

105 Latest Cyber Security Research Topics in 2024
Home Blog Security 105 Latest Cyber Security Research Topics in 2024
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cybersecurity thesis topics helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
The network can be attacked in various ways, including Distributed DoS, Knowledge Disruptions, Computer Viruses / Worms, and many more. Cyber-attacks are still rising, and more are waiting to harm their targeted systems and networks. Detecting Intrusions in cybersecurity has become challenging due to their Intelligence Performance. Therefore, it may negatively affect data integrity, privacy, availability, and security.
This article aims to demonstrate the most current Cyber Security Research Topics for Projects and areas of research currently lacking. We will talk about cyber security research questions, cyber security topics for the project, latest research titles about cyber security.
List of Trending Cyber Security Research Topics in 2024
Digital technology has revolutionized how all businesses, large or small, work, and even governments manage their day-to-day activities, requiring organizations, corporations, and government agencies to utilize computerized systems. To protect data against online attacks or unauthorized access, cybersecurity is a priority. There are many Cyber Security Courses online where you can learn about these topics. With the rapid development of technology comes an equally rapid shift in Cyber Security Research Topics and cybersecurity trends, as data breaches, ransomware, and hacks become almost routine news items. In 2024, these will be the top cybersecurity trends.
A. Exciting Mobile Cyber Security Research Paper Topics
- The significance of continuous user authentication on mobile gadgets.
- The efficacy of different mobile security approaches.
- Detecting mobile phone hacking.
- Assessing the threat of using portable devices to access banking services.
- Cybersecurity and mobile applications.
- The vulnerabilities in wireless mobile data exchange.
- The rise of mobile malware.
- The evolution of Android malware.
- How to know you’ve been hacked on mobile.
- The impact of mobile gadgets on cybersecurity.
B. Top Computer and Software Security Topics to Research
- Learn algorithms for data encryption
- Concept of risk management security
- How to develop the best Internet security software
- What are Encrypting Viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC
- Infiltrating a Mac OS X operating system
- What are the effects of RSA on network security ?
- How do encrypting viruses work?
- DDoS attacks on IoT devices
C. Trending Information Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2024
- Discuss digital piracy in 2024
- critical cyber-attack concepts
- Social engineering and its importance
D. Current Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Firewall
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
E. Best Data Security Research Topics
- Importance of backup and recovery
- Benefits of logging for applications
- Understand physical data security
- Importance of Cloud Security
- In computing, the relationship between privacy and data security
- Talk about data leaks in mobile apps
- Discuss the effects of a black hole on a network system.
F. Important Application Security Research Topics
- Detect Malicious Activity on Google Play Apps
- Dangers of XSS attacks on apps
- Discuss SQL injection attacks.
- Insecure Deserialization Effect
- Check Security protocols
G. Cybersecurity Law & Ethics Research Topics
- Strict cybersecurity laws in China
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries' cybersecurity laws
- Discuss The Pipeline Security Act in the United States
H. Recent Cyberbullying Topics
- Protecting your Online Identity and Reputation
- Online Safety
- Sexual Harassment and Sexual Bullying
- Dealing with Bullying
- Stress Center for Teens
I. Operational Security Topics
- Identify sensitive data
- Identify possible threats
- Analyze security threats and vulnerabilities
- Appraise the threat level and vulnerability risk
- Devise a plan to mitigate the threats
J. Cybercrime Topics for a Research Paper
- Crime Prevention.
- Criminal Specialization.
- Drug Courts.
- Criminal Courts.
- Criminal Justice Ethics.
- Capital Punishment.
- Community Corrections.
- Criminal Law.
Cyber Security Future Research Topics
- Developing more effective methods for detecting and responding to cyber attacks
- Investigating the role of social media in cyber security
- Examining the impact of cloud computing on cyber security
- Investigating the security implications of the Internet of Things
- Studying the effectiveness of current cyber security measures
- Identifying new cyber security threats and vulnerabilities
- Developing more effective cyber security policies
- Examining the ethical implications of cyber security
Cyber Security Topics For Research Paper
- Cyber security threats and vulnerabilities
- Cyber security incident response and management
- Cyber security risk management
- Cyber security awareness and training
- Cyber security controls and countermeasures
- Cyber security governance
- Cyber security standards
- Cyber security insurance
Top 5 Current Research Topics in Cybersecurity
Below are the latest 5 cybersecurity research topics. They are:
- Artificial Intelligence
- Digital Supply Chains
- Internet of Things
- State-Sponsored Attacks
- Working From Home
Research Area in Cyber Security
The field of cyber security is extensive and constantly evolving. Its research covers a wide range of subjects, including:
- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
- RFID Security
- Authorisation Infrastructure
- Digital Forensics
- Autonomous Security
- Social Influence on Social Networks
How to Choose the Best Research Topics in Cyber Security?
A good cybersecurity assignment heading is a skill that not everyone has, and unfortunately, not everyone has one. You might have your teacher provide you with the topics, or you might be asked to come up with your own. If you want more cyber security research topics, you can take references from Certified Ethical Hacker Certification, where you will get more hints on new topics. If you don't know where to start, here are some tips. Follow them to create compelling cybersecurity assignment topics.
1. Brainstorm
In order to select the most appropriate heading for your cybersecurity assignment, you first need to brainstorm ideas. What specific matter do you wish to explore? In this case, come up with relevant topics about the subject and select those relevant to your issue when you use our list of topics. You can also go to cyber security-oriented websites to get some ideas. Using any blog post on the internet can prove helpful if you intend to write a research paper on security threats in 2024. Creating a brainstorming list with all the keywords and cybersecurity concepts you wish to discuss is another great way to start. Once that's done, pick the topics you feel most comfortable handling. Keep in mind to stay away from common topics as much as possible.
2. Understanding the Background
In order to write a cybersecurity assignment, you need to identify two or three research paper topics. Obtain the necessary resources and review them to gain background information on your heading. This will also allow you to learn new terminologies that can be used in your title to enhance it.
3. Write a Single Topic
Make sure the subject of your cybersecurity research paper doesn't fall into either extreme. Make sure the title is neither too narrow nor too broad. Topics on either extreme will be challenging to research and write about.
4. Be Flexible
There is no rule to say that the title you choose is permanent. It is perfectly okay to change your research paper topic along the way. For example, if you find another topic on this list to better suit your research paper, consider swapping it out.
The Layout of Cybersecurity Research Guidance
It is undeniable that usability is one of cybersecurity's most important social issues today. Increasingly, security features have become standard components of our digital environment, which pervade our lives and require both novices and experts to use them. Supported by confidentiality, integrity, and availability concerns, security features have become essential components of our digital environment.
In order to make security features easily accessible to a wider population, these functions need to be highly usable. This is especially true in this context because poor usability typically translates into the inadequate application of cybersecurity tools and functionality, resulting in their limited effectiveness.
Cyber Security Research Topic Writing Tips from Expert
Additionally, a well-planned action plan and a set of useful tools are essential for delving into Cyber Security Research Topics. Not only do these topics present a vast realm of knowledge and potential innovation, but they also have paramount importance in today's digital age. Addressing the challenges and nuances of these research areas will contribute significantly to the global cybersecurity landscape, ensuring safer digital environments for all. It's crucial to approach these topics with diligence and an open mind to uncover groundbreaking insights.
- Before you begin writing your research paper, make sure you understand the assignment.
- Your Research Paper Should Have an Engaging Topic
- Find reputable sources by doing a little research
- Precisely state your thesis on cybersecurity
- A rough outline should be developed
- Finish your paper by writing a draft
- Make sure that your bibliography is formatted correctly and cites your sources.
Discover the Power of ITIL 4 Foundation - Unleash the Potential of Your Business with this Cost-Effective Solution. Boost Efficiency, Streamline Processes, and Stay Ahead of the Competition. Learn More!
Studies in the literature have identified and recommended guidelines and recommendations for addressing security usability problems to provide highly usable security. The purpose of such papers is to consolidate existing design guidelines and define an initial core list that can be used for future reference in the field of Cyber Security Research Topics.
The researcher takes advantage of the opportunity to provide an up-to-date analysis of cybersecurity usability issues and evaluation techniques applied so far. As a result of this research paper, researchers and practitioners interested in cybersecurity systems who value human and social design elements are likely to find it useful. You can find KnowledgeHut’s Cyber Security courses online and take maximum advantage of them.
Frequently Asked Questions (FAQs)
Businesses and individuals are changing how they handle cybersecurity as technology changes rapidly - from cloud-based services to new IoT devices.
Ideally, you should have read many papers and know their structure, what information they contain, and so on if you want to write something of interest to others.
Inmates having the right to work, transportation of concealed weapons, rape and violence in prison, verdicts on plea agreements, rehab versus reform, and how reliable are eyewitnesses?
The field of cyber security is extensive and constantly evolving. Its research covers various subjects, including Quantum & Space, Data Privacy, Criminology & Law, and AI & IoT Security.

Mrinal Prakash
I am a B.Tech Student who blogs about various topics on cyber security and is specialized in web application security
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates
List of 78 Top Cyber Security Topics for Research
Table of contents
- 1 How To Choose The Best Cyber Security Research Topics
- 2 📚10 Cyber Security Topics For Research Paper
- 3 📱Mobile Cyber Security Research Paper Topics
- 4 🕵Top 10 Cyber Security Topics
- 5 👨💻Cyber Security Research Topics 2023
- 6 🔎Best Cyber Security Research Topics
- 7 👨🔬Cyber Security Future Research Topics
- 8 📑Cyber Security Topics For Research Paper
- 9 👩💻Cyber Security Topics on Computer and Software
There are many reasons to choose cyber security research topics for writing purposes. First, cyber security is a growing field, with many new and exciting developments happening all the time. This makes it an ideal topic to write about, as there is always something new to learn and discuss. Second, cyber security research can be used to improve the security of your own computer systems. By understanding the latest threats and vulnerabilities, you can make your systems more secure and less likely to be compromised. Third, writing about cyber security can help raise awareness about the importance of cyber security. By educating others about the dangers of cyber attacks and the importance of protecting their computers, you can help make the internet a safer place for everyone.
How To Choose The Best Cyber Security Research Topics
When it comes to choosing research paper topics on cyber security, there are a few things to consider. First, it is important to make sure that the topic is relevant and timely. Cyber security is an ever-changing field, so it is important to choose a topic that will be relevant for years to come. Second, it is important to choose a topic that is interesting and engaging. Cybersecurity can be a dry topic, so it is important to choose a topic that will keep readers engaged. Finally, it is important to choose a topic that is researchable. There are a lot of cyber security topics out there, but not all of them are easy to research. Make sure to choose a topic that has plenty of information available.
- Identify your audience.
- Define your research goals.
- Choose a topic that is both interesting and relevant to your audience.
- Do some preliminary research to make sure there is enough information available on your chosen topic.
- Make sure your topic is narrow enough to be covered in a single research paper.
📚10 Cyber Security Topics For Research Paper
- The Importance of Cyber Security
- The Evolution of Cyber Security
- The Future of Cyber Security
- The Impact of Cyber Security on Business
- The Role of Cyber Security in National Security
- The Challenges of Cyber Security
- The Costs of Cyber Security
- The Benefits of Cyber Security
- The Risks of Cyber Security
- The Implications of Cyber Security
📱Mobile Cyber Security Research Paper Topics
- Mobile device security: How to protect your mobile device from cyber attacks.
- The rise of mobile malware: How to protect your device from malicious software.
- Mobile phishing attacks: How to protect your device from being scammed.
- The dangers of public Wi-Fi: How to protect your device from being hacked.
- How to keep your data safe on your mobile device: Tips for keeping your personal information secure.
🕵Top 10 Cyber Security Topics
- Cybersecurity threats and attacks
- Cybersecurity risks and vulnerabilities
- Cybersecurity best practices
- Cybersecurity awareness and training
- Cybersecurity tools and technologies
- Cybersecurity policy and compliance
- Cybersecurity incident response
- Cybersecurity governance
- Cybersecurity risk management
- Cybersecurity strategy
👨💻Cyber Security Research Topics 2023
- The future of cyber security: what trends will shape the field in the coming years?
- The impact of AI and machine learning on cyber security
- The role of quantum computing in cyber security
- The challenges of securing the IoT
- The evolving threat landscape: what new threats are emerging and how can we defend against them?
- The role of data in cyber security: how can we better protect our data?
- The importance of user education in cyber security
- The challenges of securing mobile devices
- The future of cyber warfare: what trends are emerging?
- The role of cryptography in cyber security
🔎Best Cyber Security Research Topics
- The Impact of Cybersecurity on Businesses and Consumers
- The Evolution of Cybersecurity Threats and Attacks
- The Role of Cybersecurity in National Security
- The Economics of Cybersecurity
- The Psychology of Cybersecurity
- The Sociology of Cybersecurity
- The Ethics of Cybersecurity
- The History of Cybersecurity
- Cybersecurity threats and attacks.
- Cybersecurity policies and procedures.
- Cybersecurity awareness and training.
- Cybersecurity technologies and solutions.
- Cybersecurity risk management.
- Cybersecurity incident response.
- Cybersecurity governance.
- Cybersecurity compliance.
- Cybersecurity standards.
- Cybersecurity best practices.
👨🔬Cyber Security Future Research Topics
- Developing more effective methods for detecting and responding to cyber attacks
- Investigating the role of social media in cyber security
- Examining the impact of cloud computing on cyber security
- Investigating the security implications of the Internet of Things
- Studying the effectiveness of current cyber security measures
- Identifying new cyber security threats and vulnerabilities
- Developing more effective cyber security policies
- Examining the ethical implications of cyber security
📑Cyber Security Topics For Research Paper
- Cyber security threats and vulnerabilities.
- Cyber security incident response and management.
- Cyber security risk management.
- Cyber security awareness and training.
- Cyber security controls and countermeasures.
- Cyber security governance.
- Cyber security standards.
- Cyber security insurance.
- Cyber security and the law.
- The future of cyber security.
👩💻Cyber Security Topics on Computer and Software
- Cyber security risks associated with computer software
- The importance of keeping computer software up to date
- How to protect your computer from malware and other threats
- The best practices for securing your computer and software
- The different types of cyber security threats and how to avoid them
- The importance of cyber security awareness and education
- The role of cyber security in protecting critical infrastructure
Readers also enjoyed

WHY WAIT? PLACE AN ORDER RIGHT NOW!
Just fill out the form, press the button, and have no worries!
We use cookies to give you the best experience possible. By continuing we’ll assume you board with our cookie policy.
Research Topics & Ideas: Cybersecurity
50 Topic Ideas To Kickstart Your Research

If you’re just starting out exploring cybersecurity-related topics for your dissertation, thesis or research project, you’ve come to the right place. In this post, we’ll help kickstart your research by providing a hearty list of cybersecurity-related research topics and ideas , including examples from recent studies.
PS – This is just the start…
We know it’s exciting to run through a list of research topics, but please keep in mind that this list is just a starting point . These topic ideas provided here are intentionally broad and generic , so keep in mind that you will need to develop them further. Nevertheless, they should inspire some ideas for your project.
To develop a suitable research topic, you’ll need to identify a clear and convincing research gap , and a viable plan to fill that gap. If this sounds foreign to you, check out our free research topic webinar that explores how to find and refine a high-quality research topic, from scratch. Alternatively, consider our 1-on-1 coaching service .

Cybersecurity-Related Research Topics
- Developing machine learning algorithms for early detection of cybersecurity threats.
- The use of artificial intelligence in optimizing network traffic for telecommunication companies.
- Investigating the impact of quantum computing on existing encryption methods.
- The application of blockchain technology in securing Internet of Things (IoT) devices.
- Developing efficient data mining techniques for large-scale social media analytics.
- The role of virtual reality in enhancing online education platforms.
- Investigating the effectiveness of various algorithms in reducing energy consumption in data centers.
- The impact of edge computing on the performance of mobile applications in remote areas.
- The application of computer vision techniques in automated medical diagnostics.
- Developing natural language processing tools for sentiment analysis in customer service.
- The use of augmented reality for training in high-risk industries like oil and gas.
- Investigating the challenges of integrating AI into legacy enterprise systems.
- The role of IT in managing supply chain disruptions during global crises.
- Developing adaptive cybersecurity strategies for small and medium-sized enterprises.
- The impact of 5G technology on the development of smart city solutions.
- The application of machine learning in personalized e-commerce recommendations.
- Investigating the use of cloud computing in improving government service delivery.
- The role of IT in enhancing sustainability in the manufacturing sector.
- Developing advanced algorithms for autonomous vehicle navigation.
- The application of biometrics in enhancing banking security systems.
- Investigating the ethical implications of facial recognition technology.
- The role of data analytics in optimizing healthcare delivery systems.
- Developing IoT solutions for efficient energy management in smart homes.
- The impact of mobile computing on the evolution of e-health services.
- The application of IT in disaster response and management.
Cybersecurity Research Ideas (Continued)
- Assessing the security implications of quantum computing on modern encryption methods.
- The role of artificial intelligence in detecting and preventing phishing attacks.
- Blockchain technology in secure voting systems: opportunities and challenges.
- Cybersecurity strategies for protecting smart grids from targeted attacks.
- Developing a cyber incident response framework for small to medium-sized enterprises.
- The effectiveness of behavioural biometrics in preventing identity theft.
- Securing Internet of Things (IoT) devices in healthcare: risks and solutions.
- Analysis of cyber warfare tactics and their implications on national security.
- Exploring the ethical boundaries of offensive cybersecurity measures.
- Machine learning algorithms for predicting and mitigating DDoS attacks.
- Study of cryptocurrency-related cybercrimes: patterns and prevention strategies.
- Evaluating the impact of GDPR on data breach response strategies in the EU.
- Developing enhanced security protocols for mobile banking applications.
- An examination of cyber espionage tactics and countermeasures.
- The role of human error in cybersecurity breaches: a behavioural analysis.
- Investigating the use of deep fakes in cyber fraud: detection and prevention.
- Cloud computing security: managing risks in multi-tenant environments.
- Next-generation firewalls: evaluating performance and security features.
- The impact of 5G technology on cybersecurity strategies and policies.
- Secure coding practices: reducing vulnerabilities in software development.
- Assessing the role of cyber insurance in mitigating financial losses from cyber attacks.
- Implementing zero trust architecture in corporate networks: challenges and benefits.
- Ransomware attacks on critical infrastructure: case studies and defence strategies.
- Using big data analytics for proactive cyber threat intelligence.
- Evaluating the effectiveness of cybersecurity awareness training in organisations.
Recent Cybersecurity-Related Studies
While the ideas we’ve presented above are a decent starting point for finding a research topic, they are fairly generic and non-specific. So, it helps to look at actual studies in the cybersecurity space to see how this all comes together in practice.
Below, we’ve included a selection of recent studies to help refine your thinking. These are actual studies, so they can provide some useful insight as to what a research topic looks like in practice.
- Cyber Security Vulnerability Detection Using Natural Language Processing (Singh et al., 2022)
- Security for Cloud-Native Systems with an AI-Ops Engine (Ck et al., 2022)
- Overview of Cyber Security (Yadav, 2022)
- Exploring the Top Five Evolving Threats in Cybersecurity: An In-Depth Overview (Mijwil et al., 2023)
- Cyber Security: Strategy to Security Challenges A Review (Nistane & Sharma, 2022)
- A Review Paper on Cyber Security (K & Venkatesh, 2022)
- The Significance of Machine Learning and Deep Learning Techniques in Cybersecurity: A Comprehensive Review (Mijwil, 2023)
- Towards Artificial Intelligence-Based Cybersecurity: The Practices and ChatGPT Generated Ways to Combat Cybercrime (Mijwil et al., 2023)
- ESTABLISHING CYBERSECURITY AWARENESS OF TECHNICAL SECURITY MEASURES THROUGH A SERIOUS GAME (Harding et al., 2022)
- Efficiency Evaluation of Cyber Security Based on EBM-DEA Model (Nguyen et al., 2022)
- An Overview of the Present and Future of User Authentication (Al Kabir & Elmedany, 2022)
- Cybersecurity Enterprises Policies: A Comparative Study (Mishra et al., 2022)
- The Rise of Ransomware: A Review of Attacks, Detection Techniques, and Future Challenges (Kamil et al., 2022)
- On the scale of Cyberspace and Cybersecurity (Pathan, 2022)
- Analysis of techniques and attacking pattern in cyber security approach (Sharma et al., 2022)
- Impact of Artificial Intelligence on Information Security in Business (Alawadhi et al., 2022)
- Deployment of Artificial Intelligence with Bootstrapped Meta-Learning in Cyber Security (Sasikala & Sharma, 2022)
- Optimization of Secure Coding Practices in SDLC as Part of Cybersecurity Framework (Jakimoski et al., 2022)
- CySSS ’22: 1st International Workshop on Cybersecurity and Social Sciences (Chan-Tin & Kennison, 2022)
As you can see, these research topics are a lot more focused than the generic topic ideas we presented earlier. So, for you to develop a high-quality research topic, you’ll need to get specific and laser-focused on a specific context with specific variables of interest. In the video below, we explore some other important things you’ll need to consider when crafting your research topic.
Get 1-On-1 Help
If you’re still unsure about how to find a quality research topic, check out our Research Topic Kickstarter service, which is the perfect starting point for developing a unique, well-justified research topic.

You Might Also Like:

Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Print Friendly
A List of 181 Hot Cyber Security Topics for Research [2024]
Your computer stores your memories, contacts, and study-related materials. It’s probably one of your most valuable items. But how often do you think about its safety?
Cyber security is something that can help you with this. Simply put, it prevents digital attacks so that no one can access your data. Do you want to write a research paper related to the modern challenges of cyberspace? This article has all you need. In here, you’ll find:
- An overview of cyber security’s research areas.
- A selection of compelling cyber security research topics.
And don’t hesitate to contact our custom writing team in case you need any assistance!
- 🔝 Top 10 Topics
- ✅ Research Areas
- ⭐ Top 10 Cybersecurity Topics
- 🔒 Technology Security Topics
- 🖥️ Cybercrime Topics
- ⚖️ Cyber Law & Ethics Topics
🔍 References
🔝 top 10 cyber security topics.
- How does malware work?
- The principle of zero trust access
- 3 phases of application security
- Should removable media be encrypted?
- The importance of network security
- The importance of end-user education
- Cloud security posture management
- Do biometrics ensure security of IPhones?
- Can strong passwords protect information?
- Is security in critical infrastructure important?
✅ Cyber Security Topics & Research Areas
Cyber security is a vast, constantly evolving field. Its research takes place in many areas. Among them are:
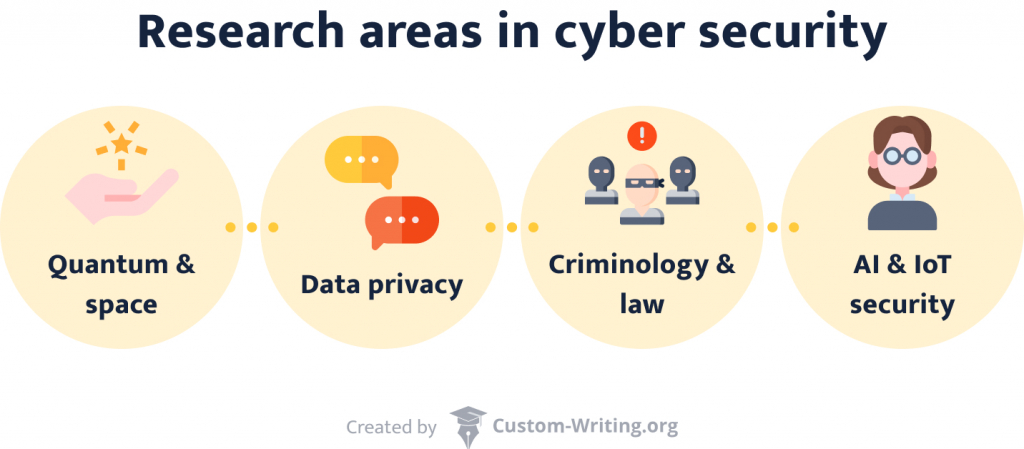
- Safe quantum and space communications . Progress in quantum technologies and space travel calls for extra layers of protection.
- Data privacy. If someone’s personal information falls into the wrong hands, the consequences can be dire. That’s why research in this area focuses on encryption techniques.
- (Inter)national cyberethics, criminology, and law. This branch analyzes how international legal frameworks work online.
- AI and IoT security . We spend more and more of our daily lives online. Additionally, our reliance on AI increases. This scientific field strives to ensure a safe continuation of this path.
As you can see, cyber security extends in various exciting directions that you can explore. Naturally, every paper needs a cover page. We know that it’s one of the more annoying parts, so it’s not a bad thing to use a title page generator for your research paper . Now, let’s move on to our cyber topics list.
⭐ Top 10 Cybersecurity Topics 2024
- Is removable media a threat?
- Blockchain security vulnerabilities
- Why should you avoid public Wi-Fi?
- How to prevent phishing attacks
- Physical security measures in banks
- Security breaches of remote working
- How does two-factor authentication work?
- How to prevent social engineering attacks
- Cybersecurity standards for automotive
- Privacy settings of social media accounts
🔒 Computer Security Topics to Research
Safe computer and network usage is crucial. It concerns not only business but also individuals. Security programs and systems ensure this protection. Explore them with one of our topics:
- How do companies avoid sending out confidential information? Sending an email to the wrong person has happened to the best of us. But what happens if the message’s contents were classified? For your paper, you can find out what technologies can prevent such slip-ups.
- What are the best ways to detect malicious activity? Any organization’s website gets plenty of daily traffic. People log in, browse, and interact with each other. Among all of them, it might be easy for an intruder to slip in.
- Internet censorship: classified information leaks . China takes internet censorship to the next level. Its comprehensive protection policies gave the system the nickname Great Firewall of China . Discuss this technology in your essay.
- Encrypted viruses as the plague of the century. Antivirus programs are installed on almost every computer. They prevent malicious code from tampering with your data. In your paper, you can conduct a comparison of several such programs.
- What are the pros and cons of various cryptographic methods? Data privacy is becoming more and more critical. That’s why leading messaging services frequently advertise with their encryption technologies.
- What makes blockchain secure? This technique allows anonymity and decentralization when working with cryptocurrencies. How does it work? What risks are associated with it?
- What are the advantages of SIEM ? Security Incident and Event Management helps organizations detect and handle security threats. Your essay can focus on its relevance for businesses.
- What are the signs of phishing attempts?
- Discuss unified cyber security standards in healthcare.
- Compare and contrast various forms of data extraction techniques.
- What do computers need protocols for?
- Debate the significance of frequent system updates for data security .
- What methods does HTTPS use that make it more secure than HTTP?
- The role of prime numbers in cryptography .
- What are public key certificates, and why are they useful?
- What does a VPN do?
- Are wireless internet connections less secure than LAN ones? If so, why?
- How do authentication processes work?
- What can you do with IP addresses?
- Explain the technology of unlocking your phone via facial recognition vs. your fingerprint.
- How do you prevent intrusion attempts in networks ?
- What makes Telnet vulnerable?
- What are the phases of a Trojan horse attack?
- Compare the encryption technologies of various social networks.
- Asymmetric vs. symmetric algorithms.
- How can a person reach maximum security in the computer networking world ?
- Discuss autoencoders and reveal how they work.
💾 Information Security Topics to Research
Information security’s goal is to protect the transmission and storage of data. On top of that, network security topics are at the forefront of infosec research. If you’re looking for inspiration on the subject, check out these ideas.
- What are the mechanics of password protection? Passwords are a simple tool to ensure confidentiality. What do users and developers need to keep in mind when handling passwords?
- What are the safest ways to ensure data integrity ? Everybody wants their data to be intact. Accidental or malicious modifications of data can have dire consequences for organizations and individuals. Explore ways to avoid it.
- How can one establish non-repudiation? Non-repudiation proves the validity of your data. It’s essential in legal cases and cyber security .
- How did the advent of these new technologies impact information security ? Mobile networks have changed the way we access information. On a smartphone , everything is permanently available at your fingertips. What adverse consequences did these technologies bring?
- How do big corporations ensure that their database environment stays conflict-free? We expect our computers to always run fast and without errors. For institutions such as hospitals, a smooth workflow is vital. Discuss how it can be achieved.
- Describe solid access control methods for organizations. In a company, employees need access to different things. This means that not everyone should have an admin account. How should we control access to information ?
- Medical device cyber security. For maximum safety, it’s best to employ several measures. Protection on the hard- and software side is just a part of it. What are some other means of security?
- Write an argumentative essay on why a career in information security doesn’t require a degree.
- Pros and cons of various infosec certificates.
- Cybersecurity in cruise ship industry
- The influence of remote work on a businesses’ infosec network .
- What should everyone be aware of when it comes to safeguarding private information?
- Select a company and calculate how much budget they should allocate on cyber security.
- What are the dangers of public Wi-Fi networks?
- How secure are cloud services ?
- Apple vs. Microsoft : whose systems offer better security?
- Why is it important to remove a USB flash drive safely?
- Is it possible to create an unguessable password?
- Intranet security: best practices.
- Does the use of biometrics increase security?
- Face recognition vs. a simple code: what are the safest locking options for smartphones ?
- How do you recover data from a broken hard drive?
- Discuss the functions and risks of cookies and cache files.
- Online privacy regulations in the US and China.
- Physical components of InfoSec.
- Debate security concerns regarding electronic health records .
- What are unified user profiles, and what makes them potentially risky?
🖥️ Cybercrime Topics for a Research Paper
Knowledge is one of today’s most valuable assets. Because of this, cybercrimes usually target the extraction of information. This practice can have devastating effects. Do you want to learn more about the virtual world’s dark side? This section is for you.
- Give an overview of the various types of cybercrimes today . Cybercriminals are becoming more and more inventive. It’s not easy to keep up with the new threats appearing every day. What threats are currently the most prominent?
- How does cryptojacking work, and why is it problematic? Cryptocurrency’s value explosion has made people greedy. Countries such as Iceland have become a haven for datamining. Explore these issues in your essay.
- Analyze the success rate of email frauds. You’ve probably seen irrelevant ads in your spam folder before. They often sound so silly it’s hard to believe they work. Yet, unfortunately, many people become victims of such scams.
- How did the WannaCry malware work? WannaCry was ransomware that caused global trouble in 2017. It led to financial losses in the billions. What made it so dangerous and hard to stop?
- Give famous examples of cybercrimes that targeted people instead of money . Not all cybercrimes want to generate profit. Sometimes, the reasons are political or personal. Explore several instances of such crimes in your essay. How did they pan out?
- Analyze the implications of the Cyberpunk 2077 leak. The game’s bugs and issues made many people angry. Shortly after its flop, hackers released developer CD Projekt Red’s source codes. What far-reaching consequences could this have?
- Why do hackers commit identity theft? Social media has made it easy to steal identities . Many like to display their lives online. In your paper, research what happens to the victims of identity thefts.
- Should governments punish cybercrimes like real-life crimes?
- How does ransomware work?
- Describe the phases of a DDoS attack.
- What cybercrime cases led to changes in the legislature?
- Track the evolution of online scams.
- Online grooming: how to protect children from predators.
- Are cybercrimes “gateway crimes” that lead to real-life misbehavior?
- What are man-in-the-middle attacks?
- Big data and the rise of internet crimes.
- Are cybercrimes more dangerous to society than they are to corporations?
- Is the internet increasing the likelihood of adolescents engaging in illegal activities?
- Do the downsides of cyberlife outweigh its positives?
- Is constantly checking your crush’s Facebook page cyberstalking?
- How do you recognize your online date is a scam?
- Describe what happens during a Brute Force attack.
- What’s the difference between pharming and phishing?
- The Lehman Bank cybercrimes.
- Should the punishments for cybercriminals be harsher than they are now?
- Compare various types of fraud methods .
- How do you mitigate a denial-of-service attack?
🕵️ Topics for a Research Paper on Hacking
Blinking screens and flashing lines of code: the movie industry makes hacking look fascinating. But what actually happens when someone breaks into another person’s computer’s system? Write a paper about it and find out! The following prompts allow you to dive deeper into the subject.
- Is it vital to keep shutting down online movie streaming sites? Many websites offer free movie streaming. If one of their domains gets closed down, they just open another one. Are they a threat to the industry that must be stopped? Or should cyber law enforcement rather focus on more serious crimes?
- Explore the ethical side of whistleblowing. WikiLeaks is a platform for whistleblowers. Its founder, Julian Assange, has been under arrest for a long time. Should whistleblowing be a crime? Why or why not?
- How did Kevin Mitnick’s actions contribute to the American cyber legislature? Mitnick was one of the US’s first most notorious hackers. He claimed to have broken into NORAD’s system. What were the consequences?
- Examine how GhostNet operates. GhostNet is a large organization attacking governments. Its discovery in 2009 led to a major scandal.
- Describe how an SQL injection attack unfolds. Injection attacks target SQL databases and libraries. This way, hackers gain unauthorized access to data.
- What political consequences did the attack on The Interview imply? In 2014, hackers threatened to attack theaters that showed The Interview . As a result, Sony only showed the movie online and in limited releases.
- Write about cross-site request forgery attacks. Every website tells you that logging out is a crucial step. But what can happen if you don’t do it?
- What is “Anonymous,” and what do they do?
- Is it permissible to hack a system to raise awareness of its vulnerabilities?
- Investigate the origins of the hacking culture .
- How did industrial espionage evolve into hacking?
- Is piracy destroying the music and movie industries ?
- Explain the term “cyberwarfare.”
- Contrast different types of hacking.
- Connections between political protests and hacking.
- Is it possible to create an encryption that can’t be hacked?
- The role of hackers in modern warfare .
- Can hacking be ethical?
- Who or what are white hat hackers ?
- Discuss what various types of hackers do.
- Is jailbreaking a crime?
- How does hacking a phone differ from hacking a computer?
- Is hacking your personal home devices problematic?
- What is clickjacking?
- Why would hackers target newspapers ?
- Examine the consequences society would have to bear if a hacker targeted the state.
- Compare and analyze different hacking collectives.
⚖️ Topics on Cyber Law & Ethics to Look Into
Virtual life needs rules just like the real one does. The online world brings a different set of values and issues to the table. And, naturally, cyberlife has a legal framework. That’s where researching cyber law and ethics comes into play.
- Is it ethical that governments can always access their citizens’ data? In some countries, online platforms for personal information are standard. From medical exams to debts, everything is available with a click. The system is inarguably convenient. But what about its downsides?
- Is it still morally permissible to use Spotify ? Spotify has made listening to music more accessible than ever. However, artists only receive a tiny fraction of the company’s profits. Discuss the implications of this fact.
- Should internet forums require users to display their real names? Online harassment is a widespread problem. Nicknames hide the identities of ordinary users as well as perpetrators. Can the mandatory use of real names change the situation?
- Analyze online gaming behavior from a psychological standpoint. If one wants to play online games, one needs to have a thick skin. The community can be harsh. You can dedicate your paper to exploring these behaviors. Or you might want to ponder what game publishers can do to reduce hate speech.
- What type of restrictions should sellers implement to prevent domain speculation? Some people buy domains hoping that they will sell them later for more money. This practice makes registering a new website trickier.
- Does the internet need regulations to make adult content less visible? Every computer without parental control can access pornographic websites. Most of them don’t require registration. Their contents can be disturbing, and their ads can appear anywhere. What can be done about it?
- What are cyber laws still missing in America? The US has established many laws to regulate internet usage. Select the most significant ones and explain their relevance.
- Why should cyber ethics be different from real-world norms?
- Are there instances in which illegal downloading is justified?
- The rule of law in real life vs. in cyberspace.
- Does the internet need a government?
- What is cyber terrorism, and what makes it dangerous?
- Who is responsible for online misbehavior?
- How binding are netiquettes?
- What did the implementation of the GDPR change?
- Compare and contrast Indian vs. Venezuelan internet regulations.
- What does the CLOUD entail?
- How should law enforcement adapt to online technologies?
- AI applications : ethical limits and possibilities.
- Discuss trending topics in cyber law of the past ten years.
- Should schools teach online etiquette?
- Does internet anonymity bring out the worst in people?
- Is data privacy more important than convenience and centralization?
- Debate whether bitcoins could become the currency of the future.
- How can online consumers protect themselves from fraud?
- Is buying from websites like eBay and Craigslist more ethical than buying from other online marketplaces?
- Present RSF’s Minecraft library and discuss its moral implications.
🖱️ Cyberbullying Topics for Essays and Papers
On the web, everyone can remain anonymous. With this added comfort, bullying rises to another level. It’s a serious issue that’s getting more and more problematic. Cyber security measures can alleviate the burden. Do you want to address the problem? Have a look at our cyberbullying topics below.
- Cyberbullying prevention in online learning environments . Online classes increase the possibility of cyberbullying. What can teachers do to watch out for their students?
- What makes online emotional abuse particularly difficult to bear? Bullying doesn’t necessarily have to be physical to hurt. Statistics show increased suicide rates among students who were harassed online. Explore the reasons behind this phenomenon.
- How can victims of identity theft reclaim their lives? Identity theft leads not only to mental distress. Thieves also have access to credit card information and other essential assets.
- What are the best methods to stay safe online? When surfing the internet, one always has to be on one’s toes. Avoiding harassment and bullying is a particularly challenging task.
- How can parents monitor their children’s behavior on the web? Children are particularly vulnerable online. They might enter dangerous online relationships with strangers if they feel lonely. They are also more susceptible to scams. What can parents do to protect them?
- Cyberbullying among university students. Online abuse in such websites is very common. Everyone can be a potential target, regardless of age or gender. Discuss whether the structure of social networks helps to spread cyberbullying.
- What societal factors contribute to online bullying? Not everyone who uses the internet becomes an abuser. It’s possible to establish several psychological characteristics of cyberbullies. Explore them in your paper.
- Define how cyberbullying differs from in-person harassment.
- Establish a link between feminism and the fight against cyberstalking .
- The emotional consequences of physical vs. verbal abuse.
- The effects of cyberbullying and academics.
- Short vs. long-term mental health effects of internet bullying .
- What are the most widespread means of cyberbullying?
- Should people who want to play video games online get over the fact that the community is toxic?
- Is defending the freedom of speech more important than preventing the spread of hate speech?
- Reasons and consequences of Amanda Todd’s suicide.
- The dangers of pro-ana/-mia communities for adolescents.
- What are effective strategies to cope with online harassment ?
- Would cyber communism decrease bullying?
- How enhanced cyber security measures can help reduce abuse.
- The importance of parental control mechanisms on children’s computers.
- Traditional vs. cyberbullying in children.
- Do image-heavy websites such as Tumblr and Instagram affect one’s mental state similarly to active abuse?
- What kind of people does cyber abuse affect the most, and why?
- Analyze how the stalker uses the internet in Netflix’s series You .
- Catfishing: effects and solutions.
Thanks for reading through our article. If you found it helpful, consider sharing it with your friends. We wish you good luck with your project!
Further reading:
- 220 Best Science and Technology Essay Topics to Write About
- 204 Research Topics on Technology & Computer Science
- A List of 580 Interesting Research Topics [2024 Edition]
- A List of 179 Problem Solution Essay Topics & Questions
- 193 Interesting Proposal Essay Topics and Ideas
- 226 Research Topics on Criminal Justice & Criminology
- What Is Cybersecurity?: Cisco
- Cyber Security: Research Areas: The University of Queensland, Australia
- Cybersecurity: National Institute of Standards and Technology
- What Is Information Security?: CSO Online
- Articles on Cyber Ethics: The Conversation
- What Is Cybercrime?: Kaspersky
- Types of Cybercrime and How to Protect Yourself Against Them: Security Traits
- Hacking: Computing: Encyclopedia Britannica
- Hacking News: Science Daily
- Cyberbullying and Cybersecurity: How Are They Connected?: AT&T
- Cyberbullying: What Is It and How to Stop It: UNICEF
- Current Awareness: Cyberlaw Decoded: Florida State University
- Share to Facebook
- Share to Twitter
- Share to LinkedIn
- Share to email

Have you ever wondered why everyone has a unique set of character traits? What is the connection between brain function and people’s behavior? How do we memorize things or make decisions? These are quite intriguing and puzzling questions, right? A science that will answer them is psychology. It’s a multi-faceted...
![computer security research paper ideas Student Exchange Program (Flex) Essay Topics [2024]](https://custom-writing.org/blog/wp-content/uploads/2021/01/student-exchange-program-284x153.jpg)
Participating in a student exchange program is a perfect opportunity to visit different countries during your college years. You can discover more about other cultures and learn a new language or two. If you have a chance to take part in such a foreign exchange, don’t miss it. Keep in...

