy KM (2014) A highly secure video steganography using Hamming code (7, 4). IEEE Long Isl Syst Appl Technol Conf LISAT 2014:2014
Mstafa RJ, Elleithy KM (2015a) “A high payload video steganography algorithm in DWT domain based on BCH codes (15, 11)”, in. Wireless Telecommun Symp 2015:1–8
Mstafa RJ, Elleithy KM (2015) A new video steganography algorithm based on the multiple object tracking and Hamming codes. Paper presented at IEEE 14th International Conference on Machine Learning and Applications (ICMLA), pp. 335–340
Mstafa RJ, Elleithy KM (2016) A video steganography algorithm based on Kanade-Lucas-Tomasi tracking algorithm and error correcting codes. Multimed Tools Appl 75(17):10311–10333
Mstafa RJ, Elleithy KM (2016a) An ECC/DCT-based robust video steganography algorithm for secure data communication. J Cyber Secur Mobil 5(3):167–194
Mstafa RJ, Elleithy KM (2017) Compressed and raw video steganography techniques: a comprehensive survey and analysis. Multimed Tools Appl 76(20):21749–21786
Mstafa RJ, K. M. Elleithy KM (2016) A DCT-based robust video steganographic method using BCH error correcting codes. Paper presented at 2016 IEEE Long Island Systems, Applications and Technology Conference (LISAT), pp. 1–6
Mstafa RJ, Elleithy KM, Abdelfattah E (2017a) A robust and secure video steganography method in DWT-DCT domains based on multiple object tracking and ECC. IEEE Access 5:5354–5365
Mstafa RJ, Elleithy KM, Abdelfattah E (2017) Video steganography techniques: taxonomy, challenges, and future directions. Paper presented at systems, applications and technology conference (LISAT) IEEE Long Island. pp. 1–6
Mumthas S, Lijiya A (2017) Transform domain video steganography using RSA, random DNA encryption and Huffman encoding. Procedia Comput Sci 115:660–666
Mstafa RJ, Ellleithy KM (2015) An efficient video steganography algorithm based on BCH codes. Paper presented at Northeast Sect Conf Am Soc Eng Educ, no. May 2015
Narayanan KL, Prabakaran G, Bhavani R (2012) A high capacity video steganography based on integer wavelet transform. J Comput Appl 5(EICA2012-4):358–365
Neuner S, Voyiatzis AG, Schmiedecker M, Brunthaler S, Katzenbeisser S, Weippl ER (2016) Time is on my side: steganography in filesystem metadata. Digit Investig 18:S76–S86
Newman LH (2018) Mysterious ‘MuslimCrypt’ app helps jihadists send covert messages, Wired, [Online]. https://www.wired.com/story/muslimcrypt-steganography/ . Accessed 03 Feb 2019
News B (2016) FBI allegations against ‘Russian spies’ in US. [Online]. http://www.bbc.com/news/10442869 . Accessed 16 Aug 2016
Nichols S (2019) A picture tells a 1,000 words. Pixels pwn up to 5 million nerds: Crims use steganography to stash bad code in ads, The Register [Online]. https://www.theregister.co.uk/2019/01/24/mac_steganography_malware/ . Accessed 03 May 2020
Nie Q, Weng J, Xu X, Feng B (2018) Defining embedding distortion for intra prediction mode-based video steganography. Comput Mater Contin 55:59–70
Noda H, Furuta T, Niimi M, Kawaguchi E (2004) Application of BPCS steganography to wavelet compressed video. In proceedings of the International conference on image processing. ICIP. Vol. 4, no. 1, pp. 2147–2150
Ohm J-R, Sullivan GJ, Schwarz H, Tan TK, Wiegand T (2012) Comparison of the coding efficiency of video coding standards-including high efficiency video coding (HEVC). IEEE Trans circuits Syst video Technol 22(12):1669–1684
Ostermann J, Bormans J, List P, Marpe D, Narroschke M, Pereira F, Stockhammer T, Wedi T (2004) Video coding with H. 264/AVC: tools, performance, and complexity. IEEE Circuits Syst Mag 4(1):7–28
Pan F, Xiang L, Yang X, Guo Y (2010) Video steganography using motion vector and linear block codes. Paper presented at IEEE international conference on software engineering and service sciences. No. 60842006, pp. 592–595
Papadopoulos NA, Psannis KE (2018) Sequential Multiple LSB methods and real-time data hiding: variations for Visual Cryptography ciphers. J Real-Time Image Process 14(1):75–86
Patel K, Rora KK, Singh K, Verma S (2013) Lazy wavelet transform based steganography in video. In: Proceedings of 2013 International Conference on Communication Systems and Network Technologies (CSNT). pp. 497–500
Paul R, Acharya AK, Yadav VK, Batham S (2013) Hiding large amount of data using a new approach of video steganography,” in Confluence 2013: The Next Generation Information Technology Summit (4th International Conference), 2013, pp. 337–343.