How can you define America? If you’ve ever asked yourself this question, studying US history will help you find the answer. This article will help you dive deeper into this versatile subject. Here, you will find:
![computer security research paper ideas 380 Powerful Women’s Rights & Feminism Topics [2024]](https://custom-writing.org/blog/wp-content/uploads/2021/01/Womens-Rights-284x153.jpg)
Are you looking for perfect feminist topics? Then you’ve come to the right place. With our help, you can be sure to craft a great essay. Here, you can find feminist topics for discussion, feminism research topics and other ideas and questions for students. Some people think all feminists hate...

If you have an assignment in politics, look no further—this article will help you ace your paper. Here, you will find a list of unique political topics to write about compiled by our custom writing team. But that’s not all of it! Keep reading if you want to: Now, without further ado, let’s get started! Below, you’ll find political topics and questions for your task. 🔝 Top 10 Political...

It’s not a secret that our health largely depends on nutrition. A balanced and wholesome diet improves our immune system. It lowers the risk of getting sick and makes us more productive. But if we don’t eat right, our overall well-being and performance worsen. You see, nutrition topics are more...

A presentation is a speech in which you explain a topic to an audience. It usually includes visuals done in a program such as PowerPoint. Teachers in schools and in colleges love to assign presentations for various reasons: In this article, you’ll find a list of 625 presentation topics in...

In modern societies, people do everything to live peacefully. Still, tensions often arise. We call them social issues when they start negatively impacting a specific group of people. Poverty, discrimination, and addiction are examples of such problems. We need to confront them to ensure equal treatment for everyone.

There are many ways to define popular culture. Here’s one of them: pop culture includes mainstream preferences in society within a specific time frame. It covers fashion, music, language, and even food. Pop culture is always evolving, engaging in new trends, and leaving the old ones behind.
![computer security research paper ideas 500 Sociology Questions and Topics [Examples & Tips]](https://custom-writing.org/blog/wp-content/uploads/2021/01/Sociology-Questions-284x153.jpg)
Sociology is a study that focuses on people’s interactions. It looks at structures and changes in social life. Any situation involving people can become a topic of sociology. This article is designed to help high school and college students with sociology assignments. Whether you’re writing an essay, creating a presentation,...

Controversial issues are the ones that evoke a variety of opinions. They often cause heated debates. And, as you can guess, controversial research topics are not easy to handle. Luckily, we’ve got you covered. This article will: We gathered controversial topics for research paper on medical, science, education, and other...

Plates break when you drop them. Glasses help you see better. Have you ever wondered why? Physics has the answer. It studies the observable as well as invisible aspects of nature. An essential part of this is examining the structure and interactions of matter.

Top 161+ Computer Security Research Topics & Ideas – Amazing Guide!
Computer security is a very important field that changes quickly as technology advances. As cyber threats become smarter and the possible damage from security breaches more serious, there is an ongoing need for new research to develop strong defensive strategies and stay one step ahead of bad actors.
Whether you are a student studying cybersecurity, a researcher exploring new techniques, or a professional wanting to learn more, finding interesting computer security research topics can be challenging.
This guide lists over 161 thought-provoking computer security research ideas in different areas, such as network security, cryptography, malware analysis , data privacy , ethical hacking, and more.
Look through these topics to get inspiration for your next big research project or school paper that could potentially shape the future of digital security.
Importance of Choosing the Right Research Topic
Table of Contents
Picking the right topic for your research is super important in computer security. The topic you choose will decide the direction and how much impact your work could have.
A good topic needs to be relevant and interesting, and new solutions or ideas for current computer security issues need to be provided. Here are some key reasons why choosing the perfect topic really matters:
- It keeps you motivated and excited about the project. Working on something you truly find interesting makes the whole research process more enjoyable and productive.
- It makes sure your work tackles real-world problems that people, businesses, or society face. The best research helps solve serious cybersecurity challenges.
- It allows you to bring something totally new to the field. Avoid topics that are way too broad or have already been researched extensively.
- It decides how big or in-depth your research will be. The right topic gives you enough to explore without being too much for your time and resources.
- It affects your chances of getting your findings published or presented. Totally new, well-done research on important current topics is more likely to get accepted by journals, conferences, and computer security experts.
Taking the time upfront to really think about topics and choose the perfect one is so worth it. It sets you up for a meaningful, rewarding research experience.
Recommended Readings: “ Top 119+ Innovative Language Development Research Topics – Innovative Ideas “.
General Guidelines for Selecting Research Topics
Here are some guidelines for selecting research topics that will surely help you select the perfect topic for yourself; please take a look.
Understanding What’s Currently Popular
When picking a research topic, it’s important to look at what computer security areas are really hot and getting a lot of buzz right now. Look for new threats, new technologies, and popular topics that people are talking about. This helps make sure your research is relevant and tackles current issues. Check cybersecurity news sites, research articles, and conference topics to see what trends are happening.
Thinking About Your Interests and Skills
The best research topics are ones that really fascinate you and fit your skills/background. If you pick something you have no interest in, it will be hard to stay motivated. And if it’s too far from what you know, you may struggle. Think about areas of computer security that truly excite your curiosity. Also, consider what technical knowledge and experience you already have that could help.
Considering Real-World Applications
For your research to have maximum impact, it needs real-world uses. Look for topics that solve actual problems faced by individuals, companies, governments, etc., such as protecting systems, securing financial info, or defending against specific attack methods. Considering the potential real-world uses upfront leads to research that delivers concrete solutions rather than just ideas.
Top 161+ Computer Security Research Topics
Here is the list of the top 161+ computer security research topics provided according to different categories; let’s look.
Network Security
- Zero-day vulnerabilities and exploits in network protocols
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
- Network traffic analysis and anomaly detection
- Secure routing protocols for ad-hoc and sensor networks
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) attack mitigation
- Wireless network security (e.g., Wi-Fi, Bluetooth, RFID)
- Next-generation firewall technologies
- Secure network design and architecture
- DNS security and DNSSEC implementation
- Threat intelligence sharing mechanisms and platforms
Cryptography
- Post-quantum cryptography algorithms and implementations
- Cryptanalysis of existing cryptographic schemes
- Homomorphic encryption for privacy-preserving computation
- Blockchain and cryptocurrency security
- Secure multiparty computation (MPC)
- Quantum key distribution (QKD) protocols
- Cryptographic protocols for secure communication (e.g., SSL/TLS)
- Side-channel attacks and countermeasures
- Cryptography in IoT devices and embedded systems
- Attribute-based encryption (ABE) for fine-grained access control
Software Security
- Static and dynamic analysis techniques for vulnerability detection
- Secure software development methodologies (e.g., DevSecOps)
- Code obfuscation and anti-reverse engineering techniques
- Secure coding practices and code review methodologies
- Vulnerability management and patching strategies
- Binary exploitation techniques and mitigations
- Software-defined security mechanisms
- Secure software updates and distribution mechanisms
- Software sandboxing and containerization for security
- Secure software testing methodologies (e.g., fuzzing, symbolic execution)
Web Security
- Web application security testing and assessment
- Cross-site scripting (XSS) and Cross-Site Request Forgery (CSRF) prevention
- SQL injection and other injection attack mitigation
- Web security headers and Content Security Policy (CSP)
- Browser security models and vulnerabilities
- Secure authentication mechanisms (e.g., OAuth, OpenID Connect)
- Web server security configurations and best practices
- Web-based malware detection and prevention
- Secure session management techniques
- Website integrity monitoring and protection against defacement
Hardware Security
- Hardware Trojans detection and prevention techniques
- Hardware-based root of trust mechanisms
- Secure boot and firmware integrity verification
- Side-channel attacks on hardware implementations
- Hardware security primitives (e.g., Physically Unclonable Functions)
- Trusted Platform Module (TPM) and its applications
- Hardware security in IoT devices and wearables
- Secure enclave technologies (e.g., Intel SGX, ARM TrustZone)
- Hardware-based secure storage solutions
- Hardware security certification standards (e.g., FIPS, Common Criteria)
Mobile Security
- Mobile application security assessment and testing
- Secure mobile app development frameworks and guidelines
- Mobile malware detection and prevention techniques
- Mobile operating system security (e.g., Android, iOS)
- Secure inter-app communication mechanisms
- Mobile device management (MDM) security
- Biometric authentication on mobile devices
- Secure data storage and transmission on mobile platforms
- Mobile payment security and NFC vulnerabilities
- Location privacy and tracking protection on mobile devices
Cloud Security
- Cloud computing security models and architectures
- Virtualization security and hypervisor vulnerabilities
- Cloud data encryption and key management
- Identity and access management in cloud environments
- Cloud service provider security assurances and certifications
- Cloud-based intrusion detection and incident response
- Data loss prevention (DLP) in cloud storage services
- Secure cloud migration strategies
- Cloud-based disaster recovery and business continuity planning
- Cloud security governance and compliance frameworks
IoT Security
- IoT device authentication and authorization mechanisms
- Secure communication protocols for IoT networks
- IoT firmware update and patch management
- IoT gateway security and edge computing security
- Privacy-preserving techniques for IoT data
- IoT device lifecycle security
- IoT interoperability and security standards
- IoT supply chain security and integrity verification
- IoT botnet detection and mitigation
- IoT security awareness and education for end-users
AI and Machine Learning Security
- Adversarial machine learning and evasion attacks
- Privacy-preserving machine learning techniques
- Secure model training and inference in distributed environments
- AI-driven cyber threat detection and response
- Explainable AI for security applications
- AI-based vulnerability discovery and exploitation
- AI-enabled authentication and access control mechanisms
- Bias and fairness in AI-powered security systems
- AI-based malware detection and classification
- AI-driven security analytics and threat intelligence
Privacy and Data Protection
- Privacy-enhancing technologies (PETs) and their applications
- GDPR compliance and data protection regulations
- Data anonymization and de-identification techniques
- Privacy-preserving data mining and analysis
- Behavioral tracking and online privacy protection mechanisms
- Secure multiparty computation (SMPC) for privacy-preserving data sharing
- Privacy implications of emerging technologies (e.g., IoT, AI)
- Privacy-aware access control models and policies
- Legal and ethical aspects of data privacy and protection
- Privacy-aware risk assessment methodologies
Cyber Threat Intelligence
- Cyber threat hunting and intelligence gathering techniques
- Threat actor profiling and attribution methodologies
- Dark web monitoring and analysis
- Malware analysis and reverse engineering for threat intelligence
- Threat intelligence sharing platforms and standards
- Machine learning for threat intelligence analysis
- Open-source intelligence (OSINT) for cybersecurity
- Cyber threat modeling and risk assessment frameworks
- Automated threat intelligence feeds integration
- Cyber threat intelligence-driven security operations and incident response
Incident Response and Forensics
- Digital forensics methodologies and tools
- Incident response orchestration and automation
- Memory forensics for volatile data acquisition and analysis
- Network forensics techniques and tools
- File system forensics and data recovery
- Live response and volatile data collection in incident response
- Cloud forensics investigation techniques
- Mobile device forensics and data extraction
- Evidence preservation and chain of custody in digital forensics
- Incident response planning and tabletop exercises
Social Engineering and Human Factors
- Psychological techniques used in social engineering attacks
- Security awareness training effectiveness evaluation
- Social engineering countermeasures and awareness programs
- Insider threat detection and mitigation strategies
- Human-centric security policies and procedures
- Influence of organizational culture on security behavior
- Behavioral biometrics for user authentication
- Security education and training for non-technical users
- Neurosecurity: Understanding Human Brain Vulnerabilities
- Usable security design principles for end-user applications
Legal and Policy Issues
- Cybersecurity incident response and coordination frameworks
- Legal challenges in cross-border data transfers
- Intellectual property protection in cyberspace
- Cybersecurity standards and certification programs
- Cybersecurity implications of emerging technologies (e.g., AI, IoT)
- Ethical considerations in cybersecurity research and practice
- Privacy regulations for data sharing and processing
- Cybersecurity implications of remote work and telecommuting
- Cybersecurity and election integrity
- Cybersecurity in critical infrastructure sectors (e.g., energy, transportation)
- International cybersecurity treaties and agreements
Emerging Technologies and Security
- Security challenges in quantum computing and quantum communication
- Security of 5G and beyond-5G networks
- Security implications of augmented reality (AR) and virtual reality (VR)
- Security of biometric authentication systems
- Security and privacy implications of autonomous vehicles
- Blockchain-based secure identity management systems
- Security of smart home devices and ecosystems
- Security implications of edge computing and fog computing
- Secure integration of AI and IoT technologies
- Security considerations in drone technology and autonomous systems
- Securing data in edge computing environments
Cross-cutting Security Topics
- Cybersecurity economics and cost-benefit analysis
- Cyber resilience and disaster recovery planning
- Security implications of global supply chains
- Cybersecurity education and workforce development
- Security implications of quantum internet
- Securing the Internet of Medical Things (IoMT)
- Security of connected vehicles and intelligent transportation systems
- Cybersecurity in the context of social media platforms
- Securing the digital transformation of businesses
- Security of satellite communication systems
These topics cover a broad spectrum of computer security research areas, providing ample opportunities for investigation and innovation in the field.
Closing Up
Computer security is a huge and constantly changing field, providing many opportunities for new and exciting research. With new threats constantly emerging and cyber-attacks becoming more advanced, there is a huge need for fresh, innovative solutions.
This guide has provided a diverse list of over 161 research topic ideas, covering areas like network security, cryptography, malware analysis, data privacy, ethical hacking, and more.
Whether you’re a student looking for a compelling project, a researcher exploring new techniques, or a professional wanting to contribute to the field, these topics offer plenty of possibilities.
By carefully picking a topic that matches current trends, your interests, and real-world applications, you can start a research journey that not only expands your knowledge but could also shape the future of digital security.
The ultimate goal is to develop strong defensive strategies and stay one step ahead of bad actors, protecting our highly connected world from cyber threats.
How do I know if a research topic is relevant to current cybersecurity challenges?
Keeping abreast of industry news, attending conferences, and consulting with experts can help you gauge the relevance of a research topic to current cybersecurity challenges.
Can I conduct interdisciplinary research in computer security?
Absolutely! Many cybersecurity challenges require interdisciplinary approaches, combining insights from computer science, psychology, law, and other fields.
How can I ensure that my research topic is original and not already explored?
Conducting a thorough literature review is essential for identifying gaps in existing research and ensuring the originality of your chosen topic.
Similar Articles

How To Do Homework Fast – 11 Tips To Do Homework Fast
Homework is one of the most important parts that have to be done by students. It has been around for…

How to Write an Assignment Introduction – 6 Best Tips
In essence, the writing tasks in academic tenure students are an integral part of any curriculum. Whether in high school,…
Leave a Comment Cancel Reply
Your email address will not be published. Required fields are marked *
This site uses Akismet to reduce spam. Learn how your comment data is processed .
75 Cyber Security Research Topics in 2024
Introduction to Cybersecurity Research
Cybersecurity research aims to protect computer systems, networks, and data from unauthorised access, theft, or damage. It involves studying and developing methods and techniques to identify, understand, and mitigate cyber threats and vulnerabilities.
The field can be divided into theoretical and applied research and faces challenges such as
- Increasing complexity
- New forms of malware
- The growing sophistication of cyber attacks
On a daily basis, approximately 2,200 cyber attacks occur, with an average of one cyber attack happening every 39 seconds. This is the reason why researchers must stay up-to-date and collaborate with others in the field.
In this article, let’s discuss the different cybersecurity research topics and how they will help you become an expert in the field.

Check out our free technology courses to get an edge over the competition.
Here are some of the latest research topics in cyber security –
Emerging Cyber Threats and Vulnerabilities in 2024
Continual technological advancements lead to changes in cybersecurity trends, with data breaches, ransomware, and hacks becoming more prevalent.
- Cyber Attacks and Their Countermeasures – Discuss – This research paper will discuss various cyber attacks and their corresponding countermeasures. It aims to provide insights on how organisations can better protect themselves from cyber threats.
- Is Cryptography Necessary for Cybersecurity Applications? – Explore the role of cryptography in ensuring the confidentiality, integrity, and availability of data and information in cybersecurity. It would examine the various cryptographic techniques used in cybersecurity and their effectiveness in protecting against cyber threats.
Here are some other cyber security topics that you may consider –
- Discuss the Application of Cyber Security for Cloud-based Applications
- Data Analytics Tools in Cybersecurity
- Malware Analysis
- What Are the Behavioural Aspects of Cyber Security?
- Role of Cyber Security on Intelligent Transporation Systems
- How to Stop and Spot Different Types of Malware?
Check Out upGrad’s Software Development Courses to upskill yourself.
Machine Learning and AI in Cybersecurity Research
Machine learning and AI are research topics in cybersecurity, aiming to develop algorithms for threat detection, enhance intelligence and automate risk mitigation. However, security risks like adversarial attacks require attention.

- Using AI/ML to Analyse Cyber Threats – This cyber security research paper analyses cyber threats and could include an overview of the current state of cyber threats and how AI/ML can help with threat detection and response. The paper could also discuss the challenges and limitations of using AI/ML in cybersecurity and potential areas for further research.
Here are some other topics to consider –
- Developing Cognitive Systems for Cyber Threat Detection and Response
- Developing Distributed Ai Systems to Enhance Cybersecurity
- Developing Deep Learning Architectures for Cyber Defence
- Exploring the Use of Computational Intelligence and Neuroscience in Enhancing Security and Privacy
- How is Cyber Security Relevant for Everyone? Discuss
- Discuss the Importance of Network Traffic Analysis
- How to Build an App to Break Ceasar Cipher
You can check out the Advanced Certificate Programme in Cyber Security course by upGrad, which will help students become experts in cyber security.
IoT Security and Privacy
IoT security and privacy research aim to develop secure and privacy-preserving architectures, protocols, and algorithms for IoT devices, including encryption, access control, and secure communication. The challenge is to balance security with usability while addressing the risk of cyber-attacks and compromised privacy.
- Service Orchestration and Routing for IoT – It may focus on developing efficient and secure methods for managing and routing traffic between IoT devices and services. The paper may explore different approaches for optimising service orchestration.
- Efficient Resource Management, Energy Harvesting, and Power Consumption in IoT – This paper may focus on developing strategies to improve energy use efficiency in IoT devices. This may involve investigating the use of energy harvesting technologies, optimising resource allocation and management, and exploring methods to reduce power consumption.
Here are some other cyber security project topics to consider –
- Computation and Communication Gateways for IoT
- The Miniaturisation of Sensors, Cpus, and Networks in IoT
- Big Data Analytics in IoT
- Semantic Technologies in IoT
- Virtualisation in IoT
- Privacy, Security, Trust, Identity, and Anonymity in IoT
- Heterogeneity, Dynamics, and Scale in IoT
- Consequences of Leaving Unlocked Devices Unattended
Explore our Popular Software Engineering Courses
Blockchain security: research challenges and opportunities.
Blockchain security research aims to develop secure and decentralised architectures, consensus algorithms, and privacy-preserving techniques while addressing challenges such as smart contract security and consensus manipulation. Opportunities include transparent supply chain management and decentralised identity management.
- Advanced Cryptographic Technologies in the Blockchain – Explore the latest advancements and emerging trends in cryptographic techniques used in blockchain-based systems. It could also analyse the security and privacy implications of these technologies and discuss their potential impact.
- Applications of Smart Contracts in Blockchain – Explore the various use cases and potential benefits of using smart contracts to automate and secure business processes. It could also examine the challenges and limitations of smart contracts and propose potential solutions for these issues.
Here are some other topics –
- Ensuring Data Consistency, Transparency, and Privacy in the Blockchain
- Emerging Blockchain Models for Digital Currencies
- Blockchain for Advanced Information Governance Models
- The Role of Blockchain in Future Wireless Mobile Networks
- Law and Regulation Issues in the Blockchain
- Transaction Processing and Modification in the Blockchain
- Collaboration of Big Data With Blockchain Networks
Cloud Security: Trends and Innovations in Research
Cloud security research aims to develop innovative techniques and technologies for securing cloud computing environments, including threat detection with AI, SECaaS, encryption and access control, secure backup and disaster recovery, container security, and blockchain-based solutions. The goal is to ensure the security, privacy, and integrity of cloud-based data and applications for organisations.
- Posture Management in Cloud Security – Discuss the importance of identifying and addressing vulnerabilities in cloud-based systems and strategies for maintaining a secure posture over time. This could include topics such as threat modelling, risk assessment, access control, and continuous monitoring.
- Are Cloud Services 100% Secure?
- What is the Importance of Cloud Security?
- Cloud Security Service to Identify Unauthorised User Behaviour
- Preventing Theft-of-service Attacks and Ensuring Cloud Security on Virtual Machines
- Security Requirements for Cloud Computing
- Privacy and Security of Cloud Computing
Explore Our Software Development Free Courses
Cybercrime investigations and forensics.
Cybercrime investigations and forensics involve analysing digital evidence to identify and prosecute cybercriminals, including developing new data recovery, analysis, and preservation techniques. Research also focuses on identifying cybercriminals and improving legal and regulatory frameworks for prosecuting cybercrime.
- Black Hat and White Hat Hacking: Comparison and Contrast – Explore the similarities and differences between these two approaches to hacking. It would examine the motivations and methods of both types of hackers and their impact on cybersecurity.
- Legal Requirements for Computer Forensics Laboratories
- Wireless Hacking Techniques: Emerging Technologies and Mitigation Strategies
- Cyber Crime: Current Issues and Threats
- Computer Forensics in Law Enforcement: Importance and Challenges
- Basic Procedures for Computer Forensics and Investigations
- Digital Forensic Examination of Counterfeit Documents: Techniques and Tools
- Cybersecurity and Cybercrime: Understanding the Nature and Scope
An integral part of cybercrime investigation is to learn software development. Become experts in this field with the help of upGrad’s Executive Post Graduate Programme in Software Development – Specialisation in Full Stack Development .
Cybersecurity Policy and Regulations
Cybersecurity policy and regulations research aims to develop laws, regulations, and guidelines to ensure the security and privacy of digital systems and data, including addressing gaps in existing policies, promoting international cooperation, and developing standards and best practices for cybersecurity. The goal is to protect digital systems and data while promoting innovation and growth in the digital economy.
- The Ethicality of Government Access to Citizens’ Data – Explore the ethical considerations surrounding government access to citizens’ data for surveillance and security purposes, analysing the potential risks and benefits and the legal and social implications of such access.
- The Moral Permissibility of Using Music Streaming Services – Explore the ethical implications of using music streaming services, examining issues such as intellectual property rights, artist compensation, and the environmental impact of streaming.
- Real Name Requirements on Internet Forums
- Restrictions to Prevent Domain Speculation
- Regulating Adult Content Visibility on the Internet
- Justification for Illegal Downloading
- Adapting Law Enforcement to Online Technologies
- Balancing Data Privacy With Convenience and Centralisation
- Understanding the Nature and Dangers of Cyber Terrorism
Human Factors in Cybersecurity
Human factors in cybersecurity research study how human behaviour impacts cybersecurity, including designing interfaces, developing security training, addressing user error and negligence, and examining cybersecurity’s social and cultural aspects. The goal is to improve security by mitigating human-related security risks.
- Review the Human Factors in Cybersecurity – It explores various human factors such as awareness, behaviour, training, and culture and their influence on cybersecurity, offering insights and recommendations for improving cybersecurity outcomes.
- Integrating Human Factors in Cybersecurity for Better Risk Management
- Address the Human Factors in Cybersecurity Leadership
- Human Factors in IoT Security
- Internal Vulnerabilities: the Human Factor in It Security
- Cyber Security Human Factors – the Ultimate List of Statistics and Data
In-Demand Software Development Skills
Cybersecurity education and awareness.
Cybersecurity education and awareness aims to educate individuals and organisations about potential cybersecurity threats and best practices to prevent cyber attacks. It involves promoting safe online behaviour, training on cybersecurity protocols, and raising awareness about emerging cyber threats.
- Identifying Phishing Attacks – This research paper explores various techniques and tools to identify and prevent phishing attacks, which are common types of cyber attacks that rely on social engineering tactics to trick victims into divulging sensitive information or installing malware on their devices.
- Risks of Password Reuse for Personal and Professional Accounts – Investigate the risks associated with reusing the same password across different personal and professional accounts, such as the possibility of credential stuffing attacks and the impact of compromised accounts on organisational security.
- Effective Defence Against Ransomware
- Information Access Management: Privilege and Need-to-know Access
- Protecting Sensitive Data on Removable Media
- Recognising Social Engineering Attacks
- Preventing Unauthorised Access to Secure Areas: Detecting Piggybacking and Tailgating
- E-mail Attack and Its Characteristics
- Safe Wifi Practice: Understanding VPN
With the increasing use of digital systems and networks, avoiding potential cyber-attacks is more important than ever. The 75 research topics outlined in this list offer a glimpse into the different dimensions of this important field. By focusing on these areas, researchers can make significant contributions to enhancing the security and safety of individuals, organisations, and society as a whole.
upGrad’s Master of Science in Computer Science program is one of the top courses students can complete to become experts in the field of tech and cyber security. The program covers topics such as Java Programming and other forms of software engineering which will help students understand the latest technologies and techniques used in cyber security.
The program also includes hands-on projects and case studies to ensure students have practical experience in applying these concepts. Graduates will be well-equipped to take on challenging roles in the rapidly growing field of cyber security.

Pavan Vadapalli
Something went wrong
Our Trending Software Engineering Courses
- Master of Science in Computer Science from LJMU
- Executive PG Program in Software Development Specialisation in Full Stack Development from IIIT-B
- Advanced Certificate Programme in Cyber Security from IIITB
- Full Stack Software Development Bootcamp
- Software Engineering Bootcamp from upGrad
Popular Software Development Skills
- React Courses
- Javascript Courses
- Core Java Courses
- Data Structures Courses
- ReactJS Courses
- NodeJS Courses
- Blockchain Courses
- SQL Courses
- Full Stack Development Courses
- Big Data Courses
- Devops Courses
- NFT Courses
- Cyber Security Courses
- Cloud Computing Courses
- Database Design Courses
- Crypto Courses
- Python Courses
Our Popular Software Engineering Courses
Frequently Asked Questions (FAQs)
Artificial intelligence (AI) has proved to be an effective tool in cyber defence. AI is anticipated to gain even more prominence in 2024, mainly in monitoring, resource and threat analysis, and quick response capabilities.
One area of focus is the development of secure quantum and space communications to address the increasing use of quantum technologies and space travel. Another area of research is improving data privacy.
The approach to cybersecurity is expected to change from defending against attacks to acknowledging and managing ongoing cyber risks. The focus will be on improving resilience and recovering from potential cyber incidents.
Related Programs View All
Certification
40 Hrs Live, Expert-Led Sessions
2 High-Quality Practice Exams
View Program

Executive PG Program
IIIT-B Alumni Status

Master's Degree
40000+ Enrolled Learners

Job Assistance
32-Hr Training by Dustin Brimberry
Question Bank with 300+ Practice Qs
45 Hrs Live Expert-Led Training
Microsoft-Approved Curriculum
159+ Hours of Live Sessions
126+ Hours of Live Sessions
Fully Online
13+ Hrs Instructor-Led Sessions
Live Doubt-Solving Sessions

2 Unique Specialisations
300+ Hiring Partners
20+ Hrs Instructor-Led Sessions
16 Hrs Live Expert-Led Training
CLF-C02 Exam Prep Support

24 Hrs Live Expert-Led Training
4 Real-World Capstone Projects
17+ Hrs Instructor-Led Training
3 Real-World Capstone Projects
289 Hours of Self-Paced Learning
10+ Capstone Projects
490+ Hours Self-Paced Learning
4 Real-World Projects
690+ Hours Self-Paced Learning
Cloud Labs-Enabled Learning
288 Hours Self-Paced Learning
9 Capstone Projects
40 Hrs Live Expert-Led Sessions
2 Mock Exams, 9 Assessments

Executive PG Certification
GenAI integrated curriculum

Job Prep Support
Instructor-Led Sessions
Hands-on UI/UX
16 Hrs Live Expert-Led Sessions
12 Hrs Hand-On Practice
30+ Hrs Live Expert-Led Sessions
24+ Hrs Hands-On with Open Stack
2 Days Live, Expert-Led Sessions
34+ Hrs Instructor-Led Sessions
10 Real-World Live Projects
24 Hrs Live Expert-Led Sessions
16 Hrs Hand-On Practice
8 Hrs Instructor-Led Training
Case-Study Based Discussions
40 Hrs Instructor-Led Sessions
Hands-On Practice, Exam Support
24-Hrs Live Expert-Led Sessions
Regular Doubt-Clearing Sessions
Extensive Exam Prep Support
6 Hrs Live Expert-Led Sessions
440+ Hours Self-Paced Learning
400 Hours of Cloud Labs
15-Hrs Live Expert-Led Sessions
32 Hrs Live Expert-Led Sessions
28 Hrs Hand-On Practice
Mentorship by Industry Experts
24 Hrs Live Trainer-Led Sessions
Mentorship by Certified Trainers
GenAI Integrated Curriculum
Full Access to Digital Resources
16 Hrs Live Instructor-Led Sessions
80+ Hrs Hands-On with Cloud Labs
160+ Hours Live Instructor-Led Sessions
Hackathons and Mock Interviews
31+ Hrs Instructor-Led Sessions
120+ Hrs of Cloud Labs Access
35+ Hrs Instructor-Led Sessions
6 Real-World Live Projects
24+ Hrs Instructor-Led Training
Self-Paced Course by Nikolai Schuler
Access Digital Resources Library
300+ Hrs Live Expert-Led Training
90 Hrs Doubt Clearing Sessions
56 Hours Instructor-Led Sessions
82 Hrs Live Expert-Led Sessions
22 Hrs Live, Expert-Led Sessions
CISA Job Practice Exams
Explore Free Courses
Learn more about the education system, top universities, entrance tests, course information, and employment opportunities in Canada through this course.
Advance your career in the field of marketing with Industry relevant free courses
Build your foundation in one of the hottest industry of the 21st century
Master industry-relevant skills that are required to become a leader and drive organizational success
Build essential technical skills to move forward in your career in these evolving times
Get insights from industry leaders and career counselors and learn how to stay ahead in your career
Kickstart your career in law by building a solid foundation with these relevant free courses.
Stay ahead of the curve and upskill yourself on Generative AI and ChatGPT
Build your confidence by learning essential soft skills to help you become an Industry ready professional.
Learn more about the education system, top universities, entrance tests, course information, and employment opportunities in USA through this course.
Suggested Tutorials

Explore Python programming with this concise tutorial, covering basics to advanced concepts for beginners and enthusiasts alike.

Introduction to C Programming, Learn all the C programming language concepts in this tutorial.
Suggested Blogs
by Rohan Vats
28 May 2024
![computer security research paper ideas Top 20 Highest Paying Programming Languages In India [2024]](https://www.upgrad.com/__khugblog-next/image/?url=https%3A%2F%2Fd14b9ctw0m6fid.cloudfront.net%2Fugblog%2Fwp-content%2Fuploads%2F2020%2F08%2F907-Banner.png&w=3840&q=75)
26 May 2024
![computer security research paper ideas 28 Best Software Development Project Ideas & Topics for Beginners [Updated 2024]](https://www.upgrad.com/__khugblog-next/image/?url=https%3A%2F%2Fd14b9ctw0m6fid.cloudfront.net%2Fugblog%2Fwp-content%2Fuploads%2F2020%2F05%2F559-Software-Development-Project-Ideas.png&w=3840&q=75)
21 May 2024
![computer security research paper ideas 33 Best Computer Science Project Ideas & Topics For Beginners [Latest 2024]](https://www.upgrad.com/__khugblog-next/image/?url=https%3A%2F%2Fd14b9ctw0m6fid.cloudfront.net%2Fugblog%2Fwp-content%2Fuploads%2F2020%2F09%2F909-Banner.png&w=3840&q=75)
by Pavan Vadapalli
19 May 2024
![computer security research paper ideas DevOps Engineer Salary in India in 2024 [For Freshers & Experienced]](https://www.upgrad.com/__khugblog-next/image/?url=https%3A%2F%2Fd14b9ctw0m6fid.cloudfront.net%2Fugblog%2Fwp-content%2Fuploads%2F2019%2F10%2FBlog_FI_Nov_DevOps-Engineer-Salary.png&w=3840&q=75)
16 May 2024
14 May 2024
![computer security research paper ideas Types of Polymorphism in Java [Static & Dynamic Polymorphism with Examples]](https://www.upgrad.com/__khugblog-next/image/?url=https%3A%2F%2Fd14b9ctw0m6fid.cloudfront.net%2Fugblog%2Fwp-content%2Fuploads%2F2021%2F06%2F18080334%2F2127.png&w=3840&q=75)
13 May 2024
12 Apr 2024
- Search Menu
- Sign in through your institution
- Editor's Choice
- Author Guidelines
- Submission Site
- Open Access
- About Journal of Cybersecurity
- Editorial Board
- Advertising and Corporate Services
- Journals Career Network
- Self-Archiving Policy
- Journals on Oxford Academic
- Books on Oxford Academic

Editors-in-Chief
Tyler Moore
About the journal
Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …
Latest articles

Call for Papers: Workshop on the Economics of Information Security
Journal of Cybersecurity is inviting submissions to a new special issue from the workshop on the economics of information security. Authors whose papers appeared at the workshop are invited to submit a revised version to the journal.

Call for Papers
Journal of Cybersecurity is soliciting papers for a special collection on the philosophy of information security. This collection will explore research at the intersection of philosophy, information security, and philosophy of science.
Find out more

Submit your paper
Join the conversation moving the science of security forward. Visit our Instructions to Authors for more information about how to submit your manuscript.