Perumal K, Muthusamy S, Gengavel G (2018) Sparse data encoder and decoder to improve security in video steganography. Concurr Comput Pract Exp 31:1–7
Petitcolas FAP, Anderson RJ, Kuhn MG (1999) Information hiding-a survey. Proc IEEE 87(7):1062–1078
Pevny T, Fridrich J (2008) Benchmarking for steganography. Paper presented at international workshop on information hiding. pp. 251–267
Pfitzmann B (1996) Information hiding terminology-results of an informal plenary meeting and additional proposals. In: Proceedings of the first international workshop on information hiding. pp. 347–350
Pilania U, Gupta P (2020) “Analysis and implementation of IWT-SVD scheme for video steganography”, in micro-electronics and telecommunication engineering. Springer, Singapore
Pinson MH, Wolf S (2004) A new standardized method for objectively measuring video quality. IEEE Trans Broadcast 50(3):312–322
Qu Z, Chen S, Ji S (2017) A novel quantum video steganography protocol with large payload based on MCQI quantum video. Int J Theor Phys 56(11):3543–3561
Rabie T, Baziyad M (2019) The Pixogram: addressing high payload demands for video steganography. IEEE Access 7:21948–21962
Raggo MT, Hosmer C (2012) Data hiding: exposing concealed data in multimedia, operating systems, mobile devices and network protocols. Newnes, Oxford
Rajalakshmi K, Mahesh K (2018) ZLBM: zero level binary mapping technique for video security. Multimed Tools Appl 77(11):13225–13247
Ramalingam M (2011) Stego machine–video steganography using modified LSB algorithm. World Acad Sci Eng Technol 74:502–505
Ramalingam M, Isa NAM (2014) Video steganography based on integer Haar wavelet transforms for secured data transfer. Indian J Sci Technol 7(7):897–904
Ramalingam M, Isa NAM (2015) A steganography approach over video images to improve security. Indian J Sci Technol 8(1):79–86
Ramalingam M, Isa NAM (2016) A data-hiding technique using scene-change detection for video steganography. Comput Electr Eng 54:423–434
Ramalingam M, Ashidi N, Isa M (2015) Fast retrieval of hidden data using enhanced hidden Markov model in video steganography. Appl Soft Comput J 34:744–757
Rashmi N, Jyothi K (2018) An improved method for reversible data hiding steganography combined with cryptography. In: Proceedings of the 2nd international conference on inventive systems and control (ICISC), pp. 81–84
Reisslein M (2012) Video trace library. Arizona State University. http//trace. eas. asu. edu. Accessed 2012
Ren Y, Zhai L, Wang L, Zhu T (2014) Video steganalysis based on subtractive probability of optimal matching feature. In: Proceedings of the 2nd ACM workshop on Information hiding and multimedia security. pp. 83–90
Rezagholipour K, Eshghi M (2016) Video steganography algorithm based on motion vector of moving object. Paper presented at eighth international conference on information and knowledge technology (IKT), pp. 183–187
Richardson IE (2004) H.264 and MPEG-4 video compression: video coding for next-generation multimedia. John Wiley & Sons, New Jersey
Robie DL, Mersereau RM (2001) Video error correction using steganography. In: Proceedings of the International Conference on Image Processing (Cat. No.01CH37205), vol. 1, pp. 164–173
Roque JJ, Minguet JM (2009) SLSB: improving the Steganographic Algorithm LSB. In WOSIS, 2009, pp. 57–66
Rowland CH (1997) Covert channels in the TCP/IP protocol suite. First Monday, vol. 2, no. 5
“S-tools.” [Online]. Available: http://www.jjtc.com/stegdoc/sec316.html . Accessed: 26 Aug 2016
Sabeti V, Samavi S, Mahdavi M, Shirani S (2007) Steganalysis of pixel-value differencing steganographic method. Paper presented at IEEE Pacific Rim Conference on Communications, Computers and Signal Processing, pp. 292–295
Sadat ES, Faez K, Saffari Pour M (2018) Entropy-based video steganalysis of motion vectors. Entropy 20(4):244–257
Sadek MM, Khalifa AS, Mostafa MGM (2015) Video steganography: a comprehensive review. Multimed Tools Appl 74(17):7063–7094
Sadek MM, Khalifa AS, Mostafa MGM (2017) Robust video steganography algorithm using adaptive skin-tone detection. Multimed Tools Appl 76(2):3065–3085
Santhosh B, Meghana NM (2016) A robust, privacy preserving secret data concealing embedding technique into encrypted video stream. Information systems design and intelligent application, Springer, pp. 645–655
Shanableh T (2012) Matrix encoding for data hiding using multilayer video coding and transcoding solutions. Signal Process Image Commun 27(9):1025–1034
Shanableh T (2012) Data hiding in MPEG video files using multivariate regression and flexible macroblock ordering. IEEE Trans Inf Forensics Secur 7(2):455–464
Shannon CE (2001) A mathematical theory of communication. ACM SIGMOBILE Mob Comput Commun Rev 5(1):3–55
Article MathSciNet Google Scholar
Sheri S, Traoudas B (2017) Video brand storytelling, the rise of content marketing: a qualitative study exploring the antecedents of brand perceptions
Sherley AP, Amritha PP (2010) A compressed video steganography using TPVD. Int J Database Manag Syst 2(3):67–80
Shimanovsky B, Feng J, M. Potkonjak M (2002) Hiding data in DNA. Paper presented at International Workshop on Information Hiding, pp. 373–386
Shou-dao W, Chuang-bai X, Yu L (2009) A High Bitrate Information Hiding Algorithm for Video in Video. World Acad Sci Eng Technol 35:413–418
Sikora T (1997) MPEG digital video-coding standards. IEEE Signal Process Mag 14(5):82–100
Solutions N (2005) Invisible secrets 4. Invis, Secrets
Song G, Li Z, Zhao J, Tu H, Cheng J (2014) A video steganography algorithm for MVC without distortion drift. Paper presented at international conference on audio, language and image processing (ICALIP), pp. 738–742
Song G, Li Z, Zhao J, Hu J, Tu H (2015) A reversible video steganography algorithm for MVC based on motion vector. Multimed Tools Appl 74(11):3759–3782
Stanescu D, Stratulat M, Ciubotaru B, Chiciudean D, Cioarga R, Micea M (2007) Embedding data in video stream using steganography. Paper presented at 4th international symposium on applied computational intelligence and informatics. pp. 241–244
Steganography — the new intelligence threat EWS 2004 subject area intelligence marine corps war college , Marine Corps University , Marine Corps, 2004
Stütz T, Autrusseau F, Uhl A (2013) Inter-frame H. 264/CAVLC structure-preserving substitution watermarking. University of Salzburg
Su PC, Lu MT, Wu CY (2013) A practical design of high-volume steganography in digital video files. Multimed Tools Appl 66(2):247–266
Sudeepa KB, Raju K, R. K. HS, Aithal G, (2016) A new approach for video steganography based on randomization and parallelization. Procedia Comput Sci 78:483–490
Sullivan GJ, Ohm J-R, Han W-J, Wiegand T et al (2012) Overview of the high efficiency video coding (HEVC) standard. IEEE Trans circuits Syst video Technol 22(12):1649–1668
Sur A, Krishna SVM, Sahu N, Rana S (2015) Detection of motion vector based video steganography. Multimed Tools Appl 74(23):10479–10494
Suresh M, Sam IS (2020) Optimized interesting region identification for video steganography using Fractional Grey Wolf Optimization along with multi-objective cost function. J King Saud Univ Inf Sci
Suttichaiya A, Sombatkiripaiboon Y, Imtongkhua P, Poonriboon C, So-In C, Horkaew P (2017) Video steganography with LSB color detection. J Telecommun Electron Comput Eng 9(2–2):23–28
Swain G (2019) Two new steganography techniques based on quotient value differencing with addition-subtraction logic and PVD with modulus function. Optik (Stuttg) 180:807–823
Swanson MD, Zhu B, Tewfik AH (1997) Data hiding for video-in-video. Proceedings of the International Conference on Image Processing. Vol. 2, pp. 676–679
Tasdemir K, Kurugollu F, Sezer S (2013) Video steganalysis of LSB based motion vector steganography. Paper presented at 4th European workshop on visual information processing (EUVIP). pp. 260–264
Tasdemir K, Kurugollu F, Sezer S (2016) Spatio-temporal rich model-based video steganalysis on cross sections of motion vector planes. IEEE Trans Image Process 25(7):3316–3328
Article MathSciNet MATH Google Scholar
Thomas TL (2003) Al Qaeda and the internet: the danger of" cyberplanning". Parameters 33(1):112–123