High-Impact Research Collection
Explore a collection of recently published high-impact research in the Journal of Cybersecurity .
Browse the collection here

Email alerts
Register to receive table of contents email alerts as soon as new issues of Journal of Cybersecurity are published online.

Read and Publish deals
Authors interested in publishing in Journal of Cybersecurity may be able to publish their paper Open Access using funds available through their institution’s agreement with OUP.
Find out if your institution is participating
Related Titles

Affiliations
- Online ISSN 2057-2093
- Print ISSN 2057-2085
- Copyright © 2024 Oxford University Press
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.
- Open access
- Published: 10 August 2020
Using deep learning to solve computer security challenges: a survey
- Yoon-Ho Choi 1 , 2 ,
- Peng Liu 1 ,
- Zitong Shang 1 ,
- Haizhou Wang 1 ,
- Zhilong Wang 1 ,
- Lan Zhang 1 ,
- Junwei Zhou 3 &
- Qingtian Zou 1
Cybersecurity volume 3 , Article number: 15 ( 2020 ) Cite this article
16k Accesses
21 Citations
1 Altmetric
Metrics details
Although using machine learning techniques to solve computer security challenges is not a new idea, the rapidly emerging Deep Learning technology has recently triggered a substantial amount of interests in the computer security community. This paper seeks to provide a dedicated review of the very recent research works on using Deep Learning techniques to solve computer security challenges. In particular, the review covers eight computer security problems being solved by applications of Deep Learning: security-oriented program analysis, defending return-oriented programming (ROP) attacks, achieving control-flow integrity (CFI), defending network attacks, malware classification, system-event-based anomaly detection, memory forensics, and fuzzing for software security.
Introduction
Using machine learning techniques to solve computer security challenges is not a new idea. For example, in the year of 1998, Ghosh and others in ( Ghosh et al. 1998 ) proposed to train a (traditional) neural network based anomaly detection scheme(i.e., detecting anomalous and unknown intrusions against programs); in the year of 2003, Hu and others in ( Hu et al. 2003 ) and Heller and others in ( Heller et al. 2003 ) applied Support Vector Machines to based anomaly detection scheme (e.g., detecting anomalous Windows registry accesses).
The machine-learning-based computer security research investigations during 1990-2010, however, have not been very impactful. For example, to the best of our knowledge, none of the machine learning applications proposed in ( Ghosh et al. 1998 ; Hu et al. 2003 ; Heller et al. 2003 ) has been incorporated into a widely deployed intrusion-detection commercial product.
Regarding why not very impactful, although researchers in the computer security community seem to have different opinions, the following remarks by Sommer and Paxson ( Sommer and Paxson 2010 ) (in the context of intrusion detection) have resonated with many researchers:
Remark A: “It is crucial to have a clear picture of what problem a system targets: what specifically are the attacks to be detected? The more narrowly one can define the target activity, the better one can tailor a detector to its specifics and reduce the potential for misclassifications.” ( Sommer and Paxson 2010 )
Remark B: “If one cannot make a solid argument for the relation of the features to the attacks of interest, the resulting study risks foundering on serious flaws.” ( Sommer and Paxson 2010 )
These insightful remarks, though well aligned with the machine learning techniques used by security researchers during 1990-2010, could become a less significant concern with Deep Learning (DL), a rapidly emerging machine learning technology, due to the following observations. First, Remark A implies that even if the same machine learning method is used, one algorithm employing a cost function that is based on a more specifically defined target attack activity could perform substantially better than another algorithm deploying a less specifically defined cost function. This could be a less significant concern with DL, since a few recent studies have shown that even if the target attack activity is not narrowly defined, a DL model could still achieve very high classification accuracy. Second, Remark B implies that if feature engineering is not done properly, the trained machine learning models could be plagued by serious flaws. This could be a less significant concern with DL, since many deep learning neural networks require less feature engineering than conventional machine learning techniques.
As stated in NSCAI Intern Report for Congress (2019 ), “DL is a statistical technique that exploits large quantities of data as training sets for a network with multiple hidden layers, called a deep neural network (DNN). A DNN is trained on a dataset, generating outputs, calculating errors, and adjusting its internal parameters. Then the process is repeated hundreds of thousands of times until the network achieves an acceptable level of performance. It has proven to be an effective technique for image classification, object detection, speech recognition, and natural language processing–problems that challenged researchers for decades. By learning from data, DNNs can solve some problems much more effectively, and also solve problems that were never solvable before.”
Now let’s take a high-level look at how DL could make it substantially easier to overcome the challenges identified by Sommer and Paxson ( Sommer and Paxson 2010 ). First, one major advantage of DL is that it makes learning algorithms less dependent on feature engineering. This characteristic of DL makes it easier to overcome the challenge indicated by Remark B. Second, another major advantage of DL is that it could achieve high classification accuracy with minimum domain knowledge. This characteristic of DL makes it easier to overcome the challenge indicated by Remark A.
Key observation. The above discussion indicates that DL could be a game changer in applying machine learning techniques to solving computer security challenges.
Motivated by this observation, this paper seeks to provide a dedicated review of the very recent research works on using Deep Learning techniques to solve computer security challenges. It should be noticed that since this paper aims to provide a dedicated review, non-deep-learning techniques and their security applications are out of the scope of this paper.
The remaining of the paper is organized as follows. In “ A four-phase workflow framework can summarize the existing works in a unified manner ” section, we present a four-phase workflow framework which we use to summarize the existing works in a unified manner. In “ A closer look at applications of deep learning in solving security-oriented program analysis challenges - A closer look at applications of deep learning in security-oriented fuzzing ” section, we provide a review of eight computer security problems being solved by applications of Deep Learning, respectively. In “ Discussion ” section, we will discuss certain similarity and certain dissimilarity among the existing works. In “ Further areas of investigation ” section, we mention four further areas of investigation. In “ Conclusion section, we conclude the paper.
A four-phase workflow framework can summarize the existing works in a unified manner
We found that a four-phase workflow framework can provide a unified way to summarize all the research works surveyed by us. In particular, we found that each work surveyed by us employs a particular workflow when using machine learning techniques to solve a computer security challenge, and we found that each workflow consists of two or more phases. By “a unified way”, we mean that every workflow surveyed by us is essentially an instantiation of a common workflow pattern which is shown in Fig. 1 .
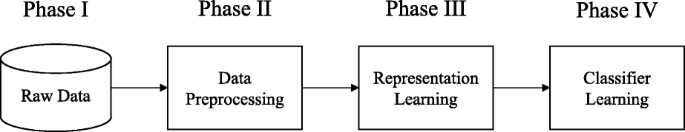
Overview of the four-phase workflow
Definitions of the four phases
The four phases, shown in Fig. 1 , are defined as follows. To make the definitions of the four phases more tangible, we use a running example to illustrate each of the four phases. Phase I.(Obtaining the raw data)
In this phase, certain raw data are collected. Running Example: When Deep Learning is used to detect suspicious events in a Hadoop distributed file system (HDFS), the raw data are usually the events (e.g., a block is allocated, read, written, replicated, or deleted) that have happened to each block. Since these events are recorded in Hadoop logs, the log files hold the raw data. Since each event is uniquely identified by a particular (block ID, timestamp) tuple, we could simply view the raw data as n event sequences. Here n is the total number of blocks in the HDFS. For example, the raw data collected in Xu et al. (2009) in total consists of 11,197,954 events. Since 575,139 blocks were in the HDFS, there were 575,139 event sequences in the raw data, and on average each event sequence had 19 events. One such event sequence is shown as follows:
Phase II.(Data preprocessing)
Both Phase II and Phase III aim to properly extract and represent the useful information held in the raw data collected in Phase I. Both Phase II and Phase III are closely related to feature engineering. A key difference between Phase II and Phase III is that Phase III is completely dedicated to representation learning, while Phase II is focused on all the information extraction and data processing operations that are not based on representation learning. Running Example: Let’s revisit the aforementioned HDFS. Each recorded event is described by unstructured text. In Phase II, the unstructured text is parsed to a data structure that shows the event type and a list of event variables in (name, value) pairs. Since there are 29 types of events in the HDFS, each event is represented by an integer from 1 to 29 according to its type. In this way, the aforementioned example event sequence can be transformed to:
22, 5, 5, 7
Phase III.(Representation learning)
As stated in Bengio et al. (2013) , “Learning representations of the data that make it easier to extract useful information when building classifiers or other predictors.” Running Example: Let’s revisit the same HDFS. Although DeepLog ( Du et al. 2017 ) directly employed one-hot vectors to represent the event types without representation learning, if we view an event type as a word in a structured language, one may actually use the word embedding technique to represent each event type. It should be noticed that the word embedding technique is a representation learning technique.
Phase IV.(Classifier learning)
This phase aims to build specific classifiers or other predictors through Deep Learning. Running Example: Let’s revisit the same HDFS. DeepLog ( Du et al. 2017 ) used Deep Learning to build a stacked LSTM neural network for anomaly detection. For example, let’s consider event sequence {22,5,5,5,11,9,11,9,11,9,26,26,26} in which each integer represents the event type of the corresponding event in the event sequence. Given a window size h = 4, the input sample and the output label pairs to train DeepLog will be: {22,5,5,5 → 11 }, {5,5,5,11 → 9 }, {5,5,11,9 → 11 }, and so forth. In the detection stage, DeepLog examines each individual event. It determines if an event is treated as normal or abnormal according to whether the event’s type is predicted by the LSTM neural network, given the history of event types. If the event’s type is among the top g predicted types, the event is treated as normal; otherwise, it is treated as abnormal.
Using the four-phase workflow framework to summarize some representative research works
In this subsection, we use the four-phase workflow framework to summarize two representative works for each security problem. System security includes many sub research topics. However, not every research topics are suitable to adopt deep learning-based methods due to their intrinsic characteristics. For these security research subjects that can combine with deep-learning, some of them has undergone intensive research in recent years, others just emerging. We notice that there are 5 mainstream research directions in system security. This paper mainly focuses on system security, so the other mainstream research directions (e.g., deepfake) are out-of-scope. Therefore, we choose these 5 widely noticed research directions, and 3 emerging research direction in our survey:
In security-oriented program analysis, malware classification (MC), system-event-based anomaly detection (SEAD), memory forensics (MF), and defending network attacks, deep learning based methods have already undergone intensive research.
In defending return-oriented programming (ROP) attacks, Control-flow integrity (CFI), and fuzzing, deep learning based methods are emerging research topics.
We select two representative works for each research topic in our survey. Our criteria to select papers mainly include: 1) Pioneer (one of the first papers in this field); 2) Top (published on top conference or journal); 3) Novelty; 4) Citation (The citation of this paper is high); 5) Effectiveness (the result of this paper is pretty good); 6) Representative (the paper is a representative work for a branch of the research direction). Table 1 lists the reasons why we choose each paper, which is ordered according to their importance.
The summary is shown in Table 2 . There are three columns in the table. In the first column, we listed eight security problems, including security-oriented program analysis, defending return-oriented programming (ROP) attacks, control-flow integrity (CFI), defending network attacks (NA), malware classification (MC), system-event-based anomaly detection (SEAD), memory forensics (MF), and fuzzing for software security. In the second column, we list the very recent two representative works for each security problem. In the “Summary” column, we sequentially describe how the four phases are deployed at each work, then, we list the evaluation results for each work in terms of accuracy (ACC), precision (PRC), recall (REC), F1 score (F1), false-positive rate (FPR), and false-negative rate (FNR), respectively.
Methodology for reviewing the existing works
Data representation (or feature engineering) plays an important role in solving security problems with Deep Learning. This is because data representation is a way to take advantage of human ingenuity and prior knowledge to extract and organize the discriminative information from the data. Many efforts in deploying machine learning algorithms in security domain actually goes into the design of preprocessing pipelines and data transformations that result in a representation of the data to support effective machine learning.
In order to expand the scope and ease of applicability of machine learning in security domain, it would be highly desirable to find a proper way to represent the data in security domain, which can entangle and hide more or less the different explanatory factors of variation behind the data. To let this survey adequately reflect the important role played by data representation, our review will focus on how the following three questions are answered by the existing works:
Question 1: Is Phase II pervasively done in the literature? When Phase II is skipped in a work, are there any particular reasons?
Question 2: Is Phase III employed in the literature? When Phase III is skipped in a work, are there any particular reasons?
Question 3: When solving different security problems, is there any commonality in terms of the (types of) classifiers learned in Phase IV? Among the works solving the same security problem, is there dissimilarity in terms of classifiers learned in Phase IV?
To group the Phase III methods at different applications of Deep Learning in solving the same security problem, we introduce a classification tree as shown in Fig. 2 . The classification tree categorizes the Phase III methods in our selected survey works into four classes. First, class 1 includes the Phase III methods which do not consider representation learning. Second, class 2 includes the Phase III methods which consider representation learning but, do not adopt it. Third, class 3 includes the Phase III methods which consider and adopt representation learning but, do not compare the performance with other methods. Finally, class 4 includes the Phase III methods which consider and adopt representation learning and, compare the performance with other methods.
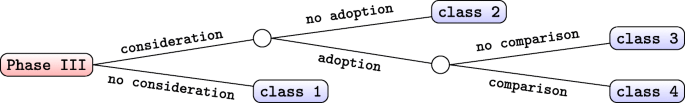
Classification tree for different Phase III methods. Here, consideration , adoption , and comparison indicate that a work considers Phase III, adopts Phase III and makes comparison with other methods, respectively
In the remaining of this paper, we take a closer look at how each of the eight security problems is being solved by applications of Deep Learning in the literature.
A closer look at applications of deep learning in solving security-oriented program analysis challenges
Recent years, security-oriented program analysis is widely used in software security. For example, symbolic execution and taint analysis are used to discover, detect and analyze vulnerabilities in programs. Control flow analysis, data flow analysis and pointer/alias analysis are important components when enforcing many secure strategies, such as control flow integrity, data flow integrity and doling dangling pointer elimination. Reverse engineering was used by defenders and attackers to understand the logic of a program without source code.
In the security-oriented program analysis, there are many open problems, such as precise pointer/alias analysis, accurate and complete reversing engineer, complex constraint solving, program de-obfuscation, and so on. Some problems have theoretically proven to be NP-hard, and others still need lots of human effort to solve. Either of them needs a lot of domain knowledge and experience from expert to develop better solutions. Essentially speaking, the main challenges when solving them through traditional approaches are due to the sophisticated rules between the features and labels, which may change in different contexts. Therefore, on the one hand, it will take a large quantity of human effort to develop rules to solve the problems, on the other hand, even the most experienced expert cannot guarantee completeness. Fortunately, the deep learning method is skillful to find relations between features and labels if given a large amount of training data. It can quickly and comprehensively find all the relations if the training samples are representative and effectively encoded.
In this section, we will review the very recent four representative works that use Deep Learning for security-oriented program analysis. We observed that they focused on different goals. Shin, et al. designed a model ( Shin et al. 2015 ) to identify the function boundary. EKLAVYA ( Chua et al. 2017 ) was developed to learn the function type. Gemini ( Xu et al. 2017 ) was proposed to detect similarity among functions. DEEPVSA ( Guo et al. 2019 ) was designed to learn memory region of an indirect addressing from the code sequence. Among these works, we select two representative works ( Shin et al. 2015 ; Chua et al. 2017 ) and then, summarize the analysis results in Table 2 in detail.
Our review will be centered around three questions described in “ Methodology for reviewing the existing works ” section. In the remaining of this section, we will first provide a set of observations, and then we provide the indications. Finally, we provide some general remarks.
Key findings from a closer look
From a close look at the very recent applications using Deep Learning for solving security-oriented program analysis challenges, we observed the followings:
Observation 3.1: All of the works in our survey used binary files as their raw data. Phase II in our survey had one similar and straightforward goal – extracting code sequences from the binary. Difference among them was that the code sequence was extracted directly from the binary file when solving problems in static program analysis, while it was extracted from the program execution when solving problems in dynamic program analysis.
*Observation 3.2: Most data representation methods generally took into account the domain knowledge.
Most data representation methods generally took into the domain knowledge, i.e., what kind of information they wanted to reserve when processing their data. Note that the feature selection has a wide influence on Phase II and Phase III, for example, embedding granularities, representation learning methods. Gemini ( Xu et al. 2017 ) selected function level feature and other works in our survey selected instruction level feature. To be specifically, all the works except Gemini ( Xu et al. 2017 ) vectorized code sequence on instruction level.
Observation 3.3: To better support data representation for high performance, some works adopted representation learning.
For instance, DEEPVSA ( Guo et al. 2019 ) employed a representation learning method, i.e., bi-directional LSTM, to learn data dependency within instructions. EKLAVYA ( Chua et al. 2017 ) adopted representation learning method, i.e., word2vec technique, to extract inter-instruciton information. It is worth noting that Gemini ( Xu et al. 2017 ) adopts the Structure2vec embedding network in its siamese architecture in Phase IV (see details in Observation 3.7). The Structure2vec embedding network learned information from an attributed control flow graph.
Observation 3.4: According to our taxonomy, most works in our survey were classified into class 4.
To compare the Phase III, we introduced a classification tree with three layers as shown in Fig. 2 to group different works into four categories. The decision tree grouped our surveyed works into four classes according to whether they considered representation learning or not, whether they adopted representation learning or not, and whether they compared their methods with others’, respectively, when designing their framework. According to our taxonomy, EKLAVYA ( Chua et al. 2017 ), DEEPVSA ( Guo et al. 2019 ) were grouped into class 4 shown in Fig. 2 . Also, Gemini’s work ( Xu et al. 2017 ) and Shin, et al.’s work ( Shin et al. 2015 ) belonged to class 1 and class 2 shown in Fig. 2 , respectively.
Observation 3.5: All the works in our survey explain why they adopted or did not adopt one of representation learning algorithms.
Two works in our survey adopted representation learning for different reasons: to enhance model’s ability of generalization ( Chua et al. 2017 ); and to learn the dependency within instructions ( Guo et al. 2019 ). It is worth noting that Shin, et al. did not adopt representation learning because they wanted to preserve the “attractive” features of neural networks over other machine learning methods – simplicity. As they stated, “first, neural networks can learn directly from the original representation with minimal preprocessing (or “feature engineering”) needed.” and “second, neural networks can learn end-to-end, where each of its constituent stages are trained simultaneously in order to best solve the end goal.” Although Gemini ( Xu et al. 2017 ) did not adopt representation learning when processing their raw data, the Deep Learning models in siamese structure consisted of two graph embedding networks and one cosine function.
*Observation 3.6: The analysis results showed that a suitable representation learning method could improve accuracy of Deep Learning models.
DEEPVSA ( Guo et al. 2019 ) designed a series of experiments to evaluate the effectiveness of its representative method. By combining with the domain knowledge, EKLAVYA ( Chua et al. 2017 ) employed t-SNE plots and analogical reasoning to explain the effectiveness of their representation learning method in an intuitive way.
Observation 3.7: Various Phase IV methods were used.
In Phase IV, Gemini ( Xu et al. 2017 ) adopted siamese architecture model which consisted of two Structure2vec embedding networks and one cosine function. The siamese architecture took two functions as its input, and produced the similarity score as the output. The other three works ( Shin et al. 2015 ; Chua et al. 2017 ; Guo et al. 2019 ) adopted bi-directional RNN, RNN, bi-directional LSTM respectively. Shin, et al. adopted bi-directional RNN because they wanted to combine both the past and the future information in making a prediction for the present instruction ( Shin et al. 2015 ). DEEPVSA ( Guo et al. 2019 ) adopted bi-directional RNN to enable their model to infer memory regions in both forward and backward ways.
The above observations seem to indicate the following indications:
Indication 3.1: Phase III is not always necessary.
Not all authors regard representation learning as a good choice even though some case experiments show that representation learning can improve the final results. They value more the simplicity of Deep Learning methods and suppose that the adoption of representation learning weakens the simplicity of Deep Learning methods.
Indication 3.2: Even though the ultimate objective of Phase III in the four surveyed works is to train a model with better accuracy, they have different specific motivations as described in Observation 3.5.
When authors choose representation learning, they usually try to convince people the effectiveness of their choice by empirical or theoretical analysis.
*Indication 3.3: Observation 3.7 indicates that authors usually refer to the domain knowledge when designing the architecture of Deep Learning model.
For instance, the works we reviewed commonly adopt bi-directional RNN when their prediction partly based on future information in data sequence.
Despite the effectiveness and agility of deep learning-based methods, there are still some challenges in developing a scheme with high accuracy due to the hierarchical data structure, lots of noisy, and unbalanced data composition in program analysis. For instance, an instruction sequence, a typical data sample in program analysis, contains three-level hierarchy: sequence–instruction–opcode/operand. To make things worse, each level may contain many different structures, e.g., one-operand instructions, multi-operand instructions, which makes it harder to encode the training data.
A closer look at applications of deep learning in defending ROP attacks
Return-oriented programming (ROP) attack is one of the most dangerous code reuse attacks, which allows the attackers to launch control-flow hijacking attack without injecting any malicious code. Rather, It leverages particular instruction sequences (called “gadgets”) widely existing in the program space to achieve Turing-complete attacks ( Shacham and et al. 2007 ). Gadgets are instruction sequences that end with a RET instruction. Therefore, they can be chained together by specifying the return addresses on program stack. Many traditional techniques could be used to detect ROP attacks, such as control-flow integrity (CFI Abadi et al. (2009) ), but many of them either have low detection rate or have high runtime overhead. ROP payloads do not contain any codes. In other words, analyzing ROP payload without the context of the program’s memory dump is meaningless. Thus, the most popular way of detecting and preventing ROP attacks is control-flow integrity. The challenge after acquiring the instruction sequences is that it is hard to recognize whether the control flow is normal. Traditional methods use the control flow graph (CFG) to identify whether the control flow is normal, but attackers can design the instruction sequences which follow the normal control flow defined by the CFG. In essence, it is very hard to design a CFG to exclude every single possible combination of instructions that can be used to launch ROP attacks. Therefore, using data-driven methods could help eliminate such problems.
In this section, we will review the very recent three representative works that use Deep Learning for defending ROP attacks: ROPNN ( Li et al. 2018 ), HeNet ( Chen et al. 2018 ) and DeepCheck ( Zhang et al. 2019 ). ROPNN ( Li et al. 2018 ) aims to detect ROP attacks, HeNet ( Chen et al. 2018 ) aims to detect malware using CFI, and DeepCheck ( Zhang et al. 2019 ) aims at detecting all kinds of code reuse attacks.
Specifically, ROPNN is to protect one single program at a time, and its training data are generated from real-world programs along with their execution. Firstly, it generates its benign and malicious data by “chaining-up” the normally executed instruction sequences and “chaining-up” gadgets with the help of gadgets generation tool, respectively, after the memory dumps of programs are created. Each data sample is byte-level instruction sequence labeled as “benign” or “malicious”. Secondly, ROPNN will be trained using both malicious and benign data. Thirdly, the trained model is deployed to a target machine. After the protected program started, the executed instruction sequences will be traced and fed into the trained model, the protected program will be terminated once the model found the instruction sequences are likely to be malicious.
HeNet is also proposed to protect a single program. Its malicious data and benign data are generated by collecting trace data through Intel PT from malware and normal software, respectively. Besides, HeNet preprocesses its dataset and shape each data sample in the format of image, so that they could implement transfer learning from a model pre-trained on ImageNet. Then, HeNet is trained and deployed on machines with features of Intel PT to collect and classify the program’s execution trace online.
The training data for DeepCheck are acquired from CFGs, which are constructed by dissembling the programs and using the information from Intel PT. After the CFG for a protected program is constructed, authors sample benign instruction sequences by chaining up basic blocks that are connected by edges, and sample malicious instruction sequences by chaining up those that are not connected by edges. Although a CFG is needed during training, there is no need to construct CFG after the training phase. After deployed, instruction sequences will be constructed by leveraging Intel PT on the protected program. Then the trained model will classify whether the instruction sequences are malicious or benign.
We observed that none of the works considered Phase III, so all of them belong to class 1 according to our taxonomy as shown in Fig. 2 . The analysis results of ROPNN ( Li et al. 2018 ) and HeNet ( Chen et al. 2018 ) are shown in Table 2 . Also, we observed that three works had different goals.
From a close look at the very recent applications using Deep Learning for defending return-oriented programming attacks, we observed the followings:
Observation 4.1: All the works ( Li et al. 2018 ; Zhang et al. 2019 ; Chen et al. 2018 ) in this survey focused on data generation and acquisition.
In ROPNN ( Li et al. 2018 ), both malicious samples (gadget chains) were generated using an automated gadget generator (i.e. ROPGadget ( Salwant 2015 )) and a CPU emulator (i.e. Unicorn ( Unicorn-The ultimate CPU emulator 2015 )). ROPGadget was used to extract instruction sequences that could be used as gadgets from a program, and Unicorn was used to validate the instruction sequences. Corresponding benign sample (gadget-chain-like instruction sequences) were generated by disassembling a set of programs. In DeepCheck ( Zhang et al. 2019 ) refers to the key idea of control-flow integrity ( Abadi et al. 2009 ). It generates program’s run-time control flow through new feature of Intel CPU (Intel Processor Tracing), then compares the run-time control flow with the program’s control-flow graph (CFG) that generates through static analysis. Benign instruction sequences are that with in the program’s CFG, and vice versa. In HeNet ( Chen et al. 2018 ), program’s execution trace was extracted using the similar way as DeepCheck. Then, each byte was transformed into a pixel with an intensity between 0-255. Known malware samples and benign software samples were used to generate malicious data benign data, respectively.
Observation 4.2: None of the ROP works in this survey deployed Phase III.
Both ROPNN ( Li et al. 2018 ) and DeepCheck ( Zhang et al. 2019 ) used binary instruction sequences for training. In ROPNN ( Li et al. 2018 ), one byte was used as the very basic element for data pre-processing. Bytes were formed into one-hot matrices and flattened for 1-dimensional convolutional layer. In DeepCheck ( Zhang et al. 2019 ), half-byte was used as the basic unit. Each half-byte (4 bits) was transformed to decimal form ranging from 0-15 as the basic element of the input vector, then was fed into a fully-connected input layer. On the other hand, HeNet ( Chen et al. 2018 ) used different kinds of data. By the time this survey has been drafted, the source code of HeNet was not available to public and thus, the details of the data pre-processing was not be investigated. However, it is still clear that HeNet used binary branch information collected from Intel PT rather than binary instructions. In HeNet, each byte was converted to one decimal number ranging from 0 to 255. Byte sequences was sliced and formed into image sequences (each pixel represented one byte) for a fully-connected input layer.
Observation 4.3: Fully-connected neural network was widely used.
Only ROPNN ( Li et al. 2018 ) used 1-dimensional convolutional neural network (CNN) when extracting features. Both HeNet ( Chen et al. 2018 ) and DeepCheck ( Zhang et al. 2019 ) used fully-connected neural network (FCN). None of the works used recurrent neural network (RNN) and the variants.
Indication 4.1: It seems like that one of the most important factors in ROP problem is feature selection and data generation.
All three works use very different methods to collect/generate data, and all the authors provide very strong evidences and/or arguments to justify their approaches. ROPNN ( Li et al. 2018 ) was trained by the malicious and benign instruction sequences. However, there is no clear boundary between benign instruction sequences and malicious gadget chains. This weakness may impair the performance when applying ROPNN to real world ROP attacks. As oppose to ROPNN, DeepCheck ( Zhang et al. 2019 ) utilizes CFG to generate training basic-block sequences. However, since the malicious basic-block sequences are generated by randomly connecting nodes without edges, it is not guaranteed that all the malicious basic-blocks are executable. HeNet ( Chen et al. 2018 ) generates their training data from malware. Technically, HeNet could be used to detect any binary exploits, but their experiment focuses on ROP attack and achieves 100% accuracy. This shows that the source of data in ROP problem does not need to be related to ROP attacks to produce very impressive results.
Indication 4.2: Representation learning seems not critical when solving ROP problems using Deep Learning.
Minimal process on data in binary form seems to be enough to transform the data into a representation that is suitable for neural networks. Certainly, it is also possible to represent the binary instructions at a higher level, such as opcodes, or use embedding learning. However, as stated in ( Li et al. 2018 ), it appears that the performance will not change much by doing so. The only benefit of representing input data to a higher level is to reduce irrelevant information, but it seems like neural network by itself is good enough at extracting features.
Indication 4.3: Different Neural network architecture does not have much influence on the effectiveness of defending ROP attacks.
Both HeNet ( Chen et al. 2018 ) and DeepCheck ( Zhang et al. 2019 ) utilizes standard DNN and achieved comparable results on ROP problems. One can infer that the input data can be easily processed by neural networks, and the features can be easily detected after proper pre-process.
It is not surprising that researchers are not very interested in representation learning for ROP problems as stated in Observation 4.1. Since ROP attack is focus on the gadget chains, it is straightforward for the researcher to choose the gadgets as their training data directly. It is easy to map the data into numerical representation with minimal processing. An example is that one can map binary executable to hexadecimal ASCII representation, which could be a good representation for neural network.
Instead, researchers focus more in data acquisition and generation. In ROP problems, the amount of data is very limited. Unlike malware and logs, ROP payloads normally only contain addresses rather than codes, which do not contain any information without providing the instructions in corresponding addresses. It is thus meaningless to collect all the payloads. At the best of our knowledge, all the previous works use pick instruction sequences rather than payloads as their training data, even though they are hard to collect.
Even though, Deep Learning based method does not face the challenge to design a very complex fine-grained CFG anymore, it suffers from a limited number of data sources. Generally, Deep Learning based method requires lots of training data. However, real-world malicious data for the ROP attack is very hard to find, because comparing with benign data, malicious data need to be carefully crafted and there is no existing database to collect all the ROP attacks. Without enough representative training set, the accuracy of the trained model cannot be guaranteed.
A closer look at applications of deep learning in achieving CFI
The basic ideas of control-flow integrity (CFI) techniques, proposed by Abadi in 2005 ( Abadi et al. 2009 ), could be dated back to 2002, when Vladimir and his fellow researchers proposed an idea called program shepherding ( Kiriansky et al. 2002 ), a method of monitoring the execution flow of a program when it is running by enforcing some security policies. The goal of CFI is to detect and prevent control-flow hijacking attacks, by restricting every critical control flow transfers to a set that can only appear in correct program executions, according to a pre-built CFG. Traditional CFI techniques typically leverage some knowledge, gained from either dynamic or static analysis of the target program, combined with some code instrumentation methods, to ensure the program runs on a correct track.
However, the problems of traditional CFI are: (1) Existing CFI implementations are not compatible with some of important code features ( Xu et al. 2019 ); (2) CFGs generated by static, dynamic or combined analysis cannot always be precisely completed due to some open problems ( Horwitz 1997 ); (3) There always exist certain level of compromises between accuracy and performance overhead and other important properties ( Tan and Jaeger 2017 ; Wang and Liu 2019 ). Recent research has proposed to apply Deep Learning on detecting control flow violation. Their result shows that, compared with traditional CFI implementation, the security coverage and scalability were enhanced in such a fashion ( Yagemann et al. 2019 ). Therefore, we argue that Deep Learning could be another approach which requires more attention from CFI researchers who aim at achieving control-flow integrity more efficiently and accurately.
In this section, we will review the very recent three representative papers that use Deep Learning for achieving CFI. Among the three, two representative papers ( Yagemann et al. 2019 ; Phan et al. 2017 ) are already summarized phase-by-phase in Table 2 . We refer to interested readers the Table 2 for a concise overview of those two papers.
Our review will be centered around three questions described in Section 3 . In the remaining of this section, we will first provide a set of observations, and then we provide the indications. Finally, we provide some general remarks.
From a close look at the very recent applications using Deep Learning for achieving control-flow integrity, we observed the followings:
Observation 5.1: None of the related works realize preventive Footnote 1 prevention of control flow violation.
After doing a thorough literature search, we observed that security researchers are quite behind the trend of applying Deep Learning techniques to solve security problems. Only one paper has been founded by us, using Deep Learning techniques to directly enhance the performance of CFI ( Yagemann et al. 2019 ). This paper leveraged Deep Learning to detect document malware through checking program’s execution traces that generated by hardware. Specifically, the CFI violations were checked in an offline mode. So far, no works have realized Just-In-Time checking for program’s control flow.
In order to provide more insightful results, in this section, we try not to narrow down our focus on CFI detecting attacks at run-time, but to extend our scope to papers that take good use of control flow related data, combined with Deep Learning techniques ( Phan et al. 2017 ; Nguyen et al. 2018 ). In one work, researchers used self-constructed instruction-level CFG to detect program defection ( Phan et al. 2017 ). In another work, researchers used lazy-binding CFG to detect sophisticated malware ( Nguyen et al. 2018 ).
Observation 5.2: Diverse raw data were used for evaluating CFI solutions.
In all surveyed papers, there are two kinds of control flow related data being used: program instruction sequences and CFGs. Barnum et al. ( Yagemann et al. 2019 ) employed statically and dynamically generated instruction sequences acquired by program disassembling and Intel ® Processor Trace. CNNoverCFG ( Phan et al. 2017 ) used self-designed algorithm to construct instruction level control-flow graph. Minh Hai Nguyen et al. ( Nguyen et al. 2018 ) used proposed lazy-binding CFG to reflect the behavior of malware DEC.
Observation 5.3: All the papers in our survey adopted Phase II.
All the related papers in our survey employed Phase II to process their raw data before sending them into Phase III. In Barnum ( Yagemann et al. 2019 ), the instruction sequences from program run-time tracing were sliced into basic-blocks. Then, they assigned each basic-blocks with an unique basic-block ID (BBID). Finally, due to the nature of control-flow hijacking attack, they selected the sequences ending with indirect branch instruction (e.g., indirect call/jump, return and so on) as the training data. In CNNoverCFG ( Phan et al. 2017 ), each of instructions in CFG were labeled with its attributes in multiple perspectives, such as opcode, operands, and the function it belongs to. The training data is generated are sequences generated by traversing the attributed control-flow graph. Nguyen and others ( Nguyen et al. 2018 ) converted the lazy-binding CFG to corresponding adjacent matrix and treated the matrix as a image as their training data.
Observation 5.4: All the papers in our survey did not adopt Phase III. We observed all the papers we surveyed did not adopted Phase III. Instead, they adopted the form of numerical representation directly as their training data. Specifically, Barnum ( Yagemann et al. 2019 ) grouped the instructions into basic-blocks, then represented basic-blocks with uniquely assigning IDs. In CNNoverCFG ( Phan et al. 2017 ), each of instructions in the CFG was represented by a vector that associated with its attributes. Nguyen and others directly used the hashed value of bit string representation.
Observation 5.5: Various Phase IV models were used. Barnum ( Yagemann et al. 2019 ) utilized BBID sequence to monitor the execution flow of the target program, which is sequence-type data. Therefore, they chose LSTM architecture to better learn the relationship between instructions. While in the other two papers ( Phan et al. 2017 ; Nguyen et al. 2018 ), they trained CNN and directed graph-based CNN to extract information from control-flow graph and image, respectively.
Indication 5.1: All the existing works did not achieve Just-In-Time CFI violation detection.
It is still a challenge to tightly embed Deep Learning model in program execution. All existing work adopted lazy-checking – checking the program’s execution trace following its execution.
Indication 5.2: There is no unified opinion on how to generate malicious sample.
Data are hard to collect in control-flow hijacking attacks. The researchers must carefully craft malicious sample. It is not clear whether the “handcrafted” sample can reflect the nature the control-flow hijacking attack.
*Observation 5.3: The choice of methods in Phase II are based on researchers’ security domain knowledge.
The strength of using deep learning to solve CFI problems is that it can avoid the complicated processes of developing algorithms to build acceptable CFGs for the protected programs. Compared with the traditional approaches, the DL based method could prevent CFI designer from studying the language features of the targeted program and could also avoid the open problem (pointer analysis) in control flow analysis. Therefore, DL based CFI provides us a more generalized, scalable, and secure solution. However, since using DL in CFI problem is still at an early age, which kinds of control-flow related data are more effective is still unclear yet in this research area. Additionally, applying DL in real-time control-flow violation detection remains an untouched area and needs further research.
A closer look at applications of deep learning in defending network attacks
Network security is becoming more and more important as we depend more and more on networks for our daily lives, works and researches. Some common network attack types include probe, denial of service (DoS), Remote-to-local (R2L), etc. Traditionally, people try to detect those attacks using signatures, rules, and unsupervised anomaly detection algorithms. However, signature based methods can be easily fooled by slightly changing the attack payload; rule based methods need experts to regularly update rules; and unsupervised anomaly detection algorithms tend to raise lots of false positives. Recently, people are trying to apply Deep Learning methods for network attack detection.
In this section, we will review the very recent seven representative works that use Deep Learning for defending network attacks. Millar et al. (2018 ); Varenne et al. (2019 ); Ustebay et al. (2019 ) build neural networks for multi-class classification, whose class labels include one benign label and multiple malicious labels for different attack types. Zhang et al. (2019 ) ignores normal network activities and proposes parallel cross convolutional neural network (PCCN) to classify the type of malicious network activities. Yuan et al. (2017 ) applies Deep Learning to detecting a specific attack type, distributed denial of service (DDoS) attack. Yin et al. (2017 ); Faker and Dogdu (2019 ) explores both binary classification and multi-class classification for benign and malicious activities. Among these seven works, we select two representative works ( Millar et al. 2018 ; Zhang et al. 2019 ) and summarize the main aspects of their approaches regarding whether the four phases exist in their works, and what exactly do they do in the Phase if it exists. We direct interested readers to Table 2 for a concise overview of these two works.
From a close look at the very recent applications using Deep Learning for solving network attack challenges, we observed the followings:
Observation 6.1: All the seven works in our survey used public datasets, such as UNSW-NB15 ( Moustafa and Slay 2015 ) and CICIDS2017 ( IDS 2017 Datasets 2019 ).
The public datasets were all generated in test-bed environments, with unbalanced simulated benign and attack activities. For attack activities, the dataset providers launched multiple types of attacks, and the numbers of malicious data for those attack activities were also unbalanced.
Observation 6.2: The public datasets were given into one of two data formats, i.e., PCAP and CSV.
One was raw PCAP or parsed CSV format, containing network packet level features, and the other was also CSV format, containing network flow level features, which showed the statistic information of many network packets. Out of all the seven works, ( Yuan et al. 2017 ; Varenne et al. 2019 ) used packet information as raw inputs, ( Yin et al. 2017 ; Zhang et al. 2019 ; Ustebay et al. 2019 ; Faker and Dogdu 2019 ) used flow information as raw inputs, and ( Millar et al. 2018 ) explored both cases.
Observation 6.3: In order to parse the raw inputs, preprocessing methods, including one-hot vectors for categorical texts, normalization on numeric data, and removal of unused features/data samples, were commonly used.
Commonly removed features include IP addresses and timestamps. Faker and Dogdu (2019 ) also removed port numbers from used features. By doing this, they claimed that they could “avoid over-fitting and let the neural network learn characteristics of packets themselves”. One outlier was that, when using packet level features in one experiment, ( Millar et al. 2018 ) blindly chose the first 50 bytes of each network packet without any feature extracting processes and fed them into neural network.
Observation 6.4: Using image representation improved the performance of security solutions using Deep Learning.
After preprocessing the raw data, while ( Zhang et al. 2019 ) transformed the data into image representation, ( Yuan et al. 2017 ; Varenne et al. 2019 ; Faker and Dogdu 2019 ; Ustebay et al. 2019 ; Yin et al. 2017 ) directly used the original vectors as an input data. Also, ( Millar et al. 2018 ) explored both cases and reported better performance using image representation.
Observation 6.5: None of all the seven surveyed works considered representation learning.
All the seven surveyed works belonged to class 1 shown in Fig. 2 . They either directly used the processed vectors to feed into the neural networks, or changed the representation without explanation. One research work ( Millar et al. 2018 ) provided a comparison on two different representations (vectors and images) for the same type of raw input. However, the other works applied different preprocessing methods in Phase II. That is, since the different preprocessing methods generated different feature spaces, it was difficult to compare the experimental results.
Observation 6.6: Binary classification model showed better results from most experiments.
Among all the seven surveyed works, ( Yuan et al. 2017 ) focused on one specific attack type and only did binary classification to classify whether the network traffic was benign or malicious. Also, ( Millar et al. 2018 ; Ustebay et al. 2019 ; Zhang et al. 2019 ; Varenne et al. 2019 ) included more attack types and did multi-class classification to classify the type of malicious activities, and ( Yin et al. 2017 ; Faker and Dogdu 2019 ) explored both cases. As for multi-class classification, the accuracy for selective classes was good, while accuracy for other classes, usually classes with much fewer data samples, suffered by up to 20% degradation.
Observation 6.7: Data representation influenced on choosing a neural network model.
Indication 6.1: All works in our survey adopt a kind of preprocessing methods in Phase II, because raw data provided in the public datasets are either not ready for neural networks, or that the quality of data is too low to be directly used as data samples.
Preprocessing methods can help increase the neural network performance by improving the data samples’ qualities. Furthermore, by reducing the feature space, pre-processing can also improve the efficiency of neural network training and testing. Thus, Phase II should not be skipped. If Phase II is skipped, the performance of neural network is expected to go down considerably.
Indication 6.2: Although Phase III is not employed in any of the seven surveyed works, none of them explains a reason for it. Also, they all do not take representation learning into consideration.
Indication 6.3: Because no work uses representation learning, the effectiveness are not well-studied.
Out of other factors, it seems that the choice of pre-processing methods has the largest impact, because it directly affects the data samples fed to the neural network.
Indication 6.4: There is no guarantee that CNN also works well on images converted from network features.
Some works that use image data representation use CNN in Phase IV. Although CNN has been proven to work well on image classification problem in the recent years, there is no guarantee that CNN also works well on images converted from network features.
From the observations and indications above, we hereby present two recommendations: (1) Researchers can try to generate their own datasets for the specific network attack they want to detect. As stated, the public datasets have highly unbalanced number of data for different classes. Doubtlessly, such unbalance is the nature of real world network environment, in which normal activities are the majority, but it is not good for Deep Learning. ( Varenne et al. 2019 ) tries to solve this problem by oversampling the malicious data, but it is better to start with a balanced data set. (2) Representation learning should be taken into consideration. Some possible ways to apply representation learning include: (a) apply word2vec method to packet binaries, and categorical numbers and texts; (b) use K-means as one-hot vector representation instead of randomly encoding texts. We suggest that any change of data representation may be better justified by explanations or comparison experiments.
One critical challenge in this field is the lack of high-quality data set suitable for applying deep learning. Also, there is no agreement on how to apply domain knowledge into training deep learning models for network security problems. Researchers have been using different pre-processing methods, data representations and model types, but few of them have enough explanation on why such methods/representations/models are chosen, especially for data representation.
A closer look at applications of deep learning in malware classification
The goal of malware classification is to identify malicious behaviors in software with static and dynamic features like control-flow graph and system API calls. Malware and benign programs can be collected from open datasets and online websites. Both the industry and the academic communities have provided approaches to detect malware with static and dynamic analyses. Traditional methods such as behavior-based signatures, dynamic taint tracking, and static data flow analysis require experts to manually investigate unknown files. However, those hand-crafted signatures are not sufficiently effective because attackers can rewrite and reorder the malware. Fortunately, neural networks can automatically detect large-scale malware variants with superior classification accuracy.
In this section, we will review the very recent twelve representative works that use Deep Learning for malware classification ( De La Rosa et al. 2018 ; Saxe and Berlin 2015 ; Kolosnjaji et al. 2017 ; McLaughlin et al. 2017 ; Tobiyama et al. 2016 ; Dahl et al. 2013 ; Nix and Zhang 2017 ; Kalash et al. 2018 ; Cui et al. 2018 ; David and Netanyahu 2015 ; Rosenberg et al. 2018 ; Xu et al. 2018 ). De La Rosa et al. (2018 ) selects three different kinds of static features to classify malware. Saxe and Berlin (2015 ); Kolosnjaji et al. (2017 ); McLaughlin et al. (2017 ) also use static features from the PE files to classify programs. ( Tobiyama et al. 2016 ) extracts behavioral feature images using RNN to represent the behaviors of original programs. ( Dahl et al. 2013 ) transforms malicious behaviors using representative learning without neural network. Nix and Zhang (2017 ) explores RNN model with the API calls sequences as programs’ features. Cui et al. (2018 ); Kalash et al. (2018 ) skip Phase II by directly transforming the binary file to image to classify the file. ( David and Netanyahu 2015 ; Rosenberg et al. 2018 ) applies dynamic features to analyze malicious features. Xu et al. (2018 ) combines static features and dynamic features to represent programs’ features. Among these works, we select two representative works ( De La Rosa et al. 2018 ; Rosenberg et al. 2018 ) and identify four phases in their works shown as Table 2 .
From a close look at the very recent applications using Deep Learning for solving malware classification challenges, we observed the followings:
Observation 7.1: Features selected in malware classification were grouped into three categories: static features, dynamic features, and hybrid features.
Typical static features include metadata, PE import Features, Byte/Entorpy, String, and Assembly Opcode Features derived from the PE files ( Kolosnjaji et al. 2017 ; McLaughlin et al. 2017 ; Saxe and Berlin 2015 ). De La Rosa et al. (2018 ) took three kinds of static features: byte-level, basic-level (strings in the file, the metadata table, and the import table of the PE header), and assembly features-level. Some works directly considered binary code as static features ( Cui et al. 2018 ; Kalash et al. 2018 ).
Different from static features, dynamic features were extracted by executing the files to retrieve their behaviors during execution. The behaviors of programs, including the API function calls, their parameters, files created or deleted, websites and ports accessed, etc, were recorded by a sandbox as dynamic features ( David and Netanyahu 2015 ). The process behaviors including operation name and their result codes were extracted ( Tobiyama et al. 2016 ). The process memory, tri-grams of system API calls and one corresponding input parameter were chosen as dynamic features ( Dahl et al. 2013 ). An API calls sequence for an APK file was another representation of dynamic features ( Nix and Zhang 2017 ; Rosenberg et al. 2018 ).
Static features and dynamic features were combined as hybrid features ( Xu et al. 2018 ). For static features, Xu and others in ( Xu et al. 2018 ) used permissions, networks, calls, and providers, etc. For dynamic features, they used system call sequences.
Observation 7.2: In most works, Phase II was inevitable because extracted features needed to be vertorized for Deep Learning models.
One-hot encoding approach was frequently used to vectorize features ( Kolosnjaji et al. 2017 ; McLaughlin et al. 2017 ; Rosenberg et al. 2018 ; Tobiyama et al. 2016 ; Nix and Zhang 2017 ). Bag-of-words (BoW) and n -gram were also considered to represent features ( Nix and Zhang 2017 ). Some works brought the concepts of word frequency in NLP to convert the sandbox file to fixed-size inputs ( David and Netanyahu 2015 ). Hashing features into a fixed vector was used as an effective method to represent features ( Saxe and Berlin 2015 ). Bytes histogram using the bytes analysis and bytes-entropy histogram with a sliding window method were considered ( De La Rosa et al. 2018 ). In ( De La Rosa et al. 2018 ), De La Rosa and others embeded strings by hashing the ASCII strings to a fixed-size feature vector. For assembly features, they extracted four different levels of granularity: operation level (instruction-flow-graph), block level (control-flow-graph), function level (call-graph), and global level (graphs summarized). bigram, trigram and four-gram vectors and n -gram graph were used for the hybrid features ( Xu et al. 2018 ).
Observation 7.3: Most Phase III methods were classified into class 1.
Following the classification tree shown in Fig. 2 , most works were classified into class 1 shown in Fig. 2 except two works ( Dahl et al. 2013 ; Tobiyama et al. 2016 ), which belonged to class 3 shown in Fig. 2 . To reduce the input dimension, Dahl et al. (2013 ) performed feature selection using mutual information and random projection. Tobiyama et al. generated behavioral feature images using RNN ( Tobiyama et al. 2016 ).
Observation 7.4: After extracting features, two kinds of neural network architectures, i.e., one single neural network and multiple neural networks with a combined loss function, were used.
Hierarchical structures, like convolutional layers, fully connected layers and classification layers, were used to classify programs ( McLaughlin et al. 2017 ; Dahl et al. 2013 ; Nix and Zhang 2017 ; Saxe and Berlin 2015 ; Tobiyama et al. 2016 ; Cui et al. 2018 ; Kalash et al. 2018 ). A deep stack of denoising autoencoders was also introduced to learn programs’ behaviors ( David and Netanyahu 2015 ). De La Rosa and others ( De La Rosa et al. 2018 ) trained three different models with different features to compare which static features are relevant for the classification model. Some works investigated LSTM models for sequential features ( Nix and Zhang 2017 ; Rosenberg et al. 2018 ).
Two networks with different features as inputs were used for malware classification by combining their outputs with a dropout layer and an output layer ( Kolosnjaji et al. 2017 ). In ( Kolosnjaji et al. 2017 ), one network transformed PE Metadata and import features using feedforward neurons, another one leveraged convolutional network layers with opcode sequences. Lifan Xu et al. ( Xu et al. 2018 ) constructed a few networks and combined them using a two-level multiple kernel learning algorithm.
Indication 7.1: Except two works transform binary into images ( Cui et al. 2018 ; Kalash et al. 2018 ), most works surveyed need to adapt methods to vectorize extracted features.
The vectorization methods should not only keep syntactic and semantic information in features, but also consider the definition of the Deep Learning model.
Indication 7.2: Only limited works have shown how to transform features using representation learning.
Because some works assume the dynamic and static sequences, like API calls and instruction, and have similar syntactic and semantic structure as natural language, some representation learning techniques like word2vec may be useful in malware detection. In addition, for the control-flow graph, call graph and other graph representations, graph embedding is a potential method to transform those features.
Though several pieces of research have been done in malware detection using Deep Learning, it’s hard to compare their methods and performances because of two uncertainties in their approaches. First, the Deep Learning model is a black-box, researchers cannot detail which kind of features the model learned and explain why their model works. Second, feature selection and representation affect the model’s performance. Because they do not use the same datasets, researchers cannot prove their approaches – including selected features and Deep Learning model – are better than others. The reason why few researchers use open datasets is that existing open malware datasets are out of data and limited. Also, researchers need to crawl benign programs from app stores, so their raw programs will be diverse.
A closer look at applications of Deep Learning in system-event-based anomaly detection
System logs recorded significant events at various critical points, which can be used to debug the system’s performance issues and failures. Moreover, log data are available in almost all computer systems and are a valuable resource for understanding system status. There are a few challenges in anomaly detection based on system logs. Firstly, the raw log data are unstructured, while their formats and semantics can vary significantly. Secondly, logs are produced by concurrently running tasks. Such concurrency makes it hard to apply workflow-based anomaly detection methods. Thirdly, logs contain rich information and complexity types, including text, real value, IP address, timestamp, and so on. The contained information of each log is also varied. Finally, there are massive logs in every system. Moreover, each anomaly event usually incorporates a large number of logs generated in a long period.
Recently, a large number of scholars employed deep learning techniques ( Du et al. 2017 ; Meng et al. 2019 ; Das et al. 2018 ; Brown et al. 2018 ; Zhang et al. 2019 ; Bertero et al. 2017 ) to detect anomaly events in the system logs and diagnosis system failures. The raw log data are unstructured, while their formats and semantics can vary significantly. To detect the anomaly event, the raw log usually should be parsed to structure data, the parsed data can be transformed into a representation that supports an effective deep learning model. Finally, the anomaly event can be detected by deep learning based classifier or predictor.
In this section, we will review the very recent six representative papers that use deep learning for system-event-based anomaly detection ( Du et al. 2017 ; Meng et al. 2019 ; Das et al. 2018 ; Brown et al. 2018 ; Zhang et al. 2019 ; Bertero et al. 2017 ). DeepLog ( Du et al. 2017 ) utilizes LSTM to model the system log as a natural language sequence, which automatically learns log patterns from the normal event, and detects anomalies when log patterns deviate from the trained model. LogAnom ( Meng et al. 2019 ) employs Word2vec to extract the semantic and syntax information from log templates. Moreover, it uses sequential and quantitative features simultaneously. Das et al. (2018 ) uses LSTM to predict node failures that occur in super computing systems from HPC logs. Brown et al. (2018 ) presented RNN language models augmented with attention for anomaly detection in system logs. LogRobust ( Zhang et al. 2019 ) uses FastText to represent semantic information of log events, which can identify and handle unstable log events and sequences. Bertero et al. (2017 ) map log word to a high dimensional metric space using Google’s word2vec algorithm and take it as features to classify. Among these six papers, we select two representative works ( Du et al. 2017 ; Meng et al. 2019 ) and summarize the four phases of their approaches. We direct interested readers to Table 2 for a concise overview of these two works.
From a close look at the very recent applications using deep learning for solving security-event-based anomaly detection challenges, we observed the followings:
Observation 8.1: Most works of our surveyed papers evaluated their performance using public datasets.
By the time we surveyed this paper, only two works in ( Das et al. 2018 ; Bertero et al. 2017 ) used their private datasets.
Observation 8.2: Most works in this survey adopted Phase II when parsing the raw log data.
After reviewing the six works proposed recently, we found that five works ( Du et al. 2017 ; Meng et al. 2019 ; Das et al. 2018 ; Brown et al. 2018 ; Zhang et al. 2019 ) employed parsing technique, while only one work ( Bertero et al. 2017 ) did not.
DeepLog ( Du et al. 2017 ) parsed the raw log to different log type using Spell ( Du and Li 2016 ) which is based a longest common subsequence. Desh ( Das et al. 2018 ) parsed the raw log to constant message and variable component. Loganom ( Meng et al. 2019 ) parsed the raw log to different log templates using FT-Tree ( Zhang et al. 2017 ) according to the frequent combinations of log words. Andy Brown et al. ( Brown et al. 2018 ) parsed the raw log into word and character tokenization. LogRobust ( Zhang et al. 2019 ) extracted its log event by abstracting away the parameters in the message. Bertero et al. (2017 ) considered logs as regular text without parsing.
Observation 8.3: Most works have considered and adopted Phase III.
Among these six works, only DeepLog represented the parsed data using the one-hot vector without learning. Moreover, Loganom ( Meng et al. 2019 ) compared their results with DeepLog. That is, DeepLog belongs to class 1 and Loganom belongs to class 4 in Fig. 2 , while the other four works follow in class 3.
The four works ( Meng et al. 2019 ; Das et al. 2018 ; Zhang et al. 2019 ; Bertero et al. 2017 ) used word embedding techniques to represent the log data. Andy Brown et al. ( Brown et al. 2018 ) employed attention vectors to represent the log messages.
DeepLog ( Du et al. 2017 ) employed the one-hot vector to represent the log type without learning. We have engaged an experiment replacing the one-hot vector with trained word embeddings.
Observation 8.4: Evaluation results were not compared using the same dataset.
DeepLog ( Du et al. 2017 ) employed the one-hot vector to represent the log type without learning, which employed Phase II without Phase III. However, Christophe Bertero et al. ( Bertero et al. 2017 ) considered logs as regular text without parsing, and used Phase III without Phase II. The precision of the two methods is very high, which is greater than 95%. Unfortunately, the evaluations of the two methods used different datasets.
Observation 8.5: Most works empolyed LSTM in Phase IV.
Five works including ( Du et al. 2017 ; Meng et al. 2019 ; Das et al. 2018 ; Brown et al. 2018 ; Zhang et al. 2019 ) employed LSTM in the Phase IV, while Bertero et al. (2017 ) tried different classifiers including naive Bayes, neural networks and random forest.
Indication 8.1: Phase II has a positive effect on accuracy if being well-designed.
Since Bertero et al. (2017 ) considers logs as regular text without parsing, we can say that Phase II is not required. However, we can find that most of the scholars employed parsing techniques to extract structure information and remove the useless noise.
Indication 8.2: Most of the recent works use trained representation to represent parsed data.
As shown in Table 3 , we can find Phase III is very useful, which can improve detection accuracy.
Indication 8.3: Phase II and Phase III cannot be skipped simultaneously.
Both Phase II and Phase III are not required. However, all methods have employed Phase II or Phase III.
Indication 8.4: Observation 8.3 indicates that the trained word embedding format can improve the anomaly detection accuracy as shown in Table 3 .
Indication 8.5: Observation 8.5 indicates that most of the works adopt LSTM to detect anomaly events.
We can find that most of the works adopt LSTM to detect anomaly event, since log data can be considered as sequence and there can be lags of unknown duration between important events in a time series. LSTM has feedback connections, which can not only process single data points, but also entire sequences of data.
As our consideration, neither Phase II nor Phase III is required in system event-based anomaly detection. However, Phase II can remove noise in raw data, and Phase III can learn a proper representation of the data. Both Phase II and Phase III have a positive effect on anomaly detection accuracy. Since the event log is text data that we can’t feed the raw log data into deep learning model directly, Phase II and Phase III can’t be skipped simultaneously.
Deep learning can capture the potentially nonlinear and high dimensional dependencies among log entries from the training data that correspond to abnormal events. In that way, it can release the challenges mentioned above. However, it still suffers from several challenges. For example, how to represent the unstructured data accurately and automatically without human knowledge.
A closer look at applications of deep learning in solving memory forensics challenges
In the field of computer security, memory forensics is security-oriented forensic analysis of a computer’s memory dump. Memory forensics can be conducted against OS kernels, user-level applications, as well as mobile devices. Memory forensics outperforms traditional disk-based forensics because although secrecy attacks can erase their footprints on disk, they would have to appear in memory ( Song et al. 2018 ). The memory dump can be considered as a sequence of bytes, thus memory forensics usually needs to extract security semantic information from raw memory dump to find attack traces.
The traditional memory forensic tools fall into two categories: signature scanning and data structure traversal. These traditional methods usually have some limitations. Firstly, it needs expert knowledge on the related data structures to create signatures or traversing rules. Secondly, attackers may directly manipulate data and pointer values in kernel objects to evade detection, and then it becomes even more challenging to create signatures and traversing rules that cannot be easily violated by malicious manipulations, system updates, and random noise. Finally, the high-efficiency requirement often sacrifices high robustness. For example, an efficient signature scan tool usually skips large memory regions that are unlikely to have the relevant objects and relies on simple but easily tamperable string constants. An important clue may hide in this ignored region.
In this section, we will review the very recent four representative works that use Deep Learning for memory forensics ( Song et al. 2018 ; Petrik et al. 2018 ; Michalas and Murray 2017 ; Dai et al. 2018 ). DeepMem ( Song et al. 2018 ) recognized the kernel objects from raw memory dumps by generating abstract representations of kernel objects with a graph-based Deep Learning approach. MDMF ( Petrik et al. 2018 ) detected OS and architecture-independent malware from memory snapshots with several pre-processing techniques, domain unaware feature selection, and a suite of machine learning algorithms. MemTri ( Michalas and Murray 2017 ) predicts the likelihood of criminal activity in a memory image using a Bayesian network, based on evidence data artefacts generated by several applications. Dai et al. (2018 ) monitor the malware process memory and classify malware according to memory dumps, by transforming the memory dump into grayscale images and adopting a multi-layer perception as the classifier.
Among these four works ( Song et al. 2018 ; Petrik et al. 2018 ; Michalas and Murray 2017 ; Dai et al. 2018 ), two representative works (i.e., ( Song et al. 2018 ; Petrik et al. 2018 )) are already summarized phase-by-phase in Table 1. We direct interested readers to Table 2 for a concise overview of these two works.
Our review will be centered around the three questions raised in Section 3 . In the remaining of this section, we will first provide a set of observations, and then we provide the indications. Finally, we provide some general remarks.
From a close look at the very recent applications using Deep Learning for solving memory forensics challenges, we observed the followings:
Observation 9.1: Most methods used their own datasets for performance evaluation, while none of them used a public dataset.
DeepMem was evaluated on self-generated dataset by the authors, who collected a large number of diverse memory dumps, and labeled the kernel objects in them using existing memory forensics tools like Volatility. MDMF employed the MalRec dataset by Georgia Tech to generate malicious snapshots, while it created a dataset of benign memory snapshots running normal software. MemTri ran several Windows 7 virtual machine instances with self-designed suspect activity scenarios to gather memory images. Dai et al. built the Procdump program in Cuckoo sandbox to extract malware memory dumps. We found that each of the four works in our survey generated their own datasets, while none was evaluated on a public dataset.
Observation 9.2: Among the four works ( Song et al. 2018 ; Michalas and Murray 2017 ; Petrik et al. 2018 ; Dai et al. 2018 ), two works ( Song et al. 2018 ; Michalas and Murray 2017 ) employed Phase II while the other two works ( Petrik et al. 2018 ; Dai et al. 2018 ) did not employ.
DeepMem ( Song et al. 2018 ) devised a graph representation for a sequence of bytes, taking into account both adjacency and points-to relations, to better model the contextual information in memory dumps. MemTri ( Michalas and Murray 2017 ) firstly identified the running processes within the memory image that match the target applications, then employed regular expressions to locate evidence artefacts in a memory image. MDMF ( Petrik et al. 2018 ) and Dai et al. (2018 ) transformed the memory dump into image directly.
Observation 9.3: Among four works ( Song et al. 2018 ; Michalas and Murray 2017 ; Petrik et al. 2018 ; Dai et al. 2018 ), only DeepMem ( Song et al. 2018 ) employed Phase III for which it used an embedding method to represent a memory graph.
MDMF ( Petrik et al. 2018 ) directly fed the generated memory images into the training of a CNN model. Dai et al. (2018 ) used HOG feature descriptor for detecting objects, while MemTri ( Michalas and Murray 2017 ) extracted evidence artefacts as the input of Bayesian Network. In summary, DeepMem belonged to class 3 shown in Fig. 2 , while the other three works belonged to class 1 shown in Fig. 2 .
Observation 9.4: All the four works ( Song et al. 2018 ; Petrik et al. 2018 ; Michalas and Murray 2017 ; Dai et al. 2018 ) have employed different classifiers even when the types of input data are the same.
DeepMem chose fully connected network (FCN) model that has multi-layered hidden neurons with ReLU activation functions, following by a softmax layer as the last layer. MDMF ( Petrik et al. 2018 ) evaluated their performance both on traditional machine learning algorithms and Deep Learning approach including CNN and LSTM. Their results showed the accuracy of different classifiers did not have a significant difference. MemTri employed a Bayesian network model that is designed with three layers, i.e., a hypothesis layer, a sub-hypothesis layer, and an evidence layer. Dai et al. used a multi-layer perception model including an input layer, a hidden layer and an output layer as the classifier.
Indication 9.1: There lacks public datasets for evaluating the performance of different Deep Learning methods in memory forensics.
From Observation 9.1, we find that none of the four works surveyed was evaluated on public datasets.
Indication 9.2: From Observation 9.2, we find that it is disputable whether one should employ Phase II when solving memory forensics problems.
Since both ( Petrik et al. 2018 ) and ( Dai et al. 2018 ) directly transformed a memory dump into an image, Phase II is not required in these two works. However, since there is a large amount of useless information in a memory dump, we argue that appropriate prepossessing could improve the accuracy of the trained models.
Indication 9.3: From Observation 9.3, we find that Phase III is paid not much attention in memory forensics.
Most works did not employ Phase III. Among the four works, only DeepMem ( Song et al. 2018 ) employed Phase III during which it used embeddings to represent a memory graph. The other three works ( Petrik et al. 2018 ; Michalas and Murray 2017 ; Dai et al. 2018 ) did not learn any representations before training a Deep Learning model.
Indication 9.4: For Phase IV in memory forensics, different classifiers can be employed.
Which kind of classifier to use seems to be determined by the features used and their data structures. From Observation 9.4, we find that the four works have actually employed different kinds of classifiers even the types of input data are the same. It is very interesting that MDMF obtained similar results with different classifiers including traditional machine learning and Deep Learning models. However, the other three works did not discuss why they chose a particular kind of classifier.
Since a memory dump can be considered as a sequence of bytes, the data structure of a training data example is straightforward. If the memory dump is transformed into a simple form in Phase II, it can be directly fed into the training process of a Deep Learning model, and as a result Phase III can be ignored. However, if the memory dump is transformed into a complicated form in Phase II, Phase III could be quite useful in memory forensics.
Regarding the answer for Question 3 at “ Methodology for reviewing the existing works ” section, it is very interesting that during Phase IV different classifiers can be employed in memory forensics. Moreover, MDMF ( Petrik et al. 2018 ) has shown that they can obtain similar results with different kinds of classifiers. Nevertheless, they also admit that with a larger amount of training data, the performance could be improved by Deep Learning.
An end-to-end manner deep learning model can learn the precise representation of memory dump automatically to release the requirement for expert knowledge. However, it still needs expert knowledge to represent data and attacker behavior. Attackers may also directly manipulate data and pointer values in kernel objects to evade detection.
A closer look at applications of deep learning in security-oriented fuzzing
Fuzzing of software security is one of the state of art techniques that people use to detect software vulnerabilities. The goal of fuzzing is to find all the vulnerabilities exist in the program by testing as much program code as possible. Due to the nature of fuzzing, this technique works best on finding vulnerabilities in programs that take in input files, like PDF viewers ( Godefroid et al. 2017 ) or web browsers. A typical workflow of fuzzing can be concluded as: given several seed input files, the fuzzer will mutate or fuzz the seed inputs to get more input files, with the aim of expanding the overall code coverage of the target program as it executes the mutated files. Although there have already been various popular fuzzers ( Li et al. 2018 ), fuzzing still cannot bypass its problem of sometimes redundantly testing input files which cannot improve the code coverage rate ( Shi and Pei 2019 ; Rajpal et al. 2017 ). Some input files mutated by the fuzzer even cannot pass the well-formed file structure test ( Godefroid et al. 2017 ). Recent research has come up with ideas of applying Deep Learning in the process of fuzzing to solve these problems.
In this section, we will review the very recent four representative works that use Deep Learning for fuzzing for software security. Among the three, two representative works ( Godefroid et al. 2017 ; Shi and Pei 2019 ) are already summarized phase-by-phase in Table 2 . We direct interested readers to Table 2 for a concise overview of those two works.
Observation 10.1: Deep Learning has only been applied in mutation-based fuzzing.
Even though various of different fuzzing techniques, including symbolic execution based fuzzing ( Stephens et al. 2016 ), tainted analysis based fuzzing ( Bekrar et al. 2012 ) and hybrid fuzzing ( Yun et al. 2018 ) have been proposed so far, we observed that all the works we surveyed employed Deep Learning method to assist the primitive fuzzing – mutation-based fuzzing. Specifically, they adopted Deep Learning to assist fuzzing tool’s input mutation. We found that they commonly did it in two ways: 1) training Deep Learning models to tell how to efficiently mutate the input to trigger more execution path ( Shi and Pei 2019 ; Rajpal et al. 2017 ); 2) training Deep Learning models to tell how to keep the mutated files compliant with the program’s basic semantic requirement ( Godefroid et al. 2017 ). Besides, all three works trained different Deep Learning models for different programs, which means that knowledge learned from one programs cannot be applied to other programs.
Observation 10.2: Similarity among all the works in our survey existed when choosing the training samples in Phase I.
The works in this survey had a common practice, i.e., using the input files directly as training samples of the Deep Learning model. Learn&Fuzz ( Godefroid et al. 2017 ) used character-level PDF objects sequence as training samples. Neuzz ( Shi and Pei 2019 ) regarded input files directly as byte sequences and fed them into the neural network model. Rajpal et al. (2017 ) also used byte level representations of input files as training samples.
Observation 10.3: Difference between all the works in our survey existed when assigning the training labels in Phase I.
Despite the similarity of training samples researchers decide to use, there was a huge difference in the training labels that each work chose to use. Learn&Fuzz ( Godefroid et al. 2017 ) directly used the character sequences of PDF objects as labels, same as training samples, but shifted by one position, which is a common generative model technique already broadly used in speech and handwriting recognition. Unlike Learn&Fuzz, Neuzz ( Shi and Pei 2019 ) and Rajpal’s work ( Rajpal et al. 2017 ) used bitmap and heatmap respectively as training labels, with the bitmap demonstrating the code coverage status of a certain input, and the heatmap demonstrating the efficacy of flipping one or more bytes of the input file. Whereas, as a common terminology well-known among fuzzing researchers, bitmap was gathered directly from the results of AFL. Heatmap used by Rajpal et al. was generated by comparing the code coverage supported by the bitmap of one seed file and the code coverage supported by bitmaps of the mutated seed files. It was noted that if there is acceptable level of code coverage expansion when executing the mutated seed files, demonstrated by more “1”s, instead of “0”s in the corresponding bitmaps, the byte level differences among the original seed file and the mutated seed files will be highlighted. Since those bytes should be the focus of later on mutation, heatmap was used to denote the location of those bytes.