Torkaman MRN, Nikfard P, Kazazi NS, Abbasy MR, Tabatabaiee SF (2011) Improving hybrid cryptosystems with DNA steganography, Paper presented at international conference on digital enterprise and information systems. pp. 42–52
Tudor PN (1995) MPEG-2 video compression. Electron Commun Eng J 7(6):257–264
Video HAVCC, Tew Y, Wong K (2014) An overview of information hiding in H. 264/AVC compressed video. Circuits Syst Video Technol IEEE Trans 24(2):305–319
Wahab OFA, Badawy MB, Elshakankiry OA, El-sayed HS (2015) Utilizations of reversible lossless data hiding techniques in video sequences. Int J Comput Netw Technol 3(1)
Wang Z, Lu L, Bovik AC (2004) Video quality assessment based on structural distortion measurement. Signal Process Image Commun 19(2):121–132
Wang K, Zhao H, Wang H (2014) Video steganalysis against motion vector-based steganography by adding or subtracting one motion vector value. IEEE Trans Inf Forensics Secur 9(5):741–751
Wang K, Han J, Wang H (2014) Digital video steganalysis by subtractive prediction error adjacency matrix. Multimed Tools Appl 72(1):313–330
Wang P, Cao Y, Zhao X (2017) Segmentation based video steganalysis to detect motion vector modification. Secur Commun Netw 2017:1–12
Wang Y, Cao Y, Zhao X, Xu Z, Zhu M (2018) Maintaining rate-distortion optimization for IPM-based video steganography by constructing isolated channels in HEVC. In: Proceedings of the 6th ACM workshop on information hiding and multimedia security. pp. 97–107
Wang J, Jia X, Kang X, Shi Y-Q (2019) A cover selection HEVC video steganography based on intra prediction mode. IEEE Access 7:119393–119402
Warfare C, Wang H, Wang S (2004) Cyber warfare: steganography vs. steganalysis. Commun ACM 47(10):76–82
Westfeld A, Pfitzmann A (2000) Attacks on steganographic Systems. Inf Hiding 1768:1–16
Wiegand T, Sullivan GJ, Bjontegaard G, Luthra A (2003) Overview of the H. 264/AVC video coding standard. IEEE Trans circuits Syst video Technol 13(7):560–576
Wong K, Tanaka K, Takagi K, Nakajima Y (2009) Complete video quality-preserving data hiding. IEEE Trans Circuits Syst Video Technol 19(10):1499–1512
Xu C, Ping X (2007) A steganographic algorithm in uncompressed video sequence based on difference between adjacent frames. In Proceedings of the 4th International Conference on Image Graph ICIG 2007. pp. 297–302
Xu C, Ping X, Zhang T (2006) Steganography in compressed video stream. Paper presented at First International Conference on innovative computing, information and control, ICICIC. vol. 1, pp. 269–272
Xu X, Dong J, Tan T (2012) Universal spatial feature set for video steganalysis. In: Proceedings of the 19th IEEE international conference on image processing. pp. 245–248
Xu D, Wang R, Shi YQ (2014) Data hiding in encrypted H.264/AVC video streams by codeword substitution. IEEE Trans Inf Forensics Secur 9(4):596–606
Xu D, Wang R, Shi YQ (2016) An improved scheme for data hiding in encrypted H.264/AVC videos. J Vis Commun Image Represent 36:229–242
Xue Y, Zhou J, Zeng H, Zhong P, Wen J (2019) An adaptive steganographic scheme for H. 264/AVC video with distortion optimization. Signal Process Image Commun 76:22–30
Yadav P, Mishra N, Sharma S (2013) A secure video steganography with encryption based on LSB technique. Paper presented at IEEE International Conference on Computational Intelligence and Computing Research (ICCIC) pp. 1–5
Yang M, Bourbakis N (2005) A high bitrate information hiding algorithm for digital video content under H.264/AVC compression. Midwest Symp Circuits Syst 2005:935–938
Yang Y, Li Z, Xie W, Zhang Z (2019) High capacity and multilevel information hiding algorithm based on pu partition modes for HEVC videos. Multimed Tools Appl 78(7):8423–8446
Yao Y, Zhang W, Yu N, Zhao X (2015) Defining embedding distortion for motion vector-based video steganography. Multimed Tools Appl 74(24):11163–11186
Yao Y, Zhang W, Yu N (2016) Inter-frame distortion drift analysis for reversible data hiding in encrypted H.264/AVC video bitstreams. Signal Processing 128:531–545
Ye H, Zhang W, Yao Y, Kong C, Huang H, Yu N, “Motion vector-based video steganalysis using spatial-temporal correlation. In: Proceedings of the 6th international congress on image and signal processing (CISP). Vol. 1. pp. 148–153
Yeh H-L, Gue S-T, Tsai P, Shih W-K (2014) Reversible video data hiding using neighbouring similarity. IET Signal Process 8(6):579–587
Zhai L, Wang L, Ren Y (2017) Combined and calibrated features for steganalysis of motion vector-based steganography in H. 264/AVC. In: proceedings of the 5th ACM workshop on information hiding and multimedia security. pp. 135–146
Zhang W, Cheung S.-CS, Chen M (2005) Hiding privacy information in video surveillance system. Paper presented at IEEE international conference on image processing. Vol. 3. p II–868
Zhang H, Cao Y, Zhao X (2015) Motion vector-based video steganography with preserved local optimality. Multimed Tools Appl 89:1–17
Zhang Y, Zhang M, Niu K, Liu J (2015) Video steganography algorithm based on trailing coefficients. Paper presented at international conference on intelligent networking and collaborative systems (INCOS), pp. 360–364
Zhao Y, Zhang H, Cao Y, Wang P, Zhao X (2015) Video steganalysis based on intra prediction mode calibration. International Workshop on Digital Watermarking. pp. 119–133
Download references
Acknowledgements
This research work is supported by Technical Education Quality Improvement Project III (TEQIP III) of MHRD, Government of India assisted by World Bank under Grant Number P154523 and sanctioned to UIET, Panjab University, Chandigarh (India).
Author information
Authors and affiliations.
UIET, Panjab University, Chandigarh, India
Mukesh Dalal & Mamta Juneja
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Mamta Juneja .
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Reprints and permissions
About this article
Dalal, M., Juneja, M. A survey on information hiding using video steganography. Artif Intell Rev 54 , 5831–5895 (2021). https://doi.org/10.1007/s10462-021-09968-0
Download citation
Accepted : 29 January 2021
Published : 09 February 2021
Issue Date : December 2021
DOI : https://doi.org/10.1007/s10462-021-09968-0
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Video steganography
- Spatial domain
- Transform domain
- Motion vector
- Steganalysis
- Find a journal
- Publish with us
- Track your research

IMAGES
VIDEO
COMMENTS
Video steganography approach enables hiding chunks of secret information inside video sequences. The features of video sequences including high capacity as well as complex structure make them more preferable for choosing as cover media over other media such as image, text, or audio. Video steganography is a prominent as well as the evolving field in the information security domain and ...
The method of steganography is used to keep data safe. Video steganography is a technique for concealing a secret message or piece of information (picture or video) within a video file. As a result, this study examines the various ways of video steganography and determines which is the most effective.
Video steganography is becoming an important research area in various data hiding technologies, which has become a promising tool because not only the security requirement of secret message transmission is becoming stricter but also video is more favored. In this paper, according to the embedded position of secret message, video steganography ...
Steganography is the art and science of secret communication, concealing the very existence of a communication. Modern cover types can take many forms such as text documents, audio tracks, digital images, and video streams. Extensive research has been done on image steganography in the previous decade due to their popularity on the internet. Nowadays, video files are drawing much more ...
A comprehensive review of video steganography methods proposed in the literature, including spatial domain approaches such as least significant bits (LSB), transform domain-based methods such as discrete wavelet transform, discrete cosine transform, etc. Video steganography approach enables hiding chunks of secret information inside video sequences. The features of video sequences including ...