Different labels usage in each work was actually due to the different kinds of knowledge each work wants to learn. For a better understanding, let us note that we can simply regard a Deep Learning model as a simulation of a “function”. Learn&Fuzz ( Godefroid et al. 2017 ) wanted to learn valid mutation of a PDF file that was compliant with the syntax and semantic requirements of PDF objects. Their model could be seen as a simulation of f ( x , θ )= y , where x denotes sequence of characters in PDF objects and y represents a sequence that are obtained by shifting the input sequences by one position. They generated new PDF object character sequences given a starting prefix once the model was trained. In Neuzz ( Shi and Pei 2019 ), an NN(Neural Network) model was used to do program smoothing, which simultated a smooth surrogate function that approximated the discrete branching behaviors of the target program. f ( x , θ )= y , where x denoted program’s byte level input and y represented the corresponding edge coverage bitmap. In this way, the gradient of the surrogate function was easily computed, due to NN’s support of efficient computation of gradients and higher order derivatives. Gradients could then be used to guide the direction of mutation, in order to get greater code coverage. In Rajpal and others’ work ( Rajpal et al. 2017 ), they designed a model to predict good (and bad) locations to mutate in input files based on the past mutations and corresponding code coverage information. Here, the x variable also denoted program’s byte level input, but the y variable represented the corresponding heatmap.
Observation 10.4: Various lengths of input files were handled in Phase II.
Deep Learning models typically accepted fixed length input, whereas the input files for fuzzers often held different lengths. Two different approaches were used among the three works we surveyed: splitting and padding. Learn&Fuzz ( Godefroid et al. 2017 ) dealt with this mismatch by concatenating all the PDF objects character sequences together, and then splited the large character sequence into multiple training samples with a fixed size. Neuzz ( Shi and Pei 2019 ) solved this problem by setting a maximize input file threshold and then, padding the smaller-sized input files with null bytes. From additional experiments, they also found that a modest threshold gived them the best result, and enlarging the input file size did not grant them additional accuracy. Aside from preprocessing training samples, Neuzz also preprocessed training labels and reduced labels dimension by merging the edges that always appeared together into one edge, in order to prevent the multicollinearity problem, that could prevent the model from converging to a small loss value. Rajpal and others ( Rajpal et al. 2017 ) used the similar splitting mechanism as Learn&Fuzz to split their input files into either 64-bit or 128-bit chunks. Their chunk size was determined empirically and was considered as a trainable parameter for their Deep Learning model, and their approach did not require sequence concatenating at the beginning.
Observation 10.5: All the works in our survey skipped Phase III.
According to our definition of Phase III, all the works in our survey did not consider representation learning. Therefore, all the three works ( Godefroid et al. 2017 ; Shi and Pei 2019 ; Rajpal et al. 2017 ) fell into class 1 shown in Fig. 2 .While as in Rajpal and others’ work, they considered the numerical representation of byte sequences. They claimed that since one byte binary data did not always represent the magnitude but also state, representing one byte in values ranging from 0 to 255 could be suboptimal. They used lower level 8-bit representation.
Indication 10.1: No alteration to the input files seems to be a correct approach. As far as we concerned, it is due to the nature of fuzzing. That is, since every bit of the input files matters, any slight alteration to the input files could either lose important information or add redundant information for the neural network model to learn.
Indication 10.2: Evaluation criteria should be chosen carefully when judging mutation.
Input files are always used as training samples regarding using Deep Learning technique in fuzzing problems. Through this similar action, researchers have a common desire to let the neural network mode learn how the mutated input files should look like. But the criterion of judging a input file actually has two levels: on the one hand, a good input file should be correct in syntax and semantics; on the other hand, a good input file should be the product of a useful mutation, which triggers the program to behave differently from previous execution path. This idea of a fuzzer that can generate semantically correct input file could still be a bad fuzzer at triggering new execution path was first brought up in Learn&Fuzz ( Godefroid et al. 2017 ). We could see later on works trying to solve this problem by using either different training labels ( Rajpal et al. 2017 ) or use neural network to do program smoothing ( Shi and Pei 2019 ). We encouraged fuzzing researchers, when using Deep Learning techniques, to keep this problem in mind, in order to get better fuzzing results.
Indication 10.3: Works in our survey only focus on local knowledge. In brief, some of the existing works ( Shi and Pei 2019 ; Rajpal et al. 2017 ) leveraged the Deep Learning model to learn the relation between program’s input and its behavior and used the knowledge that learned from history to guide future mutation. For better demonstration, we defined the knowledge that only applied in one program as local knowledge . In other words, this indicates that the local knowledge cannot direct fuzzing on other programs.
Corresponding to the problems conventional fuzzing has, the advantages of applying DL in fuzzing are that DL’s learning ability can ensure mutated input files follow the designated grammar rules better. The ways in which input files are generated are more directed, and will, therefore, guarantee the fuzzer to increase its code coverage by each mutation. However, even if the advantages can be clearly demonstrated by the two papers we discuss above, some challenges still exist, including mutation judgment challenges that are faced both by traditional fuzzing techniques and fuzzing with DL, and the scalability of fuzzing approaches.
We would like to raise several interesting questions for the future researchers: 1) Can the knowledge learned from the fuzzing history of one program be applied to direct testing on other programs? 2) If the answer to question one is positive, we can suppose that global knowledge across different programs exists? Then, can we train a model to extract the global knowledge ? 3) Whether it is possible to combine global knowledge and local knowledge when fuzzing programs?
Using high-quality data in Deep Learning is important as much as using well-structured deep neural network architectures. That is, obtaining quality data must be an important step, which should not be skipped, even in resolving security problems using Deep Learning. So far, this study demonstrated how the recent security papers using Deep Learning have adopted data conversion (Phase II) and data representation (Phase III) on different security problems. Our observations and indications showed a clear understanding of how security experts generate quality data when using Deep Learning.
Since we did not review all the existing security papers using Deep Learning, the generality of observations and indications is somewhat limited. Note that our selected papers for review have been published recently at one of prestigious security and reliability conferences such as USENIX SECURITY, ACM CCS and so on ( Shin et al. 2015 )-( Das et al. 2018 ), ( Brown et al. 2018 ; Zhang et al. 2019 ), ( Song et al. 2018 ; Petrik et al. 2018 ), ( Wang et al. 2019 )-( Rajpal et al. 2017 ). Thus, our observations and indications help to understand how most security experts have used Deep Learning to solve the well-known eight security problems from program analysis to fuzzing.
Our observations show that we should transfer raw data to synthetic formats of data ready for resolving security problems using Deep Learning through data cleaning and data augmentation and so on. Specifically, we observe that Phases II and III methods have mainly been used for the following purposes:
To clean the raw data to make the neural network (NN) models easier to interpret
To reduce the dimensionality of data (e.g., principle component analysis (PCA), t-distributed stochastic neighbor embedding (t-SNE))
To scale input data (e.g., normalization)
To make NN models understand more complex relationships depending on security problems (e.g. memory graphs)
To simply change various raw data formats into a vector format for NN models (e.g. one-hot encoding and word2vec embedding)
In this following, we do further discuss the question, “What if Phase II is skipped?", rather than the question, “Is Phase III always necessary?". This is because most of the selected papers do not consider Phase III methods (76%), or adopt with no concrete reasoning (19%). Specifically, we demonstrate how Phase II has been adopted according to eight security problems, different types of data, various models of NN and various outputs of NN models, in depth. Our key findings are summarized as follows:
How to fit security domain knowledge into raw data has not been well-studied yet.
While raw text data are commonly parsed after embedding, raw binary data are converted using various Phase II methods.
Raw data are commonly converted into a vector format to fit well to a specific NN model using various Phase II methods.
Various Phase II methods are used according to the relationship between output of security problem and output of NN models.
What if phase II is skipped?
From the analysis results of our selected papers for review, we roughly classify Phase II methods into the following four categories.
Embedding: The data conversion methods that intend to convert high-dimensional discrete variables into low-dimensional continuous vectors ( Google Developers 2016 ).
Parsing combined with embedding: The data conversion methods that constitute an input data into syntactic components in order to test conformability after embedding.
One-hot encoding: A simple embedding where each data belonging to a specific category is mapped to a vector of 0s and a single 1. Here, the low-dimension transformed vector is not managed.
Domain-specific data structures: A set of data conversion methods which generate data structures capturing domain-specific knowledge for different security problems, e.g., memory graphs ( Song et al. 2018 ).
Findings on eight security problems
We observe that over 93% of the papers use one of the above-classified Phase II methods. 7% of the papers do not use any of the above-classified methods, and these papers are mostly solving a software fuzzing problem. Specifically, we observe that 35% of the papers use a Category 1 (i.e. embedding) method; 30% of the papers use a Category 2 (i.e. parsing combined with embedding) method; 15% of the papers use a Category 3 (i.e. one-hot encoding) method; and 13% of the papers use a Category 4 (i.e. domain-specific data structures) method. Regarding why one-hot encoding is not widely used, we found that most security data include categorical input values, which are not directly analyzed by Deep Learning models.
From Fig. 3 , we also observe that according to security problems, different Phase II methods are used. First, PA, ROP and CFI should convert raw data into a vector format using embedding because they commonly collect instruction sequence from binary data. Second, NA and SEAD use parsing combined with embedding because raw data such as the network traffic and system logs consist of the complex attributes with the different formats such as categorical and numerical input values. Third, we observe that MF uses various data structures because memory dumps from memory layout are unstructured. Fourth, fuzzing generally uses no data conversion since Deep Learning models are used to generate the new input data with the same data format as the original raw data. Finally, we observe that MC commonly uses one-hot encoding and embedding because malware binary and well-structured security log files include categorical, numerical and unstructured data in general. These observations indicate that type of data strongly influences on use of Phase II methods. We also observe that only MF among eight security problems commonly transform raw data into well-structured data embedding a specialized security domain knowledge. This observation indicates that various conversion methods of raw data into well-structure data which embed various security domain knowledge are not yet studied in depth.
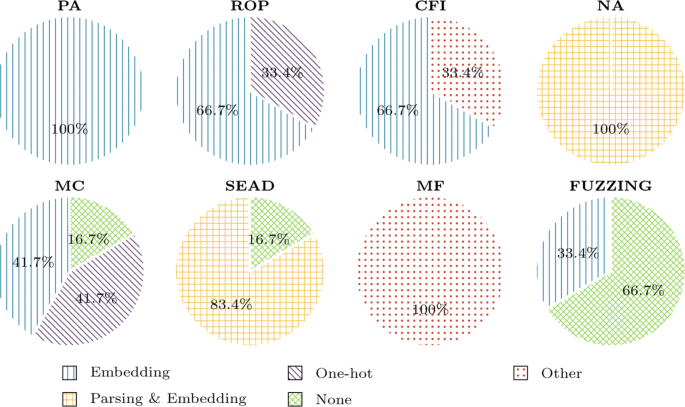
Statistics of Phase II methods for eight security problems
Findings on different data types
Note that according to types of data, a NN model works better than the others. For example, CNN works well with images but does not work with text. From Fig. 4 for raw binary data, we observe that 51.9%, 22.3% and 11.2% of security papers use embedding, one-hot encoding and Others , respectively. Only 14.9% of security papers, especially related to fuzzing, do not use one of Phase II methods. This observation indicates that binary input data which have various binary formats should be converted into an input data type which works well with a specific NN model. From Fig. 4 for raw text data, we also observe that 92.4% of papers use parsing with embedding as the Phase II method. Note that compared with raw binary data whose formats are unstructured, raw text data generally have the well-structured format. Raw text data collected from network traffics may also have various types of attribute values. Thus, raw text data are commonly parsed after embedding to reduce redundancy and dimensionality of data.
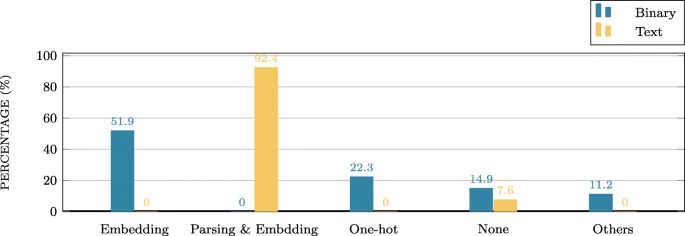
Statistics of Phase II methods on type of data
Findings on various models of NN
According to types of the converted data, a specific NN model works better than the others. For example, CNN works well with images but does not work with raw text. From Fig. 6 b, we observe that use of embedding for DNN (42.9%), RNN (28.6%) and LSTM (14.3%) models approximates to 85%. This observation indicates that embedding methods are commonly used to generate sequential input data for DNN, RNN and LSTM models. Also, we observe that one-hot encoded data are commonly used as input data for DNN (33.4%), CNN (33.4%) and LSTM (16.7%) models. This observation indicates that one-hot encoding is one of common Phase II methods to generate numerical values for image and sequential input data because many raw input data for security problems commonly have the categorical features. We observe that the CNN (66.7%) model uses the converted input data using the Others methods to express the specific domain knowledge into the input data structure of NN networks. This is because general vector formats including graph, matrix and so on can also be used as an input value of the CNN model.
From Fig. 5 b, we observe that DNN, RNN and LSTM models commonly use embedding, one-hot encoding and parsing combined with embedding. For example, we observe security papers of 54.6%, 18.2% and 18.2% models use embedding, one-hot encoding and parsing combined with embedding, respectively. We also observe that the CNN model is used with various Phase II methods because any vector formats such as image can generally be used as an input data of the CNN model.
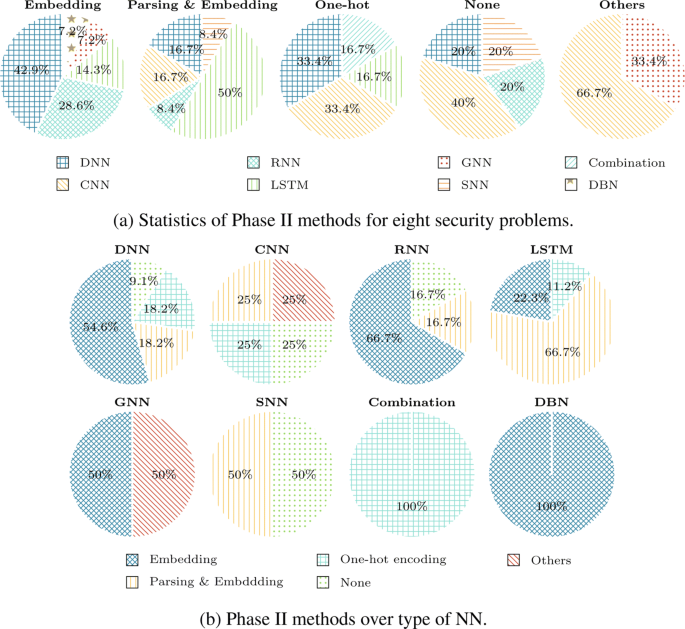
Statistics of Phase II methods for various types of NNs
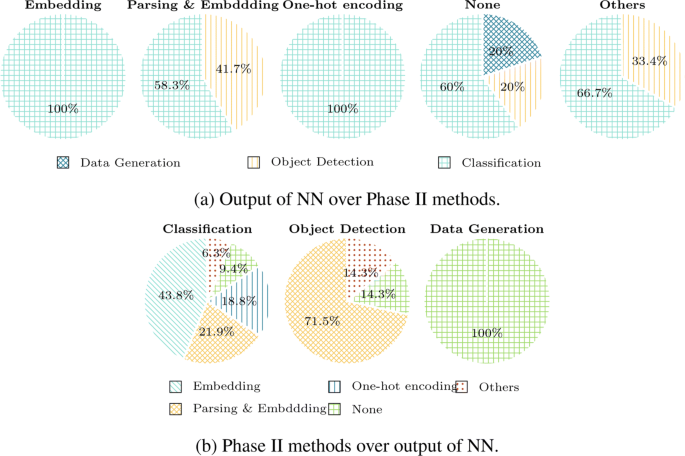
Statistics of Phase II methods for various output of NN
Findings on output of NN models
According to the relationship between output of security problem and output of NN, we may use a specific Phase II method. For example, if output of security problem is given into a class (e.g., normal or abnormal), output of NN should also be given into classification.
From Fig. 6 a, we observe that embedding is commonly used to support a security problem for classification (100%). Parsing combined with embedding is used to support a security problem for object detection (41.7%) and classification (58.3%). One-hot encoding is used only for classification (100%). These observations indicate that classification of a given input data is the most common output which is obtained using Deep Learning under various Phase II methods.
From Fig. 6 b, we observe that security problems, whose outputs are classification, commonly use embedding (43.8%) and parsing combined with embedding (21.9%) as the Phase II method. We also observe that security problems, whose outputs are object detection, commonly use parsing combined with embedding (71.5%). However, security problems, whose outputs are data generation, commonly do not use the Phase III methods. These observations indicate that a specific Phase II method has been used according to the relationship between output of security problem and use of NN models.
Further areas of investigation
Since any Deep Learning models are stochastic, each time the same Deep Learning model is fit even on the same data, it might give different outcomes. This is because deep neural networks use random values such as random initial weights. However, if we have all possible data for every security problem, we may not make random predictions. Since we have the limited sample data in practice, we need to get the best-effort prediction results using the given Deep Learning model, which fits to the given security problem.
How can we get the best-effort prediction results of Deep Learning models for different security problems? Let us begin to discuss about the stability of evaluation results for our selected papers for review. Next, we will elaborate the influence of security domain knowledge on prediction results of Deep Learning models. Finally, we will discuss some common issues in those fields.
How stable are evaluation results?
When evaluating neural network models, Deep Learning models commonly use three methods: train-test split; train-validation-test split; and k -fold cross validation. A train-test split method splits the data into two parts, i.e., training and test data. Even though a train-test split method makes the stable prediction with a large amount of data, predictions vary with a small amount of data. A train-validation-test split method splits the data into three parts, i.e., training, validation and test data. Validation data are used to estimate predictions over the unknown data. k -fold cross validation has k different set of predictions from k different evaluation data. Since k -fold cross validation takes the average expected performance of the NN model over k -fold validation data, the evaluation result is closer to the actual performance of the NN model.
From the analysis results of our selected papers for review, we observe that 40.0% and 32.5% of the selected papers are measured using a train-test split method and a train-validation-test split method, respectively. Only 17.5% of the selected papers are measured using k -fold cross validation. This observation implies that even though the selected papers show almost more than 99% of accuracy or 0.99 of F1 score, most solutions using Deep Learning might not show the same performance for the noisy data with randomness.
To get stable prediction results of Deep Learning models for different security problems, we might reduce the influence of the randomness of data on Deep Learning models. At least, it is recommended to consider the following methods:
Do experiments using the same data many time : To get a stable prediction with a small amount of sample data, we might control the randomness of data using the same data many times.
Use cross validation methods, e.g. k -fold cross validation : The expected average and variance from k -fold cross validation estimates how stable the proposed model is.
How does security domain knowledge influence the performance of security solutions using deep learning?
When selecting a NN model that analyzes an application dataset, e.g., MNIST dataset ( LeCun and Cortes 2010 ), we should understand that the problem is to classify a handwritten digit using a 28×28 black. Also, to solve the problem with the high classification accuracy, it is important to know which part of each handwritten digit mainly influences the outcome of the problem, i.e., a domain knowledge.
While solving a security problem, knowing and using security domain knowledge for each security problem is also important due to the following reasons (we label the observations and indications that realted to domain knowledge with ‘ ∗ ’):
Firstly, the dataset generation, preprocess and feature selection highly depend on domain knowledge. Different from the image classification and natural language processing, raw data in the security domain cannot be sent into the NN model directly. Researchers need to adopt strong domain knowledge to generate, extract, or clean the training set. Also, in some works, domain knowledge is adopted in data labeling because labels for data samples are not straightforward.
Secondly, domain knowledge helps with the selection of DL models and its hierarchical structure. For example, the neural network architecture (hierarchical and bi-directional LSTM) designed in DEEPVSA ( Guo et al. 2019 ) is based on the domain knowledge in the instruction analysis.
Thirdly, domain knowledge helps to speed up the training process. For instance, by adopting strong domain knowledge to clean the training set, domain knowledge helps to spend up the training process while keeping the same performance. However, due to the influence of the randomness of data on Deep Learning models, domain knowledge should be carefully adopted to avoid potential decreased accuracy.
Finally, domain knowledge helps with the interpretability of models’ prediction. Recently, researchers try to explore the interpretability of the deep learning model in security areas, For instance, LEMNA ( Guo et al. 2018 ) and EKLAVYA ( Chua et al. 2017 ) explain how the prediction was made by models from different perspectives. By enhancing the trained models’ interpretability, they can improve their approaches’ accuracy and security. The explanation for the relation between input, hidden state, and the final output is based on domain knowledge.
Common challenges
In this section, we will discuss the common challenges when applying DL to solving security problems. These challenges as least shared by the majority of works, if not by all the works. Generally, we observe 7 common challenges in our survey:
The raw data collected from the software or system usually contains lots of noise.
The collected raw is untidy. For instance, the instruction trace, the Untidy data: variable length sequences,
Hierarchical data syntactic/structure. As discussed in Section 3 , the information may not simply be encoded in a single layer, rather, it is encoded hierarchically, and the syntactic is complex.
Dataset generation is challenging in some scenarios. Therefore, the generated training data might be less representative or unbalanced.
Different for the application of DL in image classification, and natural language process, which is visible or understandable, the relation between data sample and its label is not intuitive, and hard to explain.
Availability of trained model and quality of dataset.
Finally, we investigate the availability of the trained model and the quality of the dataset. Generally, the availability of the trained models affects its adoption in practice, and the quality of the training set and the testing set will affect the credibility of testing results and comparison between different works. Therefore, we collect relevant information to answer the following four questions and shows the statistic in Table 4 :
Whether a paper’s source code is publicly available?
Whether raw data, which is used to generate the dataset, is publicly available?
Whether its dataset is publicly available?
How are the quality of the dataset?
We observe that both the percentage of open source of code and dataset in our surveyed fields is low, which makes it a challenge to reproduce proposed schemes, make comparisons between different works, and adopt them in practice. Specifically, the statistic shows that 1) the percentage of open source of code in our surveyed fields is low, only 6 out of 16 paper published their model’s source code. 2) the percentage of public data sets is low. Even though, the raw data in half of the works are publicly available, only 4 out of 16 fully or partially published their dataset. 3) the quality of datasets is not guaranteed, for instance, most of the dataset is unbalanced.
The performance of security solutions even using Deep Learning might vary according to datasets. Traditionally, when evaluating different NN models in image classification, standard datasets such as MNIST for recognizing handwritten 10 digits and CIFAR10 ( Krizhevsky et al. 2010 ) for recognizing 10 object classes are used for performance comparison of different NN models. However, there are no known standard datasets for evaluating NN models on different security problems. Due to such a limitation, we observe that most security papers using Deep Learning do not compare the performance of different security solutions even when they consider the same security problem. Thus, it is recommended to generate and use a standard dataset for a specific security problem for comparison. In conclusion, we think that there are three aspects that need to be improved in future research:
Developing standard dataset.
Publishing their source code and dataset.
Improving the interpretability of their model.
This paper seeks to provide a dedicated review of the very recent research works on using Deep Learning techniques to solve computer security challenges. In particular, the review covers eight computer security problems being solved by applications of Deep Learning: security-oriented program analysis, defending ROP attacks, achieving CFI, defending network attacks, malware classification, system-event-based anomaly detection, memory forensics, and fuzzing for software security. Our observations of the reviewed works indicate that the literature of using Deep Learning techniques to solve computer security challenges is still at an earlier stage of development.
Availability of data and materials
Not applicable.
We refer readers to ( Wang and Liu 2019 ) which systemizes the knowledge of protections by CFI schemes.
Abadi, M, Budiu M, Erlingsson Ú, Ligatti J (2009) Control-Flow Integrity Principles, Implementations, and Applications. ACM Trans Inf Syst Secur (TISSEC) 13(1):4.
Article Google Scholar
Bao, T, Burket J, Woo M, Turner R, Brumley D (2014) BYTEWEIGHT: Learning to Recognize Functions in Binary Code In: 23rd USENIX Security Symposium (USENIX Security 14), 845–860.. USENIX Association, San Diego.
Google Scholar
Bekrar, S, Bekrar C, Groz R, Mounier L (2012) A Taint Based Approach for Smart Fuzzing In: 2012 IEEE Fifth International Conference on Software Testing, Verification and Validation.. IEEE. https://doi.org/10.1109/icst.2012.182 .
Bengio, Y, Courville A, Vincent P (2013) Representation Learning: A Review and New Perspectives. IEEE Trans Pattern Anal Mach Intell 35(8):1798–1828.
Bertero, C, Roy M, Sauvanaud C, Tredan G (2017) Experience Report: Log Mining Using Natural Language Processing and Application to Anomaly Detection In: 2017 IEEE 28th International Symposium on Software Reliability Engineering (ISSRE).. IEEE. https://doi.org/10.1109/issre.2017.43 .
Brown, A, Tuor A, Hutchinson B, Nichols N (2018) Recurrent Neural Network Attention Mechanisms for Interpretable System Log Anomaly Detection In: Proceedings of the First Workshop on Machine Learning for Computing Systems, MLCS’18, 1:1–1:8.. ACM, New York.
Böttinger, K, Godefroid P, Singh R (2018) Deep Reinforcement Fuzzing In: 2018 IEEE Security and Privacy Workshops (SPW), pages 116–122.. IEEE. https://doi.org/10.1109/spw.2018.00026 .
Chen, L, Sultana S, Sahita R (2018) Henet: A Deep Learning Approach on Intel Ⓡ Processor Trace for Effective Exploit Detection In: 2018 IEEE Security and Privacy Workshops (SPW).. IEEE. https://doi.org/10.1109/spw.2018.00025 .
Chua, ZL, Shen S, Saxena P, Liang Z (2017) Neural Nets Can Learn Function Type Signatures from Binaries In: 26th USENIX Security Symposium (USENIX Security 17), 99–116.. USENIX Association. https://dl.acm.org/doi/10.5555/3241189.3241199 .
Cui, Z, Xue F, Cai X, Cao Y, Wang GG, Chen J (2018) Detection of Malicious Code Variants Based on Deep Learning. IEEE Trans Ind Inform 14(7):3187–3196.
Dahl, GE, Stokes JW, Deng L, Yu D (2013) Large-scale Malware Classification using Random Projections and Neural Networks In: IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP).. IEEE. https://doi.org/10.1109/icassp.2013.6638293 .
Dai, Y, Li H, Qian Y, Lu X (2018) A Malware Classification Method Based on Memory Dump Grayscale Image. Digit Investig 27:30–37.
Das, A, Mueller F, Siegel C, Vishnu A (2018) Desh: Deep Learning for System Health Prediction of Lead Times to Failure in HPC In: Proceedings of the 27th International Symposium on High-Performance Parallel and Distributed Computing, HPDC ’18, 40–51.. ACM, New York.
Chapter Google Scholar
David, OE, Netanyahu NS (2015) DeepSign: Deep Learning for Automatic Malware Signature Generation and Classification In: 2015 International Joint Conference on Neural Networks (IJCNN).. IEEE. https://doi.org/10.1109/ijcnn.2015.7280815 .
De La Rosa, L, Kilgallon S, Vanderbruggen T, Cavazos J (2018) Efficient Characterization and Classification of Malware Using Deep Learning In: 2018 Resilience Week (RWS).. IEEE. https://doi.org/10.1109/rweek.2018.8473556 .
Du, M, Li F (2016) Spell: Streaming Parsing of System Event Logs In: 2016 IEEE 16th International Conference on Data Mining (ICDM).. IEEE. https://doi.org/10.1109/icdm.2016.0103 .
Du, M, Li F, Zheng G, Srikumar V (2017) DeepLog: Anomaly Detection and Diagnosis from System Logs Through Deep Learning In: Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, CCS ’17, 1285–1298.. ACM, New York.
Faker, O, Dogdu E (2019) Intrusion Detection Using Big Data and Deep Learning Techniques In: Proceedings of the 2019 ACM Southeast Conference on ZZZ - ACM SE ’19, 86–93.. ACM. https://doi.org/10.1145/3299815.3314439 .
Ghosh, AK, Wanken J, Charron F (1998) Detecting Anomalous and Unknown Intrusions against Programs In: Proceedings 14th annual computer security applications conference (Cat. No. 98Ex217), 259–267.. IEEE, Washington, DC.
Godefroid, P, Peleg H, Singh R (2017) Learn&Fuzz: Machine Learning for Input Fuzzing In: 2017 32nd IEEE/ACM International Conference on Automated Software Engineering (ASE).. IEEE. https://doi.org/10.1109/ase.2017.8115618 .
Google Developers (2016) Embeddings . https://developers.google.com/machine-learning/crash-course/embeddings/video-lecture .
Guo, W, Mu D, Xu J, Su P, Wang G, Xing X (2018) Lemna: Explaining deep learning based security applications In: Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, pages 364–379. https://doi.org/10.1145/3243734.3243792 .
Guo, W, Mu D, Xing X, Du M, Song D (2019) { DEEPVSA }: Facilitating Value-set Analysis with Deep Learning for Postmortem Program Analysis In: 28th USENIX Security Symposium (USENIX Security 19), 1787–1804.. USENIX Association, Santa Clara, CA. https://www.usenix.org/conference/usenixsecurity19/presentation/guo .
Heller, KA, Svore KM, Keromytis AD, Stolfo SJ (2003) One Class Support Vector Machines for Detecting Anomalous Windows Registry Accesses In: Proceedings of the Workshop on Data Mining for Computer Security.. IEEE, Dallas, TX.
Horwitz, S (1997) Precise Flow-insensitive May-alias Analysis is NP-hard. ACM Trans Program Lang Syst 19(1):1–6.
Hu, W, Liao Y, Vemuri VR (2003) Robust Anomaly Detection using Support Vector Machines In: Proceedings of the international conference on machine learning, 282–289.. Citeseer, Washington, DC.
IDS 2017 Datasets (2019). https://www.unb.ca/cic/datasets/ids-2017.html .
Kalash, M, Rochan M, Mohammed N, Bruce NDB, Wang Y, Iqbal F (2018) Malware Classification with Deep Convolutional Neural Networks In: 2018 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), 1–5. https://doi.org/10.1109/NTMS.2018.8328749 .
Kiriansky, V, Bruening D, Amarasinghe SP, et al. (2002) Secure Execution via Program Shepherding In: USENIX Security Symposium, volume 92, page 84.. USENIX Association, Monterey, CA.
Kolosnjaji, B, Eraisha G, Webster G, Zarras A, Eckert C (2017) Empowering Convolutional Networks for Malware Classification and Analysis. Proc Int Jt Conf Neural Netw 2017-May:3838–3845.
Krizhevsky, A, Nair V, Hinton G (2010) CIFAR-10 (Canadian Institute for Advanced Research). https://www.cs.toronto.edu/~kriz/cifar.html .
LeCun, Y, Cortes C (2010) MNIST Handwritten Digit Database. http://yann.lecun.com/exdb/mnist/ .
Li, J, Zhao B, Zhang C (2018) Fuzzing: A Survey. Cybersecurity 1(1):6.
Li, X, Hu Z, Fu Y, Chen P, Zhu M, Liu P (2018) ROPNN: Detection of ROP Payloads Using Deep Neural Networks. arXiv preprint arXiv:1807.11110.
McLaughlin, N, Martinez Del Rincon J, Kang BJ, Yerima S, Miller P, Sezer S, Safaei Y, Trickel E, Zhao Z, Doupe A, Ahn GJ (2017) Deep Android Malware Detection In: Proceedings of the 7th ACM Conference on Data and Application Security and Privacy, 301–308. https://doi.org/10.1145/3029806.3029823 .
Meng, W, Liu Y, Zhu Y, Zhang S, Pei D, Liu Y, Chen Y, Zhang R, Tao S, Sun P, Zhou R (2019) Loganomaly: Unsupervised Detection of Sequential and Quantitative Anomalies in Unstructured Logs In: Proceedings of the Twenty-Eighth International Joint Conference on Artificial Intelligence.. International Joint Conferences on Artificial Intelligence Organization. https://doi.org/10.24963/ijcai.2019/658 .
Michalas, A, Murray R (2017) MemTri: A Memory Forensics Triage Tool Using Bayesian Network and Volatility In: Proceedings of the 2017 International Workshop on Managing Insider Security Threats, MIST ’17, pages 57–66.. ACM, New York.
Millar, K, Cheng A, Chew HG, Lim C-C (2018) Deep Learning for Classifying Malicious Network Traffic In: Pacific-Asia Conference on Knowledge Discovery and Data Mining, 156–161.. Springer. https://doi.org/10.1007/978-3-030-04503-6_15 .
Moustafa, N, Slay J (2015) UNSW-NB15: A Comprehensive Data Set for Network Intrusion Detection Systems (UNSW-NB15 Network Data Set) In: 2015 Military Communications and Information Systems Conference (MilCIS).. IEEE. https://doi.org/10.1109/milcis.2015.7348942 .
Nguyen, MH, Nguyen DL, Nguyen XM, Quan TT (2018) Auto-Detection of Sophisticated Malware using Lazy-Binding Control Flow Graph and Deep Learning. Comput Secur 76:128–155.
Nix, R, Zhang J (2017) Classification of Android Apps and Malware using Deep Neural Networks. Proc Int Jt Conf Neural Netw 2017-May:1871–1878.
NSCAI Intern Report for Congress (2019). https://drive.google.com/file/d/153OrxnuGEjsUvlxWsFYauslwNeCEkvUb/view .
Petrik, R, Arik B, Smith JM (2018) Towards Architecture and OS-Independent Malware Detection via Memory Forensics In: Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, CCS ’18, pages 2267–2269.. ACM, New York.
Phan, AV, Nguyen ML, Bui LT (2017) Convolutional Neural Networks over Control Flow Graphs for Software defect prediction In: 2017 IEEE 29th International Conference on Tools with Artificial Intelligence (ICTAI), 45–52.. IEEE. https://doi.org/10.1109/ictai.2017.00019 .
Rajpal, M, Blum W, Singh R (2017) Not All Bytes are Equal: Neural Byte Sieve for Fuzzing. arXiv preprint arXiv:1711.04596.
Rosenberg, I, Shabtai A, Rokach L, Elovici Y (2018) Generic Black-box End-to-End Attack against State of the Art API Call based Malware Classifiers In: Research in Attacks, Intrusions, and Defenses, 490–510.. Springer. https://doi.org/10.1007/978-3-030-00470-5_23 .
Salwant, J (2015) ROPGadget. https://github.com/JonathanSalwan/ROPgadget .
Saxe, J, Berlin K (2015) Deep Neural Network based Malware Detection using Two Dimensional Binary Program Features In: 2015 10th International Conference on Malicious and Unwanted Software (MALWARE).. IEEE. https://doi.org/10.1109/malware.2015.7413680 .
Shacham, H, et al. (2007) The Geometry of Innocent Flesh on the Bone: Return-into-libc without Function Calls (on the x86) In: ACM conference on Computer and communications security, pages 552–561. https://doi.org/10.1145/1315245.1315313 .
Shi, D, Pei K (2019) NEUZZ: Efficient Fuzzing with Neural Program Smoothing. IEEE Secur Priv.
Shin, ECR, Song D, Moazzezi R (2015) Recognizing Functions in Binaries with Neural Networks In: 24th USENIX Security Symposium (USENIX Security 15).. USENIX Association. https://dl.acm.org/doi/10.5555/2831143.2831182 .
Sommer, R, Paxson V (2010) Outside the Closed World: On Using Machine Learning For Network Intrusion Detection In: 2010 IEEE Symposium on Security and Privacy (S&P).. IEEE. https://doi.org/10.1109/sp.2010.25 .
Song, W, Yin H, Liu C, Song D (2018) DeepMem: Learning Graph Neural Network Models for Fast and Robust Memory Forensic Analysis In: Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, CCS ’18, 606–618.. ACM, New York.
Stephens, N, Grosen J, Salls C, Dutcher A, Wang R, Corbetta J, Shoshitaishvili Y, Kruegel C, Vigna G (2016) Driller: Augmenting Fuzzing Through Selective Symbolic Execution In: Proceedings 2016 Network and Distributed System Security Symposium.. Internet Society. https://doi.org/10.14722/ndss.2016.23368 .
Tan, G, Jaeger T (2017) CFG Construction Soundness in Control-Flow Integrity In: Proceedings of the 2017 Workshop on Programming Languages and Analysis for Security - PLAS ’17.. ACM. https://doi.org/10.1145/3139337.3139339 .
Tobiyama, S, Yamaguchi Y, Shimada H, Ikuse T, Yagi T (2016) Malware Detection with Deep Neural Network Using Process Behavior. Proc Int Comput Softw Appl Conf 2:577–582.
Unicorn-The ultimate CPU emulator (2015). https://www.unicorn-engine.org/ .
Ustebay, S, Turgut Z, Aydin MA (2019) Cyber Attack Detection by Using Neural Network Approaches: Shallow Neural Network, Deep Neural Network and AutoEncoder In: Computer Networks, 144–155.. Springer. https://doi.org/10.1007/978-3-030-21952-9_11 .
Varenne, R, Delorme JM, Plebani E, Pau D, Tomaselli V (2019) Intelligent Recognition of TCP Intrusions for Embedded Micro-controllers In: International Conference on Image Analysis and Processing, 361–373.. Springer. https://doi.org/10.1007/978-3-030-30754-7_36 .
Wang, Z, Liu P (2019) GPT Conjecture: Understanding the Trade-offs between Granularity, Performance and Timeliness in Control-Flow Integrity. eprint 1911.07828, archivePrefix arXiv, primaryClass cs.CR, arXiv.
Wang, Y, Wu Z, Wei Q, Wang Q (2019) NeuFuzz: Efficient Fuzzing with Deep Neural Network. IEEE Access 7:36340–36352.
Xu, W, Huang L, Fox A, Patterson D, Jordan MI (2009) Detecting Large-Scale System Problems by Mining Console Logs In: Proceedings of the ACM SIGOPS 22Nd Symposium on Operating Systems Principles SOSP ’09, 117–132.. ACM, New York.
Xu, X, Liu C, Feng Q, Yin H, Song L, Song D (2017) Neural Network-Based Graph Embedding for Cross-Platform Binary Code Similarity Detection In: Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, 363–376.. ACM. https://doi.org/10.1145/3133956.3134018 .
Xu, L, Zhang D, Jayasena N, Cavazos J (2018) HADM: Hybrid Analysis for Detection of Malware 16:702–724.
Xu, X, Ghaffarinia M, Wang W, Hamlen KW, Lin Z (2019) CONFIRM: Evaluating Compatibility and Relevance of Control-flow Integrity Protections for Modern Software In: 28th USENIX Security Symposium (USENIX Security 19), pages 1805–1821.. USENIX Association, Santa Clara.
Yagemann, C, Sultana S, Chen L, Lee W (2019) Barnum: Detecting Document Malware via Control Flow Anomalies in Hardware Traces In: Lecture Notes in Computer Science, 341–359.. Springer. https://doi.org/10.1007/978-3-030-30215-3_17 .
Yin, C, Zhu Y, Fei J, He X (2017) A Deep Learning Approach for Intrusion Detection using Recurrent Neural Networks. IEEE Access 5:21954–21961.
Yuan, X, Li C, Li X (2017) DeepDefense: Identifying DDoS Attack via Deep Learning In: 2017 IEEE International Conference on Smart Computing (SMARTCOMP).. IEEE. https://doi.org/10.1109/smartcomp.2017.7946998 .
Yun, I, Lee S, Xu M, Jang Y, Kim T (2018) QSYM : A Practical Concolic Execution Engine Tailored for Hybrid Fuzzing In: 27th USENIX Security Symposium (USENIX Security 18), pages 745–761.. USENIX Association, Baltimore.
Zhang, S, Meng W, Bu J, Yang S, Liu Y, Pei D, Xu J, Chen Y, Dong H, Qu X, Song L (2017) Syslog Processing for Switch Failure Diagnosis and Prediction in Datacenter Networks In: 2017 IEEE/ACM 25th International Symposium on Quality of Service (IWQoS).. IEEE. https://doi.org/10.1109/iwqos.2017.7969130 .
Zhang, J, Chen W, Niu Y (2019) DeepCheck: A Non-intrusive Control-flow Integrity Checking based on Deep Learning. arXiv preprint arXiv:1905.01858.
Zhang, X, Xu Y, Lin Q, Qiao B, Zhang H, Dang Y, Xie C, Yang X, Cheng Q, Li Z, Chen J, He X, Yao R, Lou J-G, Chintalapati M, Shen F, Zhang D (2019) Robust Log-based Anomaly Detection on Unstable Log Data In: Proceedings of the 27th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering, ESEC/FSE 2019, pages 807–817.. ACM, New York.
Zhang, Y, Chen X, Guo D, Song M, Teng Y, Wang X (2019) PCCN: Parallel Cross Convolutional Neural Network for Abnormal Network Traffic Flows Detection in Multi-Class Imbalanced Network Traffic Flows. IEEE Access 7:119904–119916.
Download references
Acknowledgments
We are grateful to the anonymous reviewers for their useful comments and suggestions.
This work was supported by ARO W911NF-13-1-0421 (MURI), NSF CNS-1814679, and ARO W911NF-15-1-0576.
Author information
Authors and affiliations.
The Pennsylvania State University, Pennsylvania, USA
Yoon-Ho Choi, Peng Liu, Zitong Shang, Haizhou Wang, Zhilong Wang, Lan Zhang & Qingtian Zou
Pusan National University, Busan, Republic of Korea
Yoon-Ho Choi
Wuhan University of Technology, Wuhan, China
Junwei Zhou
You can also search for this author in PubMed Google Scholar
Contributions
All authors read and approved the final manuscript.
Corresponding author
Correspondence to Peng Liu .
Ethics declarations
Competing interests.
PL is currently serving on the editorial board for Journal of Cybersecurity.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Choi, YH., Liu, P., Shang, Z. et al. Using deep learning to solve computer security challenges: a survey. Cybersecur 3 , 15 (2020). https://doi.org/10.1186/s42400-020-00055-5
Download citation
Received : 11 March 2020
Accepted : 17 June 2020
Published : 10 August 2020
DOI : https://doi.org/10.1186/s42400-020-00055-5
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Deep learning
- Security-oriented program analysis
- Return-oriented programming attacks
- Control-flow integrity
- Network attacks
- Malware classification
- System-event-based anomaly detection
- Memory forensics
- Fuzzing for software security
237 Cyber Security Essay Topics, Ideas, and Examples
🏆 best cybersecurity essay topics and examples, 💡 most interesting cybersecurity topics to write about, 👍 good essay topics on cybersecurity, ⭐ simple & easy cyber security essay topics, ✍️ cyber security topics for college, ⌨️ good cyber security essay examples and topics, 🖱️ compelling computer security research topics, ❓ cyber security paragraph questions.
- Ethical and Illegal Computer Hacking For the ethical hackers, they pursue hacking in order to identify the unexploited areas or determine weaknesses in systems in order to fix them.
- Artificial Intelligence in Cybersecurity The use of AI is regulated by a large amount of documentation, which should take into account the current legislation in the country of use and ethical issues related to AI, many of which have […]
- Computer Forensics Tools and Evidence Processing The purpose of this paper is to analyze available forensic tools, identify and explain the challenges of investigations, and explain the legal implication of the First and Fourth Amendments as they relate to evidence processing […]
- The Future Career in Cybersecurity During the interview, it is necessary to highlight the knowledge of working as a graph as a mathematical theory and the simple use of spanning trees in cybersecurity.
- Cybersecurity Workforce in Emergent Nations The lack of help from developed countries in the training and education of a cybersecurity workforce for developing nations can negatively affect the former. Public and private organizations also contribute to the development of cybersecurity […]
- Importance of Army Cybersecurity This includes bringing awareness to the cybersecurity issue, involving more people to combat the problem of cyberattacks, and organizing the information based on specialty and tasks that must be completed.
- Cyber Security Issue: RansomWare Until the victim pays a specific amount of money to the attackers within a particular time, cybercriminals can use the virus mentioned above to access the user’s sensitive personal or organizational information. The infection and […]
- Hacking: Positive and Negative Perception The possible advantage of cooperating with hackers for security systems mangers of international organizations and governmental organizations is the probability to recruit them and use their knowledge to empower different organizations to improve their security […]
- Benefits and Dangers of Ethical Hacking The advantages of ethical hacking The following are some of the advantages associated with the use of ethical hacking in an organization.
- Global Cybersecurity in the 21st Century Research Question: Is there a significant connection between the US President’s approach to cybersecurity and the actual presence of the given phenomenon?
- Public-Private Partnerships for Election Systems Cybersecurity In public contracts, the private sector provides the service directly to the public and bears all the associated end-user risks. Private parties can use all the gained knowledge and expertise to conduct security assessments of […]
- Cybersecurity and How It Impacts Identity Protection and/or Ransomware Firstly, organizational leadership should not undervalue the importance of cybersecurity since the risk of losing the data stored in the company’s database may harm the corporate reputation and trustworthiness.
- Computer Forensics: Identity Theft The forensics process that is maintained in the framework of computer-related technologies provides professionals with the opportunity to gather, analyze, and report on the information.
- Computer Forensics and Digital Evidence When electronic data has been collected to identify the kind of the incident and introduce evidence of the crime, it is important to organize a meeting with the witness who can provide details of the […]
- Assessment of Cybersecurity Program Maturity Padgett-Beale Financial Services must choose the appropriate framework and standards, determine required regulations and laws to comply with, and identify the best practices for maturity assessment to achieve an impenetrable cybersecurity management program.
- Sifers-Grayson Company: The Cybersecurity Breach Finally, the recommendations, as per the improvement of the incident response capability, are introduced to ensure the elimination of the identified drawbacks and the compliance of the engineering company with the security requirements presented by […]
- Hacking as a Crime and Related Theories The move to embrace the novel technology has led to the emergence of a new form of crime and behavior referred to as “hacking”. Today, the term is used to refer to individuals engaged in […]
- Sources of Digital Forensic Data With live system data, the aim of the investigator is to capture information concerning volatile data that may disappear when a device powers off or it is disconnected from the network.
- The Impact of Mobile Devices on Cybersecurity The very popularity and extent of the use of mobile computing devices and the internet creates a special vulnerability to businesses.
- Information Security Fundamentals: Computer Forensics In addition, the paper provides an overview of the techniques used in obtaining evidence from the internet and web resources, the types of evidence that can be recovered from electronic and computer resources, and the […]
- The Department of Homeland Security’s Cybersecurity Mission Cybersecurity is evolving rapidly, and DHS’s cybersecurity mission is equipped with models adapting to the ever-changing security and information dynamics. The DHS cybersecurity mission is designed with models that adapt to changing dynamics and landscapes.
- Cybersecurity in the Financial Services Industry In reaction to ransomware attacks, a business such as a bank may have to spend a substantial amount of money, which may cause customers to lose faith in the safety of their funds.
- The Biggest Cybersecurity Treat to Expect First of all, all employees who somehow use the Internet of Things devices and have access to the corporate IoT network are to be trained to utilize it correctly.
- Securing Offboarded Employees: Modern Cybersecurity Strategies Disgruntled employees can be potentially dangerous to the whole company’s well-being due to cybercrimes that can affect the entire company’s work.
- Advanced Research Methods in Cybersecurity Performance measurements refer to the internal functions of the company and ways in which cybersecurity management contributes to the accomplishment of critical tasks within the firm.
- Gaps in Cyber Security Caused by BYOD In conclusion, these vulnerabilities caused by the insufficient regulation and general unpreparedness of organizational and public networks expose facilities that use BYOD to severe risks of data leaks and hacker attacks.
- Cybersecurity Threats in Physician Practice The purpose of the source is to inform readers of the strategies to help healthcare professionals identify, avoid and respond to ransomware dangers.
- Digital Forensic Analysis of Fitbit The comparison of the results and the analyses of the data as a result of the research gave the authors of the article a conclusion in regards to the methodology that has evidence-based results in […]
- Cybersecurity Contingency & Incident Review Process Next, it is necessary to implement various stages of digital transformation of cybersecurity, which include improving the maturity of enterprises in cybersecurity issues and the use of new solutions.
- Forensic Accounting and Cyber Security The recent trend of increased exposure due to the access of extended financial and fraud concerns by social media and the internet has necessitated the need to curb the tendency.
- Hacking Prevention: Mobile Phone Anti-Virus However, the less discussed and addressed subject is the cybersecurity of mobile phones, which are among the most used and vital devices for the majority of the population.
- Legal Risks of AI Cybersecurity in the European Union Thus, this paper seeks to fill the gap on whether or not safety and security can be covered in cybersecurity for AI by the same rules that are used in private law. The EU has […]
- Cyber Security: Critical Infrastructure Protection Objects of forensic science are storage mediums that are not part of other devices and which fulfill the function of information storage as the main one.
- Relation Between Cybersecurity and Cybercrime Meanwhile, one should not assume that cybersecurity is the prerogative of technicians and software engineers only since the consequences of a breach will affect the entire business or private life of those not associated with […]
- Cybersecurity in 2021-2022: Cybersecurity Advancements In IoT, Blockchain is being utilized to protect connected devices through decentralization and encryption, adding to the evolving nature of system security.
- Encryption and Hacking Techniques There are several advantages of text-based encryption, and they include the fact that the data can be used across different devices through the concept of multi-device encryption techniques.
- The US, Russia, and China Cybersecurity Conflict The current situation in the space of cybersecurity provides a significant example of how complicated this area of National Security and its influence on foreign politics can be.
- Cybersecurity and Geopolitics Relationship Provision of security to information technology and the tools used in the technology is also paramount. Cyber security is also described as measures and operations that are put in place to be to ensure that […]
- Cybersecurity and Corporations’ Input to It Whatever committee or board of directors is in charge of overseeing cybersecurity risks, the primary goal is for an organization to have an integrated approach to preparing for and protecting against cyber incidents and detecting […]
- Cybersecurity and Corporations’ Role First, it is worth indicating some of the key reasons for corporations to be in the center of cybersecurity discussion. In April, the company rejected the possibility of a data breach and apparently did not […]
- Cybersecurity and Geopolitical Issues Geopolitics is the study of integration and effect of earth geography and physical outlay on the political structures, and international relations and reforms that affect the same at different levels.
- Virtual Reality and Cybersecurity As a result, it is the mandate of the framework entities to establish solutions to the inherent barriers to the implementation of the business plan.
- Cybersecurity Policy Regarding Critical Infrastructures The article will explicitly analyze the processes behind cybersecurity development as well as the impact of the cybersecurity polies to the global security policies.
- Cybersecurity: Critical Infrastructure Control Systems The most vital stages of this nature include the analysis of the situation, the assessment of goals to make sure that they are realistic, and the expected effectiveness of implementing new policies.
- Cybersecurity in the United States Thus, the current research project is going to address the following question: Is there a significant connection between the US President’s approach to cybersecurity and the actual presence of the given phenomenon?
- Cybersecurity: The Matter of National Security However, if the security of cyberspace is critically evaluated and all the risks eliminated, cyberspace can be an asset that will continue to transform the world.
- Cybersecurity Advancements in Electric Power Systems Therefore, there will be an increase in the volume of work performed, a reduction in design time and an increase in the quality of work through the use of technology in the next five years.
- Cybersecurity Dangers and Their Analysis The officer clicks the file, and the malware attacks the system stealing the data and bypassing some security measures. The cyber security framework under the NIST is helping organizations to understand and manage cybersecurity.
- The US and Apple Relationship in the Field of Cybersecurity In this paragraph, an important aspect is to determine the degree of interaction between the two structures. This paper argues that in times of crisis, such powers should be surrendered to the more considerable public […]
- Data Management and Cybersecurity Namely, the principal standard of the HIPAA, as well as the concept of cybersecurity, have proven to factor into some of the key aspects of my professional and personal life.
- Cybercrime and Cybersecurity as Challenges One will also learn the defensive cyber security technologies and techniques used in modern organizations to protect systems data and achieve Knowledge of the maintenance and design of reliable and safe information systems.
- Digital Forensics Tools and Software One of the most famous software programs for digital forensics is Autopsy, a toolkit that examines the images present on a device’s hard drive.
- Tim Cook’s Leadership and Apple’s Cybersecurity In this paper, the main types of leadership that can be applied to the leadership style of Tim Cook are considered.
- Cybersecurity Weaknesses: The Case of LinkedIn The Internet has become the largest storage of personal and corporate information in the history of the world. The data relating to hundreds of millions of users was leaked online in the Dark Web segment […]
- The Importance of Leadership Skills in the Field of Cybersecurity The wider the information networks cover the world, the more frequent and dangerous cyber-attacks are, and the more cybersecurity specialists become in demand.
- White Hat and Black Hat Hacking On the other hand, White Hats work with companies and help them identify weaknesses in their systems and fix relevant vulnerabilities to ensure that attackers cannot illegally gain access to data.
- Modern Cybercrime: Most Recent Threats and Cybersecurity This is due to the fact that the Internet is a public open system in which data moves uncontrollably and can be discovered, intercepted, or stolen if the correct knowledge of the equipment is applied.
- Cybersecurity Strategy, Law, and Policy Team Assignment It may be critical to prevent cybersecurity breaches or data leaks to maintain the effective functioning of the government and ensure the sovereignty of the country.
- The Cybersecurity Threat Landscape The threats may come from different sources, and the criminals may focus on distinct vulnerabilities in the security of the system.
- Solving the Cybersecurity Workforce Crisis Since cyber security specialists are highly demanded in the current market, the private sector has been offering increased compensation in comparison with the government sector, which has led to decreased interest in IT positions in […]
- Cryptographic Algorithms: The Use in Cyber Security Cryptographic protection of a system depends on two factors, 1) the strength of the keys and effectiveness of associated protocols, and 2) protection of said keys via key management.
- Cybersecurity Implementation Plan for PBI-FS Therefore, the current plan will define the objectives, goals, and objectives, and scope of the implementation. The implementation of the cybersecurity management plan pursues both business and project goals and objectives.
- Facebook Compatibility With Padgett-Beale Cybersecurity Philosophy The purpose of this paper is to evaluate Facebook on the subject of cybersecurity and compatibility with Padgett-Beale’s cybersecurity philosophy and goals.
- Cybersecurity Issues in Industrial Critical Infrastructure This way, the author analyzes the potential impact of various cybersecurity threats capable of interrupting the stability of the supply of energy to communities and industries.
- Supply Chain’s Cybersecurity and Risk Analysis Since there are so many parties involved, it is crucial to assess every part of the process, from obtaining the raw material to the delivery to the customer. Cybersecurity is the critical answer to most […]
- Amazon Inc.’s Business Profile and Cybersecurity On the contrary, Amazon has continued to rise in the industry and has expanded from selling only books to trade in nearly any product and providing various services.
- Integrating Cybersecurity Framework With Information Technology Governance Frameworks ISMS builds a model of relationships between the aforementioned activities, and, as Almuhammadi and Alsaleh argue, companies “understand their cyber security risk management approach and what are the processes in place to manage the risk”.
- Cybersecurity, Ethics, and Privacy in the Global Business Environment Therefore, the purpose of this paper is to cover the types of possible threats and mitigation methods, explain the importance of a continuity plan, and outline ethical and privacy concerns for organizations.
- Technology Acceptance Model and Cybersecurity In this context, the implementation of TAM in the company is critical for the effective functioning of the organization. In this context, the introduction of TAM leads to the fact that satisfaction directly affects the […]
- Cybersecurity: Multi-State Information Sharing and Analysis Center The MS-ISAC also advises the agencies on the best tools available in the market that provide the best protection of the government systems and data.
- Cybersecurity Strategy and Plan of Action Padgett-Beale’s primary intention of merging the company was to relocate the call epicenter to a property owned by the company roughly 10 miles from the company’s previous location and opposite the newly released Padgett-Beale resort.
- Digital Forensic Examination, DVR Another application would be to determine the network’s or a user’s IP and track their online activity. The information can be used to determine an unknown individual’s location and possibly identity, or for a known […]
- Cybersecurity in the Energy Sector The stable supply of energy is the key to the normal functioning of American society, as it fuels all essential industries that ensure the vitality of the nation.
- Cybersecurity for Open Data Initiatives Governments continue to play a vital role in the open data movement.Data.gov was developed under OPEN Government Data Act; this is Title II of Foundations for the Evidence-based Policymaking Act.
- Computer Forensic Incident All evidence should be collected in the presence of experts in order to avoid losing data as well as violating privacy rights.N.
- Cybersecurity Threats to Educational Institutions The rapid adoption of digital solutions is exposing schools to the cyber-security threat, which is currently the biggest concern that these institutions face as they make a complete shift from the analog to the digital […]
- Cybersecurity Necessity and Benefits Second, the exploration of human factors in the framework of cyber-security can assist in resolving the issues of understanding a defender’s cognitive state, possibilities for automation, and an attacker’s subjective traits.
- Internet Hacking and Cybersecurity Conundrum Analysis Many people have gained access to computer systems, the Internet, and related products and services, leading to the emergence of cyber-related threats. Cybersecurity improvements are vital to the continuous developments in information technology, national security, […]
- Internet Hacking and Cybersecurity Conundrum Therefore, the increasing number of attacks during the pandemic could be handled with the help of machine learning and have the numerous human workers assigned to less crucial tasks that actually require human judgment.
- Government and Private Sector in Cybersecurity Richards highlights the government’s leading role in the context of cyber threats while stating that the number of attacks is still on the increase.
- Ethical Hacking: Is It a Thing? Computer programmers implemented the term ‘hacker’ at the beginning of the 1960s in the framework of a positive definition for an individual of dexterous software development skill.
- Computer Network Security Legal Framework With the introduction of cloud computing, the need of data protection has been rising significantly within computer networks to facilitate the protection of Intellectual Property among the users.
- Computer Forensics and Audio Data Retrieval Advanced technology in the modern society has contributed to the increase in computer and computer supported criminal activities due to the soaring increases in the number of internet users across the world and computerization of […]
- Cyber Security: Security Audit On the issue of computers and laptops, I learned from the administration that each laptop was specifically assigned to a single person who was entrusted with a password known to him and the organization’s administration […]
- Computer Forensics: Data Acquisition Data acquisition is a branch of computer forensics concerned with the retrieval of data originally located on a suspect medium such as a hard drive.
- Computer Forensic Timeline Visualization Tool The necessity to save time in computer forensic investigations is the basis of the tool that Olssen and Boldt came up with.
- The Qatar Independence Schools’ Computer Network Security Control The result of the interviews mainly outlined several common themes and patterns in terms of the design of the proposed security system.
- Computer Sciences Technology and HTTPS Hacking Protection Many are assured when they see the SSL symbol of a lock at the bottom of the screen and feel their information is confidential and the website is protected.
- Moral Issues Surrounding the Hacking of Emails The devises to enter into another people’s email and steal information in the email is called Email Hacking. It should noted that stealing of valuable information through email hacking has become a phenomenon in both […]
- Hacking Government Website From the View of Right and Justice Computer crimes refers to the use of the computer system or the internet to commit criminal activities A computer crime is an unlawful act done via a computer or a network and some of the […]
- COBIT5 vs. ITIL4 in Cybersecurity Significantly, ITSM is the alignment of information systems and enterprise IT services with business and the needs of the customer who is the end-user.
- Cybercrime and Cybersecurity: Data Protection One of the biggest Constitutional concerns for electronic surveillance as well as search and seize of evidence is protected by the Fourth Amendment which limits any such activities against the private persons, property, or effects […]
- Cyber Security Threat and Its Impact on the UAE In 2018, the UAE government and private sector were the subject of a total of 230 cyber attacks, as The National UAE reports.
- Agility and Situational Awareness in the Context of Cyber Security As a result, measures should be implemented to create cyber security, which will protect the information resources of an organization from damage.
- Research Tools Used by Computer Forensic Teams Computer Forensics is a branch of digital forensics which is used in “identifying, preserving, recovering, analyzing and presenting facts and opinions about the information”.
- Cybersecurity and Social Networks Recently, there have been many trends the security of information and communication technologies, in particular, due to the expansion of the reach of social media which increase the size of social network, which has taken […]
- Business and Cybersecurity Research Thus, a more sophisticated theoretical approach is taken to represent the goals of cyber security. A mediating variable, in turn, is the effectiveness of cyber security measures perceived from theory- and practice-related standpoints.
- Quality Control of Digital Forensics The quality control over computer forensic products is necessary because of the growth of the Internet services. Thus, the investigator and the lab are challenged not only with solving a case but also providing the […]
- Windows Logs: Improving Cybersecurity The specified event points to the need to configure the current settings of the master browser in order to address possible security issues and close the loopholes that potentially make the computer vulnerable to malware.
- Cybersecurity: Weak and Strong Passwords The strong passwords have a low probability of being guessed because the amount of possible iterations and combinations is extremely high.
- “Evolution of Federal Cyber Security” by J. Roth Even after training, the GAO report continued to demonstrate system control deficiencies due to failures in the identification of enough boundary security mechanisms, breakdown in the need to know, insufficient restriction of physical access, and […]
- The Different Sides of Hacking In a general sense, computer hacking involves the intrusion of the computing privacy of other people, damage of the computing property of other people like files, software etc.or the theft of private information by unauthorized […]
- US Brokerage Hacking by India Issue The personal accounts of the defendants were used to purchase shares of stocks, following which they hacked into other people’s accounts and made good use of their passwords and usernames.
- Computer Forensics in Criminal Investigation In this section, this paper will address the components of a computer to photograph during forensic photography, the most emergent action an investigating officer should take upon arriving at a cyber-crime scene, the value of […]
- Computer Forensics and Cyber Crime Due to age characteristics, the insufficient educational activity of parents, the provision of unlimited opportunities in the online environment, and also due to the low media literacy of the population, people can become victims of […]
- Cyber Security: Shadow Brokers Hacker Group A concealed group of hackers stole several disks containing secret data belonging to the National Security Agency in 2013; In 2016, they announced an auction to sell off the data they had obtained illegally; […]
- Cybersecurity and Encryption Analysis: VPN, PKI & Firewalls The end-to-end encryption is the more complex process that can be discussed as the data encryption between the client application and the server provided with the help of additional technologies.
- Cybersecurity as a Leadership Challenge Cybercrime can lead to the leakage of important data, system interference, and the delivery of unsatisfactory services to consumers. This sophistication has amplified the insecurity of information systems to the extent of creating more threats […]
- Shadow Brokers Hacker Group and Cyber Security Industry Therefore, in order to prevent the recurrence of such attacks, the N.S.A.needs to strengthen the security system of particularly essential information to eliminate its diversion.
- Deutsche Telecom Company’s Cyber Security The present work deals with the issue of DDoS attacks and builds a case on one of the well-known IT companies to single out the problem, the immediate solutions and preventive practices, and the lessons […]
- Cybersecurity: Deutsche Telekom Company’s Case The example of Deutsche Telekom proves the importance of the development of cybersecurity programs and strategies to protect users and their interests.
- Cybersecurity Risks Affecting Enterprises From a national security standpoint, it is crucial to know and understand the nature of the enemy and be prepared for an increase in cyberterrorism attempts.
- Cyber Security and Employees The major factors that define the thriving of cyber ganging are the insufficient level of employees’ competence, the lack of knowledge about the technical side of information protection, and non-compliance with safety standards.
- Cybersecurity Directives and Laws Describe the National Strategy for the Physical Protection of Critical Infrastructures and Key Assets and how it attempts to protect cyber assets.
- Cybersecurity and Vital Elements The focus of any risk management effort is a standard system or a framework that help organizations and individuals to manage integrity, confidentiality, and data and ensure critical resources availability.
- Emerging Cyber Security Approaches and Technologies These emerging cyber security approaches and technologies are unique and new, and they look promising for securing critical infrastructures in the cyberspace.
- Cybersecurity Dilemmas: Technology, Policy and Incentives The value of the assets determines the amount of time and resources that can be invested to protect a particular system.
- Hacking: White, Black and Gray Hats Living in the era of the Internet and online technology increases the vulnerability of the information stored online and on electronic devices.
- A Duty of Care for Cyber Security Hence, the sensitive data can be easily accessed by cyber criminals in the event that the cloud service is breached by users.
- Digital Forensics: Open Source Tools The National Software Reference Library is a project at the National Institute of Standards and Technology, the primary goals of which are to store all existing software, file profiles, and file signatures and to provide […]
- Digital Forensic Methodology In the event that sufficient information is available, the required system configuration should be developed by ensuring that the forensic software and hardware are established and validated.
- Automotive Industry’s Cybersecurity and Threats It is significant to ensure the security of this system because it focuses not only on the audio and video entertainment but also allows to control navigation system and manipulate the behavior of the car.
- Cybersecurity and Risk Control Implementation The first component of the risk treatment framework refers to the decision not to go through with the procedures that may present a risk; the second one stands for the minimization of the possibility of […]
- Online Predators and Childrens’ Cybersecurity To win the battle against online predators it is important to craft laws that were created by people with a thorough understanding of how perpetrators utilize information systems and the Internet to commit sexually-related cyber […]
- Computer and Digital Forensics and Cybercrimes This has greatly affected the success of computer forensics and it is the main drawback in this area. The world is now safer due to the increasing usage of computer forensics in court cases.
- The Role of U.S. Government in Cybersecurity According to the government of the United States, cybersecurity is among the most serious economic and security challenges that the government needs to deal with.
- Cyber Security’s and Counter Terrorism’ Intersection Realization of national interests is the concern of many states in the current international and security is the main challenge that each government is trying to cope up with given the fact terrorists are ever […]
- Cybercrime, Digital Evidence, Computer Forensics The website “howstuffworks” carries an article discussing the basics of computer forensics, this is a good example of a website that is useful in explaining or understanding the reality of cybercrime and digital evidence. Not […]
- Middle East Cybersecurity, E-Government, Ecommerce The findings in the research revealed that five main issues led to the reluctance in the adoption of e-commerce and e-governance by the Emirates.
- Sony Corporation Hacking and Security System The organization had to stop the hackers and ensure information did not flow freely but it was unfortunate, as the company sought the services of the California court because it had no capacity to deal […]
- Growth Hacking and Marketing Methods As a result, it could be observed that the combination of the growth hacking methods and the permission-based marketing appear to be one of the most efficient techniques towards marketing that is low-cost and effective.
- Cybersecurity: Stuxnet Virus Cyber security is one of the major concerns of governments in the contemporary world. It is important to note that in case of Stuxnet the three aspects prove to be vulnerable.
- Ways to Stop Cell Phones Hacking Although it is in the view of many that their phones cannot be hacked as they only protect their computers from hacking, mobile phone operators are more predisposed to being hacked since a mobile operator […]
- Banking Sector Cyber Wars and International Hacking Flaws in the network allow hackers to access the systems. In efforts to reduce hacking in the country, a number of police units have been formed.
- The Threats of Cyber Security Under the PPD-21, the owners of the critical infrastructure will work with the government to hasten the process of strengthening the national critical infrastructure in terms of the much needed security.
- Two Greatest Hacking Systems in the USA Appropriating intellectual output of someone else is also a computer malpractice that is intolerable. Generally, Computer malpractice is seen when a person shows hasty and careless conducts or behaviors when making use of computer systems.
- Cybercrime: Gary McKinnon’s Hacking Event It is the lack of effective controls that accounts for most hacking incidences, as depicted by the case of Gary McKinnon who was able to gain unauthorized access to NASA and pentagon systems, deleting crucial […]
- Important Problem of Cybersecurity Simulations The information stored in the company’s database was encrypted to create confidence in the customers on the security of the data.
- Cyber Security Technologies The technology is regularly designed to alter the attack surface of a network, making it hard for attackers to access a system and reducing the susceptibilities and predictabilities available at any time.
- Analysis of Mandiant Cyber Security Company The company’s innovation theories and products need to accommodate other companies that do not view cyber crime as a major risk on their systems.
- Leadership: Mandiant Cyber Security Company Kevin Mandia is the founder and the CEO of the company. The achievements behind Mandiant Cyber Security Company owe its success to the leadership styles exhibited in the firm.
- Adrian Lamo’s Hacking: Is It Right? The example of Galileo introduces a theory about the construction of the Solar System that was the target of interest of the well-known scientist.
- Cyber Security Threat Posed by a Terrorist Group These among other features of the internet have been identified to form the basis of the cyber terrorism attacks. A comprehensive international collaboration among investigators and prosecution teams in cases of cyber attacks have also […]
- Computer Forensics Related Ethics Due to advancement in technology, individual information can be kept in databases, the risk of accessing this data is evident and this necessity the need of such a law so as to ensure security.
- The Cyber Security Act of 2009 Analysis This would contribute to enormous benefits to both the government and private stakeholders by ensuring a cyber security strategy that serves the interests of all.
- Air Force and Cyber Security Policies The use of technology in processing financial transactions implies that there is need to boost the trustworthiness, security, resilience, and reliability.
- The Role of Computer Forensics in Criminology In fact, since the development of the virtual machine monitors, the live-state analysis in digital forensics has become common and easy to understand.
- Ethical Hacking: Bad in a Good Way Introduction of personal computers led to the increase in the number of hackers as well as hacker targets were widened. Many hackers lack the skills to damage network systems in a major way.
- Hacking: Social Engineering Online The information is fed to the main web site that’s runs the hacking software, where the information is sorted according to various numbers.
- Cyber Security in Private and Public Sectors The US has the Health Insurance Portability and Accountability Act that ensures that patients’ data remain accessible only to the authorized segment of the staff.
- Cyber Crime and Necessity of Cyber Security This is one of the policies that has been proposed to curb cyber crimes and is being debated in the congress.
- Cybersecurity in the Energy Industry In this regard, in the event that a cyber attack is launched against the energy sector, it is bound to have far reaching consequences.
- Ethics in Computer Hacking Hacking by no means follows ethics; the infiltration is to the benefit of hacker and loss of users of computer system, network or website.
- Computer Forensics and Investigations It is crucial in the investigation of crimes that are related to the manipulation of computer systems. For digital evidence to be admissible in court, investigations should be conducted in a manner that adopts the […]
- Preparing a Computer Forensics Investigation Plan However, if the information is thought to be contained in the permanent storage, then a computer has to be shut down before transporting it to a laboratory for forensic analysis. The first step in the […]
- Basic Operations of Computer Forensic Laboratories All computer forensic laboratories in the US have to adhere to the national standards before they could be certified. Standard computer forensic equipment is used to support standard procedures and conditions in the laboratories.
- Kosovo 1999: Hacking the Military The paper addresses the motivation behind the attacks, the methods of attack, and the responses of the defenders to these attacks.
- Introducing Cybersecurity Policies: Challenges and Solutions The major purpose for establishing security guidelines is to set an organization’s data security standard and describe the role of employees in safeguarding the documents of the firm, as well as the significance of a […]
- Société Générale Bank: Effective Security Controls The management of the bank revealed that Kerviel exploited every loophole to hack the computer operations at the bank. It is also important to list the potential risks because it enables the security personnel to […]
- Computer Security Breaches and Hacking To avoid such an attack in the future, it is advisable to keep both the client and server applications up to date.
- Analysis of BJG Cybersecurity Consultants
- Analysis of Cybersecurity and Risk Management
- Analysis of Cybersecurity Metrics as Well a Governmental
- Analyzing the Impact of Mobile Devices on Cybersecurity
- Assessing the Impact of Cybersecurity Attacks on Power Systems
- Building Cybersecurity Awareness: What Should Both Companies and Consumers Do to Protect Themselves?
- Current Practice Analysis for IT Control and Security
- Why Cybersecurity Is Important?
- Cybersecurity in Banking Financial Services Secto
- Cybersecurity in the European Union: Resilience and Adaptability in Governance Policy
- Cyber Security : Is No Silver Bullet For Cybersecurity?
- Dealing With Cybersecurity Threats Posed by Globalized Information Technology Suppliers
- Emerging Technologies That Impact the Cybersecurity Field
- Hacker’s Culture and Cultural Aspects of Cybersecurity
- How Cybersecurity Is an Aspect of Security?
- How Cybersecurity Is Important Resources?
- How Policies, Laws and Regulations Affect the Cybersecurity Field?
- Is Cybersecurity a Big Deal?
- Risk Assessment Uncertainties in Cybersecurity Investments
- What Is Cybersecurity?
- When Cybersecurity Policy Is Discussed the Topics Often?
- Why Computer Scientists Should Care About Cybersecurity?
- Access Single Most Important Cybersecurity Vulnerability Facing IT Mangers
- Model for the Impact of Cybersecurity Infrastructure on Economic Development in Emerging Economies: Evaluating the Contrasting Cases of India and Pakistan
- Cybersecurity and Its Importance in the Modern World
- Architecture for Managing Knowledge on Cybersecurity in Sub-Saharan Africa
- Benefits of Using Cybersecurity
- Border and Cybersecurity in the United States
- Botching Human Factors in Cybersecurity in Business Organizations
- Companies Responsibilities in Enhancing Cybersecurity Chapter
- Cybersecurity and Law Enforcement
- Cybersecurity and Organizational Change Concept Map
- Cybersecurity at European Level: The Role of Information Availability
- Cybersecurity for Critical Infrastructure Protection
- Cybersecurity for Digital Financial Service
- Cybersecurity Policy Making at a Turning Point: Analysing a New Generation of National
- Effect of Bring Your Own Device (BYOD) on Cybersecurity
- Human Aspects in Cybersecurity on a Government Agency and a Private Organization
- Improvement of Cybersecurity Is Necessary
- Most Important Cybersecurity Vulnerability Facing It Managers Computer Knowledge
- Obama Administration’s Policy Views on Cybersecurity
- Review of Cybersecurity Risks of Medical Device Software
- Small Business Cybersecurity and the Public Cloud
- The Influence of Cybersecurity Define the Hacker Motives
- Effect of Cybersecurity on Higher Education
- Importance of Cybersecurity for The Future
- Role of Cybersecurity and Its Effects on the World
- Why Should Computer Scientists Care About Cybersecurity?
- What Are the Roles and Responsibilities of an Organization in Considering Cybersecurity?
- What Are Three Models for Sharing Cybersecurity Incident Information?
- What Are the Private Sector and Public Sector Cybersecurity Issues?
- How Do Policies, Laws, and Regulations Affect the Cybersecurity Field?
- How to Improving Password Cybersecurity Through Inexpensive and Minimally Invasive Means?
- What Kind Are International Cybersecurity Collaboration Initiatives and Multinational Cybersecurity?
- What Is the Most Important Cybersecurity Vulnerability Facing Managers in Computer Science?
- What Are New Concepts for Cybersecurity in Port Communication Networks?
- What Does Cyber Security Do?
- Is Cyber Security a Promising Career?
- What Are the Three Major Threats to Cyber Security Today?
- What Qualifications Do You Need for Cybersecurity?
- What Is a Cyber Security Example?
- What Are the Main Problems With Cyber Security?
- What Is the Biggest Threat to Cyber Security?
- What Are Cyber Security Tools?
- What Is the Risk in Cyber Security?
- What Is the Best Cyber Security?
- What Is Wireshark in Cyber Security?
- Which Are Fundamentals of Petroleum Energy & Mitigating Global Cybersecurity Attacks?
- Which International Cybersecurity Collaboration Initiatives and Multinational Cybersecurity?
- Which Vulnerability Assessments and Mitigating Global Cybersecurity Attacks on the Enterprise?
- Who Is the Founder of Cyber Security?
- What Are the Seven Types of Cyber Security?
- What Is the Most Significant Cybersecurity Company?
- Cryptocurrency Essay Ideas
- Identity Theft Essay Ideas
- Viruses Research Topics
- Cryptography Paper Topics
- Encryption Essay Titles
- Internet Privacy Essay Topics
- Digital Transformation Topics
- Software Engineering Topics
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2024, February 27). 237 Cyber Security Essay Topics, Ideas, and Examples. https://ivypanda.com/essays/topic/cybersecurity-essay-topics/
"237 Cyber Security Essay Topics, Ideas, and Examples." IvyPanda , 27 Feb. 2024, ivypanda.com/essays/topic/cybersecurity-essay-topics/.
IvyPanda . (2024) '237 Cyber Security Essay Topics, Ideas, and Examples'. 27 February.
IvyPanda . 2024. "237 Cyber Security Essay Topics, Ideas, and Examples." February 27, 2024. https://ivypanda.com/essays/topic/cybersecurity-essay-topics/.
1. IvyPanda . "237 Cyber Security Essay Topics, Ideas, and Examples." February 27, 2024. https://ivypanda.com/essays/topic/cybersecurity-essay-topics/.
Bibliography
IvyPanda . "237 Cyber Security Essay Topics, Ideas, and Examples." February 27, 2024. https://ivypanda.com/essays/topic/cybersecurity-essay-topics/.
Custom Essay, Term Paper & Research paper writing services
- testimonials
Toll Free: +1 (888) 354-4744
Email: [email protected]
Writing custom essays & research papers since 2008
154 exceptional cybersecurity research topics for you.

If you are studying computer science or IT-related course, you will encounter such a task. It is one of the most technical assignments, primarily in the era of advanced digital technologies. Students may not have the muscles to complete such papers on their own. That is why we provide expert help and ideas to make the process easier.
Do you want to excel in your cybersecurity paper? Here is your number one arsenal!
What You Need To Know About Cyber Security Research Topics
A cybersecurity paper deals with the practices of protecting servers, electronic systems, computers, and networks from malicious attacks. Although most students think this only applies to computers, it also applies to mobile computing and other business models.
There are various categories in cybersecurity, including:
Network security Application security Information security Operational security Disaster recovery and business continuity
Therefore, your cybersecurity topics for research should:
Examine the common security breaches in systems and networks Offer practical ways of protecting computers from such attacks Highlight the legal and ethical implications of hacking and other related practices Point out the challenges encountered in combating cybercrime
Since this is a technical paper, you should endeavor to do your research extensively to prevent rumors and unverified facts. The topics should also inform and educate people who are not conversant with cybersecurity in simple terms. Avoid using jargon at all costs, as this will make the paper difficult to read and understand.
Are you worried about where you can get professional cybersecurity topics and ideas? Well, here are a few of the most reliable sources that can furnish you with top-rated issues.
- Government legislation on cybersecurity (Acts of Parliament)
- The UN Office of Counter-Terrorism (Cybersecurity initiatives)
- The CISCO magazine
- Forbes also has excellent coverage on cybersecurity
You can find impressive topic ideas from these sources and more. Furthermore, news headlines and stories on cybersecurity can also help you gather many writing ideas. If all these prove futile, use our tip-top writing prompts below:

Quality Cyber Security Thesis Topics
- Impacts of coronavirus lockdowns on cybersecurity threats in the US
- Why ethical hacking is contributing to more harm than good
- The role of computer specialists in combating cyber threats before they occur
- Technological trends that are making it difficult to manage systems
- Are passwords reliable when protecting computer systems?
- Effects of having more than one systems administrator in a company
- Can the government shut down the dark web once and for all?
- Why should you bother about the security of your mobile device?
- Evaluate reasons why using public WIFI can be harmful to your security
- The role of cybersecurity seminars and conferences
- How universities can produce ethical computer hackers who can help the society
- How to counter-terrorism with advanced cybersecurity measures
- Impacts of teaching children how to use computers at a tender age
- Latest innovations that are a threat to cybersecurity
- The role of monitoring in combating frequent cyber attacks
- How social media is contributing to cyber attacks
- Discuss the relationship between cyberbullying and cybersecurity
- Why fingerprints may be the best method of protecting devices
- The role of YouTube in contributing to the rising number of hackers
Top Research Topics For Cyber Security For Master Thesis
- Impact of cyber threats on attaining the sustainable development goals
- Why websites are becoming easy to hack in the 21 st century
- Effects of not having an SSL certificate for a website
- Discuss the security threats associated with WordPress websites
- Impacts of frequent maintenance while the website is still running
- How computer colleges can contribute to a safe cyberspace
- Latest cyber threats to business and financial websites
- Discuss the implications of cyber threats on privacy
- The role of Facebook in advancing cyberbullying and hacking
- Is hacking becoming a global epidemic in the digital world?
- Why using Cyber Cafes may be detrimental to your digital security
- The role of systems analysts in responding to data breaches
- How cybersecurity movies are contributing to cyber threats
- Should hackers face lifetime jail imprisonment when found guilty?
- Loopholes in cyber laws that make the practice challenging to curtail
Good Thesis Topics For Cyber Security
- The relationship between privacy and data security in computing
- Why cloud computing offers a haven for computer hackers
- The role of character and human-based behavior in cybersecurity
- How to determine safe organizational security management and policy
- How the Internet of Things is promoting cyber attacks
- Effects of using cracked computer software
- Are biometrics in cybersecurity able to put off hackers?
- The role of studying mobile platform security
- Why companies should frequently monitor their firewalls
- The role of antimalware in curbing cyber attacks
- Why is Ransomware a headache to most companies handling big data?
- How does antivirus software improve the security of your computer?
- Compare and contrast between the security of UNIX and Ubuntu
- The role of data encryption technologies in ensuring system security
- Is the process of encrypting viruses safe?
Top-Grade Thesis Topics For Cyber Security
- Describe the effectiveness of cybersecurity audits on company systems
- Is it proper to conduct device synchronization?
- Why is it difficult to manage the security of an intranet?
- Discuss the effects of logging in to many devices at the same time
- Evaluate the significance of computer forensics
- How are hackers inventing new ways of breaching the systems of companies?
- Why it is necessary to review the data protection laws
- Practices that increase the vulnerability of a system to cyber attacks
- Can organizations implement impenetrable network systems?
- Why administrators should check the background of users before giving them rights and privileges
- The role of risk management cybersecurity
- Discuss the impact of reverse engineering on computing systems
- Effects of a cyber-attack on a company’s economic performance
- What legal frameworks work best for a computer company?
- The role of social engineering in cybersecurity
Information Security Research Topics
- The implication of the proliferation of the internet globally
- Innovative technologies used in keeping off hackers
- The role of information communication technologies in maintaining the security
- Are online courses on informative security practical?
- Why should people avoid sharing their details on Facebook?
- Effects of using your image on social media
- The role of pseudo names and nicknames on social media
- Discuss the implications of Wi-Fi hacking apps on mobile phones
- How to detect malicious activity on a system
- Evaluate the potential threats of conduct self-hacking on a system
- The impact of sharing personal details with hiring agencies
- How con artists lure unsuspecting applicants into giving out their details
- Effects of frequent maintenance on systems
- How to strengthen the firewall of an information system
- The role of the media in propagating security breaches to information systems
Latest Computer Security Research Topics
- Tricks that black hat hackers use to infiltrate company systems
- How children learn about cybersecurity from their parents
- The impact of watching hacking movies and TV series
- How various companies are protecting themselves from cyber attacks
- Why every company should have a systems security consultant
- Discuss the implication of digital piracy
- Threats that biometrics are bringing to digital systems
- How to block a network intrusion before it causes any effect
- Why MacOS is challenging to infiltrate, unlike Windows
- Results of two-step authentication security measures for login systems
- The role of updating computer systems during working days
- Evaluate times of the year when hackers infiltrate systems the most
- Why it isn’t easy to manage big data on the cloud
- What happens during a system breakdown and maintenance?
- Discuss the role of data synchronization in creating a backup
Network Security Research Paper Topics
- The impact of having self-configuring and decentralized network systems
- Effects of ad-hoc networks for large companies
- Discuss the role of wireless sensor networks in contributing to security breaches
- How malicious nodes join a network
- Why it is difficult to detect a passive network attack
- How active network attacks reduce a network’s performance
- Evaluate the various parameters used in network security
- Analyze how a black hole affects a network system
- Describe techniques used in detecting malicious nodes on networks
- How to improve the safety of a company network
- The role of data encryption in maintaining the security of a network
- Describe the various channels of establishing secure algorithms in a network
- How does RSA increase the safety of a particular network?
- Effective policies and procedures for maintaining network security
- The role of a unique ID and Password in securing a website
Computer Security Research Topics
- Why it is challenging to maintain endpoint security
- The role of a critical infrastructure cybersecurity
- How to create secure passwords for your computer network
- The part of scanning for malware often on your PC
- How to detect apps that invade your privacy unknowingly
- Why ordering software from the black market is a threat to security
- Safe computing techniques for first-time computer users
- The role of digital literacy in preventing hacking
- Why most online users fall to online scams
- The role of smartphones in enhancing cybersecurity threats
- Evaluate the mobile landscape concerning data security
- The implication of private email accounts in data breaches
- Sites that contain a barrel of internet criminals
- How to develop comprehensive internet security software
- How children can navigate the internet safely
Impressive Cyber Crime Research Topics
- Why cyber currencies are a threat to online security
- Why cyberbullying is rampant in the 21 st century unlike in any other time
- The impact of online persuasion campaigns on cybersecurity
- Why teenagers are victims of cyberbullying than adults
- Discuss the effects of technology evolution on cybercrime
- How online hackers collect information without the knowledge of the victim
- Traits of a robust cybersecurity system
- Practices that can help reduce cybercrime in institutions of higher learning.
- Effects of global coordinated cyber attacks
- The penalties of cyber-attack in the First Amendment
- Why the world is experiencing increased cyber attacks
- Critical concepts of cyber attacks
- Cybercriminals and enterprises
- Role of NGOs in combating cyber terrorism
- Cyberbullying in campus
World-Class Cyber Security Thesis Ideas
- Effects of the cyber-attack on Sony in 2014
- The role of globalization in enhancing cybersecurity
- How to prevent automotive software from malicious cyber attacks
- The role of cyber technology in changing the world since the 1990s
- How the private sector is essential in combating cyber threats
- Computer infrastructure protection against cyber attacks
- Impact of social networking sites on cybersecurity
- Threats that cyber-attacks pose the national security of a country
- How cyber monitoring affects ethical and legal considerations
- Factors leading to the global nature of cyber attacks
- Analyze law enforcement agencies that deal with cyber attacks
- Evaluate cyber-crime court cases
- Evolution of the cybersecurity industry
- Cyber terrorism in the US
- Implementing adequate data protection strategies
We offer paper writing help on any cybersecurity topic. Try us now!