This thesis proposes an image steganography technique using LSB embedding, specifically the palindromic number sequence. ... Video steganography is a prominent as well as the evolving field in the ...
Video steganography is drawing more impulse due to its scope of masking larger amount of secret information. This paper furnishes the leading-edge techniques and methodologies concerning video as covert communication channel. Both processed and un-processed videos are considered for surveying. Further the feasibility of encryption techniques ...
In this paper, we introduce an end-to-end robust generative video steganography network (RoGVS), which achieves visual editing by modifying semantic feature of videos to embed secret message. We employ face-swapping scenario to showcase the visual editing effects. We first design a secret message embedding module to adaptively hide secret ...
Moreover, video steganography will be of more interest because it provides more concealing capacity. Contrariwise, investigation in video steganalysis methods does not seem to follow the momentum even if law enforcement agencies and governments around the world support and encourage investigation in this field. In this paper, the authors review ...
Video steganography approach enables hiding chunks of secret information inside video. sequences. The features of video sequences including high capacity as well as complex. structure make them ...
The benefit of video steganography is the capacity to hide a large amount of data and the changes in the contiguous flow of data cannot be easily identified. The method of video steganography merges both audio and video strategies. The video is the accumulation of frames [4], and the frame selection is done in the embedding process [12]. The ...
Steganography hides secret messages inside the covers while ensuring imperceptibility. Different from traditional steganography, deep learning-based steganography has an adaptable and generalized framework without needing expertise regarding the embedding process. However, most steganography algorithms utilize images as covers instead of videos, which are more expressive and more widely spread ...
Video steganography is becoming an important research area in various data hiding technologies, which has become a promising tool because not only the security requirement of secret message transmission is becoming stricter but also video is more favored. In this paper, according to the embedded position of secret message, video steganography is divided into three categories: intra-embedding ...
Steganography is the art and science of writing messages which is to be hide behind original cover file which may be audio, video or image. In this paper we are working on audio-video ...
We have to read the video. Go through the video frame by frame and save all the images into a new directory. To load the video, we run: vidcap = cv2.VideoCapture("video.mp4") This loads the video into vidcap. Now we can use the read method to read the frames from "video.mp4:" success, image = vidcap.read()
Digital video provides various types of embedding domains, which lead to a great diversity in video steganography. However, in the detection of video steganography, the existing video steganalytic features all specialize in a particular domain, and are hardly to detect the steganography in other embedding domains. In this paper, we propose a universal feature set which is capable of detecting ...
A novel video steganography cloud security has been proposed for secure data transfer in cloud. In encoding side, the military secret data has been given as input and embedded in each frame based on Region on Interest pixel. This ensures the secret on the decoding side while extract the secret data by receiver.
My thesis initiates the study of steganography from a cryptographic point of view. We give a precise model of a communication channel and a rigorous de nition of steganographic security, and prove that relative to a channel oracle, secure steganography exists if and only if one-way functions exist. We give tightly matching upper and lower ...
2.1 Digital Video Steganography. After carefully analyzing all the existing frameworks, the video steganography techniques are primarily classified into seven methods as (1) substitution techniques, (2) transform domain techniques, (3) adaptive techniques, (4) format-based techniques, (5) cover generation, (6) convolutional neural network (CNN), and (7) general adversarial network (GAN)-based ...
Steganography is a science that maintains the confidentiality of information (text, image, audio, video) between two communicating parties (the sender and the receiver), and it is a science that studies the invisible communication of information. In this paper, the researcher reviewed the most important techniques of previous studies for the ...
Program that uses steganography and cryptography to hide a video file within another video file without noticeably effecting the appearance of the video. Networking component to securely send encoded files over a network. python cryptography networking steganography video-steganography. Updated on Apr 6, 2022.
In the last few decades, information security has gained huge importance owing to the massive growth in digital communication; hence, driving steganography to the forefront for secure communication. Steganography is a practice of concealing information or message in covert communication which involves hiding the information in any multimedia file such as text, image, or video. Many ...
Decomposing joint distortion for adaptive steganography. IEEE Transactions on Circuits and Systems for Video Technology 27, 10 (2016), 2274--2280. Google Scholar Digital Library; Xiang Zhang, Fei Peng, and Min Long. 2018. Robust coverless image steganography based on DCT and LDA topic classification.