Top 111+ Stunning Cybersecurity Research Topics For 2023

Are you confused about cybersecurity and its research topics? So here, in this blog, we will discuss cybersecurity research topics. This article is important If you are studying computer science or a cybersecurity course.
If you want good grades in cybersecurity research topics, you should pick the latest cybersecurity research topics for your academic exam or test. Here, you can choose the good and latest cybersecurity research topics.
You know that cybercrime is increasing day by day because millions of people use the internet. Several applications deal with the internet, and people normally use the internet for bank transactions, food delivery, online shopping, social media, gaming, etc. Attackers can steal your information, data, and money with the help of malicious software, So we need cybersecurity services.
What is Cybersecurity?
Table of Contents
Cybersecurity is a process of preventing unauthorized access or protecting networks, devices, and data from digital attacks. Cybersecurity is also known as IT(Information Technology)Security which is designed to prevent threats against network systems, applications, and other platforms. In simple words, It prevents or protects any information, data, and others.
Here Are Some of the Best Writing Tips From Statanalytica’s Expert
As you might already know that a well-planned action and a set of useful tools will also help you write a high-quality research paper. On the other hand, remaining motivated throughout the process.
- By choosing an interesting topic for your research paper.
- Conduct some research to find reputable sources.
- Clearly state your cybersecurity thesis.
- A rough plan should be created.
- Finish your paper by drafting it.
- Make sure your content is properly formatted.
- Make sure you understand the assignment before you begin writing your research paper.
Let’s Discuss the 111+ Stunning Cybersecurity Research Topics
Below we listed 111+ cybersecurity research topics that can be used in 2023:
Top 10 Cyber Security Topics of 2023
Here are the top 10 cyber security topics of 2023:
- Can strong passwords protect information?
- Is security in critical infrastructure important?
- The importance of end-user education
- Cloud security posture management
- How does malware work?
- The principle of zero trust access
- 3 phases of application security
- Should removable media be encrypted?
- The importance of network security
- Do biometrics ensure the security of iPhones?
Latest Cybersecurity Research Topics of 2023
- Is removable media a threat?
- Cybersecurity standards for automotive
- How to prevent social engineering attacks
- Security breaches of remote working
- How to prevent phishing attacks
- Physical security measures in banks
- Privacy settings of social media accounts
- Blockchain security vulnerabilities
- Why should you avoid public Wi-Fi?
- How does two-factor authentication work?
- Cryptography
- Discuss the importance of intranet security
- Rise of Automotive Hacking
- What is ethical hacking?
- The evolution of phishing and how it is becoming more sophisticated
- Which antivirus software is the best in the world?
- The most up-to-date and trending cybersecurity technology
- How can organizations prevent network attacks?
- What is Digital Piracy?
- Application of biometrics in cyber security?
- Identity theft on the Internet
- Risk management in computing
- Rise of computer forensics
- Threats are analyzed using digital forensic techniques
- What is a Remote Access VPN?
- Digital security and Social Networks
- The risks of using public Wi-Fi networks
- Popular online scams in 2022
- Artificial intelligence security systems
Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
Topics for Application Security Research
- Discuss SQL injection attacks.
- Inadequately configured security protocols.
- Talk about data leaks in mobile apps.
- Backend access control is critical.
- Logging has many advantages for applications.
- Malicious apps are available on Google Play.
- AI applications: ethical constraints and opportunities.
- What is the effect of insecure deserialization?
- The most effective application security testing practices.
- Apps are vulnerable to XSS attacks.
Information Technology Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2022
- Discuss digital piracy in 2022
- critical cyber-attack concepts
- Social engineering and its importance
Operational Security Research Topics In 2023
- Securing containerized applications in cloud environments.
- Implementing secure remote access policies for remote workers.
- Evaluating the effectiveness of endpoint protection solutions.
- Protecting against DNS tunneling attacks.
- Securing cloud-based storage solutions.
- Developing secure mobile device management policies.
- Analyzing the effectiveness of honeypots in detecting attacks.
- Securing software supply chains against attacks.
- Investigating the effectiveness of deception technologies in cybersecurity.
- Developing secure network segmentation strategies.
- Evaluating the effectiveness of network traffic analysis solutions.
- Analyzing the effectiveness of two-factor authentication in securing systems.
- Securing critical infrastructure against cyber threats.
- Developing secure email policies to prevent phishing attacks.
- Investigating the use of artificial intelligence in cybersecurity.
- Developing secure DevOps practices.
- Analyzing the effectiveness of security information and event management (SIEM) solutions.
- Securing the Internet of Things (IoT) devices.
- Evaluating the effectiveness of password management solutions.
- Developing secure incident response strategies.
Topics for a Research Paper on CyberCrime Prevention
- Criminal Specialization.
- Drug Courts.
- Capital Punishment.
- Criminal Courts.
- Crime Prevention.
- Community Corrections.
- Criminal Law.
- Criminal Justice Ethics.
Computer and Software Security Research Topics
- Learn algorithms for data encryption.
- Concept of risk management security.
- How to develop the best internet security software.
- What are Encrypting viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC.
- Infiltrating a Mac OS X operating system.
- What are the effects of RSA on network security?
- How do encrypting viruses work?
- DDoS attacks on IoT devices.
Computer and Software Cyber Security Topics
- The importance of updating computer software.
- How to safeguard your computer against malware and other threats.
- The best security practices for your computer and software.
- The various types of cyber security threats and how to avoid them.
- The significance of cyber security education and awareness.
- The importance of cyber security in protecting critical infrastructure.
Data Security Research Topics
- Importance of backup and recovery.
- Benefits of logging for applications.
- Understand physical data security.
- Importance of Cloud Security.
- In computing, the relationship between privacy and data security.
- Discuss the effects of a black hole on a network system.
Application Security Topics
- Detect Malicious Activity on Google Play Apps.
- Dangers of XSS attacks on apps.
- Insecure Deserialization Effect.
- Check Security protocols.
CyberSecurity Law Research Paper Topics
- Strict cybersecurity laws in China.
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries cybersecurity laws.
- Discuss The Pipeline Security Act in the United States.
If you are interested in criminal research topics, then here are the best criminal justice research topics for you.
How to Choose The Best Cybersecurity Research Topics in 2023
There are a few factors to consider when selecting cybersecurity research topics. The first and main thing to consider is to ensure that the topic is current and relevant. Because cyber security is a changing field. As a result, it is very crucial to select a topic that will be relevant for a few months.
On the other hand, the second thing to consider is to select an interesting and engaging topic. Because cyber security can be a dry subject, it is critical to select a topic that will keep readers interested.
Finally, it is very important to select a researchable topic. There are several cybersecurity topics available, but not all of them are simple to research. Choose a topic about which there is a lot of information.
- Determine your target audience
- Define your research objectives
- Choose a topic that your audience will find both interesting and relevant
- Conduct preliminary research to ensure that there is sufficient information available on your chosen topic
- Make sure your topic is focused enough to fit into a single research paper
Research Area in Cyber Security
Cybersecurity is extensive, and constantly evolving field. On the other hand, its research takes place in many areas:

- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
Get More Cybersecurity Research Topics
In this blog, we have covered the 111+ best cybersecurity research topics. These cybersecurity topics help in your exam or test. If you have any difficulty with cybersecurity research topics, you can take cybersecurity research paper help or research paper assignment help at a very affordable price.
Here are some of the benefits of taking cybersecurity research topics help from us.
- 24 Hours Availability
- On-time Delivery
- Free Corrections
- Money-Back Guarantee
- Affordable Deals
- Professional Experts
You can contact us any time and impress your teacher by choosing a good cybersecurity research topic.
This is the end of the post, which is about cybersecurity research topics. On the other hand, we mentioned 111+ stunning cybersecurity research topics for 2023 offer an excellent opportunity for researchers to explore and address critical cybersecurity challenges. However, the ever-evolving technological landscape presents new security challenges every day, and it is essential to keep up with the latest trends to stay ahead of cyber threats.
On the other hand, these research topics provide many areas to explore, from network security, the internet of things, and software security to network security, cryptography, and data security. I hope you like this post.
Q1. What are the types of cyber security threats?
There are several different types of cyber security threats. More popular are Trojan horses, worms, ransomware, and phishing scams. These types of threats can be very dangerous for the cyber system.
Q2. What are the most controversial topics in criminal justice?
1. Prisoners being granted the right to work 2. Carrying a concealed weapon 3. Prison rape and violence 4. Plea agreement/bargain 5. Rehab vs. reform. 6. Is an eyewitness testimony effective? 7. Enforcement and effectiveness of stalking laws. 8. Rape culture and the victim’s rights
Q3. What are the main cyber threats of 2023?
There are multiple cyber security threats, but the main social threats of 2023 are email impersonation and phishing. On the other hand, email impersonation is a phishing technique in which a fake email address that appears to be legitimate is used.
Related Posts

Step by Step Guide on The Best Way to Finance Car

The Best Way on How to Get Fund For Business to Grow it Efficiently
Burp Scanner
Burp Suite's web vulnerability scanner

Product comparison
What's the difference between Pro and Enterprise Edition?

Download the latest version of Burp Suite.

How I choose a security research topic

James Kettle
Director of Research
Published: 14 June 2023 at 13:09 UTC
Updated: 14 June 2023 at 13:16 UTC

How do you choose what topic to research? That’s the single most common question I get asked, probably because selecting a topic is such a daunting prospect. In this post, I’ll take a personal look at how I select topics for security research. As a case study, I’ll use my latest research, which will be presented at Black Hat USA and DEF CON this August:
Smashing the State Machine: the True Potential of Web Race Conditions
The hardest part
Before we start, I should mention that I firmly believe that choosing a topic is not the hardest part of web security research.
I’ve spoken to so many people who have cool ideas but never attempt to execute them. On the rare occasion that someone does mention a research idea that I think is doomed from the outset, it’s clear that attempting it will still provide them with a major learning experience - hardly a terrible outcome.
In fact, I don’t think that coming up with research ideas is the hard part either. Once you start researching, you’ll likely find every topic you explore leaves you with ideas for three more projects.
I think the hardest part of research is knowing when to bail, and when to push on.
Fast failure
My primary criteria when I evaluate a topic is how much time I’ll need to invest before I have enough information to decide whether to abandon it or continue. Knowing when to abandon a topic and when to push on is an extremely valuable skill for research, and it’s worth putting thought into this before starting.
This year, the attack-concept I wanted to explore initially looked like it required a major up-front time investment. However, I identified a short-cut - if I could build a test website that was vulnerable and reasonably realistic, that would prove the concept was pursuing. I built the website, quickly discovered that the attack concept was extremely unrealistic, and quickly pivoted to a different concept.
The second concept showed just enough promise to make me waste six weeks on it before it flopped too. When looking for a third concept, race conditions was an attractive topic because I already had powerful tooling from the prior project. This meant it would only take about a day to adapt the tooling, and a week or two of manual testing to see if I could discover something significant in the wild. I found a novel high-impact vulnerability in under a week, which cemented my commitment to the topic.
The fear factor
I like to research topics I’m scared of. Fear is a great indicator of something I don’t fully understand, and challenges that I don’t know how to tackle. Race conditions provided this in buckets, and I place this up-front and center in my abstract:
For too long, web race-condition attacks have focused on a tiny handful of scenarios. Their true potential has been masked thanks to tricky workflows, missing tooling, and simple network jitter hiding all but the most trivial, obvious examples. In this session, I’ll introduce multiple new classes of race condition that go far beyond the limit-overrun exploits you’re probably already familiar with... [read full abstract]
Direct impact vs audience impact
As a security professional, it’s tempting to rate a research project’s impact based on the direct impact. For example, over the years I’ve seen a range of serious flaws in a certain popular CDN, and I suspect that if I directly targeted it, I could find multiple ways to take over all their customers’ websites - a reasonable chunk of the web. In terms of direct impact, this would be pretty good.
But when you submit to Black Hat, they ask you to specify ‘three actionable take-aways’ for the audience. How would my hypothetical CDN-popping talk answer this? The only action required would be from that sole CDN vendor - in effect I’d just be giving a war-story talk. These can be entertaining and inspiring, but that’s not what I’m aiming for.
I try to pick a topic where the audience will take away novel attack techniques, and any tools or methodology required to make them practical to apply.
Applicable audience
Over the last five years, my research has been focused on HTTP Request Smuggling and Web Cache Poisoning . Since I’m well-versed in this topic, doing further research directly on top has become relatively easy, and I’m perpetually aware of multiple promising ideas.
However, while creating the presentation for last year’s Browser-Powered Desync Attacks , I became acutely aware that it demanded an exceptional amount of prior technical knowledge from the audience.
Building on a little recent research often works well because you can summarise it yourself. However, building on a large volume of recent research means that anyone in the audience who isn’t already familiar is going to struggle, and overall less people will get the benefit.
This year, by focusing on race conditions - a topic with minimal recent developments - I’ve been able to start building on a foundation that most attendees will be familiar with. Relative to last year’s talk, you can expect this talk to have both greater potential for the experts, and greater accessibility for the masses.
Existing skill-sets vs personal development
There’s a second, more personal reason why I changed my research focus away from request smuggling. I expect request smuggling to keep yielding good research for years to come, but just like any topic, at some point it’ll dry up. If I maintain my exclusive focus on this topic, there’s a risk I’ll become over-specialised and end up in a bad place when the topic stops yielding fruit.
I deliberately choose race conditions to avoid this over-specialisation risk, even though I regarded it as a much riskier bet than doing even more request smuggling exploration. Personal development is a huge and easily overlooked part of research. I rarely repeat my presentations across months for the same reason - if you spend your time sharing the same presentation over and over, you’re sacrificing novel research time.
That said, there’s a balance to be had here - if you have specialist knowledge, that will give you an edge on certain topics. Race conditions appealed from the start because I’d observed low-level HTTP quirks that could enhance these attacks, and I’d also observed them in the wild when trying to exploit response queue poisoning.
No topic is perfect; this presentation has fewer case studies than usual for me because fully automated detection of these vulnerabilities is not practical. On the plus side, this leaves a large number of vulnerabilities on the table that the audience can find simply by applying the methodology.
Ultimately, I see over-thinking topic choice as a pitfall. Save your energy for the research itself - you’ll need it! If you found this useful, you might also like So you want to be a web security researcher , and the presentation Hunting Evasive Vulnerabilities .
If you’re got any thoughts or queries, feel free to ping me on Twitter or LinkedIn . Hopefully I’ll see some of you in-person at the presentation too!
Back to all articles
Related Research
Refining your http perspective, with bambdas, introducing signsaboteur: forge signed web tokens with ease, making desync attacks easy with trace, using form hijacking to bypass csp.
This is a potential security issue, you are being redirected to https://csrc.nist.gov .
You have JavaScript disabled. This site requires JavaScript to be enabled for complete site functionality.
An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock Locked padlock icon ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
- Drafts for Public Comment
- All Public Drafts
- NIST Special Publications (SPs)
- NIST interagency/internal reports (NISTIRs)
- ITL Bulletins
- White Papers
- Journal Articles
- Conference Papers
- Security & Privacy
Applications
Technologies.
- Laws & Regulations
- Activities & Products
- News & Updates
- Cryptographic Technology
- Secure Systems and Applications
- Security Components and Mechanisms
- Security Engineering and Risk Management
- Security Testing, Validation, and Measurement
- Cybersecurity and Privacy Applications
- National Cybersecurity Center of Excellence (NCCoE)
- National Initiative for Cybersecurity Education (NICE)
Security and Privacy
- digital signatures
- key management
- lightweight cryptography
- message authentication
- post-quantum cryptography
- random number generation
- secure hashing
- cybersecurity supply chain risk management
- general security & privacy
- access authorization
- access control
- Personal Identity Verification
- public key infrastructure
- personally identifiable information
- privacy engineering
- categorization
- continuous monitoring
- controls assessment
- privacy controls
- security controls
- risk assessment
- roots of trust
- system authorization
- advanced persistent threats
- information sharing
- intrusion detection & prevention
- vulnerability management
- accessibility
- testing & validation
- acquisition
- asset management
- audit & accountability
- awareness training & education
- configuration management
- contingency planning
- incident response
- maintenance
- media protection
- patch management
- personnel security
- physical & environmental protection
- program management
- security automation
- reliability
- artificial intelligence
- cloud & virtualization
- combinatorial testing
- personal computers
- quantum information science
- smart cards
- operating systems
- communications & wireless
- cyber-physical systems
- cybersecurity education
- cybersecurity framework
- cybersecurity workforce
- industrial control systems
- Internet of Things
- mathematics
- positioning navigation & timing
- small & medium business
Laws and Regulations
- Comprehensive National Cybersecurity Initiative
- Cybersecurity Strategy and Implementation Plan
- Cyberspace Policy Review
- Executive Order 13636
- Executive Order 13702
- Executive Order 13718
- Executive Order 13800
- Executive Order 13905
- Executive Order 14028
- Executive Order 14110
- Federal Cybersecurity Research and Development Strategic Plan
- Homeland Security Presidential Directive 7
- Homeland Security Presidential Directive 12
- OMB Circular A-11
- OMB Circular A-130
- Cyber Security R&D Act
- Cybersecurity Enhancement Act
- E-Government Act
- Energy Independence and Security Act
- Federal Information Security Modernization Act
- First Responder Network Authority
- Health Insurance Portability and Accountability Act
- Help America Vote Act
- Internet of Things Cybersecurity Improvement Act
- Federal Acquisition Regulation
Activities and Products
- annual reports
- conferences & workshops
- quick start guides
- reference materials
- standards development
- financial services
- hospitality
- manufacturing
- public safety
- telecommunications
- transportation
- Write my thesis
- Thesis writers
- Buy thesis papers
- Bachelor thesis
- Master's thesis
- Thesis editing services
- Thesis proofreading services
- Buy a thesis online
- Write my dissertation
- Dissertation proposal help
- Pay for dissertation
- Custom dissertation
- Dissertation help online
- Buy dissertation online
- Cheap dissertation
- Dissertation editing services
- Write my research paper
- Buy research paper online
- Pay for research paper
- Research paper help
- Order research paper
- Custom research paper
- Cheap research paper
- Research papers for sale
- Thesis subjects
- How It Works
50 Great Cybersecurity Research Paper Topics

Students are required to write papers and essays on cyber security topics when pursuing programs in cyber security disciplines. These topics are technical and they require learners to inherently understand this subject. What’s more, students should have impeccable research and writing skills.
Additionally, students should choose cyber security topics to write their papers and essays carefully. As a science field, cyber security is developing rapidly and constantly. As such, learners can always find interesting topics to write papers and essays about.
Pick Cyber Security Topics From Our List
Software and computer administration cyber security topics.
- Cyber Security Research Paper Topics on Data Protection
- Cyber Security Awareness Topics
Network Security Topic Ideas
- Current and Interesting Topics in Cyber Security
Nevertheless, selecting cybersecurity topics for research shouldn’t be a rushed process. That’s because the chosen topics will influence the experience of students while writing and the grades they will score. Therefore, learners should focus on choosing topics that they will be comfortable researching and writing about.
If you’re having a hard time choosing the topics to research and write about, here are categories of some of the best cybersecurity paper topics that you can consider. We also advise you to check out capstone project topics .
The cyber security of a company can be compromised in many ways when it comes to software and computer administration. As such, software and computer administration is a great sources of cybersecurity research paper topics. Here are some of the best topics in this category.
- Evaluation of the operation of antimalware in preventing cyber attacks
- How does virus encryption work
- Is countering malware difficult because of the fast evolution of technology?
- Why should companies train their staff on cyber security?
- Why should people worry about identity theft?
- How important are software updates when it comes to cyber security?
- What causes cyber crimes?
- What are the major threats to the cyber security of social media users?
- What are the most effective methods of preventing phishing?
- What is the major threat to cyber security today and why?
These topics address issues that affect anybody or any organization that uses a computer or any device to access the internet and exchange information. As such, most people, including teachers and professors, will be impressed by papers and essays written about them.
CyberSecurity Research Paper Topics on Data Protection
Individuals and companies send and receive a lot of data every day. As such, this category has some of the best cybersecurity topics for presentation. That’s because they address issues that affect many people and organizations. Here are some of the best information security topics to consider when writing papers and essays or preparing a presentation.
- The best security measures for protecting your data
- How third-party applications can be used to access and acquire data without permission
- How to prevent the loss of data from a computer
- Can biometrics be used to prevent unauthorized data access?
- Can you protect yourself from cyber crimes by keeping personal data private?
- What should you do in case of a data breach?
- How can you secure your data with a 2-steps authentication process?
- How can public Wi-Fi or the internet be used to steal personal data?
- What information can be accessed by unauthorized persons if they hack an account?
- Can software updates help in protecting personal data?
Every computer or internet user wants to be sure that their data is safe and protected. Papers and essays that are written on these topics address issues of data protection. As such, many people will find them worth reading.
CyberSecurity Awareness Research Paper Topics
The best cyber security topics for research papers do more than just address a single issue. They also inform the readers. Here are some of the best cyber security topics for research papers that also focus on creating awareness.
- What is reverse engineering?
- How efficient are RFID security systems?
- How does the dark web propagate organized cyber crimes?
- How can steganalysis be applied?
- Analyze the best authorization infrastructures today
- How important is computer forensics in the current digital era?
- What strategies have been proven effective in preventing cyber-attacks?
- Which forensic tools are the best when it comes to detecting cyber threats?
- Can changing the password regularly help in predicting a cyber attack?
- How can you tell that you’re at risk of online identity theft?
Many people are not aware of many things that affect their cyber security. These topics are relevant because they enhance the awareness of the internet and computer users.
Most organizations today have networked systems that enhance their operations. Unfortunately, criminals have learned to target those networked systems with their criminal activities. As such, students can address some of these issues with their cyber security thesis topics. Here are interesting topics that learners can research and write about in this category.
- Evaluation of the cyber security legal framework in the U.S
- Analysis of the most difficult aspect of the administration of cyber security
- How can the possibilities of multiple threats be managed effectively?
- How does data backup help when it comes to cyber security?
- How effective is two-factor authentication?
- How should a company respond to hacking in its system?
- Which are the best cyber security protection approaches for a multinational company?
- What are the pros and cons of unified user profiles?
- What are the most important components of effective data governance?
- What motivates individuals to commit cybercrimes?
These computer security topics can be used to write papers and essays for college or even commissioned by organizations and used for presentation purposes.
Current and Interesting Topics in CyberSecurity
Some computer security research topics seek to address issues that affect society at the moment. Here are examples of such topics.
- How phishing is evolving and getting more sophisticated
- Explain the evolution of Ransomware strategies
- Explain how the cryptocurrency movement affects cybersecurity
- Cyber-Physical Attacks: How do they work?
- What are state-sponsored attacks and how do they affect cyber security at a global level?
- Discuss cyber security risks when it comes to third-party vendor relationships
- How digital advertisements are being used to collect user characteristics
- How can a person sync all their devices while ensuring their protection
- Why it’s advisable to avoid downloading files from sites that are not trusted
- Why consumers should read the terms and conditions of software before they decide to install it
Such technology security topics are trendy because they address issues that affect most people in modern society. Nevertheless, students should conduct extensive research to draft solid papers and essays on these topics.
This cyber security topic list is not exhaustive. You can contact our thesis writers if you need more ideas or help. Students have many topics to consider depending on their academic programs, interests, and instructions provided by educators or professors. Nevertheless, students should focus on choosing topics that will enable them to come up with informative and comprehensive papers. Thus, every student should choose an information security topic for which they can find relevant and supporting data.
Leave a Reply Cancel reply
Fall 2012: 0x1A Great Papers in Computer Security (53135)
Course description.
Topics in Computer and Network Security
Stanford cs 356, fall 2023.
CS 356 is graduate course that covers foundational work and current topics in computer and network security. The course consists of reading and discussing published research papers, presenting recent security work, and completing an original research project.
Course Information
Discussion: Mon/Wed 3:00–4:20 PM. Gates B12 . This course is largely based on in-person discussion rather than lecture. Attendance and participation is expected.
Instructor: Zakir Durumeric Office Hours: M/W 4:30–5:00 PM, or by appointment.
Course Assistant: Kimberly Ruth . Office hours by appointment.
Prerequisites: CS 356 is open to all graduate students as well as advanced undergraduate students. While the course has no official prerequisites, it requires a mature understanding of software systems and networks. Students are expected to have taken CS 155: Computer and Network Security or equivalent.
Topics and Readings
The tentative schedule and required readings for the class are below:
9/27 Introduction
Against security nihilism.
Blog Post. 2016. Chris Palmer.
Mining Your Ps and Qs: Detection of Widespread Weak Keys...
SEC '12 . N. Heninger, Z. Durumeric, E. Wustrow, J.A. Halderman.
How to Read a Paper
10/2 web privacy and security, the web never forgets: persistent tracking mechanisms in the....
CCS '14 . Gunes Acar, Christian Eubank, Steven Englehardt, Marc Juarez, Arvind Narayanan, Claudia Diaz.
Imperfect Forward Secrecy: How Diffie-Hellman Fails in Practice
CCS '15 . D. Adrian, K. Bhargavan, Z. Durumeric, P. Gaudry, M. Green, J.A. Halderman, N. Heninger, A. Springall, E. Thomé, L. Valenta, B. VanderSloot, E. Wustrow, S. Zanella-Beguelin, P. Zimmermann.
10/4 Usability
Alice in warningland: a large-scale field study of browser security.
SEC '13 . Devdatta Akhawe, Adrienne Porter Felt.
...no one can hack my mind”: Comparing Expert and Non-Expert Security Practices
SOUPS '15 . Iulia Ion, Rob Reeder, Sunny Consolvo.
10/9 Authentication and Phishing
The tangled web of password reuse.
NDSS '14 . Anupam Das, Joseph Bonneau, Matthew Caesar, Nikita Borisov, XiaoFeng Wang.
Detecting credential spearphishing in enterprise settings
SEC '17 . Grant Ho, Aashish Sharma, Mobin Javed, Vern Paxson, David Wagner.
10/11 Denial of Service
Inferring internet denial-of-service activity.
SEC '01 . David Moore, Geoffrey Voelker, Stefan Savage.
Understanding the Mirai Botnet
10/16 spam and ecrime, framing dependencies introduced by underground commoditization.
WEIS '15 . Kurt Thomas, Danny Huang, David Wang, Elie Bursztein, Chris Grier, Thomas Holt, Christopher Kruegel, Damon McCoy, Stefan Savage, Giovanni Vigna.
Spamalytics: An Empirical Analysis of Spam Marketing Conversion
CCS '08 . Chris Kanich, Christian Kreibich, Kirill Levchenko, Brandon Enright, Geoffrey Voelker, Vern Paxson, and Stefan Savage.
10/18 Software Attacks
Hacking blind s&p '14 . andrea bittau, adam belay, ali mashtizadeh, david mazieres, dan boneh. sok: eternal war in memory.
S&P '13 . Laszlo Szekeres, Mathias Payer, Tao Wei, Dawn Song.
10/23 Software Defenses
Native client: a sandbox for portable, untrusted x86 native code.
S&P '09 . Bennet Yee, David Sehr, Gregory Dardyk, J. Bradley Chen, Robert Muth, Tavis Ormandy, Shiki Okasaka, Neha Narula, Nicholas Fullagar.
Multiprogramming a 64 kB Computer Safely and Efficiently
SOSP '17 . Amit Levy, Bradford Campbell, Branden Ghena, Daniel B. Giffin, Pat Pannuto, Prabal Dutta, Philip Levis.
10/25 Malware and Supply Chain
Towards measuring supply chain attacks on package managers for interpreted languages.
NDSS '21 . Ruian Duan, Omar Alrawi, Ranjita Pai Kasturi, Ryan Elder, Brendan Saltaformaggio, Wenke Lee.
Before We Knew It: An Empirical Study of Zero-Day Attacks In The Real World
CCS '12 Leyla Bilge and Tudor Dumitraş.
10/30 Side Channels and Information Leakage
Timing analysis of keystrokes and timing attacks on ssh.
SEC '01 . Dawn Song, David Wagner, Xuqing Tia.
Spectre Attacks: Exploiting Speculative Execution
S&P '19 . P. Kocher, J. Horn, A. Fogh, D. Genkin, D. Gruss, W. Haas, M. Hamburg, M. Lipp, S. Mangard, T. Prescher, M. Schwarz, Y. Yarom.
11/1 Hardware
Stealthy dopant-level hardware trojans.
CHES '13 . Georg Becker, Francesco Regazzoni, Christof Paar, Wayne Burleson.
Comprehensive Experimental Analyses of Automotive Attack Surfaces
SEC '11 . Stephen Checkoway, Damon McCoy, Brian Kantor, Danny Anderson, Hovav Shacham, Stefan Savage.
W32.Stuxnet Dossier
Symantec Technical Report . Nicolas Falliere, Liam Murchu, Eric Chien.
11/8 Machine Learning
Towards evaluating the robustness of neural networks.
S&P '16 . Nicholas Carlini and David Wagner.
Outside the Closed World: On Using Machine Learning For Network Intrusion Detection
S&P '10 . Robin Sommer and Vern Paxson.
11/13 Vulnerable Populations / Security For Everyone
A stalker’s paradise: how intimate partner abusers exploit technology.
CHI '18 Diana Freed, Jackeline Palmer, Diana Minchala, Karen Levy, Thomas Ristenpart, Nicola Dell.
A11y Attacks: Exploiting Accessibility in Operating Systems
CCS '14 Yeongjin Jang, Chengyu Song, Simon Chung, Tielei Wang, Wenke Lee.
11/15 Privacy and Dark Patterns
Robust de-anonymization of large sparse datasets.
S&P '08 . Arvind Narayanan and Vitaly Shmatikov.
Dark patterns at scale: Findings from a crawl of 11K shopping websites
S&P '08 . Arunesh Mathur, Gunes Acar, Michael Friedman, Eli Lucherini, Jonathon Mayer, Marshini Chetty, Arvind Narayanan.
11/20 Thanksgiving Break
11/22 thanksgiving break, 11/27 surveillance and anonymity, keys under doormats.
MIT Technical Report '15. H. Abelson, R. Anderson, S. Bellovin, J. Benaloh, M. Blaze, W. Diffie, J. Gilmore, M. Green, S. Landau, P. Neumann, R. Rivest, J. Schiller, B. Schneier, M. Specter, D. Weitzner.
Tor: The Second-Generation Onion Router
SEC '04 . Roger Dingledine, Nick Mathewson, Paul Syverson.
11/29 Government Attacks and Disinformation
When governments hack opponents: a look at actors and technology.
SEC '14 . Bill Marczak, John Scott-Railton, Morgan Marquis-Boire, Vern Paxson.
Disinformation as Collaborative Work: Surfacing the Participatory Nature of Strategic Information Operations
CSCW '19 . Kate Starbird, Ahmer Arif, Tom Wilson.
12/4 Ethics and Problem Selection
The moral character of cryptographic work.
Phillip Rogaway.
Science, Security, and the Elusive Goal of Security as a Scientific Pursuit
S&P '17 . Cormac Herley and P.C. van Oorschot.
12/6 Final Presentations
No required reading. attendance mandatory., course structure.
This course is composed of three parts: reading and discussing foundational papers in every class, reading and presenting recent work for one class, and completing a group research project. Grading will be based on:
Readings and Discussion (30%)
We will read and discuss 1–2 papers for each class. Typically, these are formative works in an area of security. Students should come prepared to actively discuss assigned papers and to make substantive intellectual contributions. This means that you need to thoroughly read each paper ahead of time. Before each section, students will submit a short (400 word) summary and reaction for each each paper, as well as a proposal of one discussion question for class.
Students should submit the reading assignments through Gradescope by 2:30 pm on the day of each class . Paper responses should be completed individually without the assistance of LLMs (e.g., ChatGPT).
Grading will be based 20% on these written responses and 10% on in-class participation. We do not allow any late days for paper reactions, but students may skip two paper summaries and two lectures without penalty. We will take class attendance. However, participation grades are based on not only attendence, but active participation during class discussion.
Do not underestimate the amount of time required to properly read and process a research paper. Expect to spend several hours preparing for each section.
Topic Presentation (15%)
While reading formative papers helps to demonstrate how a subfield started, it oftentimes leaves us wondering how the area has evolved. To fill this gap, each student in the class will present one recent paper during the quarter topically relevant to that day's class. At the start of the quarter, students will have the opportunity to sign up for the topic/date that they want to present their paper. Stuents will have 12-15 minutes to present their paper.
Students are expected to do a literature search and to select a paper that was published in the last three years from a top-tier venue in security (e.g., IEEE Security and Privacy, USENIX Security, ACM Computer or Communication Security) or adjacent field (e.g., CHI, NSDI, ASPLOS, PLDI, etc.). Students should submit their papers to approval to the teaching staff a week prior to their presentation.
Course Project (55%)
Students will complete a quarter-long original research project in small groups (1–3 students) on a topic of their own choosing. Groups will present their work during the last two sections as well as submit a 6–10 page report, similar to the papers we read in the course.
- Project Proposal (5%). Project groups will meet with course staff to discuss their project during the third week of class and submit a one page project proposal. Written proposals are due on 10/16.
- Mid-Quarter Progress Report (5%). Submit a short (1–2 pages) progress report part way through the quarter. The report should indicate what has been accomplished, what work is remaining, obstacles the team has encountered, and any preliminary data or insights. Due 11/17.
- Class Presentation (10%). Each group will give a 10 minute class presentation during the last week of the course.
- Final Paper (35%). Groups will submit a final project report similar to the papers we read in the course. Papers should be 6–10 pages and use the USENIX LaTeX template . It may be helpful to read Writing Technical Articles if you haven't previously published any work in computer science. Due 12/8.
Students should submit all reports through Gradescope by 11:59PM on the day of each deadline.
In past offerings, well-executed projects have led to publications at top-tier security conferences and workshops. I'm happy to work with groups to publish their work.
This class has no final exam. Attendance on 12/6 is required.
network security Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
A Survey on Ransomware Malware and Ransomware Detection Techniques
Abstract: is a kind of malignant programming (malware) that takes steps to distribute or hinders admittance to information or a PC framework, for the most part by scrambling it, until the casualty pays a payoff expense to the assailant. As a rule, the payoff request accompanies a cutoff time. Assuming that the casualty doesn't pay on schedule, the information is gone perpetually or the payoff increments. Presently days and assailants executed new strategies for effective working of assault. In this paper, we center around ransomware network assaults and study of discovery procedures for deliver product assault. There are different recognition methods or approaches are accessible for identification of payment product assault. Keywords: Network Security, Malware, Ransomware, Ransomware Detection Techniques
Analysis and Evaluation of Wireless Network Security with the Penetration Testing Execution Standard (PTES)
The use of computer networks in an agency aims to facilitate communication and data transfer between devices. The network that can be applied can be using wireless media or LAN cable. At SMP XYZ, most of the computers still use wireless networks. Based on the findings in the field, it was found that there was no user management problem. Therefore, an analysis and audit of the network security system is needed to ensure that the network security system at SMP XYZ is safe and running well. In conducting this analysis, a tool is needed which will be used as a benchmark to determine the security of the wireless network. The tools used are Penetration Testing Execution Standard (PTES) which is one of the tools to become a standard in analyzing or auditing network security systems in a company in this case, namely analyzing and auditing wireless network security systems. After conducting an analysis based on these tools, there are still many security holes in the XYZ wireless SMP that allow outsiders to illegally access and obtain vulnerabilities in terms of WPA2 cracking, DoS, wireless router password cracking, and access point isolation so that it can be said that network security at SMP XYZ is still not safe
A Sensing Method of Network Security Situation Based on Markov Game Model
The sensing of network security situation (NSS) has become a hot issue. This paper first describes the basic principle of Markov model and then the necessary and sufficient conditions for the application of Markov game model. And finally, taking fuzzy comprehensive evaluation model as the theoretical basis, this paper analyzes the application fields of the sensing method of NSS with Markov game model from the aspects of network randomness, non-cooperative and dynamic evolution. Evaluation results show that the sensing method of NSS with Markov game model is best for financial field, followed by educational field. In addition, the model can also be used in the applicability evaluation of the sensing methods of different industries’ network security situation. Certainly, in different categories, and under the premise of different sensing methods of network security situation, the proportions of various influencing factors are different, and once the proportion is unreasonable, it will cause false calculation process and thus affect the results.
The Compound Prediction Analysis of Information Network Security Situation based on Support Vector Combined with BP Neural Network Learning Algorithm
In order to solve the problem of low security of data in network transmission and inaccurate prediction of future security situation, an improved neural network learning algorithm is proposed in this paper. The algorithm makes up for the shortcomings of the standard neural network learning algorithm, eliminates the redundant data by vector support, and realizes the effective clustering of information data. In addition, the improved neural network learning algorithm uses the order of data to optimize the "end" data in the standard neural network learning algorithm, so as to improve the accuracy and computational efficiency of network security situation prediction.MATLAB simulation results show that the data processing capacity of support vector combined BP neural network is consistent with the actual security situation data requirements, the consistency can reach 98%. the consistency of the security situation results can reach 99%, the composite prediction time of the whole security situation is less than 25s, the line segment slope change can reach 2.3% ,and the slope change range can reach 1.2%,, which is better than BP neural network algorithm.
Network intrusion detection using oversampling technique and machine learning algorithms
The expeditious growth of the World Wide Web and the rampant flow of network traffic have resulted in a continuous increase of network security threats. Cyber attackers seek to exploit vulnerabilities in network architecture to steal valuable information or disrupt computer resources. Network Intrusion Detection System (NIDS) is used to effectively detect various attacks, thus providing timely protection to network resources from these attacks. To implement NIDS, a stream of supervised and unsupervised machine learning approaches is applied to detect irregularities in network traffic and to address network security issues. Such NIDSs are trained using various datasets that include attack traces. However, due to the advancement in modern-day attacks, these systems are unable to detect the emerging threats. Therefore, NIDS needs to be trained and developed with a modern comprehensive dataset which contains contemporary common and attack activities. This paper presents a framework in which different machine learning classification schemes are employed to detect various types of network attack categories. Five machine learning algorithms: Random Forest, Decision Tree, Logistic Regression, K-Nearest Neighbors and Artificial Neural Networks, are used for attack detection. This study uses a dataset published by the University of New South Wales (UNSW-NB15), a relatively new dataset that contains a large amount of network traffic data with nine categories of network attacks. The results show that the classification models achieved the highest accuracy of 89.29% by applying the Random Forest algorithm. Further improvement in the accuracy of classification models is observed when Synthetic Minority Oversampling Technique (SMOTE) is applied to address the class imbalance problem. After applying the SMOTE, the Random Forest classifier showed an accuracy of 95.1% with 24 selected features from the Principal Component Analysis method.
Cyber Attacks Visualization and Prediction in Complex Multi-Stage Network
In network security, various protocols exist, but these cannot be said to be secure. Moreover, is not easy to train the end-users, and this process is time-consuming as well. It can be said this way, that it takes much time for an individual to become a good cybersecurity professional. Many hackers and illegal agents try to take advantage of the vulnerabilities through various incremental penetrations that can compromise the critical systems. The conventional tools available for this purpose are not enough to handle things as desired. Risks are always present, and with dynamically evolving networks, they are very likely to lead to serious incidents. This research work has proposed a model to visualize and predict cyber-attacks in complex, multilayered networks. The calculation will correspond to the cyber software vulnerabilities in the networks within the specific domain. All the available network security conditions and the possible places where an attacker can exploit the system are summarized.
Network Security Policy Automation
Network security policy automation enables enterprise security teams to keep pace with increasingly dynamic changes in on-premises and public/hybrid cloud environments. This chapter discusses the most common use cases for policy automation in the enterprise, and new automation methodologies to address them by taking the reader step-by-step through sample use cases. It also looks into how emerging automation solutions are using big data, artificial intelligence, and machine learning technologies to further accelerate network security policy automation and improve application and network security in the process.
Rule-Based Anomaly Detection Model with Stateful Correlation Enhancing Mobile Network Security
Research on network security technology of industrial control system.
The relationship between industrial control system and Internet is becoming closer and closer, and its network security has attracted much attention. Penetration testing is an active network intrusion detection technology, which plays an indispensable role in protecting the security of the system. This paper mainly introduces the principle of penetration testing, summarizes the current cutting-edge penetration testing technology, and looks forward to its development.
Detection and Prevention of Malicious Activities in Vulnerable Network Security Using Deep Learning
Export citation format, share document.
- SUGGESTED TOPICS
- The Magazine
- Newsletters
- Managing Yourself
- Managing Teams
- Work-life Balance
- The Big Idea
- Data & Visuals
- Reading Lists
- Case Selections
- HBR Learning
- Topic Feeds
- Account Settings
- Email Preferences
AI Will Increase the Quantity — and Quality — of Phishing Scams
- Fredrik Heiding,
- Bruce Schneier,
- Arun Vishwanath

How businesses can prepare now.
Gen AI tools are rapidly making these emails more advanced, harder to spot, and significantly more dangerous. Recent research showed that 60% of participants fell victim to artificial intelligence (AI)-automated phishing, which is comparable to the success rates of non-AI-phishing messages created by human experts. Companies need to: 1) understand the asymmetrical capabilities of AI-enhanced phishing, 2) determine the company or division’s phishing threat severity level, and 3) confirm their current phishing awareness routines.
Anyone who has worked at a major organization has likely had to do training on how to spot a phishing attack — the deceptive messages that pretend to be from legitimate sources and aim to trick users into giving away personal information or clicking on harmful links. Phishing emails often exploit sensitive timings and play on a sense of urgency, such as urging the user to update a password. But unfortunately for both companies and employees, gen AI tools are rapidly making these emails more advanced, harder to spot, and significantly more dangerous.
- FH Fredrik Heiding is a research fellow in computer science at Harvard John A. Paulson School of Engineering and Applied Sciences and a teaching fellow for the Generative AI for Business Leaders course at the Harvard Business School. He researches how to mitigate AI-enabled cyberattacks via technical innovations, organizational strategies, and national security policies. Fredrik also works with the World Economic Forum’s Cybercrime Center to improve cybersecurity standards of AI-based cyber defense.
- Bruce Schneier is an internationally renowned security technologist, called a “security guru’ by the Economist. He is the New York Times best-selling author of 14 books — including A Hacker’s Mind — as well as hundreds of articles, essays, and academic papers. His influential newsletter Crypto-Gram and blog Schneier on Security are read by over 250,000 people. Schneier is a fellow at the Berkman-Klein Center for Internet and Society at Harvard University, a Lecturer in Public Policy at the Harvard Kennedy School, a board member of the Electronic Frontier Foundation and AccessNow, and an advisory board member of EPIC and VerifiedVoting.org. He is the Chief of Security Architecture at Inrupt, Inc.
- AV Arun Vishwanath , PhD, MBA, is a distinguished scholar and practitioner at the forefront of addressing cybersecurity’s “people problem” who has contributed commentary Wired , CNN, and The Washington Post . A former fellow at Harvard University’s Berkman Klein Center, he is the founder of the Cyber Hygiene Academy and serves as a distinguished expert for the NSA’s Science of Security & Privacy directorate. He is the author of the book The Weakest Link , published by MIT Press.
Partner Center
Suggestions or feedback?
MIT News | Massachusetts Institute of Technology
- Machine learning
- Social justice
- Black holes
- Classes and programs
Departments
- Aeronautics and Astronautics
- Brain and Cognitive Sciences
- Architecture
- Political Science
- Mechanical Engineering
Centers, Labs, & Programs
- Abdul Latif Jameel Poverty Action Lab (J-PAL)
- Picower Institute for Learning and Memory
- Lincoln Laboratory
- School of Architecture + Planning
- School of Engineering
- School of Humanities, Arts, and Social Sciences
- Sloan School of Management
- School of Science
- MIT Schwarzman College of Computing
Modular, scalable hardware architecture for a quantum computer
Press contact :, media download.

*Terms of Use:
Images for download on the MIT News office website are made available to non-commercial entities, press and the general public under a Creative Commons Attribution Non-Commercial No Derivatives license . You may not alter the images provided, other than to crop them to size. A credit line must be used when reproducing images; if one is not provided below, credit the images to "MIT."
Previous image Next image
Quantum computers hold the promise of being able to quickly solve extremely complex problems that might take the world’s most powerful supercomputer decades to crack.
But achieving that performance involves building a system with millions of interconnected building blocks called qubits. Making and controlling so many qubits in a hardware architecture is an enormous challenge that scientists around the world are striving to meet.
Toward this goal, researchers at MIT and MITRE have demonstrated a scalable, modular hardware platform that integrates thousands of interconnected qubits onto a customized integrated circuit. This “quantum-system-on-chip” (QSoC) architecture enables the researchers to precisely tune and control a dense array of qubits. Multiple chips could be connected using optical networking to create a large-scale quantum communication network.
By tuning qubits across 11 frequency channels, this QSoC architecture allows for a new proposed protocol of “entanglement multiplexing” for large-scale quantum computing.
The team spent years perfecting an intricate process for manufacturing two-dimensional arrays of atom-sized qubit microchiplets and transferring thousands of them onto a carefully prepared complementary metal-oxide semiconductor (CMOS) chip. This transfer can be performed in a single step.
“We will need a large number of qubits, and great control over them, to really leverage the power of a quantum system and make it useful. We are proposing a brand new architecture and a fabrication technology that can support the scalability requirements of a hardware system for a quantum computer,” says Linsen Li, an electrical engineering and computer science (EECS) graduate student and lead author of a paper on this architecture.
Li’s co-authors include Ruonan Han, an associate professor in EECS, leader of the Terahertz Integrated Electronics Group, and member of the Research Laboratory of Electronics (RLE); senior author Dirk Englund, professor of EECS, principal investigator of the Quantum Photonics and Artificial Intelligence Group and of RLE; as well as others at MIT, Cornell University, the Delft Institute of Technology, the U.S. Army Research Laboratory, and the MITRE Corporation. The paper appears today in Nature .
Diamond microchiplets
While there are many types of qubits, the researchers chose to use diamond color centers because of their scalability advantages. They previously used such qubits to produce integrated quantum chips with photonic circuitry.
Qubits made from diamond color centers are “artificial atoms” that carry quantum information. Because diamond color centers are solid-state systems, the qubit manufacturing is compatible with modern semiconductor fabrication processes. They are also compact and have relatively long coherence times, which refers to the amount of time a qubit’s state remains stable, due to the clean environment provided by the diamond material.
In addition, diamond color centers have photonic interfaces which allows them to be remotely entangled, or connected, with other qubits that aren’t adjacent to them.
“The conventional assumption in the field is that the inhomogeneity of the diamond color center is a drawback compared to identical quantum memory like ions and neutral atoms. However, we turn this challenge into an advantage by embracing the diversity of the artificial atoms: Each atom has its own spectral frequency. This allows us to communicate with individual atoms by voltage tuning them into resonance with a laser, much like tuning the dial on a tiny radio,” says Englund.
This is especially difficult because the researchers must achieve this at a large scale to compensate for the qubit inhomogeneity in a large system.
To communicate across qubits, they need to have multiple such “quantum radios” dialed into the same channel. Achieving this condition becomes near-certain when scaling to thousands of qubits. To this end, the researchers surmounted that challenge by integrating a large array of diamond color center qubits onto a CMOS chip which provides the control dials. The chip can be incorporated with built-in digital logic that rapidly and automatically reconfigures the voltages, enabling the qubits to reach full connectivity.
“This compensates for the in-homogenous nature of the system. With the CMOS platform, we can quickly and dynamically tune all the qubit frequencies,” Li explains.
Lock-and-release fabrication
To build this QSoC, the researchers developed a fabrication process to transfer diamond color center “microchiplets” onto a CMOS backplane at a large scale.
They started by fabricating an array of diamond color center microchiplets from a solid block of diamond. They also designed and fabricated nanoscale optical antennas that enable more efficient collection of the photons emitted by these color center qubits in free space.
Then, they designed and mapped out the chip from the semiconductor foundry. Working in the MIT.nano cleanroom, they post-processed a CMOS chip to add microscale sockets that match up with the diamond microchiplet array.
They built an in-house transfer setup in the lab and applied a lock-and-release process to integrate the two layers by locking the diamond microchiplets into the sockets on the CMOS chip. Since the diamond microchiplets are weakly bonded to the diamond surface, when they release the bulk diamond horizontally, the microchiplets stay in the sockets.
“Because we can control the fabrication of both the diamond and the CMOS chip, we can make a complementary pattern. In this way, we can transfer thousands of diamond chiplets into their corresponding sockets all at the same time,” Li says.
The researchers demonstrated a 500-micron by 500-micron area transfer for an array with 1,024 diamond nanoantennas, but they could use larger diamond arrays and a larger CMOS chip to further scale up the system. In fact, they found that with more qubits, tuning the frequencies actually requires less voltage for this architecture.
“In this case, if you have more qubits, our architecture will work even better,” Li says.
The team tested many nanostructures before they determined the ideal microchiplet array for the lock-and-release process. However, making quantum microchiplets is no easy task, and the process took years to perfect.
“We have iterated and developed the recipe to fabricate these diamond nanostructures in MIT cleanroom, but it is a very complicated process. It took 19 steps of nanofabrication to get the diamond quantum microchiplets, and the steps were not straightforward,” he adds.
Alongside their QSoC, the researchers developed an approach to characterize the system and measure its performance on a large scale. To do this, they built a custom cryo-optical metrology setup.
Using this technique, they demonstrated an entire chip with over 4,000 qubits that could be tuned to the same frequency while maintaining their spin and optical properties. They also built a digital twin simulation that connects the experiment with digitized modeling, which helps them understand the root causes of the observed phenomenon and determine how to efficiently implement the architecture.
In the future, the researchers could boost the performance of their system by refining the materials they used to make qubits or developing more precise control processes. They could also apply this architecture to other solid-state quantum systems.
This work was supported by the MITRE Corporation Quantum Moonshot Program, the U.S. National Science Foundation, the U.S. Army Research Office, the Center for Quantum Networks, and the European Union’s Horizon 2020 Research and Innovation Program.
Share this news article on:
Related links.
- Quantum Photonics and AI Laboratory
- Terahertz Integrated Electronics Group
- Research Laboratory of Electronics
- Microsystems Technology Laboratories
- Department of Electrical Engineering and Computer Science
Related Topics
- Computer science and technology
- Quantum computing
- Electronics
- Semiconductors
- Electrical Engineering & Computer Science (eecs)
- National Science Foundation (NSF)
Related Articles

Scaling up the quantum chip
Quantum sensing on a chip

Toward mass-producible quantum computers
Previous item Next item
More MIT News

Nuh Gedik receives 2024 National Brown Investigator Award
Read full story →

Reducing carbon emissions from long-haul trucks
Mouth-based touchpad enables people living with paralysis to interact with computers

Advocating for science funding on Capitol Hill

Unique professional development course prepares students for future careers

New technique reveals how gene transcription is coordinated in cells
- More news on MIT News homepage →
Massachusetts Institute of Technology 77 Massachusetts Avenue, Cambridge, MA, USA
- Map (opens in new window)
- Events (opens in new window)
- People (opens in new window)
- Careers (opens in new window)
- Accessibility
- Social Media Hub
- MIT on Facebook
- MIT on YouTube
- MIT on Instagram
Daniel Gillen Recognized for Statistical Methods Research and Impact on Public Health
- Share on Facebook
- Share on Twitter
- Share on LinkedIn
- Share through Email
- Copy permalink

On April 18, 2024, Daniel Gillen was named a fellow of the American Association for the Advancement of Science ( AAAS ), the world’s largest general scientific society. Gillen, a Chancellor’s Professor and chair of Statistics in UC Irvine’s Donald Bren School of Information and Computer Sciences ( ICS ), was recognized for distinguished contributions to statistical methods. Specifically, he was honored for research on survival and longitudinal data analysis methods, and clinical trials methodology and implementation, as well as for impactful collaborative work in drug development, regulatory policy and epidemiology.
“My research is divided into two parts: the development of new statistical theory and methodologies to better address scientific problems, and the application of those methods to public health-focused research,” says Gillen. He explains that much of his group’s work lately has been devoted to biomarker discovery for Alzheimer’s disease (AD) and increasing diversity in AD clinical trials to better address health disparities in the field.
“When we evaluate new disease therapies, we are generally evaluating them on primarily non-Hispanic white populations that are pretty well educated and well off,” says Gillen. “We don’t necessarily know if new therapies work equally well across all groups.” His approach to addressing this shortfall is two-fold, as he works to diversify both clinical trial recruitment and biomarker development.
Diversifying Recruitment & Biomarker Development Gillen is a principal investigator on a $3.7M National Institutes of Health grant awarded to UCI that aims to diversify study cohorts by increasing recruitment in disadvantaged neighborhoods. “Our research design over-samples people in neighborhoods with high health disparity indices and will ultimately determine what strategies work when inviting them into research,” says Gillen. Using randomized trials, they are testing strategies such as using Facebook ads or postcards, in combination with different languages, to determine what works best in recruiting more diverse populations to participate in clinical trials run by UCI.
“My job is to design those studies to allow for increased statistical efficiency to better quantify differences in the effect of a given intervention across low and high disparity populations,” says Gillen. But it doesn’t stop there. They are also developing new statistical methodology to validly estimate the effect of a given intervention and ensure the generalizability of their results. “In this context we are developing novel methods for something called ‘interrupted time series,’ where we seek to infer points of inflection in recruitment outcomes — what’s working and what’s not over time — as we implement new intervention strategies.”
When it comes to more inclusive biomarker development, Gillen is researching alternative sampling designs, especially related to interventions for AD. Candidate AD biomarkers often require burdensome and costly measurements based on either cerebral spinal fluid or PET scan results. “As you can imagine, participants aren’t necessarily eager to get cerebral spinal fluid taken,” says Gillen. “You want to use those resources as efficiently as possible, so we oversample people who have progressed to dementia as well as those from underrepresented groups. By statistically accounting for this intentionally biased sampling, our group is able to validly estimate biomarker effects for the overall population, while ensuring that we maximize all possible information on groups historically underrepresented in research.” They achieve this through something called “inverse probability of sampling weights.” As Gillen explains, “my research involves ways to incorporate these weights and to develop the asymptotic theory of our estimators to ensure that we are making valid probabilistic statements regarding the role of biomarkers.”
Ensuring Safety and Ethics Gillen has also served as an advisor to the U.S. Food & Drug Administration ( FDA ) for approximately 20 years. In this role, he advises the FDA on controversial clinical trial results as interventions are being reviewed for potential approval. His statistics and probability research guides his advice to the FDA as they try to weigh the “risk:benefit” profile of new therapies in the face of uncertainty.
In addition, Gillen works with a multitude of pharmaceutical companies on the appropriate design and monitoring of internationally run clinical trials. He has served on over 80 independent data monitoring committees (IDMCs) for industry-sponsored multicenter clinical trials in disease areas ranging from Pompe disease to breast cancer to cardiovascular disease. As an IDMC member, he serves as an independent reviewer of incoming trial data to protect the safety and ethics of patients participating in the study.
“My role as an academic statistician is crucial to the goals of an IDMC. My expertise in statistics and probability provides me with a unique ability to not only efficiently design trials but also to monitor them for safety and efficacy in order to determine if there is a need for interim trial modifications or early stoppage,” says Gillen. “As clinical trial data accrues during the course of a study, our estimates of safety and efficacy are typically highly variable, so my role as a statistician is of utmost importance when interpreting these results and making decisions about the future conduct of the trial in order to protect participants.”
Gillen was pleased and humbled to be named a AAAS Fellow, noting that it’s also an acknowledgment of the work of his collaborators and students. He is most proud of the fact that this esteemed recognition highlights and recognizes the practical implications of statistics.
“It’s good to see statisticians acknowledged not only for the mathematical and theoretical developments that we have made, but also for the impact of our research on other sciences,” says Gillen. “To me, that’s a guiding principle of statistical research — not just developing theory for theories sake, but being able to translate it to, in my case, the mission of public health.”
— Shani Murray
Related Posts
Curious mind, compassionate heart, senior spotlight: shengyuan lu overcomes visa limits to reach new heights, marco levorato wins emerging innovator of year award, machine learning and statistics collaboration leads to outstanding student paper at aistats, senior spotlight: maya lee’s journey from anteater to googler, embedded security team ranked 11th in the world at ectf.
Special Features
Vendor voice.
Personal Tech
Two big computer vision papers boost prospect of safer self-driving vehicles
New chip and camera technology bring closer potential of hands-free road time.
Like nuclear fusion and jet-packs, the self-driving car is a long-promised technology that has stalled for years - yet armed with research, boffins think they have created potential improvements.
Citizens of Phoenix, San Francisco, and Los Angeles are able to take one of Waymo's self-driving taxis, first introduced to the public in December 2020. But they have not been without their glitches. Just last month in San Francisco, for example, one of the taxi service's autonomous vehicles drove down the wrong side of the street to pass a unicycle. In December last year, a Waymo vehicle hit a backwards-facing pickup truck , resulting in a report with the US National Highway Traffic Safety Administration (NHTSA) and a software update.
But this week, not one but two groups of researchers bidding to improve the performance of self-driving cars and other autonomous vehicles have published papers in the international science journal Nature.
A design for a new chip geared towards autonomous vehicles has arrived from China. Tsinghua University's Luping Shi and colleagues have taken inspiration from the human visual system by both combining low-accuracy, fast event-based detection with more accurate, but slower visualization of an image.
The researchers were able to show the chip — dubbed Tianmouc — could process pixel arrays quickly and robustly in an automotive driving perception system.
In a paper published today, the authors said: "We demonstrate the integration of a Tianmouc chip into an autonomous driving system, showcasing its abilities to enable accurate, fast and robust perception, even in challenging corner cases on open roads. The primitive-based complementary sensing paradigm helps in overcoming fundamental limitations in developing vision systems for diverse open-world applications."
In a separate paper, Davide Scaramuzza, University of Zurich robotics and perception professor, and his colleagues adopt a similar hybrid approach but apply it to camera technologies.
Youtube Video
Cameras for self-driving vehicles navigate a trade-off between bandwidth and latency. While high-res color cameras have good resolution, they require high bandwidth to detect rapid changes. Conversely, reducing the bandwidth increases latency, affecting the timely processing of data for potentially life-saving decision making.
To get out of this bind, the Swiss-based researchers developed a hybrid camera combining event processing with high-bandwidth image processing. Events cameras only record intensity changes, and report them as sparse measurements, meaning the system does not suffer from the bandwidth/latency trade-off.
The event camera is used to detect changes in the blind time between image frames using events. Event data converted into a graph, which changes over time and connects nearby points, is computed locally. The resulting hybrid object detector reduces the detection time in dangerous high-speed situations, according to an explanatory video.
- Among AI infrastructure hopefuls, Qualcomm has become an unlikely ally
- GhostStripe attack haunts self-driving cars by making them ignore road signs
- Boston Dynamics' humanoid Atlas is dead, long live the ... new commercial Atlas
- US military pulls the trigger, uses AI to target air strikes
In their paper , the authors say: "Our method exploits the high temporal resolution and sparsity of events and the rich but low temporal resolution information in standard images to generate efficient, high-rate object detections, reducing perceptual and computational latency."
They argue their use of a 20 frames per second RGB camera plus an event camera can achieve the same latency as a 5,000-fps camera with the bandwidth of a 45-fps camera without compromising accuracy.
"Our approach paves the way for efficient and robust perception in edge-case scenarios by uncovering the potential of event cameras," the authors write.
With a hybrid approach to both cameras and data processing in the offing, more widespread adoption of self-driving vehicles may be just around the corner. ®
Narrower topics
- Large Language Model
- Machine Learning
- Neural Networks
- Tensor Processing Unit
Broader topics
- Self-driving Car
Send us news
Other stories you might like
Ai smartphones must balance promise against hype and privacy concerns, will windows drive a pc refresh everyone's talking about ai, ai chip sales predicted to jump by a third this year – then cool off, building cheaper, greener 5g networks.
HPE Q2 sales rise was brought to you by the letters A and I
Prepare your audits: eu commission approves first-of-its-kind ai act, using ai in science can add to reproducibility woes, say boffins, raspberry pi unveils hailo-powered ai kit to make the model 5 smarter, google finally addresses those bizarre ai search results, 'building ai co-workers going to be largest opportunity of tech in our lifetime', mit professor hoses down predictions ai will put a rocket under the economy, by 2030, software developers will be using ai to cut their workload 'in half'.
- Advertise with us
Our Websites
- The Next Platform
- Blocks and Files
Your Privacy
- Cookies Policy
- Privacy Policy
- Ts & Cs

Copyright. All rights reserved © 1998–2024

COMMENTS
95+ Latest Cyber Security Research Topics in 2024. The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cybersecurity thesis topics helps overcome attacks and take mitigation approaches to security risks and threats in real-time.
9 👩💻Cyber Security Topics on Computer and Software. There are many reasons to choose cyber security research topics for writing purposes. First, cyber security is a growing field, with many new and exciting developments happening all the time. This makes it an ideal topic to write about, as there is always something new to learn and ...
If you're still unsure about how to find a quality research topic, check out our Research Topic Kickstarter service, which is the perfect starting point for developing a unique, well-justified research topic. A comprehensive list of cybersecurity-related research topics. Includes 100% free access to a webinar and research topic evaluator.
204 Research Topics on Technology & Computer Science. A List of 580 Interesting Research Topics [2024 Edition] A List of 179 Problem Solution Essay Topics & Questions. 193 Interesting Proposal Essay Topics and Ideas. 226 Research Topics on Criminal Justice & Criminology.
This guide lists over 161 thought-provoking computer security research ideas in different areas, such as network security, cryptography, malware analysis, data privacy, ethical hacking, and more. Look through these topics to get inspiration for your next big research project or school paper that could potentially shape the future of digital ...
Machine learning and AI are research topics in cybersecurity, aiming to develop algorithms for threat detection, enhance intelligence and automate risk mitigation. However, security risks like adversarial attacks require attention. Using AI/ML to Analyse Cyber Threats - This cyber security research paper analyses cyber threats and could ...
Cyber Security Research Topics. Cyber Security Research Topics are as follows: The role of machine learning in detecting cyber threats. The impact of cloud computing on cyber security. Cyber warfare and its effects on national security. The rise of ransomware attacks and their prevention methods.
About the journal. Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …. Find out more. The simple economics of an external shock to a bug bounty platform. The cybersecurity of fairy tales.
Although using machine learning techniques to solve computer security challenges is not a new idea, the rapidly emerging Deep Learning technology has recently triggered a substantial amount of interests in the computer security community. This paper seeks to provide a dedicated review of the very recent research works on using Deep Learning techniques to solve computer security challenges.
The article is a full research paper (i.e., not a presentation or supplement to a poster). • The article should make it apparent that AI is its primary emphasis or include AI as a large part of the methodology. For example, publications that explicitly include machine learning as a core component of their methodology/research. •
🖱️ Compelling Computer Security Research Topics. ... It contains thousands of paper examples on a wide variety of topics, all donated by helpful students. You can use them for inspiration, an insight into a particular topic, a handy source of reference, or even just as a template of a certain type of paper. ...
154 Exceptional Cybersecurity Research Topics For You. If you are studying computer science or IT-related course, you will encounter such a task. It is one of the most technical assignments, primarily in the era of advanced digital technologies. Students may not have the muscles to complete such papers on their own.
Operational Security Research Topics In 2023. Securing containerized applications in cloud environments. Implementing secure remote access policies for remote workers. Evaluating the effectiveness of endpoint protection solutions. Protecting against DNS tunneling attacks. Securing cloud-based storage solutions.
Before we start, I should mention that I firmly believe that choosing a topic is not the hardest part of web security research. I've spoken to so many people who have cool ideas but never attempt to execute them. On the rare occasion that someone does mention a research idea that I think is doomed from the outset, it's clear that attempting ...
Computer Security Resource Center. Projects; Publications Expand or Collapse Topics ... Topics Select a term to learn more about it, and to see CSRC Projects, Publications, News, Events and Presentations on that topic. ... Federal Cybersecurity Research and Development Strategic Plan;
The cyber security of a company can be compromised in many ways when it comes to software and computer administration. As such, software and computer administration is a great sources of cybersecurity research paper topics. Here are some of the best topics in this category. Evaluation of the operation of antimalware in preventing cyber attacks.
Check out this list of complex computer security research topics: Discuss the concept of risk management security; The basic principles of a social engineering attack; ... Important Cyber Security Research Paper Topics. Some things are more important than others in the world of cybersecurity. Here are examples of what we consider to be the most ...
Course description. This course covers selected topics related to theory and practice of computer security. It is organized around 26 research papers taken from the past 40 years of computer security research. These papers reflect the instructor's personal taste and are not intended to give a comprehensive survey of modern computer security.
Topics in Computer and Network Security Stanford CS 356, Fall 2023. CS 356 is graduate course that covers foundational work and current topics in computer and network security. The course consists of reading and discussing published research papers, presenting recent security work, and completing an original research project.
Wireless Network Security . Wireless Router . Network Security System. The use of computer networks in an agency aims to facilitate communication and data transfer between devices. The network that can be applied can be using wireless media or LAN cable. At SMP XYZ, most of the computers still use wireless networks.
Håkon Olsen, security engineer and founder of cybersecurity firm Cybehave, weighed in on cybersecurity thesis topics in a recent forum on Quora, where he suggested tackling the subject of identity management. "Investigate how to maximize security within each user's threshold for usability impact," Olsen wrote, adding that most users don't use ...
The methodology adopted in this paper is a review of papers with keywords network security, network attacks and threats and network security measures. The aim of this paper is to critically review ...
The CERT Division is a leader in cybersecurity. We partner with government, industry, law enforcement, and academia to improve the security and resilience of computer systems and networks. We study problems that have widespread cybersecurity implications and develop advanced methods and tools to counter large-scale, sophisticated cyber threats.
He is the New York Times best-selling author of 14 books — including A Hacker's Mind — as well as hundreds of articles, essays, and academic papers. His influential newsletter Crypto-Gram ...
We are proposing a brand new architecture and a fabrication technology that can support the scalability requirements of a hardware system for a quantum computer," says Linsen Li, an electrical engineering and computer science (EECS) graduate student and lead author of a paper on this architecture.
June 5, 2024. Sergio Gago-Masague in front of the CALIT2 Building at UC Irvine. Curiosity killed the cat, goes the old adage. But for Sergio Gago-Masague, curiosity created an unexpected career. The path to becoming a UC Irvine assistant professor of teaching in computer science was winding and uncertain for Gago-Masague.
Security Research Paper Topics - Free download as PDF File (.pdf), Text File (.txt) or read online for free. This document discusses the challenges of writing a security thesis and recommends the service BuyPapers.club for assistance. It outlines the difficulties of selecting topics, conducting in-depth research, and meeting academic standards for security-related theses.
On April 18, 2024, Daniel Gillen was named a fellow of the American Association for the Advancement of Science (), the world's largest general scientific society.Gillen, a Chancellor's Professor and chair of Statistics in UC Irvine's Donald Bren School of Information and Computer Sciences (), was recognized for distinguished contributions to statistical methods.
Like nuclear fusion and jet-packs, the self-driving car is a long-promised technology that has stalled for years - yet armed with research, boffins think they have created potential improvements. Citizens of Phoenix, San Francisco, and Los Angeles are able to take one of Waymo's self-driving taxis, first introduced to the public in December 2020.